

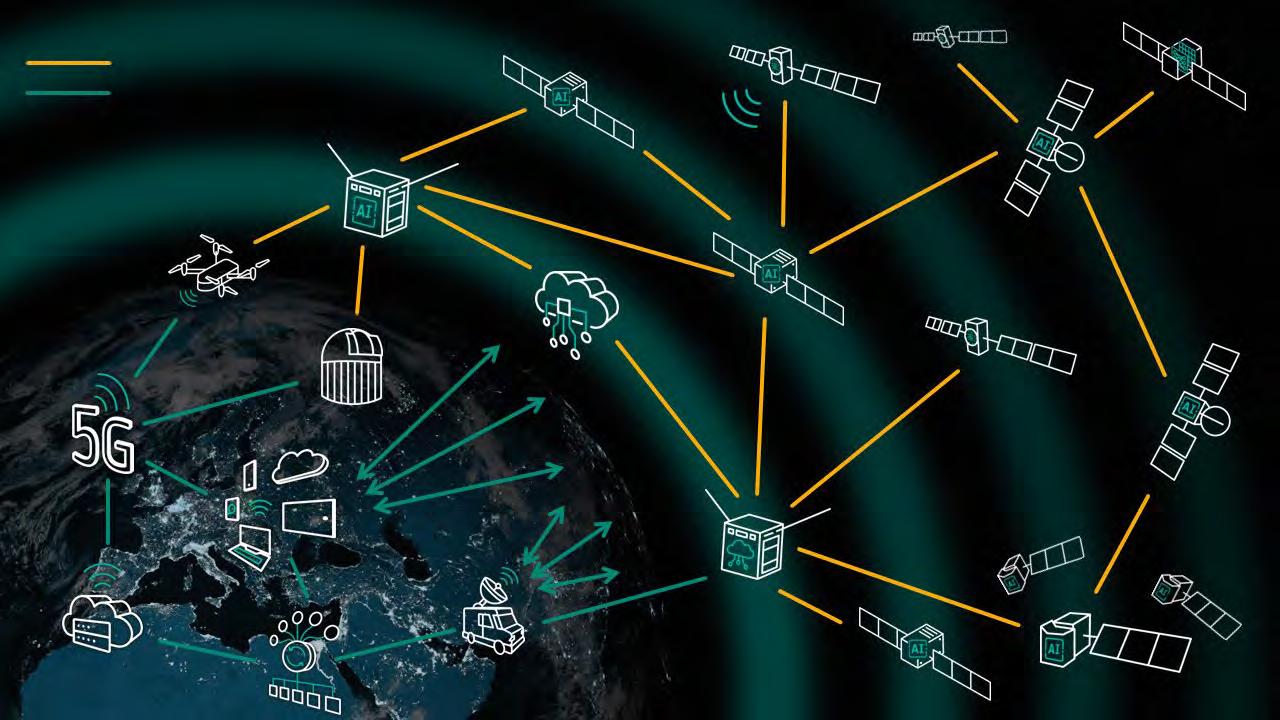
The evolving landscape of space and cybersecurity
Digital Twins
Virtual platforms for real-world breakthroughs in cyber and space
Spanish Space Sector
The Director of the Spanish Space Agency reveals current plans and future strategies


Cyber in Defence
The evolving role of cyber in modern defence to maintain security and sovereignty
Civil Security from Space
Using space technology and assets to mitigate and resolve humanitarian crises
Editors
Isabelle Roels, Karen Rogers, Karen Packham, Damian Schogger and Alastair Pidgeon
Design
Cary Fielder
Contributors
Federico Antonello
System and Applications Engineer, European Space Agency (ESA)
Jose Pizarro
AI and Data Science Engineer, ESA
Antonio Romeo
Project Manager for DestinE Platform Use Cases, Starion
Simone Urbano
System Simulation Engineer – Security Services, Nexova
Matteo Merialdo
Cybersecurity Principal, Nexova
Hanna-Miina Sihvonen
Head of Civil Security from Space Programme Office, ESA
Alex Vorobiev
Programme Manager, Starion
Luis Rodriguez
Space Missions Project Manager, Starion
Juan Carlos Cortés Pulido Director, Spanish Space Agency
Rubén Francisco Pérez Moreno
Sales Manager, Starion España
Roberto Mazzolin
Cyber, Space, Defence and Security Technology Strategist, Starion and Nexova
Panagiotis Bellonias
Technical Lead of the Scenario Team, Starion
Alexandru Militaru
CITEF Product Owner, Nexova
Simon Machin
Meteorologist and Manager of the Met Office Space
Weather Programme
Alexi Glover
ESA Space Weather Service Coordinator
Publisher
Federico Da Dalt
Space Weather Application Scientist, Starion
Gareth Lawrence
Space Environment Specialist, Starion
Yorgos Efstathiou
Data Systems Project Manager, Starion
Paolo Astolfi
AIV/AIT Engineer, Starion
Cristian Michael Tracci
Policy Analysis and Outreach, Senior Manager, European Cyber Security Organisation (ECSO)
Peter Kirkov
Former National Cybersecurity Coordinator, Bulgarian Government
Douglas Wiemer
Chief Technology Officer – Cyber, Starion and Nexova
Delia Ioana Spinu
Cybersecurity Legal Consultant, Nexova
Bruno Merín
Head of ESA’s European Space Astronomy Centre (ESAC) Science Data Centre (ESDC)
Teodoro Bonariol
Flight Operations Engineer, Argotec
Pablo Beltrami
Programme Manager and Ground Segment Competence Lead, Starion
Sara De La Fuente
Work Area and Project Manager, Starion
Alfredo Escalante Lopez
Spice Work Package Manager at ESA, Starion
Héctor Pérez
Archives and SPICE Software Development and Operations Work Area Manager, Starion
Starion and Nexova Group, Rue des Etoiles 140, 6890 Libin, Belgium





Welcome to
Welcome to the September edition of OpenSpace.
OpenSpace provides insights into key programmes and initiatives within the space and cybersecurity sectors. As a reader of the magazine prior to joining Starion and Nexova, I found it very informative to read insiders’ views of some of the activities and advancements taking place in our sectors. That’s why, as the new Chief Executive Officer of Starion and Nexova, I was keen to continue publication of this unique magazine.
Starion and Nexova, which are focused predominantly on space and cybersecurity respectively, are sister companies working to continue to bring the exceptional service clients have come to expect from our experts. Both companies are entering a new chapter of growth, and within this publication you will hear from many of our clients and industry organisations who are driving some of the initiatives and programmes we are working on.
Our first article looks at the ongoing debate about ‘what is a digital twin’ and how they are being increasingly used within space, cybersecurity and other market sectors. Then, as the importance of cybersecurity continues to grow, we look at how it is being used within the defence sector by both international organisations and national agencies, especially now that space and cyber have been
designated as strategic operational domains within defence. Alongside this, we investigate how international defence exercises are preparing cybersecurity experts for real-world attacks, highlighting how defence is, in turn, a priority focus for cybersecurity. You will also find an article on how organisations are having to adapt to one of the new EU cybersecurity regulations – the Cyber Resilience Act.
From a space perspective, we were delighted to speak to Juan Carlos Cortés Pulido, Director of the Spanish Space Agency (created in 2023), who provides an insight into the importance of the space sector in Spain and the Agency’s ambitions for the future.
We also look at the growing significance of space data and technologies within civil security, and why tracking space weather activities is so vital for our critical infrastructures globally. Finally, we invite you to meet some of the ‘unsung heroes of space’ – the people and technologies that underpin every space mission but never appear in the spotlight.
Enjoy your read.
Gaëtan Desclée CEO, Starion & Nexova




Powerful tools for simulating, analysing and optimising real-world systems
Digital Twins: Virtual Platforms for Real-World Breakthroughs


The growth of digital twin applications has been significantly driven by advances in big data and artificial intelligence (AI). They now provide powerful tools for simulating, analysing and optimising real-world systems in virtual/ hybrid environments. But what is a digital twin? OpenSpace looks at how they have evolved and are being used in a range of scenarios and markets, making real-world differences.
Throughout history, simulation and modelling have been widely used across various fields. In the space sector, for example, software-based simulators and mission models have long been employed to support spacecraft design, validation and operations preparation, and to predict and analyse satellite anomalies while in orbit. Yet only in recent years, with advancements in technology, have we been able to develop ’digital twins’ – virtual replicas powered by near-real-time data feedback.
Although digital twins are relatively new, the concept of using replicas, twins, models and simulations dates back thousands of years. A good example of this is the tomb of the Mausoleum of the First Qin Emperor that was built in the town of Lingtong District in the city of Xi’an, China. Dating back to around 210 BCE, it contains potentially one of the first models we are aware of. Relatively recent excavations around the complex discovered in the region of 7,000 statues of terracotta warriors, horses, officials, acrobats, strongmen and musicians created to serve the emperor in his afterlife. In more recent years, using non-invasive techniques
such as geo radar and gravimeter investigations, archaeologists have determined that the ‘palace’ measured 140 x 110 x 30m. Interestingly, they found mercury being used in the tomb to simulate the hundred rivers, the Yangtze, the Yellow River and the Great Sea, which sat below a representation of the heavenly constellations.
What is a digital twin?
The first practical definition of a digital twin originated from NASA in an attempt to improve physical model simulation of spacecraft in 2010 – it believed a digital twin can be defined as a model-based approach with digital implementations.
Today, the definition of a digital twin varies depending on who you are talking to, the market it is used in, what it is created to represent and the intended use. It can be a simulation or emulation of a system that is updated with data from the operation of that system and therefore works as a twin of the real system. In recent years, people have started calling a broader set of models, simulations or emulations “digital twins”,
but this is incorrect. A digital twin must be supplied with the relevant data to enable it to represent the full life cycle of a product or system, updating continuously via real-time data feeds.
Federico Antonello, System and Applications Engineer at the European Space Agency (ESA), comments: ”To me, a system qualifies as a true digital twin only when it incorporates active feedback from the physical asset to support informed decision-making. It begins with a model that is continuously refined using test and/or operational data to improve its accuracy and ensure alignment with the actual asset. The digital twin uses data from tests and operations to refine the design of an asset – either during development or for future versions – and to support ongoing operations and troubleshooting.
“During the testing phase, the digital twin enhances outcomes by integrating real-time test data into simulation models, helping to identify optimal strategies and detect anomalies early. This enables timely adjustments to the asset itself. In operation, digital twins support both day-to-day decision-making and long-term planning by providing insights into asset

health, consumables and system status – ultimately boosting performance, efficiency and scientific return.”
Jose Pizarro, AI and Data Science Engineer at ESA, adds: “If you look at a cybersecurity operations centre, you model your network of assets and the interactions of all the communications. In the event that one part of the network fails or someone hacks into the system, you can use your digital twin to identify how it affects the rest of the network. You can model the operating system on each asset, detect the vulnerability and patch it without bringing down the whole network.
This is a different perspective, but because a lot of the time what we do in cybersecurity is the same as we do in space operations, it’s just called fault diagnostics or fault tolerance and fixing stuff that’s broken. In space operations we fix things that are just broken: in cybersecurity we fix things that have been deliberately broken.”
Emulation vs model-based digital twins
There are two common approaches for digital twins: emulation-based and model-based. Each offers distinct advantages.


Image © ESA


Emulation-based digital twins aim to replicate real devices, systems and networks with high fidelity, enabling a true-to-life digital environment. Their ability to interact dynamically with changing conditions makes them ideal for real-time testing, development and operational analysis.
The strength of emulation-based twins lies in their precision and responsiveness. By mirroring actual hardware and network behaviours, they can deliver detailed and accurate results that closely reflect real-world performance. This makes them especially suitable for testing cybersecurity strategies, network configurations and mission-critical systems. However, their reliance on high-fidelity emulation can become a limitation when dealing with components or scenarios that are too abstract, too complex or not feasible to replicate directly.
By contrast, model-based digital twins rely on mathematical models and algorithmic representations of systems. Rather than replicating physical components, they simulate behaviours using rules, formulas and assumptions. This approach is suited to scenarios that require abstraction, such as long-term forecasting, optimisation tasks or systems that cannot
be emulated efficiently. While this method often results in lower fidelity and less specificity, it offers scalability and computational efficiency, making it essential in many large-scale or conceptual applications.
The most effective digital twin implementations often combine both approaches. Emulation provides depth and realism where accuracy is critical, while modelling offers flexibility and abstraction where needed. Choosing the right balance depends on the goals of the simulation, the nature of the system and the constraints of the environment. Understanding the distinctions between these two approaches is key to building digital twins that are both reliable and fit for purpose.
Digital twins in the space sector
Within the space sector, digital twins of the Earth are being used to develop a simulation of a system and provide critical insights for tackling global challenges. They can provide a digital representation of the Earth system, spanning scales and domains. Their purpose is to monitor, forecast and assess the Earth system and the consequences of human interventions on Earth. They provide users with the capability to
Digital models can provide an interactive emulation of a real-life system for testing, development and operational analysis.



protection efforts by enabling data-driven decisions, optimising resource allocation and fostering collaboration among diverse stakeholders.
In cybersecurity for space, digital twins are used to create safe, simulated environments for real-time training and testing, as well as emulating functionalities that allows organisations to strengthen their defences without risking operational systems.

Destination Earth
In 2021, the European Commission (EC) launched a flagship programme called Destination Earth (DestinE), which is being delivered through a collaboration between EUMETSAT, ESA and the European Centre for Medium-Range Weather Forecasts (ECMWF). DestinE offers a highly accurate digital twin of the Earth to
The DestinE core platform – the Data Lake – and the first digital twins have been made operational as part of the EC’s Digital Europe Programme. Horizon Europe provides research and innovation opportunities that support the further development of DestinE. There are synergies with other relevant EU entities and programmes, such as the EuroHPC Joint Undertaking and the European Space Programme, as well as related national initiatives.
Earth observation satellites provide a wealth of data for digital twins. Image © ESA





form. User numbers are expected to rise significantly thanks to a set of general-purpose services that enable data visualisation, access and interactive exploration to test ’what if’ scenarios. The first two available digital twins focus on enhancing our understanding and response to climate and weather-related challenges. One supports long-term climate change adaptation through climate simulations, while the other provides detailed forecasts and on-demand simulations of weather-induced extremes.”
Antonio Romeo continues: “As more advanced services are integrated into the Data Lake platform, users will be able to generate more impactful predictions that bring real benefits to society. Take air quality, for example: by combining historical and real-time data with policy information, AI modelling and powerful computing resources, we can better understand both environmental and social impacts. The digital twin enables us to simulate different scenarios, helping us determine whether we’re on the right path.
“Looking to the future, I believe digital twins could play an important role in simulating and supporting broader space missions. For instance, with innovative sensors, having accurate models of both the sensor and the Earth would allow us to virtually test their performance in space and identify potential issues before launch. An accurate model will enable us to simulate what could happen in orbit and how the sensors would work.
Similarly, digital twins could be invaluable for future missions to Mars, allowing key aspects to be simulated on Earth, saving significant time, resources and budget. The potential for digital twins is truly exciting!”
Digital twins in cyber
Within cybersecurity, digital twins provide a different service. They offer a high-fidelity virtual/hybrid replica that can mirror both a system and the processes it supports, from information technology (IT) networks to operating technology (OT) assets, radio frequency (RF) links and mission flows. This offers a comprehensive system and process emulation, enabling the user to replay real-time telemetry, control logic and business workflows to produce a ‘what if’ analysis for training and testing purposes.
In cybersecurity, digital twins are used in three main ways: to train personnel in an ultra-realistic environment; to test systems safely, so failures don’t compromise data or operations; and to emulate functions and behaviours to support research and development and study behaviour in operational contexts.
Simone Urbano, System Simulation Engineer – Security Services at Nexova, is working on a cybersecurity for space (CSS) project utilising digital twin technology. “Digital twins are used in the ‘cybersecurity in space’ domain to increase the resilience of space systems. We
are currently working on a cooperative finance research project in Toulouse, France, to build a simulator of a constellation of CubeSats. The 3-year programme has several streams, and we are involved in the definition of the space system simulation, cyber threat intelligence and verification, and testing work packages.
“We started the project in 2023 and presented an initial simulation demonstration during the CYSAT 2025 conference in Paris. This project’s environment is hosted on Nexova’s Cyber Integration, Test and Evaluation Field (CITEF) platform, where we have uploaded a lot of different attack scenarios. We are
also using open-source software, specifically NASA’s NOS3, which is an operational simulator for SmallSats, and CryptoLib for the encryption layer.
“For the satellite, we are considering using specific data from a CubeSat mission – STF-1 – which was deorbited in February 2024. We aim to simulate all the Consultative Committee for Space Data Systems (CCSDS) standards for space communications, representing all the layers of communications between the ground and the satellite. The only aspect that is not represented is the radio frequency layer, which can be added at a later date.



