



Paladin Technologies growing in America
B.C. company merges with California integrator to leverage U.S. market opportunities p. 6
ONVIF and access control
Standards body outlines the advantages of Profile A p. 20
ADGA’s CEO on security acquisitions
Françoise Gagnon discusses the Ottawa company’s strategy and the need to create more female leaders in security p. 22












Gunshot detection, facial recognition and voice integration with home security systems are among the hot trends that are likely to get hotter this year.
By Will Mazgay
By Bob Dolan
• Bosch renews commitment to AI • Paladin Technologies merges with California systems integrator
• Milestone partner develops tools to manage software updates
9 Camera Corner The secret sauce in VSaaS By Colin Bodbyl
10 Lessons Learned What I have learned about selling security businesses By Victor Harding
New year, new opportunities By Patrick Straw





IBy Neil Sutton
n this issue of SP&T News, we highlight three technology trends that are likely to continue into 2019 and beyond: facial recognition, shot detection and voice integration in home security.
These are among the hottest trends, but they’re not the only ones. Here are a few more to watch for:
With legal recreational cannabis now only a few months old, we can expect to see growth in this market and security along with it. Whether it’s protecting facilities, managing transportation or equipping retail outlets, there is still a lot more work ahead for the security industry.
Last year, ULC launched its Technical Committee S4400 to oversee a new standard for safety in cannabis production. Theresa Espejo, project manager for the committee, told SP&T in the Aug/Sept issue the proposed standard has come “at the behest of local regulators concerned about security in a new and emerging industry.” You can imagine when that committee delivers its findings, there will be a great deal of interest from the security community.
Expect to see more imaginative applications for surveillance in the future, particularly as the industry rolls out the welcome mat for software developers who see camera apps as the next frontier.
The security industry in general has become more adept at marketing its value proposition for applications other than just surveillance. (Our story in the October
issue, for example, looked at how cameras are being used more effectively in smart buildings.)
ONVIF also recently held an open source developer contest, which received entries from all over the world. It was won by Liqiao Ying, a Waterloo, Ont.-based developer, whose winning software utilizes a blockchain framework for storage of camera information (see the Aug/Sept issue for that story). A Bosch start-up called SAST is also working on a camera operating system that could be a haven for app developers (see p. 6 for more on this). There are great things to come and 2019 could be the tipping point.
Drones are probably one of the most difficult technologies to speculate about, since there are so many variables in play. But we are at least seeing some movement in this sector. At the beginning of this year, Ottawa released new rules governing the use of drones. On the flip side, look for drone detection technology to get more sophisticated and widespread. The number of reported drone sightings near airports has created a more urgent need for this. Disruptions at two major U.K. airports, Gatwick and Heathrow, are two of the most recent incidents, but they’re not the only ones. (Read more commentary on this subject from Unmanned Systems Canada in the Winter issue of Canadian Security magazine.)
All in all, expect 2019 to be one of the most exciting years yet for the security industry.

Your Partner in Securing Canada Security Products & Technology News is published 8 times in 2019 by Annex Business Media. Its primary purpose is to serve as an information resource to installers, resellers and integrators working within the security and/or related industries. Editorial information is reported in a concise, accurate and unbiased manner on security products, systems and services, as well as on product areas related to the security industry.
Group Publisher, Paul Grossinger 416-510-5240 pgrossinger@annexbusinessmedia.com
Account Manager, Adnan Khan 416-510-5117 akhan@annexbusinessmedia.com
Editor, Neil Sutton 416-510-6788 nsutton@annexbusinessmedia.com
Associate Editor, Will Mazgay wmazgay@annexbusinessmedia.com
Media Designer, Graham Jeffrey gjeffrey@annexbusinessmedia.com
Account Coordinator, Kim Rossiter 416-510-6794 krossiter@annexbusinessmedia.com
Circulation Manager, Aashish Sharma asharma@annexbusinessmedia.com Tel: 416-442-5600 ext. 5206
President & CEO, Mike Fredericks
EDITORIAL ADVISORY BOARD
Colin Doe, Veridin Systems Canada Anna Duplicki, Lanvac Victor Harding, Harding Security Services Carl Jorgensen, Titan Products Group Antoinette Modica, Tech Systems of Canada Bob Moore, Axis Communications Roger Miller, Northeastern Protection Service Sam Shalaby, Feenics Inc.

111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1 T: 416-442-5600 F: 416-442-2230
PUBLICATION MAIL AGREEMENT #40065710
Printed in Canada ISSN 1482-3217
CIRCULATION
e-mail: asingh@annexbusinessmedia.com
Tel: 416-510-5189 • Fax: 416-510-6875 or 416-442-2191
Mail: 111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1
SUBSCRIPTION RATES: Canada: $42.00 + HST/yr, USA: $74.00/yr and International: $84.50/yr
Published 8 times a year


Occasionally, SP&T News will mail information on behalf of industry-related groups whose products and services we believe may be of interest to you. If you prefer not to receive this information, please contact our circulation department in any of the four ways listed above.
Annex Privacy Officer privacy@annexbusinessmedia.com Tel: 800-668-2374
No part of the editorial content of this publication may be reprinted without the publisher’s written permission. ©2019 Annex Publishing & Printing Inc. All rights reserved.
Annex Publishing & Printing Inc. disclaims any warranty as to the accuracy, completeness or currency of the contents of this publication and disclaims all liability in respect of the results of any action taken or not taken in reliance upon information in this publication.















Stefan Hartung, the member of Bosch’s board of management responsible for energy and building technology, recently stated that “in 10 years, every electronic Bosch product will either utilize AI itself or will have been developed and manufactured with its help.”

According to Bosch, the company will increase its investment in AI, and has earmarked 300 million euros ($456M) to expand the Bosch Center for Artificial Intelligence (BCAI) by 2021. The BCAI currently employs 170 experts; Bosch anticipates that number will increase to 400.
“They are currently working on some 80 development projects — from automated driving to applications in medicine and manufacturing.
Many of these are being carried out in collaboration with academic partners, including the universities of Tübingen, Stuttgart, and Amsterdam,” the company said in a recent press release.
One example of Bosch technology that utilizes AI is a camera that uses smart image analysis to locate fires — spotting smoke or flames within seconds, according to the company.
Bosch also recently established a new company called SAST (Security and Safety Things) which is working on an IoT platform for security cameras that can run on the edge.
Hartmut Schaper, the CEO of SAST, told SP&T News in a September 2018 interview, that the company’s operating system, currently under development, will initially be provided to the members of the new Open Security and Safety Alliance, and will soon be available more widely. (The alliance formed in Sept. 2018 with founding
B.C.-based Paladin Technologies announced in January it has completed a merger with U.S. installer Tekworks Inc.
TekWorks is based in San Diego, Calif., with clients across the U.S. The company employs more than 200 people and offers professional services including security systems, audio visual, network cabling, data centres and network services. According to Paladin, it will maintain all operations including current branding and office locations.
“TekWorks will continue to operate as is under the TekWorks brand, as a Paladin Technologies company for the foreseeable future, yet there will be a significant amount of collaboration with TekWorks for consistent implementation of best practices amongst the Paladin group of companies,” said Ted Reid, pres-
ident of Paladin Technologies, in an email to SP&T News.
“As we reviewed our strategic options, it was clear that merging with Paladin Technologies was the right fit not only for our people, but also our clients,” added William Bourgeois, president of TekWorks, in a statement.
ROTH Capital Partners, LLC served as TekWorks financial advisor on the merger and Hahn Loeser & Parks LLP provided legal counsel. Morrison & Foerster LLP served as legal advisor to Paladin Technologies.
This is the first U.S. deal from Paladin since its 2017 merger with Criterion Security, which was subsequently renamed PalAmerican Security.
The Paladin group of companies currently employs more than 13,000 people.
— Neil Sutton
members Bosch Building Technologies, Hanwha Techwin, Milestone Systems, Pelco by Schneider Electric and VIVOTEK.)
Ultimately, the OS, which is based on the Android Open Source Project, will be an ecosystem “where people will develop apps for surveillance cameras that haven’t even been thought of today,” he said.
The OS could provide more flexibility and freedom, he added, since developers wouldn’t have to develop for specific cameras but create an app once and have it run on many different cameras. “We think this is a significant change to the industry, driven by the increasing connectivity, but also by the much higher computing power on the edge,” he said.
The OS has been tested with facial recognition and licence plate recognition apps, said Schaper, and has been well received by integra-

Boring Toolbox aims to improve the management of routine but time-consuming updates like password management
ACalifornia-based systems integrator has made “boring” a business.
El Segundo-based Continental Computers has worked with Milestone Systems for more than a decade, deploying and managing Milestone’s video management system for end user clients.
Ronen Issac, vice-president at Continental, says the company originally began as an IT services firm and moved into video surveillance 11 years ago — about the same time it started working with Milestone. The bond between the companies has strengthened since then. Continental is a platinum Milestone partner and won its regional partner of the year award in 2014.


