BSIDES LEEDS 2023 BSIDES LEEDS 2023 BSIDES LEEDS


2023 LEEDS 2023
"IN THE REALM OF INFORMATION SECURITY, COLOURS
"IN THE REALM OF INFORMATION SECURITY, COLOURS

CONVERGE, AND UNITY BECOMES STRENGTH. RED, BLUE, AND CONVERGE, AND UNITY BECOMES STRENGTH. RED, BLUE, AND
PURPLE INTERTWINE TO FORM AN UNSTOPPABLE FORCE; A PURPLE INTERTWINE TO FORM AN UNSTOPPABLE FORCE; A
TESTAMENT TO COLLABORATION, INNOVATION, AND SHARED
TESTAMENT TO COLLABORATION, INNOVATION, AND SHARED
PURPOSE. IN THIS VAST INTERCONNECTED NETWORK, WHERE PURPOSE. IN THIS VAST INTERCONNECTED NETWORK, WHERE
THREATS LOOM AND VULNERABILITIES HIDE, WE STAND AS
THREATS LOOM AND VULNERABILITIES HIDE, WE STAND AS ONE, FOR EACH MEMBER HOLDS A CRUCIAL ROLE. WHETHER ONE, FOR EACH MEMBER HOLDS A CRUCIAL ROLE. WHETHER WE TEST, DEFEND, OR ANALYZE, REMEMBER THAT OUR WE TEST, DEFEND, OR ANALYZE, REMEMBER THAT OUR DIVERSITY EMPOWERS US, OUR EXPERTISE ENRICHES US, DIVERSITY EMPOWERS US, OUR EXPERTISE ENRICHES US, AND OUR COLLECTIVE EFFORTS FORTIFY OUR DEFENSES. AND OUR COLLECTIVE EFFORTS FORTIFY OUR DEFENSES.
TOGETHER, AS A VIBRANT TAPESTRY OF MINDS, WE SHAPE A TOGETHER, AS A VIBRANT TAPESTRY OF MINDS, WE SHAPE A SAFER DIGITAL LANDSCAPE. EMBRACE YOUR ROLE, UNLEASH SAFER DIGITAL LANDSCAPE. EMBRACE YOUR ROLE, UNLEASH YOUR POTENTIAL, AND LET US FORGE AHEAD, AS ONE BIG YOUR POTENTIAL, AND LET US FORGE AHEAD, AS ONE BIG TEAM, SAFEGUARDING THE REALM OF BYTES AND BITS WITH TEAM, SAFEGUARDING THE REALM OF BYTES AND BITS WITH
UNWAVERING DETERMINATION. "
UNWAVERING DETERMINATION. "
- CHATGPT (2023) CHATGPT (
)
2023
LEE GILLBANK @YORCYBERSEC
THE



TEAM
WOULD
LIKE

HUMPHRIES @SAFESECS
BSIDES LEEDS 2023










BSIDES LEEDS

TO WELCOME YOU TO VS. BLUE VS. PURPLE
THE TEAM WOULD LIKE TO WELCOME YOU TO RED VS. BLUE VS. PURPLE
2023
CLOTH HALL COURT FLOORPLAN

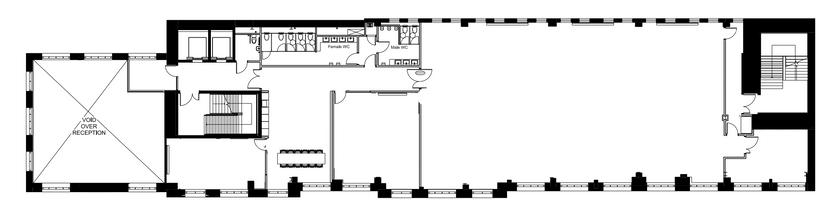
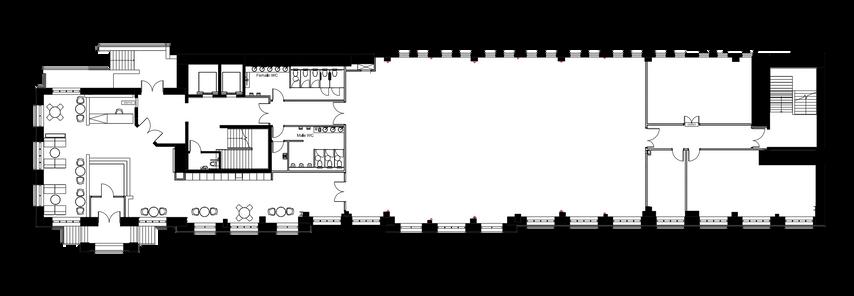
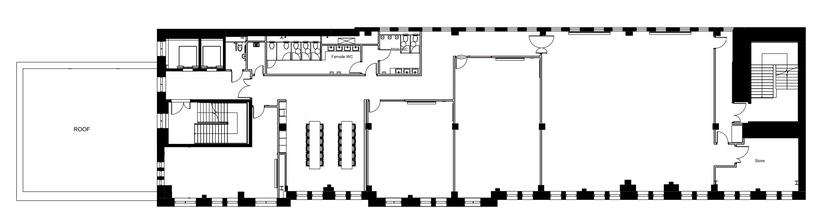

