Applicationsof ComputationalIntelligence inMulti-Disciplinary
Research
Editedby
AhmedA.Elngar FacultyofComputersandArtificialIntelligence,Beni-SuefUniversity,Beni-SuefCity,Egypt CollegeofComputerInformationTechnology,AmericanUniversityintheEmirates, UnitedArabEmirates
RajdeepChowdhury DepartmentofComputerApplication,JISCollegeofEngineering,Kalyani,WestBengal,India
MohamedElhoseny CollegeofComputingandInformatics,UniversityofSharjah,UnitedArabEmirates FacultyofComputersandInformation,MansouraUniversity,Egypt
ValentinaEmiliaBalas
DepartmentofAutomaticsandAppliedSoftware,FacultyofEngineering, “AurelVlaicu”UniversityofArad,Arad,Romania
SeriesEditor
ValentinaEmiliaBalas
DepartmentofAutomaticsandAppliedSoftware,FacultyofEngineering, “AurelVlaicu”UniversityofArad,Arad,Romania
AcademicPressisanimprintofElsevier 125LondonWall,LondonEC2Y5AS,UnitedKingdom 525BStreet,Suite1650,SanDiego,CA92101,UnitedStates 50HampshireStreet,5thFloor,Cambridge,MA02139,UnitedStates TheBoulevard,LangfordLane,Kidlington,OxfordOX51GB,UnitedKingdom
Copyright©2022ElsevierInc.Allrightsreserved.
Nopartofthispublicationmaybereproducedortransmittedinanyformorbyanymeans,electronicormechanical,including photocopying,recording,oranyinformationstorageandretrievalsystem,withoutpermissioninwritingfromthepublisher. Detailsonhowtoseekpermission,furtherinformationaboutthePublisher’spermissionspoliciesandourarrangementswith organizationssuchastheCopyrightClearanceCenterandtheCopyrightLicensingAgency,canbefoundatourwebsite: www.elsevier.com/permissions .
ThisbookandtheindividualcontributionscontainedinitareprotectedundercopyrightbythePublisher(otherthanasmaybe notedherein).
Notices
Knowledgeandbestpracticeinthisfieldareconstantlychanging.Asnewresearchandexperiencebroadenourunderstanding, changesinresearchmethods,professionalpractices,ormedicaltreatmentmaybecomenecessary.
Practitionersandresearchersmustalwaysrelyontheirownexperienceandknowledgeinevaluatingandusinganyinformation, methods,compounds,orexperimentsdescribedherein.Inusingsuchinformationormethodstheyshouldbemindfuloftheir ownsafetyandthesafetyofothers,includingpartiesforwhomtheyhaveaprofessionalresponsibility.
Tothefullestextentofthelaw,neitherthePublishernortheauthors,contributors,oreditors,assumeanyliabilityforanyinjury and/ordamagetopersonsorpropertyasamatterofproductsliability,negligenceorotherwise,orfromanyuseoroperationof anymethods,products,instructions,orideascontainedinthematerialherein.
BritishLibraryCataloguing-in-PublicationData
AcataloguerecordforthisbookisavailablefromtheBritishLibrary LibraryofCongressCataloging-in-PublicationData
AcatalogrecordforthisbookisavailablefromtheLibraryofCongress
ISBN:978-0-12-823978-0
ForInformationonallAcademicPresspublications visitourwebsiteat https://www.elsevier.com/books-and-journals
Publisher: MaraConner
AcquisitionsEditor: ChrisKatsaropoulos
EditorialProjectManager: IsabellaC.Silva
ProductionProjectManager: SelvarajRaviraj
CoverDesigner: GregHarris
TypesetbyMPSLimited,Chennai,India
Contents
Listofcontributorsix
1.Irisfeatureextractionusing three-levelHaarwavelettransform andmodifiedlocalbinary pattern1
PrajoyPodder,M.RubaiyatHossainMondaland JoarderKamruzzaman
Abbreviations1
1.1Introduction1
1.2Relatedworks3
1.3Irislocalization4
1.4Irisnormalization6
1.5Theproposedfeatureextraction scheme7
1.6Matchingresults11
1.7Performanceevaluation11
1.8Conclusion13 References14
2.Anovelcrypt-intelligent cryptosystem17
PratyusaMukherjeeand ChittaranjanPradhan
2.1Introduction17
2.2Relatedwork18
2.2.1Machinelearningcontributionsin cryptology18
2.2.2Geneticalgorithmcontributionsin cryptology20
2.2.3Neuralnetworkcontributionsin cryptology21
2.2.4BackgroundofDNAcryptography23
2.3Proposedmethodology23
2.3.1Proposedencryptionscheme24
2.3.2Proposeddecryptionscheme25
2.4Discussion25
2.5Conclusionandfuturework26 References26
3.Behavioralmalwaredetectionand classificationusingdeeplearning approaches29
T.Poongodi,T.LuciaAgnesBeena, D.SumathiandP.Suresh
3.1Introduction29
3.1.1Digitalforensics—malware detection30
3.1.2Malwareevolutionandits taxonomy32
3.1.3Machinelearningtechniquesfor malwareanalysis32
3.1.4Behavioralanalysisofmalware detection33
3.2Deeplearningstrategiesformalware detection35
3.2.1Featureextractionanddata representation35
3.2.2StaticAnalysis36
3.2.3Dynamicanalysis38
3.2.4Hybridanalysis38
3.2.5Imageprocessingtechniques38
3.3ArchitectureofCNNsformalware detection41
3.3.1Preprocessing41
3.3.2ClassificationusingCNNs41
3.3.3Evaluation42
3.4ComparativeanalysisofCNN approaches42
3.5Challengesandfutureresearch directions43
3.6Conclusion43 References43
4.Optimizationtechniquesand computationalintelligencewith emergingtrendsincloud computingandInternetofThings47
JayeshSVasudeva,SakshiBhargavaand DeepakKumarSharma
4.1Introduction47
4.1.1Introductiontooptimization48
4.1.2Introductiontocloudcomputingwith emphasisonfog/edgecomputing48
4.2Optimizationtechniques49
4.2.1Anoptimizationproblem49
4.2.2Solutiontotheoptimizationproblem52
4.3Understandingfog/edgecomputing54
4.3.1Whatisfog?54
4.3.2Preludetoourframework54
4.3.3Ourgoal55
4.3.4Frameworkforfogcomputing55
4.4Optimizingfogresources57
4.4.1Definingoptimizationproblemfor foglayerresources57
4.4.2Optimizationtechniquesused58
4.5Casestudies60
4.5.1CasestudyI:floorplanoptimization60
4.5.2CasestudyII:Gondwana— optimizationofdrinkingwater distributionsystem63
4.6Scopeofadvancementsandfuture research63
4.7Conclusion64 References65
5.Bluetoothsecurityarchitecture cryptographybasedongenetic codons67
AsifIkbalMondal,BijoyKumarMandal, DebnathBhattacharyyaandTai-HoonKim
5.1Introduction67
5.1.1Bluetooth67
5.1.2Bluetoothsecurityarchitecture67
5.2Surveyofliterature69
5.3Plaintext-to-ciphertextconversion process71
5.3.1Basicworkflow71
5.3.2Algorithm72
5.3.3Analysisanddiscussion78
5.4Conclusion79
5.5Futurework79 References80
6.Estimationofthesatellitebandwidth requiredforthetransmissionof informationinsupervisorycontrol anddataacquisitionsystems83 MariusPopescuandAntoanelaNaaji Abbreviations83
6.1Introduction84
6.2Supervisorycontrolanddataacquisition systems84
6.3Theverysmallapertureterminal networks87
6.3.1Thesatellitecommunication systems87
6.3.2Architectureverysmallaperture terminalnetworks89
6.3.3Connectivity92
6.3.4Multipleaccess93
6.4Algorithmforestimatingthesatellite bandwidth95
6.4.1Determiningthebandwidth requiredfordatatransmission95
6.4.2Casestudy98
6.4.3Overviewofsomerecent algorithmsindetail99
6.4.4Validationofbandwidth calculations104
6.5Challengesandfuturework106
6.6Conclusions107 References107
7.Usingartificialintelligencesearch insolvingthecameraplacement problem109
AltahirA.Altahir,VijanthS.Asirvadam, NorHishamB.HamidandPatrickSebastian Nomenclature109
7.1Introduction109
7.1.1Therolesofvisualsurveillance systems110
7.1.2Thecameraplacementproblem fromanartificialintelligence perspective111
7.1.3Chapterdescription112
7.2Background112
7.3Modelingthevisualsensors113
7.3.1Thesensorspacemodeling114
7.3.2Thecameracoveragemodeling114
7.3.3Theanalysisofcameravisibility115
7.4Solvingthecameraplacementproblem usingartificialintelligencesearch116
7.4.1Generateandtestalgorithm117
7.4.2Uninformedsearch118
7.4.3Hillclimbingstrategy119
7.5Furtherdiscussion121
7.5.1Theefficiencyofthealgorithms122
7.5.2Theperformanceofthealgorithms123
7.6Conclusion123 References124
8.Nanotechnologyandapplications129
KanikaDulta,AmanpreetKaurVirk, ParveenChauhan,ParasBoharaand PankajKumarChauhan
8.1Introduction129
8.2Nanoscienceandnanotechnology130
8.3Computationalnanotechnology130
8.3.1Molecularmodeling131
8.3.2Nanodevicesimulation133
8.3.3Nanoinformatics133
8.3.4High-performancecomputing135
8.3.5Computationalintelligence135
8.4Applicationsofcomputational nanotechnology137
8.4.1Nanotube-basedsensorsand actuators138
8.4.2Nanoinformaticsfordrugs138
8.4.3Moleculardocking138
8.4.4Nanotoxicology138
8.4.5Otherapplications139
8.5Conclusion139 References139
