






Vipond recently held a customer and partner event to showcase some of the major innovations in security technology and design, often with the added benefit of providing information and intelligence that goes beyond the security department. The event, held at Toronto’s Royal Ontario Museum (see p.3 for more on the ROM’s recent security upgrade), included presentations and demonstrations from Axis Communications, AI solutions firm Anyvision and Genetec. It was co-hosted by Vipond’s own integration division Habtech.
Axis, known for its depth in the surveillance market, showcased solutions that go “beyond video security” or augment more traditional camera solutions. Stanley Kuan, regional sales manager, Axis, provided insights into the company’s radar detection solution, which uses electromagnetic waves to detect movement.
According to Axis, the solution is less likely to be triggered by common nuisances like animal movements and weather, resulting in fewer false alarms.
Kuan also reviewed Axis’ network audio systems, which offer security-based applications, such as mass notification and gunshot detection, but can also be utilized day-to-day for paging and broadcasting marketing messages.
In some cases, security and marketing can be part of the same package, said Kuan. For example, pre-recorded audio can be triggered if a person is detected as loitering in a specific area. Baby departments might be targeted by would-be thieves, since baby formula is a valuable commodity and potential theft opportunity. A pre-recorded message that simply says, “Thank you for shopping in

Stanley Kuan, Axis Communications (Image: Neil Ta)
the baby department” could also serve as a reminder that the area is being monitored and thus deter thieves. These types of solutions “make surveillance systems more robust,” offered Kuan.
Anyvision, an AI solutions company, is able to identify a person from a video stream without actually having to store an image of that person on file. The key, said Adnan Kichlu, regional sales manager, Anyvision, is utilizing the mathematical vectors that describe a person’s face rather than a picture of the face itself.
Kichlu demonstrated the principal by using a 20-year-old photo of a person to then detect that same person from current video — the geometry, not the image, is the key to detection and recognition. The solution is completely agnostic to the type of camera sensor or video stream it draws data from, he added, and is also GDPR compliant.
Kichlu said his company’s solution can be integrated with an
access control solution, such as a turnstile, to allow (or refuse) entry based on facial recognition. It can also be integrated into a smartphone to confirm the identity of the user.
Heat mapping, gender detection and gaze estimation (approximating where a person is looking, i.e. what draws their attention) are non-security related functions that would be of interest to a marketing department, he said.
Nada Ebeid, business development manager at Montreal-based Genetec continued the “beyond security” theme of the meeting with a presentation titled “Your building is talking. Are you listening?”
“Our mission is to really allow people to flow,” said Ebeid of her company, describing how technology enables people to “flow” through public life (public buildings, museums, transit systems, etc.), by enabling their movement rather than impeding it.
Genetec, known for its video management software, provides
other solutions that serve security purposes, like access control and licence plate recognition. It can also provide useful data points of how people utilize and navigate spaces. “Knowledge of how people are flowing through our different buildings helps us make better business decisions,” she said. “Anyone not acting on this data is going to get left behind.”
Ebeid indicated that work spaces are changing as the workforce becomes more mobile. Office real estate can be put to better use if tenants have a handle on how it is being utilized — “security” data (i.e. that generated by cameras, access control and LPR) can be useful in that regard.
Ebeid also cautioned that data comes with a cost if measuring tools are not deployed in a cybersafe manner. She estimated that only 30 per cent of cameras deployed in the field have up-todate firmware installed. “It’s about managing your exposure and being mindful of the technology you are putting in place,” she said.
— Neil Sutton
Anew industry consortium aims to change the way devices communicate by developing a technology that can pinpoint the location of objects within centimeters, while operating within line of sight up to 200 meters.

The FiRa Consortium (short for “fine ranging”) aims to harness UltraWideband (UWB) technology for use in access control, object detection and location-based services.
UWB has existed as a technol-
ogy for decades, but recent updates to the IEEE standard 802.15.4/4z, have enabled new use cases. The standard is “one of the key triggers for this renewed attention to this radio technology,” said Ramesh Songukrishnasamy, the consortium’s director and treasurer and CTO of HID Global.
“Any effort like this can only happen when we can build a rich ecosystem of partners,” he added. “One of the primary focuses of this consortium is really to create interoperability standards so that multiple device manufacturers, chipset manufacturers and service providers can all come together and deliver a more interoperable open solution to the market.”
Sponsor members of the consortium include HID Global, ASSA ABLOY (HID’s parent company), Bosch, Samsung and NXP. Newer members are Sony, Litepoint and TTA.
UWB isn’t designed to replace
technologies that are already in common use for wireless security and access control, like WiFi, Bluetooth and NFC (near-field communication), but could work in conjunction to produce superior results.
There are multiple use cases for the technology — an obvious one is access control. Songukrishnasamy explained that NFC requires the user to practically touch a device to a reader in order to gain access, but with UWB the interaction is smoother. “That type of friction or inconvenience could be eliminated with this type of technology,” he said.
For example, since a device (and its user) can be pinpointed to a highly accurate degree using UWB, the technology should be able to infer the user’s intention to approach a door much more easily.
“Using UWB, you can get more precise ranging and positioning, up to a centimeter. That would help one to determine how close they are to the door or the
lock or a particular location, or where an asset is… things like that,” said Songukrishnasamy. He added that the “angle of arrival” will be much more apparent — i.e. whether the user is walking towards a receiving object, like a reader, or simply passing by it. “It’s very seamless compared to how you would do it otherwise.”
The consortium was in the planning stages in May, said Songukrishnasamy, and was formally established in August. Songukrishnasamy estimates that by the end of this year, or early next, the standard will be available for use in future products. “The fact that we have all the key industrial players as part of the consortium clearly demonstrates their commitment… We are talking to other players as well.”
HID Global conducted demonstrations of the technology at the recent GSX conference in Chicago along with partners Samsung and NXP. More information about FiRa, UWB and its use cases are available on the consortium’s website (www. firaconsortium.org).
— Neil Sutton
For Ascanio Odorico, security is a balancing act between protecting and pleasing the public who visit the Royal Ontario Museum.
A Toronto tourism and cultural staple, the ROM is home to a massive collection of artifacts — approximately 13 million — five per cent of which are on display at any given time across 40 exhibit areas. The goal, said Odorico, is to mind the precious objects and protect the patrons but in an environment that doesn’t feel restrictive or oppressive. “I need to find that balance of technology that is out there and be able to mitigate that risk without impacting the visitor experience,” he said.

There is a trend in museums globally towards more openness, allowing visitors to get up close to art and historical objects to enhance their appreciation, he said. The downside is, some people want to get too close — encouraging their children to be a little too hands-on, or sidling up to exhibits to pose for selfies.
Odorico spoke recently at an event hosted in the ROM and organized by Vipond, a Mississauga, Ont.-based provider of fire and security systems.
He was interviewed by Nada Ebeid, business development manager at Genetec. The manufacturer has a long-standing partnership with the ROM and was recently engaged with the facility as it
upgraded security systems over a four-year period.
Upgrading security systems, while at the same time simplifying them, was a goal for Odorico, who has worked in the ROM’s security department for 16 years, the last five as its head of security.
The ROM was using multiple systems to handle security, which sometimes proved difficult in terms of management and staff training. The ROM’s most recent upgrade has helped in that regard, he said. “We kind of undertook a four-year project. In the last year and a half, it’s been fully implemented.”
Odorico is eager to embrace new technology, but is also “old school” when it comes to big picture thinking. With pen and paper, he said he likes to outline a plan based on three categories: “My needs” — the essentials for

a successful security implementation; “My wants” — the nice-tohaves if budget wasn’t an issue; and “My wishes” — a category of possible future implementations based on vendor partners’ product roadmaps and how the museum’s security requirements might evolve over time.
Addressing broad trends across security, Odorico said he believes cloud-based technology will continue to play a large role, due to its affordability and scalability. He also sees biometrics stepping up as the technology gets cheaper and its ability to deliver real-time information becomes even more useful to security professionals. Whatever security professionals adopt, now or in the future, Odorico encourages them to hold their vendors accountable for their products.
— Neil Sutton

