









Collaboration, business accumen, sharper cyberskills — what you need to succeed in today’s (and tomorrow’s) security environment

Canada’s only national not-for-profit security solutions provider.


Canadian Security reached out to security professionals across multiple sectors to ask their opinion on what their peers should focus on this year and in the future.


College and university security leaders in B.C., Saskatchewan and Ontario share best practices to keep students safe and aware.
By Will Mazgay
New regulations and industry collaborations bode well for the future of the UAS market in Canada.
By Mark Aruja

Stricter privacy legislation and the IT skills shortage are just two of the cybersecurity items that may cross your desk this year.
By Matt Tyrer and Don Foster

Sutton

A reminder of our data security obligations 24x365
’m sitting down to write this on January 28, International Data Privacy Day.
According to the Office of the Privacy Commissioner of Canada’s website, this day has been observed since 2008, to mark the 1981 signing of the first international treaty on privacy and data protection. Privacy Day is observed by Canada, as well as the U.S., Israel and most of Europe.
What privacy, particularly data privacy, means today is vastly different than what it meant almost 40 years ago. Notionally, not much has changed, but the technology that manages private information, as well as the sheer volume of data that people share about their lives (either by design or unwittingly) is completely different.
“Every business should be diligent... but attitude counts for a lot.”
This has led to the rise of new privacy data protections over time (PIPEDA in Canada and GDPR in Europe), as well as stiff penalties for businesses and organizations that do not meet their obligations.
What has also risen commensurately is the spectre of “the breach,” where data is stolen, intercepted, leaked or spied upon by someone not authorized to view it or share it. It’s a scary proposition. Gathering and storing data is a part of business but keeping it safe from malicious actors is no simple feat. In fact, it can seem almost impossible. It’s this line of thinking that has led to the generally held believe that sooner or later, everyone gets breached.
I had the privilege of interviewing former Privacy Commissioner of Canada Jennifer Stoddart recently (read the Q&A on p.21) and I asked her a question I’ve probably asked a dozen other people over the last 10 years: Should Canadian businesses view breaches as inevitable and if so, what should they do about it?
I’ve heard all kinds of responses to this question, but most people take it on faith that breaches are a strong likelihood and then posit some options that businesses can pursue. Stoddart, on the other hand, took exception to the word “inevitable,” and in doing so re-framed the way I look at breaches too. “I think that’s a really, really dangerous attitude to have,” she said.
Every Canadian business and organization should be diligent in preventing, preparing for, and responding to possible data breaches, but as Stoddart put it, “attitude counts for a lot.” Maybe it was my bias going into the interview. Maybe I’ve read too many reports citing the number of businesses that experience a breach, or the odds of experiencing one in the first place. But I doubt I’m the only one who has been swayed by this line of thinking. Yes, breaches are going to occur; yes, you should be ready. But I think Stoddart and other privacy warriors like her are the people who keep us vigilant and remind us of the duty to protect personal information. That’s really what should be inevitable when it comes to this discussion.


Group Publisher Paul Grossinger pgrossinger@annexbusinessmedia.com
Account Manager Adnan Khan akhan@annexbusinessmedia.com
Editor Neil Sutton nsutton@annexbusinessmedia.com
Associate Editor Will Mazgay wmazgay@annexbusinessmedia.com
Art Director Graham Jeffrey gjeffrey@annexbusinessmedia.com
Account Coordinator
Kim Rossiter
krossiter@annexbusinessmedia.com
Circulation Manager
Aashish Sharma asharma@annexbusinessmedia.com Tel: 416-442-5600 ext. 5206
President & CEO Mike Fredericks

Editorial and Sales Office
111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1
(416) 442-5600 • Fax (416) 442-2230 Web Site: www.canadiansecuritymag.com
Canadian Security is the key publication for professional security management in Canada, providing balanced editorial on issues relevant to end users across all industry sectors. Editorial content may, at times, be viewed as controversial but at all times serves to inform and educate readers on topics relevant to their individual and collective growth and interests.
Canadian Security is published four times per year by Annex Business Media. Publication Mail Agreement #40065710
Printed in Canada I.S.S.N. 0709-3403
Subscription Rates Canada: 1 Year $42.00 + HST; U.S.A. (payable in US dollars): 1
Circulation Anita Singh asingh@annexbusinessmedia.com Tel: 416-510-5189 Fax: 416-510-6875 or 416-442-2191 111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1
Annex Privacy Officer Privacy@annexbusinessmedia.com Tel: 800-668-2384
The contents of Canadian Security are copyright by ©2019 Annex Publishing & Printing Inc. and may not be reproduced in whole or part without written consent. Annex Business Media disclaims any warranty as to the accuracy, completeness or currency of the contents of this publication and disclaims all liability in respect of the results of any action taken or not






The transition from policing to private security can be challenging for lifelong police officers.
To that end, the Toronto chapter of ASIS International sought to demystify the world of corporate security for interested police officers, with a special event held recently in Brampton, Ont.
ASIS Toronto: Law Enforcement
Transition to Private Security, hosted at the Peel Regional Police Association on Jan. 10, featured a panel of security directors fielding questions on resume building, networking, interviewing, adapting to corporate culture and a variety of other issues.
Taking part were Carmela Demkiw, senior director, security services, Rogers Communications; Sherri Ireland, director, Security Exclusive; Chad Hanlon, national account manager, Xpera; and Harold Wax, senior director and chief security officer, BGIS.
One of the biggest challenges law enforcement professionals making this transition have is getting a foot in the door of a hyper competitive industry. Security Exclusive’s Ireland says to make inroads with an organization, officers may have to target a junior position then work their way up.
“It’s a bit of a tough pill to swallow when you’re in a senior role and have tons of experience and suddenly you have to take a junior role, but what I’ve known from the security companies is that it doesn’t take long for someone with really good skillsets who is dedicated and motivated to move up in the ranks of those companies,” she said.
The panel also said taking professional development courses, in areas relevant to private security, can give officers a leg up, as can honing and refreshing skills transferable to the private sector, and highlighting those skills on resumes.
Taking courses “shows that you’ve got ambition,” said Xpera’s Hanlon.
When it comes to resumes, changing the wording and format to suit a

