
Interview: Anand Subbiah
Specifications Are Passé: Just Show Us Your System To Get The Optimal Solution
Products&Systems
Next-Gen Data Center
Security: AI and Biometrics Advantage


Interview: Anand Subbiah
Specifications Are Passé: Just Show Us Your System To Get The Optimal Solution
Next-Gen Data Center
Security: AI and Biometrics Advantage
We create more than world-leading security solutions, we’re revolutionizing the way organizations around the world protect, secure and manage their people assets and permises.




Command Centre Mobile App









Professional media for complete security solutions
Management
Mahir Hodžić, General Manager mahir.hodzic@asmideast.com
Adis Hodžić, CEO adis.hodzic@asmideast.com
Editorial Staff
Mahir Hodžić, Editor-in-Chief mahir.hodzic@asmideast.com
Orhan Hadžagić, Associate Editor orhan.hadzagic@asmideast.com
Emily Lin, Contributing Editor Emily.Lin@taiwan.messefrankfurt.com
Mirza Bahić, Journalist editorial@asmideast.com
Nermin Kabahija, Journalist editorial@asmideast.com
Art Staff
Sanel Palislamović, Art&Design Editor sanel.palislamovic@asmideast.com
Nelmedin Kolubara, DTP&Art Design dino.kolubara@asmideast.com
Sales Amar Pap, Business Development Manager amar.pap@asmideast.com
International Sales Israel Gogol, International Sales Director Israel.Gogol@taiwan.messefrankfurt.com
International Associates Qatar – Mirsad Selimović, mirsad@techman.qa
a&s Middle East offers the latest news and insights on video surveillance, access control, intrusion detection, fire alarm, mechanical protection, man guarding, cyber security, artificial intelligence, IoT, big data, smart homes and buildings, industrial automation, information, communication technology to Middle East region professional channel players.
a&s Middle East is part of the media network of the Messe Frankfurt Ltd – Taiwan Branch, which offers several media platforms — asmag.com and a&s magazines, published in English, traditional Chinese, and three other languages, providing the most comprehensive industry trends, product, and supply chain information. The total annual circulation is approximately 515,000 copies around the globe. a&s Middle East is published 6 times a year, Jan/Feb, March/ April, May/June, July/August, Sept/Oct, and Nov/Dec.
Payment Instructions
Annual subscriptions are payable in USD, EUR, or AED. Subscription inquiries per your request.
EUR: AE340400000653005131002
Account No. 0653005131002
USD: AE070400000653005131003
Account No. 0653005131003
AED: AE610400000653005131001
Account No. 0653005131001
Copyright Statement
© Copyright by Privus Agency Ltd. All rights reserved. Any republication, copying, redistribution, or reproduction of the magazine in any form, including electronic, without the prior written consent of the publisher, is prohibited. Advertisers are solely responsible for the content of advertising material. The publisher bears no responsibility regarding possible legal, patent, content, or brand disputes of the advertiser.
Legal disclaimer
The information in this magazine has not undergone any formal testing by Privus Agency Ltd. and is distributed without any warranty expressed or implied. Implementation or use of any information contained herein is the reader’s sole responsibility. While this information has been reviewed for accuracy, there is no guarantee that the same or similar results may be achieved in all environments.
Corporate Address
Privus Agency FZ-LLC
JT010006, Al Shohada Road, Ras Al Khaimah, UAE
Tel: +971 58 983 4258
Web: www.asmideast.com
Marketing: marketing@asmideast.com
Welcome to the latest edition of a&s Middle East, where we embark on yet another journey of discovery within the realm of security. In this issue, we delve into diverse facets of security technology and trends that are reshaping the ever-shifting landscapes of the industry in our region and beyond.
Our cover story features an exclusive interview with Anand Subbiah, Regional Director at Secure Logiq. Delving into Secure Logiq’s pioneering approach to crafting custom hardware solutions tailored for HD surveillance, Anand underscores the transformative impact of innovative designs on advancing security infrastructure.
We also explore critical topics such as easy digital access management in healthcare facilities, highlighting the imperative need for streamlined security solutions that ensure both efficiency and reliability.
Additionally, our focus shifts to the next generation of data center security, where biometrics and AI converge to safeguard sensitive information and infrastructure with the next-gen precision.
Last but by no means least, we shine a spotlight on Intersec Saudi Arabia, poised for its largest event yet in 2024. As Saudi Arabia’s premier trade fair for safety, security, and fire protection, this event continues to lead the region in fostering dialogue and innovation within the security industry.
As a&s Middle East aligns with Intersec Saudi Arabia’s mission of advancing security innovation, we find ourselves on a joint mission to first discover and then redefine the boundaries of industry excellence. By doing this together, we aim to propel the industry forward, by forging strategic partnerships to meet evolving security challenges head-on together.
Let our latest edition remind us of this joint endeavor on a quest to celebrate where our industry stands now and pioneer where it will excel in the future.
Please visit our official website www.asmideast.com and select ‘Subscribe Now’ option under THE MAGAZINE menu.
Subscription includes all six editions.
Digital edition is FREE and readily available at the official website.


The Abu Dhabi Artificial Intelligence and Advanced Technology Council (AIATC) and the French Ministry of Economy, Finance and Industrial and Digital Sovereignty jointly signed a Memorandum of Understanding on artificial intelligence (AI).
This agreement builds on the strengths of the strategic partnership between the UAE and France and aims to develop the artificial intelligence ecosystems of both countries through a combination of investment programmes and collaborations that foster the responsible development and deployment of AI.
The agreement was signed by Khaldoon Khalifa Al Mubarak, Chairman of the Executive Affairs Authority, member of the Abu Dhabi Executive Council and member of AIATC, and Bruno Le Maire, French Minister of Economy, Finance and Industrial and Digital Sovereignty.
The partnership will cover the following areas of collaboration: Data centre and supercomputing infrastructure buildout: This initiative will make cost-competitive AI training and inferencing capacity available to both French and European enterprises, as well as foster partnerships with international and local cloud and computing capacity operators to enable innovation and R&D.
Investment in the UAE, French, and global AI ecosystem: The UAE and France will explore investment opportunities in startups and investment funds focused on AI models, artificial in -

telligence applications in key sectors (health, financial services, software, retail, industry), and next-generation hardware. Manufacturing and sourcing cooperation: The partnership will explore opportunities for the bilateral production and offtake of semiconductors, including leading-edge and essential chips for AI applications.
Talent pipeline: The two countries will explore an education initiative to offer best-in-class AI training to nurture and develop talent across the UAE and French AI ecosystems. n

Under the patronage of His Royal HighMoro Hub, a subsidiary of Digital DEWA, the digital arm of Dubai Electricity and Water Authority (PJSC), signed an agreement with National Security Services Group (NSSG), Oman’s leading cybersecurity services provider, to introduce innovative Smart City and IoT solutions across Oman. This collaboration marks a significant milestone in both companies' efforts to revolutionize urban living and drive digital transformation in the region. The
agreement was signed by Arif Almalik, Chief Digital Products Officer of Moro Hub and Hamza Al Jaafari, Chief Technology Officer of NSSG.
The partnership aims to explore cutting-edge solutions tailored to enhance the infrastructure and efficiency of cities in Oman. In addition, the engagement underscores the client's keen interest in leveraging Moro Hub's state-of-the-art technologies to address their evolving needs and aspirations.
“We are pleased to associate with NSSG advancing Oman's digital landscape. Our collaboration represents more than just a partnership; it's a commitment to empowering communities, revolutionizing infrastructure, and fostering sustainable growth. Together, we stand at the forefront of innovation, harnessing the power of Smart Cities to redefine urban living and elevate the quality of life for citizens across Oman. With our combined expertise and unwavering dedication, we are set to unveil limitless possibilities, driving progress and prosperity for generations to come. This initiative exemplifies Moro Hub's core values of innovation, collaboration, and excellence, as we continue to push the boundaries of what's possible in the digital age,” said Mohammed Bin Sulaiman, CEO of Moro Hub. n

Saudi Arabia is set to become the world’s largest construction market, thanks to a slew of ambitious projects transforming the nation’s landscape. This boom in development is not just a catalyst for the
construction industry but also significantly boosts the security systems sector.
Major projects such as the NEOM smart city, the Red Sea Project, and the King Salman Energy Park require advanced

security solutions to protect assets and ensure safety. These mega-projects demand cutting-edge technologies in surveillance, access control, and cybersecurity, driving significant investment and innovation in the security systems industry.
The integration of state-of-the-art security technologies is essential to the successful execution of these projects. As a result, security system providers are witnessing increased demand for sophisticated solutions, including AI-driven surveillance, biometric access control, and integrated security management platforms
Industry experts predict that this trend will continue as more projects commence, making Saudi Arabia a key market for security technology providers globally. The focus on enhancing security measures reflects the Kingdom’s commitment to ensuring a safe and secure environment for its ambitious development plans.
This surge in the security systems industry is also expected to create numerous job opportunities and foster technological advancements, further cementing Saudi Arabia’s position as a leader in both construction and security innovation. n
Dubai Department of Economy and Tourism (DET) appointed Dr. Marwan Alzarouni as its chief executive officer of AI. This step is seen as a strategic move to galvanize the artificial intelligence projects ahead.
This appointment is a pivotal step in advancing Dubai’s AI blueprint, aimed at enhancing the quality of life for its residents and enriching the experiences of its visitors, said DET.
This announcement follows a directive by Sheikh Hamdan bin Mohammed bin Rashid Al Maktoum, Crown Prince of Dubai and Chairman of The Executive Council of Dubai, who recently declared the appointment of 22 chief AI officers across various government entities in Dubai.
Dr Alzarouni expressed his vision for Dubai’s AI future, emphasising the impact on everyday life, “Our AI initiatives are dedicated to prioritising the well-being and experiences of Dubai’s residents and visitors.”
“By harnessing advanced technologies, we strive to create a smarter, more sustainable, and enjoyable urban environment. Every innovation we introduce is designed to directly contribute to improving the daily lives of our community.” n


The Kingdom of Saudi Arabia has achieved the top global ranking in the cybersecurity indicator, as reported in the 2024 World Competitiveness Yearbook by the Swiss-based Institute for Management Development (IMD).
Dr. Musaed Al-Aiban, Chairman of the National Cybersecurity Authority (NCA) Board of Directors, congratulated the Saudi leadership on this accomplishment. He emphasized that this recognition affirms the country’s leading role in international cybersecurity and its dedication to Saudi Vision 2030.
Dr. Al-Aiban credited the success to the continuous guidance of His Royal Highness Prince Mohammed bin Salman bin Abdulaziz Al Saud, Crown Prince and Prime Minister, whose vision has established the Kingdom as a global model in various sectors.
He highlighted the strategic development of the cybersecurity sector in Saudi Arabia, driven by Vision 2030. This development addresses both security and growth, focusing on domestic and international dimensions. The Saudi model has become a pioneer in the field, attracting global attention. The National Cybersecurity Authority serves as the central authority, with the Saudi Information Technology Company (SITE) acting as its technical arm.

The NCA attributes the Kingdom’s rise in cybersecurity rankings to its efforts on both local and international fronts. This includes the launch of the Global Cybersecurity Forum (GCF), a platform for global dialogue on strategic cybersecurity issues, and the GCF Institute, which promotes international collaboration. n
Ooredoo Group today announced it is becoming an NVIDIA Cloud Partner (NCP), aligned with its strategy of becoming the leading digital infrastructure provider in the MENA (Middle East and North Africa) region. Through this collaboration, Ooredoo is leveraging NVIDIA’s advanced accelerated computing platform to help enable the AI revolution in the region.
Capitalising on the significant market demand for accelerated computing and hyperconnectivity across its MENA footprint, Ooredoo is developing an AI-ready platform powered by NVIDIA’s full-stack innovation across systems, software, and services. This platform will serve as a valuable resource, supporting governments and empowering enterprises and startups to securely process their private datasets, as well as produce valuable insights as tokens that power innovations for its users.
Aziz Aluthman Fakhroo, Group CEO,
Ooredoo, said: “Implementing NVIDIA’s full-stack platform for accelerated computing and generative AI,
as the leading digital infrastructure provider in the region. Working with NVIDIA, we aim to meet the signifi -