WBy Neil Sutton
e have a new employee in our office and her name is Moxie.
SP&T News’ parent company, Annex Business Media, operates approximately 65 other magazines, so there are new employees on-boarded every month. Moxie, however, could likely be described as our first digital co-worker.
A few months ago, Annex introduced a new visitor management system to our Toronto office and called it, cheerfully enough, “Moxie.”
Annex employees all received an email when the system was first installed: “Moxie is our new ‘recep-
tionist’ who will be taking over the reception role at the Annex North office. Moxie will be responsible for checking guests in, alerting individuals that their guest has arrived and
short shifts of a few hours.
We’re not a public-facing business, so the foot traffic to our Toronto office isn’t heavy, but we do receive daily guests, couriers, interview candidates for job openings, as well as staff from our office in Simcoe, Ont., who all use the system to check in (and out).
out is just as important as check-in. Companies need an accurate count of personnel in their office at any given time in the event of an emergency situation or an evacuation.
checking out guests when they leave.”
Prior to Moxie, we relied on a paper-based system to check guests in and out, and the reception desk was staffed on a rotating basis by Annex employees who sat in for
As someone who writes about the industry on daily basis, I immediately recognized Moxie for what it is: a piece of security technology. So naturally, I had to try it out. There is signage next to the tablet where Moxie resides indicating you need to sign in, and the interface itself is very simple: provide your name and the name of the person you are visiting and the system will automatically generate a text and email, notifying that person that you have arrived. You are also invited to take a seat in our visitor area. If you don’t check out when you leave, Moxie will prompt your host to do it for you.
Anyone familiar with security procedure will know why check-
I’ve used systems similar to Moxie in other facilities and businesses. In some cases, companies may also employ a receptionist or greeter who will direct the guest to use the visitor management tool. The more intuitive the interface, the less they need to intervene or explain. And these systems are becoming more and more common. A researchandmarkets.com report from August of this year forecasts that the global visitor management market will grow more than 15 per cent CAGR over the period 2019-2025, driven by the increasing need to “inspect and detect intruders” and also to “enhance the customer experience.”
“We look forward to working with Moxie,” concludes the introductory staff email. So far, so good, Moxie.







How ONVIF’s Profile A is helping to improve interoperability between different manufacturers’ products.
By Bob Dolan
Access control systems and their components have historically been designed and manufactured in a proprietary way. This approach has made achieving interoperability between different manufacturers’ products a difficult process. It sometimes has involved developing unique drivers for specific devices or creating workarounds to get readers, panels and other

“When enabled with artificial intelligence, access control and other building systems can begin to recognize patterns, anticipate events and behaviours and make proactive changes.”
access control peripherals to share information and communicate with a common access control management platform.
The need for interoperability, which is making different types of devices or technologies communicate with one another, is certainly nothing new in our industry. At Anixter, we have been testing interoperability in our Infrastructure Solutions Lab for many years, connecting devices and clients from different suppliers to our test server site to ensure that integrations and multi-supplier solutions are going to work correctly for our customers in real-world scenarios.
As a result of access control’s proprietary nature, customers often have remained confined to deploying single-supplier access control systems and felt forced to buy access control panels from a particular manufacturer in order to maintain their current investments in legacy card readers, door controllers and card technology. But the industry is changing as the development of standards-based applications grows, and end users and system integrators alike are recognizing the value of open standards, such as the interoperability standards created by ONVIF.
ONVIF Profile A provides an interface for ONVIF member developers to use when developing access control software and other security products. Profile A defines the requirements that govern how one Profile A application can communicate and interact with another, facilitating interoperability for multi-vendor projects.
The open device driver used in Profile A conformant access control panels allows end users to integrate control panels and management software from different manufacturers. This gives end users the ability to make choices on specific hardware for their access control systems and, even more importantly, means that if you want to install another supplier’s access control management software in the future, you don’t have to rip and replace existing access control hardware in order to do so. The common interoperability of ONVIF Profile A provides the bridge between the legacy hardware and new software if both are Profile A conformant.
The tipping point is now
In contrast to the video surveillance market, access control technology has historically been slow to change in large part because of the high upfront costs to acquire and install a system and the longevity of the equipment — commonly between 12 and 20 years. End users and their need for open network-based infrastructures are driving recent changes in this market, as the line between physical security and IT continues to blur. Physical security systems are now often managed by IT departments and IT directors are rightfully demanding open architecture approaches (like IP networks) rather than the proprietary and sometimes duplicative design of traditional security systems.
The drive to an open architecture approach has proliferated across many related industries, and today we see lighting, HVAC and other functions residing on the network as well, offering businesses the option to minimize operating costs and to better control and monitor their facilities. This trend of hosting everything on an IP network clears a path for an Internet of Things, which in many respects is already here.
The network can already transfer pieces of data from one system or device and correlate it with other data in analytics software programs, ultimately providing usable, actionable information to end users, aggregated from such several systems as video, audio, intrusion, voice and other systems. Multiple network-based systems make things like intelligent building automation a reality, delivering costs savings, keeping people and assets safer and using less energy.
As one of the major platforms within a smart building environment, access control systems play a large role in this IoT scenario. When connected to other, seemingly disparate building systems using a common
interface, this deeper interoperability enables increased productivity to the overall system. As a contributor to an intelligent building ecosystem, access control systems also serve as a repository of large amounts of data — tracking people’s movements for real time facility population data or facility usage based on the day’s meeting room booking schedule. The more data that is available within a system means the more quickly adjustments can be made, further ensuring the security and efficiency of the building.
When enabled with artificial intelligence, access control and other building systems can begin to recognize patterns, anticipate events and behaviours and make proactive changes to the building environment, enabling its occupants to work more efficiently. Whether the temperature and lighting for a room is adjusted based on recognized patterns — a 10 a.m. meeting every Thursday on the fifth floor, or doors are unlocked in anticipation of a recurring event, AI allows for systems to be smarter, more effective and provide additional costs savings by further reducing the administrative burden of the system.
With so much data being fed into these management platforms, from AI technology or other more traditional sensors, a stumbling block to true interoperability still remains. To effectively be able to harvest actionable information out of the received data, it has to be readable in a common format. Data readable in only one proprietary ecosystem will jeopardize the idea of interchangeable information, and further reinforce the silos that exist between the largest providers. Profile A could offer a solution for this in the future, by providing users with that common interface, and allow the market to continue to grow through interoperability and innovation.
Profile A essentially levels the playing field between large and small manufacturers, eliminating the need for proprietary protocols between suppliers for communications between different components of a system. End users can, for example, choose specialized, high-end access controllers and panels from one manufacturer to use with Profile A conformant access control software that is perhaps lesser known, but that provides what the end user needs when it comes to management and reporting.
And as manufacturers continue to adopt Profile A into their products, access control componentry that conforms to Profile A will mean that a business doesn’t have to rip and replace the Profile A conformant access control devices in the facilities that they’ve acquired. Instead, they can deploy and use their own preferred management software in the newly acquired facilities using existing hardware.
With the development and release of Profile A, ONVIF is making a long-term commitment to open access control systems in particular. The development of Profile A took two years and the work of many ONVIF member company representatives from all over the world to develop a standard that can take the physical security market into the next decade.
One thing that ONVIF and Anixter have in common is our view that standards are created to be tools that let customers make educated decisions, with the freedom to choose the hardware and software of their choice, regardless of manufacturer. When end users can just think “It works,” and move on with their day, that’s when we know ONVIF has done a good job in developing a practical solution.
To learn more about Profile A or any of the ONVIF Profiles, visit www.onvif.org.
Bob Dolan serves on the ONVIF Technical Services Committee and is Director of Technology for Anixter.

