
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
G Swaroop1 , Harish Budarpu2 , Manasa B N3 , Prof. Meghashree N4
1 2 3Student Scholar, Dept. of Computer Science and Engineering, Atria Institute of Technology, Karnataka, India
4Asst.Professor, Dept. of Computer Science and Engineering, Atria Institute of Technology, Karnataka, India ***
Abstract - Computers, mobile devices, and other networks andsystemsarenotsufficientlysecureandareopentovarious cyberthreats. Every year, there are more and more cyberthreats. Vulnerability assessment is the process of locating the weaknesses in networks and systems. Vulnerability assessment aids in offering the required countermeasures to online threats. It entails identifying vulnerabilities, such as those in networks, physical systems, and applications, and evaluating the risks that come with them. This paper presents a new method for performing cyberattack analysis by utilizing penetration testing and vulnerabilityassessmenttechniques.Thesuggestedapproach makes use of a variety of Kali Linux tools, combined with an intuitive menu system and Python modules. A comparative study is conducted between the results of a major proposed approach and Kali Linux's built-in tools. Notably, the results show significant advancements in a number of critical domains,suchasinformationgathering,networkandwebsite testing, system modifications, sniffing, and spoofing. These enhancementsmakecyber-attackanalysismoreeffectiveand efficient overall and provide valuable data for more effective security measures.
Key Words: cyber security, cyber-attack prevention, vulnerability assessment, penetration testing.
Cyber-attacks and threats are defined as a broad range of actionsconductedbyindividualswhotypicallyusemalicious software to gain access to a person's or an organization's network or systems. They may even result in data loss, system crashes, and poor performance when computer systemsmalfunction.Cyberattackscanbecarriedoutfrom any location by an individual or a group. Hackers and cybercriminals are the ones who carry out these types of cyberattacks.WecanusethetoolsthatKaliLinuxprovides toaddressthesevulnerabilities.Wehavepresentedamenubasedinterfaceforvulnerabilityassessmentandpenetration testingusingPythonmodulesinthispaper.
[1] A comparison of web application automation testing tools is presented in this paper. The popular automation testing tools were chosen for this study their features, usability,performance,easeofuse,andcompatibilitywith web applications were assessed. The study's limitations includeitsnarrowfocusonwebapplicationsandthesmall
numberoftoolsitexamined.Futurestudiescaninvestigatea widervarietyofinstrumentsandexpandtheassessmentto differentkindsofapplicationsinordertogetaroundthese limitations.[2]Apaper'smainfocusisonpenetrationtesting andvulnerabilityassessment.Forthesetasks,theauthors suggest an implementation of a solution. As part of the methodology, a portable testing platform for penetration testingandvulnerabilityanalysisisdesignedanddeveloped. The paper's limitations include its particular focus on a portablesolutionanditsrequirementforadditionaltesting and validation of the recommended solution. provides a thorough examination of numerous cyberattacks. [3] The research methodology employed in this study entails a reviewandanalysisofvariouscyber-attacktypes,covering their attributes, methods, and possible consequences. [4] Thereportingandanalysisofwirelessnetworksecuritytest results using Kali Linux is the main goal of this study. Utilising Raspberry-Pi and Kali devices, experiments are conducted as part of the methodology to assess wireless networksecurity.Thestudyhasseverallimitations,suchas itsnarrowfocusonRaspberryPidevicesandtheneedfor moreextensivevalidationoftheresults.Toovercomethese limitations, even more research can compare evaluations with other security assessment methods using different hardware platforms. [5] A comparative analysis of web applicationsecurityaspectsispresentedinthispaper.Key securityparameters wereidentifiedandcurrenttrendsin web application security were reviewed as part of the research techniques. The study's shortcomings include its emphasisonparticularsecuritycriteriaandtheabsenceofa thoroughassessmentofthestate-of-the-artmethodsforweb applicationsecurity.Futureresearcherscanincludeawider rangeofsecurityparametersandcomparetheeffectiveness ofvarioussecuritytechniquesin order toovercome these limitations.[6]Thispaperprimarilyfocusesoninformation gathering and pen testing tools. Analyzing current information-gatheringmethodsandpenetrationtestingtools ispartofthemethodology. Theprimarylimitationsofthe paper are the narrow range of information collection methods discussed and the need for further empirical validation of the instruments. To overcome these constraints, future investigators can investigate supplementary data collection methods and carry out empirical investigations to verify and contrast various instruments. [7] The implementation and comparison of various password cracking tools is the main topic of this paper.Theprocessentailschoosingwell-knownpasswordcrackingsoftwareandassessinghowwellit performsand crackspasswords.Thesmallnumberoftoolsexaminedand

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
thelackofaspecificthoroughassessmentofeverypassword crackingmethodaretwooftheresearch'slimitations.