corporate environment is a crucial step in the process.
“Take a look at your training, experience, skillsets in policing and tweak the language in your resume to make it more applicable to the corporate sector,” said Wax. He explained that policing language, potentially heavy with jargon, may not be understood by private sector hiring managers.
Beyond building a solid resume, everyone on the panel stressed the importance of networking, through private security organizations like ASIS, mentorship opportunities from security professionals and online through LinkedIn.
Ireland said she actively searches for candidates with specific skill sets on LinkedIn, and stressed the social network’s importance, while Demkiw cautioned that profiles need to be polished, concise and professional in both appearance and narrative. Wax said if someone hands him a polished resume but has a sloppy LinkedIn profile, it raises an alarm.
After building an attractive resume and landing an interview through a solid contact, making a good first impression is crucial.
Hanlon said, “When you walk into an interview, your first interview is with the receptionist. Treat them like a CEO… treat everybody like the CEO.”
“Be humble” said Wax. “If you’re coming in with a 30-year career in policing, that’s an amazing contribution, with your service to your community, and you’ve got a lot of experience to offer, but you’re entering into a space that is new territory for you. You may have been the ace within the police service, but you’re the new person applying for a job and there’s many other aces applying for it as well.”
The panel explained that the interview process is as much about finding the right fit for the firm’s culture as it is about finding someone qualified. Coming off as too authoritative, aggressive or arrogant can be a deal breaker.
Hanlon said, “Private sector is a different thing. You work very close…if you’re not fitting in with the team, it’s not pleasant.”
The issue of fit cuts both ways, as officers should be researching and asking questions about the company they are applying to, to determine if the culture aligns with their values.
The differences can be striking, said Wax, using the example of a company “where they let you come in in sandals and bring your dog to work. [If] you’re used to a very paramilitary lifestyle, you may not click in that environment, and you may be setting yourself up for failure.”
February 21, 2019
4th Annual Mission 500 Hockey Classic Toronto, Ont. www.sptnews.ca
March 7, 2019
Security Career Expo Toronto, Ont. www.securitycareerexpo.com
April 2-4, 2019
Canadian Technical Security Conference Cornwall, Ont. www.ctsc-canada.com
April 10-12, 2019 ISC West Las Vegas, Nev. www.iscwest.com
April 17, 2019
ASIS Toronto Chapter Best Practices Toronto, Ont. www.asistoronto.org
April 24, 2019
Security Canada East Laval, Que. www.securitycanadaexpo.com
May 8, 2019
Security Canada Ottawa Ottawa, Ont. www.securitycanadaexpo.com
May 19, 2019
IAHSS Annual Conference and Exhibition Orlando, Fla. www.iahss.org
May 29, 2019
Security Canada Alberta Edmonton, Alta. www.securitycanadaexpo.com
June 13, 2019
Security Summit Canada Toronto, Ont. www.securitysummitcanada.com
June 19, 2019
Security Canada West Richmond, B.C. www.securitycanadaexpo.com
September 11, 2019
Security Canada Atlantic Moncton, N.B. www.securitycanadaexpo.com
Christina Duffey recently became the 64th president of ASIS International. She is first woman to serve in the role since 2004 and the second Canadian. More precisely, Duffey is the third “international” president (i.e. not American) — a short, but growing, list that includes Canadian Dave Tyson (who served in 2015) and Eduard Emde, from the Netherlands (2012). Duffey will be succeeded in 2020 by Godfried Hendriks, also from the Netherlands.
“The time is right,” says Duffey of ASIS’s more recent global approach. “It’s exciting to be part of a board that mirrors our international membership.”
multiple years of going out to the different regions and realizing that, in order to be a global organization, there needs to be some sort of focus so that regionally you can meet the needs of that particular member,” adds Duffey. “One size doesn’t fit all.”

Duffey is originally from Kleinburg, Ont. (just north of Toronto) and now resides in Arizona. She has lived and worked in Toronto and Chicago, and has spent two periods of her life in Arizona — for three years in the early 2000s and again starting in 2015. She is currently senior vice-president and regional director of the Midwest Region for SOS Security, based in its Phoenix headquarters. Duffey has had a long association with ASIS, including serving as president of the organization’s Professional Certification Board, and is the recipient of the Ron Minion Security Pioneer Award, conferred annually by ASIS Canada.
The ASIS board approved a 20162020 strategic plan in early 2017, which includes a swath of potential changes to the organization. This document has evolved over the years and ASIS’s enhanced framework for 2020-2024 was approved by the board in January.
“We’ve already notionally approved the new governance structure with six regional boards overseen by a global governing board. We are in the process of working through the roles and responsibilites, distributing authority, and how it impacts chapters [and] councils,” explains Duffey.
“The whole global governance initiative that we’re taking on is really born out of
Another major focus for this year and beyond is ASIS’s latest professional certification, the Associate Protection Professional. ASIS has had considerable success with its CPP, PSP and PCI certifications, but the APP ultimately targets a different group: relative newcomers to professional security. CPP, for example, requires the applicant to have a minimum of seven years of work experience (nine without a degree) before taking a qualifying exam. APP cuts that time down to as little as one year (with a Master’s degree, or two with a Bachelor’s in security management), enabling younger professionals, or those who are new to security, to attain a recognized qualification faster.
“We identified that there was a need to have an entry-level certification, which is important for that vocational knowledge,” she says. “It was certainly something that our members were asking for. We’re a board and an association that listens to members and provides the value that they’re looking for.”
ASIS has also pursued other initiatives, such as ASIS Connects, an online community that allows ASIS members to share information and resources with each other. Duffey is confident that these and other changes will enable the organization to move with the times and provide more touchpoints for its members.
“Although I will be out front in this coming year, it’s not about me,” says Duffey of her tenure. “It’s really not about the one individual, it’s about what we’re building and what we’re preparing for the future. I’m excited about it. It’s going to be a fun year.”
— Neil Sutton
Canadian Security editor Neil Sutton addressed Mississauga City Council on Jan. 16 to highlight two of the magazine’s award programs: Security Director of the Year and the Community Leader Award. In 2018, both were awarded to Silvia Fraser, head of security for the City of Mississauga.
Fraser is the 13th recipient of Security Director of the Year and the first recipient of the Community Leader Award in its inaugural year.
During his presentation to council, Sutton described the traits that judges look for in a security director, including mentorship, project management, leadership and ingenuity. He also spoke of the community aspect of the security profession.
Fraser has demonstrated her capacity to give back to the industry by participating with security associations like ASIS International and the Canadian Security Association; motivating others through speaking engagements such as Canadian Security’s Security Career Expo; as well as raising funds for security education through her sponsored participation in recent marathons. Read more about the Community Leader Award and Security Director of the Year in the July/August and September/ October 2018 issues of Canadian Security.
























































Laval, Quebec
April 24, 2019
Richmond, British Columbia
June 19, 2019
Ottawa, Ontario
May 8, 2019
Moncton, New Brunswick
September 11, 2019
Edmonton, Alberta
May 29, 2019
Toronto, Ontario
October 23 – 24, 2019
Last December, Canadian Security hosted its annual Focus On Healthcare Security seminar, highlighting topics such as: marijuana in the workplace; the role of social media in mass notification; and handling mass casualty events like the Toronto van attack.
The event was attended by more than 100 professionals and was supported by the International Association for Healthcare Security & Safety (IAHSS), Dataminr, MNP, Paladin Security, Darktrace, ASSA ABLOY, Commissionaires, Securitas, Convergint Technologies, Fitch Security Integration, G4S Canada and Groove Identification Solutions.