More recently, Issac says, the staff at Continental recognized that efficiencies could be achieved within the Milestone tools, particularly when it comes to managing essential but tedious updates.
After working with a large customer, “we realized that while the management client is super-powerful, it’s missing something that larger system admins would really want — namely bulk features,” explains Issac. “The big one was, for cybersecurity purposes, password management.”
Issac’s company created a tool for its installers to use to handle batch updates. The tool proved to be a huge success, says Issac, warranting a spin-off software company to support it.
“We realized that there’s a market out there for this,” he says. “There’s other people out there who have the same issue. Let’s turn it into a product.”
Issac and his team created a company called The Boring Lab and thusly named its new software suite The Boring Toolbox “to do all those boring tasks that Milestone systems admins need to do in order to be compliant or to simply manage their system in an appropriate way.”
Issac says Milestone was very supportive from the outset. “We have a really good relationship with Milestone simply because we’ve been working with them for so long.
When we started developing this tool, we basically came up with a prototype and showed it to their alliances team. They actually got really excited about it.”
(Milestone has published a post on its official blog about the Boring company entitled “The Boring Toolbox Slashes Time Spent Managing XProtect VMS – Up to 97%”)
Milestone provided input along the way to help improve the software and its ability to manage aspects of Milestone’s XProtect VMS, says Issac. In addition to password management, it can also help with reporting functions and device management. For example, Boring software can be used to manage settings on surveillance cameras that are connected to the VMS.
The Boring Toolbox can be integrated tightly into Milestone but it is still a third-party tool, says Issac. Adding software to VMSes is quite common, he notes, such as analytics or other feature-based tools, but he says he isn’t aware of other software that is explicitly designed to improve the performance of a VMS. “As far as I know, we’re a bit of an outlier.”
Boring officially launched last October and had two clients at press time: an integrator and a university.
Demo versions of the software and 30-day free trials are available from the Boring Lab website. The company is also fine-tuning a software licensing model for future sales of its Toolbox. “It’s been a really good ride so far and we’ve had a lot of good feedback,” says Issac.
— Neil Sutton
Benefits include:
n Directly addresses unauthorized card use and eliminates threat of lost cards
n Compatible with many 13.56 MHz and 125 kHz RF readers
n Secure and intuitive biometric 2-factor authentication, without upgrading readers
n Features on-card fingerprint touch sensor with 3D capacitive technology for superior imaging
n Addresses privacy concerns with on-card biometric data storage
n Delivers consistent and accurate fingerprint reads in one second
n Eliminates the need to manage and secure an external database since biometric data is stored on the card
n Works with most existing employee ID systems and Electronic Access Control (EAC) Solutions
For more information on the product please call: 416-614-7777 (ext. 81) or email at sales@abcsecurity.ca

Kentucky medical facility upgrades access control

Estill County Emergency Medical Services, in Irvine, KY, has upgraded its access control using infinias access control from 3xLOGIC. Bates Security, of Lexington, KY, designed and installed the system.
“We were looking to secure a building that is in operation 24/7/365,” said Shelia Wise, who is in charge of accounting and training for Estill EMS and also oversaw the security upgrade.
“Our main goals were to secure our medical room, per DEA regulations, and to make our facility safe when staff are here, but also when they need to clear out at a moment’s notice.”
Installation was completed about two years ago and the infinias system manages a total of six doors at the main EMS building.


• Ottawa-based Feenics, a provider of access control as a service technology, recently opened a new office in Beirut, Lebanon, led by Nancy Abou Eid.
• Paladin Technologies has appointed Chris Clarke as director, Atlantic Canada.
• Arecont Vision Costar has announced the appointment of John Sprague as regional sales
Pharm Research Associates Ltd., a research centre located in the U.K., recently updated the entrance door at its Reading headquarters.
The centre worked with provider Boon Edam on a new entrance solution — one that would meet the requirements of a pharmaceutical company and its stringent security and data protection requirements. Pharm Research Associates required an access solution that not only met security needs, but also fit in with the established culture. The client selected Boon Edam’s automatic Tourlock 180+90 security revolving door with an aluminum finish for its entrance.
According to Boon Edam, the Tourlock 180+90 prevents unauthorized entry attempts (tailgating and piggybacking), while supporting simultaneous, bi-directional throughput.



manager. Sprague is responsible for customer and partner sales support across the Northeastern United States and Eastern Canada.
• Bold Perennial announced that Robert Gelinas has joined the executive team as vice-president of sales and marketing.
• ALE, operating under the Alcatel-Lucent Enterprise brand, announced they have

A discount shopping chain in Dubai and across the United Arab Emirates is expanding and required a solution to manage employee attendance and overtime across its many locations.
The store provides everything from apparel to appliances to office supplies. It has more than eight locations, the largest of which is in Sharjah, the third largest city in the UAE.
The company has deployed a biometric solution from Matrix, utilizing its time-attendance module along with a fingerprint and cardbased door controller.
The solution helps to manage employee arrivals and departures, as well as overtime hours. It also generates reports with filtering options for attendance details. Matrix says that its client has experienced easier shift and schedule management as well as smoother HR processes.


appointed Darren Giacomini, director of Advanced Systems Architecture at BCDVideo, to their Global Customer Advisory Board.
• Rick Caruthers was recently appointed to the position of president at Galaxy Control Systems. Caruthers has risen through the ranks in positions ranging from regional sales manager to his new role.
February 23, 2019 4th Annual Mission 500 Hockey Classic Toronto, Ont. www.sptnews.ca
March 7, 2019
Security Career Expo Toronto, Ont. www.securitycareerexpo.com
April 2-4, 2019 Canadian Technical Security Conference Cornwall, Ont. www.ctsc-canada.com
April 8-11, 2019 ICT Canada Toronto, Ont. www.bicsi.org
April 10-12, 2019 ISC West Las Vegas, Nev. www.iscwest.com
April 24, 2019
Security Canada East Laval, Que. www.securitycanadaexpo.com
May 8, 2019
Security Canada Ottawa Ottawa, Ont. www.securitycanadaexpo.com
May 29, 2019
Security Canada Alberta Edmonton, Alta. www.securitycanadaexpo.com
June 2-6, 2019
Electronic Security Expo Indianapolis, Ind. www.esxweb.com
June 13, 2019
Security Summit Canada Toronto, Ont. www.securitysummitcanada.com
June 19, 2019
Security Canada West Richmond, B.C. www.securitycanadaexpo.com
September 8-12, 2019 GSX Chicago, Ill. www.gsx.org
September 11, 2019
Security Canada Atlantic Moncton, N.B. www.securitycanadaexpo.com

VBy Colin Bodbyl
The “as a service” model is quickly gaining ground in the surveillance world
aaS stands for Video Surveillance as a Service.
The name is a spinoff of SaaS (Software as a Service) which was introduced in the late 1960’s but did not gain widespread recognition until the early 2000’s after Salesforce leveraged the SaaS business model to build the world’s most popular customer relationship management software.
The concept behind SaaS is simple. Rather than asking customers to buy software, install it on their own computer, and maintain it throughout its lifecycle, SaaS companies allow you to use the software through a web browser over the internet. This removes the responsibility of the user to maintain the software. It also allows them to access it from any computer with an Internet connection. The cost structure is also very different; instead of paying an upfront fee to purchase the software, SaaS customers pay a recurring fee (usually monthly). The SaaS business model