Overall, by offering insights into automated testing tools, vulnerability assessment and penetration testing, cyberattacks, web application security, information gathering,wirelessnetworksecurity,andpasswordcracking tools,thesepaperscontributetothefieldofcybersecurity. Everypaperdoes,however,havecertainshortcomingsthat shouldbeaddressedbymoreresearchinordertoadvance understandingandproviderobustsecuritysolutions.
In this specific work, we perform vulnerability research, which helps to find both new and old vulnerabilities in softwareandsystems.Thisisasignificantcontributiontoa vulnerability assessment and penetration testing tool project. Vulnerabilities can be found and exploited by developingvulnerabilityassessmentandpenetrationtesting tools, which aids in improving system security for organisations. In addition to having a thorough understanding of software and systems architecture, vulnerability researchers usually need to be familiar with commonattack vectorsand techniques.Thispapermakes three significant contributions: (i) it implements a menu driven approach; (ii) it provides accurate reports on risk assessment using custom tools; and (iii) it reduces the likelihood that the systems may be compromised. The second section explains the anticipated work on vulnerability assessment and penetration testing tools. SectionIIIpresentsthefindings,whileSectionIVclosesthe study.
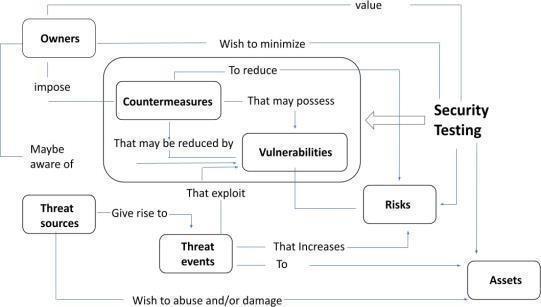
This section emphasizes on system architecture, vulnerability scanner and utilization of vulnerability assessmentandpenetrationtestingtools.
Multiplelevelsof protection are used for differentsystem componentsinthisvulnerabilityassessmentandpenetration testing system architecture. Figure 1 displays the componentsofthesystem.
Threatsources:Thesearetheentitiesthatposeapotential threat for the security issues of an organization. Threat sources can be internal or external. Identifying potential threat sources is a major part of VAPT, as that helps organizationstounderstandwheretheirsecurityriskslie.
Eventsorsituationsthatposeathreattoanorganization's resourcesorinterferewithitsregularbusinessoperations areknownasthreatevents.Databreaches,denial-of-service attacks,andmalwareinfectionsareafewexamplesofthreat
events. VAPThelpsorganizationsidentify potential threat eventsanddevelopstrategiestopreventthem.
Countermeasures: These are defences against possible threatsthatareputinplacetosafeguardanorganization's assets. Firewalls, intrusion detection systems, access controls, and security policies are a few examples of countermeasures.OrganisationscanuseVAPTtodetermine which countermeasures will work best for their specific securityrequirements.
Securitytestingistheprocessofevaluatinganorganization's securitypostureinordertospotpotentialthreatsandweak points in an attack. A variety of methods, including vulnerability scanning, penetration testing, and social engineering,canbeusedinsecuritytesting.