Testing / R&D

&
Twin
Blue Team
Red Team
White Team
Digital Twin OT & IT
“The CSS project aims to enhance the resilience of space systems against threats from the space environment. Our goal is to develop a simulation for a constellation of CubeSats, through which we can analyse and test potential vulnerabilities. We’re building a library of attack scenarios and designing complex attack simulations to support this work. These efforts allow us to explore and develop innovative mitigation strategies that can be applied to real systems using the same architecture. Examples include a customised on-board intrusion prevention system or a hybrid approach that combines groundbased and space-based data to detect and counter emerging threats.”
Protecting ESA’s systems
Matteo Merialdo, Cybersecurity Principal at Nexova, has been working with ESA on several projects, and directly on ESA’s cyber resilience for the past 4 years.
“We are investigating with ESA how to best use digital twin technologies to enhance cybersecurity. This could be to deploy a replica of a security operations centre [SOC] into a digital twin environment: for example, ESA’s Security Cyber Centre of Excellence [SCCoE] cyber-range is based on Nexova’s CITEF. Real data from the SOC is mirrored into the twin; this type of capability helps to predict the behaviours of the original system. It can enable operators to train, test

new features and systems, and support effective alert handling and threat investigation without affecting live operations.
“This is the one difference between an emulation and a digital twin. In the cybersecurity sense, using an emulation of Windows, Linux or other platforms, you can perfectly emulate a one-to-one scenario. By enhancing this with the original traffic copied and uploaded into the digital twin, the fidelity and representation of the live system is more realistic. The level of emulation can be tailored based on complexity, cost and schedule, demonstrating that the most important features and characteristics can be performed efficiently, while

helping to provide hands-on, real-life testing and training facilities. Our target is to put in place a first proof of concept during 2026.”
Where next?
Federico Antonello comments: ”For ESA, the use of digital twins is expanding beyond operations to support pre-launch phases, providing users with realistic system representations, advanced simulations and predictive insights. In operational contexts, digital twins serve as a valuable tool for mission operators, enhancing situational awareness, validating procedures and supporting decision-making. A digital twin can also be an enabler for embedding AI tools that will leverage quality data and simulation models to provide precise predictions, improving prognostics, health management and assessment of the remaining life of a spacecraft.
“Digital twins strengthen digital continuity by enabling more automated and data-driven workflows. They also contribute to mission planning, testing and troubleshooting by offering high-fidelity virtual models that help reduce risks and improve autonomy.”
For ESA and many other organisations across Europe, digital twins are proving to be essential tools for enhancing cybersecurity compliance. When applied to specific critical processes, they offer efficient testing, validation and training capabilities by replicating real-world conditions. They also play a key role in enabling detailed cybersecurity reviews and supporting conformity assessments across supply chains. As European cybersecurity regulations continue to evolve, these technologies will be increasingly vital in ensuring compliance and resilience.

Civil Security from Space

In the past decade, Europe, along with the rest of the world, has started to face increasing challenges caused by climate change, humanitarian crises, natural disasters, extreme weather events, cybercrime and geopolitical instability. OpenSpace looks at how government organisations and industry are working together using space technology and assets to help support, mitigate and resolve civil security and crisis events.
According to the Global Risks Report 2025 commissioned by the World Economic Forum1, geopolitical unrest, extreme weather events amplified by climate change and continued technological advancements, such as artificial intelligence (AI), are among the top concerns of organisations and society in general. Data and services provided by space systems have a very important role to play in helping to deal with many of the challenges and can also benefit from technological developments.
Protecting the Earth from space
In November 2022, the European Space Agency (ESA) launched its Civil Security from Space (CSS) programme. The aim was to foster the use of spacebased solutions that help save lives and livelihoods and enable organisations involved in civil security to prepare and then act swiftly in the event of humanitarian crises, law enforcement, and safety and emergency events – anytime, anywhere, for the benefit of everyone.
The primary objective of the CSS programme has been to build on and enhance existing and planned

governmental and commercial capabilities to rapidly develop effective solutions, while also fostering long-term innovation. Co-funded by industry, the programme was designed to support the development of commercially viable solutions for the European market, backed by ESA.
“The CSS has been a pioneering programme, paving the way for end-users and industry to foster mutual understanding of how space-enabled services and products can deliver real benefits to users,” explains Hanna-Miina Sihvonen, Head of Civil Security from Space Programme Office at ESA. ”It also helps endusers gain clearer insights into the technologies available on the market and what they can offer. Most importantly, it gives users a platform to convey their needs, share their operational practices and goals, and articulate the problems they’re trying to solve.
”I’ve spent over 20 years working in civil security, and in an ideal world these kinds of solutions should have been in use for crisis responders and first responder organisations yesterday. But with ESA’s CSS programme activities, we have been able to bridge the gap between users and industry.
”CSS has gone beyond simply focusing on the technology – it adopts a user-centric approach and supports comprehensive capacity building within user organisations. You can’t just impose new technology on users; you have to walk alongside them, understand their situation, let them feed back their experiences into the system, and then identify the right organisation capable of turning the project into a viable commercial solution once the project ends.”
The CSS programme has also recognised the importance of delivering interoperable industry solutions that support the creation of a federated system-of-systems. This approach allows for broader industrial participation, enables the development of new use cases, and supports scalable solutions that evolve through continuous improvements and advanced capabilities. Ultimately, this model is expected to drive growth, encourage adoption among
end-users, and promote a diverse and collaborative supply chain of compatible technologies and services.
Building blocks
“There are currently 10 distinct projects under the CSS programme,” Hanna-Miina Sihvonen continues.
“All the projects have contributed to creating novel space-enabled solutions and help to shape future activities, which will focus on establishing space resilience nodes in different countries. These nodes are intended to work together to support first responders. When similar nodes exist across countries, they can be connected and made interoperable through agreed frameworks, enabling seamless collaboration and data sharing.
“The programme focuses on designing and scoping various foundational building blocks that use a wide range of data services, including Earth observation
“ESA’s Civil Security from Space programme focuses on transforming raw data into actionable information.”
The vision for 2035 of ESA’s Civil Security from Space programme is to foster the creation of a unified, secure, resilient, responsive and smart network for civil security actors. Image © ESA
[EO], drones, telecommunications, Internet of Things [IoT] and open data. While these are valuable, they alone are not sufficient for end-users. To truly meet their needs, an additional layer of building blocks is required – ones that can transform raw data into actionable information. This involves deploying advanced AI algorithms to process data from secure data lakes, establishing testbeds for validation, and building onsite capacity to support users in effectively integrating and utilising these services. All this information needs to have a secure and resilient connectivity solution in place to get the information to the responders on the ground via the best connectivity platform available.
“Ultimately, we have different nodes: these are data services, information services, a digital marketplace and the authorities who can receive and process the data in the field in an actionable form. It is also important that users can interact in their own language during any incident.”
A new crisis management platform
As part of the CSS programme, Starion is leading a multinational consortium developing a new service that will provide prompt, up-to-date situational awareness information for crisis and disaster management
organisations. SAFEPLACE will leverage EO, wearable device-based positioning of personnel and assets, IoT data and satellite communications (satcom) services to help overcome challenges caused by poor communications, lack of access to the affected areas, data delays and bottlenecks, and the need to identify key information from raw data.
“SAFEPLACE offers a centralised and secure crisis management platform for relevant disaster management services and products. It will provide near real-time actionable information to an array of different stakeholders – be it for operation centres or first responders who deal with preparedness and crisis management,” says Alex Vorobiev, Programme Manager at Starion.
“What that means is there are a lot of different technologies, services and applications already being developed by experts in their domain. The purpose of SAFEPLACE is to bring these assets together, combining the information to create other value-added products and distribute all the information to downstream users in consolidated and standardised ways through its own portal or via APIs, ready to be integrated into existing crisis management software already utilised in operation rooms around the world. The SAFEPLACE platform not only provides a hub that can share

data with national resilience nodes but can itself be replicated to provide the basis for those national nodes.
“Another great advantage for SAFEPLACE is that it will provide multilingual guidance to crisis managers, using its AI-based large language models [LLM] to interpret user inputs and provide guidance in their preferred languages. This enables fast support for different actors across Europe and helps them make informed decisions in the face of complex emergencies such as wildfires, floods, toxic chemical spills and earthquakes.
”By fusing diverse data into a unified interface, SAFEPLACE will allow first responders and crisis managers to access critical information without the need for technical data expertise. Importantly, it can help keep the first responders, such as emergency services and those on the ground, safe. And, of course, the system must be trustworthy because in an emergency there is no room for error.”
Although there are several commercial satellite constellations that already offer timely EO data, SAFEPLACE goes further by combining this spacebased data with terrestrial data. It will apply AI and advanced data fusion techniques to translate raw data into actionable information. This information can then be delivered directly through existing platforms already used by emergency responders, eliminating the need to learn new systems during a crisis.
Alex Vorobiev adds: “An initial proof of concept was successfully demonstrated in June this year during an event held at ESA’s ESEC [European Space Security and Education Centre] in Redu, Belgium, and the completed platform is scheduled for delivery in 2027. To date, SAFEPLACE includes organisations from Belgium and Spain, and is being extended to Luxembourg, but other countries have expressed interest in becoming involved as well as their emergency services.”
Other regional programmes
Another critical disaster response platform being developed for southern and eastern Mediterranean countries is the Prevention, Preparedness and Response to Natural and Man-Made Disasters in the Mediterranean (PPRD-Med) programme, which offers a collaborative web portal to strengthen resilience in the region. Countries such as Algeria, Egypt, Israel, Jordan, Lebanon, Libya, Mauritania, Morocco, Palestine and Tunisia will benefit from this initiative, which uses publicly available information and offers access to secure data and tools, including educational, training and country-specific content.
PPRD-Med is part of ESA’s Rapid and Resilient Crisis Response (R3) programme. It is funded by the European Union Directorate-General for European Civil Protection and Humanitarian Aid Operations (DG-ECHO) and led by the International Science and Technology Center (ISTC). The platform will provide a broad, publicly available knowledge base about disaster risk management and secure access to educational and training (‘didactic’) information and

tools. Future phases will add operational tools, such as stakeholder and resource mapping, designed for use during crises caused by natural or technological hazards, including technological incidents triggered by natural hazards.
Alex Vorobiev, who also works on this project, comments: “PPRD-Med is a ‘wiki’ type interactive platform that empowers member states with access to essential information and tools. This gives them the information they need to deal with each disaster and make informed decisions. To ensure strict data sovereignty and privacy, the team follows a ‘security by design’ approach, ensuring authentication, confidentiality, integrity and privacy of information.
“Our design places security at its core, featuring local hosting for country modules connected to a central hub and strict access controls to ensure users can only view data they are authorised to access. Each country’s data is stored on segregated nodes secured by robust
access controls. In parallel, the ‘least privilege’ principle is applied to ensure that only authorised personnel can access sensitive data. This overall design and implementation strategy supports compliance with data protection regulations and alignment with local legal requirements in each country.”
Providing disaster-related information in a centralised format and fostering collaboration among participating countries strengthens the entire region. Broader access to information benefits all stakeholders, including through the education and training resources offered by PPRD-Med, as well as valuable insights derived from satellite-based data. Part one of the project has been delivered, with part two expected to be available in October 2025.
Addressing RF spectrum vulnerabilities
As the rollout of 5G networks accelerates across Europe, the radio frequency (RF) spectrum is now



emerging as a critical area of vulnerability. The rapid growth of the telecommunications market has outpaced the development of tools needed to effectively monitor and manage the RF spectrum used by next-generation networks. At the same time, 5G-based services are increasingly becoming a core element of civil security programmes, providing the means to share essential data and information, while their unauthorised use could indicate potential sources of conflict or areas for concern, both on land and at sea. Recognising this gap, there is a growing consensus for the need for an independent European system dedicated to RF spectrum oversight.
In response to this challenge, Starion is leading an innovative project to launch an in-orbit demonstrator for a European RF Spectrum Monitoring Service (ESMS) as part of ESA’s Space Systems for Safety and Security (4S) programme, which in turn is part of ESA’s Advanced Research in Telecommunications Systems (ARTES) framework. The project is 75% funded by the Belgian Science Policy Office (Belspo) and 25% funded by Starion. Initially, ESMS will launch a demonstrator

mission that will lay the groundwork for a robust, sovereign capability that will enhance spectrum security and support the safe deployment of 5G and future 6G networks across Europe.
ESMS will provide a fully integrated end-to-end solution, combining space- and ground-based products to enable continuous space-based monitoring of the wireless spectrum environment on land, sea and air. While not limited to 5G, it will specifically offer insights into the deployment of 5G and 6G networks throughout Europe. Once proven, it will offer a commercial service to telecom operators, military organisations, regulatory bodies and European institutions, as well as to governmental and commercial stakeholders.
Testing new technologies
The ESMS consortium brings a wealth of innovative technologies. Aerospacelab, a leading satellite manufacturer in Belgium, will build and operate the spacecraft – a SmallSat measuring 100 x 60 x 60cm based on its Versatile Satellite Platform (VSP).

Together, Starion and Aerospacelab are co-developing the satellite’s payload. The VSP will be adapted to incorporate and test ArianeGroup’s innovative water propulsion system.
Recently, another Belgian company, Edge X, has joined the programme, bringing new AI capabilities that will allow operators to pre-process the data on the satellite itself, rather than on the ground. This provides the opportunity to remove ‘garbage’ data on the satellite, reducing the amount being sent back down to the ground station.
Luis Rodriguez, Space Missions Project Manager at Starion, says: “In a nutshell, ESMS will be monitoring radio frequency bands from 160 megahertz up to 24 gigahertz. We are all familiar with 4G and 5G, but as we make our way up to 20 or even 24 gigahertz, we can open the door for a broader range of use cases.
“In a security context, the system could be used to monitor remote areas, such as dense jungles, polar regions or open oceans, where no legitimate signals are expected. ESMS can detect unauthorised or ‘rogue’ signals, determine if they are moving, track their trajectory and monitor them from space. This capability supports the regulated use of the RF spectrum by supplying data to authorised stakeholders, helping to detect and respond to illegal or unauthorised activities. Ultimately, ESMS aims to equip Europe with the technological foundation and intelligence needed to progress toward a future space-based spectrum monitoring constellation and a viable, long-term operational solution.”
5G-based services are increasingly becoming a core element of civil security programmes
Where next?
ESA’s Hanna-Miina Sihvonen concludes: “ESA is undertaking the fundamental groundwork by bringing industry and the user community together, while breaking down barriers between military and civil activities and fostering international collaboration. There are many governance models and barriers between different authority organisations and we’re working to bridge these gaps – delivering information and services that can be adapted to fit the specific structures of each country.
“By taking a user-driven approach and actively engaging mandated public protection and disaster relief organisations, we are placing a strong emphasis on standardisation and interoperability. This will be key to enabling effective pooling and sharing of resources.”
In the future, the hope is that there will be a catalysed deeper cooperation across countries and authorities, allowing organisations to work more closely together to respond to a broad range of civil security-related requirements. Ultimately, the goal is not only to support disaster response efforts on the ground, but also to strengthen early warning and prediction capabilities, reducing the number of people affected by future crises.

