Message Camouflage in an Image using EDGE-Based Steganography
Akkimsetti Mohana Sai Chandra
ofthesteganographyalgorithmdependson the pixel selection. Noisy pixels are considered ideal as
Certified Journal | Page942
p
1.1 Literature Review
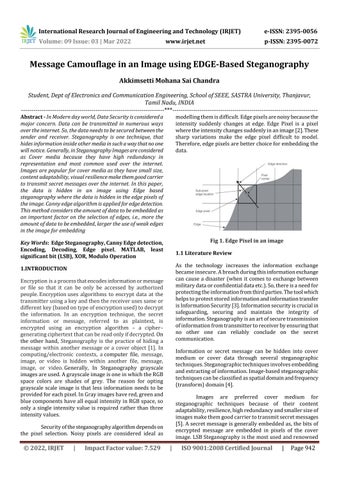
Fig 1. Edge Pixel in an image
***
Key Words: Edge Steganography, Canny Edge detection, Encoding, Decoding, Edge pixel, MATLAB, least significant bit (LSB), XOR, Modulo Operation
As the technology increases the information exchange becameinsecure.Abreachduringthisinformationexchange can cause a disaster (when it comes to exchange between militarydataorconfidentialdataetc.).So,thereisaneedfor protectingtheinformationfromthirdparties.Thetoolwhich helpstoprotectstoredinformationandinformationtransfer isInformationSecurity[3] Informationsecurityiscrucialin safeguarding, securing and maintain the integrity of information.Steganographyisanartofsecuretransmission ofinformationfromtransmittertoreceiverbyensuringthat no other one can reliably conclude on the secret
© 2022,
Securityvalues.
International Research Journal of Engineering and Technology (IRJET) ISSN: 2395 0056
1.INTRODUCTION
| ISO
e
Abstract In Modern day world, Data Security is considereda major concern. Data can be transmitted in numerous ways over the internet. So, the data needs to be secured betweenthe sender and receiver. Steganography is one technique, that hides information inside other media insuch a way that no one will notice. Generally, inSteganography Images are considered as Cover media because they have high redundancy in representation and most common used over the internet. Images are popular for cover media as they have small size, content adaptability, visual resilience make themgoodcarrier to transmit secret messages over the internet. In this paper, the data is hidden in an image using Edge based steganography where the data is hidden in the edge pixels of the image. Canny edge algorithm is applied for edge detection. This method considers the amount of data to be embedded as an important factor on the selection of edges, i.e., more the amount of data to be embedded, larger the use of weak edges in the image for embedding
Encryptionisaprocessthatencodesinformationormessage or file so that it can be only be accessed by authorized people.Encryptionuses algorithms to encrypt data at the transmitterusingakeyandthenthereceiverusessameor differentkey(basedontypeofencryptionused)todecrypt the information. In an encryption technique, the secret information or message, referred to as plaintext, is encrypted using an encryption algorithm a cipher generatingciphertextthatcanbereadonlyifdecrypted.On the other hand, Steganography is the practice of hiding a message within another message or a cover object [1]. In computing/electronic contexts, acomputer file, message, image, or video is hidden within another file, message, image, or video.Generally, In Steganography grayscale imagesareused.AgrayscaleimageisoneinwhichtheRGB space colors are shades of grey. The reason for opting grayscale scale image is that less information needs to be providedforeachpixel.InGrayimageshavered,greenand bluecomponentshaveallequalintensityinRGBspace,so only a single intensity value is required rather than three intensity
| Impact
Student, Dept of Electronics and Communication Engineering, School of SEEE, SASTRA University, Thanjavur, Tamil Nadu, INDIA
message can be hidden into cover medium or cover data through several steganographic techniques.Steganographictechniquesinvolvesembedding andextractingofinformation.Image basedsteganographic techniquescanbeclassifiedasspatialdomainandfrequency (transform)domain[4]
Volume: 09 Issue: 03 | Mar 2022 www.irjet.net ISSN: 2395 0072 IRJET Factor value: 7.529 9001:2008
Informationcommunication.orsecret
Images are preferred cover medium for steganographic techniques because of their content adaptability,resilience,highredundancyandsmallersizeof imagesmakethemgoodcarriertotransmitsecretmessages [5].Asecretmessageisgenerallyembeddedas,thebitsof encrypted message are embedded in pixels of the cover image.LSBSteganographyisthemostusedandrenowned
modellingthemisdifficult.Edgepixelsarenoisybecausethe intensity suddenly changes at edge. Edge Pixel is a pixel wheretheintensitychangessuddenlyinanimage[2].These sharp variations make the edge pixel difficult to model. Therefore,edgepixelsarebetterchoiceforembeddingthe data.
