
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Prof.Rita Kadam1, Aishwarya Kakade2, Aarati Pawar3,Badadhe Tanaya4,Jadhav Vaishnavi5
1Guide Department Of AIDS 2345Students ,Department Of Computer Engineering Dy Patil School Of Engineering And Technology Ambi, Pune, Maharashtra ,India
Abstract - Blockchain, a distributed record technology, may be used for a variety of purposes. Perhaps the most advanced blockchain applications with unavoidable appropriation among these are decentralized payment systems, like Bitcoin. This thesis offers methods for examining transactions in untested services and cryptocurrencies. Online payments are made safely using cryptocurrencies. Bitcoin, the original cryptocurrency, uses pseudonymous addresses for payments with little assurance of privacy or anonymity.
Key Words: 1.blockchain, 2.cryptocurrency, 3.smart contract, 4.anonymity, 5.privacy regulation, 4.decentralized 5.conditional anonymous payment.
1.INTRODUCTION
Moneylaunderingormixingservicesareamongthemostdeceptivetoolsthatburythelinkbetweensenderandrecipientof moneyincryptocurrencies:combiningdifferentsourcesofmoneywithdirtymoneymakestrackingdirtymoneycomplicated andobscureanddistortstherelationshipbetweenthesenderandreceiverofmoney.Asaresult,moneylaunderingservices are widely used to eliminate the track of income from ransomware, thefts, sales of weapons and drugs, and other illegal activitiesbycombiningtheseincomeswithothersourcesofmoneyanddisruptingthetrackingoftheseincomes.Blockchainis arelativelyrecenttrend,especiallyfueledbythepopularityofBitcoinanditscapacitytocreateatrustworthyecosystemfor conductingbusinessinasettingwhereinformationisasymmetricalandidentitiesareunpredictable(forexample,becauseof itsdecentralized,immutable,verifiable,andprogrammablefeatures).Thisservesasanadditionaldegreeofprivacyforsome people,shieldingtheirfinancialactivitiesfrompryingeyes.Forothers,thisservesasaveilthathidestheirillegalactivities, suchascurrencytheftorthesaleofcounterfeititems.
A. An advanced Decentralized Conditional Anonymous Payment System for Cryptocurrency using Blockchain
Incontrasttostandarde-moneyschemes,decentralizedpaymentsystemsrelyonadistributedrecordratherthantrusted parties. The Decentralized Anonymous Payment (DAP) structures in the current system are completely unmanageable. Ultimately,theseframeworkscanbemisusedforcriminalpurposes,suchasunlawfultaxevasionandcybercrimeinstances (such as paying a ransomwarepayout or engaging in online coercion). can be used for illegal purposes. Anyone can deanonymizewithoutmuchdifficulty.AnefficientDecentralizedContingentAnonymousPayment(DCAP)systemisusedinthe proposedworktoachievesomedegreeofbalancebetweensecurityguaranteesandguidelines.Certaincompoundsareallowed to be included in our proposed framework. We also provide a strongconstruction of the DCAP framework (based on the proposedCAPConditionAnonymousPaymentscheme)andassesstheproposal'sabilitytomeetsecuritystandards.Inthis research, wedeveloped a decentralized restricted anonymous payment (DCAP) system that achieves both obscurity and guidelineproperties.Oursuggestedframeworkisincrediblystrongandsafe.
