







By Neil Sutton









By Neil Sutton
The theme of our cover story this issue is essentially about the need to made sure cybersecurity training is up to par for employees.
But I think the real takeaway here might be the way security departments are being reframed within the organizations they serve.
Experts quoted in the article repeatedly state that blaming users for errors is counterproductive, and punishing them for those errors even more so.
There’s an old saying that you catch more flies with honey — and that principle applies here as well. In other words, get your employees on-side and make them your allies by training them to engage with a security problem rather than simply showing them how to avoid doing the wrong thing.
I have heard of various approaches to this, including “gamification,” which is pretty much what you’d expect it to be based on the name — make a game of training and problem-solving in order to harness that part of the brain we all engage when we sit down to play a board game with family or swipe over to the games menu
Jason Caissie: Profile Group
Ken Close: Shangri-La Hotel
Ashley Cooper: Paladin Security
David Hyde: Hyde Advisory & Investments
Sherri Ireland: Security Exclusive
on our phones.
HR leaders have known for years that team-building exercises are most effective when they’re fun (and perhaps held outside the office). These are tools and techniques that could be employed to good effect for security and cybersecurity training too.
“Being welcoming while watchful is a powerful approach, balancing both vigilance and trust.”
Tim McCreight also explores elements of this approach in his column this month, asking security professionals to lift the veil of secrecy, reach out across their organizations and encourage other staff members to participate in the security process.
“ There is a cultural change that is challenging security professionals to look at our employees as advocates for the security program,” he writes. “This approach asks security professionals to see their employees as the greatest strength of the corporate security program.”
I think some organizations will have an easier time with this shift in mindset than others, since some security procedures are so deeply root-
ed they are not easily diverted.
But I have also seen good examples of security departments that are truly on the cutting edge of this new breed of thinking.
You can also see it in the adjustment of security tactics towards elements of customer service.
Winston Stewart’s column this issue exhorts building owners to demand more of their security guards, particularly as facilities adjust to the post-COVID realities of building management, tenant preferences and multi-purpose venues.
Customer service combined with attentiveness is one way to serve a dual function as a security professional. That’s not always an easy combination to pull off, but I think it’s where security, especially on the frontline, is headed.
B eing welcoming while watchful is a powerful approach, balancing both vigilance and trust.
These are some fascinating times for the security professional, with new approaches being considered all the time. They won’t all work, but that’s OK. Ultimately, it’s all about problem-solving. | CS
Summer 2022 Vol. 44, No.3 canadiansecuritymag.com
READER SERVICE
Print and digital subscription inquiries or changes, please contact Shawn Arul, Audience Development Manager
Tel: (416) 510-5181
Fax: (416) 510-6875
Email: sarul@annexbusinessmedia.com
Mail: 111 Gordon Baker Rd., Suite 400, Toronto, ON M2H 3R1
EDITOR
Neil Sutton nsutton@annexbusinessmedia.com
ASSOCIATE EDITOR
Madalene Arias marias@annexbusinessmedia.com
GROUP PUBLISHER
Paul Grossinger pgrossinger@annexbusinessmedia.com
ASSOCIATE PUBLISHER Jason Hill jhill@annexbusinessmedia.com
MEDIA DESIGNER
Graham Jeffrey
ACCOUNT COORDINATOR Kim Rossiter krossiter@annexbusinessmedia.com
COO Scott Jamieson sjamieson@annexbusinessmedia.com
Printed in Canada
I.S.S.N. 0709-3403
Publication Mail Agreement #40065710
SUBSCRIPTION RATES
Canada: 1 Year $43.00 + Taxes; U.S.A. (payable in CAD dollars): 1 Year $95.55; International (payable in CAD dollars): 1 Year $110.00
EDITORIAL AND SALES OFFICE
111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1 (416) 442-5600 • Fax (416) 442-2230 canadiansecuritymag.com
Canadian Security is published four times per year by Annex Business Media. Annex Privacy Officer Privacy@annexbusinessmedia.com Tel: 800-668-2384
Canadian Security is the key publication for professional security management in Canada, providing balanced editorial on issues relevant to end users across all industry sectors. Editorial content may, at times, be viewed as controversial but at all times serves to inform and educate readers on topics relevant to their individual and collective growth and interests.
Mark LaLonde: Simon Fraser University
Bill McQuade: Final Image
Carol Osler: TD Bank
Tim Saunders: G4S Canada
Sean Sportun: GardaWorld




The contents of Canadian Security are copyright by ©2022 Annex Publishing & Printing Inc. and may not be reproduced in whole or part without written consent. Annex Business Media disclaims any warranty as to the accuracy, completeness or currency of the contents of this publication and disclaims all liability in respect of the results of any action taken or not taken in reliance upon information in this publication




By ASIS Canada
ASIS International Canada members will be celebrating the 28th anniversary of Canada Night in Atlanta, Ga., this year.
We are excited to announce that the event will take place on Sunday, Sept. 11, 2022, at Hudson Grille, in downtown Atlanta.
Canada Night, hosted by the ASIS Canada Region 6 event committee and supporting sponsors, is excited to hold their annual social mixer event which welcomes close to 1,000 attendees each year.
After a two-year hiatus due to travel and social restrictions, the event will be open to all ASIS Canada and ASIS International members and guests attending the 2022 Global Security Exchange (GSX) and Expo.
“It’s time to get out, reunite and celebrate,” said Jason Caissie, PSP, PCI, CPP, and senior regional vice-president of ASIS Canada.
“ The main objective of the event is to provide an informal atmosphere where fellow Canadians and ASIS members working in the security industry can meet and mingle, and get inspired to develop their international network. We are very proud to host this popular annual event for our members and international community. We are grateful to all who support us each year, making it possible for us contribute to the ASIS Foundation, providing scholarships, grants and research,” said Caissie.
Although Canadian constituents host Canada Night 2022, all attendees at GSX are invited to attend to acknowledge and celebrate our Canadian members and achievements. Canada Night 2022 offers a vibrant atmosphere for all ASIS members and guests to gather. Admission, as well as a complimentary appetizer buffet and latenight pizza will be offered (as available). Drinks may be purchased at the bar.
This not-for-profit event is made possible solely through the generous donations of all our sponsors. For a full listing of all supporting sponsors and event details,

