Campion , Director of ITAD Services



3 Pillars of Digital Transformation Event - Private Sector 10th November 2022
Craig
About Stone Group
• Originally founded in 1991 as an Original Equipment Manufacturer building our own Stone branded Laptops, PCs and Servers for the Education sector

• Stone are the only UK based IT manufacturer with its own 100,000sq.ft recycling facility, ADISA and Government accredited based out of our main office located just off M6 Junction 13 Stafford

• 500+ Employees

www.stonegroup.co.uk



Fast Facts • £140m OEM Manufacturer & Value-Added Reseller based in Stafford • One of the UK’s fastest-growing VARs • OEM system builder – Stone-branded product – 120,000 devices per year • 500-staff single site operation • Customer Service ethos • Market-Leading Value Added Proposition • Multi-award winning Reseller, and ITAD provider • Staffordshire Business Of The Year & CRN Best Company To Work For 2021 (£101m-plus) • Strong, robust partnerships with key vendors (Microsoft, Senso, Acer, Asus, Dynabook, Cisco Meraki) • Forecast £150m Turnover for 2022 • In-house Support Desks – break-fix, expertise, consultancy
Endpoint Isolation Introduction and Value
Ryan Walker NWE Market – Category Manager Ryan.walker@hp.com
The endpoint PC is the key security battleground

•
It’s where people, data and the internet meet
•
That makes it the focus for cyber-attackers using social engineering
• Phishing • Ransomware • Therefore, organizations must prioritize defending their endpoints








HP CONFIDENTIAL SHARED UNDER NDA © Copyright 2021 Hewlett Packard Development Company, L.P. The information contained herein is subject to change without notice 7 Sure Start Sure Run Sure Admin Sure Recover Tamper Lock Sure Sense Sure Access Below the OS In and Above the OS Protection against BIOS Rootkits like Sednit LoJax Protection against Unauthorized Firmware Configuration Changes Recovery from Destructive Wiper attacks such as NotPetya, Shamoon Application Persistence against AV deactivation attacks like H1N1 Secure privileged assets from OS malware like Remote Access Toolkits Protection against malicious executables like CryptoLocker, TrickBot Protection against physical intrusion attacks like Evil Maid ATTACKS PROTECTED Protect user passwords from Credential Phishing attacks Credential Protection Sure Click Threat Containment for web or email borne malware like Emotet, Dridex
Organizations

two
• Next-Gen Anti-Virus (or “Endpoint Protection Platforms”/EPP) • Good at stopping known attacks • Endpoint Detection & Response (EDR) • Good at providing visibility about new threats, or variants of existing threats Clearly NGAV and EDR aren’t enough –attacks still get through every day
usually rely on
endpoint security products
HP CONFIDENTIAL. © 2021 HP Development
EPP AV/NGAV Visibility EDR/MDR/XDR Microsoft ATP Crowd Strike Vmware Carbon Black Containment & Isolation HP Sure Click Enterprise Z-Scaler MENLO Hysolate HP Sure Access Enterprise MS Defender, McAfee, Broadcom, Sophos, TrendMicro Tanium ENTERPRISE ENDPOINT SECURITY CONTROLS BUILDING A DEFENCE IN DEPTH STRATEGY AND IMPLEMENTING A ZERO TRUST Cylance
Company, L.P. The information contained herein is subject to change without notice.

Endpoint Isolation fills the endpoint security gap, stopping what NGAV and EDR miss. Provides inherent protection from malware and threats
Isolation fills the gap between NGAV and EDR
Provides inherent protection from known and unknown malware and other threats
Lowers security operational overhead
Provides seamless user experience
Endpoint
•
•
•
Endpoint Isolation Technology and Key Benefits











Endpoint Isolation – Advanced Protection Technology Endpoint software that virtualizes individual tasks Micro-virtual machine destroyed when task completes, eliminating any malware that may have been present Each high-risk task is isolated inside a “micro-virtual machine” • Email attachments • Office documents • Browsing • USB drive files
Inherent protection
Benefits of Endpoint Isolation
ZERO TRUST: Runs everything from untrusted sources in an isolated space on the endpoint
Protection
Doesn’t rely on detecting anything: “inherently protects”, including against zero-day attacks Protects against attacks from both “corporate” and “personal” vectors
Ransomware example
Endpoint Isolation in Action

Protection
Ransomware encrypts files within µVM. Blocked from Intranet. Introspection records malware activity. User closes task. No remediation necessary. Delivered via email; opened in µVM.
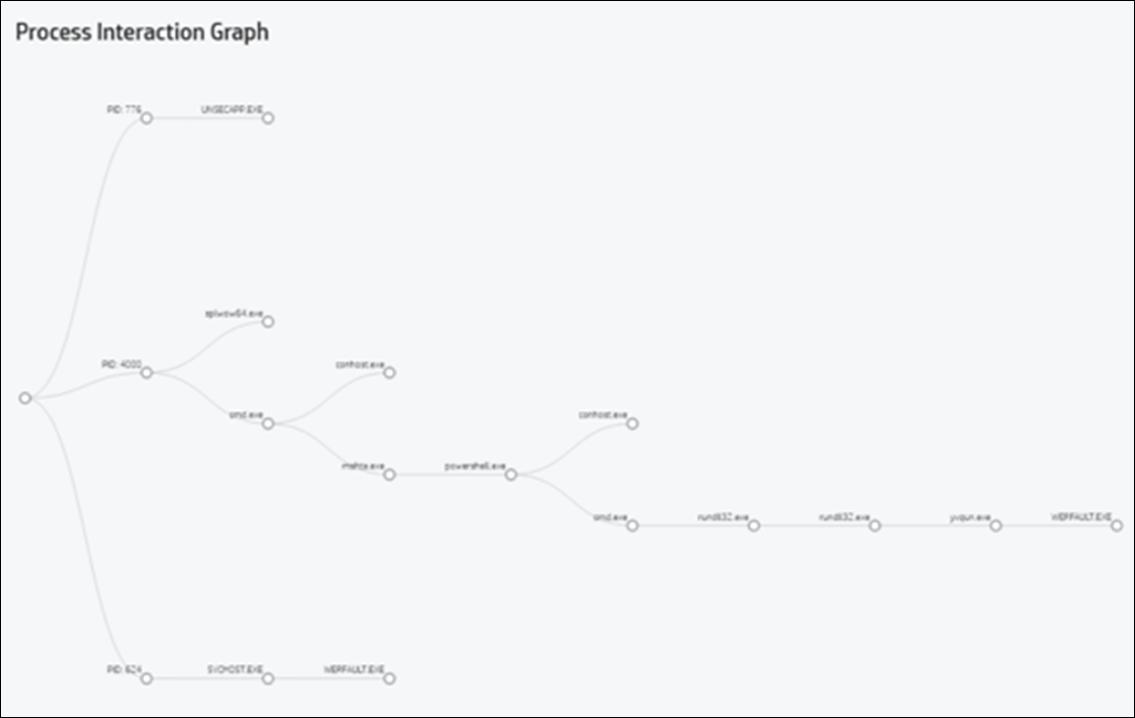
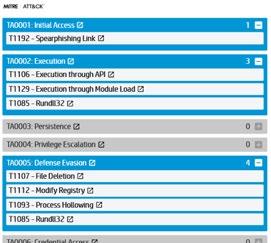

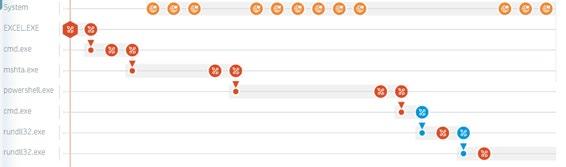
”Safe space” for observation allows for introspection
of Endpoint Isolation Realistic environment provides superior threat intelligence Cloud analytics provides historical analysis
Visibility Benefits
Visibility
Security

Endpoint
Efficiency Benefits of
Isolation
(urgent) Support Tickets
SecOps isn’t just a matter of minimizing the number of tools; what counts are the processes associated with those tools
false positives (inherent protection)
endpoint remediation (because we stopped attacks from dropping payload or propagating)
Security efficiency Fewer
Efficient
Fewer
Less