SUITE BOBBIN BOBBIN SUITE SUITE TAILORS TAILORS SUITE SUITE MERCHANT MERCHANT HALL HALL G R O U N D F L O O R G R O U N D F L O O R F I R S T F L O O R F I R S T F L O O R HERRINGBONE HERRINGBONE SUITE SUITE COTTON COTTON ROOM ROOM DENIM DENIM ROOM ROOM WOOL WOOL ROOM ROOM S E C O N D F L O O R S E C O N D F L O O R TWEED TWEED ROOM ROOM TALKS | ROOM 1 TALKS | ROOM 1 TALKS | ROOM 2 TALKS | ROOM 2 TALKS | ROOM 3 TALKS | ROOM 3 WORKSHOPS | ROOM 4 WORKSHOPS | ROOM 4 ENTRANCE | RECEPTION ENTRANCE | RECEPTION
TOILETS
VILLAGES THE GREEN ROOM THE GREEN ROOM QUIET AREA QUIET AREA LUNCH & VENDOR AREA LUNCH & VENDOR AREA
SEAMSTRESS SEAMSTRESS SUITE
TOILETS
VILLAGES
WHERE AM I?
SPEAKER & WORKSHOP SCHEDULE SPEAKER & WORKSHOP SCHEDULE
KIM HENDRY THE NSM OUROBOROS: EMBRACING THE ENDLESS CYCLE OF NETWORK SECURITY
: SECGEN, HACKTIVITY, AND HACKERBOT RANDOMISED HACKING CHALLENGES

MACKENZIE JACKSON
DETECTING INTRUSIONS WHEN THEY HAPPEN - CREATING HONEY TOKENS TO CATCH ATTACKERS
LEUM DUNN AI AIEEEEEE! (REDUX) : FURTHER ADVENTURES IN AI
YAKUB DESAI SENTINEL AUTOMATION FOR POWER USERS
ROOM 1 ROOM 2 ROOM 3 ROOM 4 09:00 OPENING REMARKS 09:15 09:30 HOLLY
RED
KEYNOTE 10:00 ANDY GILL PENTESTS: THE JASON BOURNE APPROACH - TURNING REGULAR BIROS INTO WEAPONS
HACKANORY
POWER OF STORIES
EDUCATION
-GRACE WILLIAMS |
TEAM
JANETTE BONAR LAW
, THE
DR Z. CLIFFE SCHREUDERS INNOVATIONS IN CYBER SECURITY
10:30
WHINE
DAN CANNON RED RED
MONITORING
11
MORNING
SASKIA COPLANS OUTSOURCING DEVELOPMENT
:00
BREAK
PETER JONES PRACTICAL BLUE TEAMING
11:30
BRAD STORAN EVASION ON AISLE FIVE: FROM BACON TO BEACON
JOHN ATKINSON THE OBFUSCATION SITUATION
12:00
JAMES BORE THE BUSINESS PHILOSOPHY OF SECURITY
TOM HARRISON SOCIAL ENGINEERING THE KILL CHAIN LUNCH BREAK (SITTING ONE)
12:30 TOMNOMNOM JSLUICE
IN THEM THAR FILES
: THERES GOLD
13:00
LUNCH BREAK (SITTING TWO)
LEIGH HALL
BEING RIGHT IS JUST THE BEGINNING (A TALK VERY MUCH NOT ABOUT POLITICS)
LORNA ARMITAGE
SEAN WRIGHT DOCKER TO THE SECURITY
YAKUB DESAI SENTINEL AUTOMATION FOR POWER USERS
13:30
14:00
14:30
DAN HOUGHTON WEB BROWSER AUTOMATION: HOW TO BE MORE ROBOT, EASILY!
CHAT GPT AND THE BENEFITS FOR CYBER SECURITY
DARREN CONWAY SO YOU WANT MONEY TO FUND YOUR COOL TOOLS, NOT SO FAST
LISA FORTE | BLUE TEAM KEYNOTE
AYOUB SAFA UNCOMMON AND ADVANCED TECHNIQUES FOR ACCOUNT TAKEOVER ATTACKS

