Cyber Month Spotlight on Expert Insights & Digital Defense






Editor-In-Chief
Swati Gupta
Chief Strategist
Mohit Agarwal

Your Digital Sherpa to Tech Enigma

Your Digital Sherpa to discover Tech Enigma
Embark on a thrilling expedition into the future of digital advancement with CXO TechBOT, your ultimate gateway to unlock the boundless potential of technology.
JOIN THE COMMUNITY
MAGAZINE I NEWSLETTER I WEBSITE

Head of Design
Harsh Kumar
Communication Manager
Bhumika Nandhani
Head of Content
Suhas Vittal
Content Editors
Suhas Vittal, Priya Sharma
Head of Technology, Delivery & Operations
Priyanka Gautam
Director of Talent and Communication Manager
Ruchika Sharma
Digital Partner
Fusionflare media
Creative Manager
Mayuree Rastogi
Web developer Alok Bhade
Video & Production Manager
Bhawesh Mishra
Creative Co-coordinator
Umesh Tiwari
Customer Success Manager
Subha Gupta
CEO Swati Gupta

As we mark Cyber Month, it's essential to reflect on the dynamic landscape of cyber threats and the innovative strategies emerging from the cybersecurity sector With cybercriminals growing increasingly sophisticated, insights from Chief Information Security Officers (CISOs) highlight the urgent need for organizations to adopt a proactive approach to risk management
The integration of AI-driven security solutions has become a crucial focus, enhancing organizations' threat detection and response capabilities. As adversaries leverage advanced technologies, employing machine learning and automation is vital for identifying anomalies and preventing potential breaches before they escalate.
A significant transformation in cybersecurity is the widespread shift towards Zero Trust Architecture This paradigm emphasizes the continuous verification of trust rather than assuming it, empowering organizations to protect sensitive data more effectively and minimize potential attack surfaces.
This Cyber Month serves as a poignant reminder of the critical role cybersecurity plays in our increasingly digital world Together, let’s promote security awareness, encourage collaboration, and develop forward-thinking strategies that protect our organizations and communities
Secure the future today, for a safer digital tomorrow

SWATI GUPTA CEO & Editor-in-Chief


























74 Emerging AI-Powered Ransomware A New Frontier in Cyber Extortion
76 The Future of AI in Cyber Warfare National Security and AI-Powered Attacks
80 Consolidation vs. Optimization
68 Enforcing Security Protocols Best Practices for Safeguarding Sensitive Information Which Is More Cost-Effective for Improved Security?

68



76


The collaboration between SoftwareOne and OPSWAT aims to enhance the security of critical infrastructure and addresses modern cybersecurity challenges. The venture merges SoftwareOne’s expertise in cloud and software solutions with OPSWAT’s specialism in IT, OT, and ICS (Industrial Control Systems) critical infrastructure cybersecurity, delivering comprehensive solutions.
OPSWAT: Aleaderincriticalinfrastructuresecurity
For over 20 years, OPSWAT has specialised in cybersecurity for IT, OT, and ICS environments. Guided by the principle of "Trust no file Trust no device ™ , " OPSWAT offers end-to-end solutions designed to protect complex networks and ensure compliance Their approach includes zero trust solutions and patented technologies that safeguard networks, data, and devices from both known and unknown threats, including zero-day attacks and malware For more information, visit OPSWAT.

Manish
ManagingDirectoratOPSWATIndia&SAARC

Manish Gautam, Managing Director at OPSWAT for India and the SAARC region, is a prominent figure in the cybersecurity industry with 18 years of experience. Previously serving as Managing Director at Array Networks and starting his career at Select-WeP (Wipro Group), Gautam has a proven track record in delivering complex IT solutions and achieving high client satisfaction. His leadership focuses on prioritising people and fostering a culture of growth and development. Based in New Delhi, he holds a degree from NIT Trichy and an MBA from FMS Delhi
Organisations are driven to deliver on their missions, but they only have finite resources to innovate and succeed. That’s where SoftwareOne comes in As a global IT reseller, solutions, and services company, SoftwareOne systematically optimises IT environments, producing savings to fund the technology businesses' needs to transform and keep on transforming
SoftwareOne optimises ROI from IT spend, simplifies access and support, enhances workplace productivity, and accelerates SaaS, cloud, data, and AI adoption With approximately 9,300 employees dedicated to delivering a portfolio of 7,500 software brands, SoftwareOne provides sales and delivery capabilities in over 60 countries.



Munish Gupta, Managing Director at SoftwareOne India, brings over 20 years of experience in the technology sector His approach of keeping customer first, sharp focus on operational excellence and belief in continuous development of team has led to hyper growth over last 3 years for SoftwareOne in India. His career includes significant roles at Microsoft, Nortel Networks, and Vodafone, where he successfully managed multi-million-pound businesses Munish Gupta’s expertise in business strategy, operations management, and technological innovation has driven substantial growth He is dedicated to leveraging technology for societal advancement and educational transformation.


According to a recent survey, the Global AI investment is expected to reach $200 billion by 2025 Artificial intelligence (AI) has become a transformational force that's changing economies, industries, and our everyday lives While the more obvious applications of AI, like driverless cars, virtual assistants, and predictive analytics are well known, there is another, less obvious, but no less significant aspect of AI that is slowly but surely seeping into many industries.
Blockchain Technology and Invisible AI hold huge potential for transforming industries by creating systems that are not only more
efficient and autonomous but also more secure and transparent. Reports indicate significant growth in the AI market for blockchain technology, projecting a CAGR of 25.3% from USD 228 million in 2020 to USD 703 million by 2025 (MarketsandMarkets) This growth heralds a future where AI and blockchain synergize to redefine operational paradigms across diverse sectors, offering novel solutions and reshaping business landscapes worldwide.
The Evolution of AI: Visible to Invisible Technology is undergoing radical change as artificial intelligence (AI) develops from visible to unseen forms Initially, artificial intelligence (AI) systems were clearly visible and distinct. They were used in fields where interactions were well-defined, like robotics and complicated computing systems. With time, artificial intelligence (AI) has permeated more aspects of daily technology, evolving into intuitive parts of devices like voice assistants and merging in with our surroundings We are living in the age of invisible AI, when technology improves user


experiences without requiring direct contact by working quietly in the background In addition to making technology more userfriendly and less obtrusive, this shift towards invisibility also poses significant concerns around privacy and ethical usage As AI becomes more ingrained in our personal and professional lives, the challenge is to leverage these advancements while prioritizing transparency and ethical standards
The authenticity of Invisible AI lies not only in its capacity to replicate human decisionmaking but also in its deep ability to enhance and personalize user experiences while remaining largely unseen This technology operates discreetly within the systems we engage with on a daily basis improving our interactions and streamlining our tasks without drawing attention to itself The most compelling feature of Invisible AI is its profound ability to deliver user-centric personalization, tailoring interactions to match individual preferences and behaviors. This customization cultivates more authentic and intuitive user experiences, significantly enhancing overall satisfaction. By seamlessly integrating Invisible AI into daily activities, it ensures that technology serves and anticipates the unique needs of each user, making every interaction more relevant and engaging
Although Invisible AI can greatly improve personalization and efficiency, it also poses serious ethical questions. Consent, privacy, and transparency are major concerns Users frequently don't know how much data is being processed or what judgments are being made for them because AI systems work in the background It is essential to uphold moral principles and legal requirements for these intangible
systems in order to preserve public confidence and safeguard individual liberties
Transparency and user control must be given top priority by developers and businesses in order to solve these ethical issues. Users ought to have control over their personal data and knowledge about the AI systems they use This can be accomplished with the aid of clear user agreements, options to decline AI interactions, and robust security measures to protect data privacy



Invisible AI is rapidly gaining traction across diverse industries where its ability to improve security, expedite processes, and guarantee authenticity is vital Retail and E-commerce, Healthcare, Finance and Banking, Manufacturing and Automotive and Smart Cities among others are some examples of how Invisible AI is rapidly becoming a cornerstone technology for multiple industries
Invisible AI, integral to Ennoventure's operations, is critical in improving customer satisfaction and business operations. Ennoventure ensures that the cryptographic code remains undetectable to the naked eye, by integrating artificial intelligence into its solutions, thus preserving the integrity and aesthetic of product packaging
For our clients, this translates into a stable and dependable authentication solution that is inexpensive and simple to implement because it doesn't require alterations to current packaging procedures. The AI-driven technology provides a scalable way to fight counterfeiting and can be applied to various product package designs in just 48 hours. This seamless integration enhances efficiency and protects brand identity
For customers, Invisible AI guarantees a simple and easy product verification process for consumers They can use their smartphones to scan products and instantly verify their authenticity, enhancing their trust and confidence in the brands they purchase Additionally, the AI-driven encryption also provides customers with comprehensive details on the product, such as its ingredients, manufacturing date, and possible adverse effects.
Incorporating invisible AI into services has a number of challenges, primarily centered around data security and privacy Large volumes of user data are frequently needed for these systems to operate efficiently, which raises questions regarding data security and compliance with laws like the CCPA and GDPR. To safeguard user data, providers need to use strong encryption and anonymization methods There are a number of difficulties when integrating invisible AI into services, most of them are related to data security and privacy Retaining integrity and trust also depends on upholding ethical AI techniques. This entails creating biased-free and equitable AI systems, which calls for ongoing algorithmic monitoring and development. To control AI use, businesses must set explicit ethical standards and legal frameworks
In addition, it might be technically difficult to integrate invisible AI into platforms; it calls for large expenditures in infrastructure, data management, and AI knowledge. Meticulous preparation and execution are necessary to achieve seamless integration without interfering with current services. Moreover, even if seamless user experience is the aim of invisible AI, consumers must be made aware of its features and advantages. Users must be aware of these systems' benefits before they can completely trust and accept them Companies should invest in user education and support to facilitate this understanding.
The era of invisible AI promises more innovation and adaptation in the future Artificial intelligence (AI) capabilities will continue to improve detection accuracy and reactivity, keeping up with changing counterfeit strategies Ennoventure is steadfast in its commitment to advancing these technologies, working together with companies to negotiate the intricacies of a digital economy.
In summary, invisible AI signals the beginning of a new era in which invisibility and authenticity combine to reimagine brand protection At Ennoventure, we welcome this change and give brands the tools they need to protect their good name and customers' confidence in a time when being genuine is crucial




rPadmakumar Nair is the CoFounder and CEO of Ennoventure, Inc An alumnus of the MIT Sloan School of Management, he brings with him over 18 years of leadership experience across the globe in devising strategies that bring companies to success. He has managed multi-disciplinary, crossfunctional, and geographically diverse teams to optimise business value by following a motivational style of leadership and encouraging open communication
The arrival of generative artificial intelligence (Gen AI) is transforming numerous sectors, with cybersecurity standing out as one of the most critically impacted. The technology brings forth both unprecedented opportunities and formidable challenges How Gen AI is redefining the cybersecurity landscape, how it’s enhancing defence capabilities while also creating new threats, and key considerations for CISOs and senior management to address these emerging challenges effectively let’s find out
Historically, cybersecurity threats have been generally fixed or semi-static and oriented
around a core set of tactics, techniques, and procedures (TTPs) But now the advent of Generative AI has ushered in a new era – one that brings with it more complex and flexible threats. While traditional AI is mainly centred on recognizing patterns and detecting outliers, Gen AI can self-generate content, replicate human behaviours, and even create new types of malware
Generative AI’s dual nature is both a blessing and curse in the realm of cybersecurity where it not only creates risks but also powers up defence mechanisms.