Spain is currently the fifth largest contributor to ESA, providing €300 million per year



SpainSat Next Generation satellite. Satellite image © ESA

The Evolution of the Spanish Space Sector

Spain joined the European space effort at the beginning of the space era, around 1957, when the first man-made satellite, Sputnik, was placed in orbit.1 Since then, much has changed, particularly with the creation of a national space agency in 2023. OpenSpace speaks to Juan Carlos Cortés Pulido, Director of the Agencia Espacial Española (AEE – the Spanish Space Agency) to find out what the newly-formed agency has planned for Spain’s future space business.
The early years of Spain’s space activities were mainly supported by the efforts of a few government departments and a handful of private investors. It wasn’t until 1988 that substantial financial support was granted by the Spanish Government. Since then, support has been maintained at a level unprecedented in Spain for any R&D activity.
In the beginning, Spain worked with NASA and the European Space Research Organisation (ESRO), which was later merged with the European Launcher Development Organisation (ELDO) to become the European Space Agency (ESA). The country played a crucial role in collaboration with NASA for the US Moon missions under the Apollo programme and subsequent crewed missions. The two ground stations it established provided vital ground tracking and communication support for manned flights that took place between 1967 and 1985.
The first Spanish satellite, Intasat, was developed by the National Institute of Aerospace Technology (INTA) and launched into orbit in 1974. Since then, Spain has been involved in the launch of more than

20 satellites, some with international collaboration, for telecommunications, Earth observation (EO) and communications. This development has been accompanied by the establishment of key European institutions such as SATCEN to support the European Union’s (EU’s) Common Foreign and Security Policy by providing geospatial intelligence derived from space assets.
Working with ESA
Spain was one of 10 ESA Member States that were the initial signatories of the ESA Founding Convention in 1975. It is currently the fifth largest contributor to ESA, providing €300 million per year (5.9% of the total Member State contributions) at the last Ministerial. 2
Spain is home to ESA’s European Space Astronomy Centre (ESAC), located near Madrid. This is the primary ESA hub for operating planetary and astronomy missions, with scientists in the areas of astronomy, planetary science, astrophysics and solar science. The archives for most of ESA’s astronomy, planetary science and heliophysics missions are developed and maintained at ESAC by the ESAC Science Data Centre

(ESDC) in coordination with the science operations centres, instrument teams and consortia of the various missions.
ESA has established several Business Incubation Centres (ESA BICs) in Spain to support space-related startups in different regions. These centres aim to foster innovation by providing entrepreneurs with resources, mentorship and access to space industry networks.
Spain is also part of the Deep Space Network of NASA and ESA, via ground stations at Robledo de Chavela and Cebreros.
Leading activities
Over the past 20 years, the Spanish space industry has progressed from a secondary role in the value chain to a leadership position in high-tech, value-added subsystems and the development and integration of instruments, platforms, satellite ground segments and complete systems.
Spain has been a leader in many significant activities3 as part of missions and programmes including AmerHis, SMOS, SmallGEO, Proba-3, CHEOPS, MetopSG ICI instrument, Sentinel-3, Smile and the Galileo Ground Control Segment. Others include the European GNSS (global navigation satellite system) Evolution Programme and EGNOS, the SouthPAN System, low Earth orbit positioning, navigation and timing
(LEO-PNT), quantum key distribution (QKD), DRACO, space surveillance and tracking (SST) and civil security from space (CSS).
In 2019, ESA renewed its focus on the Canary Islands for laser space operations, thanks to the winning combination of high altitudes and clear skies, which make it one of the world’s best locations for astronomy4 and SST telescopes. Building on these conditions, in 2022 the Caramuel project was started to provide the first QKD system implementation from geostationary orbit.5
2020 saw the first Spanish-led EU mission, Copernicus Land Surface Temperature Monitoring (LSTM), which provides long-duration daytime and nighttime land surface temperature measurements globally.
In 2022, work started on ARRAKIHS, which became the first mission from ESA’s Science Programme to be coordinated by Spain, studying dark matter.6 In addition, two new Spanish astronauts became part of ESA’s astronaut corps. The following year, Miura made history as the first European private rocket to reach space. This instigated further planned launches: Miura 1, Miura 5 and Miura Next.
SpainSat Next Generation (NG) is considered the most ambitious space programme carried out by Spain so far. With one satellite launched successfully in January 2025 and another due for launch by end of October,
Cebreros deep space ground station. Image © Cebreros

SpainSat NG will provide more cost-effective, adaptable and secure communications services to governments and emergency response teams in Europe, North and South America, Africa, the Middle East and Singapore.7
A new impulse
Within the space sector, Spain’s focus has expanded from launchers and scientific development to satellites, paying attention to the need for telecommunications for institutions and civilians. TEDAE (Spain’s Association of Defense, Aeronautical and Space Technologies) estimates that total sales in the Spanish space sector were around €1.01 billion in 2022 and €1.13 billion in 2023. 8
In December 2020, the Spanish Government created a strategic project for Economic Recovery and Transformation (PERTE) aligned to the aerospace industry, which was supported by the European Recovery and Resilience Funding; €4.5 billion was allocated from 2021 to 2025, split between public (~€2.2 billion) and private (~€2.3 billion) investment. The objective was to position the aerospace industry as a key player in the face of the new challenges and opportunities associated with the major transformations planned at national and international levels, including the creation of the Spanish Space Agency. In addition to large multinationals, the plan was to attract many emerging New Space companies specialising in aerospace technologies to get onboard.
SpainSat NG-I satellite launch. Image © SpaceX
Spanish Satellites

2018
EO and reconnaissance satellite 2014
Deimos-2
Remote sensing EO satellite
2013
Spanish low-cost technology demonstrator

2013
HumSat-D
Spanish demonstrator for educational training
2009
Deimos EO satellite
First Spanish satellite
1992-2018
Hispasat IA, IB, IC, AG1 & 30W-6
First communications satellites operated by a Spanish company
1995
UPM-Sat 1
Microsats for Spanish educational, scientific and technology purposes
2022
Urdaneta-Armsat
Spanish-American research nanosats

2013
Amazonas 3
Communications satellite
2004-2009
Nanosat 01 & 1B
Communications satellites
2025
Startical IOD-1 and -2
To explore instant communications between air traffic controllers and aircraft
2025
SpainSat
Telecommunications satellite
2014
Amazonas 4A
Commercial communications satellite (also known as Hispasat 74W-1)

2017
Amazonas 5
Commercial communications satellite
2005
XTAR-EUR
Communications satellite developed by Spain and US for secure comms over India
1995
Helios 1A & 1B
French military satellite with Spanish and Italian participation
Agencia Espacial Española (AEE) was inaugurated in Seville in 2023. The AEE has a dual mission: to coordinate national space activities and Spanish participation in international programmes. The Agency is establishing collaborations between all the ministerial departments with competences in the field of space. OpenSpace spoke to Juan Carlos Cortés Pulido, Director of AEE, to find out more.
What are the main objectives of AEE? And how is it structured?
The primary mission of AEE is to coordinate and integrate all space-related activities across Spain. Before its establishment, 17 different ministries were involved in the space sector, with overlapping responsibilities ranging from policy and management to industry and user engagement. This fragmentation made it necessary to create a unified structure. Today, the AEE leads national efforts in space industrial and scientific policy, bringing together industry, researchers, scientists, technology centres, academia and endusers under a comprehensive, integrated framework.
The founding of the AEE has driven a new era for Spain’s space sector, enabling us to maximise the return on institutional investments in space. In addition to programmatic divisions focused on science, industry and user engagement, the Agency also includes a dedicated Security Directorate, headed by an Air Force General, and a unique Office for Space and Society. This outreach division is tasked with raising public awareness of the role space plays in
daily life. For instance, the average person relies on more than 100 satellites each day – demonstrating just how critical space technologies are to modern society.
Overall, the Agency is responsible for 29 areas of expertise and 15 clearly defined functions, all united by a single overarching goal: to enhance the wellbeing of citizens through space. Every initiative we undertake is driven by this purpose. The AEE also holds three strategic mandates: to develop a national Spanish space policy; to design and implement a long-term space strategy; and to draft a comprehensive space law. To date, we have launched over €580 million in programmes spanning a range of technologies and applications, and we have already surpassed 100% of our initial staffing goals.
What is AEE’s position on synergies between defence and civil programmes?
The AEE operates under the oversight of the Ministry of Science and the Ministry of Defence, meaning we report to both. It’s increasingly clear that space has a dualpurpose role, serving both civilian and OpenSpace
defence interests. When the Agency was established in 2023, it was decided that a dual structure was necessary. Given today’s geopolitical climate, that decision has proven to be the right one.
Within the AEE, we manage a wide range of activities, both civil and military. We oversee programmes and applications across technologies, operations and launches, with security playing a crucial role. A business study published a few months ago revealed that 2 to 3 years ago, the main concern for society was sustainability; today, security has become the primary concern and focus. This report reinforces our activities for dual activities, but this is not new. During the Agency’s creation, I was working on a space debris proposal with the Ministry of Defence where we were leading the technological heart of the programme.
Looking to the future, dual activities will be more evident. We will be working with the Ministry of Defence on programmes such as secure communications with quantum key distribution and will be reinforcing our space debris infrastructure.
We are also working on launching different initiatives, including satellite constellations to provide our armed forces with the information they need to carry out their policies. We are also working with organisations in Spain, especially in the regions, and have launched some committees where the regions can express their opinions. We are coordinating activities in different provinces to maximise the benefits of our investments.
How does AEE work with other national space agencies in Europe?
Cooperation is in our DNA. The AEE was founded by consolidating responsibilities, staff and budgets from various ministries, making cooperation an intrinsic part of our identity. Collaboration remains essential to achieving our strategic priorities. For this
reason, we have created a dedicated Directorate for International Relations.
Globally, we’re observing a shift in space cooperation from multilateral frameworks to more multipolar dynamics. Since the invasion of Ukraine, this trend has become even more evident, with the focus of multipolar cooperation largely centred around the USA and China. In response, we are operating along two strategic axes. First, we are strengthening our partnerships with key European institutions such as ESA, the European Union Agency for the Space Programme (EUSPA) and EUMETSAT through the Agencia Estatal de Meteorología (AEMET), a state agency of the Government of Spain responsible for providing weather forecasts. Secondly, we are expanding our bilateral initiatives. Recently, we’ve signed new agreements with countries including Italy, Colombia, Turkey, Greece and Mexico, and we plan to continue pursuing such partnerships.

A notable example of bilateral cooperation is the Atlantic Constellation, a joint initiative with Portugal. This constellation currently includes eight satellites from each country, with the concept of an open constellation that enables shared data to reduce revisit times. It represents a significant step forward and we aim to continue strengthening similar collaborative efforts.
Our long-term goal is to establish a national satellite constellation providing different services and applications aimed at reducing revisit times. However, across all our efforts, cooperation and collaboration remain at the heart of what we do.
How are AEE’s relationships with space agencies beyond Europe?
In the same spirit, international collaboration is a cornerstone of AEE’s mission. We already have a cooperation agreement in place with NASA: for instance, all of the rovers in its Mars exploration programme contain Spanish technology. We are actively participating in the Mars exploration effort and
are eager to expand our involvement in future lunar and deep space missions.
Spain has also built a strong relationship with the China National Space Administration (CNSA), a major global player in the space sector. Through an ESA framework, we are already collaborating on the Smile mission9, and we aim to deepen this cooperation further.
Are there any collaborations with other agencies?
Interestingly, we are observing a new trend: the emergence of multilateral space organisations in various regions. In Latin America, for example, the Latin American and Caribbean Space Agency (ALCE) has recently been established. We are committed to becoming one of its founding members, recognising the strategic importance of this partnership for Spain.

Similarly, the creation of the African Space Agency marks a significant development. Fostering cooperation with our African partners in the space sector is a top priority for us.
What are Spain’s priorities and budgetary expectations for the ESA Ministerial meeting in November?
Within Europe, Spain is the fifth largest contributor to ESA. I do not have a crystal ball, but this is the first Ministerial Meeting where the AEE is taking part, and
Teide Observatory, Tenerife, Canary Islands. Image © IQOQI Vienna, Austrian Academy of Sciences
we hope this will entail a change in our contribution. Over the years, our Government has increased its investment and participation by 50%. Our ambition in this Ministerial is to reinforce our commitment, because ESA has been instrumental in the development of the Spanish space sector. We have already been in discussions with ESA relating to our potential investment, but everything needs to be approved by the Council of Ministers. We hope to have our final proposal by the end of October, and it is our priority is to reinforce our commitment to ESA.
It is important to note that the AEE is a management agency. We are more than 100 people developing the conditions to make the Spanish space sector grow. The execution of our programmes is done through industry, by scientists and by technology centres. We manage the programmes and sometimes we rely on ESA to execute some of our national programmes through third-party agreements; this is important for us.
We are advancing in the definition and consolidation of our priorities, and we want to a launch powerful technology programme dealing with critical technologies such as quantum key distribution and artificial intelligence.
domain of small launchers and, in particular, we want to look at the European launcher challenge. We are also focused on applications; for instance, we are interested in EO programmes and we are the leaders in low Earth orbit PNT, an initiative being led by a Spanish company. We want to launch an Atlantic Constellation Plus programme that will complement the Atlantic Constellation satellites – two EO satellites, each with a high resolution infrared optical system. We aim to build


Other important areas for us include space transportation. We want to reinforce our role in the
situational awareness (SSA). We are interested in launching secure telecoms initiatives, reinforcing intersatellite communications and laser communications. And we want to be the first country to launch an active space debris removal to make a testbed for the re-entry of space debris. We are also working with
AEE and ESA collaborate on satellite removal in-orbit demonstrator: CApTure Payload Bay (CAT). Image © ESA
programmes looking at space sustainability. The more satellites that are launched, the more vulnerable space becomes. The situation with space weather and solar storms has been very prominent in recent years and we want to launch a space weather operational system to reinforce our SSA programme and space sustainability.
We need to protect space for generations to come and in that respect space law is also important. The current laws date back to 1967, so we need a new global law for everyone to work towards to protect the space domain for the future. We currently have over 14,000 satellites operational in orbit10, but with the explosion in the number of planned launches, this is expected to exceed 100,000 satellites by 2030! We are interested in the life cycle assessment of all space activities, and we need punishment measures globally for those who do not abide by these rules.
What investment initiatives is the Government implementing to support the growth of Spain’s space sector?
We need to actively engage venture capital companies to help scale up our national space sector. Beyond providing grants to start-ups, it’s essential to develop mechanisms for direct capital investment in companies, potentially through innovative financial instruments. Across Europe, we are observing consolidation efforts within the industrial sector, where companies are joining forces to enhance competitiveness. This is a strategic move. When comparing European and US companies, a significant difference in scale becomes evident, and collaboration is key to bridging that gap.
In Spain, we have already launched five space incubators that have supported approximately 120 companies developing advanced technologies. Notably, 80% of these firms are now consistently collaborating with the Agency. We are committed to expanding this effort, with plans to establish three additional incubators in the coming months.
Our overarching goal is to ensure that Spain has the capabilities and industrial base required to contribute meaningfully to future space programmes. We also aim to foster regional development, creating jobs and building technological expertise across the country.
Spain is home to many high-tech companies with world-class capabilities: this strength enables us to play a critical role in European and international space initiatives. Ultimately, the wellbeing and prosperity of our country will increasingly be supported by the benefits of space technology.
What advice would you give to
European companies with Spanish brands aiming to build relationships with national space agencies?
European companies for us are domestic companies. We make no differentiator where companies in Spain are part of an international group. All our activities are run by competition and we award each contract on the basis of merit. We don’t mind if its 100% Spanish or European.
In some countries it is far easier for start-ups to set up a company as their procedures are much simpler. We need to learn from these countries, especially if we want to expand further and build on our space technology capabilities.
Where do you see the Spanish space sector in the next 5 to 10 years?
We are already experiencing growth in both turnover and capabilities, and our focus now is on expanding and strengthening the entire space value chain. This requires agility, making strategic decisions in real time, often with incomplete information. Despite these challenges, we are advancing several key programmes with clear objectives.
One of our priorities is the development of EO constellations. A current focus in this area is improving

‘revisit time to zero‘ and we aim to take an active role in such constellations. We are targeting missions with budgets of several million euros and satellite platforms in the 250-300kg range. In parallel, we are also committed to expanding Spain’s capabilities in launch systems and technologies.
While we work to meet the technical requirements of these programmes, we are equally committed to addressing the broader needs of our institutions and society. It is critical that space becomes more integrated into our national mindset. To support this, we have established a User and Applications Directorate within the Agency, tasked with identifying and addressing user needs through space-based solutions.
One example of this is our collaboration with the Ministry of Infrastructure, which is seeking to modernise and streamline space-based traffic management systems. To meet this need, we launched Startical – a programme involving a constellation of 300 satellites designed to provide air traffic management data.
Our broader vision is to apply space solutions across other key societal sectors, such as water management, pollution monitoring, energy and fisheries. We are looking to replicate the UK’s Catapult programme, an initiative that was set up to help organisations use space technologies and data in their activities and programmes as well as to support start-ups.
On the international front, we aim to deepen our relationships with global space actors. Whether through multilateral cooperation or bilateral partnerships, we are committed to reinforcing Spain’s role on the world stage and contributing meaningfully to the global space community.
What inspired you to lead AEE? And what legacy would you like to leave behind?
For me, I am honoured to be the first Director of the Agency. In this role, my main challenge is to fulfil the expectations of the space sector. We are a mature sector with many programmes and we are the leader of many initiatives. We also have a responsibility to capitalise on all the Spanish experience in space from the past 60 years to reinforce and develop the sector.
I have a mandate of 5 years plus 2, and my goal in that time is to significantly strengthen the Spanish space sector: doubling or even tripling its turnover. I want to position us to play a leading role in international initiatives and, where appropriate, to lead major global space programmes. The AEE is not just shaping Spain’s future in space but also ensuring that space delivers tangible benefits for every citizen. We are putting the boundary conditions for a smooth transition from current space activities to future commercial markets.
I often think of my 16-year-old son and what the space sector means for his generation. It’s essential that the next generation understands the importance of space activities and the vast potential they hold. Space innovation is driven by people. That’s why we must ensure that everyone is aware of the opportunities the space sector can offer, especially young people. Inspiring them today is how we build the future of space.
Sources: See page 86
IOD-1 in orbit around Earth showing the 3 metre VHF antenna. Image © Startical