Vulnerabilities:Anorganization'ssecurityflawsthatcould be used by adversaries to gain access; Vulnerability Assessment and Penetration Testing (VAPT) assists organisations in proactively locating and resolving these issuestostoppotentialexploitation.
A tool named a vulnerability scanner is made to automatically find security flaws in specific networks, applications,andsystems.Byscanningthetargetsystemfor known vulnerabilities, the tool detects any flaws that an attackercouldexploit.Vulnerabilityscannersuseaspecific databaseofknownvulnerabilitiesinadditiontoavarietyof other techniques to locate and exploit vulnerabilities. Typically,thescannerhastwomodesofoperation:passive and active. In order to find and fix vulnerabilities, the scanner sends packets to the target system while it is in active mode. When in passive mode, the scanner scans a network for traffic and, mainly, uses the traffic it sees to identifyvulnerabilities.
Following the identification of every vulnerability, the scanner will produce an extensive report that clearly explains each vulnerability's characteristics, including its severity.Securityexpertswouldprimarilyusethereportto

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
scheduleandprioritiseremediationactions,asindicatedin Fig2.
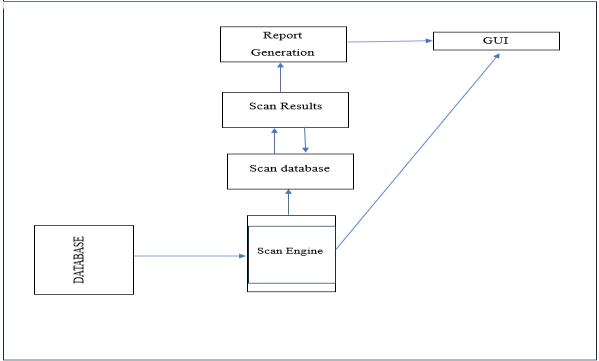
4.3. Utilization of vulnerable assessment and penetration testing.
Security experts use penetration testing and vulnerability assessment tools to identify and test vulnerabilities in computer systems, networks, and applications. Security expertsusethesetoolstoproactivelyfindandfixsecurity risksandvulnerabilitiesaswellastomakesurethesystems are safe from possible attacks. The main purpose of vulnerableassessmenttoolsistosearchcomputernetworks andsystemsforknownvulnerabilities.Automatedsystem andapplication scanswill becarried out bythese tools to find vulnerabilities.Reports detailingthe specifics of each vulnerability,suchasitsseverityandsuggestedremediation actions, will be generated. Tools for vulnerability assessmentsareoftenusedtofindholesinsystemsbefore attackers take advantage of them. Tools for penetration testing are used to mimic actual attacks on networks and systems.Penetrationtestingtoolsarecapableofdetecting vulnerabilitiesinsystemsthatvulnerabilityassessmenttools are unable to detect. They can alsoassist organizations in evaluating the effectiveness of their security controls in thwartingattacks.Figure3illustratesthestepsinvolvedin vulnerabilityassessmentandpenetrationtesting.Toolsfor vulnerability assessment and penetration testing are essential for spotting possible security threats and weaknessesthatanattacker mighthaveusedagainstyou. Through proactive identification and mitigation of these risks, organisations can decrease the probability of successfulattacksandmitigatethepotentialconsequences of diverse security incidents. All things considered, penetrationtestingandvulnerabilityassessmenttoolsare crucialpartsofanysuccessfulsecuritytestingprogramme. Organisationscouldstrengthentheirsecurityposture,lower thechanceofsuccessfulattacks,andadheretoindustrybest practicesandlegalrequirementsbyutilisingthesetoolsto findandfixvulnerabilities.