9.Advancesofnanotechnologyin plantdevelopmentandcrop protection143
RokeyaAkter,Md.HabiburRahman, Md.ArifurRahmanChowdhury, ManirujjamanManirujjamanand ShimaaE.Elshenawy
9.1Introduction143
9.2Agriculture’snanofarming:amodern frontier143
9.3Synthesisofgreennanoparticlesandits sources144
9.4Gooddistributionpossibilitiesallowed bynanoparticles:amodernsustainable agricultureportal145
9.5Nanofertilizers:agoodfoodsupplyfor crops146
9.6Germination,fieldproduction,and efficiencyenhancementofseed nanomaterials148
9.7Plantsensorysystemsandresponsesto radicalclimatechangeinfluences nanomaterials149
9.8Nanosensorsandnanomaterials: perturbationdetectionandcontrol150
9.9Pesticide-basedplantsafety nanomaterials150
9.10Nanotechnologyinpesticidesand fertilizers151
9.11Controlofplantpests152
9.12Concludingremarks152 Consentforpublication152 Conflictofinterest153 References153
10.Amethodologyfordesigning knowledge-basedsystemsand applications159
HienD.Nguyen,NhonV.Doand VuongT.Pham
10.1Introduction159 10.2Relatedwork160 10.3Designtheknowledge-basedsystem160 10.3.1Thearchitectureofa knowledge-basedsystem160 10.3.2Theprocessfordesigningthe knowledge-basedsystem162
10.4Knowledgebaseandinferenceengine ofaknowledge-basedsystem163 10.4.1Designtheknowledgebase163 10.4.2DesigntheInferenceengine164 10.5Applications168
10.5.1Designanintelligentproblem solverforsolvingsolidgeometry athighschool168
10.6ConclusionandFuturework183 References184
11.IoTinhealthcareecosystem187
PoonamGuptaandIndhraOmPrabhaM 11.1Introduction187 11.2ApplicationsofInternetofThingsin healthcare188
11.2.1Patient-centricIoT188 11.2.2Hospital-centricIoTapplications189 11.2.3IoTbenefittinghealthinsurance companies190
11.2.4Pharmaceuticalgovernance190 11.3Implementationmethodologies190 11.3.1Fogcomputing191 11.3.2Edgecomputing192 11.4Implementationmodels193
11.4.1Heartdiseaseprediction193 11.4.2HealthcareIoT-basedaffective stateminingusingdeep convolutionalneuralnetworks194
11.5ChallengesinhealthcareIoT195
11.5.1Technology-orientedchallenges195
11.5.2Adaptingtoremotehealthcare andtelehealth195
11.5.3Datasecurity195
11.6Securityissuesanddefense mechanismsandIoT196
11.6.1Securityrequirementsin healthcareIoT196
11.6.2AttacksonIoTdevices196
11.6.3Defensivemechanism197
11.7Covid19—howIoTrosetotheglobal pandemic198
11.7.1AboutCovid19199
11.7.2Decodingtheoutbreakand identifyingpatientzero199
11.7.3Quarantinedpatientcare199
11.7.4Publicsurveillance200
11.7.5Safeguardinghygiene200
11.7.6IoTandrobotics200
11.7.7Smartdisinfectionandsanitation tunnel201
11.7.8Smartmasksandsmartmedical equipment201
11.8FutureofIoTinhealthcare202
11.8.1IoTand5G202
11.8.2IoTandartificialintelligence202
11.9Conclusion203 References203 Index205
Irisfeatureextractionusingthree-level Haarwavelettransformandmodified localbinarypattern
PrajoyPodder1,M.RubaiyatHossainMondal1 andJoarderKamruzzaman2 1BangladeshUniversityofEngineeringandTechnology,InstituteofInformationandCommunicationTechnology,Dhaka,Bangladesh, 2Schoolof EngineeringandInformationTechnology,FederationUniversityAustralia,Churchill,VIC,Australia
Abbreviations
i ðx; yÞ 2Dcepstrumwith ðx; yÞ representingquefrencycoordinates
I ðu; vÞ 2Ddiscrete-timeFourierTransform
Gx; y ðÞ 2DGaborfunction
F ðU ; V Þ 2Ddiscretecosinetransform(DCT)coefficientmatrix
W Angularfrequency
σ x and σ y Standarddeviationsof x and y
xc The x-axiscoordinateoftheiriscircle
yc The y-axiscoordinateoftheiriscircle
r Radiusoftheiriscircle
gc Graylevelofthecenterpixel, c
gp Grayleveloftheneighboringpixel, p
ψ" sp BinaryiriscodeobtainedasXORoutput
LBPp MLBPoperator
1.1Introduction
Theconcernofhighsecurityandsurveillanceinthepresentworldhasmadetheidentificationofpeopleanincreasingly importantissue.Amongvariousidentificationmodes,biometrichasbeenconsideredoverthelastfewdecadesforits reliableandaccurateidentification [1 5].Commonlyusedbiometricfeaturesincludetheface,fingerprint,iris,retina, handgeometry,andDNAidentifications.Amongthem,nowadays,irisrecognitionhasattractedsignificantinterestin researchandcommercialization [6 15].Irisrecognitionhasseveralapplicationsinthesecuritysystemsofbanks,bordercontrol,restrictedareas,etc. [1 3].Onekeypartofsuchasystemistheextractionofprominenttextureinformation orfeaturesintheiris.Thisfeatureextractionmethodgeneratesfeaturevectorsorfeaturecodes.Thefeaturevectorsof theunknownimagesareusedtomatchthoseofthestoredknownones.Inanirisrecognitionsystem,thematchingprocessmatchestheextractedfeaturecodeofagivenimagewiththefeaturecodespreviouslystoredinthedatabase.In thisway,theidentityofthegivenirisimagecanbeknown.
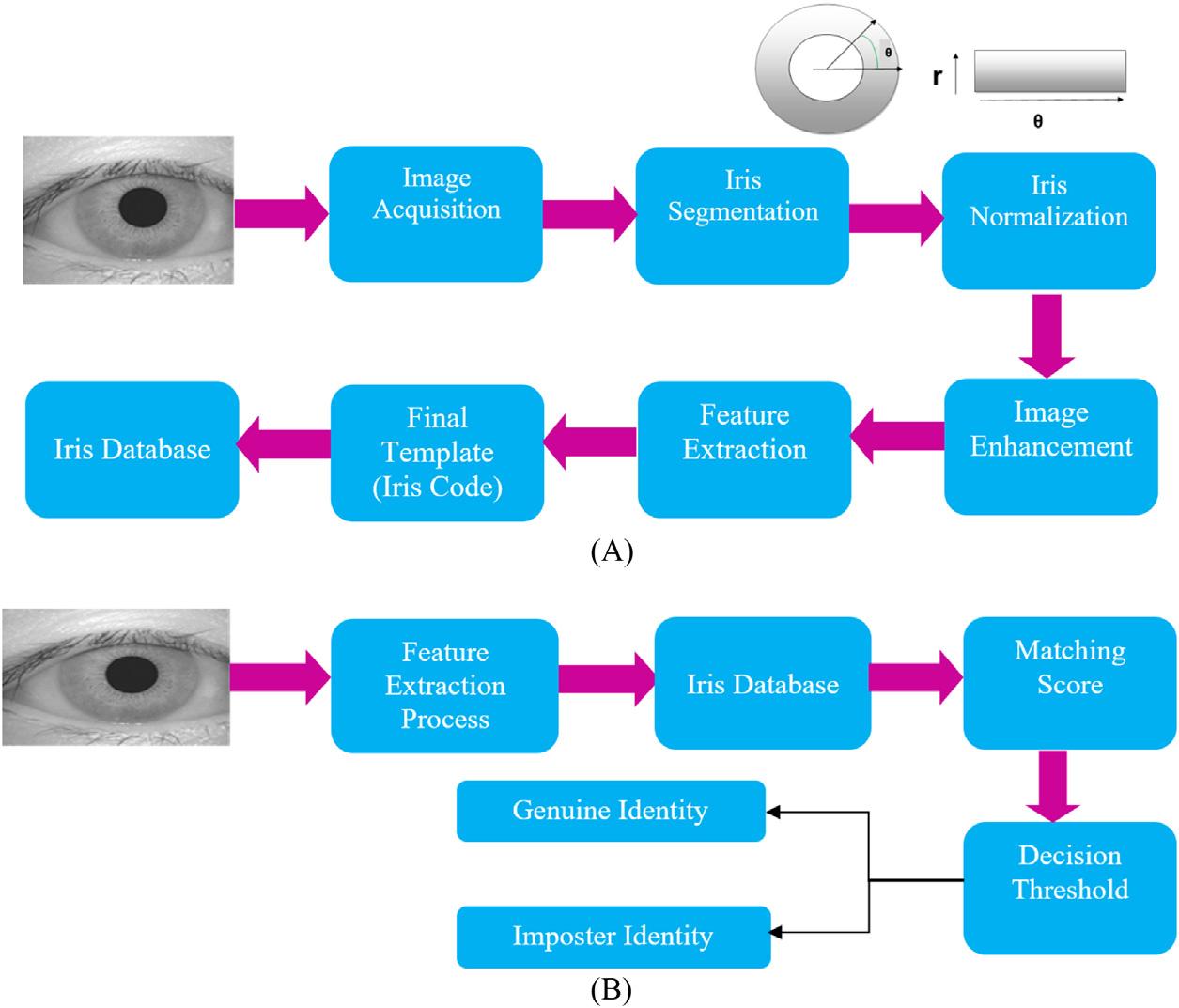
Ageneralizedirisrecognitionschemeispresentedin Fig.1.1.Therearetwomajorpartsof Fig.1.1,oneshowing thefeatureextractionandtheotherdescribingtheidentificationportionofaniris.Thesystemstartswithimageacquisitionandendswithmatching,thatis,thedecisionofacceptanceorrejectionoftheidentity.Inbetween,therearetwo mainstages:irisimagepreprocessingandfeatureextraction [3,4].Furthermore,irisimagepreprocessingincludesthe stagesofirissegmentation,normalization,andenhancement [5,11].Intheacquisitionstage,camerasareusedtocapture imagesoftheiris.Theacquiredimagesarethensegmented.Inirissegmentation,theinnerandtheouterboundariesare
FIGURE1.1 Exampleofatypicalirisrecognition system:(A)processoffeatureextractionfromaniris image;(B)identificationofaniris.
detectedtoseparatetheirisfromthepupilandsclera.Acircularedgedetectionmethodisusedtosegmenttheiris regionbyfindingthepixelsoftheimagethathavesharpintensitydifferenceswithneighboringpixels [3].Estimating thecenterandtheradiusofeachoftheinnerandoutercirclesreferstoirislocalization.Afteririssegmentation,any imageartifactsaresuppressed.NextisthenormalizationstepinwhichtheimagesaretransformedfromCartesianto pseudopolarscheme.Thisisshownin Fig.1.1,whereboundarypointsarealignedatanangle.Imageenhancementis thenperformed.Asapartoffeatureextraction,theimportantfeaturesareextractedandthenusedtogenerateaniris codeortemplate.Finally,irisrecognitionisperformedbycalculatingthedifferencebetweencodeswiththeuseofa matchingalgorithm.Forthispurpose,HammingandEuclidianarewellknownandalsoconsideredinthischapter [15]. Thematchingscoreiscomparedwithathresholdtodeterminewhetherthegivenirisisauthenticornot.
Despitesignificantresearchresultssofar [3 9,11,12,14],thereareseveralchallengesinirisrecognition [13,15 26].Oneproblemistheocclusion,thatis,thehidingoftheiriscausedbyeyelashes,eyelids,specularreflection,andshadows [21].Occlusioncanintroduceirrelevantpartsandhideusefuliristexture [21].Themovementofthe eyecanalsocauseproblemsinirisregionsegmentationandthusaccuraterecognition.Anotherissueisthecomputation timeofirisidentification.Forlargepopulationsizes,thematchingtimeoftheiriscansometimesbecomeexceedingly highforreal-timeapplications,andtheidentificationdelayincreaseswiththeincreaseinthepopulationsizeandthe lengthoffeaturecodes.Ithasbeenreportedintherecentliterature [13,18,22] thattheexistingirisrecognitionmethods stillsufferfromlongruntimesapartfromotherfactors.Thisisparticularlytruewhenthesamplesizeisverylarge,and theirisimagesarenonidealandcapturedfromdifferenttypesofcameras.Hence,devisingamethodthatreducesthe runtimeofirisrecognitionwithoutcompromisingaccuracyisstillanimportantresearchproblem.Theidentification delaycanbereducedbyreducingthefeaturevectorofirisimages.Thusthischapterfocusesontheissueofreducing thefeaturevectorwhichwillleadtoareductioninidentificationdelaywithoutloweringtheidentificationaccuracy. Forloweringthefeaturevector,theconceptofHaarwaveletalongwith modifiedlocalbinarypattern (MLBP)isused inthiswork.Notethatinthecontextoffacerecognition [27 30] andfingerprintidentification [31],theHaarwavelet transformdemonstratesanexcellentrecognitionrateatalowcomputationtime.InRef. [32],theHaarwaveletisalso proposedwithouttheuseofMLBP.
Themaincontributionsofthischaptercanbesummarizedasfollows.
