

















The future belongs to those who can imagine it, design it, and execute it
There are leaders, and then there are visionaries, the kind who see skyscrapers in sand dunes and smart cities where others see limits. H.H. Sheikh Mohammed bin Rashid Al Maktoum, Vice President and Prime Minister of the UAE and Ruler of Dubai, has never just led, he has relentlessly imagined, built, and accelerated the future.
As we celebrate his birthday, it’s not just a tribute to a statesman, but to an architect of modern ambition, one whose achievements have redefined how nations think about innovation, technology, and the art of what's possible.
Long before "smart city" became a buzzword, Sheikh Mohammed was coding Dubai’s future.
The launch of Smart Dubai aimed to make the city not just digitally advanced, but intelligently humane, optimizing everything from government services to traffic lights using data and AI. Today, Dubai is paperless, wireless, and virtually timeless in its ambition.
Dubai Internet City was launched in 2000, planting the seeds of the region’s tech ecosystem. It’s now home to global tech giants and regional unicorns, all operating in a sandbox Sheikh Mohammed envisioned decades before tech hubs became cool.
Some chase the stars. Sheikh Mohammed sends missions to them.
Under his leadership, the UAE launched the Hope Probe to Mars, making it the first Arab nation to reach the Red Planet. it was a statement: We belong to the future, not the past.
From founding the UAE Space Agency to announcing the Emirates Lunar Mission, his belief in homegrown talent and deep-space vision is boldly unapologetic. With initiatives like One Million Arab Coders, Sheikh Mohammed sparked a regional movement. The goal: empower Arab youth with digital skills, turning passive users into future innovators.
The UAE became the first nation to appoint a Minister of Artificial Intelligence, embedding AI into governance and public life with proactive strategy, not reactive panic.
Where bureaucracy often drags innovation down, Sheikh Mohammed's governance model elevates it. He declared the goal of a paperless government by
Impossible is a word used by some people who fear to dream big.
Today, Dubai government services are available 24/7, fully digital, and often powered by AI.
Thanks to his vision, Dubai is now a gravitational hub for:
• GITEX Global – the region’s biggest tech expo.
• Dubai Future Foundation – incubating bold ideas in AI, robotics, and bioengineering.
• Museum of the Future – not just an attraction, but an active research platform.
• Expo 2020 Dubai – a celebration of human progress and connectivity.
Behind every megaproject is a mindset. Behind every vertical garden, autonomous taxi, and blockchain integration is the belief that tomorrow is a team project, and leaders must engineer the climate where it thrives.
Sheikh Mohammed’s legacy isn’t static, it’s scaling.




The most critical story of our time is cybersecurity. Not because it is new, but because it is necessary. It touches every institution, every economy, every individual. Governments are quietly targeted. Critical systems are breached.
Societies face threats they do not fully understand. Behind these incidents lies structure. A growing network of actors operating with intent and precision. Cybercrime is no longer a side issue. It is a core challenge to global stability, national governance, and personal freedom.
Much of the narrative remains surface level. But the deeper questions, of responsibility, resilience, and consequence, demand more attention.
That is why TECHx Media exists. Not to echo the noise, but to explore what others overlook. Not to promote, but to investigate. Cybersecurity is not just technical. It is institutional. It is political. It is human.
CHAIRMAN



Resilience is the new currency of leadership. And
transformation, they are also opening new frontiers of risk. From AI hallucinations to deepfakes, from state-sponsored attacks to insider breaches, cybersecurity is no longer just a
At the board level, we must move beyond reactive policies and embrace cybersecurity as part of the organization’s ethical and economic infrastructure
It's not only about preventing loss, it's about preserving stakeholder trust in an era where trust is everything.
This is a defining moment. The companies that embed cybersecurity into their DNA, not just their IT departments, will be the ones that lead in a future where risk is constant and
EXECUTIVE BOARD MEMBER

We are TECH x Media, officially registered with the UAE's National Media Council. As a media platform dedicated to addressing the media and marketing needs of the tech ecosystem, we have built a strong reputation as a trusted partner for leading global vendors, distributors, government entities, and major global tech events. With a proven track record of providing comprehensive industry coverage, our team of seasoned professionals and tech journalists, boasting over 150 years of combined expertise, delivers the latest technology insights, backed by in-depth analysis and creativity.

There’s no firewall strong enough to protect a blind spot. In this Code RED edition, we spotlight the growing collision between global supply chains and increasingly sophisticated cyberattacks. What used to be a logistics concern is now a digital battleground, where malware, ransomware, and zero-day exploits have become as disruptive as port closures and raw material
Supply chains today span thousands of partners, vendors, platforms, and endpoints, each a potential point of failure.
Our reporting dives into the anatomy of modern cyber-supply chain attacks, from initial infiltration to final fallout. We talked to CISOs, security analysts, and cyber heads who are living the new reality: that one overlooked integration or outdated patch can take down entire systems.
Cybersecurity is everyone’s business and the first step is knowing where the risks really lie.



Cybersecurity is no longer a backend function, it is the backbone of business resilience.
World is in constant disruption, from AI breakthroughs to geopolitical shifts, digital threats have evolved from isolated attacks into systemic risks.
Cybercrime is projected to cost the global economy over $10 trillion annually in the coming years, not just from stolen data, but lost trust, broken supply chains,and destabilized industries.
Our mission is to spotlight the evolving threat landscape while equipping business leaders with clarity, not just fear. Through beyond alerts, we provide frameworks for action..
This is not just about technology. It’s about culture, accountability, and building smarter systems at every layer of business.
The organizations that thrive in the next decade will be those that treat cybersecurity not as a cost center, but as a competitive edge.
CHIEF EXECUTIVE OFFICER

Editorial: +971 50 100 2275 Sales: +971 50 300 4450 Events: +971 50 700 7216 Marketing: +971 50 800 8341













Cybersecurity is the integral pillar of all of this digital transformation… with these technologies … we need to build the culture of cybersecurity



We are in an age where toddlers swipe before they speak and every app comes with a trail of data, cybersecurity has become far more than a technical concern, it’s a way of life. And in the UAE, no organization has embraced this reality more comprehensively than the Cybersecurity Council.
Under the leadership of His Excellency Dr. Mohamed Al Kuwaiti, the Council has emerged as a national force for awareness, prevention, and empowerment. From policy halls to living rooms, its initiatives are building a digitally resilient society, one informed citizen at a time.
In a powerful example of community engagement, the Council recently hosted an awareness session titled “The Role of the Family in Cybersecurity Prevention” on Friday, 27 June 2025, in partnership with Abu Dhabi Majalis at the Office of Citizens and Community Affairs – Presidential Court.
It was a dynamic, well-attended event that fostered genuine dialogue between cybersecurity specialists and the public. Parents, educators, and community leaders came together to better understand how families, not firewalls, are often the first and most critical line of defense in protecting children from digital threats.
While the session didn’t release formal quotes, the Council shared that Dr. Al Kuwaiti emphasized the vital role families play in cybersecurity resilience, particularly as smart technologies and artificial intelligence become everyday fixtures in children's lives.
The Council’s commitment to public education extended further as it participated in the Drug Prevention Forum 2025, showcasing the inextricable link between digital safety and broader social resilience.
One highlight was the Council-led session titled “Cybersecurity Fundamentals of Personal Data Protection in the Digital Age”. The aim? To arm attendees with the knowledge needed to safeguard their personal data and understand how cyber awareness intersects with emotional and behavioral health especially among youth.
Throughout the forum, running until June 29, the Council offered daily awareness workshops, covering topics such as:
• Data privacy best practices
• Identifying digital manipulation and social engineering
• Online safety for children and teens
• Cyber hygiene for families and seniors
These sessions are presented by Council-affiliated cybersecurity experts and designed to be accessible to the general public, proof that national security can, and should, be a household conversation.
The Cybersecurity Council isn’t stopping at events. It has laid the groundwork for a sustained national movement, delivering education and resources through a multi-channel strategy that includes:
• Outreach in schools and universities
• Digital campaigns across social media
• Partnerships with tech providers
• Specialized training for frontline government and private sector staff
These programs reflect Dr. Al Kuwaiti’s long-standing commitment to embedding cyber awareness into the cultural fabric of the UAE. As he said at the 2022 Cybertech Global Conference:
The Council’s strategy is as practical as it is visionary. Rather than treating cybersecurity as a technical addon, it’s reframing it as a lifestyle, a conversation, and a personal responsibility, one that spans generations and communities.
As the UAE continues to lead in technological innovation, from AI integration to smart city infrastructure the Council’s role will only grow in relevance. Its work ensures that every digital advancement is met with equally robust awareness, preparedness, and protection.



In 2025, it’s not the hackers breaching your firewalls that should keep you up at night. It’s the vendors you trust the most, the small software firm managing your data sync, the overseas hardware supplier, or even your outsourced payroll provider.
Cybercriminals are no longer attacking the front doors of the world’s most secure enterprises. They’re slipping through the side gates, quietly piggybacking on the digital supply chains that keep global business ticking.
Verizon’s 2025 Data Breach Investigations Report (DBIR) highlights this troubling trend with hard numbers: one in three breaches now involves a third party. The percentage of incidents tied to partners or suppliers has doubled from the previous year, underscoring how deeply embedded these risks have become. What’s more, ransomware, often delivered via these indirect attack paths has seen a 37% increase, now factoring into nearly half of all reported breaches.