Wars are no longer solely kinetic – they are hybrid
The Strategic Role of Cybersecurity in Modern Defence


The international security landscape has undergone a profound transformation, with implications for contemporary military conflict and the core role of cybersecurity systems in defence. OpenSpace spoke to Roberto Mazzolin, Cyber, Space, Defence and Security Technology Strategist for Starion and Nexova and Retired Brigadier General from the Canadian Armed Forces, to understand how and why nations must adapt their strategic, operational and technological approaches to maintain security and sovereignty.
Historically, wars were predominantly kinetic, with armed forces battling over land, sea and air domains to secure geographic advantages. Although ideological conflicts, such as communism versus free liberal societies, shaped alignments and motivations, the central considerations often boiled down to controlling territory or protecting economic lifelines. Fast forward to today and these drivers have become more complicated, with multiple dimensions and challenges.
Economic influence and access to natural resources are now as critical to international strategic competition as military superiority. For decades, a rules-based international economic order resulted in a relatively stable global system that promoted free trade and cooperation. Now, though, we’re starting to see a move towards a multipolar international environment –one with many important global powers, not just a few superpowers – which is intensifying regional tensions.
In this new environment, outright kinetic conflict between major powers is less desirable, because it can
backfire significantly due to how intertwined the global economy is. For instance, crippling a rival nation’s infrastructure can inadvertently damage the attacker’s own economy through disrupted supply chains, energy markets or technological interdependencies. This forces countries to seek alternative means to project power, assert influence and achieve strategic objectives without triggering full-scale war. Wars are no longer solely kinetic – they are hybrid.
Protecting critical infrastructures
One vital element that epitomises the complexity of contemporary security is the dependence of modern societies on interconnected critical infrastructures. Finance, agriculture, healthcare, telecommunications, energy and transportation all rely heavily on digital networks and space-based systems for effective operation. These systems form the backbone of a functioning society and, by extension, underpin the authority of national governments.

If critical infrastructures fail or are compromised, public confidence in government erodes rapidly. Populations expect continuous, reliable services, so any very significant disruptions can cause economic loss, political instability and panic. Twenty-first century national security therefore increasingly revolves around the ability to protect such critical infrastructures – both physically and digitally.
In recent years, space and cyber have each been defined as operational domains from a military context, alongside the traditional domains of air, land and sea. NATO explicitly acknowledges cyberspace and outer space as such, declaring cyberspace and space to be operational domains in 2016 and 2019 respectively.1,2 Many nations now have dedicated commands responsible for operations in these areas.
For NATO, cyber defence is central to its overall deterrence and defence posture. Its aim is to both
protect its own networks and help allied nations to enhance their own national resilience and use cyber as an operational domain. To this end, it has made continuing efforts to coherently engage industry and external partners.
Cyber is so fundamental that NATO holds an annual conference for member states and selected partners centred on the Cyber Defence Pledge. 3 This Pledge was implemented in 2016 and then enhanced in 2023 with ambitious new goals to strengthen national cyber defences, including critical infrastructures.4 In addition, recent policy guidance has resulted in the development of a NATO Commercial Space Strategy, published in June 2025, that seeks to strengthen the Alliance’s relationship with industry players.5
Meanwhile, the European Union’s (EU’s) main framework is the EU Cyber Defence Policy, which was adopted in 2014 and updated in 2018. Specific
conclusions were adopted in 2023 that stressed the need for both the EU and individual Member States to further strengthen their resilience to cyber threats and enhance their cybersecurity and defence.6 As part of related activities, the EU has in recent years introduced several Acts and Directives focused on the cybersecurity of products and organisations, in a bid to raise the overall cyber resilience and security of Europe.
The EU takes another tack with the Cyber Diplomacy Toolbox7, a joint EU diplomatic response to malicious cyber activities within the Common Foreign and Security Policy. The aim is to help prevent conflicts, mitigate cybersecurity threats and promote greater stability in international relations, including by influencing the behaviour of potential aggressors. Building on this, in June 2025, the EU adopted the EU blueprint for cyber crisis management, which gives guidance for the EU’s response to large-scale cybersecurity incidents or cyber crises.8
Cyber and space as strategic domains
The internet and satellite-based systems provide fundamental tactical capabilities: telecommunications, positioning, navigation and timing (PNT), and Earth observation (EO). There is virtually no critical infrastructure untouched by these networks and technologies. Consequently, any state actor seeking to influence, coerce or degrade a rival nation’s capabilities is increasingly likely to focus on the cyber and space domains. These domains provide more subtle, scalable and reversible means to exert influence compared with traditional kinetic attacks, which often cause irreversible infrastructural damage requiring costly reconstruction efforts.
It is no surprise, then, that the past decade has witnessed a shift whereby both cyber and space have been elevated to the same strategic level as conventional domains. This evolution has been driven
by multiple factors in modern conflict, including recognition of the electromagnetic spectrum as vital to command and control, situational awareness and the ability to deploy forces beyond national borders. Russia and China exemplify this long-standing strategic emphasis on dominance in the electromagnetic domain. Both nations view control of cyber and electronic warfare as central to their broader military and geopolitical objectives. Their tactics range from cyber espionage and sabotage to misinformation campaigns designed to sow discord and weaken adversaries internally.
Misinformation and propaganda are not new phenomena. In the Cold War, radio broadcasts such as Radio Moscow, Radio Free Europe and Radio China International were used to influence foreign populations. Today, these approaches have migrated to the internet and social media, magnifying their reach and impact with alarming efficiency. Cyberattacks targeting energy providers, financial systems or health services can have tangible effects on the civilians’ hearts and minds, creating internal pressures that affect political stability and government decisionmaking.
As such, cyber and space domains serve as critical tools during times of both peace and conflict. They enable calibrated, remediable effects that can be deployed strategically prior to or alongside kinetic military operations. When you have that continuum from peace through crisis to high-intensity conflict, cyber warfare becomes an attractive, cost-effective method of achieving national objectives without crossing thresholds that typically demand full military mobilisation. Cyber, along with space, is now likely to be the first domain attacked in any conflict.
The modern battlefield
Military operations have been transformed by digital technologies and space-based systems.

Communication no longer depends solely on radios and wired telephony. Instead, wireless networks, satellite communications and real-time digital command and control systems now dominate.
Brigadier General (Retired) Roberto Mazzolin, Cyber, Space, Defence and Security Technology Strategist for Starion and Nexova, observes: “When I began my armed forces career, we used acetate-covered paper maps and grease pencils. Since then, battlefield visualisation has evolved dramatically, now featuring high resolution, computer-generated graphics representing operational scenarios in real time. Weapon systems have integrated precision guidance capabilities including GPS-guided munitions, drones and autonomous platforms that explicitly rely on uninterrupted connectivity and accurate positioning.
“However, this dependence introduces vulnerabilities. Electronic warfare, including jamming and spoofing, seeks to block armed forces’ access to the electromagnetic spectrum. Current conflict zones, such as Ukraine, and strategic flashpoints like the Baltic

States and the South China Sea vividly demonstrate the intensity of electromagnetic and cyber contestation.
“Nations invest heavily in disrupting adversary networks while protecting their own. The terrain of these operations extends beyond physical geographies into radio frequencies, satellite links, undersea fibre-optic cables, cellular towers, microwave relays and fixed wirelines, all interconnected in a complex civilian–military infrastructure matrix.
“This networked ecosystem is predominantly dual use. Because civilian infrastructures support military installations, and vice versa, the stakes are amplified. For example, disabling a civilian electrical grid might degrade military readiness, while a cyber breach of defence communication systems could expose sensitive intelligence.”
Cyber commands
In recent decades, armed forces have increasingly established dedicated cyber units, often referred to as ‘cyber commands’. This trend reflects the expansion of

operational domains into cyberspace and the growing need to strengthen the cyber defence of military networks and systems to ensure their continuous operational availability, as highlighted in the ‘White Paper for European Defence – Readiness 2030’ published in March by the European Commission.9
These cyber commands are tasked with conceiving, planning and conducting military operations in cyberspace. To achieve these objectives, they are equipped with substantial capabilities for monitoring IT/OT networks and incident response, including security operations centres (SOCs), enabling them to react immediately in case of an intrusion or attack.
NATO’s Integrated Cyber Defence Centre, for example, is designed to enhance network protection, situational awareness and the implementation of cyberspace as an operational domain throughout peace time as well as during times of crisis and conflict.
Cyber commands place a strong emphasis on training and preparedness using cyber-ranges. These dedicated simulation environments, known as digital twins,

allow military cyber operators to practice defending complex, realistic network architectures against sophisticated adversary scenarios. By replicating both friendly and hostile cyber infrastructures, cyberranges provide a safe yet highly realistic environment for testing defensive tactics, refining offensive cyber capabilities and conducting large-scale joint exercises.
Some cyber commands will already have a complete set of cybersecurity facilities, including both SOCs and cyber-ranges. Others may utilise managed services, such as those provided by Nexova’s Cybersecurity Centre of Excellence, to address one or more requirements, as either their primary solution or an additional layer of cybersecurity.
Quantum and AI
Looking ahead, quantum computing and artificial intelligence (AI) are set to radically shape the future cybersecurity landscape.
Quantum computing threatens to undermine current cryptographic systems, potentially exposing
communications and data previously considered secure. Adversaries capable of harnessing quantum decryption could gain strategic advantages unimaginable just a few years ago. This potential has catalysed global efforts to develop and deploy quantum-resistant cryptographic algorithms and secure communication protocols before this quantum advantage becomes a reality.
Meanwhile, AI is increasingly embedded into the fabric of military decision-making systems, supporting operational analysis, threat detection, pattern recognition and autonomous weapons systems. In cyber defence, AI has become essential. The volume and complexity of network traffic make it impossible for human analysts alone to detect and respond to adversarial actions swiftly. Instead, AI is being used to look at network activity to recognise suspicious behaviour, identify adversaries, attribute the activities and propose counter actions in near real-time.
In April 2025, NATO published a version of its first Data Strategy, with the aim of accelerating integration and interoperability across all of its operational domains.10 The Strategy includes the creation of a secure data sharing ecosystem that will allow access and collaboration by member states, industry and academia, including on AI models, while ensuring that nations retain control of their own data.
However, there are challenges when using AI. Probability-based identification means there are always risks of false positives or negatives. Human oversight is therefore crucial to provide context within strategic objectives, avoid escalatory missteps and ensure cyber operations are aligned with national interests and ethical standards.
Strategic integration of cyber
Cyber operations do not function in isolation. Instead, they must be integrated seamlessly with other warfare
activities. Roberto Mazzolin comments: “Offensive cyber operations can disrupt enemy command and control, degrade situational awareness or kill logistics flows, amplifying the effectiveness of kinetic strikes or diplomacy. Meanwhile, defensive cyber operations ensure the continuity and resilience of one’s own infrastructure and communications. The interplay between offensive and defensive cyber activities often forms a silent but decisive battlefield where establishment or denial of cyber presence can alter the entire conflict’s trajectory.”
Given the sophistication of adversary cyber capabilities, such as those of China, Russia, Iran and North Korea, cyber warfare requires meticulous planning. National actors must consider operational risks, geopolitical consequences and financial costs before launching cyber operations.
Neutralising a target with a few lines of malicious code may be far cheaper than a multi-million-dollar missile strike, but the risks of escalation or counterattack remain formidable.
Cyberattacks and resilience
When looking at the nature of potential armed conflict, it’s not a question of ‘if’ a cyberattack will happen, but ‘when’.
The 2020 SolarWinds cyberattack, which compromised US Government networks and critical infrastructures, highlights the scale and complexity of modern cyber threats.
Building resilience demands that nations marshal their full military, industrial and civilian capabilities. Companies play an indispensable role, especially those operating critical infrastructure nodes. This dual-use nature of infrastructure demands close cooperation between governments and the private sector.

Unfortunately, many companies, particularly in free-market economies, remain reluctant or slow to invest sufficiently in cybersecurity. Roberto Mazzolin observes: “Even with regulations such as the EU’s NIS2 [European Union’s Network and Information Security Directive 2], some business leaders view cybersecurity
as a cost rather than an essential enabler of business continuity. The danger is that without protecting a company’s individual infrastructure, disengaged businesses remain ripe for attack or penetration by adversaries who are keen and quick to exploit.”
To address this, there is growing emphasis on forming collaborative mechanisms such as information sharing and analysis centres (ISACs) that enable governments and industry to share actionable intelligence to improve sector-specific cybersecurity. These efforts extend into awareness, education, professional development and training programmes. Roberto Mazzolin says: “Collectively, public agencies, industry leaders and specialist firms must cultivate a cybersecurity culture that prioritises resilience as a shared responsibility.”
Navigating the complex security landscape
The ever-evolving international security environment is compelling nations to rethink traditional assumptions about war, peace and power. Economic imperatives and technological interdependencies are creating new vulnerabilities and opportunities. Within this context, cybersecurity and space-based systems have become indispensable arenas of strategic competition and military conflict.
Roberto Mazzolin summarises: “Success in this nuanced environment depends on comprehensive strategies that fuse technological innovation, resilient infrastructures, joint military capabilities and cooperative partnerships. Nations must invest not only in capabilities, but also in leadership awareness and organisational culture to mitigate the complex risks of today’s cybersecurity landscape.
“Cybersecurity is now far more than a technical domain; it is a cornerstone of national and international security, sovereignty and survival.”

Image © Belgian Ministry of Defence
Strengthening Cyber Defence Through Exercise

As cyber operations increasingly rival traditional warfare in strategic importance, nations are investing heavily in both offensive and defensive cyber capabilities. From cutting-edge technologies to specialist training, preparation is vital, with rigorous practice being an essential key to readiness, just as it is on the physical battlefield. OpenSpace peers into the world of national and international cyber warfare exercises to find out who wins.
It might surprise you to learn that for a few days in May 2025, people from 41 nations were engaged in a shortlived war. The reason most people across the world were oblivious to the intense activities underway was because this occurred not out in the open in towns and cities but online, away from the media spotlight.
The ‘war’ in question was Locked Shields 2025, a cyber defence exercise organised by the NATO Cooperative Cyber Defence Centre of Excellence. This annual event is just one of many that take place at national and international levels to enable managers and practitioners to test their cybersecurity-related skills – and learn from each other – at both strategic and detailed levels.
Cyber warfare is now an established part of international military aggression: for example, one hour before Russia launched its invasion of Ukraine, a cyberattack took place against satellite operator Viasat. This was later assessed to have been launched by the invading country with the likely intent of
disrupting Ukraine’s command and control during the invasion.1 Other cyberattacks attributed to state actors occur outside formally recognised conflicts but are still essentially warfare. The Center for Strategic & International Studies in the US lists numerous examples of incidents designed to gain access to military intelligence, steal other forms of data, spread misinformation or strategically sabotage critical services.
2
The breadth of types of attack is why cyber exercises are so varied. In addition, the Viasat attack emphasises the fact that it’s not enough simply to consider protecting ground-based computer systems: space now plays a vital role in defence too.
“The formal declaration of cyber and space as operational domains has stepped up the importance and accelerated the emphasis on conducting cyber exercises,” explains Roberto Mazzolin, Cyber, Space, Defence and Security Technology Strategist for Starion and Nexova.

