Security Products and Technology News


























































































































16 The new IQ for installers
Complex systems, software integrations and networked technologies are all demanding new skills from the integrator
By Ellen Cools
20 Beyond the hype We hear more about artificial intelligence every day, but what can it really do for security?
By Paul Kong
6 Line Card
• ULC tackles new standard for safety in cannabis production
• Waterloo developer wins ONVIF contest
• Honeywell gives a name to impending home business spin-off
• Allegion president on IP access control in Canada
10 CANASA Update
CANASA opens doors to new members
12 Camera Corner Let’s face it By
Colin Bodbyl
14 Lessons Learned Beyond the alarm deal By
Victor Harding

Alarm horn/beacon units
The D2x family of beacons and combined alarm horn/ beacon units from E2S are compliant to UL464 and UL1638/UL1971 for public mode fire alarm installation as emergency signaling devices for the hearing impaired, as well as private mode fire and general signaling applications.

Perimeter intrusion detection
FiberPatrol FP1150 from Senstar detects and locates intrusion attempts for up to 10 km or 5 km per side in a compact, rugged platform. The FP1150 extends the operational temperature range to 50°C, uses solid-state disk drives and integrates previously external optical modules.


IBy Neil Sutton
f I had to start from scratch, maybe I would have gone to school to learn more about the security industry and pursue a profession in the field.
My vocation has always been writing and publishing, so I doubt I would have been swayed to enter another career. But that point is basically moot. I gave no thought to security systems. It wasn’t on my radar. Unfortunately, I don’t know if that situation is much different for young people today.
I think there is a more active discussion about this issue on the end-user side of the equation, i.e. people who develop careers as security managers and chief security officers.
ble. Even Brzozowski, an accomplished professional in his own right, noted that he more or less fell into security via a bank teller job at a credit union. The interest in financial services security came later.
skills shortage certainly isn’t unique to security.”
SP&T’s sister magazine, Canadian Security, has followed the professional development cycle in the end -user community for years. Times are changing and there is more emphasis today on encouraging young people to pursue careers in professional security than ever before.
In Canadian Security’s most recent issue, our 40th anniversary edition, we profiled Michael Brzozowski, risk and compliance manager at Symcor, a financial processing service provider.
Brzozowski, who is the recipient of Canadian Security’s Emerging Leader Award, is helping to create a new ASIS designation that encourages young professionals to achieve a recognized security certification much earlier in their careers than was previously possi-
So where does this leave us with security installation and integration? There is certainly education available in some areas — such as the Security Systems Technician program at the B.C. Institute of Technology in Burnaby — and CANASA also actively promotes education through its technical courses offered in partnership with Centennial College and with its annual scholarship program. But I am still left with the impression that there are not enough entry-points to security careers.
Our cover story this issue focuses on the skills required to be an installer today. Many of the people interviewed in that story indicate it can be difficult to find people with those qualifications. As a result, on-thejob training, and constant retraining to stay current, has taken on a new urgency, particularly in this dynamic environment where cybersecurity is at a premium.
The skills shortage certainly isn’t unique to security. It has been widely documented that IT skills are in short supply across many industries — and it’s likely that security is a symptom of that broader trend.
Whatever the case, this is a complex issue with no easy answers.

Your Partner in Securing Canada Security Products & Technology News is published 8 times in 2018 by Annex Business Media. Its primary purpose is to serve as an information resource to installers, resellers and integrators working within the security and/or related industries. Editorial information is reported in a concise, accurate and unbiased manner on security products, systems and services, as well as on product areas related to the security industry.
Group Publisher, Paul Grossinger 416-510-5240 pgrossinger@annexbusinessmedia.com
Publisher, Peter Young 416-510-6797 pyoung@annexbusinessmedia.com
Account Manager, Adnan Khan 416-510-5117 akhan@annexbusinessmedia.com
Editor, Neil Sutton 416-510-6788 nsutton@annexbusinessmedia.com
Assistant Editor, Ellen Cools ecools@annexbusinessmedia.com
Art Director, Graham Jeffrey gjeffrey@annexbusinessmedia.com
Account Coordinator, Kim Rossiter 416-510-6794 krossiter@annexbusinessmedia.com
Circulation Manager, Aashish Sharma asharma@annexbusinessmedia.com Tel: 416-442-5600 ext. 5206
President & CEO, Mike Fredericks
EDITORIAL ADVISORY BOARD
Colin Doe, Veridin Systems Canada Anna Duplicki, Lanvac
Victor Harding, Harding Security Services
Carl Jorgensen, Titan Products Group
Antoinette Modica, Tech Systems of Canada Bob Moore, Axis Communications Roger Miller, Northeastern Protection Service Sam Shalaby, Feenics Inc.

111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1 T: 416-442-5600 F: 416-442-2230
PUBLICATION MAIL AGREEMENT #40065710 Printed in Canada ISSN 1482-3217
CIRCULATION
e-mail: asingh@annexbusinessmedia.com
Tel: 416-510-5189 • Fax: 416-510-6875 or 416-442-2191
Mail: 111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1
SUBSCRIPTION RATES:


Canada: $42.00 + HST/yr, USA: $74.00/yr and International: $84.50/yr
Published 8 times a year

Occasionally, SP&T News will mail information on behalf of industry-related groups whose products and services we believe may be of interest to you.
If you prefer not to receive this information, please contact our circulation department in any of the four ways listed above.
Annex Privacy Officer privacy@annexbusinessmedia.com Tel: 800-668-2374
No part of the editorial content of this publication may be reprinted without the publisher’s written permission. ©2018 Annex Publishing & Printing Inc. All rights reserved.
Annex Publishing & Printing Inc. disclaims any warranty as to the accuracy, completeness or currency of the contents of this publication and disclaims all liability in respect of the results of any action taken or not taken in reliance upon information in this publication.








Bosch empowers you to build a safer and more secure world. Our products are designed to work together to maximize facility control, better mitigate risks, and make systems easier to use and manage. Increase security and automate functions for easy operation. Trigger and execute audio announcements based on security events. Manage data with enterprise-wide control of video and security devices. Bosch products integrate seamlessly to help you create complete security solutions. Call us at 1-866-266-9554 to learn more.

With recreational cannabis set to become legal on Oct. 17 this year, the question of safety and security in cannabis producing facilities has taken centre stage.
In fact, ULC Standards recently announced the proposed first edition of CAN/ULC-S4400, Standard for Safety of Buildings and Facilities Utilized for the Cultivation, Production and Processing of Cannabis.
The standard is intended to:
• Provide minimum requirements for the protection of buildings and facilities used to cultivate, process and produce cannabis and cannabis-related products “to minimize dangers resulting from the effects of fire”;
• Provide minimum requirements regarding “cover devices, equipment and systems utilized for cannabis cultivation, processing and production”; and
• “Provide minimum requirements for the security of buildings and facilities from intrusion and infiltration, as well as considerations for secure access and safe egress.”
In an email to SP&T News, Theresa Espejo, project manager for the ULC Technical Committee S4400, explained the proposed standard has come “at the behest of local regulators concerned about security in a new and emerging industry.”
“There is a severe deficiency in code requirements, standards, regulations, by-laws, or even codified best practices specifically addressing the unique challenges facing this emerging industry,” she elaborated.
The proposed standard focuses solely on the safety of buildings and facilities used to cultivate, produce and process cannabis because “this is an identified priority concern of regulators and government stakeholders,” Espejo explained.
According to Espejo, Health Canada has said, “Mitigating the inversion and diversion of cannabis products is a primary goal to reduce and eliminate the black market. Hence it is crucial for all facilities storing, handling or processing cannabis to have a robust security system and be protected from intrusion and infiltration.”
“Safety, egress, building codes … don’t always combine well with a heavy security environment. It can be a real challenge to balance both interests. “
—
Jeff Hannah,JH &Associates
“The standard aims to set the bar to an ideal, practical and attainable security set of requirements among all players,” she added.
To develop a consensus-based standard that can be applied nationally, ULC recently formed the ULC Technical Committee S4400. The committee is composed of 34 voting members and six associate, non-voting members, said Espejo.
Its members represent a mix of seven interest categories: AHJs (authorities having jurisdiction)/regulators, producers, supply chain, commercial/industrial users, general interest, standards and testing, and government. They will help develop technical requirements, address comments in their respective fields of expertise, attend meetings and vote on ballots.
CANASA is one of those members. According to Patrick Straw, CANASA’s executive director, they became involved after inviting Al Cavers, engineering manager of ULC, to sit on their national board.