Take the Hertz incident earlier this year. The car rental giant itself wasn’t hacked. Instead, the Russian-linked ransomware gang Clop infiltrated Cleo Communications, a trusted third-party file transfer provider used by Hertz and gained indirect access to sensitive customer information. By exploiting an unknown vulnerability in Cleo’s software, the attackers avoided Hertz’s own hardened defenses altogether.
This tactic, often called a supply chain attack, isn’t new. But what’s changed is how quickly it’s become the go-to method for sophisticated cybercriminals, including state-backed groups. Why try to breach a billion-dollar enterprise with enterprise-grade security, when you can compromise a smaller supplier with minimal resistance and get the same prize? The damage from these attacks goes far beyond lost data or a ransom paid. They undermine trust in entire ecosystems. If an organization can't vouch for its vendors' security posture, how can it vouch for its own?
Supply chains have always been complex. But now it has also become invisible. Many large enterprises now rely on thousands of vendors, software-as-a-service providers, open-source libraries, cloud partners, APIs, and more, creating sprawling digital ecosystems where a single weak link can compromise an entire network.
Recent data shows that software supply chain incidents are sharply on the rise. According to Cyble, the average number of such attacks per month increased by 25% from late 2024 to mid2025-. In the last two months alone, this number nearly doubled. Attackers are getting more strategic, more patient, and more effective at exploiting interdependencies between systems that most companies barely map, let alone monitor.
Credential abuse remains a leading cause of breaches, with nearly a quarter of attacks stemming from stolen or weak credentials. Vulnerability exploitation is close behind, accounting for 20%. These numbers reflect a sobering reality: as businesses grow more interconnected, the attack surface is no longer within their walls.
Certain sectors are feeling the burn more than others. Healthcare, with its sensitive patient data and critical uptime requirements, remains a prime target. The DBIR found 1,710 incidents in the sector this year, with over 1,500 involving confirmed data disclosure. The most compromised data types? Medical and personal. Manufacturing is facing a different but equally insidious threat: espionage. Breaches in the industry
nearly doubled this year, and for the first time, 20% were tied to espionage, up from just 3% the year before. Analysts believe this rise is likely linked to state-sponsored actors targeting supply chains to access emerging technologies and industrial secrets.
Meanwhile, the financial and education sectors continue to grapple with familiar foes: phishing campaigns, credential stuffing, and basic web application attacks. But the thread tying all of these sectors together is supply chain vulnerability. Regardless of industry, the weakest point isn’t the organization, it’s often the people and partners just outside of it.
Despite years of warnings and a growing pile of headlines, many organizations still don’t conduct comprehensive security reviews of their suppliers. Some don’t even know how many third-party services are connected to their systems. A recent survey found that fewer than 30% of enterprises require a Software Bill of Materials (SBOM) , a basic inventory of components used in applications, from their vendors.
The regulatory landscape is beginning to catch up. New compliance mandates in the U.S., EU, and GCC region are placing greater onus on companies to verify vendor security. In the UAE, cybersecurity requirements tied to national digital transformation efforts are already pushing public and private organizations to step up. But policy alone won't solve the problem.
Security teams must rethink their architecture from the ground up. The old model, perimeter defense no longer applies in an age where the perimeter includes thousands of third parties. Strategies like Zero Trust architecture, real-time threat intelligence sharing, and continuous monitoring of third-party behavior are no longer “nice to haves.” They are essential.
The phrase “a chain is only as strong as its weakest link” is now a cybersecurity cliché. But in 2025, it's painfully accurate. As enterprises double down on digital transformation, AI tools, and cloud-first strategies, their reliance on supply chains will only deepen. That means vigilance can't stop at the firewall, it must extend across every digital handshake.
Because in today’s cyber era, the breach you didn’t notice might just be the one that shuts everything down.






















In the digital age, it’s not the biggest or fastest companies that win, it’s the ones that are secure. As cyberattacks become increasingly sophisticated, no organization is immune, especially early-stage startups. Once seen as too small to target, startups are now sitting ducks in a world where hackers don’t discriminate.
To understand what’s at stake and what emerging businesses should do, we sat down with Vivek Chandran, cybersecurity expert, thought leader, and founder. With years of experience across startups and enterprises, Vivek brings a grounded, tactical view of the evolving threat landscape, and how startup leaders can survive and thrive in 2025 and beyond.
What are the top cybersecurity threats that startups should be most concerned about in 2025 and the coming years?
The cybersecurity threat landscape isn’t what it was even five years ago, it’s evolving constantly. That’s the first thing startups need to understand: it’s not a static problem. The tools and tactics used by cybercriminals change every few months, if not weeks. If I had to pick the top three threats right now, AIenabled cyberattacks would top the list. We’re seeing a rise in sophisticated attacks powered by artificial intelligence, from deepfake phishing to automated vulnerability scanning and exploitation. These are faster, more adaptive, and harder to detect than traditional threats.
Second, and this may surprise some, is human negligence. It's not a “threat” in the classic sense, but it’s often the root cause of security breaches. You can spend millions on tech, but one employee clicking the wrong link can still bring the system down. Humans remain the weakest link.
And third, phishing is still a huge problem. It's oldschool, but highly effective. Startups are particularly vulnerable because they often lack the infrastructure to detect and respond to social engineering attacks quickly. Phishing doesn’t need to be advanced to be dangerous, it just needs to be convincing.
Winning the Best Innovative Product Award at GISEC is a big milestone. What did that recognition mean for you?
Winning the Best Innovative Product Award at GISEC was a defining moment for us. As you know, GISEC is one of the most respected cybersecurity events globally. To be recognized on that stage among
hundreds of groundbreaking technologies and startups from around the world was both humbling and validating. It reinforced that we are solving a truly urgent problem in a differentiated and unique way.
Our platform stood out because it doesn't just highlight cyber risk, it quantifies it. Through meaningful use of AI, we compute a cyber hygiene score, loss prediction models, and automate compliance, enabling a new way to measure and manage cyber resilience, especially in the context of cyber insurance.
This award has amplified our visibility in the global cybersecurity ecosystem. The event itself brought together a global community of innovators, cybersecurity professionals, enterprises, and startups, and the scale of participation was truly impressive. We had the opportunity to directly engage with key stakeholders, including CISOs from large corporations and security professionals across multiple domains.
What really stood out was the urgency of the conversations. As I mentioned earlier, cybersecurity is no longer just an IT issue, it’s a business and national resilience imperative. The event provided global exposure and connected us with extraordinary minds from all over the world, each working on real, impactful problems in cybersecurity. It was an incredible experience and, above all, a global validation of our vision and approach.
How has the cybersecurity landscape changed over the past five years? What trends should startups keep an eye on?
The past five years have been transformational. The biggest disruptor has been AI and, again, it’s a double-edged sword. AI is helping us build smarter, more efficient cybersecurity tools that automate detection and response. But on the flip side, attackers are using the same AI to supercharge their campaigns.
Another major shift is that every new technology introduces new vulnerabilities. AI, blockchain, IoT they all come with their own security challenges. And often, organizations adopt these technologies faster than they can secure them.
Finally, governmental and regulatory forces are playing a bigger role. From GDPR to CCPA and now the Cyber Resilience Act, we're seeing a global trend toward mandatory cybersecurity compliance. This is actually a good thing it forces businesses to maintain at least a minimum viable security posture.
VIVEK CHANDRAN CEO RISKNOX Private Limited

Should cybersecurity be a legal responsibility for startups, or is that too ambitious at an early stage?
In an ideal world, yes, cybersecurity would be a legal responsibility for every business, regardless of size. But in the real world, especially for startups, it’s complicated.
Startups often don’t have the budget or the team to build a fullfledged cybersecurity framework. As a founder myself, I know how tough it is, cybersecurity can feel like a luxury when you’re trying to stay afloat. But that doesn’t mean startups are off the hook.
What I believe and advocate is a shared responsibility model. Cybersecurity shouldn’t be one person’s job. Everyone, from founders to interns, should be aware of the basic principles of digital safety. Startups may not be able to do everything, but they can start with the basics: secure passwords, multi-factor authentication, data access control, and regular backups. These don’t cost much but can go a long way.
How do global data regulations like GDPR, CCPA, and the Cyber Resilience Act shape the way startups operate?
They’re reshaping the mindset and that’s crucial. A few years ago, cybersecurity was often viewed as a luxury. Many smaller companies thought, “Why would anyone target us?” That thinking no longer holds.
These regulations are forcing accountability. They’re saying: If you're collecting user data, you’re responsible for securing it. No exceptions. And that accountability builds trust not just with regulators, but with customers.
What these regulations have done is establish a baseline culture of cybersecurity. Even if a company


isn’t directly under the purview of something like GDPR, they often adopt the practices anyway to future-proof their operations. This is especially important as startups scale globally.
Do you believe governments should impose stricter cybersecurity regulations on startups, or offer more support instead?
Support first, regulations later. Imposing strict rules too early can backfire. Startups, already stretched thin, might try to find workarounds just to stay in business.
What governments should do instead is invest in capacity-building offer grants, training programs, and subsidized tools. Help small businesses adopt best practices without breaking their budgets.
Once there’s a baseline maturity in the ecosystem, then phase in stricter compliance rules.
This layered or phased approach is more sustainable and more effective in the long run.
There’s talk of a cybersecurity talent shortage. Is it really that hard to find skilled professionals?
There’s no shortage of interest but there is a gap between certifications and real-world skills. Many candidates have credentials but lack hands-on experience. Startups, in particular, need practical problem-solvers, not just textbook experts. What we need more of are experiential learning platforms, internships, cyber ranges, environments where people can learn by doing
For founders, my advice is to hire based on potential and adaptability. You might not be able to compete with tech giants on salary, but you can offer learning, autonomy, and purpose, which many securities professionals’ values just as much.
If you could give one piece of cybersecurity advice to every new founder, what would it be?
Don’t let lack of budget stop you from doing something. There are tons of free and low-cost resources out there from SANS to OWASP to NIST guidelines. You can absolutely build a minimal, but meaningful, cybersecurity foundation even if you’re bootstrapping.
Treat cybersecurity like any other critical function, your dev team, your HR, your marketing. It’s not optional anymore. Even a basic security hygiene culture can drastically reduce your risk.
Do you think cybersecurity will eventually be seen as a fundamental utility, as essential as electricity or water?
Without a doubt. We already rely on digital infrastructure for everything, finance, healthcare, transportation, energy. If any of these go down due to a cyberattack, the consequences are devastating.
Cybersecurity is no longer just about protecting data. It's about protecting lives and national security. We’re also seeing how cyber warfare is becoming a central strategy in geopolitical conflicts.
So yes, cybersecurity will and should, become a default layer of modern society. It’s the new electricity. Invisible, but absolutely essential.
Vivek Chandran’s message to founders is clear: cybersecurity is a necessity, not a luxury. Startups may face budgetary and staffing constraints, but that’s no excuse for ignoring the risks. From AI-driven threats to phishing scams and regulatory pressures, the cyber battlefield is real, and unforgiving.
Fortunately, knowledge is power. And as Vivek points out, the tools to get started are already out there, many of them free. For founders in 2025, the goal isn't perfection, it’s proactive protection many of them free.