please visit www.asiscanada.ca.
Hudson Grille, downtown Atlanta, next to CNN and the Georgia World Congress Center, is located at 120 Marietta Street, NW. The doors will open at 6 p m to Canadian members, followed by the presentation of the Ron Minion Award at 6:30 p.m.
At 7 p m , the event is open to all ASIS International members and guests with the evening wrap-up at midnight. Admission to enter is free to all attending the GSX conference and guests.
The 2022 Ron Minion Award will be presented during Canada Night festivities in Atlanta.
The Canadian Security Industry Pioneer award, as it was originally named, was established in the late ’90s to recognize the contributions of ASIS Canadian members who had distinguished themselves through their contributions to the growth and professionalism of the security industry. The security practitioners that initiated the award looked not only at the contributions that individuals made to the Canadian security industry and contributions to ASIS International in Canada but also to ASIS International globally.
Ron Minion, CPP, was the first recipient of the award in 1999. Ron was instrumental in bringing ASIS to Canada.
He, along with others primarily in west-
ern Canada, worked tirelessly to establish the first chapter in Edmonton and then in Calgary. Ron passed away after a lengthy battle with ALS, also known as Lou Gehrig’s disease. The award was renamed in his honour. | CS
1999 – Ron Minion, CPP
2000 – Denis O’Sullivan, CPP
2001 – Patrick Bishop, CPP
2002 – Dennis Shepp, CPP
2003 – Phill Banks, CPP
2004 – Howard Moster, CPP
2005 – David Tyson, CPP
2006 – Roger Maslen, CPP
2007 – John Rankin, CPP
2008 – Gary Vikanes, CPP
2009 – John Grady, CPP
2010 – Greg Hurd, CPP
2011 – Chris McColm, CPP
2012 – Bill Bradshaw, CPP
2013 – Geoff Frisby, PCI, CPP
2014 – Christina Duffey, CPP
2015 – Dan Popowich, CPP
2015 – Dr. Wayne Boone, CPP
2016 – Patrick Ogilvie, PSP, CPP
2017 – Parnell Lea
2018 – Marie Thibodeau
2019 – William (Bill) VanRyswyk, CPP
2020 – Stéphane Veilleux, CPP
2021 – Mark Folmer, CPP
By Madalene Arias

Security professionals brushed shoulders with staff at Toronto-based Baycrest Health Sciences Centre while others connected virtually where they joined Martin Green, the facility’s manager of security, telecommunications and emergency preparedness, as he unveiled Baycrest’s first ever security operations centre in June.
“If I could take my mask off, you would see a fantastic huge smile,” he told his colleagues and guests before the lobby of the security centre.
G reen began his speech with words of recognition for team members present, including Joni Kent, president and corporate CHRO at Baycrest’s Centre for Geriatric Care; Scott Ovenden, president and CEO of Baycrest Hospital and LTC.; Cathy Borsa, vice-president of corporate redevelopment and facilities; Rabbi Dr. Geoffrey Haber and Brine Hamilton, IAHSS president.
Founded in 1918, Baycrest serves as a research and teaching facility for elderly care. It also houses the Apotex Centre, a Jewish home for the aged, holding 472 beds and various independent living arrangements.
“For over 104 years, our primary mission at Baycrest never changed. We are here to provide a safe and secure environment for our residents and patients, clients, their families, and of course our staff,” said Green before Kent joined him in cutting the “Baycrest Blue” ribbon from the doorway of the security centre.
Kent explained that seven years before the creation of the Baycrest Security Operations Centre, the security team managed the safety of the facility with 48 CCTV cameras and 12 card readers. Presently, the facility’s security system operates with 320 CCTV cameras and 350 card readers.
“To be able to monitor in this way is just excellent. They’re in and of themselves great security features, but to have the 24-hour monitoring is so much better,” she said.
Currently, Hamilton is a senior system engineer with Omnigo Software, as well as president of IAHSS. In 2016, he served as Baycrest’s security coordinator. It was during this time that he first learned of Green’s vision for a security operations centre. “It’s been a lot of work for Martin to get his vision to fruition,” he said.
D uring the initial stages of the project, Green met with an architectural firm and project team at Baycrest to design the centre. After this they issued an RFT for the project
Baycrest awarded the request for proposal to a general contractor who worked with 3D Network Technology and other sub-contractors to implement the design and integrations.
Green said that everyone associated with the project had to follow strict COVID-19 screening protocols, and only contractors who were fully vaccinated could work on the premise as part of their mission to keep everyone safe. | CS
SEPTEMBER 11, 2022
ASIS Canada Night Atlanta, Ga. www.asiscanada.ca
SEPTEMBER 12-14, 2022 GSX Atlanta, Ga. www.gsx.org
OCTOBER 5-6, 2022
Sector Toronto, Ont. www.sector.ca
OCTOBER 6, 2022
Canadian Security Honours Online www.canadiansecuritymag.com
OCTOBER 18-19, 2022
Securing New Ground New York, N.Y. sng.securityindustry.org
OCTOBER 19-20, 2022
“We are here to provide a safe and secure environment.”
— Martin Green, Baycrest
Security Canada Central Toronto, Ont. www.securitycanada.com
NOVEMBER 16-17, 2022
ISC East New York, N.Y. www.isceast.com
NOV. 30 - DEC. 2, 2022 The Buildings Show Toronto, Ont. www.thebuildingsshow.com
DECEMBER 6, 2022
Focus on Healthcare Security Vaughan, Ont. www.focusonhealthcaresecurity.com
MARCH 28-31, 2023
ISC West Las Vegas, Nev. www.iscwest.com
MAY 1-3, 2023
IAHSS Annual Conference & Exhibition Nashville, Ten. www.iahss.org
JUNE 27-30, 2023
IACLEA Annual Conference & Exposition Orlando, Fla. www.iaclea.org