• Security guards • Mobile patrol and alarm response • Event security • Executive protection
• Investigations and consulting
• Loss prevention
• Concierge services
• Travel security

This can be the year you take that big step towards ESRM
We’ve all made New Year’s resolutions.
Some are small, some are grandiose and others are just downright crazy! I took some time to work on a resolution for our profession — let me know what you think.
This year, we resolve to focus on the principles of Enterprise Security Risk Management (ESRM) in our every day approach to protecting the people, property and information of our organizations. We realize our goal is to understand the goals and objectives of our business, and then identify the assets that support these goals.
message is spreading beyond the original core group of pioneers and practitioners. And ASIS continues to bring forward programs and materials focused on the benefits of ESRM for security professionals and organizations at a global level.
“Gone are the days when security is seen as the ‘department of no.’”
When we talk to our business leaders and organization stakeholders about potential risks to these assets, we’ll make sure we listen to their concerns, document their points and opinions, and assess the risks facing the assets using a sound, repeatable process. Once we’ve had the opportunity to assess these risks, we will create mitigation strategies to reduce the risks as best we can, let the business determine the path to success, and document the risk decisions.
We’ll make sure we have a risk management program in place, develop incident response procedures for the organization, and ensure we create a closed loop by conducting post mortem reviews of incidents, and incorporating that feedback into our processes.
That’s quite the resolution! But it encompasses all we want from a risk-based approach to a security program. And 2019 is a year when we’re going to see progress toward this philosophy. I’m optimistic about this approach because I’ve seen the ESRM philosophy appear in a number of different places.
Security professionals I follow on Twitter, LinkedIn and Facebook are outlining projects and initiatives that describe the ESRM approach. I’m seeing conferences highlight ESRM topics and panel discussions that involve new speakers and risk professionals. That means the ESRM
At a local level, I’m seeing the benefits of a risk-based approach expand beyond a handful of companies. My current organization, along with a number of other local and national teams, have embraced and deployed a risk-based, businessfocused approach to security and are realizing the benefits of these programs. Gone are the days when security is seen as the “department of no.” We are now seen as advisors and business professionals who happen to run a security department.
One recent discussion really helped me understand how far we’ve come these past few years. During a project meeting with another team, we collectively began to assess a new initiative and started to look at the “why” of the project. One of the team members (not a security person) asked how the new project was linked back to the organization’s business objectives, and can we identify the risks?
The team member really wanted to know how the project was supporting the goals of the organization, but more importantly what risks could this new project address. That was a pretty amazing moment for me — the message my team has presented for quite some time was mirrored back in a project meeting by someone other than a security professional.
We’ve all made resolutions to try something new, push ourselves to achieve a difficult goal or focus on making a change in our lives. I think this year we can actually do it. I think this year we can change the direction of our profession and move toward the principles of ESRM. It starts today — with you.
Tim McCreight is the manager, corporate security (cyber) for The City of Calgary (www.calgary.ca).
By Kenrick Bagnall

Identify the person responsible for your data leak. Better yet, discourage that behaviour in the first place
There is a popular idiom that says, “better the devil you know than the devil you don’t.”
The problem with this, when it comes to insider threats, is that the devil you know also knows you. Sun Tzu, in the Art of War, said, “Begin by seizing something which your opponent holds dear; then he will be amenable to your will.” This is precisely what the insider attacker tries to do.
red flags should be raised when an employee exhibits emotional or aggressive behaviour that is out of the norm during the course of an interview, performance appraisal or their day-to-day job function.
“Insider threats are not born, they are made.”
This individual who becomes a threat to your organization has two major advantages over a potential external adversary: they have access, both physical and logical. They can get into your brick and mortar facilities and login with approved credentials.
Insider threats are not born, they are made. In the vast majority of cases, people are interviewed and hired into companies where they have every intention of working hard and doing a good job. So what goes wrong?
An employee may develop disgruntled feelings if they are passed over for promotion, if they did not receive the credit that perhaps they feel they deserve for some work they did. Also, an employee may feel that they are the victim of office politics or even workplace harassment or bullying.
When any of these and/or a number of other factors are taken in isolation, it may not become an issue. However, when several of these issues combine and we also factor in human vulnerabilities and our susceptibility to social engineering, you have all the hallmarks of possible insider threat to your organization. Early detection of changes in behaviours could indicate that a staff member may be responding to external stressors, and may have been negatively influenced by a social engineer trying to take advantage of them.
Detection is often the first step towards prevention, so what can organizations do? There are mainstream technologies that can monitor user activity when it comes to account logins and resource access.
For example, a 9 to 5 employee working in manufacturing would be flagged if they tried logging on at 3 a.m. and attempting to access resources belonging to R&D.
From a human resources perspective,
Ideally, when HR personnel work collaboratively with IT security with a view to share anomalous information about concerning individuals, this can produce the best results and potentially stop an insider threat in its tracks. Using software tools and having well trained HR personnel is a great start. From an information security perspective, what makes this work is good governance and strict adherence to established best practices. To that end, well established onboarding policies and procedures for new staff can go a long way in protecting your organization. Written and signed policies for the expected use and ownership of systems, data and work product is essential. The International Standards Organization (ISO) 27001 guidelines include recommendations for Privileged Access Management. This framework includes controls to help your organization better manage privileged access to the crown jewel digital assets of your organization.
As always, your strategic partner when it comes to dealing with criminal offences that result from insider threats is your local law enforcement agency. If there are immediate life safety issues do not hesitate and call 911 to engage all emergency services. In a nonemergency and controlled situations, call the non-emergency number for your local agency. For the Toronto Police Service, the number is 416-808-2222.
For organizations large and small in public, private and non-profit sectors, the most valuable assets are their people. Finding better ways to manage human resources and efficiently use technology can go a long way toward developing efficient teams and reducing the risk of possible insider threats. Be safe, everyone.
Kenrick Bagnall is a Detective Constable with the Toronto Police Service Computer Cybercrime Unit (C3) @KenrickBagnall.



We asked the experts what skills today’s (and tomorrow’s) security leaders need to enhance or acquire in order to best serve their customers, staff, C-suite and organizations.
Skills development is a vital component of any professional’s career and the skillset required of security professionals is expected to be broader every year. To kick off 2019, we asked chief security officers, as well as the consultants, trainers and suppliers they work with, to share their views on what those skills are (or should be). Respondents are allied with a variety of industries, from communications to municipal government to hospitality, as well as leading associations that are also setting the bar high for security education. The responses are, not surprisingly, diverse. Education, soft skills, cyber and physical security interaction, credentials and designations, communication skills, business skills, professionalism and ethics — are all components that describe great leaders in security.

TJames Armstrong Vice-president, Chief Security Officer, Shaw Communications Security Director of the Year 2017
he threat that cyber-attacks pose to businesses of all sizes has never been greater, and as we move into 2019, it’s increasingly important for security leaders and professionals to ensure they have a strong familiarity with cyber security.
Data breaches, malware and ransomware attacks are now just as prevalent as physical threats. This increase in cyber-crime requires that security leaders become holistic subject matter experts on all aspects of security. This means having a firm understanding of all facets of the business they support to better identify risks and develop effective, targeted security programs to protect their organizations.
It is also important for security leaders to educate and empower their employee base such that they can exercise strong security principles in their day-to-day work. Doing this requires that security leaders work hand-in-hand with the internal business leaders and departments they are supporting to develop programs to change employee behaviour for the better. These programs should provide real-life examples to help employees always understand what’s at stake for the business and teach employees to report threats and risks, and engage in safe security practices.

