www.counterterrorbusiness.com | ISSUE 53 HVM STADIUM SECURITY SURVEILLANCE MARTYN’S LAW What has the inquiry revealed? VOLUME 2 FINDINGS MANCHESTER ARENA INQUIRY An update from AEV on Martyn’s Law SECURITY FOR VENUES


In December, it was announced that Protect Duty will now be known as Martyn’s Law, with legislation set to be published in the spring. The announcement comes after years of action by campaigners, including Figen Murray, the mother of Martyn Hett who was killed in the Manchester Arena attack and whom the law is named after.

In November, Volume 2 of the Manchester Arena Inquiry was published. Volume 2 focusses on the emergency response to the attack and identified failings by the emergency and security services. In this issue of Counter Terror Business, Martyn’s Law campaigner Nick Aldworth investigates the findings of Volume 2.




CTB53 also includes a feature on how HVM can be used as a solution to other common problems faced by towns and cities, such as flooding and global warming and an article on what happened at the men’s Champions League final in Paris in 2022.


Finally, we also cover how facial recognition technology can be used in the fight against terror, how to protect offshore oil and gas installations and how to install and update access control systems.







 Polly Jones, editor
Polly Jones, editor


COUNTER TERROR BUSINESS PROGRESS ON MARTYN’S LAW 5 www.counterterrorbusiness.com | ISSUE 53 HVM STADIUM SECURITY SURVEILLANCE MARTYN’S LAW SECURITY FOR VENUES An update from AEV on Martyn’s Law What has the inquiry revealed? VOLUME 2 FINDINGS MANCHESTER ARENA INQUIRY To register for your FREE Digital Subscription of Counter Terror Business, go to: www.counterterrorbusiness.com/digital-subscription or contact Public Sector Information, 226 High Road, Loughton, Essex IG10 1ET. Tel: 020 8532 0055 ONLINE // MOBILE // FACE TO FACE www.counterterrorbusiness.com © 2023 Public Sector Information Limited. No part of this publication can be reproduced, stored in a retrieval system or transmitted in any form or by any other means (electronic, mechanical, photocopying, recording or otherwise) without the prior written permission of the publisher. Whilst every care has been taken to ensure the accuracy of the editorial content the publisher cannot be held responsible for errors or omissions. The views expressed are not necessarily those of the publisher. ISSN 2399-4533 PUBLISHED BY PUBLIC SECTOR INFORMATION LIMITED 226 High Rd, Loughton, Essex IG10 1ET. Tel: 020 8532 0055 Web: www.psi-media.co.uk EDITOR Polly Jones PRODUCTION MANAGER & DESIGNER Dan Kanolik PRODUCTION DESIGNER Jo Golding PRODUCTION CONTROL Deimante Gecionyte WEB PRODUCTION Freya Courtney PUBLISHER Jake Deadman Follow and interact with us on Twitter: @CTBNews
Terror Business would like to thank the following organisations for their support: COMMENT
Counter
3 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE





THE NEW PROTAC ® 2.0 USB RECHARGEABLE SERIES
2,000 LUMENS WITH NO REDUCTION IN RUN TIME HANDS FREE PROTAC ® 2.0 HEADLAMP USB-C RECHARGEABLE LITHIUM-ION BATTERY PACK POWERED BY THE NEW SL-B50 ® Made for situations when failure is not worth contemplating, Streamlight® has created the broadest range of professional torches and lighting tools that can be trusted for a lifetime. streamlight.com WEAPON MOUNT PROTAC ® 2.0 RAIL MOUNT LONG GUN LIGHT HANDHELD PROTAC ® 2.0 TACTICAL FLASHLIGHT Come and visit us at 28 Feb -1 Mar 2023 Nuremberg Hall 10. Stand 10-345. 2-5 March 2023 Nuremberg Hall 3. Stand 316.
TAKING BRILLIANT THINKING TO A WHOLE NEW LEVEL
FEATURING
CONTENTS CTB 53
07 NEWS
Martyn’s Law plans unveiled; Changes to airport security rules; and Government legislation targets bomb-making materials

10 MANCHESTER ARENA INQUIRY
Nick Aldworth of Risk2Resolution and Martyn’s Law campaigner investigates the findings of Volume 2 of the Manchester Arena Inquiry, which was published in November last year
14 MARTYN’S LAW
Henry Havis, head of security at ExCeL London and chair of the AEV security working group gives an update on Martyn’s Law
17 HVM
Christian Schneider, hostile vehicle mitigation advisor explains how HVM can be integrated into towns and cities and address other problems besides security
21 BAPCO 2023 PREVIEW
BAPCO returns to Coventry Building Society Area on 7th-8th March 2023, with an exhibition, free-to-attend education programme, dinner, networking lounge and much more
24 STADIUM SECURITY

Lina Kolesnikova, security and crisis management expert looks into the 2022 Stade de France incident including its crowd management, policing, and event management


29 SECURITY & POLICING PREVIEW
Event Preview: Security & Policing, 14-16 March 2023, Farnborough International Exhibition and Conference Centre


32 SURVEILLANCE
Tony Porter on how facial recognition technology can help in the fight against terrorism



36 OFFSHORE OIL & GAS
Based on her Counter Terrorism Studies Masters Thesis, Debbie Rafferty MSc asks“How do energy companies manage and mitigate the security of offshore oil and gas installations?”


38 UK CYBER WEEK PREVIEW

National infrastructure, government and emergency services are prime targets for cybercrime with the sophistication and regularity of attacks on the rise. Are the teams, IT/OT processes and suppliers trained and protected?



40 ACCESS CONTROL
Andrew Sieradzki, group director, Security, at Buro Happold on how to introduce a new access control system
42 INTERVIEW
In a Q&A session with Counter Terror Business, David Owen, the recently appointed country manager for the UK at Heras, talks about a move to a standardised product portfolio and puts the spotlight on perimeter intrusion detection systems (PIDSs)
CONTENTS
Counter Terror Business magazine // www.counter terrorbusiness.com
5 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
Sponsored by

Martyn’s Law plans unveiled
to improve public safety, with measures dependent on the size of the venue and the activity taking place. Recent attacks demonstrate that terrorists may choose to target a broad range of locations. Martyn’s law will ensure that security preparedness is delivered consistently across the UK, ensuring better protection of the public.”
The legislation will work on a tiered model, linked to the type of activity taking place and the size of the expected audience. The standard tier will apply to publicly accessible locations with a maximum capacity of more than 100 people, with the enhanced tier applying to high-capacity locations.
Draft Martyn’s Law Legislation is set to be published in the spring.
The government has said that the law will require venues and local authorities to set out preventative action plans against terror attacks. The law will cover the whole of the UK. The announcement follows a public consultation in which 70 per cent of respondents said that officials responsible for publicly accessible locations should take measures to protect the public from potential attacks.
The Home Office said: “The new duty will require venues to take steps

Protect Duty will now be known as “Martyn’s Law”, after Martyn Hett, who was killed at the Manchester Arena attack. His mother, Figen Murray, has campaigned for Martyn’s Law. Murray said: “Martyn’s law isn’t going to stop terrorism, but common-sense security and making sure venues are doing all they can to keep people safe could mean fewer suffer what myself and the families of Manchester have had to endure.
“I welcome the government’s commitment to including smaller venues and working quickly on this legislation. It is vital we now take the necessary steps to protect ourselves and others wherever possible and I hope other countries learn from this groundbreaking legislation.”
Prime minister, Rishi Sunak said: “The way the city of Manchester came together as a community in the wake of the cowardly Manchester Arena attack, and the amazing work of campaigners like Figen Murray who have dedicated their lives to making us safer and promoting kindness and tolerance, is an inspiration to us all.
“I am committed to working with Figen to improve security measures at public venues and spaces and to delivering this vital legislation to honour Martyn’s memory and all of those affected by terrorism.”
CLICK TO READ MORE
AVIATION PREVENT
Changes to airport security rules

The government has announced changes to airport security rules signalling an eventual end to the 100ml rule on liquids at large airports.
The rules are set to change by 2024, with the installation of new technology at major airports across the UK.
New systems will be installed in most major airports over the next two years.
In a statement, the Department for Transport said: “Not only will it mean greater convenience for travellers – as people will no longer need to spend time taking items out of their bags – but it will also enhance passenger safety, as security staff will have more detailed images of what people are carrying.”
Current rules mean that passengers must remove laptops, tablets and liquids from the cabin baggage. Liquids are limited to 100ml and must be in a clear plastic bag. The government intends to eventually lift this requirement, with the liquid limit to be raised to two litres.



Transport secretary Mark Harper said: “The tiny toiletry has become a staple of airport security checkpoints, but that’s all set to change. I’m streamlining cabin bag rules at airports while enhancing security.
“By 2024, major airports across the UK will have the latest security
tech installed, reducing queuing times, improving the passenger experience, and most importantly detecting potential threats.
“Of course, this won’t happen straight away – this is going to take 2 years to be fully implemented. Until then, passengers must continue following the existing rules and check before travelling.”
Christopher Snelling, policy director at The Airport Operators Association (AOA), said: “This investment in nextgeneration security by the UK’s airport operators will provide a great step forward for UK air travel, matching the best in class around the world.

“It will make the journey through the UK’s airports easier and air travel itself more pleasant.”
Far right referrals outnumber Islamic extremism for second year running
Recently released figures reveal that a fifth of Prevent Counter Terror Programme referrals (1300) to the year March 2022 are flagged for extreme right-wing ideology. This compares with just over 1,000 people flagged over Islamist extremism concerns. This marks the second year in a row that far-right related referrals outnumber those relating to Islamist extremism. Individuals flagged over extreme rightwing concerns also made up the highest number of referrals to the Government’s Channel programme, which escalates cases if individuals are deemed to be at a significant risk of radicalisation. Those displaying signs of extreme rightwing ideology made up 42 per cent of the 802 cases referred to the Channel programme — more than double those flagged for Islamist extremism. Despite being completed in May last year, the Government’s Independent review of Prevent, conducted by Sir William Shawcross, has still not been released. However, leaks have revealed that in the review, Shawcross recommends an increased focus on Islamic extremism, seemingly ignoring hard evidence which demonstrated a rapid increase in right wing extremism.
CTB NEWS
MARTYN’S LAW
CLICK TO READ MORE
TO READ MORE
CLICK
7 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
LEGISLATION
Government legislation targets bomb-making materials

of suspicious activity, adding new substances, providing additional obligations on online marketplaces, and requiring that certain information is recorded when selling regulated explosives precursors to business users. The changes will come into effect on 1 October.

The Home Office said: “Following the Manchester Arena attack in 2017, the government committed to enhancing its capabilities to detect terrorist activity including that which involves the use of bomb making materials.”
The UK Government has laid secondary legislation intended to tighten controls on poisons and chemicals which can be used to make explosives.
The changes are part of updates to the Poisons Act 1972.

The new measures include improving requirements for reporting
COUNTER TERRORISM
New chemicals are set to be added to the lists of reportable and regulated substances, which is intended to prevent access to materials of the highest concern for illicit purposes, but also maintain access for legitimate purposes.
Security minister Tom Tugendhat said: “Around the UK, businesses
and individuals use various chemicals for a wide range of legitimate uses. However, we must also minimise the risk posed by the illicit use of bomb making materials and poisons.
“It is our responsibility to ensure our robust controls of these substances are updated and controls in place against those who wish to abuse them. These steps will do just that.”
Head of Counter-Terrorism Policing Matt Jukes added: “Every year, reports from the public, including industry and businesses, play a vital role in how we tackle the terrorist threat in the UK.
“These new measures will serve to enhance how we received information and intelligence from our communities and also enable us to take targeted and robust enforcement action to keep people safe.”
UK Government publishes counter-terrorism disruptive powers report
The UK Home Office has published its counter-terrorism disruptive powers report 2021.
The annual report provides information and statistical data on the use of disruptive powers and tools used by the government, law enforcement and the security and intelligence agencies to combat terrorism and serious organised crime.
The 44-page report begins with a foreword by Home Secretary, Suella Braverman, who says: The terrorism threat to the UK is ever-present and ever-changing. Our law enforcement and intelligence agencies will have all the resources they need to keep the British people safe. Our world-leading counter-terrorism disruptions system has been made even stronger by this government.”
She mentions the Online Safety Bill which she claims will require companies to better protect people online by removing illegal content.
Braverman talks about the CounterTerrorism and Sentencing Act 2021, which introduced new and longer sentences and imposed stricter monitoring of terrorist offenders on their release.
She also mentions the National Security Bill, which she says “will establish a modern framework for tackling the contemporary state threats we face.”
Braverman said: “Of course, much of the work done by our brave law enforcement, intelligence and security services must take place in the shadows, but we will be as transparent as we responsibly can. British taxpayers need to know that their money is being well spent and that outstanding professionals are working around the clock with great courage and skill to keep them safe.”
The introduction to the report says: “Terrorism remains one of the most direct and immediate risks to our national security. The terrorist threat to the UK primarily emanates from self-initiated terrorists who are unpredictable and difficult to detect, and are inspired to act by terrorist ideology rather than directed or supported by terrorist groups.
“Islamist terrorist groups overseas, such as ISIL (Daesh) and Al-Qa’ida (AQ), continue to play an important role in driving the terrorist threat in the UK; however, at present this role is primarily limited to attempts to inspire would-be attackers. We also face emerging extreme right-wing and single-issue terrorist threats.”
The report contains figures on the use of counter-terrorism disruptive powers in 2021 and explains their utility and outlines the legal frameworks that ensure they can only be used when necessary and proportionate, in accordance with the statutory


functions of the relevant public authorities. The report also includes information on the use of Serious Crime Prevention Orders (SCPO), specifically in relation to terrorism.
The report reveals that in the year ending 31 December 2021, 186 people were arrested for terrorismrelated activity, a decrease of 1 per cent from the 188 arrests in 2020. 57 (31 per cent) of the arrests resulted in a charge, and of those charged, 49 were considered to be terrorism-related. Many of the cases are ongoing, so these numbers can be expected to rise.
As of 31 December 2021, there were 229 people in custody in Great Britain for terrorism-related offences. This includes 154 people (67 per cent) who held Islamist extremist views, 52 (23 per cent) who held extreme right-wing ideologies, and 23 (10 per cent) who held other ideologies.
CLICK TO READ MORE
TO READ MORE
CLICK
CTB NEWS
8 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
Man arrested in connection with airport uranium investigation
“Our priority since launching our investigation has been to ensure that there is no linked direct threat to the public. To this end, we are following every possible line of enquiry available to us, which has led us to making this arrest over the weekend.
BORDER FORCE Inspection of Border Force insider threat begins
A man has been arrested and released on bail as part of the investigation into the uranium found at Heathrow airport in December.
A security alert was triggered at the airport on 29 December, leading to a response from officers from the Metropolitan Police’s Counter Terrorism Command.