Let’s start with your recent win at GISEC. Walk us through the experience. What led you to stand out??
GISEC is more than just a trade show. It’s a convergence point, investors, startups, customers, policy makers, all in one place. For us at Snode, it was an opportunity to showcase not only our innovation but also our deeper mission.
Yes, we build cybersecurity technology, but our “why” goes beyond that. It’s about securing the digital futures of underserved regions, from North Africa to Southeast Asia. It’s about educating people, protecting democracies, safeguarding children online. That’s what security means to us.
GISEC gave us a global platform, especially important for a company like ours based in South Africa. Competing in dollar and euro-based markets while earning in other currency is no small feat. GISEC allowed us to participate in a cost-efficient way, and that made a difference.
Winning the North Star Award wasn’t just a pat on the back, it was a powerful reference. When you’re up against names like IBM and Cisco, credibility is currency. That award told the world: this isn’t just a passionate team, it’s a world-class solution worth trusting.
How did GISEC impact your visibility and partnerships going forward?
Massively. Let’s be honest, we’re not a giant yet. But what GISEC offered was not just floor space; it was validation. It gave us access to buyers and markets that wouldn’t normally take a meeting with a company they hadn’t heard of.
The North Star Award is more than a trophy, it’s a reference. It tells potential partners, “These guys are vetted. Their tech is worth your attention.” That kind of credibility opens doors. We’ve had conversations with investors, decision-makers, and ecosystem players we would have struggled to meet otherwise.
GISEC didn't just amplify our voice, it handed us the mic.
As a startup founder, what have been your biggest challenges?
Two things: access to decision-makers and market awareness.
Our product is executive-level. It’s not something a

junior engineer or procurement officer can greenlight. But getting face time with C-suite execs in a new market say, the MENA region, is tough when no one knows your name.
The second challenge? Getting people to know we exist. We're not another “me-too” startup. We’ve built something truly different, better performance, better cost-efficiency, less admin bloat. But if people don’t know there’s an alternative to the legacy players, they’ll keep renewing their old contracts out of habit.
It’s David versus Goliath, except David has a kickass cybersecurity engine, but no one’s opened the email yet.
Based on your journey, what practical advice would you offer to early-stage entrepreneurs?
Three pieces of advice , let’s call them my "startup gospel."
Acknowledge your fear, but don’t live in it. Fear isn’t weakness. It’s human. But once you commit to building something, leave that fear behind. Perseverance beats perfection every time. You don’t fail unless you quit.
Execute like hell.
A mediocre idea with stellar execution beats a genius idea gathering dust. Move fast, fail fast, learn faster. The winners? They’re the ones who learn the fastest.
Be specific to someone specific. Don’t try to solve everything for everyone. Find a real problem, for a real person, and solve it beautifully. Design matters. Empathy matters. Don’t bolt on 10 features to chase every market, dig deep and serve one thing incredibly well.
What mindset shifts did you need to make as a founder, especially coming from a technical background?
The first shift? Believing we could compete with global tech giants. You look at the big players and think, “They’ve got billions. How can we match that?” But guess what? Being small is an advantage. We're agile, we’re focused, and we don’t need a committee to pivot.
Second, realizing your environment doesn't define your potential. Snode started in my mom’s kitchen, no VC backing, no fancy office. Just code, coffee, and commitment. The internet changed everything. You don’t need machines anymore, just a good idea, skill, and persistence.
The third shift was probably the most profound: it’s not just about improving yourself it’s about lifting others.

So my mission now is to dismantle those lies, not just for me, but for the next generation. Helping them unlock their potential helped me unlock my own.
You mentioned networking wasn’t always a strength. How important has it become in your journey?
I used to think building a great product was enough. That people would just... find us. But that’s not how the world works. People buy from people. What you're selling, especially in cybersecurity, is trust.
Networking is about building relationships, inside and outside your company. And not just transactional ones. Real, meaningful connections based on mutual value. The moment I started showing up, listening, collaborating, things changed. So if you’re a technical founder who hates networking: tough luck. Learn it. Lean into it. It’s not just part of the job, it is the job.

Tell us how your GISEC journey began. How did you end up with your own booth and a place in the competition?
We were part of the Cyber E71 incubator, which is affiliated with the UAE Cybersecurity Council. Through that program, we were placed in a dedicated pavilion at GISEC and provided with our own booth.
But it wasn’t just a free space, it came with serious training. We were given workshops on how to pitch, how to structure a startup, how to scale. That mentorship shaped our confidence. Out of 11 startups in the incubator, three moved to the finals, and we were the one that ultimately won. That win wasn’t just a trophy, it came with exposure and the funding we needed to kick off our post-GISEC journey.
What motivated your team to get involved, and how did you prepare for the competition?
At the core, we were driven by a simple belief: we want to make a real impact in the UAE. Our vision is to help elevate the country as a leading global market in cybersecurity. GISEC felt like the perfect platform to test that vision.
Our preparation? Let’s just say, it was relentless. We practiced our pitch constantly, tweaking and improving every sentence. At an AI exhibition in late 2024, we weren’t even planning to pitch, but someone from the organizing team came by our booth and asked, “Wanna give it a shot?” We had ten minutes to prep. We pitched and won third place. That moment cemented our belief: practice pays off. Confidence comes from repetition.
How did winning at GISEC impact your startup’s visibility and momentum?
Prior to GISEC, we already had some local recognition. But winning elevated our status to a completely new level, it opened international doors. We started receiving invitations from companies and exhibition organizers across different countries. They asked us to speak, showcase, or set up booths in their global events. So the biggest shift was in moving from national recognition to international visibility. We're now actively part of global conversations in cybersecurity.
What challenges have you faced along the way, particularly as a startup in this domain?
Like most startups, the biggest hurdle has been getting paying clients. We’ve built great partnerships, strong
connections across different sectors in the UAE, but when it comes to actual revenue, we’re still in the pre-revenue phase.
That said, we’re optimistic. The partnerships we’ve formed are the kind that build long-term pipelines. We’re laying the foundation so when we turn on the revenue tap, it’s ready to flow.
Let’s talk mistakes. What lessons have helped shape your current strategy?
The most valuable lesson? Lead management. After GISEC, we saw a massive spike in interest. Our inbox and DMs exploded. At first, it was chaos, we didn’t have a structured way to manage those incoming leads.
That changed quickly. We implemented a CRM system, set up automations, streamlined our internal processes. Now, we’re far better prepared to handle large volumes without letting anyone slip through the cracks.
Managing limited resources is a challenge for any early-stage startup. How did your team navigate that while staying aligned with your long-term goals?
We’ve always operated with a “quality-first” mindset. When resources were tight, we focused not on reaching everyone, but on reaching the right people, the 20% of clients who would eventually bring 80% of the value.
For example, we collaborated with HCT (Higher Colleges of Technology), the UAE’s largest educational institution. We built a gamified education program for them in under a week. From ideation to deployment, seven days. That project became a major milestone and opened doors for a potential yearly contract. When you focus your energy smartly, limited resources don’t feel so limiting.
What role did mentorship and networking play in your success story?
A massive one. For most of us on the team, except our CEO, this was our first time building a startup. So mentorship wasn’t just helpful; it was crucial.
We had multiple mentors reviewing our GISEC pitch. Imagine this: a two-minute pitch getting two-hour feedback sessions. Every second was dissected. The language, the delivery, the transitions. That kind of granular coaching was instrumental. Without it, we wouldn’t have delivered the winning pitch we did.
MIAN MUHAMMED KHAYYAM Co Founder and COO Exploit3rs

What was the biggest mindset shift you had to make as a founder?
The biggest shift? Realizing that you have to do everything yourself, at least in the beginning. Marketing, business development, tech, branding, you can’t wait for specialists. You become the specialist.
We enrolled in online courses, trained ourselves, and applied everything immediately. That DIY, self-starter mentality isn’t optional in early-stage startups. It’s survival.
Startups look glamorous, but they’re rarely easy. Have there been moments of doubt or burnout?
Surprisingly, no regrets so far. The recognition we’ve received has been incredibly validating. We’ve won multiple competitions. Just two weeks ago, we were awarded by the Cybersecurity Council as the most influential startup in community building. Personally, I was so convinced of this vision that I never took a full-time job after graduation. I went straight into building this company. And every win, every milestone, just reinforces that we’re on the right path.

Chief Information Officer
M.H. Enterprises L.L.C

What are the top cybersecurity priorities for your organization this year?
Our top cybersecurity priority this year is building a resilient, Zero Trust-driven hybrid security model that protects both on-premise and cloud environments. We’re actively working on enhancing privileged access controls, implementing network access control (NAC), and deploying intelligent threat detection tools for real-time visibility across endpoints and user behavior.
Additionally, we're emphasizing automated vulnerability assessments and database activity monitoring to proactively identify potential weaknesses. Security awareness training remains critical, as human error continues to be a common threat vector.
How do you align cybersecurity initiatives with overall business goals?
Cybersecurity is tightly aligned with our broader business strategy. Every security initiative we

implement is assessed for its impact on risk mitigation, operational continuity, and customer trust. For instance, during major automation and digitization projects, security controls are embedded right from the design stage. We track metrics such as risk reduction, incident response time, and compliance coverage all of which tie back to our strategic goals of efficiency, resilience, and credibility.
Can you share a recent cybersecurity incident or close call and how your team handled it?
We encountered a situation where abnormal login activity was detected within our internal network. The behavioral patterns resembled a brute force attempt. Thanks to proactive monitoring, our team was able to isolate the endpoint and investigate immediately. The root cause turned out to be a dormant user account that hadn’t been deactivated post offboarding. We conducted a full access review and strengthened our user lifecycle management practices. It was a timely reminder of how even non-malicious oversights can open doors to risk.