1. Anewirisfeatureextractionmethodisproposed.Thisnewmethodisbasedonrepeated Haarwavelettransformation (HWT)andMLBP.NotethatMLBPisthelocalbinarypattern(LBP)operationfollowedbyExclusiveOR (XOR).ThisproposedmethodisdifferentfromthetechniquedescribedinRef. [30],whichusessingle-levelHWT andLBP(withoutXOR)inthecontextoffacerecognition.
2. TheefficacyoftheHWT MLBPmethodisevaluatedusingthreewell-knownbenchmarkdatasets:CASIA-Iris-V4 [33],CASIA-Iris-V1 [34],andMMUirisdatabase [35]
3. Acomparisonismadeofthisnewtechniquewiththeexistingmethodsoffeatureextractionintermsoffeaturevectorlength, falseacceptancerate (FAR),and falserejectionrate (FRR).Itisshownherethattheproposedmethod outperformstheexistingonesintermsoffeaturevectorlength.
Theremainderofthischapterisorganizedasfollows. Section1.2 providesaliteraturesurveyoftherelevant research. Section1.3 showstheirislocalizationpartwheretheinnerboundaryandouterboundarycanbedetected. Section1.4 describesirisnormalization. Section1.5 illustratesourproposedapproachforthepurposeofencodingthe irisfeatures. Section1.6 describestheirisrecognitionprocessbymatchingscore.Theeffectivenessofthenewmethod isevaluatedin Section1.7.Finally, Section1.8 providesasummaryoftheresearchworkfollowedbythechallenges andfuturework.
1.2Relatedworks
Anumberofresearchpapersdescribeirisfeatureextractiontechniques,whicharediscussedinthefollowing. Maetal. [3] appliedabankofspatialfilterstoacquirelocaldetailsoftheiris.Thesespatialfiltersgeneratediscriminatingtexturefeaturesforanirisimagebasedonthecharacteristicsoftheiris.Maetal. [4] consideredabankofcircularsymmetricfiltersforirisfeatureextraction.Thesefilters [4] aremodulatedbyacircularsymmetricsinusoidal function,whichisdifferentfromtheGaborfiltermodulatedbyanorientatedsinusoidalfunction.Monroetal. [5] used discretecosinetransform(DCT)foririsrecognition.Daugman [6] introducedtheideaofusinga2DGaborwaveletfilterforextractingfeaturesofanirisimage.Furthermore,Maseketal. [9] used1Dand2DLog-Gaborfiltersforfeature extraction.Lietal. [8] usedaconvolutionalneuralnetwork(CNN)algorithm,whichisaformofdeeplearning,to extractirisfeatures.Umeretal. [12] usedanoveltexturecodedefinedoverasmallregionateachpixel.Thistexture codewasdevelopedwithvectororderingbasedontheprincipalcomponentofthetexturevectorspace.Solimanetal. [11] consideredfeatureextractionusingtheGaborfilter,wheretheoriginalGaborfeaturesweremaskedviaarandom projectionscheme.Themaskingwasperformedtoincreasethelevelofsecurity.Inthisscheme,theeffectsofeyelids andeyelasheswereremoved.Anirisfeatureextractionmethodusingwavelet-based2Dmel-cepstrumwasproposedin Ref. [14],wherethecepstrumofasignalistheinverseFouriertransformofthelogarithmoftheestimatedsignalspectrum.The2Dcepstrumofanimagecanbedefinedbythefollowingexpression:
where ^ i ðx; yÞ isthe2Dcepstrumwith ðx; yÞ representingquefrencycoordinates,IDFTrepresentstheinversediscrete Fouriertransform,and I ðu; vÞ isthe2Ddiscrete-timeFourierTransformoftheimage.Thisschemeappliedthe Cohen Daubechies Feauveau 9/7filterbankforextractingfeatures.Inwaveletcepstrum,nonuniformweightsare assignedtothefrequencybins.Inthisway,thehigh-frequencycomponentsoftheirisimageareemphasized,resulting ingreaterrecognitionreliability.Furthermore,thiswaveletcepstrummethodhelpstoreducethefeatureset.
Barpandaetal. [15] usedatunablefilterbanktoextractregion-basedirisfeatures.Thesefilterswereusedforrecognizingnoncooperativeimagesinsteadofhigh-qualityimagescollectedincooperativescenarios.Thefiltersinthisfilter bankwerebasedonthehalfbandpolynomialof14thorderwherethefiltercoefficientswereextractedfromthepolynomialdomain.Toapplythefilterbank,theiristemplatewasdividedintosixequispacedpartsandthefeatureswere extractedfromallthepartsexceptthesecondone,whichmainlycontainsartifacts.Betancourtetal. [13] proposeda robustkeypoints basedfeatureextractionmethod.Toidentifydistinctivekeypoints,threedetectors,namely Harris Laplace,Hessian Laplace,andFast-Hessiandetectors,wereused.Thismethodissuitableforirisrecognition undervariableimagequalityconditions.
Foririsfeatureextraction,Sahuaetal.in [22] used phaseintensivelocalpattern (PILP),whichconsistsofdensitybasedspatialclusteringandkey-pointreduction.Thistechniquegroupssomecloselyplacedkeypointsintoasingle keypoint,leadingtohigh-speedmatching.Jamaludinetal. [18] useda1DLog-Gaborfilterandconsideredthesubiris regionforfeatureextraction.Thisfilterhasasymmetricalfrequencyresponseonthelogaxis.Inthiscase,onlythe loweririsregionsthatarefreefromnoise,aswellasocclusions,areconsidered.
InRef. [17],combined discretewavelettransform (DWT)andDCTwereusedfortheextractionofirisfeatures. Firstly,DWTwasperformedwheretheoutputofthisstagewasinthespatialdomain.Next,DCTwasperformedto transformthespatialdomainsignaltothefrequencydomainandtoobtainbetterdiscriminatoryfeatures.AnotherfeatureextractionmethodisthediscretedyadicwavelettransformreportedinRef. [16].Indyadicwavelettransform,the
decompositionateachlevelisdoneinawaythatthebandwidthoftheoutputsignalishalfofthatoftheinput.InRef. [26],aPILPtechniqueisusedforfeatureextractionandtoobtainafeaturevectorofsize1 3 128.InthisPILPmethod, therearefourstages:key-pointdetectionviaphase-intensivepatterns,removalofedgefeatures,computationoforientedhistogram,andformationofthefeaturevector.Irisfeatureswereextractedusing1DDCTand relationalmeasure (RM),whereRMencodesthedifferenceinintensitylevelsoflocalregionsofirisimages [21].Thematchingscoresof thesetwoapproacheswerefusedusingaweightedaverage.Thescore-levelfusiontechniquecompensatesforsome imagesthatarerejectedbyonemethodbutacceptedbytheother [21].Anotherwayofextractingfeaturevectorsfrom irisimagesisbytheuseoflinearpredictivecodingcoefficients(LPCC)andlineardiscriminantanalysis(LDA) [24]. Llanoetal.in [19] useda2DGaborfilterforfeatureextraction.Beforeapplyingthisfilter,thefusionofthreedifferent algorithmswasperformedatthesegmentationlevel(FSL)oftheirisimagestoimprovethetextualinformationofthe images.Oktianaetal. [36] proposedanirisfeatureextractionsystemusinganintegrationofGradientface-basednormalization(GRF),whereGRFusesanimagegradienttoremovethevariationintheilluminationlevel.Furthermore, theworkinRef. [19] concatenatedtheGRFwithaGaborfilter,adifferenceofGaussian(DoG)filter,binarystatistical imagefeature(BSIF),andLBPforirisfeatureextractioninacross-spectralsystem.Shuaietal.proposed [37] aniris featureextractionmethodbasedonmultiple-sourcefeaturefusionperformedbyaGaussiansmoothingfilterandtexture histogramequalization.Besides,therehavebeensomerecentstudiesinthefieldofirisrecognition [38 49],withsome focusingonirisfeatureextractionmethods [38,40 42,45,49] andsomeonirisrecognitiontasks [39,44,46,48]
The2DGaborfunctioncanbedescribedmathematicallybyusingthefollowingexpression:
and2DDCTcanbedefinedas:
where f(X,Y)istheimagespacematrix;(X, Y)isthepositionofthecurrentimagepixeland FU ; V ðÞðU ; V 5 1; 2; ... ::; M 1Þ isthetransformcoefficientmatrix; W istheangularfrequency;and σ x and σ y arethe standarddeviationsof x and y,respectively.
Theconceptsofmachinelearning(ML)-drivenmethodsforexample,neuralnetworksandgeneticalgorithmshave beenreported [46],whiletheideaofdeepCNNshasalsobeenapplied [40].Moreover,researchersarenowinvestigatingtheeffectivenessofmultimodalbiometricrecognitionsystems [43,47].
Acomparativesummaryofsomeofthemostrelevantworksonirisfeatureextractionisshownin Table1.1.Itcan beseenthatthereareseveralalgorithmsandtheseareappliedtodifferentdatasets,achievingvaryingperformance results.
1.3Irislocalization
ThissectiondiscussestheirislocalizationstepthatemployscircularHoughtransformation,whichiscapableofproperlydetectingcirclesintheimages.Houghtransformsearchesforatripletofparameters(xc ; yc ; r )determining(xi ; yi ), where xc ; yc ,and r representthex-axiscoordinate,y-axiscoordinate,andtheradiusoftheiriscircle,respectively.In thiscase,(xi ; yi )representsthecoordinatesofanyofthe i pointsonthecircle.Withthisconsideration,theHoughtransformcanbedefinedasfollows.
Inthisregard,edgepointsaredetectedfirst.Foreachoftheedgepoints,acircleisdrawnhavingthecenterinthe middleoftheedge.Inthisway,eachoftheedgepointsconstitutescircleswiththedesiredradius.Next,anaccumulator matrixisformedtotracktheintersectionpointsofthecirclesintheHoughspace,wheretheaccumulatorhasthenumberofcircles.ThelargestnumberintheHoughspacepointstothecenteroftheimagecircles.Severalcircularfilters withdifferentradiusvaluesareconsideredandthebestoneisselected.
TABLE1.1 Summaryofliteraturereview.
ReferencesAdoptedtechniqueinreferenceRemarksDatabase
[3] Spatialfiltersconstructedbasedon observations
Extractionoffeaturesisperformedonlyin theupperportionofthenormalizediris regionasitprovidesusefultexture information.Thefeaturevectorlengthis large,beingofsize1 3 1536.
[4] CircularsymmetricfiltersAbout75%ofthetop-mostofthe unwrappedirisimagesareusedfortexture information.Thevariationofthetextureof theirisinthelocalregionisnotfocusedon inthispaper.
[5] Patch-codingtechniqueforextracting featuresfromnormalizediris.The featuresarederivedbyusingfastFourier transformation.
Themethodhaslowcomplexitywithahigh amountofaccuracy.Additionally,the dimensionalityofthefeaturevectoris 1 3 2343.However,nonidealimagesarenot considered.
[6] 2DGaborfilterThedimensionalityofthefeaturevectoris 1 3 2048.
[9] 1Dand2DLog-GaborfiltersThismethodcannotproducefeaturesof differentfrequencies,andthesizeoftheiris templateis1 3 4800.
[8] DeeplearningCNNasdeeplearningisusedtoextractiris features,andthefeaturesarethenusedfor imageencryption.
[12] TexturecodecooccurrencematrixFeaturevectorsizeof1 3 400.Themethod usesonlyaneffectiveportionoftheiris imagestoavoidtheocclusionpartcausedby notonlyeyelashesbutalsoeyelids.
