











The upcoming release of Avigilon Control Center (ACC) 7, our latest and most advanced version of ACC™ video management software, is designed to revolutionize how users interact with and gain situational awareness from their video surveillance systems.
Introducing Focus of Attention — a cutting-edge user interface for live video monitoring that leverages AI and video analytics technologies to determine what information is important and should be presented to security operators.
Using our deep learning video analytics and Unusual Motion Detection technologies, ACC 7 software is designed to provide customers with actionable information to help ensure critical events don’t go unnoticed.

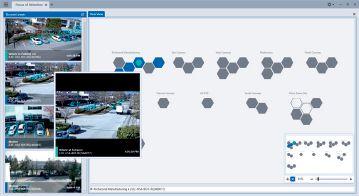
ACC 7 software introduces a new theme with colors specifically chosen to reduce eye strain and improve user experience in dark environments, such as video surveillance control rooms.

By Neil Sutton

hen you launch a new feature, contest or event for a magazine, you tend to approach it with cautious optimism.
At least, that’s usually my take. In all my years of developing, supporting or implementing surveys, events, contests — basically anything that requires audience participation — I never really know how they will be received until the rubber hits the road.
When the Canadian Security team planned a Top 10 Under 40 feature this year, I allowed myself a more sanguine outlook than usual. Our audience has always been loyal and it’s been my experience that the security management community increasingly values young talent and fresh perspectives. I was right — the submissions we received were detailed and excellent.
“It

Group Publisher Paul Grossinger pgrossinger@annexbusinessmedia.com
Account Manager
Adnan Khan akhan@annexbusinessmedia.com
Editor Neil Sutton nsutton@annexbusinessmedia.com
Associate Editor Will Mazgay wmazgay@annexbusinessmedia.com
Art Director Graham Jeffrey gjeffrey@annexbusinessmedia.com

Account Coordinator
Kim Rossiter krossiter@annexbusinessmedia.com
Circulation Manager
Aashish Sharma
asharma@annexbusinessmedia.com Tel: 416-442-5600 ext. 5206
COO Scott Jamieson sjamieson@annexbusinessmedia.com
President & CEO Mike Fredericks
Editorial and Sales Office
111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1 (416) 442-5600 • Fax (416) 442-2230 Web Site: www.canadiansecuritymag.com
was the mentorship that caught
What struck me the most about the submissions to Top 10 Under 40 wasn’t that the candidates had achieved positions of seniority or authority early in their careers. It wasn’t even that many of them are highly decorated with degrees, certifications and accolades. While those accomplishments are certainly impressive, it was the mentorship piece that caught my eye — particularly the nominations that were submitted by people who counted the Top 10 candidate as their personal mentor.
my eye.”
A resumé will tell you a lot about a person, but a relatable personal experience will tell you a lot more. When someone, well on their way to climbing up the corporate ladder, goes out of their way to help one of their peers or juniors realize their own ambitions, it says a lot about their character. It also says a lot about their qualifications as a leader. The best bosses I have had in my career also know how to take a position of mentorship — equal parts encouragement and constructive advice. (That second one is notoriously difficult to deliver.)
Reading through the submissions, I was reminded of a recent presentation given by another leader, Rosanne Manghisi, senior vice-president at SOS Security and a former police officer. Manghisi, speaking at the ASIS Toronto Women in Security event last year, encouraged security professionals to “lift as they climb” — strive for success but remember to help develop the talent of others around you.
Our Top 10 Under 40 is timely, since it coincides with the launch of ASIS International’s Associate Protection Professional certification — a brand new designation that allows young security professionals, or those who are new to security, to earn a qualification earlier in their careers.
Michael Brzozowski writes about the new APP on p. 8 of this issue. Brzozowski was also one of the initial architects of the APP, helping to conceptualize it and steer it through completion. This is one of the major reasons he received our Emerging Leader award last year at our CS@40 event.
On a related note, one of our Top 10 winners, Richard Strickler, was among the first to take the APP beta test. He passed, of course.

Canadian Security is the key publication for professional security management in Canada, providing balanced editorial on issues relevant to end users across all industry sectors. Editorial content may, at times, be viewed as controversial but at all times serves to inform and educate readers on topics relevant to their individual and collective growth and interests.
Canadian Security is published four times per year by Annex Business Media.
Publication Mail Agreement #40065710
Printed in Canada I.S.S.N. 0709-3403
Subscription Rates Canada: 1 Year $42.00 + HST; U.S.A. (payable in US dollars): 1 Year $72.00; International (payable in US dollars): 1
Circulation
Anita Singh asingh@annexbusinessmedia.com Tel: 416-510-5189 Fax: 416-510-6875 or 416-442-2191
111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1
Annex Privacy Officer Privacy@annexbusinessmedia.com Tel: 800-668-2384
The contents of Canadian Security are copyright by ©2019 Annex Publishing & Printing Inc. and may not be reproduced in whole or part without written consent. Annex Business Media disclaims any warranty as to the accuracy, completeness or currency of the contents of this publication and disclaims all liability in respect of the results of any action taken or not taken in reliance upon information in this publication.









































































Formany people carrying highly sensitive business, legal or political information, surrendering information to international border officers just isn’t an option.
Erinn Atwater, PhD student and researcher in Computer Science at the University of Waterloo, along with a colleague, Ian Goldberg, has developed an encryption app to help protect sensitive digital data, called “Shatter Secrets.”
Prior to travelling, a “secret,” such as an encryption key to a device or a password to a cloud service, is split into pieces or “shares” and those are sent to one or more friends of a user, or “secret keepers,” at their destination — over a secure communication platform. The user must then visit those secret keepers in-person when they arrive at their destination to retrieve the pieces of their key or password and decrypt their secret, ultimately regaining access to their device or online information.
The idea behind this is simple: the key or password to the user’s device or information isn’t available to them while they’re travelling. As a result, they can’t comply with a border agent’s request to provide access to personal data.
Atwater said of her app, “We wanted to make it possible for you to be completely honest and forthright with the border agents that you are unable to access the data that they’re asking for.” She continues, “We don’t advocate lying to border agents. We don’t advocate breaking any laws, and the system doesn’t require you to lie.”
While users are technically unable to comply with border agents, locking them out of information they want access to can still cause problems. Atwater said officials may confiscate the device in question, or turn the user away at the border. For most individuals, these are dire scenarios, but she explained that for Shatter Secrets’ target demographic, surrendering sensitive information is much worse.
“Shatter Secrets is not meant for protecting your vacation photos,” she said. “If they (border agents) don’t want you crossing the border without giving them access to the data you have, this is for people who would rather not cross the border at all in that case.”
Once a secret is split up, it can’t be retrieved remotely. When a user successfully crosses the border, they need to physically retrieve the shares by tapping their device against their secret keeper’s device, using a close-range electronic communication protocol called near field communication (NFC) — if the secret is access to a laptop or phone, a secondary device is usually needed to retrieve the shares.
Atwater said of the NFC protocol, “if it works over the Internet, if you can get your private data back remotely, it opens up a lot of potential for software vulnerabilities, it opens up possibilities for social engineering.”
She said another worry was that “the border agent would call up your friend, or even have you call them and ask them