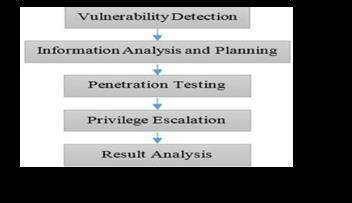
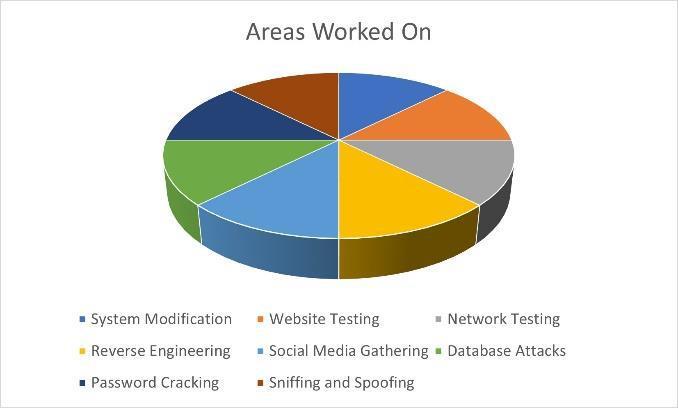
Figure 4 illustrates that, in contrast to [8], which has implemented only three areas of concern, we have implementedeightareasormodules.Themoduleswe'veput in place include information gathering, database attacks, sniffing and spoofing, website testing gathering, system alterations, password cracking attacks, and reverse engineeringtoolsareallexamplesofnetworktesting.
After comparing the results with [8], improvements were observedinmultipleareasincludingsystemmodifications, network and website testing, sniffing and spoofing, and informationgathering.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
Our application provides a wide range of categoriesfor performingpenetrationonthechosen system ornetworks identifyingvulnerabilitiesasshown below in Figure 6.Our meticulousselectionandapplicationofarangeofeffective anduser-friendlytoolshasproducedremarkable accuracy whencomparedto[8].
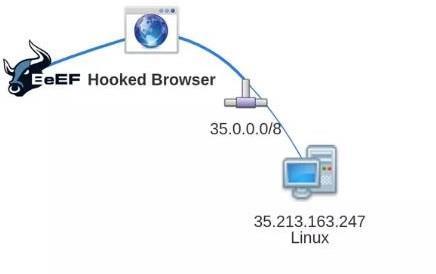
Malicious URLs can be added to the Plugin URL and a commandcanbewrittentocauseanalerttoappearonthe target'sbrowserbyutilisingBeEF,asshowninFig7.
Zenmap is a free ASCII text file programme that offers advanced options to users with experience while streamlining Nmap for novice users. To enable basic recursiveruns,scansaremaintainedasprofiles.
AwirelessassaulttoolcalledWifiteisprimarilyutilizedfor penetrationtesting.Itisreliablewhenitcomestotestinga network'sabilitytohandlepacketsandperformingwireless injections.Itistheperfecttoolfortheeffectiveoperationof thisprimarytoolbecauseofitsautomation.
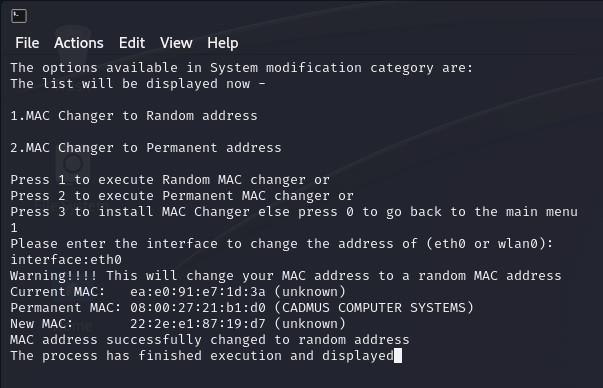
OneofthemostimportanttoolsselectedistheMACchanger, whichisdepictedinFig.8.Itprovidesanumberofoptionsfor changingsystemconfigurations,facilitatinga returntothe factorydefaultdevicesetups.