[11] 1DGaborfilterwhereGaborfeatures aremasked
[7] 2DkernelandhybridMLPNN PSO algorithm
[14] 2Dwaveletcepstrumtechniquefor featureextraction
[15] Tunablefilterbankbasedonhalfband polynomialof14thorder
[13] Keypoints basedfeatureextraction method
MaskstheoriginalGaborfeaturesfor improvingsecuritywhileexcludingthe effectsofeyelidsandeyelashes.Moreover, onlytheupperhalfofthenormalizediris portionisconsidered.
Featureextractionisperformedonasmall sampleof140imagesatanaccuracyrateof 95.36%.Inthiscase,1000iterationsare performed,whichleadstohigh computationaltime.
Falseacceptancerateis10.45%;recognition accuracyis89.93%.
Falseacceptancerateis8.45%;recognition accuracyis91.65%.
Considersonlysalientkeypointsinthe wholeregion.Thefeatureextractionstageis timeconsuming.
[23] Low-densityparitycheckandSHA-512Comparativelyhighfalserejectionrate.
[22] Density-basedspatialclusteringandkeypointreductiontobeappliedonPILP
Forfeatureextractionandfeaturevector reduction,postprocessingisrequired, leadingtoadditionaltimeconsumption.
[18] SubiristechniqueDoesnotextractfeaturesoftheunoccluded upperpartoftheirisregion.
CASIA-Iris-V1
CASIA-Iris-V1
UPOL,CASIA-Iris-V3Interval,MMU1,and IITD
CASIA-Iris-V3-Interval
CASIA-Iris-V3
CASIA-Iris-V3, UBIRISv1,IITD
CASIA-Iris-V3, UBIRISv1,IITD
CASIA-Iris-V4-Interval, MMU2,UBIRIS1
BATHandCASIA-IrisV3
CASIA-Iris-V4
(Continued )
CASIA-Iris-V1
CASIA-Iris-V4
TABLE1.1 (Continued)
ReferencesAdoptedtechniqueinreferenceRemarksDatabase
[17] DWTandDCTcombinationforfeature extraction
Providesgoodperformanceonlyforlowcontrastimages.Arecognitionrateof88.5% wasachievedonthePhoenixdatabase.
[16] DiscretedyadicwavelettransformIrisimagesofonly10peopleareusedanda featurevectorwithasizeof1 3 256is achieved.Resultsneedtobevalidatedwitha highernumberofsubjects.
[26] Localfeaturebasedonphase-intensive patterns
Featureextractionisbasedonkeypoint detectionviaphase-intensivepatterns. Obtainsafeaturevectorofsize1 3 128.
[21] DCTandRMBasedonthedissimilarityscoreofDCTand RMandusingtheHammingdistancemetric, thematchingofimagesisperformed.Thisis usedtocompensateforimagesrejectedby eitherDCTorRMbutacceptedbytheother.
[24] LPCCandLDAThemethodhashighcomplexity,andinthe caseofLPCC,resultsinafeaturevectorwith asizeof1 3 546.
[19] Texturalinformationdevelopmentand exploration
Thismethodhasthreestages:quality evaluation,automaticsegmentation,and fusionatthesegmentationlevel.This methodrejectsimagesthathavelowquality. Theobtainedfeaturevectorisofsize 1 3 2048.
[36] Gaborfilter,aDoGfilter,BSIF,andLBPThefeatureextractionisdoneusingthe fusionofGRFwithaGaborfilter,aDoG filter,aBSIF,andLBP.Hammingdistanceis usedformatchingpurposes.
[37] ConvolutionalneuralnetworkFeatureextractionisdoneusingtheconcept offeaturefusion,whichisachievedbyusing aGaussianfilterandatexturehistogram equalizer.
1.4Irisnormalization
PhoenixandIITDiris database
BATH,CASIA-Iris-V3, UBIRISv2,and FERETv4
CASIA-Iris-V4Interval, Lamp,andselfcollectedIITK
MBGC-V2,CASIA-IrisV3,CASIA-Iris-V4, andUBIRISv1(foriris image)
HongKong PolytechnicUniversity Cross-SpectralIris ImagesDatabase
JLUirislibrary
Thissectiondescribestheirisnormalizationstep.Thesizeofdifferentacquiredirisimageswillvarybecauseofthevariationinthedistancefromthecamera,angleofimagecapturing,illuminationlevel,etc.Forthepurposeofextracting imagefeatures,theirisimageistobesegmentedandtheresultantsegmentsmustnotbesensitivetotheorientation, size,andpositionofthepatterns.Forthis,aftersegmentation,theresultantelementistransformedtoCartesian.Inother words,thecircularirisimageistransformedintoafixeddimension.
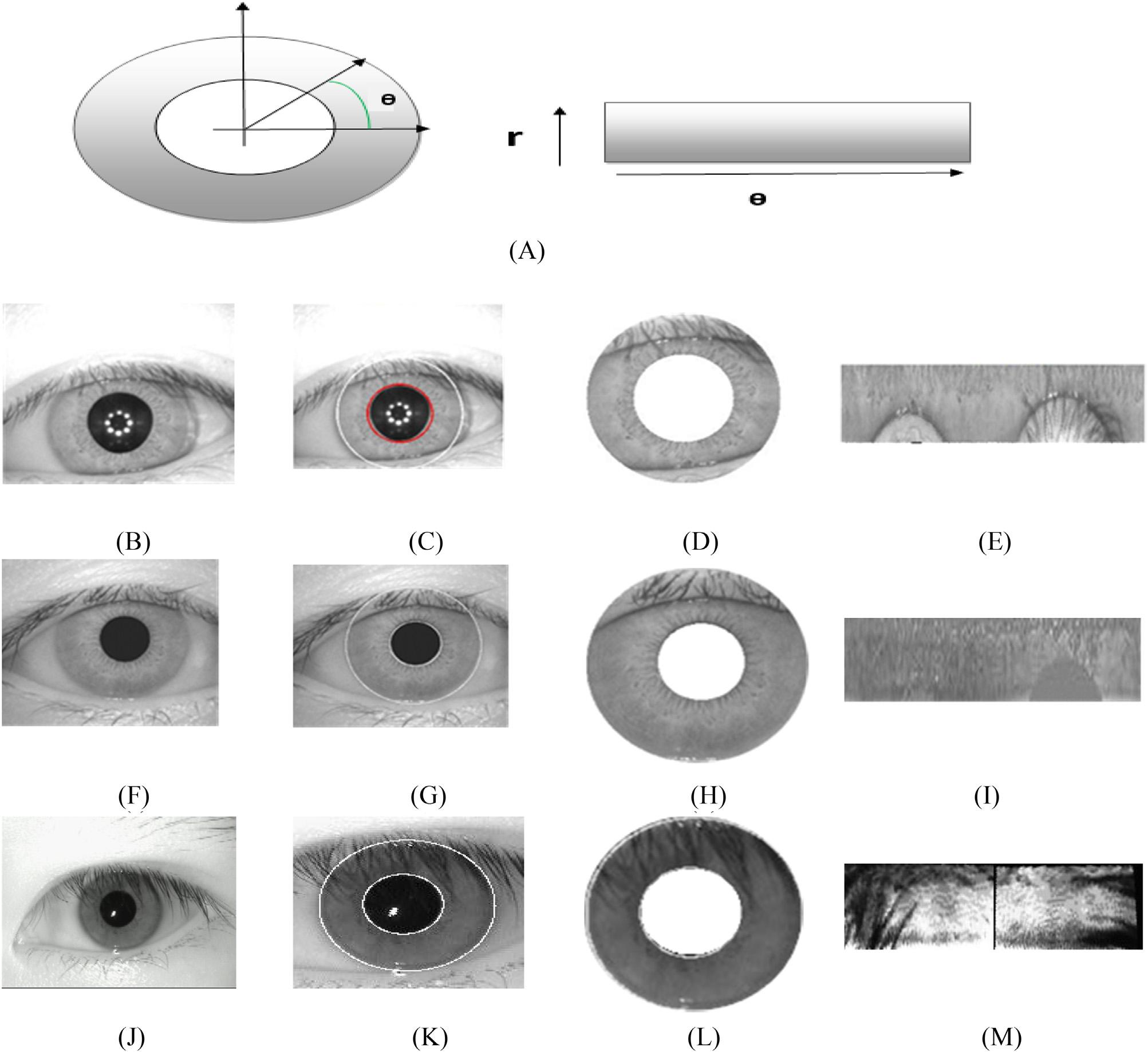
Fig.1.2 illustratesthenormalizationofirisimagesfromthreedatasets.Foreachofthedatasets,theoneoriginal inputimageisshown,followedbyitsinnerandouterboundarydetection,andthenitssegmentedversion,andfinally itsnormalizedversion. Fig.1.2A describesDaugman’srubbersheetmodelforirisrecognition.Threeoriginalimages fromthreedatasetsareshownin Fig.1.2B,F,andJ.Firstofall, Fig.1.2B isoneoriginalimagefromtheCASIA-IrisV4dataset [33].Fortheirisimagein Fig.1.2B E representthecorrespondinginnerandouterboundaries,the segmentedversion,andthenormalizedversion,respectively.Secondly, Fig.1.2F isoneoriginalimagefromthe CASIA-Iris-V1dataset [34].Fortheirisimagein Fig.1.2F I representthecorrespondinginnerandouterboundaries, thesegmentedversion,andthenormalizedversion,respectively.Thirdly, Fig.1.2J isoneoriginalimagefromthe MMUirisdatabase [35],and Fig.1.2K M representthecorrespondinginnerandouterboundaries,thesegmentedversion,andthenormalizedversion,respectively.
CASIA-Iris-V1
FIGURE1.2 Illustrationsof(A)Daugman’srubbersheetmodel;(B,F,J)originalinputimages;(C,G,K)imageswithinnerandouterboundary detection;(D,H,L)segmentedirisregions,and(E,I,M)irisimagesafternormalization.