By Kevin Magee
Much of the work we do in cybersecurity requires a whole lot of technical reading. Tryi ng to keep up with and learn new tools, technologies, tactics, techniques and procedures is extremely difficult and demanding.
We rarely, if ever, have the opportunity to step back and think much more strategically — to put the threats and threat-actors we see evolving as part of our daily work as defenders into a greater perspective that includes a deeper understanding of the geopolitical and historical factors that inform, influence and motivate the actions of our adversaries.
For me, summer is a great time to explore new ideas and that means books. Warm, sunny afternoons on the deck are the perfect setting for some quality thinking. Many of my peers clearly feel the same way as I find book recommendations and discussions beginning to appear around this time every year throughout the social media chats I follow and participate in.
T hese conversations have created new opportunities for me to meet others with common interests and many of my greatest relationships and collaborations in the industry can be traced back to sharing thoughts on an interesting chapter in a good book!
S o, what are my reading recommendations for this summer? If you are new to

“Summer is a great time to explore new ideas and that means books.”
the industry or would simply like to gain a bigger picture perspective, then I am happy to light the path forward with a few of my top recommendations
My top pick for both readability and for a fascinating look into the world of zero day and cyberweapons arms dealers is This Is How They Tell Me the World Ends: The Cyberweapons Arms Race by New York Times journalist Nicole Perlroth. It is an incredibly well researched piece of investigative journalism and yet un -
folds as a real page turner as well. Perlroth includes incredible stories such as how the Russians managed to install key loggers into typewriters. She also brings many of the characters that populate this world to life, which makes the book highly entertaining, informative and a little unnerving.
S imilar books in the field by other great journalists and storytellers include The Perfect Weapon: War, Sabotage, and Fear in the Cyber Age by David Sanger, which is a must read. Sanger has updated this work with new material for a second edition and released a companion documentary of the same title on HBO.
Kingdom Of Lies: Unnerving Adventures in the World of Cybercrime by Kate Fazzini, a former journalist and now university professor and cybersecurity practitioner, is another incredibly well researched survey of the cybercriminal landscape as told through the stories of actual people who enthusiastically embraced or simply fell into this dark and shadowy world.
If you want to go back and explore the early days of our industry and its cultural roots, then Cult Of The Dead Cow: How the Original Hacking Supergroup Might Just Save the
World by Joseph Menn is a wonderful book that will transport you back in time to the 1980s world of elite hackers such as Mudge and RaD Man. Ghost In The Wires: My Adventures as the World’s Most Wanted Hacker by Kevin Mitnick is a look into the real life of the most well-known or mythological hacker of all time and is another one of my all-time favourites.
By next summer I expect the shelves will be full of books exploring this topic, however if you are looking for an excellent primer then there are three books I would highly recommend. Sandworm: A New Era of Cyberwar and the Hunt for the Kremlin’s Most Dangerous Hackers by Wired’s Andy Greenberg is a masterpiece of investigative journalism that explores the rising menace that Russian hackers pose in modern hybrid warfare and unfolds much like a Tom Clancy thriller novel.
Mr. Putin: Operative in the Kremlin by Fiona Hill and Clifford Gaddy provides the best psychological portrait of a leader who is pushing the world into a new area of persistent engagement and cyberwarfare while A Short History of Russia: How the World’s Largest Country Invented Itself, from the Pagans to Putin by Mark Galeotti provides a sweeping overview of the foundations of Russian society and much of the historical background needed to better interpret the current conflict.
I’ll end with some lighter reading recommendations that are still very thought-provoking, including a new category of Fictional Intelligence (FICINT) which is being developed by Peter Singer and August Cole who have written two excellent books, Ghost Fleet and Burn-In. Both books leverage a fictional and narrative story telling approach to teach strategic concepts and include a full and detailed reference section citing all the source material
behind the technologies and concepts included in the books. While the story and characters are made up, all the technology is real or potentially real.
Hopefully there is something on this list for everyone! If you have recommenda -
tions for me or would like to connect and discuss some of these books, I would be more than pleased to chat with you on LinkedIn or Twitter as I explore some of my own summer reading on the deck over the coming weeks! | CS

With ännT‘s high security K12 bollard, a full-size speeding vehicle is brought to a dead stop.*
• Versatile Operation: choose from fixed, removable, semi-automatic or automatic bollards.
• A Reliable Sentry: a single 275 K-rated bollard is certified to K/M standards.
• Easy to Use: operated by key fob, RFID card, keypad or smart phone.
• Blend in: with your urban landscape with brushed stainless steel or powder coated in any RAL colour.
* Just one ännT K12 rated bollard will stop a 6,800 kg vehicle moving at 80km/h.
ännT distributed by Ontario Bollards, 53 Armstrong Ave., Unit 1, Georgetown ON L7G 4S1 8 44-891-8559 contact@anntbollards.com www.annt.c a

