SMART BODY-WORN





Advanced Access Control That:
Simultaneously Captures & Authenticates in Iris/Face Modes
Allows Multifactor Authentication


Works with MIFARE®/DESfire® (HID® SEOS/iCLASS®)13.56MHz
Proximity Cards
Protects Physical Infrastructures
Ensures Privacy
Co-exists with Iris ID iCAM 7 Legacy Systems
Sets Industry Standards



Make your access ready for what’s ahead
We help you digitalize and future-proof your buildings with a wide range of access solutions meeting your individual needs, supporting your move from the mechanical to the digital world. We are experts in access. With us, you digitalize with confidence.

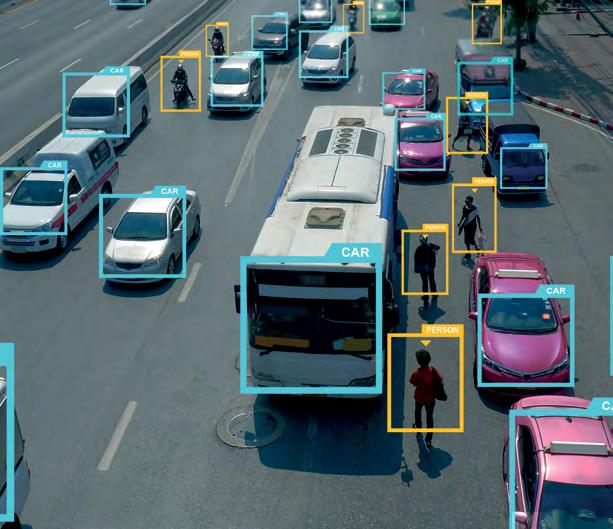
In an era where smartphones have made everything instantly shareable and live, body-worn cameras have evolved to match this always-on expectation. These devices have grown from simple accountability tools into AI-enhanced security assets that not only capture, process, and respond to incidents but increasingly support applications across diverse fields
26 Harris Chen, Chiayi District Prosecutor’s Office in Taiwan Intensive Curricula of Cyber World Education Should be Implemented from High Schools to Colleges
32 Mohammed Murad Iris ID
Biometrics Push Physical Security Beyond Keycards and PINs 34 Peter Dempsey, Axis
How indoor air quality sensors play a critical role in data centers
36 Gautam D. Goradia, Com-Sur Beyond the Hype: A Strong Case for Human-Centric AI in Security
38 HID Global
Yes, You Can Have Both Security and Convenience: Mobile Credentials and Biometrics Prove It Across the GCC 40 ASSA ABLOY
Device Range, Cyber-Security and Weather Resistance Make eCLIQ the Right Choice
security solution protects remote archaeology site
44 IRIS ID Iris Biometrics Push Physical Security Beyond Keycards and PINs
46 Genetec
Genetec brings new capabilities to Security Center SaaS
48 Aligntech
Aligntech’s Lead Forward Roadshow 2025 Showcases ForwardThinking Innovations 50 Alarm.com Alarm.com Showcases Vision and Growth in Ibiza 52 Intersec Shanghai China Emerges as a Key Security Tech Hub


Professional media for complete security solutions
Management
Mahir Hodžić, General Manager mahir.hodzic@asmideast.com
Adis Hodžić, CEO adis.hodzic@asmideast.com
Editorial Staff
Mahir Hodžić, Editor-in-Chief mahir.hodzic@asmideast.com
Orhan Hadžagić, Associate Editor orhan.hadzagic@asmideast.com
Emily Lin, Contributing Editor Emily.Lin@taiwan.messefrankfurt.com
Mirza Bahić, Journalist editorial@asmideast.com
Nermin Kabahija, Journalist editorial@asmideast.com
Art Staff
Sanel Palislamović, Art&Design Editor sanel.palislamovic@asmideast.com
Nelmedin Kolubara, DTP&Art Design dino.kolubara@asmideast.com
Sales Amar Pap, Business Development Manager amar.pap@asmideast.com
International Sales Israel Gogol, International Sales Director Israel.Gogol@taiwan.messefrankfurt.com
International Associates Qatar – Mirsad Selimović, mirsad@techman.qa
a&s Middle East offers the latest news and insights on video surveillance, access control, intrusion detection, fire alarm, mechanical protection, man guarding, cyber security, artificial intelligence, IoT, big data, smart homes and buildings, industrial automation, information, communication technology to Middle East region professional channel players.
a&s Middle East is part of the media network of the Messe Frankfurt Ltd – Taiwan Branch, which offers several media platforms — asmag.com and a&s magazines, published in English, traditional Chinese, and three other languages, providing the most comprehensive industry trends, product, and supply chain information. The total annual circulation is approximately 515,000 copies around the globe.
a&s Middle East is published 6 times a year, Jan/Feb, March/ April, May/June, July/August, Sept/Oct, and Nov/Dec.
Payment Instructions
Annual subscriptions are payable in USD, EUR, or AED. Subscription inquiries per your request.
EUR: AE340400000653005131002
Account No. 0653005131002
USD: AE070400000653005131003
Account No. 0653005131003
AED: AE610400000653005131001
Account No. 0653005131001
Copyright Statement
© Copyright by Privus Agency Ltd. All rights reserved. Any republication, copying, redistribution, or reproduction of the magazine in any form, including electronic, without the prior written consent of the publisher, is prohibited. Advertisers are solely responsible for the content of advertising material. The publisher bears no responsibility regarding possible legal, patent, content, or brand disputes of the advertiser.
Legal Disclaimer
The information in this magazine has not undergone any formal testing by Privus Agency Ltd. and is distributed without any warranty expressed or implied. Implementation or use of any information contained herein is the reader’s sole responsibility. While this information has been reviewed for accuracy, there is no guarantee that the same or similar results may be achieved in all environments.
Corporate Address
Privus Agency FZ-LLC
JT010006, Al Shohada Road, Ras Al Khaimah, UAE
Tel: +971 58 983 4258
Web: www.asmideast.com
The Human Element in an Age of Hi-Tech Security
Welcome to the 15th edition of a&s Middle East, where we delve into the evolving balance between human insight and advanced security technologies.
In our cover story, we examine how body-worn cameras have evolved far beyond simple recording devices into AI-enhanced intelligence platforms. These smart systems now offer real-time threat detection, facial recognition, and encrypted live-streaming capabilities—transforming passive documentation into active security intelligence. Whether in retail settings or during high-stakes emergency responses, these devices show how technology can sharpen human perception and support faster, more informed decisions.
Complementing this technological focus, our interview with prosecutor Harris Chen from Taiwan’s Chiayi District Prosecutor’s Office reveals a fundamental truth about security: even the most sophisticated systems remain vulnerable to human psychology. With 17 years of experience investigating cybercrime and fraud, Chen highlights how easily unseen threats slip past even the most advanced security measures—often due to simple human oversight.
Together with other topics we tackle in this issue, these pieces underscore a vital principle for security professionals across the Middle East: effective protection requires both smart technology and even smarter understanding of human factors. As body-worn cameras stream encrypted data to command centers, the security of that transmission becomes as critical as the physical incident being recorded. When AI systems detect suspicious behavior, human judgment remains essential for appropriate response.
In today’s environment of heightened regional tensions, this human-technology partnership becomes even more crucial. Security professionals must navigate complex threat landscapes where traditional perimeters extend into digital domains, and where the reliability of both technological systems and human operators determines operational success.
Join us as we look at how this blend of human expertise and technology is redefining physical security across industries, regions, and some of the most complex environments in the world.
Marketing: marketing@asmideast.com WANT TO RECEIVE THE MAGAZINE AT YOUR DOORSTEP?
Please visit our official website www.asmideast.com and select ‘Subscribe Now’ option under THE MAGAZINE menu.
Subscription includes all six editions.
Digital edition is FREE and readily available at the official website.

Mahir Hodžić, General Manager
FOBOS XR FULL-BODY FORENSIC RADIOGRAPHY SYSTEM
The perfect solution for morgues, coroners and forensic centers

The FOBOS XR is an advanced system capable of capturing high-resolution X-ray images of a body for non-invasive forensic pathology examinations. With the ability to capture detailed and clear images, it enables pathologists to determine causes of death and to assess the damage caused by trauma. The FOBOS XR Body Scanner can provide detailed analysis that is required for research into human tissue, organs and bones that are often outside of traditional imaging capabilities. You can use this device for the examination of road traffic accidents, suicide cases, as well as homicides, drownings, or other difficult situations.
KSA ANNOUNCES FIRST TRIAL OF DRONE-BASED MEDICINE DELIVERY IN HOLY SITES
The healthcare system announced the successful pilot launch of drone-based medicine delivery between primary healthcare centers and hospitals in the holy sites, marking a significant milestone and a first-of-its-kind initiative. The project aims to enhance the efficiency of healthcare services provided to pilgrims during the 1446 Hajj season.
The achievement was made possible through active collaboration between the Makkah Health Cluster and the National Unified Procurement Company (NUPCO), which jointly ensured the supply of medicines and medical equipment to the holy sites using drones.
The initiative is designed to accelerate response times and support healthcare operations by delivering medicines and medical supplies during Hajj. In one key instance, Mina Emergency Hospital received a drone delivery of ice packs used for treating heat exhaustion and sunstroke, as part of intensified preparedness efforts coinciding with the start of

the stoning ritual on the first day of Eid Al-Adha.
The drone-based delivery service follows a multi-phase process starting with preparation, including determining quantities and coordinating with healthcare facilities. Next is packaging using advanced technology in line with Saudi Food and
Drug Authority regulations. Then, medical, pharmaceutical, and laboratory items are processed, issued, and delivered to healthcare locations across the holy sites. The final phases include transport scheduling and real-time tracking via a central monitoring dashboard to ensure smooth operations. n
SMART CITIES MARKET TO SURPASS $1.4 TRILLION BY 2030, DRIVEN BY ASIA PACIFIC SURGE
The smart cities sector is expected to reach $1,445.6 billion by 2030, growing from $699.7 billion in 2025 at a CAGR of 15.6%, according to Marketsandmarkets. Smart cities leverage technologies like IoT, AI, and smart grids to boost urban living, optimize resources, and support sustainability. These advancements
improve efficiency, reduce emissions, and enhance safety in utilities, transport, and public services.
Rapid urbanization, environmental concerns, and infrastructure needs are key drivers for smart city adoption, spanning smart waste management to green buildings. In particular, commercial smart

buildings lead the segment by deploying BMS, AI-driven space usage, and IoT sensors to cut energy use, boost security, and minimize costs.
Passenger information management (PIM) is the fastest-growing area within smart transportation, using real-time data to inform commuters and reduce traffic. Integrated with mobility solutions, PIM enhances accessibility and meets the demand for sustainable transport.
The Asia Pacific region is poised for the highest growth due to urbanization, rising middle-class populations, and government investment in smart infrastructure, especially in India and China. Initiatives like India’s Smart Cities Mission and China’s New Urbanization Plan are accelerating adoption. Key players driving this market include Cisco, IBM, Microsoft, Siemens, Hitachi, Schneider Electric, Huawei, NEC, and ABB, using strategies such as partnerships and acquisitions to expand their global presence and meet growing smart city demands. n




SIRA SHOWCASES
THE “MURAQIB” PROGRAM DURING ITS PARTICIPATION IN THE WORLD POLICE SUMMIT
The Security Industry Regulatory Agency (SIRA) participated in the World Police Summit 2025 Exhibition and Conference as part of its strategic plan to maintain a strong presence at key international security forums. In its second participation at the summit, SIRA is showcasing its latest projects that directly contribute to enhancing collaboration between security entities, reflecting its steadfast commitment to supporting Dubai’s vision of a safer and more sustainable society. Among the key highlights at the agency’s pavilion is the “Muraqib” program, in addition to the impactful participation of the Professional Security and Safety Association (PSSA).
SIRA launched the “Muraqib” program, one of the latest technological initiatives developed by the agency’s Specialized Projects Department. The program aims to secure and monitor the movement of hazardous material shipments within the Emirate of Dubai through an integrated system that includes an advanced track-

ing device, a high-resolution surveillance camera, a smart electronic lock, and a central operations room responsible for full supervision and control of the shipments’ movement.
This system represents a significant advancement from the previous method, which relied on escorting hazard-
ous material transport trucks with an additional security vehicle. “Muraqib” marks a major step forward in reducing dependence on human resources, improving control, and increasing operational efficiency, ultimately enhancing safety levels while achieving tangible operational savings. n
SHARJAH STARTS FIRE SAFETY IN BUILDING CAMPAIGN
Sharjah has initiated a comprehensive fire safety campaign to enhance building safety standards ahead of the summer season, a period when high temperatures elevate fire risks. This initiative is a collaborative effort between Saned Facility Management, the Sharjah Civil Defence Authority, and the Sharjah Prevention and Safety Authority.
Key Objectives and Strategies:
• Inspection and Maintenance: The campaign focuses on assessing and improving the performance of fire alarm and early warning systems across various buildings in Sharjah. Particular attention is given to structures identified by the ‘Aman’ system as having technical faults.
• ‘Aman’ System Integration: Central to this effort is the ‘Aman’ system, an integrated digital platform that connects building fire alarms directly to the operations centers of both the civil defence and Saned. This connectivity allows for real-time monitoring and quicker detection of faults, facilitating faster emergency responses.
• Stakeholder Engagement: Building owners and property managers are being notified about identified issues and are encouraged to conduct timely maintenance using contractors officially approved by civil defence authorities.
• Continuous Monitoring: The campaign is ongoing, with no fixed end date, em-
phasizing the importance of regular system checks and maintenance to ensure the effectiveness and responsiveness of safety infrastructure. This initiative reflects a shared commitment to public safety and operational readiness, aiming to resolve issues proactively before emergencies arise. n


Secur n o l& s nfr s ruc ure n he M ddle E s for over 15 ye rs.