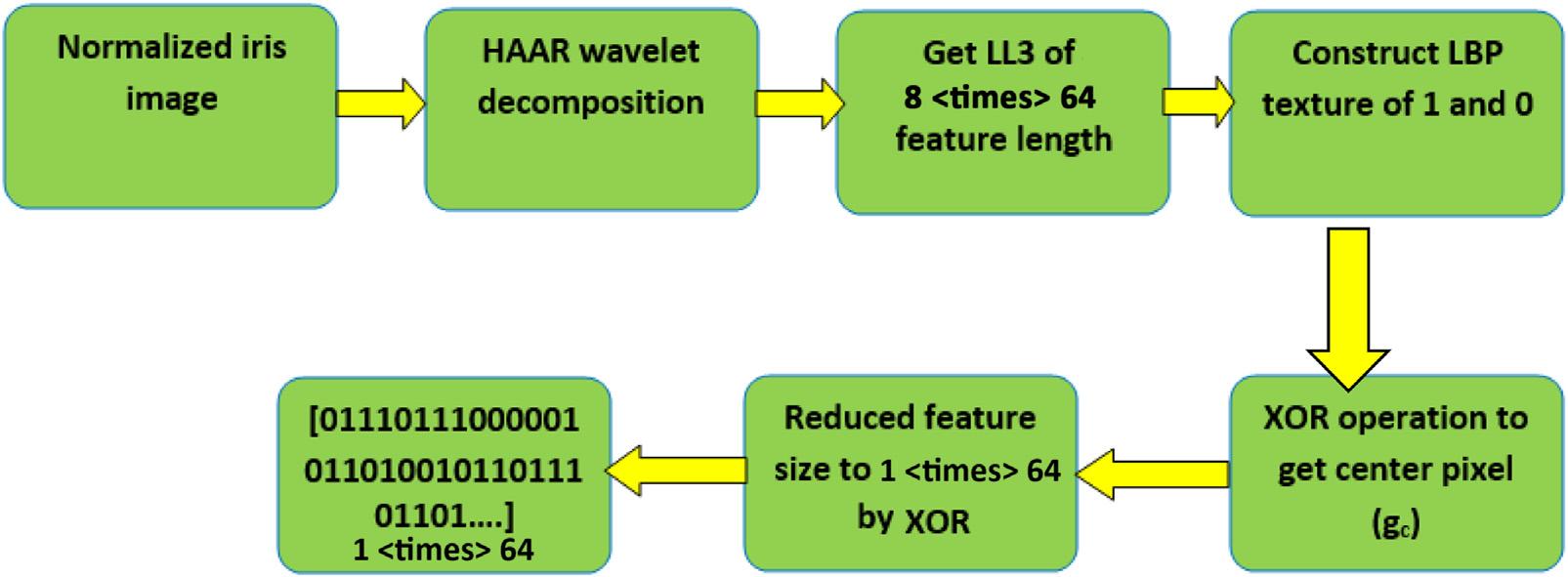
1.5Theproposedfeatureextractionscheme
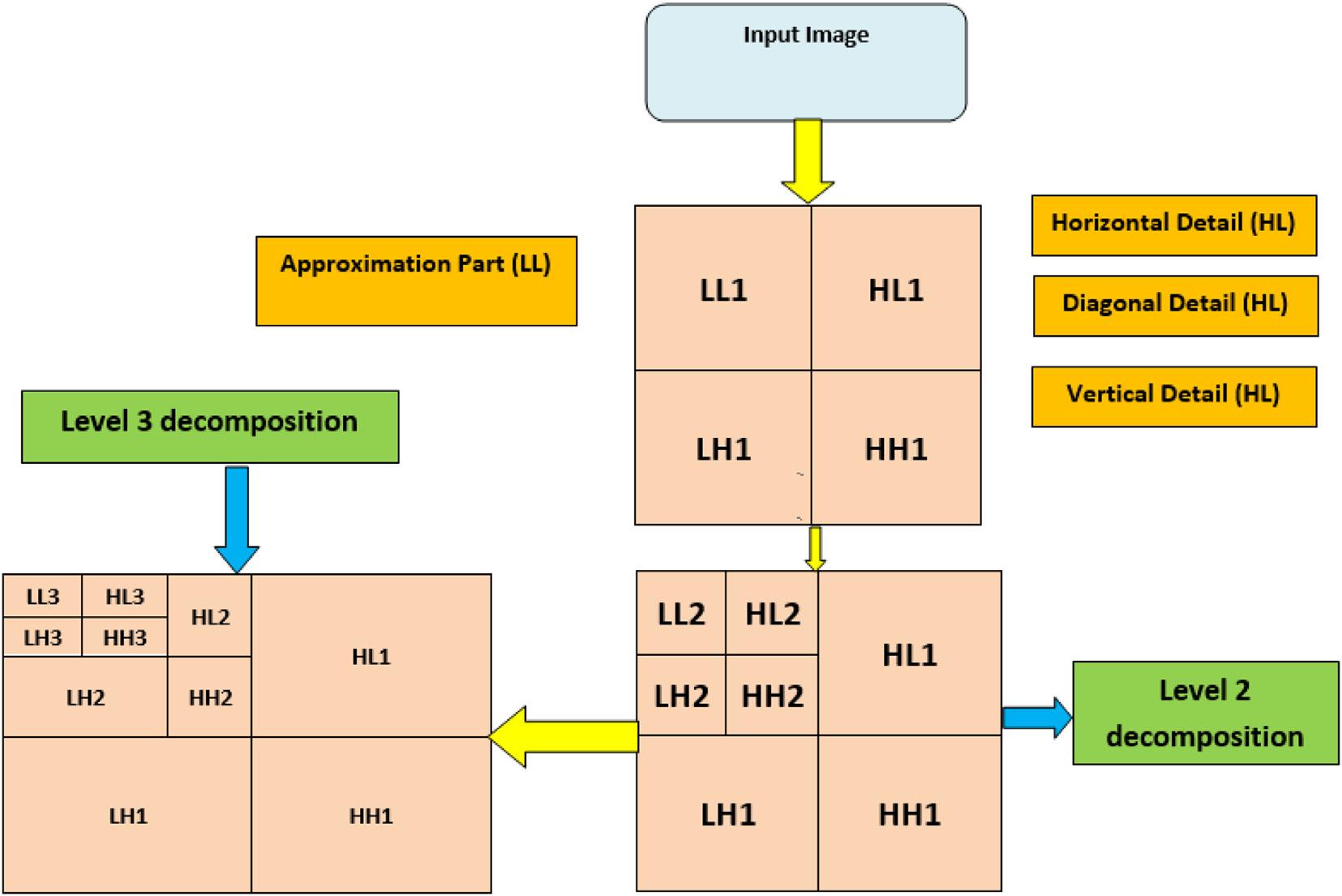
Thissectiondescribestheproposedirisfeatureextractionmethod. Fig.1.3 representstheblockdiagramoftheproposed three-levelHWTandMLBP.ThedecompositionoftheimagethreetimesbyHWTresultsinthereductioninfeature sizewithoutsignificantlossintheimagequalityorimportantattributes.TheuseofMLBPfurtherreducesthefeature vectorsizewithoutlossinimageattributes. Fig.1.4 showsthethree-levelHWT.Itcanbeseenfromthefigurethatat eachlevelofHWT,theinputimageisdividedintofouroutputimages.Theseoutputimagesaredenotedas horizontal detail (HL), verticaldetail (VL), diagonaldetail (HH),and approximation (LL)images.TheLLsubimage,alsoknown astheLLsubband,containssignificantinformationabouttheoriginalimage.Inotherwords,theLLsubbandisa coarseapproximationofanimageanditdoesnotcontainhigh-frequencyinformation.Next,thethree-levelHWTalgorithmisdiscussed.
Algorithm1:HWT
Input:Normalizedirisimage
Output:Approximationpartoflevelthree
MainProcess:
Step1:Applyfirst-levelHWTtothenormalizedirisimagetogenerateitswaveletcoefficients.
Step2:Applysecond-levelHWTontheapproximationpartobtainedfromStep1togenerateitswavelet coefficients.
Step3:Applythird-levelHWTontheapproximationpartobtainedfromStep2togenerateitswaveletcoefficients.
Step4:GetthelevelthreeapproximationpartobtainedfromStep3.
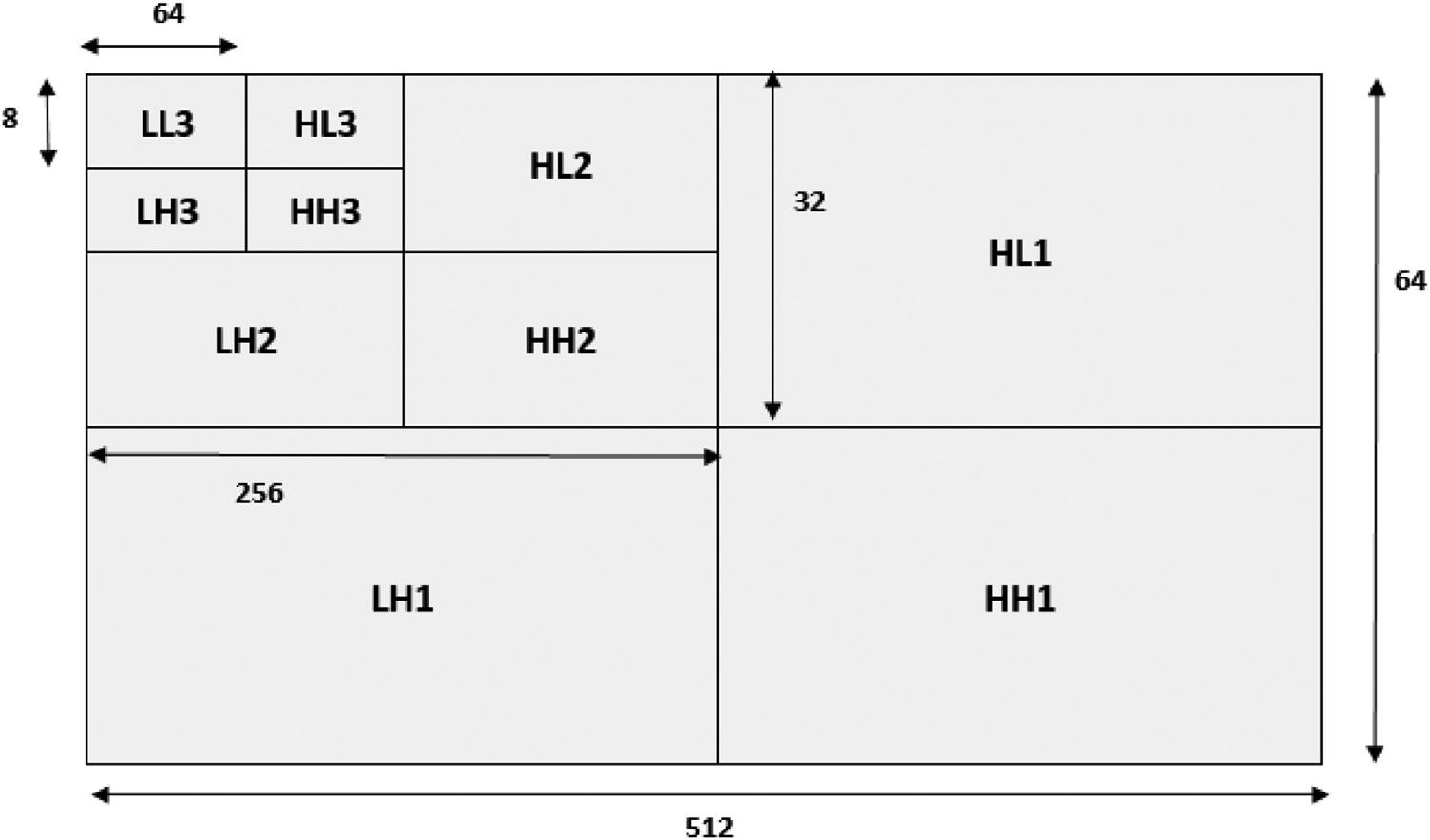
ThemainideaofusingHWTisthatwaveletdecompositioncantransformadetailedimageintoapproximation images.Theapproximationpartscontainamajorportionoftheenergyoftheimages.TheHWTisrepeatedlyexecuted toshrinktheinformationsize.Theresultsofthethree-leveldecompositionproduceareducedcharacteristicsregion havinglittleloss.Thisisshownin Fig.1.5.Itcanbenotedthatmostoftheinformationoftheirisimageiscontained intheextractedLL(low-frequency)regiononthemultidividedirisimageasindicatedby Fig.1.5.Theotherregions havelessinformationasindicatedbytheirlowintensity(dark)levels. Fig.1.6 illustratesthesizeofeachlevelforthe three-levelHWT.Theapplicationoflevel1HWTtothenormalizedimageofsize64 3 512resultsinwavelet
FIGURE1.4 Three-levelHWT.
FIGURE1.3 Blockdiagramoftheproposedapproachforirisfeatureextraction.
FIGURE1.5 Three-levelwavelet decompositionofnormalizediris.
