





















By Ellen Cools
By Ching Mac



By Neil Sutton

’ve become more active in social media in the last few years, building Canadian Security’s Twitter account, establishing Facebook groups and utilizing my own LinkedIn account to widen my network.
With Facebook and Twitter in particular, I’ve had a lot of help from several people who have worked on this magazine with me. This is definitely a team effort, and we still have a lot more work to do.
I marvel at the people who are able to communicate regularly and effectively on social media. Some of them work in the security industry, others are colleagues who work at our company, Annex Business Media, and there are many others I follow who comment, Tweet, post, blog and video blog (“vlog”) about other topics that interest me outside of work. The common denominator is that all of these people work at it every single day.
“Security
can benefit from the tremendous power and reach of social media.”
When I started in the journalism world, there was no such thing as social media. You could post news items on websites and send out email newsletters to a list of subscribers, but in terms of outreach, the options were limited. Website traffic numbers were the best indicator of success. In terms of actual feedback, the best you could hope for was an encouraging email from a reader or a positive comment delivered in person or over the phone. Website traffic is still the coin of the realm today, but outreach and interaction through social media has totally changed the face of journalism.
I think in some ways, this parallels what is happening in the security industry.
Journalism and publishing have always been about outreach and communication, so we really had a head start when it came to adopting social media. In security, the dynamics are a lot different.
Security, as a profession, has sometimes been accused of operating in a silo, whether that’s isolation from other company units, or interacting with customers or clients only when an emergency demands a response or action. Whether that perception is accurate or not, I think almost everyone can agree that the industry has changed a great deal in recent years, with many security leaders stepping up to interact more fully with their organizations and constituents.
Social media is one more tool that security professionals can utilize as part of that transformation. It is arguably the most important communications technical breakthrough since the invention of the cell phone and is rapidly becoming the go-to platform of choice for interaction and outreach. Security, in particular, can benefit from the tremendous power and reach of social media.
I encourage you to read our feature story on this topic (p.13) which is filled with great advice and examples. Protection may be the core of security, but communication could be the key to its future.


Group Publisher Paul Grossinger pgrossinger@annexbusinessmedia.com
Publisher Peter Young pyoung@annexbusinessmedia.com
Account Manager Adnan Khan akhan@annexbusinessmedia.com
Editor Neil Sutton nsutton@annexbusinessmedia.com
Associate Editor Will Mazgay wmazgay@annexbusinessmedia.com
Art Director Graham Jeffrey gjeffrey@annexbusinessmedia.com
Account Coordinator Kim Rossiter krossiter@annexbusinessmedia.com
Circulation Manager
Aashish Sharma asharma@annexbusinessmedia.com Tel: 416-442-5600 ext. 5206
President & CEO Mike Fredericks
Editorial and Sales Office

111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1 (416) 442-5600 • Fax (416) 442-2230 Web Site: www.canadiansecuritymag.com
Canadian Security is the key publication for professional security management in Canada, providing balanced editorial on issues relevant to end users across all industry sectors. Editorial content may, at times, be viewed as controversial but at all times serves to inform and educate readers on topics relevant to their individual and collective growth and interests.
Canadian Security is published six times per year by Annex Business Media.
Publication Mail Agreement #40065710
Printed in Canada I.S.S.N. 0709-3403
Subscription Rates
+ HST;
Circulation Anita Singh asingh@annexbusinessmedia.com Tel: 416-510-5189 Fax: 416-510-6875 or 416-442-2191 111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1
Annex Privacy Officer Privacy@annexbusinessmedia.com Tel: 800-668-2384
The contents of Canadian Security are copyright by ©2018 Annex Publishing & Printing Inc. and may not be reproduced in whole or part without written consent. Annex Business Media disclaims any warranty as to the accuracy, completeness or currency of the contents of this publication and disclaims all liability in respect of the results of any action taken or not taken in reliance upon information in this publication.