Patrick Straw, CANASA
He asked Cavers how CANASA could become more involved with ULC. This standard seemed to be a good fit, as it’s “pretty close to the security industry and there’s a lot of security companies that are already aggressively marketing to that business sector,” Straw said.
Consequently, he applied to be part of the committee. Three other CANASA members are
“The standard aims to set the bar to an ideal, practical and attainable security set of requirements among all players.”
—Theresa Espejo,ULC
also on the committee, he shared.
Straw believes it’s very appropriate that ULC develop a standard on security and safety in cannabis cultivation and processing, given the close relationship between electronic security and fire.
“To me, they’re [ULC] the perfect entity to come up with a national standard for protecting these facilities,” he elaborated.
Jeff Hannah, owner and principal of JH & Associates, a security consultancy with expertise in the Access to Cannabis for Medical Purposes Regulation (ACMPR), agrees. Although he is not on the committee, he is “definitely in favour.”

“There’s a lot of safety and egress [components] they’re going to develop, which, to be honest, I think is needed,” he elaborated. “Safety, egress, building codes … don’t always combine well with a heavy security environment. It can be a real challenge to balance both interests. So to get some clarification and a defensible standard that balances all those interests with the regulatory influence taken into account would be a great thing to have.”
These types of cultivation and production facilities haven’t existed en masse before, so “that’s a great reason to have some good, solid, well-thought out standards to lean on when you’re designing these to be safe and secure,” he concluded.
ULC aims to complete the standard by Q2 of 2019, Espejo said.
Once complete, “it will be incumbent on the security companies that are working in that space to conform to whatever regulations come out of it,” Straw added.
— Ellen Cools
Security standards body ONVIF recently announced its first Open Source Spotlight Challenge was won by a Waterloo, Ont., resident.
ONVIF’s challenge is a technology competition that encouraged entrants to provide open source solutions applicable to IP video streaming applications.
The contest, provided in conjunction with BeMyApp, received 37 entries, which were judged based on innovation, viability, functionality and ease of use. The judging committee included representatives from ONVIF members Axis Communications, Bosch, Dahua Technology, Hikvision and Uniview. Cash prizes of up to $3,000 were

awarded to seven finalists and judges ultimately selected an app submitted by Liqiao Ying, a developer who works for Waterloo-based Aimetis, a division of Senstar. Ying’s winning app, CAM X, comprises “an AI-based object detection system that utilizes blockchain solutions for storing information obtained from ONVIF cameras,” according to ONVIF.
Ying originally moved to Canada from China to attend the University of Waterloo. He started working for Aimetis as a developer upon graduation and heard about ONVIF’s contest through a co-worker.
“In the last few years, deep learning and blockchain are the hottest technologies. Early this year, I decided to take a deep learning
course,” explains Ying. “When this [contest] came up, I thought, it’s a great opportunity to practice what I’ve learned.”
Hans Busch, chairman of ONVIF’s Technical Committee and a senior engineer with Bosch, says the organization wanted to explore new ways of utilizing the ONVIF standard. That led to the launch of the open source challenge.
Russia, Europe and North America.

Making the contest open source (i.e., code or software that is non-proprietary and freely available) was key, says Busch, to encourage the sharing of information across the developer community and avoid the issues that come with proprietary code belonging to an ONVIF member.
“In the beginning, I was a bit skeptical of what the outcome would be, but in the end, we were surprised to get almost 40 submissions in eight different programming languages,” says Busch. “We never dreamed of that.”
ONVIF received entries from all over the world, including India,
“All [submissions] are good ideas, especially the winning application… great ideas,” adds Busch.
Deep learning and blockchain have the potential to be revolutionary technologies for the security industry, says Ying. “I encourage everyone to learn about it. It’s already happening… it’s transforming the industry.”
— Neil Sutton
Honeywell recently announced that “Resideo” will be the new name of its home products portfolio and ADI distribution business.
Honeywell first announced the corporate spin-off last year — it is expected to be completed by the end of 2018.
The company said it will license its brand to Resideo under a long-term agreement covering its home comfort, security hardware and software solutions for all channels.
Honeywell Homes (the business that will become Resideo) in a statement.

“The home is the biggest investment most of us will ever make — the place where we create a lifetime of memories,” said Mike Nefkens, president and CEO,
Because the home is a centrepiece of our lives, we expect it to be secure, comfortable and safe at all times. Resideo builds on Honeywell’s strength in providing the world’s best solutions to help people to live more productive, comfortable and safer lives. And because smart home choices can be truly overwhelming, our mission is to provide consumers with integrated, simple solutions for today’s connected home.”
“Through its iconic brand and unparalleled presence in the home and low-voltage product distribution markets, Resideo will have
an enviable position from its first day,” added Roger Fradin, chairman of the board, Resideo. Fradin was announced as chairman earlier this year.
According to Honeywell, its network of partners and customers for home products includes more than 110,000 contractors. “As an independent company, Resideo will support their growth by investing in sales and technical training, improving channel partner marketing and related programs to enhance their ability to meet the needs of homeowners,” stated Honeywell.

The home products network also includes 3,000-plus distributors and 1,200 OEMs (original equipment manufacturers), retailers and online merchants. After the spin-off, Honeywell estimates the new company will already have approximately 30 million installed sensors generating more than 250 billion data transmissions annually.
ADI Global Distribution has more than 200 physical locations across 20 countries.
ADI will retain its name and operate as a free-standing distribution business of Resideo.

New VMS helps with dog IDs

Play Dog eXcellent (PDX), a dog care centre based in Chattanooga, Tenn., has upgraded its surveillance with a Vicon Valerus VMS solution. The surveillance system was installed by Meyers Security, also of Chattanooga. The install took advantage of many of the centre’s existing analogue cameras as well as new high-definition models.
PDX encompasses a 20,000 sq.ft. building and four-acre property that provides boarding, dog day care, training, seminars, workshops and performance events. The new surveillance technology allows PDX management to distinguish more easily between different dogs and provides coverage of the grounds and parking lot.
PDX also uses video footage of dogs’ interaction with staff as a training tool.


• James Henderson, Avigilon’s president and COO, has been selected as a recipient of Canada’s Top 40 Under 40 Award for 2018.
• Optiv Security recently appointed Debbie Heiser as vice-president, Canadian services delivery. The company has also named Daina Proctor as regional director.
Caesars manages surveillance across 14 sites
Caesars Entertainment EMEA (Europe, Middle East and Africa) has deployed Pivot3 HCI to protect its video surveillance data and future-proof its IT infrastructure. According to Pivot3, its solution unifies storage, computer and virtualization resources. Using Pivot3, Caesars can support multiple missioncritical workloads, including video surveillance, on a single platform.
Caesars EMEA is also deploying Milestone’s video management software across its 14 sites. The Milestone VMS is integrated into Pivot3’s solution. Caesars utilizes 75 to 200 cameras or more for its individual EMEA sites.
“It’s critical that video data is protected, always available and easily accessible at any time, from any device or location. Pivot3 supports our broader roadmap initiatives,” said Charles Rayer, IT director, Caesars Entertainment EMEA.



