






ADI’s commercial off-the-shelf (COTS) software-defined radio (SDR) system-on-module (SOM) digitizers enable customers to deploy high-performance distributed sensing techniques at the tactical edge, as quickly as possible.


Editor’s Perspective
7 Demand for open standards, architectures growing in Europe By John M. McHale III
Defense Tech Wire
8 By Dan Taylor
Technology Update
10 Marine Corps ARV prototype can control UASs, anticipate component failures By Dan Taylor, Technology Editor
Guest Blog
28 Solving CJADC2’s last mile By James Kubik, Somewear Labs
Connecting with Mil Embedded

Subscribe to the magazine or E-letter
Live industry news | Submit new products http://submit.opensystemsmedia.com
WHITE PAPERS – Read: https://militaryembedded.com/whitepapers
WHITE PAPERS – Submit: http://submit.opensystemsmedia.com


SPECIAL REPORT: Enabling CJADC2 with Secure Tactical Clouds
12 Connected combat: How U.S. military branches are learning to fight as one By Dan Taylor, Technology Editor
MIL TECH TRENDS: Leveraging MOSA Strategies for Technology Refreshes
16 Achieving technology overmatch with system-on-module (SoM) embedded architecture By Rodger Hosking, Mercury
20 MOSA in defense acquisition: challenges, solutions, and a model By Marc Steiner, IMCO America
INDUSTRY SPOTLIGHT: Direct RF for EW & SIGINT Applications
24 Golden Dome: Nonkinetic weapon performance methods for negating and automating asymmetric missile-defense threats left of launch By Dr. John Carbone, Everfox
To unsubscribe, email your name, address, and subscription number as it appears on the label to: subscriptions@opensysmedia.com

The U.S. Department of Defense (DoD) Combined Joint All-Domain Command and Control (CJADC2) concept will connect sensors, platforms, and warfighters across multiple domains into a single network, similar to what the E-3A Airborne Warning and Control System (AWACS) aircraft – an integrated command-and-control battle management, surveillance, target detection, and tracking platform –has enabled on a smaller scale for decades. Pictured is a NATO E-3A AWACS platform. U.S. Air Force photo by William R. Lewis.
Develop and deploy technology faster with an innovative system-on-module approach that delivers high-bandwidth conversion and processing for applications at the edge.
FEATURES
Four 64 GSPS A/D and D/A converters
Altera™ Agilex 9 SoC FPGA 16 GB DDR4 SDRAM
100 GigE optical interfaces
FPGA design kit for custom IP development
Explore Mercury’s new direct RF solutions. mrcy.com/drfsom

Behlman Electronics, Inc. –When it comes to VPX, one company has the most flavors
13 Elma Electronic – Leaders in modular open standards enabling the modern warfighter
32 GMS – VIPER. The world's most advanced battlefield cross domain OpenVPX mission computer
9 LCR Embedded Systems, Inc. –Making MOSA work where it counts
5 Mercury Systems, Inc. –Maximize design flexibility with Direct RF
26 Pixus Technologies – SOSA aligned products in the slot profile configuration you need
17 State of the Art, Inc. –Reliability … the only option
embedded world North America November 4-6, 2025 Anaheim, CA https://embedded-world-na.com/
AOC 2025:
62nd Annual Association of Old Crows International Symposium & Convention December 9-11, 2025 National Harbor, MD
https://aoc2025.org/
Embedded Tech Trends (ETT) 2026 January 26 & 27, 2026 Savannah, GA
https://embeddedtechtrends.com/
AUVSI Xponential 2026 May 11-14, 2026 Detroit, MI
https://xponential.org/
GROUP EDITORIAL DIRECTOR John McHale john.mchale@opensysmedia.com
ASSISTANT MANAGING EDITOR Lisa Daigle lisa.daigle@opensysmedia.com
TECHNOLOGY EDITOR – WASHINGTON BUREAU Dan Taylor dan.taylor@opensysmedia.com
CREATIVE DIRECTOR Stephanie Sweet stephanie.sweet@opensysmedia.com
WEB DEVELOPER Paul Nelson paul.nelson@opensysmedia.com
EMAIL MARKETING SPECIALIST Drew Kaufman drew.kaufman@opensysmedia.com
WEBCAST MANAGER Marvin Augustyn marvin.augustyn@opensysmedia.com
VITA EDITORIAL DIRECTOR Jerry Gipper jerry.gipper@opensysmedia.com
DIRECTOR OF SALES Tom Varcie tom.varcie@opensysmedia.com (734) 748-9660
STRATEGIC ACCOUNT MANAGER Rebecca Barker rebecca.barker@opensysmedia.com (281) 724-8021
STRATEGIC ACCOUNT MANAGER Bill Barron bill.barron@opensysmedia.com (516) 376-9838
EAST COAST SALES MANAGER Bill Baumann bill.baumann@opensysmedia.com (609) 610-5400
SOUTHERN CAL REGIONAL SALES MANAGER Len Pettek len.pettek@opensysmedia.com (805) 231-9582
DIRECTOR OF SALES ENABLEMENT Barbara Quinlan barbara.quinlan@opensysmedia.com AND PRODUCT MARKETING (480) 236-8818
INSIDE SALES Amy Russell amy.russell@opensysmedia.com
STRATEGIC ACCOUNT MANAGER Lesley Harmoning lesley.harmoning@opensysmedia.com
EUROPEAN ACCOUNT MANAGER Jill Thibert jill.thibert@opensysmedia.com
TAIWAN SALES ACCOUNT MANAGER Patty Wu patty.wu@opensysmedia.com
CHINA SALES ACCOUNT MANAGER Judy Wang judywang2000@vip.126.com
CO-PRESIDENT Patrick Hopper patrick.hopper@opensysmedia.com
CO-PRESIDENT John McHale john.mchale@opensysmedia.com
DIRECTOR OF OPERATIONS AND CUSTOMER SUCCESS Gina Peter gina.peter@opensysmedia.com
GRAPHIC DESIGNER Kaitlyn Bellerson kaitlyn.bellerson@opensysmedia.com
FINANCIAL ASSISTANT Emily Verhoeks emily.verhoeks@opensysmedia.com
SUBSCRIPTION
By John M. McHale III
While speaking with embedded computing suppliers at the DSEI 2025 show in London in September, I heard growing support of requirements for open standards and open architectures, even if they don’t necessarily know about the U.S. Department of Defense (DoD) mandate for MOSA, or modular open systems approach, content.
“I haven’t seen open architecture or MOSA or CMOSS [C5ISR Modular Open Suite of Standards] requirements internationally,” Bill Guyan, SVP, Business Development & President, International, Leonardo DRS told me during an interview on the European defense market at DSEI (visit https://tinyurl.com/ ydwyfh9e to read the whole interview). “I have had a great deal of interest and curiosity on the part of our international customers about what’s going on – again, because in many cases, the systems and the architectures in use by international armies are not as advanced or complicated as the U.S. All of the benefits that come with MOSA don’t necessarily provide value to an international customer that doesn’t have electronic sensors, EO/IR sensors, three radios in a computer.”
Many European customers don’t bring up MOSA per se, but they do want VPX products and to build systems based on common standards, said Patrick Dietrich, President of Connect Tech, when we spoke at DSEI. VPX, an open standard – and an example of MOSA – has been used for years in European defense systems.
Large MOSA initiatives are often driven by large programs of record in the U.S.; such programs are rarer in European militaries, as their budgets are much smaller.
“While Europe doesn’t currently have a direct equivalent to the MOSA mandate or the SOSA [Sensor Open Systems Architecture] Technical Standard, there is strong momentum toward open standards across allied nations,” noted Paul Tanner, Vice President and General Manager, Mercury Systems International. “We’re seeing increasing alignment on the need for modular, scalable, and upgradeable systems to ensure readiness and strengthen collaboration across the transatlantic defense community.”
There might not be a European equivalent because of the value proposition, Guyan said.
“I don’t know that it’s caught on and that the value proposition is near the same as it is for the U.S.,” he continued. “The value proposition for MOSA and CMOSS is tied to three things: The first is complex architecture. The second is high-density systems out there in the field – you make a change, you’re changing thousands or tens of thousands of platforms. That’s
John.McHale@opensysmedia.com