INTERSEC SAUDI ARABIA RETURNS WITH RECORD
EXHIBITION SPACE SHOWCASING INNOVATIONS SECURING KINGDOM’S FUTURE
Intersec Saudi Arabia, the premier industry platform for security, safety and fire protection, will return to the Riyadh International Convention and Exhibition Centre (RICEC) from 30 September to 2 October.
Aligning global innovation with national priorities, Intersec Saudi Arabia brings together government authorities, industrial leaders and international solution providers to secure the infrastructure, environments and communities building the nation’s prosperous future.
Organised by 1st Arabia and licensed by Messe Frankfurt, Intersec Saudi Arabia will be held in association with a range of government entities under the theme Securing progress, igniting safety: Unveiling tomorrow’s solutions for Saudi Arabia. With a series of giga-projects underway in Saudi Arabia, including Neom, Qiddiya, and Red Sea Global, and major global events on the horizon, such as Expo 2030 and the 2034 FIFA World Cup, the Kingdom is undergoing a significant transformation. Together, these developments mark a pivotal moment in Saudi Arabia’s evolution, positioning it as a key player in global tourism, sports, and industry.
Bilal Al Barmawi, CEO and Founder of 1st Arabia Trade Shows & Conferences, said: “Intersec Saudi Arabia provides an im-

portant platform for decision makers across Saudi Arabia’s major projects to connect with global innovators and work together to build a secure, future-ready environment. We look forward to facilitating important business connections that support the country’s growth and long-term success.” n
ABU DHABI CIVIL DEFENCE AUTHORITY
AND E& PARTNERED
TO
ACTIVATE EARLY FIRE DETECTION SYSTEMS IN HOMES
The Abu Dhabi Civil Defence Authority and e& have partnered to activate early fire detection systems in homes by installing, operating and managing the “Hassantuk for Homes” electronic system, thereby enhancing preventive safety standards within homes across the UAE capital.

The partnership covers the provision of smart infrastructure capable of detecting fires in their earliest stages and reinforces home safety by installing an AI-enhanced Hassantuk smart system, with direct connectivity to control rooms.
The collaboration highlights the use of artificial intelligence to identify potential hazards in their earliest stages, significantly reducing risks to life and property. It also supports the broader goal of achieving the highest civil safety standards through innovative sensing technologies.
The UAE Cabinet had mandated the installation of Hassantuk systems in all existing and under-construction residential villas from January 1, 2024. As of 2024, Hassantuk for homes covered over 50,000 villas in the UAE and successfully detected over 400 fires.
The Hassantuk programme aims to support the achievement of the UAE National Agenda 2021 in becoming one of the safest countries in the world as well as sustaining the reduction of the rate of fires and fire related deaths compared to numerous countries worldwide.
It is largest and first project of its kind, targeting over 500,000 buildings and private housing at a Federal level. n

READERS WITH UNLIMITED POSSIBILITIES






www.xpr-readers.com
Strong and elegant, the Xpro range combines multi-technology security with full customization. Powered by Xsecure®, it delivers a unique layer of advanced protection.
Compatible with MIFARE® (13.56 MHz) and supporting RS-485, OSDP, and Wiegand, Xpro is easy to configure via USB-C or programming card.
Includes free setup software, and is certified IK10 / IK11, IP65, withstanding -30 ºC to +65 ºC.
UAE’S $3.7B TECH ECONOMY TAKES SPOTLIGHT IN GITEX EUROPE
Europe’s largest inaugural tech, startup, and digital investment event, GITEX EUROPE x AI Everything, was held at Messe Berlin this week, with the UAE’s innovation taking centre stage.
The three-day show, which concludes today, brought together more than 1,400 exhibitors, 600 top global investors, and over 500 speakers from 100-plus countries, together marking the strongest cross-border tech mobilisation the continent has seen. National pavilions stretched from India to Italy, Morocco to South Korea, and 35 European states, alongside participation from the UAE, showcasing how the nation is becoming a global reference for technology advancement across multiple industries, including governance and public service.
The UAE’s IT services market is forecast to achieve record growth to reach $3.76 billion in 2025, according to fresh Statista data, a momentum that was impossible to miss on a show floor featuring 65 UAE organisations – the nation’s biggest ever

entrepreneurship and digital investment delegation to a European tech event.
The Ministry of Economy pavilion presented a cohort of home-grown tech ventures aimed squarely at addressing global challenges. Among them are Zeroe, which delivers comprehensive carbon management to accelerate net-zero goals; Hikmah
Labs, which merges AI with cutting-edge research to transform industries; IngenioData, which deploys AR and BLE-based indoor navigation, asset tracking, and analytics; and Responsive Drip Irrigation, which created the world’s first plant-responsive irrigation system, which allows the plant to self-regulate its own water delivery. n
GOOGLE LAUNCHES SECOND ‘AI FIRST’ ACCELERATOR FOR MENA, TURKIYE STARTUPS
Google announced the launch of its second “Google for Startups Accelerator: AI First” programme for the Middle East, North Africa, and Turkiye (MENA-T). The 12-week, equity-free programme is designed to empower the most promising Seed to Series A startups that are harnessing the power
of artificial intelligence, providing them with the essential infrastructure, tools, and expertise to scale and succeed.
The MENA-T region is rapidly emerging as a significant hub for AI innovation, driving transformative change across various industries. Highlighting this potential,

PwC estimates AI could contribute $15.7 trillion to the global economy by 2030, with McKinsey projecting up to $150 billion for GCC countries alone. Regional AI investment is also accelerating, with its share of total startup funding more than doubling year-over-year from 2023 to 2024, according to Wamda reports. PwC further expects the region to accrue US$320 billion, or 2 percent of the total global benefits of AI, by 2030.
“The incredible momentum of AI development in the Middle East, North Africa, and Turkiye region presents a unique opportunity to foster a new wave of technological advancement,” said Abdul Rahman Al Thehaiban, Managing Director, MENA-T, Google Cloud. “Google Cloud is committed to providing a robust and scalable platform for AI innovation. Our aim is to equip these pioneering companies with the cloud infrastructure and expertise necessary to optimize their AI workloads and accelerate their growth trajectory in this dynamic field.” n
5 - 6 November 2025,




Body-Worn Cameras
SILENT WITNESS NO MORE: SMART BODY-WORN CAMERAS GO LIVE
In an era where smartphones have made everything instantly shareable and live, body-worn cameras have evolved to match this always-on expectation. These devices have grown from simple accountability tools into AI-enhanced security assets that not only capture, process, and respond to incidents but increasingly support applications across diverse fields
n By: Mirza Bahić mirza.bahic@asmideast.com
Body-worn cameras are no longer silent witnesses—they’re intelligent, networked, and mission-critical. Equipped with advanced optics, encrypted livestreaming, and integrations that support AI-driven analytics, today’s body-worn cameras are becoming essential tools across frontline operations. In retail, they flag suspicious behavior and generate courtroom-ready evidence. In emergency response, they cut through chaos, functioning in smoke-filled environments and delivering real-time insights that drive life-saving decisions. And the evolution goes well beyond public safety and commercial applications. The technology has even reached sports and entertainment. At the 2025 FIFA Club World Cup, miniature cameras mounted on referees’ headsets capture live match footage from unprecedented angles. These devices stream unique perspectives of goals and key moments while broadcast directors make real-time editorial decisions about which footage to feature. It’s a telling example of how body-worn camera technology has expanded far beyond its security origins into entertainment, sports, and countless other sectors.
This isn’t the body-worn camera technology of five years ago. What began as simple recording devices for police accountability has evolved into a sophisticated ecosystem where advanced optics, edge AI, and cloud-based evidence management converge. Today’s body-worn cameras represent a fundamental shift in how organizations approach safety, security, and operational transparency, transforming from passive documentation tools into active intelligence platforms.
Market Surge and Innovation Drive Evolution
The numbers underscore this rapid expansion. Spherical Insights projects the global body-worn camera market will surge from $7.48 billion in 2023 to $27.65 billion by 2033—a remarkable 13.97% compound annual growth rate. This growth reflects not just increased adoption in traditional security roles, but explosive diversification into new applications across industries.
“More than 18,000 law enforcement agencies in more than 100 countries
deploy Axon products and technology,” notes Anas Hammouri, Director of the Middle East, Turkey & Africa at Axon. This global footprint illustrates how bodyworn cameras have become indispensable tools in modern security.
Martin Ekman, Business Development Director for Body-Worn Solutions at Axis Communications, echoes this sentiment.
“We’ve been fortunate enough to sell our solution to around 50 countries globally, with a significant number of those being in the EMEA region.” He highlights substantial deployments, adding, “One of our biggest law enforcement installations has over 17,000 body-worn cameras, and we’ve also had some substantial successes in prisons, where we’ve deployed over 6,000 cameras.” Ekman further points out that “body-worn cameras are quickly becoming standard issue and, in many places, even mandatory,” underscoring their growing importance and ubiquity.
Behind these projections lies a technological revolution. Modern body-worn cameras fuse high-definition imaging, advanced audio capture, real-time analytics, and end-to-end encrypted workflows into platforms that would have seemed like sci-
ence fiction just a decade ago. This evolution represents more than technological advancement. It signals a fundamental transformation in how organizations ensure accountability, enhance operations, and manage critical incidents in an increasingly complex security landscape.
Transforming Public Safety
Beyond operational improvements, bodyworn cameras have matured enough to offer measurable financial benefits. Leslie Li, Deputy General Manager of BWC Business Unit at Hytera, reports that reduced crime and fewer complaints translate into significant savings in the ballpark of tens of thousands of dollars, which, according to him, are achieved by cutting down costly investigations and litigation. Enhanced suspect identification is aided by facial recognition technologies integrated into their modern BWCs. “These have successfully assisted frontline officers in discovering several potential suspects”, says Li. He adds that a public safety department in an unnamed country experienced an 18.7% reduction in crime rates within six months of adopting body-worn cameras.