Tripathi Director,OctalLimited
There are numerous predictions on the tendency of cybersecurity with the emergence of the concept of Gen-AI. The overall development of AI behind the generation of text, images and codes has accelerated and brought with them new challenges and opportunities to cybersecurity defenders Here’s how:
Improved Threat Detection and Response
AI-Driven Security Solutions
Gen AI models can detect patterns within massive volumes of data that may be indicative of a cyber threat This helps in identifying an attack in the initial stage and ward off the attack resulting in less damage.
question the effectiveness of biometrics such as fingerprinting and voice recognition. This increases the importance of identity and access management implementations
Spoofing and Impersonation: Since Gen AI can impersonate persons or generate fake personas, attackers can just forge past security measures.
Data Privacy and Protection

Automation and Predictive Analytics: The use of AI in cybersecurity can help identify threats that are likely to emerge in an organisation and deal with them proactively before they occur.
AI-Powered Cyber Attacks:
Gen AI is applied by cybercriminals to create improved phishing, malware, and social engineering experiences. AI can easily create more or less realistic fake messages, which increases the difficulties of differentiating between real and fake messages between individuals and systems
Automated Hacking Tools: The technologies of AI are being applied to create tools capable of detecting weaknesses and exploiting them, which may increase the speed of cyber attacks.

relating to Authentication and Identity Management
Deepfakes and Voice Cloning: Gen AI allows deepfakes and cloned voices that may

AI-Generated Content and Data Privacy: What substantially enhances the process is the use of AI for the generation of synthetic data; however, it entails novel difficulties concerning data protection Care must be taken to avoid the fact that such created content does reveal information which ideally should not be disclosed
Regulatory Compliance: As for Gen AI, new cybersecurity AI regulation is required to regulate the application of AI to promote proper use and protect data privacy.

AI vs. AI: While the defenders are applying AI to protect the systems, the attackers also employ the use of AI to identify the gaps in the implemented AI-security defence. This leads to the formation of a new cycle of attack and defence whereby AI algorithms are used to counter other AI algorithms.

Adversarial Attacks: There are specific methods such as adversarial machine learning, where the attackers can manipulate the AI models so that they can make the wrong decision on certain issues, like for instance, identifying a fraudulent activity as legitimate.
Bias in AI Models: AI is dependent on data fed into the systems and hence its quality depends on the data used in the training of these systems. Hence, when the training data selected is skewed, one may find that their AI-deployed security tools are not as effective in some scenarios as they could be – translating to vulnerabilities.
Ethical Considerations: Various ethical concerns are associated with the application of AI in the cybersecurity field; this includes questions of surveillance as well as privacies and Civil liberties.
Need for AI Expertise: This is because the implementation of AI in the cybersecurity industry generates a need for a workforce that has equal knowledge in both AI and Cyberspace security. This thus demands developing new programs that will enable the current workforce to be trained, as well as the development of new courses to be taught.
Changing Roles: More specifically, as AI continually takes on mundane work, these cybersecurity specialists may transition from simple tasks to more complex ones such as AI governance, AI policy, AI governance, and future threat identification.
Nation-State Actors and AI: Governments are also deploying AI applications in their
cyber strategies for both countermeasures and cyber attacks Consequently, these have impacts on the overall state security and international cyberspace power relations.
Collaboration and Information Sharing: The sophistication of artificial intelligence in craft and launching cyber threats requires governments, private sectors and international organisations to intensify information sharing and come up with a common front
With the emergence of Generative AI, the responsibilities of CISOs are changing more profoundly and rapidly than at any point in time in the past. Security professionals are confronted with challenges and opportunities of this emerging age known as Gen AI as organisations adapt themselves to this period of change Key considerations for CISOs and senior managers include: Key considerations for CISOs and senior managers include:
Strategic Alignment: Cybersecurity should be aligned with the business strategy and has to incorporate AI for improved security and client’s growth
Adapting to AI-Driven Threats: CISOs require proactive threat management which involves using artificial intelligence in threat intelligence, automated detection and adversarial artificial intelligence readiness
Ethical AI Usage: Understanding definitions of fairness and prevention or mitigation of biases and privacy violations in the AI systems with accountability and explainability of AI decision-making
Workforce Transformation: Training those working in the cybersecurity domain for AI,
encouraging interdisciplinary work, and adopting the human-AI Work Partnership model.
Continuous Monitoring: Implementing flexible security measures, perpetual model assessment, and the use of big data Regulatory Compliance: Updating oneself with the new regulations on AI and cybersecurity, the data protection laws as well as the legal issues at play.
Investment in Emerging Technologies:
Looking into a new generation of AI-based security solutions, thinking of AI SOC and collaboration with the AI tech companies.
Culture of Security and Innovation:
Creating awareness, providing the means to foster creativity and thus establish a security-aware culture, and demonstrating the significance of security in the new age of AI within the company’s IT environment.
Cognitive cybersecurity is evolving into a generative force, offering enhanced protection and new avenues for both defence and exploitation by cybercriminals This dual nature of generative AI demands a more proactive and strategic approach, particularly for CISOs and senior management. To stay ahead of sophisticated threats, organizations must align AI-driven security measures with broader business objectives, treating the integration of AI not as an option but as an essential strategic priority. This means consistently leveraging AI security solutions to preemptively counteract evolving threats while recognizing that malicious actors are also advancing their use of AI In this new era, AI must be embedded at the core of cybersecurity strategies, empowering organisations to stay resilient and defend against increasingly sophisticated cyberattacks.




Rakesh Tripathi is an independent consultant in Cyber Security, Risk Management, and IT Governance, with over two decades of experience across various industries. His expertise spans Identity and Access Management (IAM), Cyber Security, and Project/Programme Management, with a strong emphasis on designing and implementing security architectures and compliance frameworks like ISO and NIST.
Rakesh holds a Master's degree in Computer Science, with advanced certifications from Oxford University and Harvard University in Executive Leadership and Risk Management. His extensive industry experience spans investment and retail banking, healthcare, payments, and FMCG, and he has earned professional certifications including CCISO, CISSP, and CISA.
Currently providing consultancies as the interim Head of Identity and Access Management for a leading banking client, Rakesh has a proven track record in delivering complex enterprise-wide projects and strategies. He has led global engagements, working closely with senior management and board members to enhance security and risk management frameworks, with expertise extending to financial regulations and compliance to ensure robust protection against emerging threats


The current world’s business environment can best be described as unpredictable which requires not only a sound but also a resilient IT system. This capability is not just a function of how they run their business, but it is a necessity if they are to compete effectively To be effective, leadership in IT must pay prior attention to the development of robust systems that incorporate security and business continuity strategies to protect organisational credibility and efficiency.
Such a competitive environment calls for the adoption of new technologies as well as the use of enhanced security measures. The development of a culture of agility and refinement thus enables organisations to prepare for, and adapt to, future challenges, thus guaranteeing ongoing success and market superiority
BCDR plans are critical components of contemporary approaches to business IT infrastructure management A sustainable IT system should not only be able to cope with unexpected interruptions but also be able to combine successful strategies with possible threats. Business continuity and disaster recovery work hand in hand to guarantee that business continues even under unfavourable conditions Business continuity can be defined as the ability to keep critical business operations running during and after disruptions, while disaster recovery is more specific to the recovery of information technology systems after a disaster However, both elements are essential in strategy formulation to reinforce the stability of any organisation.

The development of a robust IT environment is a long process that requires reflection and careful planning Threats and vulnerabilities should be identified and a detailed business continuity plan (BCP) as well as disaster recovery plan (DRP) has to be prepared to cope with threats and risks. They should include guidelines and protocols for actions and outcomes of responses and recovery measures, predetermined roles and tasks of every participant. Availability of communication points, as well as regularly updated records of IT assets is necessary when managing incidents.
Risk management is a critical element in protecting the strategic foundation of an IT architecture. Another best practice involves performing comprehensive risk analyses to assess potential risks and risk-prone areas Consequently, this approach allows for the enhancement of sound security measures, as well as well-coordinated strategies and backup plans the organisation might require In this context, the potential impacts can still be managed by IT leaders and sustained operational effectiveness achieved due to constant risk assessment and adaption.
Due to the many and varied threats present in today’s environment, a layered security approach is imperative for safeguarding an organisation’s IT resources This includes the use of better firewalls, intrusion detection systems and better encryption technologies In addition, periodic security audits and vulnerability assessments serve to define possible weaknesses. Secondly, ingraining a security-conscious culture in the organisation makes the employees more sensitive to security risks and take the necessary action in the event of an incident
Data backup and failover are important because they help to maintain the accuracy of the data and the organisation’s operations That is why such measures as the deployment of redundant systems and data replication measures prevent interruption of business processes. The performance of these systems should be checked frequently to verify operability in cases of crisis With the help of cloud and hybrid systems implemented, it is possible to build an even more flexible and scalable system that will contribute to organisational resilience

Antifragile IT goes deeper than technology; it incorporates the organisational character. Training and developing employees means that they acquire all that they need to know and do to control risks. Risk management is not merely avoided within a resiliencefocused mindset, but it makes the overall organisational ability to adapt to changing conditions.
Cloud and hybrid IT solutions can be used effectively to enhance IT operational business continuity These solutions provide businesses with efficient and affordable solutions for data storage, backup and retrieval When cloud services are incorporated into organisational IT plans, they also add backup and continuity in case of catastrophes. Additional options such as using a combination of on-premises and cloud-based resources enhance flexibility and reliability precluding the necessity to make dramatic changes to the system in response to new requirements
Where IT resilience management is concerned, the future is equally unpredictable and more specifically proactive as the advancement in technologies is escalating at an alarming rate The adoption of newer and more sophisticated tools like AI and big data analytics will improve the ability to better predict and manage existing and future pressures that organisations may face while providing the organisation with the ability to recover from problems quickly.
As threats become more complicated and prevalent with cyber criminals employing various tactics and techniques, security will have to be dynamic with the use of intelligence feeds and self-defence mechanisms. Building a culture of flexibility and constant improvement will only strengthen IT environments even more It’ll help organisations be prepared for future disruptions and thrive in a complex digitallydriven environment



Mr Pradeep Rao is a distinguished IT leader with over two decades of comprehensive experience in technology, consulting, and executive roles As the Director and Chief Architect at Kyndryl, Mr. Rao leads the Security and Resiliency Services Center of Competency, focusing on delivering advanced and secure architectural solutions His extensive expertise encompasses public and private cloud computing, IT service management, data centre services, and enterprise architecture.
Prior to Kyndryl, Mr Rao served as Chief Architect at IBM, where he was instrumental in IT transformations, cloud migrations, and data centre relocations. His tenure at Capgemini as a Manager in IT Infrastructure Solutions saw him overseeing multimillion-dollar projects and leading cross-cultural teams to successful outcomes Mr Rao’s career began at HCL Infosystems as a Senior Engineer, where he managed large infrastructure projects and led technical teams.
Holding a Master’s in Information Technology from Kuvempu Vishwavidyanilaya, Mr Rao’s credentials include numerous certifications such as Certified Independent Director (IICA), Google Cloud Certified Professional Cloud Architect, and Microsoft Certified Azure Solutions Architect Expert His strategic vision and technical prowess position him as a leader in driving meaningful technological change and innovation.
As quantum computing advances at an unprecedented pace, the landscape of cybersecurity faces a looming threat The immense computational power of quantum systems is expected to render current encryption methods obsolete, enabling quantum cyberattacks capable of crippling entire networks in mere minutes. With traditional cryptographic algorithms vulnerable to quantum decryption, organizations must act swiftly to safeguard their digital infrastructures Enter PostQuantum Cryptography (PQC), a solution designed to withstand the capabilities of quantum computers and secure the future of digital security
Quantum computing has the potential to revolutionize industries with breakthroughs in artificial intelligence, drug discovery, and financial modelling However, it also poses a dire threat to global cybersecurity. Quantum cyberattacks, driven by the ability to break current encryption standards, can compromise critical infrastructure, financial systems, and sensitive data across industries. Once quantum computers reach their full potential, cryptographic keys, certificates, and sensitive information will be exposed to rapid decryption
This threat is not distant. Even before quantum computers become capable of breaking encryption, malicious actors are already engaging in "Harvest Now, Decrypt Later" (HNDL) attacks, where encrypted data is stolen now and stored for future decryption when quantum systems mature This creates an urgent need for cybersecurity professionals to adopt quantum-resistant cryptographic strategies

