09:30
10:00

OPENING REMARKS (HERRINGBONE SUITE)
KEYNOTE - HOLLY FOXCROFT (HERRINGBONE SUITE)
10:30 THE MISCREANT'S FIELD MANUAL FOR EXPLOITING SECRETS
MACKENZIE JACKSON
11:00 PHYSICAL AND INFORMATION SECURITY IN THE NHS
PHIL SMITH
11:30 V FOR VEDETTE (A WARNING FROM THE FRONTLINES) SIMON DYSON
12:00
EXPLOITING SNI SSRF TO ACCESS THE AWS IMDSV2 OLIVER MORTON
12:30 WEARABLE, SHAREABLE... UNBEARABLE? THE IOT AND AI TECH NOBODY ASKED FOR BUT CYBERCRIMINALS LOVE!
LIANNE POTTER & JEFF WATKINS (COMPROMISING POSITIONS)
DECODING CRISIS: UNRAVELLING THE HUMAN BRAIN’S ROLE IN CRISIS RESPONSE BEC MCKEOWN
DISSECTING THE APT WILDERNESS: A JOURNEY BEYOND BEARS AND DRAGONS ALSA TIBBIT
BACK TO THE FUTURE: A LOOK AT FUTURE TECH AND ITS IMPACT ALEX MARTIN
POTENTIAL SECURITY DEVIATION: I HAVE A NUMBER FOR YOU TO CALL SEÁN GUTHRIE
LUNCH BREAK
13:00
LUNCH BREAK 13:30
"FROM NOISE TO INSIGHT: SUPERCHARGE YOUR SOC WITH AUTOMATED ALERT CORRELATION" ANICET FOPA TCHOFFO 14:00
RESPONDING TO CYBER ATTACKS HEATHER LOWRIE (SPECIAL GUEST!)
14:30
ABUSING AZURE ARC: FROM SERVICE PRINCIPAL EXPOSED TO REVERSE SHELL CHRISTIAN BORTONE
FREAKS OF THE WIRELESS – THE STORY OF THE FIRST WIRELESS HACK DEN KNOWLES
BEYOND THE DIAL TONE: UNDERSTANDING PBX PHREAKING AARON KELLY
15:00 COFFEE BREAK
15:30 DEALING WITH THE DEVIL: RANSOMWARE NEGOTIATION TACTICS
MICHAEL LAMB THE MORE THINGS CHANGE, THE MORE THEY STAY THE SAME TIM BURNETT
16:00
WORKSHOP SLOTS FOR MAIN STAGE
UNVEILING THE CYBERSECURITY BALANCING ACT: A DAY IN THE LIFE OF A PURPLE TEAMER HANI MOMENIA & CHRISTOPHER TAYLOR
16:30 CLOSING PANEL (HERRINGBONE SUITE)
17:15 CLOSING REMARKS - BSIDES LEEDS TEAM (HERRINGBONE SUITE)
17:30 CONFERENCE CLOSE DOWN - HEAD TO AFTERPARTY!!!
09:30

OPENING REMARKS (HERRINGBONE SUITE)
10:00 KEYNOTE - HOLLY FOXCROFT (HERRINGBONE SUITE)
10:30 THE ALGORITHMIC ADVANTAGE: OPTIMIZING CYBERSECURITY WITH COMPUTER SCIENCE
SARA ANSTEY
11:00 THE LADYBIRD BOOK OF QUANTUM: EVERYTHING YOU WILL EVER NEED TO KNOW (AND SOME STUFF YOU PROBABLY DON'T) FREY WILSON
11:30
DANGER? LOOK HERE AND LET ME KNOW SEL ROBERTSON
12:00 LUNCH BREAK 12:30
13:00 FROM PANIC TO PROTOCOL: DIGITAL FORENSICS AND INCIDENT RESPONSE RORY WAGNER
13:30 FROM 0 TO 1337: A BEGINNER’S GUIDE TO COMPETITIVE HACKING VIC GALVAN
14:00 AN INTRODUCTION TO CODE COMPILATION TOM BLUE
14:30 CYBER FRAUD LANDSCAPE JORDAN POWELL
15:00 COFFEE BREAK
15:30 LIFTING THE HOOD, OPEN-SOURCING A TTX METHODOLOGY FOR YOUR DIY SUCCESS. ELIZA-MAY AUSTIN
16:00 HOW TO INVESTIGATE YOUR FIRST RANSOMWARE CHRISTOPHER LAIRD
16:30 TEACH A MAN TO PHISH? DESIGNING A WORKSHOP TO ADDRESS GAPS IN PHISHING SIMULATIONS
LINDSAY WOJTULA
16:45 CLOSING PANEL- (HERRINGBONE SUITE)
17:15 CLOSING REMARKS - BSIDES LEEDS TEAM (HERRINGBONE SUITE)
17:30
CONFERENCE CLOSE DOWN - HEAD TO AFTERPARTY!!!
C O N F E R E N C E T I M E T A B L E C O N F E R E N C E T I M E T A B L E

SINCEIT’SINCEPTIONINJAN2018,BSIDESLEEDSHASBEENKNOWN INTHEUKINFOSECCOMMUNITYFORPUSHINGTHEENVELOPE.
ITWASTHEFIRSTUKCONFERENCETOHAVEMENTALHEALTHAND CARHACKINGVILLAGESANDTHEFIRSTUKBSIDESWITHAPUBLISHED CODEOFCONDUCT.IT’SENCOMPASSEDEVERYTHINGFROMLOW LEVELHARDWAREHACKINGTOSECURITYARCHITECTURE,AITOOFFTHE-RECORDWARSTORIESFROMINDUSTRYLUMINARIES.ITWAS ALSOTHEFIRST( ERHAVEPERSIAN POETRYUSED INGSPEECHES.
IT’SRUNENTIRELYB
OFKEEPINGTICKET PRICESASLOW AVAILABLETO EVERYONE.WEWOR ENTGROUPS,HACK SPACES,ANDOTHE WITHSOMEOFTHE BESTSPEAKER REAFOCUSOF KNOWLEDGESHA EBRIGHTESTAND BESTFROMTHEA OSELOOKINGFOR SOME EDITS!

PREVIOUSSPEAKERS&EVENT/VILLAGEORGANISERSHAVEINCLUDED (INNOPARTICULARORDER)LISAFORTE,DANCUTHBERT FC&DRJESSBARKER,HOLLYGRACE-WILLIAMS, ANDREW“CYBERGIBBONS”TIERNEY,AMANDABERLIN, MARKCARNEY,TOM‘TOMNOMNOM’HUDSON,‘LINTILE”, CHRISRATCLIFF,IAN“MINTYNET”TABOR,ELIZA-MAYAUSTIN,SARAH YOUNG,ANDYGILL,SASKIACOPLANS,IAN“PHATHOBBIT” THORNTON-TRUMP, JAYHARRIS,MEADOWELLIS,DARENMARTIN,DAN“MRR3B00T”CARD, CHRISROBERTS,JAMESBORE,LEWISARDEN,GLENNPEGDEN...
…TONAMEBUTAFEW.








K E Y N O T E S P E A K E R


HOLLY FOXCROFT IS AN AWARD-WINNING SPEAKER AND LEADER IN CYBER NEURODIVERSITY SHE CHAMPIONS NEUROINCLUSION, PROMOTING BEST PRACTICES AND FURTHERING RESEARCH TO UNDERSTAND NEURODIVERSITY AND ITS CRITICAL ROLE IN CYBER.
HOLLY STARTED HER CAREER IN DEFENCE AND HOLDS A FIRST-CLASS DEGREE IN CRIMINOLOGY AND CYBERCRIME; SHE CARVED HER CAREER IN SPECIALISING IN NEURODIVERSITY AND CYBER. HOLLY ALSO LEADS THE PORTSMOUTH DIGITAL DRIVE TEAM IN CYBER, SUPPORTING THE CITY AND ITS SCHOOLS IN CYBERSECURITY AWARENESS AND SHOWCASING HOW TO BUILD DIGITAL TECHNOLOGY RELATIONSHIPS
HOLLY IS CURRENTLY RESEARCHING NEURODIVERSITY’S IMPACT ON CYBER SECURITY AND RISK MANAGEMENT SHE WORKS TIRELESSLY TO ENSURE THE INCLUSION OF NEURODIVERGENT INDIVIDUALS IN CYBER, PROMOTING THE IMPORTANCE OF MENTAL WELLBEING
THIS TALK WILL CLOSELY LOOK AT THE HUMAN FACTORS IN CYBER SECURITY, EXPLORING THE LINKS BETWEEN BRAIN NEUROTYPES AND CHARACTERISTICS INCLUDING IMPULSIVITY, CYBER CRIME, INTERNET ADDICTION AND ATTITUDES TOWARDS CYBER SECURITY. THE TALK WILL ALSO LOOK AT WAYS WE CAN ADDRESS RISKY BEHAVIOURS AND FURTHER BOLSTER CYBER SECURITY POSTURE