By Tim McCreight
For decades, security awareness programs focused on the human element of security, but from a negative perspective.
We learned early on as security professionals that the weakest link in our security program is the human we’ve been trying to protect. Our security awareness training focused on changing negative behaviours of our employees to reduce the impacts caused by them clicking on links, propping open doors, or inadvertently providing sensitive information to competitors or criminals.
We targeted the issues we all had to deal with — the employee who continually forgot their badge, or the executive who kept clicking on links embedded within our phishing campaigns.
Consequence and punishment followed — ranging from extra courses from our cybersecurity team right up to suspension and even dismissal for continually disobeying the “security rules.”
Throughout my career I’ve been fascinated by security’s response to the people we’re trying to protect and to what lengths we go to ensure they’re doing “the right thing” to keep our organizations safe.
In so many cases, though, we missed the mark. We’d send out brochures, stickers, stress-relieving squeeze balls or security-themed mouse pads, all with our department mantra and messages. Desperately trying to convince our employees to think before they click, assess your surroundings before you open a door, or challenge someone (albeit politely) if you see they don’t have a badge.
What if we looked at our biggest “problem” as part of the solution?

What if security professionals start from a different place — one of respect and acknowledgement? What if we took a part of the ESRM (Enterprise Security Risk Management) philosophy, truly engaged our employees, and asked them to join the security team in creating a more resilient organization?
right training and executive support to help champion the security program without fear.
“What if we relied as much on our employees as our technology?”
There is a cultural change that is challenging security professionals to look at our employees as advocates for the security program. This approach asks security professionals to see their employees as the greatest strength of the corporate security program — empowering every employee to actively look for risks, report them to the security team and become ambassadors for the security program! This is a paradigm shift from our current perspective, but one we really should assess for our own organizations.
What if we changed our perspective and looked at our employees as an extension of the security team?
Concepts like Human Risk Management and recent research conducted on the human element of security are taking hold in organizations, with measured success. The concepts seem straightforward — create an environment where every employee in an enterprise receives the
If this looks so easy, why isn’t every company following this approach? First, we must move from the negative headspace of employees being “the weakest link” to becoming security program ambassadors. The organization must empower all employees to report risks they identify and even help develop mitigation strategies in collaboration with the security team. This approach is a supplement to ESRM and creates greater engagement while reinforcing the concept of Design Thinking.
We’d train our employees to look at a situation through our eyes, and then report their observations to the security team. The process takes more time, support and training — but the rewards can far outweigh the initial costs. Employees become fully engaged with the security program!
How successful would our security programs be if employees became true partners, not only taking our security training and following our policies and standards, but also evangelizing them? What if we relied as much on our employees as our technology? I’d sure like to find out! | CS
With security in constant flux, Global Security Exchange (GSX) is your stabilizing force. Powered by ASIS International, the premier association supporting the field, GSX is the industry’s most trusted annual event— and the cornerstone of security resilience and advancement worldwide.
To stay ready amid today’s evolving risks, you need to be here, this year and every year, in the center of it all:
• CPE-eligible education on current and emerging threats
• New technology to upgrade and expand your capabilities
• Impressive community with a pulse on your biggest challenges
REGISTER NOW AT GSX.ORG
GLOBALCLIMATECHANGE CYBER CRIMINALS SNOOPING HEALTHCARE FACILITIES ESPIONAGECYBERTERRORISM MALWARE SCHOOL GROUNDS SENSITIVE DATA CARTELS FLOODS EXPLOSIONS SCAMS DISEASES HIDDEN BACKDOOR PROGRAMS
SOCIAL MED HOSTILE GOVERNMENTS INSIDER THREAT SOCIAL ENGINEERING LOCAL DEVICE ACCESS PANDEMIC OUTBREAK CONDITION OF THE GLOBAL ECONOMY PROLIFERATIONINTELLECTUAL PROPERTY RANSOMWARE ASSAULT POLITICAL RISK AND VIOLENCE INFRASTRUCTURE
TAMPERING
TRANSNATIONAL CRIMES
UNPATCHED SECURITY VULNERABILITIES
EDUCATIONAL FACILITIES
RISK PERCEPTION DISASTER RISK REDUCTION ACTIVE ASSAILANT SECURITY POLICY MANAGEMENT