Ooredoo is equipped to be at the forefront of the AI revolution in MENA, driving digitalisation and innovation
cantly growing demand for accelerated computing infrastructure to support advanced AI models.” n
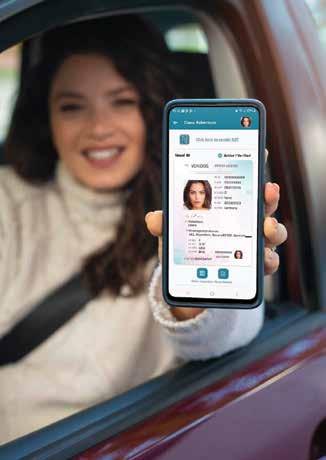
With VeriGO MobileID, users can carry all their important ID documents wherever they go – digitally, securely and conveniently. Government authorities can now offer their citizens a modern and convenient way to manage all government documents on their smartphones. The goal is to create a new level of security for public and private use cases through efficient and digital verification processes.
Whether checking into a hotel, travelling or renting a car, verifying one’s identity with official ID documents is an integral part of our everyday lives. Instead of continuing to rely solely on physical documents and their security features for identification, VeriGO MobileID’s innovative technology relies on unique encryption processes that allow the authenticity of a document to be verified quickly, easily and electronically.
Designed as a mobile-first solution, the application requires only a smartphone or tablet and is not dependent on an internet connection. With VeriGO MobileID, users can conveniently store all forms of traditional physical ID documents such as driver’s licenses, health insurance cards or ID cards in a secure environment. Veridos presents a comprehensive digital solution that combines all types of digital proof of identity and is available to users anytime, anywhere. n
The Saudi Data and Artificial Intelligence Authority (SDAIA) announced a major advancement for the Arabic language at the ongoing IBM Think event in Boston: its ALLaM

model, which generates Arabic text, has been integrated into the IBM watsonx platform, recognized as one of the world’s leading models.
This inclusion highlights the advanced technical capabilities of the ALLaM model. During its experimental phase, the model underwent rigorous testing against international standards for generative AI to ensure its readiness to compete with other models on watsonx, a platform widely used by developers globally.
Currently available in a trial version, ALLaM’s integration into watsonx allows for further professional evaluation. This testing will be crucial in accelerating the release of the model’s full capabilities and establishing it as a highly competitive force in Arabic language generation.
This inclusion also aligns with Saudi Arabia’s, specifically SDAIA’s, broader mission to serve and empower the Arabic language on both regional and global scales. The efforts focus on preserving the integrity of the language while promoting its use by enriching Arabic content across various fields, including technical, cultural, literary, scientific, and other humanities-based domains.
Ultimately, this initiative aims to leverage AI technologies and digital applications to foster cultural diversity and benefit all humanity, regardless of language, nationality, or educational background. n
The UAE’s Artificial Intelligence, Digital Economy, and Remote Work Applications Office and Samsung Gulf Electronics have signed a Memorandum of Understanding (MoU) to collaborate on driving artificial intelligence adoption and development in the UAE. The signing of the Memorandum of Understanding came as part of the efforts of the Artificial Intelligence, Digital Economy, and Remote Work Applications Office to achieve the targets of the UAE’s Artificial Intelligence Strategy and its ambitious goals to establish the UAE’s global leadership in the field of artificial intelligence by 2031. It also aligns with Samsung’s objectives and efforts in this field, through joint work to use the capabilities of artificial intelligence to enhance economic growth, contribute to sustainable development, and improve the well-being of life in communities.
Saqr binghalib, the Executive Director of the UAE’s Artificial Intelligence, Digital Economy, and Remote Work Applications Office, and Seong H Cho, President

of Samsung Electronics MENA, signed a Memorandum of Understanding during the activities of the “AI Retreat 2024,” organized recently by Dubai Center for Artificial Intelligence (DCAI) in collaboration with the National Program for Artificial Intelligence.
Saqr binghalib affirmed that expanding
partnerships between the government and the private sector represents an important factor in achieving the visions and directions of the UAE government. This aims to solidify the UAE’s position as a leading global destination in the field of artificial intelligence. n
The Cyber Security Council has launched the “Ethical Hacker” specialised training course as part of the training programmes under the “Cyber Sniper” initiative, which the council launched last year in partnership with the Federal Authority for Government Human Resources.
The Cyber Sniper initiative is a key element of the council’s comprehensive strategy to secure the country’s digital infrastructure, support secure digital transformation, and increase government entities’ readiness to address emerging cyber threats and develop their capabilities to counter them.
The Ethical Hacker course aims to equip participants with the knowledge and skills necessary to understand cyber-attack methods and techniques, and how to test information systems and networks for vulnerabilities (security gaps) before hackers can exploit them.
It also aims to equip participants with advanced penetration testing tools and programmes and best practices for ensuring the security of information systems and networks.
Dr. Mohamed Hamad Al Kuwaiti, Chairman of the UAE Cyber Security Council,
emphasised that the Cyber Sniper initiative embodies the country’s unwavering commitment to being a global leader in cyber security. He added, “This initiative contributes to building a strong national workforce in the field of cyber security,
capable of protecting the nation’s critical infrastructure and effectively countering evolving cyber threats.”
This training is conducted with leading international cyber security partners such as SANS, EC-Council, and Offsec. n



Control iD, part of ASSA ABLOY, is a leading developer of hardware and software solutions for access control and time & attendance. The products are developed with modern designs, latest equipment incorporating most advanced features for identification and commercial automation, providing maximum security against vulnerabilities. Learn more


Kelly Gill, Chief Technology Officer at ASSA ABLOY Opening Solutions EMEIA, discusses the critical role of mechanical technology as an enabler for the latest innovations in digital access
A rapid process of digitalization in access and security technologies is underway. But electronics are not a replacement for – but a complement to – robust, secure, trusted mechanical design.
Growing demand for convenience, connectivity and new functionality continuously extends the power and level of choice in access devices. Digitalization is a key enabler of more comfortable and tailored access solutions in both residential and commercial buildings.
Yet the necessity for innovations in mechanical design remains as great as ever. Why? Because all new digital locking functionality must be backed up by intelligently designed, secure mechanical elements. It is not the electronics that keep a door bolt in position, but rather the lock’s physical components.
and security work together
The digital components of many ASSA ABLOY solutions are designed to enhance usability and convenience. For example, they replace the need to carry a heavy keychain by providing a programmable credential – card, key or

But to be fully effective, every digital locking device requires the electronics and mechanical security to work in tandem. If the mechanical part of the lock is flawed, the door can be opened regardless of its digital security.
smartphone – which can unlock several openings. In the event of a lost a key or card, the digital element enables easy disabling of those access rights, eliminating the need to replace keys and cylinders. This saves management costs, time and hassle.
But to be fully effective, every digital locking device requires the electronics and mechanical security to work in tandem. If the mechanical part of the lock is flawed, the door can be opened regardless of its digital security. This is where access providers with a strong heritage in mechanical manufacturing have the edge in our rapidly digitalizing market. Many components within a digital access device are and will remain mechanical. Authentication and authorization will continue transitioning to digital, clearly, but internal mechanics must keep the door locked and the space secure.
An additional convenience benefit, digitalization also enables seamless integration with complementary products and solutions: in a domestic setting, with smart doorbells, security cameras and intruder alarms; in the workplace, with a range of business-critical systems from time-andattendance software to complex smart building management systems.
This interaction between digital and mechanical technology is fundamental in future-proofing homes and businesses – far beyond just their security.

Agreed standards help customers make an informed decision. They provide a scale to make comparisons – for example, from high to low security needs. As a long-time industry leader, ASSA ABLOY Opening Solutions takes an active part in driving independent standards to a higher level, to ensure customers have access devices with mechanical and digital components which deserve their trust. Our inhouse testing labs push every device and component to its limit, long before it ever reaches the market.
A growing focus on security standards is also evident in the realm of IoT devices, where data breaches and cyber-attacks
are increasingly common and potentially costly. In 2023, IBM estimated the average cost to a business of a data breach at more than 4m EUR.
In response to increased risk, supra-national regulators such as the European Union have begun promoting more robust cybersecurity measures, including to regulate the security of all products with digital components. Very soon, companies which want to sell into the EU market must show that their product meets basic cybersecurity requirements. PSTI has been introduced in UK law to set security standards for IoT devices.
This higher profile for standards will help ASSA ABLOY and our industry peers to better communicate security benefits,
risks and best practices. A commitment to developing secure products, both their mechanical and digital elements, is quickly repaid by customer peace of mind.
All over the world customers rely on ASSA ABLOY – whether that’s the new Tekirdağ City Hospital which needed a large mechanical master-key system for multiple types of locking point; or Helsinki Airport selecting digital solutions for doors and cabinets to integrate with existing access management software.
Experience gained in designing and manufacturing mechanical solutions for all types of application is an essential ingredient. It fosters and supports the digital innovation that customers increasingly rely on. n

In an exclusive chat with a&s Middle East, Anand Subbiah, Regional Director at Secure Logiq, explores the company’s pioneering approach to crafting custom hardware solutions tailored for HD surveillance, emphasizing their innovative designs and substantial impact on advancing security infrastructure within the industry

n By: Mirza Bahić editorial@asmideast.com
a&s Middle East: Could you share your educational and professional background that led to joining Secure Logiq and describe your current role as Regional Director within the company?
Subbiah: The original three founders of Secure Logiq were an electronic engineer, an IT specialist, and an industry veteran sales professional. Collectively, they had been involved in the electronic security industry for a cumulative 50 years, even back in 2011, and this extensive experience was probably the most important differentiator for Secure Logiq. First and foremost, we are all seasoned video experts who also possess a deep knowledge of specialist IT solutions. We don’t just understand the IT hardware we supply, but the entire electronic security infrastructure surrounding it.
Personally, I joined Secure Logiq in 2022 with 35 years of industry experience. By that stage, I had known and worked with one of the original founders for over 30 years. When he approached me and asked if I would set up the Middle East operation for them, I jumped at the chance, having observed their success in the UK and Europe over the previous 10 years. The rest is history.
a&s Middle East: What inspired Secure Logiq to specialize in developing servers specifically tailored for HD surveillance and how has this innovation impacted the industry?
Subbiah: Before Secure Logiq, the Sales Director at the time, Robin Hughes, had been very successful in bringing a startup end-to-end HD surveillance solution to the market across EMEA. The other two founders were his customers at the time. Robin observed that this customer would buy cameras and VMS software but never the server hardware. Eventually, he asked them why and was told, “You are doing it all wrong. We make our own servers that have 16 times the throughput and 25 times the storage of your rebadged IT-centric servers, meaning we use less IT hardware to do the same job, resulting in lower CAPEX and OPEX.” They soon decided that this was a business opportunity and Secure Logiq was born. Since then, Secure Logiq has grown organically and remains 100% employee-owned. No one else was doing it. As they grew, they realized just how powerful offering pre-and post-sales support from experts in electronic security was—a resource that was entirely missing from the CCTV industry, often filling a gap in skillsets within the electronic security industry at the time. A large part of what we do is educating the market. Our motto is, ‘Don’t come to us with a specification; come to us with your system design and we will design the optimum hardware solution for you.’
a&s Middle East: Could you provide insights into the Middle East market for HD surveillance technologies? How does Secure Logiq approach this region in terms of business strategy and market adaptation?
Our strategy remains the same: where we can, we educate and add value over a simple dollarper-TB pricing structure
Don’t come to us with a specification; come to us with your system design and we will design the optimum hardware solution for you
Subbiah: As we saturated the UK market, the Middle East was the obvious next target for us. Simply put, the systems there are bigger and retention periods are significantly longer than anywhere else in the world. This ultimately means that the projects and therefore individual sales, are significantly larger. We always knew it was a different and difficult market and we have seen this as many of our competitors have withdrawn from the region in recent years. Pricing structures must be different. Success in the UK and Europe has been achieved through an education process, which we are also striving to bring to the Middle East. However, this takes time and is much harder in the region due to many projects being specification-driven and difficult to change. Because of the exponential growth in the region, many projects have long lead times and we are often asked to specify a solution before building works have even begun. Our strategy remains the same: where we can, we educate and add value over a simple dollar-per-TB pricing structure. We knew we had to open an office here to be taken seriously and rapidly expanded to six staff in the region in our first year.
We realized that many technology partners in the region did not have a physical office, so we designed our new premises with this in mind. We have six hot desks for technology partners to use when they are visiting and they have full use of our high-tech demonstration suite. The advantage of this is that we get to meet every customer they bring in and introduce ourselves as their hardware partner of choice. So far, this strategy is working out really well and naturally builds trust with our technology partners and their customers too.
a&s Middle East: Looking forward, what innovations or developments is Secure Logiq focusing on to meet the evolving needs of the security industry, both globally and in specific regions like the Middle East?
Subbiah: Again, our specialty is understanding the leading technologies in both the electronic security and IT markets and bringing them together to create solutions never seen or proposed in our industry. Specifically, the technologies we bring to the market are the highest-performance and highest-density storage servers in the industry. However, we are a systems house and understand that our technologies, when teamed with other IT industry technologies, can offer a better overall solution. For instance, particularly in the Middle East, there is a tipping point where external storage such as SAN or NAS offers a more costeffective and environmentally friendly solution.
Another area of specialty for us that is beyond the comprehension of most IT-centric hardware suppliers is advanced failover models for VMS and Video Analytics solutions. We can offer High Availability and even Fault Tolerant solutions, even when our software partners said it couldn’t be done! Many customers are wary of these advanced solutions, but the main advantage of purchasing from Secure Logiq is that all solutions are prebuilt and configured in our manufacturing facility so that they are ready to install out of the box.
Of course, globally, environmental concerns are at the forefront of many purchasing decisions and this is something we take very seriously. We find that documenting the rack space, power, cooling, and carbon savings that we make over our competitors’ solutions really does make a difference.
a&s Middle East: What are the primary advantages of using servers optimized for HD surveillance over traditional IT-centric solutions?
Subbiah: To put it simply: we know what we’re doing, we don’t just understand the server hardware side but the entire infrastructure that is being installed. Unlike traditional IT vendors, our principle is: ‘Don’t come to us with a specification, come to us with your operational requirements and we will design the optimal solution for your application.’ An optimized solution is where we, as the experts, look at the overall system parameters and provide the most effective solution, meeting or exceeding expectations while often massively reducing the total hardware footprint. We achieve this either by utilizing more powerful, high storage density solutions or, for example, by integrating multiple applications into the same hardware.
Our specialty is understanding the leading technologies in both the electronic security and IT markets and bringing them together to create solutions never seen or proposed in our industry
For instance, our design team might suggest integrating the Access Control, PSIM, Analytics, and CCTV management layer into a single layer with added fault tolerance. Instead of having four separate servers running each application, each of which could fail with disastrous consequences, we supply just two servers and guarantee 99.999% uptime. We understand that most electronic security applications are mission-critical and the importance of maintaining the video archive, camera and system settings, software licensing, and many other factors that simply don’t occur in an IT-focused environment.
both CAPEX and OPEX for Petabyte-scale storage retention. This led us to delve into Storage Area Network (SAN) and Network Attached Storage (NAS) solutions.
Recording retention periods are generally dictated by customer requirements and managed by the Video Management System (VMS). However, if we handle the storage calculations, they are backed by the Secure Logiq Design Guarantee. Should there be any shortfall in recording duration or processing needs, we commit to covering it at our own expense. This guarantee serves as a compelling reason to entrust us with design tasks, saving integrators’ design teams significant time.
a&s Middle East: Can you discuss the RAID architectures Secure Logiq utilizes to enhance data resilience in surveillance applications and the benefits of these configurations?