to read out the secret data over the phone.” Atwater said the data being locked by NFC makes it very difficult for all but the most tech-savvy secret keepers to access, and a white paper on the app explains that encrypted shares are wiped from secret keepers’ devices once they have been successfully delivered to the original user.
One potential issue is whether this technology might be used by nefarious actors seeking to harm innocent people. To this Atwater said, “most terrorists we find aren’t actually relying on consumer devices to give them encryption; they have their own programmers.”
Right now, Shatter Secrets is available as a prototype Android app, which Atwater cautioned not to use yet because it requires more scrutiny and a security audit. But, “if you’re good at Android development you can download it and play with it,” she said.
Atwater said she is looking to move the project from university research to “a fully-fledged open source free app,” (for both Android and iOS) developed by her Vancouver-based non-profit, Open Privacy. She continued, “We’re in the process of trying to obtain funding to do that.”
Will Mazgay
May 28-31, 2019
CHRNet Annual Symposium Winnipeg, Man. www.crhnet.ca
May 29, 2019
Security Canada Alberta Edmonton, Alta. www.securitycanada.com
June 13, 2019
Security Summit Canada Toronto, Ont. www.securitysummitcanada.com
June 18-19, 2019
Grower Day
St. Catherines, Ont. www.growerday.com
June 19, 2019
Security Canada West Richmond, B.C. www.securitycanada.com
June 25- 29, 2019
IACLEA Annual Conference & Exhibition Vancouver, B.C. www.iaclea.org
July 15, 2019
15th Annual IAHSS Ontario Chapter Golf Challenge Richmond Hill, Ont. www.iahss.org
September 8-12, 2019 GSX Chicago, Ill. www.gsx.org
September 11, 2019
Security Canada Atlantic Moncton, N.B. www.securitycanada.com
October 3, 2019
CS Honours Toronto, Ont. www.canadiansecuritymag.com
October 7-11, 2019
Sector Toronto, Ont. www.sector.ca
October 23-24, 2019
Security Canada Central Toronto, Ont. www.securitycanada.com
Softwarevirtualization company
VMware recently announced that its cloud platform is now available on Amazon Web Services (AWS) in Canada, opening up new opportunities for Canadian customers to move data to the cloud.
The companies, along with IT services partner Scalar Decisions, made the joint announcement in Toronto recently via a press event and roundtable at AWS’s downtown office facilities.
“By bringing that exact same platform that Canadian customers are using on premise to the AWS cloud in Canada, it’s a really fast migration opportunity for Canadian customers to move towards the cloud,” said Peter Near, national director, solution engineering, VMware.
the IT talent gap, said Sean Forkan, vicepresident and country manager, Canada, VMware.
“One of things that we see as a wonderful opportunity for both public and private sector is you get to take advantage of world-class systems and processes in the AWS environment and help bridge some of that talent gap that we’re seeing here today,” he said.

VMware on AWS has previously been available in the U.S., but this is the first offering in Canada.
Near said that Canada is behind in cloud adoption compared to international peers. “A lot of that had to do with regulation like the Patriot Act,” he explained.
Also, there were comparatively fewer cloud providers in Canada. AWS first made its services available in Canada in 2016, which, said Near, sparked a resurgence of Canadian interest in cloud adoption. He referred to 2019 as potentially a “leapfrog” year for Canadian organizations — an opportunity to catch up or jump ahead.
“This particular offering is now a catalyst for getting Canadian organizations, private and public, to the cloud, so they can take advantage of that innovation,” he said.
Cloud is a potential solution to common problems facing Canadian businesses — data storage capacity and
The skills gap is of particular concern to small and mid-size companies, added Forkan. Cloud-based services open up a world of options that wouldn’t otherwise be available to them, he argued.
Stewart Beak, director of product services, Scalar Decisions, joked that he’d spent the first part of his career helping clients move data into the data centre — now he’s helping them move it out.
“Customers are looking to get out of the data centre business,” he said.
The view of the cloud has shifted quite dramatically in recent years, according to Eric Gales, country manager, Amazon Web Services Canada.
“As recently as three years ago, I was making the case for the cloud. I was fielding lots of questions around security and privacy and those sorts of things. Largely, I don’t have those discussions [now]. We’ve moved past those discussions. Most customers are interested in how [to move to the cloud] and where to start,” he said.
“I think the level of comfort that customers have that the cloud is part of their future is very high now. Between our two companies [Amazon and VMware], our job is to identify what is the right strategy for them.”
— Neil Sutton

For security professionals, to demonstrate proficiency in our craft, the trio of ASIS certifications (CPP, PSP, PCI) are the global standard.
These certifications were purpose built with seasoned professionals in mind to demonstrate a senior level of expertise. However, with the influx of young professionals, the certification path for these future leaders in the security industry has been delayed.
To address this need, ASIS International has developed an entry-level certification for security professionals: Associate Protection Professional (APP). Developed for those with less practical experience, the APP

is specifically designed for security professionals working in tactical and supervisory careers, as well as for those aspiring to future managerial and executive positions. The APP can help to build a foundation for a career in security and risk management through this new ASIS Certification pathway to the CPP, PSP, and PCI certifications.
In 2016, as co-chairs of the newlyformed ASIS International Young Professionals Council, Angela Osborne and I discussed the idea of promoting a new designation geared for YPs; we called it the ELiS (Emerging Leader in Security). We put forward a proposal to Gayle Rosnick (Director of Certification at ASIS International), and Gayle went to work. Within a few weeks

Angela, Gayle and I received a Saturday morning e-mail from Peter O’Neil (CEO of ASIS International) endorsing the idea, and the ball was rolling.
Over the next two years, this new certification idea evolved and gained traction. In early 2017, the ASIS Board of Directors formally approved a market assessment study to validate the viability of the new security management entry-level certification. In July 2017, we got our answer: the job analysis study confirmed that there was significant support for introducing a new certification.
The hard work, as I came to learn, had just started. Consistent with industry best practices and ANSI accreditation standards, a job analysis study was the next step.
On a frigid weekend in January 2018, I got the opportunity to spend three days with Gayle and her outstanding team (Janine OneySmith and Lisa Currie) as an observer on behalf of the ASIS Professional Certification Board. Gayle invited 12 eager security and risk professionals from all over the world to define the test domains, along with the major tasks performed by an aspiring APP, and the knowledge needed for competent performance. Finally, Gayle brought in Cameron Kayfish from Prometric to keep us all in line and provide us with guidance on the domain development process.
The work that was done by the ASIS Certification team, Cameron, and most notably the volunteers, was incorporated into a survey distributed to a global mailing list of security professionals. Upon completion of the
survey, we reconvened at ASIS HQ this past summer for another weekend and had the opportunity to review the survey results. As it turned out, the hard work had paid off. The domains that were defined in the job analysis study (Security Fundamentals, Business Operations, Risk Management and Response Management) were spot on.
So here we are, ASIS now has four certifications that are the global standard for security professionals, and a defined certification path for those future leaders of our industry.
To close, Angela and I stepped down as co-chairs of the Young Professionals council in 2019. However, as we transition out, we want to share how proud we are, both collectively and on behalf of the Council, to finally bring this much-needed certification to fruition. It has been a long journey and there are many uncredited individual efforts that deserve to be recognized. Above all, we thank the many dedicated professionals who generously contributed their time and expertise, as over three hundred individuals participated in different phases of the development of the APP. Secondly, Angela herself for her leadership as the co-chair of the YP Council over the past three years. I have had unique visibility into the effort and passion she brings to the Council and to ASIS as a whole. At ASIS HQ: Gayle Rosnick (and her team at the Certification department), and Peter O’Neil for immediately recognizing the potential and importance of this new certification. To my colleagues at the Professional Certification Board, both past and present, for their collective engagement and support throughout this development process. I truly have a new appreciation for the value that we all bring as a collective.
Michael Brzozowski is a member of ASIS International’s Professional Certification Board and a former co-chair of ASIS’s Young Professionals Committee.