B. Mixing detection on Bitcoin transactions using statistical patterns
Financialcrimeshaveexpandeddramaticallyintheseservices,alongwiththegrowingpopularityofcryptocurrenciesand theiruseinmanysituations.Moneylaunderingormoney-mixingservicesareamongthemostdishonestinstrumentsthat concealtheconnectionbetweenthesourceandtherecipientofcryptocurrency.Therelationshipbetweentheoriginatorand therecipientofmoneyisdistortedwhenmanysourcesoffundingarecombinedwithdirtymoney,makingtrackingitdifficult andelusive.Thischaracteristichasledtothewidespreadusageofmoneylaunderingservices,whichcombineincomefrom ransomware,theft,thesellingofgunsanddrugs,andotherillicitactivitieswithothersourcesoffundingandinterferewiththe trackingoftheseincomes.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Asapublicledger,blockchainisadecentralizedsystemthatisrunbyanetworkandisindependentofanyreliablethirdparty. Blockchain, a cutting-edge technology, has made it possible for a wide range of applications, particularly in the banking industry(usuallyknownasDeFi),includingborderlesstransactionsandsmartcontracts.Blockchainhasmadeitpossiblefora wholenewsectoroffinance,butitsfullpotentialhasnotyetbeenrealized.Utilizingblockchain'sfullpotentialishinderedbya number of obstacles, chief among them being regulatory. Using blockchain and holding users accountable are regulatory concernsinseveralnations.
Decentralizationisafundamentalprerequisiteforasystemthatmapsuser-friendlyidentitiestotheinitialuser-unfriendly strings.Whiledecentralizedtrustlesssystemsfrequentlylackuser-friendlyidentities,centralizedsystemstypicallydo.Inorder toavoidbecomingcentralized(andpossiblyasinglepointoffailure)inadecentralizedenvironment,thenewsystemmustbe abletokeepupwiththesystemsforwhichitoffersIDs.Thispaperpresentsourcryptoaddresssystem,whichusesthecurrent DNSinfrastructuretooffere-mail-likeIDs.Byassigningauser-selectedservertoeachoftheirdomainnames,DNSusageoffers simpledecentralizationatthe"domainnamespace"level.Theresolutionofcryptoaddressestotheoriginalcryptographic identitiesisprovidedbyservers.
BoththeDNSandservercommunicationaspectsofthesystemaresafeguarded.Thesystemisglobalandhasawiderangeof potentialuses;therefore,itsapplicabilityisnotrestrictedtocryptocurrencies.
E.Investigating transactions in cryptocurrencies
TheissuesofcensorshipandcentralizationinafinancialsystemarelessenedbyBitcoin.Justbysupplyingtheirpublickey, anyone can freely build a bitcoin wallet and receive coins. To create such a wallet, no user identification, passport, or verificationisrequired.ThisgetsbeyondtheconventionalfinancialKnowYourCustomer(KYC)principles,whichformthe basisofasetofguidelinesthatfinancialinstitutionsemploytoidentifycustomersbeforedoingbusinessand,asaresult,predict andpreventcriminalactivity.Thisindependenceallowscoinstobesenttoanyaddresswithouthindranceordiscrimination. Unlessthenewownerspecificallyrequestsit,thesecoinscannotbeexchangedorreturned.AccordingtotheBitcoinwhite paper,thesystembydefaultprovidespseudonymityfortransactions.
Anewparadigmindigitalbankinghasemergedasaresultofthequickriseofcryptocurrencies,offeringconsumerssafe, decentralized,andfrequentlyanonymousmeansofconductingbusiness.Blockchaintechnology'spseudonymityhasprivacy benefits,butitalsopresentsseriousproblemsforregulatorymonitoring,fraudprevention,andcompliance.Thechallengeof identifyingthefinalrecipientinbitcointransactionsisoneofthemainissuesfacingregulators,financialinstitutions,andlaw enforcement.Thefollowingareasarewherethisproblemismostproblematic:
1. Money Laundering and Financial Crime:
Because pseudonymous addresses, mixers, and privacy coins may frequently conceal the eventual recipient, cryptocurrenciesarebeingusedmoreandmoreinmoneylaundering,taxevasion,andotherfinancialcrimes.Finding transactionendpointsiscrucialfortrackingdownillegalcashandprosecutingpeopleengagedinillegalactivity.
1. Regulatory Compliance: ToadheretoAnti-MoneyLaundering(AML)andCombatingtheFinancingofTerrorism(CFT) norms, numerous nations are enacting laws mandating that bitcoin transactions be traceable. Conducting client due diligence ismandatory forfinancial institutionsand exchanges, but it can be difficultwithout toolsto determinethe transactiondestination.