EXPOSED SECRETS LIKE API KEYS AND OTHER CREDENTIALS ARE THE CROWN JEWELS OF ORGANIZATIONS BUT CONTINUE TO BE A PERSISTENT VULNERABILITY WITHIN SECURITY. THE MAJORITY OF SECURITY BREACHES LEVERAGE SECRETS AT SOME POINT DURING THE ATTACK PATH
THIS PRESENTATION SHEDS LIGHT ON THE VARIOUS METHODS USED BY ATTACKERS TO DISCOVER AND EXPLOIT THESE SECRETS IN DIFFERENT TECHNOLOGIES
THIS MANUAL WILL INCLUDE HOW TO: ABUSE GITHUB PUBLIC API, GAIN UNAUTHORISED ACCESS TO PRIVATE GIT REPOS, DECOMPILE CONTAINERS DECOMPILE MOBILE APPLICATIONS FROM THE APP AND PLAY STORES
WE COMBINE NOVEL RESEARCH, REALLIFE ATTACK PATHS, AND LIVE DEMOS TO PROVE EXACTLY THE STEPS ATTACKERS TAKE, REVEALING THEIR PLAYBOOK!
RECENT RESEARCH HAS SHOWN THAT GIT REPOSITORIES ARE TREASURE TROVES FULL OF SECRETS A YEAR-LONG STUDY SHOWED THAT 10 MILLION SECRETS WERE PUSHED INTO PUBLIC REPOSITORIES IN 2022 ALONE
WE WILL SHOW EXACTLY HOW ADVERSARIES ABUSE THE PUBLIC GITHUB API TO UNCOVER THESE SECRETS, EVEN LEAKING SECRETS LIVE TO SHOW HOW QUICKLY ATTACKERS DISCOVER AND EXPLOIT THEM PUBLIC SOURCE CODE, HOWEVER, IS ONLY THE TIP OF THE ICEBERG AS PRIVATE CODE REPOSITORIES HAVE PROVEN TO BE MUCH MORE VALUABLE TARGETS
WE WILL DEMONSTRATE HOW TO GAIN UNAUTHORISED ACCESS TO PRIVATE GIT REPOSITORIES AND DISCOVER SECRETS DEEP IN THEIR HISTORY. THIS WILL INCLUDE SUPPLY CHAIN POISONING, DEVELOPER PHISHING, AND CONFIGURATION EXPLOITATION AMONG OTHER TECHNIQUES. FINALLY, THIS TALK WILL DIVE INTO DECOMPILING CONTAINERS, PACKAGES, AND MOBILE APPLICATIONS TO BE ABLE TO UNCOVER THE HUGE AMOUNT OF SECRETS BURIED WITHIN REVEALING HOW SHOCKINGLY COMMON IT IS TO FIND HARDCODED SECRETS
KNOWING HOW ATTACKERS OPERATE IS ESSENTIAL IN BUILDING EFFECTIVE DEFENCES, UNDERSTANDING THE ATTACKER'S PLAYBOOK ALLOWS YOU TO UNDERSTAND THEIR NEXT MOVES THIS PRESENTATION IS PERFECT FOR ANYONE WANTING TO KNOW HOW TO PREVENT ATTACKERS FROM GETTING HOLD OF YOUR CROWN JEWELS.

SOME TALES FROM THE NHS, LOOKING AT VULNERABILITIES CAUSED BY COMPLIANCE, PEOPLE, PORN, OLD EQUIPMENT AND EVERYONE'S FAVOURITE; THE GOVERNMENT TRYING TO SELL OUR HEALTH DATA
I) COMPLIANCE CONFLICTS AND COMPROMISES - HOW COMPLIANCE WITH ACCREDITATION STANDARDS CAN DEGRADE PHYSICAL SECURITY.
II) PORNOGRAPHIC MEDICAL EQUIPMENTHOW A PORN VIRUS GOT ONTO A HOSPITAL NETWORK VIA AN ULTRASOUND MACHINE RUNNING WINDOWS XP THIS ALSO COVERS THE FAD OF STICKING WEBCAMS ON MEDICAL EQUIPMENT THAT IS PROBABLY GOING TO BE IN SERVICE LONG AFTER MANUFACTURERS STOP SUPPORTING IT
III) PAPERLESS WOES - A CURRENT SITUATION; COMPLEXITIES OF GOING PAPERLESS, TRANSFERRING OF RESPONSIBILITIES FOR RECORDS FROM CLINICAL DEPARTMENTS TO CENTRALISED IT.

HOW DO WE ENSURE CLINICAL TEAMS HAVE ACCESS TO PATIENT RECORDS WHEN THE NETWORK IS DOWN? WHAT'S THE NEW PLAN B WITHOUT PAPER RECORDS?
IV) PEOPLE PLEASING PEOPLE - THE EFFECT OF PSYCHOLOGICAL PROFILES OF PEOPLE WHO ENTER CARING PROFESSIONS ON SECURITY AND HOW I'VE NOT WORN AN ID BADGE FOR OVER A DECADE I ALSO MADE AN ID BADGE FOR THE FISH TANK HE'S A CONSULTANT FISHIOLOGIST
V) MY MP DID THIS BEFORE GOING TO PRISON - THE INTENDED NHS CENTRALISED "BIG DATA" DATASET TO SELL TO COMPANIES FOR RESEARCH. GOT STOPPED BY MY MP, PENDING FIXING. HE THEN WENT TO PRISON FOR SOMETHING COMPLETELY DIFFERENT.
VI) STEAMPUNK SYSTEMS - WHAT HAPPENS WHEN YOU INTRODUCE MODERN NETWORKING EQUIPMENT INTO A VICTORIAN ERA BUILDING (HINT: YOU FIND NETWORKING KIT SHOVED INTO RANDOM STORAGE CUPBOARDS WITH THE DOORS HANGING OPEN AND USING 1970S LATCHES WHICH APPEAR TO GET ROUTINELY SLIPPED OPEN BY THE IT GUYS)

REVISITING SOME OF THE MEMORABLE HACKING AND CYBER-ATTACKS OVER THE LAST FEW DECADES FROM A FRONTLINE CYBER DEFENDER AND INVESTIGATOR
REVISITING 20 YEARS OF TECHNICAL AND INVESTIGATION EXPERIENCE AS A POLICE OFFICER THEN AS A CYBER DEFENDER IN LARGE CYBER SECURITY OPERATIONS CENTRE (CSOC) ENVIRONMENTS.

FROM THOSE EARLY MEMORIES OF COMPUTING AND EARLY WORKPLACE EXPERIENCES BEFORE STARTING A 14YEAR POLICE CAREER TAKING IN TECHNICAL INVESTIGATIONS BEFORE WORKING AS CYBER CRIME INVESTIGATOR INVESTIGATING EARLY RANSOMWARE GROUPS AND THE START OF CRYPTOCURRENCY INVESTIGATIONS
WE WILL TALK ABOUT THE RISE OF THE BOTNETS, DDOS & STRESSORS. INTERESTING DARKWEB INVESTIGATIONS
AS A CYBER SECURITY PROFESSIONAL SIMON HAS LED TEAMS IN THE NHS AND MORE RECENTLY IN THE HOME OFFICE HE CHOSE TO JOIN THE LEAD ROLE AT THE NHS CSOC JUST WEEKS BEFORE THE START OF COVID! IN ADDITION HE HAS FURTHER SUPPORTED PUBLIC SECTOR AREAS AND FOLLOWING SOME MATURITY WORK HE LATER BECAME THE HEAD OF THE CYBER SECURITY OPERATIONS CENTRE FOR THE HOME OFFICE.
THIS TALK WILL COVER INCIDENTS AND VULNERABILITIES THAT STOLE OUR SLEEP AND ANALYSE SOME OF THE FUNDAMENTAL TECHNIQUES AND DRIVERS OF THESE CYBER CRIMINAL GROUPS IN ADDITION VISIT SOME OF THE THEMES AROUND CRYPTOCURRENCY AND BLOCKCHAIN INVESTIGATIONS FROM A FEW OF SIMONS PUBLISHED ACADEMIC PAPERS ON THE SUBJECT TOUCH ON SOME NEW AND EMERGING TRENDS
CONCLUDE WITH A LOOK ACROSS THE TIMELINE TO ASSESS IF ANYTHING HAS REALLY CHANGED THIS TALK IS A SUNSET TALK ON THE GLORY DAYS OF INVESTIGATIONS PERFORMED BY ACTUAL HUMANS!
AWS HAVE GONE TO SIGNIFICANT EFFORT TO PROTECT VERSION 2 OF THEIR INSTANCE METADATA SERVICE FROM SERVER SIDE REQUEST FORGERY.
THIS TALK DISCUSSES A MEANS OF BYPASSING ALL THE PROTECTIONS (WHEN CIRCUMSTANCES ARE RIGHT)
THE WALK WILL ALSO INCLUDE AN "ACCESSIBLE TO ALL" BREAKDOWN OF THE TECHNOLOGIES INVOLVED AND SPECIFIC VULNERABILITIES.