STANLEY Security provides customized security solutions for a variety of industries including schools, hospitals, retail stores, banks, commercial buildings, distribution centers, and more. Based on extensive experience protecting local, regional and national businesses, STANLEY understands the security needs and challenges you face on a daily basis. This in-depth understanding allows us to work with you to design a security solution that will help you protect your employees, assets, facility and ultimately your bottom line.
STANLEY offers one of the most comprehensive portfolios of products and services available—all tailored to fit your security needs, large or small.


Communicating risk to the C-suite does not occur in a vacuum
Communicating risk is problematic. A solid security risk assessment is inherently detailed and comprehensive. It must be presented in a digestible manner to ensure the successful implementation of its recommendations.
The challenge today, when everyone is inundated with media images of protests, or sound bites about terrorist attacks, is to clearly explain “risks” about business operations, facility integrity or staff safety in a way that corporate leadership can understand for due diligence.
categories: human, political, operational, reputational, procedural, financial or technical. In doing so, it is essential to understand the corporate risk appetite — is it adverse, neutral, calculating or seeking?
“Be ready to adjust your own analysis frequently as the situation evolves.”
Articulate the risk mitigation trade-offs: ranging from avoidance to assumption, limitation or transference. Translate risk management policies and approaches into day-to-day advice and guidance.
Unfortunately, decision makers often react to detailed threat-risk assessment (TRA) documents negatively as a needlessly complex and inflexible process. The challenge for security professionals is to overcome this perception and educate leaders to view TRAs as part of the underlying strength of the corporation.
To start with, right-sizing a risk methodology to fit each corporation is essential. A scaled, flexible risk assessment process should provide timely and accurate recommendations. Leaders need to be able to understand and absorb the key takeaways. These key results must be communicated in clear and concise business terms to allow leaders to quickly gauge the impact of risk and make informed decisions.
The security professional is instrumental in facilitating security and risk awareness. Leaders need to know more about security and risk in general. They need to understand that security measures cannot reduce vulnerabilities to zero but that risk can be effectively mitigated.
Describing the ongoing relevance of risk mitigation to the enterprise starts by familiarizing leaders with TRA terminology. Focus on key assets, determine vulnerabilities of current protective safeguards, protect against likely threats, justify appropriate measures, balance costs with benefits and prioritize future actions.
Security professionals can engage leaders by framing recommendations to safeguard assets (people, places, materials) within the corporate culture. Focus on priority risk
Also recognize that despite all attempts to neutrally communicate an evidence-based risk assessment, emotions play a very significant role in every decision-making process. Human beings, regardless of business titles or academic credentials, have a tendency to exaggerate risk during dramatic events (e.g. plane crashes) and downplay it during more mundane incidents (e.g. car accidents), where they are actually more at risk. We all have a bias that skews decision-making toward relying on our own experiences rather than on objective fact, probability or logic.
Therefore, it is necessary to anticipate and address your leaders’ emotions. Be ready to adjust your own analysis frequently as the situation evolves and change your communication strategy as needed. Ask yourself, how can the presentation of risk arouse emotion? Then, use that emotion to spur action or provide situational awareness to assuage unsubstantiated fears. Know that risk can be misinterpreted due to unintended emphasis on historical precedent. A past incident can be seen by a leader as a determinant of a future occurrence. When media soundbites purport growing dangers (e.g. mass shootings) consider how to effectively demonstrate any tenuous or nonexistent linkages to the actual security risk environment of the corporation.
Recognizing that risk is neither assessed nor communicated within a vacuum provides the proper framework to develop and transmit meaningful, relevant and accurate information about risks impacting a corporation.
Camille McKay is the manager, security risk at the City of Mississauga, Ont. (www.mississauga.ca).
for being recognized in the Top 10 under 40

At GardaWorld, we learn from and adapt to the challenges of today’s complex world to provide effective security services and business solutions to our clients. Jason Yuel embodies how our entrepreneurial spirit carries into everything that we do as a company, a team and a trusted partner for our clients. In the complex world we live in, our reputation is based on the quality of our services, as well as the commitment and integrity of our people, just like Jason.
We are proud of you Jason!

Security products can be a huge help, but they are not problemsolvers
It’s spring.
Winter has been replaced with the promise of new adventures, and new risks to identify. It’s also the beginning of conference and exhibition season — a chance for vendors, developers and integrators to try to influence security professionals that their latest equipment or software will change the way we secure our organizations.
I’ve heard this so often during my career. A conversation starts off with, “Tim, I went to a conference last week and saw this great widget! We absolutely need to buy this, but I can’t get my executives to agree. Can you help me convince them how good this widget is?”
Sound familiar?
I appreciate the skills and expertise our industry vendors and developers display. These folks are amazing with their ability to design a product or solution that can reduce risks to environments, and offer greater service and functionality that we’ve never experienced in the past. I’m not downplaying the role all our vendors, developers and integrators play to help us security professionals protect our organizations.
I’m concerned that some security professionals immediately leap to the conclusion that their organization absolutely needs a new widget, without understanding if the widget will support their business objectives, reduce risks facing their enterprise assets, and provide a practical and pragmatic approach to continually securing their organization.
Purchasing solutions is the last step we should take after we’ve gone through the Enterprise Security Risk Management (ESRM) methodology. If we jump directly to a purchasing decision without doing our

homework first, we run the risk of presenting a flawed business case to our executives and may not receive any funding, while potentially damaging our relationships with leadership as well.
The ESRM methodology focuses our mindset on business goals and objectives, and how the assets we have in place must ultimately support these goals. When we assess the risks to these assets, and come up with alternatives to mitigate the risk, we need to be practical in our approach by understanding if our current controls can reduce risks if we actually have them implemented correctly. Sometimes, all it takes to reduce risk is to follow a process that should be in place!
Too often I’ve been involved in projects that went directly to recommending a new widget, only to have the new solution fail because we didn’t do our business homework. We didn’t identify how any new technology or control must still support business objectives, and that installing any new widget requires training, education and awareness along with updates to our existing control framework. Simply installing a new camera system or updating a card access program won’t address risks if we don’t understand how these new controls will support business objectives by reducing risks.
I have seen changes in how we purchase new widgets from the vendor community. I’ve had some great discussions with vendors who wanted to be more helpful to their clients, so they began reading their current or targeted clients online financial statements, or published business strategies. Understanding what your client’s business requirements are can truly change a typical sales discussion into a collaborative assessment of how a proposed solution can address business goals and reduce risks to the enterprise.
I’m not saying don’t go to conferences, or look at buying new widgets. Far from it! What we need to do is focus on the goals of “why” we want to buy a widget, and ensure it has a direct link to business goals while reducing risk. We need to become risk-based consumers, because ESRM isn’t about buying new stuff, it’s about reducing risk.
Tim McCreight is the manager, corporate security (cyber) for The City of Calgary (www.calgary.ca).

By Kenrick Bagnall

Being prepared for digital threats means a lot more than investing in the right technology
Let’s look at three areas of consideration for cybercrime risk, starting with system susceptibility.
This is a combination of the value the target represents to the attacker and the potential vulnerability of the target. Has due diligence been done by the system developer/ manufacturer to minimize any zero-day implications? What steps have been taken internally to ensure that patch management is up to date? Has decommissioned hardware been removed from the network?
Threat accessibility is where information and physical security intersect. How physically and logically accessible are your systems and data? Have you implemented strategies like defence in depth and least privilege to protect your information systems? Are you using “air gapping,” a physical separation strategy, to secure your systems? (However, the ability to deliver a malware payload from one system to another by “piggy-backing” on the heat signature of the systems microprocessor, has been proven successful in a lab environment. This somewhat neutralizes the effectiveness of air gapping.)
Two important considerations for threat accessibility are social engineering and the insider threat. Human beings remain the weakest link in the chain of cybersecurity. This forces organizations to consider the potential threat represented by customers, staff and third-party organizations.