Post-Quantum Cryptography (PQC), also known as Quantum-Resistant Cryptography (QRC), is the field focused on developing cryptographic algorithms that can withstand quantum attacks These algorithms are specifically designed to remain secure against the computational power of quantum computers, providing a robust defence against future decryption efforts
The quantum threat has prompted global action The National Institute of Standards and Technology (NIST) is expected to finalize its standards for PQC algorithms between March and June 2024, setting the stage for widespread adoption Early adopters, such as Cloudflare and Google Chrome, have already integrated PQC algorithms into their systems, signalling the beginning of the transition toward quantum-safe encryption.
Leaders in cybersecurity must embrace a forward-thinking approach to quantum preparedness The first step is adopting a crypto-agile strategy, which involves building systems that can easily switch between cryptographic algorithms as new threats emerge This approach ensures that as quantum-resistant algorithms are standardised, organisations can seamlessly transition to stronger encryption protocols without disrupting their operations.
Conducting comprehensive risk assessments is also critical. Organisations must evaluate their current cryptographic infrastructure, identifying vulnerabilities and areas where traditional encryption is at risk By understanding where quantum threats could strike, cybersecurity teams can prioritise the implementation of PQC across critical systems, from public key infrastructure to sensitive data repositories.
Additionally, organisations must focus on upskilling and reskilling their cybersecurity workforce. The rapid evolution of quantum technologies necessitates specialised knowledge in quantum cryptography and quantum threat mitigation. Cybersecurity teams will need continuous training to stay ahead of emerging quantum risks and ensure their systems remain resilient against future attacks.
Adopting PQC is not just a technical necessity but a strategic imperative for organisations across industries As quantum computing matures, industries such as finance, healthcare, and critical infrastructure will be at the highest risk of quantum-driven cyberattacks Implementing PQC protocols and revamping key management practices will be essential to securing AI models, protecting sensitive data, and ensuring business continuity
In the coming years, organisations that embrace quantum readiness will be better positioned to navigate the challenges of the post-quantum era. By investing in quantumresistant technologies, businesses can safeguard their assets, maintain trust with stakeholders, and lead the charge in a world where quantum power redefines cybersecurity.
The quantum era is approaching, bringing with it unprecedented opportunities and formidable risks Cybersecurity leaders must act now to prepare for the quantum threat by adopting Post-Quantum Cryptography. The future of digital security depends on the proactive implementation of quantum-resistant algorithms, the development of crypto-agile systems, and the cultivation of a cybersecurity workforce ready to defend against the challenges of the post-quantum world.
Creating a resilient IT infrastructure has always been an idea way before the turn of events, but now it seems things are more about necessity than intelligence It is clear that as businesses become more and more tech-centred, consequential risks such as cyberattacks or systematic faults maturing could crash all enterprise operations. It’s no longer enough to just react to threats; organisations need to plan ahead, ensuring they can both protect themselves from attacks and recover quickly when something does go wrong.


sophistication daily AI-driven attacks, ransomware, and even the prospect of quantum computing breaking today's encryption now present businesses with a more existential threat than ever before A strong-rooted cyber security background is thus mandatory
Resilience in IT infrastructure means creating systems that don’t just withstand cyber threats but also guarantee business continuity in the event of a disaster It is a delicate balance of computer security and running business as usual, often at odds in practice if not strictly by definition.
Building Strong Foundations in Cybersecurity
It is a simple fact: Cyberattacks have become very common. They are the new normal and they continue to advance in
Organisations can’t afford to wait for an attack to happen. organisations cannot be reactive: they must embark on a proactive approach allowing them to continuously monitor the threat environment and receive intelligence in real time as required. Using sophisticated tools such as artificial intelligence and machine learning, companies can recognise patterns and outliers before they materialise in widescale attacks These technologies can do a better job of predicting and identifying security threats than humans– which means that organisations they help to defend will be able to respond quickly
Today's encryption methods may be compromised by the new generation of quantum computing. The bottom line is that we must prepare for this shift By investing in quantum-resistant encryption now, at least businesses can hedge their bets against the fact that this new technology will arrive on the market (via VentureBeat).
Incidents can still happen, even with the best and most robust cybersecurity measures This is why mixing in security with business continuation and recovery works. A reliable infrastructure not only prevents attacks but ensures the business keeps running with little interruption
Organisations also face the challenge of managing a dynamic regulatory environment Moreover, adhering to guidelines like GDPR, PCI DSS and the Digital Personal Data Protection (DPDP) Act, falls straight into legal requirements; it's what will keep us in good books with our customers and more importantly as a credible industry partner
Governance is vital here. Adhering to regulation is not just about staying legal but building compliance into the operating model of an organisation and being prepared for when new rules are implemented That includes monitoring risks, conducting audits and remaining informed on the best practices in data privacy.
Security also needs to be embedded in the development process a concept known as DevSecOps. By including security at every stage of development, from initial design to deployment, companies can ensure that vulnerabilities are addressed before they become a problem This proactive approach
helps prevent breaches, reduces risk, and fosters a culture where security is everyone’s responsibility.
No organisation operates in a vacuum or as silos, especially when it comes to cybersecurity. With modern digital ecosystems where everything is interconnected, a security breach in one organisation affects all others who are connected within that frame Which is why it requires strong collaboration.
Collaborating allows businesses to create threat intelligence, industry-wide baselines and response frameworks for large-scale attacks. It is not only a matter of protecting individual institutions but that should protect all the industry as such.
The key lies in making cross-industry partnerships and working together with regulators This partnership extends beyond national borders. Cyber threats are international so the response to them should be likewise Organisations that share knowledge across nations can fortify their protections and bolster international financial resilience in the process.



Creating a robust IT infrastructure is not only about the latest technology, but it also demands highly skilled staff that know how to use this innovative tech Unfortunately, the shortage of cybersecurity talent is a challenge that many organisations face To bridge this gap, businesses need to invest in training their current staff and finding new ways to attract top talent
But it’s not all about human resources. New technologies like AI can partially bridge this gap by taking over manual work and allowing the human workforce to focus on more complex problems Businesses that can blend the necessary capabilities of a talented workforce with technology will have what it takes to manage whatever challenges they face
In a world that is constantly evolving as new technologies are born, organisations should be more focused than ever on creating systems and networks defaulting to an up-todate resilient IT infrastructure. Security has evolved from basic cybersecurity into a comprehensive strategy that combines security with business continuity, governance and collaboration
By focusing on the future, investing in both technology and talent and fostering a culture of resilience, businesses can protect themselves not just from today’s threats but from whatever challenges tomorrow may bring. The time to act is now because resilience isn’t just about survival it’s about leading the way forward


CISO, Ujjivan Small Finance Bank Limited
Mr Ratan Jyoti, Chief Information Security Officer (CISO) at Ujjivan Small Finance Bank, leverages over two decades of expertise in cybersecurity, cloud security, and DevSecOps At Ujjivan, he leads the security strategy and operational direction for 20,000+ employees across four regions, focusing on incident response, disaster recovery, and digital security
His distinguished career includes significant roles at Vijaya Bank, where he developed the bank's information security framework, and earlier positions at Corporation Bank and Oriental Bank of Commerce He also pioneered India’s first Data Warehouse at the Indian Agricultural Statistics Research Institute.
Mr Jyoti’s contributions to the field have been recognized with numerous awards, including the Top 50 Global Thought Leaders

and Influencers on Cloud Computing (January 2020), 100 B2B Thought Leaders and Influencers to Follow in 2020, CSO 100 Award 2019, Champion CISO 2019, Infosec Maestro 2018, CISO Platform 2018, Infosec Maestros Award 2017, DynamicCISOMagnificent Seven Award 2017, and Infosec Maestros Award 2016.
His influential publications include "Will Blockchain Replace Banks?" (CPO Magazine), "Will the Self-Securing Cloud Replace Security Professionals?" (CPO Magazine), "Are Humans Necessary to Cyber Threat Intelligence?" (CSO Forum), and "Data Security and Privacy Concerns for the Indian Banking Industry" (CIO Review), among others. His certifications, including CISSP, CISA, and CDPSE, further underscore his deep commitment to advancing cybersecurity practices Mr Ratan Jyoti’s innovative approach continues to drive resilience and security in an evolving digital landscape.


In today's digital age, where organizations heavily rely on technology to drive their business operations, the importance of application security cannot be overstated As data becomes the lifeblood of any organization, protecting it from potential threats is crucial especially for insurance
visibility is critical because it allows the CISO to understand the entire landscape of applications, systems, and data repositories that need protection In an insurance company, where multiple applications are often interconnected, and data flows between various systems, knowing exactly what assets are present and where they are located becomes essential.
One of the foundational aspects of application security is having clear visibility of all the assets within an organization. This
Without proper visibility, it is impossible to implement effective security measures For instance, if an outdated or unsupported application is not identified, it could become a weak link in the organization’s security chain By maintaining a real-time inventory of all assets, insurance companies can ensure that every application is accounted for and that appropriate security measures are in place.







DeputyVicePresident,TATAAIGGeneralInsuranceCompany
Dhiraj Ranka, an industry veteran and Chief Information Security Officer (CISO) at TATA AIG General Insurance Limited, brings extensive expertise in cybersecurity and risk management He spearheads the implementation of comprehensive security frameworks, ensuring all software and solutions meet rigorous security standards through vulnerability assessments, penetration testing, and incident response planning
Automation plays a pivotal role in enhancing application security, especially in large organizations where manual monitoring and management of security processes can be overwhelming For a CISO in an insurance company, automating security tasks such as vulnerability scanning, patch management, and incident response can significantly reduce the risk of human error and ensure that security protocols are consistently applied across all applications Automation also enables the continuous monitoring of applications, ensuring that any vulnerabilities or anomalies are detected and addressed in real-time This is particularly important in the context of an insurance company, where the exposure to cyber threats is constant, and the consequences of a data breach can be severe.
To effectively manage the risks associated with application security, insurance companies should adopt a multi-layered approach. Here are some strategies that can help:
Conducting regular audits of all applications to identify potential vulnerabilities is essential These audits should not only focus on identifying known risks but also on uncovering new threats that may have emerged due to changes in the application or its environment
Patch Management:
Ensuring that all applications are up-to-date with the latest security patches is crucial. Automated patch management systems can help streamline this process, ensuring that no application is left vulnerable due to outdated software.
Encrypting sensitive data, both at rest and in transit, adds an additional layer of protection. This ensures that even if data is intercepted, it remains unreadable to unauthorized users
Employee
Human error is often the weakest link in the security chain. Regular training sessions for employees on best practices for application security can go a long way in mitigating risks
Incident Response
Having a well-defined incident response plan in place ensures that the organization can quickly and effectively respond to any security breach This plan should include steps for containment, eradication, and recovery.
For a CISO in the insurance sector, the role of application security in safeguarding organizational data is more critical than ever. With the increasing complexity of IT environments and the ever-present threat of cyberattacks, it is essential to have robust strategies in place that focus on visibility of assets and the automation of security processes. By adopting a proactive approach to risk management, insurance companies can protect their most valuable asset data and ensure that they remain resilient in the face of evolving threats




With the emergence of a knowledge-based economy, data has become the key resource for many innovations and development. When organisations extend their operations internationally, the protection of information becomes not only crucial but comes with its set of challenges.
Information security is becoming increasingly complex due to rapid technological change and the growing sophistication of cyber threats Organizations need to navigate a constantly evolving landscape, balancing protection, compliance, and the integration of new technologies Here are the key trends, challenges, and opportunities in the world of modern information security.
The unprecedented proliferation of data in various sectors is transforming the global economy, with the data sphere expected to hit 175ZB in 2025. This surge, in layman's terms, defines the transformation being witnessed in a digitally-driven world \by the Fourth Industrial Revolution However, with this massive influx comes an equally
significant responsibility: to find approaches to data protection and keep data safe from threats when it is located in different countries and jurisdictions Leadership, in this area, is not only about responding to specific situations but also about identifying several risks and devising strategies that will guarantee security and privacy at the same time.
Information is driving everything from corporate plans to customer interactions, and the risks that come with it have never been more exposed This is a resource that needs to be defended at all costs since its loss can compromise a company’s operations and reputation. It necessitates a proper framework for cybersecurity and risk management.

