International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Computer
Science & Engineering, MIT ADT University, Pune Maharashtra, IndiaAbstract - Anytypeofproofofidentitymustbeshownto complete any legal formality or verification process. Regardless of the industry in which a client wants to participate, whether it is banking, insurance, healthcare, technology,travel,education,oranyotheronlineservice,the consumerisrequiredtoshowIdentityprooftoprovethat theyarewhotheyclaimtobe.Verifyingcustomeridentities canhelptolessentheriskofidentitytheft.Whilevalidating IDs sounds great, it will take money, effort, and human resourcestoadoptsecuredocumentverificationsolutionsas acorporation.Theoverlydemandingauthenticationprocess degradestheentireclientexperience.Whilemostcustomers despisethelengthyverificationprocedure,nothavingone diminishes brand trust and can lead to businesses losing more clients throughout the onboarding process. This project will help the different organizations in detecting whether the Idprovided to them by their employees or customersoranyoneisoriginalornotasitisaverification portal.
Key Words: Computer Vision, Document Verification portal, documents verification, Tampered, analyzer,docs verification.
We have recently witnessed the tremendous rate of globalization and its consequences for humanity. New technologies,suchastheInternetandothernetworks,have bothadvantagesanddisadvantages.Speed,efficiency,better time management, access to an ocean of information, mobility,agility,automation,connectivity,remotesharing, betterresourcemanagement,andthelistgoesonarejusta fewofthebenefitsofemergingtechnology.Inacountrylike India, for example, Document Verification is a very hectic process.Peopleneedtostandinqueuefortheverification and the process is very slow. As also some people submit fake documents so the employees have to be very careful while checking Documents so it becomes very time consuming, sometimes the process takes months and months. So to overcome this issue we are making our project.
Before we go into detail about how digital identity verification works, it's crucial to understand why organizations need to verify papers in the first place, whether using technology or by hand. Online document verificationhastwopurposes:a:itprotectsagainstthreats such as financial fraud and identity theft; b: it aids in industry widelegalcompliance.
Accordingtoresearch 2020IdentityFraudStudy:Genesis oftheIdentityFraudCrisispublishedon07April2020By KristaTedder,andJohnBuzzard,theoveralldamagefrom identityfraudin2020isexpectedtobearound$16.9billion. Theftofidentitiescausesmorethansimplyfinanciallosses; italsoleadstosexual,racist,andgender relatedcomments onsocialmedia,whichcanbringaslewofproblems.
Theglobalepidemicofcovid 19hasincreasedoverallonline transactionsand digital banking,aswell asthenumber of digital fraud and identity theft cases, causing more harm than good. Banks and financial institutions are investing heavilyinAI basedidentityverificationsystemstocombat thisformoffraud.
The section presents the existing work done for the verificationsystemrelatingtomulti formatdocumentanda GenericCertificateVerificationSystem
In December 2020 a paper was published by Rajapakshe, Madura & Adnan, Muammar & Dissanayaka, Ashen & Guneratne, Dasith & Yapa Abeywardena, and Kavinga. (2020).
Theauthorpresents thewidespreaddistributionofbogus documentspurportingtobefromofficialsourcesonsocial media has increased public distrust and doubt. Currently, there is no easily accessible technique of document verification that the general public may use. Using digital signaturesandBlockchain,thisstudypresentsamechanism for multi formatdocument verification. To sign document contents extracted using Optical Character Recognition (OCR)technologies,authorsusedigitalsignaturealgorithms and convert the signature into a 2D barcode format. This code can then be used to extract the digital signature of a shared document, and OCR can be used to validate the signature. Furthermore, the authors offer an alternate method of verification in the form of forgery detection systems. These signed documents are maintained in a blockchain baseddecentralizedstoragesolution,increasing thesolution'soverallreliabilityandsecurity.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Obilikwu, Patrick, Usman, Karim, Dekera, Kenneth, and Kwaghtyo, Dekera published a paper in October 2019. (2019).