The third one, while significant, is the one you have least control over: threat capability What are the tools, techniques and overall capabilities being used by those who are targeting you or your organization? When the hacking group “The Shadow Brokers” compromised the National Security Agency, not once but twice, it led to the development of some very sophisticated malware. It also solidified the adaptation of cybercrime into the Software as a Service business model. No longer does one have to be able to write code or understand computer networks to profit from cybercrime. With all of these threats looming
around us, what are we to do? Our mindset will dictate our actions. We must begin by thinking not if we will be breached, but when. This does not mean all efforts are put solely into cyber incident response and recovery.
We need what I refer to as the Y2K mindset. In 1999, the effort that was put into finding and mitigating potential issues to systems that would have been caused by the calendar switching over to the year 2000 was unprecedented. Addressing 2019 cybersecurity issues requires this same hypervigilance.
In the event of a breach, it’s time to execute your incidence response plan. You will want to control the narrative and get the correct message out in your initial media statement. You will need to notify your board, your staff and your customers. Regulatory compliance will require you to advise regulators and credit reporting. PIPEDA will require mandatory reporting to the office of the privacy commissioner, notifying your customers and also retaining logs/records of the breach. Breach mitigation will require technical cyber security incidence response either internally and or externally depending on available resources. The results of this work can be used for mitigation and if disclosed to law enforcement may also be used to form reasonable grounds and assist with attribution. If you have cyber insurance, a predetermined call to your insurer will activate your policy.
While there is no specific direction that law enforcement shall be contacted during or shortly after a breach, recommendations have been made that the involvement of law enforcement could contribute to mitigating the risk to the customer. When it comes to cybercrime, much like traditional street crime, law enforcement is interested in achieving attribution by working with victims, witnesses, partner agencies and prosecutors to build strong cases that have a reasonable prospect of conviction. Successful cybersecurity is a team sport and law enforcement is your strategic partner in the fight against cybercrime.
Kenrick Bagnall is a Detective Constable with the Toronto Police Service Computer Cybercrime Unit (C3) Twitter: @KenrickBagnall.

Reliable surveillance is critical. Bad weather, for example, shouldn’t stop you from seeing what you need to see. Whatever your challenge is, we do our best to assure that your surveillance system will meet it. Today. And tomorrow.
Explore innovations that make a difference at axis.com/technologies or call us at 1800 444 AXIS, option 1.
By Elliott Goldstein

A recent case highlights reasonable expectations of privacy in a public place
In R. v. Jarvis1, the accused was a high school teacher who, using a pen camera, made surreptitious video recordings of female high school students at school, when they did not know they were being recorded.
The breasts and upper bodies of the female students were the focus of the video recordings. Jarvis was charged with voyeurism and acquitted at trial because the trial judge was NOT satisfied that the recordings were made for a sexual purpose.
The trial verdict was appealed to the Ontario Court of Appeal, which unanimously concluded that the trial judge erred in law in failing to find that the accused made the recordings for a sexual purpose.
However, in a split decision, the OCA also found that the trial judge erred in finding that the students were in circumstances that give rise to a reasonable expectation of privacy. That issue was the basis of the appeal to Supreme Court of Canada.
recording was done.
(5) The subject matter or content of the observation or recording.
(6) Any rules, regulations or policies that governed the observation or recording in question.
(7) The relationship between the person who was observed or recorded and the person who did the observing or recording.
(8) The purpose for which the observation or recording was done.
(9) The personal attributes of the person who was observed or recorded.
“Whether observation or recording is regarded as an invasion of privacy depends on a variety of factors.”
The SCC heard the appeal and found Jarvis guilty because “there can be no doubt . . . that the students recorded by Mr. Jarvis were in circumstances in which they would reasonably have expected not to be the subject of videos predominantly focuses on their bodies, particularly their breasts — and a fortiori not to be the subject of such videos recorded for a sexual purpose by a teacher.” The SCC concluded that the students recorded by Mr. Jarvis were in circumstances that give rise to a reasonable expectation of privacy for the purposes of s. 162(1) of the Criminal Code.”
In determining whether a person who was observed or recorded was in circumstances that give rise to a reasonable expectation of privacy, a Court should consider the following non-exhaustive list:
(1) The location the person was in when she was observed or recorded.
(2) The nature of the impugned conduct, that is, whether it consisted of observation or recording.
(3) Awareness of or consent to potential observation or recording.
(4) The manner in which the observation or
The SCC held that persons CAN HAVE an expectation of privacy when they know they can be observed by others or when they are in a place from which they cannot exclude others, such as a “public” place.
Whether observation or recording is regarded as an invasion of privacy depends on a variety of factors, such as: “the person’s location; the form of the alleged invasion of privacy, (i.e., whether it involves observation or recording); the nature of the observation or recording; the activity in which a person is engaged when observed or recorded; and the part of a person’s body that is the focus of the recording.”
A minority of judges of the SCC held that section 8 jurisprudence should NOT inform the interpretation of s. 162(1) because, among other things, “(T)he purpose and function of s. 8 and s. 162(1) are fundamentally at odds.”
The minority concluded that the students had a (subjective) reasonable expectation of privacy and the videos of their clothed breasts infringed their autonomy. The recordings were also objectively sexual in nature as focused on the women’s intimate body parts, at close range. So, the recordings infringed their sexual integrity.
A longer version of this column is available at www.canadiansecuritymag.com.
Elliott Goldstein is a lawyer, deputy judge of the Ontario Small Claims Court and author of “Visual Evidence: A Practitioner’s Manual” (elgold@rogers.com).
1. 2019 SCC 10 (Appeal Heard: April 20, 2018, Judgment Rendered: February 14, 2019). All quotes are from this case.

Congratulations to G4S Supervisor Richard Strickler and the Top 10 under 40 winners! At G4S we recognizes the role young talent plays in the future success of our industry. We place an emphasis on the training and professional development of our greatest asset, our people, by offering over 2,000 unique training programs. Learn more about how G4S is nurturing young talent by visiting www.g4s.ca

Young professionals are making their mark today and helping to shape security for the next generation through leadership and mentoring
If the quality of submissions Canadian Security magazine received for its first annual Top 10 Under 40 is anything to go by, the future of the security industry is in good hands.
Narrowing the nominations down to 10 recipients was a difficult process — which is all the more reason to celebrate the final 10 for their accomplishments, work ethic, volunteer efforts and commitment to the profession. Please join us in congratulating the winners.
— profiles by Neil Sutton and Will Mazgay

Jason Yuel works at GardaWorld in Winnipeg, where he is “in charge of the performance of the entire branch and making sure that we’re up to the standards that GardaWorld expects of us,” he says, which includes ISO 9001 certification, and on the account management side, making sure contracts are delivered on. Yuel also manages a mobile division, a fleet of vehicles that service the entire city.
Yuel was recognized as GardaWorld Canada’s top account manager for 2018.
“It was gratifying, and nice to be recognized to show that the hard work you put in does pay off and doesn’t go unnoticed,” he says.
He recently became Manitoba’s youngest Certified Protection Professional (CPP). “I think I kind of moved quickly up the ranks and got to a point where the CPP would become very valuable and decided ‘why not, I’m ready to take it,’” Yuel says. “I know I probably won’t be the youngest for long.”
Mentorship is important for Yuel, who serves on ASIS Manitoba’s executive board as its Youth Liaison for Young Professionals. He says the role not only gives him an opportunity to teach and coach young people, but to inform them of the myriad avenues available in the security industry.
“That’s a huge satisfier for me,” he says.
Yuel got his start working events like concerts, festivals and sporting events, and moved into entry level corporate security.
“I’ve had the experience of being a security officer in both of those settings. It transitioned me to know what to look for in security guards specifically, and then also when speaking to clients and talking to other stakeholders, I have a knowledge of what it’s like on the front line, which I think is very valuable,” he says.