IN A WORLD OF 5G (NO CONSPIRACY THEORIES PLEASE!) SMARTPHONES, SMART TVS AND SMART HOMES, WE'RE INVITING MORE TECH INTO OUR LIVES THAN EVER. WE'RE SLEEPWALKING INTO A FUTURE NOBODY ASKED FOR, BUT MAYBE MANY FEAR
HOW ALWAYS-ON MICROPHONES, CAMERAS AND AI ARE CREATING A "DIGITAL PANOPTICON" NONE OF US PROBABLY WANT OR NEED, UNLESS YOU'RE AMAZON SHOULD WE BECOME "DIGITAL PREPPERS"? IS THE PRIVACY AND SECURITY RISK SO HIGH, WHAT ARE THE STAKES?
THIS IS AN ANTHRO-TECHNOLOGIST VIEW ON HOW DUMB AN IDEA THE SMART REVOLUTION IS AND HOW WE'VE ERODED OUR SOCIAL CONTRACTS IN FAVOUR OF BIG TECH.



LIANNE POTTER IS HEAD OF SECURITY OPERATIONS AT A MAJOR UK RETAILER, SHE IS ALSO A CYBER ANTHROPOLOGIST AND PODCAST HOST AT COMPROMISING POSITIONS
JEFF WATKINS IS CHIEF PRODUCT AND TECHNOLOGY OFFICER AT XDESIGN AND PODCAST HOST AT COMPROMISING POSITIONS.
RESPONDINGTOANDRECOVERINGFROMCYBERATTACKSISAKEY STRATEGICCHALLENGEFACINGTHEHIGHEREDUCATIONSECTOR. THIS IS A GLOBAL CHALLENGE, ESPECIALLY FOR UNIVERSITIES INVESTEDWITHKEYRESEARCHPARTNERSHIPSANDINTELLECTUAL PROPERTY
THE UNIVERSITY OF MANCHESTER IS A POWERHOUSE OF RESEARCH,WITHAHISTORYOFWORLD-CHANGINGACHIEVEMENTS, ANDISRANKEDAMONGTHELEADINGRESEARCHUNIVERSITIES GLOBALLY MANCHESTERWASTHEFIRSTBRITISHUNIVERSITYTO SETSOCIALRESPONSIBILITYASACOREGOAL.
THISTALKWILLDISCUSSTHEANATOMYOFACYBERATTACKON THEUNIVERSITYANDPROVIDEANOVERVIEWOFTHESTRATEGIC RESPONSEANDRECOVERY THETALKDISCUSSESTHEINCIDENT RESPONSEANDSECURITYROADMAPFROMTHEPERSPECTIVEOF THEUNIVERSITY’SFIRSTCHIEFINFORMATIONSECURITYOFFICER, FACEDWITHTHEATTACKDURINGHERFIRST100DAYSINTHEROLE.




AZURE ARC IS AN INNOVATIVE HYBRID CLOUD PLATFORM THAT FACILITATES THE MANAGEMENT OF WINDOWS AND LINUX MACHINES LOCATED OUTSIDE OF AZURE, WHETHER ON CORPORATE NETWORKS OR WITH OTHER CLOUD PROVIDERS.
IN THIS TALK, WE WILL EXAMINE A NEWLY IDENTIFIED SECURITY FLAW THAT ALLOWS BAD ACTORS WITHIN A CORPORATE ENVIRONMENT TO GAIN CONTROL OVER A SERVICE PRINCIPAL ACCOUNT, GIVING THEM THE ABILITY TO CONTROL BOTH AZURE ARC AND INTERNAL INFRASTRUCTURE.
WE WILL EXAMINE THE TECHNICAL DETAILS OF THE ATTACK, LOOKING AT THE SCRIPTS, TOOLS, AND TECHNIQUES USED CONCURRENTLY WE WILL EXPLORE THE PIVOTAL ROLE PLAYED BY THE SERVICE PRINCIPAL DURING THE ONBOARDING PHASE, EXAMINING HOW ITS CREDENTIALS ARE SAFEGUARDED
AND STORED FINALLY, WE WILL EXPLORE THE RAMIFICATIONS OF THIS VULNERABILITY AND DISCUSS POTENTIAL REMEDIATION STRATEGIES
THIS TALK IS ESSENTIAL FOR ANYONE WITH AN INTEREST IN AZURE SECURITY, ESPECIALLY PENETRATION TESTERS AND SECURITY ANALYSTS IT PROVIDES VITAL INSIGHTS INTO A NEW TECHNIQUE THAT CAN BE USED IN PENETRATION TESTING AS A STRATEGIC METHOD FOR PIVOTING TO THE CLOUD


THIS PRESENTATION WILL PROVIDE A COMPREHENSIVE OVERVIEW OF MY EXPERIENCE NEGOTIATING WITH A THREAT ACTOR
THROUGHOUT THE TALK, I WILL SHARE VALUABLE TIPS AND STRATEGIES ON HOW YOU CAN EFFECTIVELY WEAR THEM DOWN, ULTIMATELY CAUSING THEM TO TRIP UP AND EXPOSE THEMSELVES
THE GOAL OF THIS TALK IS TO PROVIDE KNOWLEDGE AND INSIGHTS THAT CAN MAKE A SIGNIFICANT DIFFERENCE IN YOUR APPROACH TO DEALING WITH THREAT ACTORS.


 MICHAEL LAMB MICHAEL LAMB
MICHAEL LAMB MICHAEL LAMB



WE’VE GOT NICE AND NIST AND PLAYBOOKS GALORE, YET TECHNOLOGY ALONE CAN'T WIN THIS WAR HUMAN KNOWLEDGE AND SKILLS WE NEED TO EXPLORE, TO FACE CYBER THREATS LIKE NEVER BEFORE.
THE GROWTH OF TECHNOLOGYDRIVEN SOLUTIONS MIGHT REDUCE THE IMPACT OF A CRISIS BUT IT DOESN’T ELIMINATE THE CHALLENGE OF UNCERTAINTY OR HELP US UNDERSTAND WHY PEOPLE ACT THE WAY THEY DO IN A CRISIS
COME ALONG TO THIS 30-MINUTE TALK FOR A WHISTLE-STOP TOUR OF THE BRAIN AND LEARN ABOUT THE HUMAN SCIENCE BEHIND CRISIS RESPONSE.

THIS TALK EXPLORES THE NAMING CONVENTIONS FOR ADVANCED PERSISTENT THREATS (APTS) WITHIN CYBERSECURITY
DISSECTING THE VARIED NAMING SYSTEMS USED BY PROMINENT SECURITY ORGANISATIONS, THIS TALK HIGHLIGHTS THE CRITICAL IMPACT OF THESE CONVENTIONS ON THE BROADER ASPECTS OF DETECTION, PREDICTION, AND POLITICAL DISCOURSE IN CYBERSECURITY
THE CHALLENGE TO EXISTING NAMING PRACTICES UNDERSCORES AN ESSENTIAL DEBATE ON IMPROVING CYBERSECURITY MEASURES.
THIS TALK WILL EMPHASISE THE NEED FOR A STANDARDISED NAMING SYSTEM TO ENHANCE THREAT INTELLIGENCE SHARING AND OPERATIONAL COLLABORATION ACROSS THE INDUSTRY
THIS TALK IS PART




A LOOK AT EMERGING TECHNOLOGY AND HOW IT WILL MOST LIKELY BE ADOPTED VERY QUICKLY, REMOVING THE NEED FOR MOBILE PHONES, COMPUTERS AND LAPTOPS
DISCUSS HOW THIS NEW TECHNOLOGY AND ACCESS TO DATA ONLINE WILL IMPROVE EFFICIENCY IN THE WORKPLACE, CREATIVITY AND INNOVATION
CONSIDER THE IMPACT THAT AN INCREASE ONLINE COMMUNITY WILL HAVE ON DATA CENTRE WORKLOAD AND HOW THEY WILL NEED TO EVOLVE TO MEET THE DEMAND
HIGHLIGHT HOW, AS MORE PEOPLE JOIN THESE ONLINE COMMUNITIES THERE WILL BE A HUGE INCREASE IN THE AMOUNT OF PERSONAL DATA STORED ONLINE
THIS WILL LEAD TO AN INCREASED THREAT FROM MALICIOUS THREAT ACTORS ATTEMPTING TO ACCESS AND STEAL SUCH DATA THROUGH NEW AND INNOVATIVE METHODS SPECIFICALLY TAILORED TO THIS TECHNOLOGY.
THERE ARE ALSO MENTAL HEALTH CONSIDERATIONS. POSITIVELY, VISUAL BIAS WILL DECREASE, AND INCLUSIVITY WILL INCREASE NEGATIVELY, THE LACK OF HUMAN INTERACTION WILL IMPACT SOFT SKILLS AND THERE IS A POTENTIAL FOR A RISE IN DISCONNECTION FROM REALITY


SECURITY DISCLOSURES ARE A CRUCIAL VECTOR IN THE CYBERSECURITY INDUSTRY FOR HELPING COMPANIES WITH IDENTIFYING AND MITIGATING WEAKNESSES IN THEIR SYSTEMS - THIS IS NO DIFFERENT IN THE AVIATION SECTOR, AFFECTING EVERYONE FROM THE TICKET VENDORS TO THE COMPANIES FLYING THE PLANES
HISTORICALLY, RESPONSIBLE DISCLOSURE HASN'T ALWAYS WORKED IN AVIATION, AND IT TOOK SEVERAL YEARS FOR COMPANIES TO GET TO THE POINT OF EFFECTIVELY ACCEPTING AND MANAGING SECURITY REPORTS
THIS TALK WILL COVER THE HISTORY OF SECURITY DISCLOSURES IN AVIATION, SOME EXAMPLES OF SUBMISSIONS WE'VE RECEIVED IN MY TIME IN THE AVIATION SPHERE, AND HOW THEY'VE BEEN MANAGED.