IN FOCUS




A similar trend is visible outside traditional law enforcement. Since May 2024, Slovakia’s ZSSK railway company has equipped its train drivers with 419 Axis body-worn cameras, resulting in a 5% decrease in overall incidents and a 21% drop in aggression toward staff and passengers. Beyond deterrence, the cameras helped clarify around 50 cases, with police repeatedly praising their high evidentiary value in investigations.
Axon’s Hammouri describes a similar trend in Spain, where la Policía Foral de Navarra saw a 50% drop in violence and misconduct incidents against officers
during the San Fermín Festival, thanks to Axon body cameras. Officers equipped with Axon Body 3 cameras observed that the mere presence of the cameras improved attendee behavior. Police authorities noted that, in complicated situations, the awareness that actions were being recorded by the police had a deterrent effect.
Furthermore, the recordings promoted transparency in officer-civilian interactions, reinforcing the agency’s commitment to meeting community expectations. By balancing effective law enforcement with citizens’ privacy and peace of mind, body cameras contrib-
uted significantly to bolstering security during the annual Running of the Bulls while maintaining accountability in policing efforts.
According to Hammouri, Italy’s Ravenna police also recorded a 50% reduction in incidents when comparing Q1 2021 to Q1 2020. A similar approach was adopted by Greater Manchester Police, who leveraged Axon’s body-worn cameras with live streaming at the Parklife festival. This granted commanders realtime situational awareness directly from the field, enabling more efficient coordination, better communication with event organizers and paramedics, and

Anas Hammouri, Director of the Middle East, Turkiyë & Africa, Axon
Erik Frännlid, Director, New Solutions Initiatives - Products and CTO Organization, Axis Communications
Robert van Dijk, Sales Manager, Zepcam
Leslie Li, Deputy General Manager of BWC Business Unit, Hytera
ultimately enhancing officer and public safety through quicker, better-informed decisions.
Post-event debriefs also benefited from the recorded footage, allowing teams to review specific incidents, refine tactics, support prosecutions, and improve festival policing over time. Officers further noted that simply wearing the cameras had a measurable calming effect on crowd behavior, helping deter anti-social conduct on site while still ensuring a reliable evidentiary record when needed.
Body-Worn Cameras Gain Ground in Commercial and Public Spaces
Body-worn cameras are rapidly expanding their utility beyond traditional law enforcement, revolutionizing operations across diverse sectors such as emergency services, healthcare, education, retail, transportation, and aerospace/defense. This multi-sector adoption highlights the versatility and significant impact of BWC technology in addressing a wide range of operational and safety challenges.
In fact, the cameras’ impact on de-escalation now extends beyond law enforcement, reaching other high-risk environments where safety and conflict management are critical. For instance, in 2024, Axon launched the dedicated Axon Body Workforce, a body-worn camera designed specifically to address workplace violence affecting frontline workers in retail stores and healthcare facilities. Meanwhile, Axis has demonstrated the effectiveness of its camera solutions in other settings. Erik Frännlid, Director of New Solutions Initiatives - Products and CTO Organization at Axis Communications, describes what happened following the installation of Axis cameras at a major UK airport. One of the airline attendants remarked, “The de-escalation factor is huge — many situations that are about to escalate stop right away when they notice the camera. And I’ve never even started it yet.” These examples highlight how bodyworn cameras are becoming essential tools across diverse sectors to promote safety and reduce conflict.
By 2024, major retailers like Tesco, Coles, and TJ Maxx plan to standardize

While not strictly a security function, body cameras provide crucial legal protection for healthcare organizations and their staff
BWCs for loss prevention, with surveys showing over half of retailers investing in wearable video technology. Transportation agencies are also embracing BWCs, as transit systems such as the U.K. National Highways, Swedish Rail, and the Rio de Janeiro metro adopt integrated bodycam solutions.
Some of these users are already reporting notable results: a U.S. trial retailer experienced a 53% reduction in incidents, while another noted that 47% of active incidents were effectively de-escalated once recordings were activated, according to Hammouri.
In education, teachers are beginning to use body-worn cameras for training and behavioral management, leveraging ob-
More than 18,000 law enforcement agencies in more than 100 countries deploy Axon products and technology
jective records for professional develop ment. This wider adoption underscores BWCs’ effectiveness across operational contexts—from de-escalating incidents in retail and transport to providing valuable training insights in education.
From Security to Training Excellence in Healthcare
Yet, the poster child for non-security applications of BWCs might be healthcare. In fact, one of the most valuable nonsecurity applications of body cameras in healthcare settings is their use as training and professional development tools. The experience of CoxHealth, a premier US-based healthcare system, with Axis body cameras illustrates how these devices can serve multiple non-security functions that enhance patient care, staff development, and organizational operations.
IN FOCUS
Supervisors and officers regularly review camera recordings not for disciplinary purposes, but for educational growth and skill enhancement. The recordings provide an objective perspective that allows healthcare staff to step back from high-stress situations and analyze their responses with clarity. This continuous learning approach contributes to improved patient satisfaction and safer healthcare environments for everyone involved.
Body cameras now serve as invaluable documentation tools for healthcare incidents, providing accurate, timestamped records that support quality improvement initiatives. The detailed audio and video records capture nuances that written reports might miss, including tone of voice, body language, and environmental factors.
While not strictly a security function, body cameras provide crucial legal protection for healthcare organizations and their staff. The objective documentation can protect against false claims and provide accurate records for legal proceedings. All of these healthcare use cases demonstrate that body-worn cameras have evolved far beyond their original security-focused applications, now serving as comprehensive tools for organizational improvement by enhancing training, fraud protection, documentation, communication, and overall quality of care.
Built by Those Who Use Them
Body-worn cameras are increasingly being shaped by those who use them daily. For many manufacturers, direct input from police officers, security personnel, transport workers, and emergency responders has become essential to product development.
Axis Communications, for instance, worked closely with law enforcement teams across Europe and the U.S. during early development. Officers stressed the importance of handling difficult lighting and minimizing motion blur, says Erik Frännlid, Director of New Solutions Initiatives - Products and CTO Organization at Axis Communications.
They also asked for cameras that were easy to carry and operate in high-stress situations. This input directly influenced the device design and continues to guide software updates through Axis’s operating system.
Hytera also actively gathers input from frontline users through a dedicated research team, says Leslie Li, Deputy General Manager of Hytera’s BWC Business Unit. Users highlighted the need for longer battery life, improved audio clarity, and devices that can withstand harsh environments. In response, Hytera enhanced battery performance, integrated noise cancellation and more powerful speakers, and made their devices more rugged.
Going beyond physical performance, Axon added another layer by embedding ethical considerations into its design philosophy. According to Anas Hammouri, Director for the Middle East, Türkiye, and Africa at Axon, user feedback has helped shape privacy settings, user controls, and data protection features. The company’s development approach integrates customer input with guidance from ethics experts to ensure responsible innovation.
Innovations in Design and Durability for Modern BWCs
Modern body-worn cameras represent a dramatic leap from earlier generations, engineered as smart, resilient tools for complex, high-pressure environments.

Body-worn cameras are quickly becoming standard issue and, in many places, even mandatory
Axon’s Body 4 camera, for instance, integrates 5-megapixel resolution, a wide 160° field of view, and a 4:3 aspect ratio that enhances vertical visibility by nearly 40%. Its 3400 mAh battery provides coverage even with demanding features active, while the IP68 rating ensures dust and water resistance for rugged field conditions.
Axis Communications emphasizes the demand for robust construction through open architecture, delivering high-quality video and audio performance that earned recognition, including a Red Dot Award for ergonomic design. Their cameras incorporate Wide Dynamic Range and Electronic Image Stabilization, and proprietary. Finally, Axis Zipstream compression technology reduces file sizes while maintaining image clarity, and the units meet IPX5/IPX8 waterproof standards for reliable operation across various environments.
Similarly focused on flexibility and adaptability, Zepcam provides modular solutions allowing customization in software, camera types, and mounting configurations for both public and commercial clients. Their systems support national cloud or on-premise setups, offer infrared capabilities for low-light environments, and include external

configurations for helmets or uniforms. Smart sensor and audio processing enhance performance in motion-heavy scenarios.
Hytera adds another dimension with devices designed around frontline safety, integrating unique alert systems that bolster officer security. “Our BWCs also support intercommunication with narrowband radios, enhancing communication flexibility and reliability… if an officer falls down, the BWC lens is blocked, or someone tries to tamper with the device, our equipment immediately sends alerts to the command center,” says Li. These safety features combine with AIdriven noise cancellation, image stabilization, super wide-angle lenses, starlight night vision, and infrared capabilities for reliable performance in harsh environments.
Advanced Connectivity Enables Dynamic Situational Awareness
Modern BWCs prioritize robust connectivity to function as integrated network nodes rather than standalone recording devices. Axon’s Body 4 exemplifies this approach through GPS location sharing, bidirectional communication, and livestreaming capabilities. As Hammouri explains, “Each connected Axon Body 4 becomes a live node in a broader, smarter network,” enabling real-time coordination and immediate data sharing. Another company advancing connected capabilities is Zepcam. Its body-worn
Reduced crime and fewer complaints translate into significant savings in the ballpark of tens of thousands of dollars, which are achieved by cutting down costly investigations and litigation
cameras feature advanced sensor and audio processing, with infrared illumination available to enhance image capture in low-light environments. The proprietary Secure Link technology dynamically manages wireless video and data transmission, optimizing performance in highly variable network conditions such as 4G and Wi-Fi. A dedicated antenna is incorporated to improve connectivity and signal stability in challenging 4G coverage areas.
Hytera extends this emphasis on intelligent connectivity. According to Li, Hytera’s terminals support hybrid communication and real-time positioning, enabling comprehensive situational coordination beyond simple documentation. This connectivity infrastructure ensures high-performance data transmission even under pressure, facilitating immediate response and command center coordination.
Moreover, as Li explains, the BWC solution “supports the synchronization of track and evidence,” automatically linking evidence cases to their geographic locations. This capability enables a simultaneous display on the same screen, providing law enforcement personnel with a multi-dimensional playback of the truth
The public safety department experienced an 18.7% reduction in crime rates within six months of adopting body-worn cameras
and comprehensive, precise information support.
The Rise of Intelligent Analytics and AI
AI-driven features are fundamentally reshaping BWC capabilities from reactive recording tools to proactive intelligence platforms. Axon recently introduced Draft One, an AI-powered report-writing assistant that cuts paperwork time by over 40%.
The company has also introduced Axon Assistant, a voice-powered AI system providing real-time translation (supporting over 50 languages), voice-enabled policy chat with citations, general Q&A functionality, and situational support directly from officers’ vests. Hammouri notes this tool “immediately bridges language barriers” while continuously evolving to include future capabilities like license plate lookup and weather updates. New Axon Assistant skills, including voice-driven license plate lookup and weather queries, are planned for release later this year as part of their fixed-cost AI Era Plan.
Supporting and expanding on such AI capabilities, recent academic research— including an April 2025 case study with Rochester PD—demonstrates AI’s potential to detect behavioral patterns, including escalation versus de-escalation, in real time through combined video, audio, and natural language processing. These
analytical capabilities promise to assist command centers in both post-event analysis and proactive supervision. At the same time, Axis focuses on an open architecture strategy that enables seamless integration with third-party analytics platforms. Partners can access live video streams and overlay real-time intelligence for advanced situational assessment.
Finally, Zepcam focuses on triggered recording and streaming with features like remote ON/OFF and panic button activation, delivering excellent low-latency live streaming performance.
EMEA Rides the Adoption Wave
Body-worn cameras are finding increasingly diverse applications across EMEA, and all four interviewed companies— Axon, Axis, Hytera, and Zepcam—point to accelerating adoption trends. The adoption of body-worn cameras in law enforcement continues to expand across multiple countries, with several major implementations taking place in 2025. Luxembourg is preparing to equip
Turkey’s Accelerated Bodycam Rollout
Turkey has also embraced body camera technology as part of a major enhancement to its law enforcement operations. Beginning in June 2025, both the Police Department and the Gendarmerie General Command have implemented widespread deployment of body cameras among field personnel. In 2025, Interior Minister Ali Yerlikaya announced plans to equip all police and gendarmerie officers with body cameras featuring integrated facial recognition technology by the end of the year.
These cameras, developed by defense contractor ASELSAN, feature advanced capabilities including real-time monitoring and recognition technology that can instantly identify wanted suspects and vehicles involved in criminal activities.
its Grand Ducal Police officers with body cameras starting July 1, 2025. Scotland has initiated an ambitious nationwide rollout of body-worn video cameras for Police Scotland, beginning in March 2025, with 10,500 cameras distributed over an 18-month period, targeting all frontline officers.
Across the Gulf Cooperation Council (GCC) countries, body-worn cameras are gradually becoming a fixture in law enforcement and security operations, though deployment levels differ sharply.
A U.S. trial retailer experienced a 53% reduction in incidents, while another noted that 47% of active incidents were effectively de-escalated once recordings were activated
The United Arab Emirates (UAE) leads the region. The UAE began exploring body-worn cameras in 2015, when Dubai Police launched a six-month trial involving 80 officers. In 2020, Sheikh Mohammed bin Rashid Al Maktoum issued Resolution No. 14, formally authorizing the use of security cameras by Dubai Police in public areas, including strict privacy rules prohibiting unauthorized transfer or publication of footage. Since then, both Dubai and Abu Dhabi Police have formally adopted