Melinda Saunders Security Manager, Workplace Safety & Insurance Board, 38
At Workplace Safety & Insurance Board (WSIB), Ontario’s workplace compensation board, Melinda Saunders’ focus is on dealing with disruptive and threatening clients, and she is currently auditing that part of her department. She says, “just to see how our current security culture and our programs are actually working.”
Saunders has co-ordinated security training for staff across the province — which she says is focused on threat protocol and co-operating with emergency services. She says when it comes to preparing for worst-case scenarios, “it’s changing the culture. It’s that broad view of ‘it’s not going to happen here.’ That’s a big thing.”
She also started the organization’s employee security screening program.
Saunders says her biggest accomplishment was getting a peer support program off the ground: “It’s near and dear to my heart. I have been witness to a lot of situations where people have needed help within our organization and outside as well… It’s basically having that non-judgemental and compassionate service.”
In 2017, Saunders received an award for her role in helping a client, injured at work by an assault, to return safely to work. “I worked with the case management team, the return to work specialists, and that client as well to put some different types of safety in place at that location where they were working just so that they felt safe,” she says. “I was astonished when I was recognized for that because I didn’t think it was outside the box.”
When referencing her past experience, Saunders says, “I pretty much did it all.” Working for a number of corporate security firms, she dabbled in investigations, human resources, recruiting and training. She was also an executive protection officer “for certain high-profile clients,” and she worked in national accounts for an organization heading up an anti-piracy program. “I always like changes,” she says.

Dennis Ellahi Chief Operating Officer, Commissionaires Southern Alberta, 39
Ellahi started in his role as COO at Commissionaires Southern Alberta in September 2018, but the Calgary-based executive has hit the ground running.
He says, “My priorities as COO are: implementing a customer care program, frontline training and safety.” He is working with the Alberta Security College to train staff. For customer care, “it’s quality management and having the right partnerships and engagement levels, and having the right measurements for service delivery.”
And as for safety, Ellahi says he is drawing on his experience in the oil and gas sector, when he worked for a boutique resource security company. “We were able to take what safety looks like in an oil and gas environment and make it relevant to the security environment.”
Ellahi had a varied employment history before landing at Commissionaires, including working in aviation security. “Airports are awesome places to work. They’re little cities and communities unto themselves and from a safety and security perspective there’s just so many stakeholders and layers,” he says. It was during this period when he worked the 2010 Vancouver Olympics: “That was a hectic time.”
Another career highlight for Ellahi was supporting the response to the 2016 fires in Fort McMurray, Alta., while working in the oil sands. “I leveraged the corporation, mobilized the resources we had within our Calgary/Edmonton operation, HR, safety, recruitment, ops, training.
“My experiences across a bunch of different companies, a bunch of different sectors, that’s helping this organization (Commissionaires) evolve and grow,” he says, referencing a breadth of frontline and corporate experience. “I’ve had some exposure to some very smart people and I’ve been able to see what good looks like.”
Ellahi has some advice for young professionals looking to follow similarly successful trajectories: “It’s critical for people to find mentors and role models that challenge them.... If you’re the smartest guy in the room, you’re in the wrong room.”

Sean Sterna
32
Sean Sterna is the assistant security manager for the Bow, a high-rise office tower in downtown Calgary owned and operated by real estate investment trust H&R REIT.
Sterna says of his role, “We’ve got a couple of supervisors who worry about day-to-day operations and I work from the strategic planning and objectives standpoint.” He continues, “It’s a new operation. The building has been open for about six years now. When we (the security team) came into this role, me especially, probably four and a half years ago, there really wasn’t anything built. There were no training programs, there was no structure. It’s been building those pieces that’s been the most challenging.”
Sterna says he provides the same training to both contract staff and in-house staff. “We’ve created a full booklet program for our new-hire orientation guide, to make sure everyone is getting the same training, so there’s consistency there.”
Sterna also developed a multi-level emergency exercise program. He explains that his goal is to build a strong relationship with emergency services. “So, if they’re needed, they know us, we know them, we all know how we’re operating, and it just streamlines that response.”

Before moving into the high-rise environment, Sterna worked as a security supervisor at CF Chinook Centre (the largest mall in Calgary) where he took on training as well.
“At Chinook, I was given a training program that was more or less complete, it was just out of date. We updated it and I brought it in line with where we were at the time,” Sterna says. “That certainly guided me with what I did at the Bow as well.”
As for what makes it worth it for Sterna, he says it’s seeing his staff progress and move into supervisory and leadership positions. His nominator says Sterna is always encouraging others to continue to grow and educate themselves.
In his spare time, Sterna is a volunteer fire captain, which he says has helped him grow as a leader.

Erin Steeksma
Superintendent, Canada Border Services Agency, 34
Erin Steeksma helps lead a busy land border crossing in Abbotsford, B.C. She says, “On a daily basis I’m managing everything that comes through our door, I’m managing the officers who are interacting directly with the public, and dealing with the leadership and development of those officers.”
She started at the Canada Border Services Agency (CBSA) as a student officer, before being bridged into a full-time role. “I spent the majority of my career as an officer at the Peace Arch, which is one of the busiest crossings in British Columbia. That’s where I gained most of my experience — in the interesting and kind of crazy things that you expect to see at the border,” she says.
Steeksma then moved into a role as a spokesperson. “It can be very challenging to stand up in front of the press or to be responding to media inquiries and balance giving the information the public needs/wants versus protecting privacy of people involved and telling our story,” she says.
She stepped into her current role around three years ago, and has acted in a chief role (the person in charge of the entire port) on a temporary basis. Steeksma says, “You are introduced to a much wider range of issues, challenges, managing even more people and bigger picture things.”
Steeksma spent last summer in Quebec dealing with the influx of refugees into the province, working in a manager role of a unit processing claims for those crossing the border.
Steeksma was also a part of the TV show “Border Security: Canada’s Front Line.” She says, “Having cameras follow you around at work was definitely something new.”
The border agent says that for young women looking to carve out a career at the CBSA or other law enforcement agencies, “Don’t feel that because you’re a woman you’re not fit, and regardless of gender, if you have the drive and leadership and security-minded mentality you can be successful.”