very expensive. And the third thing is a continued commitment to modernization and upgrades. You want to keep the edge with your technical solutions, and CMOSS and MOSA promise the ability to do that more easily, more cost-effectively.
“I think also the fact that it is still fairly nascent in application in the U.S., [and that] those international customers that may have a need are still in a wait-and-see approach,” he added. “I think they’re doing a ‘let Uncle Sam kick the tires on this’ before they wade into the pool.”
Similarity to the SOSA approach
While it might not mention MOSA specifically, the U.K. Ministry of Defense (MoD) is starting to ask for technology aligned to the SOSA Technical Standard, especially in airborne situations, Nigel Norman, CEO of Sarsen Technology, told me at the show.
Noah Donaldson, Chief Technical Officer of Annapolis Micro Systems, speaking with Nigel and me, concurred, saying that the MoD released its own type of SOSA Technical Standard, called STICS or Standards for Integrated C5ISR/electronic warfare (EW) Systems.
“STICS is an approach that enables U.K. Strategic Command to achieve the rapid integration and reconfiguration of costeffective, high performance C5ISR/EW capabilities,” according to information from the MoD. “It is a set of federated open technical standards, system structures, modular building blocks and behaviors to enable industry to deliver open and modular C5ISR/EW systems.”
STICS [which the MoD released in May 2025] is very similar to CMOSS, Simon Collins, Director of Product Management at Abaco Systems, told me. The commonality regarding MoD versus DoD solutions is at the circuit-card and backplane level and common interfaces. The specification for a U.S. standard like VICTORY [which focuses on standardizing interfaces and protocols for military-vehicle communications] would be placed on top of that, or – for the U.K. MoD – where STICS specifications would exist, he explained.
Developing products that align to the SOSA Technical Standard for European embedded suppliers would be difficult because of the export regulations like the International Traffic in Arms Regulations (ITAR), said Flemming Chistensen, CEO at Sundance Microprocessor Technology. Because of ITAR, many European firms develop products based on open standards like VITA, for instance VPX and VITA 90. These standards are embraced by organizations like the SOSA Consortium, so customers can choose to adapt to them later on if needed.
By Dan Taylor, Technology Editor

A new General Dynamics Land Systems (GDLS) vehicle powered by artificial intelligence (AI) and designed in line with the modular open systems approach (MOSA) could serve as the “quarterback” of the Marine Corps’ future mobile reconnaissance battalions, according to a GDLS official involved with the program.
General Dynamics Land Systems has been testing the advanced reconnaissance vehicle (ARV) C4/UAS variant since last year at Michigan Technological University’s Keweenaw Research Center and the Army’s Detroit Arsenal. The vehicle uses AI to anticipate component failures and leverages software that enables the crew to control uncrewed aerial systems (UASs), according to the company. (Figure 1.)
This ARV variant features the company’s Next Generation Electronic Architecture (NGEA), which is built around MOSA and is intended to help scale the integration of new battlefield technologies. It’s also compatible with the Sensor Open Systems Architecture, or SOSA, Technical Standard, as well as with the C5ISR Modular Open Suite of Standards (CMOSS), says Christopher Dell, ARV program manager for GDLS.
NGEA “strongly supports interoperability and seamless integration with complementary systems and standards,” Dell says.
Dell notes that the design prioritizes modularity at all levels: “Our aim is to make ARV as modular and practical as possible to maintain in austere, field, and combat conditions.”
The university and military-arsenal testing aims to validate advanced logistics capabilities powered by embedded AI. To this end, GDLS uses a predictive maintenance suite known as Vehicle Intelligence Tools & Analytics for Logistics & Sustainment (VITALS), which is intended to increase uptime and mission readiness.

“AI and machine learning are integral to several aspects of our design,” Dell says. “VITALS can accurately predict component failures before they occur, thereby enhancing mission and operational readiness.”
The platform’s communications suite is engineered for integration with uncrewed systems, enabling the ARV to control uncrewed aerial systems (UASs) on the battlefield using onboard software, Dell says.
“A focus area in 2024 and into 2025 involved a maintenance and logistics capability assessment by Marines using the ARV,” Dell says. “To this end, General Dynamics Land Systems has incorporated modern digital maintenance and prognostic monitoring systems in the ARV.”
General Dynamics took feedback from the Marines and modified the design accordingly.
“Testing to this point has included Marines from across the light armored reconnaissance (LAR) and maintenance communities, to mention two important groups of stakeholders,” Dell says. “Their comments often are directly incorporated into iterative design uplifts.”
General Dynamics plans to deliver a second Systems Integration Lab (SIL) in 2025, alongside a new 30-mm ARV variant. The SIL is designed to replicate the full interior environment to provide immersive training and simulate real-world missions with full, representative vehicle functionality, GDLS officials say.


LCR is at the forefront of COTS open standards chassis and custom system designs for VPX, CMOSS, and SOSA architectures in accordance with MOSA directives. Intelligently engineered designs that bring operational advantage to the battlefield.
Find out how we can help you achieve mission success.
SERVING CRITICAL DEFENSE PROGRAMS FOR OVER 35 YEARS





By Dan Taylor, Technology Editor

AI-based networking architecture wins NASA contract Technology firm AiRANACULUS won a NASA contract to develop an advanced communications platform – leveraging artificial intelligence (AI) and machine learning (ML)-based wireless network solutions – that will be used to support exploration of the lunar surface. Under the terms of the contract, the company states, AiRANACULUS will design and prototype a dynamic network architecture intended to notably increase the range and reliability of lunar communications.
The AiRANACULUS product will integrate spectrum-aware cognitive radio technology, 3GPP Integrated Access and Backhaul, plus support for legacy NASA radio devices that will expand network coverage area and enable delay-tolerant communications.
AiRANACULUS will also leverage its INSPIRE network-management platform to enable protocol-agnostic, multivendor network optimization. The company affirms that the AiRANACULUS platform is expected to be a key piece of NASA’s upcoming manned Artemis missions to the Moon and Mars.
Manufacturing company Machina Labs, which deals in advanced manufacturing that combines artificial intelligence (AI) and robotics for the rapid production of metal structures, won a contract from the Air Force Research Laboratory (AFRL) in partnership with the Advanced Robotics for Manufacturing (ARM) Institute, a U.S. Department of Defense (DoD) Manufacturing Innovation Institute based in Pittsburgh, Pennsylvania.
According to the announcement, the contract is aimed at expanding the company’s flagship RoboCraftsman platform to leverage advanced AI and machine-learning capabilities intended to address DoD sustainment modernization needs. The company says the program initially will focus on automating toolpath generation for airframe skins and panels, which is critical to maintaining fleet readiness, and laying the foundation to extend these capabilities across additional sustainment applications.
CACI International won a five-year task order valued at as much as $180 million to provide secure network operations for Pacific Air Forces (PACAF) in support of U.S. IndoPacific Command, the company announced. The task order, awarded under the Air Force’s Base Infrastructure Modernization indefinite-delivery/indefinite-quantity contract, calls for CACI to operate, sustain, and modernize the Base Area Network across PACAF installations.
According to CACI, the effort will replace legacy infrastructure with software-defined networks and incorporate features such as zero-trust security, cloud integration, and multidomain operational support. CACI says the work is aimed at strengthening cyberdefense and ensuring resilient connectivity for Air Force personnel in the region.