Cloud Security & Zero Trust Architecture:
As businesses migrate to the cloud, securing these environments is a top priority Organizations are adopting Zero Trust Architecture, where continuous verification of all access points ensures that no one is trusted by default whether they are inside or outside the network
AI and Automation:
The use of AI and machine learning is enhancing security efforts, enabling more effective threat detection, incident response, and predictive analysis of vulnerabilities. Automation is also helping to manage the overwhelming volume of cyber alerts and attacks.
Evolving Threats:
The sophistication of ransomware, malware, and supply chain attacks is on the rise, forcing organizations to improve their defenses and be prepared for increasingly complex cyberattacks.
Regulatory Compliance:
Regulations like GDPR, CCPA, and other global privacy laws demand strict data protection measures Organizations must keep up with these evolving standards to avoid penalties and protect customer trust.
Sophisticated Threats & Insider Risks: Cybercriminals continue to evolve their tactics, leveraging techniques like social engineering, ransomware, and advanced persistent threats (APTs). Simultaneously, insider threats whether from malicious employees or inadvertent mistakes add another dimension of risk.
Skilled Labour Shortage:
There is a global shortage of cybersecurity professionals, creating gaps in implementing and managing effective security measures This lack of talent is a significant roadblock to maintaining strong defenses.
Balancing Security with Usability:
Implementing robust security often hampers user experience and business operations Organizations face the challenge of striking a balance between usability and stringent security controls
Third-Party & Supply Chain Risks:
Many businesses rely on third-party vendors, which can introduce vulnerabilities Ensuring the security of external partners and maintaining supply chain security has become critical but complex



AI-driven tools provide an opportunity to detect threats in real-time, automate responses, and enhance overall security monitoring. Best practices include integrating AI into your security operations center (SOC) for anomaly detection and leveraging machine learning models to predict and prevent potential attacks.
The Zero Trust security model offers a proactive approach to managing risk by ensuring that all users, whether inside or outside the network, are continuously verified. Best practices involve implementing multifactor authentication (MFA), microsegmentation, and ensuring least-privilege access to minimize attack surfaces. Collaborative threat intelligence allows organizations to share data on emerging threats, enhancing collective defense. A best practice here is to participate in industryspecific threat-sharing networks and maintain real-time threat feeds.
Providers (MSSPs) is an efficient way for companies to scale their security efforts without needing extensive in-house teams Best practices include regularly assessing MSSPs' security standards, ensuring alignment with your organizational risk tolerance, and maintaining clear communication regarding responsibilities and incident response protocols
Preparing for the future, quantum-resistant encryption provides an opportunity to safeguard against the upcoming risks of quantum computing Best practices include
beginning the transition to quantum-safe algorithms and assessing current encryption methods to identify areas where upgrading will be required. Early adoption and continuous research are key to staying ahead in this area
The complexity of modern information security presents a mix of challenges and opportunities. With emerging technologies like AI, the adoption of Zero Trust models, and innovative encryption techniques, organizations can strengthen their defenses while staying ahead of increasingly sophisticated threats. However, balancing regulatory compliance, operational efficiency, and effective security strategies remains critical to thriving in this evolving landscape.


Mr Santosh Chachar currently heads the information security program at Conviva, a global leader in streaming intelligence and analytics With over two decades of rich experience in the security domain, Mr Chachar has established himself as a pragmatic leader adept at building and managing comprehensive Information Security functions across diverse product and service organisations
Throughout his career, he has worked with renowned companies such as Jifflenow, Helpshift, GS Lab, and Atos, where he spearheaded security initiatives ranging from GDPR compliance to SOC 2 attestation. At Conviva, he oversees critical aspects of cloud, application, network, and endpoint security, as well as

Sr.SecurityProgramManager,Conviva
privacy, DevSecOps, and vendor risk management His expertise extends to leading organisation-wide efforts to meet global security standards such as ISO 27001, SOC 2, GDPR, CCPA, and HIPAA.
A certified CISSP, CEH, CCIO, and RHCE professional, Mr Chachar has successfully implemented Secure SDLC programs and defended against active cyberattacks. He is also passionate about driving business growth through innovative security solutions and awareness programs. Additionally, he serves as Director of the ISC2 Bangalore Chapter, guiding cybersecurity professionals in the region. Mr Chachar’s technical acumen, leadership, and commitment to security make him an invaluable asset to the industry.
Cybersecurity leaders grapple with the ongoing challenge of adapting to a rapidly evolving threat landscape while maintaining the robustness and effectiveness of their defence strategies As external factors such as economic shifts and geopolitical tensions influence threat actors, and as technological advancements continually reshape the tools and skills available, the complexity of a leader's role intensifies. To navigate this ever-changing environment, it is essential for leaders to periodically assess the maturity of their cybersecurity strategy. This comprehensive evaluation should cover tools, processes, and teams, establishing a framework for strategic progress and resilience.
Assessing the maturity of cybersecurity tools can be effectively guided by maturity models like the hype cycle. This model illustrates the progression of tools from the initial stages of innovation through peaks of inflated expectations, troughs of disillusionment, and slopes of enlightenment, eventually reaching a plateau of productivity. Leaders should position their tools within this internal cycle to gauge their current effectiveness and identify areas for improvement.

Well-established tools that are integral to the security stack offer reliability and consistent performance. However, newer acquisitions might still be aligned with the organisation’s specific use cases and may not yet deliver the anticipated results. By understanding where each tool stands on the maturity curve, leaders can make informed decisions regarding further investment or refinement.
Processes: FromPrimitivetoPowerful
Processes form the foundation of any effective cybersecurity strategy, dictating the use of tools and the management of threats. Regular evaluations of these processes are crucial to ensuring they are optimised for efficiency and effectiveness Leaders must review processes related to threat intelligence collection, prioritisation, and response to confirm their comprehensiveness and adaptability
Streamlining and automating processes can significantly enhance operational efficiency Leaders need to assess whether existing processes are capable of evolving and improving over time An iterative, continuous improvement approach is essential for aligning with the evolving threat landscape and optimising resource utilisation
Teams: EvolvingfromTacticaltoStrategic
The ultimate objective of refining tools and processes is to empower security teams to execute a more effective and responsive security strategy. Team maturity is often reflected in the metrics used to evaluate performance While less mature teams may be assessed based on activity metrics, such as the number of tickets handled, more advanced teams focus on metrics related to employee satisfaction and retention
As organisations enhance their cybersecurity maturity, their teams should also progress by gaining experience, additional training, and, when possible, increased headcount. Leaders must ensure that teams are equipped to manage tools and processes effectively and are engaged in continuous learning and development Gathering feedback from team members regarding their experiences with tools and processes can provide valuable insights for further improvement


Conducting a thorough cybersecurity maturity review is a crucial step for leaders aiming to strengthen their security posture. By evaluating the maturity of tools, processes, and teams, leaders can establish benchmarks for progress and develop a proactive improvement strategy This approach enables organisations to effectively absorb external impacts and navigate the complex cybersecurity landscape with agility and resilience.

The significance of cybersecurity in operational technology (OT) cannot be overstated, particularly in the manufacturing sector, where the repercussions of cyberattacks can be catastrophic As industries increasingly digitize their processes, the convergence of information technology (IT) and operational technology (OT) has become essential This integration not only enhances efficiency but also raises cybersecurity challenges that organizations must address to safeguard their assets and operations.
The landscape of operational technology (OT)
Networks. This report reveals a concerning trend: one in four industrial enterprises experienced temporary operational shutdowns due to cyberattacks within the past year. This statistic highlights the gravity of the issue, which spans across various countries and sectors, underscoring the global nature of the threat
Cyberattacks on OT systems have escalated significantly, with the geopolitical climate exacerbating these risks As organizations rely more heavily on interconnected technologies, cybercriminals have capitalized on vulnerabilities within outdated systems and third-party connections The complexities surrounding OT security solutions further complicate the situation

The landscape of cyber threats targeting operational technology (OT) environments has evolved dramatically, particularly over the past decade Cybercriminals are increasingly leveraging advanced techniques to exploit vulnerabilities within OT systems. Notably, incidents such as the Colonial Pipeline ransomware attack in May 2021 serve as stark reminders of the potential consequences of these threats. The attack disrupted fuel supplies across the eastern United States, showcasing how cyber incidents can lead to significant logistical challenges and economic repercussions
Unlike traditional IT threats, which primarily compromise data integrity and confidentiality, cyberattacks on OT have the potential to cause direct physical damage. For instance, compromised control systems can lead to failures in machinery, resulting in hazardous situations such as explosions or chemical spills. In a report from cybersecurity firm Dragos, it was highlighted that in 2022, 35% of reported OT cyber incidents led to physical harm, a stark contrast to the more data-centric focus of IT threats Cybercriminals often exploit vulnerabilities in legacy systems, such as outdated Windows servers or unpatched industrial control systems, to gain unauthorized access and disrupt operations. The implications of these attacks are severe, as they can halt production, jeopardize worker safety, and inflict substantial financ losses.
protocols. These systems are inherently vulnerable due to outdated software and hardware that lack the necessary security measures to defend against modern cyber threats. For example, legacy control systems may still operate on platforms like Windows Server 2008, making them prime targets for attackers who can exploit known vulnerabilities.