Even today, most commercial end users choose to use an on-premise solution utilizing their own hardware rather than pay for a VSaaS solution, but things are changing.
Traditionally, investing in a fully on-premise video surveillance system has always made sense. The technology changed very little over
“VSaaS has a huge advantage over traditional systems in that it can offer the service immediately.”
has proven extremely successful as it is cost effective for customers to signup, creates a constant stream of cashflow for the provider, and makes it very difficult for customers to ever leave. With the obvious benefits of the SaaS business model, it is no surprise that video surveillance software providers have been making efforts to enter the SaaS business for some time now.
Historically VSaaS has not been particularly popular for commercial video surveillance. Bandwidth costs and limited benefits prevented end users from adopting the technology.
a five-year period and there was little reason to upgrade until the system had reached the end of its useful life. But the introduction of AI is beginning to change that. End users are starting to expect features like video analytics and object recognition as part of their surveillance solution, but these features require expensive hardware that may sit idle unless the customer is actively using the software. Furthermore, when new features are released, end users expect to have access to these features in a much shorter timeline and without having to upgrade their
hardware. All these requirements make specifying the hardware for a new install challenging, and that is where VSaaS may become a better option.
VSaaS solutions typically operate on one of the large cloud platforms hosted by either Google, Amazon or Microsoft. If a new software feature requires more processing power, these providers scale up in an instant to meet that demand, and the costs are insignificant. Where an end user with an on-premise solution may be facing the cost of a two thousand dollar GPU card to add AI to their server, that same service could cost pennies a month to contract through a VSaaS provider.
The biggest challenge facing VSaaS providers is bandwidth. Consistent and stable bandwidth is often difficult to get. Most VSaaS providers get around this issue by supplying a bridge appliance or mini server that sits on the client site and acts as a backup should the internet connection be lost for any reason. This of course somewhat reduces the value of using VSaaS if a physical piece of hardware is

required for the system to function. While VSaaS providers may be able to work around unstable bandwidth with the use of a bridge appliance, the cost of bandwidth is a bigger issue. Streaming video to the cloud requires a lot of bandwidth, something that may be unlimited in some areas, but in others unlimited bandwidth is not available and exceeding your ISP’s bandwidth cap can get extremely expensive.
The same costs that prevented VSaaS adoption in the past remain relatively unchanged. The benefits of VSaaS, however, are changing rapidly. As AI improves and more end users push for access to the technology, VSaaS has a huge advantage over traditional systems in that it can offer the service immediately, with almost no upfront cost to the customer. If bandwidth costs do change in the future VSaaS may enjoy even faster user adoption but even if they remain the same the benefits of VSaaS are quickly going to eclipse the costs.
Colin Bodbyl is the chief technology officer of Stealth Monitoring (www.stealthmonitoring.com).

IBy Victor Harding
Wisdom gleaned from 20 years in the industry, the last 10 running a brokerage firm
have been involved in buying and selling security companies in Canada for more than 20 years, and owning and running a brokerage business like Harding Security for the past decade has given me invaluable insight and experience into how fire, guard and integration companies are valued and sold. Here are some insights I have gleaned. I hope many of you might profit from my experience.
1. Despite all the naysayers on the usefulness of EBITDA as a valuation tool, most small and medium sized companies in almost all industries today are valued as a Multiple of Normalized EBITDA or Earnings before Interest, taxes and depreciation. We use EBITDA rather than simple Earnings before taxes because buyers want to factor out debt and depreciation charges to get to a cash flow number. Normalizing EBITDA refers to the process of adjusting EBITDA for any material, non-recurring revenue or expense items and any abnormal “Owner’s Take.” In determining price, buyers will pay more attention to past EBITDA numbers than the future.
2. One calculates Enterprise Value (EV) by settling on a suitable “multiple” of EBITDA to determine a company’s worth. Generally small companies trade for three to five times EBITDA. Larger public companies can trade for multiples of anywhere from eight to 15 times. Besides the size of the company, this multiple can be affected by the following: Is the company growing? Are the margins in the company attractive? How much recurring monthly revenue does the company have? Does the company have a unique value proposition that will protect it from competitors? Is the company’s revenue spread over a large number of customers? In the integration and fire companies I have sold in the last year, the multiple have varied from 4.5 to 6.5.
3. As mentioned above, Enterprise Value is what you get when you multiply EBITDA times a suitable multiple. But here’s the thing: Enterprise Value = Working Capital + Fixed Assets + any Intangibles. When you sell a business valued this way, the buyer expects to get a reasonable amount of working capital plus all the fixed assets

required to run the business for the price. Some of my clients have suggested to me after I quote them a ball park valuation figure, in addition they should get the value from their balance sheet on top of the Enterprise Value. Not going to happen.
4. Alarm companies, companies where the bulk of the value is in the recurring monthly revenue, can also be valued using a multiple of EBITDA but for simplicity’s sake buyers tend to revert to a Multiple of Recurring Monthly Revenue (RMR). Some owners of alarm accounts think all alarm accounts bases will sell to anybody for 36X RMR. Not true. A large batch of high margin, low attrition accounts all on signed contracts and on a call forward line may sell to a strategic buyer like a bigger alarm company for 36 times but the buyer has to be able to buy the base without any other expenses and get the seller’s telephone number in the deal for future referrals.
5. You might think that all buyers will end up with the same Enterprise Value when looking at a target company. After all, how much can EBITDA and the multiple vary? Well the answer is quite a lot depending on the buyer. A strategic buyer — someone from the same industry that is “rolling up” companies — may well get the opportunity to take more efficiencies post closing than a financial buyer who basically has to leave the existing organization and cost structure in place post closing. Being able to reduce
costs produces a higher normalized EBITDA number and therefore a higher potential purchase price. Valuations can depend on who the buyer is. Strategic buyers generally pay higher prices than financial buyers.
6. Selling any business, no matter how small, takes time. Most security businesses I have been involved in take anywhere from six to 12 months to sell or longer. Fire and integration businesses take longer than alarm companies. Security businesses in big cities usually sell faster than those in the hinterland. Deals where the buyer uses financing usually take longer than when the buyer has the capital. Share deals generally take longer than asset deals. Over-riding all these points is another rule: the longer it takes to close a deal, the greater the chance of the deal not closing.
7. A good time to sell your business is when:
• Economic times are good and valuations of public and private companies are high.
• Your company is doing well and growing. You have two years of solid numbers to show.
• There are lots of buyers in the marketplace. Interest rates are low.
Generally the more deals you do as a broker, buyer or seller the better you get at it.
Victor Harding is the principal of Harding Security Services (victor@hardingsecurity.ca).
By Patrick Straw
CANASA plans to execute on its strategies and support members’ growth throughout 2019
At CANASA, we have identified a number of initiatives for 2019 that will see the association increase our influence and efforts within the profession and the public as we continue to build awareness of the issues revolving around all things security.

Recent initiatives have been put in place as CANASA expands the focus on providing security professionals with the tools to assist them in their day-to-day operations.
The following information is an outline of the services provided to assist industry professionals:
Advocacy: CANASA participates in a number of industry-related organizations ensuring that members are up-to-date on the latest issues. Some of the organizations where CANASA participates includes the Canadian Association of
Chiefs of Police, ULC, ASIS, Crime Stoppers and fire and safety associations across Canada.
Security Canada: The country’s leading security shows will look to continue the growth experienced in 2018 by once again producing six shows in major centres across the country: Laval on April 24; Ottawa on May 8; Edmonton on May 29; Richmond, B.C. on June 19; Moncton on Sept. 11 and culminating with the largest security show in Toronto for two days on Oct. 23 and 24. Information on all of the Security Canada shows is available at www.securitycanada.com.
Council events: Members are encouraged to attend the important industry events held throughout the year organized by the various CANASA regional councils.
In 2018, we saw a number of important events designed to provide relevant information to members’ businesses. Key experts and leaders in their respective fields participate throughout the
year. Watch for all the details at www.canasa.org.
Education: This is a vital component, ensuring that our members stay competitive. CANASA offers a number of courses that provide insight and guidance into how to grow and maintain members’ businesses, such as the Alarm Technician Course.
In addition, CANASA offers opportunities through the Professional Security Knowledge Network; Safety Culture and STAM interactive training courses via our Affinity Partners. More information can be found at www.canasa.org.
Not a member of CANASA?
For more on membership and how to join Canada’s national security association, please contact erepper@canasa.org or call at 1-800-538-9919 extension 223.
Patrick Straw is the executive director of CANASA (www.canasa.org).