Agnes Pienio-Ganthier Regional Manager, Loss Prevention, Amazon Fulfillment Services, 38
Ordering products from Amazon has become so effortless, it’s sometimes easy to forget there are many people behind the scenes.
Agnes Pienio-Ganthier is one of those people. Pienio-Ganthier has worked in Amazon’s LP department since 2014 and currently has oversight over two of the company’s major Canadian fulfillment centres in Brampton, Ont. and another three across the GTA. One of the Brampton centres was brand-new when she started at Amazon. The second, an Amazon Robotics building, opened across the street under her watch.
Pienio-Ganthier assumed she would enter a career in law enforcement while she was still attending college, but a chance opening in Sears’ LP department steered her in a different direction. She says she enjoyed the challenges and opportunities loss prevention presented and carved out a 15year career at Sears before accepting a role at Amazon.
“The key focus for our job is rooted in the safety of our employees and their security while they’re working on our premises,” she says.
Pienio-Ganthier has made her mark in her first five years at Amazon. She helped to launch an x-ray screening program for Amazon fulfillment centres in Canada (it was first piloted in the U.S.) and completed x-ray safety officer training to help her better understand the technology and its workplace safety requirements. She also brought an on-call loss prevention program to Amazon Canada, ensuring that there is always an LP manager available 24x7 to provide support when needed.
She is part of Amazon’s Women in Security Group and coedits their quarterly newsletter. She also serves as a mentor to several other Amazon employees, two in North America and one in India.
Pienio-Ganthier says one of her goals is to keep learning and acquiring new skills. She is LPCertified (and also coordinates the certification program for other Amazon Canada employees) and is aiming to attain an ASIS CPP designation within the next few years.

GSOC Physical Security Access Program Supervisor, G4S, 31
Time management is frequently a hallmark of a solid security program, but for Richard Strickler, it is practically a way of life.
Strickler learned the ropes the same way a lot of people do — by becoming a frontline guard — and has transformed himself into an expert in access control through a series of career moves and some
careful attention to detail.
Strickler joined the Commissionaires right out of school through a training program, and was promoted to supervisor at the age of 23 while working for Commissionaires client 3M Canada in London, Ont. He became the company’s badging coordinator, working in co-operation with the 3M head office in St. Paul, Minn. Strickler says his access control duties include programming categories as well as managing name changes, photo updates, etc.
“When I was at 3M, my mentor at the time brought me into some of the projects for access control,” he says.
From there, Strickler accepted a role, also through Commissionaires, at Wolseley Barracks (Canadian Forces Base London). There, he conducted security inspections, which covered a gamut of audits, vulnerability assessments and physical security surveys. “I found all that stuff really interesting… here’s where we’re benefitting, here’s where we’re lacking, here’s where we need to improve and actually effecting meaningful change.”
Earlier this year, Strickler moved to a new position, this time with G4S, working for Canadian software developer OpenText at the company’s Waterloo, Ont., facility. There, he runs the OpenText badging and physical security access control program globally, and works with two other operators at the company’s GSOC. Coordinating a global program


requires a dedication to both time and detail. Managing across time zones “takes you to a whole other level of thinking,” he says. “Time management is the key thing. I live and die by the calendar and emails. I’m very fastidious with the things I have control over.”
In addition to his professional work, Strickler also makes time for his local ASIS International chapter, Southwestern Ontario. He is currently chapter secretary and has also served as vice-chair and chair. He credits his supervisor at 3M for encouraging him to become a member. Strickler also holds the ASIS PSP designation and was among those who wrote and passed the new APP certification beta test.

CEO and founder, TrackTik, 37
The security industry is being transformed through technology and Simon Ferragne is one of the pioneers making it happen.
Ferragne, a software engineer by trade, started his company TrackTik five years ago. TrackTik’s software helps clients manage guard scheduling — more than that, it helps


them make informed decisions about security operations by better utilizing the data that is generated through that process.
Ferragne was working for a Silicon Valley company when he first realized there was an opportunity to address some of security’s pain points. He says he met someone from the industry and was enlightened to some of the major challenges they face.
What started as a side project for Ferragne quickly became a full-time occupation as word about the company began to spread. “There was a natural push from the industry to have more data-driven systems,” he says.
Today, Montreal-based TrackTik employs 128 people and serves customers in 35 countries.
Ferragne entered the industry as security professionals were taking a hard look at the benefits they can offer in terms of customer value and data-driven decision making. “Every guard company wants to provide that extra layer of value, so I think it was great timing for us,” he says.
Ferragne also says his company is helping to fuel that transformation. “We like to think we contributed to that. So early on, we spent a lot of time educating end users on what they should be getting and what’s possible.”
The next stage for Ferragne and TrackTik is amping up data-driven choices even further. TrackTik is working on integrating other AI inputs, like the latest surveillance cameras, while still keeping the human central in the decisionmaking process.

Joey Bourgoin says he has achieved success in his dozen years of professional security by pushing himself and encouraging others to do the same.
Bourgoin started his security career in loss prevention as an investigator right out of college.
“From that point on, I progressed through various roles that led me to where I am today. As opportunities came, I would take them on. I think the key piece in all of this is networking.”
Retail environments gave him some knowledge he could utilize in other aspects of security — he joined one of Canada’s largest banks as a member of its protection program team about five years ago. “For me, it’s not being afraid to get out of your comfort zone and take on new challenges. I think that’s been a resonating theme throughout my career,” he says. “I remember when I was interviewing with the bank, [I was asked questions like], ‘You come from a retail background, how would you transition to banking?’ Part of that answer is being able to articulate your experience in security.”
He was promoted to his current position a year and a half ago, and is grateful that “CIBC has given me a ton of opportunities.” A major undertaking right now is helping to
guide the CIBC’s security department as the bank undergoes its own global transformation to serve the needs of its clients better.
Bourgoin credits the mentors he has worked with along the way for helping him achieve success and is a big believer in passing his knowledge and experience along.
He is a member of Sheridan College’s professional advisory council for the public and private investigations diploma program and helps to guide the program so that it keeps up with current trends in the industry. (Sheridan is also his alma mater.) He also holds a CPP and has volunteered with ASIS International. He has served in chapter level roles in Toronto, on the organization’s young professionals council, and also as an assistant regional vice-president for the national young professionals program.

Manager, Fire and Life Safety, Cadillac Fairview,
28
To call Shannon Toomey goal-oriented would be an understatement.
“I was that student in high school that had a two, five, 10 and 15-year goal. I definitely wanted to be in a leadership role,” she says.
At 28, Toomey has already marked some major milestones. She is currently manager of fire and life safety for Cadillac Fairview, looking after Toronto’s Eaton Centre, Ryerson University and three nearby office towers. Emergencies, floods, power outages, fires and assaults all fall under her jurisdiction and three fire inspectors report to her.
Toomey started out in a police foundations program, which she took at Seneca College. The world of security opened up to her and she was immediately intrigued. “I recognized in school that policing is fantastic… but it wasn’t for me. I’m all about prevention, regardless of whether it’s security, fire safety or emergency management,” she says.
She interned with another property management firm, RioCan, and got some first-hand experience of what it was like to work on a site. She has since worked at LRI Engineering and at Paladin Security as senior fire and safety coordinator for Canada.
Toomey joined Cadillac Fairview about a year and a half ago and already has some new goals in mind. She is taking a degree in security and emergency management at the Justice Institute of British Columbia on a parttime basis and has already amassed an impressive list of certifications and achievements, including several from the National Fire Protection Association.
She has also volunteered with the Toronto chapter of ASIS International, serving on its education committee and as executive secretary. “My next step for myself is really to refine my skillset,” she says. “I have a passion for the industry and I love being to able to share that passion with my team.”