Securing operational technology (OT) environments is fraught with challenges th organizations must navigate to protect the critical infrastructures One of the most significant hurdles comes from legacy systems, which often run outdated

To effectively enhance cybersecurity measures within operational technology (OT) environments, organizations must adopt a collaborative approach that integrates strategies across various industrial sectors. This approach revolves around five key strategies which when implemented effectively results in a secure and safe OT environment
The segmentation of operational technology (OT) networks from other systems is a fundamental strategy for enhancing cybersecurity and safeguarding critical assets By isolating OT environments using systems like Data Diode, organizations can significantly reduce the potential attack surface, limiting the pathways that cybercriminals can exploit to gain unauthorized access. This is particularly important in the context of modern manufacturing, where interconnected systems can inadvertently create misconfigurations that adversaries can leverage Organizations should consider adopting a multi-layered security framework that utilizes firewalls, intrusion detection systems, and strong access controls to protect OT assets. Firewalls should be strategically deployed at the network perimeter and between OT and IT environments to monitor and filter traffic based on predefined security policies.
Understanding the assets within operational technology (OT) environments is crucial for effective cybersecurity management Each asset, ranging from control systems to sensors, actuators, RTUs, FRTUs, numerical relays etc. possesses unique vulnerabilities that can be exploited by cybercriminals if not properly identified and monitored. An organization must not only catalog its assets but also assess their specific vulnerabilities to develop an effective threat detection and mitigation strategy. One of the primary tools for managing cybersecurity within OT systems is comprehensive asset management software. These platforms provide visibility into the assets deployed within a facility, including their configurations and current security posture. By integrating asset management with threat detection systems, organizations can create a robust framework for identifying and responding to potential threats. This integration allows for real-time monitoring of asset vulnerabilities, enabling quicker responses to emerging threats Threat detection mechanisms can include Intrusion Detection Systems (IDS) tailored for OT environments These systems monitor network traffic and system behavior to identify anomalies that may indicate a cyber threat
Enhancing governance and teamwork between operational technology (OT) and information technology (IT) departments is vital for strengthening cybersecurity posture within organizations. The convergence of these two domains presents unique challenges, particularly in defining roles and responsibilities. A lack of clarity can lead to gaps in security measures and hinder effective communication during cyber incidents. Therefore, organizations must
prioritize strategies that foster collaboration and alignment between IT and OT teams.
In the realm of operational technology (OT) cybersecurity, developing internal expertise is crucial to effectively mitigate risks and respond to evolving threats. Organizations must prioritize training initiatives that equip their workforce with the necessary skills to manage and secure OT environments This involves not only foundational cybersecurity training but also specialized programs tailored to the unique challenges of OT systems By fostering a culture of continuous learning, companies can ensure that their personnel remain informed about the latest trends and best practices in cybersecurity.



Krishnendu De is an accomplished cybersecurity leader with over 24 years of experience in developing and securing business-critical applications As the Head of Information Security at CESC Limited, he oversees IT and OT cybersecurity for power generation and distribution. Previously, Krishnendu served as Global Senior Director of Enterprise Security at BCG, leading cloud security, application security, and red teaming He holds certifications including CISSP, CISM, AWS, GCP, and Azure Administrator.
With expertise across diverse industries and regions, Krishnendu excels in cybersecurity strategy, risk management, and leadership, mentoring teams to strengthen organizational security postures.
The digital transformation in India is accelerating, reshaping industries and driving new growth opportunities As businesses move towards increased digitisation, the role of Chief Information Security Officers (CISOs) becomes critical in balancing innovation with the need for robust cybersecurity and regulatory compliance. For Indian enterprises, especially in sectors like finance, healthcare, and manufacturing, achieving this balance is no longer optional but essential to survival in a rapidly evolving digital landscape
India’s digital economy is projected to grow to $1 trillion by 2025, driven by technological advancements such as artificial intelligence (AI), the Internet of Things (IoT), and cloud computing This shift has led to unprecedented efficiencies and consumer conveniences but has also expanded the attack surface for cybercriminals A 2023 report indicated 79 million cyberattacks in India alone, highlighting the urgent need for strengthened cybersecurity measures across industries
The adoption of digital technologies introduces unique risks AI and machine learning are revolutionising operations, yet they also pose challenges related to data privacy, model bias, and explainability Similarly, the proliferation of IoT devices has
increased the number of network endpoints vulnerable to attack For CISOs in India, navigating these risks while enabling technological innovation is a complex but vital task

CISOs in India face the challenge of ensuring that digital innovation does not come at the expense of security or compliance The Personal Data Protection Bill (PDPB) and the Reserve Bank of India’s cybersecurity guidelines impose strict requirements on data protection and privacy, with non-compliance resulting in significant penalties and reputational damage. However, focusing solely on regulatory adherence can stifle innovation
To manage this dichotomy, CISOs must adopt a compliance-by-design approach, ensuring security and regulatory requirements are integrated into all digital initiatives from the ground up. This strategy not only addresses compliance needs but also ensures that innovation continues to drive business competitiveness.
In today’s threat landscape, CISOs must adopt a proactive approach to risk management, focusing not only on reacting to incidents but preventing them before they occur. According to IBM’s 2022 report, the average cost of a data breach in India has reached ₹179 million in 2023, underscoring the need for a forward-thinking risk management strategy.
One of the key pillars of proactive risk management is cultivating a culture of security awareness across the organisation Human error remains one of the primary causes of data breaches, and regular employee training on cybersecurity best practices can significantly reduce this risk. A report claims that 88% of data breaches are attributable to human error, emphasising the need for ongoing education.
CISOs must engage all levels of the organisation in cybersecurity efforts, ensuring that each employee understands their role in safeguarding sensitive data. By conducting regular phishing simulations and awareness campaigns, organisations can minimise risks associated with social engineering attacks
For businesses to succeed in the digital era, innovation must be coupled with strict compliance protocols. With regulatory frameworks such as the PDPB expected to come into force soon, ensuring that data privacy and protection standards are met is paramount The compliance-by-design approach allows organisations to integrate security measures into every aspect of their digital strategy
This integration is especially important in industries like financial services, where digital transactions have skyrocketed CISOs must ensure that these services are compliant with data security standards, such as RBI’s cybersecurity norms while continuing to innovate in areas like mobile banking and digital wallets.

AI plays a dual role in today’s cybersecurity landscape it presents risks and solutions. To mitigate risks such as AI model inversion or data poisoning, CISOs must deploy AI explainability frameworks and ensure transparency in how AI systems are designed and operated On the flip side, AI-driven security tools can significantly enhance an organisation’s ability to detect and respond to threats in real time.
A Capgemini report revealed that 69% of Indian organisations using AI for cybersecurity have reported improved threat detection Automation tools like security orchestration, automation, and response (SOAR) can further streamline incident security teams to fo rather than routine
The adoption of cloud and IoT technologies has created significant efficiencies for Indian businesses but has also introduced new security challenges The International Data Corporation (IDC) forecasts that India's public cloud services market will expand significantly, reaching $13 5 billion by 2026, up from $4 6 billion in 2021 Managing these new technologies requires a cloud-first security approach, focusing on encryption, access control, and continuous monitoring
In addition to cloud security, organisations must secure their IoT networks This requires CISOs to implement robust endpoint protection strategies, ensuring that connected devices in sectors like healthcare and manufacturing do not become weak points in the network.


Building a resilient cybersecurity architecture is essential for organisations to recover quickly from cyberattacks and minimise downtime A multi-layered security architecture that includes disaster recovery and business continuity plans ensures that organisations can continue operations even in the face of a major security breach
By implementing network segmentation, realtime monitoring, and backup solutions, CISOs can create an environment that is both secure and adaptable to evolving threats.

As India’s digital transformation accelerates, CISOs are tasked with balancing innovation with stringent security and compliance requirements By fostering a culture of security awareness, leveraging AI for risk mitigation, and building resilient architectures, Indian CISOs can lead their organisations into a future where innovation and security coexist. This proactive approach not only ensures compliance but also positions organisations to thrive in the increasingly competitive digital landscape.


hakur is an acclaimed d business leader currently CISO and DGM IT at Astral over 19 years of distinguished ience, Mr Thakur has mself as a top CIO and CISO, his strategic vision and proach to digital transformation urity.
hakur career trajectory includes uch as Group CISO and Head IT gy Exchange (IEX/IGX), where he nhanced the organisation's posture and drove impactful es. Prior to IEX, he excelled as oud CoE, IT Infrastructure,and x Capital, and led Cloud CoE, Datacenter Operations at DHFL Insurance His tenure at nd other notable companies Systems and 3i Infotech further s expertise in IT infrastructure gement ntial speaker and cyber t, Mr Thakur is renowned for his harness emerging technologies, AI and cloud computing, to perational excellence and ory compliance His accolades de being ranked among the Top CISOs by IDC and CISO Platform, receiving the Most Promising Innovative CIO Award in 2023 m CIOAXIS.

Cloud technology plays an increasingly pivotal role in today’s digital landscape. As businesses migrate their applications to the cloud, ensuring robust application security is more critical than ever. This article explores key best practices for securing cloud-based applications, focusing on secure onboarding and effective monitoring strategies to safeguard your data and systems.
Implement a Comprehensive Security Policy
Before migrating critical applications to the cloud, establish a detailed security policy outlining security objectives, standards, and procedures This policy should cover secure application development, data protection, identity and access management (IAM), and compliance with regulatory requirements A well-defined policy provides a framework for secure onboarding and ensures consistency across the organization

Authentication and Authorization


Authentication is the first line of defense for cloud applications. Weak or poorly implemented authentication often leads to security breaches Use robust authentication mechanisms like multi-factor authentication (MFA) to protect user accounts. Device-


based authentication can further enhance security Additionally, follow the principle of least privilege by granting users only the minimum permissions necessary.
RBAC restricts access to system resources based on assigned roles. It is widely used in cloud environments for its flexibility, scalability, and ease of management, providing finegrained control over access to resources.
To protect applications from vulnerabilities, adopt secure coding practices. Use Static Application Security Testing (SAST) to analyze code for vulnerabilities, Dynamic Application Security Testing (DAST) to test running applications, and penetration testing to simulate attacks and identify weaknesses
Leverage automation tools such as Infrastructure as Code (IaC) and CI/CD pipelines to reduce human error and ensure consistency in deployment Incorporate automated security checks to detect vulnerabilities before applications are deployed to production
Encrypt sensitive data both in transit and at rest using strong encryption algorithms. Manage encryption keys securely and ensure that your cloud provider supports encryption.


Centralize logging to gain visibility into your cloud applications’ security posture. Aggregate logs from various sources into a single platform, and use monitoring tools to detect unusual activities or potential security incidents.
Use real-time threat detection systems, such as Security Information and Event Management (SIEM) tools, to identify and respond to security threats as they occur. Set up alerts to notify the security team of potential threats

Monitor both the performance and security of cloud applications. Use Application Performance Management (APM) tools and security monitoring solutions to ensure optimal functionality and detect vulnerabilities
Regularly perform vulnerability scans and penetration tests to identify security weaknesses. These assessments should be scheduled periodically or after significant changes to applications or infrastructure
Use machine learning and AI-based threat intelligence solutions to analyze data and identify emerging threats Integrate threat intelligence feeds into your monitoring systems for quicker threat detection and response
Engage third-party auditors or internal teams to conduct regular security audits These audits ensure compliance with security policies and identify areas for improvement
Develop an incident response and recovery plan to address security breaches effectively Regularly update and test the plan to ensure its effectiveness in mitigating incidents.
Securing cloud applications is crucial for protecting sensitive data and preventing unauthorized access Implementing robust security policies, secure coding practices, and automated deployment processes provides a strong foundation for cloud security. Continuous monitoring and regular security assessments are essential for detecting and responding to potential threats, ensuring a resilient and secure cloud environment.



Ninad Varadkar is an accomplished cybersecurity leader with over 20 years of professional experience and industry-recognized certifications
Possesses strong expertise in designing cyber-resilient systems and driving strategic cybersecurity roadmaps while acting as a trusted business advisor in managing cyber risks.







