ACCESS CONTROL
A look into the products, technologies and solutions shaping the market






A look into the products, technologies and solutions shaping the market





We asked experts from across the security industry to offer advice, tips and opinions on successful customer service strategies
Tracy Larson, President and Co-Founder, WeSuite
What does it take to keep your clients and partners happy today?
In the security industry, technology is continually being re-evaluated and upgraded, while the importance of great customer service remains a constant. SP&T News reached out to a group of security professionals and asked them: What should security integrators, dealers and related industry professionals be thinking about this year to ensure customer satisfaction and great results?

Eliminate surprises! We’re still dealing with a lot of uncertainties in the market.
There are labour shortages, supply chain issues, and quickly rising prices. Everyone understands that. However, security integrators must still meet customers’ expectations. Those problems can’t become an excuse for inaccurate quotes and missed installation deadlines.
Security integrators must communicate with customers, upfront, the possible challenges a project may face and establish mutually agreed upon plans to address them.
For example, are they willing to substitute parts if availability becomes an issue? Would they prefer partial project delivery even though labour will cost more? Is there an absolute deadline by which the system must be installed? The integrator must understand where there is room for flexibility and where there isn’t. Then, they must quote in a way that takes all of these considerations into account. Sales software can help. It makes it much easier to quote various options, add contingency pricing, and generate comprehensive proposals with current terms
and conditions, substitution clauses, and pricing expiration dates.
Highly detailed quotes benefit everyone. The client understands exactly what to expect, while accounting and operations have clear guidelines for proceeding. Ultimately, the only surprises should be good ones, like the project delivered ahead of schedule and under budget!

Dealers/integrators need to continue to stay up to speed to make sure they are offering their customers the right solutions. Consumers expect ease of use, aesthetically pleasing devices — and both while offering technology that reduces false alarms. For example, the advancements in visual verification combined with ease of deployment have made it easy to offer technology that significantly reduces false alarms.
Within seconds, both the end user and central station can have multiple snapshots of what caused the sensor to go into alarm, helping to decide what action should take place. In addition, you can quickly have visual verification of smoke during a fire alarm and can share with the applicable parties. I strongly recommend you stay close to your industry associations, central stations, distributors and manufacturing partners to ensure you are armed with the latest information.

From an end-user perspective, perhaps the most important consideration is the ability to solve a problem the client is encountering in new and innovative ways. Physical security measures play a crucial role in ensuring the safety and security of users in various settings, including homes, offices and public places. Over the years, there has been a shift in the way physical security is approached, and it has a significant impact on user experience.
The key drivers we are seeing post-pandemic are the decline of resources, both financial as well as available workforce. The possible solution is the integration of physical security measures with technology. This integration allows for real-time monitoring, remote access control and automated
“The human element of the channel, from the manufacturer to the customer, is fundamental.”
alerts in the case of security breaches. However, this integration also raises concerns about cyber threats and data privacy.
The ability to track an individual’s (or group’s) current and historic movement, behaviour and activity has the potential to greatly improve security, but it also raises new security and privacy concerns that must be addressed.
With the ever-changing legislative decisions related to privacy as well as the exponential growth of potentially invasive technology, the ability to walk the fine line between the protection of assets while staying attentive to solutions that may simply not be palatable to the public, will be a significant value add to consumers and the public at large.

In 2023, we expect to see a lot of old trends continue to evolve plus some new trends become more predominant.
Of course cloud storage and AI are expected to continue to produce novel ways to manage security. Cloud storage will move processes off site, reducing on-site IT and hardware requirements. AI will move some of the mundane tasks from humans to machines freeing up human resources.
Some existing trends expected to continue to grow and evolve is the use of mobile credentials. Using both mobile devices like smartphones and smart watches are offering new ways to provide identity verification to security systems without issuing physical cards or other traditional RIF devices.
Another existing technology that is expected to continue to grow is biometric verification. Biometric verification has evolved from simply hand or face geometries to AI-driven analysis of facial patterns, gait and other forms of biometrics that do not require touch. AI systems are trained on how to recognize various forms of identity falsifications and biometrics through cameras can move verification from being just a one-time authentication as you enter a building to continuous verification as you move through any camera view.
— David Sime, PaladinTechnologies
Wireless technologies is another expected trend. As 5G ramps up with improved security protocols it is expected to see a wider use of 5G enable IoT devices used to further augment security systems in ways that might be very different and exciting.