User experience Benefits of Endpoint Isolation User Experience No changes to user workflow Users operate as normal No remediation work Inherent protection lowers need to remediate endpoints Work with confidence Users less concerned about “infecting the whole place” Hardware assist Endpoint performance maintained
Endpoint Isolation Product Portfolio
•
Wolf Pro Security
Click Enterprise
•
•
•
•
•
•
•
Isolation Security for any Organization PC Pre-installed Software
Endpoint Isolation Product Portfolio World-Class
Sure
Software only (HP and Non HP PCs)
Enterprise class Threat Containment through EI and Credential Protection
Rich policy configuration and situational awareness
Cloud or on premises management
available
For enterprises, government, and any security-mature organization Edition PCs
on select HP Pro, Elite & Z PCs Software only (HP and Non HP PCs)
Complete endpoint security suite
Threat Containment via Isolation, Credential Protection, Optional NGAV (EPP)
Simple, cloud based management
Optimized for limited security expertise
*: 25 device minimum. SCE supports on premises Wolf Controller option **: Minimum purchase required
purchased, includes a paid 1 year or 3 year license. The HP Wolf Pro Security Edition software is licensed under the
terms of the HP Wolf
license Agreement (EULA) that can be found at: https://____________ as that EULA is modified by the following: “7. Term. Unless otherwise terminated earlier pursuant to the terms contained in this EULA, the license for the HP Wolf Pro Security Edition (HP Sure Sense Pro and HP Sure Click Pro)
will continue for either a twelve (12) month or thirty six (36) month license term (“Initial Term”). At the end of the Initial Term, you may either (a) purchase a renewal license for the HP Wolf Pro Security Edition from HP.com, HP Sales or an HP Channel Partner, or (b) continue using the standard versions of HP Sure Click and HP Sure Sense at no additional cost with no future software updates or HP Support.” 3. HP Wolf Pro Security Service is sold separately. HP services are governed by the applicable HP terms and conditions of service provided or indicated to Customer at the time of purchase. Customer may have additional statutory rights according to applicable local laws, and such rights are not in any way affected by the HP terms and conditions of service, or the HP Limited Warranty provided with your HP Product. For full system requirements, please visit www.hpdaas.com/requirements. 4. HP Wolf Enterprise Security is an optional service and may include offerings such as HP Sure Click Enterprise and HP Sure Access Enterprise. HP Sure Click Enterprise requires Windows 10 and Microsoft Internet Explorer, Google Chrome, Chromium or Firefox are supported. Supported attachments include Microsoft Office (Word, Excel, PowerPoint) and PDF files, when Microsoft Office or Adobe Acrobat are installed. HP Sure Access Enterprise requires Windows 10 Pro or Enterprise. HP services are governed by the applicable HP terms and conditions of service provided or indicated to Customer at the time of purchase. Customer may have additional statutory rights according to applicable local laws, and such rights are not in any way affected by the HP terms and conditions of service, or the HP Limited Warranty provided with your HP Product.
CAPABILITIES WOLF PRO SECURITY SURE CLICK ENTERPRISE Hardware Enforced Threat Containment Credential Protection Malware Prevention NGAV (optional) Customer Choice Cloud Based Wolf Controller (Management Console)* Simplified Advanced Advanced Policy Configuration Onboarding Service Partner Provided ** HP Wolf Security – Summary of Capabilities
product data sheet for details.
Edition (including
Pro and
SKUs
1. HP Security is now HP Wolf Security. Security features vary by platform, please see
2. HP Wolf Pro Security
HP Sure Click
HP Sure Sense Pro) is available preloaded on select
and, depending on the HP product
license
Security Software End User
is effective upon activation and
Summary Protection Visibility Security Efficiency User Experience Compliance & Audit Thank ! • The PC endpoint is the key security battleground • Operational efficiency is a crucial consideration for endpoint security • EDR and EPP solutions are not enough – attacks still get through Background Endpoint Isolation • Uses per-task micro-virtual machines to isolate and contain malware • Fills the endpoint security gap, stopping what NGAV and EDR miss Endpoint Isolation delivers unique value across five key dimensions
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
Peter Jones, CISSP, CISM, CIEH SASE Specialist
November 2022 SASE Your Way.
The future is evolving…fast.


of companies believe that their current business models will be economically viable through 2023 ONLY
11%
Source: The new digital edge: Rethinking strategy for the postpandemic era, McKinsey, May 2021
Hybrid work is transforming the way your organization operates



of CIOs say it’s important to empower a distributed workforce with seamless access to applications and consider high-quality collaborative experiences top of mind 85%
 Source:
Source:
Accelerating Digital Agility Research (CIO Data) Cisco, 2021
Applications are hyper-distributed across a diverse IT landscape

of CIOs say it’s important to maintain security, control, and governance across user devices, networks, clouds, and applications 85%

69% of CIOs believe insights will be more important than ever to deliver a seamless consumer experience

Accelerating Digital Agility Research (CIO Data) Cisco, 2021
 Source:
Source:









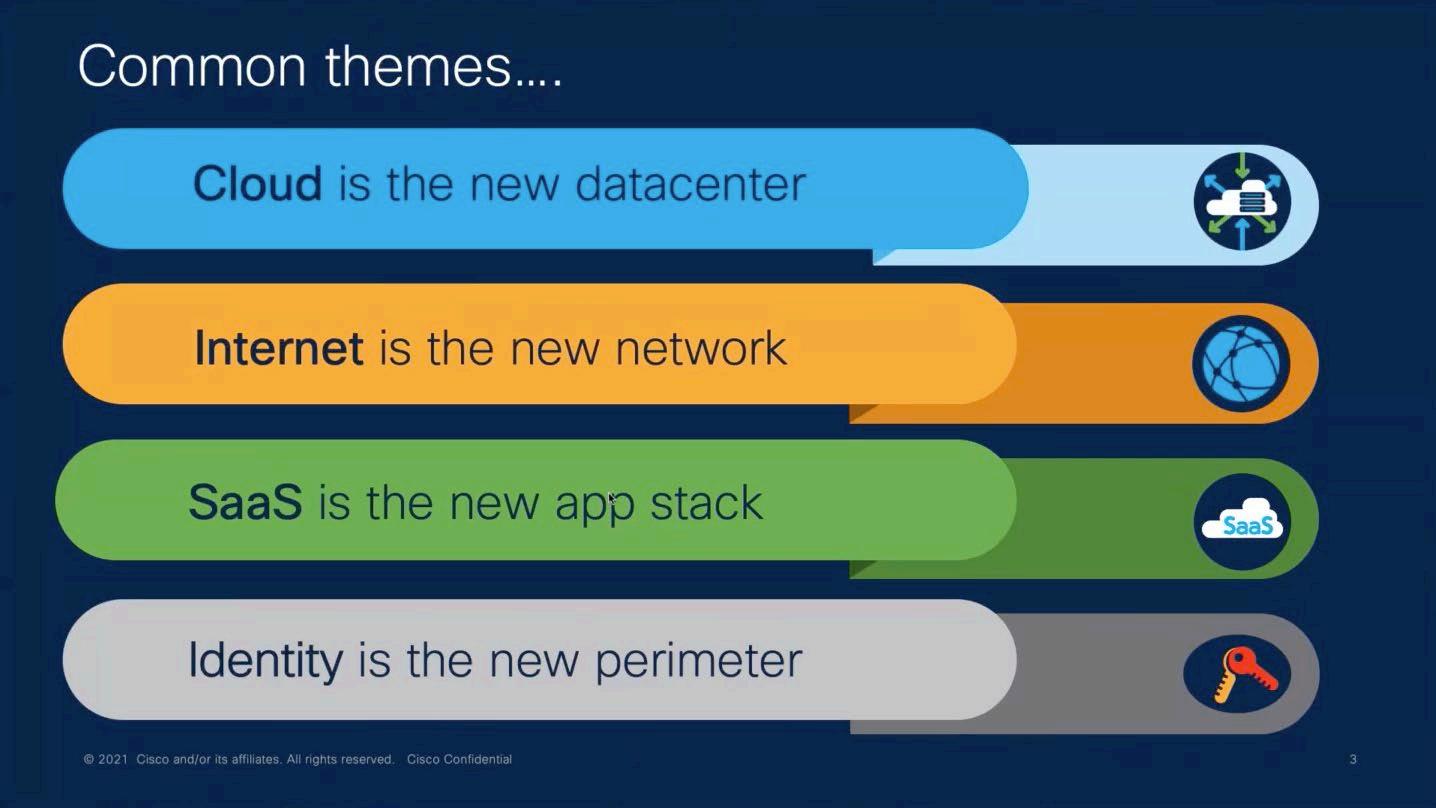
Hybrid work Applications The traditional networking model is inadequate The traditional networking model is inadequate SaaS IaaS Private cloud Internet Bottle neck MPLS VPN Internal 20% Internet 80% Traffic Changes in traffic patterns are creating bottlenecks and performance challenges Problems • App performance • User experience • Security efficacy • # of tools / vendors • Integrations
Are you ready in the Networkmiddle?transformation is needed
A transition to a cloud enabled topology
SASE
is










