



























































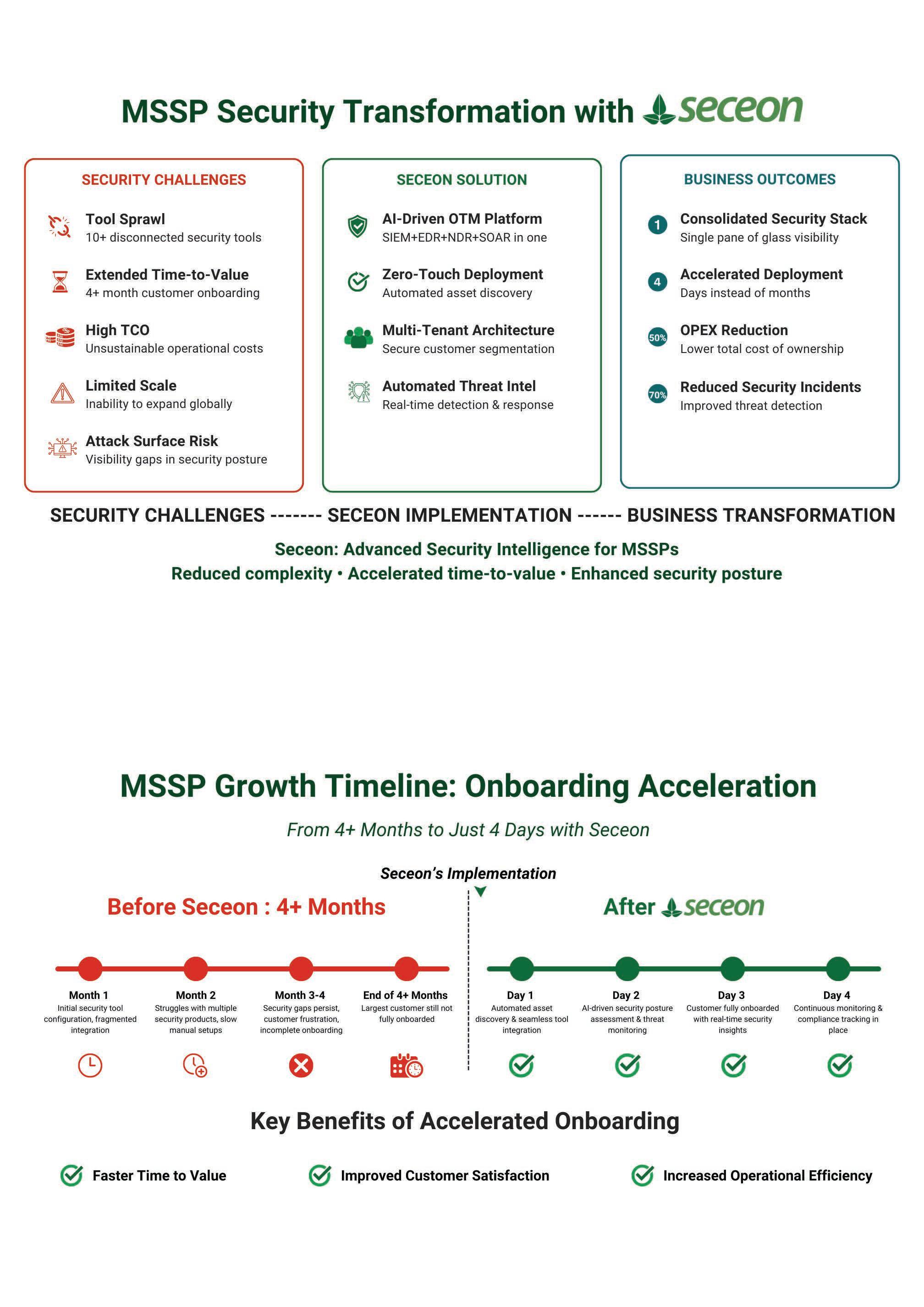
At Tech First Gulf, teamwork fuels everything we do — and GITEX stands as the perfect stage to showcase the power of our collective vision
As we step into GITEX 2025, I’m excited to present this edition of TFG What’s On, your inside view of everything Tech First Gulf is showcasing at the region’s biggest technology stage.
The past year has been one of growth, innovation, and collaboration for TFG. We’ve strengthened our cybersecurity, infrastructure, and collaboration portfolios, expanded into new markets, and continued to push boundaries with transformative solutions. Every milestone reflects our focus on enabling businesses with the right technologies to stay future-ready.
GITEX is where this vision comes alive. At Hall 2 – Stand B30, we’re bringing together a dynamic showcase of next-generation solutions—from
advanced cybersecurity and intelligent infrastructure to powerful collaboration technologies. Beyond products, it’s about creating meaningful conversations, building stronger ecosystems, and empowering our partners and customers to drive measurable outcomes.
This issue of TFG What’s On captures our key highlights, leadership insights, and the innovations we are proud to spotlight at GITEX. It is more than just a glimpse of our participation—it’s an invitation to connect, explore, and co-create the future with us.
We look forward to welcoming you at our stand and shaping the next chapter of growth together.
DESIGNER: MEGHA EP




balance strategic. .
TFG - CSO
Priority to Purpose: At this superfast growing distribution house. .
Architect of Growth: Jai bhatia’s partner first vision for TFG. .