Fundamentally, our industry protects assets. However, it is built on relationships. Who knows who, and who do I trust? What technology solves my business problems and who has used it successfully before? The human element of the channel, from the manufacturer to the customer, is fundamental. As anyone that has participated in this industry knows, there is also rigor in most procurement processes. Sometimes the rigor is valid due diligence, and sometimes it’s checking boxes. AI like ChatGPT will disrupt this interaction this year. When a buyer is asking you to “describe” a process, or a quality program, or even your delivery plan, a marginally passable response can be churned out by these tools in a few keystrokes. I don’t condone using these tools, but they will be used. If you’re going to use AI to support your technical writing, use it as a tool and don’t depend on it. Use AI to inspire content, not to create it. Don’t be the first of many to get caught doing so.
Strategies for direct marketing and cold call emails will also change. Especially for sales that exist in the “long tale of the market” (high volume, low value). As an end user, how do you distinguish interactions from an AI script? Our industry will be encouraged to leverage and enforce more reliance back to our roots, real human interaction. I encourage end users to be mindful of the content that is being pushed out to you on the daily. Read and interact with intention. When Bob sends you an email and it doesn’t sound like Bob sent it, Bob’s reputation is ruined. We remain a relationship-based industry that leverages technology to solve complex problems, let’s not forget the humanity in it all.

While other access control solutions may address one area of your building’s needs, ASSA ABLOY offers a holistic approach with our range of Intelligent Openings solutions. From perimeter to interior, these state-of-the-art solutions efficiently integrate into your day-to-day operations while improving overall security.
Access control goes beyond technology. An intelligent Opening not only secures the people or assets behind the opening, but can also increase efficiency and productivity, improve the user experience, and provide valuable data and insight.
Migrating to higher security credentials and mobile access
Credential technology is continuously evolving to ensure the highest level of security – an important reason to build an access control infrastructure with resiliency and future-proofing in mind. This evolution is an essential consideration as facilities evaluate their options for electronic access control (EAC) locks and readers.
Planning should include a migration path that allows for a seamless transition from legacy credentials to higher security card formats, mobile credentials, and other emerging technologies. ASSA ABLOY Group brands offer a broad range of locking solutions that support the latest credentials, including mobile.
Wireless Technology Platforms
Intelligent WiFi Locking Solutions
ASSA ABLOY Intelligent WiFi locks and exit devices provide complete access control in locations where it would be difficult or cost-prohibitive to install a wired lock. They use standard IEEE 802.11b/g/n WiFi connectivity and AES 128-bit encryption to connect to the access control system, significantly reducing installation costs and eliminating the need for proprietary equipment.
Aperio Wireless Lock Technology
Aperio is a global wireless platform that allows you to expand your access control footprint – quickly, easily and affordably – using existing platforms
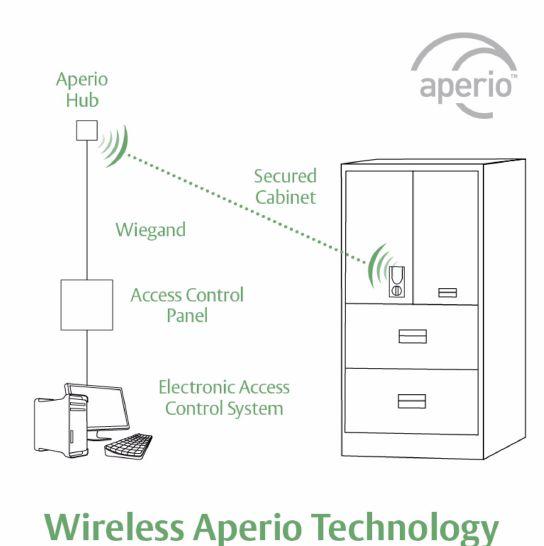
that you trust. Available across a broad range of locking hardware from ASSA ABLOY Group brands, Aperio provides the flexibility to address a variety of applications through any facility.
Mobile Access
Mobile technology is at the forefront of people’s lives. Everyday mobile devices provide new ways to interact with our environment, communication with others, and simplify transactions all while increasing conve-

nience and security. For ASSA ABLOY, mobile access means the ability to gain entry to a complete array of secured doors, gates, networks and services at your facility. Mobile solutions allow institutions to meet growing demands for mobile-first design.