Hybrid work Applications
an approach and a cohesive long-term strategy to address these challenges
Cisco has a strong vision to deliver a fully integrated SASE solution, as well as the financial resources to execute the vision.
Gartner MQ report for WAN Edge Infrastructure, September 2021


Network transformation
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
a DC-centric
DC-centric MPLS VPN Cloud-Enabled S A S E Perimeter security appliances to protect network Internet Private Apps Internet SaaS
Transition from
topology to one that’s cloud ready
Major SASE use cases
Secure remote worker
• Seamless connection to apps and data anywhere users work
• Secure access to internet and cloud apps
• Authenticate users and ensure device health before establishing connection
Internet/ SaaS/ IaaS
Secure Access Service Edge
Secure edge
• Streamline connectivity to public and private apps across all office locations
SD-WAN fabric
• Provision SD-WAN fabric across thousands of users and locations
• Secure access to apps and direct internet access
Remote worker Campus/Branch, colocation and hosted data centers
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
SASE
End-to-end visibility
SASE Consumer
SD-WAN
Middle Mile
Security
Reduce cost
Improve OpEx with circuit consolidation and consolidation of UI touchpoints
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
Improve user experience
Bring services closer to user and leverage middle mile partnerships + password-less authentication to optimize connections
Minimize risk
Decryption & inspection addressing data loss, leveraging a true zero-trust approach across the IT perimeter
Cisco
Internet SaaS IaaS Provider
Private DC
Cisco SASE - Detail
Consumer
Branch / HQ
Network
Segmentation
End-to-end visibility
SASE
Provider
Secure Remote Worker
VPN-less Client VPN
Reduce cost
• Improve OpEx through circuit consolidation
• Reduce IT complexity and improve OpEx by consolidating UI touchpoints and leveraging centralized policy
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
Application Aware Routing Application Visibility
Device Posture Health
Hierarchical Topologies App to App
Multi-cloud Access
SD-WAN Optimization Middle Mile
Security
DNS security NGFW
CASB / DLP
Remote Browser Isolation Secure Web Gateway
Improve user experience
• Leverage password-less authentication measures to streamline workflows
• Leverage Cisco® SD WAN + middle mile partnership to optimize connections and reduce latency
Minimize risk
Private DC IaaS
Internet SaaS
• Proxy based architecture decrypts, inspects, and assists with data loss prevention to protect brand
• Leverage a true zero-trust approach by securing workplace and offpremises workforce to workloads
Cisco SASE Architecture
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
End-to-end visibility
Internet SaaS Private DC IaaS Provider SASE Consumer Branch / HQ Secure Remote Worker CASB / DLP Device Posture Health DNS security NGFW Remote Browser Isolation Secure Web Gateway Application Aware Routing Application Visibility Segmentation Multi-cloud Access Hierarchical Topologies App to App ZTNA Client VPN Network Security Service Edge SD-WAN Optimization Middle Mile Is it the WiFi? Is it the home network? Is it the SECaaS? Is it SD-WAN underlay? Is it the transit ISP? Is it the SaaS app? Is it the Application? Is it the ISP? Is it SD-WAN overlay?
Journey to SASE from DC-centric Topology
An example outcome of a joint session
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
DC-centric topology Move to SD-WAN and DIA Private DC to cloud-enabled and consolidating services Wrap in Zero-Trust Branch Campus INET SaaS IaaS Private DC Internet MPLS Remote User VPN Branch Campus SaaS IaaS Private DC Remote User VPN SD WAN INET MPLS LTE DIA Branch Campus Remote User SD WAN SASE Middle Mile optimization SD-WAN Security INET SaaS IaaS Branch Campus Remote User SD WAN Middle Mile optimization SD-WAN Security SASE Workload Workplace Workforce Zero Trust INET SaaS IaaS
Cisco SASE Offers
Cisco + Secure Connect SASE a la Carte
Build-your-own approach
© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public
Unified solution with converged UI and turnkey service



© 2022 Cisco and/or its affiliates. All rights reserved. Cisco Public At Cisco, we’re uniquely positioned to help Largest SD-WAN solution provider Leader in Zero Trust two years running Defending 100% of the Fortune 100 Networking Security Observability Cloud Computing 2021 Product of the Year Largest collective view of internet and cloud networks WAN Edge Magic Quadrant Leader 2021
CHG-MERIDIAN FINANCIAL SOLUTIONS
 Dominic Cockram, Country Service Manager UK/IE
Dominic Cockram, Country Service Manager UK/IE
Efficient Technology Management®








Technology Areas




Efficient Technology Management®
46



Efficient Technology Management® CORPORATE FIGURES The CHG-MERIDIAN Group in numbers: 2021 47 79% Information Technology Volume of lease origination broken down by technology sector 17% Industrial Technology 4% Healthcare Technology countries 29 nearly 1,200 employees Total technology portfolio financed and managed as at Dec 31, 2021 €7.8 billion Volume of lease origination as at Dec 31, 2021 1.727 billion


Lifecycle Management
TESMA®

Efficient Technology Management® 49

Efficient Technology Management® IT Project Allocation 50 70% 20% 20% 20% 10% 20% 20% 5% 10% 60% 20% 40% 75% 10% 20% 40% 40% 0% 20% 40% 60% 80% 100% Scoping Launch Initial Phase Useful Life End-of-Life Personnel Services Software Hardware
Taking care of the lifecycle




Efficient Technology Management®
51
Systems & Processes from start to finish Data management and analysis End-of-life/Refresh lowering total costs.


Efficient Technology Management® Total Cost of Ownership (TCO) 52 Tangible Costs Time Environmental Concerns Total Cost of Ownership 3. Environmental Concerns • Home vs Office • Partner Selection • Carbon Reporting 1. Tangible Costs • Hardware/Software • Maintenance/Support • Shipping & Taxes 2. Time • Internal vs External • All lifecycle stages • Scalability
Cost Reduction

53



Efficient Technology Management® Full absorption of project costs 54 = Something-as-a-Service Manufacturer & Supplier Contracts Implementation/Ongoing Services Hardware/Software Costs


Efficient Technology Management®
Process & System Integrations
Fixed costs throughout the lifecycle
Scalability Matrix
Asset Tracking
Useful Life Management
Refresh & Replace Repeatable Solutions 55 A connected network of platforms live & nimble
•
•
•
•
•
•

• Manufacturer solutions & tools • Supplier solutions & tools • Internal ITSM/accounting systems • Multi-party processes • Project management Portfolio Management Automation reduces the workload
Simple reporting and analysis of previous, existing and future IT estates






Efficient Technology Management® Auditing 03 Secondary Life 58 Collection 01 Erasure 02 Remarketing 04

Efficient Technology Management® Sustainable Lifecycle Thinking 60 1 Responsible Procurement 2 Eco-friendly distribution 6 Remarketing 3 Customer use 4 Data erasure 5 Refurbishment 7 Reuse carbonZER0 Technology asset management Lifecycle extension and waste reduction
Here's how it works

Efficient Technology Management®
61
Certified calculation
The calculation of CO2 emissions covers all greenhouse gases generated throughout the lifecycle of your IT devices, from manufacture and transport to use phase and end-of-life phase.