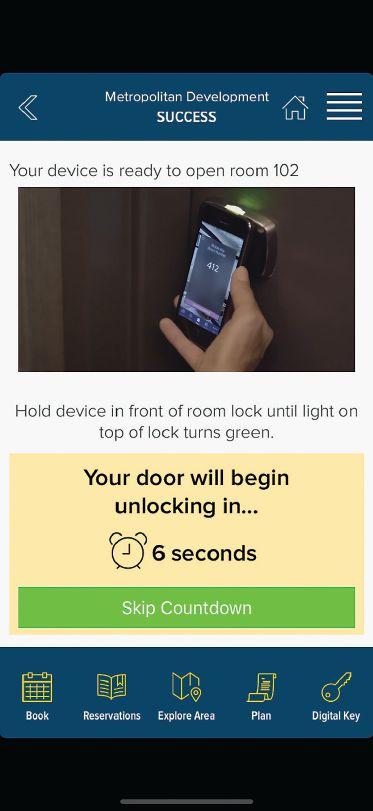
Using a phone to open doors, instead of a key card that can be easily lost, can make life easier for both end users and security teams, but there are barriers to adoption.
By Will Mazgay
For decades, key cards have been a pivotal piece of access control in public spheres, but increasingly, more offices, educational institutions, condominiums, hotels and other organizations are making this part of their security system digital, with access control through mobile phones.
“Some of the benefits are clear … you don’t have to worry about a lost or forgotten card.”
— Brandon Arcement, HID Global
Research firm IHS Markit found nearly 20 per cent of sales of access control readers sold in North America in 2018 were designed to be able to accept mobile credentials, and the global market size for mobile-capable access control readers is expected grow from approximately 700,000 annual unit shipments in 2018 to nearly 2.5 million shipments by 2023. Also, by 2023, more than 10% of new security credentials issued worldwide will be mobile credentials.
Bryan Montany, analyst with IHS Markit, says industries with a high proportion of Millennials and Generation Z workers, such as IT, web services and marketing, represent strong markets for mobile credentials, as do other types of corporate offices, higher education and hospitality.
Montany continues, “Another strong market for mobile credentials are commercial buildings that employ a significant percentage of temporary workers, such as contractors.” He says managing credentials for temporary workers is much easier through mobile than with cards or badges.
The security technology industry’s heavy hitters are investing in this technology in a big way.
HID Global, for example, has 2,500 organizations using its Mobile Access solution, first launched in 2014. This is according to Brandon Arcement, senior director, Strategic Partnerships at HID Global.
So why is using a phone as a key becoming so popular, and why is this technology more appealing than a plastic card?
Arcement lays out three value propositions:
1. Greater user convenience
“For users, some of the benefits are clear: you have fewer items to carry, you don’t have to worry about a lost or forgotten card,” Arcement says. Also, “you don’t have to go to a specific location or wait for a shipment in the mail to get a credential — it’s delivered in milliseconds over the air.”
2. Greater operational efficiency for the security department itself
“Think about a large global organization oper-

ating in several countries. Today they are managing pieces of plastic with RFID chips in them that they are shipping and printing and distributing and managing around the world,” he says.
“With mobile access, they can convert that process of managing those physical pieces of plastic into digital, online and automated processes.” Acrement also notes that overnight shipping an access card to a new employee can cost $40-$50 a piece.
3. Higher security
“The vast majority of cards that are used today have significant security vulnerabilities,” Arcement says. “HID Mobile Access uses very secure technology to encrypt the data being exchanged between the reader and the phone. It cannot be forged or cloned or spoofed the way many prox cards, magnetic stripe and legacy smart cards can be.”
Arcement says managing lost credentials is also easier with mobile.
“We did a study some years ago that showed the average lost card took three days to be reported lost or stolen,” Arcement says. “If you compare that against the fact that the average person checks his or her phone 70 times a day, it’s far less likely that a mobile device is lost, forgotten or stolen, and if it is, you can revoke the credential over the air — it’s noticed immediately and wiped within the hour.”
According to Arcement, another element boosting security for mobile credentials is the presence of phone authentication via biometrics, such as facial recognition or touch ID. Whereas, if someone get a hold of a card, they
A range of devices featuring HID’s Seos credential technology (image courtesy HID Global)
immediately have access to whatever it opens.
Montany agrees that phone-based biometrics are a major selling feature of mobile credentials, as they “offer increased security to end users at a much cheaper price than the average cost of installing biometric readers on-site.”
Lastly, mobile credentials provide flexibility. “With cards, any time there’s a vulnerability it’s required to replace all cards. With mobile applications, security updates are addressed in the middle of the night in a few seconds while everyone sleeps,” Arcement says.
Providing mobile credentials is done through two different types of communication technology, Bluetooth and near field communication (NFC), and debate swirls over which is superior.
NFC only works at close range and mimics contact with an access card.
“In terms of emulating the traditional card experience, NFC does that best,” says Arcement. “Whenever you’re trying to disrupt an industry or change an industry, a lot of times the best thing to do is just emulate what the user had before. So NFC is more consistent, more reliable and more familiar to someone who’s conditioned to using a smart card.”
The downside is that the read range is limited to 10 cm, and it’s also open on Android, but closed by Apple, which is prohibitive for many smart phone users.
On the other hand, Bluetooth is available cross-platform with no conditions. The other value is its long range.
“What it (Bluetooth) lacks in speed and
“Cards and badges won’t be disappearing any time soon.”
— Bryan Montany, IHS Markit
throughput and familiarity in a conditioned user, it makes up for by innovative ways to open up a door. For instance, triggering a door as you walk up to it by tapping something on your device, so by the time you get there it’s already opened,” says Arcement.
Bluetooth is also ideal for parking garages, because users don’t have to roll down their car window to access the premises. It can also be programmed to work within close proximity to door readers, like cards, in addition to being used from a distance.
He argues that HID’s solution provides the best of both worlds by supporting both NFC and Bluetooth.
“That combination of both makes it a more seamless access experience, because there are some circumstances where NFC is preferred and there are some very good cases for the use of Bluetooth,” Arcement says.
For HID’s mobile credential solution, an organization’s physical access control system is largely preserved: wiring, cabling, panels, power supplies, software. The only hardware upgrade that is potentially necessary is HID readers compatible with the firm’s solution. “Those will support your existing card population alongside mobile credentials that can reside on either Android or iOS operating systems,” says Arcement. “If you’ve purchased something in the last few years, chances are very good that it will work with the solution,” he continues. “But obviously there is a lot of legacy infrastructure out there from HID, sister organizations, as well as the competition that would not be compatible and would need to be upgraded.”
The cost of upgrading readers, despite the fact that they accommodate card credentials as well, can be a barrier for some firms.
One method to bring down the cost of implementation, which isn’t always possible depending on the technology, is by retrofitting existing readers or locks, a solution that is appealing in the hotel industry, where the prospect of replacing every lock on a property is very expensive.
Fuel Travel Marketing, a software support and marketing firm that operates a white label app for boutique hotels, is partnering with ASSA ABLOY Hospitality to add mobile phone access control to its app’s functionality.
For hotels to integrate mobile credentials throughout their properties, they have two options, according to Stuart Butler, chief operating officer at Fuel Travel. “Either you can buy the lock with the wireless communication functionality built in or you can actually retrofit existing locks to work with this technology,” he says. “They essentially add a chip into the ex-
Fuel Travel’s mobile access control app (image courtesy Fuel Travel)
isting lock so you’re not having to replace the physical hardware.” Butler asserts that this can be a huge cost saver.
This system employs short range Bluetooth — users have to hold the phone right up to the lock. Butler says the close proximity reduces the risk of the data exchange between the lock and the phone being intercepted, and encryption provides an additional layer of security.
The firm’s app provides independent hotels with the ability to offer the same high-tech features available on the big chain’s apps, such as booking capabilities, tourist information, value-added promotions, and digital check-in and check-out. Mobile access control is just the latest piece of that puzzle. Butler says it helps to streamline the check-in process, allowing guests who have checked in digitally ahead of time to simply show up at the front desk at an express line with a piece of identification, and then authenticate into the mobile app — using either biometrics or a password. After this, they are given access to their mobile key.
Butler says user conveniences like mobile access control are essential to help independent hotels compete with chains, which have traditionally been early adopters of technology. “They were early upgrading their websites to be mobile friendly, they were early releasing mobile apps, so they have a tool kit and infrastruc-
ture at scale that makes it hard for independent hotels to compete… especially Marriott and Hilton primarily,” he says. Both Marriott and Hilton offer digital keys on their hotel apps.
Despite the convenience provided to users by mobile credentials, there is still hesitation to adopt the technology.
Arcement says he sees hesitation from organizations and security professionals because of unfamiliarity. “This is new technology, where there is still some reluctance by some in order to adopt it until it’s more proven…there are still many in the security industry who wait until there are more definitive use cases and studies and follow the market.”
IHS’s Montany concurs: “Access control is a very slow market to evolve and embrace new technologies, and mobile credentials are no exception.”
He reiterates that the cost of mobile capable readers and installation is a stumbling block for some companies, “Mobile-capable readers tend to cost at least $50 more than non-capable variants.”
Montany also says fear of cybersecurity vulnerabilities is causing hesitation. Any time an organization is hosting data remotely beyond their central control, as is the case with smart phones, regardless of the encryption, there are risks, he says.
There are also some markets where adoption generally isn’t gaining much traction, he explains, such as transportation, industrial facilities, government buildings and health care, “where buildings tend to employ much more sophisticated access control systems that still require physical credentials,” says Montany.
Arcement is optimistic about the future of the technology, “It’s a once in a generation change for our industry. I think we’ll see significant growth, modest growth likely over the next few years and then a significant pivot or inflection,” he says. “Of the 2,500 customers that we have, you can probably count on one hand the number that have replaced cards.”
Montany says we are a long way off from mobile credentials replacing physical credentials completely, and instead we will see a hybrid approach, where access control readers are designed to accept either mobile or physical credentials. He explains that more mobile-capable readers are being adopted in anticipation of later implementation of mobile credentials.
Montany says, “There are a few specific markets where outright replacement of physical credentials with mobile credentials is slightly more likely — hotels, university campuses, businesses that hire younger employees — but, most access control vendors view mobile credentials as an additional feature to offer along with physical credentials, so cards and badges won’t be disappearing any time soon.”