Subbiah: So, without revealing too much, RAID cards within a server serve two primary purposes. Firstly, they efficiently distribute video images across multiple hard disks. When correctly configured with suitable HDDs, this capability is crucial in achieving performance figures significantly higher than those of our competitors.
a&s Middle East: How does Secure Logiq address the varying global regulations on recording lengths to ensure sufficient storage capacity for HD surveillance recordings?
Subbiah: We already had the highest storage density servers in the industry, offering over 1.5 Petabytes of storage in a single 4U Direct Attached Storage (DAS) server. This capability was well-suited for most IP CCTV applications in the regions where we operated. In practice, processing overhead often became a limiting factor before the storage capacity could be fully utilized. As we explored the potential in the Middle East, we recognized that storage retention times were significantly longer compared to other regions. Typically, CCTV footage is retained for 7 days in the EU, 30 days in the UK, and up to 180 days in the Middle East. We identified scenarios where exploring alternative storage technologies beyond DAS could offer greater efficiency in
Secondly, as you noted, RAID cards are essential for safeguarding data in the event of HDD failure. Considering that HDDs are the only moving parts in servers and are subjected to rigorous use in CCTV applications, they are inevitably prone to failure regardless of their quality. In some cases, RAID configurations are dictated by integrators or even by legal requirements in the Middle East. While we can provide any RAID configuration, our default setup prioritizes Value, Performance, and Risk Optimization.
The likelihood of disk failure increases with the number of disks, which raises concerns about resilience and rebuild times. The rebuild process, which is the most intensive phase for a server, occurs while it continues to perform its primary duties and other data-intensive tasks. In our system designs, we always account for this factor. For larger servers with 36, 60, or even 104 drive bays, we mitigate this risk by splitting RAID formations into multiple arrays and employing multiple RAID cards. For large-scale projects, we often opt for SAN solutions because

they allow us to move away from traditional RAID configurations and leverage advanced technologies like ADAPT. ADAPT enhances rebuild times with more HDDs, which contrasts with RAID where more disks can prolong the rebuild process.
a&s Middle East: How does Secure Logiq’s “Power of Partnerships: Intelligent Integration” initiative contribute to enhancing security system performance through effective hardware and software integration?
Subbiah: Our partnerships are more than mere checkboxes; we take them seriously. When we initiate a partnership, we rigorously test solutions together. This approach not only helps us minimize the hardware footprint but also makes the combined hardware and software solution more cost-effective per channel. Our technology partners require reliable hardware they can trust, which significantly reduces their support needs. Moreover, communicating with technical support teams who understand the application further enhances reliability.
a&s Middle East: Can you elaborate on Secure Logiq’s approach to ensuring high performance and reliability in its HD surveillance servers, especially in demanding environments?
Subbiah: We design solutions tailored to specific applications. Our portfolio includes ruggedized, extreme-temperature, lowpower, mobile, vibration-proof, and even water-cooled solutions—essentially everything except laptops and quantum computing. While servers should ideally be installed in a suitably cooled environment, we prioritize understanding our customers’ applications to craft appropriate solutions.
As we saturated the UK market, the Middle East was the obvious next target for us
a&s Middle East: How does Secure Logiq collaborate with leading IP camera and VMS providers to optimize compatibility and performance with your server solutions?
Subbiah: We value our technology partnerships immensely. Communication and thorough testing are at the core of our approach. Through continuous online and in-person training, our technical and design teams stay abreast of the latest advancements in the market. This commitment distinguishes us from traditional IT-centric suppliers.
Initiatives like the Axis Communications TIP program and Milestone Marketplace assure our customers that our hardware is endorsed and recommended by industry leaders.
a&s Middle East: What are the key challenges you foresee in the future of HD surveillance technology and how is Secure Logiq preparing to address these challenges?
Subbiah: Interestingly, the challenges are not only industry buzzwords but also focal points for investment in the industry. While there is significant discussion surrounding ‘the cloud,’ the reality in large-scale Enterprise CCTV solutions includes ongoing challenges with connectivity, likely persisting for years to come. Recently, we have collaborated with multiple cloud solution providers to facilitate their business growth by establishing truly hybrid solutions, which many users are likely to adopt as a compromise in the foreseeable future.
Another critical issue in this IP-connected era is cybersecurity. Despite CCTV originally meaning ‘Closed Circuit TV,’ such closed systems are rare today. Based on our experience, once a solution is network-connected and secured with endpoint protection, users typically prefer to implement their own practices and protocols to defend against cyber threats.
a&s Middle East: Secure Logiq emphasizes resilience as one of its core principles. Could you explain how your servers achieve resilience beyond RAID configurations, such as in power redundancy and system monitoring?
Subbiah: We don’t take risks. All Secure Logiq servers include 5 layers of resilience as standard, often offered as optional upgrades elsewhere. Our Enterprise servers feature dual redundant power supplies, battery-backed RAID cards tailored to the application, operating system, and application separation on mirrored solid-state disks (SSDs), and our proprietary, complimentary health monitoring software, Logiqal Healthcheck Pro. Additionally, we have extensive expertise in failover options. Our software development team has crafted a cost-effective High Availability solution compatible with any electronic security application. For higher resilience needs, we integrate third-party solutions like Stratus everRun.
The advantage of choosing us lies in our understanding of your goals. Instead of merely delivering a product, we prebuild and preconfigure the hardware and software for immediate use out of the box.
a&s Middle East: Can you share a case study or success story where Secure Logiq’s solutions have made a significant impact on a client’s surveillance operations?
Subbiah: One notable example is the Abraj Al-Bait, a govern-

ment-owned complex of seven skyscrapers spanning over 1.5 million square meters in Makkah, Saudi Arabia. They were early adopters of IP CCTV, but technology has evolved significantly since the original installation. Our regional partners, VNS, replaced over 100 Network Video Recorders with just 11 super high-density storage servers in a single rack. This change drastically reduced power and cooling requirements while enhancing resilience and performance. Additionally, they integrated Video Analytics capabilities from the Netavis software suite.
a&s Middle East: How has the increase in demand for GPUs affected Secure Logiq’s manufacturing processes and product offerings, particularly in relation to video analytics and high-resolution camera solutions?
Subbiah: GPUs are among the fastest-evolving technologies our planet has witnessed. They are designed for a multitude of applications such as gaming, crypto mining, displaying increasingly high-resolution image streams across multiple monitors, and of course, AI, Video Analytics, and machine learning. The GPU market can be highly volatile, especially due to price fluctuations in cryptocurrencies, causing high-end GPUs to become scarce and expensive at times.
Unlike CPUs, which excel at executing a sequence of tasks quickly, GPUs are optimized to handle multiple small tasks simultaneously. However, in most cases, no single application fully utilizes all available resources. Without divulging too much, our Product Development team is actively collaborating with technology partners to test a new generation of alternative hardware known as ‘AI accelerators,’ specifically designed for video analytics applications. These accelerators promise to process many more streams of HD video at a fraction of the cost of a GPU.
Achieving cost-effectiveness in video analytics hinges on minimizing hardware expenses to meet objectives. Software pricing, once developed, can be adjusted to some extent and is
Our partnerships are more than mere checkboxes; we take them seriously
unaffected by component availability and price fluctuations. Hardware, however, represents a fixed cost that naturally depreciates over time.
a&s Middle East: Considering the advancements in camera technology and the need for more powerful client hardware, how does Secure Logiq anticipate future trends in surveillance technology, both in terms of hardware requirements and market demand?
Subbiah: Interestingly, this can often be the weakest link in many Enterprise CCTV projects. As camera resolutions and frame rates increase and compression technology adapts to meet these demands, the decompression (and display) of camera streams is frequently overlooked. Some Video Management Software solutions incorporate sophisticated image scaling and stream management options, yet a commercial off-the-shelf desktop PC is often chosen as the user-facing interface for the solution. Such PCs were not designed to consistently decode multiple streams of HD video 24/7, which can lead to poor and irregular image quality that does not accurately represent the captured images stored in the solution.
Our advice is to procure end-to-end hardware solutions from experts who understand your application. If they don’t inquire about your VMS and display requirements, consider exploring other options.
a&s Middle East: What role does Secure Logiq’s free design service play in the customization and deployment of surveillance

solutions? Can you share examples where this service has led to innovative solutions for your clients?
Subbiah: We continually analyze the market to maintain a competitive edge. While we have always provided detailed explanations of our solutions, in 2021 Secure Logiq made a significant investment in a dedicated design department and introduced our design guarantee. Unlike competitors who offer itemized breakdowns of quoted hardware, we provide detailed system schematics. These include power, cooling, and rack space requirements, connectivity, and networking specifications, comprehensive recording schedules itemized per camera, and a complete technical submission for customer review.
This approach allows customers to confidently create tender submissions, enhancing their trust and securing orders. The impact of an IT-savvy customer understanding the complexity of our solutions cannot be overstated. We take great pride in having our servers installed in over 300 data center security systems worldwide, all of which are exclusively filled with IT-centric servers!
We have the highest performance and highest density storage servers in the industry
a&s Middle East: Finally, looking at the broader industry landscape, what trends do you believe will shape the future of HD surveillance over the next five years, both globally and regionally?
Subbiah: Cause and effect are crucial, thus our focus on ‘The Power of Partnerships’. AI and video analytics will undoubtedly gain stronger traction, but there will be casualties—many new entrants lack industry insight despite substantial investments. Enhanced integration with VMS platforms (now increasingly offering built-in analytics) promises improved solutions at reduced hardware costs.
The cloud is currently oversold; widespread adoption within the next 5 years seems unlikely, but possibly within 15. Ultimately, integration remains pivotal. A single, seamless interface for managing CCTV, alarms, fire, access control, and BMS enhances safety and security. This unified approach simplifies monitoring and performance, reduces CAPEX, and OPEX, and minimizes business interruption incidents. Who wouldn’t see the value in that? n