Certified climate change mitigation projects
Through carbonZER0, you are supporting internationally recognized and certified climate change mitigation projects based on the UN's 17 sustainable development goals.
Certificates
Low offset payments
The payments for offsetting carbon emissions increase your monthly lease instalment by just a few cents.
You receive an internationally recognized certificate as proof of the CO₂ emissions saved.
62
Certified climate change mitigation projects




DRINKING WATER in Kono, Sierra Leone WINDENERGY in Ovalle, Chile
MICROCREDITS in India
Efficient Technology Management®
63


64
asset
Flexible management; straightforward financial control and reporting Manage and allocate costs based on where they are incurred; internationally, departmentally, individually
technical and commercial asset data
Every stage of the
lifecycle
Full Transparency Combining
Improvement Strategies

66




Self-Service Platforms Asset & Portfolio Management Digital Planning Multi-Vendor Integration






Efficient Technology Management®
Landscape 68 Precise Forecasting Cost & Process Analysis Circular Economy Partner Processes Repeatable
Future

Software Review Meetings
Jordan Hewitt- Software Licensing Specialist

Review Meetings





Overview
Software
Purpose Line of Business Back Up Security












Line of Business Microsoft, Google or Both M365 Business Basic M365 Business Standard M365 Business Premium Office365 E1 Office365 E3 EMS E3 Azure Active Directory Plan 1 Intune

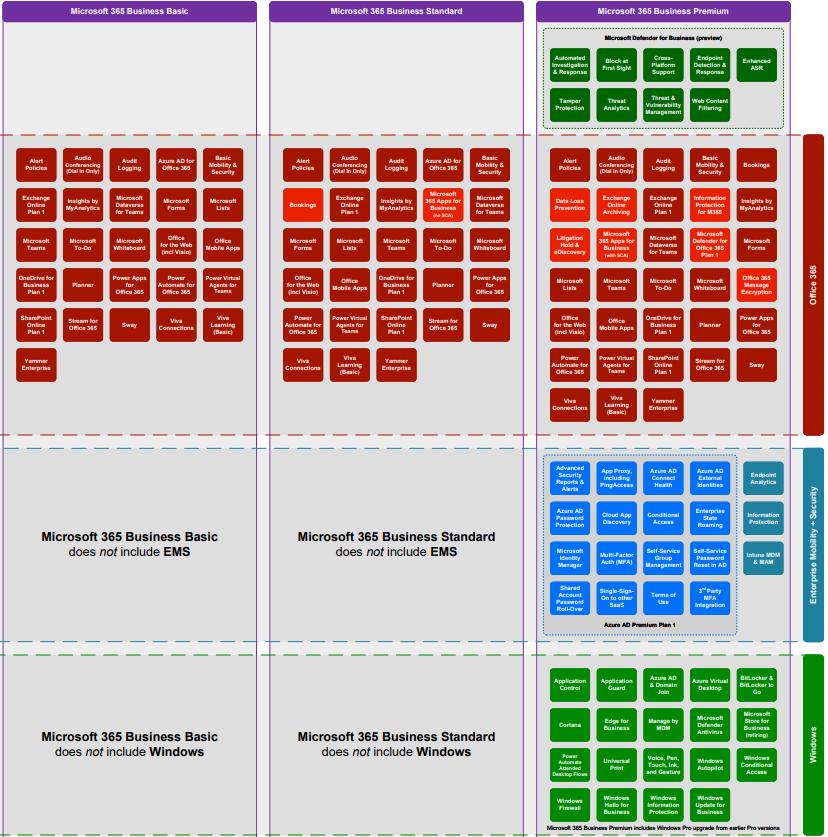




Microsoft Business Plans M365 Business Basic M365 Business Standard M365 Business Premium Sub Users 300




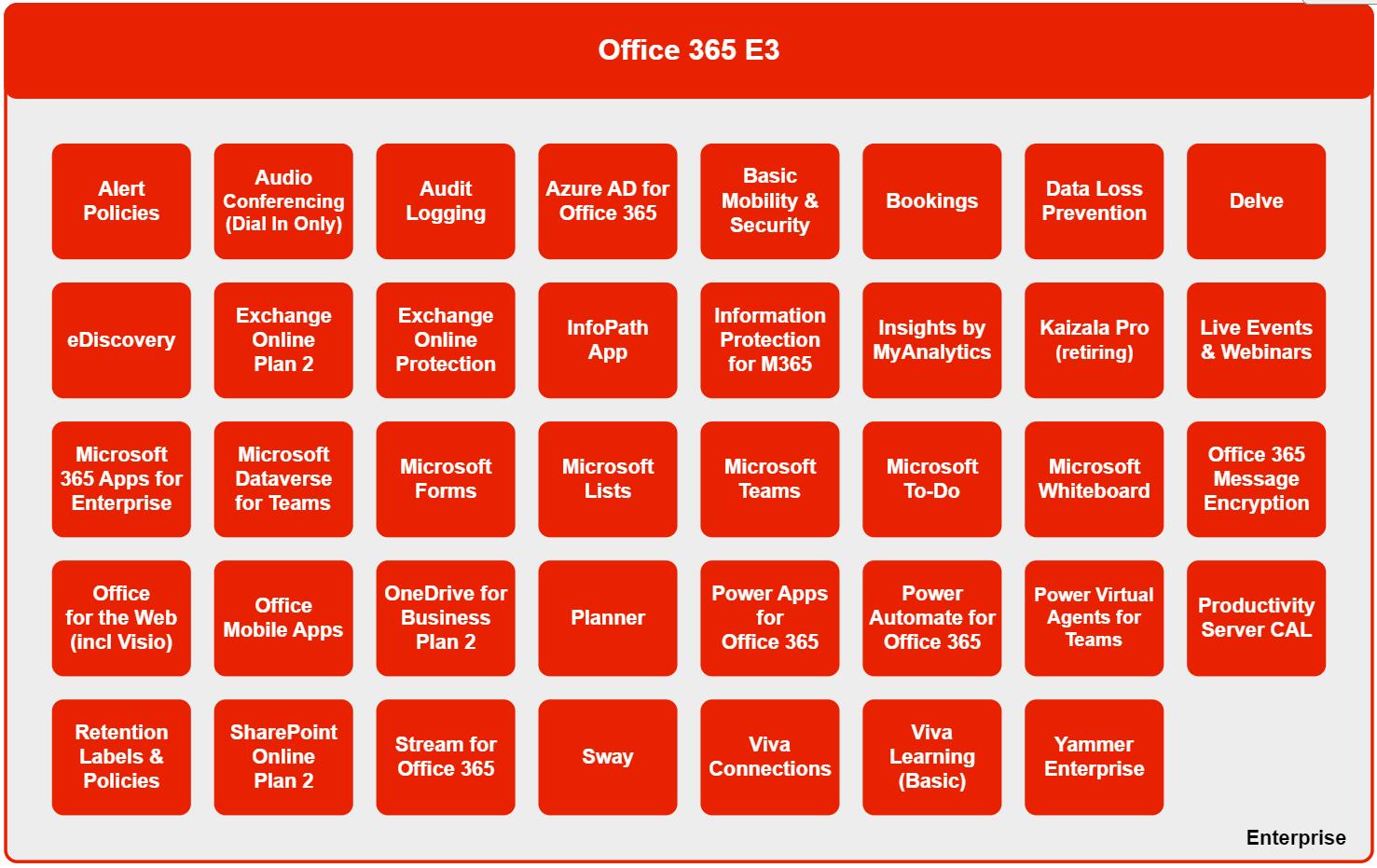
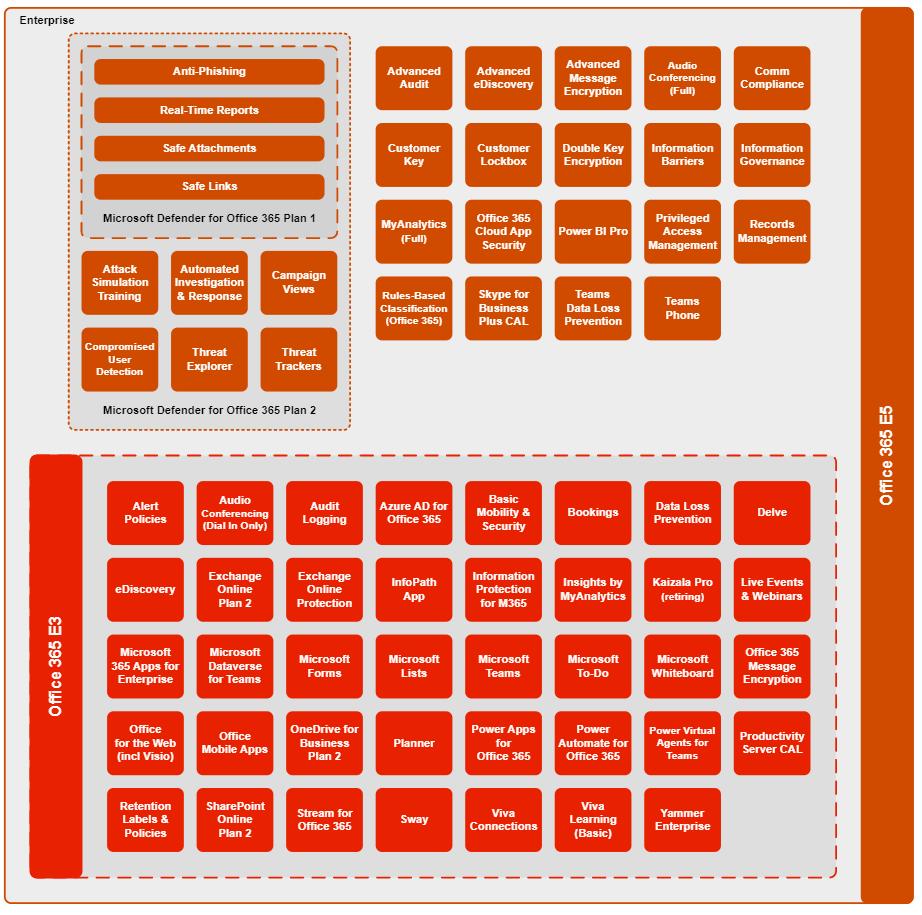
Office 365 E3 / E5 Office E3 Office E5 Step-up No License restriction (Min 1)