Steganographictechnique.LSBsteganographyistechnique in which the least significant bit of the pixels is used for embeddingthesecretinformation.LSBsteganographycan befurtherclassifiedasLSBreplacementandLSBmatching [7].InLSBreplacementtheleastsignificantbitofeachpixel of cover image is replaced by next bit of secret message, whereasinLSBmatchingthepixelvalueofcoverimageis randomlyincreasedordecreasedby1exceptatboundary pixelsifanymismatchoccursbetweenleastsignificantbit andsecretmessage[8].Edgeadaptiveimagesteganography is another technique based on LSB matching which calculatesthedifferencebetweentwoadjacentpixels.Ifthe differenceisgreaterthanthepredefinesthresholdthenboth pixels are marked as edge pixels, then one bit of data is hidden in each of them. But the major limitation of this techniqueisiftheimageis smooththendetectionofedge pixelswillbedifficult.
Journal | Page943
Prewitt Algorithm:PrewittalgorithmissimilartotheSobel algorithm, but the difference is the source image point is convolved with two 3x3 kernels vectors to obtain the horizontal and vertical derivatives. By using the “EDGE” functioninMATLABandthePrewittalgorithmresultsina binary image where bit 1 corresponds to edges and bit 0 corresponds to non edges. Prewitt operator is the best operatortodetecttheorientationofanimage,butdiagonal directionpointscan’tbedetermined.
Laplacian of Gaussian Algorithm (log) and Zero Crossing Edge detection Algorithm: LaplacianofGaussianAlgorithm (log)isdifferentfromtheSobel,Prewittasitdoesnotuse thegradientofintensityvalues(liketheotheredgedetection techniques),insteadituseszerocrossingtechnique.Initially, Gaussianfunctionisemployedtominimizetheeffectofnoise and smoothness. Then the Laplacian of the resultant is calculated.IfanysignchangeoccursintheLaplacian,wecan concludethatanedgeisdetected,inotherwordswhenthe Laplacian crosses zero then an edge is detected and the resultantbinaryimagehasahighvalue ‘1’inthatpointto indicatetheedge.Iftheintensitygradientstartsincreasing or decreasing then the zero crossing reports an edge, and thismayhappenatplaceswhicharenottrueedges.So,the logmethodusesotheralternativemethosforedgedetection. One such method is utilizing threshold of the log value so thatavaluehigherthanthethresholdwouldreportanedge. There is a chance of multiple edges are being detected. Anothermethodbycomparingthepixellogvaluewiththat of its adjacent pixels and choosing those points that are havinglesserlogmagnitudethanthatofitsfourneighboring points. But there is a risk of missing few edges in this technique.
