
13 minute read
Exploring augmented reality
Inti De Ceukelaire, Head of Hackers, Intigriti, Belgium, emphasises the need for continuous cybersecurity testing in the oil and gas pipeline sector.
Mention oil and gas pipeline security, and most people think of large physical assets, sometimes spanning continents, needing protection from saboteurs. But protecting the digital attack surface has become just as critical for the safety and functioning of this vital infrastructure.
Today’s pipelines are monitored and controlled by advanced software and hardware systems, and these are open to attack from that decidedly modern type of saboteur: the malicious hacker.
Why would a hacker spend hours trying to bypass the cybersecurity a pipeline operator has put in place? Put simply: to steal or compromise digital assets. System functionality is a common area of attack through ransomware and denialof-service attacks (DoS), but these hackers may also be after customer and financial information, intellectual property, and other sensitive data.
The cost of cybercrime While major industries like pipeline providers, airlines, port authorities, etc. can face serious real-world consequences if their cybersecurity is compromised, the financial costs of a successful attack can also be staggering. In 2021, the annual ‘IBM Cost of a Data Breach Report’ found that the global average cost of a successful data breach on individual businesses was US$4.24 million (up from US$3.86 million in 2020).1 The trend looks set to continue, and some security experts are estimating that global cybercrime will hit US$10+ trillion by 2025.2 In 2021, the cost had already topped US$6 trillion. If that were GDP, it would make cybercrime the third-largest economy in the world, after China and the USA.
Beyond bearing the financial brunt of these attacks, organisations often also suffer damage to their reputations, and see major disruptions to the work they do. For gas and oil pipelines providers, the crippling of operating systems has the potential to cause not only major financial losses, but also disruption of critical energy supplies that can impact people far and wide.
In short, the stakes are high, and with the number of malicious attacks trending upwards, the need for effective and continuous security monitoring of digital attack surfaces has become a high priority.
Evolving threats on the digital attack surface An organisation’s digital attack surface is defined as the totality of connection points available to a malicious hacker seeking unauthorised access. Vulnerabilities in these connection points are how hackers gain entry to software and systems to do their damage.
These hackers are persistent and patient. They know that just as technology evolves, so do security vulnerabilities. If your security posture means you have comprehensively protected your pipeline IT infrastructure against all known threats, it unfortunately does not mean that you will be protected against unknown and evolving threats in the near future.
Tomorrow is another day, as they say. And tomorrow, there is always the potential of new vulnerabilities being discovered in your systems. Robust cyber defences must therefore continuously test for cybersecurity threats, and be able to pre-empt the creativity of these hackers.
Problems with common cybersecurity approaches Until recently, automated scanning and pen testing were considered among the most viable ways to protect an organisation against cyberattack. But such security methods, while useful, are far from providing a symmetrical response to the creativity of the world’s malicious hackers.
First, they test primarily for known vulnerabilities and have no ability to creatively
explore for evolving attack vectors – and these undiscovered weaknesses are precisely what the most sophisticated hackers are looking for. Secondly, and perhaps most importantly, pen tests – once the gold standard for cybersecurity testing – assess attack surface vulnerabilities only at a single moment in time, and are not performed day-in day-out. To put it bluntly, that is not frequently enough to secure your pipeline systems.
In its 2022 ‘Ethical Hacker Insights Report’, Intigriti interviewed over 1700 security experts on this very subject.3 Of the respondents, 90% agreed that “pen tests cannot provide continuous assurance that an organisation is secure year-round.”
Penetration tests focus on one snapshot in time, whereas bug bounty programs are continuous; as attackers shift tactics, cyber defences must too. The only way to test their effectiveness is to apply continuous pressure against them. Considering that an organisation’s security posture will change with each new feature release or update, it’s not only a logical step to implement more security testing, but also critical.
The growth of crowdsourced bug bounty programs A bug bounty program uses the crowdsourcing of independent security researchers – often called ‘ethical hackers’ – to test an organisation’s security. If bugs (vulnerabilities) are found, they are reported in a legally compliant matter.
Bug bounty programs have been around in various guises since the 1980s, but have seen accelerated adoption among enterprise, government and other large organisations in the past ten years. The reason? More and more security experts have come to recognise them as the best way to provide continuous security testing that functions at the same level of ingenuity as malicious hackers.
Major companies like Intel, Meta, Google, Microsoft, and many more now run bug bounty programs. Governments too have been fast to adopt this method of cybersecurity. In Europe, the EU runs an ongoing program, and the US government has been running programs since March 2016 when its first bug bounty program, known as the ‘Hack the Pentagon’ program, saw 138 unique, valid reports from over 1400 security experts.
Advantages of crowdsourced cybersecurity The popularity of bug bounty programs can be explained by the distinct advantages they deliver over traditional cybersecurity approaches. For a start, they enable organisations to leverage the skills, experience, and creativity of thousands of security experts from across the globe. These ethical hackers will be working around the clock to test for vulnerabilities in a customer’s systems, with a hope of gaining a ‘bug bounty’ – often a financial reward.