What are the key factors you consider when evaluating cybersecurity vendors?
Our evaluation criteria are centered around solution maturity, ease of integration, scalability, local and remote support, and measurable business value.
We value vendors who understand our environment and challenges, offer transparent pricing, and provide long-term partnership not just product delivery. Proven references, handson trials, and solution roadmaps also play a role in our selection process.
How do you prefer vendors to approach you, with education, product demos, or proof of
A consultative, educational approach works best. We prefer vendors who start by understanding our needs and pain points, then offer targeted insights and practical examples. Short, focused demos and access to a test environment help us evaluate feasibility. The more relevant and hands on the engagement, the better the outcome for both sides.
What are the biggest gaps in current cybersecurity solutions that vendors should
Many solutions today still lack context-awareness, they flag activities without prioritizing based on risk or business impact.
Another gap is the difficulty in integration. Products should come with out-of-the-box connectors or easy-to-deploy APIs. Finally, licensing and usage models need simplification. Too many options often confuse buyers rather than helping them.
Are there specific challenges in integration, scalability, or support that you've faced?
Integration with legacy infrastructure continues to be a challenge. Some newer tools are built cloud-native but struggle in hybrid or transitional environments.
Scalability is generally less of a problem now, but consistent and regionally-aware support is still a pain point. We now make it a practice to test vendor support responsiveness before full-scale onboarding.
How is your cybersecurity budget evolving year-over-year?
Our cybersecurity budget has seen incremental growth, with a reallocation towards analytics driven monitoring, user awareness, and

automation-based defense. We’re also optimizing our spend by balancing commercial products with open-source tools wherever feasible, without compromising on coverage or reliability. Budget discussions are increasingly linked to risk and incident trends.
What’s your advice to vendors looking to position their solutions for budget approval?
Focus on outcomes. Position your solution in terms of business impact, risk reduction, operational efficiency, or compliance readiness.
If your tool replaces multiple systems or reduces manual work, quantify that. Avoid overly technical selling and instead align with planning cycles and strategic goals. A clear ROI narrative goes a long way in securing buy-in.
Have you collaborated with vendors on co-developing or customizing solutions?
Yes, collaboration has been crucial in several successful deployments. In cases where off-the-shelf solutions didn’t fully meet our operational nuances, we worked with vendors to fine-tune workflows and reporting structures. Such partnerships have led to better user adoption and product stability.
What common mistakes do vendors make when engaging with CISOs?
Some vendors come in with pre-built pitches that may not align with our actual environment. Others dive too deep into technology before understanding our business context.
Inconsistent follow-ups or ignoring compliance and data residency considerations are also common pitfalls. The best engagements are those where vendors listen more than they sell.
What’s one innovation or improvement you hope to see from vendors in the next 12 months?
I’d like to see more intuitive AI-driven analytics that reduce false positives and prioritize alerts based on context. Also, easier deployment models ,something that doesn’t take weeks to configure. Vendors who can offer modular, adaptable solutions with strong analytics will stand out in the coming year.


We sat down with Mr. Mohammed Ilyas, COO of AmiViz and resident slayer of outdated channel models, who shared how the company is ditching the dusty distribution playbook in favor of digital platforms, deep partner enablement, and bundles that actually make sense.
AmiViz has positioned itself as a next-generation, value-added cybersecurity distributor. What do you see as the core differentiators that set you apart in a traditionally commoditized space?
AmiViz has redefined what it means to be a true value-added cybersecurity distributor in the Middle East by shifting from traditional, transactional distribution toward a model focused on enablement, innovation, and deep domain expertise.
We provide a digital platform where partners can evaluate technologies, initiate PoCs, and collaborate seamlessly, enhancing transparency and efficiency. We are 100% focused on cybersecurity, which gives us an edge in curating a portfolio that addresses today's evolving threats, whether AI-driven attacks, Zero Trust adoption, or OT and cloud security. Our pre-sales support,
technical expertise, and regional lab capabilities make us an essential partner in the sales cycle, not just a distributor.
Our partner enablement programs are another standout. We regularly conduct workshops, training, and certifications to elevate partner skill sets and improve win rates. This investment in people extends to our local market approach, especially in high-growth areas like Saudi Arabia, where we've expanded resources to meet local needs more effectively. We also go beyond distribution through joint go-to-market initiatives, helping vendors and partners generate leads, run campaigns, and close business faster.
The channel landscape is evolving fast, with partners demanding more than just product access. How is AmiViz reimagining its role to support VARs, MSSPs, and integrators in delivering value-added cybersecurity services?
The channel landscape has shifted dramatically VARs, MSSPs, and integrators no longer seek just product
access; they demand value, enablement, and collaboration. At AmiViz, we've reimagined our role to become a true business enabler, not just a product distributor.
We support our partners with end-to-end technical enablement, including solution architecture, demos, PoCs, and RFP responses. Our regional pre-sales teams act as an extension of the partner's workforce, helping reduce sales cycles and improve customer win rates. For MSSPs, we help build scalable service offerings by bundling the right technologies with operational and technical training.
Our partner skill-up programs have trained and certified hundreds of channel professionals across the region. We focus not only on product knowledge but also on real-world deployment, compliance understanding, and threat landscape awareness, key factors for MSSPs and integrators delivering managed and consultative services.
Most importantly, we take a localized approach, understanding each region's cultural and operational needs. Our in country presence in key markets like Saudi Arabia, UAE, Egypt, and Qatar enables us to deliver responsive support and build deeper relationships.
With an increasing number of cybersecurity vendors entering the market, how do you evaluate which technologies to bring into your portfolio and ensure they align with real partner and customer needs?
As the cybersecurity landscape becomes increasingly crowded, our approach at AmiViz is highly selective and driven by real-world partner and customer needs not just vendor momentum. We focus on technologies that solve current and emerging challenges, are scalable, and can deliver measurable value across different industries and customer segments.
Our evaluation begins with a market gap analysis based on continuous feedback from our partners, customers, and internal pre sales teams. We focus on the problems that are still unsolved. Where are customers struggling to find capable solutions? This ensures that every new technology we onboard address a real and timely demand.
You operate across a complex and diverse region. What unique challenges and opportunities do you see in cybersecurity distribution across the Middle East and Africa?
Operating across the Middle East and Africa (MEA) presents both complex challenges and exciting opportunities in the cybersecurity distribution space. This region is incredibly diverse in terms of regulations, maturity levels, infrastructure,
We focus on technologies that solve current and emerging challenges, are scalable, and can deliver measurable value across different industries and customer segments.
and buying behavior, requiring a highly localized and adaptive approach.
One key challenge is the varying levels of cybersecurity awareness and readiness. While countries like the UAE and Saudi Arabia are highly advanced, investing security, many nations in the MEA region are still in the early stages of cybersecurity adoption. As distributors, we must tailor our enablement, pricing models, and technology portfolios accordingly.
Another challenge is the fragmented regulatory landscape. Data sovereignty laws, compliance frameworks, and certification requirements differ from country to country, making it critical to offer solutions that align with local mandates. We work closely with partners and vendors to ensure our technologies are compliant and deployable across jurisdictions. However, the region also presents massive growth opportunities. Governments across MEA are prioritizing digital transformation, which naturally drives demand for robust cybersecurity solutions. Initiatives like Vision 2030 in Saudi Arabia, smart city development in the UAE, and digital transformation and fintech growth in Africa are creating a surge in security needs.
Enablement has become a strategic imperative for channel success. How is AmiViz investing in technical training, pre-sales support, and market education for your partners?
At AmiViz, we firmly believe that partner enablement is the foundation of long-term channel success. In an increasingly complex cybersecurity landscape, partners need more than access to products; they need the right skills, tools, and support to position and deliver value-added solutions effectively. That's why we've strategically invested in technical training, pre-sales support, and continuous market education. Our enablement programs are structured to upskill partners at every stage, from onboarding and product education to advanced deployment scenarios. and solution integration.


We run regular technical workshops, hands-on labs, and certification programs, often in collaboration with our vendors across the region, to ensure our partners are fully equipped to handle real-world cybersecurity challenges. Our pre-sales engineering team is an extension of our partners, supporting them with solution architecture, demos, PoCs, and RFP responses. Through our AmiViz Partner Skill-Up initiative, we've enabled hundreds of partners across the region with focused enablement sessions tailored to their business models be it VAR, MSSP, or system integrator. We also support partners through joint account planning and technical mentorship, ensuring they're confident and capable in front of customers.
With cybersecurity stacks growing more complex, how does AmiViz help partners navigate integration, interoperability, and bundled solution offerings?
As cybersecurity stacks continue to grow more complex, partners are under pressure to deliver integrated, interoperable, and outcome-driven solutions rather than just standalone products. At AmiViz, we
recognize this challenge and have built our go-to-market and technical strategy around simplifying this complexity for our partners and their customers.
First, we take a solution-oriented approach to portfolio curation. We carefully evaluate and onboard complementary technologies, allowing for easy bundling across different cybersecurity domains, such as Zero Trust, Cloud Security, Endpoint Protection, Threat Intelligence, Vulnerability Management, Network Detection, OT Security, and Identity Management. This ensures our partners can offer bundled, interoperable solutions that solve real-world customer problems holistically.
We support partners with solution integration and architectural guidance through our in-house technical lab and PoC environment, where different technologies are tested together to ensure compatibility and optimal performance. This allows us to pre-validate technology stacks, reducing risk and deployment friction for both partners and customers.
Our pre-sales and solution architects work closely with partners to help them design, position, and deliver these bundled offerings.