Byofferingactivepacketfilteringandmanipulation,MITMf enablesuserstoseamlesslytransitionbetweenanykindof protocolortraffic.Whilethetoolisoperating,userscanmake changes to the configuration file, and the changes will be implementedthroughouttheframework.
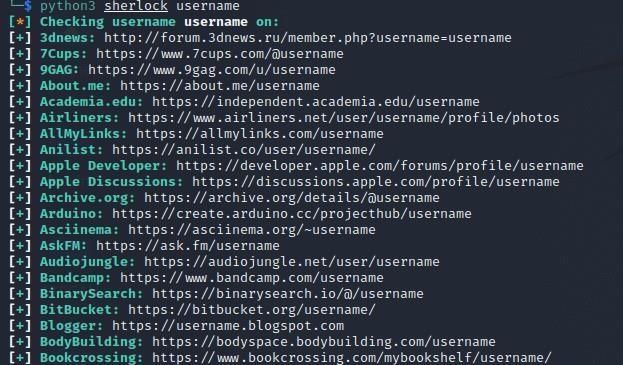
AsseeninFig.9,Sherlockisatoolforlocatingusernameson socialmediathatcanidentifymultipleaccountsmadebythe samepersonusingthesamescreennameorusername.
Osintgram is an OSINT tool primarily used for conducting reconnaissance missions and gathering, analysing, and analysinginformationaboutInstagram.
SQL injection, or SQLI, is a method that accesses data not meant for display by manipulating backend data with SQLcode.
Thisinformationincludessensitivecompanydata,userlists, andprivateclientdetails.
It has been helpful to crack passwords of various levelsof complexitywithJohntheRipper.Therearethreemodesfor JTR: progressive, word list, and single crack. The most practicalandefficientwaytocrackanentirepasswordfileis tousethesinglecrackmode.
Resources can be recreated after modifications and decrypted back to their original form using APK tools. Its automationandproject-likefilestructuremakeworkingwith supportingappseasier.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
TheZAPtoolfeaturesanintuitiveinterfaceandoffersarange of functionalities, including advanced interception tools, activeandpassivescanning,andspidering,asillustratedin Figure10.Ithasavibrantusercommunitythatsupportsand updatesthetoolfrequently,alongwithanextensiveamount ofdocumentation.
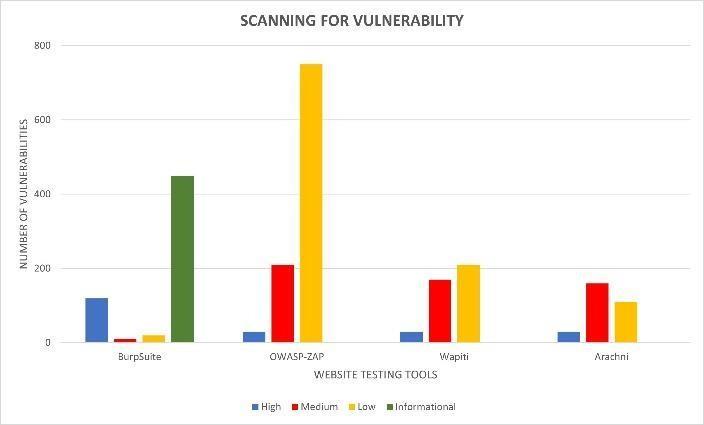
Fig 11. Graphindicatingnumberofvulnerabilities scannedbyvariouswebsitetestingtools
Since it can effectively scan for high and medium risks, as shown in Fig. 11, our suggested work incorporating the OWASP-ZAP can be regarded as the best tool for website testing.Accordingto[5],italsoscansforasizablenumberof low vulnerabilities, which helps mitigate low risks in comparisontoothertools.