The security industry, once accused of being slow to adapt, seems to have thrown off those shackles and is now accelerating at breakneck speed.
Much has been written and conjectured about the influence of AI and machine learning on security systems, but there are also outside influences that are pushing the industry in new directions.
The threat of active shooter incidents
has placed a new premium on the value of gunshot detection technology, which can help to pinpoint the location of a shooter or the origin of a gunshot, delivering valuable information to security professionals and first responders quickly.
Home security technology is also on the cusp of transformation, driven in part by the number of security tools that now integrate with popular voice command technologies from Amazon, Google and other providers.
Facial recognition, once considered too inaccurate to be truly useful has also come a long way in a short time, thanks in part to the aforementioned advances in machine learning technology.
These three technologies are not the only areas of advancement for the security industry, but they are certainly indicative of growth and transformation.
GUNSHOT DETECTION
Speed and accuracy of data are essential when there are lives on the line
By Will Mazgay
As the spectre of the active shooter looms large, firms are working to develop and hone technologies to help mitigate and even stop the damage these attacks can inflict — by finding shooters quickly and getting that information to the relevant parties.
Gunshot detection systems use audio and visual sensors to pick up the sound and sight of gunfire and pinpoint where exactly it is coming from. These systems can also communicate with video management systems (VMS) to capture images and video clips of the shooter.
Once all of the relevant information is collected — where the shot was fired, when it was fired, and who fired it — it is sent to first responders, security teams and affected civilians, through email, text or notification apps.
For Kathleen Griggs, president and founder of Virginia-based Databouy, which provides
gunshot detection through a system called ShotPoint, VMSes are particularly helpful in identifying shooters.
“We want to make sure that we get not only the best picture of the shooter but we want to get it as close to the moment as the shot has actually occurred so we have the best evidence and so you can positively identify who the shooter is. That’s the information you need to close down the shooter, mitigate the event, and make sure everything is completely safe and clear for EMS to
“The multiple sensor approach is what allows us to get good localization and it also eliminates false detection.”
— Kathleen Griggs, Databouy
arrive,” says Griggs.
ShotPoint uses acoustic sensors to pick up the sound of gunfire, each of which has four microphones that can work together in an array to find the exact spot where a shot is fired. Individual sensors can also communicate other sensors in the area to further pinpoint and verify where the shooter is, then the data is fused to create a single report.
“The multiple sensor approach is what allows us to get good localization and it also eliminates false detection,” says Griggs.
ShotPoint can be adapted for both indoor and outdoor use, but another firm has developed two separate technologies to meet the challenges of detecting gunfire in indoor and outdoor spaces.
Shooter Detection Systems LLC (SDS), a Massachusetts-based firm, provides both an outdoor system, Boomerang, and an indoor, Guardian.
Boomerang is an audio system based on miced up sensors that calculate a shooter’s location based on the shockwave of a bullet and a gunshot’s muzzle blast energy. Sensors can either be placed on fixed structures or go mobile, either affixed to vehicles or attached to a person.
Christian Connors, CEO of SDS, says the Boomerang is typically used to monitor electrical substations and critical infrastructure, targets vulnerable to terrorist attack or sabotage.
Conversely, the indoor Guardian sensors use a combination of microphones to pick up acoustics and infrared camera sensors to detect the muzzle flash from a gun, something more easily seen in the close confines of an indoor space.
“We validate the acoustics with the infrared,” says Connors.
Guardian and Boomerang sensors can be used together to protect premises that have indoor and outdoor space, such as sports stadiums and concert venues, and the challenge of walls (which impede acoustics), can be overcome with strategic placement of sensors.
“It’s not cheap to put these sensors everywhere, so we cover where the shootings happen, which is hallways, common areas, entrance ways, and any large gathering areas…where the likelihood of an active shooter event is to happen,” says Connors.
Large event spaces are also challenging because of noise, and this can be addressed, as well as in other loud locations like factories, with lighting alerts to go along with PA announcements. A blue light signaling an active shooter is easy to understand, even in loud and chaotic circumstances.
Connors continues, “Things like the Vegas incident, god forbid, any location where there’s a large gathering of people, you set up a couple of these sensors and report the location of the shooter in about a second and a half.”
Connors says his system is not only fast, but reliable, with the Guardian system boasting a 100 per cent detection rate and zero false alerts. Surprisingly, Connors does not attribute this to machine learning, but old-fashioned experience and testing.
“You learn a lot over time looking at log files and data,” he says. “We have been doing this for so long we don’t have a lot to learn about what gun shots are and what they’re not. I know some other folks using AI, that implies that there is learning going on. We have the learnings finished.”
Griggs agrees: “What we have behind our system is a decade of test data. So, whether we call it experience or however we categorize both the event and the environment, and how we know what works, there’s no substitute for actual live testing. So, I would say that this a problem space that we just know really well.”
Both firms have garnered extensive test data and experience not just from their work in civilian spaces but through their military roots.
The Guardian system cut its teeth in Iraq and Afghanistan, starting in 2003, detecting sniper fire while affixed to soldiers, transport trucks, helicopters — in the latter cases, at high speeds. The system was an initiative of The Defense

Advanced Research Projects Agency (DARPA), a research and development agency within the United States Department of Defense (DOD). Boomerang is still distributed to military customers through an SDS sister company.
As for Databouy, Griggs is a former navy engineer and technical agent for DARPA, and secured a US$18.5 million contract from the DOD.
“We have 10 years of DOD research behind our systems,” says Griggs.
Both firms moved into the private sector and commercialized in the last few years, and are now on the front lines of a different fight, keeping workers, students and people in general safe from violence, be it organized terrorism, a lone wolf shooting or street crime.
“We’re in everything from airports to Fortune 500 companies, universities, schools, aquariums, city halls, governor’s mansions,” says Connors.
Griggs says her ShotPoint system is used in hospitality, industry, corporate spaces and schools as well.
Municipalities are also interested in these systems to monitor and prevent violent street crime and other incidents.
“Cities are looking at trying to target areas where there’s a lot of high crime and a lot of shooting,” says Griggs.
Outdoor shot detection technology has already been adopted by a large number of cities across the world. This summer, Toronto’s city council approved funding for California-based ShotSpotter Inc.’s audio surveillance tool, following a mass shooting in the city’s Greek Town.
For her part, Griggs is hoping to get involved in this market. “We’re set up to go on street lights We’re definitely hoping that cities start thinking about including our system when they’re putting
in new streetlights.”
Connors, on the other hand, is setting his sights on adapting indoor sensors on a massive urban scale.
“Hopefully what we’ll be able to announce here in the first quarter is one of the largest cities in the U.S. doing something that no one’s ever done, all about indoor active shooter detection,” Connors says.
Despite his optimism on this new initiative, he is still preaching patience. “City outdoor gunshot detection has become somewhat of a standard. We’re not there yet for indoor, but it’s growing at a pretty fast clip.”
Databouy is even looking beyond just detecting gunshots, to tracking falling objects or car crashes.
“These are things that happen in a busy environment that cameras don’t necessarily pick up very well, that actually do enhance public safety,” Griggs says. “In all likelihood, you’re going to have a sensor that’s put out there, that’s going to sit out there for 20 years that may never hear a shot. But it’s going to hear a lot of other things, that sending an alert would help for public safety reasons.”
As for the future of shooter detection technology, Connors is predicting growth: “You’ll see it get more widespread. We’re always looking at larger coverage areas, lower costs, easier installations, and for us a lot of it is focused on the market itself. It’s still a very small market, compared to the overall security industry.”
Fueling that growth for SDS is its network of integrators, which includes firms like Johnson Controls, Convergint and Siemens, which have been spending advertising capital on gunshot detection — not the case a few years ago.
“Integrators are seeing that the market is growing, and they’ve put a lot of horsepower behind it,” says Connors.

Systems are becoming smarter, more effective and more accurate
By Will Mazgay
Once considered unreliable, facial recognition has taken a huge leap forward and become increasingly accurate and fast.
One expert says this is due to advanced machine learning techniques, greater computing power that can process very large amounts of data, and the availability of larger databases.
Elke Oberg, marketing manager of German multinational facial recognition firm Cognitec Systems GmbH says, “It is now at a point where end users can see the benefits, see that it’s working, that the accuracy is sufficient enough, and that you get a very low rate of false alarms.”
Oberg says Cognitec’s main business is in identification management, using face recognition to check for ID fraud in large databases. The firm is also heavily involved in border security, through e-gates, self-service checkpoints used in airports which verify individuals against their passports.
But Cognitec’s latest addition to its product portfolio is real time video surveillance — run ei-
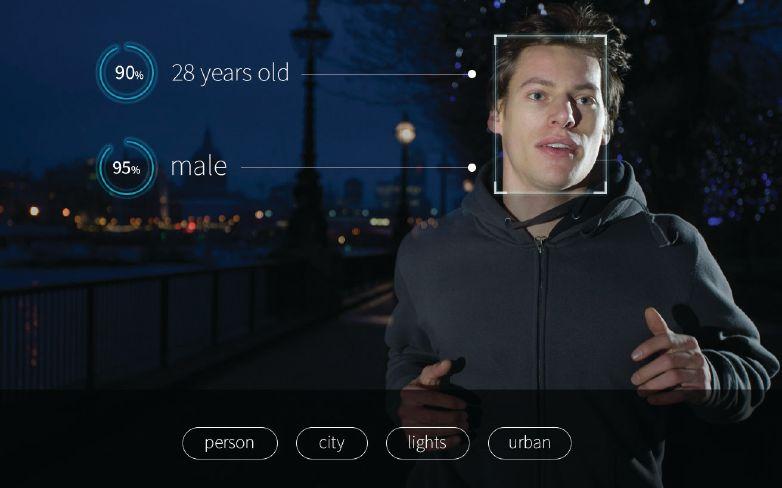
ther through existing video management systems and cameras or its own IP camera — looking at people in a room and comparing them against a database of known persons of interest.
“These people don’t necessarily have to be people you’ve banned or who’ve stolen, or who have committed some kind of crime,” said Oberg. “You can also use it to recognize valued customers, or what we are doing in the gaming industry as well, people who have a gambling problem, they can self-enroll in a database and