Assessing and upgrading security procedures and equipment for condominium buildings comes with its own specific set of requirements
By Scott Hill
William H. Webster, a former director of the FBI and chair of Homeland Security Advisory Council, once said, “Security is always seen as too much until the day it is not enough.”
Although the quote was said during a debate titled National Security vs. Personnel Liberty, it is equally applicable to condominium corporations and their operational procedures. Condominiums face several challenges when it comes to implementing and upgrading security.
The first could be the governing body; boards of directors are elected from the owners (mostly) of the condominium and they are charged with managing the well-being of the condominium. These owners usually come from diverse backgrounds and bring their own expertise to the board. However, if there is no one familiar with security or risk management on the board, quite frequently (in the absence of serious or frequent security events) security is pushed to the back burner.
The reason it gets pushed to the
back is the second challenge that condominiums face when looking for ways to better protect the residents and their property: money. While most security professionals will agree that the allocation of funds to the security budget is almost always a challenge, in condominiums it is compounded by the source of the funding. Condominiums are solely funded through the common element (or condominium) fees that are collected from the owners. When costs increase, that means that the board of directors must meet this increase in costs by raising the condominium fees for all owners (which is never a popular decision). When board members (and the condominium managers who advise them) look at cost-cutting during the annual budget process, quite frequently security in the building is carefully reviewed and debated, with sometimes less than optimal results.
The third challenge in funding security solutions in condominium buildings is the transparency of the system. When it is working properly, no one notices it. This can sometimes cause owners and board members to question the need to even have it in place.
Despite the challenges, many condominiums and their stakeholders are taking a proactive approach to evaluating and upgrading their security within the facility. This enlightened approach has resulted from many different sources, but a primary one has been the widespread reporting of security vulnerabilities of condominiums.
A second reason that condominiums are undertaking a preemptive look at security is due to owner/resident demand. Earlier this year, TD Canada Trust conducted a survey of what potential buyers are looking for when they consider the purchase of a condominium. In that survey, 94 per cent of those polled listed security as the most important consideration, ahead of energy efficiency (92 per cent), having a balcony (90 per cent), parking spots (87 per cent), or being close to public transport (84 per cent). This has caused management at condominiums to review their security systems, not only to protect persons and property, but to protect owner investment and market competitiveness within the industry.
One of the struggles of management is where to start when they decide to evaluate their security.
A popular option is the commissioning of a security audit. The goal of the security audit is to review the effectiveness of the existing security measures, identify vulnerabilities within the complex, and to provide multiple


options to address them. In order to be a proper review of the security systems in place, condominiums are recommended to ensure that the person conducting the audit is impartial (is not a supplier or installer of security systems within the complex), is familiar with condominium operations (and their challenges), and is a security professional experienced in providing such reports.
It has been our experience that a condominium chooses to undertake a security audit during one of three times. Two are proactive and the third is reactive.
The reactive time is after security incidents have taken place. A condominium that suffers serious break-ins, vandalism, theft or assault will look to better protect their residents by identifying and rectifying the vulnerabilities within the condominium. In this manner, the board of directors and managers can report back to the owners — who are usually legitimately concerned about such matters — that action has been taken, and that the corporation is addressing the issue in a professional manner by hiring qualified advisors.
A second time that condominiums undertake (proactively) a security audit is before they update their Reserve Fund Study (RFS) report. Condominiums in Ontario are required to complete a report every seven years (with an update in between) which ensures that they have adequate funding to meet all capital projects that may be required in the future (30 years). This is called a reserve fund report and is instrumental
in condominium operations and budgeting. Previously, very few of the RFS reports incorporated detailed physical security components and/or upgrades.
Condominium management is addressing this issue by completing an assessment in advance of the scheduling of the RFS. Once the audit is reviewed and recommendations approved, a copy of the security audit can be provided to the engineer completing the study and incorporated into the funding schedule. In this manner, security upgrades and enhancements can be scheduled over a period of several years, reducing the financial impact to the condominium and the owners. Additionally, the life-cycle of the security equipment within the condominium can be determined so that replacements and/or upgrades can be inserted into the funding schedule. This is the beginning of having a master security plan and it ensures that the equipment will be cycled out when they reach the end of their useful life.
Recently, we have seen a trend where condominiums are proactively commissioning a security audit within their first year of operations. Given the rate that condominiums are being built (specifically in Ontario), it is becoming increasingly important to ensure that inherent security vulnerabilities do not go unnoticed. Condominiums, in their first year of operations (in Ontario, but we believe this is becoming more widespread across Canada) are charged with conducting a report with an engineer that identifies, within the scope listed by Tarion Home Warranty, the construction deficiencies within the condominium. This report is called a performance audit and is provided to the developer (builder) who is responsible for addressing the deficiencies listed. Much in the same manner as the reserve fund study, a copy of the audit can be provided to the engineer conducting the performance audit.

In many cases, some of the vulnerabilities in the condominium have been judged to be construction deficiencies and were included on the report as a warrantable item on the Tarion Report. As such, these issues would then be the responsibility of the building, and should be fixed by the developer at no cost to the condominium corporation.
As noted above, condominium corporations have many different options to consider when deciding on how to protect the property and the people that live inside. The first step in considering these options is to audit the current security solutions and identify their effectiveness. As part of the review, unaddressed vulnerabilities will come to light and they must be evaluated based on the level of risk that they pose to the owners and their property. It is of limited value to start implementing new procedures/equipment before the effectiveness (or lack of) of the current systems has been determined. Once these two steps have been completed, only then can the corporation allocate the resources/funds required to properly and professionally protect the facility.

JUNE 18TH
Flourishing in the technological age
Topics include:
• Biofungicides: Microbe vs. microbe
• Managing pests in the digital age
• Clean water: Filter by design
• Grounds for a DIY mix
• Software solutions for greenhouse automation
• The payback on mechanization: A tale of two growers
• Lighting & plant science: A deep dive into using smart LED lighting
• How to co-exist with your cannabisgrowing neighbour
JUNE 19TH
Cultivating your cannabis enterprise
Topics include:
• Innovation in cannabis cultivation
• Safety in cannabis production
• Going organic
• The business case for outdoor grow
• All about hemp
• Procedures and protocols
• Business briefs
• Product packaging
• KEYNOTE: Security and Risk Management for your Cannabis Business




DDavid Hyde
president, 3 Sixty Secure
avid Hyde has worked in professional security for decades, but when the legalization of cannabis became a potential reality for Canadians, he saw an opportunity to apply his skills to an emerging and idiosyncratic market. The learning curve was steep, and not always steady, says Hyde, but he persevered and is now recognized as a leading expert. Hyde recent joined 3 Sixty Secure, a major provider of security services to the cannabis industry, as the company’s president. He will also be a featured speaker on Day 2 of Grower Day, which will be held June 19 in St. Catherines, Ont. Canadian Security recently sat down with Hyde to get a sense of how the marijuana market is shaping up.
Canadian Security: How has the market changed since the legalization of recreational cannabis last year?
David Hyde: We’ve learned that we have a nascent industry with nascent infrastructure and it’s been a challenge. We now have 159 total licensed parties and counting, which is a lot higher than ever before. A lot more cannabis is being moved around roads in Canada than has ever happened before, so there has been a lot of supply expansion — the production of cannabis has increased, so the security needs really coalesce around that. There’s increased risks as we have more facilities, more retail locations, more cannabis transportation and movement. This expands the considerations for the licensed entities who need to secure that product and for us as a security and risk management company, how we navigate this increased risk landscape, where there’s a lot more moving parts. There’s new licence categories for new licensed producers that have new