• Montreal-based Genetec recently announced Philippe Ouimette will now serve as director of strategic partnerships for the APAC region. Tiago Ferreira joins Genetec as business development manager in the ANZ region.
• Control4 Corp. announced the appointment of Charlie Kindel as senior vice-president
door helps restaurant keep out the weather

A Floridian who moved to Virginia and opened restaurant locations was dealing with brand new issues: outside weather affecting his inside patrons.
Evan Matz, CEO and founder of Crafthouse USA, has since selected a revolving door system over swing doors in his three new restaurants to deal with inclement conditions, particularly during the winter months.
“Snow and cold air could blow in and disturb the customers,” explained Matz. “The revolving door not only blocks out the elements but creates a smooth entrance for customers as opposed to swing doors that can jam. I can also fit more tables with the space savings and that brings in a tangible ROI.”
The restaurants are now utilizing Boon Edam’s BoonAssist TQ manual revolving door installed by St. Clair Construction of Lousiville, KY.


of products and services. Kindel was most recently at Amazon, where he created and led the Alexa and Echo Smart Home efforts for the company.
• Intelligent Security Systems (ISS) recently appointed Janet Fenner to the newly created role of chief marketing officer (CMO). Fenner joins from Dahua Technology U.S.A.
September 9-13, 2018 BICSI Fall Conference & Exhibition San Antonio, Tex. www.bicsi.org
September 12, 2018 Security Canada Atlantic Moncton, N.B. www.securitycanadaexpo.com
September 13, 2018 CANASA Atlantic Golf Tournament Moncton, N.B. www.canasa.org
September 13, 2018 Anixter Showcase Toronto, Ont. www.anixter.com
September 13, 2018 ADI Expo Vancouver, B.C. www.adiglobal.ca
September 23-27, 2018 Global Security Exchange Las Vegas, Nev. www.gsx.org
October 4, 2018 CS@40 Toronto, Ont. www.canadiansecuritymag.com/ cs40
October 13-17, 2018 TMA Annual Meeting Manalapan, Fla. www.tma.us
October 24-25, 2018 Security Canada Central Toronto, Ont. www.securitycanadaexpo.com
November 2, 2018 Anixter Showcase Montreal, Que. www.anixter.com
November 14-15, 2018 ISC East New York, N.Y. www.isceast.com
November 29, 2018 Anixter Showcase Edmonton, Alta. www.anixter.com
December 4, 2018 Focus On Health Care Security Mississauga, Ont. www.focusonseries.ca
According to Tim Eckersley, Allegion’s president of the Americas, the company’s recently announced acquisition of ISONAS will help expand its portfolio in edge computing and electronic access control products.
Eckersley, who spoke to SP&T News via email, said that “ISONAS has a distinctive product offering and strong pipeline and will benefit from being part of a $2.4 billion company with a core competency in safety and security.”
ISONAS, based in Boulder, Colo., and founded in 2000, describes itself as a “manufacturer of Pure IP Access Control hardware.”
Eckersley remarked that IP solutions have “evolved... which is why you’re seeing more innovation
in the market. IP-based solutions are moving from the panel to the edge.”
He said that while ISONAS’ largest installed base is in the U.S., their solutions are also available in Canada, sold through distribution partners based here. “Allegion has a presence in Canada and will continue to serve that market,” he added.
“It’s our goal to help expand the reach of ISONAS technology, using our global presence (which includes Canada), electronics expertise and channel relationships.”
Terms of the acquisition, which is expected to close in Q3 this year, were not disclosed. Allegion is headquartered in Dublin, Ireland; ISONAS will operate within Allegion’s Americas territory.
— Neil Sutton & Ellen Cools

SP&T News: How long have you offered monitored security services?
David Wilson: Wilsons Security is approximately 10 years old. It is a subsidiary of a 100-year-old Nova Scotia based [fuel] business. We entered security to complement the traditional business, and then quickly decided it was a business we wanted to get good at. We set about acquiring other security dealers and building an experienced team to grow organically as well. We service customers across the country and are probably the largest independent security dealer in Atlantic Canada.
SP&T: Residential security seems to be changing dramatically. Is that your experience?
DW: Yes, I think it has changed quite a bit. In our market, there are a lot fewer owneroperated businesses now than there used to be… partly because of the evolution of the industry, changing technology, entrance of the cablecos and telcos into this space. It’s evolved quite a bit over 10 years. I think from our perspective, though, what we’ve really seen is the important role of the professional security installer. We just don’t see that changing. Not all security systems
are the same… there will always be a role for the professional installer, in our minds. Now, some portions of the market can be addressed more efficiently using different go-to-market models, but when things don’t work, there’s got to be someone you can call.
SP&T: Are you seeing your customer demographic shift as Millennials and younger people are becoming home owners and thinking about security more seriously?
DW: Being able to provide the solution, independent of generation — you have to be able to deliver the solution for the customer. There will always be a portion of the market that will always demand that level of service. I don’t feel that some of the other players can offer that level of service. It doesn’t mean the traditional security dealer will dominate, but there will always be a role — and a meaningful role.
SP&T: Do you offer security solutions other than alarm monitoring?
DW: We offer a full breadth of solutions for residential customers. We actively encourage

them to leverage the capabilities of the alarm system to help them manage their lifestyles. Remote access to the security system and to the home is a really valuable capability.
SP&T: What types of questions are you getting from customers? Are they talking about systems or solutions they’ve seen at retail?
DW: In some ways the distribution through mass market retailers has helped create awareness of what the capabilities are. We have customers who will try to do things on their own and then they’ll call us and say, “I like this, but I can’t make it work. Can you do it for me?” That, in some ways, has been very positive for us. Our penetration of enhanced systems — everything that’s more than just a traditional security system — has increased significantly, even over the last five years.
We were an early adopter of advanced services, but it felt like we were pushing water uphill six or seven years ago. Now customers want to listen. It’s not for everybody, but the mix has changed significantly. The majority of systems have advanced capability.

By CANASA staff
New membership category to include consultants and other professionals in light of recent policy revision
CANASA has announced a new membership category permitting full membership for consultants and professionals.
Based on the recent update to the bylaw and membership policy revision, the following conditions now apply for regular membership: “Any person or corporation who is engaged in providing security products and services, or security related products and services, may join as a regular member of the Association, each of whom shall be entitled to one vote.”
Examples applicable to this change would include architects, consulting engineers and cybersecurity consultants who design/recommend security systems, products and/or services.
For additional information on CANASA membership, benefits and the affinity program for members, please contact Erich Repper, membership services specialist at erepper@canasa.org or call 905-513-0622 Ext. 223.
CANASA is pleased to announce that Patrick Straw, executive director of CANASA, has been named to the ULC Standards committee for the production and distribution of cannabis. Straw will be joined on this important committee by representatives of three CANASA member companies. (See p. 6 for story details on this.)
Security Canada Atlantic will be held in Moncton on Sept. 12. CANASA is pleased to announce that Stephen Sayle, CEO of Sayle Group & Sayle Safety, specializing in developing health and safety environment management systems, will present the keynote address at the event.
Next up on the Security Canada calendar will be the big event in Toronto — Security Canada Central — on Oct. 24 and 25. The keynote address will be presented by David Shipley, CEO of Beauceron, focusing on cybersecurity and its role in government, military and public/

private safety. Please visit www.securitycanada. com for more information on the Moncton and Toronto events.
CANASA awards Kim Caron and Chris Izatt
Kim Caron, director of business development for Armstrong’s National Alarm Monitoring and past president of CANASA, has been awarded the R.A. Henderson Award for outstanding contributions to the advancement of the industry.
Chris Izatt of Falcon Security has been awarded the CANASA Outstanding Contributor Award for his commitment and contributions to the industry.
Congratulations to both!
All the information on CANASA membership categories and benefits, job board, links to Security Canada and the latest security-related news is available on our new and improved website: www.canasa.org.










Security Canada, produced by the Canadian Security Association (CANASA), returned for a full calendar of shows in 2018, making stops in Laval, Que., on April 25; Ottawa on May 9; Edmonton on May 30; and Richmond, B.C. on June 13. CANASA’s two remaining Security Canada shows are in Moncton, N.B. on Sept. 12 and Toronto on Oct. 24 and 25. For more details, visit www.securitycanada.com.





By Colin Bodbyl




Why facial recognition is superior to fingerprint alternatives and offers greater versatility
iometrics is the technical analysis of a person’s unique physical features.
“In many cases only an image of the person is needed to enroll them.”
The longest standing use of biometrics in the security industry is fingerprint recognition. This technology is commonly used as a form of access control to validate users without forcing them to carry an RFID badge or memorize a PIN number. While successful by many measures, biometric technology has never gained the kind of traction one would expect from such a futuristic technology. Recently, a different biometrics technology has been getting a lot of attention as facial recognition promises to overcome the challenges inherent to fingerprint recognition. Like fingerprint recognition, facial recognition is marketed as a credential validation tool for access control. It promises to overcome many of the challenges faced by fingerprint recognition.
The most common complaint about fingerprint recognition is hygiene. Studies have shown that touching a fingerprint reader is no less hygienic than touching a door knob. Somehow that has not been enough to change people’s minds about the cleanliness of these readers. Facial recognition easily solves this problem as no contact is required for it to operate; a person simply looks into a camera and the door unlocks, removing hygiene concerns completely.
Another challenge with fingerprint readers is their application in cold climates. Many parts of the world face sub-zero temperatures.