California-based Kogniz Inc., a start-up with about 20 employees, also offers video facial recognition, along with object identification, activity monitoring and watchlists for access control, but with a slightly different product — an edge-based camera which runs the processing within itself. Managed through the cloud, the firm says this method eliminates the need
“The fact that we have so much processing capability running locally on the device itself, lets us literally put in a camera in any environment with no additional hardware and provide industry leading recognition,” says Jed Putterman, the company’s co-founder. “This has traditionally been a difficult, inaccurate, cumbersome type of technology to implement. And we’ve tried to democratize it to the point where it’s as simple as plugging in a camera and turning it on.”
He asserts that the ease of use and affordability of his firm’s technology have made it a viable option for smaller businesses who “traditionally never would have been able to afford it.”
On the software side, Putterman says frequent upgrades help his cameras “keep getting smarter,” and the firm’s algorithms benefit from machine learning and extensive training.
While Putterman is confident in his solution, he notes that the models used are only as good as the data that is fed into them.
“A lot of them (data) probably are very skewed towards white, middle-aged personalities,” said Putterman. “What happens is, when you train against a specific group, you become very good at finding that group and you become very bad at finding anyone outside of that.”
He says the solution is to train algorithms with data that pulls from a diverse and representative collection of people.
Oberg agrees that larger databases, which are becoming more readily available, are helpful, since the more images algorithms have to train on, the more accurate they are going to be.
FOR MORE THAN 30 YEARS, ALTRONIX HAS PROVIDED STATE-OF-THE-ART POWER SOLUTIONS MERGING INFRASTRUCTURE WITH EMERGING TECHNOLOGY. OUR TEAM OF ENGINEERS AND DESIGNERS PRODUCE AWARD WINNING PRODUCTS FOR THE PROFESSIONAL SECURITY INDUSTRY - PROUDLY MANUFACTURED IN OUR NEW YORK HEADQUARTERS. ...TECHNOLOGY IN MOTION.
While access to extensive data is a boon to facial recognition, combing through exhaustive information can also pose a challenge.
“When you have an IT database with millions of images, the rate of false positives or false negatives is obviously still quite high. It’s just a massive amount of images, so the more you can reduce that, the better,” Oberg says.
Putterman agrees that the technology is not infallible, and says to mitigate errors and create the desired outcomes for his customers, Kogniz’ system can make adjustments.
“If you’re looking for someone who you’re concerned will cause harm… you’d rather put up with a few false positives, but you really want to make sure with certainty that you don’t miss that person,” he says. Conversely, if a customer is looking for a VIP guest to give them a warm welcome, false positives aren’t ideal. “We can error on one side or the other to give pretty extraordinary results.”
Another challenge the technology is grappling with is poor image quality.
Oberg says machine learning techniques and enhanced data processing have allowed lighting processing to improve and algorithms to learn different poses and get more accurate tracking variances.
“We can error on one side or the other to give pretty extraordinary results.”
— Jed Putterman, Kogniz
Accuracy isn’t the only priority; customers need results fast too.
“If the person is seen and you get the alert five minutes later, that does not help security staff at all,” says Oberg.
She preaches a holistic approach to getting it right quickly, cameras with adequate bandwidth so the data can move quickly, enough computing power to scan and compare images quickly, and how security staff act on the information: “The human aspect is obviously not completely going away; they need to react to the information as well.”
Beyond picking out persons of interest, Oberg says facial recognition in video surveillance has useful anonymous applications, in crowd control and people counting. Cameras can survey if people are moving through an area in a prescribed time, or if too many people are gathering in an area. Oberg says airports are using it to measure how long it takes people to get from the entrance all the way to the gate, data that has implications on how airports are set up, security practices and regulations.
Putterman says people counting has applications beyond security in retail, Kogniz’ most significant vertical. Understanding how many

people are in a store and how long they’ve been standing in line can help businesses to allocate staff, or for marketing purposes, it can be determined how long shoppers are staying in the store and in which areas, whether they are new or repeat visitors, and if they’ve been to other stores.
Facial recognition can also target advertisements to individuals based on demographics data.
Agustin Caverzasi, CEO and co-founder of Argentina-based multinational Deep Vision AI Inc., is applying this concept on a city-wide scale, part of his firm’s Smart Cities video monitoring initiative. Age and gender of pedestrians are gathered by cameras, and people are counted. This data can then help customers understand the makeup of a particular area of a city, and target ads accordingly.
Caverzasi says, “brands and advertisers are taking the meta data we provide, which is anonymous information, but it’s hyper-personalizing the ads to the right people and increasing the value of the advertising.”
Deep Vision’s technology can be deployed by customers connecting their application programing interface to the firm’s cloud infrastructure; on premise, for environments with security constraints like banks or airports; and on the edge, through graphic processing units embedded in cameras. Regardless of the preferred method, Caverzasi says the technology can be seamlessly integrated into an organization’s existing video management system and security infrastructure.
Caverzasi’s firm’s services also rely heavily on analytics and machine learning.
“What we are doing is training with different data, and over time, our data sets are getting more and more robust,” he says.
This technology is being embraced by municipalities, as Deep Vision currently has three different pilots in three different cities, both for advertising and its security application, which tracks persons of interest and vehicles.
When it comes to getting his technology to market, Caverzasi credits integrators, VMS companies, camera manufacturers and even partners that provide complimentary technology, such as weapons detection on the security side.
Cognitec also makes use of integrators and value-added resellers, and while Kogniz does work with integrators, Putterman promotes direct sales as a way of providing extra attention to customers.
Putterman says that regardless of its use, facial recognition technology will keep getting better. “We’ll continue to evolve. We’ll continue to get smarter in how we do things. We’ll get better at using the information we have.”
Caverzasi concurs, explaining that algorithms are not only focused on detecting specific objects but also gathering information on environments and what people are doing in them, to create a more holistic picture for security and marketing applications.
Oberg says the potential applications for facial recognition technology are limitless, and as such its future is wide open, but she hopes above all else that future is ethical.
“I don’t want drones with facial recognition. I don’t want body cameras with face recognition. There’s definitely some applications that are going in a very scary direction,” she says, also stressing the importance of lawmakers and regulators in ensuring the technology isn’t abused by mass surveyors.
Putterman agrees that the next frontier of facial recognition is making sure data is used in responsible ways: “We are also very considerate of the data. We throw out as much data as we can.”
Privacy is also important for Deep Vision. “When we have situations or environments in which you need to preserve privacy, the default is the device acting as a sensor, so no imaging or video information is getting extracted from the camera. The only thing you are getting out of the device is meta data,” Caverzasi says.
On the other hand, Oberg says there are future applications that can make life easier, such as an individuals’ face acting as tokens that allows them to travel through an airport without ever showing a passport, making air travel a much quicker and more painless experience.
Another benevolent application, that has potentially life-saving ramifications, is finding missing people or rescuing them from dangerous situations. Deep Vision has a partnership with an organization called the Global Emancipation Network, which is integrating its technology to fight human trafficking, using facial recognition to narrow down search databases of victims.
Whether the future of facial recognition is one of time saving conveniences and life-saving innovations, gross violations of privacy, or a mixture of all of the above, recent improvements and an ever-growing list of applications suggest that it is only going to become more common.