Samsung Ruggedized Devices for Frontline Excellence. .
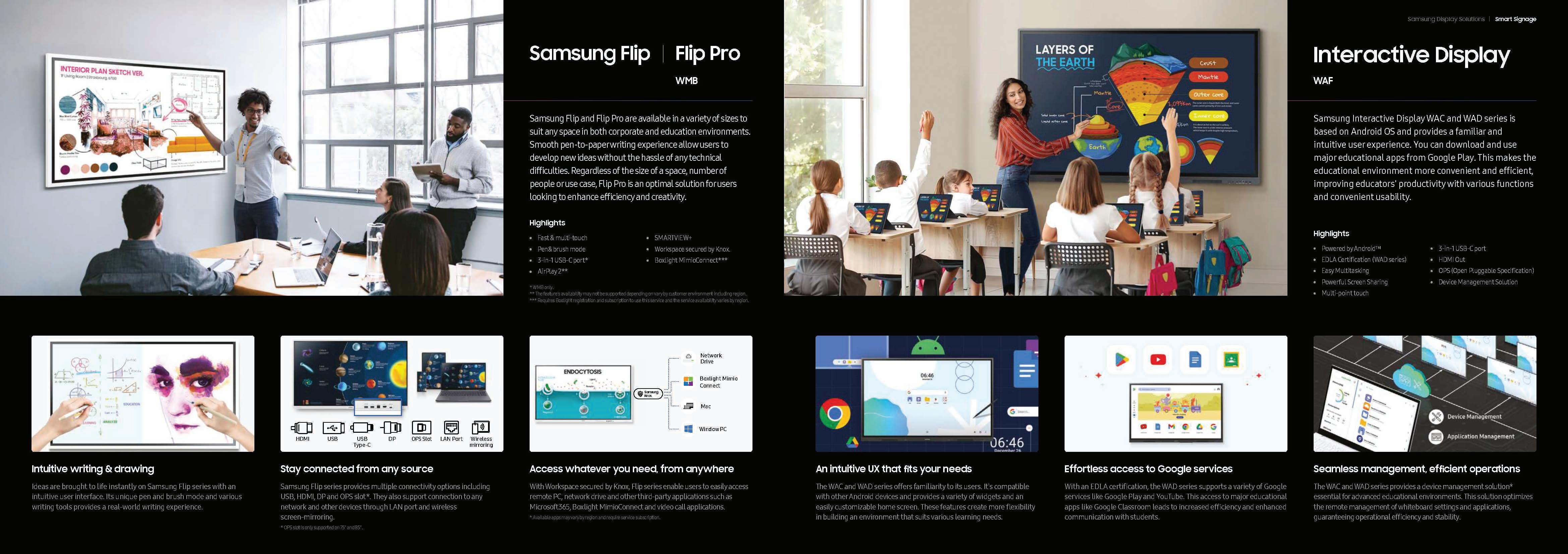
Rally Board 65: Everything you need quickly add video to meeting rooms. .
SAMSUNG DISPLAY
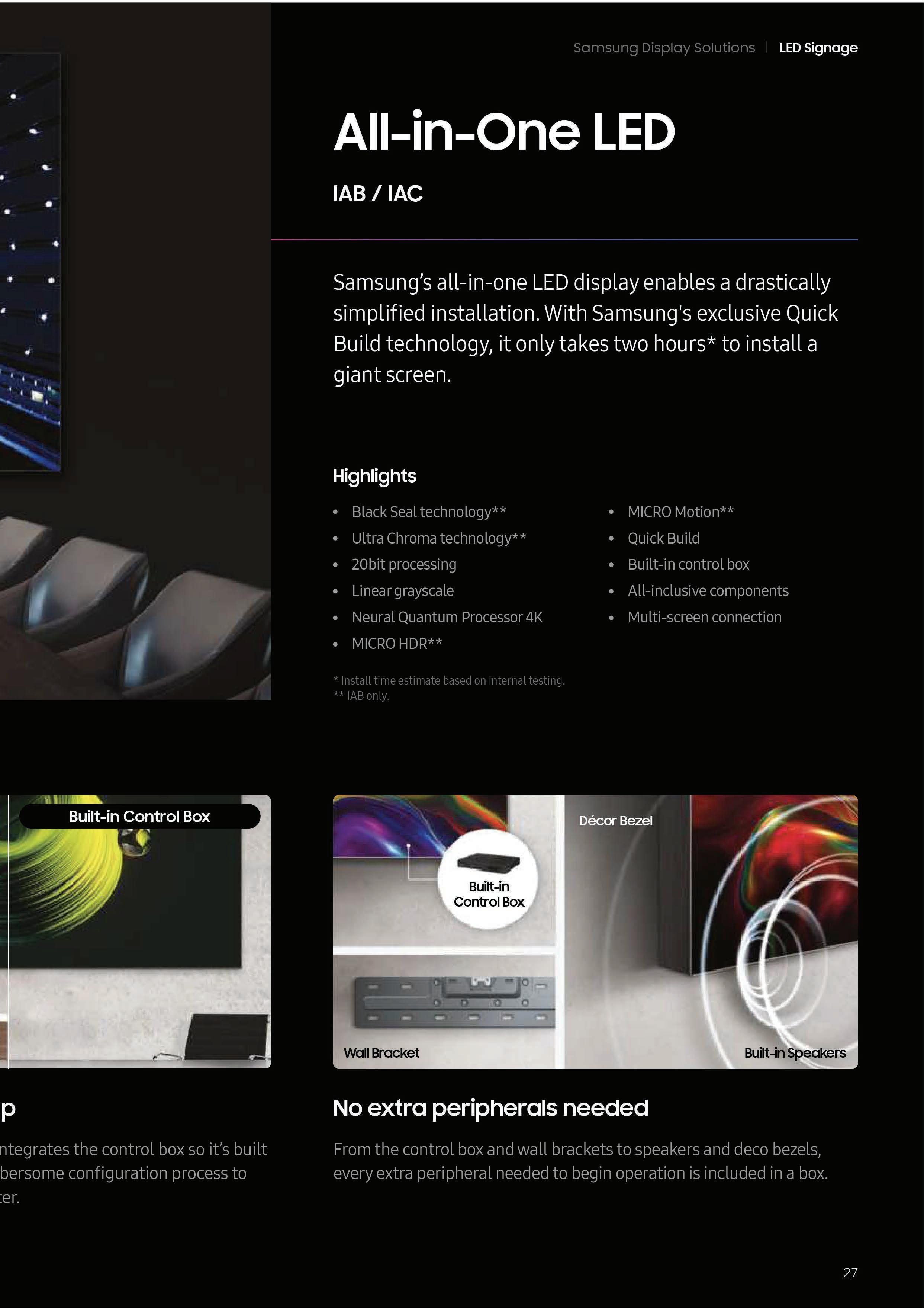
Samsung’s all-in-one LED display enables a drastically simplified installation. .
AI's double -edged sword: why business leaders must rethink cyber risk. . FORCEPOINT
Measure Risk Exposure with Forcepoint's Data Risk Management. .