In our previous issue, in the article “Roadmap To Compliance: Bosch And VdS Decipher EN 54 & NFPA 72 Standards,” we published an incorrect paragraph quoting Onur Sönmez, Head of Sales and Marketing, Bosch Fire Alarm Systems, Türkiye, Middle East and Africa. The paragraph that was mistakenly published is as follows:
“The product serves as an all-in-one solution, providing a comprehensive range of functions in a single package. It incorporates an addressable aspiration system, enabling precise detection and monitoring capabilities. Additionally, integration with third-party systems is supported, facilitating seamless connectivity with existing infrastructure. Soft addressing functionality offers flexibility in device identification and configuration, enhancing user convenience. Each device includes a built-in isolator, contributing to system reliability and resilience. Furthermore, the system allows for a significant number of devices to be connected on a single loop, making it suitable for larger installations with efficient utilization of resources. On top of the product features, we also have good delivery times, less commissioning time compared to UL solutions, competitive pricing, and extra warranty.”
functionality. It means that the panel meets several UL functional requirements such as audible distinguishing of fire & fault signals, signaling line circuit

exceed them offering extraordinary robustness in the 10-50kHZ frequency range and live measurements of the EMC value in the field. That results in high reliability and reduces the total cost of ownership, minimizing false alarms.
Our signaling devices frequently offer ISO 8201 driven signaling tone and come with luminous intensity information (cd) that let the planners easily follow NFPA 72 requirements. Additionally, many of them offer a unique power supply concept, meaning built-in batteries that can ensure 30-minute alarm functionality even upon double loop breakage.
Last but not least, I’d like to mention our AVENAR all-inone signaling device, which is a single-point solution for applications when both visual and audible alarm signaling is required. It can be used with or without a detector, and also it doesn’t need an extra power supply to work.
Instead, the intended content should have been:
“Let me share some benefits or special features offered by Bosch to help designers transform an originally UL project into EN. Firstly, our AVENAR panels are pretty unique when it comes to their
separation, or flexibility to add modules that offer auxiliary monitored outputs. That, followed by the newest technological achievements such as a 7’’ color touchscreen or an integrated Ethernet switch, makes the overall state-of-theart solution that satisfies even the most demanding users.
Then I’d like to highlight our detection range. For instance, AVENAR 4000 point type detectors that do not only meet high electromagnetic requirements given by EN 54 standards but
On top of the product features, we also have good delivery times, advanced tools shortening project design and commissioning time, competitive pricing, and a 3-year warranty with an advanced replacement procedure. Scan the QR code on the upper right of this page to learn more about Bosch Fire Alarm Systems.”
We apologize for any inconvenience this error may have caused and appreciate your understanding.
Sincerely,
Orhan Hadžagić, Associate Editor, a&s Middle East

With the abundance of solar-powered cameras on the market, protecting your off-grid home or business premises has never been easier or more affordable

n By: Orhan Hadžagić editorial@asadria.com
Most cameras today are easy to install and allow you to monitor indoor spaces, perimeters, and outdoor areas from anywhere. However, those are all ideal scenarios. What if you need to place your outdoor cameras far from a power source? Wireless cameras emerge as a solution as they are very convenient for outdoor spaces and eliminate the need for visually unattractive cable installations. A smarter answer is cameras with solar power, which, due to advancements in technology and falling prices of solar equipment in recent years, are becoming
more common on equipment procurement lists, especially if they serve the most demanding environments.
Despite all the convenience they offer, wireless cameras aren’t perfect. Their batteries need regular charging, and as an unwritten rule, this often happens at inconvenient times for the user, such as during travel. Equipping cameras with suitable solar panels is a way to ensure regular battery charging at all times, regardless of circumstances or user availability. All of this has led to the rise of solar-powered cameras that free users
from dealing with complex wiring and dead batteries, while still offering good enough performance comparable to cameras with standard power supply.
Solar-powered surveillance cameras are standalone devices that don’t require electrical wiring before being put into operation. This is closely related to a significant advantage of these devices over standard cameras, which is simplified installation. By choosing a security camera powered by solar energy, you eliminate the need to connect the camera to a power source because it draws energy from solar panels that come with the selected product or are sold separately.
Another important advantage of these devices is the flexibility in choosing the location you want to cover with surveillance cameras. These devices are an excellent option for homes, businesses, and remote off-grid locations such as farms, ranches, and construction sites. Broadly speaking, solar-powered cameras are suitable for any location where there aren’t enough people or staff, or for spaces that are too demanding for standard cameras by design.
Agricultural lands and farms, for example, are vast areas with little to no constant human presence, making surveillance challenging. This becomes even more demanding when there is no stable source of electricity or internet connection. In such terrains, solar-powered cameras can assist farmers in monitoring livestock movements and receive alerts about property boundaries being crossed. Festivals are events where a large number of attendees are present, but they are usually temporary and last only a few days each year. Surveillance is crucial at such events, but installing conventional systems is uneconomical and inefficient for a short-term event. Solar cameras, especially their mobile versions, are ideal solutions for festivals because they offer extremely fast installation and excellent mobility of the devices.
A third important application scenario for solar-powered cameras is highways. With the expansion of road networks, highways now extend to even the most remote rural areas where on-site surveillance and patrols can be a very expensive option. Moreover, infrastructure facilities like roads are often exposed to vandalism and theft. Solar-powered cameras are suitable for deployment in remote sections of highways that require no less protection than routes closer to urban centers.
One of the questions that interests many new users of solar-powered cameras is how their power system actually works. The most important thing to know is that solar-powered cameras rely on small solar panels that convert sunlight into electrical energy. This energy is used to charge the built-in rechargeable batteries in the cameras, which typically last for several
Monitoring forested land is essential for preventing illegal exploitation, protecting wildlife, and providing early warnings about fires. However, densely wooded areas and abundant water sources make it difficult to install power cables for standard cameras. Once again, this recommends solar-powered cameras for carrying out surveillance tasks in this highly demanding environment.
months. The energy stored in the batteries during the day serves as a power source on which solar-powered security cameras rely for operation during the night or periods without sunlight. This means that users should not have problems with battery drainage overnight – if this does occur, the first item for checkup should be the battery itself, and only then the camera’s solar panel. There is also a version with an integrated inverter that converts direct current (DC) energy from solar panels into alternating current (AC) electricity to ensure power supply to NVRs, routers, and other connected devices, as well as charging additional batteries that extend the autonomy of the entire system. Since solar-powered security cameras use batteries to store energy produced during the day, several cloudy days will not necessarily result in a power outage. Depending on the sunny intervals in the region where you install the cameras, solar panels can significantly extend the battery life of outdoor cameras or even minimize the need for their regular replacement. Regardless of this factor, the user can also influence the battery life by keeping the solar panels at an optimal angle and regularly cleaning them from dirt. The panels themselves usually come
with an adjustable design to achieve the ideal charging angle at different locations and geographical latitudes. The ideal adjustment angles range from 26 to 45 degrees, as we move from south to north.
ones?
When considering alternatives to standard surveillance cameras, the inevitable question is whether they are “better” than the solutions they are compared to. With solar-powered cameras, the answer is not straightforward and mostly concerns usage scenarios and environmental circumstances. If you anticipate that wired installation will be problematic, solar cameras are a good option because you don’t have to connect them to power sources. This applies not only to power cables but also to data transmission cables, which are also unnecessary for these models since they can be connected to home or business security systems via Wi-Fi. Solar-powered surveillance cameras are “better” than standard wireless models if you consider maintaining the power system a demanding task. For models without solar power, battery replacement or charging is a standard measure that is

An important advantage of these devices is the flexibility in choosing the location you want to cover with surveillance cameras

taken every few months. This involves removing and then reinstalling the camera, which can be time-consuming and technically challenging for some users.
In assessing the desirability of these models, it should be kept in mind that solar-powered security cameras can record footage continuously. On the other hand, wireless security cameras typically remain in power-saving mode to conserve battery power and only wake up when motion is detected. The need to switch between modes is a potential source of delay in recording events on-site. If you feel that you cannot afford to miss important moments on-site, solar cameras once again emerge as a solution worth considering in procurement.
Currently, there are hundreds of models of security cameras on the market that vary in price, functionality, and quality. However, only a few of them offer solar power, which theoretically makes it easier for the user to choose the best models.
To begin with, the search for the best solar-powered surveillance camera for homes or offices involves applying similar common-sense criteria as for standard cameras. These include camera resolution, field of view, night vision function,
One of the frequently asked questions is how solar-powered security cameras perform during cloudy and rainy days since they rely on solar energy. However, solar panels connected to cameras can generate energy even during cloudy and rainy days because the excess energy stored in rechargeable batteries during sunny days can help them weather unfavorable conditions. Nevertheless, the laws of meteorology are unforgiving, and in regions farther from the global north or south pole, you will likely generate less energy than in zones closer to the equator. Similarly, the amount of energy produced will typically vary according to the season and the prevailing weather patterns in your region.
motion detection activation, remote monitoring, and the ability to receive alerts on a smartphone.
Video quality should be a crucial factor in the procurement of any camera, regardless of whether it has solar power or not. Most models on the market now have a 1080p resolution, but some go up to 2K resolution or higher. It is recommended to look for a model with at least high-definition (HD) or even higher resolution. Otherwise, a solar camera will not be effective if the footage is grainy and unrecognizable. It should not be forgotten that higher video quality on a solar-powered camera also requires more network bandwidth capacity. If you are unable to provide it, there is a higher chance that the camera will experience more frequent
Users can influence the length of battery life by keeping the solar panels at the optimal angle and regularly cleaning them from dirt
picture delays or distortion.
The choice of adequate storage is also related to the quality of the display, and there are two options available to the user. The first one is cloud storage, which sends footage to a remote server for storage purposes and often involves paying a fee for accessing these capacities. The second one is local storage, which relies on a special add-on or hardware, usually a microSD card.
A wider field of view is always better for a surveillance camera, including solar models, especially since they are most often installed in inaccessible locations. Night vision and motion detection activation are already standard features that enable recording in less-than-ideal conditions. The same applies to smartphone alerts and remote monitoring, which are modern features that help users monitor homes or offices when they are not there.
Other optional features to consider include two-way audio, a virtual boundary
detection system around locations, an integrated intruder alarm, and a built-in spotlight. Depending on the model, some solar-powered cameras can also serve as security systems that activate flashlights or emit sounds to deter intruders from breaking in.
In addition to desirable camera features, there is one essential factor exclusively associated with solar-powered models – the power of the solar panel. This parameter describes the amount of electrical energy the camera can generate from sunlight. It’s important to note that higher-power panels charge the included battery faster and supply the camera with more energy.
Similarly, the capacity of the solar-powered security camera’s battery determines how long the camera can operate when sunlight is not available. The best solar-powered cameras have batteries that ensure functionality for at least 12 hours, even in cloudy weather. Some models have batteries that last up to three days. If you live in an area that is well-exposed to sunlight throughout the year, cameras with batteries that last one night are sufficient. However, longerlasting rechargeable batteries are necessary if you live in a location that receives little sunlight throughout the year. In such cases, it’s crucial to pay special attention to the quality and lifespan of the battery.
To maximize the efficiency of the solar panels on your selected camera, you need to orient them towards the south and ensure that no shadows from nearby objects such as buildings, trees, or roofs fall on the panel.
Logically, the optimal location for solarpowered cameras is where the device can receive the most sunlight and provide the best coverage of the desired area. For a location with limited sun exposure, it’s preferable to mount the camera on a south-facing wall to ensure at least six hours of sunlight daily. When mounting

on a wall, it’s important to position the camera high enough to prevent easy access by intruders aiming to remove it. Additionally, a more compact security camera will have less visibility and thus be a tougher target for intruders. However, even these positions may not always be ideal for cameras of this profile. Many solar cameras offer enough flexibility with the option of cable connections between associated devices, i.e., the camera and the panel. In such cases, you can place the camera or panel around the corner from the other component so that the solar panel can receive the necessary light while the camera covers the desired field of view.
Quality solar-powered security cameras should provide years of stable operation. As with other related technologies, be sure to check the warranty of the purchased product, as some offer limited timeframes, such as one year.
A good idea before making the purchase is to verify whether the camera is weather-resistant to the prevailing weather conditions at the installation location. It’s also important to check the supported operating temperature of the camera for the installation site. Even if the solar camera is stated to operate at temperatures below freezing, many batteries will discharge
The laws of meteorology are unforgiving, and in regions farther from the global north or south pole, you will likely generate less energy than in zones closer to the equator.
rapidly at this temperature. Specifically, battery performance at low temperatures will vary depending on the model type. In such situations, it’s not uncommon to have to bring the batteries indoors to charge them during severe cold spells. However, keep in mind that solar panels perform much better at lower temperatures than at high temperatures.
TVT Digital Technology, a Chinese company, addresses the users’ needs for reducing high wiring costs, especially in demanding terrain. The TVT series of solarpowered products continues to grow with more features and formats, now offering solar power kits that can be independently designed for each application scenario. These products offer flexible viewing angles, easier installation, and reliable performance in practically all scenarios where 4G and wireless solutions are sought for areas without adequate power and internet connectivity. The solar power kit can power various products such as network security cameras, radar units, and LED displays.
Since inaccessible terrains often entail unfavorable ambient conditions, TVT’s kit comes with a robust IP67-rated housing for protection and high reliability against strong winds, rain, dust, and corrosion. This solution is managed via HCP/HCC, where the unified platform enables power and data flow control from any connected camera, along with sending and receiving real-time event notifications in the field.

