
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 06 | Jun 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 06 | Jun 2024 www.irjet.net p-ISSN: 2395-0072
Suryaprakash Nalluri1, Karanpreet Kaur2
Abstract - The adoption of open-source libraries in software development has revolutionized the industry, offering significant benefits such as reusability, reduced costs, and accelerated development cycles. However, this practice also introduces a variety of security risks and challenges, particularly concerning the software supply chain. This paper explores the benefits and risks associated with open-source library ingestion, examines various ingestion patterns, and discusses specific attacks targeting this process. It also highlights the motives behind these attacks and their potential impact on organizations. Additionally, the paper outlines best practices to combat supply chain issues, ensuring the security and integrity of thesoftwaredevelopmentpipeline.
Key Words: Security, vulnerability, Software Supply chain, risk, Open-Source library ingestion, DevSecOps
In recent years, the proliferation of open-source libraries has revolutionized software development, offering developers a treasure trove of pre-built components and frameworks to expedite the creation of innovative applications. This paradigm shift towards open-source adoption not only fosters rapid application development but also promotes reusability, reduced risk, and collaboration within the developer community. However, amidst the convenience and flexibility offered by opensource libraries lies a complex landscape of supply chain risks that demand careful consideration. This article delves into the critical domain of open-source library ingestion, exploring the process of integrating third-party libraries into software projects and the associated supply chainrisks.
Theadoptionofopen-sourcelibrarieshastransformedthe software development landscape, offering developers a vast repository of reusable components and frameworks. This section provides an overview of the evolution of open-source libraries and their impact on software developmentpractices.
Therootsofopen-sourceculturecanbetracedbacktothe earlydays ofcomputing, notablywith the development of
Unix in the 1970s. Unix's open design and collaborative development model laid the groundwork for the ethos of sharing and collaboration that underpins modern opensource development. In the 1990s, the emergence of programminglanguagessuchasJavafurtherpromotedthe adoption of open-source practices by providing platforms and frameworks that encouraged code reuse and communitycontributions.Additionally,theproliferationof the internet facilitated global collaboration and acceleratedthegrowthofopen-sourcecommunities.
TheadoptionofAgilemethodologiesandDevOpspractices in software development has further accelerated the uptakeofopen-sourcelibraries.Agile'semphasisonrapid iteration and customer feedback, combined with DevOps' focus on automation and collaboration, align seamlessly withtheprinciplesofopen-sourcedevelopment,fostering acultureofcontinuousimprovementandinnovation.
The advent of collaboration platforms such as GitHub, SourceForge, GitLab, and Bitbucket has democratized access to open-source code, providing developers with robust tools for version control, issue tracking, and collaborativedevelopment.Theseplatformsserveashubs for sharing, discovering, and contributing to open-source projects, fueling the growth of vibrant developer communities, and fostering innovation across diverse domains.
Open-sourcelibrarieshavebecomeindispensabletoolsfor developers, offering a wide range of functionalities and reducing time-to-market for software projects. Numerous librariesareavailableonGitHub,includingbutnotlimited to Eureka, Hystrix, and Chaos Monkey from Netflix, TensorFlow and Angular from Google, and React from Facebook. These libraries exemplify the contributions of prominent companies to the open-source ecosystem, drivinginnovationandcollaborationwithinthedeveloper community.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 06 | Jun 2024 www.irjet.net p-ISSN: 2395-0072
The integration of open-source libraries into software projectsoffersseveralbenefits:
Accelerated Development: Open-source libraries provide ready-made solutions for commonprogrammingtasks,allowingdevelopers to focus on implementing unique features and functionalities.
Enhanced Functionality: By leveraging existing libraries, developers can incorporate advanced features and capabilities into their applications withoutreinventingthewheel.
Reduced Development Costs: Open-source libraries are often available free of charge or at a nominal cost, significantly reducing the financial burdenofsoftwaredevelopment.
Community Support: Many open-source libraries are backed by vibrant developer communities that provide support, documentation, and contributions, enhancing the qualityandreliabilityofthecodebase.
Open-source libraries are typically ingested into software projects through various patterns, each with its own implications for security and maintenance [3]. Common ingestionpatternsinclude:
Direct Usage: Developers manually download and incorporate open-source libraries into their projects without relying on any automated tools orpackagemanagers.Whiledirectusageprovides developers with maximum control over library versions and configurations, it also increases the risk of overlooking security updates and introducespotentialvulnerabilitiesduetomanual oversight.
Opensource Package Managers: Package managers such as npm for JavaScript, pip for Python, Maven for Java, and NuGet for .NET offer centralized repositories of open-source libraries, making it easy for developers to discover, install, and manage dependencies. Package managers automate dependency resolution and version management, streamlining the ingestion process and facilitating consistent updates. However, relianceonpackagemanagersalsointroducesthe risk of downloading malicious or outdated packagesfromuntrustedsources.