TKen Hoggart President, Universal Training Solutions
the technology and operators necessary to follow and deter the newer forms of crime? It goes way beyond learning new access control systems. Now security professionals need to be aware of new facial recognition software, cyber investigations, drones, smart systems and fully integrated buildings. With that said, there are many individuals in the public that we still need to interact with face-to-face, for a variety of reasons. We are seeing an increase in substance abuse and various mental health conditions in society that require our interaction. Our face-to-face interaction skills are also an extremely valuable asset when interviewing a variety of people, whether we are assessing job candidates or conducting interviews for investigative purposes. Can we balance the old and new? I like to believe that we can.
As leaders, it is important to develop the necessary skills to embrace new technology and welcome people who understand and can operate such technology. Leaders should impart the knowledge and skills of human interaction by mentoring people for career development and succession planning. As old as communication is, and mostly looked at as a legacy skill set, it is likely still the most important skill to utilize, train, and pass on.

Brine Hamilton Healthcare Security Specialist, GardaWorld
IAHSS
Ontario Chapter Chair, Board of Directors
“Due to the importance of personnel management, the CSO will require a high level of emotional intelligence and strong soft skills.”
Mechnology is developing at a rapid pace and being implemented just as quickly. There has been a major shift in loss prevention from shoplifting, to cyber and online fraud. Similar to other areas of society, criminals find it easier to avoid face-to-face interaction and find a way to hide behind keyboards and commit crimes. Can we embrace
ost professionals have experienced the pressure to increase efficiency — faced with growing expectations but met with declining resources available to them. CSOs will need a broad understanding of multiple disciplines to keep pace with these expectations as well as support operations or divisions with direct and indirect overlap of security operations. As technology continues to evolve, the CSO will need an understanding of these new technologies to implement them into their programs and protect the organization. The CSO will also require a strong business acumen to address responsibilities while relating to and collaborating with other C-level executives.

Results are an obvious requirement for a CSO, however an underappreciated yet related element of the CSO’s responsibilities is retention. Without some level of retention, sustainable results are negatively impacted, as is succession planning. Due to the importance of personnel management, the CSO will require a high level of emotional intelligence and strong soft skills. CSOs must also be astute to the innerworkings of their organization in order to navigate the potential challenges of working with multiple groups.

Sherri Ireland Director, Security Exclusive Vice-chair, Toronto chapter, ASIS International Instructor, PSI program, Fleming College
“Physical and cyber security are interwoven — CSOs and CIOs must speak the same language.”
While the basics of security haven’t changed, the complex environment introduced by new technologies (e.g. drones, artificial intelligence) and hosting security systems through IP-based communications requires every security professional to stay up-to-date with technology and evolving cyber security information. Physical and cyber security are interwoven — CSOs and CIOs must speak the same language. Subsequently, continuing education has become fundamental to security professionals.
Protection, Security and Investigation graduates learn the basics of security, then apply these skills in a practical environment, usually through placement programs. Graduates are equipped with the ability to obtain a security officer licence, and professional designations like the CHSO Certified Healthcare Security Officer as well as first aid and CPR certificates. Seneca College has recently introduced an Honours Bachelor of Crime and Intelligence Analysis degree. A college diploma has become the minimum benchmark with the degree program — a new bar will be set for folks entering the industry. No longer will years on the job ensure promotability.
Professional designations recognized globally are becoming the new benchmark. ASIS International designations are becoming a requirement for more senior roles. Other professional designations beneficial to the physical security realm are CSPM (Certified Security Project Manager),
PMP (Project Management Professional), CISSP (Certified Information Systems Security Professional) as well as IAHSS security health-care designations.
The complexity of the security landscape is a moving target. Security professionals must continue to invest in themselves and be willing to adapt and learn.

Janice Holmes Security, Health and Safety Manager, Friday Harbour Resorts
“All security professionals need to develop a personal code of ethics that governs the way they work and act.”
Security skills can be developed, however, core values, professionalism, ethics and integrity are what make you a leader in the private security industry. Employers want to work with people who have a strong work ethic. Ethical behaviour is doing the right thing when no one else is watching, and ultimately, what you believe to be morally true! This leads to overall professionalism and integrity. Integrity should permeate every aspect of your job. All security professionals need to develop a personal code of ethics that governs the way they work and act; this is above and beyond the Private Investigator Security Guard Act code of conduct. This personal code should filter through your day-to-day work, from how you deal with customers to the way you treat your co-workers and supervisors. It’s pivotal in maintaining integrity and ethics when it comes time to making decisions.
Training and an organization’s core values help security professionals follow their own code of ethics and that’s what makes them professionals in the industry. A quote that I have always followed during my career is, “Great leaders don’t set out to be a leader, they set out to make a difference. It’s never about the role, it’s about the goal.” I believe when you live by that, you remember that we’re all a part of the same team. To me, a leader is someone who coordinates the day to day, but it is the team who executes it and pulls it all together. Without core values, professionalism, ethics and integrity, you are never going to stand out as a leading edge professional. Remember to be loyal, dedicated and strive to raise the bar of excellence as everyone will gain from your attitude and your professionalism.

TPatrick Ogilvie
Security Advisor, Security Assessment Unit, Ontario Provincial Police
he evolving and advancing skillsets of future CSOs must not just include, but focus on being business enablers. It does not matter if a CSO works in the private or public sector, the requirement to best protect organizational assets must align with the enterprise’s responsibilities that are profit and market driven and/or in the public’s best interest of safety and financial integrity.
Being a business enabler will include all enterprise security risk management (ESRM) elements, plus the pivotal contribution to the business goals, which will include revenue generation, cost reductions and continued efficiencies.
What could be the largest obstacle is aligning those who have both a direct and primary responsibility for asset protection (i.e. CSO staff) and those with indirect responsibilities. It is vital to learn, foster and promote the cultural necessity to be risk adverse, where everyone is responsible for the prosperous, safe and secure functions of the organization.
A CSO who can drive an enterprise’s strategic vision through their tactical and operational abilities will be a valued, trusted and relied upon asset for any organization, for a long, long time.

SSilvia Fraser
Head of Security, City of Mississauga, Ont.
Security Director of the Year, Community Leader Award 2018
fundamentals of security management remain the building block regardless of whether it is physical security, cyber security or both. However I also believe that while security skills and knowledge might have got you there, they certainly will not keep you there.
What I found most useful for me, and I see this as the future mantra for CSOs, is: leadership, vision and strategy, together with business administration and development, with a focus on building partnerships and collaboration. There is a mix of skills, knowledge and experience that is very valuable to draw from in any of these areas that can then be complemented by specific knowledge and experience in other areas such as: real estate, property management, government, IT, and ultimately any other area that may be of interest or touches the organization or business you are in. This proves to be so important as we support the business areas within our own organizations.
In other words, if there are no assets (the business), there is nothing to protect. In many cases, the CSO is not the custodian of these assets; the CSO is primarily a service provider to the other business areas, therefore understanding them, collaborating and creating partnerships becomes very important.