Uncrewed rotary-wing system from Thales debuts with U.K. navy Thales noted the U.K. navy’s announcement of the official in-service date of the Thales Peregrine rotary-wing uncrewed air system (RWUAS) capability, which the company called “a major milestone in strengthening the Fleet’s intelligence, surveillance, and reconnaissance (ISR) effectiveness.”
The RWUAS – developed in partnership with UAS company Schiebel – gives the U.K. naval force a shipborne uncrewed aerial platform that “extends the eyes and ears of the Fleet far beyond the horizon,” according to Thales officials. Peregrine is equipped with the Thales I-Master radar and aims to deliver all-weather, day-and-night surveillance, tracking, and target identification in complex maritime and littoral environments. Thales officials term Peregrine “a core element of the Royal Navy’s Maritime Aviation Transformation Strategy, under which the navy is introducing a new generation of crewed and uncrewed systems.”
under Shield AI and HII partnership Shield AI and shipbuilder HII announced at DSEI UK 2025 a partnership to advance modular, cross-domain mission autonomy. Under the agreement, Shield AI’s Hivemind mission autonomy software will be leveraged with HII’s Odyssey suite to develop next-generation autonomous solutions.
“By pairing Shield AI’s cutting-edge Hivemind software with HII’s Odyssey suite, we are creating scalable, modular solutions that will give U.S. and allied forces an operational edge across every environment – air, land, surface, and undersea,” said Eric Chewning, executive vice president of maritime systems and corporate strategy at HII. “Our partnership with HII expands our commitment to delivering autonomy rapidly, safely, and repeatedly at scale across all domains,” said Nathan Michael, Shield AI’s CTO. “As we look toward the future of autonomy, we see our partnership with HII as a step toward redefining what maritime operations will look like.”
Raytheon $205 million Navy contract
Raytheon won a contract worth $205 million with the U.S. Navy for continued production of the Phalanx Close-In Weapon System (CIWS), which includes upgrades, conversions, overhauls, and related equipment.
The Raytheon announcement describes the Phalanx weapon system as a radar-guided, rapid-fire, computer-controlled gun designed to defeat antiship missiles and other close-in threats. The CIWS is installed on all U.S. Navy surface combatant ship classes and on the ships of 24 allied nations. Work on this contract will take place at RTX facilities in Louisville, Kentucky, and at other U.S. sites through 2029.
The SANCAR armed unmanned surface vehicle (AUSV), developed by HAVELSAN and Yonca Shipyard, completed live-fire trials in the Marmara Sea, according to the companies’ joint statement. The companies stated that the trials confirmed the AUSV’s ability to engage targets with a 12.7 mm stabilized weapon system, which was integrated with the ADVENT ROTA mission system and executed through the ADVENT combat-management system.
The AUSV is designed for multimission roles including port protection; intelligence, surveillance, and reconnaissance (ISR); mine countermeasures; and search and rescue. The vehicle is equipped with navigation radar, electro-optical cameras, sonar, and other sensors to support situational awareness in maritime operations.


By Dan Taylor
An Army radar detects incoming missiles while a Navy ship simultaneously tracks the same threats and an Air Force interceptor calculates engagement solutions. Within seconds, all three systems share data, coordinate responses, and execute a unified defense strategy without human operators manually relaying information between branches. This level of integration represents the end goal of Combined Joint All-Domain Command and Control (CJADC2); achieving this level of connection requires fundamentally rethinking how military systems communicate in hostile environments.
It’s all in the timing: Today’s adversaries can detect threats, make decisions, and launch attacks faster than traditional command structures can respond. When an Army radar spots incoming missiles, precious minutes tick by as operators relay information through radio calls and secure channels to Navy ships and Air Force interceptors that could help defend against the attack.
The solution sounds straightforward –connect everything electronically so all military branches see the same threats simultaneously. For the U.S. Department of Defense (DoD) that is the Combined
Joint All-Domain Command and Control (CJADC2) strategy, which will aim to connect sensors and shooters across all military services into a single network, ultimately enabling Joint All-Domain Operations (JADO) in cooperation with the U.S.’s allies, according to Lockheed Martin.
However, creating those connections opens new vulnerabilities that adversaries can exploit. Cloud networks that enable lightning-fast data sharing also create targets for cyberattacks. Communication links that work perfectly during training exercises may fail completely when enemies jam radio frequencies or cut internet cables.
Defense contractors are racing to close the breach with technologies borrowed from commercial Internet companies that are hardened for military use. Using these tools, artificial intelligence (AI) systems process sensor data faster than human analysts can read it, backup satellite networks activate automatically when ground communications fail, and zero-trust security protocols assume every network connection might be compromised and plan accordingly.
The role of CJADC2
The CJADC2 concept addresses a basic inefficiency: Military branches have traditionally fought with limited awareness of what other branches were doing, which leads to missed opportunities and wasted resources.
“The ‘C’ actually stands for combined,” says Ron Fehlen, national security space mission architect vice president at Lockheed Martin (Littleton, Colorado), during his keynote address at the CJADC2 At the Edge 2025 Virtual Summit presented by Military Embedded Systems. “It focuses now on exportability and how we share this across multiple systems, and not just the systems, but also our allies.”
[To watch the archived event, visit https://resources.embeddedcomputing. com/series/cjadc2-at-the-edge-2025virt/landing_page .]
Instead of Army radar operators spending minutes relaying threat information through human channels, all systems would share data instantly.
“In practical terms, it means a Navy ship, an Army radar, and an Air Force interceptor can all see the same picture and respond as one,” says John Breitenbach, director of aerospace and defense markets at RTI (Sunnyvale, California).
The vision extends internationally, which adds complexity since systems must work not only across U.S. branches but also with allied systems using different technologies and security protocols.
Justin Pearson, senior director of architecture and business growth for aerospace and defense at Wind River (Alameda, California), describes CJADC2 as “focused around the concept of enabling faster, more informed decision-making across all branches of the military” by connecting “systems/sensors/devices and decisionmakers across air, land, sea, space, and cyber domains in real time.”
The security challenge
Connecting military systems to cloud networks creates a problematic situation, however: The same links that speed up decision-making also give adversaries more ways to infiltrate. Traditional
military radios were built to work alone, but CJADC2 requires sharing classified information across networks that hostile forces actively target.
“The minute you spread data across more networks or push it to the cloud, you expand the attack surface,” Breitenbach notes. “Cloud connections, in particular, are prime targets for adversaries.”
Military systems cannot simply rely on the stable internet connections that commercial cloud services take for granted. “Tactical systems operate at the edge, where connectivity may often be intermittent and adversaries are actively trying to disrupt communications,” Pearson says. The challenge involves “maintaining cybersecurity and data integrity in highly dynamic, often hostile environments,” he adds.
Military planners must prepare for the worst case from Day 1, Breitenbach says. “The starting assumption has to be that edge systems will often be operating in DDIL







Go from development to deployment with the same backplane and integrated plug-in card payload set aligned to SOSATM and CMOSS. Includes chassis management, power and rugged enclosure for EO/IR, EW, SIGINT and C5ISR applications.
environments – disconnected, degraded, or contested,” he says, adding that systems can’t just shut down when cloud connections fail.
“Those systems need to continue functioning independently, and when they do reconnect, the data has to move securely,” Breitenbach continues. “That requires authenticating endpoints, encrypting data, and protecting information in flight.”
The requirements go beyond typical cybersecurity. Military systems must provide “secure data transmission, authenticating users and devices, and protecting against cyber intrusions, all while maintaining low latency,” Pearson notes. This must-have combination of security and speed creates engineering problems that commercial systems never face.
The solution requires “strong encryption, zero-trust architectures, and resilient network designs,” Pearson says. Technologies that assume networks are already compromised and plan accordingly, he adds.
Leveraging commercial innovation
The technologies addressing these challenges borrow from commercial innovations but harden them for life-or-death situations. “I see a lot of technologies like zero-trust networks, for example, where it’s recognized that you may not be able to trust the network you’re on, but you still need to pass the data,” Fehlen says.