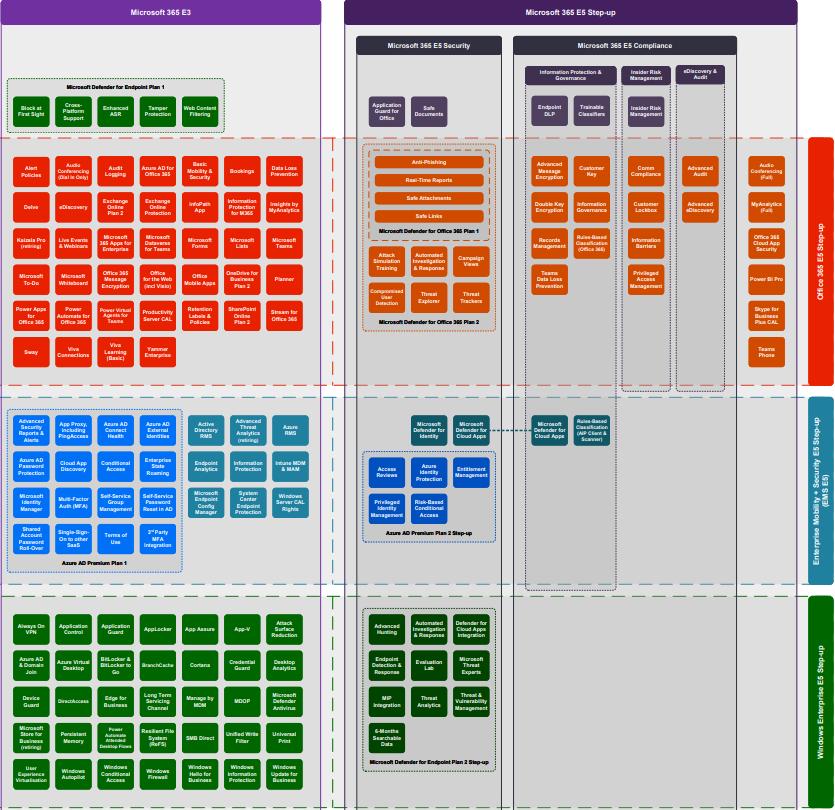
Microsoft 365 E3 / E5 Cloud Suite Office 365 Enterprise Mobility & Security Suite Windows Operating System Defender for Endpoint Microsoft Defender for Office 365 Power BI













Backup Microsoft do NOT Back up your data Cloud to Cloud / On-Prem BackUp Vendors : Barracuda Redstor Veeam Azure BackUp Many More









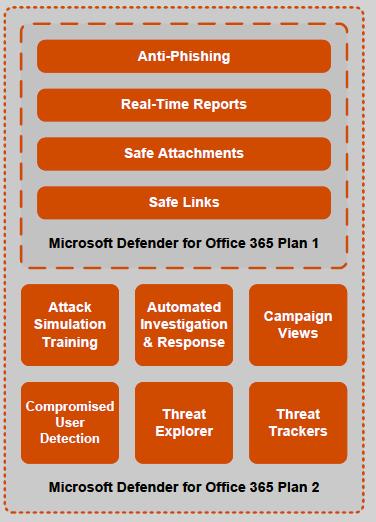




Security Microsoft Defender for Endpoints / O365 Device & Data Vendors: Watchguard Sophos Sonicwall McAfee Many More
Thank You.

Sustainability and E - Waste: Our Journey Craig
Campion

IT Asset Disposal – A Global Challenge

• Unwanted or surplus PCs, printers, networking, communications and telecoms equipment plus other electronic devices is collectively known as e - waste.


• In 2019, the Global E - Waste Monitor reported that out of 53.6m metric tonnes of e - waste produced worldwide, 82% of it was sent to landfill, incinerated or illegally traded.
• The world collectively is increasing the total e-waste figure by approximately 4% every single year.
www.stonegroup.co.uk




www.stonegroup.co.uk IT Asset Disposal – UK e - Waste Facts & Value 1.5 tonnes of WATER 21kg of CHEMICALS 240kg of FOSSIL FUELS The production of a single computer and monitor uses at least…







www.stonegroup.co.uk IT Asset Disposal – A National Challenge 23.9kg of e - waste Per Person £370m lost each year in valuable raw materials 500,000 tonnes unaccounted e - waste 31m laptops currently hoarded Global Waste Monitor Report Lancaster University Anthesis Report & Lancaster University Lancaster University







Protect The Planet and… PROTECT OUR CHILDREN AND OUR ENVIRONMENT




















Choosing the Right E - Waste Partner Free Collections Fully Accredited Secure Data Destruction Complete Traceability Cash Rebates Peace of Mind Own Onsite Facility
Stone 360 Demo
Craig Campion


Stone 360

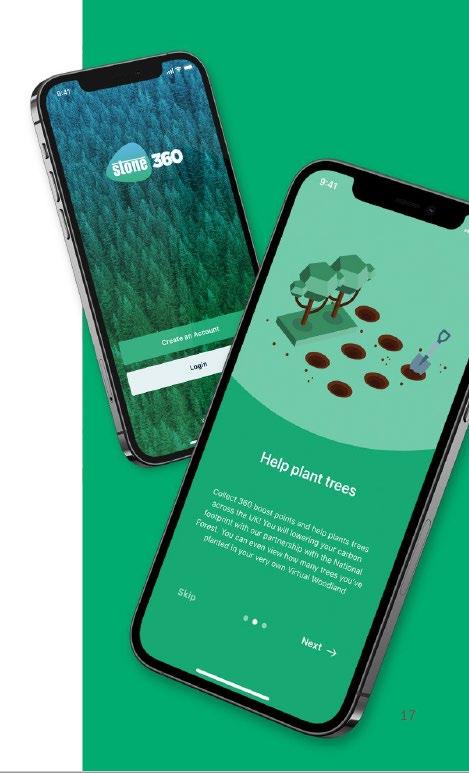
Stone 360 Statistics Since Launch 10,000 downloads (both iOS/Android) 4,100 registered users (200 per month) 4 million head count from registered customers 940,000 units collected 5,000 trees planted (est. 60 tonnes of CO2 reduced). 88% ITAD conversion for registered customers



Constant Innovation 1. New Partnership - Ecologi 2. Major UI/UX enhancements (Woodland seasons, dark mode) 3. Edit a collection feature 4. In-App Messaging 5. Site location enhancements (Geo-location) 6. Driver location tracking 7. Welcome screen & on-boarding 8. In-App documentation & signatures
Thank You

Making a Digital Difference
Stone Group Sustainability Framework
 Sheryl Moore Head of Sustainability
Sheryl Moore Head of Sustainability
What does Sustainability mean to ensuring a responsible business?