Cecurity departments have evolved to become their own individual business units, with their own budgets and corporate identity. The role of the CSO has also had to evolve based on the growth of security organizations and the need for an enterprise approach that can cross traditional domains and encompass all security aspects of an organization. Relying on security-related skill, knowledge and experience alone does not satisfy the maturity of the CSO role. The
Mark Folmer Vice-president, security industry, Tracktik
Senior Regional Vice-President, Region 6 (Canada), ASIS International
SOs are going to need to speak the language of business and secure a spot within an organization. Increasingly, security operations are expected to show a return to the company and even demonstrate a profit. To produce the kind of well-oiled machine that can meet these business demands, the future CSO needs to know business skills and as a result, how to establish KPIs that increase their ROI.
To meet business objectives, the CSO will need access to tools that capture data and the ability to harness that data, allowing them to put into action the kind of efficiencies that will produce a profitable security operation. The CSO can expect more from all of their service providers and partners that will generate data to justify an organization’s investment in their operations.
CSOs will also need to be actively surfing trends in the security industry. If a game-changing technology or model is being adopted in the business, the CSO needs to be familiar with it going into their next meeting. From there, they must be able to take a trend that suits their operation and distil it into something specific and localized. A nimble operation that can adapt to change is future proof.


New priorities and challenges are keeping post-secondary campus security directors busy, but students and faculty have a part to play too
By Will Mazgay
Ensuring a safe and healthy environment on university campuses has always been a tall task for the security professionals at these institutions, but new risks and heightened awareness of existing problems have added new dimensions to the responsibilities of campus security departments.
For Kirsty Bradley-McMurtrie, director of safety and security at Conestoga College in Kitchener, Ont., mental health is a priority at her school.
“My team are always the first responders to any medical situation, including mental health crises, so they’re all now trained in mental health first aid,” she says.
Bradley-McMurtrie continues, “There’s a real focus on how we respond to those situations, so we can better help the students that could be in crisis, or could be trying to reach out for help…we’re the only ones here 24/7, so for us it was important how we responded first at the scene to those incidents.”
Pat Patton, director, security and operations, for the University of Regina (U of R), agrees that there is a need for security officers to be able to respond to students grappling with mental health issues.
“We often see people at the face of an issue, if they’re having a challenge in the middle of the night, it’s often our folks that
get called to it,” Patton says. Her officers also receive mental health first-aid training.
At Vancouver’s Simon Fraser University (SFU), there is a 24/7 number that’s available in over 40 different languages for students experiencing a crisis during off-hours, says Mark LaLonde, the school’s chief safety officer. “They can speak to somebody right away, which can then loop them into a physical meeting,” he says.
“Mental health, and especially emergency mental health, for our community has been a really big focus for us for several years. When we have a critical event, we have a critical issues management team that we’ll rally, either in-person or on phone right away,” LaLonde continues. “We’re also offering mental health first aid training for our security teams.”
Another issue that has received heightened attention on campuses in recent years is sexual violence.
To that extent, Patton has played a pivotal role in championing a sexual violence awareness program at U of R, “Man Up Against Violence.” The program emphasizes prevention and the root causes of gender-based and sexual violence, and it asks men to take an active role in prevention, by speaking out and speaking up. She was interviewed by Canadian Security magazine for the September/October 2016 edition about the program, when she was named Security
Director of the Year.
Now, in 2019, Patton says, “I think that people in general are starting to recognize the issue of gender-based violence and the issue around toxic masculinity and how that affects violence in our society and on our campuses.”
When it comes to recent developments like the #MeToo movement, Patton says, “I think it’s strengthened the resolve for the people on the university campus to understand that this is a major problem and that we need to have a solid policy in order to deal with it.”
With respect to that policy, “the university has undergone a bit of an assessment on the area around sexual violence and our response to that,” says Patton. “So, there is a task force that’s set up to support the policy that we have in place. What it ends up doing is giving us basically an integrated response, where we have more than just one unit involved in sexualized violence and responding to it — it’s really a group effort on behalf of the university.”
Bradley-McMurtrie says Conestoga focuses on educating its community on sexual violence, not just students but staff, visitors and contractors, and the school is offering new courses to staff and students, such as non-violent crisis intervention, “upstander” training (intervening against bullying or harassment) and free self-defence training. She says the school offers information for survivors on how to get support, on campus and off, reporting incidents, and for friends and allies of survivors, how they can help.
At SFU, there is a standalone office, the Sexual Violence Support & Prevention Office, which LaLonde says facilitates investigations, survivor support and safety planning.
One of the most daunting challenges facing campus security is what to do in a worst-case scenario.
LaLonde says SFU’s Campus Public Safety department holds events several times throughout the year where they simulate a catastrophe.
“We’ve got a schedule of how we do these throughout the year, and at least three times a year we’ll do something where we have the president and vice presidents involved as the senior policy group for an emergency,” LaLonde says.
“Everybody gets comfortable with their roles, everybody gets comfortable with how information flows and decisions are made.”
He says his team has simulated a forest fire, a cyber breach and an active shooter situation.
In particular, the danger posed by an active shooter on a postsecondary campus has come into sharp focus.
“We use the run, hide, fight procedure for our lockdown,” says Bradley-McMurtrie.
Conestoga’s security director says it’s important to communicate to faculty what their responsibilities are in an emergency like a violent lockdown, and for faculty members to then communicate to students what their options are.
Another challenge, according to Bradley-McMurtrie, is ensuring her school’s emergency response policy is the same across its several different campuses in several different cities. “It doesn’t matter which campus you are at, you know the policy and procedure,” she says.
For U of R, their emergency response program is helped by a mass notification system called Alertus, which uses wall-


mounted devices integrated throughout campus that provide visual, text and audio alerts in the event of an emergency. Patton says her staff can use the system to send out a message that is not only communicated through the wall beacons, but to TV monitors, desktop computers and student smart phones via the school’s app.
Conestoga has a mobile app specifically for safety which is used for emergency notification. BradleyMcMurtrie says the app also allows students to report suspicious activity, send their location to security staff in the event of an emergency and a sexual assault button is directly connected to 911. A safety toolbox, equipped with a flashlight and personal alarm, is also provided, as are links to support services and maps.
SFU also has an app for emergency messaging. “We’re trying to add more features to it to draw more users,” says LaLonde.
While campus security teams are adopting new tools, students also need to do their part to help keep themselves and their classmates safe. “We all have a level of responsibility in keeping our own security,” says Patton. But it’s up to the security departments to communicate important safety tips to the students.
Patton elaborates, “A typical security group in terms of being proactive would always be giving the advice of locking up laptops, don’t leave things lying about, lock your door to your residence room, lock your car, make sure you hang on to your valuables, that kind of stuff, and I don’t think that has changed so much.”
LaLonde, who also sees safety and security as a shared responsibility, says faculty need to do their part as well, by learning where the emergency escape routes are, as well as the defibrillators. “Look at our online training materials around active threats, our emergency plans; what would you do if somebody had a heart attack in your classroom or there was some sort of event?”
Bradley-McMurtrie also stresses the importance of faculty and student