By Will Mazgay
Smart home technology is becoming increasingly ubiquitous, as more and more home owners move to install devices or entire systems in their homes.
The global install base for smart home technology is now at 70 million homes, according to a recent report by research firm ABI Research. Jonathan Collins, ABI Research’s Smart Home research director, says the value that end users see in the technology is driving that growth.
“There’s certainly a usability and an awareness around these devices that’s grown. I think you’re seeing it where it’s become a very simple financial choice whether you want one of these devices in your home or not. You’re talking around $20 low-end at the moment,” he says.
According to Collins, a lot of money is being pumped into marketing, promoting and consumer education on smart home devices, so that the public understands what the benefits are.
Another huge draw for consumers is voice control, using it to make sure if your front door is locked or to turn smart lights on and off.
Collins says Amazon’s Alexa, and Google and Apple, have really made headway in voice
technology in the last couple of years, and in addition, consumers are becoming more acquainted with voice commands on smart phones.
As well as making life easier for end users, Collins says there is value to be gleaned by platform providers through the relationship between the platform and the end user: “They get to understand a great deal more about that customer. They get to understand daily routines, personal preferences, plans, spending habits — and that is of great value, to advertisers, to the platform providers.”
“The consumer, if they really want ‘smart home,’ then they need to do the research.”
— Blake Kozak, IHS Markit
He stresses that for big providers like Amazon and Apple, armed with a greater understanding of customer habits, the goal is to entice customers to buy more of their hardware or hardware that is compatible with their platforms.
Blake Kozak, principal analyst, Smart Home and Security Technology, with research firm IHS Markit, agrees that the smart home space is growing in a healthy manner.
New technologies, new horizons
Kozak says video doorbells will continue to be a big trend, especially those with a social aspect. He cited Neighbors from home security products manufacturer Ring (owned by Amazon), a smart phone app that allows end users to share video footage or photos of crimes (such as package theft) or suspicious activity recorded on video doorbells with their neighbours.
When it comes to access control, Collins says that voice biometrics are increasingly being used to profile and verify voices.
Kozak also sees big things in this space: “In terms of disarming the alarm system I think Honeywell and a few others have suggested that that’s going to become a trend where you can send a text to your camera and you can walk up and it will automatically disarm the system, or maybe audio analytics where if you just talk or something like that, maybe it will disarm the system.”
Collins says certain companies are also using Wi-Fi disturbance to understand who and what is moving around in a space.
Kozak elaborates further on spatial awareness technologies, explaining that identifying what’s happening in an environment ties into video analytics: “It’s becoming table stakes now for a consumer video surveillance camera manufacturer to have at least the capabilities, whether it’s a free or paid for service, to determine the difference between an animal or a flag or a tree blowing in the wind versus a person,” he says.

Artificial intelligence is a big driver of these technological improvements: “It’s not so much AI that’s enabling these systems to talk together, but there’s certainly a wealth of data being collected, or that can be collected, that can certainly be leveraged by AI to finesse and make their (platform provider’s) services better,” Collins says, explaining that the more AI that is applied to these technologies, in terms of understanding environments within homes and preferences of specific individuals, the more seamless they become.
For consumers looking to create a smart security system in their home through the do-it-yourself (DIY) route, it can be a little overwhelming.
“That’s the continuous challenge,” Kozak said. “The consumer, if they really want ‘smart home,’ then they need to do the research. They can’t just walk into a retailer or go online and just make it happen with a few clicks of a mouse. They really have to do their homework.”
Creating a seamless smart home ecosystem is also a challenge for platform providers, as they deal with synchronizing devices from different manufacturers with their systems.
“They do it in a number of ways,” says Collins. “They have outreach programs and developer programs and a degree of funding set aside.” He says there’s a big push and pull factor, with platform providers drawing in original equipment
manufacturers, and these players vying to attach their devices to platforms.
Platform providers are also working feverishly to expand their own offerings.
“This year Amazon brought out a number of devices that can start to make a security system, through a couple of acquisitions,” Collins says. “Google also extended their offering. They already had cameras, but they added some contact sensors, key fobs, to really round out that security offering.”
Collins says that when it comes to security offerings, there is going to be increased competition between the traditional installer market and the DIY market.
“If you look at a traditional home security system, that’s not necessarily the same thing as smart home. You’re not necessarily talking to the same level of intelligence in the home, or the same degrees of sensing or flexibility,” he says. “Certainly, there’s more and more interest and more and more capabilities for consumers to build up their own security system, not pay that monthly revenue, or have that monthly revenue as an a la carte option if you like, instead of committing to a long contract.”
Kozak agrees: “Consumers will move more towards the home automation aspect and less focus will be given just to security…especially as price comes down.”
Conversely, Collins says consumers who do
commit to long term contracts expect more from their security system, for it to have smart home capabilities.
“We’ve seen in the past the professional security market growing quite slow, not a whole lot of innovation. But I think those companies and those providers have really improved,” says Kozak.
According to Collins, the installer market and the DIY market are also meshing.
“We see retailers start to offer installation services, crossing over into that traditional home security market,” Collins says, explaining that Office Depot recently announced it was going to be offering installer services for smart home devices. Other firms, like Comcast, are “also offering that kind of gateway ability to host and control a lot of smart home devices. They’re doing that very much so they also can get that customer connection and don’t miss out on their valuable subscriber base.”
As for what this means for traditional security installation, Collins put it this way: “There’s probably still a role for installers there; there’s certainly still a role for home security of some sort. It’s just a matter of whether it takes a dedicated, long contract, installation that’s just about security, or really if it’s about a whole range of smart home services and one of them happens to be security. Maybe installation is a part of that and maybe it’s not. It’s a time where a lot of boundaries are being crossed.”







How ONVIF’s Profile A is helping to improve interoperability between different manufacturers’ products.
By Bob Dolan
Access control systems and their components have historically been designed and manufactured in a proprietary way. This approach has made achieving interoperability between different manufacturers’ products a difficult process. It sometimes has involved developing unique drivers for specific devices or creating workarounds to get readers, panels and other
“When enabled with artificial intelligence, access control and other building systems can begin to recognize patterns, anticipate events and behaviours and make proactive changes.”
access control peripherals to share information and communicate with a common access control management platform.
The need for interoperability, which is making different types of devices or technologies communicate with one another, is certainly nothing new in our industry. At Anixter, we have been testing interoperability in our Infrastructure Solutions Lab for many years, connecting devices and clients from different suppliers to our test server site to ensure that integrations and multi-supplier solutions are going to work correctly for our customers in real-world scenarios.
As a result of access control’s proprietary nature, customers often have remained confined to deploying single-supplier access control systems and felt forced to buy access control panels from a particular manufacturer in order to maintain their current investments in legacy card readers, door controllers and card technology. But the industry is changing as the development of standards-based applications grows, and end users and system integrators alike are recognizing the value of open standards, such as the interoperability standards created by ONVIF.
ONVIF Profile A provides an interface for ONVIF member developers to use when developing access control software and other security products. Profile A defines the requirements that govern how one Profile A application can communicate and interact with another, facilitating interoperability for multi-vendor projects.
The open device driver used in Profile A conformant access control panels allows end users to integrate control panels and management software from different manufacturers. This gives end users the ability to make choices on specific hardware for their access control systems and, even more importantly, means that if you want to install another supplier’s access control management software in the future, you don’t have to rip and replace existing access control hardware in order to do so. The common interoperability of ONVIF Profile A provides the bridge between the legacy hardware and new software if both are Profile A conformant.
The tipping point is now
In contrast to the video surveillance market, access control technology has historically been slow to change in large part because of the high upfront costs to acquire and install a system and the longevity of the equipment — commonly between 12 and 20 years. End users and their need for open network-based infrastructures are driving recent changes in this market, as the line between physical security and IT continues to blur. Physical security systems are now often managed by IT departments and IT directors are rightfully demanding open architecture approaches (like IP networks) rather than the proprietary and sometimes duplicative design of traditional security systems.
The drive to an open architecture approach has proliferated across many related industries, and today we see lighting, HVAC and other functions residing on the network as well, offering businesses the option to minimize operating costs and to better control and monitor their facilities. This trend of hosting everything on an IP network clears a path for an Internet of Things, which in many respects is already here.
The network can already transfer pieces of data from one system or device and correlate it with other data in analytics software programs, ultimately providing usable, actionable information to end users, aggregated from such several systems as video, audio, intrusion, voice and other systems. Multiple network-based systems make things like intelligent building automation a reality, delivering costs savings, keeping people and assets safer and using less energy.
As one of the major platforms within a smart building environment, access control systems play a large role in this IoT scenario. When connected to other, seemingly disparate building systems using a common
interface, this deeper interoperability enables increased productivity to the overall system. As a contributor to an intelligent building ecosystem, access control systems also serve as a repository of large amounts of data — tracking people’s movements for real time facility population data or facility usage based on the day’s meeting room booking schedule. The more data that is available within a system means the more quickly adjustments can be made, further ensuring the security and efficiency of the building.
When enabled with artificial intelligence, access control and other building systems can begin to recognize patterns, anticipate events and behaviours and make proactive changes to the building environment, enabling its occupants to work more efficiently. Whether the temperature and lighting for a room is adjusted based on recognized patterns — a 10 a.m. meeting every Thursday on the fifth floor, or doors are unlocked in anticipation of a recurring event, AI allows for systems to be smarter, more effective and provide additional costs savings by further reducing the administrative burden of the system.
With so much data being fed into these management platforms, from AI technology or other more traditional sensors, a stumbling block to true interoperability still remains. To effectively be able to harvest actionable information out of the received data, it has to be readable in a common format. Data readable in only one proprietary ecosystem will jeopardize the idea of interchangeable information, and further reinforce the silos that exist between the largest providers. Profile A could offer a solution for this in the future, by providing users with that common interface, and allow the market to continue to grow through interoperability and innovation.
Profile A essentially levels the playing field between large and small manufacturers, eliminating the need for proprietary protocols between suppliers for communications between different components of a system. End users can, for example, choose specialized, high-end access controllers and panels from one manufacturer to use with Profile A conformant access control software that is perhaps lesser known, but that provides what the end user needs when it comes to management and reporting.
And as manufacturers continue to adopt Profile A into their products, access control componentry that conforms to Profile A will mean that a business doesn’t have to rip and replace the Profile A conformant access control devices in the facilities that they’ve acquired. Instead, they can deploy and use their own preferred management software in the newly acquired facilities using existing hardware.
With the development and release of Profile A, ONVIF is making a long-term commitment to open access control systems in particular. The development of Profile A took two years and the work of many ONVIF member company representatives from all over the world to develop a standard that can take the physical security market into the next decade.
One thing that ONVIF and Anixter have in common is our view that standards are created to be tools that let customers make educated decisions, with the freedom to choose the hardware and software of their choice, regardless of manufacturer. When end users can just think “It works,” and move on with their day, that’s when we know ONVIF has done a good job in developing a practical solution.
To learn more about Profile A or any of the ONVIF Profiles, visit www.onvif.org.
Bob Dolan serves on the ONVIF Technical Services Committee and is Director of Technology for Anixter.