From securing storerooms, to protecting the perimeter. With a unified security system, the adage ‘the whole is greater than the sum of the parts’ still holds true.
by Pat Alvaro
Security is a big business, $8.6 billion industry in Canada. And as an ongoing concern for business owners and those tasked with managing the safety of others, it’s important to have a security system you can trust.
Access control continues to change, with the expanded use of technology making security management increasingly accessible. No longer do you carry around a big bunch of keys in your pocket. It’s now possible to unlock your home, workplace, car, or enter your gym using your smartphone, as well as remotely manage security for your property from anywhere in the world.
Many businesses struggle to bring together the separate strands of security, such as access control, alarms (intrusion
detection), video surveillance and perimeter protection. Yes, you might have all these systems in place, but imagine how powerful it would be if they were all working together in unison, to keep your staff or customers safe.
Think of access control as the heart of a modern-day security solution. The system still needs to provide the basic function of keeping unauthorized people out. But it should also be flexible so you can easily adapt to changes in the business environment, while allowing for future growth.
Unfortunately, many legacy security systems rely on outdated technology that leaves businesses vulnerable, and don’t offer the advantages of today’s increasingly interconnected world. Advancements in access control have led to the adoption of technology such as secure, encrypted protocols like OSDP (Open Supervised Device Protocol), MIFARE DESFire smart card technology, and mobile or biometric credentials. By themselves, they are great technologies, but when used as part of a unified security package, there are exponential benefits.
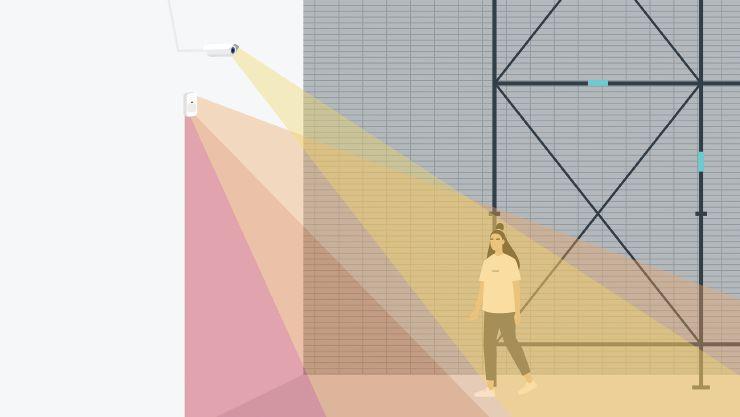
If access control is at the heart of security, then intrusion detection and perimeter protection are the first line of defence. Times have changed since a security fence and floodlight alone could be considered effective deterrents. While alarms and passive infrared (PIR) motion detectors are commonplace, you should also be demanding native intrusion detection as part of your platform.
The digital transformation of video surveillance has reduced costs and uptake has increased so much that it’s now a nonnegotiable in most installations. Other technologies such as LiDAR or fibre optics have also led to great steps forward in functionality and accuracy of perimeter and approach systems.
It’s easy to tie in perimeter detection systems with your security platform at a low level. But the real value comes with a high-level integration (HLI) such as our OPTEX Redwall integration with Protege GX, where users can monitor and receive alarms from the OPTEX units in the same interface as the rest of their security solution. It can save costs as installers don’t have to run additional cabling.
Adding video surveillance in the mix, with a VMS (video management systems) integration extends the capabilities of intrusion or perimeter solutions. The ability to control cameras, and view live and historical video footage from a single interface gives security staff immediate, actionable information.
Other integrations can add even more value and flexibility to your security solution. It’s not just the traditional uses such as elevators, wireless locking, or biometrics either. Custom integration tools and APIs allow for any number of external elements to exist as part of your security ecosystem and complement your offering.
You can reduce management time and create efficiencies with a secure data sync, which combines the power of enterprise level integrated access control with external data sources –such as human resource systems or student databases. Or use ICT’s SOAP Web Service to develop a custom interface that is tailored to your exact needs.
Or you could have use for additional measures such as Telaeris’ XPressEntry handheld reader which provides an emergency mustering solution that integrates with your access control system to quickly verify who is safe at evacuation sites, assisting security and emergency personnel.
A unified solution like ICT’s Protege platform enables simple, endto-end management. Features such as status pages, user groups, and area counting are standard, and built-in door interlocking, anti-passback, and other enhanced functionality are also included creating a single, cohesive offering.
Native intrusion and integrated IP reporting on-board all ICT system controllers also make offsite monitoring a breeze. So if an intruder alarm or a problem with the fire panel is triggered, the monitoring station alerts the appropriate authorities so a response can be initiated. Additionally, Protege GX offers email on events, for customized notifications that are sent automatically, direct to whoever needs to act.
Modern access control doesn’t just keep your property and people safe. All these capabilities mean staff get ease-of-use, while system operators get overview and control from one easy interface. As a business owner, the solution brings cost savings and efficiencies while providing a higher level of security and true peace of mind.
It’s simple to link access control with intrusion detection and building automation with a unified system like Protege. And when you include integrations with the likes of perimeter protection, video surveillance, or wireless locking, you soon unlock the full value of your access control platform.
ICT has been leading the way with integrated solutions for almost 20 years (in fact, it’s even in our name – Integrated Control Technology). Designed, engineered, and manufactured in New Zealand, and trusted by tens of thousands of businesses across Canada and around the world. To find out how ICT’s unified solution could add value to your business, visit info.ict. co/can-sec-access
Pat Alvaro is Country Manager, Canada at ICT (www.ict.co)

By Winston Stewart
When it comes to retail and office space in the postCOVID era, it won’t be business as usual again.
W hile we may do away with masks, and see people cautiously return to public spaces, the pandemic has forever changed the way we work, shop, and live our lives.
This means owners of commercial spaces are faced with an avalanche of change management issues. Reimagined spaces, new technologies, health safeguards, and the hybrid workplace. There’s so much you may be grappling with!
It might seem to follow that with fewer people in your stores, restaurants, offices or service centres on a daily basis, your security services and guards may also be scaled back, right? Just like desks and square footage? Unfortunately, this is not the case and a very dangerous assumption.
With fewer employees and customers on site at once and changing tenant expectations, now is the time to rethink and reconfigure — not scale back — your security systems on site.
In securing the office or retail space of tomorrow, technology will lead the way. Live security guards will remain vital — especially with lower numbers of people on your sites and more/different risks to your premises, and the personal safety of customers and workers on site moving between less populated spaces of buildings/malls and retail centres.
While the number of guards on