Omada by Tplink: Unified networking & suveillance solutions. . COMMVAULT
Bolstering your cyber resilience strategies with cleanrooms. . H3C
we are constantly improving the capability of digitalization and intelligence. .
Simplify IT deployment. One Rack PDU for most applications. .



Unveil new LTE body camera, Next-generation PoC Radio. .
ALE
Why Network Security Needs IoT Fingerprinting and Profiling. .
Closing the Data Gap:Se clore’s Next-Gen Digital Rights & Asset. .



The perfect sound requires both excellent technology and an. .
The perfect sound requires both excellent
Shaping the Next Era for Digital Trust. .
Discover our complete suite of products and services accessible in a. .
Proves commitment towards safeguarding users’ digital life and. .
Building resilient and trustworthy AI systems hinges on data. .
Connect with Huawei eKit, Leader of Gartner Magic Quadrant. .

At Tech First Gulf, my vision has always been to balance strategic growth with responsibility. Over the years, we’ve expanded across the MEA region, strengthened our vendor portfolio, and earned the trust of our partners.
In 2026, our focus is clear: expanding into new markets, deepening our cybersecurity and infrastructure solutions, and ensuring that growth remains sustainable and meaningful for all stakeholders.
For me, leadership is about creating clarity, empowering teams, and setting benchmarks of excellence. As we step into another transformative year, I believe TFG is well-positioned to lead the next chapter of innovation and growth in the distribution sector.
“Leadership is about creating clarity, empowering teams, and setting benchmarks of excellence!

HEMANT MALI, Founder & Managing Director
As Chief Strategy Officer at TFG, I drive here a unique role of putting direction & flow to all the actions. At this superfast growing distribution house, every single day is about actions and tactics. We’re quite sizeable already on markets we work in, team size and the number of brands. Ensuring organization wide focus on the vision & mission, aligning KPIs and objectives with market opportunities, I must ensure the company stays competitive. I work with leaders across departments to drive innovation and long-term growth.
My core responsibility involves assessing industry trends, market dynamics, and internal capabilities to recommend initiatives. I also prioritize development of scalable operations and fostering agility to adapt in a rapidly changing environment. Customer-centric solutions and cross-functional collaborations are vital in supporting company goals, in which I play an instrumental role in guiding performance measurement and setting clear, actionable goals for each department.
My 30 years’ experience in IT, Pharma & Consulting and varied roles across MENA, Africa, and India, from Profit Center to product management, and from Channel Operations to fund raising comes in good stead while setting companywide measurable outcomes and continuous improvement. My role demands a forward-thinking mindset and active engagement with external stakeholders to make informed decisions towards progress & business development. Focused on driving results through effective communication and teamwork, I ensure the organization meets its long-term objectives.

AMIT KHANDELWAL, Chief Strategy Officer (CSO)
performance rhythms so initiatives advance consistently from hypothesis to impact. I use scenario planning and descriptive analytics to surface risk, quantify trade-offs, and focus resources where strategic advantage is strongest.
I ‘m working to accelerate digital adoption and ecosystem partnerships to expand addressable markets while protecting core margins and service reliability. My approach is to build capability by equipping product, commercial, and delivery teams with straightforward metrics, decision protocols, and rapid experimentation loops so strategy is operational, not theoretical.
I bring a consultative, evidence-first approach to shaping growth and operational clarity across markets. I partner with country leadership teams to translate market signals, customer insight, and regulatory constraints into pragmatic strategic choices and measurable priorities. I design roadmaps that balance short-term delivery with long-term value creation, embedding clear KRAs and
I’m striving to foster a culture of inclusive leadership and continuous improvement that privileges customer value, evidence-based learning, and timely course correction. Measures success through sustained topline growth, margin resilience, shortened time-to-market, and demonstrable customer outcomes.
Focused on turning complexity into repeatable advantage through clear choices, accountable execution, and disciplined learning.
In the dynamic world of technology distribution, true leadership is defined by a vision that transcends transactions to build a thriving ecosystem. Jai Bhatia, the new President - Volume at Tech First Gulf, embodies this principle. An experienced senior executive with a distinguished track record in the information technology and services industry, he brings extensive expertise in marketing management, business planning, retail, sales, and retail category management to his new role. Jai Bhatia is now channeling his proven philosophy of strategic growth and agile transformation, signaling a new era for Tech First Gulf—one rooted in deep collaboration and the pursuit of shared success.
At the core of Jai Bhatia’s strategy is a foundational belief in a partner-first mindset. He champions a mission shaped by operational excellence and a deep understanding of local market dynamics. Tech First Gulf’s core strength lies in its loyal bonding with top resellers and its privileged access to their home accounts, which the company strategically leverages to benefit its vendors. The company deploys a high-touch TAS (Territory Account Strategy) concept meticulously aligned with each vendor’s objectives, ensuring that both partners and vendors are integral to the ecosystem. As Jai Bhatia asserts, "Both our partners and vendors are not just part of our strategy—they are our strategy," a principle that underpins this collaborative, results-driven approach.

Looking ahead, the vision for Tech First Gulf under Jai Bhatia’s
leadership is clear: to evolve into a strategic enabler for its partners. This means moving beyond product delivery to provide data-driven insights, tailored solutions, and the emerging technologies needed to navigate an increasingly complex landscape. With Jai Bhatia at the helm, Tech First Gulf is poised to redefine technology distribution in the region, championing an accessible, impactful, and partner-first future




