February 21, 2019
4th Annual Mission 500 Hockey Classic Toronto, Ont. www.sptnews.ca
March 7, 2019
Security Career Expo Toronto, Ont. www.securitycareerexpo.com
April 2-4, 2019
Canadian Technical Security Conference Cornwall, Ont. www.ctsc-canada.com
April 10-12, 2019 ISC West
Las Vegas, Nev. www.iscwest.com
April 24, 2019
Security Canada East Laval, Que. www.securitycanadaexpo.com
May 8, 2019
Security Canada Ottawa Ottawa, Ont. www.securitycanadaexpo.com
May 19, 2019
IAHSS Annual Conference and Exhibition Orlando, Fla. www.iahss.org
May 29, 2019
Security Canada Alberta Edmonton, Alta. www.securitycanadaexpo.com
June 13, 2019
Security Summit Canada Toronto, Ont. www.securitysummitcanada.com
June 19, 2019
Security Canada West Richmond, B.C. www.securitycanadaexpo.com
September 11, 2019
Security Canada Atlantic Moncton, N.B. www.securitycanadaexpo.com
TerryHoffman, president and founder of Zerobit1, a Toronto-based security consulting firm, is about to launch a new e-learning platform he says will help to address the significant knowledge gap when it comes to keeping people and companies cybersafe.
The new service, 2B Cyber Bright, will offer a mixture of different learning tools such as educational videos and tip sheets as well as services like cyber and social media investigations, and cyber policy development.
“It was a thought process I had about a year ago, seeing what was happening in society with cybersecurity,” explains Hoffman, whose Zerobit1 business also offers professional risk assessment tools and security design consultation.
Whereas the bulk of Hoffman’s professional security business has focused on corporate clientele, the 2B Cyber Bright project addresses a much broader base, including students, families and small and medium businesses.
A major focal point for Hoffman is working on the human factor skills — the slips that can be made through lack of awareness, whether that’s clicking on a phishing email or using an unsecured WiFi network.
Small businesses in particularly may find themselves targeted for attacks, he adds. They may have vital data to protect but are often ill-prepared to deal with the harsh realities of today’s malware and cyberattacks. “Outside of large, enterprise companies, there is no on-boarding for cyber [training],” maintains Hoffman. “Small companies just don’t have it.”
One of the major pillars of 2B Cyber Bright is a comprehensive series of animated training videos that address topics such as using VPNs, managing your social media footprint and recognizing ransomware.
“It’s quite amazing how an endlessly useful technology like encryption has found its foul use when in the wrong hands,” states the ransomware video.

“Those hands belong to greedy criminal hackers, out to profit from your misery. What these hackers have done is create a lightweight, lightning fast, sophisticated little piece of software that’s able to encrypt most of the useful files on your computer within minutes of being activated.”
The video offers a series of solutions and tips that help to prevent the user from accidentally downloading the ransomware in the first place.
The videos are populated by characters including a CEO, receptionist, warehouse worker, human resources professional, and high-school student, all of whom might be exposed to or targeted by cybercrime differently. The videos are hosted by a real-life actor who goes by the name Ms. Char CyberBright.
The service will launch in January, with 17 training modules up and running by February. It will be available via the 2B Cyber Bright website or potentially via a third-party model where the curriculum can be licensed out to other trainers. It can be conducted online or in a classroom situation where the videos are used as teaching tools.
2B Cyber Bright has also partnered with STOP. THINK. CONNECT., a cybersecurity awareness campaign comprising a coalition of private and public organizations and managed by the National Cyber Security Alliance and the Anti-Phishing Working Group.
— Neil Sutton

Michael Tryon is a Cisco veteran of 15 years. He moved into the Cisco Canada operation earlier this year, taking over the role of director of cybersecurity.
Tryon says his main focus is educating the customer on the constantly evolving challenges that come with network security. Older models, like viewing a network as the castle and perimeter defence solutions as the moat no longer fit, he says. The perimeter has eroded, or more accurately, has multiplied, creating more surfaces that might be targeted or attacked.
The number of potential attackers has also increased. “For every defender, there’s three to five attackers targeting our environments every single day,” he explains. For smaller organizations, the challenges are more intense, as they may
lack the resources that enterprises can spend on defending their networks. The owner of a small business may also be its de facto IT manager or CISO.
Cisco offers multiple approaches, adds Tryon, including changing the mindset from threat defending to threat hunting, i.e. becoming a more active agent in cybersecurity.
There’s also a greater recognition that people, rather than technology, may be the key to a good cyber defence. “The primary weak link in the chain is always going to be you and I — the human element,” says Tryon.
“We know that people aren’t breaking in, they’re logging into networks. That’s because it’s the easiest way to gain entry into anybody’s environment,” he says, alluding to the fact that it’s more effective
to trick a user into giving up their password than trying to guess it or hack a network through brute force.
“It starts with largest attack vector, which continues to be email. We know how many people are susceptible to email phishing campaigns,” he adds.
The biggest weapon in Cisco’s arsenal is its Talos Intelligence Group, which blocks about 20 billion threats a day and is the largest non-governmental threat intelligence organization in the world, according to Tryon.
Private and public institutions have a “collective responsibility” to promote good cybersecurity practices, he says. The challenges may seem vast, but there is an “acceleration of acknowledgement” regarding those challenges.
— Neil Sutton





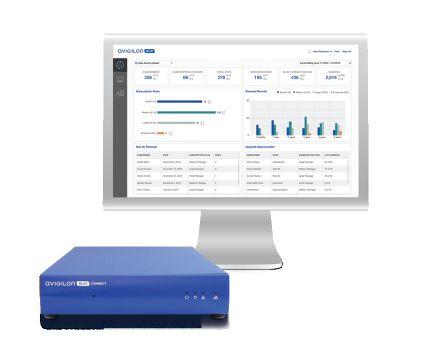
Avigilon Blue™ – our powerful integrator cloud service platform for security and surveillance – is rapidly expanding with new features and updates.