2. Fraud and Scam Prevention: Because end-receiver identification is opaque, criminals might take advantage of blockchainsystemstocreateintricate,hard-to-tracehoaxes.Inordertoevadedetection,scamslikePonzischemesand phishingattacksfrequentlyuseanonymousorpseudonymousaddresses,whichmakesitchallengingtorecoverassetsor identifythescammers.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Additional challenges arise from privacy-focused cryptocurrencies and devices, like tumblers or mixers, which purposefullyobscuretransactionhistories.Tosolvethisproblemandunderstandcomplicatedtransactionswithout jeopardizingtherightsoflawfuluserswhorespecttheirprivacy,sophisticatedsolutionsareneeded
Thissectionwilloutlineourapproach,whichincludesgatheringthenecessaryinformationandidentifyingrecurringthemesin themixingtransactionsinordertodevelopanalgorithmforfilteringthem.
1.DATACOLLECTIONWerequireaccesstothecompleteblockchaintransactiondataandlabelsfortransactionsthattookpart inmixingservicesproceduresinordertolookintomixingtransactions.
1.1)ExtractingBlockchainInformationUsingafull-nodeBitcoinclient,wegatheredthenecessarydatafromtheblockchain usingitsJSON-RPCAPIsinordertoaccesstransactiondata.Informationaboutblocksandtransactions,includingblockhashes, transactioninputandoutputaddresses,transferredvalues,timestamps,and other necessaryinformationincludedinthe blockchain, can be obtained after executing the Bitcoin client in accordance with its established RPC capabilities. 1..2)GatheringLabelsforTransactionMixingPeopleusemixingservicesforavarietyofreasons,suchashidingtheirfinancial activitiestoavoidtaxes,commitcrimes,orprotecttheirprivacy.Itisevidentthatpeoplearehesitanttorevealtheirmixing transactions,regardlessoftheirmotivations,andasanticipated,thereisnodatasetofexchangespertainingtoservicemixing. Eventhoughtherearecertainlabelsavailableformoneylaunderingserviceaddresses,heuristicsandclusteringtechniques thatlabelotheraddressesbasedonthepreviouslylabeledaddressesmaycauseinaccuracies.Ordinaryaddressescouldbe linkedtomoneylaunderingservicesthroughoutthisprocedure,makingitmisleadingtoexaminetheirtransactions.Wehadto gatherprecisedataonourownsincetherewasnopredefineddataset.
ThreeofthemostpopularmixingservicesthatweremostlydiscussedonReddit2andBitcoinTalk1werechoseninorderto compileadatasetofmixingtransactions.Byusingtheirservice,puttingfundstothedesignatedaddress,andthentransferring fundsfromthemtoourtargetaddressviathemoneylaunderingprocedure,everytimeweusedtheseservices,weconducted twomixedtransactions:oneforthedepositandoneforthewithdrawal.ThesethreechosenmixingservicesarelistedinTable alongwiththequantityofmixingtransactionsweproducedforeach.
2.STATISTICALPATTERNEXTRACTIONWehadtousestraightforwardstatisticaltechniquesthatworkwellwithsmalldatain ordertoextractthemixingpatternbecausegatheringarichdatasetofmixingtransactionswasbothexpensiveandtimeconsuming.First,webrieflygooverthemechanismsthatvariousmixingprovidersemploy.Twoprimarycategoriesofmixing servicesaredescribed.•Conventionalmixingservices:Inclassicmixingservices,theservicedecideshowmuchmoneyfrom desiredtransactionscanbecombinedwithapredeterminedquantityofmoney.Theseservicesfacilitatethetransferoffunds betweensendersandrecipientsatrandom.Theservicegeneratesafreshrandomdepositaddressforthesenderinthefirst stage.Theaddressisupdatedeverytimetheuserreloadsthepagecontainingthemixingrequest.Asendermustthenwaituntil atleastN−1othermixingrequestswiththesameamounthavebeenrecordedbeforedepositingtheirfundsintotheaddress theyhavecreated.Inordertoremovethetraceofthemoneytransferbetweenthesenderandtherecipient,themixingservice inthisstage,alsoknownastheintermediatestage,generatestransactionsinwhichtheseNinputsareswitchedatrandomand sent to N anonymous output addresses. The anonymity set is set to a probability of 1/N by this action. This displays the likelihoodofdiscoveringtherightconnectionbetweenasenderandtheirmatchingrecipient.Theoperationoftheseservicesis depictedinFigure1.•Contemporarymixingservices:Theseserviceshavethreestages,justasconventionalservices.The requestedfundsarefirsttransferredtoarandomlygenerateddepositaddressbythemixingservice.