In today’s fast-paced industries, frontline workers need devices that can keep up with the rigors of demanding environments without compromising performance. Samsung answers this call with the Galaxy XCover7 Pro and Galaxy Tab Active5 Pro — two ruggedized, enterprise-ready devices engineered to deliver military-grade durability, seamless connectivity, and smarter productivity tools.
Carrying forward Samsung’s legacy of rugged innovation, the XCover7 Pro smartphone and Tab Active5 Pro tablet are designed to excel in tough conditions. Both devices combine IP68-rated water and dust resistance with military-standard durability testing, ensuring they remain
dependable even when exposed to dust, accidental splashes, or outdoor challenges. Whether used in construction, emergency response, logistics, or field operations, these devices are built to perform.
Performance upgrades make these models stand out. Both devices feature 5G connectivity, Wi-Fi 6E, and network slicing, delivering fast and reliable access in even the most crowded network environments. The XCover7 Pro comes equipped with a robust 4,350mAh battery, while the Tab Active5 Pro boasts a massive 10,100mAh battery with Dual Hot-Swap functionality, enabling users to replace batteries without powering down. For stationary use, the Tab Active5 Pro also supports No Battery Mode, allowing uninterrupted

operation when connected to external power — a game-changer for vehicles, kiosks, and workstations.
In frontline work, clarity of communication can make all the difference. The XCover7 Pro introduces a new stereo speaker system with anti-feedback technology, minimizing disruptive audio loops and improving walkie-talkie functionality. The Tab Active5 Pro further enhances collaboration with intelligent sound processing, optimized audio tuning, and boosted volume levels — ensuring teams stay connected and critical information is relayed without disruption.
Samsung has also focused on improving visibility in challenging environments. Both devices feature Vision Booster technology, enhancing screen readability under bright light. The Tab Active5 Pro raises brightness to 600 nits, a notable upgrade from its predecessor, making it easier to review workflows, maps, or technical data outdoors.
Beyond durability and power, Samsung integrates AI-driven enhancements that streamline daily tasks and empower workers to operate more efficiently. These intelligent features reinforce Samsung’s commitment to making advanced technology accessible across its rugged ecosystem, giving frontline professionals the tools they need to stay agile and productive.
With the Galaxy XCover7 Pro and Galaxy Tab Active5 Pro, Samsung redefines what ruggedized devices can achieve — enabling frontline excellence from the office to the most demanding field environments.






The cybersecurity landscape across APAC—and especially in India—is reaching a critical inflection point. With digital transformation accelerating, organizations are facing not just more frequent attacks, but also more sophisticated ones that target applications, APIs, and data at scale. Businesses here can no longer afford a reactive approach. They need proactive, AI-driven defenses that align with the unique challenges and opportunities of this region.
First, malicious AI models are professionalizing cybercrime. Tools like WormGPT and FraudGPT showed what happens when guardrails are stripped away. Their successor, Xanthorox AI, takes this further. It’s offered as a subscription-based hacking platform, capable of generating malware, ransomware, and phishing campaigns at scale. What once required skilled hackers can now be automated by anyone with some cryptocurrency and intent.

































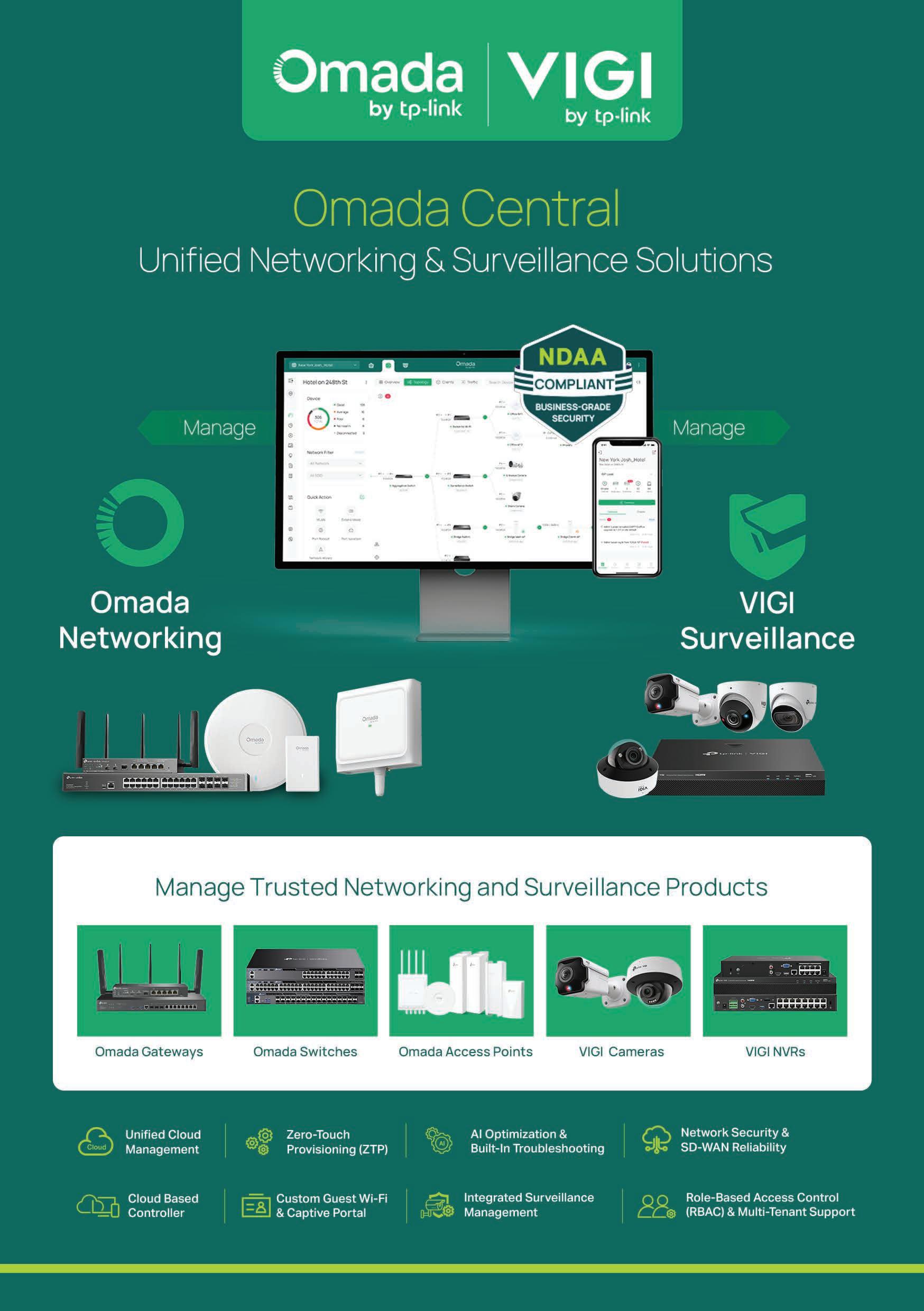

•Offices & Hotels: Guest Wi-Fi, AI detection, low-light monitoring
•Retail & Restaurants: POS roaming, cross-store analytics, deterrence alerts
•Schools & MDUs: Perimeter protection, attribute-based search, AAA integration
Trusted by TP-Link
•28 years of innovation, strict quality control
•Up to 5-year extended product warranties*
•Local support & quick inventory
•Competitive pricing & exclusive partner
benefits