SureView Systems Immix® Integration
New integration with SureView Systems provides powerful video analytics-based event verification to central alarm monitoring stations.
Subscription Centre
A unified view of your business to help you track and analyse customer subscription data.
16-Channel Avigilon Blue Connect Device
Connect to the cloud, add analytics and manage more cameras. Includes 12 TB of onsite storage capacity for up to 30 days of video.
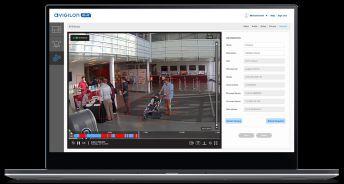
Remote Camera Disarm/Arm Feature
Conveniently pause notification alerts directly from your mobile device.
Timeline Scrubber
Search specific points on the timeline and scrub multiple cameras simultaneously with synced views.
As the platform continues to expand, new features and services will be added that are designed to help your business grow.
Silvia Fraser, head of security, City of Mississauga, was named Security Director of the Year 2018 by Canadian Security magazine’s editorial advisory board for her diligence and work towards establishing goals for her department in coordination with the city. Judges were particularly impressed by the fact that she accomplished so much in her first year as security director.

Fraser celebrated with friends, colleagues and well-wishers at a gala event sponsored by Anixter Canada on Oct. 24 in Toronto. She thanked her staff and mentors for their support and also acknowledged the strides other women have made in the field of professional security. She said accomplished women, like previous Security Director of the Year winner Carol Osler, have been a tremendous inspiration.





ASIS Toronto’s annual Women in Security event, held Nov. 15, focused on changing attitudes towards diversity in the industry, as well as the value of networking and mentoring in career development.
Keynote speaker Rosanne Manghisi reflected on her career as a police officer in the New Jersey State Police. She now works as senior vice-president and chief of staff for SOS Security, a New Jerseybased security solutions provider — a company she says actively promotes women into leadership roles.
Manghisi dispensed career and life advice to the assembled ASIS Toronto members, suggesting that finding a good mentor can make a radical difference in a

person’s outlook and career development. Do you want to learn and do you
want to listen? said Manghisi. You have to be willing to listen. Have a career plan, she added — and run that plan by your mentor. Also, support your mentors — recognize their accomplishments by, for example, nominating them for an award.
Manghisi said she writes notes on the business cards she receives through networking — they help her remember the person and important takeaways from the conversation. “I always carry my business cards,” she said, “because you never know what door might open.”
One of the major themes of Manghisi’s presentation was “Lift as you climb” — strive in your career but also support those around you as you succeed.



You may stumble when implementing an ESRM strategy, but it’s worth the journey
Every ESRM program requires continuous monitoring, awareness and adjustment to keep moving forward.
As I look back on 2018, I try to reflect on what the year has taught me, both personally and professionally. I’ve had an interesting year in both aspects, but I’m not unique. What’s different for me was the discussions I had with security professionals across the globe, and their understanding (and in many cases, acceptance) that a risk-based approach to security can really work.
than just coincidence security professionals I was briefly talking to during the early part of the year were asking for guidance on how to begin developing their own ESRM-based security program these past few months.
”It’s amazing what can happen when you allow yourself the opportunity to adjust your strategy.”
Earlier this year, I was worried. Worried that I had gambled everything both personally and professionally on Enterprise Security Risk Management. Worried that we, as an industry struggling to become a profession, had placed so much importance on ESRM. We were promoting it every chance we could through ASIS, were highlighting ESRM at sessions across GSX, and I was speaking about ESRM at every conference or event that would have me.
The first half of this year was difficult at times, trying to divine some sort of sign that ESRM was taking hold, that business and security leaders would see the benefits of this “new” approach to developing a security program. Others and I made personal sacrifices, learned hard lessons and had to adjust our own strategies to try to “keep the faith,” hoping that what we had started would begin to take hold, to resonate across