GERALD BENISCHKE
PRECISION MUNITIONS FOR DENIAL OF SERVICE
SARA ANSTEY
15:00
RAEL SASIAK-RUSHBY WHOS INPUT IS IT ANYWAYS
ALEX MARTIN FIVE DAYS, ONE RED TEAM, A BREACH LIKE NO OTHER: THE BANK JOB
EDUCATING YOUR GUESSES: HOW TO QUANTIFY RISK AND UNCERTAINTY
JAMES STEVENSON WRITING AND BREAKING ANDROID TAMPER DETECTION TECHNIQUES
15:30
SARAH YOUNG FANTASTIC CLOUD SECURITY MISTAKES
CHRIS ROBERTS CHATHAM HOUSE SESSION
CHARLES BAIN FAWLTY TOWERS
16:00
16:15
16:45
17:30
17:45
AFTERNOON BREAK
ELIZA MAY AUSTIN | PURPLE TEAM KEYNOTE
DR MARK CARNEY, HOLLY-GRACE WILLIAMS, DR ANDREA CULLEN, NIALL CLARKE FROM FAILURES TO FORTRESSES: UNVEILING CYBERSECURITY'S GREATEST MISSTEPS AND REINVENTIONS (PANEL)
CLOSING REMARKS
AFTERPARTY
ROOM 1 ROOM 2 ROOM 3 ROOM 4



MEET THE MEET THE SSPEAKERS PEAKERS

SPEAKER BIO
Holly-Grace has sixteen years of experience working within cybersecurity, with a focus on penetration testing and cybersecurity consultancy.
Holly-Grace is a CREST Fellow and has been a CREST Certified Application Tester since 2015. She has professional software development experience in Python and Rust, including taking software products to market. She has strong experience in building and securing cloud environments, with a focus on AWS and Azure.
She has performed a significant number of penetration testing engagements for a wide range of companies from innovative start-ups to multinational corporations, in fields ranging from e-commerce to banking.

She's also often found speaking at conferences and on podcasts all about technology, cloud computing, cybersecurity, chaos engineering, and more.

Links & Socials
@HollyGraceful @AkimboCore https://www.akimbocore.com
R E D T E A M K E Y N O T E
R E D T E A M K E Y N O T E
9:30AM • ROOM 1 • HERRINGBONE SUITE
B L U E T E A M K E Y N O T E
B L U E T E A M K E Y N O T E
SPEAKER BIO

Lisa is a partner at Red Goat Cyber Security who specialise in helping companies around the world prepare for a cyber attack. Her career in security started a bit differently though. She worked in the counter piracy industry helping to protect merchant vessels from pirates off the coast of Somalia. She then worked for the U.K. police in counter terrorism intelligence and then for one of the cyber crime units. She then co-founded Red Goat in 2017.
Lisa is a passionate climber, caver and abandoned mine explorer (which is weird. She knows!) she recently realised she hums the A Team soundtrack when she is scared climbing!
She has some hugely ambitious climbing and cyber goals for the coming years!

Links & Socials
@LisaForteUK
@redgoatcyber
https://www.red-goat.com
14:00PM • ROOM 1 • HERRINGBONE SUITE
SPEAKER BIO
Eliza knew she wanted to work in tech from the moment she saw Sandra BullockorderPizzaoverdial-upinherfavouritefilm,1995's'TheNet'.
Eliza has a degree in Digital Forensics, is SANS trained in Network Forensics, PurpleTeamingandPenetrationTesting. Shehaspreviouslyworkedincyber defence in a number of FTSE100 companies and was the original founder of theLadiesHackingSociety.


Despite her fascination with tech she has taken on a more business-centric role and guided the company through impressive sales-driven growth, won a slew of awards, and was voted one of the most inspirational voices in cybersecurity.
Links&Socials
@Eliza_MayAustin
@th4ts3cur1ty
https://www.th4ts3cur1ty.company
P U R P L E T E A M K E Y N O T E
P U R P L E T E A M K E Y N O T E
16:15PM • ROOM 1 • HERRINGBONE SUITE
ABOUTTHETALK
Notadaygoesbythatthere’snotanewthreatactor or company that has been breached. Many engagements we see as pentesters and red teamers are often a tier harder than your average threat actorcomesupagainst.

https://blog.zsec.uk

@ZephrFish
SPEAKER BIO


Andy has been working in security for over a decade. Starting in information risk and quickly pivoting to offensive security, he works on everything ranging from your run-of-the-mill external pentests through to full-blown red teams and everything in between. He has also written two books aimed at those looking to learn the tradecraft of security from both an offensive and defensive perspective. Outside of security he can befoundwanderingthestreetsofGlasgowwithhis camera taking night photography pics and driving the roads of Scotland enjoying the adventure of beautifulcountryroadsandscenery.