Cyber Physical systems, also referred as Operational Technology (OT) and Industrial Control Systems (ICS) forms the backbone of a nation's critical infrastructure and business unit Operations These systems are crucial for the smooth operation of power grids, water treatment facilities, transportation networks, and production lines However, the integration of digital technologies into OT/ICS has introduced numerous new vulnerabilities, making them prime targets for cyberattacks. As these systems become more interconnected and automated, they face increased risks from malicious actors seeking to exploit vulnerabilities This heightened exposure necessitates robust security measures and constant vigilance to safeguard essential services and infrastructure Failure to address these vulnerabilities could lead to severe
disruptions and significant consequences for public safety and economic stability This near-doubling of vulnerabilities (close to 57%) highlights a real growing need for robust security to protect these critical systems
In recent years, new revelations have exposed the real danger that malware poses to OT/ICS systems One concrete example is TRISIS, also known as Triton, and BlackEnergy, which are pieces of malware specifically designed to disrupt industrial processes and override safety mechanisms. These sophisticated threats highlight the evolving nature of cyberattacks and the need for advanced security measures As attackers develop increasingly complex tactics to target critical infrastructure, it becomes imperative for public sector units to adopt a proactive and strategic approach to cybersecurity.
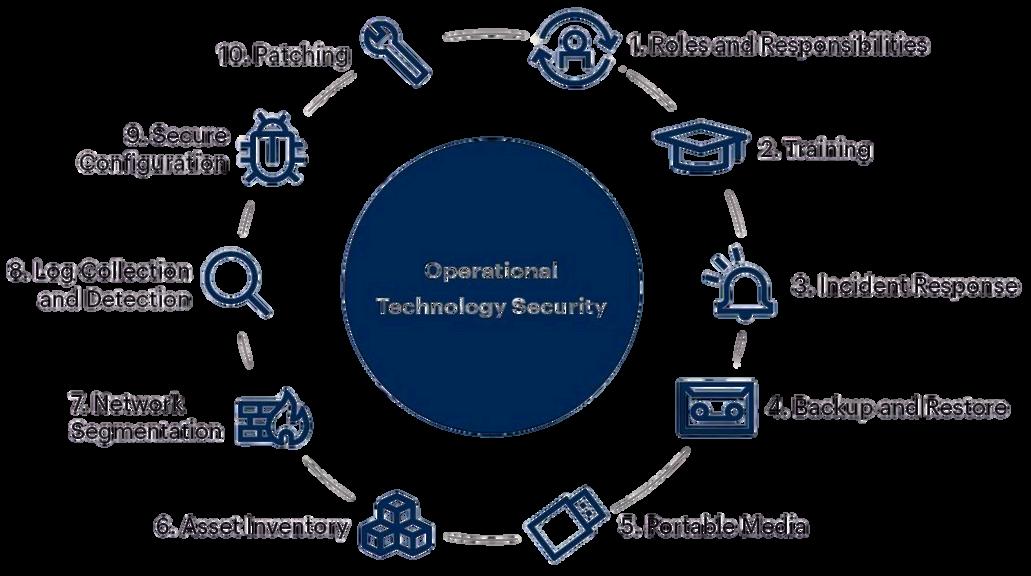
The strategy to secure OT systems revolves largely around following vital factors as depicted:
Roles and Responsibilities:
Establish clear accountability and designate individuals responsible for overseeing OT security. Defining roles ensures coordinated efforts in maintaining and enforcing security protocols among multiple stakeholders when operating in CPS domain.
Comprehensive Security Training and Incident Response:
Regular training is crucial to ensure that personnel are well-versed in security policies, risks, and best practices, particularly in OT environments. This helps reduce human error and enhances the organization's ability to respond to incidents In OT (cyber-physical systems), the establishment of on-the-ground response teams is critical for managing day-to-day operations and providing central monitoring teams with accurate information during incident responses Unlike IT SOC and IR operations, OT SOC functions under a different model, where factors such as routine maintenance, operational disruptions, equipment failure, and safety considerations play a significant role. This necessitates a highly customized approach for OT SOC compared to traditional IT SOC operations.
Backup and Restore:
Maintain secure and regular backups of critical OT systems. Having a robust recovery plan ensures minimal downtime and data loss in the event of a security incident.This is a critical requirement, as it's widely understood that our systems will likely face ransomware attacks at some point. What truly matters is how wellprepared we are to respond when that
happens. The key to this preparedness lies in our backup strategy, which must account for ransomware scenarios
In the realm of OT security, asset visibility is a critical component for effective risk management and threat mitigation. Achieving comprehensive visibility into all assets within an industrial control system is essential for identifying vulnerabilities, monitoring system health, and ensuring robust protection. This involves maintaining an up-to-date inventory of all devices, including hardware and software components, as well as understanding their configurations and interconnections Effective asset visibility enables organizations to detect unauthorised changes, assess the security posture of each asset, and respond swiftly to any anomalies or potential threats.
Network segmentation is one of the most effective ways to protect OT/ICS systems from unauthorised access or lateral movement by threat actors Public sector organisations can achieve major attack surface reductions simply by isolating zones of OT systems from corporate networks This level of strategic separation not only limits the number of attack vectors a malicious actor can use but also isolates breaches from spreading across other areas within your network.
Control and monitor the use of portable media (e.g., USB drives) to prevent the introduction of malware and unauthorised access. Implement strict policies for usage and scanning of such devices.
Set up comprehensive logging and monitoring systems to detect anomalies or suspicious activities Collecting and analysing logs helps
in identifying and responding to potential security incidents in real time.
Robust Access Control and Authentication
It is important to secure your critical systems using access controls and authenticate mechanisms Access control: PSUs should install systems to prevent people who are not authorised from entering into the company ´ s OT/ICS environments. Examples of these safeguards include enforcing multi-factor authentication and regularly reviewing access privileges. These protections are necessary to reduce the risk of insider threats, however, only legitimate users should be able to interact with sensitive systems.
Ensure that all OT systems and devices are securely configured based on best practices. Regularly audit configurations to prevent unauthorised changes that could introduce vulnerabilities.
The practice of promptly applying security patches and firmware updates is critical to maintaining the resilience of OT/ICS systems In particular, we are seeing a rise in vulnerabilities targeting legacy devices. There must be stringent patch management processes in place for public sector units so that systems never miss a critical update and are by and large protected against known threats
An integrated IT and OT team approach is essential for a holistic cyber security strategy. Communication and staying together must be transparent with closer coordination in all public sector units to counter this changing threat landscape When IT/OT security practices are aligned, organisations can improve overall readiness for, and protection from, evolving cyber threats on critical infrastructure
As the digital transformation accelerates across industries, Operational Technology (OT) and Industrial Control Systems (ICS) face new security challenges and opportunities The future of OT/ICS security is shaped by the convergence of these systems with traditional IT infrastructure, increasing the attack surface and the sophistication of cyber threats Here the journey highlights the shift from security by isolation ("Security by Obscurity") to a more Asset centric, integrated, proactive, and layered defence approach necessary for modern OT systems. This progression highlights the importance of evolving security measures to match the increasing complexity and connectivity of OT systems.
Key trends and developments that will define the future of OT/ICS security are Zero Trust Architecture, AI & ML for Threat Detection, Secure Remote Access solutions, Digital Twin & virtual Patching, Edge Computing and Increased focus on Sector specific regulatory/Compliance with Increased focus on Supply Chain & product Cyber security.

The future of OT/ICS security will be defined by the balance between innovation and protection. As industrial systems become more connected and digitalized, organisations will need to adopt advanced security
frameworks that can evolve with emerging threats. From AI-driven threat detection to Zero Trust models and digital twin technologies, the next generation of OT/ICS security will prioritise resilience, flexibility, and seamless integration between IT and OT systems By staying ahead of these trends, organisations can ensure the safety and reliability of their critical infrastructure in an increasingly interconnected world.
Fully"Air-Gapped" OTSystems
OTSystems Partially Connectedto EachOthers
"Retrofitted" CyberPhysical Systems ThroughIT/OT convergence
NewGeneration ICS&OTsystems
Security
Obscurity



Ltcdr Vaibhav Ranjan Rai (Retd ) is a distinguished leader in Cyber and OT/ICS Security, currently serving as the Deputy General Manager for Cyber & OT Security at Adani Group With over 14 years of experience, Mr. Ranjan has demonstrated exceptional expertise across a diverse range of security disciplines, including IEC 62443, NIST frameworks, and Cyber Forensics.



is decade-long service with the Indian Navy as Deputy Director of Cybersecurity further underscores his deep-rooted knowledge in safeguarding critical defence systems
Mr Ranjan's career spans pivotal roles in both government and private sectors, showcasing his ability to spearhead complex security initiatives Prior to his tenure at Adani Group, he served as Chief Manager of Cyber Security at State Bank of India, where he implemented ISO 27001:2013 certification and led risk assessments and security operations H
At Adani Group, Mr Ranjan has been instrumental in transitioning Cyber Security Operations to an in-house model, establishing a comprehensive OT security practice, and leading technology implementations for secure remote access. His efforts have included pioneering 24x7 monitoring setups, conducting rigorous security audits, and implementing centralised patch management, solidifying his role as a key figure in advancing organisational security and resilience
The advent of Zero Trust Architecture (ZTA) represents a pivotal shift in cybersecurity strategies, fundamentally challenging the traditional notions of network security
Introduced in 2009 by Forrester’s John Kindervag, the Zero Trust Model has evolved from a conceptual framework to a cornerstone of modern security practices
The core tenets of this model unwavering verification, least privilege access, and continuous monitoring have been refined over time, adapting to the increasingly complex and dynamic threat landscape.
Zero Trust initially emerged as a revolutionary approach, dismissing the outdated perimeterbased security model in favour of a more granular, context-aware framework. The term itself, coined partly as a critique of prevailing security practices, underscores a fundamental principle: " never trust, always verify." This principle challenges the complacency of trusting internal actors and emphasizes continuous scrutiny of all access requests, regardless of their origin.
Google’s BeyondCorp initiative, launched in 2014, was instrumental in cementing Zero Trust's relevance in an era dominated by cloud
computing and SaaS applications BeyondCorp exemplified a transition to a perimeterless security model, advocating for comprehensive authentication and authorization mechanisms independent of network boundaries. This shift has been crucial as organizations increasingly operate without traditional perimeters, necessitating robust security measures that adapt to this new reality.
The Zero Trust Model, while revolutionary, has faced ongoing challenges and adaptations.
The concept of “microperimeters,” introduced by Kindervag, aimed to address network segmentation and access control within a seemingly boundless digital environment
However, the tension between traditional network models and Zero Trust’s perimeterless approach remains a point of contention
Critics argue that while micro perimeters offer enhanced security, they can inadvertently reintroduce outdated perimeter concepts


Moreover, Zero Trust has grappled with the dual-edged nature of insider threats. The initial focus on malicious insiders exemplified by notable cases such as Edward Snowden has somewhat overshadowed other critical aspects of security While internal threats are significant, the broader spectrum of potential breaches, including third-party impersonation and unintentional employee errors, must be equally addressed to ensure a comprehensive security posture.
As we look towards 2030, the evolution of Zero Trust will be shaped by several critical factors:
The balance between stringent data privacy and leveraging data for innovation will be a central theme. As digital interactions become increasingly integral, negotiating a fair return on investment for data usage while ensuring robust privacy protections will be paramount.ation to stay
The competition for cybersecurity talent is intensifying. Future strategies must focus on nurturing a skilled workforce capable of managing sophisticated security technologies and mitigating emerging threats The rise of AI and automation underscores the need for advanced training and education to stay ahead of adversaries
The challenge of maintaining device security amidst the proliferation of Bring Your Own Device (BYOD) policies will persist Ensuring
that devices are secure before granting access to corporate resources remains a critical aspect of Zero Trust
The intersection of cybersecurity and sustainability will become increasingly prominent As technology advancements drive up energy demands and expand the IoT landscape, integrating climate and energy resilience into digital infrastructure will be essential to safeguard against emerging threats.
The evolution of Zero Trust Architecture is a testament to the adaptive nature of cybersecurity. As we approach 2030, the principles of Zero Trust will continue to evolve, driven by technological advancements, shifting threat landscapes, and the imperative for robust data privacy Embracing these changes and preparing for the future will be critical for leaders aiming to fortify their organizations against the sophisticated challenges of the digital age.