IN THE RELENTLESS BATTLE AGAINST CYBER THREATS, ATTACKERS MOVE SWIFTLY AND STEALTHILY THROUGH NETWORKS.
TO KEEP PACE, SECURITY ANALYSTS AND INCIDENT RESPONDERS MUST QUICKLY LOCATE AND CONTAIN THESE THREATS HOWEVER, TRADITIONAL SECURITY TOOLS OFFER LIMITED INSIGHTS – A TROUBLESOME ALERT WITH MINIMAL CONTEXT ABOUT THE ATTACK AND PRECIOUS TIME IS LOST IN MANUAL INVESTIGATIONS.
THIS IS WHERE KIBALCOR, A TOOL I DEVELOPED USING OPEN-SOURCE COMPONENTS, OFFERS A SOLUTION IT TRANSFORMS EVEN THE MOST BASIC SECURITY ALERT INTO ACTIONABLE INTELLIGENCE

KIBALCOR AUTOMATICALLY CORRELATES EVENTS, BUILDING A COMPREHENSIVE TIMELINE OF AN ATTACKER'S ACTIONS ON A SYSTEM, REVEALING THE CRITICAL "WHAT" AND "WHEN" OF AN INCIDENT KIBALCOR'S PRIMARY GOAL IS TO STREAMLINE THE TRIAGE AND SCOPING PROCESS OF SECURITY INVESTIGATIONS
CONTEXT IS EVERYTHING ANY SOC ANALYST KNOWS THE FRUSTRATION OF VAGUE, LOW-PRIORITY ALERTS KIBALCOR CUTS THROUGH THE NOISE, AUTOMATING THE LABOR-INTENSIVE PROCESS OF LOG ANALYSIS AND CORRELATION ANALYSTS OFTEN DISMISS REPETITIVE ALERTS AS FALSE POSITIVES, BUT WHAT IF ONE OF THOSE "FALSE POSITIVES" IS THE REAL DEAL?
BECAUSE MANUAL INVESTIGATIONS ARE SO TIME-CONSUMING, THE RISK OF MISSING A CRITICAL THREAT INCREASES. KIBALCOR EMPOWERS ANALYSTS WITH THE ENRICHED CONTEXT TO MAKE INFORMED DECISIONS QUICKLY - IS IT A GENUINE THREAT OR NOT? IN THIS TALK, I WILL PROVIDE A BRIEF OVERVIEW OF MY TOOL, DEMONSTRATING ITS IMPLEMENTATION AND HOW ITS CORE CONCEPTS CAN EMPOWER SECURITY INVESTIGATIONS ACROSS DIFFERENT ENVIRONMENTS.
IN 1901 A GRAND RIVALRY FORMED BETWEEN THE FAMOUS MAGICIAN NEVIL MASKELYNE AND GUGLIELMO MARCONI, THE FATHER OF RADIO. OVER THE FOLLOWING YEARS THE CONFLICT INTENSIFIED, STERN WORDS WERE EXCHANGED, EGOS WERE BRUISED, AND REPUTATIONS CRUSHED
THE EXPERIMENTS THEY CONDUCTED DURING THE EARLY DEVELOPMENT OF WIRELESS TELEGRAPHY AND THEIR MUTUAL DISDAIN LED TO THE FIRST WIRELESS HACK, THE FIRST BUG BOUNTY, THE FIRST HACKER PSEUDONYM, AND THE FIRST DENIAL OF SERVICE ATTACK WELL PROBABLY
THIS TALK WILL COVER AN EXAMINATION OF MASKELYNE, THE KEY EVENTS DURING HIS RIVALRY WITH MARCONI, AND THE COMMERCIAL CONSIDERATIONS THAT ULTIMATELY LED TO MARCONI’S SUCCESS OVER HIS COMPETITORS.



RELIVING THE WORLD BEFORE TEAMS WAS IN WIDE USE, WE WILL BE LOOKING AT HOW AN ATTACKER CAN TAKE CONTROL OF A PBX SYSTEM AND MAKE THEMSELVES THOUSANDS IN THE PROCESS
THROUGH THIS TALK, I WILL EXPLAIN HOW PBX'S WORK, HOPEFULLY IN A SOMEWHAT COMICAL FASHION, WHY THIS MAKES THEM VULNERABLE, HOW THE EXPLOITATION WORKS AND WHAT MADE THEM SO SUCCESSFUL
THE TALK WILL INCLUDE A SHORT DEMO WHERE A SMALL VOIP SYSTEM I SET UP PRIOR TO THE TALK, WILL BE USED TO DEMONSTRATE THE EXPLOITATION, AND HOW EFFECTIVE IT CAN BE LIVE TO EVERYONE IN THE ROOM
THE TALK TAKES INSPIRATION FROM DARKNET DIARIES EPISODE 1 AND A RECENT ACQUISITION OF AN OBSOLETED VOIP PHONE FROM LANCASTER UNIVERSITY RADIO STATION
I WILL ALSO USE THIS TO LEAD INTO DISCUSSING HOW TO SECURE THESE SYSTEMS,



I’VE BEEN AN IT AND SECURITY PROFESSIONAL FOR OVER 30 YEARS YOU’D LIKE TO IMAGINE THAT, IN THAT TIME, WE’D HAVE MOVED ON SIGNIFICANTLY, WITH RADICAL IMPROVEMENTS TO HOW WE ACCESS, PROCESS AND, MORE IMPORTANTLY, SECURE INFORMATION. YET, WHEN I ATTEND INDUSTRY CONFERENCES AND READ ARTICLES ON SITES LIKE LINKEDIN IT STRIKES ME:
HE PRESENTATIONS AND RECOMMENDATIONS WERE PRETTY MUCH EXACTLY THE SAME AS WE WERE DISCUSSING 20 YEARS AGO OK, SO THE TECHNOLOGY HAS GOT MORE POWERFUL, FASTER, SMALLER AND CHEAPER; CONNECTION SPEEDS HAVE ROCKETED AND WE NOW DO EVERYTHING ONLINE, BUT THE BASICS REALLY HAVEN’T CHANGED PERHAPS IT’S BECAUSE HUMANS HAVEN’T CHANGED MUCH – WE’RE STILL REALLY ONLY A FEW GENERATIONS ON FROM OUR CAVEDWELLING, CHEST-BEATING HUNTER/GATHERER ANCESTORS

THE INDUSTRIAL REVOLUTION WAS ONLY ABOUT 150 YEARS AGO AND WHAT WE CONSIDER NOW TO BE THE CYBER WORLD IS A MERE COUPLE OF DECADES ALTHOUGH THERE HAVE BEEN SOME SEISMIC CHANGES IN THAT TIME, TO THE POINT WHERE WE HAVE ACCESS TO THE GLOBAL INTERNET FROM A DEVICE THAT FITS IN OUR POCKETS, THE UNDERLYING PRINCIPLES REALLY HAVEN’T MOVED ON SO, WHAT WE CAN ALL DO ABOUT THIS? WHAT HOPE IS THERE FOR ALL OF US TO BE ABLE TO STILL SEE CUTE CAT VIDEOS ONLINE WITHOUT BEING HACKED INTO OBLIVION?