The stakes differ dramatically between civilian and military applications. Fehlen illustrates with a personal example: “I’m flying out here to D.C. last night, and I’m on the plane and I’m doing email and I’m chatting with folks, and all of a sudden, the WiFi on the plane goes out. For me, it’s an inconvenience. In wartime or an operational environment, that’s a big deal.”
Defense contractors must design for inevitable disruption rather than hoping communications won’t fail. “The key is designing for resilience,” Breitenbach says. “In a contested environment, you have to assume communications will be interrupted – the question is how systems continue to operate when that happens.” (Figure 1.)
“The answer is redundancy and smart data handling,” he continues. “ By sending information over multiple paths, buffering it when links go down, and backfilling once they come back up, systems can maintain continuity.”
The approach accepts that stopping all attacks may be impossible. “You can’t stop an adversary from trying to jam or disrupt communications, but you can make sure the mission continues despite it,” Breitenbach notes.
Pearson points to emerging solutions: “Technologies such as mesh networking, low-Earth orbit (LEO) satellite constellations, and software-defined radio (SDR) are showing some promise. These systems can dynamically reroute communications, operate across multiple frequencies, and adapt to jamming attempts.”
AI’s potential
CJADC2’s success creates an unexpected problem: Connecting military systems means commanders will drown in more information than humans can process. Without AI to sort through this flood of data, the connectivity designed to speed decisions could slow them down by overwhelming operators.
“Once you get all that, you’re going to have a lot more than you had before,” Fehlen says. “How do you make sure that it doesn’t become a room full of humans
that has to go through it in detail?” The solution is for AI to step in and “put context to what they’re translating, so that they can turn that into something actionable,” he says. (Figure 2.)
The relationship works both ways. While AI processes more information, it needs reliable data to function, Breitenbach says. “AI is only as good as the data it receives,” he says. “I like to say data is oxygen for AI – without it, the algorithms suffocate.”
This dependency becomes critical when AI systems make life-or-death classifications.
“Think about a counter-UAS [uncrewed aerial system] scenario – an AI algorithm may be tasked with classifying whether an object is a bird, a drone, or a missile,” Breitenbach explains. “To make that call, it needs radar data, video feeds, and threat libraries, all fused together in real time.”
Timing leaves no room for error. “If that data is delayed, incomplete, or compromised, the AI can’t perform its mission –and the system could fail at the moment it’s needed most,” he adds.
Pearson sees AI handling multiple functions: He believes it could help with filtering noise, detecting anomalies, and
prioritizing threats in real time. “This allows commanders to focus on strategy while machines handle data fusion, pattern recognition, and rapid-response recommendations,” he says.
Systems architects will need to take location into account as they build these AI systems: “It will be important to have AI applied as close to the sensors and other sources of data as possible for a host of reasons: latency, security, network bandwidth, and robustness in a DDIL environment,” Pearson notes.
An unclear timeline
Predicting when the military will achieve complete cross-branch integration proves as challenging as the technical hurdles themselves. Industry experts agree the transition will happen gradually rather than through a single dramatic rollout.
“We’ll probably wake up one day and realize it,” Fehlen says. “And the reason I say that is because the ‘it’ starts from a very, very simple approach.” He draws an analogy to consumer technology: “If I think back to the first versions of the phone that I hold in my hand … I finally got rid of my last flip phone on my Verizon account as of two years ago, because they would no longer support it.”
Breitenbach sees substantial progress in specific areas. “Programs like IBCS [Integrated Battle Command System] and CBC2 [Cloud Based Command and Control] are showing what joint command and control can look like,” he says.
The challenge now involves connecting existing capabilities. “The next big step – and it’s what Golden Dome is all about – is pulling these together so they operate as one unified system of systems,” Breitenbach explains. [Golden Dome is a multi-layered missile defense system being developed by the U.S. military.]
Pearson also believes that while progress is accelerating, full integration is “still a multiyear journey,” with the main challenges being cultural alignment, technical interoperability, and a general harmonization across services. “Pilot programs and joint exercises are demonstrating the potential, but scaling these capabilities globally and securely will require sustained investment, collaboration, and innovation,” he asserts. MES
Open standards provide the technical backbone for CJADC2 [Combined Joint All-Domain Command and Control], but their importance goes beyond making systems talk to each other. They change how military systems are built and updated over time. “MOSA [the modular open systems approach] as a practice is very important,” says Ron Fehlen, national security space mission architect vice president at Lockheed Martin (Littleton, Colorado). “Implementing that within an architecture, so that everybody understands how it’s implemented specifically for certain mission sets, becomes pretty important. From our perspective, we look at it as valuable. It is where the commercial market is at now.”
In practice, military acquisition has evolved from past approaches. Fehlen acknowledges that as an acquisition officer a decade ago, he was more worried about just getting the capability out there and wasn’t worried about how to evolve the capability over time. That’s a much bigger consideration today. The philosophy has shifted from building systems designed to last decades unchanged to enabling continuous updates. “I want to build it for a year, then evolve it over time, and you need open architecture in order to do that,” Fehlen explains.
Not all standards deliver equal value. “Open standards are essential, and their importance will only grow as more systems need to work together. But it’s not just about having a standard – it has to be the right standard,” says Breitenbach. “Some have proven their value in real-world deployments, while others have added complexity without solving the real problems.”
Standards also enable flexibility beyond technical integration. “They’re the common language that allows systems, vendors, and even nations to connect, upgrade, and evolve together,” John Breitenbach, director of aerospace and defense markets at RTI (Sunnyvale, California) explains. “Without them, integration is brittle and costly; with them, militaries can modernize faster and respond more effectively to new threats.”
Justin Pearson, senior director of architecture and business growth for aerospace and defense at Wind River (Alameda, California), sees standards as essential for avoiding vendor dependence. “Open standards are essential to CJADC2 because they ensure interoperability, prevent vendor lockin, and strengthen security across joint-force operations,” he says. “By relying on community-driven frameworks … the DoD can unify data and workloads across air, land, sea, space, and cyber domains without being tied to a single vendor.”
Leveraging MOSA strategies for technology refreshes

By Rodger Hosking
Maintaining technological superiority requires rapid adoption of new commercial technology. System-on-module (SoM)-based designs can address the industry’s critical need for quickly deploying technology to keep pace with evolving requirements and adversarial advancements. SoM architecture can foster faster development, greater adaptability, and cost efficiency.
The rapidly evolving technological landscape in military and defense operations mandates systems that are not only high-performing but also adaptable, cost-effective, and quick to deploy. Military and defense systems are typically subject to stringent requirements, including ruggedness, reliability, real-time performance, and security. System-on-module (SoM) embedded system architectures have emerged as a solution to address these critical needs by offering an embedded subsystem that combines essential components, including processors, memory, communication interfaces, and sometimes data converters into a single compact module.
SoMs are a powerful, efficient, and flexible platform for a range of defense applications, allowing engineers to immediately start application development, port IP, and deploy on traditional and custom form factors. This flexible integrated approach is ideal for advanced defense applications including electronic warfare (EW), surveillance, radar, drones, and communication systems.
SoMs are designed to meet military-grade standards for temperature tolerance, vibration resistance, and electromagnetic compatibility, ensuring that they perform reliably even in challenging situations. Many defense applications, such as radar or missile guidance systems, require real-time data processing. SoMs, often equipped with FPGA [fieldprogrammable gate array] processors, offer the necessary computing power for fast data analysis, decision-making, and system control.
Because of their small size, SoMs support major initiatives to move these capabilities closer to the edge, often directly behind the antenna. By reducing weight, and power (SWaP) as well as cost, SoMs are highly appropriate for drone, aircraft, and mobile applications.
For the defense sector, timely delivery of new technology is often critical, especially in scenarios where technological superiority plays a decisive role. Traditional systems that involve custom designs and extensive testing can take years to develop. For example, several new families of direct RF devices combine multiple wideband ADCs and DACs [analog-todigital converters and digital-to-analog converters] capable of digitizing RF signals up to 36 GHz with FPGAs containing powerful vector processors and artificial intelligence (AI) engines. Housed in a single ball-grid-array (BGA) package, they also sport onboard Arm processors to control operations. These devices perform RF signal acquisition, real-time processing, and generation to notably extend the performance levels of military radar, EW, and communications systems.
However, because the BGA array pins of direct RF devices are so tightly spaced, designing them into products requires significant engineering effort. The numerous wideband analog RF signals must be shielded from multiple high-current switching power supplies, and hundreds of digital gigabit serial signals for SDRAM, 100 GbE, all operating within the same frequency band. Extensive signal-integrity (SI) analysis modeling is essential for circuit board signal and shield traces, layer stack-up, and ground plane geometries to optimize crosstalk, impedance, differential skew, and dynamic range. For such extreme design complexity, SI analysis must often be iterated several times before performance objectives are met.
One major advantage of SoM architectures is that once SoM circuit board design goals are verified at the SoM signal connectors for analog RF, clocks, and digital I/O, the SoM can be installed
on a carrier board to bring those signals to the required signal connections of the system. Designing a carrier board is comparatively simple, because all of the critical work of properly protecting BGA pin signals of the direct RF device has already been optimized within the SoM. This customizability enables defense organizations to select the right SoM for specific missions, whether it be for tactical communication systems, sensor networks, or autonomous vehicles.
SoMs enable defense industry engineers to quickly prototype new systems by selecting SoMs that are already thoroughly tested and validated. These modules can be integrated into new systems with minimal design complexity, notably reducing development time. This capability enables the faster rollout of cutting-edge technology, so that military missions can take advantage of the latest innovations to maintain defense superiority.