One consideration in modern warfare is that even if only two countries are formally engaged in conflict, international cooperation is still an underlying factor
Rooted in history
Roberto Mazzolin explains the background to today’s cybersecurity exercises: “Military exercises have long been the principal medium for preparing nations and coalitions to be able to contribute to military operations in a coherent and coordinated fashion. With cyber and space having been identified as new domains of warfare, not only by NATO but by many nations, it’s very important to be able to use exercises to train against an accurate representation of real-time threats that take this into account.
“The objectives of such exercises include coordinating the operations and rehearsing both response actions and potential offensive actions. They also provide a means to work through scenarios that help to integrate cyber effects in a coordinated manner with conventional effects.”
Locked Shields
NATO’s Locked Shields event demonstrates the breadth of some cyber exercises, as it encompasses both technical and non-technical aspects. In Locked Shields,
a scenario is built around a fictional country that comes under attack on a large scale, carried out by the ‘Red Team’. The ‘Blue Teams’ represent national cyber rapid reaction teams that are deployed to protect the mock state’s information systems and critical infrastructures from thousands of attacks, make management decisions in a crisis situation and ensure that decisions are well considered.
During this year’s Locked Shields, the teams faced over 8,000 complex cyberattacks targeting 8,000 virtual systems, with the exercise aiming to reflect what happens in a real conflict, such as geopolitical tensions, sovereignty violations and large-scale cyberattacks. Cloud computing and strategic decision-making tasks at ministry level were integrated into the exercises for the first time.
The exercise is also a competition, with teams tackling challenges to amass points. Each team comprises a great variety of people playing different roles that emulate real-life ones. For example, there are engineers configuring workstations, servers and software, and

others monitoring the network for signs of attacks and trying to collect evidence that hosts have been compromised. Alongside them are people with legal and communications backgrounds who act as lawyers and social media managers, so that the whole team can realistically represent a single entity, such as a country. Points are scored for the engineering-related aspects and for actions taken by the non-technical team members.
Despite being a competition, Locked Shields is ultimately a training exercise, similar to many others that take place each year. Some exercises focus on practicing defensive measures, while others, such as NATO’s Crossed Swords, centre on offensive cyber actions. Some incorporate both. There are also cyber exercises that focus on specific elements, for example forensics, where the aim is to analyse evidence from an attack and craft a report.
The exercises vary in style too. Some, like Locked Shields, are primarily ‘live fire’ exercises. Others are ‘capture the flag’ exercises in which participants
compete to find and exploit vulnerabilities in a simulated environment, the goal being to locate hidden pieces of data or information, called ‘flags’.
Coalition coordination
Ultimately, national exercises will reflect the specific needs the country has identified. However, one consideration in modern warfare is that even if only two countries are formally engaged in a conflict, international cooperation is still an underlying factor. This is especially true when NATO countries are involved.
Cooperation between countries is therefore as necessary in the online environment as on the ground – if not more so. To maximise the success of such cooperation, regular practice is vital.
Events such as NATO’s Locked Shields and Luxembourg’s Cyber Fortress therefore play another vital role, which is providing a means to optimise the way countries in a coalition work together in a cyber warfare environment.
“Different nations may have different policies governing the use of cyber in support of strategic activities. There are also different organisations and agencies involved, because no two countries ‘do’ cyber in exactly the same way,” explains Roberto Mazzolin. “Exercises are therefore an important medium for different nations in the context of a coalition to be able to normalise and develop the associated doctrine and tactics, techniques and procedures, and then formulate coordinated operations within a coalition environment.”
Individual benefits
For all the automation available and the focus on international and national inter-agency cooperation, ultimately it is the individuals at their computers who make the difference in cyber warfare.
Nexova’s Panagiotis Bellonias, Technical Lead of the Scenario Team, and Alexandru Militaru, Product Owner for Nexova’s CITEF Cyber Digital Twin, took part in May 2025’s Locked Shields event as part of an international team from Latvia, Belgium and Luxembourg, where their combined team came fourth out of 17 teams. Panagiotis took a role in defending industrial control systems, keeping the power and water infrastructure operating, while Alexandru was in the Windows team, ensuring it remained usable by all the sub teams. Both engineers also took part in Cyber Fortress earlier in 2025.
Panagiotis Bellonias explains some of the key benefits of working with people from other organisations and countries: “Organisations and companies do things very differently. When you take part in these exercises,
you bring your knowhow from your own company and apply some of the tips and tricks you know to the role that you have been assigned, which will be consistent with your area of expertise. Importantly, however, during the exercise you can see the varied methodologies, processes and tricks that experts from different organisations follow. You then brainstorm all of these and decide together which you are going to actually apply. Not only do you learn a lot from this, which is the point, but it’s very inspirational.”
An added bonus is the interpersonal and communication skills that are built during these exercises. “You learn how to talk to and interact with diverse people, and with people you don’t know but need to cooperate with and trust. Ultimately, you can end up making friends and forging relationships that last beyond the exercise itself, which is really valuable.”
As cybersecurity is an online discipline, exercises can be held with all participants situated totally remotely from each other. For Locked Shields, however, Panagiotis and Alexandru travelled to Riga to work alongside their fellow team members.
“The main issue with being located remotely is that you cannot really communicate easily with each other because the teams can consist of more than 100 people,” says Alexandru Militaru. “If you want to approach someone from a different sub-team, it’s very hard to do it remotely, whereas if you are in the same location, you can just leave your desk to find them and talk immediately. That’s why some teams prefer to gather onsite to compete, because the communication is much better.”
”Defensive cyber activities have been going on since the implementation of the internet in the modern military context.“

In reality, the teams of cyber experts involved in tackling a genuine defence-related cyberattack or threat will mostly not be co-located. Roberto Mazzolin explains: “Depending on the nature of the operation, there is likely to be a central team providing coordination, monitoring and deconfliction. But the execution of cyber activities would predominantly be decentralised, with each contributing nation employing its own cyber resources to support both coalition and national operations at strategic, operational and tactical levels, commensurate with their sovereign national interests, competencies and legislation.”
Panagiotis Bellonias adds: “During training, having everyone in the same place helps teams learn faster and sort things out quickly. But in a real cyber conflict, things work differently. These operations are built to run across different locations, with systems and processes in place to keep everything coordinated. What really matters then isn’t being side by side, it’s being well prepared, organised and able to stay connected, no matter where people are.”
Future cyber exercises
International cyber exercises are not new. NATO’s Locked Shields was first organised in 2010 and has been held annually ever since. Luxembourg’s Cyber Fortress is a more recent addition to the cyber exercises calendar, taking place annually since 2021.
Another good example of these large exercises is Ciber Perseu3, organised by the Portuguese Ministry of Defence.
“Defensive cyber activities have been going on since the implementation of the internet in the modern military context,” observes Roberto Mazzolin. “Since I was involved in running the cyber exercise programme at the US Cyber Command, it’s really stepped up in pace in the context of NATO and other multinational exercises.”
That pace isn’t likely to abate any time soon, with cyberattacks becoming ever more frequent. NATO itself reported last summer that “cyber threats to the security of the Alliance are complex, destructive and coercive, and are becoming ever more frequent. Cyberspace is contested at all times and malicious cyber events occur every day, from low-level to technologically sophisticated attacks.” 4
The sheer scale of some of the exercises is staggering but their contribution to national sovereignty and international security is undeniable. While they continue, we can be optimistic about our chances of retaining strong cyber defences whenever they are needed.
Sources: See page 86
Image © Belgian Ministry of Defence

Future Vigil mission. Image © ESA/A. Baker
When the Space Weather Threat Becomes Reality

In May 2024, Earth found itself in the path of the most powerful solar storm to head in our direction for over 20 years. Although the Gannon Storm didn’t cause any major power outages or other serious incidents, over time reports surfaced of a diverse range of impacts. Taken together, these underscore the importance of the many space weather activities currently underway globally, from studying the Sun to mitigation planning. OpenSpace spoke to Simon Machin from the Met Office and Alexi Glover from the European Space Agency to find out the current state of space weather activities.
The phenomena that we collectively refer to as ‘space weather’ are not new. The Sun has been emitting solar flares, radiation storms and coronal mass ejections (CMEs), and causing geomagnetic storms and other disturbances, for billions of years, as far as we can tell. However, the effects of these phenomena didn’t matter to most people until the digital age, when we became increasingly reliant on power and communications networks, and services provided by satellites such as positioning, navigation and timing (PNT).
The first ‘major’ recorded impact on technology was in 1859 due to what is known as the Carrington Event – this is the most powerful solar storm to impact Earth on record. Geomagnetically induced currents caused telegraph operators to receive shocks and continental telegraph lines were destroyed by fires. In the 20th century, solar storms had varying levels of impact, including a geomagnetic storm in 1989 that caused communications blackouts, a major power outage in Quebec, Canada, and the loss of positional knowledge
for over 1,000 space objects for nearly a week. But the intensity of the Sun’s activity rises and falls across an 11-year cycle, and not every ‘peak’ sees a notable event on Earth. As a result, even after the 1989 storm, concern around space weather waned once more.
In the end, it took the Halloween storms of 2003 to emphasise just how serious the impacts of space weather could be. As a consequence of multiple flares and CMEs, many satellites experienced anomalies, with anecdotal evidence suggesting that the majority of satellites in low Earth orbit (LEO) were temporarily ‘lost’ as their positions altered and had to be reestablished; there was also one total loss and 10 cases of loss of operational service for more than a day. Aircraft flights were diverted away from the poles to lower latitudes to avoid radiation, there was a power outage in Sweden and GPS systems were seriously affected, including those used for deep-sea and land drilling, and surveying. 3, 4


Since then, organisations around the world have set up or enhanced programmes to gather related data in space and on land, and to study the Sun and the effects of its behaviour. The ultimate goal is to create a space weather forecasting system analogous to the terrestrial weather forecasts we now take for granted. In the meantime, we need to continue to improve our ability to mitigate the effects of space weather events.
What’s the problem?
Space weather describes the interaction of phenomena caused by solar activity with the Earth’s magnetosphere, atmosphere and ground, and with technology and engineered systems, such as satellites, aircraft, power cables and electronic systems. Each of the phenomena can cause different impacts, including loss of radio signals caused by solar flares, power outages due to geomagnetic storms emanating from CMEs, and disruption to satellite operations from radiation storms.
There are too many potential impacts of space weather events and mitigating actions to describe in a single article – a report published earlier this year on Severe Space Weather Impacts on UK Critical National Infrastructure, led by Starion as part of the UK’s Space Weather Instrumentation, Measurement, Modelling and Risk (SWIMMR) project, runs to over 100 pages. Lloyd’s, the insurance marketplace, estimates that the global economy could be exposed to losses of US$2.4 trillion over a 5-year period – or up to US$9.1 trillion in the most extreme scenario – from the threat of a hypothetical solar storm.5
As a result, there are many projects assessing the threats to space-, ground-, sea- and air-based infrastructures and systems, and potential mitigations. In the European Union (EU), the EU Space Programme’s Space Situational Awareness component includes a Space Weather Events (SWE) subcomponent. In March 2025, the Commission adopted its ‘Implementing
Decision’ for the selection of a space weather service under SWE. The UK Government has been particularly active with the SWIMMR programme, given that the UK is further north than many other European countries and therefore more at risk in terms of ground- and seabased systems.

Earth’s magnetic field. Image © ESA/AOES Medialab
Meanwhile, the European Space Agency (ESA) is actively engaged in a broad range of space weather projects and activities. “Space weather has the ability to impact a large number of technologies and systems that form part of our everyday lives, and many aspects of our critical infrastructure,” says Alexi Glover, ESA Space Weather Service Coordinator. “Our Space Safety Programme is developing new sources of data and service capabilities geared towards increasing the resilience of our society to space weather impacts.”
ESA’s projects include the development of the Space Weather Payload Data Centre (SWE PDC), which is being led by Starion. Alexi Glover explains: “The new PDC in development is intended to be a flexible and scalable system carrying out Level-1 data processing for ESA’s space weather hosted payload missions and beyond. In future, the PDC will also support further elements of the Distributed Space Weather Sensor System [D3S] under development, plus the Vigil mission due to launch in 2031.
“The SWE PDC will make processed Level-1 data available in near real-time to the Space Weather
Service Network for further Level-2/3 data processing into space weather products. The PDC project will also implement the SWE Data Hub capability, replacing and extending the current Space Weather Database [SWEDB] functionality, enabling the storage, retrieval, analysis and visualisation of data in support of space weather services and their users.”
The PDC will be scalable, secure (zero trust) and cloud native. With more space weather missions in development, including Vigil and Aurora, it’s essential that the ground segment is scalable in order to store, process and disseminate the growing volume of data, and can integrate new data types.
The project will also include the development of enhancements for the current SWE Data System that supports the ESA Space Weather Service Network. This provides an overview of current space weather conditions and a set of domain-specific dashboards for areas such as spacecraft, aviation, pipeline and
critical services, with the primary examples being satellites and power grids.
Given our reliance on satellite-based data and services, it’s essential to understand the risks satellites face from space weather. One is ‘single event effects’ caused by ionising radiation damaging onboard electronics. This can be mitigated to an extent by using radiationtolerant components, shielding and redundancy in the design, but all of these come at a cost.
Another concern is the increased drag caused by solar flares and CMEs temporarily heating Earth’s upper atmosphere – something that mainly affects spacecraft in LEO, of which there are now many thousands. Increased drag makes satellites speed up and lose altitude, requiring precious fuel to return them to their operational orbits. Federico Da Dalt, Starion Space Weather Application Scientist, explains: “The planning phases of a satellite mission consider propulsion and fuel consumption as very important factors. Propulsion



“Space weather can affect our ability to accurately track objects in orbit, including debris, which can vary hugely in size.”
Image © Spacecraft: ESA/ATG medialab; Sun: ESA/NASA SOHO

to reach its objectives. Failing to consider an increase of solar activity during the planning phases, for example when approaching a period of maximum solar activity, would result in an increase in risks to the operation, such as spacecraft disruptions, unplanned manoeuvres and shortened lifespan. This is particularly important
Among the satellites at risk are the thousands of Starlink SmallSats, which operate in LEO and now comprise 65% of all active satellites.6
49 Starlink satellites deployed at an altitude of 210km en route to their final operational altitude of around 600km. A weak CME around that time caused a minor geomagnetic storm, sharply increasing drag, which brought down 38 of the Starlink now launches to 320km instead, where the atmosphere is thinner, but during a severe geomagnetic storm, satellites at that altitude would still
main technologies we use to track satellites. Space weather can also affect communications with satellites at some frequencies, including command and control. Taken together, this reduces confidence in any warnings that are sent to satellite operators.”
A further concern is the risk presented by multiple satellites all having their positions adjusted simultaneously, without knowledge of how nearby satellites are about to change paths.
Increased drag also increases the risk presented by defunct satellites that can no longer be controlled. Gareth Lawrence, Space Environment Specialist at Starion, describes how serious a problem this is: “It’s hard to know exactly where defunct satellites are because they are no longer providing any telemetry and there’s not enough radar capacity globally to monitor everything in space more than a fraction of the time. The positions of some old satellites that are thought not to be a risk are only checked very occasionally. But if you suddenly have an extended period of higher atmospheric density due to a space weather event, and therefore greater drag, the orbit of one of those old satellites may fall by tens or even hundreds of metres, so that it’s suddenly presenting a new and very serious risk to other satellites.”
Simon Machin, Meteorologist and Manager of the Met Office Space Weather Programme in the UK, explains the broader problem: “Over the next 5 years, low Earth orbit will become increasingly congested as other mega constellations are launched. If none are affected in any way, that’s not a problem. But space weather can affect our ability to accurately track objects in this orbit, including debris, which can vary hugely in size. This is compounded by the fact that increased atmospheric density causes objects to react in different weather, which is an issue because radar is one of the
Why does this matter? “The 2009 collision between an operational American communications satellite and a long-defunct Russian satellite created more than 2,000 new large pieces of space debris that required cataloguing, one of which necessitated a collision avoidance manoeuvre by the International Space Station more than 2 years later in 2011.8 Since the advent of mega-constellations, the impact of any future collision will be far greater.”
Positioning and timing
We rely, directly and indirectly, on satellites for a wide range of services and data, including positioning and
The lack of positioning data due to a solar storm, and thereby the impact on navigation for vehicles, is a cause for concern

timing from global navigation satellite systems (GNSS). The lack of positioning data due to a solar storm, and thereby the impact on navigation for vehicles on land, at sea and in the air, is an obvious cause for concern. But continuous accurate timing is also vital, being more critical than many realise.
The SWIMMR report (mentioned previously) notes both the energy and communications services are dependent on GNSS timing systems, as are many other sectors, such as financial services and transport.9 As a result, one of the report’s priority recommendations is that in the UK: “Government and relevant policymakers ensure a diversity of position, navigation and timing systems for safety-critical applications in CNI [critical national infrastructure]. In particular, it recommends that GNSS should not be solely relied upon by emergency services, maritime port operations, tracking of trains and aircraft operations.” It also recommends
that “space-based timing services should not be solely relied upon for … electricity network synchronisation and cellular network synchronisation.”
GNSS timing only requires a signal from one satellite, so timing is unlikely to be completely disrupted, and alternative timing solutions do exist, such as crystal oscillators and atomic clocks. (National Grid Electricity Transmission – the UK’s national grid transmission asset owner – uses centralised atomic clocks as backup timing during GNSS disruptions.) However, given that long-term disruption can’t be completely ruled out, and because the same satellites are used for positioning, for which multiple satellites are required, it is important to consider using multiple satellite systems to provide redundancy and resilience. The SWIMMR report, which is UK-specific, recommends development of national-scale backup PNT systems for fixed and mobile systems.
The magnetic field around Earth can be thought of as a huge bubble, protecting us from cosmic radiation and charged particles in solar winds that bombard Earth.
Power
Power underpins so many services that it is a primary focus for research into its vulnerabilities and potential mitigations.
Geomagnetic storms can induce powerful direct currents in power lines and other lengthy conductors such as railways and pipelines. These geomagnetically induced currents (GICs) in transmission networks are the most likely impact of space weather on power systems, although there’s also the potential for problems caused by single event effects in electronics and dependencies on GNSS and communications systems, which are themselves vulnerable. The interdependencies between the various organisations within the power industry further complicates matters.
Because power is recognised as a vulnerable sector, a lot of related work is going on, both within and
for the industry. One project being led by Starion for ESA is EuroGIC, which is focusing on the impact of severe space weather on power grids across Europe, with the aim of enabling electricity grid operators to assess the risk to their transformers and, ultimately, avoid blackouts. EuroGIC will be a web application that will model GICs in power grids, using data from existing geomagnetic sensor networks across Europe and providing information to users in near-real time.
Emerging technologies
Any consideration of the effects of space weather needs to include emerging technologies. One notable example is autonomous vehicles, which are poised to revolutionise transportation. Safety is vital for such vehicles, whether they are on public roads, such as selfdriving cars, on private land (for example agricultural vehicles), or in the air or at sea.
Image © ESA/ATG medialab
In the Starion-led Space Weather Autonomous Vehicle Effects (SWAVE) project, experts are helping ESA understand the risk that space weather may pose to this emerging industry, and the support that could be offered to mitigate the risks. The focus has been on the vast array of technologies autonomous vehicles employ to navigate, communicate and make splitsecond decisions. Although the space weather impacts on these technologies individually – GPS receivers and radar systems, cellular networks and onboard computers – are known, it’s important to understand the effects their disruption would have on the autonomous transport systems that depend on them.
ESA’s Alexi Glover says: “In addition to our preoperational service provision, the Space Safety