Ottawa-based ADGA, a professional services firm with a substantial business in Canada’s defence sector, had a busy 2018, acquiring two security companies.
In March, ADGA brought Quebec-based integrator Extravision Video Technologies Inc. into the fold and only weeks later purchased Presidia Security Consulting, which offers investigations and intelligence services.
SP&T News recently spoke with Françoise Gagnon, ADGA’s CEO, about its recent expansion in security services and the need for greater female representation in the industry.
SP&T News: What was attractive about Presidia and Extravision?
Françoise Gagnon: When we look at acquisitions, it’s going to be the services that they offer. It’s going to be something that differs from and complements what we offer.
We’re also big on culture. You need to look and make sure this is a good fit with us from a cultural perspective. Inevitably, if you’re not buying or acquiring a company that’s nuts and bolts, you’re acquiring talent. You want to make sure you retain those experts. There needs to be a fit with the individuals that are coming on board. Both companies, we had worked with in the past and had successful partnerships with, so that’s how the relationship began.
Presidia and Extravision offer two completely different services but, again, complementary services. That, coupled with what we already had [in terms of] expertise, was a good fit.
Extravision is on the Quebec side, which also gave us an extra foothold in Quebec.
Presidia is very much Ottawa-based but has an international clientele.

By Neil Sutton
“I don’t want to be the only woman at the table when I go to board meetings.”
SP&T: How much cross-selling is there between the security businesses?
FG: If you look at the private sector and the commercial sector, I think there’s a recognition that there isn’t anybody who hasn’t been subject to being hacked. There’s an appreciation of the need for those services, but there’s a lack of awareness about, “How do I even begin? I’ve got a building, so do I put perimeter security around that building? What’s the menu of options?” Our approach is really to take a holistic look at the requirements and give them a menu of options. Rather than have to go to one person for access control and somebody else to look into cyberthreats, we do a holistic analysis, offer the menu of options and our recommendations and it’s worked exceptionally well. We demystify it.
SP&T: What does your client base look like for security-based services?
FG: We do some work with the federal government, and we always have. We’ve opened up offices in Toronto — they do primarily professional services with City of Toronto, a lot of municipal work. We’re very much looking at the commercial sector, and obviously both companies came with their own book of business. They range from very high level public sector to high-profile individuals who need corporate private security to large academic institutions. We work with companies in the Fortune 500 — I would say top 20 — providing security services for them. We work in the mining industry… we work in the transportation industry. It covers the full spectrum.
SP&T: Do you find more cross-over between your cybersecurity and physical
security business today?
FG: Our model is, if you’re an account executive and you’re selling, converged security is also part of your portfolio. We don’t have a model whereby you sell to a certain client and that’s your client. Everybody has converged security solutions as part of their mandate. The crossover has been very favourable. When you’re already a known entity to your client, and you have that trusted relationship, and you now have this additional service that you can offer them… that door is already open. You can leverage your existing relationship. You can bring that additional value to the table.
SP&T: Did any aspects of the business surprise you when you joined ADGA full-time?
FG: Is there anything that surprised me? I would have to say it was the first time in my career I’d found myself to be the anomaly by virtue of my gender. I don’t know of another defence and security and enterprise computing company — certainly of this scope — that has a woman at the helm. From that regard, I was very much a fish out of water. That was a surprising aspect. I knew there would be a substantial learning curve, so that wasn’t a surprise to me.
SP&T: What should the industry be doing to be more inclusive?
FG: When you come in there as a woman, let alone from another culture, it’s striking. How do we go about addressing it? You need to start in high school and open up those opportunities and have young girls thinking about careers as experts in science or leading defence, and the exciting work that is available. We’ve got a lot of women in the Forces and

in leadership roles there. The first deputy minister is a female (Deputy Minister of Defence, Jody Thomas), so that aspect is changing, but there are still not a lot of role models out there for women.
I’ve always benefitted from having a very strong network of women peers, so I was a little surprised to not find that when I came into this industry. I don’t want to be the only woman at the table when I go to board meetings.
SP&T: How does your company promote female leadership?
FG: We’ve developed a program called ADGA Women that we are launching. When women get into management, one of the stumbling blocks [is] as soon as you assume a management role, typically you’ve got some fiscal oversight or responsibility. You find with a lot of women they’ve not necessarily done those courses in university or had that background. It tends to intimidate a lot of women. One area that we’re doing is we’re teaching them financial literacy — not just understanding the numbers on the spreadsheet but ... be able to ask questions and feel very comfortable doing so.
We are working on a mentoring program for women. We’ve got a whole program internally. There’s a lack of women at a certain stage — in middle management and upper management. We are working with local colleges and we’ve put bursaries in place for young women in technology to increase adhesion to those programs. It’s certainly top of mind with the current political administration, so it’s forced the issue, which is a good thing, from my perspective. Typically, there are well paying jobs in this sector. It’s really exciting work and it’s a shame not to be able to have that sector of our economy fully participating.