And then, it started. Gradually at first — a productive client meeting talking about refocusing their existing security program to reflect the principles of ESRM, a well-received presentation or even a call out for help to find resources to run ESRM workshops within a fellow security professional’s company. It was more
The courses and education programs conducted at GSX brought more attention, more focus, and more volunteers to the global ESRM program managed by ASIS. I finally believed things were starting to change for the better. It felt like those first days of spring, when the ice begins melting from the rooflines, and you can feel the warmth of the sun embrace you as you eagerly enjoy a lunchtime walk.
As 2018 draws to a close, I feel a renewed energy and a restored faith that ESRM is really the most effective approach an organization can take to reduce the risks facing their people, property, and information. I’m not trying to preach this as a religion — although I do identify myself as an ESRM evangelist! No, what gives me hope now are the comments, emails and phone calls I get from security professionals I’ve met at a conference, or who have read this article. Folks who are genuinely interested in learning more about ESRM and how it can be incorporated into their organization.
In many ways, I applied the principles of ESRM to my own personal and professional choices. I had to take stock of what was important to me (what are my goals, what are my assets, and what was crucial to my personal and professional success), look at the risks to these assets (challenges to my belief system, struggling to remain positive against difficult situations), and then identify what paths I needed to stay on (or move away from) to achieve my objectives (my personal risk mitigation strategy). It sounds a bit corny, I know. But it’s amazing what can happen when you allow yourself the opportunity to adjust your strategy and deal with your risks.
Tim
McCreight is the manager, corporate security (cyber) for The City of Calgary (www.calgary.ca).
Canada’s only national not-for-profit security solutions provider.

Fresh ideas and diverse backgrounds help us address new challenges in security
In the face of an evolving security landscape, the paradigm shift of managerial attitudes towards security risks and the public’s perception of the threat environment can be defined as either a tremendous opportunity or a daunting challenge.
In reaction to this changing threat environment, the physical security industry has matured over the past decade. While asset protection remains at the industry’s core, it has evolved from a focus on “people, places and products” to include “reputation, information and environment.”
stereotypes continue to abound in security — whether it is a perception that the industry consists primarily of security guards and private investigators, or that executive protection is restricted to former military or law enforcement personnel, or that security certifications are mandatory prerequisites for security positions.
“Staff with unconventional backgrounds can point out the elephant in the room.”
The question remains, are the right people in the right places to address developments in security technology, criminal trends or risk methodologies? I propose that there are still opportunities for the industry to reflect on how to build their teams for the future while leveraging skillsets outside the traditional security field.
My unconventional entry into the security field began in 2005, equipped solely with a B.A. in Development Studies. Through diverse professional experience in community relations, volunteer management, event coordination and policy development, I brought inquisitiveness, resourcefulness and communication skills to positions within a national security agency, international financial institution and a municipal government.
I found that my capacity to transition from positions in intelligence, corporate security, protective services, investigations and security risk management was not hindered by a limited (albeit growing) security knowledge base. Rather, my advancement was built upon competencies to translate knowledge into action, strategy and tactics.
A few years ago, while waiting at an airport luggage carousel, a member of a business executive contingent was surprised to hear that I was part of their security delegation. Sardonically, he asked if I was “carrying” in my purse. I pointed to my head and replied, “Security starts up here.”
This experience highlights that
While all of the above are valuable components of effective security teams; looking to hire outside the lines can also attract individuals with fresh, innovative perspectives. Staff with unconventional backgrounds can often point out the elephant in the room and expand the team’s capacities.
To assess whether or not a security team is built to attract diverse perspectives and skillsets, consider:
• What story is depicted in the organizational chart? Does it visually describe the mandate? Are its foundations broad enough to address the corporation’s mission and vision in five years?
• How do current job titles and position descriptions reflect the core competencies required to build a successful team? While certifications (e.g. CPP, PSP, CPTED, IALEIA) provide theoretical knowledge of industry standards, credentials cannot replace staff proficiencies to conduct comprehensive risk assessments, successfully deploy de-escalation tactics, or clearly communicate complex security terminology to stakeholders. How effectively do job descriptions filter or attract qualified candidates?
• Is there opportunity to leverage consultants or collaborate with other business units? What insights can adult education specialists bring as training coordinators? Can an engineer with project management experience be tapped to design innovative security system frameworks?
Security teams filled with individuals from diverse backgrounds have better toolkits to face the security challenges of tomorrow.
Camille McKay is the manager, security risk at the City of Mississauga, Ont. (www.mississauga.ca).

Social media can be a powerful tool for both intelligence and outreach, but crafting your communications requires skill and timing
By Ellen Cools
As the “social media generation” matures, it’s becoming increasingly normal to hear of people learning about crises via social media.
Unlike traditional media, social media allows users to share information and create a conversation. In a crisis, it even allows them to become the “boots on the ground,” providing real-time updates.
Consequently, companies and authorities involved in an emergency need to understand how to use social media, both to gather information and to communicate with stakeholders.
But with billions of users and massive amounts of
information available at your fingertips, the challenge is figuring out how to get a clear message out amidst all the noise.
“An actual investigations solution tool”
The first step to doing that is to understand how social media’s role in crisis communications has evolved. According to Suzanne Bernier, president of SB Crisis Consulting, it has evolved very quickly, especially in the field of emergency management.
For her, the defining moment was Hurricane Sandy in 2012. Social media enabled cities, emergency management authorities and first response agencies to be extremely efficient in informing people about the storm, how to prepare, and what to do afterwards, she says.
Any organization or authority impacted by the hurricane was using social media to share information, even the local power authority, she says.
“We’d really never seen that kind of social media communication from that kind of entity,” she adds.
But not only has social media become a way of sharing information, it’s also a way for authorities to gather information,