Crowdsourced bug bounty programs are also seen as providing guaranteed ROI. Unlike a pen test, where you pay a fee irrespective of whether vulnerabilities are discovered or not, bug bounty hunters are only paid when they report a unique and valid vulnerability. This increases the motivation of ethical hackers and ensures businesses only pay when something useful is uncovered.
Businesses deploying bug bounty programs can also scale their security testing at any time by running additional programs or increasing the scope of existing ones. This will frequently turn up new vulnerabilities of different severity levels, enabling security teams to gain awareness of vulnerabilities faster, and, in turn, introduce fixes faster.
So how do you get started with running a bug bounty program? While some organisations still set up their own bug bounty programs, today, increasingly sophisticated bug bounty platforms are becoming the norm for businesses and institutions because of the many benefits they provide.
The evolution of bug bounty platforms A bug bounty ‘platform’ is usually a cloud-based offering from an independent company that allows for the set-up and administration of bug bounty programs.
Each platform provider will have a different offering, and while we can’t speak for others, Intigriti has developed some very effective services that make running bug bounty programs particularly suited to the business world.
As a cloud platform, getting up-and-running is greatly simplified compared to building an internal bug bounty program. User experience is maximised, and set-up, budgeting and launch of a program are so streamlined that even a non-technical user can run a program – though ample documentation and human support is always available.
Programs can also be private or public. With a private program, you select only the researchers you want to work with and no one else knows about the program. Alternatively, launching a public program will make it open to our full, global ethical hacker community. In both cases, all the ethical hackers working with Intigriti are contractually bound to respect high standards of privacy and safety.
Customers launching a bug bounty program regularly see multiple vulnerabilities reported within a couple of days of launch. While that might sound overwhelming, it is a lot less to deal with than a successful attack. Moreover, Intigriti offers a unique, time-saving triage service as part of every program where secure researcher submissions are checked for uniqueness and validity before they are delivered to the customer.
Throughout the lifecycle of each program, the platform also provides a 100% transparent status overview, comprehensive budget reports, and real-time updates that can include centralised communication with the ethical hackers working for you.
These are just some of the reasons why organisations like PortXchange, European Commission, Brussels Airlines, and Europe’s second-largest port – Port of Antwerp – choose Intigriti as their bug bounty platform.
Effective cybersecurity for oil and gas pipelines In a world of fast-evolving tech, the key to effective cybersecurity for the oil and gas pipeline industry is to deliver continuous security testing that can anticipate the actions of malicious hackers. In the best of both worlds, this type of cybersecurity would also be affordable and would deliver critical results rapidly. This is precisely what a bug bounty platform like Intigriti provides to businesses across the globe.
References
1. www.ibm.com/security/data-breach 2. cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/ 3. www.intigriti.com/landing/the-ethical-hacker-insights-report-2022
The oil and gas industry as a whole is increasingly waking up to the potential applications of AR and VR technology, suggests Francesca Gregory, GlobalData, UK.
ugmented reality (AR) allows users to see the real world overlaid with a layer of digital content. This digital content layer can include sensor-based data, location-based data, sound, video, graphics, or other datasets. The use of AR can involve headsets that overlay information onto the viewer’s field of view or the use of AR software, which can overlay the data onto a live video feed. While the application of AR to the oil and gas sector is still in its early stages, this technology has the potential to significantly disrupt the industry within the next few years.
AR provides a means of addressing key challenges Adoption of AR within the sector will accelerate as oil and gas companies increasingly realise the potential for AR to improve the efficiency of their operations. AR will be used to streamline workflows in two key ways. Firstly, AR’s ability to facilitate remote assistance saves machine downtime and lengthy maintenance visits to sites. Remote experts can support field technicians by overlaying annotations and instructions onto their field of view. As a result, AR can improve the efficiency of planning, maintenance, and repair tasks. Furthermore, AR devices will help workers utilise large volumes of data as the oil and gas industry integrates Internet of Things (IoT) technology into its operations. AR devices that are safe, secure, and handsfree will be the missing link between data and the meaningful application of this information.
AR’s second primary use case relates to the oil and gas industry’s shifting workforce. AR is a technology that can be used to tackle the industry’s ageing workforce and the need to train a new generation of workers. The next few years will be crucial for oil and gas companies as they seek to expedite the training of younger workers and pursue more flexible ways of working to maximise knowledge capture from those that are

retiring. Emerging technologies such as AR will be a vital piece of the puzzle for knowledge capture and transfer, and will help prevent a skills gap from emerging.
Companies that are realistic about the use cases of AR, and apply the technology appropriately, stand to benefit significantly. The integration of technologies such as AR into workflows as part of the industry’s wider digitalisation will yield both time and cost savings, rewarding innovative companies with an edge over their competitors and a workforce resilient to disruption.