FIGURE1.6 Three-levelHWT withthesizeofeachlevel.
coefficientsof LL1, LH1, HL1,and HH1.Inthiscase,theapproximationpartoflevel1,denotedas LL1,becomesof size32 3 256.Next,level2HWTisappliedto LL1,whichgenerateswaveletcoefficientsof LL2,LH2, HL2,and HH2 Inthiscase,theapproximationpartoflevel2(LL2)becomesofsize16 3 128.Afterthat,level3HWTisappliedto LL2 togenerateitswaveletcoefficients LL3,LH3, HL3,and HH3.Inthiscase,theapproximationpartoflevel3(LL3) becomesofsize8 3 64.Henceamajordistinctiveregion LL3 isobtainedbyperformingthewavelettransformation threetimes.Next,the LL3 regionisusedfortheMLBPtasks.
NowconsidertheMLBPoperation [25],whichgeneratesrobustbinaryfeatures.Furthermore,MLBPhaslow computationalcomplexity.MLBPlabelseachpixelbasedontheneighboringpixelsandconsideringagiventhreshold. MLBPthenproducesoutputsinthebinaryformat.Thisbinarycodecandescribethelocaltexturepattern.Notethat MLBPisanLBPfollowedbyanXORoperation.Next,MLBPoperationisdescribedinthefollowing.
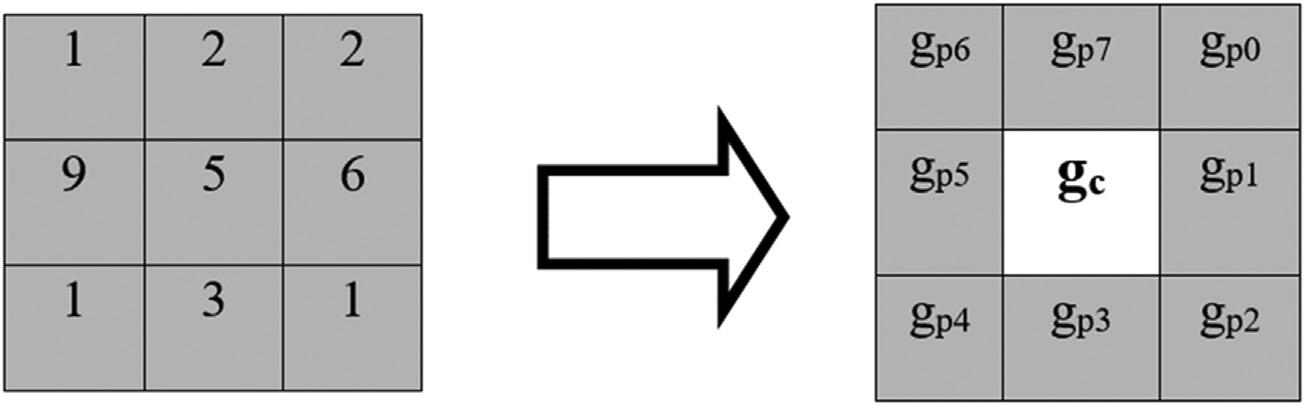
Foracenterpixel c,andneighboringpixels p withinaneighborhoodof P pixels,theMLBPoperationcanbe expressedasfollows.
where LBPp istheMLBPoperator, gc isthegraylevelof c,and gp isthegraylevelof p pixels.Moreover, SxðÞ in(4) referstothesignfunctiondefinedas,
FIGURE1.7 Centerelementofa3 3 3pixel image.
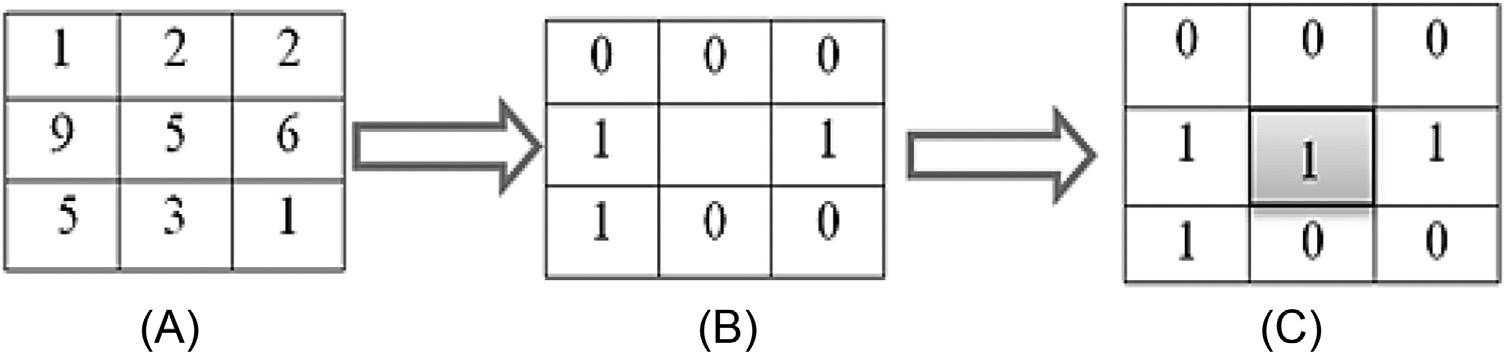
FIGURE1.8 MLBPoperationof a3 3 3subregion:(A)theneighborhoodofapixelwithinthe image,(B)thethresholdversionof theneighborhood,and(C)the MLBPpatternwherethemiddle pixelhasbeencomputed.
Next,thecenterpixelvalueisgeneratedbyapplyingXORoperationonthevaluesof LBPp .Thisresultsinthefollowingexpression.
ψ" ðsp Þ 5 so " "sP-1 (1.6) where " denotestheXORoperatorand ψ" sp isthebinaryiriscodeobtainedastheXORoutput.SinceitisacommutativeoperationofXOR,thiscanbeperformedbycircularlyshiftingon sp intheclockwiseoranticlockwisedirection.NowXORisperformedtoreducethesizefrom8 3 64to1 3 64.XORiscomputedinthecolumnvector.Inother words,theeight-rowirissignatureisreducedtoonlyasinglerow. Figs.1.7and1.8 describetheMLBPoperation. Fig.1.7 showsthecenterpixelina3 3 3neighborhood,while Fig.1.8 illustratesthecomputationof LBP8;1 withXOR forasinglepixel.
Algorithm2:FeatureencodingusingtheproposedMLBP
Input:Levelthreeapproximationpartofthenormalizedimage
Output:Binarysequenceofthenormalizedirisimage.
MainProcess:
Step1:Readtheintensityvaluesofthelevelthreeapproximationpartofthenormalizedimage.
Step2:ConverttheRGBimagetograyscaleform.
Step3:Resizetheimageifrequiredandthenstorethesize ½M ; N oftheimage.
Step4:Dividetheimageintoeightsegments.
Step5:Foreachoftheimagesegments,applya3 3 3kernel.
Step6:Fori 5 1:P // P 5 8fora3 3 3kernel.
Step7:Compute DiðÞ 5 gp ðiÞ gc ðiÞ // gp isthegraylevelforneighboringpixelsand gc isthecenterpixel.
Step8:If DiðÞ , 0
else
end.
Step9:ComputeLBP_p 5 XOR(SiðÞ);//ApplyXORoperationtogetthebinarymask.
Step10:PlacethebinaryoutputoftheXORoperationinthecenterpixel.
Step11:Movethekernelinordertoobtainabinarytemplate.
Step12:ApplyXORoperationacrossthecolumns.
So,forthecaseofMLBP,thefirstLBPoperationextractsthedistinctivefeaturestogenerateauniqueiriscode. Thiscodeisreducedfrom8 3 64featuresto1 3 64byapplyingtheXORoperation.
1.6Matchingresults
Thissectionprovidesresultsonirisrecognitionusingthematchingprocessofiriscodes.Inordertofindthesimilarity ortomeasuretheclosenessofanunknowniriscodewithatemplateiriscode,thedistancebetweenthesetwoiscalculated.Thedistanceisamethodofdefiningthedegreeofmatchingbetweentwoiriscodes.Forthis,Euclideanand Hammingdistancesareconsidered.TheEuclideandistanceiscalculatedasfollows.
where ED istheEuclideandistancebetweentwocoordinatepoints:(X1,Y1)and(X2,Y2).InthecaseofHammingdistancebetweentwoiriscodes,thenumberofunmatchedbitsisdividedbythenumberofbitsusedforcomparison.The mainoperationintheHammingdistanceistheuseofanXORgatewhichcomputesthedisagreementbetweentwo inputbits.If P and Q aretwobitwisetemplatesofirisimagesand N isthenumberofbitsofeachiriscode,thenthe Hammingdistancecanbemathematicallyexpressedasfollows.
where HD denotestheHammingdistance.Henceaccordingto(6), HD 5 0indicatescompletesimilaritybetweentwo iriscodes,while HD 5 1meanstotaldissimilaritybetweenthecodes.Inpractice,thetwoiriscodesareassumedtobe thesame,iftheHammingdistanceislowerthanathreshold.SimilartotheworkinRef. [6],thischapterconsidersa Hammingdistancevalueof0.32foriristemplatestobeidentical.