Cyber threats and incidents are increasing in frequency and sophistication at an alarming rate, resulting in the desperate need for security leaders to strengthen their organisation’s ability to prevent, withstand and recover with minimal disruption or risk.
In order to achieve this, testing is paramount. To test cyber recovery and readiness capabilities, organisations should be implementing an isolated recovery environment (IRE), like a cleanroom, to minimise any risk of data contamination, as a priority.
Providing an isolated environment where organisations have a safe environment to help undertake the retrieval of data from infected systems, a cleanroom is more than just a physical space. It’s a comprehensive approach to cyber recovery that encompasses the creation of an environment separate from the production environment, together with well-defined best practices and testing procedures that can help minimise the risk of further damage to your systems.
In the event of a breach, affected systems or devices are first isolated from the production network and all compromised data securely transferred to the cleanroom using encrypted channels and protocols. The compromised data is then analysed and assessed to evaluate the extent of the breach and any potential impact on the organisation. And this is exactly how we operate using Commvault Cloud Cleanroom Recovery. Next, clean backups or unaffected copies of the data can be restored in the cleanroom environment that are designed to ensure that recovered data is free from malware or
malicious code and has been verified for accuracy and completeness.
Since clean recovery plays such a vital role in keeping compliant with industry standards and legislation, organisations will need to follow industry best practices, use advanced security technologies and minimise potential risks during the reintroduction process.
By doing so, organisations are better supported when remaining compliant with cybersecurity directives such as NIS2 as well as industry-specific regulations such as HIPPA, PCI DSS or DORA. At Commvault, this is imperative for our customers, as a lot of these new legislations globally are constantly coming into force.
Clean recovery is evolving fast, thanks to the integration of advanced tools that elevate the accuracy of recovery processes and automate tasks for greater speed and efficiency. Meanwhile, the emergence of cloud-based recovery solutions means organisations have the option to recover data directly from cloud environments and take advantage of powerful data analytics and visualisation tools that deliver deeper insights into their recovery efforts.
capabilities, organisations should be implementing an isolated recovery environment (IRE), like a cleanroom, to minimise any risk of data contamination, as a priority.



platform that includes cloud computing, big data, artificial intelligence (AI), industrial internet, information security, intelligent connectivity, and edge computing, as well as end-to-end technical services. We are also the exclusive provider of HPE® servers, storage and associated technical services in China.
“Shaping the Digital Future for a Better Life” is the corporate vision of H3C. We are aiming to drive the development of the digital economy, and together with customers and partners, to create a better life for all to enjoy.
We have firmly oriented ourselves towards the needs of our customers, supported by a deep foundation with more than 30 years of operation. We provide scenario-based and customized solutions to our customers, enabling digital transformation in various industries that include, but not limited to carrier, government, finance, healthcare, education, transportation, manufacturing, utilities, energy, Internet, and building etc., products are widely used in over 100 countries and regions.
We take technical innovation as the engine for growth. Currently, more than 50% of our employees are R&D staff. We have filed over 14,800 patents, of which more than 90% are invention patents. Facing the new era of intelligence led by AI technology, we comprehensively deepen the strategy of "Cloud & AI Native" and upgrade the "Digital Brain", releasing the value of computing power resources through computing power x connectivity, and solidifying the base of intelligent computing to empower the digital transformation of various industries, in a bid to continuously help customers realize smarter business decision-making (Smart), faster response to business needs (Timely), more agile business deployment (Agile), more reliable support to business development (Reliable), safer business environment (Safe).









Enterprises across virtually every business vertical continue to adopt digital technologies such as mobility, data analytics, cloud, the Internet of Things (IoT), and connected infrastructure. Gartner® predicts that “in 2025, more than 85 percent of enterprises will have more smart edge devices on their network than laptops, tablets, desktops, or smartphones.”
Gartner also notes that “By 2028, IIoT platform providers will increase their total addressable market by 30% due to IT/OT integration requirements.”
Furthermore, Gartner adds, “By 2026, 65% of IoT-enabled middleware sales will include purpose-built IoT applications, an increase from 35% in 2023.”
This accelerating digital transformation, particularly around the proliferation of unapproved and unplanned IoT devices, introduces significant network infrastructure challenges:
Traditional, static network configurations are not designed to securely or efficiently accommodate this influx of IoT endpoints while maintaining optimal network performance Many IoT devices lack embedded security or are shipped with default configurations, making them highly susceptible to exploitation and misuse
Faced with these challenges, IT administrators must decide whether to block unknown devicespotentially disrupting operations and frustrating users - or find scalable ways to enable their secure usage. One of the most effective approaches is leveraging device fingerprinting and profiling.
Manually provisioning, securing, and managing the ever-growing variety of IoT devices is
becoming unfeasible for most organizations. Instead, by applying device fingerprinting and profiling techniques, IT teams can identify and classify devices based on their unique attributes and behaviors. This enables the automatic application of tailored security, bandwidth, and access policies aligned to the device's purpose and risk level.
Fingerprinting and profiling allow the creation of an up-to-date, dynamic inventory of connected devices stored within a cloud database. Administrators can then group these devices into customized categories and assign dynamic Universal Network Profiles (UNPs) to govern access. These profiles define bandwidth, quality of service, and security settings, ensuring IoT devices are handled according to policy within their own network containers.
For IT teams, this process acts as a force multipliersimplifying IoT onboarding and lifecycle management while reducing manual overhead and risk. For organizations, it means employees, partners, and customers can benefit from connected devices without compromising security or network performance.
Alcatel-Lucent Enterprise’s OmniVista® Network Management System (NMS) is purpose-built to address these challenges. Within a Service Defined Network architecture, OmniVista NMS enables advanced device fingerprinting and profiling when deployed alongside OmniSwitch® and OmniAccess® Stellar Wireless Access Points.
OmniVista NMS inspects network traffic to determine the type of connected device, then communicates with a cloud-based fingerprinting service to categorize it and assign an Access Role Profile (AR Profile). These profiles dynamically enforce access control and security parameters, placing IoT devices into logical containers with predefined behaviors -- such as bandwidth limits or certificate-based authentication.