In these cases users may be wearing gloves or just have their hands buried in their pockets in places where every second exposed to the cold is unpleasant. In these applications, it doesn’t take long for users to resent the technology that forces them to chill their hand daily while waiting for the reader to analyze their fingerprint. Again, facial recognition does not have this issue.
User enrollment is another big challenge. Unlike RFID cards or even physical keys, where they can simply be handed to users, fingerprint recognition requires every user to enroll their finger in the system by scanning it several times while an administrator logs it in the software. Facial recognition is less invasive where in many cases only an image of the person is needed to enroll them.
The final issue with fingerprint recognition is false negatives. A false negative is when a user who is in the system is rejected by the reader because of a misread. Manufacturers
will boast a 99 per cent or higher accuracy rate but that still means users are rejected several times per year. This may not sound like a huge issue, but the reality is that users (especially those expecting perfect performance) can quickly become frustrated by the false negatives. Facial recognition doesn’t solve this problem either. Similar to fingerprints, faces can present differently under different conditions, which can generate a false negative.
Facial recognition is without question superior to fingerprint recognition, but it cannot overcome every challenge related to biometric technology. That being said, even though facial recognition may have a limited future in access control, it has many other applications outside of access control where false negatives are not an issue. In particular, the technology is good in active monitoring situations where a guard or monitoring centre only wants to be alerted of unknown visitors and the occasional false negative is
expected. Similarly, the technology will be extremely effective as a data collection tool to recognize frequent visitors or loyal customers. It is these types of applications that will make facial recognition far more successful than fingerprint recognition.
Biometrics is an exciting technology that has existed for many years now. Limitations around cost and functionality have prevented wide spread adoption. Fingerprint recognition has led the way in mainstream applications but inherent limitations prevent it from growing faster. Facial recognition promises to overcome many of these hurdles and while it is not perfect, it has many applications beyond access control that will bolster its growth and ultimately see it surpass the popularity of biometrics products of the past.
Colin Bodbyl is the chief technology officer for UCIT Online (www.ucitonline.com).

125 years of experience in putting the security of others first.
We understand you need to protect more than brick-andmortar, which is why ADT does more than monitor. ADT has a wide range of alarm and security options for organizations of any size to help protect people, goods, and data. With 24/7 surveillance, solutions against intrusion and fire, remote monitoring, interactive services and more, ADT has a security solution for your organization. Join those who trust ADT with their livelihoods and protect your business.
We are an integrator, meaning we can take over nearly any of the existing security equipment you have on-site.

We are customer-service oriented, innovative and technology savy.
With over 125 years of experience and 15 branches in Canada alone, including four monitoring stations, you can trust the experts.

IBy Victor Harding
All deals require diligence, but some bring added complexity and surprises
have been quite busy recently doing valuations and closing some deals, which is great. Being so busy also means that I learn things on almost every deal I do. Here are some of my latest tips.
Selling an integration or fire company takes much longer than selling an alarm company
This may seem obvious, but I have experienced this first hand. Think six months for selling a decent sized alarm company from start to finish and almost twice that for an integration or fire company. In my mind, this is partly because there is not as much of an established market or the same number of obvious buyers in Canada for integration or fire companies as for alarm companies. You can sell monitoring recurring monthly revenue or RMR. Installation and service revenue are more difficult.
Most buyers of shares expect to get working capital included in the deal When working for Voxcom and Protectron, helping them buy alarm companies, we very seldom cared if the seller gave us working capital in the deal or not.
Working capital is made up of all those current assets and liabilities at the top of the balance sheet and generally includes cash, accounts receivables, inventory, prepaid expenses, account payables and accrued liabilities. Most of the time, we preferred it if the seller’s balance sheet was completely zeroed out and just left us the deferred revenue.
As I learned later, this is unusual and relates partly to the fact that the buyer does not plan to continue to operate the company as a stand-alone business and partly to the fact that the monitored accounts will be folded into the rest of the buyer’s account base with very little added cost. With most buy-out situations, buyers of shares, and even sometimes the assets of a company, will expect to get some working capital included with the price they offer for the business. Many owners of small businesses are not ready for this and think that they are giving up money when they have to turn over the business with working capital in it. This is simply not correct. Buyers offering a price for the shares of the business should not expect to have to write a cheque to fund the activities of the business immediately

after buying it. Another way of looking at this is, the buyer is buying the entire business including all the working capital in buying the shares.
How much working capital a buyer gets upon closing is a science in itself and usually needs an analysis on what working capital the business generally needs day in, day out to operate.
One more important point to keep in mind when calculating working capital is expect that the buyer will include any of the business’ deferred revenue at the time of close, whether you normally calculate it or not.
If your deal requires your buyer to get a bank loan, count on adding months to get the deal closed
Again, this may seem obvious, but generally it does not come up when the buyer is examining the prospective business or even when an offer is put forward.
Getting a loan from the Canadian banking system to buy a company, no matter how good the asset you are buying, takes time. Secondly, often the security for the bank loan is the seller’s operating assets. So, the better the seller’s company, the easier it should be to get the loan.
When all is said and done, most integration companies don’t actually make that much money
This was a shocker to me. Truthfully, this is just a generalization I learned from talking to someone in the U.S. who deals with integration companies all the time.
Originally I thought it was just the integration businesses I was selling that were the problem. I sold one integration business two years ago that was doing more than $5 million in revenue annually but only making about $500,000 per year in net operating profit. I later found out that 10 per cent operating profit for an integra-
tion company was actually quite good and many only make five per cent of total revenue per year. Those making 10 per cent or more most likely have a sizable base of monitored accounts or other recurring monthly revenue. The only answer I can give for that lower profitability is pure competition.
The market has a way of re-establishing itself
For a while there, I was worried because many of the bigger buyers of monitored accounts in Canada had either been bought out or were not buying. VOXCOM, Protectron and Microtec were gone. ADT and Counterforce were simply not buying alarm accounts. I needed more buyers. Well, the wheel has turned and Counterforce and ADT are back in the game looking for accounts to buy. On top of this, there are at least two new, potentially national, buyers on the scene now looking to buy alarm accounts. The buyers for alarm accounts are there again.
Rushing a deal’s closing almost never works
If you are just selling alarm accounts and nothing else, it is possible, with planning, to close a deal quickly — although even the simplest deal will probably take at least two months to close. Buyers like to close at month’s end. However, if you are selling shares of your company and the buyer wants to operate the business as a branch office or standalone business afterwards, the deal will almost always take more time to close. This is particularly true if the seller is going to be working for the buyer. You have to do extra due diligence because it is a share deal. You will have to make decisions about working capital, employment agreements and other staff decisions.
Victor Harding is the principal of Harding Security Services (victor@hardingsecurity.ca).