Our number one goal is to make your life easier and provide solutions you need to operate efficiently, reduce costs and meet compliance requirements. While our solutions solve these challenges, AMAG’s first priority is to become your number one trusted advisor. As your true partner, together we can determine how to use your data to identify risks, streamline business, automate processes and reduce costs.

Securing venues as large and as busy as sports stadiums requires a team approach to communications, surveillance, weapons detection and access control
By Will Mazgay


Sports bring people together. A lot of people.
Stadiums and arenas take in thousands of spectators every time there is a sporting event or a concert, and controlling where they can and cannot go, keeping track of individual behaviour, and ensuring they don’t bring dangerous items past the gates are difficult undertakings — next to impossible today without the smart use of technology.
To that extent, multinational security services firm G4S says it offers a full suite of integration services.
Jason Simpson, manager, corporate risk services for G4S Canada, says the security operations centre is “the beating heart of the security program that runs any sort of massive event space like a stadium…and you’re going to have everything flowing through that.” He continues, “Your people on the ground are going to be integrated with the command centre and issue commands about where to go or what to do or what’s happening.”
One of the firm’s most notable projects was their involvement in the renovation of Hard Rock Stadium in Miami, home to the National Football League’s Dolphins and the University of Miami football team, the Hurricanes.
Simpson says of the project, “The hub of the solution is the G4S security command centre, where all the trained personnel maintain eyeballs inside and outside of the stadium to be able to respond quickly and efficiently to any incidents.”
G4S says it helped build the new security operations centre for the venue, from initial design to cabling infrastructure, as well as ensuring the capabilities of the server worked in conjunction with the camera system installed. G4S partnered with camera manufacturer Avigilon to provide video management software and 829 cameras for the stadium and an accompanying training facility. “There is the very high resolution surveillance system now that covers the facility, the parking areas, the perimeter,” Simpson says.

Edmonton’s Commonwealth Stadium is home of the Canadian Football League’s Eskimos — called “The Brick Field at Commonwealth Stadium” during Eskimos games and team events — and it is a venue that relies heavily on surveillance technology as well. To keep track of what’s going on in every corner of the sprawling 56,400 seat venue, roughly 150 high-definition CCTV cameras are utilized.
Jason Fesyk, events supervisor for Commonwealth Stadium, says, “It’s really helpful to have the CCTV cameras. We utilize them for a lot of monitoring of specific areas, areas where we know that there’s going to be congestion, areas that we know have high traffic volumes. That way we have a firsthand look at what’s going on there, and we’re able to deploy our resources, be it our usher teams, our security teams, and even Edmonton Police Service, to areas when we need to.”
However, given that Commonwealth is an outdoor stadium, ensuring that cameras are able to capture what’s happening clearly in all lighting conditions can be tough. Fesyk says, “It becomes a lot more of a challenge with the sun setting in the west. A lot of the cameras along that side need to be strategically placed so that when the sun is going down or at the highest point of the day, we’re able to still get quality views from those areas.” He continues, “Our group of security electricians that help us to install and get these cameras into the right positions do a really great job of making sure that we’re putting the cameras in the place where they’re the most valuable for us, that will allow us to use the full extent of the camera and not be blocked out by bad angles or dark corners.”
Fesyk says artificial lighting, both in open air and indoor areas, is also crucial to ensuring cameras are capturing clear footage. “We’ve moved a lot of our lighting over to LED lighting, in the concourses and in our food service areas so that we have the best available vision with those cameras
“Drones bring a ton of unique and creative security challenges.”
— Jason Simpson, G4S Canada
either during the day or at an evening event,” he says. Fesyk explains that LED lighting “helps us with bridging that gap from natural light to our covered-in areas. It’s easier to pick up and detect when the light is a little bit more consistent.”
Beyond adjusting to shifting lighting conditions, G4S’s Simpson says another potential issue facing outdoor stadiums is dealing with drones. “How people are able to mitigate those drone incursions and what they can do might be as simple as a network of wire mesh that nothing can pass through.” He continues, “The technology to stop the drones isn’t necessarily widely available or invented yet…You can’t cut a wireless signal, you can’t cut a radio signal without messing up other stuff. Drones bring a ton of unique and creative security challenges.”
While flying robots buzzing through a football field might provide headaches for security, what really keeps these professionals up at night is the prospect of weapons entering their facilities. In the age of mass shootings, weapons detection at large event venues has become a focal point for security.
Walk-through metal detectors have become standard policy for most North American sports leagues.
Kevin Kempcke, director of security for Maple Leaf Sports & Entertainment (MLSE), is in charge of two marquee sports stadiums in downtown Toronto: Scotiabank Arena, the home of the Maple Leafs and the
“Once metal detection started to be implemented, people changed their ways.”
— Kevin Kempcke, MLSE
Raptors; and BMO Field, where Toronto FC and the CFL’s Argonauts play. He says walk-through detectors, mandated by the National Hockey League in 2015, made an immediate impact. “When we first introduced metal detectors we were catching approximately 50 knives a game from people coming in,” he says, noting the detectors provide a quicker throughput of guests as well.
Kempcke further explains that since initial introduction of metal detectors, guests have shifted their behaviour. He says, “People would carry swiss army knives, utility knives, box cutters. But once metal detection started to be implemented, people changed their ways and said, ‘I can’t bring my swiss army knife to the game anymore.’”
Kempcke does acknowledge that metal detectors aren’t perfect, as they are tripped by benign items like keys and cell phones. He says, “But there’s new technologies and we’ve been looking at them — technologies that won’t detect cell phones or keys and it’s only going to hit knives and guns.”
Liberty Defense Technologies, a Vancouver-based firm, is working to bring such a technology to market, which it licensed from the Massachusetts Institute of Technology.
The firm’s CEO, Bill Riker, says his weapons detection system, called Hexwave, uses three-dimensional radar imaging to create images of objects on individuals’ bodies, and those images are analyzed by artificial intelligence to determine if they are benign, or in fact, knives or guns or bombs. He says the system can also pick out objects like bottles of alcohol, and it works for both metallic and non-metallic items.
Riker explains further that the system’s panels send out low-power radio frequency signals, and that energy hits objects and generates 3D maps that are then received by the same panels. That’s when the AI-powered analytics go to work to determine what an object is and where it is on a person’s body. Riker says, “We teach the algorithm what all the target objects look like, and it’s that algorithm that resides in each of the units that enables us to do the real-time threat determinations. So it’s the algorithm taking a look at this image and saying, ‘Ah, that’s a handgun, that’s a set of keys, or that’s something else’…And we teach the algorithm what an object looks like at all different angles.”
All computing is done within the units themselves, and according to Riker, quickly. “When I say real-time, it’s actually doing the detection and the analysis in roughly 0.2 seconds, and that’s a constant update, like a video rate almost.”
The CEO touts the system’s versatility, saying it can be deployed overtly or covertly—behind walls or in kiosks or vestibules. It works both inside or outside, and it can integrate into existing systems like video management, access control or a security operations centre, and detection can be set up to trigger locking doors, queuing up cameras or communication with the stadium’s central hub. The system can also be manned by guards with tablets.
Riker says the system makes security teams more agile. “Right now you’ve got a bunch of dumb stations out there. Something goes wrong, you’ve got to get on the walkie talkie. There’s a latency in detection and action. What we’re finding as we talk to venues, is they want to have everything connected, fast.”
Riker imagines a future when these machines will replace metal detectors as the weapons detection standard. He says, “The breadth of this capability enables us to be able to do something that metal detectors are limited in…The threats are evolving beyond metallic threats, plastic handguns, for example, explosives, those are things that are going to require a different detection capability.”
The system is already garnering interest from large sports venues, as