says John Rainford, director of the Warning Project.
Social media has transitioned from being a “one-way information dissemination tool towards an actual investigation solution tool,” he says.
For Rainford, the watershed moment was the Boston bombings in 2013.
“The authorities there turned a corner and they said, ‘Wow, this social media world actually has incredible potential for us to gather intelligence about what’s actually occurred,’” he explains. “They had an active investigation going on … and they used social media to say, ‘We need help.’”
Security institutions and law enforcement agencies asking the public for help is nothing new, he admits; communication tools such as hotlines have been available for years. But social media acts like a “supercharger, making it a lot more dynamic and intense,” he says.
Beating the noise
useful tool,” adds Rainford. “But then it can also be a really, really destructive tool, in that you can see examples of online vigilantism, you can see examples of wild rumour and misinformation being spread in the age of fake news.”
Additionally, given the number of users on social media, authorities can be overwhelmed with information when asking for the public’s help.
“There has to somebody dedicated to [social media] who has some experience and tact.”
— Duncan Koerber, Brock University
“You’ve got an active threat situation, an active disaster situation — what value is this if you can’t process it?” Rainford asks.
“For authorities, the key is understanding what misinformation and rumours really, really matter,” he says.
Misinformation about a government minister being involved in a scandal, for example, isn’t as important as misinformation about where people should shelter during a crisis.
Nevertheless, this “supercharger” can have its downsides. In the event of an emergency, such as a terrorist attack or natural disaster, it can be difficult to get a clear message out to the public.
“It’s very hard to get that message out if there are people on the front line, just average citizens, using Twitter to send images, videos, that kind of thing — it’s very hard to wade into that and stand out from that on social media,” says Duncan Koerber, assistant professor at Brock University and the author of Crisis Communication in Canada
“Engaging through social media can be a really, really
“Misinformation where we want people to head north to get away from the nuclear fall out cloud [as opposed to south], that’s very, very different…We saw this in Fukishima, where misinformation there resulted in people, instead of moving away from the potential radioactive zone, moving towards it.”
To beat the noise, “You’ve got to process all the information so you understand what’s out there, and then you have to decide what’s important,” he says.
Information processing tools can help make that determination, but it’s still up to emergency responders or security experts to decide what is important.
Accomplishing that is “the next frontier in terms of how

Incorporating SALTO’s proven reliability and stability in cloudbased access control, SALTO KS - Keys as a Service - offers a solution that every business is looking for with vastly better functionality and performance than is possible with a traditional solution.


SALTO SYSTEMS INC.
950 Rue Valois, Suite 104
Vaudreuil-Dorion, QC, J7V 8P2
Phone: 514-616-2586
Email: info.canada@saltosystems.com www.saltosystems.com
SALTO KS provides a flexible access control management system that requires no software installation or the added expense of a fully-wired electronic product. All that is needed is an online device with an Internet connection.
www.saltoks.com