JOIN THIS ENGAGING TALK AS WE DELVE INTO THE DYNAMIC WORLD OF A PURPLE TEAMER, NAVIGATING THE INTRICATE BALANCE BETWEEN OFFENSE AND DEFENSE IN THE REALM OF CYBERSECURITY.
THROUGH REAL-WORLD ANECDOTES AND PRACTICAL INSIGHTS, THIS SESSION PROMISES AN IMMERSIVE EXPLORATION OF THE CHALLENGES, STRATEGIES, AND IMPACTFUL COLLABORATIONS THAT DEFINE A TYPICAL DAY IN THE LIFE OF A PURPLE TEAMER
ATTENDEES WILL GAIN PRACTICAL INSIGHTS INTO THE DAY-TO-DAY OPERATIONS OF A PURPLE TEAMER, UNDERSTANDING THE STRATEGIC DECISIONS AND COLLABORATIVE EFFORTS THAT CONTRIBUTE TO A RESILIENT CYBERSECURITY POSTURE
AN INTRODUCTION TO PURPLE TEAMING:
DEFINING THE ROLE OF A PURPLE TEAMER AND ITS PIVOTAL POSITION IN CYBERSECURITY
HIGHLIGHTING THE FUSION OF RED AND BLUE TEAM METHODOLOGIES FOR COMPREHENSIVE SECURITY
THREAT MODELING AND ASSESSMENT:
DEEP DIVE INTO THE PROACTIVE IDENTIFICATION OF THREATS AND VULNERABILITIES.
THE ART OF SIMULATING REAL-WORLD ATTACKS IN COLLABORATION WITH THE RED TEAM
LIVE PENETRATION TESTING:
ILLUSTRATING THE HANDS-ON APPROACH TO PENETRATION TESTING, EMPLOYING CUTTING-EDGE TOOLS
THE CRUCIAL ROLE OF PURPLE TEAMERS IN TRANSLATING OFFENSIVE FINDINGS INTO ACTIONABLE DEFENSE STRATEGIES
INCIDENT RESPONSE DRILLS:
REAL-WORLD SIMULATIONS TO TEST AND REFINE INCIDENT RESPONSE CAPABILITIES.
THE IMPORTANCE OF AGILE RESPONSES TO EMERGING THREATS AND VULNERABILITIES
SECURITY AWARENESS INITIATIVES:

KEY TAKEAWAYS INCLUDE ACTIONABLE STRATEGIES FOR THREAT IDENTIFICATION, INCIDENT RESPONSE OPTIMISATION, AND FOSTERING A SECURITY-CONSCIOUS CULTURE

PRINCIPALINCIDENTRESPONSE NORM
CRAFTING AND DELIVERING ENGAGING SECURITY AWARENESS TRAINING SESSIONS
FOSTERING A CULTURE OF CYBERSECURITY MINDFULNESS ACROSS THE ORGANISATION
CONTINUOUS MONITORING EXCELLENCE:
IMPLEMENTING AND FINE-TUNING CONTINUOUS MONITORING SOLUTIONS
COLLABORATIVE EFFORTS WITH SIEM TEAMS FOR EFFECTIVE THREAT DETECTION AND RESPONSE
DOCUMENTATION AND REPORTING MASTERY:
THE ART OF DOCUMENTING FINDINGS AND IMPROVEMENTS FOR ORGANISATIONAL LEARNING
CRAFTING COMPREHENSIVE REPORTS TO COMMUNICATE INSIGHTS AND RECOMMENDATIONS TO LEADERSHIP
CHRISTOPHER SARA ANSTE SARA ANSTE DIRECTOROFDATAAN NOVACO
SARA ANSTE SARA ANSTE DIRECTOROFDATAAN NOVACO







THE
LADYBIRD BOOK OF QUANTUM: EVERYTHING YOU WILL EVER NEED TO KNOW (AND SOME STUFF YOU PROBABLY DON'T)
AN INTRODUCTION TO ALL THINGS QUANTUM SECURITY THAT EVERYONE WILL BE ABLE TO UNDERSTAND THIS TALK WILL COVER....
WHAT DOES QUANTUM MEAN?
WAVES, CATS AND ENTANGLEMENTTHE FUNDAMENTALS HOW IT WORKS:
QUANTUM COMPUTERS HOW THEY WORK
CRYPTOGRAPHY THE PROBLEM WITH QUANTUM
FIGHTING QUANTUM WITH QUANTUMQKD
THE RACE TO FIND AN UNSOLVABLE PROBLEM - PQC
WHAT'S NEXT AND SHOULD YOU BE WORRYING ABOUT IT?

 FREY WILSON FREY WILSON
FREY WILSON FREY WILSON


PRONOUNS: SHE/THEY
JOB TITLE: CYBER SECURITY ANALYST COMPANY NAME: E2E-ASSURE LTD
EVER WONDERED HOW A SOC ANALYST TAKES AN ALERT TO AN INCIDENT, AND JUST WHAT THE HECK THEY DO ABOUT IT?
THIS TALK WALKS THROUGH THE PROCESS OF TAKING AN ALERT THROUGH TRIAGE, ANALYSIS, AND RAISING TO AN INCIDENT ALL THE WAY TO NOTIFCIATION, INVESTIGATION, & REMEDIATION.
THIS INVOLVES A REAL-WORLD EXAMPLE OF OPPORTUNISTIC MALWARE FROM 2022 AS THE MAIN CASE STUDY, BUT THE NARRATIVE PRESENTED WILL BE FICTITIOUSFROM THE PERSPECTIVE OF A SOC ANALYST INTERNAL TO A COMPANY,
WITH ACCESS TO FAR MORE OPTIONS THAN AN ANALYST WITH A SOC-AS-A-SERVICE OR MSSP MIGHT HAVE. WE’RE AIMING FOR BEST CASE SCENARIO HERE - AND YOU GET TO JOIN IN THE FUN! THINK OF THIS PROCESS LIKE A MURDER MYSTERY, EXCEPT THERE’S COMPUTERS AND NO DEAD BODIES (WE HOPE) GRAB A DRINK, GRAB A BISCUIT, AND LET’S GET NOSY IN THESE LOGS.
THE TALK TAKES A HIGH-LEVEL VIEW SEVERAL FACETS OF DIGITAL FORENS AND INCIDENT RESPONSE INCLUD CYBER INTELLIGENCE
THE AIM IS TO PROVIDE A WELL-ROUN INTRODUCTION TO THE MYSTERI WORLD OF DFIR AND HAVE THE AUDIE TAKE AWAY KEY CONCEPTS EXAMPLES FOR THEM DIG INTO LATER
GRASPING THE ESSENTIALS OF DIG FORENSICS AND INCIDENT RESPO (DFIR) IS INCREASINGLY CRITICAL AS CYBER WORLD CONTINUES TO EVO WITH AI CAUSING MUCH DISRUPTION QUANTUM COMPUTING JUST AROUND CORNER
RORY WAGNER, A SENIOR INVESTIGA AT CYBERCX UK, WILL LEVERAGE BROAD EXPERIENCE IN DFIR TO PRES THE WORKSHOP "DFIR 101"
SENIOR INVESTIGATOR CYBERCX
THIS SESSION SEEKS TO CLARIFY THE INTRICATE REALM OF DIGITAL FORENSICS AND EQUIP PARTICIPANTS WITH A ROBUST FOUNDATION FOR MANAGING CYBER INCIDENTS RORY'S WORKSHOP WILL ADDRESS THE FUNDAMENTAL ASPECTS OF DFIR, BEGINNING WITH THE BASICS OF EXECUTING THOROUGH FORENSIC EXAMINATIONS ACROSS A VARIETY OF DIGITAL DEVICES AND SYSTEMS.
ATTENDEES WILL DISCOVER THE TOOLS AND TECHNIQUES FOR IDENTIFYING, PRESERVING, AND ANALYSING ELECTRONIC EVIDENCE, ENCOMPASSING DIGITAL ARTEFACTS, NETWORK LOGS, AND SYSTEM LOGS THIS PRACTICAL WORKSHOP WILL STEER PARTICIPANTS THROUGH THE STEPS OF REVEALING EVIDENCE OF CYBER-ATTACKS OR DATA BREACHES.
RORY WILL HIGHLIGHT THE SIGNIFICANCE OF COLLABORATION AMONG CROSSFUNCTIONAL TEAMS AND STAKEHOLDERS DURING INCIDENT RESPONSE. PARTICIPANTS WILL OBTAIN INSIGHTS INTO ORCHESTRATING RESPONSE EFFORTS, OFFERING ADVICE ON TECHNICAL ISSUES, AND COMPILING DETAILED REPORTS THAT ENCAPSULATE THE FINDINGS OF INVESTIGATIONS
AIMED NOT JUST AT TRANSFERRING TECHNICAL SKILLS BUT ALSO AT MOTIVATING ATTENDEES TO FURTHER THEIR UNDERSTANDING OF DIGITAL FORENSICS AND INCIDENT RESPONSE, THIS WORKSHOP IS INTENDED FOR BOTH NEWCOMERS TO THE FIELD AND THOSE WISHING TO UPDATE THEIR SKILLS