The uranium was found in a shipment of scrap metal and police said there was no threat to the public.

Commander Richard Smith, who leads the Met’s Counter Terrorism Command, said: “The discovery of what was a very small amount of uranium within a package at Heathrow Airport is clearly of concern, but it shows the effectiveness of the procedures and checks in place with our partners to detect this type of material.
COUNTER TERROR POLICING
“I want to be clear that despite making this arrest, and based on what we currently know, this incident still does not appear to be linked to any direct threat to the public.
“However, detectives are continuing with their enquiries to ensure this is definitely the case.”
On Saturday morning, officers attended an address in Cheshire, supported by colleagues from Cheshire Police and Counter Terrorism Police North West and a man was arrested on suspicion of an offence under Section 9 of the Terrorism Act 2006. Officers also carried out a search at the property and no material that could be a threat to the public was found.
The man, in his sixties, was taken to a police station in north west England and has been released on bail until April. The investigation is continuing.
CLICK
Counter Terror Policing officers receive New Year Honours
Counter Terrorism Policing officers have been recognised in the King’s first New Year’s Honours List.
Officers have been recognised for their achievements and commitment to policing.
Detective Superintendent Claire Moxon (now retired) received the King’s Police Medal (KPM) for distinguished services to the Metropolitan Police Service.
Moxon has been recognised as a role model for others and for leading the development of the next generation of officers through mentoring and guidance, including both female detectives and officers selected for fast-track promotion.
Police Constable Richard Fox, Counter Terrorism Command and Metropolitan Police Choir received the British Empire Medal (BEM) for services to policing and music.
Counter Terror Policing said: “His dedication to the choir, alongside his policing role, has led to him revamping it in a myriad of ways,
including recruitment and repertoire. His attention to musicality and insistence on excellence ensures consistently first-class performances at high profile events.”
PC Richard Fox said: “Being able to use my lifetime’s hobby to show a different side of the police and work with the talent the Met has to offer is truly inspiring.
“The choir enables the Met to reach places and people it otherwise may not and to raise money for a vast number of charities and good causes.
“Being nominated for this award is truly remarkable and leading the choir musically, an honour. I would like to thank the choir in its entirety for their support, commitment and drive to continually making the choir as successful as it can be.”
Detective Sergeant Paul Griffiths, Counter Terrorism Command received the King’s Police Medal (KPM) for distinguished services to the Metropolitan Police Service. According to Counter Terror Policing:
“DS Griffiths is one of the UK’s lead practitioners for witness interviewing and has dedicated his career to supporting witnesses and victims of major trauma and terrorism. He is considered an exceptional police officer and his work has had enormous impact upon countless people, in the UK and overseas, it has left a lasting legacy for policing.”
DS Paul Griffiths said: “I am truly delighted to be the recipient of this honour. Few achievements are those of a single individual and this reflects the hard work, dedication and wonderful support I have been fortunate enough to receive from family, friends and colleagues, both past and present; over the years.
CLICK TO READ MORE



TO READ MORE 9 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE

CTB NEWS
HEATHROW AIRPORT
“I would also like to acknowledge my War Crimes Team colleagues, who show tenacity, compassion and professionalism when they deal with extremely complex investigations.” TO READ MORE
The Independent Chief Inspector of Borders and Immigration has commenced an inspection of Border Force insider threat. The inspection will focus on measures to identify insider threat in the Border Force and examine how the risk of insider threat is mitigated and responded to. Insider threat was included in the Independent Chief Inspector of Borders and Immigration’s inspection plan for 2022-23.
CLICK
Nick Aldworth of Risk2Resolution and Martyn’s Law campaigner investigates the findings of Volume 2 of the Manchester Arena Inquiry, which was published in November last year


“A LITANY OF FAILURE”
“
Enough is enough.... Saffie’s life is not a practice exercise…. if we’re still learning lessons on terrorism in 2020, nothing will ever change”
These were the words of Andrew Roussos at the start of the Manchester Arena Inquiry in September 2020. Andrew is the father of the Manchester Arena attack’s youngest victim, Saffie-Rose. She was 8 years old when she died. When Volume 2 was published, Andrew and his family learned that there was a ‘remote’ chance that Saffie might have survived if she had received specialist trauma care earlier. I’ve
met Andrew and his family and we remain in touch; I know how strongly he believes that Saffie was a fighter and could have survived. I can only imagine how painful, and enduring, carrying that thought will be.
I don’t know John Atkinson’s family, but the inquiry also found, with greater certainty, that his were survivable injuries with earlier intervention. When you read the detail of his treatment, or lack of it, in The City Room (where the attack happened) and beyond, a lay person is likely to be deeply concerned about how this man came to die.
MANCHESTER ARENA INQUIRY
COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53 10
WHAT WENT WRONG
At a thousand pages long, I’m not sure I even know where to start commenting on this report. It’s taken me the better part of three days to read it, and even then I’ve had to skip through some parts. It will need to be read again and again to fully comprehend its totality.
Every page is a litany of failure, across all three emergency services, their leadership, their processes, and their absorption of learning. In the middle of it, there are failures by individuals to be bold, to be inquisitive and, frankly, to apply even a modicum of common sense. There are some who have excelled, been brave and made positive contributions but, as individuals, were not going to change the outcome.
Saffie and John didn’t get the help they deserved because they found themselves in the middle of an emergency services response full of catastrophic failures of well-established processes and command structures. At some points, I can’t even see the most basic of Gold, Silver and Bronze (GSB) command structures being implemented in a way that provides coherence and compatibility.
Everybody seems to have forgotten the first principle of the Joint Emergency Services Interoperability Procedures (JESIP), colocation, and throughout my read of the document I found my inner-self screaming to everybody, ‘for the love of God, just get some people to a forward control point’.
I’m genuinely shocked at the failure to implement even the most basic principles of incident management, the most basic communication practices, and an abject lack of competence among some. Some of the individual failures are so profound, they are close to being malfeasance. This wasn’t failure of resolving a terrorist incident, this was a failure of core policing. I’m not qualified to comment on what core competence looks like in the ambulance or fire services, but as a casual observer, it’s hard to see leadership and processes that would match my expectation.
Sir John Saunders, chairman of the inquiry and author of the report, has been more compassionate than me by saying that he recognises that people he has named found themselves in the most awful and extreme of circumstances but qualifies this by saying that taking on such responsibilities should come with a requirement to be able to execute them effectively. He is correct and repeatedly highlights that some of those individuals were let down through lack of training. He is of course right. The seeds of failure were not sown on the night, they had been germinating for years
and are systemic across policing. They are fertilised by the inadequate implementation of learning, promotion processes that rely on story telling not competence, and budget. The fact that a significant number of recommendations have been referred to national bodies such as the College of Policing, CTPHQ and the Home Office is indicative of this being systemic national failure. After the report was published, I received an email from a renowned journalist that said, “My biggest worry is that Manchester may well have improved things, but I bet many others haven’t”. Looking at how basic many of these failings were, I sense that their concern is valid.
PREPARATION
One of the alarming things I read in this report was that Greater Manchester Police (GMP) had conducted over 100 relevant exercises in the two years leading up to 22 May 2017. One exercise, about 12 months before the bombing and named Winchester Accord, highlighted that there were weaknesses in how the emergency services in Manchester worked together. Importantly, Winchester Accord highlighted that the Force Duty Officer (FDO) became overwhelmed, but because they were testing whether that role could work from their force HQ and not their control room, they chose not to recognise that this was likely to happen in any environment. That is a lack of common sense and experience.
During Winchester Accord, Greater Manchester Fire and Rescue Service (GMFRS) considered that GMP forgot to include them in a deployment to help evacuate the injured. GMP dispute this, but the evidence in this inquiry suggests otherwise. Winchester Accord, and its failures, have chilling resonance with what happened on the night of 22 May 2017.
The GMP planning team had been decimated by funding cuts, and revisions to important documents, like PLATO plans were done at pace and without the consultation and scrutiny that might make them more likely to succeed. GMP had been one of the worst hit forces, losing roughly 25 per cent of its officers and budget. How can that be right?
The GMFRS consistently failed to include North West Fire Control (NWFC) in exercising and testing thereby missing opportunities to identify weaknesses, especially in
how tri-service communication takes place. GMFRS’s approach to incident command didn’t map directly into the standardised GSB structure, but the greatest failure is probably their practice of not having tactical commanders who operated away from the scene. Had this happened, a tactical commander might have gone to GMP force HQ and obtained situational awareness much earlier than was the case. I’ve worked with many fire services, they are rigid on the rules and procedures that exist and operate to the most hierarchical governance of all three services. You can see this throughout this inquiry. North-west Ambulance Service (NWAS) are not without fault; they didn’t even have a site-specific incident plan for what is one of the largest arenas in the country. Crucially, they operated a non-discretionary policy that non-specialist responders should never go into a PLATO warm zone. On the night this became critical, for despite knowing that some NWAS responders were operating in the City Room, they failed to provide support until much later in the evening. There is so much more in the report indicating failures to learn, prepare, and engage effectively through the Greater Manchester Resilience Forum (GMRF), that it would be impossible to cover all of it in this article. Needlessto-say, the old 6-Ps saying of ‘prior preparation and planning prevents poor performance’ was never truer.
COMMAND AND CONTROL
The GMP Force Duty Officer, Inspector Dale Sexton, is singled out for significant criticism. It is right and justifiable criticism, well evidenced by Sir John. It becomes even more significant because the police were the lead agency for this incident. He failed at so many different stages, it is difficult not to sympathise with the families who believe that he was wrongly awarded for his contribution on that night. But he is not alone in this failure. He was leading a response in a control room where there was insufficient support for him, excessive access to him while he was trying to coordinate the response, burdened with firearms command for an excessive period, and unsupported by his tactical (Silver) commander, T/ Supt Arif Nawaz. T/Supt Nawaz was so out of his depth that he had to be replaced, but by that time, the conditions that he and Sexton had created were probably irrecoverable. E
MANCHESTER ARENA INQUIRY
ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE 11
THE SEEDS OF FAILURE WERE NOT SOWN ON THE NIGHT, THEY HAD BEEN GERMINATING FOR YEARS AND ARE SYSTEMIC ACROSS POLICING
THE STARTING POINT FOR COMMAND FAILURES WERE SET BY GMP FAILING TO DECLARE EVENTS AT MANCHESTER ARENA AS A MAJOR INCIDENT
An added complication was the division of responsibilities between BTP and GMP, although I cannot see that this was the greatest contribution to failure, and those BTP officers deployed to the City room, the seat of the explosion, were brave and did their best.
The starting point for command failures were set by GMP failing to declare events at Manchester Arena as a Major Incident. BTP declared it as such but didn’t inform GMP or GMFRS. Emergency service professionals will know that by declaring a major incident, you immediately create awareness among the other emergency services, and other responders and receivers, such as hospitals and local authorities, all of whom can significantly add to the overall effectiveness.
Operation Plato, the response to a marauding terrorist firearms attack (MTFA) was declared quite quickly by Inspector Sexton and this was described as a right and proper decision, by Sir John Saunders. However, Sexton did not inform the other services of this decision nor undertake the critical element of Plato, zoning. If Plato is to be declared, the creation of Hot, Warm and Cold zones is vital as it is these classifications that define what emergency service works can enter each area. Sexton was not alone in failing to do this. He was subsequently relieved by a groundassigned firearms commander who also failed to grasp the importance of this.
In his evidence, Sexton maintained that he deliberately decided to not inform the other services that he had declared Plato. His grounds for this are not clear, and Sir John highlights many inconsistencies in this, especially the fact that it was being openly referred to in telephone calls and radio messages, and became known to those in the Arena environs. Failure to notify the other services of Plato, was another missed opportunity to get a joint enterprise underway. The inquiry found that critical medical support was denied to those inside the City Room because there was a perception that it was a warm zone, which limits the nature of NWAS staff who can enter. In reality, the GMP firearms team had boldly taken control of the area very quickly and the area was in fact a cold zone. There was a residual concern of a secondary device being present and it took an excessively long time for an EOD search dog to be deployed. However, the fact that NWAS paramedic Patrick
Ennis was allowed by his tactical controller to move in and out of the City Room, suggests a significant inconsistency in the risk assessment.

JOINT WORKING
My view is that the single biggest failure of the night, and one repeatedly referenced in the inquiry, was a failure of the emergency services to follow the Joint Emergency Services Interoperability Programme (JESIP) principles.
JESIP sets out 5 principles that underpin working together. While not mandated, there is an expectation that they work best in the following order: Collocate; Communicate; Coordinate; Jointly Understand Risk; and Shared Situational Awareness. All of the failings that led to inadequate casualty management on 22 May 2017, would have been overcome if all three emergency services had attended a single rendezvous point (RVP) and sent commanders to a forward control point (FCP). So much of this was inhibited by the failure to set the Plato zoning, however it was also set
by individuals who failed to exercise sufficient attempts, and persistence, to get JESIP working effectively. There is also a strong indication that the failures in joint preparedness meant that GMP and NWAS didn’t fully appreciate the role that GMFRS could play in casualty management. This included supporting evacuation with stretchers carried on each appliance. GMFRS has been subject to significant, justified, criticism both in this inquiry and in the earlier Kerslake report. What this inquiry has shown is that their failures are shared by others and, to a significant degree, created by them.
RECOMMENDATIONS
Sir John has identified 149 individual recommendations, a great many of which are then clustered into 21 monitored recommendations. The implication of this is that he will require updates on his recommendations in 3 months’ time followed by witness statements from individuals tasked with making progress, 3 months after that. In summer, he will ask some of those witnesses to give live evidence.
MANCHESTER ARENA INQUIRY
COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53 12
This scrutiny is to be welcomed but I don’t believe it goes far enough. Many of the recommendations are organisation-specific. For example, recommendation 2 states: “BTP should ensure that all its Inspectors are trained to undertake the Bronze Commander role in the event of a major incident”.