ABOUT THE TALK
security communications stories are gold They be used to communicate complex ideas to technical and non technical audiences in a way that both meaningful and memorable. Join me for ‘Scrooge - the insider threat edition’ - learn its tacticsandtechniques&emulateitssuccess
10:00AM • ROOM 1 • HERRINGBONE SUITE
10:00AM • ROOM 2 • TWEED ROOM
ABOUTTHETALK SPEAKER BIO
We have designed open source techniques, software, and content for generating randomised hacking challenges. In this talk I will describe our approach to teaching cyber security, designing fun security challenges, and our technology and infrastructure.





Socials&Links
http://z.cliffe.schreuders.org
DrZ.CliffeSchreudersisReaderinCyberSecurityand Director of the Cybercrime and Security Innovation (CSI) Centre at Leeds Beckett University. Cliffe believes that learners should be given the opportunity to put theory into practice. He has a well established publication track record, including publications in journals such as ACM Transactions on Information and System Security (TISSEC), International Journal of Information Security, and Computers&Security,andistheauthorofmanypeerreviewed papers. Cliffe leads the Hacktivity and SecGen projects (as lead architect and developer, working collaboratively with others). Cliffe has experience working as a software engineer and leading funded collaborative research projects with a largenumberofstaff.
ABOUT THE WORKSHOP
An avenue of privilege persistence and elevation for attackers is to find and exploit plain text secrets in our systems. Honeytokens are fake AWS tokens that alert us when an attacker tries to exploit them, notifying us of a breach. In this workshop, we learn howtocreateanddeploythem.
The workshop will be 90 minutes long - please bring yourlaptopwithyou.
10:00AM • ROOM 3 • WOOL ROOM
10:00 AM • ROOM 4 • CORDUROY ROOM
ABOUTTHETALK SPEAKER BIO

ABOUTTHETALK
is the story of how, in the wake of Roe v Wade, weranalittleexperimenttoseewhatthesecurityof cheaply outsourced mobile symptom tracking application would look like. The results ranged from comictoterrifying.
Simulating real-world attacks against organizations, Red Teaming showcases potential attack chains used by malicious actors. But, not all companies are ready for this assessment. Focusing on security basicsandhygieneiskey.

Socials&Links
Links&Socials
https://www.digitalinterruption.com
@ms__chief
https://www.northgreensecurity.com @dancannon__

An enthusiastic and determined individual, Dan has spent over a decade working in the cyber security industry. Dan has been a pentester, a consultant, the head of a pentesting team of 30, a global head of technical assurance, a trainer, and much more. Throughout his career he has always been keen to share knowledge and teach tradecraft to those working their way up and finding their niche. As a professional with extensive practical experience, Dan knows what skills are required to be successful in this industry. When not delivering security consultancy services or training, Dan enjoys focussing on community outreach programs that teach students the skills needed to join the industry as well as working with military veterans transitioning into a civilian careerincybersecurity.
ABOUT SPEAKER BIO
ABOUT THE TALK
This talk will look at some real-world examples of compromises to cover the role of threat hunting, data collection, rulesets, detection, alerting and analysis/investigation - and how they all work cyclicallytokeepacompanysafeusingaSIEM.


is a lot of discussion around those who don’t right, but how about those constantly maturing focus on improvement? Being to objectively reinvent and reinvigorate the team with understanding and knowledge to defend against the latestattackmethods.
Socials&Links
https://www.linkedin.com/in/triwebdesignpj/ @cyberbadgeruk
Kimberley Hendry is SOC Team Lead at th4ts3cur1ty,company for their PocketSIEM service and chapter lead of the North East Ladies Hacking Society. She's based in the North East and hasaMastersincybersecurity.

Links&Socials @Kimberley_HG

10:30AM • ROOM 1 • HERRINGBONE SUITE
10:30AM • ROOM 2 • TWEED ROOM
ABOUTTHETALK SPEAKER BIO
This is the story of how, in the wake of Roe v Wade, weranalittleexperimenttoseewhatthesecurityof a cheaply outsourced mobile symptom tracking application would look like. The results ranged from comictoterrifying.
Socials&Links
https://www.digitalinterruption.com @ms__chief
Saskia is an award loosing security specialist and the co-founder and managing director of both Digital Interruption and REXSCAN. She sits on a number of cyber security advisory groups including the Greater Manchester Cyber Advisory Group and the OWASP Education Committee. She runs both the local Manchester OWASP chapter and a group aimed at up-skilling women and gender minorities in cyber called the Infosec Hoppers.
She was featured as one of the Top 30 Female Cybersecurity Leaders by SC magazine in 2022 and can be seen speaking internationally at tech conferences such as TestBash, EXPOQA and (ISC)² Security Congress. She really, really likes dinosaurs.