site may possibly be reduced, more secondary security systems must now be in place for office and retail site owners to have complete peace of mind. Security technology systems that commercial site owners should be investing in include:
• Virtual concierge — cameras that conduct exterior patrols that a live officer can monitor from the central desk
• Upgraded CCTV systems and recording equipment throughout the site
• Access control systems (with browser and mobile access)
• Glass break, carbon monoxide and motion detectors
• New card access systems to control traffic in different areas of the building
With all this new tech comes a need for a new breed of security guard. No longer does the stereotype of the old guard sitting at the desk, checking badges and greeting visitors, apply. The security guards of tomorrow will need to be crosstrained, tech-savvy and aware of the threats present in the postCOVID world. They will also have to be up to speed on new health and safety
“Your guard will be the first face of your facility.”
regulations. And of course, they must confidently exude an aura of vigilance. This means even greater care must be taken when selecting your guards. Don’t risk putting any individual on watch at your building who does not have the right character, confidence or mandatory training in the latest technology and safety policies. They must be able to proficiently use electronic systems and to navigate building security systems with ease. Trained guards, familiar with key software and savvy in security technology, should be a mandatory prerequisite.
In addition to being tech-savvy, the commercial building guard of the future needs to possess excellent people and customer service skills. As the nature of building use itself changes, the ability to liaise with employees, shoppers and visitors in a variety of situations is becoming more of a priority. Your commercial building itself may be in the midst of a major transformation. Multiplexes are on the rise: buildings or complexes where people are coming not just
for work, but for shopping, dining, exercise and other purposes. Security guards protecting these new multi-use facilities will need to liaise with the public in a myriad of ways, from providing friendly customer service and vital information to emergency response.
More than ever, your guard will be the first face of your facility — playing an essential role in “public perception.” They will need to respond quickly and professionally when someone requires help with their shopping bag, when there is a slip and fall in the parking lot but also when there is a crime, a serious mechanical failure or suspicious activity.
If a guard does not have the right combination of tech skills, people savvy, diligence
(“duty of care”), and site-specific routines and protocols, you may be exposing your building to costly liabilities.
Especially in the post-COVID era, most sites have their own expanded set of rules and health and safety protocols. Each guard needs to be brought up to speed and trained on the requirements and site protocols of each specific location before they arrive for duty.
Here’s a quick rundown of key duties for security guards in the commercial facility of tomorrow:
• Enforcing new safety regulations
• Using customer service skills to assist visitors, workers, shoppers and tenants, especially in multi-use facilities
• Overseeing new fire safety roles to safeguard vacant or less traveled areas
• Expanding patrols and monitoring of more extensive spaces, including car



parking, open-access sites and queuing systems
• Monitoring, programming and sometimes installing new technology security systems
• Applying higher levels of crowd control and traffic management
• Assisting customers and workers in navigating new layouts and protocols
• Overseeing cameras and conducting mobile patrols
• Enforcing processes by screening visitors What steps can you take to prepare for the future of commercial security? The best way to begin is with a comprehensive security assessment of your facility by a trusted security provider. Whether you own a store, restaurant, office building or multi-use facility, no two locations are the same, and a custom approach to your security needs is vital. | CS


In an ever-escalating malware war, the solution lies in effective education.
By Madalene Arias
There is no single or short answer as to what sort of training techniques are most effective in combatting cyber-attacks.
However, it is clear that cyber awareness education must evolve as quickly as cyber criminals can craft a new attack.
“The majority of cyber attacks, unfortunately, start with phishing,” says Tony Anscombe, chief security evangelist at ESET.
He holds the position that remote and hybrid work models have contributed to increased cyber risks, simply because people are more likely to click on phishing emails in the comfort of their own homes as opposed to an office setting with potential witnesses.
Eric Skinner, vice-president of market strategy and corporate development at Trend Micro, adds that remote work meant corporations lost network visibility of their employees. In some cases, corporations have also lost visibility to the very computers employees use as some chose to work on personal devices.
“The saving grace with respect to email is that the corporate email system is still centralized,” says Skinner.
The great resignation has also contributed to increased vulnerability in the cyberspace, according to Ernst & Young Canada’s cybersecurity leader Yogen Appalraju.
He says that for the first time, many people left roles in the
finance sector, which is not known to have particularly high turnover rates. This meant people resigned from their positions at places like banks — institutions that have traditionally invested heavily into fraud prevention, phishing awareness and cybersecurity training.
“If I think about what is the most fundamental issue companies are facing today, it’s that if you lose some of your skilled people, you can’t train the new entrants coming in,” says Appalraju, explaining that organizations sometimes rely on company veterans to school new-hires in cybersecurity best practices. When staff with senior-
“We really have to expand beyond thinking that this is primarily the employee’s job to do the right thing.”
— Eric Skinner, Trend Micro
ity leave, it creates a knowledge gap.
As Anscombe describes, many cyber risk insurance firms now require companies to conduct training around phishing and cybersecurity.
However, the type of training that has shown to prevent cyber attacks from entering corporate networks begins with providing staff with a clear understanding of how phishing works.
Content falsely implied in many phishing attempts relates to contemporary events in the world. For example, during the onset of the coronavirus pandemic, many phishing emails contained messages about masks and PPE. More recent phishing attempts have used the conflict in Ukraine to reel in clicks in those moments before people stop to think.
Though more and more companies have taken measures to ensure their staff receive training, Anscombe says that educating workers just to meet the minimum requirements of insurance firms is insufficient.
“It’s typically on an annual basis. I personally think it should be done far more frequently,” he says.
For Anscombe, cybertraining should be more of an ongoing, constant element in the workplace. Phishing attempts that land in the inbox of one staff member for instance, should be shared with all other members of the organization as an example of a live, current phishing attempt.
“I think it’s important that teachings make sure that people understand what phishing is when it’s happening,” says Anscombe. “It’s not, ‘Next year, I’m going to show you some of these examples that are from last year.’”
Appalraju also states that training must be ongoing as phishing attacks are becoming more sophisticated. Fortunately, training has become commercially available for companies to purchase and provide to their staff.
Imparting cybersecurity education is only half of the equation. Appalraju says companies must test their training through mock attempts to see whether members of their organization still click on simulated phishing.
Skinner recalls a time in cyber history when phishing emails were detected almost effortlessly. They often contained grammatical errors and poor spelling, and this made it relatively easy for employees to discern.
Over the years, attackers have accounted for the details that might make their messages stand out from the rest. The spelling and grammatical errors are gone, and they now use better graphics. They have compromised internal email addresses, enabling them to pose as CFOs or other executive roles within a company.
Skinner says this increased sophistication in the style of attacks has brought on a wave of new technologies that is focused on fraud detection.
Trend Micro has deployed an AI-based technology to conduct writing style analysis. “So, we can figure out whether this is how the CFO really writes, or does this claim to come from the CFO but does not match the writing style.”
While training is an important piece of a company’s cybersecurity strategy, reliance on training places too much of an onus on employees, according to Skinner.
Since cyber attacks are ultimately financially-motivated, Skinner advises financial teams within a company look at their internal processes. Even if a compromised business email leads a staff member to pay an invoice, there should be enough checks and balances within the execution of that decision that prevent funds from ever leaving the company.
Further to this, as it is people in senior management or executive roles who often become the targets of phishing and false invoices, companies can and should do much more than simply take C-suite employees through a simulation. Skinner said IT and cyber staff can sit down with executives and have more personalized conversations that teach subtle clues in phishing attempts.
“We really have to expand beyond thinking that this is primarily the employee’s job to do the right thing and recognize these emails,” says Skinner. “In the cybersecurity community, whether we’re vendors or practitioners, we have to step up and help make it way more safe for employees to click on things and messages instead of blaming employees.”