The digital revolution in banking has redefined customer experiences, with online platforms emerging as the primary channels for financial transactions As the industry embraces technology-driven servic role of cybersecurity leadership bec critical to ensuring both innovation a safety Robust cybersecurity is no lo a necessity; it is a strategic advanta strengthens trust, drives resilience, a enables the seamless operation of f institutions Leadership in this doma the future of digital banking, ensurin institutions remain secure in the fac evolving threats
The Current Cybersecurity Landscape in Banking
Cybersecurity in banking has rapidly grown in importance as financial institutions face increasingly sophisticated attacks In 2021, the market for IT security in banking reached $38.72 billion, with projections of $195.5 billion by 2029 This growth reflects both the rising volume of cyberattacks and the complexity of the threats banks face daily.
From phishing attacks to advanced persistent threats (APTs), cybercriminals leverage cutting-edge technology to breach bank networks Fraudsters now target internal systems, compromise supply chains, and exploit insider vulnerabilities. In response, banks have increased security investments, with cybersecurity leadership playing a vital role in protecting organisational assets and consumer trust




Cybersecurity leadership has moved beyond technical oversight into a core business function. Chief Information Security Officer (CISO) and other leaders now guide strategies that align cybersecurity with longterm business objectives. Strong leadership ensures that cybersecurity measures not only protect the organisation but also support its growth and innovation. A strategic approach to security, integrated with business goals, positions banks to navigate regulatory complexities, protect assets, and preserve customer trust.
Leaders must drive a culture where cybersecurity becomes a part of every decision-making process, making it a shared responsibility across all departments This holistic approach transforms cybersecurity into a key enabler for business resilience and customer confidence
Embedding a security-first mindset throughout the organisation is essential for protecting critical assets and sensitive data Leadership must ensure that cybersecurity is woven into the fabric of the institution, from executive decisions to everyday operations. By promoting a culture that emphasises vigilance and awareness, organisations create an environment where all employees are proactive in safeguarding data.
Regular training, employee engagement, and clear communication about the importance of cybersecurity foster a sense of ownership among staff Cybersecurity leaders must also ensure that teams across the organisation understand their role in protecting information, reducing the likelihood of human error and mitigating internal vulnerabilities.
Forward-thinking cybersecurity leaders approach risk management with a proactive, rather than reactive, mindset As technology evolves, so do cyber threats. Leaders must continuously assess their security frameworks, adapting to new risks while leveraging emerging technologies like artificial intelligence (AI) and machine learning (ML) These tools are essential for detecting threats in real time and enhancing overall threat intelligence.
Leaders who harness the power of AI and automation can streamline incident response processes and reduce the burden on their teams By automating repetitive security tasks and analysing vast data sets, AI improves operational efficiency while minimising risks A proactive stance ensures that banks can innovate safely, launching new products and services while maintaining a fortified security posture
Trust is the foundation of any successful banking relationship Customers expect their financial institutions to protect their sensitive data, and banks must meet those expectations by demonstrating a commitment to cybersecurity. Strong leadership in this area helps establish and maintain customer confidence, which is crucial for long-term success in a highly competitive market.
Effective cybersecurity measures such as encryption, multi-factor authentication, and rigorous data protection protocols show customers that their financial information is secure. By consistently communicating security efforts and ensuring transparency during potential breaches, leaders build
stronger relationships with customers, reinforcing loyalty and trust
Regulatory compliance has become a central aspect of cybersecurity in banking. Leaders are tasked with ensuring that their institutions adhere to complex regulations, such as the Digital Personal Data Protection Act, 2023 (DPDPA) and Payment Card Industry Data Security Standard (PCI DSS) The rapidly changing regulatory landscape requires vigilant leadership that keeps the organisation compliant while protecting its assets.
Cybersecurity leaders guide organisations through the intricacies of compliance by implementing scalable security frameworks that can adapt to new regulations They also conduct regular audits, review policies, and collaborate with legal teams to address compliance challenges before they arise. This proactive approach not only avoids costly penalties but also reinforces the institution’s reputation as a responsible, secure financial entity
Fostering Collaboration Across the Ecosystem
Leadership in cybersecurity extends beyond internal systems and policies. Banks today operate in a highly interconnected ecosystem with numerous third-party vendors, cloud services, and external partners Securing this extended network requires collaboration and vigilance Leaders must work closely with third-party providers to ensure that cybersecurity standards are upheld across the supply chain.
Moreover, collaboration with regulatory bodies, government agencies, and industry peers is essential for mitigating systemic risks Sharing information about threats and vulnerabilities strengthens the overall resilience of the financial sector By participating in cross-industry cybersecurity initiatives, leaders can contribute to a more secure financial environment and protect not only their institutions but the broader ecosystem.

Cybersecurity leadership is crucial to shaping the future of digital banking Leaders who prioritise security alongside innovation ensure that banks can thrive in an increasingly complex digital landscape. By embedding cybersecurity into the strategic fabric of the organisation, leaders create institutions that are agile, resilient, and prepared to face both current and emerging threats
. Banks that succeed in securing their digital future will be those that invest in strong cybersecurity leadership These institutions will not only protect their assets and customers but will also lead the industry in setting new standards for secure, innovative, and customerfocused banking services
As digital transformation accelerates, leadership in cybersecurity will continue to play a defining role in shaping the financial sector and driving trust, growth, and long-term success.


Mr Pranav Paranjpe currently serves as the Chief Information Security Officer (CISO) at Unity Small Finance Bank Limited, where he has been leading cybersecurity initiatives since November 2022. With a robust career spanning over 21 years, Mr. Paranjpe has accumulated extensive experience in information security across several prominent institutions.
Prior to his role at Unity Small Finance Bank, Mr Paranjpe was the Deputy Vice President at HDFC Bank. He also held the position of Deputy CISO (and Interim CISO for a year) at Mahindra Finance for close to five years, where he played a critical role in enhancing the company’s security posture His previous roles include serving large MNC Banks like Standard Chartered Bank and Deutsche Bank.
Mr. Paranjpe's career began as a Network
Security Engineer with HCL Infosystems with journeys spanning across varied industries including BFSI, NBFC, Knowledge Process Outsourcing (KPOs) to Insurance.
He holds a Bachelor of Engineering (B.E.) in Electronics Engineering from Shri Ramdeobaba Kamla Nehru Engineering College. Mr. Paranjpe is a CISA Certified Professional, reflecting his deep expertise in information security He has been representing his organisation as a Panellist and Individual Speaker at many Information and Cyber Security Conferences across India. He is a regular attendee at many government organised conferences and he has received many accolades like CISO of the Year 2024 and Cyber Security Leader of the Year 2023, to name a few. Mr. Paranjpe loves to interact with the Young Cyber enthusiasts and keeps guiding them as part of guest lectures at different Management and Engineering Colleges.

Privacy of information has remained an essential consideration as organisations modernise to adapt to the ever-changing technological environment As cyber threats continue to evolve and become more complex, protecting an organisation’s key assets requires a well-coordinated system of protection based on standard protocols. While there is general acceptance of the importance of IS & IT governance CISOs and security leaders must pay attention to the establishment and enhancement of governance frameworks that are flexible and compliant with business goals and legal requirements. Implementing security measures is not just an enforcing process but rather a strategic measure that is crucial for safeguarding business operations and the validity of stakeholder claims.
With increased cybersecurity risks including ransomware, insider threats, and supply chain risks, the implementation of security measures has become crucial Security measures prevent breaches, minimise data leakage, and strengthen the organisation’s defences against possible threats Inability to adhere to such measures can result in business loss, reputational loss, and huge statutory penalties
In addition to external threats, there are internal threats that organisations need to guard against Data breaches arise from misconfigurations, insider negligence, and privilege misuse indicating the need to have proper internal controls/monitoring mechanisms based on security principles.





This means that through regular and constant adherence to the security features, organisations can avoid the requisite point of unlawful access and significantly minimise the risks that are inherent in an organisation’s systems
The establishment of a robust framework for combating cyber threats requires the identification and analysis of the organisation’s specific vulnerabilities. It therefore becomes the responsibility of security leaders to engage in quarterly risk appraisals to determine the risks that are present within the network, applications, and the cloud Once these risks are identified, a robust cybersecurity framework for the organisation can be established, with elaborate security features such as the technology to ensure that security features are integral parts of the organisation.
The security framework should address key areas such as identity and access management (IAM), data encryption, incident response, and continuous monitoring To ensure long-term effectiveness, these protocols must be aligned with industry standards like ISO 27001, NIST, DPDPA, GDPR and regulatory guidelines. This not only demonstrates a commitment to protecting sensitive information but also ensures compliance with regulatory requirements.
Implementing strict access control mechanisms ensures that only authorised personnel have access to sensitive information. Role-based access control (RBAC) and least privilege principles should
guide the assignment of access rights, minimising the risk of unauthorised access or data breaches
Encrypting data both at rest and in transit is one of the most critical security measures for protecting sensitive information Advanced encryption standards (AES) ensure that even if data is intercepted, it remains inaccessible to unauthorised users Encryption protocols must be reviewed regularly and updated to meet the latest standards.
A strong authentication process is a frontline defence against cyberattacks MFA requires users to provide multiple credentials to verify their identity, making it significantly harder for attackers to breach accounts through compromised passwords.
The ability to detect and respond to threats in real-time is critical for minimising damage Security Information and Event Management (SIEM) systems, combined with realtime monitoring, enable security teams to identify suspicious activities and take immediate action.
Organisations should also have a well-defined incident response plan that ensures rapid containment and recovery from security incidents.
Routine security audits are vital for identifying vulnerabilities and ensuring compliance with internal policies and external regulations. Vulnerability assessments and penetration testing simulate potential attack scenarios, enabling organisations to fortify their defences before real threats exploit weak points
While technological defences are essential, human error remains one of the leading causes of security breaches. Employees can unintentionally compromise sensitive information through phishing attacks, poor password hygiene, or negligence. As a result, creating a security-conscious culture is just as important as implementing advanced technologies.
Security awareness training should be a mandatory part of an organisation’s security protocol. Employees should be trained to recognise phishing attempts, understand the importance of secure data handling, and follow best practices in password management. Regular refresher courses ensure that security remains top of mind and that employees are equipped to act as the first line of defence.
Furthermore, organisations must monitor insider activities closely User behaviour analytics (UBA) can detect unusual or suspicious actions, enabling security teams to intervene before insider threats cause damage By proactively addressing the human factor, organisations can prevent


insider breaches and maintain the integrity of sensitive information
In an interconnected digital ecosystem, thirdparty vendors often have access to an organisation’s sensitive data Managing this extended attack surface requires strict thirdparty risk management protocols Security assessments and due diligence should be conducted before onboarding new vendors, ensuring they adhere to the same security standards as the organisation
Third-party contracts should include clauses related to data protection, incident reporting, and compliance with relevant regulations
Organisations should also implement continuous monitoring to detect potential security risks originating from third-party partners and enforce contractual obligations to secure their data environments
Data Loss Prevention (DLP) solutions are essential for identifying, monitoring, and protecting sensitive information across the organisation. By controlling the flow of data within the network, DLP tools prevent unauthorised access and ensure that sensitive information is not transmitted outside of the organisation without appropriate safeguards
In addition to DLP, a comprehensive backup strategy is critical for ensuring business continuity in the event of a breach Regular backups of critical data should be maintained both on-site and off-site, with encrypted storage solutions to protect the integrity of backups
Organisations should also conduct frequent disaster recovery tests to ensure they can quickly restore data and resume operations following an incident
Enforcing security protocols is a critical business imperative. As organisations continue to face an expanding array of cyber threats, the role of security leaders in safeguarding sensitive information has never been more important By implementing strong cybersecurity frameworks, training employees, and rigorously monitoring thirdparty risks, organisations can protect their valuable assets, maintain compliance, and build resilience in the face of future challenges.