When I revert to my journalist friend’s concerns, I wonder how many other police services have the same deficiencies as BTP and would benefit from the application of such learning.
The Home Office, The College of Policing and the National Police Chief’s Council will be unwise to not recognise that these were failures waiting to happen in many places. There is nothing in the evidence that would imply these are problems unique to the North West. Failure to nationalise the opportunities presented by this inquiry would be indicative of how I think learning is treated now inside policing. There is a pervasive attitude of ‘it wouldn’t happen here’ and the implementation of learning is seldom sustained. If it was, the same mistakes wouldn’t keep occurring.
THERE ARE PEOPLE WHO FAIL TO RISE TO THE OCCASION, AND OTHERS WHO EXCEED ALL EXPECTATIONS
FINAL THOUGHTS
While my summary of the evidence is as harsh as the inquiry’s, I do recognise that at the heart of every disaster are people who don’t intend to fail. There are people who fail to rise to the occasion, and others who exceed all expectations. Some of the public compassion and bravery on the night brought a tear to my eye.
Many people will have been adversely affected by the events of 22 May 2017. Some will have experienced physical and mental pain, some will have experienced unbearable grief, and many will carry scars forever. Some will have suffered vicariously, that is the nature of stress.
The best that we can do to honour those who have suffered so much is to not waste the opportunities
that this inquiry has identified. This inquiry shows that so much of what prevented the saving of lives, or the reduction of trauma in those that survived, was entirely avoidable. I can only imagine how some victims and survivors will feel about that. While we continue to absorb this report, we must also brace ourselves for more bad news to come. Both the intelligence and police services could have done more to manage the threat posed by the attacker and his conspirators. Part 3 of the report is unlikely to be comfortable reading. L
https://manchesterarenainquiry. org.uk/report-volume-two
FURTHER INFORMATION
MANCHESTER ARENA INQUIRY 13 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
AEV SECURITY UPDATE: EVENTS AND VENUES
It’s great to have been asked to provide an update regarding security changes for event venues and a lot has happened in the last six months!

Homeland Security released an update on the long-awaited Protect Duty in December 2022. The first change being that the government announced that the Protect Duty will now be known officially as ‘Martyn’s Law’ in tribute to Martyn Hett, who was tragically killed alongside 21 others in the Manchester Arena terrorist attack in 2017.
TIERS
To provide everyone some more clarity on the new legislation, Homeland Security have advised that proportionality is a fundamental consideration for Martyn’s Law, which I think will be reassuring for us all. They are proposing a tiered model linked to activity that takes place at a location and its capacity.
A ‘standard tier’ will apply to locations with a maximum capacity of over 100. The aim is to drive up use and engagement with existing resources that help teams undertake low-cost, simple yet effective activities to improve preparedness. This can include training, information sharing and completion of a preparedness plan to embed practices, such as locking doors to delay attackers’ progress or knowledge on lifesaving treatments that can be administered by staff whilst awaiting emergency services.
An ‘enhanced tier’ will focus on highcapacity locations in recognition of the potential consequences of a successful
attack. Locations with a capacity of over 800 people, at any time, will additionally be required to undertake a risk assessment to inform the development and implementation of a security plan to assess the balance of risk reduction against the time, money and effort required to achieve a successful level of security preparedness – a recognised standard in other regulatory regimes (including Fire and Health and Safety).
They have stated that nearly all places of worship will be placed within the standard tier, regardless of their capacity and the government will reportedly establish an inspection and enforcement regime, promoting compliance and positive cultural change and issuing credible and fair sanctions for serious breaches.
SUPPORT AND GUIDANCE
Dedicated statutory guidance and bespoke support will be provided by the government to ensure those in scope can effectively discharge their responsibilities. Expert advice, training and guidance is already available on the online protective security hub, ProtectUK. It is worth stressing the point that the tiers are being set for capacities, not numbers of attendees. Meaning that an event space with the capacity for over 800 but with only 500 attendees, would still need to prepare using the ‘enhanced tier’ requirements. Legislation for the proposed duty will be brought forward as soon as parliamentary time allows. Martyn’s Law will extend to and apply across the whole of the United Kingdom.
MARTYN’S LAW
Henry Havis, head of security at ExCeL London and chair of the AEV Security Working Group gives an update on Martyn’s Law
14 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
THE EVENTS INDUSTRY
What does this mean to the events industry? Over the course of 2022, myself and my peers in the events world, alongside the Counter Terrorism Business Information Exchange (CTBIE), a counter terrorism forum working with the Home Office, NaCTSO, Homeland Security and the SIA as well as many representatives from non-event-industry associations, discussed how we best share direct source information on Martyn’s Law, but also many subjects that affect our businesses regarding terrorism.
For the events industry, we identified that there are many associations that may not have a voice in this area, but they do have a desire to learn more about the subject directly from the source. As we know, the Protect UK platform bridges many of the gaps we have regarding CT awareness and preparedness, but associations need to be represented in the early phases of new legislation as well as guidance, trends and changes in the best ways of working.
Together with my peers in the Association of Event Venues, specifically the Security Working Group, we spoke to many other event-orientated associations and formed a forum known as the Multi Association Security Awareness Group (MASA). The group came together and represented associations across the events industry to discuss the information disseminated via CTBIE to enhance how we share information. The group is still growing and will have a positive impact on the preparedness of the events industry regarding counter terrorism and security issues in general.
SCOPE
At estimate, some 600,000+ venues across the UK, may be classified as small ‘non tier’, larger ‘standard tier’ and significantly larger ‘enhanced tier’ locations”. The most recent information provided from the government demonstrates that Martyn’s Law is likely to affect nearly all event

venues in all tiers. We can see that the Home Office are already providing us with many of the resources we need to do this through CT Policing support and, more importantly, through the Protect UK platform. Where we need to develop ourselves as an industry is through working closely with all stakeholders to ensure we develop a risk-based plan to ensure events like Manchester Arena Attack do not happen again and, if in the worstcase scenario they do, we are prepared to act quickly and decisively to contain the incident and reduce the loss of life.
TAKE ACTION NOW
The output from the Manchester Arena Inquiry so far looks at many steps that could have been taken to protect and prepare venues from terrorist incidents and the aftermath and the learning is already out there for everyone to take appropriate responsibility and start making realistic changes now. Waiting for legislation to take effect could still take several years but with the understanding that is available now, venues, organisers, suppliers, businesses and associations need to take the steps they can to ensure that we are doing all we can, as one entity, to ensure the safe running of our events and protecting the public we open our doors to on a daily basis.
The question of how still hasn’t fully taken form and will take time to fully understand but collaboration at all levels will be the key to this endeavour. Those waiting for the Competent Person Scheme to be released by the Home Office and for Martyn’s Law to be cleared through the government need to see that there is a very real and substantial threat from terrorism in the
UK and now is the time to take some realistic and balanced changes within the ways we work as the responsibility for this sits with everyone involved whether directed by law or not. Subtle changes can make a world of difference including working with NaCTSO’s Safer Business team, and completing thorough, but not complicated risk assessments looking at the major threat types. In the current environment, I would like to see every Security Officer thoroughly trained in Behaviour Detection Recognition and First Responder Trauma Care, but this isn’t realistic for every company and every venue, but having robust security plans, preprepared and practiced emergency procedures and conducting rehearsals will ensure that, should the worst happen, everyone is ready to react and reduce the impact. The amount of free training available such as Action Counters Terrorism and See, Check and Notify is incredible and easy to get hold of. There’s a lot more to come from the Home Office and learning and enhancing our processes, policies and procedures should be an ongoing endeavour however, we are at a point now that change is happening and groups such as CTBIE, MASA, AEV, NAA, AEO, ESSA and many others are working together closely to influence those changes across the industry. It will take time, but the changes have begun, and I am proud to be a part of the changes many of us are making now, for the better. L
www.aev.org.uk
MARTYN’S LAW
INFORMATION
FURTHER
15 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
THE MOST RECENT INFORMATION PROVIDED FROM THE GOVERNMENT DEMONSTRATES THAT MARTYN’S LAW IS LIKELY TO AFFECT NEARLY ALL EVENT VENUES IN ALL TIERS



Christian Schneider, hostile vehicle mitigation advisor, explains how HVM can be integrated into towns and cities and address other problems besides security
SYNERGIZING FUTURE URBAN DESIGN

The competition for coveted residents, visitors and businesses has always been won by those cities that, as innovative pioneers, offer their clientele the highest level of quality of life. Those cities prevail because they are perceived as more innovative, secure, sustainable and healthy than their counterparts.
Urban quality of life is inextricably linked to a high level of perceived security, which gives people the sense of well-being they often crave in order to be carefree, creative and productive. As such, even the slightest emotionally perceived inkling of terror and crime is diametrically opposed to this desired state, a situation that underlines the importance of urban security.
Hence, this article discusses an important aspect of urban security, the structural protection of urban spaces against the growing threat of hostile vehicle attacks and its intelligent implementation to also overcome a number of further urban challenges simultaneously.
How do innovative cities fund their ambitions in the face of scarce resources and ever-growing tasks? Perhaps, just in the same way as successful business enterprises do, through the constant search for innovations and the prudent use of simple, multifunctional and self-supporting systems! However, it would be rather silly to assume that in an increasingly complex world, adding more complexity will lead to more sustainable solutions. Most of the time, the opposite holds true. This applies to all areas of future cities, regardless of whether we are talking about highly complex requirements in the implementation of pedestrianisation or protecting publicly accessible locations against terrorism, extremism and the growing use of vehicles as weapons (VAW) in acts of violence. In all cases, the solution is to look at many municipalities most important challenges in a comprehensive way and then tackle them with most simple and cross-sectoral measures. This not only saves time and money but also ensures
the smart (multi)use of valuable resources for installation and maintenance.
SOLUTIONS TO CITY PROBLEMS
Most cities are currently facing an overwhelming number of urgent demands. These include an increased desire for perceived security, urbanisation, climate change and urban warming, particulate pollution management, outdated infrastructures, ageing populations, pedestrianisation, social tensions and a growing number of despicable attacks against police and emergency services. In addition, staff shortages, inflation and falling revenues are not really helpful to cope with these mammoth tasks. It is therefore essential to find sustainable solutions to simultaneously solve as many of the above-mentioned tasks as possible while at the same time requiring as little of the scarce urban resources as possible.
HVM
A promising way of killing several birds with one stone has recently E
HVM
17 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
emerged in the field of Hostile Vehicle Mitigation (HVM).
While HVM’s primary task surely is to protect people from extremists who are misusing vehicles as weapons to run people over or harm them through shrapnel dispersion. Still, modern HVM schemes also ought to offer the very opportunity to combine the potential resources of a city, nature and technology in such a smart and cross-sectoral way that solutions to the plethora of demands can in fact benefit from it. Hence, we smartly solve five issues with just one solution. Anyone who nowadays is just thinking of hostile vehicle mitigation in terms of bollards, barriers and steel constructions is kindly advised to get an update from a national Counter Terrorism Security Advisor (CTSA) or an experienced and impartial Hostile Vehicle Mitigation Advisor (HVMA). Modern, innovative Vehicle Security Barriers, so-called VSBs, are now much more efficient than they recently used to be. Whereas in the past, HVMAs had to apply expensive and space-consuming additional measures to compensate for sometimes insufficient retention capacity of standard VSBs (usually Ekin approx. 1,850kJ), the latest barriers are now four times as powerful (Ekin 7,400 kJ), so that they effectively stop all heavy lorries (24t. plus) approaching at full speed within a few metres. Moreover, they now no longer require deep foundations that interfere with subterranean infrastructure to achieve this impressive performance. Ultimately, this is an immense economic and architectural advantage! However, compared to the latest generation of multi-use-planters these new barriers still are just an evolution in terms of performance and foundation, without
offering any other additional benefits. A real revolution, in the sense of our initial question of increasing the quality of life in modern cities, however, comes with this new generation of multifunctional, and greenable planters, the so-called “Green Beans”. These are an impressive innovation of highperformance raised beds, that are not only architecturally largely free in terms of shape and dimensions as well as choice of materials and appearance but also offer significantly more benefits than just keeping vehicles out. Urban planners, security authorities, emergency services and security architects may now make use of the multitude of “Green Beans” additional positive technical, climate-protecting, water-storing and, of course, economic capabilities that can be optimally adapted to the respective local needs. The many benefits of these barriers could well be considered a disruptive technology, that now opens up entirely new and creative possibilities for urban planners and security professionals.
CROSS-SECTORAL COOPERATION
However, the key to success, as so often, lies in the cross-sectoral cooperation of different offices and authorities, which still goes somewhat beyond the pure consideration of security and urban design. Synergies can be created through comprehensive cooperation, which can even range from the promotion of inner-city biodiversity and spontaneous, virtual unsealing of urban areas to urban climate cooling, the creation of resilient

sponge cities, or the relief of the city sewage system during heavy rain falls.
But before we now go to deploy this new generation of VSBs, it is particularly important to understand that security is not a product but a process. Hence, security is not resulting from merely placing barriers somewhere but from their proper application. Hostile vehicle mitigation is an instrument of vital security and therefore is regulated by standards and guidelines. Thus, its application is much more demanding than just an installation of simple traffic control measures, e.g. aiming to avoid car park search traffic or the like. More often than not this still is being confused and therefore leading to serious consequences in terms of effectiveness and cost explosion. Hence, the question that rightly arises here is; “how can such a project, which is supposed to simultaneously address so many requirements of future-oriented cities, be planned and implemented properly”? The simple answer is “with foresight and balance”. In this context, “balance” is about constantly keeping the three core principles of security design in mind and bringing them into synergetic harmony with one another. For without balance and synergy, the full potential of an action can neither be fully recognised nor exploited. In the successful handling of securityrelevant projects, “foresight” means that at any preparation of a project the three core principles of process, cooperation and proportionality are duly taken into account.
HVM
18 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
MOST CITIES ARE CURRENTLY FACING AN OVERWHELMING NUMBER OF URGENT DEMANDS
LEGISLATION
The core principle of “process” focuses on the task of clarifying the project aims, expectations, limitations, budgets, stakeholders, project participants, project structure and process organisation as well as compliance with relevant legislation, standards, and guidelines.
In Europe, the relevant standard of Hostile Vehicle Mitigation currently still is ISO IWA 14, which will soon be superseded by its updated version, ISO22343. Just Germany, due to its federal structure and recent extremely negative incidents, got its own HVMregulations, DIN Spec 91414 guideline, stipulating that any HVM measure must be supervised by an impartial, experienced and trained HVMA or CTSA.
The core principle of “cooperation” considers the fact that almost every successful security architecture owes its success to the good cooperation of experts from all affected areas, who were involved in the project from the very beginning in order to jointly find balanced solutions in the sense of project aims and best user experience later on.
And so, the third core principle, “proportionality”, is indispensable, because throughout the entire project, the parameters of security level, aesthetics, utility and added value, sustainability and costs shall always be balanced.
Securing the urban future increasingly is a question of taking a holistic view
on urban tasks and the art of bringing them together; synergistically and economically. Fortunately, nowadays, perceived security and a high quality of life are no longer about dominant “fortress designs” but can once again become central elements of aesthetic urban design, have an inspiring effect and at the same time exert a positive influence on a multitude of other municipal tasks. All that is needed is a commitment to make use of the potential of available innovations and to fully exploit it through cross-sectoral cooperation between municipalities, security professionals and business.
Modern HVM therefore is an active contribution to the well-being of people and a liveable, urban future. L
About the author
Christian Schneider founded the INIBSP “Initiative Breitscheidplatz” in 2017 after the terrible Vehicle Ram Attacks of Nice and Berlin, as a nonprofit expert forum aiming to quickly provide relevant HVM know-how to decision makers in Germany.
Since then, his enterprise has developed into the leading consultancy on the topic in German-speaking countries. Together with international experts and local authorities, he developed and implemented numerous HVM schemes for the protection of entire city centres, airports, critical infrastructures, stadiums and public spaces. Schneider

also is member of HVM standards and norms committees, and author of multiple articles on the topic of HVM. His commitment and devotion to protecting people form hostile vehicles earned him the nickname “PollerPabst” (Bollard Pope) in Germany.