Solar-powered cameras are compatible with various smart home environments. Cameras that integrate with smart home systems allow users to monitor surveillance footage from their smart screens and televisions. Therefore, before purchasing a camera for these environments, it’s important to check what this compatibility entails. For example, if you use an assistant like Alexa, your solar-powered camera should be compatible with the Amazon Echo ecosystem. The same applies to environments such as Google Home or Apple HomeKit.
In addition to checking compatibility, attention should also be paid to the security robustness of the solar-powered camera itself. Since these are wireless security devices, these cameras may be more susceptible to hacking due to their connection to Wi-Fi networks and remote access technology.
TVT also offers solar-powered cameras with full-day color surveillance, whether day or night. The TD-9846SP1 model is TVT’s latest solar IP camera, offering a high-quality 4K display and detailed monitoring in both day and night modes. This camera is used for various scenarios such as license plate recognition, radar, and PIR detection. Time and effort savings on battery maintenance and replacement are achieved through advanced energy storage capabilities, paired with low consumption and longlasting battery life.
Power is provided by solar and lithium batteries that can be managed with a consumption display, built-in protection against high and low temperatures, and battery idle and PIR wake-up functions. The camera offers flexible viewing angles such as varifocal, PT, and PTZ for wide coverage from all directions. Integration with 4G/Wi-Fi technology significantly reduces installation time and costs.
Supported LTE-TDD/LTE-FDD/VCDMA/ GSM 4G mobile network communication ensures global coverage of different signal systems. There is also a Micro SIM slot for a Micro-SD card (512 GB) and eMMC (64 GB), meeting users’ needs for permanent local storage.
Hikvision has focused its solar-powered cameras on an important aspect of implementation: installation speed. For this purpose, the consolidation of all components of this system has been done to eliminate the need for separate purchase and assembly of various parts. Instead
of this often lengthy and demanding process, Hikvision’s solar cameras consist of a significantly smaller number of parts, which should ensure accessibility of these systems even among less technically savvy users. Solar-powered kits consist of a solar panel, mounting bracket, battery module, and the camera itself, and are currently available in two storage options: 256 GB and 1 TB.
These systems require only one solar panel and can operate continuously for up to seven days with a single battery charge, which brings significant cost savings. Solar power kits are suitable for use in parking lots, where ANPR cameras powered by solar energy can recognize license plates. In addition to outdoor parking lots, other facilities that can benefit from mobile solar towers include construction sites, oil and gas plants, as well as temporary buildings for hosting festivals, concerts, sports events, and similar mass gatherings.
Equally supported are scenarios in which details play a crucial role in conducting investigations and reconstructing events. For such scenarios, Hikvision offers special PTZ solar-powered cameras that provide advanced zoom capabilities, allowing operators to identify key details in the footage. Hikvision’s solar solutions operate in a range of different weather conditions thanks to internally developed ColorVu technology, which offers clear color video even in very dark environments often associated with remote locations. At the same time, the housings of solar cameras are resistant to low temperatures, strong winds, and heavy rain.
Finally, for scenarios involving temporary surveillance in inaccessible terrain,

For a location with limited sun exposure, it’s preferable to mount the camera on a south-facing wall to ensure at least six hours of sunlight daily
Hikvision offers mobile solar towers consisting of network cameras, recorders, and speakers, in addition to the tower itself. This solution is an excellent option for temporary security scenarios where mobile trailers can be quickly brought to the location without the need to search for a separate power source.
ZKTeco also has its representatives in the solar-powered camera market. The C4FS series includes a 4G PTZ camera with a monocrystalline solar panel (5 watts) and a rechargeable lithium battery of 8,400 mAh. ZKTeco has equipped this advanced model with a night vision system, fast activation, and person detection based on false alarm filtering. This solar camera is compatible with the ZSmart smart home application, supporting real-


Hikvision’s solar solutions operate in a spectrum of different weather conditions thanks to ColorVu technology, which provides clear color video even in very dark environments
time video verification, as well as cloud video and image storage. According to the manufacturer, this camera can be used on farms, in gardens, remote agricultural lands, etc.
Before investing in solar-powered cameras, it is important to carefully assess various factors, including price, installation location, and specific security requirements. The latter relates to readiness for initial investment, as well as the cost-effectiveness of these models compared to the length of sunny intervals at the location for which the cam-


Ongoing developments underscore the construction industry’s commitment to excellence, emphasizing safety as a top priority in all projects
era is procured. The second stage of analysis involves comparing different models and brands based on battery life, solar panel efficiency, and integration capabilities with existing security systems. Despite initial challenges, the sustainability and efficiency offered by these cameras significantly contribute to raising the level of security at locations without electrical installations, as well as in projects seeking environmentally sustainable solutions. Installation flexibility, reliability, and positive environmental impact position solar-powered cameras as a modern and worthwhile security option whose significance will continue to grow with technological advancements and price reductions. n

Powered by biometrics and AI, security technologies that protect data centers can ensure that only authorized personnel access sensitive data and infrastructure, significantly enhancing the overall security framework of data centers
n Source: asmag.com editorial@asmideast.com
In the fast-evolving realm of data center security, advancements in biometric technologies are crucial for balancing robust security with user convenience. As the demand for secure, efficient authentication grows, industry leaders are increasingly adopting sophisticated biometric solutions. AI plays a key role in distinguishing legitimate threats from false alarms, enhancing detection capabilities, and reducing false positives. By analyzing real-time data from sensors and surveillance systems, AI swiftly identifies suspicious activities, reduces response times, and continuously refines its threat detection processes through ongoing learning. Addressing insider threats has also become critical, with modern access control solutions evolving to incorporate advanced biometric systems, continuous authentication, and behavioral analytics.
Perimeter security is the first line of defense in protecting sensitive data environments. AI technology plays a pivotal role in this arena by enabling advanced detection capabilities that can discern between normal activities and potential threats. AI systems are equipped to analyze vast amounts of data from various sensors and surveillance systems continuously monitoring the perimeter. By processing this data in real-time, AI can quickly iden-

Perimeter security is the first line of defense in protecting sensitive data environments
tify unusual or suspicious activities that may indicate a security breach.
In the context of reducing false alarms, AI’s capability to learn and adapt from ongoing data and experiences is invaluable. This adaptive learning process allows the system to fine-tune its detection algorithms over time, thereby enhancing its accuracy and reducing the likelihood of false positives. This aspect of AI not only bolsters security but also ensures that the resources are efficiently used, focusing human attention where it is most needed.
“When protecting any sort of perimeter, AI can be used to detect what trig-
gered the alarm to help alleviate false alarms,” Jason Goldberg, Director of Global Partner Program at Intellicene. “AI can also be used to continuously monitor data from various sensors and surveillance systems around the perimeter. Ideally, it should analyze data in real-time to detect unusual or suspicious activities. We have seen how AI systems learn and adapt over time from data and new experiences, improving their overall accuracy. This adaptive learning process helps finetune the system to reduce false positives and enhance threat detection.”
Moving deeper into the data center’s security layers, access control systems are critical in managing who can access what data and when. AI technology significantly augments these systems by analyzing access control logs and user behavior patterns. By understanding typical user behaviors, AI can flag any deviations from these norms as potential threats.
For instance, if a user attempts to access sensitive areas or data at unusual times, or tries to gain entry into areas they have not previously accessed, AI-powered systems can recognize these actions as potential security threats. This capability not only helps in immediately alerting the security teams but also ensures that the alarms raised are more likely to be genuine, thus reducing the burden of investigating numerous false alarms.
“One of the most reliable ways users can filter out false alarms is by leveraging artificial intelligence to monitor access control logs and user behavior patterns to determine if alarm triggers are genuine,” said Jason Kallio, Senior Solutions Marketing Manager at acre security. “AIpowered access control solutions can analyze typical user behavior patterns and flag deviations from these patterns as potential threats when alarms are triggered. For example, AI may recognize subsequent alarms as authentic if a user suddenly attempts to access sensitive data, areas they haven’t accessed before or at unusual times.”
One of the most significant advantages of AI in security is its capacity for continuous improvement. As AI systems are exposed to more data and various security scenarios, their ability to differentiate between real threats and benign incidents becomes more refined. This continuous learning process is critical in environments where threat vectors are constantly evolving and becoming more sophisticated.
Moreover, integrating AI with other security technologies like facial recognition, anomaly detection, and predictive analytics can further enhance the security posture of data centers. By creating a cohesive security ecosystem that leverages AI at multiple points, organizations can ensure a robust defense against both internal and external threats.

Moving deeper into the data center’s security layers, access control systems are critical in managing who can access what data and when
While AI offers numerous benefits, it also presents challenges such as privacy concerns, the need for constant updates, and the risk of reliance on technology. Ensuring that AI systems are used responsibly and that they comply with all relevant laws and regulations is crucial. Additionally, while AI can significantly reduce the number of false alarms, it is not infallible. Maintaining a balanced approach that combines technology with human oversight is essential to address these challenges effectively.
Looking forward, the role of AI in physical security is set to expand further. Innovations in machine learning and neural networks will likely lead to even more sophisticated AI solutions capable of predicting and preemptively addressing potential security threats before they materialize. As these technologies continue to evolve, they will play an increasingly vital role in shaping the security landscapes of data centers and other critical infrastructure. In short, the integration of AI into physical security systems represents a significant advancement in the ability to discern real threats from false alarms. With continuous improvements and strategic integration, AI is poised to transform the field of security, making data centers safer and
more resilient against the complexities of modern-day threats.
Traditionally, access control systems have relied on methods like key cards and PINs to secure entry to physical and digital spaces. However, these measures often fall short when it comes to preventing insider threats. Modern technologies have revolutionized this landscape through the integration of biometric verification and role-based access controls.
Biometrics technology, which includes fingerprint and facial recognition systems, ensures that access is granted based on physical traits, which are nearly impossible to replicate or forge. This method significantly reduces the risk of unauthorized access by insiders who might otherwise acquire traditional forms of entry credentials. When coupled with role-based authorization, which tailors access privileges to the specific roles and responsibilities of individual employees, a more secure environment is created. This dual approach not only restricts entry to sensitive areas but also enforces the principle of least privilege, ensuring that employees have access only to the information necessary for their job functions.
Integrating AI with other security technologies like facial recognition, anomaly detection, and predictive analytics can further enhance the security posture of data centers

“In access control, integrating biometrics and role-based authorization significantly enhances security against insider threats,” said Hanchul Kim, CEO of Suprema. “Utilizing biometric technologies for both physical entry and system access ensures that only authorized personnel can gain entry. Combining this with role-based authorization, which assigns access levels based on specific roles and responsibilities, creates a robust security framework.”
This approach not only restricts access to sensitive areas and data but also enforces the principle of least privilege, ensuring that employees can only access the information necessary for their job functions. Together, these strategies form a multilayered defense that mitigates the risk of unauthorized access and maintains the integrity of critical systems and data.
To further bolster security measures, some companies have implemented continuous authentication systems. These systems continuously verify the identity of individuals as they interact with data center resources, rather than relying on a single point of entry check. This method ensures that any anomaly or deviation
from normal behavior is detected in realtime, thereby preventing potential security breaches from unfolding.
Furthermore, behavioral analytics are now being employed to monitor and analyze user behavior continuously. These systems use algorithms to detect unusual patterns in access and usage, which could indicate a potential insider threat. By integrating inputs from various departments like HR and Finance, these tools can assign risk scores to individual cardholders, flagging any suspicious activity for further investigation.
“Some companies have developed analytics or Business Intelligence tools to detect and report abnormal behavior and card activity to detect potential insider threats,” said Gaoping Xiao, Director of Sales for APAC at AMAG Technology.
“The algorithm can determine a cardholder’s risk score based on the card activities, the profile of the cardholder, and other factors like input from HR or Finance etc.”
The adoption of these advanced access control measures requires careful planning and implementation. Data centers must as-
sess their current security posture, identify potential vulnerabilities, and determine the appropriate technologies that align with their specific security needs.
This involves not only the integration of new technologies but also training personnel to understand and effectively manage these systems.
Comprehensive risk assessment: Before implementing new access control technologies, it is crucial to conduct a thorough risk assessment. This helps in identifying specific areas where insider threats could potentially arise and tailoring the access control solutions to address these risks.
Interdepartmental collaboration: Collaboration between security, IT, HR, and other relevant departments ensures that all aspects of insider threats are comprehensively addressed. By sharing information and insights, organizations can better identify potential threats and respond more effectively.
Continuous monitoring and evaluation: The effectiveness of access control systems should be continuously monitored and evaluated to ensure they are functioning as intended. Regular audits and updates to the system as technologies evolve are also crucial to maintain a high level of security.
As data centers continue to be prime targets for insider threats, the importance of sophisticated access control systems cannot be overstated.
By integrating biometric technologies, continuous authentication, and behavioral analytics, organizations can create a robust security framework that not only prevents unauthorized access but also ensures the integrity and confidentiality of critical data.
As we move forward, these technologies will play an increasingly vital role in protecting the assets that drive our digital world.
The onset of the COVID-19 pandemic has accelerated the shift towards more hygienic and touchless security solutions.
Traditional fingerprint recognition systems are making way for advanced facial recognition technologies and mobile access solutions.
These changes are particularly important in environments like data centers, where security and convenience are paramount.
“The COVID-19 pandemic has significantly impacted various aspects of security, including data center security,” said Hanchul Kim, CEO of Suprema. “One notable trend is the shift from fingerprint recognition to touchless facial authentication and RFID physical card to mobile solutions.”
Data centers, known for their stringent security requirements, are now employing two to three-factor authentication (MFA) systems as standard practice. The integration of mobile access with biometric verification forms the backbone of this new approach.
Users can now utilize their smartphones as keys, which, when combined with an additional authentication method like facial recognition or iris scanning, provides a secure yet convenient access solution.
“In data center security, two to threefactor authentication (MFA) is essential for securing highly restricted areas,” Kim said. “The most common method now is a combination of mobile access and biometrics.”
In response to the increasing demands for higher security in sensitive areas, companies are broadening their authentication strategies. A notable advancement is the adoption of a comprehensive multicredential approach.
This method incorporates a variety of verification options such as facial authentication, fingerprint scans, mobile access, QR codes, and RFID, thereby enhancing the security of highly restricted areas without compromising on user convenience. Moreover, the importance of integrating mobile solutions is emphasized, allowing users to easily incorporate mobile access into their existing apps. This integration simplifies the authentication process, making access both quicker and safer, while also enhancing user experience by leveraging the convenience of smartphones.