NASA first selected our chip resistors for a mission to Jupiter and Saturn that launched in 1977 and is still operating in interstellar space. Our chip resistors continue to be selected for high reliability applications on Earth and in space. On Earth, our resistors are selected for mission critical applications in military weapon and defense systems. In space, our chips are found in weather and communications satellites and on missions to Mars, Jupiter, and Pluto.
Choose State of the Art resistors.

With defense budgets under increasing scrutiny, cost control is essential not only for military organizations, but also for contractors competing for design wins. SoMs help reduce costs in several ways, making them an attractive choice for defense applications.
SoMs enable military contractors to take advantage of economies of scale. Because SoMs are often produced in larger quantities, production volumes provide cost savings that are passed on to defense organizations. This cost reduction is critical, especially when developing large-scale systems such as fleets of drones or extensive surveillance networks. Phased-array antenna systems require independent channels for each element, further emphasizing the importance of reducing SWaP and cost per channel.
Instead of developing new products from the ground up, manufacturers can leverage existing SoM platforms and focus their efforts on integrating the modules into specific defense systems rather than developing entire architectures from scratch. Software and firmware development costs traditionally account for a major portion of new product engineering.
Because SoMs usually represent the core technology of the derivative carrier products, their existing firmware, software, FPGA code, and high-level APIs are all highly reusable, greatly reducing overall engineering costs.
For similar reasons, qualification testing of SoM-based products is streamlined by borrowing heavily from the test procedures for the functional, security, reliability, and environmental requirements already established for the SoM, usually the most complex portion of the product.
The integration of SoMs also helps reduce ongoing maintenance costs. Since the modules are pre-validated and reliable, the likelihood of system failures is reduced. Additionally, the modular nature of SoMs means that replacing or repairing faulty components is often simpler and far more cost-effective than repairing complex nonmodular, custom-designed systems.
Putting SoMs to work
As a Xilinx early access partner, Mercury developed its Quartz SoM mezzanine card, performing three iterations of signal integrity analysis to optimize all signal performance metrics. The company’s family of 14 Quartz SoM carrier products adds a 3U SOSA-aligned VPX card, a PCIe card, two small-form-factor subsystems, and


a ruggedized weatherproof enclosure, shown in Figure 1.
The Quartz SoM-based products can digitize 2 GHz of instantaneous signal bandwidth for transceiver applications including multi-channel phased array systems for radar, EW, communications, signals intelligence, and countermeasures.
Mercury also offers the Agilex 9 product family based on Altera’s Agilex 9 Direct RF SoC FPGA Series sporting 64 GS/sec 10-bit ADCs and DACs, Agilex 9 FPGA resources, and multiple ARM processors. The Agilex 9 ARGW014 device features four ADCs and DACs, while the AGRW027 device features eight ADCs and DACs and roughly twice the FPGA resources of the former device in a larger multi-chip module.
SoM embedded system architectures address critical needs by offering reliable, rugged, and real-time capable systems. SoMs accelerate the delivery of new technology, reduce costs through modularity and economies of scale, improve interoperability across platforms, and provide the adaptability needed to meet the evolving challenges of modern defense. SoMs will continue to play an increasingly vital role in shaping the future of military technology. MES

Rodger Hosking is vice president, Mercury Systems Mixed Signal.














Rodger has more than 30 years in the electronics industry and is one of the co-founders of Pentek; he has authored hundreds of articles about software radio and digital signal processing. Prior to Pentek, he served as engineering manager at Wavetek/Rockland, and he holds patents in frequency synthesis and spectrum-analysis techniques. He holds a BS degree in physics from Allegheny College in Pennsylvania and BSEE and MSEE degrees from Columbia University in New York.

®

Most manufacturers offer just a few VPX power supplies off the shelf, with high costs for full-custom. The Behlman the most COTS AC to DC and DC to DC units configured for a wide range of high-end industrial and military applications. All feature our state-of-the-art new engineering standard, Xtra-reliable design and Xtra-rugged construction.
Insist on the leader. Not just VPX,




By Marc Steiner
The U.S. Department of Defense (DoD) is adopting a modular open systems approach (MOSA) to keep pace with rapidly evolving threats. MOSA creates long-term value by making systems easier to upgrade, maintain, and integrate. Its success will depend on clear standards, robust cybersecurity, and cultural shifts in acquisition practices. It has the potential to deliver rapid technological upgrades and improved interoperability to those who need it on the battlefield.
The modern battlefield evolves much faster than current defense acquisition programs, as weapon systems become increasingly complex, interconnected and costly. The Fiscal Year 2021 (FY2021) National Defense Authorization Act mandates a modular open systems approach (MOSA) implementation to “the maximum extent practicable” to make weapon systems more flexible, upgradable, and cost-effective over their
life cycle. Beyond just a design philosophy, MOSA is a deliberate technical and operations strategy to create more sustainable defense acquisition programs.
Technically, MOSA ensures that defense systems – from physical weapons to digital networks – are easier to develop, maintain, and upgrade. Systems designed with modular architectures are less likely to become obsolete because
they provide the flexibility needed to integrate new capabilities as they emerge without needing to redesign the entire system.
From an operational perspective, MOSA enables the U.S. Department of Defense (DoD) to acquire modules – the system’s components – from multiple vendors, enhancing competition and reducing costs over the system’s life cycle. With open

competition for individual components, MOSA encourages vendors to innovate and reduces the DoD’s dependence on legacy suppliers. Furthermore, as MOSA leverages universal standards it improves interoperability while saving cost because components can be reused across platforms and programs.
Together, these technical and operational benefits accelerate acquisition programs, which is essential for DoD to maintain technological superiority in the face of evolving threats.
While the intentions driving MOSA are admirable, achieving true MOSA across the entire DoD is proving to be much easier said than done. To attain MOSA at scale, the DoD must first clarify and formalize its standards.
At its core, MOSA enables defense systems to be modular, loosely coupled, and highly cohesive, similar to the concept of “plug-and-play” components in
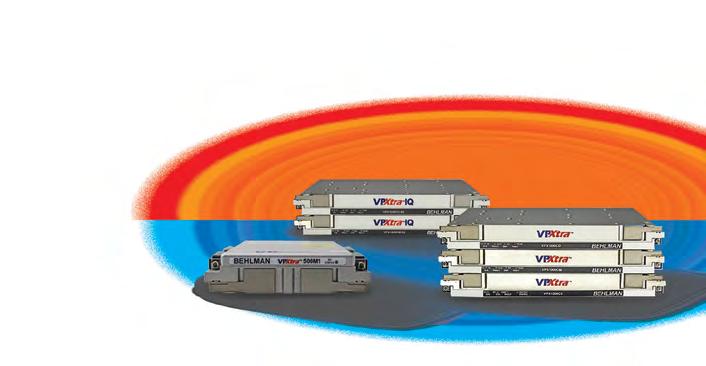
commercial computing. A weapon system designed with MOSA principles consists of components – such as engines, sensors, and software modules – connected through well-defined interfaces that adhere to universal standards. One such standard is the U.S. Army’s VICTORY [Vehicle Integration for C4ISR/EW Interoperability].
VICTORY is specifically designed to modernize ground-vehicle networks. By replacing point-to-point cabling with a shared, Ethernet-based architecture and using standards like time-sensitive networking (TSN), VICTORY enables different mission systems to share data and resources more efficiently.