orientation. She and her team go to a friends and family orientation for first year students to fill them in on the safety app, security resources, safe zones and how to deal with emergencies. As for returning students, they have videos they are required to watch prior to starting school. She says pop-up lunch and learn drop-in sessions are also helpful, as are giveaways, iPads for example, which can help keep a busy student body engaged.
Patton says student engagement is a challenge for her team is well: “They’re very busy young people, they’ve got lots on the go, so they don’t necessarily engage in the same way that I do as a working professional.”
LaLonde says, “We look at a whole variety of ways to get the message out to students throughout the year. We’re at all the different student events with a booth. When there’s a student fair we’ve got a booth at that. We’re constantly trying to get in their face.” He says his team is also engaged in a postcard campaign to educate students on emergency response.
While the tried and true methods of generating awareness still work, security departments are increasingly connecting with students online.
“We have online reporting, we have social media pages for students so we can connect with them that way, through Facebook and Twitter, as well as Instagram,” Bradley-McMurtrie says.
Patton says her team has had to become more savvy with social media: “We do have one or two staff that try to stay engaged in it…we’re trying to become more accepting of getting information via email, via social media,
so students, that’s how they reach out now.” She says one of her department’s goals is to expand its online presence going forward.
Creating a partnership
While reaching out to students, both in-person and online, is a means of education, it can also help facilitate a better relationship between a campus security department and the students it is protecting.
Bradley-McMurtrie says her department has tried to be more accessible to students, with full service security desks in hallways. “We’re no longer behind a door…we are the first people that you see now, for assistance. We’re there to say good morning, have an interaction, not just security-related questions.” She continues, “We want to be seen more as a partner, rather than enforcement.”
Outreach to international students is particularly important to BradleyMcMurtrie’s team since, “depending on which country they come from, they might not have the trust of their local police or security in their own country.” Her staff makes an effort to explain their role and how security can support these international students.
LaLonde concurs that it is important not to be seen as an enforcement group, and stresses the importance of working with students, both by utilizing student safety patrollers and working with SFU’s undergraduate and graduate student societies. These student societies have been invited to take part in safety and emergency planning, and a new security hiring process had two student representatives on the interview panel. “They had an equal voice,” LaLonde says. “It worked really well, they were great; I’d do it again in a heartbeat.”
Patton agrees that a healthy partnership with students is crucial: “We’ve got 16 staff here that are out 24/7, but they can’t do it all on their own. Educating people to be their own best friend in these things and looking out for each other and working together with us, all of those things are still very important today.”
ennifer Stoddart served as the federal Privacy Commissioner from 2003 to 2013. Among her many other distinctions, Stoddart has held positions on the Human Rights Commissions of Canada and Quebec, was named an Officer of the Order of Canada for her service to privacy rights, and is a mentor for the Women’s Executive Network (WXN). Most recently, Stoddart joined Montreal law firm Fasken as a strategic advisor in its privacy and cybersecurity group. Canadian Security spoke with Stoddart to get her take on privacy today and how Canadian businesses should prepare for cyberthreats. This is an excerpt from that conversation.
Canadian Security: How has privacy changed since you were commissioner?
Jennifer Stoddart: I think the trends have intensified [but] I don’t think there’s anything drastically new that wasn’t being evoked five years ago. But what I’ve noticed now… is how anxious people seem to be about their privacy… There was a good chunk of Canadians who were anxious, but the whole intensification of the scene between what can happen, cyberbreaches, cyber predators… and then the reaction of the government, not only here but in the European Union and elsewhere [like] California to try to contain this. It’s making a perfect storm of privacy anxiety.
CS: What is your opinion of the new breach notification legislation that came into effect in November as well as GDPR legislation in Europe?
JS: That’s a big game changer. We knew both were coming for a long time. But it requires much more attention on the part of organizations as to what

they’re doing with people’s personal information. As you know, in Canada, they have to do data breach reports. This is the most stringent Canadian legislation we’ve ever seen.
The GDPR is a game-changer with these huge fines that are possible. [There are] quite stringent requirements in terms of investing in privacy and security. It’s really pushed data protection and security way up the regulatory chain of attention for organizations.
CS: Are Canadian organizations where they need to be in order to comply with the latest privacy legislation?
JS: Well, we’ve know about this for a while, but I gather from the lawyers here at Fasken that a lot of organizations are very busy, because they didn’t have anything like this before. Not only do they have to report significant harm but they have to keep records of data breaches. I gather that a lot of them are scrambling to put this in place.
CS: What about smaller companies that may not have the resources to appoint a privacy officer?
JS: This has always been a challenge. PIPEDA requires that people have somebody in charge of protection of personal information.
If you’re a very small firm, either you can outsource it or you ask somebody to multi-task. Small firms have to look for somebody who’s really interested in this and wants to keep up with the field. They should spend a small amount helping them to follow the major trends. I don’t think you can just put your HR person in charge of this overnight and expect that will do the job. It’s an investment, I think.
CS: Given the large number of privacy breaches that are happening, should businesses view them as inevitable?
JS: Can I push back on that on principle? I think organizations can be passive and say, “Oh well we’ll probably be breached one day.” I think that’s a really, really dangerous attitude to have. If we go back to the big TJ Maxx breach — and there are ones that are even bigger that are happening now — I would say, don’t say it’s inevitable we’ll be breached. In the public and private sector, there are [organizations] that probably haven’t been breached or can be breached in a relatively minor way — which is why the new regulation says there has to be a harm factor. I would say, take that as an attitude. “What can I do to lessen the ability to be breached… or if I am breached, it’s a superficial breach.”
CS: Not to suggest that businesses are complacent, but there seems to be a prevailing sentiment that it’s getting really tough out there.
JS: I would agree with you there. It is getting more challenging, but I think attitude counts for a lot. If you’re up to date and you’re got a good procedure and you know what can happen in event of a breach, you can lower your risk. You can’t eliminate it, but you can certainly minimize it.
CS: What do you hope to accomplish in your new role at Fasken?
JS: This is a firm I’ve known for a long time. Almost 30 years. I was working in Montreal a long time ago. I hired people from both their Montreal and Toronto offices to do work and to write publications that were published by the Office of the Privacy Commissioner, so they’ve certainly got their credentials. I am an advisor, advising on general directions of files. What I hope to accomplish is to be able to continue to work in this area [and] help to make data protection more effective for Canadians.