The global AR market will grow rapidly AR revenue is expected to increase as the rate of adoption rises. GlobalData forecasts that the market will increase from US$7 billion in 2020 to US$37 billion by 2025. In this early phase of AR’s growth, the market size of consumer and enterprise AR are similar, each contributing just under US$20 billion. In this stage, the price point will restrict the uptake of AR wearable devices. In February 2022, a consumer Microsoft HoloLens 2 is priced at US$3500. Similarly, with additional certifications, the industrial edition will cost companies US$4950 per headset. This price point for industrial devices has historically limited AR adoption to the oil and gas industry’s biggest players, such as Chevron, Baker Hughes, BP, and Shell.
The AR market will enjoy strong growth beyond 2025 (Figure 1). AR revenue will reach US$150 billion by 2030, with a CAGR of 33% between 2025 and 2030, according to GlobalData forecasts. This can be attributed to the cost of AR devices decreasing as the technology becomes increasingly ubiquitous and the improved user experience. The growth will largely be facilitated by enterprise applications, which will contribute US$100 billion to the size of the overall market in 2030, compared to US$50 billion for the consumer segment. The increasing proportion of enterprise AR revenue also reflects a growing awareness of the number of potential use cases for the technology.
More AR wearables being certified as intrinsically safe will catalyse adoption in the oil and gas industry. As a result, the oil and gas industry will become a key market for both AR hardware and software. Technology vendors are also positioning themselves to address oil and gas companies’ requirements. This was confirmed in an interview conducted by GlobalData with industrial technology company Trimble, where the Director of Product Strategy and Innovation revealed how the company had tailored its products for oil and gas use cases. Examples of modifications include achieving a Class 1 Division 2 safety rating on the ruggedised AR headset, the Trimble XR10. Trimble also added bone conduction to the original audio device of the HoloLens 2 for ease of hearing. In addition, the clip-on Trimble HoloTint provides a sunshade for outdoor use in hot environments. While still an emerging technology in the oil and gas sector, the specialisation of AR devices to the industry’s requirements is already taking place and will facilitate future adoption.
AR mentions are on the rise The oil and gas industry as a whole is increasingly waking up to the potential applications of AR and Virtual Reality (VR) technology. GlobalData’s company filing analytics database (Figure 2) reveals that in 2021, these two technologies were mentioned on 302 occasions in oil and gas companies’ filings. The number of companies mentioning the technology within their filings also increased, rising from 59 in 2017 to 106 in 2020. The significant increase in companies mentioning AR and VR can be attributed to the release of industrial AR headsets. In particular, the release of rugged and intrinsically safe headsets, such as the Trimble XR10 and HoloLens 2 combination and the RealWear HMT1Z1, increased the potential for AR to provide a hands-free solution to many technical challenges in the oil and gas industry, boosting the number of companies talking about this technology within their filings.
AR active jobs are also on the rise within the oil and gas industry (Figure 2). GlobalData’s jobs analytics database shows a 61% increase in active jobs related to AR and VR within oil and gas companies between March 2021 and March 2022. The growth trend across this year is particularly interesting given the COVID-19 context. Despite the pandemic disrupting demand and causing oil prices to decline, the increase in hiring activity around
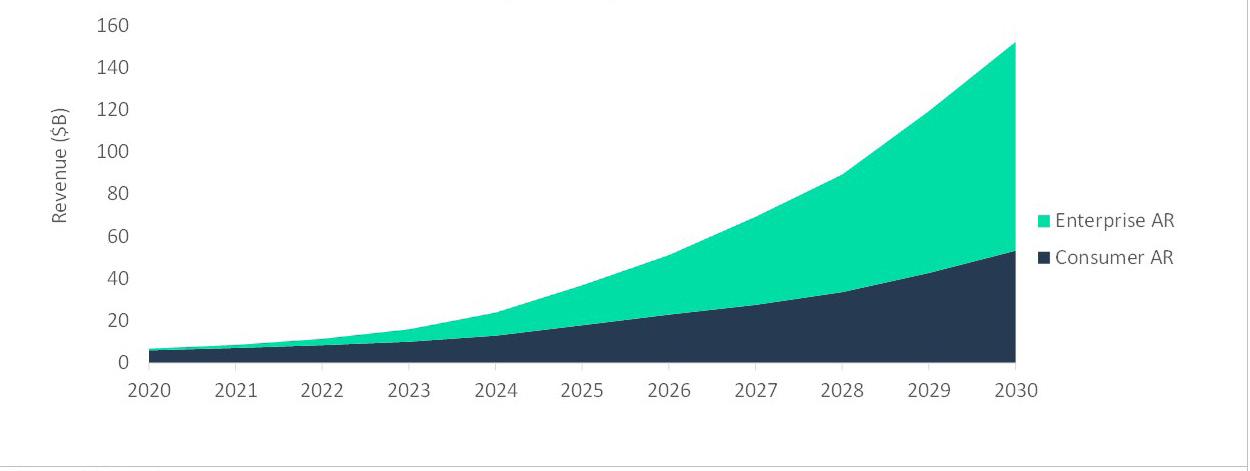
Figure 1. Global AR revenue by end user, 2020 - 2030. The global AR market will reach US$37 billion by 2025 and US$152 billion by 2030. Source: GlobalData.