Figure 1 shows VICTORY’s basic tenets, including proving architecture compliance via testing, identifying a roadmap from current to future architectures, and treating information assurance as essential.
These standards detail a network-based architecture for integrating electronic systems on ground vehicles. They aim to support a full spectrum of platform functionality, from simple, low-functionality platforms to highly sophisticated ones. Moreover, they’re intentionally designed to strike a balance between allowing subsystems to interoperate as necessary, while simultaneously empowering manufacturers to propose novel implementations.
MOSA interfaces at large can encompass physical connections, power requirements, data protocols, and communication methods. Importantly, not all interfaces in a

system need to be open. MOSA standards like VICTORY should focus on key interfaces that are likely to change, fail, or require interoperability.
By isolating functionality into modules and standardizing critical interfaces, MOSA can meet its key goal: allowing components to be easily added, replaced, or upgraded without redesigning the entire system.
MOSA: Easier said than done
Even with well-defined standards, transitioning to MOSA presents significant challenges. For one, open interfaces can introduce cybersecurity risks. If they’re not properly secured, these interfaces may allow unauthorized access to classified systems or data. It’s essential to implement robust cybersecurity measures, including authentication, encryption, and continuous monitoring, to prevent potential exploitation.
In addition to introducing cyber vulnerabilities, the transition to MOSA requires significant upfront investment. While MOSA has long-term cost-saving benefits, applying MOSA to existing legacy systems can be expensive, often demanding extensive engineering work and acquisition of interface data rights. Requirements like open standards licenses, digital engineering tools, and personnel trained in modular architectures are costly, both in terms of time and funding. With countless competing priorities, these initial investments can seem overwhelming.
AirBorn’s VPX Power Module is a VITA 62, Open VPX compliant, 6U system with models for a 270 VDC input IAW MIL-STD-704.
Auxiliary DC Output: +3.3V/60A
Peak Efficiency of 95%
Input-Output Isolation 2100VDC
Main DC Output: +12V/180A
Overvoltage, Overload, & Overtemperature Protection
Programmable Regulated Current Limit
VITA 46.11 System Management

Beyond technical and financial hurdles, there is the human element. MOSA’s principles contrast starkly with traditional acquisition and integration practices, meaning program managers and system integrators must adopt an entirely new mindset: one that prioritizes modularity, flexibility, and iterative upgrades over individual acquisitions. Training requirements and maintenance protocols must evolve in parallel to complement modular systems.
Overcoming these challenges requires deliberate planning, extensive coordination, and technical precision. It’s important for system designers to integrate
360 is a 360-degree, live-view situational-awareness system built for armored vehicles operating in dynamic and high-risk environments. The system leverages artificial intelligence (AI)-driven processing capabilities with a mission computer, high-end video matrix, and a wide array of sensors. Image courtesy IMCO.
modularity into all designs from the outset, at both the interface and application layers. Open, standardized interfaces enable interoperability and reduce integration friction, while application layer flexibility ensures modular components can serve multiple functions based on operational requirements.
System architectures should also support future growth by allowing for rapid upgrades. When implemented effectively, these strategies allow modular systems to adopt plug-and-play upgrades, replacing outdated components without disrupting the broader platform.
MOSA in action
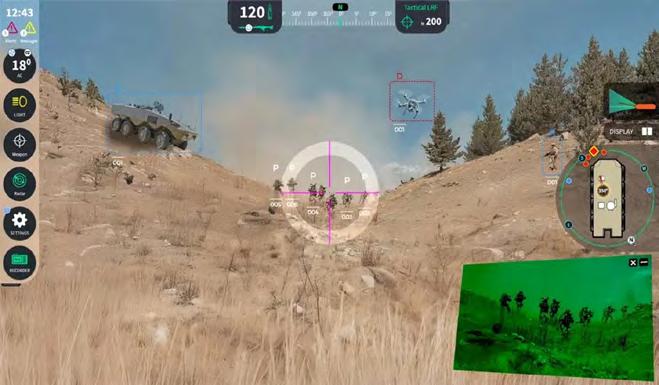
A concrete example of MOSA in action is the SAVS 360, an AI-powered situationalawareness video system for armored vehicles. SAVS 360 integrates day and night sensors with advanced video processing to give crews 360-degree visibility and real-time threat detection, even while the vehicle’s hatches are closed.
This system exemplifies MOSA principles through its modular architecture, enabling upgrade or replacement of sensors, processing units, and interfaces without impacting the entire vehicle. Open system integration ensures that SAVS 360 can be deployed across multiple platforms, supporting interoperability and rapid technology refreshes.
The system’s core technology is an advanced AI-powered video matrix. Its modular nature enables any configuration of sensors to be easily integrated into a central processing unit distributing real-time data and video analytics throughout the vehicle’s systems and users. (Figure 2.)
An ever-growing challenge is the need to be able to adopt improvements in hardware and software for the different vehicles’ applications.
IMCO’s vehicle computing module enables a “remove and replace” approach to the main computing modules of the most advanced armored-vehicle platforms. A unified box hosting upgradable, standalone, computing units enables both logistics and support flexibility as well as ease of upgrade in both software and hardware capabilities without the need to change anything in the vehicle. (Figure 3.)
The remove and replace approach demonstrates how modular, open systems can accelerate fielding, simplify maintenance, and rapidly integrate emerging technologies.

After the shift
MOSA is a fundamental shift in the DoD’s acquisition philosophy. By emphasizing modular design, open interfaces, and life cycle-oriented planning, MOSA will enable the DoD to deploy adaptable, competitive, and cost-effective systems.
Despite challenges such as cybersecurity concerns, the reality of legacy system upgrades, and resource constraints, MOSA is an imperative goal. With consistent and clear coordination between the DoD and its industry partners, intentional design practices, and well-defined standards, the defense industrial base can overcome these obstacles to attain MOSA.
With technological advancements outpacing acquisition timelines, MOSA is a powerful and necessary strategy for the DoD to maintain its superiority on the world stage. It’s vital for the defense industrial base to wholeheartedly embrace this new mindset and support the DoD as it transitions to MOSA at scale. MES

Marc Steiner is the CEO of IMCO America. In this role, he ensures IMCO America delivers cuttingedge technologies that advance aerospace and defense missions. Before joining the private sector, Marc served as a U.S. Navy officer and Fleet Support Branch Chief at the National GeospatialIntelligence Agency.
IMCO America • https://imco-america.