With stakeholders, suppliers and regulators moving in the same direction, expect UAS services to continue an upward trajectory in 2019
By Mark Aruja
The rapid development of Unmanned Aerial Systems (UAS) over the years has brought global attention to managing associated aviation safety risks.
Developing safe practices which bring together best practices in training, processes and technology applications has been the cornerstone of UAS regulatory development in Canada since the joint government/industry Unmanned Aerial Vehicle (UAV) Program Design Working Group was established in 2010.
Since then, industry and regulator guidelines have been developed, enabling rapid growth. For example, in 2012, Unmanned Systems Canada (USC), a not-for-profit that promotes the development of the Canadian unmanned systems industry and Transport Canada (TC), respectively,
published guidance for the industry and regulator regarding the operation of small UAS in Visual Line of Sight (VLOS). While there were only 100 authorizations for commercial operations of small UAS that year, there were over 4,000 commercial certificates last year.
The consolidation of lessons learned by both industry and the regulator has resulted in the publication of regulations on Jan. 9, 2019, governing VLOS operations. But what role do safety and security play in the development of this industry, and what should we expect in the near future?
The commercial UAS industry in Canada has doubled every two years with new applications continuously being developed. Today, over 1,000 Canadian companies are engaged in the UAS sector, two-thirds of which are operators — and safe operations are
critical to their success.
Although there have been disturbing reports of UAS sightings that could endanger aviation, these are almost exclusively attributable to recreational flyers, with no confirmed reports of malfeasance by the commercial industry. Therefore, industry has a vested interest in working with stakeholders to educate and — if necessary — support the enforcement of safety violations.
Fortunately, Transport Canada has now assigned resources to the task with the creation of a 30 person-strong Remotely Piloted Air Systems (RPAS) Task Force in 2017. However, industry and government are not the only key players in developing UAS safety best practices.
Reducing risk through technology
UAS technology has made tremendous strides in improving the reliability of these systems. Software updates have added more safety features that are amortized across a massive inventory.
For example, features such as geofencing, which can prevent a UAV
from entering a restricted area or from being activated within one, are now ubiquitous. Likewise, flight control software, electric motors and datalinks ensure robust performance. Most of these developments are applied to small devices — categorized as those weighing less than 25kg — and designed to operate within visual sight of the operator.
anticipated to reduce aviation risk.
“The commercial UAS industry in Canada has doubled every two years.”
However, the major commercial opportunities lie with Beyond Visual Line of Sight operations. BVLOS requires procedural and electronic means to be in place in order to achieve hazard avoidance. There are a range of possible scenarios in which BVLOS is required, from a crop survey over several sections of land to surveying a thousand kilometres of pipeline with variations in topography, weather and airspace type.
In fact, trials have started with four Canadian consortia (selected by Transport Canada) that are demonstrating BVLOS operations in coordination with TC. USC is supporting these trials with a BVLOS best practices document, published in 2017, and, more recently, with funding for the deployment of a national risk assessment model.
Safety is at the core of these trials, which aim to identify use cases that can be adequately managed from an aviation safety perspective to permit commercial operations as early as 2019. Expected outcomes include the development of technical certification standards for larger UAS (beyond 25kg), operational processes and knowledge requirements. With the reduction in bureaucratic requirements associated with the announcement of regulations, Transport Canada has indicated that they now have resources to turn to this effort.
Not only do UAS operations lead to improved business practices in numerous applications, but some, such as geomagnetic survey in the mining industry and crop-dusting, are also
In January 2019, after six months of exploratory discussions, TC and NAV CANADA (Canada’s Air Navigation Service Provider) jointly chaired the inaugural meeting of a steering committee, which also included DND and expert participants from Canada, the U.S. and Europe to explore ways to develop a national roadmap for implementation. Safety and security go hand-in-hand as network security needs to be assured. Rapid innovation is taking place with many technologies, such as blockchain, which could be used to secure flight plan “contracts.”
Key players and processes
NAV CANADA co-founded a new company, Aireon, with Iridium Satellite Communications, a satellite company that offers voice and data communications coverage solutions through its satellite networks.
With the imminent completion of the Iridium NEXT satellite constellation, Aireon will be able to provide spacebased global air traffic management services. As the Iridium constellation also provides proven UAS command and control communication links, the prospect of utilizing this system across Canada to integrate the management of manned and unmanned traffic has a lot of potential for the near future.
The transition to computer-based traffic management will also change operational processes. A driving commercial influence is in logistics services where manpower costs are the most significant. Whether it be parcel delivery, defibrillators or postal services, urban planners and technology developers foresee an integration of smart cities with automated vehicles both on the ground and in the air as the future of mobility.
As the UAS industry expands, and
commercial success stories accumulate, so do concerns about malfeasance and counter-UAS technologies, driven by the use of UAVs by terrorists. Defence needs are also driving innovation and investment, while other applications such as special events and prison protection are also being funded.
A number of Canadian companies are active in this field, developing sensor technologies including optical, acoustic and radio frequency (RF) with decision-support tools. Some of these technologies are being trialed at Canadian airports. In fact, at Edmonton International Airport ground-breaking work is being done to integrate counter-UAS technologies into airport operations.
Generally, the counter-UAS market can be divided into two categories: Co-operative and non-co-operative targets. Co-operative targets are easier to deal with and are typically those used at airports where recreational flyers operate “in the neighbourhood.”
Therefore, activities can be monitored and procedural intervention can be taken when necessary. Noncooperative targets are expected to be driven by military requirements or sensitive critical infrastructure, which requires access to the most sophisticated and often sensitive technologies, integration with complex command and control systems and the most significant investment.
Ultimately, the UAS industry is a good news story in every respect in Canada. A close working relationship between industry and the regulator has been founded on a crawl-walk-run strategy, which is now unfolding with the publishing of legislation for small UAS, and the expectation of commercial BVLOS operations commencing in 2019.
All of these efforts have been predicated on the assertion that the best safety practices make for best business practices.
Mark Aruja is the Chairman of the Board for Unmanned Systems Canada (www. unmannedsystems.ca).

What to expect this year as new data privacy regulations take hold and IT skillsets take on a premium role in the enterprise
By Matt Tyrer and Don Foster

Privacy-first becomes a priority
As government agencies increasingly cite enterprises for non-compliance with the European Union’s GDPR and other strict data privacy regulations, and other governments implement new data privacy regulations, enterprises will increasingly adopt a “Privacy First” approach to data management. We’ve seen this discussion quite a bit in the Waterfront Toronto / Sidewalk Labs (smart cities) project where the push for “privacy by design” has come to the forefront. Canada recently expanded its
own data privacy act (PIPEDA) to include much more stringent requirements around record keeping for data breaches and notifications of those incidents to the public. However, the challenges enterprises will face as they seek to integrate data privacy best practices into their existing applications, as well as new mobile, IoT and other applications, will be significant. Enterprises will need AI-powered, automated, outcomedriven data management solutions to address these challenges if they hope to implement strong data privacy policies
without sacrificing productivity or agility.
2019 will be game-changing for cloud adoption in production IT workloads globally Enterprises will continue to pour investment into cloud initiatives, focusing increasingly on technologies and services that enable them to transform the cloud from merely a storage location into a solution that enables new, more agile ways of working. Technology providers will increasingly move to deliver this agility