This paper discusses the critical role that vulnerability assessmentandpenetrationtestingtoolsplayinpreventing cyberattacks. Organisations must take proactive steps to detect and fix vulnerabilities in their systems and applicationsduetotherisingfrequencyandsophisticationof cyberattacks.Organisationscanimprovetheircybersecurity posture by identifying potential weaknesses and implementingtheappropriatecorrectivemeasureswiththe help of a penetration testing and vulnerability assessment systemarchitecture.Inordertoensurethoroughcoverageof potentialsecurityrisks,thissystemarchitectureusesawide range of different tools and techniques to cover various systemcomponents,suchasfilesystems,applications,system services, device drivers, libraries, system calls, and networking. In the face of increasing cyber threats, companies can protect their data, uphold their reputation, andguaranteethecontinuousintegrityoftheiroperationsby putting penetration testing and vulnerability assessment tools into place. Therefore, maintaining a high level of security and stability for the systems and data of organisationsdependsontheuseofvulnerabilityassessment andpenetrationtestingtoolsincyber-attackprevention.
Future research and development will focus on creating penetrationtestingandvulnerabilityassessmenttoolsthat areevenmoresophisticatedandadvanced,Futureresearch anddevelopmentwillfocusoncreatingpenetrationtesting and vulnerability assessment tools that are even more
sophisticatedandadvanced,andthathaveimprovedfeatures like network mapping scanning and reporting to help find andfixcomplexsecurityvulnerabilitieslikefilelessmalware, supplychainattacks,andadvancedmalware.Inordertooffer morethoroughandproactivedefenceagainstcyberthreats, thereisalsoagreatdealofroomforadditionalresearchinto theintegrationofvulnerabilityassessmentandpenetration testingtoolswithothercybersecuritytechnologies,suchas artificialintelligenceandmachinelearning.
[1] E. Pelivani and B. Cico, "A comparative study of automationtestingtoolsforwebapplications,"2021 Embedded Computing (MECO), Budva, Montenegro, 2021.
[2] R.Pandey,V.JyothindarandU.K.Chopra,"Vulnerability Assessment and Penetration Testing: Aportable solution Implementation," 2020 12th Global Conference on Computational Intelligence and Communication Networks(CICN),
[3] Kavya Rani S R,Soundarya B C, "Comprehensive AnalysisofVariousCyberAttacks",IEEEInternational Conference on Distributed Computingand Electrical CircuitsandElectronics(ICDCECE),2022
[4] D. Delija, Ž. Petrović, G. Sirovatka and M. Žagar, "An Analysis of Wireless Network Security Test Results providedbyRaspberryPiDevicesonKaliLinux,"2021 44th International Convention on Information, CommunicationandElectronicTechnology(MIPRO), Opatija,Croatia,2021
[5] Shahid,J.;Hameed,M.K.;Javed,I.T.;Qureshi,K.N.;Ali, M.;Crespi,N.Comparative Study of Web Application Security Parameters: Current Trends and Future Directions. Appl.Sci.2022
[6] A.S.LaxmiKowta,K.Bhowmick,J.R.KaurandN.Jeyanthi, "Analysis and Overview of Information Gathering & Tools for Pentesting,"International Conference on a ComputerCommunicationandInformatics(ICCCI),pp no.1-13Coimbatore,India,
[7] Disha Pahuja, Prerna Sidana,”Implementing and Comparing Different Password Cracking Tools,” International Research Journal of Engineering andTechnology(IRJET)Volume:08Issue:05|May2021
[8] S.R.KavyaRani,B.C.Soundarya,H.L.GururajandV. Janhavi, "Comprehensive Analysis of Various Cyber Attacks,"2021IEEEMysoreSubSectionInternational Conference(MysuruCon),Hassan,India,2021

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
BIOGRAPHIES:




GSwaroop DepartmentofComputerScienceand Engineering, AtriaInstituteofTechnology.
HarishBudarpu DepartmentofComputerScienceand Engineering, AtriaInstituteofTechnology
ManasaBN DepartmentofComputerScienceand Engineering, AtriaInstituteofTechnology
Asst.ProfessorMeghashreeN DepartmentofComputerScienceand Engineering, AtriaInstituteofTechnology.