Business Development Manager PowerDMARC

From the classrooms of Muscat to boardrooms across the MENA region, Zainab Al Lawati’s journey proves that women in tech can lead with confidence, credibility, and impact. Featured in TECHx Media’s Women in Tech series, her work at PowerDMARC is opening doors for both markets and mindsets.
Zainab Al Lawati was born and raised in Muscat, the capital of Oman. Growing up in the 1990s, she witnessed a time of significant transformation in the role of women in society.
“Women were beginning to enter the education sector, take up ministerial positions, and hold influential roles,” she recalls. Her own schooling experience was progressive. She studied in a co-ed environment where girls received equal attention and encouragement.
“The teachers invested in shaping us. Girls had the same rights and attention as boys,” Zainab says.
Being the first child, and the first daughter, in her family made her journey even more meaningful. Her mother, a
highly educated professional, became her first mentor and strongest supporter.
“She made sure I received quality education and even arranged for tutoring after school. I hated it at the time,” she laughs. “But looking back, it made all the difference.”
Her upbringing was shaped by a belief that women could, and should excel. Today, she proudly notes that women in Oman are not only ministers but also governors and decision-makers, enjoying full rights and opportunities.
Zainab’s educational journey took a significant turn when she received a government scholarship to pursue higher education abroad.
At just 17, she moved to the Netherlands to study International Business Administration at NHL Stenden University.
“It was a major shift. Living independently in Europe, surrounded by diverse cultures and ideas, shaped me deeply,” she says.
Her undergraduate program blended theory with real-world application. “We didn’t just learn business
concepts, we applied them in real scenarios. That practical exposure gave me a head start professionally.”
Zainab didn’t stop at a bachelor’s degree. She continued at the same institution to earn a Master’s in Digital Innovation. The program bridged her interest in tech with her business background.
“I’ve always been drawn to technology. The master's helped me see tech from a business lens,” she explains. “It wasn’t about coding. It was about understanding how tech can transform industries.”
This passion sparked a deeper interest in cybersecurity. On returning to Oman, she pursued further professional certifications, including Certified Information Security Manager (CISM).
“I’m a saleswoman, yes. But I believe a saleswoman should speak tech fluently. That’s how you add real value to your clients.”
Zainab Al Lawati’s first job came while she was still in the Netherlands. She joined Neat, a Norwegian hardware firm specializing in video conferencing solutions, as a Business Development Representative.
Her job involved more than just client relations. “I was on the front lines, handling live chats, troubleshooting, and doing video support for technical issues.”
This early exposure to hardware gave her a taste of real tech.
When she moved back to Oman, she shifted focus to cybersecurity. “Cybersecurity fascinated me. The more I learned, the more I realized how essential it is to modern businesses.”
She dove deep, learning how cybersecurity infrastructure is built, how products are integrated, and how organizations stay protected. This technical understanding became a cornerstone of her career.
As a woman in the cybersecurity space, Zainab faced hurdles early on.
“I did feel underestimated, both by colleagues and clients. Some assumed I didn’t have the technical knowhow,” she says.
Instead of being discouraged, she chose to rise above it.
“I spoke confidently about what I knew. And what I didn’t know, I made sure I learned. I joined technical demos, I asked questions, I showed up.”
Another challenge was managing the emotional dynamics of the workplace.
“As women, we’re often expected to do more. That strength sometimes becomes an excuse for others to offload more on us,” she observes. She also recalls how emotional manipulation or
“valuation games” sometimes affected professional interactions.
“People, whether male or female sometimes use emotional angles to influence women in business discussions. But these experiences have made me tougher, more composed, and emotionally intelligent.” Her message: “Challenges will come. But they shape you. Let them.”
Today, Zainab Al Lawati is steering growth across the MENA region at PowerDMARC. As Business Development Manager, she handles both channel partnerships and direct end users across the region.
“I work with a brilliant team, technical implementers and account managers who support our regional expansion,” she shares.
In the past year, she’s led some of the company’s most significant milestones.
“We expanded into Morocco and Tunisia. In Morocco, we onboarded Onetech Africa as our first distributor. In Tunisia, we successfully partnered with Ooredoo Tunis for one of the largest regional implementations.” Her work also helped PowerDMARC solidify its presence in the Middle East through key partnerships.
“We signed with Spire Solutions, adding PowerDMARC to their cybersecurity portfolio,” she says.
The roadmap ahead includes entering new, complex markets. “We’re looking at Lebanon, Jordan, and Egypt in the coming months pending political and economic conditions. These are markets with huge potential.”
As a prominent woman in cybersecurity, Zainab has a message for aspiring female professionals: “We are survivors. We know more than they think. We can always do more.”
Her advice to young women entering the tech industry? “Don’t doubt yourself. Learn the tech. Understand the business. Speak with confidence. And never let a ‘no’ define you.”
To the industry at large, she adds: “Technology is shaping the world. It doesn’t discriminate. There is room for everyone, regardless of gender. What matters is passion and knowledge.”
Zainab Al Lawati is not just building markets, she’s building momentum for women in tech. Her career is a case study in how education, determination, and a bold vision can lead to real impact in a male-dominated industry.

so did Positive Technologies
Chief Technology Officer
Positive Technologies

At the Positive Hack Day Fest, we had the opportunity to speak with Alexey Andreev, Chief Technology Officer of Positive Technologies, a global leader in cybersecurity solutions. The event brought together cybersecurity professionals, vendors, and government representatives to explore innovations, exchange ideas, and experience live simulations of attacks and defenses in a real-world-like environment.
How has the cybersecurity threat landscape evolved over the past 3 to 5 years?
The cyber landscape has dramatically changed, especially compared to 3 or 4 years ago. Several factors contributed to this:
Increased Attack Frequency and Sophistication Geopolitical tensions have escalated the number and complexity of attacks globally.
AI-Powered Attacks – Adversaries are leveraging AI and large language models (LLMs) to orchestrate more calculated and intelligent attacks. These tools help them
gather intelligence, conduct reconnaissance, and simulate vulnerabilities before launching an attack.
Cloud and Infrastructure Changes – With cloud technologies becoming mainstream, attackers have shifted focus to exploit hybrid environments, APIs, and remote access systems
How is Positive Technologies leveraging AI and ML to detect and respond to these evolving threats?
Even before LLMs became widely available, we used deep learning to power our behavioral analytic detection systems. These tools can identify anomalous or malicious processes in real time with high precision and low false positives, without requiring human intervention. Now, with the rise of large language models, we are enhancing our systems to act more like copilots or autopilots for security operations centers (SOCs). We’ve invested heavily in GPU-powered clusters to support these AI models, allowing real-time analysis and decision-making. Our hybrid systems combine rule-based expertise with deep learning and LLMs to create intelligent, adaptive defenses.
What about cloud transformation, how are your solutions adapting to it??
We've made significant strides in making our solutions fully compatible with both public and private cloud environments. Our focus is on ensuring that customers can operate securely without sacrificing performance or violating data localization laws. This flexibility is critical for modern businesses.
With GDPR and other regulations in place, how do you ensure compliance while maintaining operational agility?
Our technology is built with compliance at its core. Clients can operate our products without transmitting any data outside their environment. All data is localized, it stays within the customer’s data centers or country-specific perimeter. This approach allows clients to comply with GDPR and other regulations without hindering their operational agility. Our role is to ensure our products support this framework by design.
Let’s talk about zero trust architecture. How critical is it to modern cybersecurity?
Zero trust is absolutely critical, especially in today’s interconnected world. However, implementing it is not simple. Legacy systems weren’t designed with zero trust principles like access on demand and least privilege in mind. Moreover, human factors make it difficult. People resist restrictions, and infrastructure redesign takes time and resources. So, while zero trust is powerful, it’s not a silver bullet. It must be part of a broader strategy, combined with user awareness, strong authentication, and continuous monitoring.
What strategies do you recommend for ransomware resilience?
Ransomware remains a high-impact threat, despite many organizations taking preventive measures. Just last year, we partnered with VirusBlockAda, a Belarusian cybersecurity firm known for its role in analyzing the Stuxnet worm, to develop a next-generation endpoint protection solution.
This solution is specifically designed to combat ransomware using a blend of behavioral analytics, deep learning, and memory forensics. It's a significant evolution from traditional antivirus tools and is tailored for modern threat scenarios.
Are ransomware attacks in the Middle East increasing or decreasing based on your recent reports?
While I can't provide the exact figures offhand, our most recent reports indicate that ransomware remains a persistent threat in the Middle East. The region is rapidly digitizing, which presents new opportunities for attackers. This is why we’re actively expanding in the region and working with local stakeholders to bolster cyber resilience.

Finally, what’s next for Positive Technologies? Any innovations on the horizon?
Our most exciting development is around autopilot cybersecurity systems. These systems will enable security teams to automate threat detection, response, and even remediation a leap toward fully autonomous SOCs.
We are also exploring generative AI for real-time threat simulation, automatic report generation, and contextual threat intelligence, which could revolutionize how cybersecurity professionals work.