One of the world’s experts in malware research remembers an era during which companies followed policies that terminated employees who caught viruses on their computers.
Rob Slade, an author, senior instructor and course developer with (ISC)2, adds that environments that cast blame, as Skinner describes, might only cause people to hide an error.
“Punishment is not the answer. Education is the answer,” he says.
When it comes to protecting an organization against a more sophisticated level of attack like ransomware, the best source of protection is a highly skilled cybersecurity department. As Appalraju says, ransomware attacks are not solved intuitively.
“The type of cyber team you have internally, or the type of support you are getting and procuring externally makes all the difference in the world,” says Appalraju.
Companies have caught on in the last few years, he adds. Clients of E&Y, for example, are placing more emphasis on elevating their cybersecurity teams to a higher level. They are also trying to hire candidates who have already acquired cybersecurity training and have demonstrated skills in that area.
Appalraju also suggests corpor-
ate executives take advantage of the many masters level cyber programs and MBAs now offered at universities to become better equipped as leaders.
“Most organizations should encourage that, especially the high performers who are well-positioned for management roles in the future. Train them early on by sending them
done and how that can be transferred,” he says.
After more than four decades in the industry, Slade has grown tired of hearing that companies cannot find trained people to hire for cybersecurity roles.
He believes the problem is in the approach recruiters take when they revise resumes or profiles on
“Punishment is not the answer. Education is the answer.”
— Rob Slade, (ISC)2
to some of these formal programs,” he says.
Where internal cyber teams are concerned, training continues to be an ongoing challenge for all organizations. As Appalraju says, more complex technology environments mean greater opportunities for bad actors to break in due to increased exposure.
Being extra judicious about who gets hired is a cybersecurity measure Slade can get behind, although he doesn’t think recruiters are doing a good job of this.
“When you do understand the technology, you understand what skills are involved in what they have
LinkedIn. They’re looking for what a potential candidate has already done instead of considering the technology and software they’ve already learned to use.
Instead, recruiters who understand the technology may be able to determine how this knowledge can be applied in a new role. Slade says incorporating this approach to hiring practices could prevent turnover in the long-term.
“If you can see that they’ve worked with three different compatible firewalls in the past, then hire that person and hand them the manual. In two days you’ve got somebody who’s pretty much up to speed.” | CS





Most of us fit the definition of “lone worker” for at least part of our working lives
By Neil Sutton
For many, the term lone worker conjures images of a security guard patrolling a building late at night, or a home healthcare professional out and about on client visits. Lone workers might be people isolated for long stretches of time, or interacting with strangers in unfamiliar locations as a direct consequence of their job or profession.
B ut the whole notion is undergoing some scrutiny, with many of the assumptions around “lone work” being reassessed, and the definition widening to include more types of jobs and scenarios.
S ome of this is a bi -product of the pandemic and its dramatic effect on workplace norms. Huge swathes of the workforce found themselves essentially working alone for the first time in their careers, sent home from their offices to set up makeshift workspaces in bedrooms and basements. But many of us were lone workers well before we knew what COVID-19 was, if only for limited periods. Work-related travel and hotel stays, for
example, could constitute working alone.
Matt Smitheman is a senior solutions consultant at Interface Systems. The company’s line of security products and services includes lone worker solutions such as two-way audio and video communications. He says that there can clearly be occasions or times during the work day that transform a team employee into a lone one. Retail is a particularly keen example of this.
“You may have three or four people in your location, but if you have to send somebody from your location to a remote stockroom to pull stock, that person is a lone worker for that period of time,” explains Smitheman.
“ We’ve been supporting lone workers for years and years,” he says. “In the jewelry industry, we do this for openings and closings. Traditionally in retail, one of the most vulnerable points is opening and closing, where you’re not inside the four walls of protection yet.”
The pandemic increased the degree to which a retail employee might spend time alone. “When COVID came, there was a
huge surge in curbside delivery,” says Smitheman, as retail staff “free-roamed to various places in the mall or even completely off-premise.”
Sunita Mani, Interface’s senior VP of marketing, also notes high turnover rates in retail and restaurant positions have left some employers short-staffed, increasingly the likelihood that employees find themselves alone more frequently.
Brendon Cook, chief partnership officer at Calgary-based Blackline Safety, says the pandemic has brought more awareness to the lone worker field but the trend towards a better understanding of workplace risk was already underway. The company produces monitoring tools and wearable devices for workers in industrial settings, including gas detection technology through its G7 product line. Cook notes that educating end users on the effective use of these tools is key when it comes to their safety.
“ We have a very strong focus on learning within our own business, but also how we go to market, because we’re selling a sophisticated product to industrial customers,” he says. “We have to make sure that the employees within those client businesses are trained on how these products are different from what they may have used in the past.”
Tracy Reinhold, chief security officer for Everbridge, a provider of mass communications, crisis management and security solutions, says that the pandemic has certainly revised the definition of what constitutes a lone worker, but it has also drawn more attention to the concept of “duty of care” of an employer for its employees.
“ Now we have a whole plethora of employees around the world who are no longer coming to the office. Does our duty of care extend to the remote worker? I would argue that it does. One of the ways that we can do that is through the advance of technology,” he says.
Geo-fencing locations and overlaying real-time threat information can allow an organization to stay connected with its employees, he says. A threat could be an impending weather system, for example, that might have a direct impact
on employee safety. “ It should be the employee’s expectation that the company cares about their welfare when they are working for the organization — even if they are working remote,” he says.
Remote could mean “out of office,” or could also mean an overseas business trip, making that an employee a lone worker in a foreign location, adds Reinhold. Everbridge introduced a travel risk management solution last November following its acquisition of U.K.-based Anvil Group and its Riskmatics platform. Anvil customers collectively monitor more than 75 million trips in an average year, almost seven per cent of them to high-risk destinations, states the company’s website.
The lone worker market continues to grow, according to analyst firm Berg Insight, which notes in a 2021 report a var-
iety of contributing factors including occupational safety regulations, increasing employee insurance costs and a focus on protecting brand reputation.
The market, once driven by public sector customers, is also opening up to more private sector opportunities. Berg Insight estimates the North American lone worker market was 320,000 users of connected safety solutions at the end of 2020 and is expected to expand to 605,000 users at the end of 2025.
“ It’s developing very quickly,” says Smitheman, noting the rise in interest. “We’re constantly getting calls from our customer base and new customers saying, ‘Have you thought about this? Can you do this with that particular device?’
“ The market has more than doubled, from what we’re seeing. If there’s any indication from what we’re seeing right now, I think that’s going to happen again.” | CS