3.TRANSACTION-LEVEL PATTERNSIN THEFIRSTPHASEOFDETECTION Wediscoveredrecurrenttendencieswhenwe lookedintothemixingtransactionswemade.Withdrawaltransactionsshowedthesetrends.Sincetheformatofthedeposit transactionswasstandardacrossthewholeblockchainandthesendersmadethembyusingtheirwalletapplicationtodeposit moneytothemixingservice,wewereunabletoidentifyanypatternsinthedeposittransactionsatthetransactionlevel.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Software/Tool KeyFeature UseCase Example
ChainalysisKYT Real-time transctionmonitoringris kscoring
TRMLabs Blockchainintelligence AIpowerdanalytics
Scorechain Multi-blockchain support,sanctions screening,real-time monitoring
Elliptic(Explore) Tracingfundsacross over100cryptoassets withconfigurablerisk rulesSource/destination tracingforfinancial
DetectSuspicious andesureAML compilance
Investigatefraud, tracefunds,and buildcompliance cases
Riskscoringand regulatory reporting
Source/destinatio ntracingfor financial institutions
Identifyillict wallet addressesand tracing
Investigate fraud,trace funds,and build compliance cases
Riskscoring andregulatory reporting
Monitoring walletbehavior toprevent fraud.
Thesearchresultsrevealanumberofsoftwareapplicationsdesignedtomonitorcryptocurrencytransactionsanddetermine theultimatereceivers.Thesetoolsusewalletaddresstracking,blockchainanalysis,andforensictechniquestotracktheflowof money,particularlyincaseslikedrugtrafficking.GitHubrepositories,industryreports,andresearcharticlesaresomeofthe resourcesthatdiscussthemethodsandtechnologyusedinthissubject.Thefollowingisasummaryofthefindings:
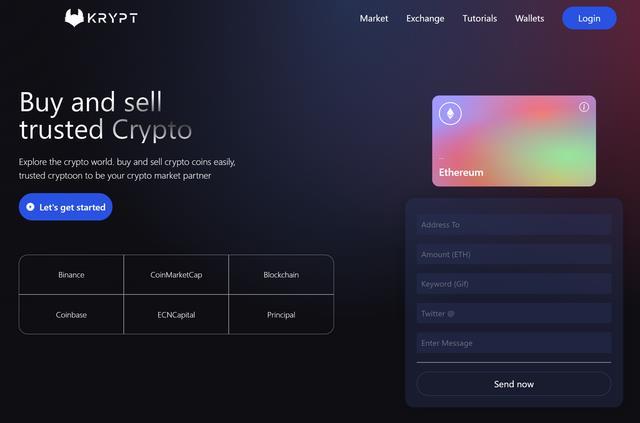
Oneofthemostdishonest methodsthatconcealstheconnectionbetweenthesourceandtherecipientoffundsismoney launderingormoneymixingservices.Thepicturedisplaysaprogramnamed"Krypt"thatisintendedtoidentifythefinal cryptocurrencyrecipient.It positionsitselfasa crypto market partner bymaking itsimple forcustomers to buyandsell reliablecryptocurrency.Numeroussources,includingBinance,CoinMarketCap,Blockchain,Corbne,ECNCapital,andPrincipal, aresupportedbytheplatform.Witha"Sendnow"option,itallowsuserstosendbitcoinbyenteringtherecipient'saddress, quantity(ETH),keyword,Twitteraccount,andmessage.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Thepicturedisplaysaprogramnamed"Krypt"thatisintendedtoidentifythefinalcryptocurrencyrecipient.Itpositionsitself asacryptomarketpartnerbymakingitsimpleforcustomerstobuyand sellreliablecryptocurrency.Numeroussources, includingBinance,CoinMarketCap,Blockchain,Corbne,ECNCapital,andPrincipal,aresupportedbytheplatform.Witha"Send now"option,itallowsuserstosendbitcoinbyenteringtherecipient'saddress,quantity(ETH),keyword,Twitteraccount,and message.