1.7Performanceevaluation
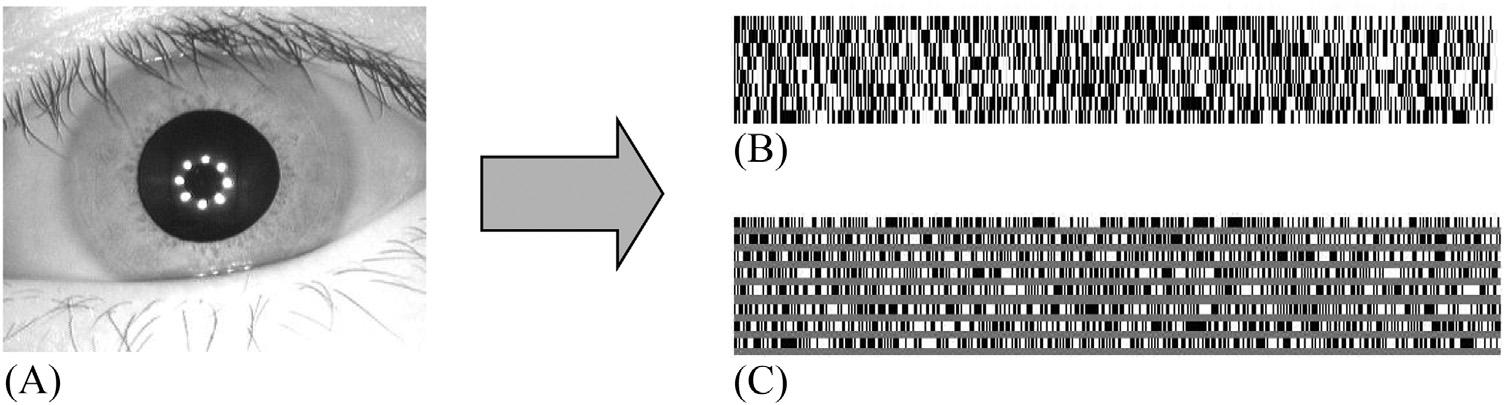
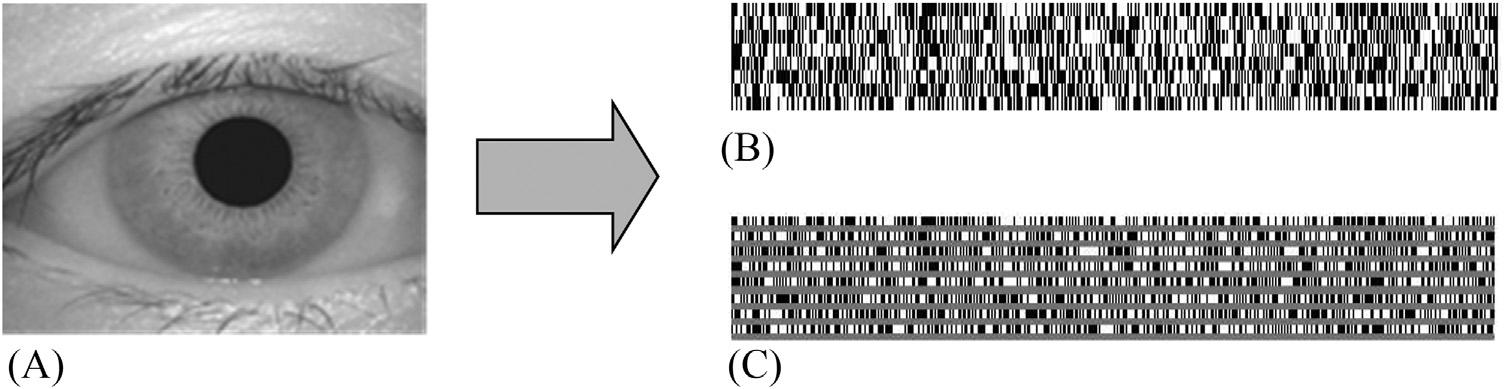
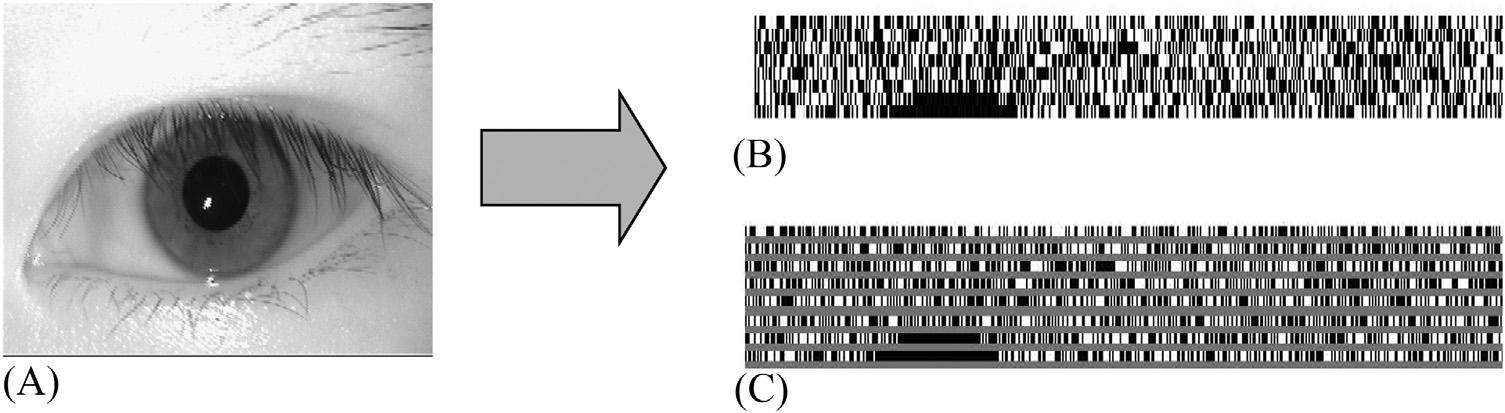
Thissectiondiscussestheexperimentalresultsoftheproposedmethod.Fortheexperimentation,imagesareobtained fromthreedifferentdatasets [33 35]. Figs.1.9 1.11 correspondtoimagesfromtheCASIA-IRIS-V4 [33],CASIAIRIS-V1 [34],andMMU [35] datasets,respectively.Thedatasetsaredescribedin Table1.2.TheCASIA-IRIS-V4datasetconsistsof2639imagesof249subjects/persons.Ontheotherhand,theCASIA-IRIS-V1datasethas756irisimages from108eyesof54subjects,whiletheMMUdatasetconsistsof450imagesof45subjects.Firstly,oneoriginaliris imagefromRef. [33] isillustratedin Fig.1.9A,whereas Fig.1.9B isthecorrespondingtemplateaftertheapplicationof LBPtoLL3ofsize8 3 64.Forclarity, Fig.1.9C illustratesalargerviewofthefinaltemplateshownin Fig.1.9B.The templateisfurtherreducedtoasizeof1 3 64byapplyingXORoperationthroughcolumnvectors.Secondly, Fig.1.10A C illustrateanotheroriginalirisimagefromRef. [34],itscorrespondingtemplateafterapplyingLBP,and alargerviewofthetemplate,respectively.Thirdly, Fig.1.11A C illustratethesameforanoriginalirisimagefrom Ref. [35]
Theperformanceoftheproposedmethodisevaluatedforthethreedatasetsmentionedabove.Foreachdataset,90% (roundeduptothenextinteger)oftheimagesareconsideredfortrainingwhiletheremainingareconsideredfortesting. Table1.3 presentsthesuccessfulrecognitionrateoftheproposedmethodusingHammingdistanceandEuclideandistance.Theresultsareobtainedonlyforthetestingirisimages.Itcanbeseenfrom Table1.3 thatfortheCASIA-IRISV1dataset,theproposedalgorithmobtainsanaveragecorrectrecognitionrateof98.30%and97.60%forthecaseof HammingdistanceandEuclideandistance,respectively.Therecognitionratesfortheothertwodatasetsareslightly lower,asshownin Table1.3
Next,theproposednewmethodiscomparedwiththeexistingtechniquesreportedintheliterature [3,4,6,16,24] Table1.4 presentsthecomparativeresultsoftheproposedmethodwiththepreviousones.Fortheproposedmethod,
FIGURE1.9 (A)Anoriginaliris imagefromtheCASIA-IRIS-V4 dataset [33],(B)thefinalgeneratediristemplate,and(C)alarger viewofthebinarizedtemplate.
FIGURE1.10 (A)Anoriginal irisimagefromtheCASIA-IRISV1dataset [34],(B)thefinalgeneratediristemplate,and(C)a largerviewofthebinarized template.
FIGURE1.11 (A)Anoriginal irisimagefromtheMMUdataset [35],(B)thefinalgeneratediris template,and(C)alargerviewof thebinarizedtemplate.
TABLE1.2 Descriptionofthedatasetsusedinthiswork.
DatasetImagesSubjectsSensorLightwavelength
CASIA-IRIS-V4(CASIA-Iris-Interval) [33] 2639249CASIAclose-upiriscameraNIR CASIA-IRIS-V1 [34] 75654CASIAclose-upiriscameraNIR MMU(MMU1) [35] 45045LGEOU2200NIR
TABLE1.3 Comparisonofaccuracyoftheproposedmethod.
DatasetSuccessrate
HammingdistanceEuclideandistance
thebestresultsthatareobtainedwiththeHammingdistancemethodusingtheCASIA-IRIS-V1datasetaretakeninto consideration.Inthiscase,thethresholdvalueissetforcomputingFAR,whichistherateatwhichabiometricsecurity systemincorrectlyacceptsanunauthorizeduser,andFRR,whichistherateatwhichthesystemincorrectlyrejectsan authorizeduser.Inotherwords,theFARistheratioofthe numberoffalseacceptances tothe numberofimposterverificationattempts,whereasFRRistheratioofthenumberoffalserejections(NFR)tothenumberof enrolleeverificationattempts.ThisproposedmethodandtheworksinRefs. [3,24] usethesameCASIA-IRIS-V1datasethavingBMP imageswitharesolutionof320 3 280.From Table1.4,itcanbeseenthattheproposedmethodhasaFARof0.003% andFRRof0.80%andanaverageaccuracyof98.30%.Thefeaturevectorlengthandsothecomputationtimeofthe proposedschemeissignificantlylowerthanexistingmethodsreportedinRefs. [3,4,6,16,24].Amongtheresearchworks listedin Table1.4,theproposedmethodhasthesecondbest(lowest)FARpercentage,whiletheworkinRef. [24] reportshavingaFARof0%,butitsgeneratedfeaturevectorlengthisover8.5timesthatofourproposedone.The
TABLE1.4 Comparisonofresultswiththeexistingmethods.
ReferencesFeature
[3] 1 3 15360.021.9898.00CASIABMPformatwithresolution 320 3 280
[4] 1 3 3840.103.5699.85CASIAandModified database Notreported
[6] 1 3 20480.010.0999.90Ophthalmology Associatesof Connecticut ImagesinRS170,VHS(NTSC),andSVHS(NTSC)formatsweredigitized by480 3 640monochrome8-bit/ pixel.
[16] 1 3 2560.032.0897.89Adatabaseofbotheyes of10peopleand,at least,10photosofeach eye. Notreported
[24] 1 3 5460.000.6999.14CASIABMPformatwithresolution 320 3 280
Proposed method (Hamming distance) 1 3 640.0030.8098.30CASIA-IRIS-V1BMPformatwithresolution 320 3 280
extremelylowFAR(0.003%)attainedbyourmethodindicatesitsstrongsecuritycapabilitybynotallowingaccessto imposteriris.AsacomparisontothemethodproposedinRef. [3],whichisahighlycitedworkinthisdomain,our methodoutperformsinallthreeperformancemetricswithahighlyreducedfeaturevectorlength(1/24thoftheformer), makingourmethodhighlysuitableforreal-timepersonidentification.ThemethodinRef. [16] thatproducesafeature vectorlengthclosesttoourmethod(256-bitvs64-bit)showsdegradedperformanceinallthreeperformancemetrics. TheaverageaccuracyoftheproposedschemeisslightlylowerthanthosereportedinRefs. [4,6,24].ThoughRef. [6] reportedthehighestoverallaccuracyamongmethodslistedinthetable,theirfeaturevectorsize(2048-bit)isextremely longandthehighestofallmethods,andthereportedFARishigherthanourmethod.Similarly,themethodinRef. [4], thoughproduceshigheraccuracy,suffersfromthehighestFARandFRRofallmethodsincludingours.Consideringall performancemetricsandtheverysmallfeaturevector,theproposedmethodishighlyattractiveforreal-time applications.
1.8Conclusion
Irisfeatureextractionisanimportantaspectofmanymodernsecuritysystems.Hence,anefficientandfasterapproach isimportantforirisrecognition.Thischapterproposesanew,hybrid,HWTandMLBP basedtechniquetoreducethe featuresizesothattheirisimagescanbematchedfaster.HWTextractsthemostprominentfeaturesoftheiris,reducingthetemplatesize.Inthiswork,athree-levelHWTisappliedtoextracttheregioncontainingthemajorinformation oftheirisimage.Thethree-levelapproximationpartresultingfromHWTisconsideredamajorcharacteristicsregion. Forinstance,therepeatedHWTconvertsa64 3 512normalizedirisimageintoanapproximationimageofsize8 3 64, whichbecomesatemplateofsize1 3 64aftertheapplicationofMLBPandXOR.TheproposedhybridHWTand MLBPalgorithmsareappliedonthreedifferentirisdatasets.Resultsshowthattheproposedmethodreducesthefeature lengthmultipletimeswhencomparedtotheexistingmethodsreportedintheliterature.Thisreducedlengthresultsina reductionincomputationtime.Thisreducedfeaturelengthisatthecostofonlya1%reductionintheaccuracylevel comparedwithsomepreviouslyproposedmethods,butitstillproducesbetterFARandFRRvaluesthansomemethods. Hence,theproposedmethodishighlyattractivefordevelopingafastandreliableirisrecognitionsystem.