Networking and IT skillsets are taking centre stage as security systems run increasingly complex software


By Ellen Cools




Internet of Things (IoT), big data, video analytics and the cloud are terms security professionals hear constantly these days.
But they’re not just buzzwords. These technologies are making security systems such as cameras and access control much more complex.
As solutions become increasingly complicated, the question arises — are integrators (and vendors) finding qualified installers for today’s systems, and, by extension, what skillsets and qualifications should installers have?
Before that question can be answered, let’s look at how the industry has evolved.
“In the last 10, 20 years…the industry has transformed from analogue to IP cameras,” shares Ken Francis, president of Eagle Eye Networks. “In the analogue world, we used coaxial cable, and when you plugged the camera in, it just worked — there was no programming or networking necessary to get a camera image.
“As we moved into IP and we introduced cameras and recorders and things with software







“As we moved into IP …the technicians had to get a lot smarter and more certified.”
— Ken Francis, Eagle Eye Networks
that were all requiring networks, the technicians had to get a lot smarter and more certified,” Francis adds.
“The previous training was strictly limited to a single device configuration, checkboxes,” says Liliana Andjic, general manager, low voltage services, at Houle, a Vancouver-based systems integrator. (Houle is also a two-time winner of SP&T’s Integrator of the Year award.) “There wasn’t really a level of complexity from the device itself, because…each and every single system was operating in an isolated environment.”
But as the industry has turned toward more connected solutions, often running on the cloud, this is no longer the case.
“We’re looking at the systems, including the


camera systems, as part of the total operational delivery,” Andjic explains. “The camera system becomes a part of the bigger ecosystem — that requires software configuration, that requires networking experiences in order to achieve the outcome the end user is looking for.”
This means installers have to focus not just on the installation, but also on the information that a device transmits to the whole system, she says.
“You’re talking about information sharing, you’re talking about dashboards, you’re talking about end users having information at the tips of their fingers,” she continues. “So it’s not just…a device sitting on the wall.”
Consequently, the necessary qualifications and skillsets for installers and integrators have changed.
Installers need a greater understanding of the software, networking and routing, Andjic says.
“They don’t have to be Cisco trained but they have to have VMware, which is becoming a big part of the virtualization, becoming a big part of the camera installation,” she elaborates.


“So the technicians have to understand how to configure the system, and, sometimes, work the applications [and] create the software applications that the camera will actually do.”
Jim DeStefano, head of security solutions for Siemens Building Technologies, adds, “While we still need installers to know inputs, relays and basic wiring, we now favour more IT backgrounds, a problem-solving mentality when it comes to the more complex projects.”
Consequently, “those that have an extensive IT knowhow and expertise are more in-demand as installers,” he says. Networking skills are highly desirable “because our customers expect us to be the experts.”
As a result, when hiring new technicians, Siemens is particularly interested in those with networking degrees and prior experience.
Additionally, cybersecurity education is key.
“Cybersecurity is a very important step that can’t be overlooked because most of our systems are on our customers’ networks, so we need to stay on top of these,” DeStefano says.
If technicians install a device and set it to its default password, “it creates a huge risk, a security hole in the customer’s network,” Andjic adds.
“You’re talking about information sharing, you’re talking about dashboards, you’re talking about end users having information at the tips of their fingers.”
— LilianaAndjic, Houle
“So it’s very instrumental that any installer has a very basic knowledge of cybersecurity.”
Sam Shalaby, CEO of Feenics, maker of the cloud-based access control solution Keep, agrees: “We need them to be in tune with the latest available technology, i.e., whether it’s software, whether we’re using the cloud, why and how we’re using the cloud, etc. The hardware is changing a bit so they need to be in tune with what changes.”
With regards to access control solutions, “Every controller has a resident IP on board, so it’s changed from the days of RS45 communica-
tion to now IP communications. So they need to understand IP communication, the utilities that allow them to address these panels,” says Shalaby. “They don’t need to be full-fledged IT people, but more or less [they need to] understand IP, understand cloud, understand the internet.”
Consequently, certifications are important.
“Installers should have networking skills and certificates that relate to their primary job responsibilities,” DeStefano says.
Certifications such as Cisco Certified Network Associate Routing and Switching (CCNA), Microsoft Certified Solutions Associate (MCSA) and Microsoft Certified Solutions Expert (MCSE) are particularly helpful, he says, along with other BICSI certifications.
Feenics also looks at integrators’ and installers’ certifications when choosing a dealer.
“We like to qualify our integrators to see if they can handle the software that we are selling, because the more qualified they are, the less taxing it would be on us,” Shalaby explains.
But Cisco and Microsoft certifications are not 100 per cent necessary, he argues.
“If you [the integrator] have a Cisco certification, if you have a Microsoft certification, of


course it’s a plus,” he explains. “But we also look at how long you’ve been in the business, who are the installers that you have — are they technologists, do you have engineering staff or engineering qualifications on staff?”
Houle, Feenics and Siemens all provide training for their installers.
Andjic says that continuous training is integral to ensuring installers understand the potential vulnerabilities in today’s security systems, as well as networking skills.
“It’s essential that ongoing training is being provided, not only from the manufacturing side, because there’s always critical updates that the manufacturer provides us …but in this complex Internet of Things environment … we have to make sure that we recognize what impact the camera creates on, perhaps, the building automation system,” Andjic explains.
“If they’re sharing several devices sitting on the same network, how to build secure networks, how to re-route a secure network, what sort of information can be stored at the facility, what sort of information can be transferred off the site [is important to understand],” she continues.
Houle has adopted a layered approach to training, Andjic shares, with entry-level, mid-level and then professional level networking training. The professional service group are Cisco trained and certified.
Likewise, Siemens provides a lot of on-thejob training.
The company provides basic training on topics such as compliance, data privacy and se-
“While we still need installers to know inputs, relays and basic wiring, we now favour more IT backgrounds.”
— Jim DeStefano, Siemens BuildingTechnologies
curity. New installers also shadow experienced colleagues in similar roles and take online courses that are pre-requisites for classroom courses, DeStefano explains.
“Typical on-the-job training might include basic wiring techniques, reviewing project drawings, basic access control and video terms,” he elaborates. “We also partner with certain equipment manufacturers and have technicians become certified in specific products and competencies.”
But in addition to general IT security training and education, “installers need to share effectively their experience as they encounter new areas of vulnerability. Lessons learned and information sharing need to be institutionalized in the organization through regular workshops with peers,” he says
As a vendor, Feenics also provides training, both online and in classroom settings, on their software.
“We do training on the hardware itself and the utility that we use for the hardware to address the panel and how to address it,” Shalaby elaborates. “And we do a little bit of recap on the network and how it works, and that’s not specifically our network but in general.”
Additionally, Feenics provides cybersecurity education to both vendors and end users.
“If an integrator took our product, we ex-
plain what we’re doing and how we’re doing it and what their role is and our role,” he shares. “We really take all the responsibility about cybersecurity ourselves, and we explain it to the integrator so the integrator can explain it to the end user. But we are also available for the end user to address all cybersecurity skills.”
Eagle Eye Networks also provides web-based and classroom training teaching technicians how to install their products, Francis shares.
However, Francis has a different opinion about the impact of today’s security systems, particularly those that operate via the cloud, on the installer’s role.
“In a cloud system, when you install the appliance or bridge, the bridge phones home to the cloud, like E.T.,” he explains. “And it does it on its own without the technician having to know how to do that. The technician does not have to open any of the customer’s ports and their networks, there’s no cybersecurity vulnerability that’s created through installing the appliance.”
In Eagle Eye Networks’ case, their cloud software identifies cameras and automatically sets them up for the installer, essentially making the camera plug-and-play, Francis says.
“That removes the burden of network skills and network savviness from the techni-
“We like to qualify our integrators to see if they can handle the software that we are selling.”
— Sam Shalaby, Feenics
cian altogether,” he argues.
“The installing company needs to understand networking skills because they have to decide whether or not they’re selling the right product,” he continues. “But the onsite technician does not.”
As a result, the company does not look for heavy certification such as Microsoft or Cisco, he says.
“The quality of the installation for the customer is really about three things. One, everything is done on a schedule. Two is the quality of the craftsmanship of the cable and device being installed. And three is the programming of the system,” Francis says.
Consequently, Eagle Eye Networks looks for program management and cabling skills in installers.
Specifically, the company looks for RCDD (Registered Communications Distribution Designer) certification, which “teaches [installers] how to properly install the cable so that the cable is not damaged, and how to put the ends on the cable so you get the best possible connection be-
tween the cable you’re installing and the network you’re plugging it into.”
Meanwhile, program management skills are key to meeting customers’ needs, Francis says.
There are a lot of logistics with customers who have a large number of sites spread out across the world, he explains. The project manager has to co-ordinate with other teams to get the equipment and cable-running parties to the correct locations.
“Getting all of that done on schedule for the customer and communicating with the customer about how they’re progressing with the schedule are all elements of project management that are really important,” he concludes.
So are integrators and vendors finding qualified installers for today’s systems?
Francis argues that there are more qualified installers in the industry compared to 10 years ago.
Shalaby agrees that while it’s difficult, the industry is “getting there.”
“And we’re helping them get there,” he says.
“As a vendor, we have a role to play with the integrators and we’re doing the best we can.”
However, DeStefano says, “Finding new people to go into the trades has become somewhat challenging.”
Siemens, therefore, is working with technical schools and high school programs to interest students in technology and recruit from that base, he says.
Andjic agrees that the challenge today is a lack of education.
“From a typical program, they [installers] come with a very limited knowledge,” she explains.
“We ended up finding the young engineers that have a combination of electrical or software development or electronics background, and we trained them to become some of those technicians.”
“It’s very, very difficult to find qualified techs,” she adds.
As such, Andjic believes the industry must create more awareness about this need and the current market.
“The industry has to educate more institutions, [develop] more programs that are tailored along the lines of where the industry is going,” she concludes. “Because I would say we are 10 years back in terms of training and where the industry is going, and it’s changing fast and furious.”