The CM-336 Series of battery-operated 915MHz wireless switches joins Camden’s SureWave line of touchless switches and features a Lazerpoint RF transmitter. The new switch replaces Camden’s CM-330 models and delivers improved performance and up to four years of battery life based on 100 activations per day. The CM-336 switches offer a wireless range of up to 300 feet. They’re available in a selection of narrow, square and round faceplates and come with retrofit mounting box conversion kits. www.camdencontrols.com

iDter can be used as a standalone security system or to augment guard services with integrated technology at the protected premises. Engineered with Niō guardian nodes and protector technology, it features artificial intelligence deep-learning, cloud video storage and video verified monitoring with dispatch to PSAP. Niō nodes are positioned around the protected premises to detect intrusion with a 4K HD resolution camera with wide-angle lens, multiple motion detectors, omni-directional microphone and quad-core intelligence. Intrusion events are detected and immediately verified with video alert recordings sent to iPhone, Android phone or iPad. Events are monitored in real-time to ensure deterrence actions were successful, and if not, a video verified alarm is sent to a UL- Listed, Five-Diamond Certified central station for dispatch of authorities through 911 operators. www.idter.com

The SR-150 radar is suited for smaller sites looking to implement enhanced radar detection and larger locations that need to fill a gap to address a dead zone in their perimeter protection. The SR-150 provides 150 meters of coverage, including up to 30 degrees of elevation coverage and 120 degrees of azimuth coverage. Using C-band frequency, the radar consumes less power than other radar detection technology and combines superior range resolution (less than 1 meter) and an angle resolution lower than 0.7° allowing for detection of threats in the most challenging environments. By combining the Magos MASS solution with AI, the SR-150 reduces nuisance and false alarms. The SR-150 provides video-based object classification, including people, vehicles and boats, and the ability to accurately filter out irrelevant alerts on wildlife and fauna, without compromising threat detection capabilities.
www.magosystems.com
Genetec


The Synergis Cloud Link PoE-enabled IoT gateway for access control provides a gateway to a cloud or hybrid deployment. Synergis Cloud Link’s open architecture allows organizations to leverage their current access control infrastructure and upgrade to a secure IP-based solution. Synergis Cloud Link provides a more efficient approach to multi-site deployments and replaces the need for servers, according to Genetec. The Synergis Cloud Link IoT gateway has embedded functionalities that keep an organization’s access control running even when connection to the server is down. Synergis Cloud Link features enhanced cybersecurity such as encrypted user data, Secure Boot, and an EAL6+ industry gold standard Secure Element that stores cryptographic elements. The device is compatible with non-proprietary access control modules. A single Synergis Cloud Link device can support up to 256 readers and electronic locks, 600,000 cardholders, 150,000 offline events, as well as monitor hundreds of zones and alarms.
www.genetec.com

The BEST Precision Visual Indicator 2110 is a code compliant safe egress with visual and directional indicators for security lockdown. This panic device incorporates the ANSI “10” function, also referred to as the “Intruder Function,” with new lock/unlock status. A directional indicator is integrated into the housing and contains reflective materials that may be seen in low light conditions. It also features an embossed directional indicator that offers quarter-turn (90°) activation to enable faster lock down. The BEST Precision Visual Indicator 2110 is available in a variety of finishes, including 630 Satin Stainless Steel and 630AM Satin Stainless Steel with UltraShield Antimicrobial Coating. www.bestaccess.com


Security Canada Central
Toronto, Ontario
October 19 – 20, 2022
Join us at Security Canada Central, the biggest and most important security show in Canada. The people who define our national security industry are here, and you should be too. Thousands of professionals from all sectors come here to network, learn and check out the latest security technology products and services.

Commissionaires offers a complete suite of services including threat-risk assessments, monitoring and response, mobile patrol, guarding and digital fingerprinting.