In today's interconnected business world, sensitive digital assets—from intellectual property to private customer data—often travel beyond the traditional IT perimeter. Relying on simple encryption or network security alone is no longer enough. Seclore's data-centric security platform gives you persistent control, visibility, and risk remediation throughout a digital asset's entire lifecycle, no matter where it goes.
Enterprise Digital Rights Management (EDRM)
•Persistent granular controls: Specify who can view, edit, print, share, or take screenshots of a file.
•Support for revocation (remotely): Regardless of where a file is downloaded or shared, it is possible to revoke access to it.
•New support for neutral CAD files: Critical for manufacturing, supply chain, aerospace, and automotive manufacturing sectors, it is now possible to track access, enforce protection, apply dynamic watermarks, and control use.
Digital Asset Classification + Risk Insights
•Classification of assets based on sensitivity, business value, and regulatory demands with labels/sub-labels, metadata, and auto-suggested classifications upon creation or use.
•Dashboards & reports to show where risk trends: external access, classification adoption, protection coverage.
•Classification-Driven Protection: Automatically apply appropriate security controls when classifying assets. Minimizes friction for users.
To ensure Seclore works in existing enterprise environments:
•Integrates with DLPs, CASBs, and discovery/classification tools to automate protection when sensitive assets are identified.
•Seamless with productivity & collaboration platforms: Microsoft 365 (Word, Excel, PowerPoint), Outlook, Teams, SharePoint, OneDrive.
•Also works with content management / VDRs / ERPs / custom apps via APIs & SDKs.
•Compliance made easier: Seclore helps organizations adhere to global privacy and security standards, classification-driven policies, full audit trails, and risk insights.
•Visibility & control over data: You know where your most sensitive assets are, who accessed them, what they did, and can act (revoke, restrict) if needed.
•Reduced friction: Protection and classification-driven policies baked into workflows, automatic protections (e.g., hot

folders, DLP-triggered) mean less manual burden on users and faster time to value.
•Supply chain and IP protection: With CAD file protection and neutral CAD support, enterprises in manufacturing or engineering can share designs securely with partners and third parties.
Conclusion:
Seclore’s combined EDRM and Digital Asset Classification capabilities represent a leap forward in data-centric security. Its technology allows organizations not just to protect static files, but to understand, classify, control, monitor, and respond to how data moves and is used—while integrating with existing platforms, workflows, and regulatory regimes. If you’re an enterprise that treats your intellectual property like its lifeblood—and can’t afford missteps in compliance or third-party risk—Seclore delivers not just tools,
It delivers a complete ecosystem that transforms data security from a simple checklist into a proactive, "always-on" defense.





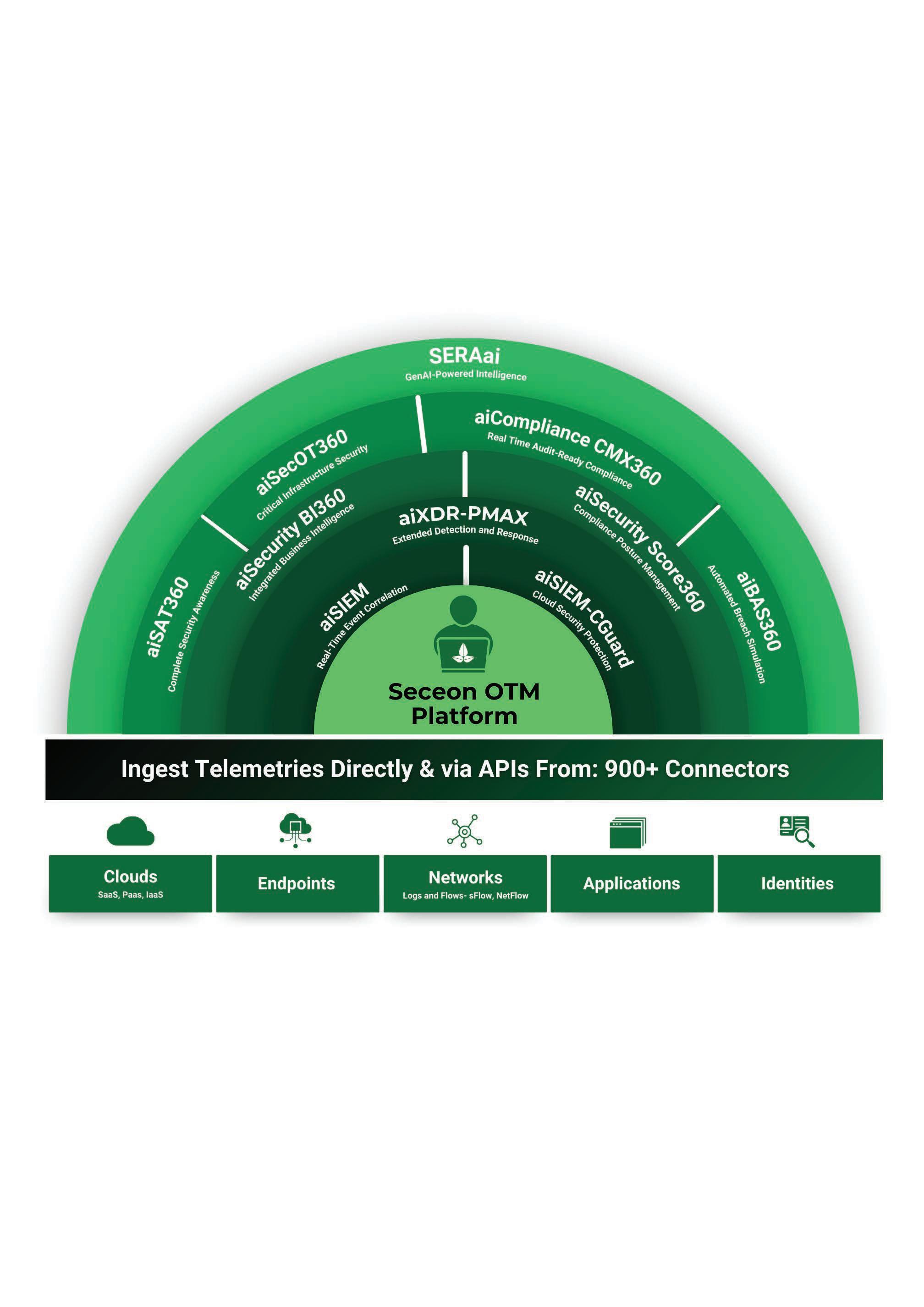
In a world where cyber threats are getting smarter every day and compliance regulations are piling up, businesses need more than just a security tool; they need a smarter, more complete defense. Seceon’s Open Threat Management (OTM) platform is that solution. It is a comprehensive, AI-driven platform that unifies security operations, combining threat detection, investigation, and automated response into a single, integrated solution. By providing real-time threat detection and automated compliance management across endpoints, networks, and cloud services, Seceon’s OTM platform empowers your organization to protect its assets and meet regulatory demands from one powerful platform.
Seceon recently introduced aiCompliance CMX360 ™, a game-changing platform that turns compliance from a headache into a major business advantage. Imagine walking into a meeting and saying you’ve achieved 60-80% readiness for over 20 global frameworks, including SOC 2, SAMA, and ISO 27001, on day one. CMX360 makes this a reality by using a company's existing security data to generate compliance evidence instantly. With CMX360, you can finally align your security and compliance efforts, eliminating the need for separate tools and manual work.
Our OTM platform is a true force multiplier, with powerful new modules like aiBAS360 (Breach and