By Dr. John Carbone
Current global instability, continued proliferation of medium- and long-range missiles, and increasingly sophisticated threats such as maneuvering reentry vehicles pose significant challenges for fielded ballistic missile defense systems (BMDSs). In response to progressively heightened real-time threats, Golden Dome’s three-year gauntlet has been laid down. Exponential technology evolution has created broad-spectrum, nonkinetic opportunities to qualitatively augment BMDS. A probabilistic “system of systems” (SoS) approach is described to harness kinetic, nonkinetic, and automated cross-domain access and transfer solutions for enabling secure C5ISR [command, control, computers, communications, cyber, intelligence, surveillance, and reconnaissance] systems and artificial intelligence (AI) platform interoperability. The cross-domain solutions can then be expeditiously deployed from cloud service provider (CSP) data centers to the tactical edge. The SoS approach aids enhanced qualitative decision-making and effector competence to satisfy complex battle operations “left of launch.”
Well-known solutions exist that provide performance assessment of kinetic solutions. Probability of single shot engagement kill (PSSEK) measures effectiveness but considers only kinetic means to neutralize a ballistic missile threat. PSSEK expresses the reliability of the combat system operating correctly as Pes and Pcs, and the probability of the interceptor neutralizing the threat (PSSK).
PSSEK =Pes*(Pcs*)Prel*PCTS*PFOV*Pdiv =Pes*(Pcs*)*PSSK, where
Probabilities:
› Pes: system engagement support services operate correctly,
› Pcs: operational reliability of system communication,
› Prel: interceptor, kill vehicle, and missile reliability,
› Pcts: correct target selection,
› Pcontain: interceptor can contain a threat given the engagement support =PFOV*Pdiv where PFOV is the probability user has field-of-view containment and,
Ptip =POCCURRENCE*PAVAILABLE*PSENSE*PTIME
› Pdiv: diverting containment.
These methods for calculating success are notional at best and ambiguous in often vast, complex environments, necessitating new solutions.
Moreover, the Common Vulnerability Scoring System (CVSS) exists to identify and prioritize vulnerabilities that pose the greatest risk. However, vulnerabilities are assigned arbitrary scores, and CVSS does not provide a method to convert scores into probability distributions.
An SoS approach is proposed for providing a comprehensive and task-oriented environment specifically focused on the needs of current BMDS rather than less beneficial enhancements to combat systems, sensor performance or interceptors. An SoS approach supports more informed decision-making and improved overall missile defense.
Traditional kinetic-only missile-defense methods need to evolve to a more holistic and contextually achievable asymmetric missile defense (AMD) approach (Figure 1).
Integrated kinetic and nonkinetic battle management
The AMD is a four-layer approach providing a mathematical method and algorithms to automatically combine and assess the performance of nonkinetic and kinetic techniques for negating missile threats. AMD integrates cyber technologies; intelligence,
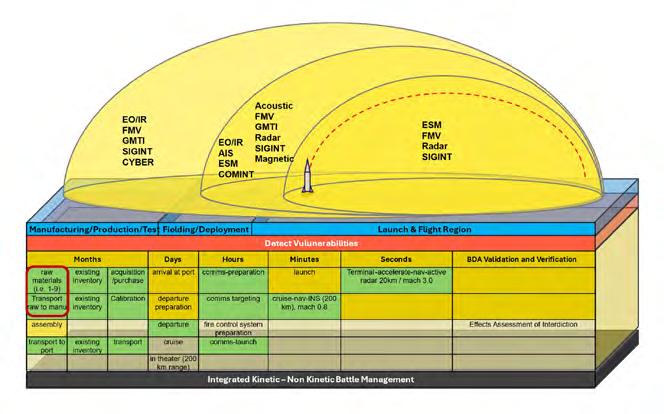
surveillance, and reconnaissance (ISR) knowledge; processing exploitation and dissemination (PED); analytics; artificial intelligence (AI); and electronic warfare (EW). These includes proven techniques like decoys and battle management (kinetic and nonkinetic) for negating missile threats, not only during flight phases but more importantly “left of launch,” the term used to describe the strategy of taking preemptive actions to prevent an attack or threat before it happens.
Figure 1 illustrates a layered AMD operational view depicting integrated kinetic and nonkinetic battle management of detectable vulnerabilities. The graphic depicts sensing types and their notional ranges for supporting enhanced effector actions. The red outline shows a potential interdiction option, months in advance of launch, which could disrupt an adversary’s use of required raw materials.
AMD’s four layers are:
1. The core level, where a Pnegation (Pn) score is computed for each Vulnerability and Technique (VT) pair.
2. A temporal level that converts VT scores into random variables, derives probability distribution functions for each and establishes conditions Pn(VT) for Time (Ti), where Pn(VTTi) is calculated for each VT pair.
3. The Battle Damage Assessment (BDA) level, where Pn(VTTi) values relate the potential technique used with probability of deployment validation (Pvd) or (Ptip) and probability of mitigation verification (Pv,n).
4. A terminal phase level Pn, calculated by combining Pn values related to each of the AMD layers.
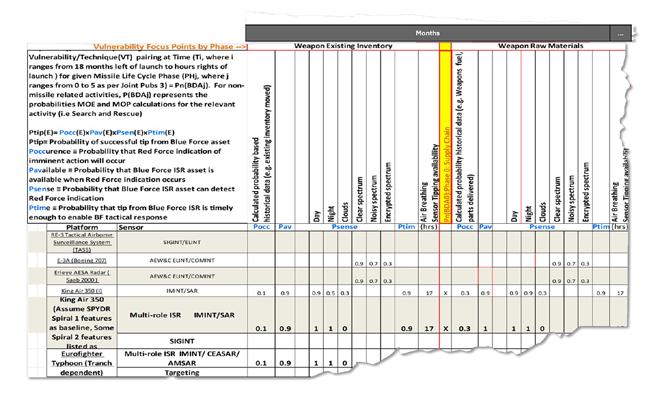
Figure 2 depicts BMDS threat vulnerability focus points by phase, where computations are based upon platform, sensor type, and availability of required intelligence to optimize the probability of negation Pn. Simple and complex negation opportunities and scenarios drive required responses.
Responses to all questions drive probability Ptip values, where:
› POCCURRENCE: enemy indication of imminent action will occur,
› PAVAILABLE: friendly ISR assets are available when enemy indication occurs,
enable real-time response and effective negation. Simultaneously, an instantaneous adversarial response requires deployment of more adaptive capabilities and rapid injection of new capabilities, including eventual autonomous DevSecOps [development, security, and operations].
PSSEK =Pes*(Pcs*)Prel*PCTS*PFOV*Pdiv =Pes*(Pcs*)*PSSK, where
› PSENSE: friendly ISR assets may be able to detect enemy indication,
› PTIME: tip from friendly ISR is timely enough to enable blue force (BF) tactical response,
› Ptip: successful tip from friendly ISR assets.
Ptip =POCCURRENCE*PAVAILABLE*PSENSE*PTIME
Automating embedded and enterprise analysis and negation
Complex multidomain, multimodality, realtime threat regions must consider many distributed platforms, AI deployments, sensors, effectors, and decision-makers. These complexities necessitate more rapid interoperability and autonomy to
Each of these systems operates on networks at varying classification levels. Every physical device, sensor, platform AI analysis system, and user must be able to access these networks from varying threat-level access points. Mitigating these challenges and




With a huge selection of SOSA aligned backplane & configuration options, Pixus has a solution for you. We offer a vast array of slot sizes in speeds to 100GbE, PCIe Gen4, & beyond. Contact Pixus today!



increasing effective autonomy for realtime threat negation requires accredited high-speed enterprise and embedded cross-domain solutions (CDSs).
CDSs provide data integrity to enable secure, automated, multi-classification operations. This provides enforced unidirectional flow, malware removal, and highly enforced data integrity. Finally, proper placement, automated configurations, and system-integrity functions provide scalable CDS, which can then be expeditiously deployed from cloud service provider (CSP) data centers to the tactical edge.
To mitigate increasingly sophisticated threats and challenges for fielded BMDS, a probabilistic four-layer AMD SoS approach can be used. This approach responds to multidomain, real-time threats, automated integration of AI technologies, and a broad spectrum of nonkinetic techniques to create substantial asymmetric opportunities to qualitatively augment BMDS. This SoS approach can harness kinetic and no-kinetic opportunities to detect adversary vulnerabilities and automate C5ISR with cross-domain system interoperability. Leveraging and extending existing effective solutions can mitigate real-time threats, even those “left of launch.” MES

Dr. John Carbone is Senior Technical Director and Chief Solutions Architect at Everfox. He is also an eight-year Adjunct Professor of Applied AI and Data Science at Baylor University. Dr. Carbone has more than 37 years of experience engineering U.S. defense-industry mission-critical warfighting systems across C5ISR systems, high-performance computing, cloud, modeling, and kill-chain optimization from operations centers to the tactical edge. He holds GIS, datascience, and missile-defense patents, and has published more than 100 AI, engineering, and data science books/ publications. Readers may reach Dr. Carbone at john.carbone@everfox.com.
Everfox
https://www.everfox.com/
1. Hershey, Paul C., Robert E. Dehnert, John J. Williams, John N. Carbone, Jeanne M. Robinson, and David J. Wisniewski. “Method for non-kinetic performance assessment.” U.S. Patent 9,779,191 issued October 3, 2017.
2. Brown, G., et al. “A two-sided optimization for theater ballistic missile defense.” Operations research 53.5 (2005): 745-763.*
3. Mell, P., et al. “Common vulnerability scoring system.” Security & Privacy, IEEE 4.6 (2006): 85-89.*
4. Garrett, R., et al. “Managing the interstitials, a system of systems framework suited for the ballistic missile defense system.” Systems
5. Pate-Cornell, E. “Fusion of intelligence information: A Bayesian approach.” Risk Analysis 22.3 (2002): 445-454.*
6. Kopp, Carlo, et al., “High Energy Laser Directed Energy Weapons”, © 2006-2012 Carlo Kopp, Technical Report APA-TR-2008-0501, Defense Today, 2006 Series, (May 2008), 39 pgs.
7. Mell. Peter, et al., “CVSS, A Complete Guide to the Common Vulnerability Scoring System”, Version 2.0 National Institute of Standards and Technology, Carnegie Mellon University, (Jun. 2007), 1-23.
8. Shein, Rob, “A Brief Summary of Cyber Warfare”, Information Security Management Handbook, Sixth Edition, vol. 4, Tipton, H.F., et al., Editors, Auerbach Publications, (2010), 6 pgs.