ABOUT THE TALK SPEAKER BIO



There is a lot of discussion around those who don’t do it right, but how about those constantly maturing with a focus on improvement? Being to objectively reinvent and reinvigorate the team with understanding and knowledge to defend against the latestattackmethods.
Socials&Links
https://www.linkedin.com/in/triwebdesignpj/ @cyberbadgeruk
MCIIS (Formerly M.Inst.ISP) Director PCI QSA PCIP
Lead ISMS Auditor & Implementator (ISO 27001)
Technical Assessor (ISO 17025) CISO Digital Forensic Professional Advisory Board Member
IASME & Cyber Essentials Assessor TV & Radio PresenterAuthorLecturerMasterofCeremonies.

10:30AM • ROOM 3 • WOOL ROOM
11:00AM • ROOM 2 • TWEED ROOM
ABOUTTHETALK SPEAKER BIO
Building on the talk I presented at BSides Lancs. Join me as I try to navigate my way through some more AI stuff. A non-technical, tech talk introducing AI tools and their potential impact on the InfoSec professional.




Medium size fat bloke with a pirate-y beard. Likes old vans, plays bass (badly), thinks music died sometimearound1992.
Socials&Links @_daddiethebaddie
ABOUT THE TALK SPEAKER BIO
Prepare for an exhilarating adventure as we dive into the world of red teaming - breaking into a supermarket chain in all ways possible. We'll evade detection whilst we identify weaknesses within their interconnected systems, from reconnaissance techniques to gaining initial access and laterally moving. So, fasten your seatbelts and let's embark on this thrilling journey together to enhance your red teaming skills, learn new techniques, and break stuff.

Brad Storan is a Passionate Red teamer and Digital Forensics Incident Responder. Beginning his career in Private investigation and now with almost a decade of IT industry experience, he specialises in providing technical solutions to a variety of cyber problems, ranging from simple security configuration reviews to cyber threat intelligence. Brad holds multiple security qualifications including CREST Registered Tester andOffensiveSecurityCertifiedProfessional.

11:00AM • ROOM 3 • WOOL ROOM
11:30AM • ROOM 1 • HERRINGBONE SUITE
ABOUTTHETALK SPEAKER BIO
Obfuscation is hard. But it doesn’t have to be boring!
Researchers face a number of issues when dealing with obfuscated data. But in Security we can flip the script and use these exact same problems against adversaries to uncover malware evasion techniques orpreventfraud.Examplecodeincluded.

John is currently Lead Data Scientist for Insider Threat at a global cybersecurity company. He looks for suspicious or weird patterns (like writing in the third person). Previous experience includes Head of Security Data Science in UK gov, similar in telecoms, network security analyst, and a Researcher of WiFi security where he picked up a PhD. Talk to me about any of the above, beer, books, games, or how great it is to have BSides Leedsback.


Links&Socials
https://github.com/fauxnetic @fauxnetic
ABOUTTHETALK SPEAKER BIO

One of the most common questions that security practitioners are asked is ‘are we secure?’ It’s a difficult, maybe impossible question to answer. What does it mean to say that an organisation, or a person, is or is not secure? How secure is secure enough?

Socials&Links
https://bores.com @coffee_fueled
James Bore has been the winner of the BestDressed in Security award for the latest 5 years (notarealaward)andhasbeenworkinginthefield for more years than he likes to think about. Over that time he’s worked with various companies, earned an MSc in Cyber Security, and been registered as a Chartered Security Professional. He’s proudest of his work teaching and training, including working with CAPSLOCK to help career changersintosecurityfindtheirplace. Nowadays he does various bits and pieces. These include running the family company Bores Group, making homebrew of questionable quality, speaking at conferences, and writing for various publications,aswellasspendingfartoomuchtime thinking about what things mean when he should beworking.

11:30AM • ROOM 2 • TWEED ROOM 11:30AM • ROOM 1 • WOOL ROOM
ABOUTTHETALK SPEAKER BIO
For years Social Engineers have clung to Phishing as the focus for orgs to defend against and we’ve seen the email control stack improving every year. For Red Teams, there’s a myriad of other ways to employ SE during an attack in initial access, lateral movement,privescanddefenderevasion.
Tom has been working in InfoSec for over 15 years, with the second half of that predominantly spent on the Offensive side, with focuses on Red Team operations, Physical Security and Social Engineering and loves nothing more than breaking systems, buildings and people in order to help the GoodGuys(tm)getbetter.



Outside of work, Tom is a Dad of 4, Psychology and Language nerd, prolific gamer, enthusiast for all types of tech and sometimes manages to find time tosleep!
Socials&Links
@pretechst
ABOUTTHETALK SPEAKER BIO
SentinelAutomationforPowerUsers
WhatareLogicApps?Howdotheyworkwith Sentinel?Howdotheyunlockthetruepotentialof Sentinel?
Thisworkshopaimstoanswerallofthesequestions, andthensome!
CoveringthebasicsofSentinelPlaybooksusing LogicApps,withaneyeforbestpracticestokeepinto consideration.Youshouldpickupfirsthand experienceofrevolutionisingyouruseofLogicApps byimplementingamodulardesignstrategyto improvereusereducefunctionalcoupling,which meansneverhavingtorewritethatcomplicated workflowmorethanonce.