we use social media as a good response tool,” Rainford believes.
But it’s not just the authorities and decision-makers who have to search through all the information on social media — the public has to as well.
To do so, Bernier encourages people to visit the websites and social media accounts of recognized sources, such as first response and emergency management agencies.
Koerber agrees, but adds, “if those official accounts are not responding right away, then that’ll be a problem.” The public will then turn to regular users’ accounts.
“That puts a burden on the official communicators … to get something our right away, within seconds or minutes of a crisis,” he says. “[It] can be really challenging to satisfy that need.”
Crisis communications plan
One way to satisfy that need is by following a crisis communications plan, says Bernier.
organization’s senior members, he adds.
Additionally, organizations need to cultivate an online following.
“You’ve got to be cultivating communities around your social media accounts so that when a crisis does occur, then you’ve already got those networks set up,” says Koerber. “You can’t just sit around with an account of 50 followers and then expect that in a crisis, people are going to jump to that account, because they’ll have no awareness of it.”
“Every single crisis is going to have some kind of social media Tweet or Facebook post.”
— Suzanne Bernier, SB Crisis Consulting
While Rainford agrees that having a crisis communications plan is crucial, he argues that organizations also need to “take it to the next level [by having] some kind of listening function embedded in what’s going on.”
This plan should address who the spokesperson will be and how the organization will use social media, with templates on how to draft a Tweet or Facebook post, she says. Implementing a plan before a crisis occurs is key, she says.
Additionally, she encourages every organization to conduct exercises or drills that include “social media specific injects.”
“That’s one area that I’ve noticed — a lot of communities … sometimes forgetting to include that important piece, because that’s reality now; every single crisis is going to have some kind of social media Tweet or Facebook post or something that’s going to come up.”
These exercises will not only help companies navigate the social media landscape, but can also alert executives to how social media itself could create a crisis, she says.
“A crisis could be created via social media, an inject itself, if you’ve got a negative Facebook post or a negative Tweet about your company or your community,” she explains. “That alone, depending on how you choose to respond or not … could be its own reputational crisis.”
A plan also allows decision-makers to implement their crisis communications strategy if or when an emergency occurs, adds Bernier. A crisis communications strategy outlines how to respond to a crisis immediately after it occurs, while a crisis communications plan outlines how to respond to a crisis more generally.
For Koerber, a key aspect of managing social media in a crisis is dedicating at least one person to manage the social media accounts.
“It can’t be just one of the millions of things one employee has to be monitoring or involved with,” he explains. “There has to be somebody dedicated to it who has some experience and tact with using social media.”
That person should monitor the platforms, look for issues that may become a crisis and communicate with the
“They send out their own message in terms of their understanding of the situation, and then they are acutely tuned in to what the people affected are actually saying and talking about, and then they’re responding in a respectful way to them,” he explains.
This creates a “back and forth” conversation that makes those affected by a crisis feel understood and heard.
In doing this, Rainford believes companies need to take a step back from the traditional approach to communications.
Traditionally, it has been “all about control,” he says. “You don’t speak to the media. You don’t say anything without running it by the communications directors.”
In his opinion, that is an “antiquated reality.”
For example, during a measles outbreak, people were undermining a health organization’s efforts to vaccinate kids by spreading rumours and misinformation online.
The organization’s communications director argued that a traditional communications approach, such as a press conference, was not working. Instead, he wanted to give nurses the authority to share their views with the public and speak on behalf of the organization via social media, Rainford continues. The executives agreed.
“This was a huge risk — what if they have a Twitter war, what if they freak out and say something stupid?” he asks. “These were all risks that were there, but you know what? The people that were involved in those conversations … they responded so well to that direct interaction.”
In the end, the “vaccine hesitancy” was lowered and the health organization got more parents to vaccinate their kids, he says.
But there are concerns about legal liability in giving employees control of corporate social media accounts, Rainford admits.
“But for an organization in terms of their reputation, in terms of their market, in terms of their standing, in terms of their trust levels, there’s huge risk in not saying anything,” he argues.
But what about when it comes to giving employees access to social media at work? How should companies govern their
employees’ use of social media?
“There should be policies in place for people using these things,” says Koerber. “I don’t think they should be banned from using them. But it’s really important to have training on this because every day we see employees of organizations doing something that causes a problem — public relations problems — for organizations.”
Five years ago, adds Bernier, several companies had rules in place prohibiting employees from using or accessing social media during work hours, and posting to social media in a way that did not positively represent the organization, adds Bernier.
“But I think that nowadays, it’s also really important for companies to encourage their employees … to check out the company Twitter account, the company’s Facebook page,” she says.
tool, Rainford says the “value exceeds the risk.”
For security professionals, it gives them the “ability to gain more perspective of what’s actually going on, on the ground with people who are using social media,” says Bernier.
“You’ve got to process all the information so you understand what’s out there, and then you have to decide what’s important.”
— John Rainford, The Warning Project
Additionally, social media has become such an important part of the majority of peoples’ lives that ignoring it often comes with a price.
Rainford therefore argues that social media should be integrated into a mass communications plan, and that companies should take a more holistic approach.
Then, during a crisis, those employees will share the information sent out on the corporate social media accounts.
“Value exceeds the risk”
When it comes to using social media as a crisis communications

Sébastien BoireLavigne is EVP and CTO for XMedius (www.xmedius.com)
For IT professionals, cybersecurity has always been a central focus, but it may have moved higher up on the priority list.
An organization’s fax lines can serve as yet another potential entry point for hackers. The vulnerability allows hackers to take over a fax device (dedicated fax machine or multifunction device) and spread malware through entire corporate networks.
Here are some steps to take to ensure your organization is protected.
“If you just focus on TV and radio and print, you’re likely going to have a big problem on your hands,” he says. “If you only focus on social media, you’re likely going to have a big problem on your hands. I think the key for planning would be to think of it as one big media landscape.”
“It’s really important to recognize that social media now is not replacing how we used to communicate traditionally during a crisis and get those messages out,” adds Bernier. “It’s just now giving us additional ways to do that if we can.”
Determine which fax devices are being used in your organization
These are the devices that have been sitting there with virtually no security in place and have likely fallen under the IT radar, but still could serve as an entry point. Once these devices have been located, unplug the phone lines from the ones not actively used for faxing.
Check for manufacturer security patches
Once the fax-capable and connected devices have been identified, make sure to follow through with any and all of the latest security patches. It is also a good idea to stick to a regular patching schedule.
Use network segmentation to keep your faxing separate and under control. Keeping the organization’s faxing devices on a segmented subnetwork not only
prevents fax traffic from reaching the general network, it also makes your fax transmissions easier to track. Network segmentation can prevent vulnerabilities like “Faxploit” and also help maintain compliance with regulations like the GDPR.
Consider FoIP solutions
For organizations that rely on faxing, it is time to consider the options. Centralized fax over internet protocol (FoIP) solutions come with several advantages over traditional faxing, mainly that they’re inherently more secure. They centralize communications to a single entry point, enabling organizations to reinforce their critical communications with the same security measures applied to their network. Centralized fax solutions are also easier to protect, update and monitor.