PRONOUNS: THEY/THEM SECURITY RESEARCHER AT CROWDSTRIKE. ALSO GOES BY THEHACKERWITCH
INTERESTED IN COMPETITIVE HACKING? IF SO, THIS SESSION IS FOR YOU! WE WILL EXPLORE CAPTURE THE FLAG (CTF) COMPETITIONS FROM THE GROUND UP. NO PRIOR KNOWLEDGE REQUIRED
THE TALK WILL BE DELIVERED AS BITESIZED HANDS-ON EXERCISES WHERE PARTICIPANTS WILL LEARN, UNDERSTAND, AND COLLABORATIVELY SOLVE PROBLEMS WE WILL COVER COMMON TECHNIQUES TO APPROACH CATEGORIES SUCH AS PASSWORD CRACKING, WEB EXPLOITATION, AND FORENSICS
YOU WILL LEAVE THIS TALK WITH A FRAMEWORK TO SOLVE HACKING PROBLEMS, AN ARSENAL OF DYNAMIC TOOLING, AND A NEW-FOUND CONFIDENCE TO APPROACH CTF CHALLENGES





WE’LL BE DELVING INTO THE PROCESS THAT TAKES PLACE BETWEEN HITTING COMPILE AND GETTING AN EXECUTABLE, AND SOME OF THE SECURITY IMPLICATIONS OF COMPILATION
FROM LEXING AND PARSING TO OPTIMISATION AND CODE GENERATION, WE’LL COVER THE COMPILATION PIPELINE FROM START TO FINISH AND EXPLAIN EACH STEP, AND ALSO TALK ABOUT MALICIOUS COMPILERS AND REMEDIATIONS FOR THEM SUCH AS DIVERSE DOUBLE COMPILATION.
EVER WANTED TO KNOW WHAT HAPPENS BETWEEN HITTING COMPILE AND HAVING AN EXECUTABLE? THIS TALK WILL COVER THE PROCESS THAT TAKES PLACE TO TURN YOUR SOURCE CODE INTO MACHINE CODE WE'LL BREAK DOWN THE PROCESS FROM HOW THE WHOLE COMPILATION PIPELINE TAKES PLACE TO PARSING IN DETAIL, AND FINALLY TALK ABOUT SUPPLY CHAIN ATTACKS RELATED TO COMPILATION AND MITIGATIONS FOR THEM

THE MAIN POINTS COVERED ARE ABOUT LEXING, PARSING, SEMANTIC ANALYSIS, OPTIMISATION AND CODE GENERATION PARSING AND FORMAL GRAMMARS ARE COVERED IN GREATER DETAIL DUE TO HOW COMPLEX THEY ARE
WE BREAK DOWN HOW THE FORMAL GRAMMAR FOR JSON WORKS TO PROVIDE A REAL WORLD EXAMPLE THAT THE AUDIENCE SHOULD BE ABLE TO RELATE TO, AS WELL AS HOW GRAMMAR AND PARSING APPLIES TO NATURAL LANGUAGE RECURSIVE DESCENT AND LR PARSERS WILL BE COVERED, WITH EXPLANATIONS OF HOW PARSING TREES ARE GENERATED AND HOW IT INTERPRETS A FORMAL GRAMMAR
WE'LL FINALLY THEN MOVE ONTO AN ATTACK FIRST DESCRIBED IN KEN THOMPSON'S 1984 PAPER, REFLECTIONS ON TRUSTING TRUST, WHICH IS ABOUT HOW A MALICIOUS COMPILER COULD BE USED TO ALTER THE CODE GENERATED AND CAUSE IT TO BE MALICIOUS REAL WORLD EXAMPLES OF THIS INCLUDE MICROSOFT VISUAL STUDIO'S C/C++ COMPILER INSERTING CODE TO GIVE MICROSOFT TELEMETRY FROM CODE COMPILED USING IT, WHICH TOOK PLACE IN 2015 AND DISPLAYS HOW THESE VULNERABILITIES MIGHT ACTUALLY BE EXPLOITED OUTSIDE AN ACADEMIC CONTEXT
SUCH EXAMPLES WILL BE DISCUSSED, AS WELL AS REMEDIATION I PLAN ON TALKING ABOUT DIVERSE DOUBLE COMPILATION, WHICH IS A METHOD OF VERIFYING COMPILERS OF THE SAME FAMILY TO ENSURE THAT UNDUE CHANGES HAVEN'T BEEN MADE, AND WE'LL DISCUSS SOME OF THE EXAMPLES IN KEN'S ORIGINAL PAPER SUCH AS MODIFYING C TO ADD AN ESCAPE SEQUENCE FOR VERTICAL TABS, TO DEMONSTRATE HOW SUCH MODIFICATIONS COULD BE MADE.
THE TALK IS DESIGNED SO THAT ANYONE CAN TAKE SOMETHING AWAY FROM IT WITH EXAMPLES THAT EXPLAIN PARSING WITHOUT ANY CODE, ALTHOUGH A LITTLE BIT OF PROGRAMMING EXPERIENCE DOES HELP BY THE END, YOU SHOULD HAVE A BETTER UNDERSTANDING OF HOW CODE GETS COMPILED AND SOME OF THE SECURITY IMPLICATIONS OF IT


CYBER FRAUD LANDSCAPE IS CONSTANTLY EVOLVING THIS TALK COVERS THE LANGUAGE AND TERMINOLOGY IN THE FRAUD LANDSCAPE. "STEREOTYPES" OF FRAUD THREAT ACTORS, REVEALING OTHERS WHICH TYPICALLY ISN'T CONSIDERED
HOW FRAUD THREAT ACTORS RECRUIT AND THE MOTIVATIONS BEHIND GETTING ACTIVE IN LANDSCAPE.
THE TARGETING OF VICTIMS AND CONSIDERATIONS WHEN TARGETING AREAS MARKETPLACES AND LOCATIONS TO FIND FRAUD ACTIVITY.
THE VARIOUS TYPES OF FRAUD CAMPAIGNS. HIGHLIGHTING THE FUTURE POTENTIAL FOR FRAUD CAMPAIGNS WITH AI AND SOPHISTICATION AMONGST THREAT ACTORS
CYBER FRAUD LANDSCAPE, BREAKING DOWN MODERN FRAUD TERMINOLOGY SEEN IN USE BY THREAT ACTORS. DISCUSSING THE RECRUITMENT PROCESS FOR FRAUD THREAT ACTORS HOW MORE ESTABLISHED THREAT ACTORS GROOM KIDS INTO FRAUD LANDSCAPE LATER EXPANDING INTO RECRUITMENT OF THEIR OWN FRIENDS
MOTIVATIONS BEHIND A CHILD BECOMING A FRAUDSTER, LACK OF IDENTITY, ETC. VICTIMS OF FRAUD, WHY CERTAIN DEMOGRAPHICS ARE LESS TARGETED COMPARED TO OTHERS, DISCUSSING THE STEREOTYPICAL FRAUDSTERS PUBLIC THINK OF AND OTHER'S THEY DON'T CONSIDER, DISCUSSIONS OF MARKETPLACES AND PLATFORMS WHICH FRAUD IS CARRIED OUT AND SOLD, SUCH AS TELEGRAM, XSS ETC. TALK AROUND CYBER SCAMS EXPLAINING THE PURPOSES AND HOW THEY OPERATE.
I ALSO WILL BE DISCUSSING WHY CYBER SECURITY PROFESSIONALS NEED TO BE AWARE OF FRAUD LANDSCAPE WITH THE RISE OF SOPHISTICATION BEHIND THREAT ACTORS' CAMPAIGNS, SUCH AS THE USE OF MALWARE AND PROXIES. I ALSO DISCUSS THE ADOPTION OF DEEPFAKE TECHNOLOGY AND AI IN PERFORMING CAMPAIGNS, SOFTWARE BEING SOLD ON MARKETPLACES AND WEAPONISED.

TTXS ARE OFTEN PERCEIVED AS LABORIOUS, COMPLEX TASKS THIS TALK SIMPLIFIES THE PROCESS INTO MANAGEABLE STEPS, DEMYSTIFYING TTXS AND EMPOWERING YOU TO CONDUCT YOUR OWN!
WHY ATTEND MY TALK?
YOU'LL RECEIVE A CONCISE GUIDE ON CONDUCTING INTERNAL TTXS AND GAIN ACCESS TO OUR DOWNLOADABLE DIY TTX LITE PACK, WHICH WILL ENABLE YOU TO...
1 PLAN AND EXECUTE YOUR OWN TTX
2 ANALYSE AND INTERPRET THE RESULTS EFFECTIVELY
3 COMPARE YOUR DIY APPROACH TO TSC'S BESPOKE PROFESSIONAL TTX
4 WALK AWAY EMPOWERED WITH THE TOOLS AND KNOWLEDGE TO IMPLEMENT IMPACTFUL TABLETOP EXERCISES WITHIN YOUR ORGANISATION.