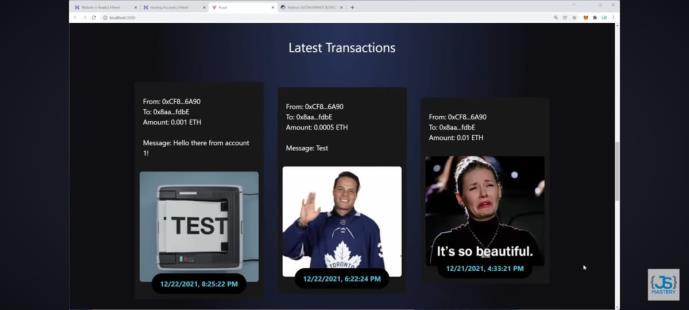
The screen captureshowsa logof "Latest Transactions," whichappears to be relatedto cryptocurrencies or blockchains becauseETH(Ether)andhexadecimalwalletaddressesarementioned.Theaddressofthesender(From),theaddressofthe recipient(To),theamountofETHtransferred,amessage,andthetransactiondateandtimestampareallincludedinevery transaction.0.001ETHwastransferredonDecember22,2021,at6:25:22PM,withthemessage"HellotherefromaccountT!" Thisisthefirsttransaction.Onthesameday,at6:22:24PM,thesecondlogsa0.0005ETHtransferwiththemessageTest.The thirdtransactionshowsthatonDecember21,2021,at4:33:21PM,001ETHwastransferredwithcomment
Theproposedworkhaseffectivelyachievedanonymityandregulationpropertiesinourdecentralizedconditionalanonymous payment(DCAP)system.BeforeconstructingourDCAP,wedevelopedaconditionalanonymouspayment(CAP)methodusing theformalsemanticandsecuritymodels.Itwillalsoshowitssecurityinsidethedesignatedsecuritymodelandprovidea concreteCAPdesignbasedonourproposedknowledgeschemesignature.BuildingontheproposedCAP,wecreatedourDCAP anddemonstratedhowitmightsatisfytherelatedsecurityrequirements.Ourprototype'sperformancewillnextbeevaluated bycomparingittoZeroCash'sunderthesametestingconditions.Theresultsindicatedthatourplancouldbeimplementedin therealworld.Weproposedatechniquefordetectingmixingtransactionsbasedonthestatisticalpatternswesawinthe mixingprocess.Duetothelackofreliablelabeleddata,weconstructedmixingtransactionsusingthreewidelyusedmixing services:MixTum,Blender,andCryptoMixer.Bylookingatthesetransactions,wewereabletoidentifyrecurringtrendsatboth the transaction and chain levels. By examining each transaction in the blockchain, comparing it with the patterns we discovered,andidentifyingmixingtransactions,wewereabletodifferentiatebetweenaddressesconnectedtomixingservices andaddressesconnectedtotheusersofmixingservices.Ourapproachis100%accurate
[1] ArdeshirShojaeenasab,AmirPashaMotamed.,BehnamBahrak,“MixingdetectiononBitcointransactionsusingstatistical patterns,”©2022
[2] ChaviKapoor.,VeeravalliShivadeepak,Konthamvinaykumarreddy“AnadvancedDecentralizedConditionalAnonymous PaymentSystemforCryptocurrencyusingBlockchain”©2021

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
[3] MahdiDarabi,AmirrezaFathi,“IdentityChain”©2022
[4] HaaroonMYousaf,“Investigatingtransactionsincryptocurrencies”©2022
[5] R.Muthumeenakshi,BalasubramaniamS.,CharanjeetSingh,PallaviV.Sapkale,“AnEfficientandSecureAuthentication ApproachinVANETUsingLocationandSignature-BasedServices”,AdHoc&SensorWirelessNetworks53(Issue1-2), 59-83,2022
[6] UttamD.Kolekar,“DevelopmentofOptimizedandSecureRoutingAlgorithmusingAODV,ACOandLSBSteganographyfor MobileAd-HocNetwork”,JournalofAdvancedResearchinDynamicalandControlSystems(JARDCS),Vol.11,issue9,pp. 560-568,Sept2019.