| ISO
Canny Edge Detection Algorithm: Thecannyalgorithmis one of the most famous and most used edge detection techniquesasitislesspronetothenoise.Inthisalgorithm, convolutionoforiginalimagewithGaussianfiltereliminates theeffectofnoise[12].Theresultantimageisthenutilized tocalculatetheintensitygradient andthedirection ofthe gradientbasedonthegradientangle.Ifthestrengthofthe intensity at that point is higher than that of its adjacent pointsalongthedirectionofthegradientthentheedgecan be pointed out on the image. This algorithm employs two thresholdvalues thehighervaluetoincludethetruegenuine edgesandthelowervaluetotracetheverysmalldetailsof
©
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
p ISSN: 2395 0072 2022, IRJET Impact Factor value: 7.529 9001:2008 Certified
Sobel’s algorithm: Whenthereisachangeintheintensity valueoftheimagepixel,thentheedgecandetect.Thereare several techniques to detect an edge. Sobel is one of the formeredgedetectiontechniques,whichusesthegradientof the image intensity to detect edge. In this algorithm or technique,theimageintensitygradientistakenateachand every point in the image. This gives the magnitude and directionofintensityoftheimage.Thenbycomparingthe resultantthresholdvalues,thepresenceofanedgecanbe determined.Sobeloperatorcanbeusedtofindthegradient oftheimageintensityvalues[10].Basically,Sobeloperator isa discretedifferentiation operator.Itisverysimpleand time efficient computation. Smooth edges can be detected very easily. But it is very sensitive to noise and not very accurate in edge detection as it needs comparison with a threshold. Thick and rough edges do not give appropriate results.
As mentioned earlier steganography can be classified into spatial and transform domain, Adaptive Steganographyisaspecialcaseofbothspatialandtransform domaintechniques.Inthespatialdomainthesecretdatais hiddeninpixelsofcoverimageusingLSBsteganography[6] This technique is widely used due to its potentiality of embedding secret information in an image with high capacity. In transform domain (frequency domain), the secretdataishiddeninthetransformedcoefficientsofthe cover image using Discrete Cosine Transform [9]. Edge detection is a technique where the edges in an image are foundoutbyusingasuitablealgorithm.Theedgewhichcan be defines as a set of pixels positions where a sudden or abrupt change of intensity values occurs. Edges represent boundariesbetweenobjectsandbackground.Edgedetection involves method of segmenting an image into regions of discontinuity. Some edge detection techniques are Sobel, Prewitt,LoG,Robert,Cannyetc.[11]
Volume: 09 Issue: 03 | Mar 2022 www.irjet.net
Roberts Edge Detection Algorithm: This technique also detectstheedgesbycomputingintensitygradientjustlike Sobel and Prewitt. Besides, this algorithm simplifies the complexityasitusesasimple2×2kernelvectorforgradient computation. In addition to this, every pixel gradient intensity is compared only with that of those diagonally adjacentpixels.So,itsmaindisadvantageisthatsinceituses such a small kernel, it is very sensitive to noise. Diagonal directioncanbepreservedbythistechnique
1.2 Classic Edge Detection Techniques
|
LOG 262,144 18,220
Algorithm Total Pixels Edge Pixels (Average)
6.
Certified Journal | Page944
4.
Canny 262,144 23,818
Fig 2.1 RGB Image Fig 2.2 Grayscale Image
theimage.Hence,thecannyedgedetectionalgorithmgivesa moreaccurate,elaborateanddetailedbinaryimage.
values
Theimageinwhichthesecretmessagewillbeembedcabe referredasCoverImage.Inthistechnique,thepreprocesses allwillbedoneonthecoverimage.Atfirst,boundarywillbe tracedforthecoverimageandthentheedgepixelswillbe detectedusingCannyalgorithm.TheCoverimageisinitially converted into grayscale image. The secret message or information will be embedded into the edge pixels of the coverimage,soanedgedetectionalgorithmwillbeapplied tocoverimagesoastodetecttheedgesinthecoverimage. Canny edge detection will be considered among other algorithm (from Table 1) since it can detect a greater number of edges compared to other algorithms. Canny detectionusesconvolutionoforiginalimagewithGaussian filtereliminatestheeffectofnoise,soitismoreresistantto noise.
International of Technology (IRJET) ISSN: 2395 0056
e
Thestegoimagewillbesentoverinternetfromtransmitter toreceiver.Atthereceiver’sendthesecretmessageshould be retrieved back. The message will be retrieved back by computingmodulo2 operations (remainder)between the stegoimagepixelsvalues.Thiswillresultinbinaryformatof thesecretmessage,whichcanbeconvertedintocharacters using‘bin2dec’function.