Resilient balance sheet and responsible business Resilient communities (Employees, Supply chain and Customers) Resilient environment
Sustainability is a mindset that seeks to create a resilient, responsible and purpose driven business by safeguarding three vital features no business can operate successfully without:
What

Sustainability mean to ensuring a responsible business? Sustainability is a mindset that seeks to create a resilient, responsible and purpose driven business by safeguarding three vital features no business can operate successfully without: Resilient environment Resilient communities Resilient balance sheet and Responsible business Includes environmental factors such as: • Resource use • Waste • Carbon • Biodiversity • Pollution (land, air and water) Includes social factors such as: • Employment of local labour • Equality and Diversity • Supporting charities through giving and volunteering • Inclusivity • Spend with social enterprises • Employee engagement and wellbeing • Training and development • Tackling social deprivation • Local supply chain Includes commercial and ethical factors such as: • Margins • Cashflow • Operational costs including lean • ROI • Risk Management • Purpose • Ethics • Responsibility
does
Framework Structure
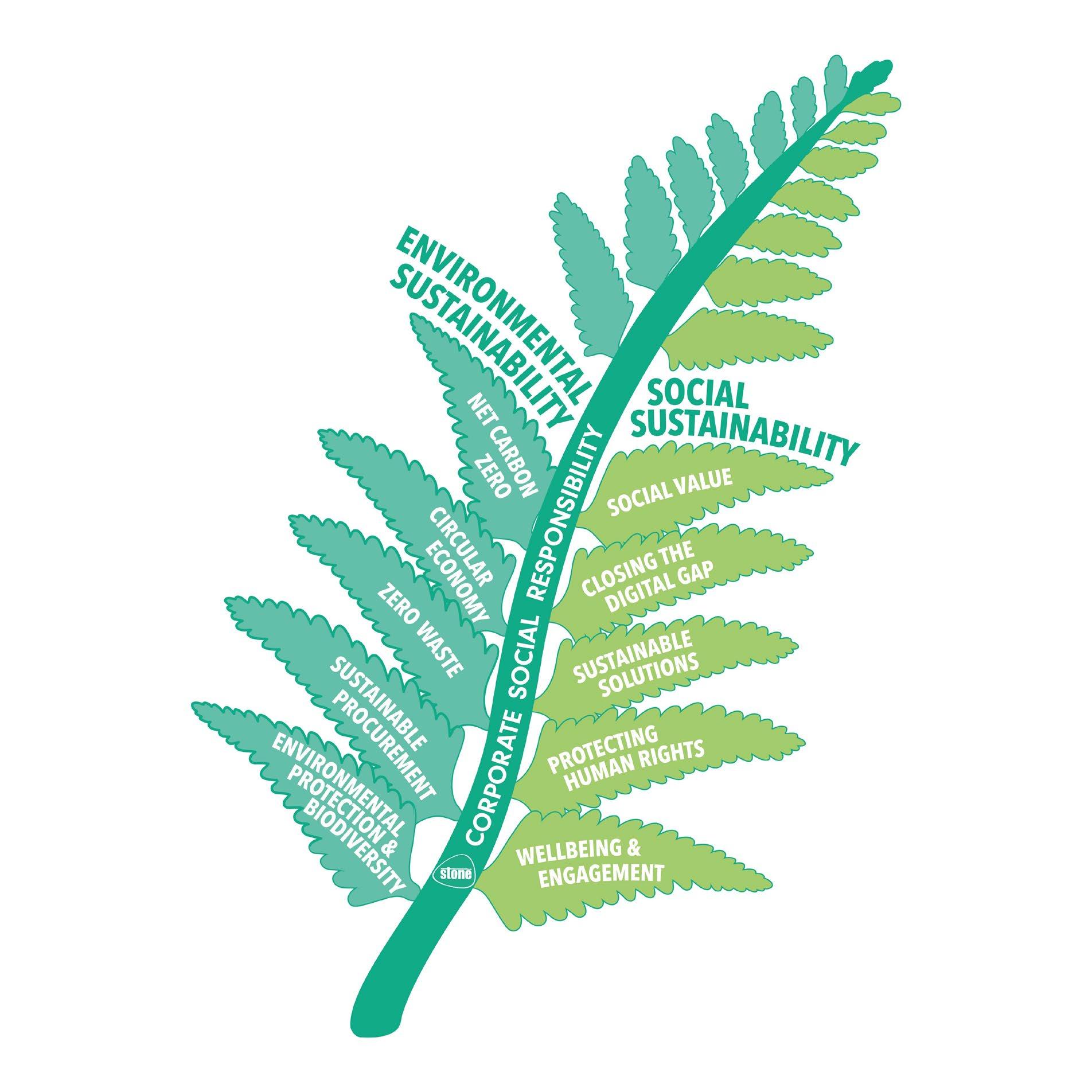