Theworkshopwillbe90minuteslong-pleasebring yourlaptopwithyou.

All round tech enthusiast that's too lazy to do thingsmyself!
XDRAutomationLeaderatCloudGuardAI Links&Socials
https://uk.linkedin.com/in/yakub-desai-41054998

12:00PM • ROOM 1 • HERRINGBONE SUITE
12:00 AM • ROOM 4 • CORDUROY ROOM
ABOUTTHETALK SPEAKER BIO


ABOUTTHETALK
ABOUT THE TALK
JavaScript files can be a goldmine for bug hunters and security researchers, but regular expressions alone aren't enough to reliably and cleanly extra data from them. jsluice is a new tool for extracting URLs, paths, and secrets from JavaScript using the powerofTree-sitter.

Tom is a security engineer at Bishop Fox. He likes to makes open source tools, like gron, meg, and anew; he also likes to teach people things, and occasioanllyhackwebstuff.

Socials&Links
Tools:http://github.com/tomnomnom

https://tomhudson.co.uk
@TomNomNom
We need to stop being the “smartest person in the room” - that’s not how we get our own way in Infosec. Is it cheaper or more expensive to do what we say? If it’s not cheaper, then we’re getting ignored no matter how “right” we are. A talk about usingSecurityArchitecturetogetourownway.

13:00PM • ROOM 2 • TWEED ROOM
ABOUT THE TALK 12:30PM • ROOM 1 • HERRINGBONE SUITE
ABOUT THE TALK SPEAKER BIO
Docker is an amazing tool! It has changed the way most businesses operate today. Why not leverage this fantastic technology to help enable security, thus helping security enable the business! This talk will cover several aspects of how Docker can be usedbysecurityteamstohelpthem.


SPEAKER BIO ABOUT THE TALK

With increasing connectivity and continuous advances in technology, the way we secure systemsneedstoevolveconstantly. This talk aims to shed light on the significant benefits that ChatGPT, an advanced AI-powered conversational agent, could bring to the realm of cybersecurity.Ornot!!!
Lorna is a Co-Founder of CAPSLOCK, an award winning cyber bootcamp. With a background in consulting, training and education, she has worked in cyber for over 15 years advising to the public and private sector and working at both strategic and operational level. Lorna is a proud northerner who is passionate and outspoken about removing barriers to entry into the cyber sector. Oh and Lego...shelovesLego!

Socials&Links
@CAPSLOCKCyber

13:00PM • ROOM 3 • WOOL ROOM
13:30PM • ROOM 2 • TWEED ROOM
So you want money to fund your cool tools, not so fast!
The tactics, techniques and procedures related to cyber security asset protection, attack prevention and event detection are what get the tech geeks propellor spinning, no doubt. Darren Conway more often rolls his sleeves up with stakeholders in defining cyber security programs and the governance framework identifying “why we do security”, “who does what”, and “to what standards or risk tolerances”. Somehow we need to impress uponexecutivemanagement;


·The budget we are requesting for cyber security maps to achieving the business objectives (“Show methemoney”)
·The tools we deploy require people and repeatable processes(“Toolsdon’trunthemselves”)
·The outcomes of our cyber security efforts are measurable and align with industry best practice and compliance demands (“All the cool kids are doingit!”)

The organisational Cyber Security Management Systemneedstoanswer;
·What needs to be documented, by whom and who ownsitall?
·Do we know what all our defensible assets and data are and that we are implementing adequate protectionsalignedwithmeasuredrisk?
·Do we understand our attack vectors, associated attack scenarios, alerts/thresholds, and have tested playbooksandrolesforeach?
This discussion is a global consultants experience in getting executives buy-in so that everything required to deliver, maintain or support networks and information systems for essential services is determined,understoodandfunded.
Cyber Security Services IT/OT Executive with over 25 years in the field. Having spent most of my career in professional services, I’ve excelled as a field practitioner, regional practice lead, services product manager, marketer, and team manager. This broad experience has helped me master the entire security services got-to-market framework.
If you’re looking to grow your cyber security advisory or deployment services revenue, while helping your customers solve their critical businesschallenges,Icanhelp.
Socials&Links
https://www.linkedin.com/in/darrenjamesconway/

ABOUTTHETALK SPEAKER BIO 13:30 • ROOM 3 • WOOL ROOM
Who isn’t trying to get lazier? In this talk, I’m going to show you how easy it is to build scripts to automate practically anything you could want to do in a web browser. We’ll create a ‘my first login’ script, weaponise it, then learn how to build web scrapers,shoppingbotsandotherfunstuff.
ABOUTTHETALK SPEAKER BIO

ABOUT THE TALK
In this talk, I’ll be sharing my findings, tips, and tools for identifying and exploiting account takeover vulnerabilities. If you are a Pentester or a Bug Bounty Hunter, Don’t miss this opportunity to enhance your skills to the next level. Join my talk tostayaheadofthegame.