By James Kubik, Somewear Labs
On today’s battlefield, the task of ensuring that critical data reaches the tip of the spear more quickly and reliably is pivotal, yet is sometimes overlooked. While major investments have been made in bolstering data flow to and from the tactical operations center (TOC), this reality disregards the most critical part of the battlespace: the ultimate edge, or the last mile, where forward-deployed warfighters and unmanned systems operate. Here, connectivity isn’t just a convenience – it’s the lifeline for split-second decisions and survivability. In an autonomy-first world, warfighters need a new paradigm for supporting operators where it matters most.
The disconnect in pushing actionable intelligence to this last mile directly undermines the front line’s ability to make swift, informed decisions and effectively manage deployed unmanned systems, especially in contested environments. Legacy communication systems compound this problem: They can be inherently rigid, incapable of dynamically adapting to changing spectrum conditions, fluctuating bandwidth availability, or evolving mission requirements. They don’t gracefully degrade or intelligently route data when networks become constrained, which forces warfighters to manually juggle multiple network, which then creates an unsustainable cognitive load that detracts from the primary mission.
The ultimate edge demands intelligent, resilient networking governed by software. While comms specialists have manually managed multiple links for decades, the future fight requires highly dynamic, automated orchestration. Imagine warfighters and unmanned systems seamlessly accessing critical intelligence across a myriad of communication modalities – from 5G and MANET to mesh and narrowband satellite – without needing to adjust network settings on the move.
Achieving this vision requires overcoming a persistent obstacle: the lack of interoperability. When network design prioritizes isolated functionality over open standards, warfighters face a fragmented battlespace. Data silos emerge, communications black holes divide units, and teams resort to cumbersome integrations to share vital information. This fundamental lack of interoperability severely restricts the scalability of operations, making it incredibly difficult to rapidly deploy and integrate new units or technologies. It cripples the ability to collaborate effectively across diverse elements of the Joint Force, slowing decision cycles and ultimately putting lives and missions at risk.
For emerging technologies to make an impact on the battlespace, they must be MOSA [modular open systems approach]compliant. Managing data across various networks is one challenge, but intelligently routing it across disparate systems and into different situational awareness platforms requires

flexibility and interoperability. This foundational shift enables maximum situational awareness for every warfighter and decision-maker across the Joint Force, unlocking the full potential of integrated operations.
This uninterrupted connection for every asset, warfighter, and command element is foundational to realizing the last mile of CJADC2, ensuring maximum situational awareness across the battlespace.
The pursuit of seamless integration and complete situational awareness becomes even more critical with the escalating proliferation of unmanned aerial systems (UASs). Warfighters increasingly depend on these assets for everything from reconnaissance to precision targeting, often needing them to deploy and act in a moment’s notice. For these systems to operate effectively – especially in coordinated efforts like swarming or complex collaborative missions – interoperability across deployed UAS is non-negotiable. A drone that cannot communicate with its robotic partner or fails to fluidly share data with a human operator or command element becomes an isolated tool, not a force multiplier.
Merely fielding more drones is insufficient; the true challenge lies in equipping these assets with reliable and resilient communications payloads. Without resilient data links, even the most advanced UAS becomes a liability when pushed beyond-visualline-of-sight (BVLOS) or into contested environments, severing the vital connection between asset, operator, and command. This isn’t just about avoiding jammers; it’s about ensuring persistent, high-fidelity data flow for true autonomy – extending human reach, gathering critical intelligence, and executing tasks in high-risk zones without putting warfighters in harm’s way.
This uninterrupted connection for every asset, warfighter, and command element is foundational to realizing the last mile of CJADC2, ensuring maximum situational awareness across the battlespace. The White House’s recent American Drone Dominance Executive Order highlights the urgency of this very challenge, emphasizing the need for robust, secure, and resilient drone ecosystems. Development and deployment of communications solutions that can withstand the rigors of multi-domain operations and leverage diverse networks will actively strengthen the Defense Industrial Base and solve for the critical last mile of CJADC2.
James Kubik is CEO of Somewear Labs.
Somewear Labs • https://somewearlabs.com




Military Embedded Systems focuses on embedded electronics – hardware and software – for military applications through technical coverage of all parts of the design process. The website, e-mags, newsletters, podcasts, virtual events, annual Resource Guide, and print editions cover topics including radar and electronic warfare, artificial intelligence/machine learning, uncrewed systems, C5ISR, avionics, and cybersecurity. Don’t miss any of it!
Military Embedded Systems is also the largest source for coverage of the Sensor Open Systems Architecture, or SOSA, Technical Standard and the Future Airborne Capability Environment, or FACE, Technical Standard. We exclusively produce the once-yearly SOSA Special Edition and FACE Special Edition. militaryembedded.com
Each issue, the editorial staff of Military Embedded Systems will highlight a different organization that benefits the military, veterans, and their families. We are honored to cover the technology that protects those who protect us every day.
By Editorial Staff

This month we are spotlighting Everyone For Veterans (E4V), a 501(c)(3) nonprofit organization that provides free comprehensive dental care and financial support to eligible veterans and families. The E4V website notes that only about 8% of veterans that are enrolled in the Veterans Administration (VA) healthcare system qualify for VA dental benefits.
Washington state dentist and periodontist Dr. Theresa Cheng started a local grassroots effort in 2008 to help veterans and their spouses with dental care, and grew the organization into a national charitable vehicle in 2017.
E4V – which serves honorably discharged veterans who have completed at least one enlistment period, plus their spouses and children – works with volunteer dental professionals across the U.S. to provide free, comprehensive dental care, resources, and support. E4V’s No-Cost Comprehensive Dental Care Program helps resolve dental problems for veterans, and it also sets them up for long-term oral care and overall health, which helps break the cycle of needing expensive urgent care.
E4V finds dental professionals to provide pro bono services in the communities where the veterans live; by sourcing dentists in the communities where they live, the likelihood of continuation of care is increased. The E4V website cites that it has signed up more than 680 volunteer dentists across 34 states; the organization says that applications for care increased 543% in 2024. The extensive waiting list, say the charity’s officials, underscores the urgent need for more dental professionals to lend their support.
E4V volunteers have donated more than $1 million worth of dental care over five years, the organization states, lending more than 850 hours of volunteer support.
For additional information, visit https://www.everyoneforveterans.org/.
Sponsored by Cubic/DTECH, Elma, Wind River, and RTI
The U.S. Department of Defense (DoD) Combined Joint AllDomain Command and Control (CJADC2) strategy “is not a single system, but a series of interconnected capabilities from the edge to the boardroom, providing the Joint commander with sensors and systems across the tactical, operational, and strategic levels to create a clearer picture of the current situation in the fog of war,” according to the DoD’s Chief Digital Artificial Intelligence Office (CDAO).
Powered by Military Embedded Systems, the CJADC2 At the Edge Virtual Summit’s sessions are designed to drive awareness and thought leadership around CJADC2 concepts and requirements and to study how artificial intelligence (AI), secure communications, high-performance computing, cyber operations, data connectivity, and other embedded technology solutions will impact system designs. (This is an archived event.)
Watch this webcast: https://tinyurl.com/4ascxfdn
Watch additional webcasts: https://militaryembedded.com/webcasts
By Rohde & Schwarz
In today’s rapidly evolving battlefield, the electromagnetic spectrum (EMS) is a coveted and limited resource, essential for effective communication across land, sea, air, and space. As information superiority becomes increasingly vital, the role of strategic communications-intelligence interception centers is crucial for national intelligence agencies tasked with anticipating and monitoring threats. In a world where speed is paramount, the ability to quickly analyze and interpret signals can mean the difference between success and failure.

In this white paper, learn how high-speed postprocessing of signals can significantly enhance operational effectiveness. It explores three key aspects of signal analysis: the significance of retrospective signal analysis; the role of situational awareness in EMS; and the benefits and methods of postprocessing signals across the intelligence cycle.
Read the white paper: https://tinyurl.com/4nyj9x6w
Get more white papers and e-Books: https://militaryembedded.com/whitepapers





TECHNOLOGY, TRENDS, AND

Military Embedded Systems focuses on embedded electronics – hardware and software – for military applications through technical coverage of all parts of the design process. The website, Resource Guide, e-mags, newsletters, podcasts, webcasts, and print editions provide insight on embedded tools and strategies including technology insertion, obsolescence management, standards adoption, and many other military-specific technical subjects.
Coverage areas include the latest innovative products, technology, and market trends driving military embedded applications such as radar, electronic warfare, unmanned systems, cybersecurity, AI and machine learning, avionics, and more. Each issue is full of the information readers need to stay connected to the pulse of embedded technology in the military and aerospace industries.