Innovations in machine learning and neural networks will likely lead to even more sophisticated AI solutions capable of predicting and preemptively addressing potential security threats
Another challenge in data center security is the enrollment process for biometric verification. Given that data center users may not visit the site daily, enrollment could traditionally take weeks or months.
To address this, some companies have developed partnerships with biometric technology providers to streamline the enrollment process.
For instance, a company may use cardholder’s photo already stored in the access control system for facial verification. If the photo meets quality requirements, there is no need for customers to be physically present onsite for enrollment.
This method significantly reduces deployment time and enhances the overall user experience.
“There is always a balance between security and user convenience,” said Gaoping Xiao, Director of Sales – APAC at AMAG Technology. “Data centers need to enroll a customer’s biometric information when using multi-factor verification such as card plus PIN. The challenge is data center users may not come to the data center daily; therefore, enrollment may take weeks or months.”
“We work with some biometric partners whose technology enables us to use the
cardholder’s photo in the existing access control system for facial verification if the photo quality meets the requirement,” Xiao added. “There is no need for the customers to physically come onsite for the enrollment of their facial information, which streamlines the entire deployment process.”
The ongoing challenge in data center security is maintaining a delicate balance between stringent security measures and user convenience. As biometric technologies evolve, they offer promising solutions to achieve this balance effectively.
The integration of facial recognition and iris scanning into access control systems is not just about enhancing security—it also makes the system more accessible and user-friendly for everyday users.
The integration of advanced biometric technologies into data center security systems is transforming how access is managed, prioritizing both security and convenience. With touchless authentication methods and streamlined enrollment processes, the future of data center security looks both secure and adaptable, ready to meet the challenges of a rapidly changing technological landscape. n
The full-day event showcased cutting-edge AI-based security solutions that are set to transform physical security across the Middle East
n By: Mirza Bahić mirza.bahic@asmideast.com
On May 27, Suprema Middle East, in collaboration with its official distributor Advanced Technology, held a highly successful partner event at the prestigious Concorde El Salam Cairo. The event attracted over 200 qualified attendees, all prominent figures in the security systems industry with extensive experience in the Egyptian market.
The attendees expressed great enthusiasm for the innovative technologies presented, highlighting the potential for these solutions to reshape security practices in the region. Suprema’s latest offerings, designed to enhance security management and streamline access control, were the focal points of the event. Suprema unveiled the new XP2-MAPB card reader, a sophisticated device supporting HID I Class, Seos, and Mobile BLE. This advanced card reader offers enhanced security features and flexibility, catering to the diverse needs of modern security infrastructure. Attendees were particularly impressed with its seamless integration capabilities and the robust security measures it provides.

The BioEntry BEW3 promises to set new standards in the industry with its cutting-edge technology and user-friendly design
The event also saw the launch of Suprema’s smallest facial recognition device, the BioEntry BEW3. This compact yet powerful device is designed for seamless integration into various security systems,
offering reliable and efficient facial recognition capabilities. The BioEntry BEW3 promises to set new standards in the industry with its cutting-edge technology and user-friendly design.

A major highlight of the event was the introduction of the latest update to Suprema’s BioStar software, version 2.9.5. This update features a revamped, userfriendly dashboard that simplifies access control tasks, making security management more intuitive and efficient. Attendees appreciated the enhanced functionality and the streamlined user experience that the new dashboard offers.
Suprema also announced the global launch of the Cloud Access-Control Service (CLUe), which has already seen success in Korea and Japan. Suprema CLUe is designed with a new integration approach, boasting both ease of use and powerful features. The global launch of CLUe marks a significant milestone for Suprema, as it aims to provide a more versatile and comprehensive access control solution to its international clientele.
Another groundbreaking solution presented at the event was Airfob by MOCA, touted as the world’s most scalable access control solution. Airfob is a 100% cloud-based, mobile-first system that eliminates the need for inconvenient access cards, enhancing user experiences for members, guests, and employees by providing a seamless and efficient access control method. MOCA System has revolutionized access control by integrating it with the cloud and securely connecting it to the online services we use daily. Already in use at 13,000 sites across five continents, MOCA’s Airfob cloud, hardware, and software solutions for commercial access control eliminate
the need for on-site servers and significantly reduce the cost of upgrading to mobile credentials. As the only fully cloud-based access control solution, Airfob is all about ensuring scalability by setting new standards for it in the access control industry.
All in all, the Suprema Egypt partner event can be described as a resounding success, providing attendees with valuable insights into the future of security solutions. The positive feedback from the audience underscored the significance of the technologies presented and their potential impact on the security industry in the Middle East. As Suprema continues to innovate and expand its offerings, the company strives to stay at the forefront of the industry, driving advancements in security and access control solutions. n
HID GLOBAL

Mobile access control and sustainable cards provide future-proof flexibility for the never-ending endeavors of digital transformation and going green.
n By: Sam Cherif, Senior Director, Regional Business Head, MEA editorial@asmideast.com
The widespread adoption of smartphones has fundamentally altered how we interact with the world— from online banking to booking services or requesting rides. For most, mobile devices have become essential components of most people’s daily lives, not just for their features but also for the convenient benefits they provide.
It is no surprise that 2023 recorded 57% of the world’s population – just 4.6 billion people – to be using mobile internet, according to the latest “State of Mobile Internet Connectivity” report by GSMA Intelligence, a research and analysis firm specializing in the mobile industry. There is no doubt mobile connectivity plays a big role in our daily lives, but the growing consensus that governments, organizations, and individuals must take immediate action to reduce their carbon footprint places it front and center as a means to replace traditional, environmentally unfriendly technologies.
In the security space, specifically in the access control segment, companies are increasingly executing access with mobile devices as a mechanism for the authentication and identity verification of their employees and visitors. Mobile access eliminates reliance on physical cards or

badges, supports multiple security protocols, and adds layers of security on top of basic card encryption, making it substantially more secure than traditional physical access control.
Digital credentialing and passwordless multi-factor authentication, for example, have encouraged financial services companies to move from issuing plastic credit cards to digital payment methods. In the higher education sector, universities are taking a mobile-first approach in lieu of plastic cards by offering mobile IDs with
the ability to open doors, check out library books, make cafeteria purchases, and more.
Much more than convenience
The benefits of mobile access control have been exposed on different occasions and in many scenarios, but its relationship with environmental sustainability and the optimization of resources for the planet deserves a particular space.

According to the 2024 State of Physical Access Control Report—produced by IFSEC Global in partnership with HID, a provider of trusted identity solutions— sustainability is playing a significant role in access control with nearly two thirds (63%) of respondents citing that those with responsibility for sustainability have either some influence or are fully consulted when it comes to upgrading physical access control systems.
What does this mean for the security and identity industry?
Forward-thinking providers know that sustainability plays an important role in technology deployment decisions. Technology, such as 5G networks and Artificial Intelligence (AI), are already enabling more end-to-end, cloud-based solutions while reducing its carbon footprint.
Another element of mobile access that is gaining recognition is the concept of multi-application, where a single product or solution can execute multiple things. This digital experience not only increases operational efficiency but also helps reduce the number of plastic cards that users use and lose, which has a positive impact on sustainability and security. Mobile credentials are issued remotely over the air, which helps to reduce physical touchpoints both for employees and visitors. Equally important, it provides a convenient, flexible, and secure access control. Advanced access control readers in the market today are ISO/IEC 27001 certified and support the latest security credentials, such as Seos, as well as digital credentials on cellphones, enabling smooth migration from less secure legacy card technologies. This flexibility enhances the user experience and helps organizations to drive their digital transformation sustainably.
Additionally, mobile access can be seamlessly integrated into Building Management System applications through a highly secure application programming interface (API) and software development kit (SDK). With robust API and SDK, organizations can collect, monitor, and manage terabytes of data.
A sustainable alternative to traditional cards
There are segments where the need for physical access cards is still required, particularly in the government and healthcare space. Although organizations are turning to renewable and eco-friendly materials as much as possible, in addition to reducing energy consumption and waste, there has been little effort by the market to implement this in finished physical access control cards.
To address this gap, leading manufacturers are introducing environmentally friendly access control credentials made from sustainable materials such as bamboo—without compromising on security. Utilizing Seos technology for the best in data protection, it is now possible to leverage modern cryptography and mutual authentication between the credential and reader to ensure reliable and secure access control.
Finally, it is important to note that organizations seeking green building certifications, including the internationally accepted Leadership in Energy and Environmental Design (LEED), should look for materials like bamboo which are appropriately certified such as the Forest Stewardship Council (FSC).
To amplify your organization’s sustainable practices, choose a sustainable and secure credential that prioritizes the design principles. The core principle here is sustainability. The card should be made from rapidly renewable, FSC-
certified materials like bamboo, minimizing its environmental impact compared to traditional PVC cards. The next one is visual appeal. While not explicitly stated, the use of bamboo offers a natural and potentially more aesthetically pleasing alternative to standard PVC cards.
In terms of functionality and user-friendliness, you need to maintain the core functionality of traditional access control cards, such as mutual authentication and TÜViT Seal 5 certification, and look for cards that offer versatility for applications beyond physical access control. The user experience should be similar to traditional access control cards. However, the use of sustainable materials can enhance user perception for environmentally conscious users.
Finally, you have scalability. The card should be designed to work with existing Seos systems, making it scalable for organizations of all sizes. This ensures a smooth integration without needing entirely new infrastructure.
The digital experience reshapes security, with interconnected devices raising the bar of what can be secured and how.
The cloud will power implementations efficiently across physical and logical footprints, elevating the value of data to drive specific business outcomes.
As consumers urge businesses to share information on things like energy use, waste reduction, and resource optimization, organizations must define a clear sustainability strategy to be better positioned to not only adapt to but anticipate environmental, social, and regulatory changes, both in the short - and long-term.
To succeed, systems integrators and end users should work with sustainably minded suppliers. Identifying and working with suppliers who demonstrate sustainability efforts in their organizations creates a sustainability component within the full value chain, helping to communicate sustainability KPIs and ROI. n
ASSA ABLOY
In hospitals, clinics and other medical buildings, small spaces need as much protection as larger areas. Traditional keys can cure many problems of medicine and equipment security. But this can come at a cost of time- or operational inefficiency
n Source: ASSA ABLOY editorial@asmideast.com
Photo: ASSA ABLOY
In a busy hospital ward, keys are easy to misplace. Me chanical security cannot log who accesses each opening, and when. Nurses either take on this labori ous task for themselves, or medi cine managers surrender some control over access. Auditing drug discrepancies or investigating inci dents becomes more difficult.
Managing the security of additional access points mechanically, outside the scope of a digital access system, increases risk, complexity and work load. And just like any sensitive open ing in any building, medical or other wise, the risks and costs of a security breach or unauthorized access can be great.
the pain points of healthcare