Volume: 09 Issue: 03 | Mar 2022 www.irjet.net ISSN: 2395 0072 2022, IRJET Impact Factor value: 7.529 9001:2008
3. temp=double(xor(LSB,a));
Engineering and
|
2. METHODOLOGY
8.7.
1. %ReadinoriginalRGBimage. rgbImage=imread('godavari1.jpg'); subplot(2,2,1); imshow(rgbImage) axis('on','image'); title('OriginalImage')
1. LSB=mod(cover(i,j),2);
©
detected
2.
2. a=str2double(binary_all(count));
Toembedthedataintoimage,thedatamustbeinbinaryto perform XOR operation. So, initially the data will be convertedintobinarydatausingASCIIvaluesforcharacters andthendecimaltobinaryconversion,whichgivesbinary data for the secret message. XOR operation will be performedbetweentheedgepixelvalueofcoverimageand binarydataofsecretmessage.TheresultantXORvaluewill beaddedtothepixelvalueofStegoimage.Stegoimagewill beformedformtheresultantofcoverimagepixelvalueand secretmessagedata.
Sobel 262,144 8,451
p
| ISO
9.
Table1. Comparison of pixels of
different algorithms
Prewitt 262,144 8,407
4. stego(i,j)=cover(i,j)+temp;
2.1 Algorithm Implementation
%Converttograyscale. grayImage=rgb2gray(rgbImage); subplot(2,2,2);
3.
Research Journal
Fig.4 Message Retrieving process from the Stego Image
5.
Fig.3 Message Hiding into Edge pixel process
10.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056 Volume: 09 Issue: 03 | Mar 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page945 11. imshow(grayImage) 12. axis('on','image'); 13. title('GreyScaleImage') 15.14. %Getedges 16. Canny_img=edge(grayImage,'Canny'); 17. %Canny_img=cannydetector(grayImage); 18. subplot(2,2,3); 19. imshow(Canny_img,[]) 20. axis('on','image'); 21. title('EdgeDetectedImage') Code 1. Canny Edge Detection on the Cover Image 1. ======%==================================== 2. %Encodingthemessage 3. ======%==================================== 4. ascii=uint8(message); 5. binary_separate=dec2bin(ascii,8); 6. binary_all=''; 7. fori=1:strlength(message) 8. binary_all=append(binary_all,binary_separate (i,:)); 9. end 10. count=1; 11. fori=1:row 12. forj=1:column 13. ifcount<=len 14. LSB=mod(cover(i,j),2); 15. a=str2double(binary_all(count)); 16. temp=double(xor(LSB,a)); 17. stego(i,j)=cover(i,j)+temp; 18. count=count+1; 19. end 20. end 21. end 22. imwrite(stego,'Stego_Image.jpg'); Code 2. Message Hiding into the edge pixels Implementation 1. ======%==================================== 2. %Decodingthemessage 3. ======%==================================== 4. message_in_bits=''; 5. fori=1:row 6. forj=1:column 7. ifcount<=len 8. LSB=mod(stego(i,j),2); 9. message_in_bits=append (message_in_bits, num2str(LSB)); 10. count=count+1; 11. end 12. end 13. end 14. i=1; 15. original_message=''; 16. whilei<=len 17. original_message=append(original_message,char (bin2dec(message_in_bits(1,i:i+7)))); 18. i=i+8; 19. end Code 3. Message decoding from the edge pixels Implementation
|
REFERENCES
e ISSN: 2395 0056
p ISSN: 2395 0072 2022, IRJET Impact Factor value: 7.529 ISO 9001:2008 Certified
International Research Journal of Engineering and Technology (IRJET)
Metrices Results
PSNR 39.4363
Table 2.1 Test Image godavari1.jpg (2816 x 2112)
Fig 5. Cover Image
[3]. Rupali Bharadwaj, Vaishali Sharmab. “Image Steganography Based on Complemented Message and InvertedbitLSBSubstitution”.
|
[2].R.Amritharajan,Akhila R,P.Deepikachowdaarapu. “A computerAnalysisofImageSteganography”,International JournalofComputerApplications,May2010.