FURTHER INFORMATION https://inibsp.de/
HVM 19 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
A SAFER, MORE PRODUCTIVE WORKFORCE
For over 50 years, Tait Communications has helped Public Safety and Transport organisations around the world serve their communities.


Developing a deeper understanding of our clients’ needs, we improve situational awareness, worker safety and organisational efficiency.
As critical industries increase their reliance on data and applications, our innovative solutions enable agencies to take advantage of both broadband and radio networks, in user-friendly converged devices.


Visit us to see how this new range of solutions can help you.

more at taitcommunications.com/BAPCO
Learn
US AT BAPCO 2023
JOIN
AT STAND F40 Coventry Building Society Arena, COVENTRY, 7–8 March 2023
BAPCO 2023 RETURNS IN MARCH!
BAPCO returns to Coventry Building Society Area on 7th-8th March 2023, with an exhibition, free-to-attend education programme, dinner, networking lounge and much more
Following on from last year’s incredibly successful show, the annual BAPCO Conference & Exhibition is back with a vengeance in Coventry this March. As ever, visitors to the event will have the chance to increase their knowledge by attending the sector’s most informative and useful educational conference programme. They will also be able to experience all the latest tech on the exhibition floor, via numerous product demonstrations and launches. At the same time, BAPCO 2023 will also offer a range of new features, including the Vehicle Demonstration Zone. Also new for this year are the themed BAPCO ‘Tech Tours,’ which will enable visitors to see some of the most cutting-edge kit the industry has to offer being demonstrated up-close. We can’t wait to welcome you to Coventry in March.


WHERE AND WHEN?
Coventry Building Society Arena, Judds Ln, Coventry CV6 6GE - Tuesday 7th- Wednesday 8th March, 2023
What’s on at BAPCO 2023?
EXHIBITION
BAPCO 2023 will bring together the entire UK public safety communications sector to experience the latest equipment and systems, develop important business relationships and generate new opportunities. Get hands-on with new equipment and speak to experts on how to transform your organisation and reach your goals. Visitors will have the opportunity to network with Platinum Sponsor Motorola Solutions, Gold Sponsors Saab and Hytera and Silver Sponsor Cradlepoint. We also have an exciting line-up of new exhibitors for 2023 including AmphenolProcom, CMI Corporation EMEA, 3S Group, CloudRF and many more. With over 80 brands in one place and thousands of innovative products and solutions to choose from, BAPCO is the best place to explore the latest public safety communications technology.
EDUCATIONAL CONFERENCES
Expand your knowledge through free-to-attend conference sessions, offering a huge range of cutting-edge presentations, delivered by some of the most respected thought leaders in UK public safety comms. The programme will consist of three streams taking place across two days, and will be packed with keynote addresses, best practice discussions, technology updates, panels and debates. The conference will cover all the big issues facing the UK public safety communications technology sector, from the evolution and continued exploitation of current solutions to the potential role of ‘future technology’ such as AI. BAPCO 2023 will also include vitally important updates on the ongoing Emergency Services Network roll-out.
VEHICLE DEMONSTRATION
ZONE (NEW FOR 2023)
New for 2023, this is a dedicated area where you can witness firsthand some of the vehicles which are currently in use by UK public safety. E
BAPCO 2023 PREVIEW
60+ SPEAKERS 80+ EXHIBITORS 40+ CONFERENCE SESSIONS 21 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE Sponsored by
Tait Communications at Bapco 2023, Stand F40

A safer, more productive workforce
For more than 50 years, Tait has been designing, delivering and supporting critical communications networks for public safety, transportation and utility customers around the world. Our mission is to help our customers stay safe and connected to essential information through wireless voice and data. We are particularly proud to have been awarded the contract to build and maintain a secure nationwide Public Safety Network (PSN) across New Zealand. With more than 450 sites, this network will be one of the largest P25 networks in the world.
Breaking down communications boundaries
Our innovative solutions enable public safety agencies to take advantage of






both broadband and radio networks, in user-friendly converged devices. Whichever devices or networks best suit your team, TAIT AXIOM Broadband Solutions can bring anyone into the conversation. Learn how your organisation can benefit from Tait DMR devices on the incident ground, alongside Tait AXIOM Broadband devices and the PTToX Push-toTalk-App on smart devices. Don’t miss Richard Russell’s presentation on day 2 and get to know on how we take the next step in connecting the fireground. Click below to book your demo with a Tait expert at BAPCO now! L
FURTHER INFORMATION
https://go.taitcommunications. com/bapco2023



22 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
www.counterterrorbusiness.com VISIT OUR WEBSITE TO SIGN UP FOR YOUR FREE DIGITAL SUBSCRIPTION 20TH APRIL 2023 10AM LIVE ONLINE SECURING MARITIME BORDERS HUMANE NATIONAL SECURITY REGISTER NOW Get the inside track from industry experts In association with:
This interactive zone is intended to facilitate discussion around invehicle connectivity, while at the same time demonstrating a range of cutting edge solutions.



TECH TOURS (NEW FOR 2023)
Individually themed, these tailored, interactive experiences will provide the perfect opportunity to explore the new and innovative products offered by our exhibitors.
Escorted by a member of the event team, each themed tour will visit a selection of companies working within a particular product space (for instance, two-way radio, control rooms and so on), who will offer demonstrations. The tours are intended to help visitors compare the best products and solutions to suit their business needs.
THE BAPCO ANNUAL DINNER
The BAPCO Annual Dinner is one of the most important events in the UK public safety calendar. As ever, it will be attended by a veritable who’s who of influencers, thought leaders and personalities from across the sector.

Guests will enjoy an evening of entertainment and great food whilst networking and catching up with colleagues and friends, old and new. The BAPCO Annual Dinner will take place following the conclusion of the exhibition and conference’s first day.
NETWORKING LOUNGE
2023 will see the return of the Networking Lounge. This is a purpose-built space at the centre of
the exhibition, enabling attendees to take time out and catch up with valued colleagues, old and new over a coffee and snack. Register free by visiting the BAPCO website below or scanning the QR code. L

www.bapco-show.co.uk

FURTHER INFORMATION
23 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE BAPCO 2023 PREVIEW Sponsored by

STADIUM SECURITY 24 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
CHAMPIONS LEAGUE FINAL: WHAT WENT WRONG?
France is one of the longest established and most reliable hosts of major sporting events. However, the security of future events and the country’s way of dealing with big sporting events was challenged on 28th of May 2022 during the UEFA Men’s Champions League Final between English team Liverpool and Spanish team Real Madrid. The event took place at the Stade de France (Saint-Denis), the biggest stadium in France. The high-profile incident involved legitimate ticket holders not managing to get into the match; people without tickets managing to get in, bypassing the controls; and legitimate visitors being confronted by the police or by local gangs (depriving visitors of their tickets and valuable belongings on their way to and from the match). The official reactions, and especially, the early comments on causes and circumstances, were disastrous and led to a loss of confidence. E

STADIUM SECURITY
Lina Kolesnikova, security and crisis management expert looks into the 2022 Stade de France incident including its crowd management, policing, and event management
25 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
There are many questions to be raised on the incident itself, as well as legitimate concerns on how France will deal with the upcoming men’s Rugby World Cup this year and the Olympic Games of 2024. The observed approach saw supporters regarded and treated as a threat to urban security, no organisation with a clear leadership role in the event management, flaws in coordination, crowd control, basic street security, crisis response and communication and left many people in a profound state of shock.
The aim of this article is to look at the sequence of failures at pre- and post-event periods, in the hope that lessons will be drawn and forthcoming events in France will employ different approach(es).
PRE-EVENT (BEFORE THE MATCH):
Most but not all issues making up this Paris incident started well before the match. There were even issues which originated far away from the match venue. The following talking points could be listed in no particular order: not-as-intended information and guidance for the route from the RER station to the stadium; access denied to spectators with tickets; resale of stolen tickets by personnel; access of ticketless opportunists to the match and access to the stadium by a ticketless mob (what about the terrorist threat?). Other talking points include: slow pre-screening; understaffing and unexperienced staff; no crowd management initiatives from police; excessive use of police force oppressing supporters; delay of the match for 36 minutes and no drinking water for people stuck waiting for three hours.
Two fan zones were set up: close to the venue, in Saint-Denis for supporters of Real Madrid (capacity 6,000 people) and, much farther way, for Liverpool supporters in more central Paris (capacity 44,000). At 5pm, fans started to move to the Stade de France.

For people from the first fan zone, it was a 15 minute walk to the stadium. This went reasonably well, though there were some attacks by criminal groups on Spanish supporters already reported around that time.
Those who were in the centre, many of whom were Brits, had three options for public transport: line 13 of the metro (not as convenient as the RER), RER D, and RER B (“RER” is an acronym for Réseau Express Régional, or Regional Express Network, and refers to the rapid transit system which serves Paris and its surrounding suburbs).
Coincidentally, and revealing a lack of control and monitoring, the most convenient and the would be mostused line, RER B, went on strike that day. Assumingly, it still provided a limited service as 6,200 people still
used RER B. Meanwhile c.37,000 used RER D to get to the venue.
The high-level logistics planned for users of line RER D to use the same route (from the station to the stadium) as passengers of line RER B. This route goes along the rue Stade de France, which is 20 m wide and designed for a crowd. The ticket prefiltering was also set up on this street.
Translation from high-level planning to the actual ground did not go well though, as planners probably did not walk the route to see how it looked and did not ensure the correct guidance and communication. Fans who left the RER D station ended up following a different route. First, they took the presumed correct direction. But 200 m down the road, they “naturally” followed a road sign, which indicated to turn left and had Stade de France marked on it. The law enforcement personnel present at the site did not correct them as they did not consider “providing guidance” to be part of their responsibility, or, possibly, they were not aware they may need to insist on fans taking a certain route. Then the crowd crossed the underbridge passage and arrived at a location that was not the one planned for the main crowd. A bottleneck quickly formed, as fans arrived at the limited throughput pre-filtering location and subsequent controls, equipped with only up to 10 lines maximum. This is where the main troubles began.
First of all, the facility was heavily understaffed and those who were hired for the match were rather inexperienced. As people continued to arrive, the lines were not followed. People then dispersed onto the adjacent national road, which was partly blocked by police vehicles. The instructions were very controversial: people at the head of the line were told to push back but people at the rear were instructed to push forward in order to get out of the road. Prescreening was handled by Stade de France and there were many issues with the technical side of the equipment. A struggling mass of people and chaos… This moment saw the arrival of locals and migrants who provoked fighting, and took the opportunity to mug people with tickets and the use of these stolen tickets to enter the stadium via other entrances, a bit later. The chaos also enabled ticketless opportunists to climb over the fence. There were also reported cases of the re-sale of stolen tickets by stewards. There were also people with disabilities among the spectators, who were robbed. They were left neglected by the organisers.
At this moment, the police stepped in. As Paris Police chief Didier Lallement explained later, they were scared that the crowd could turn unmanageable and those who were closer to the fences could be crushed. Police
closed the gates and started to push people back from the fences. Police gassed people who did not show any hostility, including families with children and people with disabilities. At least, 2,700 Liverpool fans (with families, kids, etc.) were unable to attend the match even though they had valid tickets and showed up in time.
POST-EVENT (AFTER THE MATCH)
Needless to say, that for thousands of those robbed fans and those who were not allowed in, the match was over and their experience of the event was completely ruined. But for those who managed to get into the match, there were bad surprises to come too. There were reported attacks before the match but there was an avalanche after the match, with criminal attacks on spectators by local gangs and migrants and a lack of police force against criminal groups.
Spectators (British, Spanish and others) were attacked both before and after the match, especially those who had to go to the stations or to the carparks. Many people were beaten, mugged, assaulted physically and verbally. Unfortunately, there was no evidence of active police measures to stop this. It has even been alleged that, more than once, law enforcement personnel ignored attacks that they could have seen.
The situation leaves a large open question on how France will handle larger and longer forthcoming events, if a one-off event took that turn. On a positive note, the French government has promised to increase the number
STADIUM SECURITY 26 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
of police force by extra 1000 agents in Paris before the Olympic Games. Whether or not this will be sufficient for securing larger multi-venue and multi-day events, time will tell.
POST-EVENT (REACTION)
If the above was not enough on its own to raise eyebrows and concerns, the authorities nailed it by revealing the destruction of surveillance footage, which could otherwise serve as evidence; voicing the blame strategy and publishing a questionnaire for British and Spanish supporters, which ignored the issue of excessive use of police force.
Some of the most severe criticism was levelled at the French authorities –particularly, the French minister of the interior, Gerald Darmanin, and Paris Police chief Didier Lallement – who, the day after the incident, blamed British fans and ticket scammers for the issues. Darmanin claimed that about 30,000 to 40,000 British supporters had showed up for the match, either without tickets or with fake ones. Such high numbers attracted immediate scepticism from security professionals and football clubs alike.
An inquiry was arranged and conducted. On 13 July, the French Senate published its own 14page investigative report entitled ‘Champions League Final: An Unavoidable Fiasco’. The report says that police used tear gas on the crowd, including children and other innocent bystanders. People had been bitten and pickpocketed, but the police were unable to stop such acts, nor arrest the perpetrators, the
report continues. The French Senate went on to say it hopes that the report will help avoid similar incidents at sporting events hosted by France.
In democratic societies, the postcrisis phase is increasingly marked by intense politicization. Even while the crisis is still unfolding, the drama of accountability and blame begins. This situation creates a real challenge with regard to accountability and an attempt to avoid blame by political leadership. We might, therefore, witness another crisis in the aftermath of the original crisis event.
Early statements by the French authorities, issued shortly after the event, can be regarded from the point of view of a blame game in that there were attempts to find excuses or scapegoats. With emerging evidence and the Senate report, the blame management strategy has once again proven to be ineffective and counterproductive. Could the authorities have anticipated such an outcome, and if so, why did they continue to pursue this course?
First, the negative image of British fans could have played a role, even though British organisations have done a lot in recent years to improve fans’ behaviour. That perception legacy could be one of the sources of the early blame, as it is likely that the French authorities did not have their fingers on the pulse of related developments in the football industry preceding the event.
Secondly, underestimation of the impact upon the gathered people might have led to a temporary belief that this was about a ‘voiceless
crowd’. In reality, modern information dissemination led to the almost instant ignition of comments on social networks and the topic became viral. The ‘crowd’ included multiple prominent individuals from the world of football and beyond, who are used to high-profile events and are not shy of speaking up.
Thirdly, many fans are not a bunch of isolated individuals, but members of organised football groups that operate with, and are supported by very rich football clubs. Such organisations, certainly the wealthier football clubs, have legal and communication departments, and these did not leave their organised fans defenceless. They raised their voices in defence of the affected fans and joined the loud public outcry.
To draw a line under the blame game, UEFA finally reported only 2,800 fake tickets counted overall, a far cry from the initial claim by French authorities. Something else to pay attention to, too…
When we talk about security of a sport event with mass attendance, securing the venue is not enough. One should also look at the area where the sport facility is located. Stadium and event operators can no longer consider the space outside the stadium as the responsibility of others. These areas form crucial elements to the safe arrival and departure of spectators and need full and open discussion with all stakeholders to develop coordinated plans for their safe management. The proof of that was seen last May. L