Cloudflare has announced the 11th anniversary of Project Galileo, its flagship initiative offering free cybersecurity protection to at-risk public interest organizations worldwide. Launched in June 2014, the program has defended journalists, human rights groups, independent media, environmental activists, and others working on the frontlines of democracy and civil society.
To mark this milestone, Cloudflare revealed a new interactive Radar report. The report provides detailed insights into the cyber threats faced by organizations protected under Project Galileo. It highlights the increasing risks and evolving tactics used by attackers targeting these groups.
According to the report, distributed denial-of-service (DDoS) attacks are growing more common than traditional web application exploits. From May 1, 2024, to March 31, 2025,
Cloudflare blocked 108.9 billion cyber threats aimed at Project Galileo organizations. This equates to an average of nearly 325.2 million attacks per day, representing a 241% increase compared to the previous year. Journalists and news organizations experienced the highest volume
of attacks. Over 97 billion requests were blocked across 315 such organizations.
The peak attack day was September 28, 2024. Human rights and civil society organizations ranked second, with 8.9 billion blocked requests. Their peak attack activity occurred on October 8, 2024.
Ossama
General Manager GBM

Gulf Business Machines (GBM), a leading digital solutions provider, has announced a strategic partnership with PRIME Health. The collaboration aims to deliver advanced cybersecurity solutions to protect PRIME Health’s digital ecosystem.
According to the announcement, the partnership introduces a fully managed detection and response (MDR) service. This includes 24/7 threat monitoring, fast detection, and immediate incident response.
At the core of this initiative are Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms. These tools offer real-time insights, automated workflows, and a unified dashboard. They are designed to improve visibility and speed up decisionmaking.
GBM also revealed that PRIME Health will have access to its expert Digital Forensics and Incident Response (DFIR) team. This team will investigate and contain threats quickly. Moreover, PRIME Health will benefit from specialized, contextual threat intelligence tailored to the healthcare sector.


The UAE Cybersecurity Council (CSC) has announced the development of the country’s first national Drone Cybersecurity Guidelines. This initiative is a strategic collaboration with Reach Digital, a subsidiary of Reach Group, and Shieldworkz, a firm specializing in OT/IoT and drone protection technologies.
According to the CSC, the guidelines mark a significant step toward securing the nation’s expanding UAV ecosystem. The announcement supports the UAE’s long-term vision to enhance resilience against cyber threats and drive safe digital transformation.
Dr. Mohamed Al Kuwaiti, Head of the UAE Cybersecurity Council, revealed that the new framework will strengthen drone operations across government, commercial, and industrial sectors. He noted that these guidelines are designed to ensure security, resilience, and alignment with global best practices.
“With increasing UAV deployment across sectors, from agriculture and environmental monitoring to logistics cybersecurity risks must be proactively addressed,” Dr. Al Kuwaiti stated. “This is essential to protect national airspace, infrastructure, and data integrity.”
Reach Group is playing a key role in this effort. Malik Melhem, CEO of Reach Group, reported, “This collaboration reflects our unwavering commitment to advancing the UAE’s digital and cybersecurity infrastructure. We are proud to contribute to national readiness by aligning with CSC and delivering practical, scalable cybersecurity solutions for the drone sector.”
Additionally, Mohammad Khaled, Vice President of Growth and Business Transformation at Reach Group, emphasized the strategic value of the partnership. “By developing these guidelines with CSC and our partners at Shieldworkz, we are reinforcing the UAE’s leadership in securing emerging technologies,” he said.
He added that the initiative directly supports safe drone innovation while addressing the rising cybersecurity risks in national airspace and critical infrastructure.

Nirav Shah Senior Vice President of Products and Solutions Fortinet


Fortinet announced new upgrades to its data and productivity security portfolio. The company revealed enhancements to FortiMail through the launch of the FortiMail Workspace Security suite.
These updates establish FortiMail as a highly customizable email security platform. It now extends protection beyond email to browsers and collaboration tools. This includes platforms like Microsoft 365, Teams, Google Workspace, and Slack. Fortinet reported that the new capabilities provide broader, AI-powered protection across digital work environments. These advancements also include improvements to FortiDLP, the company’s data loss prevention and insider risk management solution.
According to Nirav Shah, Senior Vice President of Products and Solutions at Fortinet, “Cybercriminals are targeting users and using tools like FraudGPT, BlackmailerV3, and ElevenLabs to automate threats.” He added that Fortinet’s enhanced AI-powered security tools help defend against these sophisticated attacks.
Chief Product Officer Check Point
Check Point Software Technologies Ltd. has announced the launch of its next-generation Quantum Smart-1 Management Appliances. The company is a global leader in cybersecurity solutions.
The new appliances deliver a 2X increase in managed gateways. They also offer up to 70% higher log processing speeds. These improvements are designed to meet the complex demands of hybrid enterprises.
Check Point revealed that the appliances are fully integrated into the Check Point Infinity Platform. This integration enhances threat detection and response using a hybrid mesh architecture. It also supports connections with over 250 third-party solutions.
Nataly Kremer, Chief Product Officer at Check Point, stated that security teams are under pressure from AI-generated threats and fragmented infrastructures. She said the new appliances simplify these challenges through AI, automation, and precision.
The rise of remote work and distributed teams has increased vulnerabilities. Check Point Research reported that AI services are now used in over 51% of enterprise networks each month. This growth widens security risks, making advanced security policies essential.
According to Check Point, the Quantum Smart-1 Management Appliances help security teams operate faster and smarter across on-premises, cloud, and remote environments.

Cloudflare has announced its participation in a coordinated effort to disrupt the Lumma Stealer malware operation.
The company’s Cloudforce One and Trust and Safety teams worked alongside Microsoft and other partners to target Lumma Stealer, also known as LummaC2. This malware is part of a growing category of information-stealing tools posing serious risks to individuals and organizations.
Lumma Stealer exfiltrates credentials, cryptocurrency wallets, cookies, and other sensitive data from infected systems. The stolen data often fuels downstream criminal activities, including financial fraud, identity theft, and ransomware attacks.
Reportedly, the malware abused multiple infrastructure providers, including Cloudflare. In response, Cloudflare identified the abuse and joined a Microsoft-led takedown operation.
This disruption involved several private partners, including those impacted and those offering intelligence support. It also included cooperation from the U.S. Department of Justice, Europol’s European Cybercrime Center (EC3), and Japan’s Cybercrime Control Center (JC3).
AmiViz, a cybersecurity-focused value-added distributor based in the Middle East, has been ranked 22nd on the 2025 list of Best Workplaces in Technology in the GCC region. The ranking was announced by Great Place to Work®, a global authority on workplace culture.
This recognition highlights AmiViz’s strong commitment to creating an inclusive, empowering, and innovation-driven work environment. It reflects the company’s efforts to foster a culture where trust, collaboration, and professional growth are a priority.
According to Great Place to Work®, the ranking is based on employee feedback collected through confidential surveys. It also includes an in-depth assessment of the company’s HR practices, leadership involvement, and focus on employee well-being.
AmiViz stood out for promoting a transparent and agile workplace. The company was recognized for encouraging employees to excel and contribute meaningfully to its mission.


New cyber threats emerge every day as malicious actors refine and escalate their attacks. Although it's impossible to predict exactly how the threat landscape will evolve, we can count on the fact that it won't remain static.
Consequently, IT and security leaders need to rethink how they manage the entire defense life cycle and evolve their approach to planning, implementing and maintaining cyber defenses. While siloed, stand-alone point solutions once offered effective protection, sophisticated threats require security solutions that can work together and proactively exchange data. By striking a balance between proactive and reactive defenses, organizations can maintain a robust security posture in a constantly changing threat landscape.
PatelRaja
Chief Product Officer, SOPHOS


New cyber threats emerge every day as malicious actors refine and escalate their attacks. Although it's impossible to predict exactly how the threat landscape will evolve, we can count on the fact that it won't remain static.
Consequently, IT and security leaders need to rethink how they manage the entire defense life cycle and evolve their approach to planning, implementing and maintaining cyber defenses. While siloed, stand-alone point solutions once offered effective protection, sophisticated threats require security solutions that can work together and proactively exchange data. By striking a balance between proactive and reactive defenses, organizations can maintain a robust security posture in a constantly changing threat landscape.
Security professionals and bad actors continue to play a game of cat-and-mouse as adversaries adapt their strategies in response to evolving defenses. That's nothing new. What's changing is the ingenuity and velocity of attacks. The current ransomware landscape illustrates this trend. In a typical ransomware event, adversaries release malicious software directly to the machine they encrypt an attack that most endpoint security tools can detect and block.
However, as defenses grow more sophisticated, adversaries are turning to malicious remote encryption. This technique (now used in roughly 60% of human-led attacks) enables attackers to deliver malicious software to an unmanaged or under protected device, bypassing traditional antiransomware solutions to encrypt data on other devices in the network.
Cyberattacks are inevitable. The appropriate response from defenders is to maintain a healthy balance between proactive and reactive defenses. Strong always-on foundational defenses are a must—together with the ability to quickly identify and respond when you need to dial up your protection.
Proactive measures like training employees in security best practices, risk-based vulnerability management and the use of multifactor authentication (MFA) are low-hanging fruit that can make a significant difference in your security posture. IT and cybersecurity leaders cited security tool misconfiguration as the top perceived security risk in our 2023 "State of Cybersecurity" survey, so it's also important to regularly check that your investments are properly deployed and delivering optimal protection.
Prioritizing these measures establishes a first line of defense that stops the vast majority of attacks. However, no matter how robust your protection is, sophisticated, persistent and well-funded adversaries will find a way to circumvent it—and you need the ability to dial up your protections to stop them from achieving their end goals.

In a typical ransomware event, adversaries release malicious software directly to the machine they encrypt—an attack that most endpoint security tools can detect and block.
Maintaining robust defenses in today's threat landscape is challenging enough. When you add the shortage of qualified security professionals to the equation, it becomes much more daunting.
Effective defense life cycle management helps streamline your security efforts and ensure comprehensive protection without overburdening your team. By investing in security tools that work together and prioritizing collaboration, you can optimize your defenses independent of resource availability.
It's crucial to have a diverse portfolio of security tools that can thwart threats at multiple points in the attack chain. However, the effort required to manage disparate tools and vendor relationships takes time and can hinder your ability to identify and respond to attacks.
Consolidating on fewer management platforms and vendors centralizes your security controls, reducing management overhead costs and enabling you to respond more effectively to active threats. Evaluate your current landscape and vendors to identify opportunities to focus on a tighter range of providers without compromising your defenses.