The two leading technology protocols supporting wireless communications are NFC and BLE. Users can now use their mobile device with Apple Wallet using just iPhone and Apple Watch, or HID Mobile Access and LenelS2 BlueDiamond™.”
ASSA ABLOY offers a range of locks that can support multiple credential technologies at once, allowing for a seamless transition from lower security credentials to higher security card formats and mobile credentials.
ASSA ABLOY Integrated Wired locks and strikes combine all standard access control components into a single device. This approach significantly reduces installation time and creates a streamlined aesthetic that blends flawlessly into any environment. Our offering provides the latest in security and versatility with a choice of Weigand communication protocol or Open Supervised Device Protocol [OSDP] that allow for secure channel, serial communication between the reader and the Physical Access Control System [PACS]. These products make it easy to incorporate doors and hardware into the existing access control systems, because the open architecture platform is compatible with all popular access control systems.
ASSA ABLOY PoE solutions take advantage of existing Local Area Network [LAN] for both power and data, eliminating the need for additional power supply or electrical wiring. Utilizing existing infrastructure streamlines that installation process, reduces costs and enables real-time communication. These solutions can secure a single building through to complete facilities.

IDN-Canada prides itself in working with the best-in-class brands. Securitron by ASSA ABLOY is no exception. The AQ series of power supplies allows for the utmost in protection, efficiency, and adaptability, regardless of your requirements.
Securitron AQL Series power supplies harness the reliability of ASSA ABLOY and the technology of LifeSafety Power® The Securitron AQL Series of switching power supplies is an out-of-the-box solution that offers unique performance and value. It is featurerich, network management ready and available in 12 or 24 VDC single, dual and multi-voltage units.
Protect and enhance the performance of access control devices and systems with Securitron AQD & AQS Power Supplies.
With a wide range of power supplies, Securitron has the right power solution to protect and enhance the performance of access control devices. Mix & Match UL Listing • Available in one to 16 Amp variants to support the smallest single door systems to the largest
enterprise access control systems • UL listed dynamic field configurable product offering • Combine any of the seven power supplies and nine distribution boards in any UL listed enclosure and maintain UL code compliance Protection & Efficiency • Heavily filtered and regulated output provides better-than-linear performance • Up to 93% efficiency, which results in decreased operating costs and lengthens the lifespan of electronics • Low battery cutoff protects readers and other sensitive components from undervoltage.
Mix & Match UL Listing • Available in one to 16 Amp variants to support the smallest single door systems to the largest enterprise access control systems • UL listed dynamic field configurable product offering • Combine any of the seven power supplies and nine distribution boards in any UL listed enclosure and maintain UL code compliance Protection & Efficiency • Heavily filtered and regulated output provides better-than-linear performance • Up to 93% efficiency, which results in decreased operating costs and lengthens the lifespan of electronics • Low battery cutoff protects readers and other sensitive components from undervoltage.
Specifications Certifications (Both) • UL294 Listed • UL603 Listed • ULC-S318 Listed • ULC-S533 Listed • RoHS Compliant • REACH Compliant • CE Compliant
Features • All combinations of AQ power supplies and distribution boards are UL Listed • Tolerates brownout or over-voltage input ± 15% of nominal voltage • Thermal shutdown protection with auto restart • Circuit breaker protects against over-current and reverse battery faults • Dedicated battery charging circuit* prevents overvoltage on locking devices • Expandable up to 16 outputs in the standard enclosure • Available with a single relay fire trigger or individually triggered relayed outputs • Low battery cutoff at 9V
Electrical • 115 or 230 VAC input (except AQD1) • Supports up to two (2) sealed gel, AGM or wet lead acid batteries • Up to 93% efficiency • Low noise design with ripple as low as 70mV p-p • Outputs are Class 2 limited when used with PTC polyswitch distribution boards • Dual voltage 12 or 24 VDC field selectable continuous output • Single voltage 12 or 24 VDC continuous output.
Warranty The AQS is covered by the MagnaCare® lifetime replacement no fault warranty. No registration is required. Product will be replaced forever, for any reason, including but not limited to in-
stallation error, vandalism, or act of God. Replacement product is shipped at Securitron’s expense next day air, if needed.
Please contact your local branch for more information on this and many other new products available through IDN-Canada.