Companies should recognize that workers will sometimes value convenience over IT policies in order to get their jobs done, but that doesn’t mean they have to make themselves vulnerable
By Ching Mac
Do security and convenience have to be at odds?
Here’s a common workplace situation: an employee wants to work from home because she is having her internet installed at her new apartment. The night before, knowing she won’t have internet access at home, she downloads the files to her personal laptop. Though this is against company policy, she doesn’t think she has any other option — she has to access the files somehow. And without access to her work drive from home, it means a big chunk of productive hours lost. So, knowingly or not, she breaks company policy.
When workers feel technology or security protocols hinder their work, they take one of two common paths:
they will bypass protocol and use their own device to complete their work, or their productivity will decrease. When security and convenience are at odds in the workplace, the latter often comes out on top.
This crossroad is typical — and the choice illustrated above is frequent. According to a recent survey from Citrix Canada called The Citrix Cloud and Security Survey, four-in-10 workers feel their employer’s security protocols make it difficult for them to work remotely. The survey, which probed Canadians on their workplace security habits on and offline, also found 63 per cent have shopped or surfed the web on a company device, and 50 per cent have been a victim of a phishing email or an online virus.
This means the opportunity for a breach caused by an employee infraction
is likely. For many companies, there is much to lose (from a reputation standpoint and a financial standpoint) if one does occur, in addition to the potential damage for customers whose information is compromised.
But for company executives looking to bolster their security strategy in an era of wide-scale breaches, and train their employees to take security protocol seriously, convenience and security cannot be at odds. With the right technologies and policies, security can be convenient, and convenience can be secure.
A smart security strategy for any organization is about striking the right balance for employees and employers, and getting IT departments, HR workers, and top-level executives to buy in and lead the way. While mobility is a staple of many workplaces, a survey from 2017

by Oxford Economics and Citrix found only 20 per cent of Canadian companies had a cohesive and integrated mobile strategy in place, demonstrating a gap in organizational security policy.
The key to a mobile workforce that mitigates the risk of cyberthreats is integrating a secure digital workspace with three important attributes. First, it is unified — it has a single window through which IT can configure, monitor and manage the entire technology infrastructure. Second, it is contextual — it uses machine learning and AI to fit each worker’s patterns and exceptions, in order to deliver a personalized experience that reflects the unique work device, location and network connection. Finally, it is secure: it has a software-defined perimeter that grants safe access and full visibility across the network and user ecosystem.
is better suited to the work environments that most employees encounter on a day-to-day basis and can be customized based on job function, seniority level or department, rather than a “one-size-fitsall” security solution.
In some situations, if employees feel the workplace software or device is too complex or consumes too much time, they will opt for their own, often unsecured technology. And if IT managers want employees to be responsible about their data security, it is important that employees understand and accept the technology at hand. IT must be focused on a seamless experience that accommodates employees and employers.
Lastly, the secure digital workspace must be implemented in conjunction with the right processes, training and education programs. This is especially relevant considering Citrix Canada’s survey found three-in-10 are not aware of the security protocols their company has in place. Although it is not necessary for employees to understand all the ins and outs of how they are being secured, HR must continuously develop and communicate security policies to help employees understand why the policies exist, and why buy-in is crucial.
“Four-in-10 workers feel their employer’s security protocols make it difficult for them to work remotely.”
A secure digital workspace with these attributes fills the gap between security policies and flexible work that many organizations are facing today. It
One important way digital leaders are adapting to the demands of the mobile workforce is by implementing a BYOD (bring your own device) policy. With BYOD, companies can use desktop virtualization so employees can access their work desktop on their personal mobile devices. Employees can access information when and where they choose, and employers can control the secure delivery of that information. This satisfies the needs of IT as well, who can keep work apps and data in a centralized data centre, and can monitor, detect and fix any problems to avoid data loss or breach.
Another key component to keeping convenience and security on the same side is to prioritize the user experience.
To have all employees buy in to the security strategy requires not just education, but a culture shift in which security is instilled as a company’s core value. HR must work with C-suite executives to enforce security policies across all levels and engage all C-suite in the discussion on cybersecurity.
Practices upheld and importance placed on security at the top will trickle down, and employees will be more likely to hold themselves accountable and encourage others to do so as well. When employees understand the risks of bypassing security protocols, and their company provides a seamless user experience, breaches are less likely to occur.
The key elements employers and employees are looking for — productivity, flexibility, security — are attainable, but companies must put in the effort to establish the right technology, policies and culture if they wish to see all three realized simultaneously.
Ching Mac is the director for Citrix Canada (www. citrix.com).