Attack Simulation), aiSAT360 (Security Awareness Training), and aiSecOT360 (Security for Operational Technology). Each module is designed to give you a complete, panoramic view of your security landscape, from understanding human behavior to protecting your most critical industrial systems. It’s a comprehensive, intelligent solution all in one place.
Our success is amplified by a thriving partner ecosystem of over 700 partners and more than 9,000 customers worldwide. We empower our partners to grow their business with high-margin cybersecurity services, all built on a platform with predictable economics. This allows partners to onboard new clients in hours, slash their operational costs, and achieve impressive profit margins.
The market is already buzzing about CMX360. As Joshua Skeens, CEO of Logically, shared, “Traditional compliance tools force our clients to start from scratch, requiring 6-12 months and significant resources. CMX360’s ability to instantly leverage existing security data means we can now help customers achieve SOC 2 readiness in weeks instead of months.”
To learn more about how Seceon can transform your security and compliance posture, visit our website at www.seceon.com



Invicti Security, a leader in dynamic application security testing (DAST), has acquired Kondukto, the pioneer of the rst Application Security Posture Management (ASPM) solution. This move ful lls a long-standing request from security teams: combining runtime-validated DAST results with ASPM insights to build more accurate, scalable, and actionable application security programs.
By integrating Invicti’s AI-powered DAST with Kondukto’s orchestration and posture management, organizations gain a uni ed view of their security posture. This provides clarity across the application ecosystem, accelerating remediation and eliminating the noise of false positives.
Unlike one-size- ts-all platforms, Invicti will continue to o er best-of-breed DAST enhanced by ASPM. Customers retain their existing testing tools and CI/CD work ows while gaining a single pane of glass for managing their AppSec posture.
Dilek Dayınlarlı, General Partner at ScaleX Ventures and early investor in Kondukto, highlighted the strategic importance: “Kondukto rede ned how modern organizations manage application security. Seeing this vision scale through Invicti is a meaningful milestone for the future of secure software development.”
Kondukto’s capabilities strengthen Invicti with:
- Centralized orchestration to unify AppSec tools across the SDLC, from code to cloud.
-
- AI-powered remediation that delivers tailored x recommendations directly into developer work ows.
-
- Automation at scale, enabling smart routing of high-priority issues to the right teams.
- 360° AppSec visibility by merging Invicti’s runtime DAST with ASPM coverage of SAST, SCA, secrets scanning, and container security.
Developer-centric integration with AI-guided remediation, reducing alert fatigue and DevSecOps friction.
-
- Less noise and more signal by feeding proof-based, runtime-validated vulnerabilities into Kondukto’s orchestration engine.
This acquisition marks a major step in Invicti’s mission to provide accurate, scalable, and actionable application security, now powered by full-stack posture management.
Neil Roseman, CEO of Invicti, emphasized that customers want fewer disconnected tools and more actionable visibility: “With Kondukto, we’re delivering centralized orchestration and signal clarity, anchored in runtime reality – where attackers live.”
President Kevin Gallagher added that the acquisition aligns directly with Invicti’s mission to deliver security with zero noise: “This helps us provide a platform backed by proof rather than guesswork.”
Cenk Kalpakoğlu, CEO of Kondukto said: “Security teams are drowning in data but starving for insight. We built Kondukto to normalize and correlate ndings across AST tools. Together with Invicti, we can deliver this at scale.”