Theresultsoftheproposednewhybridmethodhavesomeimplications.Thisworkonlyconsidersthreedatasets,so theresultsmayvarywhenappliedtosomeverylargedatasets.Theresultsmayalsovarywhennoisy,blurred,anddistortedirisimagesaretakenintoconsideration.Inthefuture,irisdatasetswithmoreimageshavetobedevelopedand
theHWT MLBPmethodhastobeevaluatedforthosedatasets.Thecomplexityoftheproposedmethodshouldalso beevaluatedandcomparedwiththeexistingtechniques.DifferentMLanddeeplearningalgorithmscanalsobeeffectivelyusedintheoverallirisrecognitionprocess.Finally,researchisneededtodevelopeffectivebiometricsystemsby combiningirisrecognitionwithotherbiometricfeatures.
References
[1] J.Daugman,C.Downing,Epigeneticrandomness,complexityandsingularityofhumanirispatterns,ProceedingsoftheRoyalSocietyof London.SeriesB:BiologicalSciences268(1477)(2001)1737 1740.
[2]L.Flom,A.Safir,Irisrecognitionsystem.GooglePatents,(1987).
[3] L.Ma,T.Tan,Y.Wang,D.Zhang,Personalidentificationbasedoniristextureanalysis,IEEETransactionsonPatternAnalysisandMachine Intelligence25(12)(2003)1519 1533.
[4] L.Ma,Y.Wang,T.Tan,Irisrecognitionusingcircularsymmetricfilters,ObjectRecognitionSupportedbyUserInteractionforService, Robots2(2002)414 417.
[5] D.M.Monro,S.Rakshit,D.Zhang,DCT-basedirisrecognition,IEEETransactionsonPatternAnalysisandMachineIntelligence29(4)(2007) 586 595.
[6] J.G.Daugman,Highconfidencevisualrecognitionofpersonsbyatestofstatisticalindependence,IEEETransactionsonPatternAnalysisand MachineIntelligence15(11)(1993)1148 1161.
[7] N.Ahmadi,G.Akbarizadeh,Hybridrobustirisrecognitionapproachusingirisimagepre-processing,two-dimensionalgaborfeaturesand multi-layerperceptronneuralnetwork/PSO,IETBiometrics7(2)(2017)153 162.
[8] X.Li,Y.Jiang,M.Chen,F.Li,Researchonirisimageencryptionbasedondeeplearning,EURASIPJournalonImageandVideoProcessing 2018(1)(2018)1 10.
[9]L.Masek,Recognitionofhumanirispatternsforbiometricidentification,Bachelor’sThesis,UniversityofWesternAustralia(2003).
[10] H.Proenca,L.A.Alexandre,Towardnoncooperativeirisrecognition:aclassificationapproachusingmultiplesignatures,IEEETransactionson PatternAnalysisandMachineIntelligence29(4)(2007)607 612.
[11] R.F.Soliman,M.Amin,F.E.AbdEl-Samie,Anovelcancelableirisrecognitionapproach,in:InternationalConferenceonInnovative ComputingandCommunications,Springer,Singapore,2019,pp.359 368.
[12] S.Umer,B.C.Dhara,B.Chanda,Texturecodematrix-basedmulti-instanceirisrecognition,PatternAnalysisandApplications19(1)(2016) 283 295.
[13] Y.Alvarez-Betancourt,M.Garcia-Silvente,Akeypoints-basedfeatureextractionmethodforirisrecognitionundervariableimagequalityconditions,Knowledge-BasedSystems92(2016)169 182.
[14] S.S.Barpanda,B.Majhi,P.K.Sa,A.K.Sangaiah,S.Bakshi,Irisfeatureextractionthroughwaveletmel-frequencycepstrumcoefficients, Optics&LaserTechnology110(2019)13 23.
[15] S.S.Barpanda,P.K.Sa,O.Marques,B.Majhi,S.Bakshi,Irisrecognitionwithtunablefilterbankbasedfeature,MultimediaToolsand Applications77(6)(2018)7637 7674.
[16]D.deMartin-Roche,C.Sanchez-Avila,R.Sanchez-Reillo,Irisrecognitionforbiometricidentificationusingdyadicwavelettransformzerocrossing,ProceedingsIEEE35thAnnual2001InternationalCarnahanConferenceonSecurityTechnology(Cat.No.01CH37186)pp.272-277 (2001).
[17] S.S.Dhage,S.S.Hegde,K.Manikantan,S.Ramachandran,DWT-basedfeatureextractionandradontransformbasedcontrastenhancementfor improvedirisrecognition,ProcediaComputerScience45(2015)256 265.
[18] S.Jamaludin,N.Zainal,W.M.D.W.Zaki,Sub-iristechniquefornon-idealirisrecognition,ArabianJournalforScienceandEngineering43 (12)(2018)7219 7228.
[19]E.G.Llano,M.S.Garcı´a-Va ´ zquez,L.M.Zamudio-Fuentes,J.M.C.Vargas,A.A.Ramı´rez-Acosta,Analysisoftheimprovementontextural informationinhumanirisrecognition,InVIILatinAmericanCongressonBiomedicalEngineeringCLAIB2016,Bucaramanga,Santander, Colombia,October26th-28th,2016(pp.373-376).Springer,Singapore(2017).
[20] K.Miyazawa,K.Ito,T.Aoki,K.Kobayashi,H.Nakajima,Aneffectiveapproachforirisrecognitionusingphase-basedimagematching,IEEE TransactionsonPatternAnalysisandMachineIntelligence30(10)(2008)1741 1756.
[21] A.Nigam,B.Kumar,J.Triyar,P.Gupta,Irisrecognitionusingdiscretecosinetransformandrelationalmeasures,in:InternationalConference onComputerAnalysisofImagesandPatterns,Springer,Cham,2015,pp.506 517.
[22] B.Sahu,P.K.Sa,S.Bakshi,A.K.Sangaiah,Reducingdenselocalfeaturekey-pointsforfasteririsrecognition,Computers&Electrical Engineering70(2018)939 949.
[23] K.Seetharaman,R.Ragupathy,LDPCandSHAbasedirisrecognitionforimageauthentication,EgyptianInformaticsJournal13(3)(2012) 217 224.
[24] C.TeChu,C.-H.Chen,HighperformanceirisrecognitionbasedonLDAandLPCC,IEEE,2005,p.5.
[25] B.Zahran,J.Al-Azzeh,Z.Alqadi,M.-A.AlZoghoul,AmodifiedLBPmethodtoextractfeaturesfromcolorimages,JournalofTheoretical andAppliedInformationTechnology96(10)(2018).
[26] S.Bakshi,P.K.Sa,B.Majhi,Anovelphase-intensivelocalpatternforperiocularrecognitionundervisiblespectrum,Biocyberneticsand BiomedicalEngineering35(1)(2015)30 44.
[27] S.A.Khan,M.Ishtiaq,M.Nazir,M.Shaheen,Facerecognitionundervaryingexpressionsandilluminationusingparticleswarmoptimization, JournalofComputationalScience28(2018)94 100.
[28] S.Kumar,S.Singh,J.Kumar,AutomaticlivefacialexpressiondetectionusinggeneticalgorithmwithhaarwaveletfeaturesandSVM, WirelessPersonalCommunications103(3)(2018)2435 2453.
[29] E.Owusu,J.D.Abdulai,Y.Zhan,Facedetectionbasedonmultilayerfeed-forwardneuralnetworkandHaarfeatures,Software:Practiceand Experience49(1)(2019)120 129.
[30] D.Bhattacharjee,A.Seal,S.Ganguly,M.Nasipuri,D.K.Basu,AcomparativestudyofhumanthermalfacerecognitionbasedonHaarwavelet transformandlocalbinarypattern,ComputationalIntelligenceandNeuroscience2012(2012).
[31]S.Shaju,D.Davis,Haarwavelettransformbasedhistogramconcatenationmodelforfingerprintspoofingdetection,In2017International ConferenceonCommunicationandSignalProcessing(ICCSP),pp.1352-1356,IEEE(2017).
[32] N.Ahmadi,M.Nilashi,Iristexturerecognitionbasedonmultilevel2-DHaarwaveletdecompositionandHammingdistanceapproach,Journal ofSoftComputingandDecisionSupportSystems5(3)(2018)16 20.
[33]CASIA-Iris-V4, http://biometrics.idealtest.org/dbDetailForUser.do?id 5 4,2020.
[34]CASIA-Iris-V1, http://biometrics.idealtest.org/dbDetailForUser.do?id 5 1,2020.
[35]M.U.Database,MMU1andMMU2irisimagedatabases. http://pesona.mmu.edu.my/Bccteo,2008.
[36] M.Oktiana,K.Saddami,F.Arnia,Y.Away,K.Hirai,T.Horiuchi,etal.,Advancesincross-spectralirisrecognitionusingintegrated gradientface-basednormalization,IEEEAccess7(2019)130484 130494.
[37] L.Shuai,L.Yuanning,Z.Xiaodong,H.Guang,C.Jingwei,Z.Qixian,etal.,Multi-sourcefeaturefusionandentropyfeaturelightweightneural networkforconstrainedmulti-stateheterogeneousirisrecognition,IEEEAccess8(2020)53321 53345.
[38] N.Ahmadi,Morphological-edgedetectionapproachforthehumanirissegmentation,JournalofSoftComputingandDecisionSupportSystems 6(4)(2019)15 19.
[39] X.-hChen,J.-sWang,Y.-lRuan,S.-zGao,Animprovedirisrecognitionmethodbasedondiscretecosinetransformandgaborwavelettransformalgorithm,EngineeringLetters27(4)(2019).
[40] Y.Chen,C.Wu,Y.Wang,T-Center:anovelfeatureextractionapproachtowardslarge-scaleirisrecognition,IEEEAccess8(2020) 32365 32375.
[41] M.Danlami,S.Jamel,S.N.Ramli,S.R.M.Azahari,Comparingthelegendrewaveletfilterandthegaborwaveletfilterforfeatureextraction basedonirisrecognitionsystem,IEEE,2020,pp.1 6.
[42] G.Huo,H.Guo,Y.Zhang,Q.Zhang,W.Li,B.Li,AneffectivefeaturedescriptorwithGaborfilteranduniformlocalbinarypatterntranscodingforIrisrecognition,PatternRecognitionandImageAnalysis29(4)(2019)688 694.
[43] R.Jayavadivel,P.Prabaharan,Investigationonautomatedsurveillancemonitoringforhumanidentificationandrecognitionusingfaceandiris biometric,JournalofAmbientIntelligenceandHumanizedComputing(2021)1 12.
[44] A.Noruzi,M.Mahlouji,A.Shahidinejad,Robustirisrecognitioninunconstrainedenvironments,JournalofAIandDataMining7(4)(2019) 495 506.
[45] H.K.Rana,M.S.Azam,M.R.Akhtar,J.M.W.Quinn,M.A.Moni,Afastirisrecognitionsystemthroughoptimumfeatureextraction,PeerJ ComputerScience5(2019)e184.
[46] N.Ahmadi,M.Nilashi,S.Samad,T.A.Rashid,H.Ahmadi,Anintelligentmethodforirisrecognitionusingsupervisedmachinelearningtechniques,Optics&LaserTechnology120(2019)105701.
[47] E.Sujatha,J.S.J.Sundar,P.Deivendran,G.Indumathi,Multimodalbiometricalgorithmusingiris,fingervein,fingerprintwithhybridGA, PSOforauthentication,DataAnalyticsandManagement,Springer,2021,pp.267 283.
[48] R.Vyas,T.Kanumuri,G.Sheoran,Crossspectralirisrecognitionforsurveillancebasedapplications,MultimediaToolsandApplications78 (5)(2019)5681 5699.
[49] J.J.Winston,D.J.Hemanth,Performancecomparisonoffeatureextractionmethodsforirisrecognition,InformationTechnologyandIntelligent TransportationSystems323(2020)62.
Chapter2