Some drawbacks of mechanical security may obstruct efficient medical care. Often multiple staff need access at different times in a 24/7 work environment. Searching for the right
All keys in circulation must be logged and monitored, for medicine safety or to ensure patient belongings are safe in cabinets. All losses must be investigated. If keys go missing, locks must be changed, which wastes staff time
and costs money. Hassle and headaches multiply many-fold if a master key is lost.
Digital access seems an obvious solution. Yet medical settings often have access points that traditional wired solutions cannot reach. These may be mobile, like Electronic Prescribing and Medicines Administration (EPMA) carts. Cylinder sizes may be small with non-standard camtypes, as on bedside cabinets or medicine storage.
To make their access ready for what’s ahead, many healthcare premises choose wireless access devices.
Digital locking for medical cabinets, cupboards, or trolleys
The robust, road-tested, batterypowered Aperio KL100 [embed link to EMEIA site product page] makes cabinets, EPMA carts, medicine drawers and almost any other small opening an integral part of a hospital’s digital access system.
An adjustable cam makes it a straightforward retrofit solution for patientaccessed medication or POD lockers and bedside cupboards. The device con-

sumes very little energy: Powered by one standard battery, it needs no specialist maintenance.
The KL100 takes away the pain of secure access for non-standard openings in healthcare environments. In line with the rest of the Aperio product range, it brings added flexibility and user convenience over physical keys.
It is compatible with smartcards and fobs using all major RFID technologies, as well as smartphone unlocking via Bluetooth LE and NFC. The device accepts multiple credential technologies simultaneously, in parallel, so site managers can roll out mobile keys slowly or to limited staff only. Choosing traceable, flexible, and convenient digital access with the Aperio KL100 brings many more access points
The KL100 takes away the pain of secure access for non-standard openings in healthcare environments
under the control of the digital system. These openings are managed from one integrated software interface and offer the same level of control as any other digital access device. As a result, medical personnel get access tailored exactly to their needs. Nurses no longer waste time looking for the right keyholder, pharmacists always know who has accessed medical storage and facilities managers can delete any missing credential with a click.
The Aperio KL100 is designed for seamless integration with any new or existing
access system from over 100 different manufacturers and counting. A KL100 may be connected Online, Offline, or via OSS-compliant integration and switched between them at any time. Online management enables real-time control over every KL100 lock, with easy access rights administration and instant availability of audit trails for any opening or user which makes incident investigation fast and accurate. The Aperio family of award-winning, energy-efficient digital access devices includes cylinders, escutcheons, handles, security locks, server rack locks and more. With a low-profile design and road-tested reliability, a KL100 is the flexible choice for securing sensitive, personal, or mobile small spaces in medical and many other settings. n
With a focused trend leaning towards technology and AI advancements, facial biometrics offer one-of-a-kind security solutions that cater to the diverse infrastructural requirements of a smart city
n Source: RecFaces editorial@asmideast.com
Being the catalysts of growth, smart cities are founded on a technologypowered infrastructure. Digitization in global economies has led the way to a transformative shift to smart security, universal convenience, and accelerated advancements. By 2026, smart cities will be expected to generate an economic benefit of USD 20 trillion globally. Unfortunately, crimes and offenses are also becoming high-tech, challenging the balance in the socio-economic ecosystem. To secure the frontiers of growth, security operations need to be spearheaded by reliable and pervasive technological solutions that also elevate the prospects of unified development. In the past decade, facial recognition technology (FRT) has gained momentum, contesting to be one of the most reliable and easy-to-use technologies for modern economies.
Public transport is the backbone of a social infrastructure. Smart transport aimed at sustainable and convenient commuting stands out as a benchmark of inclusive growth. Digitization of transport processes not only ensures optimal utilization of resources but also solidifies commuters’ trust in the administration. However, se-

curity in smart transport continues to be a primary source of stress. Misconduct, theft, security breaches, and the presence of repeated offenders create a sense of insecurity among commuters. This insecurity can only be resolved through a strong security ecosystem that reassures safe and hassle-free travels.
A facial recognition system (FRS) deployed in the video surveillance system at transport terminals to identify blacklisted individuals is effective in avoiding incidents and clashes. Entry and exit access through turnstiles enabled with facial identities allows for smooth
and unobstructed access to transportation modes, maintenance of travel accounts, and integration of security with experience. Not only does FRS help prevent security lapses but also extends the capabilities of the on-ground security department to attend to incidents promptly.
The core of smart cities is the intricate network of cloud-based operational infrastructure, integrated economic functions, and the Internet of Things (IoT). This aug-

ments the cruciality of protecting the virtual boundaries and resources to protect the smart infrastructures. As a byproduct of global integration, data intelligence, and networked management, the threats of data leaks, cyber-crimes, and identity thefts are on the rise. Cyber breaches at such a scale do not affect only a single individual but are detrimental to the security of the city’s effects and in turn, the economies at large.
While the smart infrastructure cannot function without cyber support, efficient protection of cyber confines can only be executed through reliable and multi-functional solutions. Multi-factor authentication enabled through facial recognition allows for verification and re-verification of identity, preventing access breaches. Digital data, guarded by unique facial biometrics powered by liveness detection to differentiate an actual person from a synthetic identity, are protected from leaks, misuse, and identity breaches.
With smart solutions redefining physical security, border security comes under the lens of indefectible control. A considerable amount of resources and efforts are allocated to secure border access portals like airports, train terminals, and sea ports. It is important to protect the physical and virtual boundaries of a smart city to ensure the safety of citizens, data protection, economic balance, and preservation of property, resources, and environment.
While the legality procedures and compliances are closely maintained, border management greatly relies on intelligent technologies that lend a hand to speed up compliance procedures.
Facial recognition-powered surveillance at border access portals allows for quick background checks, verification of legal compliance to enter the premises of a smart city, and checking if the individual is subject to cross-border restrictions. It provides a sense of safety to the entrants and helps maintain trust in the otherwise tiring and complex verification formalities. Not only this, the video management systems with facial recognition integration elevate the quality of video surveillance and raise alarms for efficient intrusion detection. Additionally, it strengthens the essence of a smart infrastructure by automating the security process and integrating all the border access terminals on one common system - FRS. Estimates suggest that the market size for smart security globally is to grow at a CAGR of 15.1% to reach USD 211 billion by 2033.
In a smart city, Law and order enforcement, extending to crime control, confides in intelligent solutions for investigation and circumvention. At the foundational level, identification and authentication accuracy are the primary factors that determine the monitoring and control of security violations. Legal investigations are increasingly becoming tech-
nology-driven, in terms of video monitoring, lie detection, global database integration, and smart alert systems. However, these processes are not entirely automated and depend on manual commands. This leaves the scope of human errors, risking false convictions and response delays.
In a smart city, citizens, software, and crime control are interlinked on an integrated network, making them interdependent. For accurate identification, incident detection, and controlled monitoring, facial recognition can be more beneficial than expected. It allows checking for compliances in real-time, like social curriculum, healthcare precautions, and guarded access to sensitive resources. Persecuted criminals can be accurately identified through facial recognition, facilitating easy access to their criminal records and previous litigations supported by globally integrated databases.
In a nutshell, security in smart cities is governed by technologically advanced solutions that not only cater to the requirements at present but also impede a stronger foundation of smart infrastructure. Facial recognition is a revolutionary technology exhibiting the unique features of remote and digitized control to execute complex security protocols. The best-in-use applications include access control, video surveillance improvement, and vigorous record verification. This technology is powered by advanced algorithms and top-class AI, ensuring accuracy, unbiased decision-making, and solutions that improve with changing times. RecFaces is one of the leaders in developing ready-to-use software products with facial recognition functions. RecFaces develops off-the-shelf solutions that help to quickly increase the efficiency of VMS, and ACS, as well as ERP, CRM, and time-tracking systems. “The cutting-edge technology of facial recognition perfectly complements the smart city ecosystem. It is quick, errorfree, and seamless, enabling unequivocal security of the resources and residents of the smart city,” says Tamara Morozova, Chief Executive Officer at RecFaces. n

The International Exhibition for National Security and Resilience (ISNR) Abu Dhabi 2024 concluded with resounding success, marking the most significant milestone in its history since its inception in 2008
n By: Mirza Bahić editorial@asmideast.com
Under the esteemed patronage of Lt. General HH Sheikh Saif bin Zayed Al Nahyan, Deputy Prime Minister and Minister of Interior, ISNR 2024 Abu Dhabi was organized by ADNEC Group from 21-23 May 2024 in collaboration with the Ministry of Interior. The event saw unprecedented participation and engagement from across the globe. This year’s ISNR, held in strategic partnership with the Abu Dhabi Police General Command and academic partnership with Rabdan Academy, demonstrated remarkable growth and impact, reflecting the increasing importance of national security and resilience in the region and beyond.
The exhibition spanned an impressive 24,038 square meters of gross space at the ADNEC Centre Abu Dhabi, with
13,609 square meters of net occupied space, making it one of the largest editions to date. It hosted 210 exhibitors from 35 countries, showcasing a 14% increase in participation from the previous edition. This diverse representation included six dedicated pavilions, each highlighting innovative solutions and technologies in the fields of cybersecurity, national security, and law enforcement. The exhibition attracted a record 25,128 visitors, marking a 30% increase compared to the 19,493 attendees of the previous edition, underscoring the growing interest and relevance of ISNR.
One of the standout features of ISNR 2024 was the launch of the Rabdan Security and Defense Institute (RSDI) by Lt. General HH Sheikh Saif bin Zayed Al Nahyan. This specialized research center
is dedicated to advanced security and defense studies, aimed at deepening understanding of regional security dynamics and identifying potential threats, opportunities, and challenges. The institute’s launch highlighted the UAE’s commitment to enhancing security research and education, fostering a deeper collaboration between academic institutions and security agencies.
The event’s comprehensive conference program, organized by the Ministry of Interior and Rabdan Academy in cooperation with ADNEC Group, was a major highlight. Over two days, pivotal discussions took place on critical security, policing, and crisis management issues. The conference featured 108 speakers who delivered 70 onsite sessions, engaging 1,157 attendees. The sessions delved into various topics such as “Policing and

Crisis Management in the Era of Innovation” and “Artificial Intelligence and the Future of Security Technology,” addressing key issues like strategic alliances in global stability, evidence-based policing, AI in security, and intelligence-based preparedness.
ISNR 2024 also introduced the “ISNR Dialogues” platform, which facilitated a series of presentations and interactive dialogue sessions. The third and final day of the Dialogues, themed “Cybersecurity and Critical Infrastructure Protection,” commenced with a presentation on “Using Strategic Intelligence to Understand and Confront Physical and Cybersecurity Threats.” This forum brought together 411 attendees and leading experts who discussed a broad spectrum of topics related to cybersecurity challenges and solutions for protecting critical infrastructure.
During a series of dialogue sessions for the Ministry of Interior on the second day of ISNR Abu Dhabi 2024, participants addressed several important topics that included child protection in cyberspace, institutional partnerships to improve child protection in cyberspace in the UAE, and the protection of women in cyberspace.
The sessions featured experts and specialists at the local and global levels discussing the importance of protecting society from cybercrime through governance enhancements, improvements in the quality of digital life, and cooperation between national institutions. International cooperation to raise awareness of cross-border cybersecurity challenges, and healthy and sound practices for dealing with them, were also addressed.
The Ministry of Interior stand also featured the MOI Talks with 22 distinguished speakers addressing crucial issues. Two significant graduation ceremonies were held for Ministry of Interior employees.
The first ceremony celebrated the graduation of 54 members from specialized programs in child protection, qualifying them as specialists in this critical field.
The second ceremony marked the graduation of the ninth batch of the Future Services Diploma, with 225 employees from 49 federal and local entities completing the program, aimed at enhancing government services and improving community life.
A notable feature of this year’s event was the Cyber Security Hub, launched by the UAE Cyber Security Council. This hub hosted a daily competition titled “Capture the Flag,” designed to test and evaluate the cybersecurity skills of participants through various challenges, including
hacking artificial intelligence and cryptography. The competition culminated with Mohammed Aloraimi being awarded as the winner, highlighting the UAE’s focus on nurturing and growing its cybersecurity capabilities.
The Interpol Policing Hub was another key attraction, serving as a focal point for collaboration, knowledge exchange, and innovation in global law enforcement. Attendees participated in engaging sessions, interactive demonstrations, and networking opportunities with leading law enforcement professionals from around the world, fostering international cooperation in tackling organized crime and enhancing global security.
The ISNR Talks provided a platform for leading experts to discuss various aspects of security, with a particular focus on cybersecurity and critical infrastructure protection. The series of presentations and panel discussions underscored the importance of strategic intelligence in addressing physical and cybersecurity threats. Throughout the course of the event, the ISNR Talks brought together leading experts in various fields for discussions, sessions, and panels to discuss several topics. A series of presentations and rich panel discussions were held within the ISNR Talks platform, which discussed a variety of topics related to cybersecurity challenges and solutions to protect critical infrastructure.
In conclusion, ISNR Abu Dhabi 2024 was a monumental success, showcasing the latest advancements in national security and resilience. The event’s comprehensive program, record participation, and the introduction of innovative features and platforms underscored its importance as a global forum for security and resilience. The UAE’s commitment to fostering international cooperation, enhancing security capabilities, and promoting advanced research was evident throughout the event, setting a high benchmark for future editions. n
Saudi Arabia’s premier trade fair for safety, security, and fire protection, returns for its sixth edition, featuring a 34% larger exhibition space, over 350 exhibitors from 27 countries
n By: Mirza Bahić editorial@asmideast.com
Intersec Saudi Arabia, Saudi’s leading trade fair for safety, security, and fire protection, will return for a sixth edition from 1 - 3 October at the Riyadh International Convention and Exhibition Center (RICEC). Building on the success of previous years, the exhibition space will be 34% larger this year, with 17,000 visitors expected to attend. The exhibition’s conference program will feature the Future Security and Safety Summit and the Fire Protection and Technology Summit. Organized by 1st Arabia and licensed by Messe Frankfurt, the exhibition is held in association with the Ministry of Interior and Saudi Civil Defense.
Intersec Saudi Arabia draws thousands of security and safety professionals from around the GCC each year to procure, learn, and develop their knowledge of a rapidly growing industry. A record-breaking 15,336 visitors attended the 2023 event, and 17,000 visitors are expected at the upcoming edition. The exhibition space for Intersec Saudi Arabia 2024 has now increased to cover a total area of 23,000 sqm across five halls and one outdoor showcase.
Bilal Al Barmawi, CEO and Founder of 1st Arabia Trade Shows & Conferences, said: “Intersec Saudi Arabia is tailored
specifically to the needs of the Kingdom. The event is regarded as the largest and most important exhibition and conference for the security, safety, and fire protection industries in Saudi Arabia.”
Intersec Saudi Arabia is expected to host over 350 exhibitors from 27 countries and will feature country pavilions for China, the Czech Republic, France, and the UK. Saudi-based exhibitors account for 29% of the participating companies, which are categorized across five product sectors – Commercial & Perimeter Security, Cybersecurity, Public Safety & Security, Fire and Rescue, and Safety and Health.
The annual conference program for Intersec Saudi Arabia will include the Future

Riham Sedik, Show Manager, Intersec KSA
Security and Safety Summit and the Fire Protection and Technology Summit, with both of these summits reflecting the specific needs of the Saudi market.
Riham Sedik, Show Manager — Intersec Saudi Arabia, Messe Frankfurt Middle


East, said: “We are proud to feature two pivotal summits that will unite industry pioneers to address current and emerging security threats at national and corporate levels while also bringing together leading fire and emergency service professionals to discuss the latest challenges, opportunities, and advancements in fire safety and technology.”
The summits will run throughout the three-day event and have been developed to bring together the industry’s best and brightest minds, offering significant value to attendees and high-quality, valuable educational opportunities to attendees.