the firm is scheduled to enter beta testing with Rogers Arena, home of the Vancouver Canucks, in 2020, and the home of one of Europe’s most storied soccer franchises, FC Bayern Munich, shortly after.
In addition to keeping weapons and contraband out, controlling where people can go once they’re in a stadium needs to be paid careful attention, especially ensuring that athletes and musicians have unfettered access to their private spaces and the general public is kept out.
Fesyk says at Commonwealth, “we do have a card system that we utilize for the majority of the doors in the building. You need to have either a team provided pass or a city provided pass, to get access to certain areas…. All of our stadium passes all have privileges and zones, as well as a photo and a name for the individual and who they work with.” He continues, “Depending on who you are and where you need to get to will determine which areas of the stadium you’re going to get access to and when, because things do change from our regular day-to-day to our event operations when we have a football game or a large concert.”
MLSE has moved away from cards, since at their properties, biometric readers have been used for about a decade. Kempcke says for busy athletes who need quick access to multiple areas of the facilities, the bio-readers make more sense than proxy cards. He says, “Now players just scan their finger and they get in to access their locker room or wherever their destination,” explaining further that eliminating the need for proxy cards eliminates the scenario where a player will forget their card and leave a door propped open. “We never want to see doors propped.”
For Kempcke, leveraging technology is a huge help to his operations, but keeping up with changing trends can be a challenge. “You think you put in the new system, the latest and greatest with all the bells and whistles and two months later there’s something brand new on the market and its ‘Oh, I want that new toy.’” He continues, “We go to technology trade shows every year to stay current and see what’s out there, look at what’s an investment that makes sense.”
MLSE is just about to start a three-year plan to upgrade its CCTV, security operations centre and analytics program.
However, Kempcke cautions that technology is only as good as the people using it. He says, “You can have an X-ray machine, and if staff don’t know what they’re looking for or how to use the machine, then the machine is as good as it being off.” He says the key is “educating staff, so they know the maximum use of that technology and how they can benefit from it and create a safe environment for all attending.”
For G4S’s Simpson, when a venue is putting a security program together, “you’re integrating communications, you’re integrating technology, you’re integrating access control, and you’re integrating the human element as well.”


Improvements in the technology increasingly make it a more viable option in the field
by Wayne Pak
Biometrics fuse convenience and security while validating “true identity” versus identity that is associated with possessing an ID card (or mobile credential on a smartphone), and offers numerous benefits to access control and other enterprise applications.
With the emergence of new anti-spoofing capabilities and its integration into secure platforms that protect privacy and support numerous credential technologies, biometric authentication is poised to deliver a much higher matching speed and better overall performance along with improved security and user convenience.
New developments
Development of the latest solutions has focused on the following key areas:
Improving image capture
The quality of the captured image is critical, across all types of fingerprints and environments. Many customers choose sensors that use multispectral imaging because it optimizes the quality of the captured image and illuminates the skin at different depths to collect information from inside the finger to augment available surface fingerprint data. Additionally, the multispectral sensors work for the broadest range of people with normal, wet, dry or damaged fingers, across the widest range conditions (from lotions or grease to sunlight, wet, cold conditions). The sensors also resist damage from harsh cleaning products and contamination from dirt and sunlight.
Liveness detection to enhance trust
An increasingly visible dimension of biometric performance in commercial applications, liveness detection is critical for preserving trust in the integrity of biometrics authentication.
At the same time, it must not impede performance or result in excessive false user rejections. The most trusted multispectral imaging fingerprint sensors with liveness detection provide a real-time determination that the biometric data captured by the fingerprint reader is genuine and being presented by the legitimate owner, rather than someone impersonating them.
This capability leverages the image-capture approach of using different colours or spectrum of light to measure the surface and subsurface data within a fingerprint.
In addition to this optical system, the biometrics sensor features sev-
eral core components including an embedded processor that analyzes the raw imaging data to ensure that the sample being imaged is a genuine human finger rather than an artificial or spoof material.
Advanced machine learning techniques can be used so the solution can adapt and respond to new threats and spoofs as they are identified. This is critical if biometrics are to eliminate the need to use PINs or passwords. It also protects privacy — if you can’t use a fake finger, then even if you did obtain someone’s fingerprint data, it is meaningless.
“Cryptography prevents any man-in-the-middle attacks while also protecting the biometric database.”
The top-performing solutions capture usable biometric data on the first attempt for every user and speed the liveness detection process. They quickly perform template matching to reject impostors and match legitimate users. They should be tested by skilled and independent third parties like the National Institute of Standards and Technology (NIST) for interoperability so that performance is based on data that can be trusted in all template-matching modes.
As an example, HID Global uses the top-ranked NIST certified MINEX III minutia algorithm to ensure interoperability with industry-standard fingerprint template databases. This interoperability ensures that today’s systems, which are based on much more powerful hardware than in the past, will perform accurate 1:N identification of a full database in less than a second.
Incorporating biometrics into access control systems requires a secure trust platform designed to meet the concerns of accessibility and data protection in a connected environment. The platform should leverage credential technology that employs encryption and a software-based infrastructure to secure identities on any form factor for trusted access to doors, IT networks and beyond.
Cryptography prevents any man-in-the-middle attacks while also protecting the biometric database. This system also should encompass remote management of all readers and users, spanning all onboarding as well as template loading and enrolment activities for supported authentication modes.
Tools should be available to allow system administrators to manage all configuration settings from time and data to language, security and synchronization. Additionally, the system should enable continuous live monitoring of authentication, alerts and system health. To simplify deployment, application programming interfaces (APIs) should be available for direct integration of biometrics authentication solutions with the access control infrastructure.
Biometrics data must be handled like all sensitive and identifying information, and properly architected system designs will always consider and protect against both internal and external threats and attacks.
New system architectures and data models have been created to protect personal information and maintain user privacy. Beyond the encryption of the data itself, there are now many good alternatives available for building highly secure and well protected systems, including the use of multi-factor and even multi-modal authentication to maintain security even if some identifying data is compromised.
Today’s fingerprint authentication solutions are on a fast track to deliver a unique combination of ease of use and higher security to access control systems. With their latest enhancements in liveness detection, system architectures and performance, they seamlessly combine security and convenience to make them a viable option for secure access to facilities, networks and services.
Wayne Pak is director of product marketing, physical access control, HID Global (www.hidglobal.com).