STADIUM SECURITY 27 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
GROUNDBREAKING WEAPONS DETECTION SYSTEM



THREAT DETECTION THROUGH ELECTROMAGNETICS www.ceia.net GAME DAY AT RECORD SPEED. • QUICKLY AND AUTOMATICALLY SCREEN GUESTS with their backpacks and bags • EXTREMELY HIGH THROUGHPUT with near-zero nuisance alarms
DETECTS HANDGUNS AND MASS CASUALTY THREATS, such as high caliber assault weapons and IEDs
EASY TO RELOCATE AND QUICK TO INSTALL: Less than 1 minute setup time • INDOOR AND OUTDOOR OPERATIONS
more information, contact your CEIA representative at info@ceia.co.uk or call us today at +44 1789 868 840 • +44 7887 421 410 NEW OPENGATE_advert_FC060K0480v1000gUK.indd 1 08/03/2022 08:31:08
•
•
For
Event Preview: Security & Policing, 14-16 March 2023, Farnborough International Exhibition and Conference Centre

SECURING OUR FUTURE SAFETY AND PROSPERITY
The countdown is on to Security & Policing, the Official UK government global security event, which returns to the Farnborough International Exhibition and Conference Centre between 14-16 March 2023. Hosted by the Home Office’s Joint Security & Resilience Centre (JSaRC), Security & Policing offers a world‐class opportunity to meet and discuss the latest advances in delivering national security and resilience with UK and overseasgGovernment officials and senior decision makers across the law enforcement and security sectors. The closed event welcomes over 300 exhibitors and 6,000 attendees across the three days, with all exhibitors and visitors subject to Home Office approval.
THEME
The overarching theme for this year’s event is ‘Securing our future safety and prosperity’, through advancing National Security and Resilience, Policing Innovation and Protecting our People and Places. Attendees will be able to learn about the innovations, policies and cutting-edge technology available to respond to the latest and future security challenges and threats.
EXHIBITION & PROGRAMME
Security & Policing (S&P) 2023 will offer an extensive exhibition of over 300 leading exhibitors from across the supply chain, showcasing best-in-class security solutions and capabilities to address a variety of procurement needs. Another key benefit of participation in S&P is to gain insight and help contribute to thinking and driving change in government and law enforcement. Alongside the main exhibition, there will be an impressive programme of keynotes led by senior UK government officials, policing officials and industry speakers, across the main keynote theatre and Fusion Forum.
ZONES
New for 2023, the Innovation Zone brings together government, industry and international partners to collaborate on how innovation, science and technology (IST) can help solve the latest security and policing challenges. Government partners will present technical problems and demand signals on current and future capability gaps to engage with industry, as well as how they can provide gateway access to funding and collaboration opportunities to deliver IST solutions. E
SECURITY & POLICING PREVIEW
29 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE 08:31:08


Visitors can also meet and engage with officials and operational staff from participating government departments, as well as experience hands-on demonstrations of the latest innovations and technologies.
This year’s event will feature an expanded Government Zone at the heart of the show floor. In addition to the usual blend of key government partners participating in the Government Zone, there will be a unique opportunity to get exposure to and connect with the people working in Border Security and Policing across government within two dedicated zones alongside the core area.
The Border Security Zone will bring together key government officials across the full border security journey. From overseas, at the border and in-country, to goods and people, land, sea and airports, you can learn more about some of the most innovative projects and programmes currently happening within government.
The Policing Zone will bring together key law enforcement agencies and officials to showcase the latest developments including projects and programmes across our key themes; Policing of the future, Specialist capabilities, Shaping the future workforce and International perspective.
The Government Zone gives visitors and exhibitors access and exposure to senior decision makers and policy
developers in Government, and is the place to meet and engage with officials and operational staff from a range of UK Government departments and law enforcement agencies to hear their latest priorities, developments and collaboration opportunities.
IMMERSIVE EXPERIENCE
JSaRC’s renowned Live Immersive Experience returns to this year’s event, providing visitors with a narrative-led, content-rich, immersive experience, which gives an insight into technologies and solutions to solve the latest and future security challenges and threats. This year’s immersive experience will be based on the timed escape room model which has progressive stations with a single solution. The challenge will focus on a team being required to successfully navigate several stations
Threat detection from CEIA
CEIA (Company for Electronic Industrial Automation) was founded in 1962 in Italy when it began production of metal detectors for the textile industry, since then our product line has grown covering many sectors from military and security to pharmaceutical and food. Within the security industry, CEIA provide a range of sophisticated technologies designed for the detection of threats including explosives, IEDs, weapons and radioactive materials. CEIA holds more than fifty national and international patents. The manufacturing site is in Italy with offices in the UK, Europe and the US.
CEIA systems are installed in more than 80 per cent of airports worldwide and over 95 per cent in the UK including Heathrow and
Gatwick. Currently around 20 per cent of CEIA S.p.A staff are engaged in research and development, in activities to meet new legislative changes and changing threats. Sectors we cover include: Aviation Transportation; Cargo Screening; Law Enforcement; Court and Prisons; Event Security; Loss Prevention; and Arena Security. Some of our latest technologies available to see on our stand are:
SAMDEX Shoe Scanner, for the screening of passengers’ shoes; OPENGATE for the automatic screening of individuals including their backpacks and bags; and
EMA-4 LEDS System, designed to check sealed and unsealed liquid containers carried by passengers. L
FURTHER INFORMATION
www.ceia.co.uk

– each showcasing different security skills that can be employed as part of an effort to stop a terrorist incident.
To complement the live event and enhance the visitor experience, Security and Policing+ will also provide event attendees a secure, online platform for attendees to watch back content on-demand, connect and arrange meetings at the event and browse exhibitor profiles. Limited exhibitor space is still available and visitor applications close on Friday 10 March 2023. To find out more, apply for a free visitor pass or enquire about exhibiting at the show (criteria applies), visit the website below. L
FURTHER INFORMATION
http://securityandpolicing.co.uk
SPX CommTech –A smarter, more secure future for all
SPX CommTech, compromising TCI and Enterprise Control Systems (ECS), innovates specialised technologies within the Radio Frequency (RF) spectrum to ensure a smarter, more secure future for all.

BLACKTALON is a scalable Counter-UAS solution that detects, tracks and defeats hostile UAS, and is proven in the UK and internationally, including in conflict across Eastern Europe. CommTech’s Tactical Data Link portfolio allows intelligence gathering agencies, special forces, police, emergency response, and security teams to securely and reliably transfer video and data between enabled-
aircraft and ground teams over long distances for airborne Intelligence, Surveillance and Reconnaissance (ISR).
Combining decades of technology innovation and expertise with agile and collaborative teams, SPX CommTech delivers sustainable and exceptional results to customers and partners across the globe and in civilian, law enforcement, intelligence and defence environments. For more information visit stand D61 at Security & Policing L FURTHER INFORMATION
SECURITY AND POLICING IS THE IDEAL COMBINATION OF COLLABORATION WITH AND ACCESSIBILITY TO FIRST RESPONDERS, GOVERNMENT, INDUSTRY, AND ACADEMIA ON AN INTERNATIONAL LEVEL. IT ALSO PROVIDES A GREAT OPPORTUNITY TO VIEW NEXT GENERATION INNOVATIVE TECHNOLOGY.”
SECURITY & POLICING PREVIEW
- S&P VISITOR SURVEY 2022
www.tcibr.com
www.enterprisecontrol.co.uk
31 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
By Tony Porter, previous surveillance camera commissioner for England and Wales and current chief privacy officer at Corsight AI
FACIAL RECOGNITION TECHNOLOGY IN THE FIGHT AGAINST TERROR
In his most recent review of London’s Preparedness for a Major Terrorist Attack published in March 2022, security expert Lord Toby Harris deemed London “significantly better prepared for a terrorist attack” compared to 2016. Despite the encouraging progress, Lord Harris notes that the last decade has seen the threat of terrorism shift from organised groups of attackers to lone extremists acting independently. Notably, police believe that the perpetrator of the 2017 Manchester bombing acted alone at the time of the attack. Like finding a needle in a haystack, the human eye remains illsuited to identifying one suspect in a crowd. Technologies like Facial Recognition and Visual Search have long been at the forefront
of the counterterrorism conversation, with the Met beginning operational use of Live Facial Recognition in 2020. Beyond comparing subjects with existing criminal databases, advancements in AI allow surveillance systems to run visual searches monitoring patterns of irregular behaviour. For example, someone leaving a bag unattended for an extended period or returning to a site regularly to take photographs. This information can then be used as the basis on which to perform actions, e.g. to notify officers to conduct a stop and search. Such use cases of facial recognition can play a key role in improving the efficiency of law enforcement in identifying and preempting potential terror attacks.

SURVEILLANCE
32 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
OUTDATED CONCERNS
Unsurprisingly, the deployment of Live Facial Recognition (LFR) by law enforcement has stoked furious opposition from campaign groups over concerns around the technology’s accuracy, privacy and bias. With fourteen organisations including Big Brother Watch, Liberty and Black Lives Matter UK writing an open letter to Metropolitan Police Commissioner Sir Mark Rowley requesting an end to the use of facial recognition technologies by the police force. Published in September last year, the letter characterises the technology as “privacy-eroding, inaccurate and wasteful.”
Concerns around inaccuracy, bias between gender and ethnic minorities, and the violation of privacy rights have historically taken centre stage in the public discourse around Facial Recognition Technology (FRT). Yet, these outdated narratives disregard FRT’s advancements in accuracy and bias elimination. They also fail to recognise the important checks and balances that are built into the way the technology is deployed. Most mature facial recognition solutions on the market prioritise privacy and ethics, providing recommendations to governments on further legislation that can help
ensure FRT’s proportionate and responsible use. Furthermore, nobody has ever been arrested or charged based simply on the decisions of a machine. There is always a ‘human in the loop’ to evaluate any potential matches flagged by the software. This individual will always be accountable for the decision on what happens next, just like has always been the case for any police officer, investigating any type of crime. Individual views will differ on the exact circumstances on when FRT should be used. However, we should keep in mind that there is widespread public support for its use in counter terrorism operations, where it can save numerous innocent lives.
FACIAL RECOGNITION IS HIGHLY ACCURATE
In its most recent independent analysis of leading AI facial recognition software, the National Institute of Standards and Technology (NIST) observed an unprecedented performance of just 0.0001 variance between race and gender differences. To put this number into perspective, the acceptable false capture rate in Automatic Number Plate Recognition by UK law enforcement runs at +/- 3% on nationally accepted standards. Ultimately, FRT is a tool at our disposal to help us filter through vast amounts of information, yet it should not be the only deciding factor when identifying suspects. Nearly all existing sensitive technologies apply a dual verification process; by designing FRT protocol around the concept of placing this ‘human in the loop’ as mentioned above, an operator can exert their judgement when reviewing FRT matches, thereby working together to account for both human and AI biases. Vendors and distributors of FRT must work closely with counterterror agencies to ensure that operatives are adequately trained in how to spot instances of bias, while taking the appropriate measures to safeguard privacy rights.
REFRAMING THE DEBATE
The public is increasingly aware of unethical and disreputable Nation States seeking to dominate the AI market. We need look no further than what is happening with CCTV cameras from China to understand the importance of trust and ethics in surveillance. However, to ascribe toxic human qualities of racism and
intrusion to FRT unfairly stigmatises the technology behind it. The fact remains that the speed and accuracy of FRT has come a long way since its inception, with said advancements showing no sign of slowing down.
Following the horrific events of the 2017 Manchester bombing, a new piece of legislation known as “The Protect Duty” is soon to come into force, which imposes an obligation on the public and private sector to assess and take steps to mitigate the risk of terror attacks. Judicious application of video surveillance technology can help fulfil this duty by acting as a filter for law enforcement, helping draw attention to patterns of suspicious behaviour that warrants investigation. Given the potential of FRT in preventing the preventable loss of life, it seems irresponsible to dismiss such innovations based on concerns addressable through legal safeguards and processes.