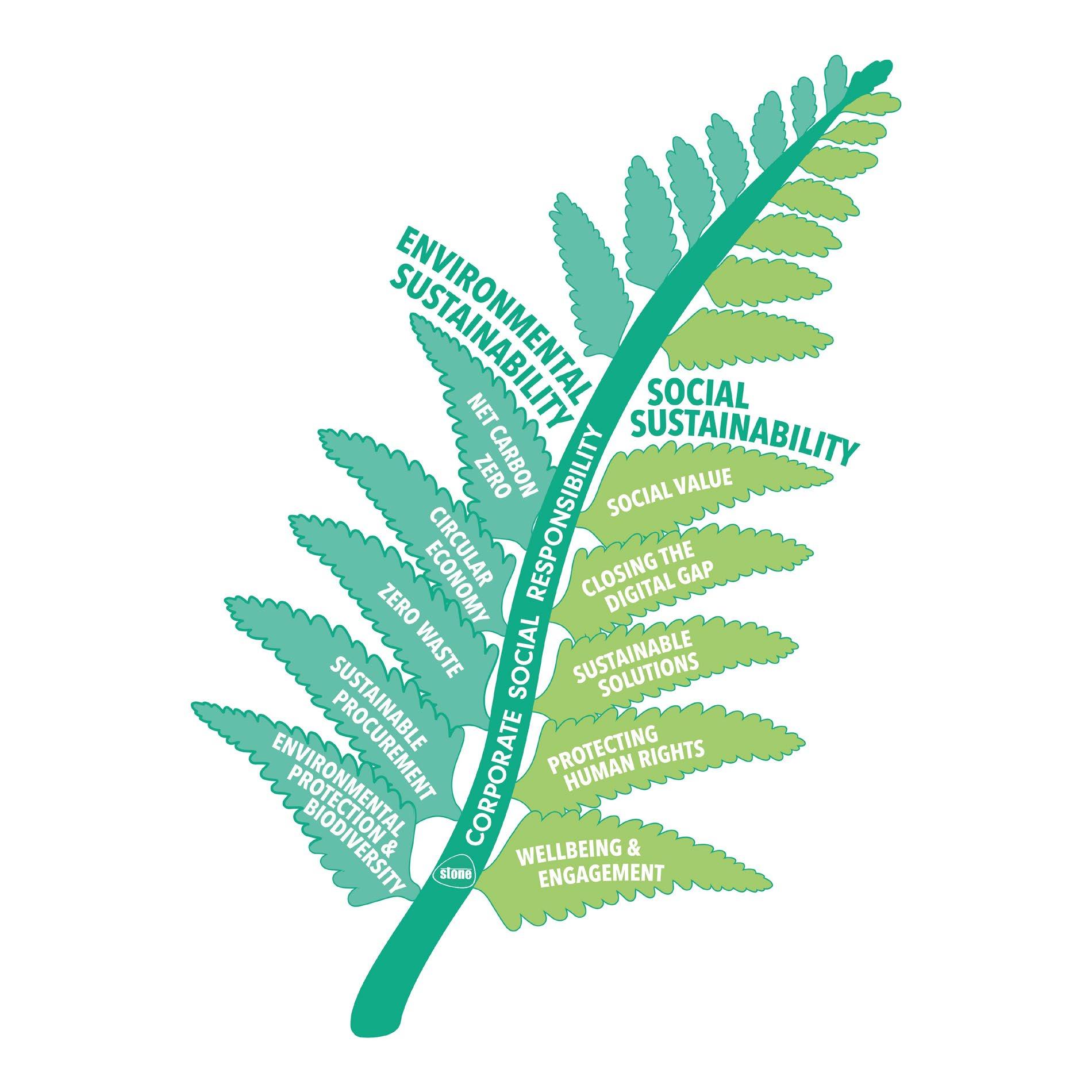
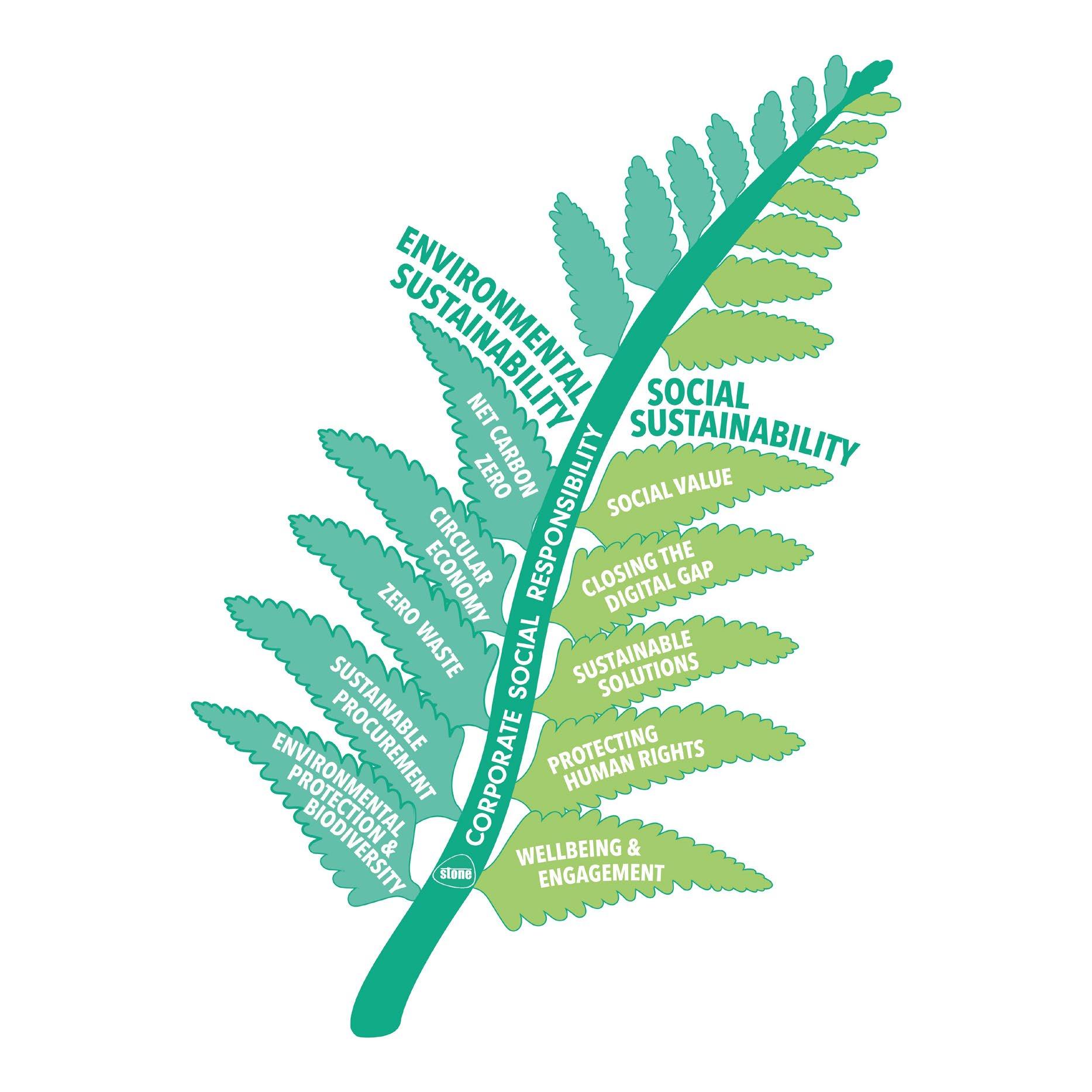
The “Making a digital difference” framework is split across the two focus areas of Environmental Sustainability and Social Sustainability with ten areas of activity
Environmental Circular Economy (SDG 12, Responsible Consumption/Pillar infrastructure/Repair/Reuse/Warranty) Sustainable Procurement (SDG 11, Sustainable Cities/Pillar Partnerhubs) Net Carbon/GHG Zero (SDG 13, Climate Action/ Target Net Zero 2030) Environmental Protection & biodiversity (SDG 14/15 Land and Sea) Zero Waste (SDG 15, Life on Land)
Framework Structure

The
Sustainable Solutions (SDG 9, Innovation, Pillar Networking)
Social Value (SDG 10, Reduce Inequalities)
Wellbeing and Engagement (SDG3, Good Health)
Protecting Human Rights (SDG8, Good Jobs/economic growth/security)
Closing the Digital Gap (SDG4, Quality Education)
“Making a digital difference” framework is split across the two focus areas of Environmental Sustainability and Social Sustainability with ten areas of activity Social Sustainability





Sustainability Pillars Circular Economy Carbon Reduction Sustainable Procurement Environment Protection & Biodiversity Zero Avoidable Waste We will achieve net zero carbon by 2030 We will continue with Zero to Landfill and be single use plastic free Our operations will ensure a healthy environment and increase biodiversity We deliver a circular IT Solution at every stage of Asset lifecycle We will always drive sustainability with our Supply Chain
Environmental
Social Sustainability Pillars




Sustainable Solutions

Closing the Digital Gap
Working with partners to reduce digital poverty through hardware and reduce digital divide through learning and development
Embracing innovation and providing sustainable solutions to all stakeholders
Social Value
Wellbeing and Engagement
Protecting Human Rights
Delivering Social Responsibility through our actions Measure, monitoring and delivering social value
Supporting employees and embracing inclusion and diversity
Supporting communities and individuals to ensure equality of opportunity and access

Sustainability Stages – 3 year programme Stage 1 Integrity and Inform Stage 2 Innovate and Engage Stage 3 Inspire and Lead
Stage 1 Integrity and Inform





To understand what we need to measure and where we are up to
Stage 2 – Innovate and Engage
Deliver on targets, enhance digital and sustainable offering to support all stakeholders
Stage 3 – Inspire and Lead
Provide leading solutions to support our customer’s sustainable ambitions through sustainable solutions, reducing environmental impact and increasing social value
Progress Divided across the Three Stages
Circular Economy Sustainable Solutions Carbon Reduction Social Value Sustainable Procurement Closing the Digital Gap Environment Protection & Biodiversity Protecting Human Rights
Zero Avoidable Waste Wellbeing and Engagement
Framework Principles

Stone’s Making a digital difference framework sets a common direction of travel and is made up of two parts: Environmental Sustainability and Social Sustainability. The framework is flexible and will be adapted as our business progresses through the stages and as the sustainability landscape changes and evolves. The framework is a 3 year programme with each stage required to be completed in turn Each business vertical will support the framework.
Framework governance will be managed through the Sustainability Leadership Forum

Framework KPIs How successfully we are progressing the actions Making a Digital Difference framework will be measured through a series of social value, cost and volume centred KPIs Each business vertical is to report on progress to Group SLF on a centrally held dashboard Environmental KPIS Social KPIS Net Zero Carbon – Scope 1,2,3 Social Value Generated by Client and Business Vertical (Thrive System) Zero Avoidable Waste – ITAD volume and Zero Waste to Landfill accreditation Charity donations and volunteering Cost and Volume of Water Learning and Development Environmental Incidents Employee Engagement

Stone Group Vision & Values
Our Vision
To empower our customers to improve the education, health and quality of life of people in the UK or to transform their businesses creating greater productivity and value.