Palanikumar Arumugam is the Chief Information Security Officer (CISO) at Hinduja Leyland Finance, where he leads the company’s information and cybersecurity initiatives With over two decades of experience in IT, cybersecurity, and data privacy. Palanikumar has an impressive track record of developing and implementing security strategies to safeguard critical data. Prior to joining Hinduja Leyland Finance, he served as Vice President of Information Security at Equitas Small Finance Bank, where he managed security operations, vulnerability assessments, security solutions and compliance audits.

His extensive career spans leadership roles at Shiksha Financial Services, Veritas Finance, and Equitas Small Finance Bank, where he honed his expertise in IT infrastructure, application development, cybersecurity, and business continuity planning Palanikumar holds multiple certifications, including Certified Information Security Auditor (CISA), Certified Data Privacy Solutions Engineer (CDPSE), and Certified Chief Data Protection Officer (CDPO). A proven leader in both information and cyber security, he is recognised for his deep understanding of security architecture design, incident management, and IT risk management
Palanikumar's strategic vision and leadership have earned him numerous accolades, including the Cyber Icon, Cyber Warrior and CIO Accelerator X Awards, highlighting his commitment to excellence and innovation in the rapidly evolving cybersecurity landscape

The rapid rise of artificial intelligence (AI) is reshaping the cyber landscape, with AIpowered ransomware emerging as a critical threat This new frontier in cyber extortion leverages AI's capabilities to execute more sophisticated, targeted, and scalable attacks, threatening to escalate the already rampant ransomware crisis Organisations must adapt their cybersecurity strategies to mitigate these emerging risks

Ransomware attacks have been one of the most devastating forms of cybercrime, costing businesses billions globally. With AI now in the equation, the scale and sophistication of these attacks are set to rise dramatically AI's ability to automate e targeting, and adapt in ntly lowers the barrier to minals


Attacks: AI can streamline a ransomware attack, from nerabilities to encrypting attackers to launch largens with minimal effort This kes attacks faster, more early impossible for urity systems to counter in
eting: AI enables attackers amounts of data to ost vulnerable targets can exploit AI’s craft highly targeted crease the likelihood of minimising exposure to
ware: AI-powered an learn and evolve during sting its methods to evade ability to adapt on the fly w level of sophistication that ersecurity defences nter.
Ransomware-as-a-Service (RaaS) and AI
The commoditization of cybercrime through Ransomware-as-a-Service (RaaS) platforms is being supercharged by AI. With AI integrated into these platforms, even novice attackers can launch sophisticated ransomware campaigns This democratisation of ransomware attacks will lead to an increase in both frequency and complexity, posing an even greater risk to organisations
While AI is fueling the rise of ransomware, it also offers robust tools for defence. AIpowered solutions can strengthen cybersecurity by providing real-time threat detection, predictive analytics, and automated incident response For example:
Real-Time Threat Detection: AI-driven systems can monitor network traffic and identify anomalies, enabling early detection of ransomware attacks. This rapid identification allows organisations to respond before significant damage occurs.
Automated Incident Response: AI can automate many aspects of incident response, such as isolating compromised systems and neutralising threats, drastically reducing response times and minimising damage
Predictive Analytics: AI's ability to analyse historical data and predict potential vulnerabilities allows organisations to stay ahead of evolving threats, proactively closing security gaps before attackers can exploit them
Despite AI’s potential in defence, there are significant challenges to its adoption. AI models are vulnerable to manipulation, suchas adversarial attacks that exploit flaws in AI algorithms Additionally, the “black box”
nature of AI means that its decision-making processes are often opaque, making it difficult for cybersecurity professionals to fully trust AI-generated insights
Organisations must carefully validate AI outputs and ensure they are combined with human oversight to avoid introducing new vulnerabilities. Cybersecurity teams must also be trained to critically assess AI systems and integrate them into broader security strategies without over-reliance on automation.
As AI continues to evolve, its role in both enabling and defending against ransomware attacks will expand Cybercriminals will likely leverage AI to create more adaptive, efficient ransomware capable of bypassing traditional security measures At the same time, defenders must invest in AI-driven tools to enhance detection, response, and resilience.
Ultimately, the key to combating AI-powered ransomware lies in balancing advanced AI defences with human oversight. While AI can significantly improve cybersecurity capabilities, it is not infallible A proactive, well-rounded approach that incorporates AI while relying on human expertise will be essential to staying ahead of this new wave of cyber extortion.
AI-powered ransomware represents a significant evolution in cybercrime, offering attackers new levels of speed, precision, and scalability. Organisations must embrace AI as part of their cybersecurity strategy to counter these advanced threats By leveraging AIdriven threat detection and response tools while maintaining vigilant human oversight, businesses can bolster their defences and prepare for the challenges posed by this new frontier in cyber extortion.
The rapid evolution of artificial intelligence (AI) is transforming many aspects of modern life, but its most profound impact may be in the domain of cyber warfare As AI-powered attacks become more sophisticated the
Today, it plays a much broader role, both in enhancing cyber defences and launching more sophisticated attacks Notable instances such as the Stuxnet worm, which disrupted Iran’s nuclear facilities in 2010, highlight AI’s capabilities in cyber warfare This attack, executed through intelligent algorithms, was a wake-up call to governments and security professionals worldwide.
From early applications during the Cold War, where computer technologies were tested for military purposes, to today’s complex AIdriven cyber operations, the trajectory of AI’s role in warfare has expanded significantly Historically, AI’s application in cyber warfare was limited to automated defence systems.
One of the most concerning developments in cyber warfare is the potential for AI to be weaponised by nation-states or criminal organisations AI-powered attacks can target critical infrastructure, including power grids, financial systems, healthcare facilities, and government networks, with devastating effects



Automated and Adaptive Attacks: AI enhances cyber threats by automating large-scale attacks with minimal human intervention. These AI systems continuously learn from their targets, exploiting system weaknesses at unprecedented speeds
Advanced Espionage and Sabotage: AIdriven espionage can efficiently sift through massive datasets to locate sensitive information. Autonomous AI agents can infiltrate networks and cause breaches that may remain undetected, potentially leading to data theft or sabotage of critical systems
Ransomware and AI: AI has intensified ransomware threats through Ransomware-as-a-Service (RaaS) platforms, enabling tailored attacks on specific sectors. AI’s adaptability allows ransomware to modify tactics in response to victim actions, complicating mitigation efforts.
Despite the threats AI presents, it also offers powerful tools for national defence. Governments and organisations are increasingly integrating AI into their cybersecurity systems to detect, prevent, and respond to cyber threats in real time. By leveraging AI for defence, nations can stay ahead of potential adversaries.
AI-Driven Threat Detection:
AI can process vast amounts of data and identify patterns that signal a cyber threat. AI-driven systems can analyse network traffic, user behaviour, and system logs to detect anomalies that indicate potential attacks. This capability allows for early threat detection and swift response, reducing the likelihood of a successful breach.
Automated Defense Mechanisms:
AI-powered defence systems can autonomously adjust to new threats, patching vulnerabilities and securing networks without human intervention. These systems not only monitor the network in real-time but also predict future attacks by analysing past data and emerging threat patterns. This proactive defence model makes it possible to defend against evolving threats
Resilience and Recovery:
AI can enhance recovery efforts following a cyberattack. Self-healing networks and AIdriven recovery systems can rapidly restore operations by identifying the root cause of the attack and initiating corrective measures This minimises downtime and mitigates the long-term effects of a cyber breach


The growing role of AI in cyber warfare raises ethical and geopolitical concerns The weaponisation of AI could lead to an AI arms race, where countries prioritise the development of autonomous cyber weapons Without clear international regulations, this escalation could destabilise global security, increasing the risk of unintended conflicts
Moreover, the use of AI in warfare poses significant ethical dilemmas. Autonomous cyber weapons, capable of launching attacks without human oversight, challenge traditional notions of accountability in warfare. If an AIdriven attack results in collateral damage, determining responsibility becomes murky, complicating both military and legal responses
To navigate the challenges posed by AI in cyber warfare, a balanced approach is required. Nations must embrace AI as a tool for enhancing security while implementing robust regulations to prevent its misuse. International cooperation is essential to develop standards and frameworks that govern the use of AI in military and cybersecurity contexts.
Additionally, governments and organisations must continue investing in AI research and development to stay ahead of emerging threats





Security leaders are currently navigating a challenging landscape where the choice between consolidation and optimisation can significantly impact their organisation’s security posture and budget. These two strategic approaches offer distinct advantages but also present unique challenges Evaluating which method provides the best value requires a nuanced understanding of their implications on costff i d ll i h
The primary goal of consolidation is to simplify security operations by reducing the number of vendors and integrating fewer, multifunctional tools This strategy promises lower costs, enhanced efficiency, and improved visibility. By investing in broader solutions from fewer vendors, organisations aim to eliminate redundancies and streamline their security infrastructure.


However, consolidation often brings unforeseen complications. Multifunctional tools intended to provide comprehensive coverage may fail to address specific, critical needs, leading to the procurement of additional solutions. This can negate the benefits of consolidation, introducing vendor lock-in, increased complexity, and a greater need for specialised skills. Such issues contribute to rising operational costs and can diminish the expected efficiency gains
Integration challenges further complicate consolidation efforts When tools do not align seamlessly, security gaps may emerge, exposing the organisation to new risks. Consequently, the initial promise of consolidation simplified management and cost savings can be overshadowed by hidden costs and increased operational complexity
Optimisation takes a different approach by focusing on enhancing the performance of existing security tools rather than acquiring new ones. This strategy involves evaluating and refining the current security infrastructure to improve effectiveness, close gaps, and align with the organisation’s evolving threat landscape
areas of greatest impact, thereby maximising their return on investment. This threatinformed defence allows for a more agile response to emerging risks while utilising existing resources


Optimisation offers a more strategic and cost-effective alternative to consolidation By fine-tuning existing systems and improving their integration, organisations can achieve a tailored response to specific challenges without incurring the costs associated with new solutions. This approach emphasises leveraging current investments and ensuring that tools are used to their fullest potential
Additionally, optimisation supports better risk management By aligning security efforts with actual threats, organisations can focus on
Compliance often drives organisations towards consolidation, as security frameworks and regulations push for broad solutions that appear to address multiple requirements. However, meeting regulatory demands does not always equate to enhanced security Overemphasis on compliance through consolidation can lead to neglecting critical threats
Optimisation provides a balanced approach by allowing organisations to address compliance while maintaining a focus on realworld risks. Ensuring that existing tools are well-configured and performing optimally supports both regulatory requirements and effective threat management This dual focus makes optimisation a more agile and costefficient strategy

When deciding between consolidation and optimisation, security leaders must carefully consider the costs and benefits of each approach. Consolidation may offer simplified management and broader capabilities but can result in hidden costs and increased complexity Optimisation, conversely, enhances existing tools and aligns security efforts with realworld threats, offering a more sustainable and cost-effective solution
Ultimately, optimisation stands out as the more effective strategy for improving security. By maximising the potential of current resources, organisations can strengthen their defences while avoiding the pitfalls associated with overinvestment and complex integrations As the security landscape continues to evolve, focusing on optimisation ensures that businesses remain both agile and secure in the face of emerging threats