TABLETOP EXERCISES, WHEN EXECUTED EFFECTIVELY, ARE AN ENGAGING AND INVALUABLE METHOD FOR GAINING INSIGHTS INTO PAST FAILURES, ASSESSING CURRENT DEFENCES, AND FORECASTING FUTURE OUTCOMES JUST AS WARS ARE WON THROUGH STRATEGIC PLANNING AND RIGOROUS TESTING, EVEN THE SMALLEST BATTLES CAN BE LOST WHEN CAPABLE TEAMS LACK DIRECTION
WHILE MANY COMPANIES OFFER TTX SERVICES, FEW DELIVER THEM WELL. OUR RESEARCH SHOWS US THAT MANY PROVIDERS CHARGE EXORBITANT FEES, FAIL TO CUSTOMISE EXERCISES, AND LACK A CLEAR UNDERSTANDING OF WHAT EXCELLENCE LOOKS LIKE
IN THIS TALK, WE WILL DEMYSTIFY THE TTX PROCESS AND PRESENT A STREAMLINED, COST-EFFECTIVE VERSION YOU CAN IMPLEMENT YOURSELF BY FOLLOWING THE TSC "TTX LITE" APPROACH, YOU'LL GATHER CRUCIAL INTELLIGENCE, REFINE YOUR STRATEGIES, AND ENSURE YOUR TEAM NOT ONLY STAYS IN THE FIGHT BUT ULTIMATELY WINS JOIN ME TO EMPOWER YOUR ORGANISATION WITH THE SKILLS AND KNOWLEDGE TO CONDUCT YOUR OWN SUCCESSFUL TABLETOP EXERCISES.
THIS TALK WILL HAVE A QR CODE LINKING TO THE FREE PACK WHICH INCLUDES:
A. TSC TTX PLANNER LITE VERSION
B TSC TTX TRACKER LITE VERSION
C TSC TTX RULE EBOOK


IN MY TALK “UNRAVELLING RANSOMWARE: STRATEGIES FOR EFFECTIVE INVESTIGATION”
I'LL ADDRESS THE SHARP RISE IN RANSOMWARE INCIDENTS, PROVIDING A GUIDE ON HOW TO CONDUCT INVESTIGATIONS OUTLINES THE PROCESS OF TRACING A RANSOMWARE ATTACK FROM THE FINAL PAYLOAD TO THE INITIAL BREACH, EXPLAINING KEY INVESTIGATION STAGES SUCH AS IDENTIFYING POINT OF ENTRY, CREDENTIAL THEFT, AND THREAT ACTOR ATTRIBUTION
DESIGNED TO DEMYSTIFY CYBERSECURITY INVESTIGATIONS, THE SESSION IS DESIGNED EQUIPS PARTICIPANTS WITH THE KNOWLEDGE TO BOTH PREVENT AND RESPOND TO THESE INCREASING CYBER THREATS
RANSOMWARE LOOMS LARGER THAN EVER; HAVING ESCALATED BY A STAGGERING 73% IN 2023 ALONE, AND COMBINING THIS WITH THE SOPHOS REPORT LAST YEAR, 66% OF COMPANIES WERE HIT BY RANSOMWARE (REPORT DATES 2022) THIS HIGHLIGHTS THE GROWING SOPHISTICATION OF CYBER ADVERSARIES BUT ALSO SIGNALS A CALL FOR BUT ALSO SIGNALS A CALL FOR THE CYBERSECURITY COMMUNITY TO UNDERSTAND THE INVESTIGATIVE PROCESS OF RANSOMWARE.
IT IS AGAINST THIS BACKDROP THAT MY TALK, TITLED "HOW TO INVESTIGATE YOUR FIRST RANSOMWARE," AIMS TO ARM ASPIRING CYBERSECURITY PROFESSIONALS WITH KNOWLEDGE ON HOW RANSOMWARE INVESTIGATIONS ARE CARRIED OUT, AND THE KEY STAGES IN THE INVESTIGATIONS MY MOTIVATION FOR DELIVERING THIS PRESENTATION IS ROOTED IN THE REALITY THAT ATTENDEES MIGHT, IN THE FUTURE, FIND THEMSELVES EITHER PARTICIPATING IN A RANSOMWARE INVESTIGATION OR MANAGING POST-INCIDENT ACTIONS UNDERSTANDING THE INTRICATE WORKINGS OF SUCH INVESTIGATIONS, THE TACTICS OF RANSOMWARE OPERATORS AND THE PROCESS OF PROBING THESE CYBER INCIDENTS IS CRITICAL.
WITH THIS KNOWLEDGE, PARTICIPANTS WILL NOT ONLY BE EQUIPPED TO IMPLEMENT PREVENTATIVE MEASURES AGAINST SUCH ATTACKS BUT WILL ALSO BE BETTER PREPARED TO RESPOND EFFECTIVELY SHOULD THEY BECOME THE TARGET OF RANSOMWARE THIS INSIGHT IS PIVOTAL FOR CULTIVATING A PROACTIVE STANCE AGAINST CYBER THREATS, ENSURING THAT INDIVIDUALS AND ORGANIZATIONS ARE WELL-POSITIONED TO SAFEGUARD THEIR DIGITAL ASSETS AGAINST THE EVER-EVOLVING LANDSCAPE OF CYBERCRIME
THIS PRESENTATION IS DESIGNED TO DEMYSTIFY THE PROCESS OF RANSOMWARE INVESTIGATION, WHERE I WILL RETRACE THE STEPS UNDERTAKEN BY THREAT ACTORS I WILL DO THIS IN A REVERSE CHRONOLOGICAL ORDER AS INVESTIGATIONS WORK IN REVERSE ORDER, STARTING FROM THE MOST RECENT EVIDENCE OF A SECURITY INCIDENT AND TRACES THE SEQUENCE OF EVENTS BACKWARDS THROUGH INTERCONNECTED PIECES OF DIGITAL EVIDENCE, TO UNCOVER THE ROOT CAUSE AND METHOD OF THE ATTACK MY GOAL IS FOR PARTICIPANTS TO GAIN AN UNDERSTANDING OF THE ATTACK'S ANATOMY, FROM FINAL PAYLOAD DELIVERY TO INITIAL BREACH THIS METHODICAL BACKTRACK IS NOT JUST A TECHNICAL ENDEAVOUR BUT A STRATEGIC ONE, OFFERING INSIGHTS INTO THE ATTACKER'S MINDSET, TACTICS, AND OBJECTIVES
THE SESSION WILL COVER A BREADTH OF TOPICS CRUCIAL FOR A ROUNDED INVESTIGATION, INCLUDING IDENTIFYING INITIAL INFECTION VECTORS, CREDENTIAL THEFT, PERSISTENCE MECHANISMS, PRIVILEGE ESCALATION, LATERAL MOVEMENT, EXFILTRATION, C2, RANSOMWARE DEPLOYMENT AND THREAT ACTOR ATTRIBUTION ADDITIONALLY I WILL SHARE PRACTICAL TIPS ON PRESERVING EVIDENCE AND LEVERAGING FORENSIC TOOLS THE PRESENTATION IS SOMEWHAT TECHNICAL TO GIVE REAL WORLD EXAMPLES OF WHAT IS HAPPENING AND HOW WE TRACK THIS, BUT KEEPING THE LEVEL BROAD ENOUGH FOR A WIDER AUDIENCE.
INVESTIGATING A RANSOMWARE CAN BE A HUGE UNDERTAKING WITH MANY ASPECTS THIS IS PRIMARILY FOCUSED ON TECHNICAL INVESTIGATION BUT I WILL TOUCH ON HOW THIS INFORMS OTHER PARTS OF THE INCIDENT I HAVE A GENUINE PASSION AND EXCITEMENT IN THIS FIELD OF WORK, BUT I FEEL FOR MANY THIS IS DONE BEHIND A VEIL OF SECRECY OR MYSTICISM EVEN FOR SOME WITHIN THE SPHERE OF INFORMATION SECURITY SO I WOULD LIKE SHINE A LIGHT INTO THE SHADY WORLD OF RANSOMWARE

THIS PRESENTATION DRAWS ON OVER 10 YEARS OF LANGUAGE TEACHING EXPERIENCE AND METHODOLOGY TO PRESENT A STRUCTURAL WALK-THROUGH OF A WORKSHOP DESIGNED TO ADDRESS A GAP IN PHISHING SIMULATIONS
IT AIMS TO OFFER AN ALTERNATIVE, MORE ENJOYABLE, APPROACH TO SECURITY AWARENESS TRAINING
THIS TALK IS BASED ON A WORKSHOP I CREATED AND GAVE AT A PREVIOUS EMPLOYER WE STARTED DOING PHISHING SIMULATIONS BUT DUE TO ETHICAL PERIMETERS OF NOT WANTING TO BURN BRIDGES WITH CRUEL PHISHING EMAILS LIKE THOSE MAKING THE NEWS, THERE WAS A GAP BETWEEN OUR SIMULATED AND VERY OBVIOUS PHISHING EMAILS AND MORE CHALLENGING ONES THAT WERE POTENTIALLY MORE LIKELY TO BE USED
I HAVE A BACKGROUND IN TEACHING ENGLISH TO ADULTS, SO I DESIGNED A WORKSHOP WITH TEACHING PRINCIPLES IN MIND, WITH