Journal | Page946
MSE 7.4037
[1]. Rengarajan Amritharajan, Benita Bose, Sasidhar ImadbathuniandJohnBoscoBalaguruRayappan.“Security BuildingattheLineofControlofImageStego”,International JournalofComputerApplications,2010.
Fig 6. Edge Detection Image
Volume: 09 Issue: 03 | Mar 2022 www.irjet.net
whereXij isStegovalueandYij isthecoverobject.
ThePSNRiscalculatedusingtheequation
Fig 7. Final Image with Message hidden
where“I”istheintensityvalueofeachpixelwhichisequalto 255 for 8 bit gray scale images. Higher the value of PSNR bettertheimagequality
TheMSEiscalculatedbyusingtheequation,
©
SNR 23.4931
3. RESULTS AND CONCLUSIONS
The message is hidden/camouflaged into an image using edge detection and XOR operation. Here Canny edge detectionalgorithmisusedforedgepixeldetection Output Image(Stegoimage)pixelsvaluesaremodifiedbasedonthe XOR operation between cover image pixels and secret message data. Large data can also be embedded into an imageusingthistechnique.
Fig5isthegiveninputimage,thecorrespondinggrayscale imageisgeneratedandreferencedasCoverimageinFig6 AftertheembeddingthemessageintotheCoverimagethe resultantStegoImage,Fig7isgeneratedwhichisusedfor transmissionovertheinternet.AtthereceiversidetheStego imageistakeasinputandthemessageisretrievedusingthe decryption process. In this present implementation, two imagesgodavari1.jpgof2816x2112pixelsandlena512.jpg of512x512pixelscolordigital imageshasbeentaken as cover image, tested for full embedding capacity and the results are given. The effectiveness of the proposed Steganography technique has been studied by calculating MSEandPSNRforthemessage‘SASTRAUNIVERSITY’
Entropy 0.9125
[7]. Ramandhan J. Mastafa, Chrostian Bach. “Information hiding in Images using Steganography Techniques”, Northeast Conference of the American Society of the AmericanSocietyforEngineeringEducation(ASEE),2013.
[9]. Reem Abdulrahman Alomirah. “An Edge based Steganography Algorithm for Hiding text into images”, Unitech Institute of Technology, Auckland, New Zealand, [10].2019.M
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
[8].RupaliRoy.“ImageSteganographyusingPython”,May7, 2020.
| ISO
Saritha, Vishwanath M Khadabdi, M Sushravya. “Image and text Steganography with Cryptography using MATLAB”, International Conference on Signal Processing, Communication, Power and Embedded System (SCOPES), 2016.
[12]. Paul bao, Lei Zhang and Xiaolin Wu. “Canny Edge Detection Enhancement by Scale Multiplication”, IEEE TransactionsonpatternanalysisandMachineIntelligence, Vol27,No9,September2005
[4].JhilikGuha,OrchiSaha,RiyaRoy.“Improvededge based ImageSteganographicTechnique”.
©
[5].SaifulIslam,MangatRModi,PhalguniGupta.Edge based Image Steganography. EURASIP Journal of Information Security,2014.
Certified Journal | Page947
|
Volume: 09 Issue: 03 | Mar 2022 www.irjet.net p ISSN: 2395 0072 2022, IRJET Impact Factor value: 7.529 9001:2008
[6].Ismail KICH,ElBachirAMEUR,YoussefTaouil.“Image Steganography on Edge Detection Algorithm, IEEE, 2018 InternationalConference.
[11].LarryS.Davis.“Asurveyofedgedetectiontechniques”, ComputerGraphicsandImageProcessing,Volume4,Issue3.