IN FOCUS

Police also recorded a 50% reduction in incidents when comparing Q1 2021 to Q1 2020
BWCs. Abu Dhabi updated its policy in January 2025 to mandate that devices be visible on officers’ uniforms, that detainees be informed when recording starts, and that all footage be securely handled and shared only following official authorization.
Building on this momentum, Hytera’s Li confirms that their BWCs are already in use in Saudi Arabia, the UAE, the UK, and across Eastern Europe, where new mandates are requiring law enforcement personnel to wear cameras on duty.
Van Dijk of Zepcam notes that customers are increasingly drawn to “a secure European solution,” with deployments now spanning “a few tens of countries in EMEA.” He adds that increased demand for system integration and flexible deployments, including commercial use, is shaping their development roadmap.
All of these examples align with market observers’ notes that commercial interest—especially from sectors like retail, private security, and transportation—is rapidly rising, supported by both practical need and regulatory alignment. At the same time, regional variations highlight the evolving regulatory landscape and the differing paces of adoption between public and commercial sectors.
Overcoming Privacy and Cybersecurity Hurdles
While the benefits of body-worn cameras are clear, security professionals must also consider the critical challenges associated with their implementation, including privacy concerns, overall costs, interoperability issues, and cybersecurity vulnerabilities. The security of digital evidence has become paramount in modern deployments. As Van Dijk explains, “We
The detailed audio and video records capture nuances that written reports might miss, including tone of voice, body language, and environmental factors
manage security along the chain, from recording on the device till viewing the recording.”
The deployment of BWCs, particularly those with experimental AI features like live facial recognition, raises significant privacy concerns. In 2024, UK police scanned nearly 5 million faces using similar technologies, prompting civil liberties groups like the Ada Lovelace Institute to call for greater oversight or bans on realtime biometric surveillance.
Vendors are responding to these concerns with comprehensive security architectures and privacy-by-design principles.
Physical security forms the foundation of these efforts. “The video data is stored on a non-removable hardware component. Unauthorized access via USB is not possible,” notes van Dijk, highlighting how manufacturers are addressing potential vulnerabilities at the device level.
Advanced encryption and authentication protocols extend protection throughout the data lifecycle. Axis uses AES256 encryption, secure boot, and signed firmware, complying with ISO/ IEC 27001:2022 and ETSI EN 303 645 standards. The company’s signed video technology addresses a growing concern in the digital age. “In times of AI manipulation, this is becoming increasingly important to verify that video has not been tampered with and remains authentic,” says Frännlid.
Another company, Hytera, offers end-toend encryption from camera to cloud and adds frame-level AES256 encryption with signature verification.
Building on this foundation of rigorous data protection, Axon’s cloud-based Axon Evidence platform ensures data immutability, with audit logs and watermarks to safeguard traceability and forensic integrity. As part of preserving the chain of custody, a serial number is burned into the evidence watermark at the time of recording as an immutable marker that cannot be altered by users or administrators. The original file and metadata remain intact, and every assignment or reassignment of a camera is logged in the device’s audit trail, ensuring that the identity of the camera operator at the time of each recording can always be confirmed. These features not only support evidence review but can also relay real-time location data during active recording. Similarly, their approach includes signed firmware updates, two-factor

authentication, and encrypted serverside storage, along with robust hardware-level protections to ensure endto-end data security. The company is also certified to the ISO 27001:2022 standard.
Despite these comprehensive security efforts, ongoing dialogue and robust regulatory frameworks remain crucial to balance security needs with individual privacy rights.
Interoperability and Implementation Costs
Seamless integration of body-worn cameras with existing dispatch platforms, digital evidence management systems (DEMS), and video management systems (VMS) remains a significant challenge for organizations deploying these technologies. While vendors such as Axis, Zepcam, Hytera, and Axon emphasize open APIs and broad integration capabilities, ensuring true interoperability across diverse vendor ecosystems can be complex. Agencies must carefully evaluate whether proposed BWC solutions can effectively communicate with their current infrastructure without causing data silos or workflow disruptions.
Beyond technical integration, implementing a comprehensive BWC program requires significant financial investment that extends well beyond
Recent academic research demonstrates AI’s potential to detect behavioral patterns—including escalation versus de-escalation—in real-time through combined video, audio, and natural language processing
hardware costs. Total cost of ownership encompasses data storage—often cloud-based—evidence management software, necessary upgrades to network infrastructure for live streaming, ongoing device maintenance, and training personnel. Although return on investment (ROI) figures vary by deployment, agencies must conduct thorough cost-benefit analyses to account for these long-term operational expenses, including the increased demand on IT resources. For example, Police Scotland’s £33 million investment in digital evidence systems underscores the scale of financial commitment required for full deployment.
This substantial investment underscores how implementing body-worn cameras involves not only procuring the devices themselves but also developing the necessary digital infrastructure to securely store, manage, and utilize the vast amounts of video evidence they produce.
Together, these factors emphasize the
In times of AI manipulation, this is becoming increasingly important to verify that the video has not been tampered with and remains authentic
need for careful planning and resource allocation to ensure that body-worn camera programs deliver sustainable operational value without compromising financial sustainability, security, or efficiency.
The Trust Equation
Body-worn cameras have evolved from simple recording devices into AI-powered intelligence platforms, reshaping security, safety, and transparency across industries. Their expanding capabilities now prove essential in retail, healthcare, transportation, and emergency services beyond traditional law enforcement. This rapid advancement, however, brings complex trade-offs. Privacy concerns, cybersecurity vulnerabilities, and implementation costs require careful navigation, while varying regional regulations complicate deployment strategies. The technology’s success depends on how effectively organizations integrate these tools while maintaining ethical standards and protecting individual rights.
BWCs are no longer just documenting events—they’re actively shaping how organizations operate and build public trust. The future of this technology will be determined by our ability to balance innovation with responsibility in an increasingly connected world. n


Cyber Security
INTENSIVE CURRICULA OF CYBER WORLD EDUCATION SHOULD BE IMPLEMENTED FROM HIGH SCHOOLS TO COLLEGES
In a rapidly evolving digital landscape, the judiciary is grappling with the complexities of cybercrime and the elusive role of artificial intelligence. Harris Chen, a seasoned prosecutor at the Chiayi District Prosecutor’s Office in Taiwan, shares his insights on these emerging challenges. With 17 years of experience investigating fraud, human trafficking, and corruption, Chen brings a unique perspective on how human psychology can lead to neglecting threats that aren’t immediately visible
n By: Orhan Hadžagić orhan.hadzagic@asmideast.com
a&s Middle East: Despite the growing threat of cybercrime, many of us still don’t see it as “real” because it’s not something they can touch or see. From your experience, what psychological barrier prevents society from fully recognizing the seriousness of digital threats?
Chen: In general, the key psychological barrier is “abstraction”. Humans are wired to respond to tangible, immediate threats — a break-in, a physical assault, something visible. Cybercrime is relatively novel and often invisible until the damage is done, and even then, it might manifest as a drained bank account or leaked personal data, which can feel surreal to the general public. There’s also a dangerous “optimism bias”: people think “it won’t happen to me.” That false sense of digital immunity is what cybercriminals exploit most.
a&s Middle East: How is Taiwanese society addressing public education around cybersecurity? Are there any specific campaigns or strategies you would highlight as successful examples for other countries?
Chen: Taiwan has taken proactive steps, but there’s a long way to go. In Aug. 2022, a new. Government authority Ministry of Digital Affairs, MODA, was established in the top administration. Under MODA, the Agency oy Cyber Security was responsible for cybersecurity affairs in terms of supervising and education. Another example is the “165 Anti-Fraud Hotline”, which the government promotes heavily. It serves both as a reporting mechanism and a public education platform, primarily focusing on cyber fraud. The Ministry of Justice and the Criminal Investigation Bureau have also partnered with influencers and social media platforms to create short, relatable videos on common scams. These efforts show that localized, emotionally resonant storytelling is far more effective than dry warnings. I think intensive curricula of cyber world education should be implemented from high schools to colleges.
a&s Middle East: Can you share one or two of the most striking cybercrime

One major misconception is that cybercriminals are lone geniuses in hoodies. Unfortunately, in reality, many operate in well-organized networks.
cases you’ve handled that might serve as a wake-up call for the public — especially in showing how cyberattacks can affect ordinary people or institutions?
Chen: I was recruited by the Taiwan High Prosecutor’s Office as a project prosecutor to the Supervisory Center for Combating Cybercrime and Fraud in 2022. I was great involved in the initiation of online disruption as DNS RPZ, to timely mitigate illegal online traffic such as piracy, fraud and money laundering. This led to the crackdown of illegal IPTV box “Unblock” in Taiwan in 2023, which

was strikingly notable in copyright field. Almost every crime nowadays is cybercrime for lots of criminality information is digitally stored and transmitted via internet.
a&s Middle East: In your daily prosecutorial work, what types of cybercrime do you encounter most frequently?
Chen: My district office is relatively medium, thus each prosecutor handles almost every type of crime, from scams to corruption, and so forth. Financial fraud is the most common — especially

phishing, investment scams, and online piracy. We’re also seeing a rise in romance scams and crypto-related fraud. But increasingly, we also deal with digital identity theft and unauthorized access to cloud or platform accounts.
a&s Middle East: Are scams targeting the elderly or social engineering attacks on businesses becoming more dominant?
Chen: Yes, very much so. Elderly people are often targeted because they’re more trusting and may lack digital literacy. But most importantly, they have assets such as savings and real estate that make them fall prey to love scams and invest scams. On the business side, attackers are using business email compromise (BEC) schemes and fake invoices to extract funds. These scams rely not on tech, but on psychology — trust, urgency, fear. That’s why education is critical.
a&s Middle East: As AI tools become more accessible, what kinds of risks do you foresee in the legal and criminal landscape?
Chen: The biggest risk is scalability. AI lowers the cost and barrier of entry to cybercrime. You don’t need to be a skilled hacker anymore. Voice cloning, fake legal documents, deepfakes — these are already being used in fraud. And with
Our experience shows that technical capability must be matched with human networks— the speed of a response often depends on relationships, not just protocols.
generative AI, even the language used in phishing emails is becoming indistinguishably human.
a&s Middle East: How is the judiciary preparing for AI-related offenses such as deepfakes, automated scams, or algorithmic manipulation?
Chen: Taiwan has begun pilot training programs for judges and prosecutors focused on digital forensics and AI-related crime. We are also exploring partnerships with academic institutions to build internal expertise. However, the key challenge is staying ahead of new threats — because the technology evolves faster than training programs. Nevertheless, the preparation to such challenges is still inadequate.
a&s Middle East: Do you see a gap between the speed of technological change and how quickly legislation adapts?
Chen: Absolutely. Law is reactive by nature, while technology is proactive. This lag creates legal grey zones that cybercriminals exploit. For example, there was a time when “ransomware” wasn’t clearly covered under existing extortion laws. Even now, AI-generated content challenges our definitions of authorship, consent, and intent.
a&s Middle East: What can lawmakers and legal institutions do to better keep pace with cybercriminal innovation?
Chen: We need agile legal frameworks — laws that define principles rather than specific tools. For example, defining illegal data manipulation broadly, rather than naming each technology. We also need to integrate technical advisors into legislative teams and encourage sandbox environments for legal experimentation, similar to fintech regu -
That false sense of digital immunity is what cybercriminals exploit most.