One of the most crucial documents for a graduate is the certificate granted by educational institutions. Certificate verificationisrequiredtoensurethatthecertificateholderis realandthatthecertificateisissuedbyatrustedsource.On theotherside,verifyingcertificationsisdemandingworkfor theverifier(theprospectiveemployerwhowantstoverify the certificate). A Certificate Verification System for Institutions(CVSI)isbeingdevelopedtoaddressthisissue, anditusesa Top DownDesigntechniqueandaniterative paradigm. A NoSQL database (MongoDB) is used for certificatestorage,whilePHPisusedforfront enddesign. Table1summarisestheoutlineofthepublicationsthatwere examined.
Understandingtheimportanceofdocumentverificationfor almost every official tasks; motivated us to choose this modeltoworkwith.Whiledrivingortraveling,wehaveto give our documents to authorized persons, and it takes a longtimeforthemtoverifythemandreturnthemtous.Asa result,wedecidedtoautomatethistaskbecauseweuseiton aspecificportal,butanyorganizationcanuseitwherever theywant,dependingontheirneeds.Section3outlinesthe workingarchitectureoftheproposedmodel.
Thissectionhighlightstheworkingofthemodel“document Verification Portal” docVP foruserDocumentVerification Portal uDVP.TheuDVPacceptsthedocumentsandverifies their authenticity with the decision parameters (dp) as formulatedintheequation(1)andequation(2).
uDVP Docupload +Docverification Eq.1) (Eq.2)
Asoutlinedinfigure1,themodeldisplaystheUserInterface that shows the front page of the website, which includes basicinformationaboutthewebsite,acontactsection,anda service section that offers a few document verification relatedservices.
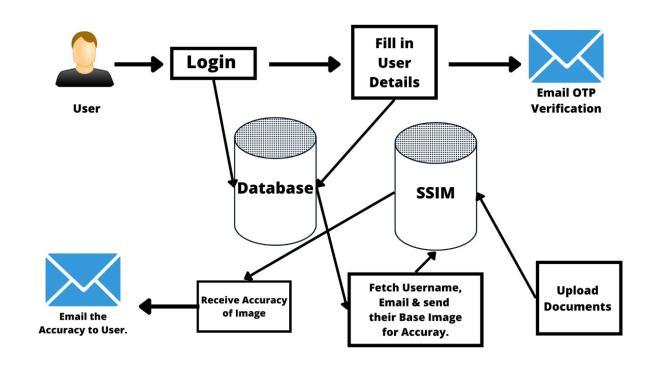
Themodelworksinthreestages(refertofigure2):
StageI:Registration/Login
StageII:EmailverificationandDocumentuploading
StageIII:Documentverificationagainstthevaliddocument
For the new user, the work flow initiates with the registrationprocessfollowedbytheloginprocesswherein authentic users can access the system with valid login credentials.
Onceauserhassuccessfullyloggedin,theuploadprocess ofstageIIstartsaslistedbelow
Basicdetailsareenteredintothesystem
{FirstName,LastName,ContactNo,DateofBirth}
UserenterstheemailidtogettheOTPontheirmailfor mailverification.
Theuseruploadsthedocuments{PANand/orAadhar card}forverification
InStageIII,oncetheuseruploadsthedocumentandsubmits it;thesystemperformsthefollowingtasks:
Fetchtheusernameandtheverifiedemail idbasedon theinputgiven
Thebaseimageispulledoutandiscomparedwiththe uploadedimage.
Theaccuracyoftheimageissharedthroughemailto theuser.
The method is based on notions of computer vision. ComputervisionisanareaofAIthatteachescomputershow to evaluate and comprehend images. Machines use digital imagesfromcamerasandwebcams,aswellasdeeplearning models,toreliablydistinguishandclassifyobjects,andthen respond to what they "observe." Computer vision tasks include methods for getting, processing, analyzing, and comprehendingdigitalimages.