Artificial intelligence has taken the security industry by storm. Understanding its promise and current limitations is an important step to take.
By Paul Kong
has become a trending topic this year. Whether it is artificial intelligence, machine learning, or deep learning with neural nets, the terms are mentioned seemingly interchangeably in conversation and marketing materials. Before moving forward, it’s time to define some terms and set boundaries so our conversations and expectations can be better informed.
Definitions
• AI (Artificial Intelligence)
AI is the theory and development of computer systems that can perform
tasks which usually require human intelligence. For the security industry, AI might represent a self-aware intelligence, similar to the human brain, that is capable of learning by itself, reasoning, and making decisions, even when presented with new and complex situations. We are still a long way away from such a machine, but there’s no doubt we are headed in this ultimate direction. Because we’re far from actual AI, it is helpful for the industry to refrain from using the term when describing some of the current sub-domains of AI such as machine learning and deep learning.
• Machine Learning
Machine learning is a subset of AI and more correctly mirrors where we are today with technology and where we’ll be in the near future. Stanford University defines machine learning as “the science of get-


Add eye-level video feed to easily see faces over your VMS.
Respond and answer emergency calls from towers. (Even while patrolling facility!)
Unlock entrances remotely for visitors without credentials.
Do more than ever before.



The IX Series is the most versatile, peer-to-peer video intercom solution that integrates multiple security layers. Doors? Certainly. Emergency stations? Done. Mobile apps to empower roaming guards? You got it.
Plus, with no licensing fees, departments can save money by removing those hidden, recurring expenses often associated with other communication tools.
Discover what you can control. aiphone.com/integrate


ting computers to act without being explicitly programmed.”
Based on the construction of algorithms, statistical data can be analyzed and compared against known data models. This allows a machine to then make informed predictions, and in a sense, “learn.” A good example is self-driving cars. Self-driving cars are not yet completely autonomous and certainly not 100 per cent safe. Using these same technologies, we can teach cameras or servers to recognize patterns in objects and alert us or take actions when it finds matches. There can be no AI without machine learning, since “learning” is an essential part of any AI.
• Deep learning and convolutional neural networks
Deep learning takes machine learning to a new level based on neural network theory that mimics the complexity of the human brain. Deep learning is a specialized subset of machine learning algorithms and is typically used to analyze video and still images. Although deep learning is still in the early stages of development, it is a natural fit for security system analytics both for server-based
and on-the-edge processing.
Current use and limitations for security and surveillance Machine and deep learning-based analytics are actively being marketed and productized by some vendors.
However, many customers have been dismayed at the number of false positives (or false negatives) that are generated. The algorithms in use are frequently not mature enough to provide the 100 per cent accuracy that many businesses require for real-time event notification and decision making. It’s not necessarily the algorithm’s fault, as ultimately they are only as good as the data they have been given.
Existing data models can be purchased from third-party companies, but the question remains: How accurate are they?
Additionally, many of these new AI-based analytics are offered as “post processes” run on a server or workstation, when a majority of customer use cases demand real-time feedback.
It takes a significant amount of computational power for a machine to “self-learn” in the field, so learning might be best left to powerful server farms in R&D labora-
“Having deep learning analytics on the edge ... is clearly what everyone has in mind when they imagine the usefulness of such technology.”
tories and universities for now. Real-time analytics also require that video streams be uncompressed to be analyzed. While this might make sense for installations with a few cameras connected to a server, it’s clearly an unacceptable resource drain to decode (open) each compressed camera stream when hundreds of cameras are involved. Once an algorithm and data set are created, it can be “packed up” and embedded on the edge to perform real-time detection and alerts for the specific conditions it has been trained to recognize. It will not self-learn, but it can provide a useful function for recognizing known objects or behaviours.
Having deep learning analytics on the edge — analyzing the image before it is compressed and sent to storage — is clearly what everyone has in mind when they imagine the usefulness of such technology to alert staff and make decisions in real time.
The more we can automate video processing and decision making, the more we can save operators from redundant and mundane tasks. Computers capable of sophisticated analysis, self-learning and basic decision making are
much better and faster at analyzing large volumes of data while humans are best utilized where advanced intelligence, situational analysis and dynamic interactions are required. Increased value comes from the efficiencies gained when each resource is used most effectively. The goal is to help operators make better informed judgements by providing detailed input and analytics. This way, false alarms can be drastically reduced. Precise object classification will be a big part of the future, as will action recognition and behaviour analysis.
We see airport security, subways and other mass transit customers as early adopters of this technology. Detecting objects left behind is crucial in the world we live in today. The benefits to retail organizations wanting to optimize their business operations is equally important. It may even be possible to rank reaction to products based on learned postures and skeletal movements.
Systems integrators will be able to sell value far beyond a security system. Integrations with other systems, even customer relationship management (CRM) systems will be not only possible, but desirable as a way to enhance metrics for retail establishments.
Solutions for the near future may be a hybrid model where on the edge hardware combines with server software to deliver a powerful combination of analysis and early warning and detection capabilities. Comprehensive facial recognition will not be practical

ject recognition and classification is perfectly suited for in-camera analytics. We can easily imagine that deep learning-based analytics might take the same progression as traditional analytics.
The first implementations were server-based, then there was a migration to a hybrid approach where some algorithms were in the camera, but a server was still required for in-depth analysis, and ultimately the entire analytic process could be hosted on the edge.
The future looks bright for image classification
Being able to identify what’s going on in a still or moving image is one of the most interesting areas of development in machine and deep learning. With moving images, analysis goes beyond simply classifying objects, to classifying the behaviours and moods of those in the frame. Already, vendors are talking about “aggression detection” as a desirable feature, but it’s easy to imagine that the cost to an
“We see airport security, subways and other mass transit customers as early adopters of this technology.”
organization of a false positive or false negative in such a scenario could be very high.
Whether it’s big players like Facebook, Google or Nvidia, significant investments are being made in AI and machine learning to classify images and objects as well as text and speech. Some of this technology development will trickle down into the security industry, and much of it will have to be custom developed to suit the needs of surveillance workflows.
It may be OK to mis-label a person’s face in Facebook, but security organizations should not be willing to make such a mistake. This is one of many reasons why
and all its variants are understandably high. However, careful consideration is needed when choosing any AI type solution, as the reality of where the technology is today and the marketing hype may not line up.
At Hanwha Techwin, our R&D department continues to actively develop deep learning algorithms. We are training edge devices to
wind, snow and rain. Our continued focus is to streamline operations and deliver truly actionable intelligence. Object classification and skeleton-based action recognition lets us better detect violent postures and abnormal behaviours.
We are currently developing our Wisenet 7 chip, which will be focused on providing deep learning analytics on the edge. Hanwha
smarter, while focusing on an analytic engine geared toward video surveillance specific intelligence. Our development so far has shown that the benefits to surveillance analytics, as this field continues to evolve, will be substantial.
Paul Kong is the technical director for Hanwha Techwin (www. hanwhatechwin.com).