Key themes for the Future Security and Safety Summit include ‘Moving Beyond Security – How to React to AI’s Transformative Potential’ and ‘Boosting International Security Co-operation’ Meanwhile, the Fire Protection and Technology Summit will explore ‘Robotics and Automation for Fire Suppression’ and ‘Fire Challenges due to Climate Change’ among other vital industry topics.
The Premium Club will once again return to Intersec Saudi Arabia, providing unrivaled opportunities for professionals in safety, security, and fire protection to network. The program is designed to encourage key buyers to connect with exhibitors away from the show floor, offering a seamless purchasing process.
Halls 1 and 2 at RICEC will feature the Commercial, Perimeter, Homeland, and Cybersecurity show sections, while halls 3 and 4 will focus on Fire Health and Safety. Security, Safety, and Fire exhibitors will be featured in Hall 5, named Intersec Plus, as well as an outdoor, purpose-built exhibition space. Intersec Saudi Arabia is organized by 1st Arabia and licensed by Messe Frankfurt. n
Saif bin Zayed Al Nahyan’s patronage heralds the International Exhibition for National Security & Resilience, showcasing the latest solutions at ADNEC Centre, Abu Dhabi in May

n By: Mirza Bahić mirza.bahic@asmideast.com
Integrate Middle East, the flagship event convening technology leaders and integrated solution buyers across diverse industries, successfully concluded after three eventful days marked by groundbreaking innovation and collaboration. Co-located with CABSAT 2024, the event’s success underscores the growing prominence of the Pro AV technology industry within the MENA region.
The event hosted over 10,000 visitors from more than 75 nations, as well as 250+ exhibitors who showcased their
cutting-edge products and services, making it an ideal platform for networking. The summit boasted an exemplary array of speakers from leading brands such as HL Group UAE, Theatre of Digital Art, JLL
Technologies, Epson, Nuevo Design UAE, Oasis Enterprises LLC, Channel Media Europe, FinesseTech IT Solutions, Elevision Media, Shure UAE, MORE UAE, Warner Music MENA, MassiveMusic, and Mubert Inc., among others.
The speakers led pertinent discussions centered around diverse topics such as the future potential of mixed realities, AI in built environment, AI integration in music and virtualization, the future of workplace design, digital signage, power of Digital Out-of-Home (DOOH), projector mapping, digital installation, and advanced Pro AV innovation. This gave visitors the unique opportunity to learn about relevant trends directly from industry experts.
“Over the years, the Middle East’s Pro AV market has undergone rapid growth, with an increasing demand for premium Pro AV technologies in the broadcast and entertainment sector. In light of the evolving market conditions, we have addressed the audience on ‘Safe Rigging Methods and Installation in the Entertainment Sector’, which highlights key safety protocols


and practices for rigging structures in our industry. Aligned with our company’s vision, we were excited to provide valuable insights on the challenges and transformation of the region’s broadcast and entertainment sector, and ultimately helping to create a safer working environment for us all”, says Paul Hadfield, Sales Director of Area Four Industries Middle East - Provision AVL General Trading LLC. Integrate Middle East connected technology leaders with solution buyers from sectors such as Education, Media, Entertainment, Hospitality, Retail, and Communication. It offered businesses the chance to access state-of-the-art solutions from leading broadcast, Pro AV, and media technology providers, and learn about best practices across various markets. The event exhibited a variety of products
and services, along with interactive learning zones, multi-conferencing demo areas, and smart home simulators.
“Our participation at Integrate ME 2024 allowed us to showcase our state-of-the-art Micro Mavel--NX COB Series, which is of a standard cabinet size and boasts a 16:9 aspect ratio for enhanced clarity. Visitors were also able to have a practical, hands-on experience of our innovative 138 all-in-one display solution, which is a powerful tool for both broadcasters and audiences. By synergizing semiconductor materials, cuttingedge core chips, illuminating light sources, high-density carrier boards, intricate driver IC, and nuanced image processing, we of-


fer services across R&D, production, and sales of Mini and Micro LED technology to our clients”, says Su Piow Ko, Vice President of AET Display Limited.
Integrate Middle East 2024 provided exhibitors an avenue to showcase innovative offerings in digital signage, command and control rooms, and live event solutions. The cutting-edge innovations offered a glimpse into the future of the Pro AV industry, bolstered by advanced technologies that cater to diverse business needs. The event served as a point of convergence for thought-provoking ideas, collaborations and opportunities while underscoring the role of Pro AV technology in facilitating immersive experiences. As the event draws to a close, its ripple effect is poised to pioneer innovation across the industry at large. n
OFSEC 2024, Oman’s premier summit and expo on fire, safety, and security, aims to unite global leaders, foster innovation, and set new standards to safeguard industries and communities in the Middle East and beyond
n By: Mirza Bahić mirza.bahic@asmideast.com
OFSEC 2024, Oman’s only and the most comprehensive fire, safety, and security exhibition is taking place from 08 - 09 October 2024, from 9 am – 6 pm at the Oman Convention and Exhibition Centre in the capital of Muscat. The event in its 8th edition will bring together over 90+ exhibitors from over 30 countries that will showcase their avantgarde solutions, latest technologies, cutting-edge innovations, cost-effective products, and services to meet the requirements of governments, businesses, industrial and commercial entities, aviation, construction, infrastructure, transportation, manufacturing, oil and gas and utilities sectors.
OFSEC is designed to meet the needs of the local, regional, and international markets by linking practitioners, suppliers, distributors, and manufacturers from the fire, safety, and security industry, with key decision-makers from the government and private sectors, making it a definitive networking platform, where new projects and partnerships are initiated and visionary objectives are implemented. This event also aims to create a synergy and strengthen the

The OFSEC Summit will feature an expansive lineup of 30+ stellar speakers, case studies, panel discussions, and unique presentations
collaboration between the authorities and the industries.
OFSEC 2024 will lay the foundation and be the gateway to the current and future market trends in the fire, safety, and security sectors, for the industry professionals to communicate, share ideas, identify solutions, operate effectively and efficient-
ly, and stay abreast with the latest global trends. It will confluence and strengthen local and international business engagement and encourage investment.
The OFSEC Summit will feature an expansive line-up of 30+ stellar speakers, case studies, panel discussions, and unique presentations providing access

to a wealth of industry-leading knowledge, sharing best practices and experiences, spotlighting trends, information exchange, insights, and outlooks with actionable takeaways.
The Summit is the definitive meeting place facilitating multi-stakeholder dialogue with power-packed networking opportunities among C-Level executives, leading industry experts, decision-makers, policymakers, and government officials from across the value chain to foster collaboration, discuss current challenges, and business opportunities, develop market strategies, share knowledge and identify solutions aimed at shaping the future of fire, safety and security.
There are several compelling reasons to visit the event. You can find the best solutions tailored to meet your business needs, experience live interactive demonstrations firsthand, explore cuttingedge innovations, compare different product variants in terms of prices and specifications, and network with special-
ist exhibitors representing top companies from local, regional, and international markets.
pality, and Emirates Safety Laboratory –Directorate Gen. of Dubai Civil Defense.
Some of the key supporters & associations are Advantage Austria, Dubai Council for Marine & Maritime Industries, Madayn, Arab Institute of Safety Sciences, Firestop Contractors International Association, National Fire Proofing Contractors Association, International Water Mist Association, and more.
In addition to these, OFSEC boasts a lineup of distinguished sponsors across

OFSEC is officially supported by the Civil Defense and Ambulance Authority of Oman, Ministry of Labor, Muscat Munici-

various tiers. Middle East Wealth’s LLC leads as the event’s Lead Sponsor, while Majees Technical Services, MTP Distribution, and Pointer LLC stand as Diamond Sponsors. The Platinum Sponsorship tier features prominent names such as Electroman LLC, Integrated Engineering Solutions, Bahwan Services & Trading LLC, Unity Fire & Safety, and White Rock United LLC from Oman, alongside international sponsors like Rosenbauer from Austria, Bristol from the United Arab Emirates, and Priority Dispatch Corp from the United States of America. Gold Sponsors include Al Hosni Trading & Contracting Ent., Al Khalili Group, and Green Light International from Oman, as well as Emirates Fire Fighting Equipment Factory LLC (FIREX) from the United Arab Emirates. Further supporting the event are Associate Sponsors like Key Technology from Oman, Al Aman Fire Fighting Equipment, and WatchNET International Trading LLC from the United Arab Emirates. n



Security Essen
Key Security Events in 2023
17-20 September 2024, Essen, Germany
https://www.security-essen.de

OFSEC, Oman

Intersec Saudi Arabia 1-3 October 2024, Riyadh, KSA
https://intersec-ksa.ae.messefrankfurt.com/ ksa/en.html
8-9 October 2024, Muscat, Sultanate of Oman
https://www.ofsecevent.com

ISAF Fuari
10-13 October 2024, Istanbul, Turkey
https://www.isaffuari.com

ANTICIPATE LONDON
2-4 December 2024, London, UK
https://www.anticipate-event.com/londo.../ home.html
Adria Security Summit Powered by Intersec 9-10 October 2024, Sarajevo, Bosnia and Herzegovina
https://www.adriasecuritysummit.com

Milipol Qatar
29-31 October 2024, Doha, Qatar
https://www.milipolqatar.com/en
Intersec Police Summit 14-16 January 2025, Dubai, UAE
https://intersec.ae.messefrankfurt.com/dubai/ en/programme-events/intersec-police-summit.html
















Bosch
Vendor-neutral Physical Security Information Management (PSIM)
Advancis Middle East
P.O. Box 73309
Abu Dhabi, United Arab Emirates
Tel. +971 2 444 2503
Email: info@advancis.ae
Web: https://advancis.net



United Arab Emirates Qatar Egypt Saudi Arabia info.me.open@assaabloy.com www.assaabloy.com/ae



Man Guarding
Technical protection
• Video surveillance
• Access control
• Intrusion detection
• Item theft protection
• IP and network solutions
• Perimeter protection
• Fire detection
• Gas detection
Mechanical protection Cash/valuables-in-transit
Cyber security
Digital forensics
Software solutions
Smart home
Internet of things
Security management
Investigations
Building management
Market research
Legislation and standards
Honeywell Commercial Security offers integrated security solutions within: * Video Surveillance * Access Control * Intruder Detection both as standard and cloud based systems. Contact:
Dubai: +971 4 4505 800 Abu Dhabi: +971 2 2349 101 https://www.honeywell.com/ae

m.shenawy@supremainc.com)
Tel: +971 4 2357 996 www.supremainc.com
www.saltohospitality.com


Technical
•
•
•
•
•
• Perimeter protection
•
• Gas detection
Mechanical protection
Cash/valuables-in-transit
Cyber security
Digital forensics
Software solutions
Smart home
Internet of things
Security management Investigations
Building management
Market research
Legislation and standards




Improve security standards through the implementation of laws, standards and international best practices in security systems as well as security management and guarding services.

SIRA now has more than 60,000 members working within the Dubai security industry, with the agency’s laws and guidelines helping to ensure that standards are continuously kept high

.
With employee badge in Apple Wallet, staff and visitors can open office doors, access laptops, elevators, secure printers and much more using just their iPhone or Apple Watch. It’s another way HID is enabling secure, convenient workplace access.

Get started with employee badge in Apple Wallet at: hidglobal.com/applewallet