SAFEGUARDING PRIVACY
It is essential that privacy remains a top priority when developing and using FRT. Yet like any other policing measure, legislative safeguards around legality, necessity and proportionality can be implemented to guarantee citizen rights and wellbeing. In the 2020 case R(Bridges) v Chief Constable of South Wales Police, the Court of Appeals recognised a sufficient legal framework within the UK legal system to enable the use of LFR. The court also stipulated police requirements for the lawful use of LFR (adherence to Public Sector Equality Duty requirements, continuous oversight of its DPIA and management of the watch list and positioning of the cameras). Such rulings are essential in establishing the precedent and rules around the use of FRT.
The FRT sector welcomes such international standards and government oversight. With NIST and International Standards Organisations currently working to harmonise their approaches to Trustworthy AI, the onus now falls upon lawmakers and regulators to establish certainty by determining what FRT should enable in society, who should be able to use it and to construct the rules (laws) which enable and constrain such use, as well as hold it to account. Only then can FRT surveillance fulfil its true potential, not just in safeguarding our physical wellbeing, but also our rights and peace of mind. L
SURVEILLANCE
UNSURPRISINGLY, THE DEPLOYMENT OF LIVE FACIAL RECOGNITION (LFR) BY LAW ENFORCEMENT HAS STOKED FURIOUS OPPOSITION FROM CAMPAIGN GROUPS
33 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
PROFILING: IT’S NOT A BAD WORD
Utter the word ‘profiling’ in a conversation regarding security countermeasures and many are quick to exclaim that such an approach to addressing the myriad of security challenges we face is unacceptable. Yet it is acceptable. There is a difference between ‘racial profiling’ where we distinguish between people based on their race or ethnicity and ‘profiling’ where, post-attack, we try to determine the likely perpetrators of a crime or pre-attack, where we seek to identify those people displaying hostile, negative or criminal intent – regardless as to the colour of their skin, their gender, religion or sexuality
Profiling is probably the most effective tool we have in our security arsenal, but in an era where we would rather rely on a technology alarming – thereby making the decision for us – it is often the technique we least embrace.
Despite this, we always tell the general public to “see something, say something”.
In an effort to encourage a better understanding of the ways in which we can identify potential threats based on observed behaviours, Green Light launched the Behavioural Analysis series of conferences in 2018. More than 130 speakers and delegates met at the Principality Stadium in Cardiff.

From there, in 2019, the conference moved to the USA when Mall of America served as the host. The 2020 event was held online due to the pandemic and last year was at the University of Northampton. Behavioural Analysis 2023 takes place in an airport setting – an environment where behaviour detection comes into its own – and already has a record number of delegates signed up to gather at Prague Airport, from 28-30 March 2023.
“The conference is designed to bring together security practitioners, keen to either benchmark or share best practice, and academics researching the true efficacy of behaviour detection,” according to conference chair and programme developer Philip Baum. It’s the event which strives to provide proof of concept.
The three-day programme encompasses a broad range of topics.
TUESDAY 28 MARCH: MORNING
In the opening session, two organisations valuing the contributions individuals can make to the identification of criminal and/or hostile intent will be presenting – the United Nations and the Airports Council International.
Dr. Aynabat Atayeva, the chief of the International Hub on Behavioural Insights to Counter Terrorism for the United Nations Office of CounterTerrorism, will be discussing how behavioural insights can help counter the terrorist threat, whilst Sébastien Colmant, director aviation and cyber security for ACI EUROPE, will be talking about the way in which behaviour detection training can both upskill aviation security personnel and, importantly, help attract and retain them. From the get-go, delegates will consider the realities of nonverbal communication.
Nonverbal communication analyst Mi Ridell will be considering the extent to which microexpressions can truly help identify potential threats, why security personnel may make errors in judgement (e.g. Halo Effect, Horns Effect & Othello Error) and how an individual’s emotional leakage might serve security’s best detection interests (from the Spotlight Effect to Duper’s Delight). From Argentina, psychologist Alan Crawley of Universidad del Salvador will set out why nonverbal communication is actually a delicate art! With the terrorist threat arguably being our greatest concern, understanding pre-attack behaviours of suicide bombers is obviously incredibly valuable. This is the subject criminologist Dr. Sagit Yehoshua, author of ‘Terrorist Minds: from socialpsychological profiling to assessing the risk’ will be addressing when she shares relevant data and CCTV footage from actual suicidal attacks.
TUESDAY 28 MARCH: AFTERNOON
One could argue that behavioural analysis is a behavioural science. In this
vein, Aaron Le Boutillier, ASIS’ regional vice president (South-East Asia) and CEO of Le Boutillier Group, Thailand, will kick off the afternoon session with a dynamic presentation exploring whether neuroscience has a role in behavioural analysis training. For any organisation considering implementing a behaviour detection programme, it is critical to set the parameters and establish reasonable aims and objectives – a topic covered by Neville Hay, director of training with the INTERPORTPOLICE. And, the session ends with an operational example of how staff can be trained in emergency response with the aid of behavioural science…and, yes, The Simpsons! Kim Covent, an advisor with Belgium’s Ghent Local Police Force will be sharing their experience of a project run in collaboration with the Ghent Museum of Fine Arts. The first day ends with a sobering focus on human trafficking, an area where behaviour detection can really show huge benefits. Aside from an frontline operational police perspective from Canada, Dr. Sarah Lloyd, a senior trainer for Pace (Parents Against Child Exploitation) will be explaining how contextual safeguarding can help make hot spots cold, and, from the USA, Dr. Katariina Rosenblatt, the founder of There Is Hope For Me, Inc., and the author of ‘Stolen: The True Story of a Sex Trafficking Survivor’, will be sharing her very personal experience of being a victim, turned survivor, of human trafficking.
WEDNESDAY 29 MARCH: MORNING
The second day kicks off with an examination of cultural and sociological issues pertaining to behavioural analysis. Included in the opening session are two presentations from the host country, Czechia. Dr. Lenka Scheu of the Police University of the Czech Republic will, from a legal perspective, be asking whether racial profiling is avoidable and whether it is even wrong, whilst Dr. Barbora Vegrichtova, an Associate
ADVERTISEMENT FEATURE
34 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
Professor at the Czech Technical University will, citing examples from her work in the prison service, be examining criminal and extremist tattoos and symbols and demonstrating how they serve as clues to mindset and affiliation. Ever heard of Laban Movement Analysis? If not, Sandra Adiarte, of Australia’s Bond University, will explain all. It’s a question of observation. And, on the subject of observation, from an operational perspective Kanan Tandi will be presenting on sexual abuse on the Indian public transportation system and explaining how the definition of suspicious signs can help identify likely offenders. The morning session ends with a further operational case study - how crowds can be observed at open air, public events. Using the Signal Festival as an example, Jiří Cmunt will explain how the police, crowd management company and festival organisers cooperate to deliver safe and secure festivities.
WEDNESDAY 29 MARCH: AFTERNOON
Much of the second afternoon will focus on how, in the age of artificial intelligence (AI), technology can assist in the identification of negative intent. For example, might wearables become the modern lie detectors? The day will conclude with the second of the conference’s keynote presentations. Having also spoken at the very first Behavioural Analysis conference in Cardiff back in 2018, Dr. Cliff Lansley, of the Emotional Intelligence Academy and a familiar face on television screens as the scientific advisor to Warner Bros/Discovery Channel in their series ‘Faking it: Tears of a Crime’ (now in in its 6th Series),

joins the line up again to explaining their six-channel analysis system.
THURSDAY 30 MARCH: MORNING
It’s a question of questioning. Resolving concerns through questioning techniques is the focus of the third morning. Dr. Abbie Maroño, a behavioural scientist and Director of Education at Social-Engineer, LLC, will be discussing non-verbal mimicry and its role as an elicitation technique during security interviewing. Behaviour analyst Thomas S. Karat will then explore deceptive strategies and acts of omission in high-stakes negotiations and interrogations. The session concludes with a presentation from a renowned researcher on the international academic circuit discussing one specific approach to investigative interviewing. Delegates will hear from the brains behind the Verifiability Approach, Prof. Galit Nahari, head of Department of Criminology at Bar-Ilan University, Israel
The insider threat is also one worthy of exploration. Elsine van Os, the CEO of Signpost Six, will be presenting some pointers as to how such threats might be identified, especially given that we are living in an era of geopolitical turmoil and post-pandemic change. And, from an aviation perspective, Dr. Karel Lehmert, the head of the CBRNe Forensic Sampling Laboratory in Czechia, will be setting out how behavioural profiling might help identify suicidal and homicidal pilots.
THURSDAY 30 MARCH: AFTERNOON
The aviation security theme continues after lunch. In the third keynote, Dr. María Carmen Feijoo Fernández, the
chair of the ECAC Behaviour Detection Study Group and the head of behaviour detection at Adolfo Suárez Madrid Barajas Airport will be talking about airport security behaviour detection programmes and the industry’s quest for scientific proof of concept. All delegates will appreciate some real examples of behaviour detection identifying potential threats. From the US, Samuel Juchtman, who was the former head of security for El Al Israel Airlines in Prague, will, in his current capacity as COO for ACTSAviation Security, Inc. be sharing some real stories from the front line. And last, but by no means least, before delegates join the Prague Airport security team on operational tours of the airport, Zdeněk Truhlář, security strategy and administration director at Prague Airport, will be presenting on airport landside protection and how the airport secures its terminals and departure halls by an appropriate mix of technology, dedicated security personnel and general staff awareness. So, there you have it… and we haven’t even included all the presenters as a few key names have yet to confirm! But conference moderators, Philip Baum and Diana Nowek hope you will join them and their panels for three days of learning, benchmarking and the sharing of best practice in the art of profiling or, if you really can’t bring yourself to utter the phrase, then in the art of behaviour detection! L
FURTHER INFORMATION
To secure your place, visit: www.behaviouralanalysis.com
ADVERTISEMENT FEATURE
35 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
Debbie Rafferty MSc(Debz) has more than thirty years’ experience in the security and counter terrorism industry, she is currently researching a PhD in Criminology and Sociology at The University of Abertay. The following article is based on a Counter Terrorism Studies Masters Thesis titled “How do energy companies manage and mitigate the security of offshore oil and gas installations?” submitted to Liverpool John Moores University in 2020, and presented at the recent International Security Expo in London last September
PROTECTING OFFSHORE OIL AND GAS INSTALLATIONS
In the 1970s, offshore maritime terrorism was identified a clear and present insidious danger. What is the menace? Oil and gas installations are susceptible to attacks - disruption by an operative or saboteur who permeates the crew, appropriation by an effective and organised terrorist faction, subaquatic attack by a diver or submarine and an unrestrained strike by an antagonistic power (Townsend, 1975). However, this is the 21st century and evidentially subversive attacks could be launched in many more sophisticated guises, including but not limited to, cyber, insider threat, insurgency infiltration via small boat, drones, light aircraft, safety boat, and helicopters used to transport rig staff, coupled with the current cold war enigma installations in the North Sea, the oil and gas infrastructure is increasingly vulnerable. So much so the UK has launched an exigent security review of North Sea energy pipelines after Russian ‘sabotage.’ Increasingly, extreme political groups have resorted to sabotage and hijacking in Britain and throughout the world. The foremost antidote relating to prevention was identified as a ternary stratagem comprising of Planning, Preparedness, and Performance. Therefore, from the aforesaid, one may presuppose that the past informs the present and subtly seeps into the future. The online magazine Rigzone reported that from 22 May 2022, in the Bay of Campeche, Mexico, there have been six maritime terrorism events. The attacks involved three supply vessels and offshore oil installations (MSTA) (Exarheas, 2022). Rewinding and reflecting on these events as to the why and wherefores of the incursions should supplement existing security knowledge. Further, highlighting what mitigating and moderating procedures are desirable in order to prevent similar incursions on exposed oil and gas installations in, for example, the North Sea. Circa 26 September 2022 events in Danish waters erupted because of “an act of ‘Sabotage’ on the Nord Stream gas pipe” (Sky News, 2022). It is thought the
saboteur set off a series of explosions to damage the pipeline. Had this been a petroleum supply line, the environmental damage would have catastrophic. In a time of increased aggressive acts against the oil and gas industry why is the UK not taking potential threats seriously?
My recent presentation on how oil and gas companies manage and mitigate security in the North Sea highlighted security failings, along with the potential for impending occurrences. Failings that are not “secret” in nature but available to the general populous..
THE MAIN POINTS
There remains an endemic culture of postulation and procrastination within the industry, with regard to the issue of insurgency and the role of the Offshore Installation Manager (OIM) in this context. This phenomenon is known as a presumption of knowledge or ‘imagined’ idea that, the OIM has specialised training to manage an unquantifiable level of security risk. This can be traced to a perceptible gap in current training and is supported by the findings of Hollnagel (2006 p.86) who alludes to risk evaluation as “work as imagined” and “work as done.”
The OIM ‘captain’ of an oil rig is supposed to maintain safe operating practises in an exceptionally hazardous environment while at the same time maximising production of a product with significant economic return to the British Government. During an interview for research purposes, rig personnel believed if there was an illegal ‘boarding’ on a rig in the North Sea the OIM would have the necessary training to deal with this situation and instruct everyone what to do. Further enquiry into the prerequisite training needed to be an OIM highlighted that there was in fact no training in the prevention of insurgency. Any training was restricted to incidents that may occur within Standard Operating Procedures, with a focus on “slips trips and falls.”
Hazard Management tools need revisiting
36 COUNTER TERROR BUSINESS MAGAZINE
ISSUE 28
|
OFFSHORE OIL & GAS
and revamping in terms of the prediction of physical projected threats. The majority of those standardised evaluation systems used across the oil and gas industry are located within the “lessons learned” and “pass process failures prevention.” Thus, there is a necessity to step back from the ‘knee jerk’ responses and a move towards a proactive dynamic predictive process. A note should be made that if the sector exists in a bubble of “the past is a reflection of the past” then why is data not collated to inform the future. Collating data from for instance, the Bay of Campeche events would inform the structure and content of training modules to mitigate and manage similar incursions. Threat defence mechanisms remain focused on threats such as, the negligent and malicious insider. The attitude that although the threat is not perceptible does not mean it does not exist.