What is open and why is it important?
Open systems is a phrase you hear often in security, but the true meaning may depend on who you ask
By Kim Rahfaldt
any discussions have occurred in the security industry lately about open versus proprietary technology. End users prefer to install and operate systems they deem as open, versus installing systems that are viewed as proprietary (or closed). An open system provides more choices. End users can easily expand their security systems and integrate with complementary technologies necessary to secure their people, property and assets. But as I researched and talked with others in the industry, I realized that everyone has their own idea of what “open” really means.

According to TechTarget, “an open API, also known as a public API, is an application programming interface that allows the owner of a network-accessible service to give universal access to consumers of that service, such as developers.”
My company’s (AMAG Technology) definition of open is when a manufacturer develops software and hardware and makes the API available to any company who wishes to integrate with another company’s software or hardware.
A proprietary system is a closed system that only works with a manufacturer’s own hardware and software. Proprietary companies do not share their API.
Some manufacturers claim they are open as part of their business model, and they will stake their brand and reputation on being open. Other manufacturers are proprietary and sell based on the features and benefits within their own system.
Some manufacturers charge their technology partners for access to their API and then make them abandon their own hardware. How can a system be open if an organization must abandon its own products and solutions? Even if that hardware is commonly used by many companies, is that system truly open? Some would call that “pay to play,” which is another form of a proprietary system.
What about when a company has to pay a fee to integrate to an API? Is that considered open?
Several organizations have partner programs established to manage the large number of companies that want to integrate with their technology. A nominal fee is charged to offset the costs associated with testing and certifying the integration. A fee is acceptable if both companies benefit from the integration, and marketing and technical support are provided.
Ultimately, an open platform can integrate and operate with any software once the API is provided. This new way of doing business means that even the biggest competitors could become technology partners if the end user chooses to install a system that way. Imagine partnering with your biggest competitor!
Progressive companies understand the importance of delivering an open platform to the market. They uncover new ways to drive revenue and create happy customers. Making your own hardware and software allows you to control what success looks like. Being open allows for others to inter-operate and provides more choice for end users.
The Physical Security Interoperability Alliance (PSIA) introduced the Physical Logical Access Interoperability (PLAI) spec in 2013.
This is an example of how the industry is committing to the idea of providing open solutions. PSIA supports licence-free standards and specifications, which are vetted in an open and collaborative manner with the security industry as a whole under the direction of its board of directors. Companies committed to PLAI have de-
“Progressive companies understand the importance of delivering an open platform to the market.”
veloped adapters that provide a bridge that allows different physical access control systems to communicate with each other and share data. [Editor’s Note: AMAG Technology is a member of the PSIA and sells products that support ONVIF, including the Symmetry CompleteView VMS. For more on the PSIA, refer to the Q&A with executive director David Bunzel on p.19]

ONVIF is an open industry forum that provides and promotes standardized interfaces for effective interoperability of a wide range of IP-based physical security products.
ONVIF lets end users select optimal products from any manufacturer without locking them into one system. Developers use the interface to integrate products from different vendors. A company must be a member to claim ONVIF conformance, and products must comply with at least one ONVIF profile. Using ONVIF conformant products helps future-proof an organization’s investment in their security system.
Installing an open system makes it easy to integrate different technologies into a security program. For example, a hospital may want to add licence plate recognition (LPR) software to its access control and video system. If it’s an open system, the LPR software will integrate so the security operator can use it as part of the company’s existing infrastructure.
It also provides more options for end users. If a customer chooses one system, and decides a few years later to change out the software, or head-end, they can do so at minimum cost. They can keep their existing hardware — controllers, readers, etc. — and install new software. While this isn’t ideal for manufacturers, it offers a selling point at the time of the sale and puts the customer at ease knowing they
could change software and not have to do a complete rip and replace.
Do integrators benefit from selling open systems to their customers? Absolutely.
When an integrator sells an open system, they are providing more options to their end users. Not only can they “sell” the idea of open and all the options that are available when an open system is installed, but they can profit from that growth. They can upsell different technologies as the system evolves and as the end user grows its security program.
If the customer is not happy with one component of their system, it is easy to replace. They can sell them a new component rather than perform a complete rip and replace, which is upsetting and expensive for the customer. An open system provides versatility, which shines a positive light on the integrator who can help them more easily solve their challenges.
As stated earlier, the primary benefit for an end user to choose an open system is to have more technology choices available at their fingertips. Security systems normally start out small, or as budget allows. As time goes by and more budget is allocated, systems grow. More cameras and doors are added to a system and often integrations with additional technologies, as new needs are uncovered. For example, a data centre may start out with access control and video, but as budget allows, an integration with an intelligent audio system or identity management system may be needed. Starting off with an open system makes adding new technologies simple and easy.
If an end user installs a system and decides after a few years that they don’t like the technology they originally chose, they can easily change it out to a different technology. They can keep their panels, readers and other hardware, but install new access control software. This is more economical than doing a complete rip and replace of a system.
Progressive manufacturers understand the importance of being open and will drive standards throughout the industry. Not only does it drive revenue, it satisfies the customer. From the manufacturer’s perspective, owning the hardware and software means manufacturers can control product upgrades and what success looks like. They do not have to depend on when third parties decide to upgrade their products. Integrators can sell the concept and profit from technology add-ons. End users have more choices in technology and more freedom to swap out or upgrade if needed.
Kim Rahfaldt is the director of media relations for AMAG Technology (www.amag.com)