considerations for both security and risk.
CS: What are the biggest challenges for the security providers who are serving this market?
DH: The biggest challenge, I would suggest, in terms of being able to capitalize on the industry’s trajectory and have a value proposition in the area of security, is grasping the context — both the regulatory context and the business context. The cannabis sector is very unique. It doesn’t fit neatly into other paradigms [like] pharmaceutical, alcohol, tobacco. You can pick a variety of things that might be comparable and they really don’t fit. You can’t just show your wares and start selling things. You need to understand the regulations and the challenges that the licence holders are facing in their everyday businesses.
CS: When did you first become aware of the security opportunity in the cannabis market?
DH: It’s quite ironic, because when I started in my consulting business in 2010, after 20 years with Cadillac Fairview, my marketing was going on TV and commenting on national security stories. I was on the TV, I think it was CBC, one night, and the CEO of one of the very first cannabis producers in Canada watched that interview and called me. He said, I heard you on TV, you sound like you know what you’re talking about… have you heard about the cannabis security regulations? I said, no I haven’t. This is 2013… right at the very beginning. I thought this is going to be really big, and if I take the time to become a subject matter expert in this area and do whatever it takes to get there, I think it’s going to pay dividends.
It wasn’t mapped out, and it’s taken a windy, successful road. [We’ve] captured quite a lot of the market when it comes to providing strategic advisory services, consulting services — and now with 3 Sixty branching out, providing guarding, integration and secure transport service.
CS: How are security professionals reacting to the legalization of cannabis?
DH: It’s been a bit of a new paradigm for security directors who need to add that to the arsenal of considerations for them, and how to navigate that from a security perspective. Also, my phone rings a lot when a new security director from outside of cannabis comes in. As these companies grow, they’re hiring directors of security. They have a significant asset protection consideration. These folks need a head of security. We help them and sometimes are that contract head of security, but they hire in-house security as well. I know some of these people from my previous life. I’ve suddenly become really popular. [They say] “Help me understand this cannabis thing.”
It’s such a learning curve to go from other industries into this one.
CS: What is the size of the opportunity for the security industry in cannabis?
DH: The opportunity is global. When you look at all of the countries right now that are either legalizing cannabis — there are several countries in addition to Canada — or bringing in medical cannabis — Australia, Jamaica, Germany — in all of these places, a very high bar is put on security, and some would argue too high a bar. We all know, from a security paradigm, that when cannabis is processed to its deliverable state, it ticks all the boxes to be a hot product; one that criminals would be interested in and could be available on the black market in a very anonymous, quiet way. That’s one the reasons why the bar will always be very, very high. I believe the market is very large and the opportunity is great.

Robert Arandjelovic is Symantec’s Americas director of product marketing
(www.symantec.com).
According to Symantec’s annual Internet Security Threat Report, one of the newest ways for hackers to steal personal data is formjacking. Here’s what you need to know about this growing online threat.
Formjacking occurs when cyber criminals inject suspect code, or malware, into an e-commerce website. When a consumer accesses the website to make a purchase, their information is sent to the merchant, but the malware copies their information and sends it to the cyber
criminals as well.
Formjacking affects an average of 4,800 websites each month. Although small and medium-sized businesses are the biggest targets, cyber criminals have also used formjacking to attack major organizations such as British Airways and Ticketmaster. In 2018, Symantec blocked more than 3.7 million formjacking attacks on websites, with one-third of those happening during the busy holiday shopping season.
For e-commerce retailers, it’s vital that systems are kept up to date, and that regular code reviews are carried out.
Many companies have strong coding review practices in place already, to make sure the user experience is maintained. If code is being reviewed regularly, this should identify anomalous code or malware.
For consumers, because the malware isn’t on your system, the best defence against formjacking is having reliable end-point security with intrusion prevention system (IPS) technology in place, especially when performing e-commerce transactions. Try to avoid using systems with questionable security, such as hotel or library computers. Without end-point security, it’s impossible to detect that an e-commerce site has been compromised and that your data is vulnerable. This also holds true for consumers who use their mobile devices to make purchases: if you access a compromised server using a mobile app, or if you open an infected webpage on your mobile phone, your data is at risk unless end-point security is in place on your device.
For the foreseeable future, formjacking will continue to increase.



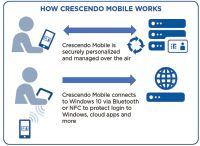
The Crescendo Mobile smart card utilizes digital certificates on users’ mobile devices for client authentication. The HID Crescendo Mobile solution provides organizations seeking to eliminate passwords with a solution that combines the high security of physical authenticators with the usability of a mobile solution. Crescendo Mobile works similarly to, and is compatible with Crescendo smart cards; however, rather than inserting a separate device into a contact smart card reader, it connects to a desktop computer via an NFC (near-field communication) reader or Bluetooth. The Crescendo Mobile app can be downloaded onto Android or iOS devices and the IT team can distribute secure cryptographic credentials to users without the need or expense of shipping smart cards or smart card readers.
www.hidglobal.com

The Securitron M680E Series Magnalock with EcoMag technology has an increased holding strength of 1,200 lbs and is eco-friendly, with an average power draw as low as 60mA at 24V.. This change in power represents a total reduced energy consumption of up to 80 percent over the previous Securitron M680 series. A new strike plate mounting template ensures strike alignment upon installation. As with the previous series of magnalocks, the Securitron M680E series has optional, integrated features such as passive infrared motion detector, Securitron BondSTAT bond sensor, Door Position Switch and door prop sensing. As standard features, the Securitron M680E series offers configurable LED, auto-relock timer, tamper monitoring as well as MagnaCare lifetime replacement coverage.
www.assaabloyesh.com/Eco
Senstar
The Senstar LM100 hybrid perimeter intrusion detection and intelligent lighting system combines two key security functions in one product, acting as a deterrent against intruders by detecting and illuminating them at the fence line. www.senstar.com

Feenics
Keep by Feenics is an access control as a service (ACaaS) platform built specifically for and hosted in the public cloud. The UI is accessible via an evergreen Windows desktop app, web client and mobile application. Using open field hardware by Mercury, Feenics works with video, intrusion and wireless lock manufacturers, and delivers these solutions through its integration channel partners. Feenics accomplishes cyber-readiness this through TLS 1.2 encryption, eliminating inbound ports, use of multi-factor authentication, penetration testing by Veracode and no default passwords.
www.feenics.com


TruProtect is a commercial security solution that unifies intrusion monitoring, access control and video surveillance into a single platform. This new platform enables users to scale the solution from a few doors to large, multisite operations that require customized integrations. The solution’s modular “add-as-you-go” design enables users to add capacity and functionality as required. Users can scale a system from a standalone intrusion panel to a fully networked security system spanning hundreds of locations. The TruProtect system supports a wide range of Interlogix TruVision cameras and network video recorders and optional third-party solutions.
www.interlogix.com/truprotect
Glass break detector
Digital Monitoring Products
Designed to detect the shattering of framed glass mounted in an outside wall, the 1128 Wire-less Glassbreak Detector is a fully supervised, low-current shock and glassbreak sensor that provides added detection coverage up to 20 feet. By detecting both high and low frequencies, the 1128 reduces the chance of false alarms. It’s also suitable for armour-coated glass. For maximum flexibility and coverage, the 1128 Wireless Glassbreak Detector can be mounted on the ceiling or on an opposing wall. It’s compatible with all DMP 1100 Series wireless receivers and existing wireless transmitters running Version 106 and higher. www.dmp.com


125 years of experience in putting the security of others first.

We understand you need to protect more than brick-and-mortar, which is why ADT does more than monitor. ADT has a wide range of alarm and security options for organizations of any size to help protect people, goods, and data. With 24/7 surveillance, solutions against intrusion and fire, remote monitoring, interactive services and more, ADT has a security solution for your organization. Join those who trust ADT with their livelihoods and protect your business.
Why choose ADT canada?
We are an integrator, meaning we can take over nearly any of the existing security equipment you have on-site.
We are customer-service oriented, innovative and technology savy. With over 125 years of experience and 15 branches in Canada alone, including four monitoring stations, you can trust the experts.