by offering native support for multiple cloud providers and other powerful cloud tools that equip enterprises with a single interface for efficiently, effectively and responsibly managing applications, workloads and data across both onpremises and cloud environments.
Artificial intelligence and machine learning will become a requirement for new solutions for simplified operations
The IT skills gap will require progressive enterprises to implement new, innovative
solutions that automate complex operations. Machine learning and artificial intelligence will become key requirements for new IT solutions to help businesses close the skills gap through smarter operations and modern IT solutions. Enterprise software firms will force their strategic vendors to integrate AI and machine learning into their existing offerings to provide a more efficient operating model and a higher level of success for meeting their desired outcomes.
Recovery readiness metrics will become the newest trend in technology RFPs
“The IT skills gap will require progressive enterprises to implement new, innovative solutions.”
aaS vs. the Cloud “as-a-Service” offerings will continue to accelerate and a new battle will be fought for the IT wallet. Cloud vs. aaS or both? On-premises solutions will still be a major part of IT, however IT growth will continue to accelerate in the cloud and through aaS offerings, forcing providers and technology vendors alike to reassess their strategies for how they will serve their customers and ultimately help them define and achieve their necessary business and IT outcomes.
Technology skillsets and time gaps will stall digital transformation Organizations that continue to leverage traditional methods to meet the modern and transformative needs of the changing digital business will run into major obstacles in 2019. Comprehensive IT skillsets that traverse the worlds of traditional IT and the new hybrid IT will become more rare. New compliance and governance measures together with a growing monetization of malware/ ransomware attacks will continue to put pressure on IT organizations and force improved operations in order to successfully meet the needs of the digitally transforming business. Without the consolidation of disconnected point solutions in data management and all areas of IT, digital transformation efforts will stall, especially as cloud computing becomes the standard for the growing digital enterprise.
Technology vendors must be prepared to meet the requirement for recovery readiness — or the speed in which a service, solution, or offering can be properly brought back online in the event of an outage — as a key requirement definition in technology solution RFPs. Business requirements to keep services active and available for their consumers will continue to mature and become part of the outcome purchasing criteria to pass or fail a solution for specific needs. Solution providers will need to prove their ability to meet necessary SLAs and will be judged on the ease and simplicity in which this metric can be met.
The end of swampy data lakes
Over the past decade, as data storage hardware costs plunged and applications proliferated, enterprises frequently collected and stored as much data as they could, often giving little to no thought to what this data was or how valuable it could be to their organization. They typically stored all this data in a repository known as a data lake. Not fully knowing or understanding what is being placed in the data lake, why it is stored, and whether it has proper data integrity will prove untenable and inefficient for mining and insight gathering. The data lake will begin to disappear in favour of technology that can discover, profile and map data where it lives, reducing storage and infrastructure costs while implementing data strategies that can truly provide insights to improve operations, mitigate risks and potentially lead to new business outcomes.
Matt Tyrer is Commvault’s senior manager, solutions marketing, Americas. Don Foster is Commvault’s senior director of worldwide solutions marketing (www.commvault.com).

Visitor kiosk
Visitor Pass Solutions
Visitor Pass Solutions has launched a Kiosk version of its visitor management software, eVisitorPass. The touchscreen application enables visitors to check themselves into an organization’s building and then pick up their badges from an administrator at the front desk. The eVisitorPass Kiosk comes in two models: Floor-Standing and Tabletop. Both versions include a one-year software subscription, a driver’s licence reader, a Zebra direct thermal printer, and a supply of “one day” expiring visitor badges, which change colour overnight to show they are void and can’t be reused. www.visitorpasssolutions.com

Eaton
Eaton introduces its new line of Wheelock Exceder LED3 notification appliances, compliant with the latest National Fire Protection Association (NFPA) code requirements for flash duration. The Wheelock Exceder LED3 line includes strobes, horn strobes, horns, speakers, speaker strobes, low frequency sounder strobes, and sounders for ceiling and wall-mount indoor applications. High-fidelity speakers provide leading intelligibility for mass notification and emergency communications. The line has been UL/ULC listed as compatible with all fire alarm control panels and accessories determined to be compatible with Wheelock RSS strobe-based products. Exceder LED3 strobes can also be installed in the same notification zone and field of view with any Wheelock RSS strobe model.

www.eaton.com
Visitor management solution
AMAG Technology
Symmetry GUEST operates on most tablets, smart phones or PCs as well as most web browsers. GUEST provides the ability for roving lobby ambassadors or self-service kiosks to check-in visitors, contractors or visiting employees. The enterprise level solution fits any size organization. Symmetry GUEST fully integrates with Symmetry Access Control software, which allows companies to assign temporary access to visitors or employees who have forgotten their badge that coincides with the visit length and status of the visit. www.amag.com/guest


The latest version of Robotic Assistance Devices’ Security Control and Observation Tower (SCOT): Wally, is a wall-mounted security solution that harnesses artificial intelligence to enhance an organization’s situational awareness, communication abilities and control. SCOT Wally provides organizations with 110° of visibility and uses the RAD Software Suite, a collection of integrated software applications hosted in Microsoft’s Azure Cloud services that allows mobile access to alerts and controls generated by SCOT. The solution can be used in lobbies, parking structures, corporate campuses or exterior areas. www.roboticassistancedevices.com
ZKTeco
ZKVAMS is a VMS which incorporates visitor authentication and security features. ZKVAMS authenticates both pre-registered and walk-in visitors, maintains their identity records, sends emergency alerts, flags unwanted visitors and tracks all the data in real-time. Security personnel will appreciate its auditing and tracking features while hosts and visitors will appreciate how fast and simple visitor registration is. ZKVAMS is used by many Fortune 500 multi-national companies from various industries including shipping and logistics, banking, consumer product manufacturers, etc. ZKVAMS features cloud-based architecture for simplicity of purchase and operation.
www.zktecousa.com
Vicon
The VAX Access Control solution now features mobile credentialing. This new feature allows VAX customers to present their smartphones, instead of cards or fobs, to specialized Bluetooth-enabled VAX door readers. Upon installation of a custom smartphone “wallet” app and a simple authentication process that links that app to the specific phone, users enter their personal VAX credentials into the wallet. Multiple credentials can be accommodated. No additional activation steps, such as entry of personal information or Bluetooth linking, are required. To unlock doors using the mobile credentials, users unlock their phone, access the credential within the wallet app and push the “unlock” button. Credentials are uniquely linked to each smartphone and cannot be shared or installed across multiple devices. Android and iOS devices are supported.
www.vicon-security.com



At G4S, we approach security differently. We aim to understand your business goals so that we can partner with you and create a program with a high level of engagement. For us, that means taking on challenges and demonstrating real results. We’ll work with you to examine your resources, the potential risks that could disrupt your business and create resolutions that will help to protect you, your employees and your customer’s interests. We do this by thinking creatively, working collaboratively and producing programs of value for your business. We are your trusted advisor and we have the expertise to help you manage your risk.






Avigilon Blue™ – our powerful integrator cloud service platform for security and surveillance – is rapidly expanding with new features and updates.

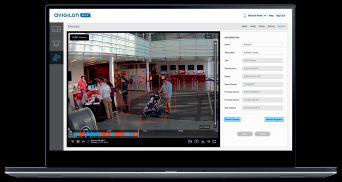
SureView Systems Immix® Integration
New integration with SureView Systems provides powerful video analytics-based event verification to central alarm monitoring stations.
Subscription Centre
A unified view of your business to help you track and analyse customer subscription data.
16-Channel Avigilon Blue Connect Device
Connect to the cloud, add analytics and manage more cameras. Includes 12 TB of onsite storage capacity for up to 30 days of video.
Remote Camera Disarm/Arm Feature
Conveniently pause notification alerts directly from your mobile device.
Timeline Scrubber
Search specific points on the timeline and scrub multiple cameras simultaneously with synced views.
As the platform continues to expand, new features and services will be added that are designed to help your business grow.