The Physical Security Interoperability Alliance (PSIA) officially turned 10 this year. Founded in 2008, and enshrined in 2009, it initially focused on establishing specifications that could address the surveillance industry along with interoperability that incorporated access control.
But by 2013, executive director David Bunzel determined that the PSIA’s efforts would best be served by focusing on the latter.
“In techspeak, I guess we did a little bit of a pivot. We focused on one of the things that we thought was the most promising and that we thought we could make a valuable contribution.”
Bunzel says the organization was reignited by this realization. PSIA board members include access power houses ASSA ABLOY and Allegion, along with a dozen other companies including vendors, integrators and end users.
SP&T News spoke with Bunzel recently about the move to access and how the organization’s PLAI specification (Physical Logical Access Interoperability) can help end users better manage disparate access control systems.
SP&T News: What were some of your initial steps with access control?
David Bunzel: With access control we actually started pursuing it as area control, which included access and intrusion.
We had some specifications that were written. We had a number of people in the industry who were very involved who were very effective and very good with that. About three years ago, one of the things that came out of our area control spec was the fact that there was a use case that [it] could address very well: the sharing of information between disparate PACS (physical access control systems).
By Neil Sutton
It was perceived as a fairly significant issue when companies were making acquisitions — they were acquiring other companies that had different PACS systems and they had a real mess trying to integrate systems and records and badges.
You’d see people with different badges and three or four different lanyards, going between facilities with different PACS systems, and buildings that have three or four different [card] readers in them to try to accommodate all the different PACS. We thought this was an interesting thing and we created the Physical Logical Access Interoperability (PLAI) spec.
We’ve gone through three years of enhancements and adoption. At ISC West this year we had a demonstration where we showed two PACS systems — Lenel and Software House — and three biometrics systems from IDEMIA, eyeLock and Princeton Identity all sharing information from one common, trusted source active directory. It all worked smoothly. There’s two components to it: there’s adapters that the vendors incorporate into their product and then an agent that is available from a couple of different sources that acts as the air traffic controller to transfer information.
SP&T: How is the PSIA currently organized?
DB: We have three different parts of the industry in our group. We have the vendors — typically PACS and biometrics, but we also have lock vendors like ASSA ABLOY and Allegion. We also have integrators. Convergint and Tech Systems are two of the most important ones involved. We also have some large customers who are advocating for us: Microsoft and Nokia. Between all these different parts, we’re able to have the industry represented in the discussion.
SP&T: To what extent is the evolution of technology like smart buildings and mobile access and cloud-based access control systems driving the PSIA?
DB: Those are all considerations. They’re all part of it. The spec can be used with all of them. With some of these things, we have to wait until the industry determines that these particular products are critical to their application.
SP&T: Is the PSIA directing most of its efforts towards PLAI?
DB: I would say most of our efforts are there. There are some opportunities we have in extensions to PLAI or things that are complementary to PLAI.
Obviously there are some things related to locking devices. They are being discussed and have been discussed over the years. We have extensions potentially into the elevator business because elevators are part of building management technology. They are also integrated into security, especially in multitenant buildings where you might see the building having one security system, but each floor, designated to a particular company, might have a separate system.
Trying to make all those work together — I guess you could call them extensions to what PLAI is doing.
SP&T: Is that where you’re headed — access control and identity management?
DB: Getting systems to support effective identity management is probably a general way to frame our focus.
SP&T: In terms of the goals of the organization, how far do you feel you’ve come and how close are you to achieving them?
DB: The organization has evolved. Whereas we initially had a pretty broad mandate to try to devel-


op standards to try to support the physical security industry, now we’re a lot more specific in terms of trying to support identity management as it relates to physical security. That crosses between logical and physical security.
In the discussion of PLAI, I guess we’re in some ways at a tipping point. We have some of the critical PACS vendors who are engaged.
SP&T: Is the goal also to have access control vendors make PLAI part of their product development lifecycle?
DB: Yes, they basically have to write a PLAI adapter. It’s fairly easy to do. Companies are doing it in four to six weeks. It’s not a very complicated process and even that is going to be shrunk down.
There are some independent parties that have done a number of PLAI implementations already. They’re able to do it even faster for a fairly modest cost, and once they have a PLAI adapter, they’re set. Then when the integrator or consultant specifies, they basically say, there’s an agent you can source from these companies, and as long as you have adapters in the system, you’re fine.
SP&T: What is the role of the integrator community in PLAI? You have Tech Systems and Convergint Technologies as board members. Are they helping you to evangelize this?
DB: They are our advocates out in the market.
Right now, we’re doing training for their sales teams. And also identify appropriate customers for PLAI, because not every company is an appropriate customer for PLAI.
We’re also working with their technical integration teams to help them understand what’s involved in putting together a PLAI implementation and how you support it.


By Neil Sutton
Security veteran Joe Grillo founded ACRE in 2012 as means to consolidate acquisitions in the electronic security industry.
He started with the software and controllers portfolio from Ingersoll Rand, creating Vanderbilt Industries, and more recent acquisitions include Open Options and RS2 Technologies. The company has focused on access control but not exclusively. SP&T News spoke to Grillo at the recent GSX conference in Chicago to learn more about ACRE and Grillo’s take on the market.
SP&T News: What led to the creation of ACRE?
Joe Grillo: We don’t use the full name [for ACRE] anymore — we haven’t in a while — but the concept was “access control and related enterprises.” That was what it originally stood for.
The highly fragmented access control landscape was what got us interested in the beginning to formulate ACRE as an entity. [We felt] like there might be an opportunity to do some consolidation of a lot of relatively small but really good properties in the industry.
In Europe, we acquired the Siemens security products business. That was a very large, restructuring and repair job. I moved there to do that myself. That’s done now and the business is doing quite well. It also has quite a significant intrusion and burglar alarm business as well.
About a year ago, we really started to focus on the U.S. market and did the two acquisitions of Open Options last December and RS2 in May of this year. It made us a much more balanced organization. Roughly half of our revenue comes from North America and the other half coming from Europe and the rest of the world —
Middle East, Asia-Pacific. So that brings us up to the current time and we’re continuing to look at other acquisitions.
But at the same time, we’re now endeavouring to do some integration of the businesses.
SP&T: Is there any overlap between product sets as a result of the acquisitions?
JG: There is some overlap in the products, but that’s OK. Over time, we will take a look at consolidating on the technology side. Having multiple brands that may compete from time to time, we’re quite OK with. There are regional strengths to the companies because of where they originated from. There are vertical market strengths because of the history of where they’ve had success. There are different channel partners who may be loyal to those brands. If sometimes there’s competition, we’re OK with that.
SP&T: How much has the cloud changed your business?
JG: It’s still a fairly small part of our business, but it’s growing. Again, that’s a situation where you have to find the right channel partners. Some of the traditional integrators — where you go in, you sell the system, you install the system, you get a maintenance contract and then you go away — they’re not set up necessarily to think through how to sell a cloud-based system, which is a different type of a sale. But that’s certainly a growing part of our business.
It’s a growing part of the industry, though still, I think, a fairly small part of it. But we view that it will accelerate.
We have sold hundreds of ACT365 cloud-based systems in the U.S., up till now under the Vanderbilt brand and going forward under a couple of our other brands. The system originated in
Europe where we began.
We also have a cloud-based intrusion installer tool in Europe for our intrusion business whereby the installers — and some of them are very large companies like Stanley or Securitas, and some smaller companies — can access their clients’ intrusion alarm systems to do system changes, management changes, without having to go on site. [The cloud-based tool is SPC Connect], which is a growing part of our business.
SP&T: As someone who’s worked in Europe and North America, how do those markets compare?
JG: There’s a lot of similarities in terms of the technology… the same types of channel partners, although the access control market can be very different in a country like Germany, where there’s a lot more direct selling to the end user. And there’s not a very developed wholesale distribution market. Whereas other parts of Europe, like the Nordic region or the U.K., have very well established wholesale distribution channels.
At a higher level, I think the macro economic environment is much tougher in Europe than it is in the U.S. right now, for all the reasons you read about in the press, whether it’s Brexit, slow growth or low growth. We hear that our competitors probably have less robust growth of the business in Europe than in North America at the moment, but I think that’s more of a macro economic influence than anything else.
SP&T: What about mobile access?
JG: We certainly hear a lot about mobile credentials. That being said, the actual demand from end users, at least in most of our verticals that we serve, is still relatively small. We are looking at various partnerships. Different ones on

“The channel, to me, is so important.”
perhaps both sides of the Atlantic because you have some very good companies and technologies that are out there that we’ll maybe try to partner with rather than try to build it ourselves. As long as we have good working relationships with the folks that are offering that technology, we’ll be able to react to our end users’ demands and reseller demands from our partners.
SP&T: What have you learned in the seven years since you founded ACRE?
JG: Some parts of the industry are the same. There’s consolidation, but there’s always new players. The channel, to me, is so important. And channel partners change. While you have the Convergints of the world, who get bigger and bigger, you always have very good, local, small, loyal resellers that you do business with. Certainly there are movements in the technology and in some of the verticals where we’re focusing a lot of our time.
Higher education and K-12 are probably the two biggest verticals where we see a lot of growth. [Also] growth in the medical industry. The impact of wireless locks and the lock companies [are] becoming so much better at the electronic side of the business. Even though they’re still relatively small, biometrics, mobile access and cloud. Those are the things we need to pay attention to. Those are the trends. That being said, this is still a fairly traditional business with a very sticky end-user customer base. People tend to keep with their suppliers and their systems for a long time. That works with you and for you, and it works against you when you’re trying to win new business.