External threats from anti-petroleum movements who plant explosives on gas lines are becoming more frequent, and yet there is no Tactical Evaluation simulations or pre-emptive response training across the industry. Current response mechanisms are outdated, and although may appear expedient on paper there is an ever-increasing gap between the reaction procedures and actual real life ‘planned responses’ if there is an event. A constant reminder is the Piper Alpha in the North Sea tragedy when a substantial leakage of gas condensate on the rig caused an unprecedented disaster. This took all of 22 minutes to unfold, 167 souls were lost and the Occidental Petroleum Corporation settled to pay $180 million in reparation to victims’ families and survivors. Overall, the Piper Alpha tragedy incurred a $3.4 billion USD loss in revenue. There are defence mechanisms in place, in the shape of a ‘safety vessel’ nonetheless inquiry has shown that often these vessels are not fit for purpose. On the other hand, Norway employs custom-built boats, while the UK relies on antiquated trailers and tugboats. Likewise safety zones and existing maritime measures are not ideal, short comings were identified by Assaf Harel (As far back as 2012). Hitherto, the frequent incursions by environmentalist groups have had little effect on the up to date ‘be prepared training’.
Response at National level is now restricted, largely by location. Amalgamation and relocation of military and maritime defences has increased an estimated response time more than 4 hours, even though Piper Alpha was devastated in 22 minutes. Lack of external learning was cited in the Cullen report (Reid 2020).
Therefore, illustrating the difficulty that companies have in learning from disasters that occur elsewhere. Government strategies have continually been challenged by scholars, and on closer inspection emergency strategies appear robust and integral on paper these strategies have not been rehearsed by the sector and/or policy makers. Legal devolution has resulted the division of the UK. This division has brought about national policies that satisfy English and Scottish law. Given the importance of the human resources, sector and commodities produced, there is a lack of investment into specialised trained and qualified response personnel to manage extremist threats.
SOLUTIONS
The initial research carried out regarding ‘How oil and gas companies manage and mitigate security in the North Sea’ reveals conspicuous and concerning vulnerabilities. There are however uncomplicated solutions to overcome these weaknesses in the North Sea. Include pre-emptive training of all oil and gas personnel, specific to anti incursion and proactive responses to intended threats. Intensify the powers of arrest for the OIM and inclusion of a counter insurgency module as part of the OIM course. Include an Offshore Security Manager who can conduct on location risk assessments and design practical standard operating procedures (one per rig). Employ a researcher within the company framework who can investigate and review the under currents of global socio-politicaleconomic developments that may precipitate insurgent events. Further, this person could liaise with the Operations Security Manager to utilise the ‘lessons learned’
to generate effective processes and procedures in response to evolving threat situations. There may be those readers who perceive that the information contained within this article will update unscrupulous individuals about national offshore security integrity and weaknesses. In response to this is that the existing vulnerabilities are already common knowledge. Finally, this is not a fictitious issue there is an imminent clear and present danger, and evidence indicates that this is accelerating. There is an expenditure effective solution which can be implemented to manage/ mitigate and protect personnel, installations and avoid financial loss. L
Thanks to Margaret A. McLay (MA, MSc, MEd) who contributed to the research and presentation of this article.
FURTHER INFORMATION
The above article is taken from a MSc thesis 2020 available from Liverpool Johns University Library. Email: d.rafferty@abertay.ac.uk
References:
EXARHEAS, A., 2022. The Gulf of Mexico Has a Pirate Problem [Homepage of Rigzone], [Online]. Available: https://www.rigzone.com/news/the_gulf_of_mexico_ has_a_pirate_problem-17-aug-2022-170005-article/ (Accessed: 7 January 2023).
HC Deb 23 May 1975 vol 892 cc1913-24. Available at: https://api.parliament.uk/historic-hansard/ commons/1975/may/23/north-sea-oil-and-gasinstallations (Accessed: 6 January 2023).
HOLLNAGEL, E., 2006. Task analysis: Why, what, and how. Handbook of human factors and ergonomics, pp. 371-383.
REID, M., 2020. The Piper Alpha disaster: a personal perspective with transferrable lessons on the long-term moral impact of safety failures. ACS Chemical Health & Safety, 27(2), pp. 88-95.
WHITESIDE, P., 2022, Sabotage’: What we know about the Nord Stream gas leaks and who was behind them [Homepage of Sky News], [Online]. Available: https://news.sky.com/story/ sabotage-what-we-know-about-the-nord-stream-gasleaks-and-who-was-behind-them-12706930 (Accessed 8 January 2023).
OFFSHORE OIL & GAS
37 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
CONFERENCE – IN LONDON
National infrastructure, government and emergency services are prime targets for cybercrime with the sophistication and regularity of attacks on the rise. Are the teams, IT/OT processes and suppliers trained and protected?


National infrastructure, government and emergency services are all critical components of a country’s security and well-being. They provide essential services to the public, and their disruption or destruction can have significant consequences. Unfortunately, these organisations are also prime targets for cybercrime, and the sophistication and regularity of attacks on them are on the rise. In this article, we will examine the challenges that these organisations face when it comes to cybersecurity and discuss the steps they can take to protect themselves.
CHALLENGES THAT NATIONAL INFRASTRUCTURE, GOVERNMENT, AND EMERGENCY SERVICES ORGANISATIONS FACE
Large amounts of personal information are processed and stored by government institutions. Cyber-espionage is rampant in the public sector, according to Verizon’s 2019 Data Breach Report, with 79 per cent of breaches involving external actors being perpetrated by state-affiliated actors. “30 per cent of breaches result from insiders (employees) misusing privileges and making mistakes.”
According to Radware’s research, government professionals are most concerned about data leakage following a cyberattack, followed by service outages, reputation damage, and revenue loss. Despite the fact that this move transforms infrastructure operations, improves user experience and reduces costs, government institutions continue to move applications and data to the cloud. However, managing and securing applications hosted in cloud environments requires less control and visibility.
The Federal Risk and Authorization Management Program, International Traffic in Arms Regulations (ITAR), and Criminal Justice Information Services (CJIS) are a few of the guidelines that government data centres must follow. Payment Card Industry (PCI) and General Data Protection Regulation (GDPR) regulations and standards require institutions to comply with them. It is important to use encryption protocols in order to secure transactions, but encryption attacks are also possible. One of the biggest challenges that
national infrastructure, government, and emergency services organisations face is the complexity of their IT and OT (operational technology) systems. These systems are often made up of a wide variety of different technologies and devices, all of which need to be protected from cyber threats. This can be a difficult task, as attackers are constantly developing new techniques and tools to bypass security measures. Additionally, many of these organisations have a large number of third-party suppliers, which can also be a source of vulnerability. Another major challenge for these organisations is the scale of the attacks they face. Cybercriminals are increasingly using advanced tools and techniques to launch large-scale attacks, which can be difficult to defend against. For example, distributed denial-ofservice (DDoS) attacks can overload a website or network with traffic, making it impossible for legitimate users to access it. In addition, attackers may use malware to infiltrate a network and gain access to sensitive information.
ARE THEY PROTECTED?
To protect themselves from these threats, national infrastructure, government, and emergency services organisations need to have robust cybersecurity programs in place. This includes having a dedicated team of cybersecurity experts who can monitor and respond to threats in real time. Additionally, these organisations should conduct regular security assessments to identify and address vulnerabilities in their systems.
One of the most important steps that these organisations can take is to ensure that their IT and OT systems are properly segmented. This means that different parts of the network are isolated from each other so that if one part is compromised, the rest of the network remains unaffected. Additionally, organisations should use firewalls and intrusion detection and prevention systems to help block and detect malicious traffic.
Another key step is to train employees and third-party suppliers on cybersecurity best practices. This includes educating
EXPO &
UK CYBER WEEK –
38 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53 UK CYBER WEEK PREVIEW
them on how to identify and respond to potential threats, as well as how to use security tools and software. Additionally, organisations should conduct regular security awareness training to ensure that employees are aware of the latest threats and how to protect themselves.
In addition to these steps, national infrastructure, government, and emergency services organisations should also have incident response plans in place. This means that they have a set of procedures in place for identifying and responding to a security incident. This includes having a dedicated incident response team that can quickly respond to a threat and take the necessary steps to mitigate it.
Finally, national infrastructure, government, and emergency services organisations should also invest in advanced threat intelligence tools and services. This includes using machine learning and artificial intelligence to detect and respond to threats in real time. Additionally, organisations can use threat intelligence feeds to stay up-to-date on the latest threats and trends in the cyber threat landscape.

HOW GOVERNMENT AGENCIES CAN PROTECT THEMSELVES FROM CYBERATTACKS
Cyberattacks on government agencies have become increasingly common in recent years. These attacks can result in the loss of sensitive information, disruption of services, and even physical damage to infrastructure. As such, it is crucial that government agencies take steps to protect themselves from cyberattacks.
One of the most important steps that government agencies can take to protect themselves from cyberattacks is to implement robust security measures. This includes firewalls, intrusion detection and prevention systems, and antivirus software. These measures can help to prevent unauthorised access to sensitive information and systems, as well as detect and respond to any attempts to breach security.
In addition to implementing security measures, government agencies should also invest in employee education and training. This can help to ensure that employees understand the risks associated with cyberattacks and know how to respond to them. Training should include topics such as safe browsing practices, password management, and identifying and reporting suspicious activity.
Another important step that government agencies can take to protect themselves from cyberattacks is to regularly update their systems and software. This is important because new vulnerabilities and exploits are discovered all the time, and older software may no longer be supported by security updates. Keeping systems
and software up-to-date can help to ensure that they are protected against known vulnerabilities and exploits. Another key element of protecting government agencies from cyberattacks is incident response planning. This includes identifying potential vulnerabilities and risks, as well as developing plans and procedures to respond to cyber incidents. This should include incident management, incident response, and incident recovery. This will help to minimise the damage caused by a cyberattack, as well as restore services and systems as quickly as possible. Government agencies should also invest in the latest threat intelligence systems and tools. This will help to identify and track the latest cyber threats and provide actionable intelligence that can be used to improve security. This includes threat feeds, threat intelligence platforms, and threat-hunting tools.
In addition to these measures, government agencies can also seek out external help from cybersecurity experts. This can include hiring consultants or contractors or engaging with third-party security vendors. These experts can help to identify vulnerabilities and weaknesses, as well as provide guidance on how to best protect against cyberattacks.
Another important step that government agencies can take to protect themselves from cyberattacks is to build strong relationships with other organisations in the public and private sectors. This can include sharing threat intelligence, best practices, and other information that can help to improve security. This can also include working together on incident response and recovery efforts.
Whenever policymakers address these principles, they have resources and industry standards to assist them. In order to take advantage of the advanced security hardware embedded in modern computing devices, including mobile phones, the Fast Identity Online (FIDO) Alliance has developed standards. There is a broad acceptance of FIDO’s standards throughout the technology community, with solutions offered by Microsoft, Google, PayPal, Bank of America, Facebook, Dropbox, and Samsung incorporating FIDO’s standards. Despite the fact that no standard or technology can eliminate cyberattack risks, adopting modern standards that
incorporate multifactor authentication can be an important step to significantly reduce cyber risk. By following these eight principles, governments can create a policy foundation for MFA that not only enhances our collective cyber security but also contributes to greater privacy and increased trust online.
CONCLUSION
In conclusion, national infrastructure, government, and emergency services organisations are prime targets for cybercrime, and the sophistication and regularity of attacks on them are on the rise. To protect themselves, these organisations need to have robust cybersecurity programs in place, which include having a dedicated team of experts, conducting regular security assessments, and training employees and third-party suppliers on cybersecurity best practices. Additionally, organisations should segment their IT and OT systems, use firewalls and intrusion detection and prevention systems, and have incident response plans in place.
If you are interested to find out more on how best to protect your business, make sure to attend UK Cyber Week –Expo & Conference on 4-5 April 2023 at the Business Design Centre, London. Our speaker sessions include 100+ cyber security experts, hackers and disruptors with perspectives from across the industry. Find out more and get your free ticket here L

FURTHER INFORMATION www.ukcyberweek.co.uk
39 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE UK CYBER WEEK PREVIEW
Andrew Sieradzki, group director, Security, at Buro Happold on how to
introduce a new access control system
DOES YOUR ACCESS CONTROL SYSTEM HAVE HEALTHY CREDENTIALS?