An open security architecture uses application programming interfaces (APIs) to connect and enhance interoperability among disparate solutions. This setup facilitates seamless data sharingsecurity tools, helping enforce policies and protocols in a consistent and cohesive manner.
The more you see, the faster you can respond. Bringing together vendor-agnostic telemetry from across your environment in an open, connected ecosystem enables you to accelerate threat detection, investigation and response while also increasing return on your security investments.
It's unsustainable to constantly remain on high alert. Fortunately, you don't have to. Instead, you can take advantage of adaptive protections that automatically deploy a heightened level of security when an attack is detected.
For instance, endpoint detection and response (EDR) tools continuously monitor your environment for suspicious activity. If the tool detects an anomaly that indicates a potential cyberattack, it can automatically isolate the affected endpoint and trigger an alert for a team of experts to investigate the incident.
Effective communication and collaboration among IT and security teams are essential for maintaining a strong security posture and avoiding redundant efforts.
Whether your teams are internal, outsourced or a combination of the two, optimizing their ability to work together and streamline engagements helps achieve superior outcomes.
Stand-alone point solutions are no longer enough to protect against evolving security threats. As attackers develop increasingly sophisticated techniques and tactics, you need tools that can work together and proactively share threat intelligence.
By optimizing your defense life cycle management through collaboration and informed investments, you can unlock real-time visibility across your entire digital environment and achieve a more comprehensive and cohesive security posture. As a result, you'll be prepared no matter what new threats are on the horizon.
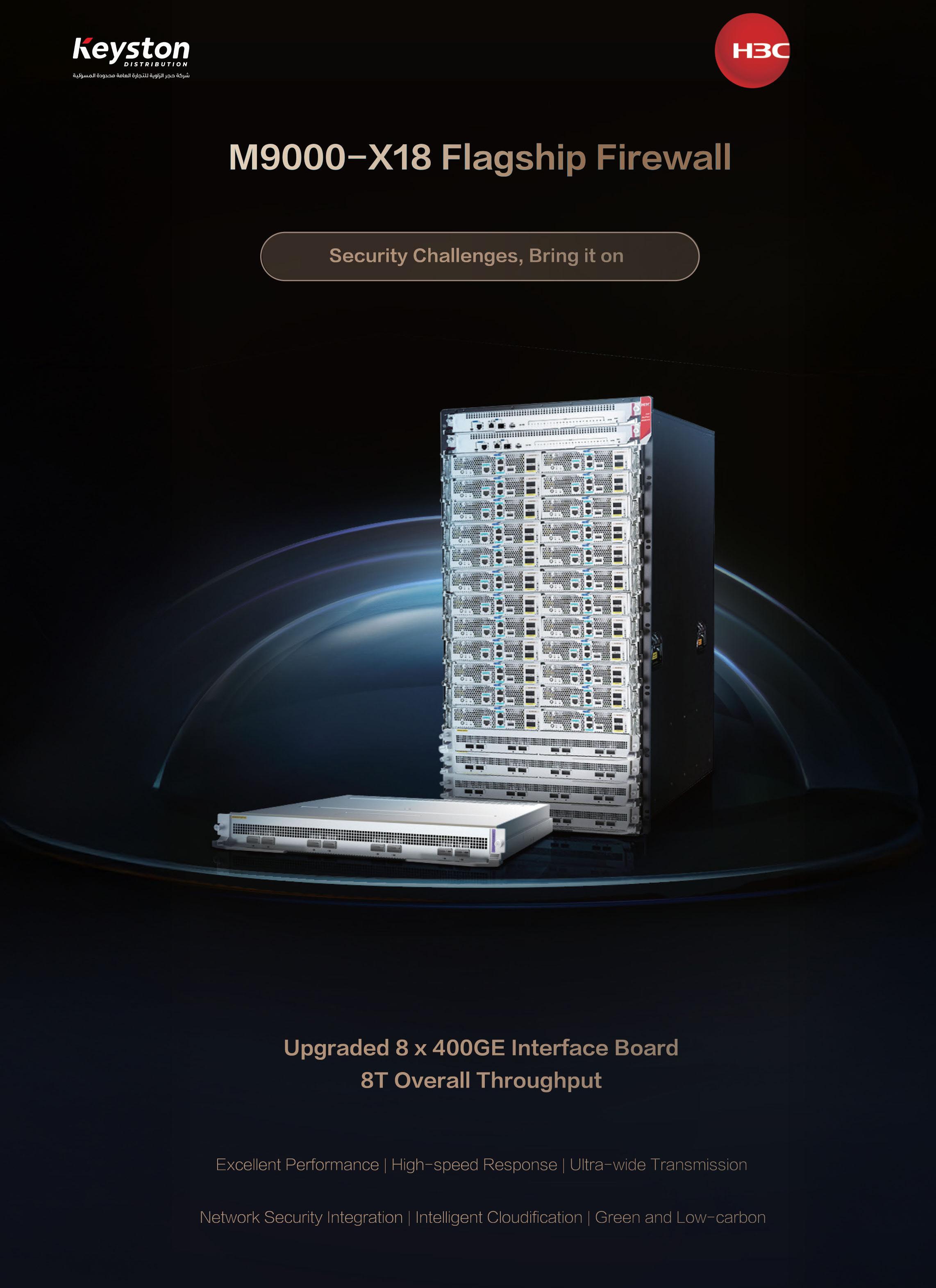


For the United Arab Emirates (UAE), the cyber threat landscape shows no signs of easing. The UAE Cyber Security Council’s “State of the UAE Cybersecurity Report 2025,” released in February, highlights concerning statistics: 223,800 digital assets within the country remain exposed to cyberattacks, and half of all critical vulnerabilities have gone unpatched for over five years. When compared to last year’s report, these numbers have worsened up from 155,000 vulnerable assets and 40% of critical vulnerabilities left unaddressed for over five years.
Globally, an estimated 94% of cyberattacks in 2024 involved data theft. Given the vulnerabilities present in the UAE, now is an opportune time to discuss data security management. The policies, technologies, and procedures we implement must adhere to the widely recognized CIA triad: Confidentiality, Integrity, and Availability.
Data Security Management: The Core of Cyber Defense
Data security management focuses on safeguarding data to prevent unauthorized access and use. Failing to secure sensitive data can expose organizations to legal risks and reputation damage. The CIA triad serves as a guiding framework for data security: ensuring that only authorized entities access sensitive data (confidentiality), maintaining data accuracy and preventing corruption (integrity), and ensuring data accessibility at all times and from any location (availability).
Implementing the CIA Triad
Confidentiality: Role-based access control (RBAC) and strong encryption, both at rest and in transit, are effective methods for protecting data confidentiality.
Integrity: Techniques such as checksums verify that data remains unaltered. Additionally, version control allows tracking of data changes and provides rollback options in case of corruption or unauthorized edits.
Availability: Redundant systems ensure business continuity by automatically taking over in case of primary system failure. Regular data backups are also crucial for maintaining availability.
Key Elements of Data Security Management
Access Control
To ensure that only authorized users can access data, organizations implement RBAC. This limits access to sensitive data based on user roles. Multi-factor
authentication (MFA) and centralized Identity and Access Management (IAM) systems further enhance protection without hindering user productivity.
Encryption transforms data into unreadable formats, ensuring that unauthorized individuals cannot access it. Data can be encrypted both at rest and during transmission. Data masking, on the other hand, obfuscates sensitive information by redacting or replacing elements with placeholders. This method is especially useful in nonproduction environments like testing, where accidental data leaks may occur.
DLP systems monitor data usage and transmission, blocking unauthorized sharing or transfers. These systems detect risky behaviors and policy violations, either automatically blocking such actions or flagging them for further review. DLP systems work in tandem with data masking to mitigate risks without unnecessarily hindering legitimate activities.
With the advancement of AI, modern threat detection tools are more effective in identifying anomalies in real time. However, organizations must have a clear incident response plan in place. Security teams, IT staff, and other employees need to understand their roles in containing and addressing breaches. Forensics teams must know how to investigate root causes, and designated parties should report findings and apply lessons learned to strengthen defenses.
Timeliness and accuracy are critical in incident response. Modern threat detection systems are highly refined and minimize false positives, enabling organizations to identify and address threats swiftly. Nevertheless, these tools are only effective if organizations have well-established response protocols.
In the event of a compromise, having a recovery plan is essential. Regular data backups ensure that organizations can restore data quickly following incidents like power outages, accidental deletions, hardware failures, or ransomware attacks. The 3-2-1 backup rule three copies of data, two different media, and one off-site copy — has become a best practice for disaster recovery. Additionally, regular recovery drills help ensure that personnel are prepared for a real-world incident.
Solutions Engineering Manager,

By implementing these elements, organizations can create a robust defense-in-depth architecture, minimizing vulnerabilities and maximizing the effectiveness of incident response. Adhering to best practices such as data minimization, data classification, and secure data migration will further strengthen defenses.
When building a defense-in-depth architecture, organizations should conduct a comprehensive assessment of their current security posture. This includes auditing systems and networks where data resides or passes through, identifying all data assets, evaluating their vulnerabilities, and assessing the business risks they pose. After this assessment, organizations should select and implement technologies and controls that align with their specific needs, integrating them in a way that does not introduce additional risks.
Defense-in-depth environments require continuous monitoring and evaluation. Regular reviews and audits ensure that security capabilities evolve alongside emerging threats.
By committing to these best practices and focusing on continuous improvement, organizations can make the UAE’s digital spaces safer for businesses and consumers alike.