[7] Sandeep B Hake, “Design and development of universal test bench for engine aftertreatment controls system”, Internationaljournalofadvancedresearchinelectronicsandcommunicationengineering,Volume6,Issue4,Pages309312,2017.
[8] Samarjeet Powalkar, “Fast face recognition based on wavelet transform on pca” International Journal of Scientific ResearchinScience,Engineering&Technology,Vol1,Issue4,PP21-24,2015.
[9] UWaghmode,DPDeshmukh,SEkshinge,AKurund,“AnInnovativeApproachUsingCyberSecurityforSteganographyfor Wireless Adhoc Mobile Network Application”International Conference on Science Technology Engineering and Management(ICSTEM),Pages1-5,2024.
[10] C Kaur, DS Rao, S Bandhekar, “Enhanced Land Use and Land Cover Classification Through Human Group-based ParticleSwarm Optimization-Ant Colony Optimization Integration with Convolutional Neural Networ”, International JournalofAdvancedComputerScience&Applications,Vol14,Issue11,2023.
[11] DivyaRohatgi,VeeraAnkaluVuyyuru,KVSSRamakrishna,YousefABakerEl-Ebiary,VAntonyAsirDaniel, “Feline Wolf Net: A Hybrid Lion-Grey Wolf Optimization Deep LearningModel for Ovarian Cancer Detection”, International JournalofAdvancedComputerScienceandApplications,Vol14,Issue9,2023.
[12] UttamD.Kolekar,“Trust-BasedSecureRoutinginMobileAdHocNetworkUsingHybridOptimizationAlgorithm”,The ComputerJournal,OxfordUniversityPress,Vol.62,issue10,pp.1528-1545,Oct2019.
[13] UttamD.Kolekar,“E-TDGO:AnEncryptedTrustbaseddolphinglowwormoptimizationforsecureroutinginmobile ad-hocnetwork”,InternationalJournalofCommunicationSystems,Wileypublication,Vol.33,issue7,May2020.
[14] DilipPDeshmukh,AbhijeetKadam,“EfficientDevelopmentofGestureLanguageTranslationSystemusingCNN”15th InternationalConferenceonComputingCommunicationandNetworkingTechnologies(ICCCNT)Pages1-6,2024.
[15] PrajwalKote,MouneshaZonde,OmJadhav,VaibhavBhasme,NitinADawande“AdvancedandSecureDataSharing SchemewithBlockchainandIPFS:ABriefReview”15thInternationalConferenceonComputingCommunicationand NetworkingTechnologies(ICCCNT),Pages1-5,2024.
[16] Prasant,P.,Saravanan,D.,Sangeethapriya,J.,“NRlayer2andlayer3”MachineLearningforMobileCommunications, Taylor&Francis,CRCPress,pp.32–45,2024.
[17] Borana,G.K.,Vishwakarma,N.H.,Tamboli,S.,M.,Dawande,N.A.,“DefendingtheDigitalWorld:AComprehensiveGuide AgainstSQLInjectionThreats”2ndInternationalConferenceonInventiveComputingandInformatics,ICICI,pp.707–714, 2024.
[18] Deshmukh,D.P.et.al,“AnInnovativeApproachUsingCyberSecurityforSteganographyforWirelessAdhocMobile NetworkApplication”InternationalConferenceonScience,Technology,EngineeringandManagement,2024