Dependency Management Tools: Dependency management tools like Gradle, Yarn, and Composer provide additional functionality for
controlling project dependencies, including specifying version ranges, locking dependencies to specific versions, and generating dependency trees. These tools enable finer-grained control over dependency resolution and allow for more sophisticated strategies to address security and compatibility concerns. However, managing dependencies at this level requires a deeper understanding of library interactions and may increasecomplexityforlargerprojects.
Despite the advantages of using open-source libraries, severalchallengesmustbeaddressedtoensuresuccessful integrationandmaintenance.Thesechallengesinclude:
Compatibility Issues:
Problem: Integrating third-party libraries into software projects can introduce compatibility issues with the existing codebase, frameworks, or dependencies, leading toruntimeerrors,conflicts,orunexpectedbehavior.
Mitigation: Careful testing and validation are required to ensure compatibility, often involving automated testing frameworks and continuous integration systems to detect andresolveconflictsearly.
Licensing Concerns:
Problem: Open-source libraries are governed by various licenses, each with its own terms and conditions. Noncompliance with license requirements can lead to legal consequences and reputational damage for software projectsandorganizations.
Mitigation: It's essential to review and understand the licensing terms of each open-source library. Tools and services for license compliance, such as SPDX (Software Package Data Exchange) or FOSSA, can help manage and automatethisprocess.
Security Risks:
Problem: Open-source libraries may contain security vulnerabilities that could expose software projects to potential threats, such as code injection, cross-site scripting (XSS), or remote code execution. Vulnerabilities can arise from inadequate code review, outdated dependencies, or malicious code injections in third-party libraries.
Mitigation: Regularly updating dependencies, using tools likeDependabotorSnyktomonitorandfixvulnerabilities, and conducting security audits can help mitigate these risks.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 06 | Jun 2024 www.irjet.net p-ISSN: 2395-0072
Dependency Management Complexity:
Problem: Managing dependencies across multiple libraries and versions can be complex, especially in largescaleprojectswithnumerousinterconnectedcomponents. Dependency conflicts, version mismatches, and transitive dependencies pose challenges for ensuring compatibility andstability.
Mitigation: Dependency management tools like Maven, Gradle, or Yarn can help manage dependencies. Implementing practices like semantic versioning, using dependency lock files, and tools for visualizing dependencytreescanalsobebeneficial.
Lack of Dedicated Support:
Problem: Open-source projects are often maintained by volunteers or small teams, and their response to bug reports or feature requests may not be as prompt or process-orientedasthatofproprietarysoftwarevendors.
Mitigation: Organizations can contribute to the opensource community by sponsoring projects, submitting patches, or even hiring developers to maintain critical open-source libraries. Additionally, having internal expertise to troubleshoot and fix issues can reduce dependencyonexternalsupport.
Supply Chain Risks:
Problem: Open-source library ingestion introduces supply chain risks, including the potential for malicious actors to compromise libraries, inject backdoors, or exploit vulnerabilities. These risks can propagate through interconnected dependencies, affecting the security and integrityofentiresoftwareecosystems.
Mitigation: Implementing stringent security measures, such as code signing, verification of library integrity, and continuous monitoring for suspicious activity, can help mitigatetheserisks.
Open-source library ingestion is susceptible to specific attacks targeting the software supply chain, driven by variousmotives[5].Thefollowingoutlinesspecificattacks andtheirmitigations:
Typosquatting:
Problem: Malicious actors register domain names or package names like legitimate ones, aiming to intercept developers'typosandservemaliciouscode.
Mitigation: Usingtrustedrepositories,implementingtypo protection mechanisms, and training developers to be vigilantcanhelppreventtyposquatting.
Problem: Attackers gain control of abandoned or unmaintained repositories to inject malicious code into unsuspectingdevelopers'projects.
Mitigation: Regularly auditing dependencies, avoiding unmaintainedlibraries,andusingforksoftrustedversions canmitigaterepojackingrisks.
Problem: Some open-source projects fall under the control of malicious maintainers who intentionally introducevulnerabilitiesorbackdoorsintolibraries.
Mitigation: Conducting thorough reviews of maintainers' contributions, using trusted maintainers, and implementing community oversight can help prevent this risk.
Problem: This attack exploits the way package managers handle dependencies by tricking them into downloading malicious packages from public repositories instead of internalorprivateones.
Mitigation: Configuring package managers to prioritize internal repositories, using repository proxies, and monitoring for unexpected dependencies can mitigate dependencyconfusion.