Programme supports a number of targeted, high priority development activities and feasibility studies. Developments such as EuroGIC address key needs identified by end-users and provide an opportunity for the development of targeted applications and products, with users directly involved in the definition and testing phases of the project. Other example areas of development include GNSS performance indicators providing end-users with information on how they may be affected by space weather conditions and radiation belt nowcasting and forecasting, which targets the needs of operators of spacecraft in Earth orbit.
“Feasibility studies such as the SWAVE project address newly emerging potential user domains where requirements for space weather information and use

cases for the data may need further elaboration. These studies provide an opportunity to analyse in detail the potential impacts and also to engage with the user community to understand their needs.”
Weather forecasts
There have been great advances in capabilities and knowledge in the last couple of years, but how far away are we from a true space weather forecasting system?
“The expertise required and the thematics are huge in comparison to terrestrial weather forecasting,” says Starion’s Federico Da Dalt. “The weather system is ‘closed’, whereas space weather is open and very complicated. You might see an active spot on the Sun, but nothing tells you when that might ‘go off’, what type it will be, whether it will head in our direction, its velocity and how it will interact with Earth. I think we are quite far off any kind of reliable forecasting system. That said, we are working towards this with the launch of satellites such as Vigil and increasing ground-based instrumentation, and eventually AI may help here too, but it is very, very complicated to solve.”
Gareth Lawrence from Starion adds: “Terrestrial weather forecasters are very lucky that they don’t have to consider magnetic fields in their models. The Sun releases most of its built-up magnetic energy through the solar wind, which is constantly flowing at different speeds. The solar flares and coronal mass ejections only happen now and again when there’s a build-up in a particular area and it moves beyond the point of stability. The hope is that Solar Orbiter and NASA’s Parker Solar Probe mission will provide at least initial data to be able to parameterise and describe these events. But the question is whether we will ever be able to predict with real confidence that a flare of a certain magnitude will originate in a particular region in the next 24 hours. There’s a huge amount of active research going on and some really clever people working on it, but it’s a very tricky problem.”

Ultimately, says the Met Office’s Simon Machin, “A ‘sun-to-mud’ forecasting system – one that can forecast all elements of space weather including flares and radiation and geomagnetic storms – is, I think, many years away: maybe 50 years away. But we are constantly improving what we can do in all respects. Our scientific understanding is improving and so is our ability to monitor and, to a limited degree, predict what will happen in response to any space weather event. But if we’re to be able to provide a sun-tomud forecast, we really need to fully understand the dynamics of the Sun and that is a long way off.”
Take action now
Despite the Gannon Storm and other subsequent powerful solar events, there have not (at the time of writing) been any major impacts on space or ground infrastructures during this solar cycle. Nevertheless, now is not the time to be complacent or to wait for others to act.
“There’s an onus on all organisations to understand their own risks,” says Simon Machin. “In the UK, the Government’s strategy requires each government department to understand the risk to the sectors they oversee, but it is still down to each organisation to decide if it is a priority and take pre-emptive action. Some sectors, such as energy, have put a lot of time and effort into understanding the risk, but I’m sure there are others that could be affected by space weather but have taken little or no interest so far.
ESA’s Solar Orbiter. Image © ESA/ATG medialab

“Ultimately, if something happens, it’s important to understand why your system is malfunctioning or degraded. There are numerous drivers that could be the cause: it could be space weather, but it could instead be an engineering or electrical fault, or even a cyberattack. Your responses to each of these might be different. If it’s a space weather event there would be specific things you would do to mitigate the effects and manage the situation that would be different from responding to a cyberattack, for example. Also, you will want to know who to contact to understand how long it might last and what the implications might be.”
There is now more information available in terms of space weather monitoring and modelling capabilities than ever before from national organisations such as the UK’s Met Office, which provides a 24/7/365 active service, and international agencies including ESA.
ESA’s Alexi Glover summarises: “The ESA Space Weather Service Network ensures the continued pre-operational provision of the space weather services through a network consisting of more than
50 different entities including academic groups, institutes and industry. Here the teams collaborate in order to provide pre-operational services to end-users supported by a helpdesk located at the Space Pole in Brussels. New products and applications resulting from targeted developments are continuously integrated into the services and the close interaction with service users enables both provision of timely and reliable space weather information, along with improved awareness of user needs and understanding of the potential impacts of space weather on our critical infrastructures.”
Now is therefore the time to maximise resilience to the impacts of space weather. After all, even when we have a comprehensive, timely forecasting system, it will not prevent those impacts – it will only give us more time to prepare to react to the Sun’s outbursts.
Resources and sources
ESA SWE Service Portal: swe.ssa.esa.int
Met Office Space Weather: weather.metoffice.gov.uk/ specialist-forecasts/space-weather
Sources: See page 86
”There’s an onus on all organisations to understand their own risks from space weather, decide if it is a priority and take pre-emptive action.”
ESA’s Smile mission will reveal how Earth’s magnetic field reacts to streams of particles and bursts of energy from the Sun. Image © ESA
The Gannon Storm of May 2024
From 10 to 13 May 2024, a series of powerful solar events occurred that had a wide range of impacts on and around Earth. Collectively known as the Gannon Storm, after space physicist Jennifer Gannon, or the Mother’s Day Storm, it gained widespread public attention when aurora caused by the storm were visible much further from the magnetic poles than usual in both hemispheres.
Beyond the pretty aurora, other effects of the storm were less welcome:
The increase in the density of a layer of the ionosphere caused by the storm affected ground-based and two-way radio communications, primarily on the HF band but also on the VHF and UHF bands.10
The GOES-16 geostationary weather satellite, which provides a view over the Americas, stopped transmitting any data for nearly 2 hours, with a further loss of transmission for 11 minutes soon afterwards.11
There were reports of degraded service from Starlink’s satellites, but these ultimately remained operational.12
The European Geostationary Navigation Overlay Service (EGNOS), which augments the GPS satellite navigation service to provide more accurate positioning data, was degraded, with no service for a period of time.13
Flight trackers showed that airlines rerouted planes to lower latitudes because solar storms can cause spikes in cosmic radiation near the poles, which is best avoided by crew and passengers.14
Some farmers in the USA experienced problems with the GPS guidance systems, including precision farming functionality, on older model John Deere tractors.15 Some veered off course or stopped working, forcing those farmers to suspend planting operations, resulting in average financial losses of about US$17,000 per farm.16
Disruption to GPS signals was reported to have affected some aerial drones.17
The storm also served to illustrate that some critical infrastructures were prepared to act on receipt of storm warnings. In New Zealand, for example, Transpower issued several ‘grid emergency notices’ due to geomagnetically induced current events and removed some transmission lines and circuit breakers from service.18 In the USA, AT&T and T-Mobile both issued statements saying they were prepared to respond to any service disruption, as did power companies in Canada, where a solar storm in 1989 caused a 9-hour power outage.


Looking at the Sun
The more data we gather about the Sun, the closer we get to understanding it. “Data from scientific missions such as ESA’s Solar Orbiter and NASA’s Parker Solar Probe, which are flying close to the Sun in different orbits, are giving us new insights into the Sun’s dynamics,” says Simon Machin, Meteorologist and Manager of the Met Office Space Weather Programme. “Solar Orbiter, for example, has recently started providing imagery and measurements of the Sun’s poles for the first time. All of this data will inform the development of our modelling, which in turn will help us improve our forecasts.“

“Over the last 18 months, through the UK’s SWIMMR programme, we’ve got a range of new modelling capabilities,“ says Simon Machin. “One enables us to provide short-term forecasting of atmospheric ionising radiation for airlines. Another provides a risk assessment of the potential impact on the UK’s power grid at a substation level. One more, developed by the British Antarctic Survey, provides a model of the Earth’s radiation belts to help us understand the realtime environment satellites are operating in and any changes driven by space weather that might lead to single event upsets.
“These models have limited forecasting capability but they help people understand what’s happening
now and in the short term, the severity, and what the duration is likely to be. But for now, we can’t give much notice of events because we don’t have the sensing capability in place in space to give us adequate warning.”
Understanding more about the Sun and space weather is a target for a number of national and international space agencies. ESA missions have been studying the Sun for 35 years, with the joint ESA–NASA SOHO mission still operational following its launch in 1995, giving insights into the Sun’s structure, interior, surface and atmosphere, and the solar wind. Another joint mission, led by ESA, is Solar Orbiter, which is studying the Sun from an incredibly close vantage point, while
Solar Orbiter traces energetic electrons to different types of sources on the Sun. Image © ESA & NASA/Solar Orbiter/STIX & EPD
Solar flares CMEs
NASA’s Parker Solar Probe became the first spacecraft to fly through the corona – the Sun’s upper atmosphere – in 2021.
Meanwhile, in November 2024, scientists reported the first significant result from Aditya-L1, the first solar observation mission launched by the Indian Space Research Organisation, when one of the instruments captured data that helped scientists estimate the precise time a CME began.
Some solar missions are constellations, such as ESA’s four-satellite Cluster mission, which studied the solar wind and the Sun’s magnetosphere until it ended in September 2024. In March 2025, NASA launched four small satellites that make up the PUNCH (Polarimeter to Unify the Corona and Heliosphere) mission, which will study how the Sun’s outer atmosphere becomes the solar wind.
Solar missions don’t have to be big to produce useful results. ESA has SmallSat and nanosatellite missions planned as part of its Space Safety Programme, including a mission to study Earth’s aurora. Studying the aurora indirectly enables the observation of solar wind variations and the impact of CMEs, so this will support nowcasting and forecasting. The mission will start with a single satellite demonstrator (Aurora-D), to be followed by a constellation of four to six SmallSats. In November 2024, ESA signed a contract for the Agency’s first space weather nanosatellite mission, Swing (Space Weather Ionosphere Nanosat Generation), that will monitor the ionosphere.
Other planned launches include China’s Solar Polar Orbit Observatory, scheduled for 2029, and ESA’s Vigil, due to launch in 2031. The latter will be the first mission to observe the Sun from the fifth Lagrange point (L5) – this gravitationally stable position provides a view of potentially dangerous solar activity before that side of the Sun rotates to face Earth. Before either of these
head into space, the National Oceanic and Atmospheric Administration (NOAA, part of the US Department of Commerce) will launch its Space Weather Follow On – Lagrange 1 (SWFO-L1) mission this year as part of its wider SWFO programme. SWFO-L1 will, as its name suggests, observe the Sun from another gravitationally stable Lagrange point.
Finally, there are also instruments hosted on other spacecraft that monitor aspects of the Sun’s activities and the solar wind.
The data from all these missions improves the ability of organisations such as ESA, the Met Office in the UK and NOAA in the USA to provide actionable information to organisations that may be affected. In addition, since some of these missions were conceived, artificial intelligence (AI) and machine learning capabilities have progressed considerably. For example, ESA is now looking at how AI will be used for post-processing data from the Vigil mission, which was originally proposed in 2018.

The Met Office’s Simon Machin says: “I think AI could help us with flare forecasting in particular, which is something we’re not otherwise able to do in any realistic way. Currently, we can provide a probabilistic forecast of solar flares. But as they’re associated with changing local magnetic fields around active areas of the Sun, I think AI could help us to recognise the specific changes that will lead to solar flares erupting.”

Enhancing EU Security Through the Cyber Resilience Act

In recent years, there has been a plethora of new European Union (EU) regulations covering technology and security. Among them is the Cyber Resilience Act (CRA), which will come fully into force in December 2027. How does this differ from all the other related Acts and Directives, and what do organisations need to be aware of? OpenSpace spoke to Cristian Michael Tracci from the European Cyber Security Organisation (ECSO) and Peter Kirkov, former National Cybersecurity Coordinator, Bulgarian Government, to find out.
Organisations selling technology-related goods and services in the EU marketplace are having to take account of a raft of recent and new Acts and Directives that place requirements on the way they operate and the security of their products. Among these are the Network and Information Security Directive 2 (NIS2), the EU AI Act, the Cyber Solidarity Act, the Critical Entities Resilience Directive and the Cyber Resilience Act (CRA). There are also vertical, or sector-specific, regulations such as the Digital Operational Resilience Act (DORA), which focuses on cybersecurity and ICT risk management in the financial sector.
Much attention has been focused on NIS2, which expands cybersecurity obligations for ‘essential and important entities’ (as defined in NIS2) and their supply chains. Of late, however, organisations have been broadening their attention to include the CRA in an effort to understand the requirements that this new regulation will place on them. Approved by the European Parliament and Council in October 2024,

it will be fully applicable by December 2027, although some reporting obligations will begin in September 2026.
Why is the CRA needed?
Unlike NIS2, which applies to entities, the CRA applies to products: specifically, all products with digital elements, which are becoming more common in the consumer and business markets. These range from simple toys and components to networked robotic tools, autonomous vehicles and spacecraft. There can be security vulnerabilities in any software or hardware, meaning that any product with a digital element is a weak point that cyber criminals can exploit to carry out an attack, and this has become a concern for the EU.
Delia Ioana Spinu, Nexova Cybersecurity Legal Consultant, explains: “The Cyber Resilience Act addresses two fundamental problems. The first is the low level of cybersecurity of all products with digital elements, making them vulnerable to cyber threats and attacks. The second is that not only is there an
insufficient understanding of this by users, but in many cases they have very limited access to relevant information when they buy a product with a digital element. They simply don’t know how safe it is – and how safe it continues to be over time.
“In some areas, manufacturers often don’t provide regular security updates or timely updates, meaning that vulnerabilities that become known later on don’t get fixed quickly or at all. Sometimes this is because in the absence of clear legal requirements, manufacturers are not currently held responsible for the cybersecurity of their products after sale. Additionally, investing in secure design and continuous updates is costly and manufacturers may opt to prioritise low consumer pricing and short-term profits.”
Peter Kirkov, former National Cybersecurity Coordinator for the Bulgarian Government, explains why a low level of cybersecurity is a growing concern: “Ultimately, due to increasing digitalisation, this can have profound effects across the EU because so many things are now interconnected. In addition, you may not know your device is compromised because in some cases an attacker will want your device to continue functioning to use it to attack a third party.”
With so many security-related regulations already in place or coming into force, the need for yet another one has been questioned in some quarters. But the CRA isn’t simply repeating existing requirements in a different guise. Instead, because product security is different from organisational security, the CRA has been established as a complementary regulation to others that already exist. ‘Ship and forget’ is no longer going to be an option for any organisation producing products with a digital element in the EU.
What does the CRA cover?
According to the European Commission (EC): ”The Cyber Resilience Act introduces mandatory

cybersecurity requirements for hardware and software products, throughout their whole lifecycle.”1 This covers all products with any digital element(s) and includes all related remote data processing components where “the software is designed and developed by the manufacturer or under the responsibility of the manufacturer, and the absence of which would prevent the product with digital elements from performing one of its functions”. 2
Manufacturers are obliged to ensure that1:
Cybersecurity is taken into account in planning, design, development, production, delivery and maintenance phases
All cybersecurity risks are documented
Actively exploited vulnerabilities and incidents are reported
Vulnerabilities are handled effectively for the duration of the support period
Clear and understandable instructions are provided for the use of products with digital elements
Security updates are made available to users for the time the product is expected to be in use.
A distinction is made between categories of products, which ultimately determines whether they can be