I think intensive curricula of cyber world education should be implemented from high schools to colleges.
lation. Moreover, strengthening regulation with stricter laws on social media platform is the very essential move to combat cybercrime.
a&s Middle East: How can media outlets avoid unintentionally promoting cybercrime—such as by glamorizing hackers or oversharing methods? What role should the press play in responsibly informing the public?
Chen: Media has a responsibility to balance reporting with restraint. Sensationalist headlines like “Mastermind Teen Hacks Millions” glamorize illegal behavior and can inspire copycats. We all know that a lot of crimes start from learning and mimicking. Instead, media should focus on victim impact and systemic solutions Collaborating with cybersecurity experts can also help journalists avoid oversimplifying or unintentionally enabling techniques.
a&s Middle East: What is one misconception about cybercriminals or cybercrime that you wish the public better understood?
Chen: Excellent question. One major misconception is that cybercriminals are lone geniuses in hoodies. Unfortunately, in reality, many operate in well-organized networks, often internationally coordinated. Some even provide “customer service” for ransomware victims. Understanding that this is undoubtedly organized crime — not random — helps people take the threat more seriously.
a&s Middle East: How important is international cooperation in fighting cybercrime, especially in cases that cross national borders?
Chen: It’s absolutely essential. Cybercriminals operate across borders with ease — routing attacks through multiple countries, exploiting jurisdictions with weak enforcement, and laundering money through decentralized networks. No single country can fight this alone. International cooperation enables timely evidence sharing, coordinated arrests, and synchronized legal processes. Taiwan, despite not being a UN member state, has proven that even outside formal alliances, proactive diplomacy, legal transparency, reciprocal relationship and
mutual trust can lead to highly effective cross-border enforcement.
a&s Middle East: Are there lessons from Taiwan’s approach that could be useful for global enforcement efforts?
Chen: Yes. Taiwan emphasizes public-private collaboration, agile response teams, and victim-centered policies. One key strength is our National Police Agency’s ability to rapidly coordinate with banks, telecom companies, and cybersecurity firms in real time. Our experience shows that technical capability must be matched with human networks— the speed of a response often depends on relationships, not just protocols.
a&s Middle East: What would be your single most important piece of advice to everyday citizens when it comes to protecting themselves in an increasingly digital and AI-integrated world?
Chen: Limit the use of cell phone and practice “intentional skepticism”. Every message, link, or voice you receive — even from someone you know — could be spoofed, deepfaked, or socially engineered. Don’t trust by default. Pause, verify, and only then respond. In a world where AI can convincingly mimic humans, your best defense is to think critically and act cautiously. Awareness isn’t paranoia — it’s solid protection. n




IRIS ID
IRIS BIOMETRICS PUSH PHYSICAL SECURITY BEYOND KEYCARDS AND PINS
Mohammed Murad, Vice President, Global Sales and Business Development, IRIS ID looks at the power of iris recognition and how it can secure data centres with biometric precision
n By: Mohammed Murad mohammed.murad@irisid.com
No firewall or encryption protocol can protect a data center if an unauthorized person gains physical access. While organizations invest heavily in cybersecurity, physical security remains an overlooked vulnerability — one that attackers increasingly exploit. In 2024, the average cost of a data breach soared to $4.88 million, a 10% increase from the previous year, according to the IBM Security Report. Yet, 68% of breaches involve human error, insider mistakes, or credential misuse, as found in the Verizon 2024 Data Breach Investigations Report.
For data centers — the backbone of global digital infrastructure — this risk is even greater. A stolen keycard, shared password, or compromised credential can bypass multiple security layers, granting an attacker direct access to critical systems. Traditional

access controls, such as PIN codes and RFID badges, are increasingly ineffective. To counter these risks and with billions of records at risk, organizations are turning to biometric authentication, with iris recognition
Traditional access controls, such as PIN codes and RFID badges, are increasingly ineffective. To counter these risks and with billions of records at risk, organizations are turning to biometric authentication, with iris recognition emerging as the most secure and scalable solution
emerging as the most secure and scalable solution.
The growing security risks facing data centers
Data centers store and process vast amounts of sensitive data, making them prime targets for both cyber and physical attacks. Organizations focus heavily on preventing malware, phishing and ransomware, but physical security remains a weak point. Cybercriminals and insider threats don’t always rely on hacking — sometimes, gaining physical access to a server room is enough to bypass even the most sophisticated cybersecurity measures.
According to Flashpoint’s Global Threat Intelligence Report, data centers experienced a 34.5% increase in physical security incidents in 2023, including unauthorized access, tailgating and credential theft. More than 80% of data breaches involve stolen or misused credentials, highlighting the urgent need for stronger access control policies.
Traditional security measures, such as keycards, PIN codes and fingerprint scanners, present their own vulnerabilities. Keycards can be cloned, PINs can be shared and fingerprint scanners often fail in environments where employees wear gloves and PPE. Meanwhile,

social engineering tactics — such as phishing or impersonation — make it easier than ever for attackers to manipulate access controls.
Iris recognition: the new standard in data center security
Security leaders are seeking solutions that offer both stronger protection and operational efficiency. Iris recog -
nition outperforms traditional access control methods, offering unmatched accuracy, speed and compliance with global security regulations.
Unmatched accuracy and protection
Iris biometrics analyze over 240 unique characteristics, delivering near-zero false acceptance rates. The National Institute of Standards and

Technology (NIST) has confirmed that iris recognition surpasses fingerprints and facial recognition in high-security applications. Since no two irises are alike — not even in identical twins — it is virtually impossible to duplicate or spoof.
Non-contact, fast and reliable authentication
Unlike fingerprint scanners, which struggle in environments where personnel wear gloves or have wet or damaged skin, iris recognition works effortlessly — even with PPE, glasses or face masks. This makes it an ideal solution for data centers with strict hygiene protocols and high employee turnover, curbing bottlenecks at security checkpoints.
Eliminating credential and insider threats
With 80% of breaches involving stolen or misused credentials, traditional keycards and passwords remain a security liability. Iris authentication ties access directly to an individual’s biological identity, eliminating the risk of shared, stolen or lost credentials. This is particularly critical in colocation data centers, where multiple organizations operate within the same facility, increasing the risk of unauthorized access. n
HOW INDOOR AIR QUALITY SENSORS PLAY A CRITICAL ROLE IN DATA CENTERS
DATA CENTERS ARE THE FOUNDATION OF OUR DIGITAL LIVES. ALMOST ALL MODERN TECHNOLOGY SERVICES RELY ON THEIR COMPUTING POWER. MAINTAINING OPTIMAL PERFORMANCE OF DATA CENTERS IS ESSENTIAL IN MAINTAINING UPTIME AND EXTENDING SYSTEM LIFESPAN. AN OFTEN OVERLOOKED BUT CRITICAL ASPECT OF DATA CENTER MANAGEMENT IS INDOOR AIR QUALITY (IAQ)
n By: Peter Dempsey, EMEA Key Account Manager & Data Centre Lead
In its recent report, “IoT Devices in Smart Commercial Buildings 2025 to 2030”, smart building-specialist industry analyst Memoori highlighted how “the demanding operational requirements of data centers have positioned them at the forefront of smart building technology innovation”. Part of this relates to the environmental sensors that “virtually every data center is filled with”, given that “even minor inefficiencies can have significant cost and performance implications.”
It’s no surprise, therefore, that indoor air quality (IAQ) sensors have become an important part of the data center environmental monitoring infrastructure.
Why IAQ is crucial for data centers
The air quality inside data centers is vital for the health of the servers, switches, routers, and storage used within them. Poor air quality can affect the overall performance of the data center, create a need for more regular maintenance to avoid downtime, and potentially increase the data center’s overall energy consumption.

The air quality inside data centers is vital for the health of the servers, switches, routers, and storage used within them
Data centers generate a significant amount of heat due to the constant operation of servers and other equipment. To maintain proper functioning, data centers rely on advanced cooling systems to regulate temperatures. Accurate, real-time visibility of temperatures throughout a data center is essential for operators to maintain optimal performance.
Dust and particulate matter can also be major culprits in degrading the performance of the sensitive IT equipment housed in data centers. When dust accumulates on servers, cooling fans, or electrical components, it can impair airflow and lead to overheating. Additionally, the buildup of dust and debris has the potential to short-circuit electronics, resulting in costly repairs or downtime.
Data centers must maintain a specific range of humidity to prevent condensation on equipment, which can cause electrical issues and corrosion. However, too little humidity can cause static electricity, which may damage sensitive components.
A data center’s cooling system is designed to regulate temperature and humidity, ensuring that equipment runs efficiently. If the air quality in the data center is compromised, the cooling systems themselves may become less effective.

Given the significant focus on the energy consumed by the world’s data centers, particularly given the explosive growth in artificial intelligence (AI), energy efficiency is a major concern in data center management. Any information and data which can both support the performance of the data center, while also contributing to energy efficiency, is welcome.
An example of the potential savings comes from Google. Using AI to analyze data collected from thousands of sensors, Google DeepMind reduced its data center cooling bill by 40%. Applying the same approach across all data centers would have a huge impact.
In addition, with greater scrutiny from regulators and the implementation of specific industry standards regarding the operation of data centers – including ISO 50001 for energy management, or the Uptime Institute’s Tier standards, which specify operational requirements for data center facilities – the need for such insight is an imperative. A report in 2023 found that fewer than half of data center operators were tracking the metrics needed to either assess their sustainability or meet upcoming regulatory requirements.
Give the impact of air quality in data centers on performance and energy consumption, operators are looking at every way in which they can measure and monitor indoor air quality (IAQ).
Indoor air quality sensors are foundational to providing the insight needed to
efficiently and effectively optimize a data center’s air quality.
What are indoor air quality sensors?
Indoor air quality (IAQ) sensors are devices designed to monitor a variety of environmental factors, including pollutants and contaminants in the air, temperature, humidity, and carbon dioxide (CO2) levels. While many people associate IAQ with human comfort and health, in the case of data centers, the focus is on creating an optimal environment for equipment to operate. These sensors provide real-time data that can help data center operators make informed decisions to optimize air circulation, filtration, and cooling systems.
The benefits of IAQ sensors in data centers
By incorporating IAQ sensors into their operations, data centers can realize numerous benefits. Real-time monitoring of air quality parameters allows data center operators to make immediate adjustments to air filtration and HVAC systems, preventing system inefficiencies and maintaining consistent performance. This continual monitoring and optimization of temperature, humidity, and airflow can reduce the need for excessive cooling and energy use, resulting in potentially significant operational cost savings.
In addition, maintaining the right air quality conditions reduces the likelihood of system failures or downtime due to overheating, dust buildup, or moisture-related issues. Such issues in air quality can be identified before they contribute to potential equipment failure, enabling predictive maintenance rather than reactive repairs, reducing the risk of unexpected disruptions and maintaining performance
Reducing energy consumption and optimizing HVAC systems contributes to overall sustainability efforts by lowering the carbon footprint of data center operations.
Ensuring data centers perform as our technological foundation
Indoor air quality can be an overlooked aspect of data center management, yet it plays a pivotal role in the efficiency, reliability, and longevity of the equipment housed within them and, in turn, the critical digital services data centers provide.
By integrating IAQ sensors into their infrastructure, data centers can improve operational performance, reduce energy costs, and ensure the optimal environment for mission-critical systems.
As the demand for data processing and storage continues to grow, the role of IAQ sensors in maintaining the health of data centers will only become more essential, ensuring that these facilities remain efficient, reliable, and sustainable for years to come. n
AI in Security
BEYOND THE HYPE: A STRONG CASE FOR HUMAN-CENTRIC AI IN SECURITY
The security industry must cut through the AI hype and recognize why artificial intelligence in physical security requires human oversight to bridge the gap between marketing promises and operational reality. In response to Mirza Bahić’s article “AI in Security: Balancing Between Digital Savior and Snake Oil,” published in a&s Middle East, COM-SUR founder Gautam Goradia exposes the uncomfortable truths about false positives, missed threats, and the critical limitations that vendors rarely discuss
n By: Gautam D. Goradia gautam@comsur.biz
After 11 years in the security industry, I’ve witnessed countless technology waves promising to revolutionize surveillance. But Mirza Bahić’s recent analysis strikes at the heart of what we practitioners know but rarely discuss publicly: AI in security is powerful, but it’s failing because we’ve forgotten the fundamental discipline of human oversight. The failure of the AI-based gun detection system at Antioch High School in Tennessee isn’t an isolated incident—it’s symptomatic of an industry-wide problem. We’ve become so enamored with artificial intelligence that we’ve abandoned the basic principle that surveillance systems require human validation to be effective.
What the Experts Are Really Saying
When Hans Kahler from Eagle Eye Networks states, “Some vendors overpromise, suggesting AI can do everything. That’s hype, that’s not reality,” he’s voicing what many of us see daily. The gap between marketing promises and operational reality has never been wider. As he correctly notes, “AI will not — and should not — replace humans. It’s a powerful assistant, not a decision-maker.”