• AQL Product Overview link: Click here
• AQD & AQS Product overview link: Click here
THE KEY TO MULTIFAMILY ACCESS CONTROL: CONSISTENT RESIDENT EXPERIENCES
Over the last five years, the multifamily industry has been adapting to an increasingly digital world. Multifamily proptech solutions, including modern access control, have made massive advances. Prior to COVID, adoption rates for new technologies that entered the multifamily market were often slowed by budget concerns and a lack of interoperability with other systems.
Today, smart buildings are commonplace, but an adoption gap has occurred in many multifamily communities. Adoption gaps occur when a property introduces a solution to solve a specific problem (e.g. main entrance access) but that solution is limited in its capabilities or is not implemented across the entire property.
Over time, these one-off solutions add up to a hodgepodge of apps, keys, devices, or credentials. Without in-house capabilities to plan, implement and manage systems integrations, property owners and managers often face significant hurdles. The challenges created by the adoption gap often impede the property from providing a seamless user experience at a time when resident expectations are higher than ever and evolving quickly.

Consider this scenario—Taylor, a discerning tenant, resides in an upscale downtown apartment. When she was choosing her apartment, security was a paramount consideration, and this building seemed to have it all. However, her daily reality is far from simple. To gain entrance, she must open a dedicated app, sign in, and swipe her screen to activate the main entry video intercom system. Once inside the building, she has to switch to a different app, activate digital keys, and tap her device to various readers as she moves through common areas, boards elevators, or accesses various amenities. Finally, to unlock her apartment door, she has a PIN pad.
Swipe. Tap. Pin. This cocktail of disparate systems leads to an inconvenient and inconsistent user experience, falling short of the seamless and smooth experience renters expect and deserve in our modern digital era.
Multifamily access control can become even more complicated when we look at mixing physical credentials with digital credentials. It can be a difficult challenge, if not impossible, for property managers to have the same keyfob work across different systems within the tech stack including video entry systems, interior access control, and unit smart locks.
I believe there is a better way to think about and plan for access control in multifamily, and it’s surprisingly simple—put the resident first.
If you shift the focus to streamlining and improving the resident experience, you will open new doors to tenant satisfaction and

retention. The simple truth is that easy-touse, convenient, and most of all, consistent resident experiences are essential to delivering on the promise of smart communities.
To achieve this, property developers should opt for open access control platforms that allow property managers to tailor resident experiences based on the unique needs of their local tenants. The key here is to ensure that a single credential can unlock all doors within the property, including access to common areas, amenities, gates, garages, elevators, rentable spaces, and individual units. This credential should be versatile enough to be a keyfob, keycard, BLUEtooth digital key, a NFC-based credential in their phone’s wallet application or even a simple PIN code.
A consistent user experience not only elevates resident satisfaction but also simplifies building management, ultimately creating efficiencies that reduce operating costs creating a win-win situation for all. The path to higher tenant satisfaction and retention lies in streamlining and personalizing the resident experience, and I believe that modern access control holds the key.
Preston Grutzmacher, Industry Solutions Leader – Multifamily & Residential, SALTO Systems








By Francisco Alcala, North American Sales Manager, Farpointe Data
As a manufacturer of RFID readers and credentials, Farpointe often gets calls similar to the following:
End-user: “Hi, I’m John Doe with XYZ Company. We need to reorder access control cards. The cards and readers we use have the Farpointe logo on them. How can I order more cards?”
Farpointe: “John, those cards are available from the security integrator that installed your system. Give them a call and they can take care of you.”
End-user: “Um…I don’t know who that is…can I buy the cards directly from you?”
In many cases, the person tasked with reordering cards has no idea who to call, and just saw “Farpointe” on the cards. While Farpointe does not sell directly to end-users, the integrator that installed the system still missed an opportunity to make life easier for the customer. Private-labeling readers and credentials—as well as panels, cameras, and other devices—can help an integrator grow their business. Printing a logo, phone number and web address on access control cards, for example, promotes the integrator and makes it easier for customers to know who to contact for every reorder.
In addition to private-labeling, here are some additional suggestions for improving the effectiveness of your marketing efforts.
Low brand awareness or insufficient leads could be attributed to a brand lacking differentiation. Marketing effectiveness will suffer if a company doesn’t attract enough attention to invite engagement with its target audience. It is imperative for brands to stand out in today’s crowded, competitive environment and leading brands do that by presenting a distinctive image in the marketplace.
While it takes time—and consistency, which we’ll touch on later—to build brand recognition, it begins by creating a unique identity that separates a business from its competitors.
Having a unique brand identity is a valuable asset when it comes to acquiring a prospect, but maintaining the interest level of that prospect is vital to earning a purchase order.
Strong brands work hard to generate interest among prospective customers by crafting communications that resonate with their target audience.