Aiphone
The new IX Series 2 Peer-to-Peer Video Intercoms offer Session Initiation Protocol (SIP) compatibility, enhanced CCTV control, line supervision, backwards compatibility with the original IX Series and many more features. End users can create efficient security operation centres using the IX Series 2 system as a single command point to control a variety of security layers. The IX Series 2 can page across multiple stations and scan through video intercoms and CCTV cameras to monitor locations.
www.aiphone.com

The Crescendo Mobile smart card utilizes digital certificates on users’ mobile devices for client authentication. Crescendo Mobile works similarly to, and is compatible with Crescendo smart cards; however, rather than inserting a separate device into a contact smart card reader, it connects to a desktop computer via an NFC (near-field communication) reader or Bluetooth.
www.hidglobal.com
SVN-Flex is a new feature that enables SALTO standalone electronic locks and cylinders to update user credentials directly at the door. Based on SALTO’s BLUEnet wireless technology, SVN core technology and in combination with the trusted access control management platform and XS4 electronic locking solutions, SVN-Flex increases the number of updating points directly to any door. SVN-Flex functionality can be enabled on any product in the SALTO XS4 BLUEnet enabled electronic lock range.

www.svn-flex.com
Morse Watchmans
Morse Watchmans’ KeyWatcher Touch key management system features a 7” touchscreen and patented SmartKey system with KeyAnywhere technology to make it simple to withdraw and return a key securely to any key cabine. AssetWatcher is a scalable RFID-enabled locker system. Suitable for mobile electronics and other valuable items, it can support more than 10,000 users on a single system and is configurable in three modes. AssetWatcher’s RFID technology allows the user to track who is removing or replacing an asset, as well as when and where in the system the asset has been taken from or placed.

www.morsewatchmans.com

























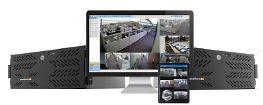
Using the exacqVision VMS (9.6), security operators can evaluate aberrant “door open” events in restricted areas with greater granularity. exacqVision 9.6 includes support for direct SD video recording with Axis cameras. When connectivity between cameras and an exacqVision NVR fails, video records directly onto the SD card. Once connectivity is reestablished, recorded video transfers back to the exacqVision NVR and is automatically stored at the correct date and time.
www.exacq.com
The LCD-MID-CB medium flat panel ceiling mount can accommodate most 27-inch to 42-inch flat panels. This versatile mount can handle a wide range of ceiling applications in a security setting with its adjustable tilt, extension, rotation, and rails to ensure ideal placement. www.videomount.com



























































































The VISIX Facial Recognition camera is a dual lens 2MP camera for instant face detection and identification. Using analytics and 3xLOGIC’s Facial Recognition application and mobile app, users can review captured facial images and choose persons of interest to place on a watch list within the camera. Using web-based Central Manage ment Application in multi-site mode allows POIs to be adde at sites to notify locally via server or mobile app. www.3xlogic.com

TruVision Navigator version 8.0 unified security software includes enhanced video streaming capabilities, integration with the Interlogix UltraSync Modular Hub systems and tighter integration with IFS networking switches. TruVision Navigator version 8.0 system is now a 64-bit application that supports a separate graphic processing unit (GPU) to provide smoother rendering of live and recorded video.

TRENDnet
TRENDnet’s 5-Port Gigabit Long Range PoE+ Switch (TPELG50) and the 8-Port Gigabit Long Range PoE+ Switch (TPELG80) each feature a DIP switch to extend the PoE+ signal up to 656 ft. at up to 10Mbps. The new long-range PoE+ switches are suitable for use in access point, VoIP phone, and IP camera applications. For an additional layer of network protection, each of TRENDnet’s new long-range PoE+ switches supports select switch management features. The DIP switch to extend the PoE+ signal also enables support for VLAN port isolation and QoS. The long-range gigabit PoE+ switches are fanless and wall mountable. www.trendnet.com

The Cable Tester Kit for the VDV MapMaster 3.0 is designed for installers of Ethernet and coax networks. The T130K4 kit is contained in a durable plastic case (p/n 4082) with an EVA foam insert, with additional places to hold up to eight test and map Smart Remotes. The T130K4 kit includes mapping-only ID network remotes (#1-#12) and includes test and map coax ID remotes (#1-#8). Along with cable adapters for different coax connectors, the kit also includes two no-fault RJ12-to-RJ12 patch cables for testing voice cables, two 5-inch shielded patch cables, and an RJ45-to-alligator clips cable.. www.platinumtools.com
Both the ZIPK4T2 and ZIPK8T2 5MP zip kits come all in one, with both the cameras, and DVR included. The ZIPK4T2 contains four 5MP IP cameras, and the ZIPK8T2 has six 5MP IP cameras. These kits also have: 60ft Ethernet cables (four for 4 ch, six for 8 ch), one three-ft. Ethernet cable, remote control and mouse. The ZIPK4T2 and ZIPK8T2 are a suitable solution for any residential and small business installation. They are enabled with EZ Wizards to allow for easier user setup, and ease of use. They also include QR code based network setup for easy remote access via mobile and desktop apps. www.specotech.com


Senstar announced a new, more compact version of its Flare Real-Time Locating System (RTLS) personal protection device (PPD), the PPD Compact. The Flare RTLS keeps staff working in high-threat environments safe by instantly identifying and locating personal duress alarms at the touch of a button. The original PPD is a robust, utility belt-holster device specifically designed for frontline correctional workers. The new PPD Compact provides a smaller option for support staff in institutional environments. In the event of danger, the user activates the PPD which emits an RF signal that is detected by a network of sensor units concealed throughout the facility. Flare immediately locates duress alarms and displays the location, status, and identity of the PPD on a map-based display in the control room. www.senstar.com

STI’s see-through polycarbonate MED Protective Cabinets allow medical kits to be highly visible while guarding against tampering and theft. They mount on the wall and are secured with a thumb lock, permitting easy access. Models are available with or without one of two flashing alarms. The clear polycarbonate (which is constructed from the same material used in football helmets) will not dent like metal cabinets. An included wire shelf holds supplies for convenience. STI’s cabinets are backed by a three year guarantee against breakage in normal use. www.sti-usa.com

Hammond Manufacturing has introduced 4U high versions and added extended 559mm depths to all heights of its RM family of 1U - 4U 19 inch rack mounting and desktop enclosures. 1U to 3U half-width versions are also available. The all-aluminium construction consists of a heavy-duty extruded frame with removable vented or plain top and bottom covers. 19 inch units are supplied with rack mounting angles; both 19 inch and half width variants come complete with self-adhesive rubber feet for when the enclosure is to be used as a desktop unit. The front and rear panels are removable and interchangeable. Front panel handles are optionally available to assist with insertion and removal of the 19 inch units from a cabinet. Adjustable rear panel mounting angles are also available for the 457 and 559mm deep units.
www.hammfg.com


Historical Headlines
2008:
Video standards committee accepting new members: Bosch exec explains how development process will unfold.
2010:
In pursuit of standards: It’s early days, but establishing standards for the security industry could grow the industry, mean cost savings and a better experience.”
2011:

























Standards body ONVIF (Open Network Video Interface Forum) turned 10 recently, and held its 10th annual membership meeting in November by reviewing its accomplishments to date, including the recent Profile T for advanced video streaming.
ONVIF was founded by Bosch, Axis Communications and Sony in 2008 and has since swelled to more than 450 members (26 full members, 14 contributing, 44 observer and the remainder are user members). There are now six ONVIF profiles which collectively provide support for more than 10,000 products.
SP&T has followed the organi-
zation’s progress since the beginning, checking in on its profile updates and asking the broader questions about how standardization might benefit the industry and its users.
In a February 2010 article, which looked at how ONVIF and the PSIA standard (Physical Security Interoperability Alliance) were vying for support in the security world, Norman Hoefler, then the Bosch Security country manager for Canada, summarized the situation thusly: “Manufacturers have proprietary systems because they want to capture a feature set that nobody else has and lure customers into their proprietary world, but in the IP world, that just doesn’t work.”
For the October 2010 issue, SP&T hosted a roundtable comprised of vendors and installers to get their take on the standards debate. One insightful comment came from Willie Kouncar, vice-president of product development for Verint (a member of both PSIA and ONVIF). “I do think we have to be careful not to over-market this stuff, because standards are not magic,” he opined. “It’s really about how to get all this stuff to talk and the impact that can have on our industry.”
“I absolutely think that ONVIF has helped the transition from analogue to IP,” stated Axis CEO Ray Mauritsson in a March 2013 Q&A with SP&T. “...ONVIF
Education, standards, HD and VSaaS in 2011: 2011 was a tipping point year in many respects, but there is still a lot to teach people about IP camera technology.
2014:
The standard bearers: ONVIF, PSIA, the HDcctv Alliance and more are on a mission to make technology easier to use, but integrators may need more convincing.
2018: Waterloo developer wins ONVIF contest
has been really important. It gives the end user a flexibility to choose different brands.”
In 2014, when SP&T checked in with ONVIF chairman Per Björkdahl, he spoke about a pivotal point in the organization’s evolution.
“The alliance was started to facilitate interoperability in relation to video only, but its scope has expanded now to include any physical security product or application,” he said.
The wider implication of this statement is that today, security devices across multiple disciplines are now being asked to share data and work together more effectively in order to manage risk.
SP&T’s latest coverage of ONVIF comes from ONVIF itself. See p.20 for more on ONVIF’s Profile A for access control.
























































