Undoubtedly many of the readers of this article have an association with electronic access control systems (EACS), whether through their day to day in gaining unfettered access into their offices, or through the specification, delivery or administration of access control systems into buildings.
The initial widescale adoption and deployment of electronic access control systems commenced in the late 1970s; from a practitioner’s perspective these systems have generally had a long life cycle – typically exceeding the traditional electronic system 10-year lifespan model. However, even now there are a plethora of these systems that are running perfectly satisfactorily in their second decade (and sometimes longer) of operation. The administrators of these platforms may not be aware that they have potentially significant exposure in terms of system efficacy due to the gradual depreciating and potentially insecure nature of these systems and the data contained on them.
While many systems have gradually been transitioned to modern platforms, there is often a concern in terms of any proposed upgrade, with a veiled nervousness from clients as to the amount of disruption such changes have
on their workplace and their workforce. The bigger the organisation, the more complex and intricated the issue becomes – especially in a post Covid-19 world of flexible working. This may be a legacy view that is cast from past card transition experiences; however, there is undoubtably some merit in being cautious about embarking on a task that involves changing the keys to the kingdom of all users; the prospect of mass lockout does not inspire the balance sheet or executive board particularly favourably. Typically, these systems involve everyone concerned, where the individual users get to take a piece of the security platform (i.e. their passes) away from the workplace and are then trusted to look after them. It is hard to picture how this would work if this practice was adopted for every other type of security solution deployed within the workplace (just imagine having the opportunity to take a piece of the CCTV solution home with you). There is therefore nervousness in new technology adoption, and the need for an understanding of the full use case of the access control ecosystem.
ADOPTING A NEW A SYSTEM
One favourable transition option often considered when replacing a large system
ACCESS CONTROL
40 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
is to adopt the existing legacy token/ user credential/card estate and build the replacement solution around this with a view of creating a pathway to later adopt a new card downstream of the deployment. This does equate to a more seamless transition, and many successful replacement solution deployments have utilised this method, but this approach is not without its risks. During adoption of this approach, some careful consideration needs to be made as to the legacy credentials encoding and enciphering (if any), where once discovered, typically require importing into the replacement solution. This is not an insignificant task: even if the credentials’ known security vulnerabilities may have been exploited to initially extract its enciphering keys and encoding pattern, did this action breach any originators latent IP? Was there any consideration by the end users in gaining permission from the original credential provider to adopt these formats? Furthermore, any consequential failure at this juncture often leads to adoption of a big bang approach to credential replacement, where you may have a true period of running the old solution in tandem with the new, until you can replace the legacy platform. This is not an insignificant and disruptive task without pre-planning and the hope of a forgiving workforce. Another often overlooked aspect of adopting replacement credentials is their initial configuration and architecture, which may end in circulation for potentially numbers of decades. Indeed, what consideration was made if their enciphering keys were ever compromised, and what type of standards were adopted from the outset? Was the fallback position considered where you can recover from a ‘loss key’ breach and ‘roll the card family keys’ without replacement of the entire card family? Where such breaches are considered serious enough, the alternative is of course to replace the whole card estate; reputationally, this is not a good position to be in. Then there’s the knotty problem of how these keys are stored on the cards – are these static and common throughout your entire card family, and do you care if these get compromised? The alternative is to consider diverse keysets on each card. This, while a complex process to initiate, does ensure that each card in your estate is completely unique from a key material perspective, and that when an individual card is compromised, this generally only equates to that single card and not your entire suite of cards. Once you have decided on the card technology, its architecture and enciphering credentials, do you then want to encode (which is quite distinct from enrolling cards) these cards on site? Or will you farm this capability out to the supply chain, and hope that
your most sensitive card aspects (keys which are required for the encoding process) don’t become compromised?
In remedy of this vulnerability, a far more manageable approach is to encode your cards on your premises, with your own securely held enciphering key family and production platform. Generally, well designed solutions incorporate these keys on to a third party validated hardware secure module (HSM) and therefore do not expose these assets to the wider supply chain or internet during your card encoding processes. Furthermore, it is entirely possible for the end user to transport these HSMs to trusted card encoding providers (if large scale is a requirement), deployed for the production run and then returned to their originator once the encoding run is completed. There are a lot more of these underthe-hood aspects of credential selection to consider at the design stage, especially if you consider and add mobile platforms to the mix. However, there is also a great emphasis on the type of access control system itself, its features and benefits, and of course cost. Selection consideration should always consider the functionality of these systems, but merit should also be given to the security aspects. For instance, how is the (user) data both in transit and at rest accounted for – is it enciphered? Are the communications between your access reader endpoints and door controllers secured? i.e. Open Supervised Device Protocol (OSDP): who holds the respective enciphering keys? What resilience do you have for system signalling faults – does the system keep running? Larger solutions can typically span many buildings or may even span a global workforce. The security and respective data processing considerations need to be considered, especially where cross jurisdictions are in force.
In conclusion, while not promising to be a comprehensive and detailed end-to-end discussion on selection of electronic access control credentials, my top tips are:
DOS
Do ensure that you know what your exposure is to the supply chain in terms of your credential, equipment and data enciphering keys. Ensure you have full and recoverable ownership of these and can store and use them securely. Also consider the eventual destruction/removal of sensitive data with any end-of-life ACS components. Do ensure you have a welldesigned token infrastructure based around an independently validated credential platform that caters for secure encoding practices and uses diverse keysets for each token.
Have a plan B, C and indeed D –design in a key rollover capability
within your token family to ensure that if there is a key compromise you can recover without an immediate and full card replacement programme.
Whenever conducting an ACS transition, plan well in advance for triaging and cleansing legacy user data and provide good clear communications as to how the transition process will take place.
Test, test and re-test: build in time and resource to conduct testing of the solution in phases before full deployment, and work with all stakeholders (including fire safety, accessibility and security representatives) in mapping out the whole life cycle of EACS use, including pass production, attesting user data, access rights, failover considerations and end of life considerations.
Use advice from reputable trade industry bodies and base your designs on current standards including GDPR. Select equipment from independently attested bodies e.g. CPNI Access Control Assured and CPNI CAPSS assured Select your system installer and maintainer carefully – make sure they belong to a relevant trade body e.g. NSI, SSIAB etc and that they are familiar with and trained on the equipment they plan to install for you. Make sure you get sufficient training to operate and administer the solution and sufficient consumables to maintain credential production, and never underestimate the time taken for any transitional bulk pass production run. Have a means in place to shred/ securely dispose/recycle spent components and consumables (including credentials).
DON’TS
Don’t share your most critical and sensitive material i.e. enciphering keys with an unknown and attested supply chain. Don’t simply throw away spent card printing consumables (noting that some production techniques genuinely produce truly excellent negatives of all your staff passes as a ‘by-product’). Don’t share user data sets without some form of data sharing agreement that binds the parties contractually to process your data appropriately.
End of life components may contain some of your most critical assets; adopt a responsible security minded approach to destruction/recycling of these.
In conclusion, the selection, design, installation maintenance and administration of access control systems is a complex web of processes and workflows that involves everyone within an organisation. L
FURTHER INFORMATION
For more information, click here
ACCESS CONTROL
41 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
In a Q&A session with Counter Terror Business, David Owen, the recently appointed country manager for the UK at Heras, talks about a move to a standardised product portfolio, puts the spotlight on perimeter intrusion detection systems (PIDSs) and explains how its Heras Security Model (HSM) is fundamental to securing the perimeters of UK sites of national or strategic importance
PIDSS AND THE HSM ARE PIVOTAL TO PERIMETER SECURITY


PLEASE CAN YOU GIVE US A BRIEF INTRODUCTION TO THE COMPANY AND WHAT IT DOES?
Heras is Europe’s leading end-to-end supplier of permanent and mobile perimeter protection solutions – and from our UK headquarters in Doncaster, we design, manufacture, install and service perimeter
protection solutions for governments, local authorities, warehousing and distribution hubs, stadia, public spaces, utility companies, and UK infrastructure sites – such as power stations. We are the only UK company that offers a full portfolio of perimeter protection products and full nationwide coverage to
INTERVIEW
42 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53
David Owen, manager for the UK, Heras
support the customers we partner with. Our perimeter protection solutions comprise products and services including demarcation, entrance control and detection products and integrated systems.
PLEASE CAN YOU EXPLAIN YOUR ROLE AT THE COMPANY AND YOUR EXPERIENCE?
I joined Heras from the oil and gas industry, where I oversaw capacity realignment and expansion projects around the world.
I’ve been part of a team that has transitioned to a more standardised and simplified product portfolio – and over the last 12 months, everyone at Heras has been focused on the common goal of serving the needs of our UK customer base. This is reflected in the positive performance of the business in the UK.
WHAT IS THE COMPANY’S FOCUS AT THE MOMENT? ARE THERE ANY PARTICULAR PRIORITIES?
In terms of Heras, the main focus over the last 12 months has been to
reconnect with, and foster a much more collaborative and partnering approach with our customers. We don’t just help them protect what they value the most – we also help with perimeter solutions that place safety at the heart of what they do: that’s the safety of staff, visitors, contractors and even intruders.
In terms of the bigger picture, the world has changed. We are seeing the results of underinvestment in security in both the public and private sectors not just in the UK but through our businesses right across Europe. There is a gap in required standards, especially, for example, in national interest infrastructure, such as energy and power distribution, but also in commercial interest areas, such as data centres.
WITH REGARD TO THE UK, WHAT TYPE OF CLIENT DO YOU TEND TO WORK WITH AND WHAT KIND OF PROJECTS DO YOU DO?
At one end of the spectrum, we supply perimeter fence lines and automatic gates for warehouses and distribution hubs, fences for schools and turnstiles for sports stadia. At the other end, we are heavily involved in the supply of perimeter systems and solutions for parts of the UK’s critical infrastructure – basically, projects that we can’t openly talk about where the government wants to keep people out or keep people in!
One of the key ways that these sites keep people out (or in) is by using perimeter intrusion detection systems (PIDSs) – which are usually installed on the fence fabric to detect any potential intruders attempting to enter the site by climbing over, cutting through or even going under the fence.
When an intrusion at the perimeter meets the alarm criteria, PIDSs will transmit an alarm signal directly to an alarm panel and/or integrated software management system (SMS) so that the onsite security team (or designated staff) can verify, and act upon, the alarm in an appropriate and timely manner.
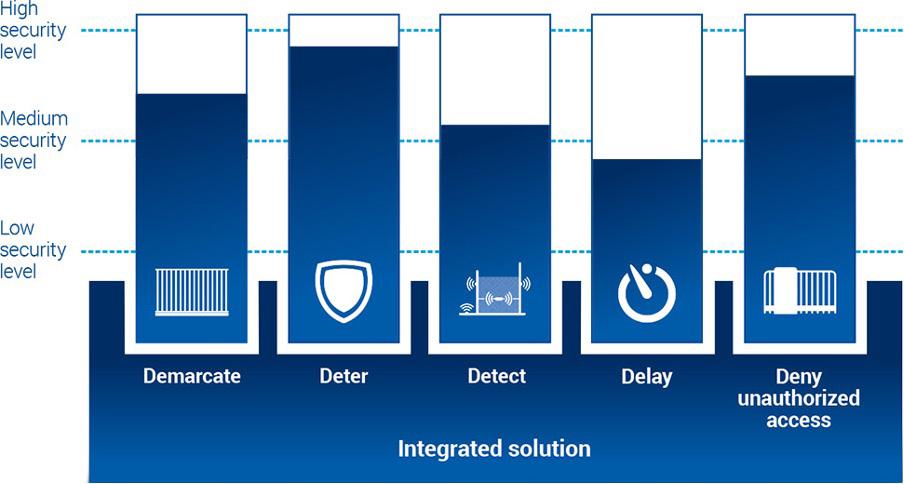

ARE YOU ABLE TO GIVE US AN EXAMPLE OF A RECENT PROJECT? IF NOT, COULD YOU GIVE US A HYPOTHETICAL IDEA OF A PROJECT THAT YOU MIGHT CARRY OUT?
Every project starts by taking customers through the Heras Security Model (HSM), which considers all the different possible scenarios. We can use our model to assign the relevant security level to each aspect of the perimeter security system and then propose the pertinent products to achieve that security level.
Part of the HSM is the site survey, where we can establish the needs in terms of a new system, upgrade, renewal or replacement. The site survey looks at the complexities of the site.
A recent project was as fascinating as it was challenging for two reasons.
The first was that the site was too big for one system. Therefore, the site was split into three distinct zones that feed into two control rooms that monitor PIDSs, CCTV, thermal imaging, electrified sections of fencing, and gates. Quite simply, the site cannot afford to have a control room go down.
The second was that the site has three rings of fencing. There’s the perimeter fence line, primary internal fencing and then secondary internal fencing. This is almost unprecedented in our industry, but there are three layers of demarcation, deterrent, detection, delay and denying unauthorised access for good reason.
One final point to mention is safety and compliance. Heras has products within our portfolio that meet industry standards and regulations in accordance with the CPNI (Centre for the Protection of National Infrastructure), CAPSS (Cyber Assurance of Physical Security Systems) and NOMS (National Offender Management Service). L
INTERVIEW
INFORMATION
more information visit www.heras.co.uk 43 ISSUE 53 | COUNTER TERROR BUSINESS MAGAZINE
FURTHER
For
Counterterrorism MSc Programme

Never before in history have the issues of what causes terrorism, how to combat it, and how to assess and manage the risks associated with it, attracted such wide international attention and controversy. The need for accessible, comprehensive and reliable research and education on terrorism and counterterrorism remains profound.
The Cranfield Counterterror Programme offers two Master’s level courses that will address these challenges and draw upon the specialist skills and knowledge of Cranfield’s expert staff, to offer you an exceptional and cutting-edge education in this critical area.


• Counterterrorism MSc www.cranfield.ac.uk/counterterrorism
• Counterterrorism Risk Management and Resilience MSc (co-funded by Pool Re). www.cranfield.ac.uk/riskandresilience




For further information, please contact: E: studydefenceandsecurity@cranfield.ac.uk

44 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 53 The publishers accept no responsibility for errors or omissions in this free service ADVERTISERS INDEX CEIA 28, 31 Cova Security Gates 16 Enterprise Control Systems 30, 31 Evendia IBC Frontier Pitts 6 Green Light 34 Mark Allen Group 21, 23 Nineteen Group IFC, BC Roar B2B 38 Streamlight 4 Tait Communications 20, 22
17 - 18 May 2023



Ex CeL London
COU NT ERING T OM
Counter Terror Expo 2023 will provide professionals from industry, infrastructure, government and policing an opportunity to discover the latest counter-terrorism solutions.
CTX 2023 will feature exhibits, seminar and workshop content delivered by leaders in CT and Security.

To find out more and to register for a free ticket, visit our website today at ctexpo.co.uk.
Co- lo cated even ts: Premier Media Partner: O rganised by:
Register now ww w.ctexpo.co.uk
PROTECT • RESPOND • RECOVER
FORENSICS EUROPE EXPO 17 - 18 May 2023 ExCeL London
email: info@evendia.co | Tel: +44 (0) 208 191 0980 | web: ctexpo.co.uk
ORROW’S TH REATS , TODAY






Founding Partners: Co-located with: Lead Media Partner: THE UK’S AWARD WINNING NO.1 COMMERCIAL, ENTERPRISE AND DOMESTIC SECURITY EVENT 25-27 APRIL 2023 NEC BIRMINGHAM UK FIND OUT MORE: WWW.THESECURITYEVENT.CO.UK





















 Polly Jones, editor
Polly Jones, editor