Upon seeing any form of marketing communication, the first thing a prospective customer will think is, “Okay, but what’s in it for me?” Marketing that answers that question, will generate interest. Companies can discover the answer to that question by asking and answering a few of their own:
• Who specifically do we help?
• In what ways do we help?
• What problems do we solve?
• What needs do we fulfill?
Marketing messages that go beyond product features to address the audience’s needs, will resonate with more customers and inspire more action.
Distinction and relevance will only go as far as consistency will take them. Once a unique image and targeted messaging is established, systems should be put in place to maintain consistency throughout all marketing efforts. That is not to suggest that a brand remain static. As businesses adjust to changing market conditions and customer expectations, marketing communications may also need to adapt. However, if addressing customers’ needs remains at the forefront, audiences will be more receptive to changes.
Over time, consistency builds trust and helps create lasting relationships— the hallmark of a thriving business.
The principles described here work across marketing channels, traditional and digital. Integrators should think beyond business cards and websites, and examine vehicles, apparel, the products they install, social media accounts, and more. Everywhere a brand is represented is an opportunity to make a meaningful connection.
Private-labeling the RFID readers and credentials you offer can help grow your business. Your logo and contact details promote your brand and make it easy for customers to contact you for every reorder.
Branding options available through Farpointe:
. Durable, UV-resistant, full-color labels for readers . Scratch- and fade-resistant laser etching for physical cards and tags
. Full-color digital branding for mobile credentials








We’ve been hearing about mobile access for years, but has it finally reached its tipping point? Maybe not quite yet, but it’s fast approaching.
Mobile devices have become essential components of people’s daily lives, not just for their intrinsic features but also for the invaluable, convenient benefits they provide. And because people nearly always have their devices with them, using them to access places and move around different parts of the building makes sense.
What’s more, the growing popularity of trusted ecosystems of cloudconnected access control devices, applications and mobile identities has made mobile access easier to adopt than ever. This has, in turn, enabled myriad new services to be securely accessed through mobile phones and other smart devices.
So, if using a mobile device as a credential to access doors, networks, services and more can significantly increase convenience, boost efficiency and maximize security, it’s no wonder that organizations around the world are increasingly adopting mobile access. 81% of respondents in HID’s 2023 State of Security and Identity study say they are offering a hybrid work model, with more companies delivering identity management “as a service” rather than via on-premises infrastructure this year.
Using a smartphone, tablet or smart watch to gain entry into buildings or restricted areas isn’t just convenient for the user, but building managers and security staff can also provision and revoke credentials over the air, further limiting physical contact and improving access control administration through a digital, cloud-based platform.
As a result, companies are increasingly using mobile devices as a mechanism for the authentication and identity verification of their employees and visitors. Mobile access eliminates reliance on physical cards and badges, supports multiple security protocols and adds layers of security on top of basic card encryption.
Another element of mobile access that is gaining recognition is the concept of multi-application, where a single product or solution can execute multiple things. This digital experience not only increases operational efficiency, but also helps reduce the number of plastic cards that users use and lose, which has a positive impact on sustainability and security. A great example is in the higher-education sector, where universities are taking a mobile-first approach in lieu of plastic cards by offering mobile IDs with the ability to open doors, check out library books, make cafeteria purchases and more.

In addition, the future generations of employees, such as the Gen Z, will drive demand for mobile access as they are relatively more environmentally conscious and more engaged with the issue of climate change than previous generations. Today, Gen Z’ers are the biggest users of mobile and related applications, and they will eventually be overtaken by Gen Alpha as the “super-users” of mobile.
As more organizations successfully deploy mobile access and new use cases arise, more people will experience the convenient benefits of the technology. Being able add an employee badge in a digital wallet, offer a secure and even more seamless experience to building users and tenants.
There’s also the sustainability perspective. Virtual credentials remove the need for plastic cards and spares the carbon footprint associated with their lifecycle. Additionally, when the access control system is integrated with the building management platform, it allows for the continuous adjustment of building resources based on occupancy.
The drive for more sustainable solutions is critical in all industries right now, including access control. Fortunately, recent advancements include the introduction of access cards made from sustainably-sourced bamboo, supporting an eco-friendlier value chain in areas where physical access cards are still required.
Want to learn more? Visit https://engage.hidglobal.com/open-more/


Open More with HID Mobile Access by using your smartphone or wearable as a credential to access doors, networks, services and more. From banking and finance, educational institutions, global corporate entities and more - we provide the solutions for a mobile-first world, giving you unrivaled convenience, enhanced security and privacy protection, and operational efficiency.