– Easily combine Altronix® power and accessories with access controllers from the industry’s leading manufacturers
– Trove enclosures with removable backplanes allow you to configure, layout and test prior to on-site installation
– Efficient, scalable designs for optimum performance and seamless integration
– Pre-assembled kits available in various configurations further reduce overall costs


Canon first announced it was creating a new spin-off company based on Milestone Systems technology back in June 2017 (Canon acquired Milestone in 2014).
The spin-off, originally known as ARCUS Global, would “address the significant unmet global market demand from large enterprises for Video Cloud IoT as a Service for security and business optimization,” according to a statement issued at the time.
The name has since changed to Arcules, but the vision remains the same. The company officially launched its Arcules Intelligent Video Cloud platform in July of this year, describing it as technology that “aggregates and analyzes previously untapped video surveillance and IoT sensor data, identifies trends in that data and applies predictive analytics to help businesses optimize operations and improve safety.”
The company is led by CEO Andreas Pettersson. Pettersson was previously the CTO and is also a veteran of Milestone, where he managed engineering teams and business units since 2010.
SP&T News: What was the genesis of Arcules?
Andreas Pettersson: Several of us came from Milestone incubation, which was a separate unit. We were up in the Bay area in a smaller office up there. It was [about] two years ago when we started getting into “what’s the real vision?” and “what is that we’re doing?” Then it was Canon together with Milestone that realized this is such a big opportunity — video Cloud IoT as a service. They said, “We have to have you as a separate company,” and that was a little more than a year ago. We launched in August [2017]. We were just a handful of people coming from Milestone. We are 60
By Neil Sutton
people already and we are probably going to be closer to 100 by the end of the year. It’s a big, big initiative. We’ve been ramping up the entire organization — R&D, sales, marketing. A lot has happened…
We knew that if we could harness video data and actually structure it and build intelligent insights with it, and then combine all of that with the IoT piece and all the types of devices that we are already seeing out there — that’s where it starts going from a reactive solution into a much more preventative type of the solution. That’s the path we’ve been on for quite some time.
We’ve seen the change [in the market]. I think a lot of it was triggered by … more and more the CIO becoming the decision maker [with] completely different expectations of what the system should be delivering. We’ve seen that happen, but it was a year ago or two years ago, where it really [started] happening.
SP&T: Where are you taking the company now and what is your relationship with Milestone and Canon?
AP: We operate completely inde-

ple say “Internet of Things,” sometimes it’s “Integration of Things.” Especially within hospitality we are already building some pretty cool, complete, end-to-end solutions. We have some really interesting early adopter partners.
SP&T: You recently transitioned from CTO to CEO. What does your role look like now?
pendently, which is one of the key reasons why this will be successful. Canon has done the same with Axis (Canon acquired Axis Communications in 2015); they have done the same with Milestone.
A few years ago, there was a lot of speculation as to what would happen. I was there [at Milestone] — nothing changed.
Of course, we are leveraging Milestone and Canon together to form Arcules. And we bring a lot of IP and knowhow from the Milestone side of that.
SP&T: What is your elevator pitch for what the company can do?
AP: Video Cloud IoT as a Service — we are going to be a global service provider for enterprises. What we do is, we’re really marrying all this data together.
Others talk about what they want to do — we are actually doing it, in terms of actionable insights, in terms of actually providing more than just video…. Smart cities, hospitality, retail are the key verticals.
There are a lot of sensors or other types of systems that we can already integrate with. When peo-
AP: I was also the CPO (chief product officer), so I have a very broad background on both the commercial side, running business units within Milestone, as well as marketing and finance. I’m not only a technologist — although I do like that — but I have been part of this since years back, creating the whole vision. I’m super excited with my new role and to keep going with the vision.
SP&T: You seem to have a big emphasis on developing company culture at Arcules.
AP: We interview about 15 or 16 people for every one hire. We do full personality assessments on everyone. We make sure they are team players. They have to be able to speak their minds, they have to be able to care for one another. They’re all results-focused, but you have to win together. That’s something we’ve been pushing since Day 1. If you walked into our office, you would see the energy — everyone is there, collaborating. They really enjoy it.
We’re trying to get people not from the traditional security industry. We are extremely diverse — on people’s skillsets, ethnicity and which industry they come from. We have one guy who is a medical doctor and decided he wanted to code. We have [another guy] who’s a lawyer…. One guy who’s a biologist. All of them are coding. If you have a lot of diversity, [you] get a lot of innovation in the long run.






























The B465 Universal Dual Path Communicator links a control panel’s digital dialer to an Ethernet connection on a local area or wide area network or to an optional cellular module to send reports to the receiver at the monitoring station. Dealers and integrators can now remotely program the device via Bosch’s Remote Programming Software (RPS) and have the option to use the Bosch Remote Connect Cloud Service to connect to it. The communicator is compatible with fire or intrusion control panels from Bosch and other manufacturers. www.boschsecurity.us

ASSA ABLOY
ASSA ABLOY’s PDU8000 Series Panic Device offers an engraved push area and boundary grooves to make exit doors highly visible. The device has keyed and nonkeyed functions, six standard exterior pull options and a selection of finishes. Designed with a patent-pending solid latch, it can be used with both mechanical and electric strikes. The PDU8000 is ADA Compliant, ANSI/BHMA A156.3-2014 and Grade 1 Certified UL305. Easy-to-install with spring size 4, the closer meets UL 228 codes. www.assaabloy.com

The A-ALR Emergency Exit Option for 6000 Series Exit Devices from Yale Commercial has all the features of an alarmed exit device and is suitable for commercial applications concerned with loss prevention. The product features a durable aluminum rail design with ANSI/BHMA Grade 1 certification. The built-in alarm is powered by a 9V battery and sounds at 90 dB at 10 ft. from the device. Other features include several alarm modes, low battery warning, tamper resistance and a red LED indicator to display that the device is armed.
www.yalelocks.com
According to Code Blue, Centry, a compact IP video help point, is the first help point to include a camera integrated into its faceplate, an embedded Station Beacon Light that will bring the visibility of blue light phone indoors. Powered by EmerComm, Code Blue’s device operating system, intelligence can be installed on location at the edge with an agnostic system of sensors and indicators to give emergency phones full computer capabilities. Available in either surface or flush mounts, Centry is also powered by Power over Ethernet, allowing a single connection to drive power and network connectivity to the device. www.codeblue.com


Constructed of polycarbonate, the Universal Stopper (STI13000 series) low-profile cover protects against physical damage, dust and grime, as well as severe environments, inside and out. The indoor/outdoor cover includes a high-strength continuous hinge and helps protect devices such as pull stations, keypads for entry systems, intercom stations, emergency buttons, electrical light switches, duplex plugs and more. Mounting options are available for exposed conduit or a waterproof Type 3RX black box. www.sti-usa.com


Eaton Wheelock Exceder LED3 notification appliances are compliant with the latest National Fire Protection Association (NFPA) code requirements for flash duration. The Wheelock Exceder LED3 line includes strobes, horn strobes, horns, speakers, speaker strobes, low frequency sounder strobes, and sounders for ceiling and wall-mount indoor applications. High-fidelity speakers provide leading intelligibility for mass notification and emergency communications. Exceder LED3 strobes can also be installed in the same notification zone and field of view with any Wheelock RSS strobe model. www.eaton.com
The INS-100 and INS-250 are the latest in the line of Potter IntelliGen Nitrogen Generators, and are built for smaller systems with the capability of being wall hung for compact applications. The INS-100 has a bypass fill capacity of 160 gallons at 40 PSI and a total system capacity of 675 gallons. The INS-250 has a bypass fill capacity of 300 gallons at 40 PSI and a total capacity of 1,000 gallons.The INS-100 and INS-250 utilize patent pending IntelliGen Controller software. This technology facilitates every aspect including pressure, runtime, power, connectivity and operational mode. www.pottersignal.com

The D2x family of beacons and combined alarm horn/beacon units are compliant to UL464 and UL1638/UL1971 for public mode fire alarm installation as emergency signaling devices for the hearing impaired, as well as private mode fire and general signaling applications. The D2x1BLD2-H utilizes an array of high power Cree LEDs. The D2xB1XH1 5 Joule Xenon strobe beacon and the D2xB1XH2 10 Joule Xenon strobe beacon both offer low inrush and operating currents that optimize cable selection. www.e2s.com