“Some vendors overpromise, suggesting AI can
everything. That’s hype, that’s not reality.”
do
Sajjad Arshad from AxxonSoft Middle East captures this perfectly: “AI doesn’t drink coffee to stay more focused, but it also doesn’t understand intent.” While AI excels at scanning images and processing massive volumes of video without fatigue, “it falls short where it matters most — in understanding why something is happening.” His observation that “Security isn’t just about spotting anomalies. It’s about judgment” resonates deeply with my own experience. This isn’t just theory. When Arshad mentions getting “truly bizarre requests from clients — the kind that make us stop and wonder: who told them these fairy tales in the first place?” he’s describing the realworld impact of AI overselling. Marketing, as he puts it, “tends to sell dreams, while AI delivers something a little messier.”
Mohammed Soliman from McLarty Associates puts it bluntly: “Marketing often exaggerates the promises of what AI in security can do... they pitch fully autonomous security or zero breaches, but that’s overselling it.” His analogy is spoton: “AI is brilliant at shrinking the haystack — flagging 100 suspicious events out of a million — but it’s still up to humans to find the needle.”
Daily Human Oversight
What strikes me most about these expert observations is how they all point to

the same fundamental gap: the absence of structured daily human review. We install cameras, deploy AI analytics, and then somehow expect the system to run itself. This is where we’ve fundamentally lost our way.
In my work developing COM-SUR, I’ve seen this pattern repeatedly. Organizations invest heavily in AI-powered security systems, but they fail to implement the basic discipline of daily footage auditing. Surveillance is installed but not audited. AI runs but is not validated. The result? Systems that generate noise rather than actionable intelligence.
The real breakthrough isn’t more sophisticated AI—it’s bringing back the discipline of systematic human oversight. This means implementing what I call the Daily CCTV Video Footage Auditing process, where operators can audit 24 hours of footage in minutes without missing critical events. It means creating structured workflows that allow humans to seamlessly review footage, tag exceptions, and build the ground-truth feedback that makes AI actually work.
Why COM-SUR
The security industry often sidesteps a tough reality: AI failures stem from deep-rooted challenges that persist even among top players. AI systems falter when trained on scarce or low-quality data, struggling to handle unique, sitespecific scenarios. They frequently miss concealed or novel threats that don’t align with their training. Without contextual judgment, AI misinterprets complex situations, and its biases can spark misguided actions, undermining trust. Opaque decision-making processes further erode confidence, while fine-tuning models proves
tough without consistent, high-quality feedback. Ultimately, AI’s effectiveness crumbles in isolation, demanding seamless integration to bridge these gaps. COM-SUR addresses these challenges directly. Unlike traditional systems that force operators to wade through hours of footage, COM-SUR enables rapid, structured auditing where users can review entire days of multi-camera footage in minutes. The system generates sitespecific, timestamped data that AI vendors can actually train on, creating what is called “Better AI” through continuous human feedback.
But more importantly, COM-SUR creates Explainable AI workflows. When Saif AlRefai from OPSWAT notes that “AI systems can make accurate predictions, but they often operate as ‘black boxes,’” he’s identifying a critical vulnerability. COM-SUR builds transparent, documented evidence for every reviewed incident, eliminating the black-box problem entirely.
The system works with all video sources—CCTV, drones, body-worn cameras, even smartphone footage—creating a unified auditing approach that scales across different technologies and environments. This isn’t just about better software; it’s about establishing a new operational discipline.
The Government Recognition Factor
The validation of this approach goes beyond market acceptance. The Government of India has formally recognized “CCTV Video Footage Auditor” as a new skill under its Ministry of Skill Development. The Ministry of Education is introducing a COM-SUR-based curriculum in Grades 11 and 12. This institutional rec-
ognition reflects a growing understanding that video surveillance requires specific skills and systematic approaches to be effective.
As part of our National Service, we’re providing COM-SUR ‘Ultima’ (highest version) free (conditions apply) to Indian police, defense forces, and paramilitary units because national security demands the highest standards of surveillance discipline. When stakes are this high, there’s no room for unvalidated AI or undisciplined surveillance practices.
Our Social Commitment
As part of our societal purpose, we’re providing the COM-SUR ‘Business’ version free (conditions apply) to the following vulnerable targets: (1) All Places of Worship – Globally, (2) All Low-Budget Government Schools – Globally, (3) All Zoos – Globally. These are high-emotion, high-sensitivity spaces that are often under-resourced and overlooked. Our aim is to give back to society by offering an affordable, simple-to-use solution that ensures proactive surveillance, greater accountability, and far better outcomes than traditional methods.
Beyond Technology: A Return to Fundamentals
The AI security industry has reached a tipping point. Over-promised solutions are being exposed through real-world failures, and the gap between marketing claims and operational reality is becoming impossible to ignore. As Maher Yamout from Kaspersky correctly observes, “The interpretation of that data remains a human responsibility.”
The answer isn’t abandoning AI—it’s grounding AI in proven operational disciplines. Cameras are sources of information that deliver optimal outcomes only when used correctly. Not everyone needs AI, but everyone needs structured human oversight, systematic data management, and standardized reporting.
COM-SUR represents this missing discipline—the structured, timestamped, explainable auditing process that transforms surveillance from reactive monitoring to proactive intelligence. It’s time to bring sanity back to security by embracing the essential truth that human intelligence must guide artificial intelligence, not the other way around. The mantra should be clear: “AI when you need it, human intelligence all the time”. n
PRODUCTS & SOLUTIONS
YES, YOU CAN HAVE BOTH SECURITY AND CONVENIENCE: MOBILE CREDENTIALS AND BIOMETRICS PROVE IT ACROSS THE GCC
As the GCC advances toward its 2030 economic goals, security leaders are turning to mobile credentials and biometrics to safeguard critical assets. HID’s latest global report reveals how these technologies are reshaping identity and access strategies across the region
n By: Sam Cherif, Senior Director & Regional Business Head of the Middle East at HID PACS
E-mail:
Economic Vision programs for 2030 and beyond seem closer now that the Arab Gulf region has passed the midpoint of the 2020s. Now, more than ever, there is an urgency among business leaders to protect progress by securing key assets – critical infrastructure, intellectual property, customers’ private data, and other assets. The investments made now in digital and physical security could mean the difference between a prominent position in an economic success story or being remembered only as a casualty of the threat landscape.
Insights from HID’s 2025 State of Security and Identity Report
In HID’s 2025 State of Security and Identity Report, we delved into the thinking of

more than 1,800 end users and industry partners around the world. From that re search, we uncovered the major trends shaping security and identity. Among the findings was the startling rise of personal mobile devices and biometrics to support organizations’ threat postures.
Momentum in the GCC
The high mobile-device penetration rates among GCC populations are well known. Some 61% of security leaders

around the world told our researchers that they regarded mobile credentials as a priority for adoption, considering their convenience (everyone owns a smartphone and carries it with them routinely) and sustainability (organizations eliminate the need for fobs and plastic cards).
Biometrics Maturing for Real-World Deployment
The capabilities and use cases found within the broad field of biometrics form a long list. However, what is clear is that the recognition of biometrics as a viable option for live environments comes from the progress being made in image-quality assessment technologies. The maturity of these technologies allows them to automatically adjust to real-world conditions such as dim lighting and harsh weather conditions. Meanwhile, AI and machine learning can combat the rise of deep fakes, making facial recognition and fingerprint scanning ideal for banks’ fulfilment of regulatory obligations such as knowyour-customer (KYC).
Fingerprints and Faces: The Core of Modern MFA
While facial recognition took a leap forward in acceptance since its inclusion in popular smartphone brands, fingerprints will likely be around for some time. Both technologies, however, offer the advantage of reliable ID verification without the required involvement of another human. Each can also be used in MFA (multifactor authentication) and rolled out to cover access to physical premises, systems, and everything in between.
Adoption Trends Reflect Regional Priorities
The progress in image-assessment tech helps explain why 37% of organizations have deployed mobile credentials and 32% plan to deploy them, accounting for 69%, or more than two-thirds. Modern mobile security solutions also allow for quick updates or the revocation of credentials if a device is misplaced or stolen. Mobile credentials also integrate seamlessly with smart-building technologies, supporting scalability and
sustainability through the minimization of waste.
Biometrics and Mobile Credentials: A Powerful Duo
Separate from mobile credentials, 35% of those surveyed said they use biometric technology, and 13% said they plan to. Of this combined group, 72% planned to implement fingerprint recognition and 52% opted for facial recognition. Most of the same group of respondents (73%) say biometrics is part of their multi-factor authentication (MFA) strategy.
Balancing Benefits with Concerns
While some decision makers still worry about implementation costs (33%), privacy (31%), and unverifiable ROI (22%), biometrics, when used with mobile credentials, can deliver the kind of stringent identity solution sought by the region’s security leaders. In the coming years, the duo will likely become best practices in securing the economic progress of GCC nations. n
ASSA ABLOY
DEVICE RANGE, CYBERSECURITY AND WEATHER RESISTANCE MAKE ECLIQ THE RIGHT CHOICE
ZMS, a Bavarian waste management association, upgrades to eCLIQ’s digital access solution, enhancing security, flexibility, and compliance across its diverse facilities
n By: Thomas Schulz, Director & Head of Marketing DAS in the Opening Solutions EMEIA division thomas.schulz@assaabloy.com
In 1979, nine districts and five cities in Bavaria, Germany founded a joint association for the disposal of residual waste. They targeted futureoriented, environmentally friendly and economical fulfilment of local statutory obligations. Now with 17 association members, ZMS (Zweckerverband Müllverwertung Schwandorf) disposes waste for around a fifth of Bavaria, almost two million citizens. They also use the energy generated by the waste power plant as efficiently as possible.
Transitioning to eCLIQ
In the past, a mechanical locking system was used on all ZMS properties. The association planned a digital upgrade to boost flexibility over their existing mechanical locking. Their principal site at Schwandorf has areas requiring different levels of security. Devices and other access hardware also need high weather resistance, for deployment outdoors.

Managers also considered workflow efficiency. They wanted a way to manage access authorizations more flexibly and align security infrastructure with upcoming IT security laws such as NIS2. The company chose eCLIQ, part of the suite of Digital Access Solutions from ASSA ABLOY. This innovative, program-
mable key-based solution now equips not only the power plant and headquarters in Schwandorf, but also buildings across eastern Bavaria, including transfer stations, a waste disposal site, a sorting plant in Bodenwöhr, and a sludge drying plant, as well as all technical and commercial offices, gate con -

trol systems and local control points.
Because eCLIQ offers a broad range of digital cylinders within its single ecosystem, it suits diverse and complex organizations like ZMS.
The benefits of programmable key-based digital access
The digitally networked eCLIQ system allows access rights and security levels to be defined and assigned flexibly and precisely. A total of 20 Wall Programming Devices (Wall PDs) installed in the head office and branch offices ensure that only authorized employees gain access. These Wall PDs also make it easy to set limited access time windows for fitters or maintenance contractors. If a key is lost, it can be programmed out immediately to prevent misuse.
“Now we are going with the times and can conveniently enjoy a wide range
Because eCLIQ offers a broad range of digital cylinders within its single ecosystem, it suits diverse and complex organizations like ZMS
of advantages,” says Manuel Emerich, Project Manager at ZMS. “As a critical infrastructure company, we can also react very rapidly and flexibly to future requirements.”
With eCLIQ, each of ZMS’s approximately 1,000 wireless digital cylinders is powered by a battery inside the keyholder’s personalized key. Standard eCLIQ keys have a battery life of 10 years with typical usage. The solution offers the advantage that a depleted battery does not render a cylinder useless. The key is simply fitted with a spare battery, saving time and effort. Security is a critical concern at mu-
nicipal and infrastructure sites: every eCLIQ device offers reliable protection against manipulation and intelligent break-in attempts. Keys are robust, with a waterproof casing, and operate reliably in the most challenging environmental conditions.
With eCLIQ, ZMS feel ready to face a future of evolving physical and cybersecurity threats. “For us, the introduction of digital locking technology and the ability to respond quickly and specifically to security incidents is a decisive step towards a holistic and future-proof system to defend against cyber–physical threats,” adds Manuel Emerich. n
IDIS
INTEGRATED SECURITY SOLUTION PROTECTS REMOTE ARCHAEOLOGY SITE
An advanced, eco-friendly security system is now safeguarding a remote archaeological site in Israel, protecting priceless artefacts from looters, vandals, and accidental damage. Using buried seismic sensors and AI-powered cameras, the integrated solution provides round-the-clock surveillance with minimal environmental impact, delivering reliable, noninvasive protection for a site that spans several square kilometers
n By: Mirza Bahic mirza.bahic@asmideast.com
Archaeological sites can be irreplaceable windows into the past, with artefacts that help to tell the story of human civilization. But these locations all too often face threats: from treasure hunters, vandals intent on destroying heritage, or inadvertent damage from trespassers.
Looters, equipped with modern tools and technology, have become more sophisticated in their attacks. They often operate at night, using careful methods to avoid detection, and target areas that contain valuable artefacts.
The damage caused isn’t just from stolen items. Careless digging can also destroy the crucial archaeological context.
Traditional security measures are often unsuitable, especially in remote locations where conventional surveillance is impractical or where it could negatively impact the site with cabling and other infrastructure.
So archaeological sites present challenges that set them apart from typical security scenarios. They often span extensive areas – in the case of this recent project

in Israel, several square kilometers – and, unlike buildings with defined entry points, are vulnerable from all angles.
Invisible shield
To address these challenges, one of IDIS’s integration partners in Israel has implemented a security solution that combines multiple technologies to create an invisible shield.
The site was divided into six zones, each containing up to thirty SensoGuard AIO
XR seismic sensors and one IDIS AI PTZ camera, working seamlessly to provide proactive protection from boundary to boundary.
The AIO XR sensors, buried carefully underground, act as an invisible early warning system, capable of detecting even the slightest disturbance over and under the ground, whether it’s footsteps, vehicle movements, or digging. At the same time, robust, pole-mounted IDIS AI PTZ cameras provide visual verification.