It’s all about the partnership. Our number one goal is to make your life easier and provide the solutions you need to operate efficiently, reduce costs and meet compliance requirements, which is central to what makes Symmetry CompleteView 20/20 the leader in deployment efficiency and access control scalability. In addition to solving all of these challenges and more, AMAG’s first priority is to become your number one trusted advisor. As your true partner, together we can establish strategies to use your data to identify risks, streamline business, automate processes and reduce costs.

Supra has introduced additions to its TRAC-Mini controller to enhance lock management in offline locations ranging from remote outdoor telecom sites to indoor office file drawers. The new configurations of the TRAC-Mini controller extend the capabilities of the Supra TRACcess system, which uses mobile credentials and Bluetooth technology. The system includes TRACcess Manager cloud-based administration, which sends access permissions to the TRACcess eKEY app on a user’s Apple or Android device. System operators can monitor access activity online or via email alerts, or generate routine reports. www.suprasystems.com

Visitor Pass Solutions has launched a Kiosk version of its visitor management software, eVisitorPass. The touchscreen application enables visitors to check themselves into an organization’s building and then pick up their badges from an administrator at the front desk. The eVisitorPass Kiosk comes in two models: Floor-Standing and Tabletop. Both versions include a one-year software subscription, a driver’s licence reader, a Zebra direct thermal printer, and a supply of “one day” expiring visitor badges, which change colour overnight to show they are void and can’t be reused. www.visitorpasssolutions.com
Symphony Access Control is an open software solution designed to support the industry’s most trusted brands of access control and intrusion hardware. Available as an extension to the Symphony Video Management Software (VMS), the module provides a full set of access control functions, including enrollment, scheduling, monitoring and reporting. www.senstar.com
Kinetic by Camden is an advanced 900 Mhz. “power harvesting” wireless system that uses the energy created by the operation of the switch to power the wireless transmitter. There are no batteries to maintain or replace and no hazardous waste entering landfill. It features an ultra-compact receiver (easily installed in automatic door operator cabinets), with field selectable momentary, delayed or latching relay operation. The system is compatible with all brands of automatic door operators and is suited for both indoor and outdoor. It delivers door activation in any commercial, industrial and institutional application. www.camdencontrols.com


Symmetry GUEST visitor management interactive touch screen kiosks automate all processes associated with the lifecycle of a visitor, streamlining the journey through the reception area, enforcing compliance and reducing operating costs. Users can eliminate paper logbooks and create an audit trail to manage visitors. Software and hardware come pre-installed. The Symmetry GUEST Kiosks come in three main designs (Countertop, Slim Wall Mount and Freestanding) and two colours (white or black) with custom branding options. Freestanding kiosks come with or without cabinet and printer. www.amag.com
Genetec
Genetec ClearID is a self-service physical identity and access management (PIAM) system that standardizes and enforces security policies. By automating access rights management, ClearID reduces bottlenecks. A self-service physical identity and access management system, ClearID enables employees to login to an online portal and make access requests directly to the supervisor. Employees control their own access requests which ClearID automatically approves, denies, or routes to an operator to review.

LenelS2’s BlueDiamond mobile readers now support iCLASS card technologies. BlueDiamond has also been enhanced to include a Phone as a Badge (PhaaB) feature, enabling hands-free access. LenelS2, in collaboration with 3millID and with LEGIC Identsystems, has enhanced the reach of BlueDiamond multi-factor readers with additional support for iCLASS card application data. The readers now support virtually all major card technologies, from standard 125kHz proximity card technologies to MIFARE, DESFire EV1 and EV2 and now iCLASS card technologies, as well as mobile credentials. www.lenel.com

www.genetec.com/clearid
The uniVerse Series single-door controllers are now available in a surface-mount version, model CICP2100S. Suited for cinder block walls and other hard-to-wire surfaces, and used in a CA4K enterprise access control software environment, the CICP2100S Power Over Ethernet Controller, with locking metal enclosure, supports two ID readers and/or one low current strike via power over Ethernet (POE). CICP2100S’s 22-gauge CRS steel locking enclosure (9.18W x 5.4H x 2.1D”) includes 5 diagnostic ethernet LEDs, plus a power indicator. www.cicaccess.com

The new IX Series 2 Peer-to-Peer Video Intercoms offer Session Initiation Protocol (SIP) compatibility, enhanced CCTV control, line supervision, backwards compatibility with the original IX Series and many more features. End users can create efficient security operation centres using the IX Series 2 system as a single command point to control a variety of security layers. The IX Series 2 can page across multiple stations and scan through video intercoms and CCTV cameras to monitor locations.
www.aiphone.com

The Securitron M680E Series Magnalock with EcoMag technology has an increased holding strength of 1,200 lbs and is eco-friendly, with an average power draw as low as 60mA at 24V, allowing for use of smaller backup batteries and longer wire runs of thinner wire. This change in power represents a total reduced energy consumption of up to 80 percent over the previous Securitron M680 series. A new strike plate mounting template ensures strike alignment upon installation. This series has optional, integrated features such as passive infrared motion detector, Securitron BondSTAT bond sensor, Door Position Switch and door prop sensing. www.assaabloyesh.com/eco
The Crescendo Mobile smart card utilizes digital certificates on users’ mobile devices for client authentication. Crescendo Mobile works similarly to, and is compatible with Crescendo smart cards; however, rather than inserting a separate device into a contact smart card reader, it connects to a desktop computer via an NFC (near-field communication) reader or Bluetooth.
www.hidglobal.com
SVN-Flex is a new feature that enables SALTO standalone electronic locks and cylinders to update user credentials directly at the door. Based on SALTO’s BLUEnet wireless technology, SVN core technology and in combination with the trusted access control management platform and XS4 electronic locking solutions, SVN-Flex increases the number of updating points directly to any door. SVN-Flex functionality can be enabled on any product in the SALTO XS4 BLUEnet enabled electronic lock range.

www.svn-flex.com

The Conekt mobile smart phone access control identification solution now integrates advantages that Apple iOS 12 delivers, such as 3-D touch, Widget and Auto-Unlock, into the Conekt Wallet App, version 1.1.0. The Widget lets the user make up to three mobile access control credentials as widgets. This allows quicker access to credentials supporting divergent building systems such as payroll, parking and cafeteria systems, directly from the smartphone’s home screen. www.farpointedata.com
As part of S&G’s Digital Platform, NexusIP is a fully scalable solution that allows for real-time, remote monitoring and control of one lock or multilock location network for a more reliable IP safe lock. Utilizing Wi-Fi networks that are already in place, NexusIP requires no additional components or drilling. The lock uses existing safe power connections, or its own external power source, to deliver consistent extended power. With the ability to assign up to four opening windows – per day, per schedule for up to 100 users through remote access control – NexusIP can be customized to fit a specific application.

Morse Watchmans
Morse Watchmans’ KeyWatcher
www.sargentandgreenleaf.com/nexusip


Touch key management system features a 7” touchscreen and patented SmartKey system with KeyAnywhere technology to make it simple to withdraw and return a key securely to any key cabine. AssetWatcher is a scalable RFID-enabled locker system. Suitable for mobile electronics and other valuable items, it can support more than 10,000 users on a single system and is configurable in three modes. AssetWatcher’s RFID technology allows the user to track who is removing or replacing an asset, as well as when and where in the system the asset has been taken from or placed. www.morsewatchmans.com

Morse Watchmans
KeyWatcher Fleet offers fleet managers a wide array of tools to maintain and optimize vehicle usage while reducing many operational costs. Managers can create user role-based “Pools”, or groups of vehicles, to automatically assign each vehicle accordingly. Flexible booking workflows enable customization to balance usage, ensure vehicle availability and more. A range of service features makes it possible to report problems and automatically initiate new or scheduled work on each vehicle.
www.morsewatchman.com