THE AIM OF PARTICIPANTS CREATING THEIR OWN PHISHING EMAILS THAT TARGETED THEIR OWN FUNCTIONS PARTICIPANTS WERE INTRODUCED TO THE EMOTIONAL TRIGGERS SEEN IN PHISHING EMAILS USING PREDICTION TASKS ALONGSIDE JENNY RADCLIFF STORIES TO START THINKING CREATIVELY AND GENERATE ENGAGEMENT AND INTEREST
THEY WERE THEN GIVEN GENUINE EXAMPLES OF PHISHING EMAILS TO CATEGORISE USING THESE DIFFERENT TRIGGERS (I E AUTHORITY, PANIC) AND DISCUSSED EXAMPLES THEY WERE AWARE OF WITH THE AIM OF MAKING THE TASK RELEVANT TO THEMSELVES/FAMILY/FRIENDS FINALLY, THE OUTPUT TASK WAS TO WRITE PHISHING EMAILS THAT WOULD TARGET THEIR BUSINESS AREA BEFORE DOING SO, THERE WAS A REVIEW OF THE ADDITIONAL FEATURES IN AN EMAIL, FOR EXAMPLE, THE SENDING EMAIL ADDRESS, ANY LINKS, OR THE TIME OF DAY THEY WOULD BE SENT - RAISING AWARENESS OF THE ADDITIONAL ASPECTS OF A PHISHING EMAIL THIS ASPECT WAS GAMIFIED, AND THE “EVALUATION” OF THE BEST EMAIL WAS DONE BY ROTATING THE EMAILS THROUGH PARTICIPANTS AND AWARDING POINTS FOR CREATIVITY AND POTENTIAL EFFECTIVENESS
THIS CLOSED THE SESSION WITH A “WINNER” AND ALSO EXPOSED THE PARTICIPANTS TO DIFFERENT PHISHING EMAILS DESIGNED TO ATTACK THEIR OWN FUNCTIONS THAT WE, AS A SECURITY TEAM, COULDN’T USE IN A PHISHING SIMULATION I HAVE PREVIOUSLY ATTEMPTED TO DO THIS SESSION AT OTHER CONFERENCES, BUT WHILE I WAS AT THE PREVIOUS WORKPLACE I FACED BARRIERS TO GET THE PRESENTATION OVER THE LINE IN TERMS OF BRANDING AND OWNERSHIP OF THE CONTENT I THINK, THEREFORE, INSTEAD OF DOING THE WORKSHOP, IF I TALK THROUGH THE ACTUAL DESIGN AND AIMS OF THE STAGES IT WOULD MITIGATE THE BARRIER I FACED PREVIOUSLY
AS SUCH, THIS PRESENTATION WOULD INVOLVE MORE STRUCTURAL EXPLANATIONS OF HOW AND WHY IT WAS DESIGNED, LEANING ON TEACHING PEDAGOGY AND STRUCTURE. I ALSO REALISED, WHEN I PASSED THE WORKSHOP ON, THAT I HAD NOT EXPLAINED WHY I HAD STRUCTURED THE WORKSHOP AS I DID AND NOTICED THAT IT WAS REVERTED BACK TO SOME STRUCTURES THAT I HAD SPECIFICALLY AVOIDED - I.E. LECTURE VS WORKSHOP STRUCTURES. THE ABOVE WOULD FORM THE STRUCTURE OF MY PRESENTATION WITH ADDITIONAL LESSONS LEARNED ON HOW IT COULD HAVE FIT INTO A BROADER PROGRAM, THE CHALLENGES OF MEASURING “SUCCESS”





A collection of hands-on retro security, retro computing and retro gaming exhibits from various members of the community.
Everything from learning to blue box like an 80s phone phreak to the best of Amiga demoscene to getting a high score on free ski or Win 95 Pinball.
find us in the Wool Room



A chance for you to try driving a ship and shooting a zombie or three...
kindly Provided by PENTEST PARTNERS






FIND US IN THE WOOL ROOM!




Running from 10:30am Seamstress Suite 2 x talk slots at 4pm

LOCK PICKING AND SAFE CRACKING GENEROUSLY PROVIDED BY KSEC



Minty (and Team) has always provided the Car Hacking Village at BSides Leeds since its inception. Minty and the Car Hack Team will be greatly missed this year! We look forward to welcoming them being back at BSides Leeds in 2025. #FuckCancer
At the request of Minty the charity this year will be...


To our fabulous speakers, volunteers, and sponsors,
We want to extend a massive thank you to each and every one of you for your incredible contributions to BSides Leeds 2024. We couldn't have done it without you!
Speakers - Your expertise, passion, and captivating presentations made the conference truly unforgettable. You shared invaluable insights and inspired us all. Thank you for taking the time to be a part of this event and making it a resounding success.
Volunteers - Your dedication and tireless efforts behind the scenes were the glue that held everything together. From assisting with logistics to ensuring attendees felt welcomed, your support was absolutely essential. We appreciate your hard work and the positive energy you brought to the conference.
Sponsors - Your generous support and belief in our vision made this event possible. Your contributions allowed us to create an enriching experience for all participants. We are deeply grateful for your partnership and the impact it had on the success of the conference.

Thank you once again for making BSides Leeds 2023 an outstanding success.
With heartfelt appreciation,

A massive shout out and huge thank you to our fabulous MVP Cooper, the amazing videographer who films countless BSides conferences across Europe and the UK. These conferences wouldn't be the same without your incredible work!
All of the videos from BSides Leeds 2024 will be available after the conference on our youtube page!



A MASSIVE THANK YOU TO OUR



















BSIDESLEEDSSPACESINCLUDETHEEVENT,WORKSHOPSANDASSOCIATED PARTIES.THESEAREINCLUSIVEPLACESWHEREALLPEOPLESHOULDFEEL SAFEANDRESPECTED.
WEWELCOMEDIVERSITYINAGE,RACE,ETHNICITY,NATIONALORIGIN,RANGE OFABILITIES,SEXUALORIENTATION,GENDERIDENTITY,FINANCIALMEANS, EDUCATION,ANDPOLITICALPERSPECTIVE.WEWANTYOUTOENJOYASAFE ANDRESPECTFULENVIRONMENT.WEWILLNOTTOLERATEANYFORMOF HARASSMENT,HATESPEECHORTROLLINGEITHEROFFORONLINE,ORANY OVERLYDRUNKEN,INTIMIDATING,HECKLINGORVIOLENTBEHAVIOURIN BSIDESLEEDSSPACES.HARASSMENTCANBEEITHERVERBAL,WRITTEN, BEHAVIOURALORIMAGERYANDINCLUDESANYRACIST,HOMOPHOBIC, TRANSPHOBIC,SEXIST,SEXUALLYINAPPROPRIATEORRELIGIOUSLY DISCRIMINATORYLANGUAGE,BEHAVIOURORIMAGERY.“JOKES”,“BANTER” AND“FREEDOMOFSPEECH”WILLNOTBEACCEPTEDASJUSTIFICATIONSOR EXCUSEFORSUCHLANGUAGE,BEHAVIOURORIMAGERY.
WEAREGUESTSOFTHEVENUESWEUSE,SOPLEASEBERESPECTFUL.DON’T TAMPERWITHFIXTURES,HARDWARE,SOFTWAREORINFRASTRUCTURE,OR GENERALLYTAKETHINGSSUCHAFOODANDDRINKWITHOUT PERMISSION.PLEASERESPECTTHEPRESENTERS,THEYAREDONATINGTHEIR TIMETOMAKETHISEVENTPOSSIBLE.PLEASEDON’TTALKAMONGST YOURSELVESDURINGTHEIRPRESENTATIONS,HAVEYOURPHONESEITHER MUTEDORSWITCHEDOFFANDBEAWARETHATTHISISAGROUPACTIVITY.WE CANNOTPOLICETHEBEHAVIOUROFATTENDEESOUTSIDETHESESPACES, HOWEVERWEWILLDOEVERYTHINGWECANTOHELPMEMBERSRESOLVEANY ISSUESTHATMAYOCCUROUTSIDEOURSPACESDURINGTHECOURSEOFTHE EVENT.
IFYOUHAVEANYISSUESORCONCERNSRELATINGTOTHECODEOF CONDUCTPLEASECONTACTONEOFTHEVOLUNTEERSINPERSONORONEOF THEORGANISERSBYEMAILORTWITTER.THEVOLUNTEERSWILLBEWEARING BSIDESLEEDSVOLUNTEERT-SHIRTSATTHEEVENT.
ed has been generously Sponsored by
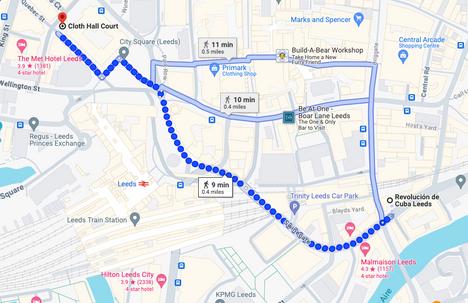
join us at
Revolución de Cuba
64-68 Call Lane, Leeds, LS1 6DT for food & drinks!