Cyber attackers employ various tactics to compromise open-source libraries for different motives, including financial gain, malicious intent, ideological reasons, or industrialespionage.
The impact of attacks targeting open-source library ingestion can be significant and wide-ranging, including reputational damage, financial losses, data breaches, intellectualpropertytheft,andoperationaldisruption.
To effectively manage and mitigate risks associated with open-source library ingestion, developers should adhere tothefollowingbestpractices:
Thorough Vetting: Before integrating a thirdparty library into a software project, developers should conduct thorough vetting to assess its quality, reliability, and security posture. This includes reviewing the library's documentation,

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 06 | Jun 2024 www.irjet.net p-ISSN: 2395-0072
examining its codebase, and evaluating its community support and maintenance status as showninFigure1.
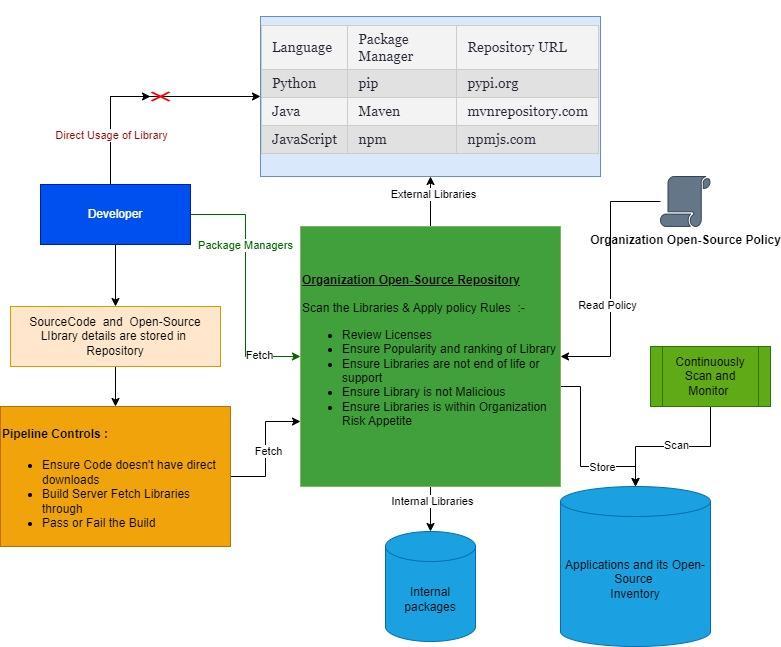
Version Control: Maintain strict version control practices to track the usage of open-source libraries within software projects. Regularly updatedependenciestoensurecompatibilitywith thelatestsecuritypatchesandbugfixes.
License Compliance: Adhere to license compliance requirements by carefully reviewing the terms and conditions of open-source licenses and ensuring proper attribution and distribution ofsourcecodeasperlicenseobligations.
Security Updates: Stay vigilant for security advisories and updates related to open-source libraries used in software projects. Implement automated tools and processes for monitoring security vulnerabilities and applying patches promptly.
Dependency Auditing: Conductregularauditsof project dependencies to identify outdated or vulnerable libraries. Utilize dependency scanning toolsandservicestoassessthesecuritypostureof dependenciesanddetectpotentialvulnerabilities.
Community Engagement: Engagewiththeopensource community to contribute back to the projects used in software development. Participateinbugreporting,featurerequests,and code contributions to foster collaboration and improvethequalityofopen-sourcelibraries.
Internal Policies: Establish internal policies and guidelines for open-source library ingestion, outlining procedures for vetting, integrating, and managing dependencies within software projects. Educate developers on best practices for open-
source usage and empower them to make informeddecisionsregardinglibraryingestion.
The integration of open-source libraries into software projects offers significant benefits, including accelerated development, enhanced functionality, reduced costs, and robust community support. However, it also introduces various challenges and security risks, particularly concerning the software supply chain. By understanding these risks and implementing best practices for vetting, managing, and maintaining open-source libraries, organizationscaneffectivelymitigatepotentialthreatsand maximizethebenefitsofopen-sourceadoption.Embracing open-source development with a proactive and informed approach ensures the security, reliability, and sustainability of software projects in an increasingly interconnecteddigitallandscape.
Perens, B., "The Open-Source Definition," Open Sources: VoicesfromtheOpen-SourceRevolution,1999.
Wheeler, D. A., "Why Open-Source Software / Free Software(OSS/FS)?LookattheNumbers!"2007.
NIST, "Cybersecurity Framework,” National Institute of StandardsandTechnology,2021.
Snyk,"StateofOpen-SourceSecurityReport,"2021.
GitHub, "Securing the Software Supply Chain: Best Practices,"2022.
FOSSA,"ManagingOpen-SourceLicensesandCompliance," 2021.