Inimageprocessing,computervisionisprimarilyconcerned with enhancing or preparing raw input images for use in other applications. Computer vision is concerned with gatheringdatafrominputimagesorvideostocomprehend themthoroughlyandpredictingvisualinputinthesameway thatthehumanbraindoes.
Isthegreyscaleconversionoftheinputandoriginalphotos required?Becausemanyapplicationsinimageprocessingdo notassistusinidentifyingtheimportance,edgesofcolored imagesandcoloredimagesareabitcomplextounderstand bymachinebecausetheyhavethreechannelswhilethegrey
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Obilikwu, Patrick & Usman, Karim & Dekera, Kenneth & Kwaghtyo, Dekera
Agenericcertificate verificationsystemfor Nigerianuniversities
Top DownDesign approachwithiterative model
Rajapakshe, Madura & Adnan, Muammar & Dissanayaka, Ashen & Guneratne, Dasith & Yapa Abeywardena, Kavinga
Certificate verification is a difficult task for the verifier (the prospective employer who wants to verifythecertificate).
CertificateVerificationSystemforInstitutions(CVSI) is developed, which employs a Top Down Design methodandaniterativemodel.
ThesystemstorescertificatesinaNoSQLdatabase (MongoDB)andusesPHPforthefront enddesign.
ThesystemconsistsofaDigiVault[DigitalStorage] website that may be linked to several government ministries.
Documents generated are digitally signed and authenticated by the website's government authoritieswhoareauthorizedtodoso.
Public Key Infrastructure is used to implement documentdigitalsignatures.
Digitalsignature algorithms
Using digital signatures and blockchain, this study presents a mechanism for multi format document verification.
Digital signature algorithms are used to sign document,contentsextractedusingOpticalCharacter Recognition(OCR)technologies
Thesignaturesarefurtherconvertedto20barcode format
(PCA)and(LDA)
This work focuses on methods to detect digital forgeries based digital pixel properties in the grey level
Themaxfrequencyintensityofplanteisexecutedas thefirstmethodandtheedgegradientasthesecond one tofindsome variance between thefolgeryand theoriginalonethencanbedetected
scalehasonlyone,Inimageprocessinginaccuracy,changing photostogreyscaleisparticularlyadvantageous.
Then we must compare the two photographs using the StructuralSimilarityIndex(SSIM).Asaresult,theStructural SimilarityIndex(SSIM)isaperceptualmetricforevaluating image quality degradation due to processing such as data compression or transmission losses. This metric is essentiallyafullreferencethatnecessitatestheuseoftwo photos from the same shot, i.e. two graphically identical images to the naked eye. The second image is usually compressed or of a lower quality, which is the index's purpose.
Structural Similarity Index (SSIM) is most commonly associated with the video business, although it also has a largepresencein photography. SSIM isusedto determine the perceptual difference between two similar photos. It can'tdistinguishwhichofthetwoisbetterbecauseitdoesn't know whichisthe original andwhichhas beenprocessed furtherwithcompressionorfilters.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Figure 2:uDVPwork flow

We'lldiscusswhatthismodel'srequirementsareinthispart, its system architecture, and the required technologies to create it. There are several software used in the project, Pythonistheprogramminglanguageusedforprogramming. Front end technologies and relevant frameworks were employedfortheGUI(GraphicalUserInterface).
Themodel'sworkingstepsareasfollows:(refertofigure3)
Step 1 Importnecessarylibraries
Step 2 Uploadtheoriginal andmodifieddocumentsfrom thewebsiteorlocalfilesonthecomputer
Step 3 Reduce the size of the changed image by scaling downthesourceimage.
Step 4 Readoriginalandtamperedimage
Step 5 Convertinganimageintoagreyscaleimage
Step 6 To compare the two images, the Structural SimilarityIndex(SSIM)approachisused.