The AI PTZ cameras feature 36x zoom, automated AI tracking, and night vision up to 1300 feet, making them ideal for expansive archaeological sites. Each pole is mounted with an IDIS AI PTZ camera and a bullet camera to protect the pole, powered by solar energy with 4G-LTE cellular connectivity. Both IDIS cameras feature IDIS Deep Learning Analytics (IDLA) on the edge.
The seismic detectors and cameras work together seamlessly. When a seismic sensor detects potential intrusion, the nearest camera automatically rotates to focus on that exact location of the event. The built-in AI analytics help verify the threat, distinguishing between harmless wildlife and genuine potential risks.

Minimal site impact
With a light footprint and minimal environmental impact, this sustainable security solution now ensures protection for the remote site. The system enables 24/7 monitoring regardless of weather or lighting conditions, noninvasive protection and security without compromising the site’s integrity, rapid response capability with its immediate alert and verification system, and sustainable operation, with solar power ensuring continuous functionality with minimal maintenance.
The system’s scalable nature also means it can be expanded or modified as needs change, ensuring long-term protection.
“After collaborating with IDIS, we’re delighted to have developed a proven integrated security solution,” says Tomer Levy, SensoGuard CEO. “One that reduces false alarms to ensure quick response to threats, utilizes green energy, and provides complete surveillance coverage.” n
BIOMETRIC SECURITY
SECURING BIOMETRIC AUTHENTICATION WITH PRESENTATION ATTACK DETECTION
Presentation Attack Detection (PAD) protects biometric systems from fake traits used to bypass security. Advances in AI and sensor technology are improving PAD’s ability to spot spoofing and keep biometric authentication secure.
n By: Mirza Bahic mirza.bahic@asmideast.com
In an era where digital security is paramount, ensuring that biometric systems remain impenetrable is a top priority. This is where Presentation Attack Detection (PAD) steps in, acting as the guardian against fraudulent attempts to breach security by presenting counterfeit biometrics. And yet, this critical component of biometric authentication is not a common integration in many developing nations due to a lack of resources and adequate funding. These constraints and many others limit the response that can be offered to combat emerging physical security breaches and cybersecurity threats, including fraud and identity theft. The fundamental premise of PAD is to distinguish genuine biometric traits from fabricated ones, a task that is more complex than it appears. Presentation attacks are crafted to deceive biometric sensors, often with astonishing accuracy. However, PAD utilizes sophisticated algorithms and techniques to analyze various param-
eters and detect the subtle nuances that differentiate a live biometric from a simulated one.
What is a Presentation Attack?
A presentation attack (or spoofing attack) occurs when a fake biometric trait is presented to the sensor in an attempt to gain unauthorized access. The attacker might use a printed photo to bypass biometric authentication. They may also deploy a 3D mask to mimic a real biometric. In some cases, a patterned or colored contact lens can be used. Another method involves using a synthetic fingerprint made from gel or silicone. These attacks can fool biometric systems that lack the ability to verify whether the biometric input comes from a live, present person.
Presentation Attack
Detection (PAD): The Defense Mechanism
Presentation Attack Detection refers to the methods used to differentiate between genuine, live biometric traits and artifacts meant to spoof the system. PAD ensures that only bona fide (real) presentations are accepted.
PAD can be categorized into two primary approaches. Sensor-level PAD (hardwarebased) uses specialized sensors to detect liveness, such as depth cameras, infrared sensors, or pulse detectors. Algorithm-level PAD (software-based) relies on image processing, computer vision, and AI to detect spoofing patterns without requiring extra hardware. Together, these techniques add a vital security layer to biometric systems.
A presentation attack (or spoofing attack) occurs when a fake biometric trait is presented to the sensor in an attempt to gain unauthorized access

PAD Techniques and Approaches
PAD techniques and approaches include several methods to detect spoofing attempts.
Feature-Based PAD analyzes still images for spoof cues such as texture anomalies, reflection inconsistencies, and low image quality resulting from printed or digital displays. Dynamic Feature-Based PAD focuses on detecting real-time signs of life, including eye blinking, facial expressions, and subtle movements or blood flow patterns.
Hardware-Based PAD utilizes additional sensors such as near-infrared and 3D cameras, multispectral fingerprint scanners, and thermal imaging for temperature detection. Software-Based PAD relies on machine learning and pattern recognition techniques, including deep learning, to identify spoof features, behavioral analysis (such as how a user types, swipes, or speaks), and liveness detection algorithms applied to image or video streams.
Hybrid approaches often combine various PAD techniques to balance these tradeoffs effectively. By leveraging different sensor technologies and software algo-
rithms, a robust security framework can be established that mitigates the weaknesses inherent in any single method. For instance, combining thermal imaging with behavioral analysis can provide a more comprehensive defense against spoofing attempts, ensuring both high accuracy and a seamless user experience.
Challenges and Limitations
While PAD is essential, it faces several challenges. Hardware-based PAD can be expensive to deploy at scale, making cost a significant barrier. False rejections may occur, meaning legitimate users are occasionally denied access. Additionally, as PAD technology improves, spoofing techniques also evolve, creating an ongoing arms race between attackers and defenders. Some PAD methods require user cooperation, such as blinking, which can hinder overall usability and the user experience.
Despite these challenges, ongoing research and development are actively addressing these issues to enhance the reliability and user-friendliness of PAD technologies. Innovations such as adaptive algorithms and user-centric design principles are being integrated to mini-
mize false rejections and improve overall user experience.
The continuous evolution of PAD technologies is paramount for maintaining the integrity of biometric systems. By staying ahead of emerging threats and integrating cutting-edge solutions, we can ensure that biometric authentication remains a secure and seamless experience for users worldwide.
The Future of PAD in Biometrics
As biometric systems become ubiquitous, PAD is evolving to keep pace with emerging challenges. Machine learning and deep learning continuously improve PAD accuracy through data-driven learning. Multimodal biometrics combine multiple traits, such as face and iris recognition, to reduce the risk of spoofing. Edge PAD performs detection directly on devices, enhancing speed and privacy. Continuous authentication monitors users over time, rather than relying on a one-time check, by analyzing behavioral biometrics. These innovations promise a future where biometric systems are not only fast and easy to use but also highly resilient against deception.
Biometrics offer a compelling solution for secure, user-friendly authentication—but they’re not foolproof. Presentation attacks threaten to undermine the trust we place in these systems. That’s why Presentation Attack Detection (PAD) is not just an add-on, but a necessity. Whether through specialized sensors, AI-powered algorithms, or smart combinations of techniques, PAD ensures that biometric authentication systems can confidently answer the critical question: Is this a real person?
As technology advances, it is imperative that our security measures also progress. In the realm of biometrics, the effectiveness of any sophisticated system is contingent upon its capability to distinguish between genuine and counterfeit inputs. n
GENETEC
GENETEC BRINGS NEW CAPABILITIES TO SECURITY CENTER SAAS
Flexible, open platform gives security professionals and integrators the freedom to deploy and scale physical security on their terms
n By: Orhan Hadzagic orhan.hadzagic@asmideast.com
Genetec Inc., a global provider in enterprise physical security software, announced new updates to Security Center SaaS, the company’s enterprise-grade Security-as-a-Service (SaaS) solution. Since its launch, Genetec has delivered new features to the platform every 12 days. This enables Genetec to provide a flexible, open, SaaS solution that is continuously extended to meet the needs of any modern security operation.
Unified
Security Platform Delivers Comprehensive Protection
Security Center SaaS combines video surveillance, access control, forensic search, intrusion monitoring, automation, and other advanced capabilities in a single solution. Designed to run fully in the cloud or in a hybrid deployment that can include on-premises systems, it gives organizations the freedom to choose how they manage and scale their security infrastructure. The latest updates expand support for direct-to-cloud cameras, improve edge recording capabilities, and introduce new third-party analytics integrations, reinforcing the

Security Center SaaS combines video surveillance, access control, forensic search, intrusion monitoring, automation, and other advanced capabilities in a single solution
platform’s pace of innovation and commitment to customer choice.
Breaking Free from Vendor Lock-In
Unlike proprietary SaaS solutions, Security Center SaaS enables security profes-
sionals and channel partners to choose the hardware that best fits their needs, without being locked into a single vendor. Its open architecture supports a broad range of devices from Axis, Bosch, and i-PRO, including direct-to-cloud, PTZ, and fisheye cameras (now with automatic de-warping). Organizations can connect

their current non-cloud-ready access control devices, cameras, and intrusion panels using Genetec appliances, avoiding the costs of replacing existing hardware.
Cloud Migration on Your Terms
This flexibility further extends to deployment models. Security Center SaaS gives organizations full control over their cloud migration, supporting cloud-native, onpremises infrastructure, or a combination of both.
Video can be stored at the edge or in the cloud, depending on bandwidth, policy, or operational needs, with centralized management through web and mobile apps. New edge recording via SD cards enables local storage on the camera, while recording profiles make it easy to define how and where video is captured across multiple devices.
Streamlined Video Access
With built-in support for WebRTC, the platform also enables peer-to-peer video streaming directly from cameras to a web interface. This reduces video call-up time and bandwidth usage, making it wellsuited for live monitoring, spot checks, and large-scale deployments, without requiring additional configuration.
Securing Complex Environments Across Industries
Security Center SaaS is intended to simplify the management of multi-site environments across sectors such as retail, education, corporate campuses, banking, healthcare, and city infrastructure. Operators can manage systems from a central Security Operations Center (SOC) or remotely via web and mobile apps. Real-time alerts enable teams to respond in a quicker and more consistent
manner, while its open architecture makes it easier to integrate partner technology that further enhances these capabilities. For example, new firearm detection analytics from Bosch can trigger immediate alerts and initiate event-to-action workflows the moment a weapon is identified, helping security teams act decisively when it matters most.
Industry Perspective
“Genetec is redefining what SaaS means for physical security. It’s not just moving to the cloud; it’s about giving customers and integrators the flexibility to build, scale, and evolve their systems,” said Christian Morin, Vice President of Product Engineering at Genetec Inc. “Security Center SaaS stands apart by unifying physical security functions on a single platform, continuously adding new cloud-native capabilities while supporting the hardware and deployment models organizations already rely on.” n
ALIGNTECH’S LEAD FORWARD ROADSHOW 2025 SHOWCASES FORWARD-THINKING INNOVATIONS
On May 20th, 21st, and 27th in Cairo, Riyadh, and Dubai, Aligntech hosted the Lead Forward Roadshow 2025, bringing together top international ELV and security system manufacturers, system integrators, and contractors to share a unified vision of forwardthinking innovation
n By: Mirza Bahic mirza.bahic@asmideast.com
Aligntech values the support and collaboration of its partners that remain central to its mission of moving security technology forward. The success of the Lead Forward Roadshow 2025, held in Cairo, Riyadh, and Dubai, is a testament to the core values of these partnerships. It is through this expert’s ecosystem, spanning its partners, vendors, and end-users, that this event came to life, carrying forward its message and name.
Commitment to a Safer, Connected Tomorrow
In a rapidly changing market landscape, the company’s commitment remains unchanged: to foster a safer, more connected tomorrow, where secure environments are not only accessible but sustainable for future generations. Furthermore, Aligntech’s expertise, along with that of its partners, vendors, and system integrators, ensures that they can all deliver on the brand’s promise.