Currently employed as a Senior Security Consultant/Penetration Tester at MDSec, with 9+ years of experience in the field. I have a deep understanding of vulnerability identification and exploitation techniques, a strong background in computer engineering, and extensive experience in Web/Mobile Apps and API security. I have also participated in bug bounty programs, finding security vulnerabilities in well-known companies andreceivingcreditsforthefindings.




Socials&Links
@sandh0t
https://ayoubsafa.com
14:30 • ROOM 1 • HERRINGBONE SUITE
ABOUTTHETALK
14:30PM • ROOM 2 • TWEED ROOM
Why use carpet bomb DDoS when a targeted strike consistent a few well crafted requests can cripple a service?

As an added bonus, precision strikes make it that mucheasiertoavoidWAFcountermeasures. And where to find this amazing cyber weapon? Why inaseeminglyunimportantCVSSscore7.5.
Socials&Links

https://beny23.github.io @giskard23


ABOUTTHEWORKSHOP
Matching with the conference’s theme of red meets blue, during this workshop we’ll create Android applications that utilise tamper detection and anticompromise techniques, then participants will swap and apply offensive security techniques to get aroundthesecuritymechanismsoftheirpeers.


The workshop will be 90 minutes long - please bring yourlaptopwithyou.


14:30PM • ROOM 3 • WOOL ROOM
ABOUTTHETALK
14:30 AM • ROOM 4• CORDUROY ROOM
ABOUT THE TALK
Misunderstanding is the foundation of misconfiguration and, later, security issues. Starting from an amusing anecdote of a misunderstanding leading to the most ridiculous XSS you’ve heard of, we’ll then look atwhat weas“security nerds” can be doingtoimprovethegeneralsecuritylandscape.


core, cybersecurity is all about risk. We need understand, report, and mitigate our risk. However, the industry adopted methods for analyzing risk lead to inaccurate assessments, math, and ultimately bad decision making andspending.Iwillshowyouwhy,andhowtofixit.
Socials&Links
https://www.linkedin.com/in/sara-anstey/
Alex played a crucial role in overseeing a team of expert penetration testers during an extraordinary assignment: a physical bank breach. This captivating talk offers insights into the pentest teams strategic utilisation of red teaming, reconnaissance, social engineering, and opensource intelligence to successfully breach the bank'sphysicalsecurity.



Socials&Links

@yorkshirecsc
Alex is a highly skilled sales and account management professional with a keen focus on the cyber security and penetration testing sector. With nearly two decades of experience in the industry, he excels in building strong client relationships. Passionate about fostering professional growth, Alex serves as a dedicated mentor, providing valuable insights and guidance to aspiring students and seasoned professionals alike. As a cyber security-focused individual, Alex brings a wealth of knowledge in security testing, infrastructure, architecture, solutions, and threat intelligence. While he may not be a technical consultant, his exceptional sales acumen and domain expertise make him a valuable partner in helping organizations address their security concernsandachievetheirbusinessobjectives.
15:00PM • ROOM 1 • HERRINGBONE ROOM
15:00PM • ROOM 2 • DENIM ROOM
At its core, cybersecurity is all about risk. We need to understand, report, and mitigate our risk. However, the industry adopted methods for analyzing risk lead to inaccurate assessments, invalid math, and ultimately bad decision making andspending.Iwillshowyouwhy,andhowtofixit.

Socials&Links


https://www.linkedin.com/in/sara-anstey/

Many cloud security breaches start from implementation mistakes: whether it be bad coding practices, misconfiguration, etc. Before (best case) your security team or (worst case) an outside attacker finds them; how can you be proactive aboutfindingandfixingcommonsecuritymistakes?



ABOUTTHETALK
15:00PM • ROOM 3 • WOOL ROOM
15:30PM • ROOM 1 • HERRINGBONE ROOM
ABOUTTHETALK
ABOUT THE TALK SPEAKER BIO
A Chatham House Style interactive session with Chris Roberts. Chris will share war stories, lessons learned, and you can ask him anything in this unrecordedsession.