‘self-assessed’ by their manufacturer against specified standards or will need to be assessed by a third party. It’s expected that around 10% of products will fall into the latter group, being subdivided into Important Products Class I and II, and Critical Products. The list of products that fall under Class I is long but includes many types of software including operating systems, plus hardware such as routers, switches and microprocessors. Class II products include, for example, firewalls and hypervisors, while Critical Products include hardware devices with security boxes, smart meter gateways and smartcards.
The current descriptions of categories are relatively broad, but this will be resolved in December 2025 when the EC will adopt an ‘implementing act’ that specifies the technical descriptions of the categories of products in each group.
Supply chains can be long and complicated, so it’s essential that manufacturers and developers of software and hardware, including components, know their existing and target client sectors. Douglas Wiemer, Chief Technology Officer – Cyber, Starion and Nexova, notes: “How a component is going to be used may determine the level of assessment required. It’s possible some manufacturers may choose not to sell
into certain sectors or to specific organisations where the final product or environment is classified as Critical, to avoid the burden of additional assessment.”
Software provided as part of a service is not covered by the CRA, as the NIS2 Directive (and other sectorial legislation) already requires that systems provided as a service or developed in-house meet equivalent technical requirements for cybersecurity. Opensource software is also exempt when distributed non-commercially by non-profit organisations, as are code contributions. But any open-source software used for commercial activities does fall under the CRA. Therefore any organisation using open-source software will be responsible for ensuring they are compliant. Smaller companies may find they need to seek external support to fully conform with the Act.
Some sectors are specifically excluded from the CRA’s remit due to their specialised nature and existing sector-specific regulations. This includes products developed or modified for national security or defence purposes. The CRA does, however, cover the space sector (when not exclusively military).
Nexova’s Delia Ioana Spinu says: “The main principles that are addressed in the CRA are cybersecurity by design and cybersecurity by default, and this applies as much in the space sector as elsewhere. For example, payload developers must identify all the threats in the design, including supply chain vulnerabilities and risks through physical access – even down to the level of ensuring passwords are sufficiently strong enough. Everything must be documented and up to date, and there need to be ways to enable security updates for the whole life cycle of the product or for at least 5 years.”
Security considerations need to be embedded in every stage of a space programme or mission’s life cycle, from design through development, deployment,
operation and decommissioning. In essence, this is no different from all other products covered by the CRA, but with so many companies likely to be involved in the supply chain, space is possibly one of the most complicated sectors in which to ensure full compliance with the new regulation – hence companies at all the stages in space supply chains need to start planning now, if this hasn’t already been initiated.
Nevertheless, Peter Kirkov comments: “The space industry is very advanced technologically and as such they understand cybersecurity very well. They are almost certainly implementing security by design already and meeting minimum cybersecurity regulations because otherwise they would be putting their costly satellites at risk. So I don’t believe it will be overly onerous for the space sector. They may need to introduce some more processes and paperwork because they will need to act on vulnerabilities if they are made aware of them by suppliers and report on any they incur.
“Despite the fact that satellites are very complex, their builders are, in effect, integrators of components and
operating systems. However, it is the organisation that introduces a product to the EU market – be they manufacturer, distributor or importer – that has responsibility for CRA compliance. Therefore, if a company builds a satellite using modules from outside the EU, they will need to factor that compliance activity into their procedures.”
Due in December 2025, the publication of detailed definitions of each type of product will be important for the space industry. In addition, Peter Kirkov notes that the cybersecurity aspects of the proposed EU Space Act3, launched in June 2025, could override elements of the CRA for the space sector. As this Act was still in its public consultation period at the time of writing, and may only be implemented by 2030, the focus for now needs to be on the requirements set by the CRA.

Dealing with incomplete information
Although the CRA itself is now law, at the time of writing not every element related to the CRA was fully specified. Cristian Michael Tracci, Policy Analysis and
Outreach, Senior Manager, ECSO, explains: “There are still some aspects that have not yet been completely set out. For example, we’re waiting for the standards to be developed and published [that organisations will need to meet to demonstrate compliance]. Overall, there will be 41 items within the standards, which is a huge task for the standardisation organisation to complete in a very short timeframe.
“And then it’s unclear as yet whether the level of detail will be the same for any requirements where there is an overlap between two or more regulations – for example how user logins are secured – which might cause some complexity.”
This interim period therefore presents challenges for manufacturers seeking to get prepared well in advance of the final deadline. Nexova’s Douglas Wiemer adds: “It’s possible that the EU Cybersecurity Certification Scheme 4 will provide a partial solution here. But while we wait for a full set of harmonised standards, there is currently no criteria for companies to measure themselves against in order to do any self-assessment.”
Over the next 2 years, there will be a number of milestones for adoption of various elements related to the standard. It’s important for manufacturers to be aware of these dates, but there are two key dates that they specifically need to prepare for. First, from 11 September 2026, it will be mandatory to report vulnerabilities and significant security incidents to national authorities and the European Union Agency for Cybersecurity (ENISA). From 11 December 2027, full compliance with the CRA is mandatory.
Even once the Act is mandatory, it is important to note that the regulation will only apply to products placed on the market before that day if they are ‘substantially modified’. But what does ‘substantially modified’ mean? Not all security updates are regarded as a substantial modification. However, a modification may be considered substantial if an existing product (with digital elements) is changed – by physical or digital means – in a way that was not anticipated in the initial risk assessment, and that change either affects compliance with essential cybersecurity requirements or alters the product’s intended purpose.

October 2024
Adoption of CRA
November 2024
Publication in official European Journal
December 2024 CRA enters into force
June 2026
National Conformity Assessment Bodies (CABs) will be authorised to assess the conformity of products with the CRA’s requirements
December 2025
Technical description of categories of Important and Critical products to be adopted; terms and conditions for CSIRTs* to withhold notifications to be adopted
* EU Member States’ appointed CSIRTs
Post-sale requirements
One aspect that companies need to build into their business processes is that the requirements of the CRA don’t stop once a product has been delivered. Instead, they will need to be compliant for a period after they are sold, during which time those companies will be expected to act upon any vulnerabilities that may be discovered.
Under the CRA, companies have to provide security updates for their digital products for a minimum of 5 years or the product’s expected lifetime, whichever is shorter. Technical documentation must be continually updated during the support period as a minimum and, along with declarations of conformity, be available for 10 years after a product has been placed on the EU market.
Manufacturers must report any actively exploited vulnerabilities and severe security incidents to their appointed national Computer Security Incident Response Team (CSIRT) and ENISA within 24 hours. They may then need to provide further information within 72 hours and a final report within 14 days for vulnerabilities or within one month for severe incidents. They must also inform any impacted users – and, where appropriate, all users – in a timely manner of an
December 2027
Full compliance with CRA is mandatory
September
2026
Mandatory to report vulnerabilities and significant security incidents to national authorities and ENISA
actively exploited vulnerability or severe incident and, where necessary, provide details about risk mitigation and any corrective measures that they might deploy to mitigate the impact. (More details on this will be published in December 2025, including in what cases public notification can be delayed or omitted.) The aim is to ensure swift action to address vulnerabilities and mitigate the impact of security incidents, thereby improving the overall cybersecurity posture of products in the EU market.
Nexova’s Douglas Wiemer points out: “Producers of commercial products will need to publish vulnerability advisories and make their clients aware of them, and that should flow through the supply chain very quickly. However, there are a number of inherent challenges and unknowns. For example, what happens when a vulnerability is identified in a previously evaluated and approved product that is being used by third parties along the supply chain? I believe the regulators are trying to mitigate the burden here, but it will be up to each company to decide what the perceived risk is based on their threats and assets, and therefore how this newly identified vulnerability will affect them. Overall, it comes down to responsible disclosure by the vendor and the risk management assessment of the buyer or user. The latter should look at the risk to their
infrastructure, how much risk tolerance they have and their understanding of the vendor’s plans to address the vulnerability.”
What do companies need to do now?
Although CRA-related standards don’t yet exist, companies should be evaluating how the Act will affect each one of their products so that they can be ready to assess them, or have them assessed, when the standards are published.

The first thing companies need to do is to understand whether they are impacted by the Act or not. In essence, all products with a digital element, including ones that don’t process data themselves but link to remote data processing, come within the scope of the Act. There are some exceptions and there are also prescriptive lists of categories of products that require more stringent conformity assessments.
The next step is to undertake a risk assessment to identify the actions needed to meet the requirements for compliance.
Nexova’s Douglas Wiemer concurs that “there is no single risk management framework that every company should use” but suggests that companies could refer to a series of publications by ENISA related to risk management frameworks and standards.5
“It’s all down to taking a risk-based approach that takes into account multiple aspects,” says Nexova’s Delia Ioana Spinu. “These include the criticality of the product within the sector it’s going to be used in, the needs of that sector, the risks it may be exposed to, the likelihood of an incident and then the impacts, severity and consequences of any incident. Based on that assessment, manufacturers should tailor their approach – there is no universal methodology that can be applied in every case.

“Another way to consider it, especially if you are using components or software from other manufacturers, is to take the risk-based approach currently used by those implementing cybersecurity across their organisations. What do I need to protect? Why do I need to protect it? What’s the threat? It’s not solely about conforming with the obligations set by national or international laws – it’s about taking appropriate measures to enhance your organisation’s resilience, including avoiding any sanctions associated with failing to take appropriate measures related to the products you sell.”
If products are found to be non-compliant, the relevant authorities could insist that they be made compliant, restrict their availability or order that they be withdrawn from the market or even recalled. There will also be provision for financial penalties for non-compliance reaching up to €15 million or 2.5% of a company’s global annual turnover, whichever is higher. Other violations, such as those related to documentation or reporting, can incur fines of up to €10 million or 2% of global turnover, while providing

misleading information could lead to fines up to €5 million or 1% of global turnover.
Ultimately, the impact on each company may vary substantially, depending on where they are in any supply chain and how complicated their products are. If a component has already been certified or assessed to be OK, it should be possible to reuse the evidence put together by that component’s supplier. However, companies will still need to do a risk assessment because they are integrating it, along with other components, in something new. Part of that assessment should look at whether it’s better to remove a non-compliant product or if it will be less damaging to keep it and try to fix any related vulnerabilities.
Towards a more secure tomorrow
The CRA specifically focuses on products, including both hardware and software, which in many respects differentiates it from other security-related regulations.
However, this does not mean that all preparatory activities can, or should, be distinct from ongoing work to meet the requirements of other EU Acts and Directives.
ECSO’s Cristian Michael Tracci advises: “The EU aims that the CRA should complement other regulations such as NIS2. It’s not the will of the regulator to make it overly complicated but there are likely to be some overlaps because they are tackling the same objective of improving security from different perspectives. Some regulations approach it from the aspect of an organisation’s practices and procedures, while the CRA is about demonstrating that the products themselves are secure. Nevertheless, there are likely to be overlaps in terms of security-related practices and procedures to reach those goals.”
For the space industry, the proposed EU Space Act will also impact security requirements in future, with resilience through tailored cybersecurity requirements being one of its three key pillars. But again, it is likely

the EC will want to avoid stifling the EU space sector by introducing another regulation that makes it overly complicated to do business.
The upshot is that while compliance with the CRA is likely to require separate, focused risk assessments and associated changes to products and processes, it is essential that all organisations shift towards seeing cybersecurity as a fundamental part of how they operate.
Ensuring cybersecurity is viewed by everyone as a core part of business, rather than an add-on or the responsibility of just one person or team, will make compliance – not just with the CRA but also with NIS2 and other security-related regulations – seem entirely logical rather than a burden.
Resources and sources
For more information on the EU CRA, including the EU CRA factsheet and Q&A, visit: digital-strategy.ec.europa.eu/en/ policies/cyber-resilience-act
Sources: See page 86
Classes of products in the scope of the CRA
Products will fall into different categories based on their risk level and criticality, with specific types classed as Important or Critical. Further information can be found in the Annexes of the Regulation and detailed definitions are due to be published in December 2025.
Important Class I
★ Identity management systems
★ Standalone and embedded browsers
★ Password managers
★ Antimalware software
★ Products with virtual private network (VPN) functionality
★ Network management systems
★ Security and event management (SIEM) software
★ Boot managers
★ Public key infrastructure (PKI)
★ Physical and virtual network interfaces
★ Operating systems
★ Routers and modems intended to connect to the internet
★ Microprocessors and microcontrollers
★ ASICs and FPGAs (application-specific integrated circuits and field programmable gate arrays)
★ Smart home products and assistants
★ Connected toys
★ Wearables
Important Class II
★ Hypervisors and containers
★ Firewalls, intrusion detection/prevention systems (IDS and IPS)
★ Tamper-resistant microprocessors and microcontrollers
Critical
★ Hardware devices with security boxes
★ Smart meter gateways
★ Smartcards or similar

Behind the scenes of any space mission are numerous individuals and brilliant technologies that rarely, if ever, get mentioned
The Unsung Heroes of Space Missions

From the day a new space mission is conceived, it involves many people in different roles and an incredible array of hardware and software, resources, innovation and technology. Here we celebrate a few of the behind-the-scenes contributions that typically get little, if any, time in the spotlight. This includes tools essential for performing planetary flybys and the data archives that are the foundation of many of the important discoveries from the European Space Agency’s (ESA’s) science missions.
Think of any space mission and what comes to mind?
Most likely it will be fiery launches, rockets arcing into space and celebrations in the mission operations room. Or maybe it’s the incredible images of other planets, stars and distant galaxies. Behind the scenes, though, there are numerous individuals and brilliant technologies that rarely, if ever, get mentioned.
Many ESA science missions are one-off designs, which, when measured from initial idea to end of life, have lifespans sometimes of decades and involve hundreds of people and many companies. They rely on special software to support activities such as project management, system engineering, mission planning and operations, and for accessing and analysing the data the missions produce. All of this requires exceptional expertise on the part of the scientists and engineers who nevertheless may never appear in the coverage of a successful launch or during a mission.
The following are just a few examples of these unsung technological and human heroes that make space missions possible.
1 Ground segment
Underpinning every satellite mission is the ground segment – the Earth-based infrastructure that supports the operation, control and data handling of the satellite, ensuring the mission runs smoothly from launch to end-oflife. The large antennas and mission control rooms are familiar to all of us, but before these come into play, a team of specialist software engineers will have been working for many months or years to prepare the software that will eventually be used by the mission operations team to ‘drive’ the satellite. This includes planning the activities, sending commands and analysing the satellite’s responses, enabling it to fulfil the mission’s aims and sometimes even helping to rescue a mission when something goes wrong.