Phishing remains one of the most dynamic online fraud threats, constantly evolving and becoming more complex in light of new technology. The active use of artificial intelligence (AI) by cybercriminals allows them to create fake email and web pages faster and generate plausible audio and video content, thus making phishing attacks targeted and even more sophisticated. This necessitates increased caution on the part of users, as well as tools which are highly effective at the detection of phishing attempts, such as Kaspersky cybersecurity solutions which have consistently demonstrated advanced capabilities in this field.
In the 2025 evaluation by AV-Comparatives, a range of security solutions were tested with more than 200 phishing URLs. To complete certification, a product needed to block at least 85% of these phishing sites. Additionally, a false-positive test was performed to verify that legitimate websites, particularly sensitive ones such as online banking, were not misguidedly blocked.
Since 2011, Kaspersky’s consumer solutions have regularly participated in Anti-phishing tests by AV-Comparatives and have demonstrated stable, high results. In particular, Kaspersky achieved a 93% detection rate with 0 false positives in 2025 and 2024, and was awarded with the “Approved” certificate.
To ensure advanced cyber protection against increasingly complex phishing threats, Kaspersky actively amplifies its consumer solutions with AI-powered tools. Kaspersky’s anti-phishing technology has two machine learning-based algorithms, which make phishing detection effective and easily adaptable to new types of phishing. In 2024 more than 67 million phishing attacks were blocked by Kaspersky Consumer solutions with the help of AI technology.
In particular, Kaspersky’s anti-phishing protection is run by the AI-powered feature OCR (Optical character recognition) which is indispensable in recognizing malicious text hidden inside pictures on a phishing site. This machine algorithm analyses all downloaded web pages and uses machine vision to detect phishing text inside the image. Every discovered phishing text is saved in the system and used for subsequent detection.

Another technology that makes the Kaspersky Anti-phishing solution highly effective is its patented machine learning model based on the examples of multiple phishing and legitimate sites. The algorithm is trained on millions of downloaded web pages, extracting from them those trappings that are the most relevant for detecting fraudulent web pages.
To be highly protected against phishing attacks Kaspersky recommends:
-Always check the authenticity of unsolicited emails and links, even if they seem trustworthy.
-Avoid sharing personal data on unverified sources.
-Double-check websites before making purchases, especially when the offer seems too profitable.
-Use a reliable security solution, like Kaspersky Premium to block phishing attempts.




























































































































































































































App-free, dongle-free wireless presentation
Platform-agnostic BYOM web meetings
All the collaboration tools you need
View content on your own device

Hazem Mahdy Sales Manager - Middle East



Why are WolfVision Cynap systems such a strong fit for corporate environments in the Middle East?
In today’s fast-paced business world, companies demand reliable, secure, and user-friendly solutions for content sharing and hybrid collaboration. The WolfVision Cynap range - including Cynap Pure, Cynap Pure Pro, and Cynap Pro - ticks all these boxes, offering seamless BYOD (Bring Your Own Device) and BYOM (Bring Your Own Meeting) capabilities that eliminate the need for cables, dongles, or additional hardware.
Corporate users can simply connect wirelessly from any device to present, collaborate, or host meetingswhether they’re in the office, working remotely, or on the move. This level of flexibility is essential for today’s hybrid work environments.
How does the Cynap platform support hybrid meetings using BYOM functionality?
BYOM is a game-changer for corporate users. With Cynap, participants can use their preferred web conferencing service - like Zoom or Microsoft Teams - while making full use of the in-room AV setup. Users connect their laptop wirelessly to Cynap and gain access to microphones, cameras, speakers, and displays already in the meeting space. This avoids the technical hassle often associated with hybrid meetings and ensures every session begins on time, with professional audio and video quality. It’s simple, efficient, and removes IT headaches.
Can you tell us more about the Viewer Mode feature and how it benefits meeting participants?
Absolutely. Viewer Mode is particularly useful in larger meeting rooms or boardrooms, where participants might be seated far from the main screen. This feature allows the main display content to be streamed in real-time to any connected personal device.
It’s especially valuable during detailed presentations, training sessions, or collaborative workshops - ensuring that everyone in the room has a clear view of what's being shared, regardless of where they're sitting.
What sets WolfVision apart in the wireless presentation space?
What really makes WolfVision stand out is the app-free, dongle-free approach. There’s no need to install software or carry special hardware. Add to that platform-agnostic compatibility, secure streaming, and exceptional ease of use, and it's clear why many corporate customers in the Middle East are choosing Cynap systems.
•Easy BYOD/BYOM connectivity for seamless hybrid collaboration
•Wireless presentation with no apps, cables, or dongles
•Viewer Mode for improved in-room visibility
•Secure, scalable solutions ideal for corporate IT teams
As AI continues to dominate boardroom conversations across the Middle East, the narrative is evolving. The initial excitement — often driven by FOMO — is giving way to a more measured, results-driven approach. Today, enterprise leaders are no longer greenlighting AI projects simply on the promise of innovation. They're demanding evidence: clear ROI, measurable outcomes, and long-term value.
Yet amid this more grounded push toward AI adoption, one critical factor is still being underestimated — data.
AI isn’t magic. It’s only as good as the data that powers it. And in many organisations, the quality, completeness, and context of
that data is lacking. An additional issue is proliferation — multiple copies of the same data sitting in different departments: if each one is tweaked, there are different versions of the truth instead of one authoritative master dataset.
Additional investment in other areas such as adding more compute won’t fix poor inputs — it will just amplify bad outcomes faster. In sectors like finance, healthcare, and government, this can have serious real-world consequences: biased credit decisions, clinical misdiagnoses, flawed public policy.
The global fragmented regulatory landscape adds further complexity, making data and especially data governance not just an IT issue, but a board-level imperative.

Omar Akar VP – METCA region at Pure Storage

To build resilient and trustworthy AI systems, data needs to be continuously captured, engineered, and refined. This isn’t a one-off project — it’s an ongoing cycle where good data leads to smarter models, smarter models drive better decisions, and those decisions generate better data. An AI flywheel — a self-reinforcing loop that transforms data into insight, and insight into impact.
But to activate this flywheel, organisations must take data lineage seriously. Every step — from ingestion to transformation to model training — must be traceable and transparent. Without this discipline, it becomes impossible to explain, audit, or improve AI systems over time. And in an era of increasing regulatory scrutiny and user distrust, that’s a risk no business can afford.
There needs to be cultural transformation as well as the operational shift demanded by AI. Shared, concurrent access to one authoritative dataset instead of department silos. Success requires one ‘golden’ copy of the data — or AI models will be broken before they’ve even started.
Let’s move the spotlight beyond algorithms and outcomes. Let’s recognise the foundational role of data — and the infrastructure, discipline, and strategy required to manage it. Because without trusted data, there is no trustworthy AI.












Aesthetic Design Leader of Gartner Magic Quadrant
Free Cloud Management
3 Years Warranty, Replace Only




Connecting Markets. Empowering Growth. Everywhere.