Our Values




Social Value Linked to PPN06/20 Representative of Stone’s commitment to being a responsible business contributing to the wellbeing, inclusion and engagement of communities Specific to your needs Social Value Return and data Reduce (Repair)– Reuse (ITAD) Stone Refurb – Recycle – Zero to Landfill Diversion from Landfill/Carbon Saved/Units recycled/Water Impact/Plastic saved/Precious Metals/Energy Saved Employment/training/work experience/community projects/ T Levels/ school Engagement Green spaces/mental health first aiders/volunteering/ apprentices
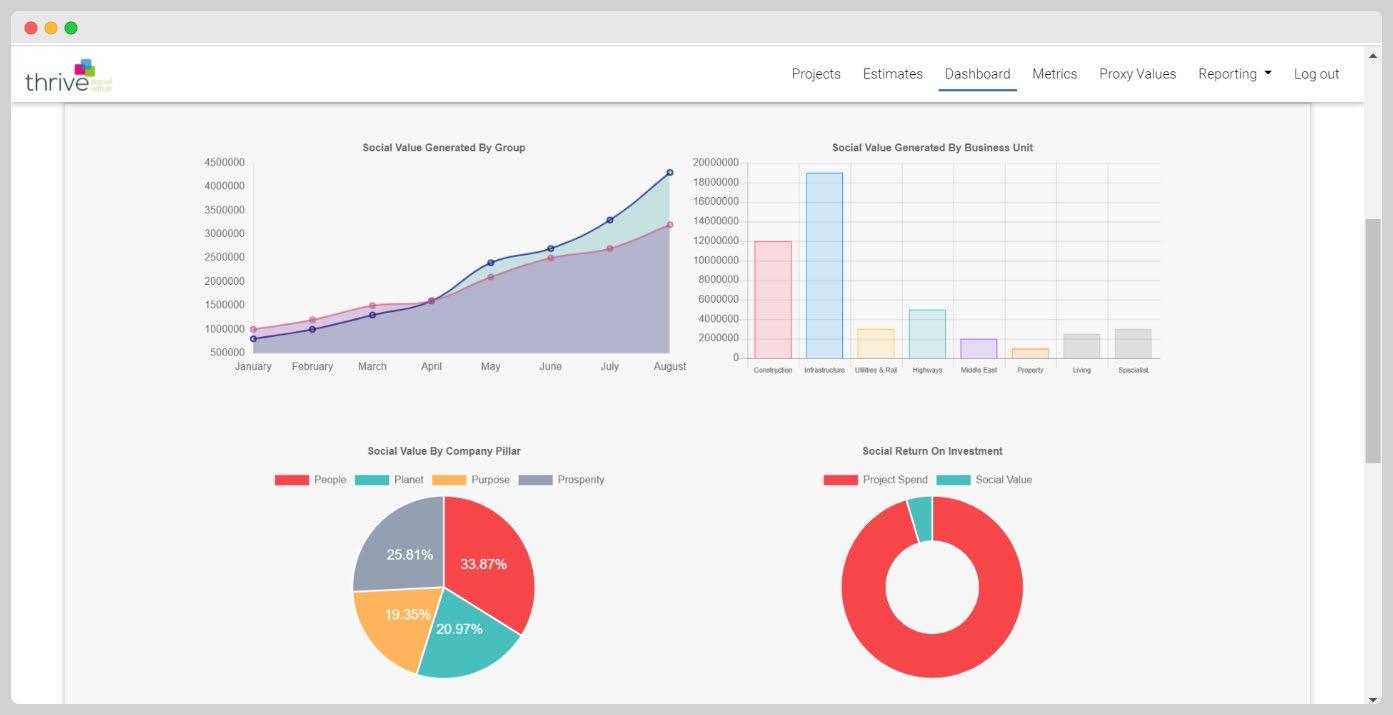
Social Calculator Timeline 107 By Customer by Business Vertical • Edit Master text styles • Second level • Third level • Fourth level • Fifth level
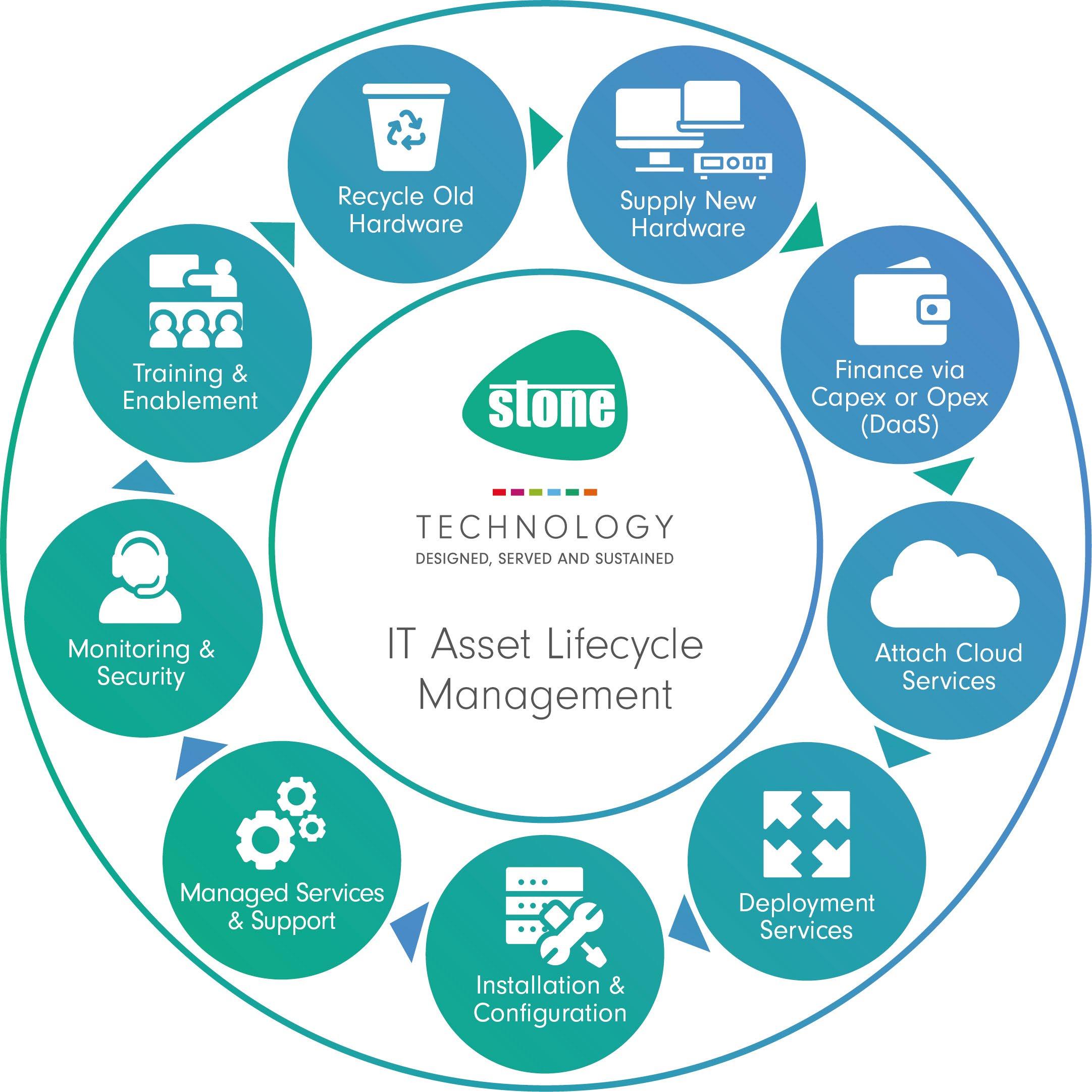
What We Do: IT Asset Lifecyle


Customers can come to us at any point in the life of technology and we can offer a solution to all needs.
Our Circular IT strategy allows us to be at the forefront of technology by providing proactive, innovative and safe ways of working.























































 Source:
Source:



 Source:
Source:


























 Dominic Cockram, Country Service Manager UK/IE
Dominic Cockram, Country Service Manager UK/IE

















































































































































 Sheryl Moore Head of Sustainability
Sheryl Moore Head of Sustainability




