OnSSI
OnSSI has released Ocularis 5.6, the latest update of its video management software. Ocularis 5.6 allows administrators to require dual operator authentication when logging in and the ability to specify system permissions for Ocularis Client or Ocularis Web/ Mobile. Every login activity into Ocularis Client is also logged and auditable for documentation and compliance where applicable. Operators can now create, edit, save and delete views directly from Ocularis Client. Users have the ability to view camera names from a number of views. Ocularis Mobile now also includes the ability to display multiple cameras in live mode while disabling the IOS idle timer to ensure continuous remote viewing. www.onssi.com
March Networks

Recording solutions
Hanwha Techwin

QRN NVRs (network video recorders) provide high-performance recording solutions for smaller installations such as offices and retailers. Customers can save on both installation costs and time by using the Wisenet Q series cameras together with the new Wisenet Q series PoE NVRs. The PoE ports negate the need for the provision of separate power cables and plug points for each camera or the need for an external PoE switch. QRN NVRs support Hanwha’s WiseStream compression technology to improve bandwidth and storage efficiency for high resolution images. The QRN-410S 4 channel models support 40Mbps network camera recording. The 8 channel QRN-810S models can record up to 80Mbps, while the 16 channel QRN-1610S models can record up to 128Mbps. QRN NVRs provide easy remote access configuration via the Wisenet Mobile App using a QR code. The recorders are fully compatible with Wisenet WAVE VMS (video management software). www.hanwhatechwin.com
American Dynamics
March Networks has introduced a new software as a service (SaaS) offering for convenience stores. The hosted service, Searchlight for Retail as a service, features loss prevention, data analytics and operational audits reporting. March Networks Searchlight integrates surveillance video with point-of-sales (POS) transaction data and analytics, enabling retailers to proactively detect fraud, theft and reduce incident investigation times by up to 90 per cent. Searchlight for Retail as a service is hosted at Amazon Web Services and managed by staff in March Networks’ secure Network Operations Centre (NOV). It includes all software licensing and camera and recorder processing, health management, upgrades and administration, including user management.
www.marchnetworks.com
The Platinum Enterprise Level 32 Channel Deep Learning NVR, LTN0732D-R8, features the latest in deep learning technology and integrates advanced algorithms built for perimeter prevention. The Deep Learning NVR is built with nearly the same precision of a human eye, according to the company, identifying objects versus human intrusion and reducing the number of false alarms. Smart Motion Detection is inspired by the brain’s ability to process data critically and works to understand the human body through enhanced secondary analyses like face detection and object analytics. The Platinum Enterprise Level Deep Learning NVR integrates to existing IP cameras and security infrastructures.
www.LTSecurityinc.com

The victor Video Management System and VideoEdge Network Video Recorders version 5.2 provides enhanced video intelligence and analytics. The victor client on VideoEdge hardware platforms allows users to leverage high-performance video streaming, audio, motion meta-data and an expansive feature set. The combination of victor and VideoEdge maximizes smart streaming resources to optimize operation of high-resolution cameras and robust analytics while providing more efficient bandwidth management. www.americandynamics.net


VIGIL V500 Hybrids are fully-integrated intelligent video appliances preconfigured with VIGIL Video Management System (VMS) software. The V500 design provides all the network components required to deploy this NVR. Not only are alarm, serial, and audio inputs built in, this hybrid includes 16 embedded PoE ports for IP devices. The V500 also integrates with the full VIGIL suite of products. VIGIL’s MULTIVIEW Technology and its RapidStream video compression engine enables users to remotely stream and view high-definition video with minimal impact on network bandwidth. VIGIL V500 Series NVRs feature many built-in capabilities: two-way audio, easy-to-use Smart Search, and integration with VISIX V-Series analytic cameras. The V500 Series includes the Easy Setup Wizard to allow those with no IP video experience to install the NVR and start recording and viewing video.
www.3xlogic.com

• Security guards
• Mobile patrol and alarm
• response teams
• Event security
• Executive protection
• Investigations and consulting
• Loss prevention
• Concierge services
• Travel security The best range of security services in Canada