Socials&Links
@Sidragon1
Chris is the CISO for Boom Supersonic and works as an advisor for several entities and organizations around the globe. His most recent projects are focused within the aerospace, deception, identity, cryptography, Artificial Intelligence, and services sectors. Over the years, he's founded or worked with several folks specializing in OSINT/SIGINT/HUMINT research, intelligence gathering, cryptography, and deception technologies. These days he’s working on spreading the risk, maturity, collaboration, and communication word across the industry. (Likely while coding his EEG-driven digital clone that’s monitoringhisteaandbiscuitconsumption!)
ABOUT THE TALK SPEAKER BIO

The rise of infrastructure automation is inevitable, but does it come at a cost? Companies have adopted various technologies to streamline their processes across different contexts. Software devs have utilised the technologies over the years, but how do we use this technology in a prod enivronment?

Socials&Links
https://www.northgreensecurity.com/



I am a senior security consultant & trainer from North Green Security, I am a massive believer in knowledge is for sharing and I have recently taken an interest in IaC, in particular Ansible and Terraform. I thought the Ansible Tower product wasanicewaytomanagethedeployment,butwas curious to how they could be taken advantage of aswell.

As for the One Direction question, completely unsure. What I can tell you though, is I like to take late night walks to the fridge, I am far to happy to seethelightasthedooropens.

15:30PM • ROOM 2 • TWEED ROOM
15:30PM • ROOM 3 • WOOL ROOM









HHACKING ACKING VVILLAGES ILLAGES


















LOCKPICKING age h t t p s : / / t w i t t e r . c o m / m i n t y n e t HACKINGVILLAGE •WOOL ROOM HACKINGVILLAGE •WOOL ROOM
INFOSEC BATTLEBOTS



At Infosec BattleBots, we're passionate about bringing together the exciting worlds of hardware-based fun and cybersecurity. Our primary focus is our Antweight BattleBot arena, where enthusiasts can engage in thrilling battles with their custom-built robots. It's an excellent opportunity to test your skills, strategies, and innovations in a physical setting.
Cloth Hall Court
In the heart of Leeds’ vibrant centre, just a twominute walk from the main railway station, Cloth Hall Court is an exciting new addition to our portfolio of events spaces. Its prime central location ensures convenient ease of access for your delegates. For more details scan the QR Code below:


HACKINGVILLAGE •BOBBINSUITE
quiet room

Soft skills workshop
An Interactive soft skills workshop, that will test your influencing and stakeholder management skills, whilst giving you a fun team based challenge to complete.

Quiet room is available at the Seamstress Suite on the second floor, apart from between 1030am and 1130am. If you need a quiet space during this time, ask one of our volunteers, who can take you to the 3rd floor space.
10:30am - 11:30am - Soft Skills Workshop is in the Seamstress Suite.

CHILLOUTSPACE •SEAMSTRESSSUITE

THANK YOU!
To our fabulous speakers, volunteers, and sponsors,
We want to extend a massive thank you to each and every one of you for your incredible contributions to BSides Leeds 2023. We couldn't have done it without you!
Speakers - Your expertise, passion, and captivating presentations made the conference truly unforgettable. You shared invaluable insights and inspired us all. Thank you for taking the time to be a part of this event and making it a resounding success.
Volunteers - Your dedication and tireless efforts behind the scenes were the glue that held everything together. From assisting with logistics to ensuring attendees felt welcomed, your support was absolutely essential. We appreciate your hard work and the positive energy you brought to the conference.
Sponsors - Your generous support and belief in our vision made this event possible. Your contributions allowed us to create an enriching experience for all participants. We are deeply grateful for your partnership and the impact it had on the success of the conference.
OUR VOLUNTEERS
Daniel Perez Cascon • Paul W • Farzan Mirza • Nathaniel McHugh
Dom Goldthorpe • Jeffrey Mark Ransom • Izabela Paul • Mhairi Joyce
Mark Spencer • Kate Woolley • Federico Murgia • Matt Treadwell
Lundsay Wojtula • Ben Docherty • Guy Fabron • Tom Singh • Tom Hebbron
Roachy • Alice McGready • Scott McGready • John Duncan
Gerard Barrett • Harvey Baxter • Laura Whitaker • Craig Nicholson • Dawid
Peter Oluwaseyi Oladotun • Nick Lines • Umair • David Higginbotham
Lisa Fellows
A heartfelt thank you to each and every one of our volunteers for your dedication, enthusiasm, and hard work. Your contributions were essential in making this conference a success. We deeply appreciate your efforts and commitment to making BSides Leeds 2023 amazing!
CONFERENCE MVP
Thank you once again for making BSides Leeds 2023 an outstanding success.
With heartfelt appreciation,
The BSides Leeds Organising Team x
A massive shout out and huge thank you to our fabulous MVP Cooper, the amazing videographer who films countless BSides conferences across Europe and the UK. These conferences wouldn't be the same without your incredible work!
All of the videos from BSides Leeds 2023 will be available after the conference on our youtube page!





M E E T O U R S P O N S O R S
M















E E T O U R S P O N S O R S

N O T E S P A G E
N O T E S P A G E



CONNECTWITHUS!





























































































