






































Talus Arukalil Regional Director MEAI, PNY Technologies


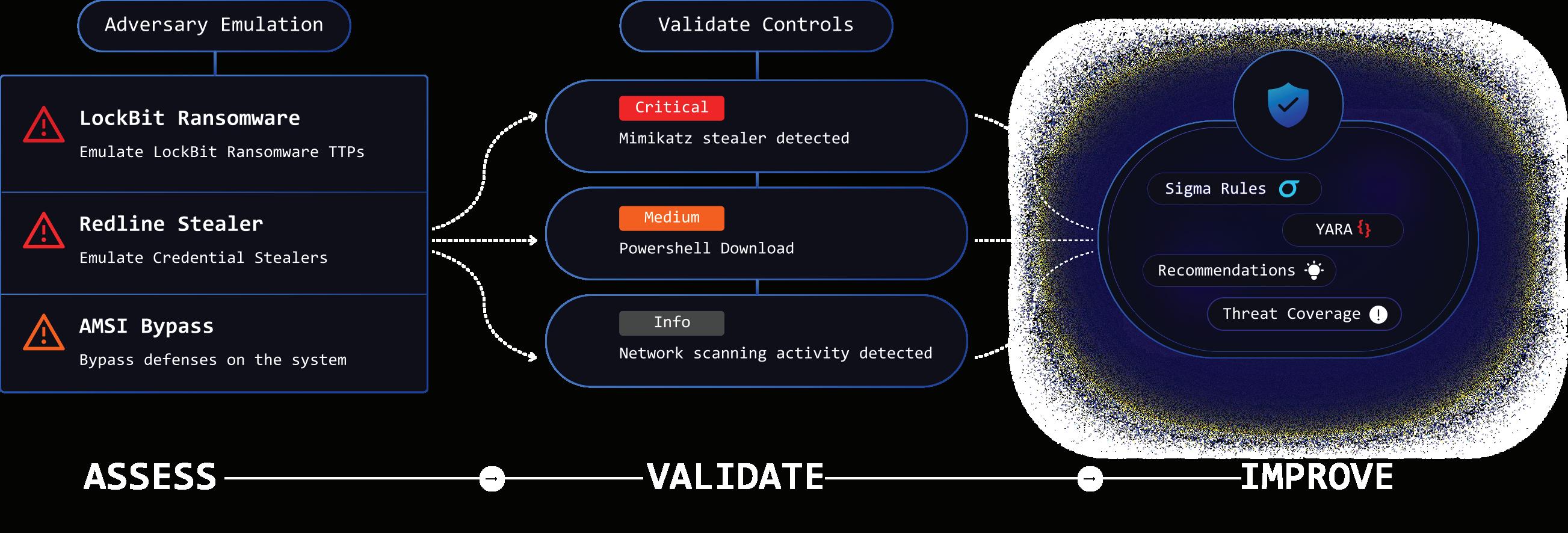
In today's digital landscape, managing IT efficiently is paramount. Cloudmon delivers a seamless observability solution that spans across on-premise and cloud environments, ensuring comprehensive visibility into servers, platforms, applications, endpoints, and the overall digital experience.
Comprehensive Coverage:
Monitor everything from on-premise hardware to cloud-based. Cloudmon's robust platform supports all major servers, platforms, and applications, ensuring you don't miss a beat.
Real-Time Monitoring and Alerts:
Stay ahead of the curve with real-time monitoring and proactive alerts. Whether it’s a spike in server load or a drop in application performance, Cloudmon alerts you instantly, enabling rapid response to ensure minimal disruption.
End-to-End Visibility:
Gain insights into every aspect of your IT operations. From hardware performance metrics to application health and user experience, Cloudmon provides a holistic view that helps you anticipate and address issues before they impact your business.
Customizable Dashboards:
Customize dashboards to meet the specific needs of different teams within your organization. From IT administrators to executive leadership, everyone can have the tailored information they need at their fingertips.
Advanced Analytics:
Leverage powerful analytics tools to parse vast amounts of data and extract actionable insights. Cloudmon helps you understand trends, predict potential outages, and optimize your IT resources for better performance.
Scalable & Secure Architecture:
Whether you're a small enterprise or a large corporation, Cloudmon scales with your business. Our platform is designed to handle the growing number of devices and data, ensuring reliability and performance at all scales.
With Cloudmon, empower your team to deliver a flawless digital experience. Monitor and analyze every interaction to ensure optimal performance and user satisfaction. Understand user behavior, diagnose issues in real-time, and improve your services based on precise, data-driven insights.
Join Leading Companies Worldwide
Leading organizations around the globe trust Cloudmon for their IT observability needs. Become a part of this elite group and propel your IT operations into a new era of efficiency and innovation.


























Sri Chakradhar Co-Founder & CEO, Entersoft Security







Anti-glare technology
Hoodless operations
Energy Star certified
USB power option
Power supply power option
For more details: www.mbuzztech.com jareesha.chirammal@mbuzztech.com Mobile compatible














Mobile compatible
Anti-glare technology
Hoodless operations
Energy Star certified
USB power option
Power supply power option
For more details: www.mbuzztech.com jareesha.chirammal@mbuzztech.com












































In today's digital landscape, managing IT efficiently is paramount. Cloudmon delivers a seamless observability solution that spans across on-premise and cloud environments, ensuring comprehensive visibility into servers, platforms, applications, endpoints, and the overall digital experience.
Comprehensive Coverage:
Monitor everything from on-premise hardware to cloud-based. Cloudmon's robust platform supports all major servers, platforms, and applications, ensuring you don't miss a beat.
Real-Time Monitoring and Alerts:
Stay ahead of the curve with real-time monitoring and proactive alerts. Whether it’s a spike in server load or a drop in application performance, Cloudmon alerts you instantly, enabling rapid response to ensure minimal disruption.
End-to-End Visibility:
Gain insights into every aspect of your IT operations. From hardware performance metrics to application health and user experience, Cloudmon provides a holistic view that helps you anticipate and address issues before they impact your business.
Customizable Dashboards:
Customize dashboards to meet the specific needs of different teams within your organization. From IT administrators to executive leadership, everyone can have the tailored information they need at their fingertips.
Advanced Analytics:
Leverage powerful analytics tools to parse vast amounts of data and extract actionable insights. Cloudmon helps you understand trends, predict potential outages, and optimize your IT resources for better performance.
Scalable & Secure Architecture:
Whether you're a small enterprise or a large corporation, Cloudmon scales with your business. Our platform is designed to handle the growing number of devices and data, ensuring reliability and performance at all scales.
With Cloudmon, empower your team to deliver a flawless digital experience. Monitor and analyze every interaction to ensure optimal performance and user satisfaction. Understand user behavior, diagnose issues in real-time, and improve your services based on precise, data-driven insights.
Join Leading Companies Worldwide
Leading organizations around the globe trust Cloudmon for their IT observability needs. Become a part of this elite group and propel your IT operations into a new era of efficiency and innovation.