Johnson Controls
The Illustra Pro line now includes the Pro Compact MiniDomes in 2MP and 3MP resolution. The mini-domes are equipped with various viewing angles including corridor mode, a 9x16 field of view aspect ratio for vertically oriented scenes. IP66 and IP67-rated for environmental protection, as well as IK10 for vandal resistance, the cameras can be installed indoors and outdoors. Illustra IntelliZip compression technology monitors and adjusts system-streaming parameters to match the level of activity in the camera’s field of view. www.illustracameras.com
Total Recall Corporation

The new portable CrimeEYE LPR licence plate recognition unit includes an automatic licence plate recognition camera, emergency battery backup, Wi-Fi and pole mount. The company says its design allows it to be attached to a street pole in an area of interest and stream captured data to a command centre instantly. This gives users an audit trail of passing traffic, and allows them to alarm on BOLOs. CrimeEye LPR joins the lineup of surveillance solutions that Total Recall pioneered with the CrimeEye video surveillance unit. www.totalrecallcorp.com
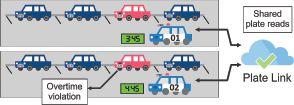
Genetec
Plate Link is a new feature for Genetec’s AutoVu automatic licence plate recognition (ALPR) solution. Designed to allow vehicles to share licence plate data while out on patrol, Plate Link acts as a force multiplier, allowing parking enforcement officers to administer shared permits and time-limited parking bylaws across multiple zones. With AutoVu Plate Link, any patrol vehicle can detect violations using licence plate data collected by other connected vehicles.
www.genetec.com
The L7 Series adjustable-height lectern has versatile adjustment options to meet users’ height requirements. Designed with both integrators and educators in mind, the L7 Series Lectern provides a welded steel frame with modular rack mount and storage option and additional small device storage below the work surface on the patented, removable Lever Lock mounting. It also provides integrated power, cable and thermal management, and AVIP plates for higher education applications. www.middleatlantic.com


Vanderbilt has released a new range of SPC wireless devices, including detectors, panic buttons, fobs and a transceiver. The devices feature two-way wireless technology that delivers ease of installation without compromising on the security of a wired system. With a 500-meter range, a building can be fitted in a couple of hours, the company says. Using Energizer lithium batteries, the devices also have an extended battery life of five years or more, and the devices’ settings are also configurable over the air. vanderbiltindustries.com



CheckPoint Tours is the latest service from the Connect ONE cloud-hosted integrated security management platform. It bundles intrusion, access control, video surveillance, energy management and critical environmental monitoring in a single user interface. CheckPoint Tours tracks and documents activities and tasks, working with conventional access control readers or ScanPass Mobile Credential to track activities by guards or other personnel required to perform tasks at specific times and locations. As the user scan/swipes each checkpoint their access is logged and can be reviewed.
simplifywithconnectone.com







The NanoLock platform guarantees device-to-cloud integrity and mutual protection during regular operations and firmware-overthe-air (FOTA) updates, according to the company. NanoLock prevents overwriting, modification, manipulation, erasure and ransomware attacks on firmware, boot images, system parameters and critical applications in connected and IoT devices. The company’s layered offering delivers a combination of cyber and cyber-physical protection, securing devices from the embedded layer out to the Cloud. www.nanolocksecurity.com

The latest version of Robotic Assistance Devices’ Security Control and Observation Tower (SCOT): Wally, is a wall-mounted security solution that harnesses artificial intelligence to enhance an organization’s situational awareness, communication abilities and control. SCOT Wally provides organizations with 110° of visibility and uses the RAD Software Suite, a collection of integrated software applications hosted in Microsoft’s Azure Cloud services that allows mobile access to alerts and controls. The solution can be used in lobbies, parking structures, corporate campuses or exterior areas. roboticassistancedevices.com
Vicon
Vicon’s new line of 180° ultra-high-definition multi-sensor cameras are designed to provide detailed coverage of large areas, such as airports, perimeter security and city surveillance. The new V1000 models are fixed camera domes containing four separate camera modules that work together to deliver a 180° view. Video can be monitored as a single horizontal image and separate quadrants.
www.vicon-security.com

Senstar
FiberPatrol FP1150 detects and locates intrusion attempts for up to 10 km or 5 km per side in a compact, rugged platform. The FP1150 extends the operational temperature range to 50°C, uses solid-state disk drives and integrates previously external optical modules. Fiber optic technology features low nuisance alarm rates, distinguishes between real threats and environmental disturbances, detects simultaneous events, provides software configurable detection zones and more. www.senstar.com

Hanwha has announced a new line of NVR servers designed for the Wisenet Wave VMS. The company also announced its turnkey WAVE client workstation pre-installed with Wisenet WAVE. All NVR servers are pre-configured with Wisenet WAVE VMS and preloaded with four professional licences. The servers include the WRT Series, the WRR Series and the WWT Series. All servers support Wisenet and ONVIF conformant IP cameras.

www.hanwhasecurity.com
The MR652 2MP outdoor IP camera, housed in an IP66-rated casing, is suitable for exposed outdoor locations that require 24/7 monitoring. The MR652 IP camera delivers full HD 1080p video at up to 30fps in H.264 compression. It also supports true day/night recording enhanced by infrared LED to achieve minimum illumination down to 0 Lux. To eliminate IR bounce, flat IR glass is positioned to the side of the lens to capture clear night-vision to a distance of 30m. www.meritlilin.com


The next wave for residential: A generation that has grown up with technology will be demanding Internet-based applications for their homes.
Fast Forward: Convergence is happening now — check your rearview mirror
Home automation, there’s an app for that: Mobile generation demands handheld-driven services for the management of their home infrastructure












Revolutions don’t come along too often — at least not in security. But the industry is sometimes eager to embrace a buzzword or capitalize on a trend. Two of the feature stories in this issue of SP&T look at how technology is changing the game — whether it’s a need for new installer training (and the potential difficulty in finding qualified technicians) or the industry’s embrace of the term “artificial intelligence” and the smarter systems it suggests.
The degree to which AI is actually having an impact currently is debatable (please read the story on p.20), but Liqiao Ying, a Waterloo developer who recently won
ONVIF’s inaugural open source contest urges security professionals to play close attention to both deep learning and blockchain — two other terms we are all hearing with increasing frequency (see p. 7).
Delving through the SP&T archives, the transition to IP-based security systems is likely the most important technology change for the industry in the last decade, though most would agree its arrival was a slow one rather than barging through the door.
Ten years ago (May 2008 issue), JF Champagne (then Canadian sales manager at Brivo Systems and later executive director of CANASA) compared the impending convergence of IT systems in
security to the earlier transformation of telephony to VoIP (Voiceover IP). “[VoIP] is now a mainstream business product and has brought new manufacturers and service providers into the field,” he wrote in his column. “The skill set required to sell and deploy such systems has also changed.”
Also in 2008, Tricia Parks, CEO of research firm Parks Associates, remarked in the November issue that IP-based remote monitoring and access control for residential applications was still very much in its infancy — but there were other factors to consider at the time, particularly the sorry state of the housing market towards the end of the decade. She did, however,
CANASA Update: It is really primetime for home automation? Manufacturers need to take a page from the Apple playbook to make their products more appealing
Camera Corner: Patience, the ultimate app — Camera technologies may take years to mature, but it’s often worth the wait

identify the potential of homebased, remote health monitoring systems and apps as “potentially huge.”
Regular SP&T Bodbyl observed more recently in the May 2016 issue that “it is not unusual to see revolutionary prod ucts take years to catch on. Most times it is the result of working out the kinks and bringing down cost that drives product out from the shadows and into the spotlight.” Bodbyl went on to identify the development cycles of hot tech nologies: thermal cameras, wire less cameras and edge recording. Revolution or evolution, hype or reality, progress almost always involves new technology.


Mobile security is about more than just monitoring passengers. A full solution helps you monitor the security, location and status of your vehicles and its passengers on the go all while utilizing advanced monitoring features from your main static location. #IntelligentSolutionsForYou


















Weiser makes it easy to increase customer loyalty and position yourself as the core provider. If you already install security or home automation systems that are Zigbee or Z-Wave compatible, you’ll appreciate the easy installation and integration of Weiser Home Connect Locks.
Gain momentum in remote access and home automation as homeowners demand more from their primary solution providers.
Grow your business by building upon your existing services with Weiser.