"I started IT when I left school at 15 years old," Jenkins recalls.
That bold start quickly evolved into launching email security companies and working as an ethical hacker.
"This started off as me trying to get into companies. One of the things I challenged was, ‘Hey, can I get into your company? If I can, then you’ll pay me to help you secure your company.’"
While that job began with friendly infiltration, it evolved into ransomware recovery.
"Lots of companies were calling me saying, ‘Hey, we’ve been hit by ransomware. I don’t know what to do.’ The current IT company doesn’t know what they’re doing. So I’d go in and help them do the recovery."
At the end of every recovery, Jenkins heard the same question: “What should I have done to stop this?” His answer was consistent, and surprisingly simple.
“Stop trying to chase threats. They’re always trying to get better threat detection, change their AV, change their EDR. It was very simple: just block what isn’t needed, allow what is, limit the programs, and really take this Zero Trust approach to security.”
But back then, the tools to implement Zero Trust were limited and complex. So, Jenkins and his team built one.
Enter ThreatLocker: Zero Trust Made Practical
“The security tools in the endpoint protection space were very limited when it came to Zero Trust and very, very difficult to implement,” Jenkins explains.
“So we created our own product, our own toolset, our own service and whole solution around Zero Trust.”
With ThreatLocker, organizations can:
• Deploy an agent that learns their environment
• Identify what’s essential
• Block everything else effortlessly
“A client could deploy an agent, learn what their environment needed to look like, block what wasn’t needed, and without putting lots of effort.” The result? Rapid growth.
“Today, we have over 54,000 companies worldwide that use us,” Jenkins shares. “In the last three years, we’ve multiplied our business by 20 times.”
The cybersecurity battleground is evolving, and AI is now on the front lines.
"Phishing emails two years ago were often badly worded,
poor English, very easy to spot. They were generated once and used a million times over, which made them very easy to detect. Now… they're unique, they're very, very hard to detect, and they're written in perfect English."
He adds: “Now, to create malware, you can literally just get onto a keyboard and ask ChatGPT to write you a reverse shell or write you malware… We're seeing this increase. And as a result, we’re seeing more and more ransomware.” Even ransomware strategies have changed.
“Attackers aren’t changing files, they’re uploading them to the internet. The biggest threat people need to think about right now is their data being copied and stolen. Even if you pay the ransom, you never know if they’re actually going to delete your data or use it again in the future.”
ThreatLocker’s Middle Eastern expansion has been nothing short of explosive, its fastest growing region globally. “When we entered the Middle Eastern market, we had to understand what everyone is looking for here, why ThreatLocker delivers more value and security than everybody else,” Jenkins explains. The key? Presence and partnerships.
“We had to have people on the ground, and we had to have offices here.”
Starting with an office in Abu Dhabi, ThreatLocker is now expanding to a larger office in Dubai to serve the region more effectively including Saudi Arabia, Qatar, and Bahrain.
“Our staff are traveling to customer sites. They’re meeting with resellers and partners constantly, and they’re covering the entire region.”
With a growing list of clients, ThreatLocker has also racked up awards including Best Ransomware Solution, Best Zero Trust, and Best EPP Solution, both globally and in the Middle East.
“We’re very excited that ThreatLocker is really changing the game against ransomware, so companies can now win rather than just being sitting ducks.”
ThreatLocker’s Zero Trust model is gaining traction because it offers clarity in an industry crowded with noise.
“Zero Trust is a really good strategy for stopping threats. Rather than trying to look for every threat that exists, we just focus on what is needed in your environment and how it needs to behave. If it’s not on the list, it can’t run.”


DENIS YAKIMOV
Head of Information
Security and
Privacy
Equiti Group

What are the top cybersecurity priorities for your organization this year?
This year, our top priority is to support the business in achieving sustainable growth and stability as it works toward its strategic objectives. I often see CISOs setting goals in isolation focusing on internal KPIs or reacting to emerging threats without aligning with the broader business context. But it’s critical to remember that security exists to enable the business, and everything we do should be guided by that principle.
How do you align cybersecurity initiatives with overall business goals?
Everything starts with the business setting its goals for the year, which are typically based on shareholder expectations. At Equiti, business goals are clearly defined and openly communicated, so every employee understands the direction in which the organization is heading.
From a security standpoint, we use these goals as a foundation and, at the beginning of the year, during strategy planning, we brainstorm which cybersecurity actions will most effectively support the achievement of these goals. For instance, in 2024 we achieved ISO 27001 certification, which helped Equiti take a significant step toward building stronger trust with key clients and partners and becoming one of the leading brokers in the UAE. Similar security initiatives are aligned with goals related to operational resilience, among others.
What are the key factors you consider when evaluating cybersecurity vendors?
We take a comprehensive approach when selecting vendors, using comparison tables and well-defined
evaluation criteria. These always include compatibility with our existing environment and compliance with local regulatory requirements. For example, in the UAE, financial institutions must store regulated customer data within the country, which immediately disqualifies many SaaS vendors without local data centers.
Given that Equiti is a rapidly growing organization, scalability and ease of deployment are critical factors for us. Once all evaluation criteria are met, we proceed with a PoC, a data privacy assessment, and a third-party risk assessment. While the process may seem complex at first, we aim to complete evaluations at a startup pacetypically within 3–2 weeks.
How do you prefer vendors to approach you, with education, product demos, proof of value?
I believe that anything that helps evaluate a solution within the context of our own environment is highly valuable. I have a hard time understanding vendors who reject proof of concept and instead get caught up in internal approval cycles at this stage. For me, that’s usually a yellow flag. If a vendor is willing to schedule as many meetings as necessary to ensure that the solution works effectively within our infrastructure, that is always an additional reason for me to prioritize them. It signals a high likelihood that they will continue to provide support after the purchase and that they have nothing to hide.
What are the biggest gaps in current cybersecurity solutions that vendors should address?
In my view, areas such as vulnerability management, despite their long history, are still underdeveloped. Even well-established and experienced vendors like Qualys and Rapid7 continue to generate a significant amount of noise in their vulnerability dashboards, and current

prioritization methods do little to change that. I regularly speak with many CISOs across the industry, and I keep hearing about hundreds or even thousands of high and critical vulnerabilities reported by their VM solutions. Yet, in reality, 99% of security incidents are either unrelated to vulnerability exploitation or are linked to vulnerabilities that were not flagged or covered by these VM tools at all.
Are there specific challenges in integration, scalability, or support that you've faced?
We’ve encountered situations where we acquire a tool that fits our needs very well, but face challenges finding the right expertise to implement it properly, considering all the specific requirements. And it’s not even about internal resources it’s about the expertise available on the market. While evaluating a solution itself is relatively straightforward, assessing the contractor's expertise, especially ensuring they are both trustworthy and fairly priced, can be quite difficult. I’ve previously worked at various MSPs, and I clearly remember how service providers often focused on selling the service first, while trying to acquire the necessary expertise during the implementation phase.
What role do vendors play in helping you maintain compliance?
When it comes to vendors and compliance, I truly appreciate the direction the market is taking toward GRC Engineering. I believe this area has the potential to become highly developed and popular in the future - similar to how DevSecOps gained momentum in its time.
Take Vanta, for example. Although it is essentially a tool for automating GRC processes, its interface is so simple and intuitive that it has successfully captured a market even among startups a segment where selling anything from the security domain is typically challenging due to immaturity and limited budgets.
On our side, we are also taking proactive steps toward compliance automation. However, we must consider a wide range of factors, including our presence in multiple countries and various privacy obligations.
How is your cybersecurity budget evolving year-over-year?
There is a lot of talk on social media about cybersecurity underbudgeting, but in reality, many organizations tend to overinvest. A common pattern is CISOs onboarding numerous dashboards that generate excessive noise and offer limited
optimization.
At Equiti, even though we're open to increasing the cybersecurity budget, our team has been focused on cost optimization for two consecutive years, mainly through smarter licensing decisions.
This often means replacing vendors always with a proper risk assessment - but given the vast range of available solutions on the market, finding quality alternatives at a lower cost is rarely a challenge today.
What’s your advice to vendors looking to position their solutions for budget approval?
My advice is not to focus on addressing yet another threat, but rather to demonstrate how your tool brings real business value. Modern CISOs are increasingly expected to speak the language of the business and sit at the board table. As a result, the tools in a CISO’s toolkit should support business enablement, not just threat mitigation or the addition of another dashboard. If you look at the most successful cybersecurity companies such as Wiz, Okta, or Zscaler they’ve become integral to their customers’ operations and have a direct impact on business efficiency.
Have you collaborated with vendors on co-developing or customizing solutions?
Absolutely. Vendors willing to adapt their roadmap for our needs are always strong candidates. For example, we’re working closely with a SAST vendor that is developing integration features for one of our specific CI/CD environments.
Since this environment is relatively niche and not widely supported out of the box, the vendor’s willingness to invest effort in saving us extensive engineering time on custom integration has been a major factor in our decision. I must admit, this kind of flexibility is more common among small to mid-sized vendors.
What common mistakes do vendors make when engaging with CISOs?
Pushing too hard and being overly persistent. In my view, if someone genuinely needs your product, they will be responsive and willing to do whatever it takes to close the deal quickly. If you spend your time chasing people who show limited interest, you might move the deal forward temporarily, but in the end, it will likely fall through and you will have simply wasted time.


What’s one innovation or improvement you hope to see from vendors in the next 12 months?
Although I remain skeptical about the grand future predicted for AI,where it is expected to replace humans, I personally would like to see more practices focused not on solving isolated microtasks or problems by introducing yet another tool to the portfolio, but rather on enabling the correlation of all available security data into a unified pool of interconnected knowledge.
Such an approach could help predict where threats are most likely to emerge or which changes would yield the most significant impact. I believe that an AI system capable of aggregating insights across the entire organization and its cybersecurity tools could deliver this kind of value.
In today’s world, many security leaders still make strategic decisions based on educated guesses and abstract, subjective risk assessments essentially, reading tea leaves rather than relying on data-driven foresight.









catch all the ACTION, INSIGHTS, and UPDATES across our socials.














catch all the ACTION, INSIGHTS, and UPDATES across our socials.




















































The first shift? Believing
So my mission now is to dismantle those lies, not just for me, but for the next generation. Helping them unlock their potential helped me unlock my own

GISEC didn't just amplify our voice, it handed

























