Alinghtech commitment remains unchanged: to foster a safer, more connected tomorrow, where secure environments are not only accessible but sustainable for future generations

Defining Excellence in Security Technology
Now, excellence in any industry begins with quality. In security technology, it is defined by premium and reliable products, committed pre- and after-sales services, and forward-thinking innovation. Aligntech’s partnerships with vendors such as Genetec, Fermax, Ipro, Gatekeeper/ Rapiscan, Orbility, Automatic Systems, Intelexvision, Safr, and others are founded on a shared pursuit of value that the company defines as a mission and end users recognize as quality products and services. These partnerships bring advanced solutions to the market, and Aligntech
complements them with exceptional service, technical expertise, and dedicated pre- and after-sales support.
Enhancing Support with the Technical Assistance Support Program
One such initiative is the newly launched Technical Assistance Support (TAS) program. This service is designed to streamline and elevate the experience for system integrators, developers, and contractors by ensuring they receive accurate, timely, and in-depth technical support throughout every stage of implementation.
Looking Ahead: Strengthening Ecosystem and Community
Lead Forward will remain a meeting point for all partners who share Aligntech’s vision and appreciate all technological advancements or developments. Moving forward, the company promises to remain committed to strengthening its ecosystem and community while expanding its capabilities with its partners. Only together can they continue to lead forward in building the secure, connected environments of tomorrow. n

ALARM.COM SHOWCASES VISION AND GROWTH IN IBIZA
In the vibrant setting of Ibiza, Alarm.com’s 2025 Partner Connections brought together global partners and industry leaders for three days of strategic insights, technological innovation, and meaningful collaboration
n By: Mirza Bahić mirza.bahic@asmideast.com
Alarm.com successfully concluded its 2025 Partner Connections event at the Hard Rock Hotel in the sunny setting of Ibiza, bringing together top-tier partners, thought leaders, and innovators from across the globe. Held from May 6 to 8, the three-day event celebrated progress, partnership, and cutting-edge innovation in smart security and automation. The event opened with a stunning rooftop welcome reception at The Ninth Rooftop Bar, setting the tone for a high-energy agenda. Reed Grothe, Alarm.com’s SVP of Global Business Development, kicked off the proceedings with inspiring opening remarks, followed by an evening of fine dining at Tatel Restaurant, giving partner guests an opportunity to catch up as well as enjoy social engagement with Alarm. com’s senior leadership team.
Insightful Sessions and Strategic Discussions
Day two featured a full slate of insightful sessions and engaging discussions,


with several standout presentations. Dan Kerzner, President of Platforms, opened the day by presenting key corporate insights and outlining Alarm. com’s strategic direction. Juan Camilo Salazar followed with a compelling ses-
sion on global market trends, enriched with case studies and success stories from across the world. Mikalai Zaiko delved into non-traditional sales channels and identified growth opportunities within emerging verticals. Expert
AnneMarie Ferraro
Dan Kerzner

Juan Camilo Salazar

strategies on partner engagement and customer retention were shared by Jorge Barragan from ADT, while Alex Freixas offered an in-depth examination of tech infrastructure, cloud solutions, and IT security.
The day ended with an idyllic beachside dinner and networking party, a memorable evening that underscored the event’s emphasis on collaboration and connection.
Innovation and Growth Take Center Stage
Thursday’s sessions built on the event’s momentum, maintaining a strong focus on innovation and partner success. Aitor Gauna addressed the evolving challenges and emerging opportunities within the DIY smart security market. Aydin Bolkar and Engin Kurtay of Pronet reflected on a decade of growth and transformation in partnership with Alarm.com, providing a unique long-term perspective. AnneMarie Ferraro contributed
valuable insights into quality-focused investments and engineering excellence. David Rimmer and Freddi Arce Gomez offered practical strategies for upselling, automation, and leveraging
2025 Partner Connections event at
the Hard Rock Hotel in the sunny setting of Ibiza, bringing together top-tier partners, thought leaders, and innovators from across the globe
business intelligence as a driver of revenue. Hector Avalos further expanded on these themes, demonstrating how Alarm.com’s tools can be used to effectively upsell, automate, and scale for sustainable growth.
Closing Showcase and Final Reflections
The event concluded with an enlightening product demo and vendor showcase, including standout presentations from CHeKT, EBS, and OpenEye.
“Partner Connections Ibiza 2025 was a successful platform for inspiration, exchange, and partnership,” said a spokesperson for Alarm.com. “We’re proud to be able to support our partners in their journeys and create spaces where innovation and collaboration can thrive.” n

Audience
INTERSEC SHANGHAI
CHINA EMERGES AS A KEY SECURITY TECH HUB
Bringing together over 500 exhibitors and more than 62,000 visits from around the globe, the debut edition of Intersec Shanghai positioned China as a rising force in security, fire protection, and emergency response. From AI-driven innovations to cross-border partnerships, the three-day event highlighted the country’s expanding role in shaping global safety technologies and strategies
n By: Mirza Bahic mirza.bahic@asmideast.com
Intersec Shanghai 2025 wrapped up on 15 May after three dynamic days at the National Exhibition and Convention Center, confirming its status as a vital platform for China’s security, fire protection, and workplace safety sectors. Co-located with the Yangtze River Delta International Emergency Disaster Reduction & Rescue Expo (EDRR), the twin events attracted 512 exhibitors and more than 62,000 visits from 27 countries and regions. The fair spotlighted China’s growing influence in the global safety tech arena—particularly in intelligent systems, automation, and integrated emergency response solutions.
Elevating Innovation and Collaboration
The inaugural edition was more than a showcase—it was a strategic move by Messe Frankfurt and CCPIT Shanghai to stimulate cross-border innovation and cooperation. “Launching Intersec Shanghai is a key step to advance innovation and strengthen cooperation across China’s security, safety, and emergency response sectors,” said Edward Che, General Manager of Messe Frankfurt (HK) Ltd. Kevin Lee, President of CCPIT, underscored the international scope of the event: “We welcomed representatives from emergency management departments from Brazil to Saudi Arabia. These exchanges reflected shared goals and emerging global trends in safety and resilience.”



A Cross-Sectoral View on the Future of Safety
Spanning 13,000 sqm, the event featured AI- and IoT-powered solutions in public safety, firefighting, industrial risk mitigation, and crisis management. Exhibitors such as Tyco, Raythink, and Crun Hydraulic presented a range of innovations—from thermal imaging and energy systems to automated fire control platforms. The feedback was overwhelmingly positive. Richard Chung of YUNHE Technology emphasized the value of real-time training systems in cutting both response time and cost, while Inrico Technologies’ Zhang Wenshun highlighted how the fair provided insights for fine-tuning AI-driven,
5G-compliant products across industries. For CammPro Technology, the fair was a catalyst for knowledge exchange and trendspotting, while VdS Schadenverhütung’s Lothar Sysk noted the event’s importance in connecting with decisionmakers adapting to increasingly intelligent infrastructure.
Insights from Global Buyers
Buyers praised the fair’s role in bridging global demand with China’s competitive supply capabilities. From solar-powered surveillance to integrated access control and AI analytics, Intersec Shanghai proved a strategic meeting point for procurement and partnership.

Buyers praised the fair’s role in bridging global demand with China’s competitive supply capabilities, from solar-powered surveillance to integrated access control and AI analytics
“I came looking for cameras, batteries, and solar panels—and I found reliable suppliers at competitive prices,” said Muhammad Faisal Aslam of Pakistan’s Aslam and Sons Traders. Romanian delegate Mircea Ciordas noted that Chinese suppliers are leading the way in video surveillance tech, while Michaela Cabusas of the Philippines found particular value in niche innovations like VR firefighter training kits.
Where Tech Meets Application
The concurrent Digitalization Applications in the Security Industry Summit dove into AI’s role in surveillance, disaster readiness, and industrial safety. Presentations from figures like Sun Chao of Shanghai Emergency Management highlighted how robotics, drones, and advanced AI models are transforming emergency response.
The a&s Top Digital Products & Solutions Award Ceremony celebrated forwardleaning technologies, with a focus on sustainability and real-time response capabilities.
Building the Future of Safety
Intersec Shanghai’s success lies not just in numbers, but in its positioning: as an emerging international hub where innovation meets purpose. The fair linked global suppliers with Chinese partners and reinforced the country’s role as both a manufacturing stronghold and a source of pioneering solutions.
With Messe Frankfurt’s global Safety, Security & Fire portfolio spanning Asia, Europe, the Middle East, and South America, Intersec Shanghai marks a key node in a growing global network of safety-focused exchange and collaboration.
The next edition of Intersec Shanghai will take place from 7–9 May 2026. n
Key Security Events in 2025/2026
Key Security Events in 2023

8 - 9 Oct. 2025, Skopje, North Macedonia
Adria Security Summit 8-9 October 2025, Skopje, North Macedonia
https://www.adriasecuritysummit.com

Gitex Global 13-17 Oct 2025, Dubai, UAE
https://www.gitex.com/home
OFSEC
11-12 Nov 2025, Muscat, Oman
https://www.ofsecevent.com

DIMDEX
19-22 Jan 2026, Doha, Qatar
https://dimdex.com
ISAF
8-11 October 2025, Istanbul, Turkey
https://www.isaffuari.com/en
Romanian Security Summit
5-6 Nov 2025, Bucharest, Romania
https://romaniansecuritysummit.com
Intersec Dubai
12-14 Jan 2026, Dubai, UAE
https://intersec.ae.messefrankfurt.com/dubai

Integrated System Europe 3-6 Feb 2026, Barcelona, Spain
https://www.iseurope.org







Secure Communications Networking and Server Solutions
Ethernet Switches
Network Extenders & Media Converters
Edge Computing & Video Storage Appliances
Remote Monitoring & Network Management
Industrial Hardened & Commercial Grade
Secure by Design
Made in the USA
Comprehensive Warranties
Global Technical Support

Market & Contacts

TECHNICAL PROTECTION
Vendor-neutral Physical Security Information Management (PSIM) Bosch empowers you to build a
Advancis Middle East
P.O. Box 73309
Abu Dhabi, United Arab Emirates
Tel. +971 2 444 2503
Email: info@advancis.ae Web: https://advancis.net


www.assaabloy.com/ae/en patricia.lomboy@assaabloy.com
Magazine Topics
Man Guarding
Technical protection
• Video surveillance
• Access control
• Intrusion detection
• Item theft protection
• IP and network solutions
• Perimeter protection
• Fire detection
• Gas detection
Mechanical protection Cash/valuables-in-transit
Cyber security
Digital forensics
Software solutions
Smart home Internet of things
Security management Investigations
Building management
Market research
Legislation and standards







www.sicurezza.it
Index of Advertisers
Magazine Topics
Man Guarding
Technical
• Video
• Intrusion
•
•
•
Mechanical
Cash/valuables-in-transit
Cyber
Digital
Software
Smart
Internet
Security
Building
Legislation

Access Control - Intrusion Detection - Building Automation.
ICT o ers a unified solution for access control, intrusion detection, and building automation - whether you are dealing with a small business or a large-scale enterprise project with thousands of doors and complex requirements.
With native support for mobile credentials, video intercoms, lift integration, and a wide array of built-in features, the Protege systems mean you can track where people are, see who’s at the door, and respond to incidents from one single, easy-to-use platform.
Event Management Platform
Tickets, Invoicing and Payments
Badging and Check-In Management
Sponsors, Exhibitors and Lead Retrieval
3d Expo Planning and Booth Configuration
AI-powered matchmaking
Techman Solution
Organize Events the Ninja Way: Fast & Flawless!
Speakers, Content and Agenda
Attendee Engagement and Gamification
Event Communications Marketing Campaigns and Tracking
Since our establishment in 2013, Techman Solution has been a leader in Systems Integration, delivering cutting-edge ICT, ELV, and software solutions. Our expertise spans from advanced network infrastructure and security systems to custom software development, ensuring comprehensive technology solutions for our clients.
Let’s talk about making your events flawless, fun, and totally unforgettable. Whether you’re creating game changing expo plans, impressing sponsors, or managing a million moving parts, you don’t have to go it alone.