Step 7 CalculateThresholdandcontours
Step 8 - Onimages,usersshouldseereal timecontoursand thresholds.
TheSSIMindexiscalculatedusingseveralimagewindows. ThedistancebetweentwoN*N sizedwindowsxandyis:
where,
Lthedynamicrangeofthepixel values(2#bits/pixel 1)
k1=0.01andk2=0.03(default)
TheSSIMvaluesrangefrom1to+1,with1indicatingthat thetwoimagesareidentical.Aslidingwindowofsize1111 andacircularlysymmetricGaussianweightingfunctionare used in the usual approach for calculating SSIM. The maximal/minimalSSIMimagessynthesizedalongtheequal MSEhypersphereinthespaceofallimagesareshowninthe followingexample.TheMSEvaluesofallimagesalongthe hypersphere are the same as the reference image, yet the perceivedqualityissubstantiallydifferent.

Image quality assessment is critical in digital image processing applications. In this work, the metrics (MSE, PSNR,SSIM, andFSIM)are usedto determinetheoptimal quality metric. To mimic trials with Gaussian noise, we employedtheGaussianfilteringapproach.Theimagequality obtainedwasassessedusingthemetricslistedabove(refer tofigure4)
Figure3:WorkingstepsofSSIM
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Input Image(s)
Scaling Down Shape of Tampered Image
Apply SSIM method
Calculate Threshold Calculate Contours
Read Original & Tampered Image
Convert an image to greyscale
Figure4:Workingstepsofthemodel
Thediscussedsystemintheformof3activitiesispresented inthefigure5(a),5(b),and5(c)
Figure5(c):Uploadconfirmation
By using the formulas of SSIM and the methodology as described above in the mathematical model and working imagewegottheoutputinpercentagevalueasshowninthe figure 6(a). The accuracy is generated through SSIM methodologyandthatvaluewillbesent inthemailtothe user.

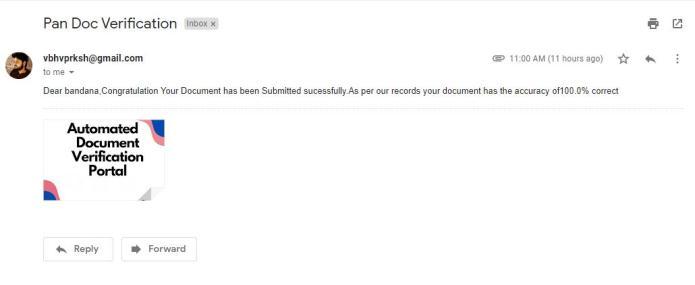
Figure5(a):Welcomescreen

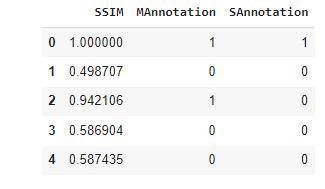
Figure5(b):Uploaddocuments
Figure6(a):Verificationaccuracy
To test the model, we created a manual dataset with two annotationvalues S Annotation and M Annotation. (refer tofigure6(b))
S Annotation Actual Value; M Annotation Predicted Value
Figure6(b):Annotations
By using these two annotation values we generated a confusionmatrix(refertofigure6(c)). Theconfusionmatrix produced four results, each representing a distinct mix of ActualandPredictedvalues.
Factor value: 7.529 | ISO 9001:2008 Certified Journal
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

TP: True Positive:Valuesthatwerebothtrulypositiveand projectedtobepositive.
FP: False Positive:Valuesthatweregenuinelynegativebut were incorrectly expected to be positive. Type I Error is anothernameforit.
FN: False Negative: Positivereadingsthatwereincorrectly forecastedasnegative.TypeIIErrorisanothernameforit.
TN: True Negative: Values that were both genuinely negativeandprojectedtobenegative.
[1] Mahdian, B., and Saic, S.: ‘Blind methods for detecting image fakery’,IEEE Aerospace and Electronic Systems Magazine,2010,25,(4),pp.