Teodoro Bonariol, Flight Operations Engineer at Argotec, which designs, manufactures and operates small satellites globally, says: “Our involvement as ground software engineers can begin months or even years before launch, sometimes as early as the mission proposal phase. At this stage, we help define the high-level architecture for ground tools and networks, ensuring that the future system will be flexible, robust and mission ready. This early engagement is crucial: it allows us to shape solutions that are tailored to the mission’s unique operational needs right from the early design phases.
“As the mission moves into design and development, we develop, test and validate the tools that will monitor, control and support mission operations. Our responsibility doesn’t end with the software delivery. Once the system is operational, we often become ground controllers ourselves, ensuring realtime software performance, reacting to anomalies, coordinating with external entities and maintaining the infrastructure that keeps the mission running smoothly.”
Ground segment software for satellite operations is not ‘plug and play’ because each mission or constellation
is different. “It needs to be adapted to the mission and the satellite, so the engineers will work in tandem with the mission development team to understand the needs and the requirements for the ground segment. This includes aspects such as which onboard software will be employed and which standards will be used on the satellite,” explains Pablo Beltrami, Programme Manager and Ground Segment Competence Lead at Starion. “Given that the ground segment software needs to be able to communicate with the onboard software, it’s typical that one or other will need to be adapted.”
Constellations and automation
The growth of satellite constellations adds another dimension, as does the drive towards increased automation. In terms of ground segment software, each mission may have its own instance. “But when you are operating many satellites at the same time, you don’t want to have to manually run the procedures for each one individually,” continues Pablo Beltrami.
“Automation is key and modern control systems are designed specifically to work with constellations, simplifying the operators’ tasks.” End-to-end
Image © Argotec
automation means that procedures can be prepared in advance, planned and commands sent automatically without the need for manual intervention during nominal operations.
“When dealing with satellite constellations, the operational complexity increases significantly,” explains Teodoro Bonariol from Argotec, whose Hawk for Earth Observation (HEO) constellation is using Starion’s Astral ground segment solution as part of its flight operations system.
“Supporting multiple spacecraft simultaneously requires robust, flexible and scalable tools. That’s why the selection and design of the ground segment software is a central focus from the very early phases of mission planning, continuing through development and testing. Our software must be able to adapt quickly to evolving needs, handle large volumes of data and support parallel operations across multiple satellites.
“Software specifically designed for constellations provides major advantages. It enables automation, efficient resource allocation and streamlined operations at scale. Most importantly, it allows us to manage multiple spacecraft with the same level of
confidence and responsiveness as a single satellite – ensuring mission success, reducing operational overhead and increasing overall reliability.”
Even when the ground segment software is handed over to the mission operations team months before launch for preparing the mission and training, the software engineers remain involved to support and maintain it.
Teodoro Bonariol says: “Our work continues for the entire duration of the mission – this can mean many years of commitment, long after the initial excitement of launch. And even as we support current operations, we are already thinking ahead, creating new solutions
for future missions.”
2 Supporting scientific payloads
Preparing and delivering commands to the science instruments (the payload) on board spacecraft is another fundamental part of ground segment mission planning. At ESA’s European Space Operations Centre (ESOC), these payload operations requests are part of a broader concept known as command request files
The Science Planning Operational Tool (SPOT) was created for the BepiColombo mission and has since been adapted for Juice.

“The SPOT tool allows scientists to stay focused on science.”

Sara De La Fuente summarises the advantages of using SPOT for payload operations: “SPOT significantly enhances efficiency and reliability by eliminating manual data handling, ensuring seamless integration with ESOC systems, and centralising data for secure, realtime access. With robust web-based monitoring and full compatibility with TM/TC Operational Database management, it streamlines operations and reduces both time and cost.”
BepiColombo exploring Mercury. Image © ESA

3
Pointing in the right direction
During the nominal mission and special observation opportunities like flybys, the instruments don’t only need to be operational and receiving commands, they also need to know where to look!
To support this, careful planning is vital to allow scientists to understand in advance what will be in the view of each instrument at any time. For ESA’s planetary missions, this is handled by a team based at ESAC, who support planning for the flybys through their work on the operations of the SPICE geometry system software. The team receives an array of mission-related data, such as trajectory and attitude predictions, in different formats from multiple sources. These are converted into the SPICE format and distributed for use in tools used to prepare flyby operations and observations.
SPICE was originally developed in the 1990s by the Navigation and Ancillary Information Facility (NAIF) at NASA’s Jet Propulsion Laboratory (JPL). Led by the Starion team, SPICE now provides the core of planning tools used for all ESA’s planetary missions,
including the Cosmographia visualisation tool, which also originated from JPL’s NAIF. The SPICE team is responsible for keeping both SPICE data and planning tools such as Cosmographia up to date and making geometry data for planning and analysing operations available to the science community.
“Cosmographia provides a powerful visual way to view the geometry data for missions such as Solar Orbiter as it holds both ‘flown’ telemetry data downloaded from the spacecraft and ‘planning’ or ‘predicted’ data,” explains Starion’s Alfredo Escalante Lopez, who is the Spice Work Package Manager at ESA. “This lets users see how the spacecraft’s trajectory will change over time. More importantly, they can also use it to display the field of view of each instrument. For Solar Orbiter, for example, it enables them to plan an observation of a specific region of the Sun. It can also be used to see the position of spacecraft components, such as solar arrays and antennas, at any time.”
Providing SPICE for the Hera flyby
Earlier this year, the SPICE team supported the Hera mission gravity-assist flyby of Mars, because scientists

wanted to use the opportunity to study Mars’ moon Deimos from close range and use that to calibrate Hera’s instruments before it reaches its final target of the Didymos binary asteroid system.
In advance of the flyby, the SPICE software operations team took predictions of the spacecraft’s trajectory and attitude from the mission’s flight dynamics team and converted these into the SPICE format. This was
then made available to the spacecraft’s instrument teams to help them plan an observation timeline for Hera’s Asteroid Framing Camera (AFC), Thermal Infrared Imager (TIRI) and Hyperscout hyperspectral imager.
Alfredo Escalante Lopez recounts: “As the flyby happened, we analysed the images in real time, using telemetry and trajectory data given to us by the flight dynamics team, to support calibration of the instruments. By comparing the images with our original simulations made using the Cosmographia tool, we then provided SPICE data kernels to let the instrument teams correct issues such as misalignment or optical distortions that may have been caused by factors such as vibrations during launch, and optimise aspects like the image exposure times. Calibrating the instruments this way before Hera reaches Didymos will let scientists start making observations straight away when they reach the asteroids, saving precious time.”
The use of SPICE is not limited to ESA missions. The SPICE service team has also been using it for constellation mission analysis prior to the launch of any of the satellites.
tool visualisation of Hera’s flyby of Deimos showing the field of view of onboard instruments.
Cosmographia
Hera flyby of Mars. Image © ESA Science Office
4 Exploring the archives
The ultimate goal of any space mission is to gather data that can be analysed and turned into useful information. To enable that process, the data needs to be stored and made accessible in useful formats. For ESA’s space science missions, this takes place at the ESAC Science Data Centre (ESDC) in Spain, where a team of 50 scientists and engineers manage an exponentially growing volume of data.
“There’s a lot of focus on the very visible rockets and the hardware flying in space, which are technological marvels. But there are also technological marvels that we build and manage quietly on the ground – essential to the success of science missions – that might be less known because of their behind-the-scenes nature,” says ESA’s Bruno Merín, Head of the ESDC.

“Our overall remit is software development, operations and maintenance of the science data archives. We start by gathering the scientific community’s requirements and then implement them, but this isn’t as simple as it may sound because from a scientific point of view, different scientific communities use data very differently, with their own standards and tools, and the types of data analysis they do. It’s a lot more complex than people think.”
The Archive team supports four scientific domains: astronomy, heliophysics (the study of the Sun, its influence on the solar system, and the space environment it creates), planetary science and, since 2018, human and robotic exploration. The latter includes aspects such as medicine and human biology on the International Space Station and material physics in low gravity. Each domain contains multiple individual archives.
“We have data from missions from the 1970s onwards and are preparing archives for missions to be launched in 10 or 20 years‘ time.”
Digital Library of the Universe
“We call the archive ecosystem the ‘Digital Library of the Universe’ because it contains data of many varied missions and scientific domains all in one place,” adds Starion's Héctor Pérez, Archives and SPICE Software Development and Operations Work Area Manager. Starion leads the development, operations and maintenance of the archives. “With these different domains, the team here needs to have a lot of technical knowledge to understand the data and process it, and make it available in a way that scientists can easily find and exploit it. There’s a huge effort going on to homogenise the look and feel of all the archives and web applications.”
Not only does the Archive contain data from a broad variety of missions, but it also keeps data for every single science mission ever launched by ESA. “We have data from missions from the 1970s onwards and in

parallel we are preparing archives for missions that will be launched 10 or 20 years in the future,” ESA’s Bruno Merín notes.
This leads to one of the biggest challenges that the team faces, which is the ever-growing volume of data: partly because of additional missions and also because satellite downlinks are improving, gradually removing a traditional limit on the data that can be captured from a spacecraft. One mission in particular is starting to make a huge difference in this respect. The archives currently hold around 1100 terabytes (1.1 petabytes) of data, whereas over the next 5 years, the Euclid mission will boost that to over 20,000 terabytes (20 petabytes).
“This massive increase means we are having to completely redesign our systems, including our data centre,” says ESA’s Bruno Merín. “It’s not just about storing all the extra data but designing it so that it
ESAC in Spain. Image © ESA

is still failproof. We are about 80% of the way there, though there are still details to resolve.”
Starion’s Héctor Pérez adds: “Another issue is the amount of data that is going to be travelling across our network. Previously users would download a product from the archive and it may not even have been as big as 1 gigabyte. But if they want products for Euclid, they will be way bigger: too big to download to their machines. So it changes what we provide and means we have to change the mindset of users too, who will instead be able to analyse the data in cloud-based platforms.”
Viewing the universe through ESASky
What often goes unrecognised is that the archives are available for anyone to access, including via the graphical ESASky tool. And yet they lie behind an enormous number of scientific discoveries. A recent analysis showed that between half and three-quarters of the scientific knowledge from ESA’s space missions came not from those who built the instruments flying on individual spacecraft or who requested observations
or measurements, but from people accessing the archives, analysing the data and publishing papers showing their findings.1 The analysis also shows that the archives remain highly scientifically productive for 20 or more years after the end of mission operations when the original instrument and science operations teams may no longer be operational.
“It’s important that people realise all this data that has been collected over decades is open for them

Remnant of supernova SN 1006, believed to be the brightest stellar event in history, seen by XMM-Newton and viewed in ESASky.
ESA’s XMM-Newton has been studying hot and extreme aspects of the universe using three x-ray telescopes since 1999. Image © ESA - D. Ducros
FYI: New version in place.
to inspect, download, analyse and play with, if they want. Anyone can use ESASky to see images from missions such as the Hubble and James Webb telescopes, and any other science mission,” says ESA’s Bruno Merín.
“There’s an important difference between hardware and software that most people don’t realise,” Bruno continues. “With hardware, once the human effort has been put in, the value really lies in the hardware itself. But the value of software lies with the people who made it and continue to support it, because the software evolves and grows almost like a living being. Rapid technological developments mean the way humans interact with information evolves quickly and we have to keep up with this. For example, 5 years ago, artificial intelligence [AI] was science fiction but now there’s a growing demand for us to understand and respond to the demand for scientists to use AI. And that’s just one example.”
Sources: See page 86
Here’s to the unsung heroes
These examples are just a small selection of the many people and technologies that lie behind orbiting satellites and successful science missions. But they serve to show how complicated space missions are and how important each piece of the jigsaw is – and the value of each person involved. Nothing is static, however, so these contributions will change over time, not least thanks to the value that will be added by AI. OpenSpace salutes the unsung heroes who are developing those new capabilities and who toil behind the scenes of each mission in so many ways.
What’s in the ESAC Science Data Centre archives?
Astronomy observation and surveys
Astronomy observation missions typically point at a target in the far distant sky to capture specific images. Survey missions scan the sky to create a map of a certain feature, such as our universe, the Milky Way (Gaia) or all the features (Euclid).
Missions include: Cheops, Euclid, Gaia, Hubble Space Telescope, XMM-Newton, James Webb Space Telescope, Herschel, ISO, Planck, Exosat, Integral and LISA Pathfinder.
Planetary observation
Primarily missions studying planets, their moons and other solar system bodies such as comets.
Missions include: BepiColombo, Juice, ExoMars, Mars Express, Rosetta, Huygens, Venus Express.
Heliophysics
Any missions studying the Sun directly or related phenomena such as the solar wind.
Missions include: Solar Orbiter, SOHO, Ulysses, Cluster, Proba-2 and Double Star.
Human and robotics exploration
Investigations funded and co-funded by ESA’s Directorate for Human and Robotic Exploration performed on microgravity and ground-based facilities, plus a spectrometer on the International Space Station.
ESASky
A science-driven portal providing access to imagery observed by ESA’s space astronomy missions plus those of its partner agencies. Access ESASky at: sky.esa.int/esasky/
Civil Security from Space
1. The Global Risk Report 2025 – World Economic Forum
The Evolution of the Spanish Space Sector
1. Spain in Space – ESA Report
2. esa.int/ESA_Multimedia/Images/2025/01/ESA_budget_2025
3. aee.gob.es/Actividades/ESA.html
4. esa.int/Enabling_Support/Space_Engineering_Technology/ESA_renews_focus_on_Canary_Islands_ for_laser_operations
5. connectivity.esa.int/projects/caramuel
6. aee.gob.es/Destacados/ARRAKIHS.html
7. esa.int/Space_in_Member_States/Spain/La_ESA_e_Hisdesat_lanzan_un_satelite_de_ comunicaciones_seguras_de_ultima_generacion
8. tedae.org/notas-de-prensa/las-industrias-de-defensa-seguridad-aeronautica-y-espacio-facturan13-900-millones-de-euros-en-2023-y-recuperan-los-niveles-prepandemia/
9. esa.int/Science_Exploration/Space_Science/Smile
10. ESA Space Debris User Portal
The Strategic Role of Cybersecurity in Modern Defence
1. nato.int/cps/en/natohq/news_133280.htm
2. nato.int/cps/en/natohq/official_texts_171584.htm
3. nato.int/cps/en/natohq/official_texts_133177.htm
4. nato.int/cps/en/natohq/topics_78170.htm
5. nato.int/cps/en/natohq/official_texts_236520.htm
6. consilium.europa.eu/en/policies/cyber-defence/
7. consilium.europa.eu/en/policies/sanctions-against-cyber-attacks/
8. consilium.europa.eu/en/press/press-releases/2025/06/06/eu-adopts-blueprint-to-better-manageeuropean-cyber-crises-and-incidents/
9. eeas.europa.eu/eeas/white-paper-for-european-defence-readiness-2030_en
10. nato.int/cps/en/natohq/news_234941.htm
Strengthening Cyber Defence Through Exercise
1. c yberconflicts.cyberpeaceinstitute.org/law-and-policy/cases/viasat
2. csis.org/programs/strategic-technologies-program/significant-cyber-incidents
3. defesa.gov.pt/pt/pdefesa/ciberdefesa/exercicios/ciberperseu
4. nato.int/cps/en/natohq/topics_78170.htm
When the Space Weather Threat Becomes Reality
1. ncei.noaa.gov/news/great-halloween-solar-storm-2003
2. Flying Through Uncertainty; TE Berger et al.; 3 January 2020
3. lunduniversity.lu.se/lup/publication/311c9806-0ed7-4773-a383-f8660555b664
4. repository.library.noaa.gov/view/noaa/19648/noaa_19648_DS1.pdf
5. lloyds.com/about-lloyds/media-centre/press-releases/extreme-space-weather-scenario
6. planet4589.org/space/stats/oactive.html
7. Unveiling the Space Weather During the Starlink Satellites Destruction Event on 4 February 2022; Ton Dang et al.; 6 August 2022

8. web.archive.org/web/20111020092342/http:/orbitaldebris.jsc.nasa.gov/newsletter/pdfs/ ODQNv15i3.pdf
9 Report on Severe Space Weather Impacts on UK Critical National Infrastructure: https://epubs.stfc. ac.uk/work/61075921
10. Geospace response to May 2024 X-class flare and coronal mass ejection; J Omojola et al.; April 2025
11. ospo.noaa.gov/
12. reuters.com/technology/space/starlink-experiencing-degraded-service-musk-sayssatellites-under-pressure-2024-05-11/
13. events.spacepole.be/event/222/contributions/3398/
14. scientificamerican.com/article/the-strongest-solar-storm-in-20-years-did-littledamage-but-worse-space/
15. deere.com/en/stories/featured/solar-storm/
16. science.nasa.gov/science-research/heliophysics/what-nasa-is-learning-from-the-biggestgeomagnetic-storm-in-20-years/
17. space-env.esa.int/solar-storms-of-may-2024/
18. transpower.co.nz/system-operator/notices-and-reporting/formal-notices
Enhancing EU Security Through the Cybersecurity Resilience Act
1. EU CRA Factsheet: digital-strategy.ec.europa.eu/en/library/cyber-resilience-act-factsheet
2. EU CRA, Article 3, paragraph 2
3. EU Space Act: defence-industry-space.ec.europa.eu/eu-space-act_en
4. certification.enisa.europa.eu/index_en
5. enisa.europa.eu/topics/risk-management
The Unsung Heroes of Space Missions
1. ESA Science Programme Missions: Contributions and Exploitation; 2025; open access publication at: link.springer.com/book/10.1007/978-3-031-69004-4

All imagery is licensed by or copyright of Starion and Nexova Group unless otherwise stated.
Rue des Etoiles 140, 6890 Libin, Belgium
To find out more visit stariongroup.eu and nexovagroup.eu