[2] Maintz, T.: ‘Digital and medical image processing’, UniversiteitUtrecht,2005
[3]Farid,H.;Lyu,S.Higher orderWaveletStatisticsandtheir ApplicationtoDigitalForensics.InProceedingsoftheIEEE Conference on Computer Vision and Pattern Recognition, CVPR,Madison,WI,USA,6 22June2003;p.94.
[4]Thakur,R.;Rohilla,R.Recentadvancesindigitalimage manipulationdetectiontechniques:Abriefreview.Forensic Sci.Int.2020,312,110311.[CrossRef]
[5]Li,J.;Li,X.;Yang,B.;Sun,X.Segmentation BasedImage Copy Move Forgery Detection Scheme. IEEE Trans.Inf. ForensicsSecur.2015,10,507 518.
[6]Y.Wu,X.Kong,andX.You,“Printerforensicsbasedon documentsgeometricdistortion,”inProc.200916thIEEE Int. Conf. Image Processing (ICIP 2009), pp. 2909 2912, IEEE,Piscataway,NewJersey(2009).
[7] C. Schulze et al., “Using DCT features for printing techniqueandcopydetection,”Adv.DigitalForensics306, 95 106(2009).
[8] D. Lee and S. Lee, “A new methodology for grey scale charactersegmentationandrecognition,”inProc.Int.Doc.
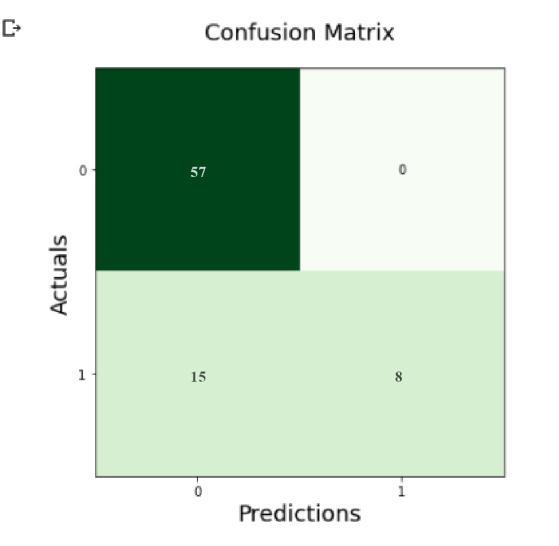
Figure6(c):Confusionmatrix
Whenthevalueintheconfusionmatrixis[1,1]itissaidtobe TruePositives.Similarly,whenthevalueis[0,0]itisTrue Negatives, when thevalue is[0,1] itis FalsePositivesand whenthevalueis[1,0]itisTrueNegatives.Asitisobserved from the figure 6(c), docVP model produces more true positives.
Thediscussedmodelcanbeenhancedfurther,aspresently, we need to have a base image and SSIM needs the image structure, pixels, and luminous to be the same when we comparetwoimages.
The working of this system is mainly based on Computer VisionandSSIM(StructuralSimilarityIndex).Theoutcome ofthedocumentverificationisgeneratedaccordingtothe document uploaded by the user. The document is being comparedtotheoriginaldocumentsubmittedbytheadmin thenthedocumentuploadedbytheuserisbeingcompared to the original picture to get the accuracy and if the documentwhichisbeinguploadedbytheuserhasaccuracy greaterthan70%thenthedocumentgetsverified.
[9]C. H. Lampert and T. M. Breuel, “Printer technique classification for document counterfeit detection,” in Int. Conf. Comput. Intell. Secur.ICCIAS, pp. 639 644, IEEE, Piscataway,NewJersey(2006).
[10]R.Bertrandetal.,“Asystembasedonintrinsicfeatures for fraudulent document detection,” in Proc. Int. Conf. Document Analysis and Recognition, ICDAR, pp. 106 110,IEEE,Piscataway,NewJersey(2013).
Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal