
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
Karthik Jataprole
Workday Inc., USA
Real-timesecuritymonitoringandalertingarecrucialforprotectingcloudenvironmentsfromcyberthreats.As organizationsincreasinglyadoptAmazonWebServices(AWS),buildingeffectivemonitoringpipelinesbecomes essential [1]. This article explores the integration of Cribl and Splunk to create robust real-time security monitoring solutions in AWS. It discusses the challenges of threat detection in the cloud [2], provides an overview of Cribl and Splunk [3, 4], and examines the architecture of real-time monitoring pipelines [5]. Techniquesfordataingestion,transformation,andenrichmentusingAWSservicesandSplunkareexplored[6, 7], along with real-time alerting configuration [8] and integration with AWS security services [9]. The article addresses performance optimization, scalability [10], and includes case studies demonstrating effective security monitoring practices [11]. It concludes by discussing future trends in real-time security monitoring, consideringtechnologicaladvancements,evolvingthreatlandscapes,andregulatoryrequirements[12].
Keywords: Real-timesecuritymonitoring,AWSenvironment,CriblandSplunkintegration,Dataingestionand transformation,Complianceandregulatoryrequirements
In today's rapidly evolving cloud landscape, real-time security monitoring and alerting have become paramount for organizationsseekingtoprotecttheircriticalassetsanddatafromever-increasingcyberthreats[1].Asmoreenterprises migrate their infrastructure to Amazon Web Services (AWS), the need for effective monitoring solutions that can detect and respond to security incidents promptly has never been greater [3]. However, building comprehensive monitoring pipelines can be challenging, requiring the integration of multiple tools and services to ensure seamless data ingestion, transformation, analysis, and alerting. This article explores the powerful combination of Cribl and Splunk, two leading

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
platforms in the domain of data management and security analytics, to create robust real-time security monitoring pipelinesinAWSenvironments.ByleveragingthecapabilitiesofCriblfordataingestion,transformation,andenrichment, along with Splunk's advanced analytics and alerting features, organizations can enhance their security posture and gain real-timevisibilityintopotentialthreats.
These are two powerful platforms that have gained significant attention in the realm of data management and security analytics. Cribl, a relatively new entrant in the market, has quickly established itself as a leader in data ingestion, transformation, and enrichment [3]. On the other hand, Splunk has long been recognized as a prominent player in data analysisandvisualization,particularlyinthecontextofsecuritymonitoring[14].
CriblLogStream,theflagshipproductofCribl,isaversatiledatapipelinethatexcelsiningestingdatafromawiderangeof sources, including logs, metrics, and traces. One of its key strengths lies in its ability to perform real-time data transformation and enrichment. With Cribl LogStream, organizations can easily parse, filter, and enrich data on the fly, ensuring that only relevant and valuable information is forwarded to downstream systems [13]. This capability is particularlycrucialinthecontextofsecuritymonitoring,wheretheabilitytoquicklyidentifyandprioritizecriticalevents isparamount.
Splunk Enterprise, the core offering of Splunk, is a powerful platform for data analysis and visualization [2]. It enables organizations to collect, index, and analyze massive volumes of machine-generated data from various sources. Splunk's search and reporting capabilities allow security teams to perform complex queries, detect patterns, and gain valuable insights from their data [14]. Additionally, Splunk provides a rich set of visualization tools, including dashboards, charts, andgraphs,whichhelpinpresentingcomplexsecuritydatainamoreintuitiveandactionablemanner.
When combined, Cribl and Splunk form a potent solution for real-time security monitoring in AWS environments. By leveraging Cribl LogStream's data ingestion and transformation capabilities, organizations can efficiently collect and preprocesssecuritydatafromvariousAWSservices,suchasCloudTrail,VPCFlowLogs,andGuardDuty.CriblLogStream canthenforwardtheenricheddatatoSplunkEnterpriseforadvancedanalysisandvisualization[5].
ThisintegrationallowssecurityteamstocentralizetheirAWSsecuritydata,performreal-timethreatdetection,andgain comprehensive visibility into their cloud infrastructure. Splunk's powerful search and correlation capabilities enable organizations to identify potential security incidents, investigate anomalies, and respond to threats promptly [14]. Moreover,Splunk'spre-builtdashboardsandcustomizablevisualizationsprovidesecurityteamswithactionableinsights, facilitatinginformeddecision-makingandenhancingoverallsecurityposture.
Data ingestion and transformation are crucial steps in building effective, real-time security monitoring pipelines. In the context of AWS, several key services provide valuable security-relevant data that can be ingested and processed using CriblLogStreambeforebeingforwardedtoSplunkforanalysis.
At AWS, there is a wide range of services available that provide logs and events containing crucial security information. Someofthemostcriticalservicesforsecuritymonitoringinclude
AWSCloudTrailprovidesaservicethatallowsforgovernance,compliance,andoperationalandriskauditingofyourAWS account [15]. This resource offers a comprehensive record of AWS API calls and actions performed using a variety of methods,suchastheAWSManagementConsole,AWSSDKs,command-linetools,andotherAWSservices[16].CloudTrail

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
logs play a crucial role in monitoring and investigating security incidents, offering in-depth insights into user activities, resourcechanges,andAPIcallswithinyourAWSenvironment[17].
VPCFlowLogsisa useful featurethatallowsyoutogatherdata ontheIPtrafficgoingtoandfromnetwork interfacesin your Virtual Private Cloud (VPC) [18]. Flow log data contains details like the source and destination IP addresses, ports, protocols, and the amount of bytes and packets transferred [15]. Through the analysis of VPC Flow Logs, security teams have the ability to identify atypical network traffic patterns, detect potential attempts to exfiltrate data, and investigate threatsthatarebasedonthenetwork[19].
Amazon GuardDuty is a highly effective managed threat detection service that provides continuous monitoring of your AWSaccountsandworkloads,ensuringtheutmostsecurityagainstmaliciousactivityandunauthorizedbehavior[20].The analysisencompassesarangeofdatasources,suchasVPCFlowLogs,AWSCloudTraileventlogs,andDNSlogs,inorderto detectpotential threatslike abnormal APIcalls,unauthorized deployments, andcompromised instances[15]. GuardDuty generatescomprehensivesecurityfindingsthatcanbeanalyzedtoinvestigateandrespondtosecurityincidents[20].
Amazon CloudWatch Logs is a convenient service that helps you consolidate logs from various sources into a single location [21]. This feature allows for the monitoring, storage, and access of log files from various sources, including EC2 instances, AWS CloudTrail, and Route 53 [15]. CloudWatch Logs offers valuable insights for troubleshooting, conducting security analysis, and performing compliance auditing. By incorporating CloudWatch Logs into your security monitoring pipeline, valuable insights can be obtained regarding application errors, performance issues, and potential security breaches[21].
Afteringestingsecurity-relevantdatafromdifferentAWSservices,itoftenneedstobenormalizedandenrichedtogiveit moremeaningandmakeiteasiertotakeactionon.CriblLogStreamoffersarobustrangeofcapabilitiesforenhancingand transformingrawlogdata[22].
Using Cribl LogStream, users have the ability to parse and extract fields from unstructured log data, resulting in a consistent and structured format across various data sources [23]. This normalization process simplifies the search, analysis,andcorrelationofeventsinSplunk.
In addition, Cribl LogStream allows for the enhancement of log data by incorporating additional context, such as geolocation details, user metadata, and threat intelligence feeds [22]. By combining different data points and providing relevant context, a more comprehensive understanding of security events can be achieved, which can help speed up incidentinvestigationandresponse[24].
Prior to forwarding the normalized and enriched log data to Splunk, Cribl LogStream provides the capability to execute advancedparsingandtransformationoperations[23].Thisguaranteesthatthedataisformattedinawaythatisidealfor analysisandmeetsthecriteriaofyourSplunkdatamodelsandindexingneeds.
Cribl LogStreamoffersa diversearrayofparsingtechniques,suchasregularexpressions,JSON,CSV,andkey-valuepairs [22]. One can extract relevant fields, filter out unnecessary noise, and apply conditional logic to route data based on specificcriteria[24].
In addition, Cribl LogStream allows for the implementation of data masking and obfuscation techniques to safeguard sensitive information, including personally identifiable information (PII) or confidential data [23]. By adhering to data privacyregulations,theriskofdatabreachesisminimized.
WiththehelpofCriblLogStream'sparsingandtransformationcapabilities,youcanguaranteethatthedatabeingingested into Splunk is clean, structured, and optimized for efficient analysis and visualization [24]. This enhances the security monitoringprocessandempowerssecurityteamstoswiftlyidentifyandaddresspotentialthreats.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
Timely monitoring pipelines are crucial for swiftly identifying and addressing security incidents in AWS environments. The architecture of these pipelines generally includes multiple essential components that collaborate to ingest, process, andanalyzesecurity-relevantdata.
Atypicalreal-timemonitoringpipelineinAWSgenerallyconsistsofthefollowingkeycomponents:
1. Some of the data sources include various AWS services that produce logs and events related to security, such as CloudTrail,VPCFlowLogs,GuardDuty,andCloudWatchLogs[25].
2. Data collectors are tools or services that gather and combine data from different sources, like AWS Kinesis Data StreamsorAWSLambdafunctions[26].
3. Data processingandtransformation:PlatformssuchasCribl LogStreamhavetheabilitytostandardize,enhance, andmodifythegathereddatapriortosendingittotheanalysislayer[27].
4. Data analysis and storage: Solutions such as Splunk Enterprise index, store, and analyze the processed data, allowingforreal-timemonitoring,alerting,andreporting[28].
Theinitialstageofconstructingareal-timemonitoringpipelineinvolvesidentifyingthepertinentdatasourceswithinyour AWS environment. Some sources that can be used for various purposes are CloudTrail for API activity monitoring, VPC Flow Logs for network traffic analysis, GuardDuty for threat detection, and CloudWatch Logs for application and service logs[25].
After identifying the data sources, it is necessary to establish data collectors to ingest the logs and events. AWS offers variousservicessuchasKinesisDataStreamsandLambdafunctions,whichenablethecollectionandaggregationofdata inreal-time[26].Thesecollectorscanbesetuptotransmitthedatatotheprocessingandtransformationlayer,likeCribl LogStream.
Oncethedataiscollected,itmustundergoprocessingandtransformationtoensureconsistency,standardizeformats,and enhancethedatawithadditionalcontext.ThisiswheresolutionslikeCriblLogStreamcomeintoplay[27].
Cribl LogStream enablesuserstodefine transformation androutingrulesfor manipulatingdata priorto forwardingitto theanalysislayer.Therulescaninvolvefieldextraction,datamasking,dataenrichment,andconditionalroutingbasedon specificcriteria[29].
Forinstance,CriblLogStreamcanbeutilizedtoextractpertinentfieldsfromCloudTraillogs,concealsensitivedatainVPC FlowLogs,enhanceGuardDutyfindingswiththreatintelligencedata,anddirectspecificeventstovariousSplunkindexes dependingontheirseverityorrelevance[27].
The last part of the real-time monitoring pipeline involves the indexing and storage layer, where the processed data is stored and analyzed. Splunk Enterprise is widely favored for this layer because of its robust indexing, searching, and reportingcapabilities[28].
Splunk efficiently indexes the data obtained from Cribl LogStream, enabling seamless searchability and easy access for real-time monitoring and analysis. The platform offers a centralized solution for security teams to analyze incidents, identifyirregularities,andgeneratealertsusingpredefinedrulesandthresholds.[28].
Splunk also provides a variety of visualization and reporting capabilities, enabling security teams to create personalized dashboards,visualizetrendsandpatterns,andgeneratereportsforcomplianceandauditingpurposes[30].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
Throughtheuseofdata collectors,Cribl LogStreamfor data processingandtransformation,and Splunk forindexingand analysis, organizations can create powerful real-time monitoring pipelines to identify and address security incidents in theirAWSenvironmentswithefficiency.
Enhancing data and making connections are essential for effective real-time security monitoring. They empower organizations to develop a more holistic grasp of security events and make well-informed decisions when responding to incidents.
Derivingmeaningfulinsightsfromsecuritydatacanbe quitechallengingduetoitsmultiplesourcesandvariousformats. Properenrichmentandcorrelationarenecessarytoovercomethisobstacle.Enhancingdataentailsincorporatingcontext andadditionaldetailstotherawdata,whilecorrelationaidsinrecognizingconnectionsandpatternsbetweenseemingly unrelatedevents[31].
Dataenrichmentandcorrelationplayacrucialroleforvariousreasons:
1. Enhancingsecuritydatawithsupplementarydetails,likeuserinformation,assetdata,andthreatintelligence,aids in providing a comprehensive understanding of events. This, in turn, enables security teams to grasp the importanceandpotentialconsequencesofanincident[32].
2. Identifying patterns and relationships: Correlating events from various sources and time periods can assist in detectingpatternsandrelationshipsthatmaysuggestasecuritythreatoranongoingattack[33].
3. Byenhancingandconnectingdata,securityteamscanmoreaccuratelyevaluatetheseriousnessandimmediacyof incidents,allowingthemtoeffectivelyprioritizetheirresponseefforts[31].
Threat intelligence and contextual information are crucial for enhancing data enrichment. Utilizing threat intelligence feeds,likeindicatorsofcompromise(IOCs),malwaresignatures,andknown badIP addresses,canenhancesecuritydata andaidinthedetectionofpotentialthreats[34].
Additional information, such as user and asset details, can be incorporated into the security data to enhance the overall understanding of the events. For instance, enhancing VPC Flow Logs with details about the instances and their roles can assistsecurityteamsincomprehendingthecontextofnetworktrafficanddetectingabnormalpatterns[32].
Cribl LogStream offers a range of built-in functions and lookups to enhance data, including GeoIP enrichment, user and asset correlation, and threat intelligence integration [35]. By utilizing these capabilities, organizations can maximize the valueoftheirsecuritydataandenhancetheirabilitytodetectandrespondtothreats.
Splunk Enterprise offers a range of features and add-ons that facilitate data enrichment and correlation, making it a powerfultoolforreal-timesecuritymonitoring[36].
Someofthekeycapabilitiesinclude:
1. Lookups: Splunk allows you to create and use lookup tables to enrich data with additional information, such as userdetails,assetinformation,andthreatintelligence[37].
2. Correlation searches: Splunk's search language enables you to perform complex queries and correlations across multipledatasourcesandtimeranges,helpingyouidentifypatternsandrelationshipsbetweenevents[38].
3. Machine learning toolkit: Splunk's Machine Learning Toolkit (MLTK) provides a suite of machine learning algorithms and tools that can be used for anomaly detection, clustering, and predictive analytics, enhancing the abilitytodetectandrespondtothreats[39].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
4. Splunk Enterprise Security: Splunk Enterprise Security (ES) is a premium security solution that builds upon Splunk Enterprise, providing out-of-the-box security use cases, workflows, and visualizations. It includes advanced correlation rules, threat intelligence integration, and user and entity behavior analytics (UEBA) capabilities[40].
By leveraging Splunk's data enrichment and correlation features, organizations can gain a more comprehensive and context-richviewoftheirsecurityposture,enablingfasterincidentdetectionandresponse.
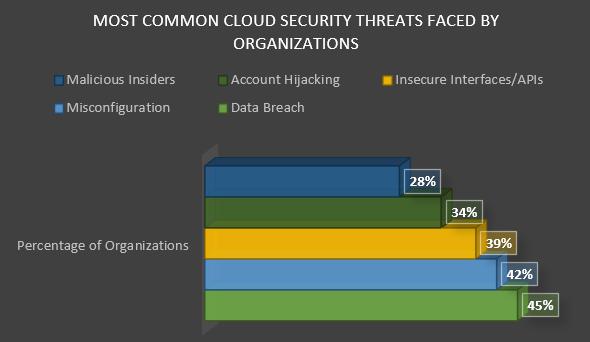
Timely alerting and notification are crucial elements of a successful security monitoring pipeline. Security teams can effectively respond to potential threats and minimize the impact of security incidents. Splunk offers robust features for settingupreal-timealertsandnotificationsbasedonspecificconditionsandthresholds.
SplunkEnterpriseenablesthecreationofreal-timealertsbasedontheoutcomesofsavedsearchesormetrics[41].These alertsareactivatedwhencertainconditionsaremet,suchassurpassingasetnumberoffailedloginattemptsordetecting acriticalsecurityevent.
Tosetupreal-timealertinginSplunk,followthesesteps:
1. Setupasavedsearchtoretrievetheeventsormetricsyouwishtokeeptrackof[42].
2. Definethealertconditionsandthresholdsbasedonthesearchresults[41].
3. Specifythenecessaryactionswhenthealertistriggered,suchassendingnotificationsorrunningascript[43].
Splunk offers a user-friendly interface for creating and managing alerts, making it simple for security teams to establish andmaintaintheirreal-timealertingworkflows.
DEFINING ALERT CONDITIONS AND THRESHOLDS
Establishing suitable alert conditions and thresholds is essential for efficient real-time alerting. Conditions are used to specifythecriteriathatneedtobemetinorderforanalerttobetriggered.Thresholds,ontheotherhand,determinethe severityandurgencyofthealert[44].
Whendefiningalertconditions,itisimportantforsecurityteamstotakeintoaccountvariousfactors:

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
1. Thenatureandextentofthesecurityincident
2. Thefrequencyandvolumeoftheevent
3. Thepotentialimpactontheorganization
4. Therateoffalsepositivesandthecapacitytoexamineandaddressthealert
Thresholds can be established using either fixed values or calculations that take into account variations from a baseline [44].Splunkprovidestheabilitytosetvariousthresholdsforanalert,allowingyoutoincreasetheseverityandresponse actionsdependingonthedegreeofdeviationfromtheusual.
Striking a balance between sensitivity and specificity is crucial when defining alert conditions and thresholds. Excessive alertsthataretoosensitivecanleadtoasignificantamountoffalsepositives,whichcanoverwhelmsecurityteams.Onthe otherhand,alertsthataretoospecificmayfailtodetectimportantsecurityevents[45].
Afterconfiguringalerts,itbecomescrucialtoestablishsuitablenotificationmethodsandescalationprotocolstoguarantee promptinformationdisseminationandenabletimelyactionsbytherelevantindividuals.
Splunkoffersarangeofnotificationmethods,suchas:
1. Notificationsviaemail
2. Textmessagesandnotificationssenttomobiledevices
3. SeamlessintegrationwithpopularcollaborationplatformslikeSlackandMicrosoftTeams
4. Integrationwithexternalsystemsandworkflowsthroughwebhooks
Securityteamshavetheabilitytodefinevariousnotificationchannelsandrecipientsdependingontheseverityandtypeof thealert[43].Asanillustration,importantalertscanbesentthroughSMSandemailtotheentiresecurityteam,whileless urgentalertsmayonlybesentviaemailtoaspecificgroupwithintheteam.
Escalation policies guarantee that alerts are escalated accordingly if they are not acknowledged or resolved within a designated timeframe [44]. These policies can be adjusted to notify other team members, like security managers or incidentresponseteams,ifanalertremainsunacknowledgedorunresolvedafteraspecifictimeframe.
Splunk offers the flexibility to customize escalation policies and notification workflows, allowing organizations to adapt theirreal-timealertingandnotificationprocessestomeettheiruniqueneedsandrequirements[41].
ThroughtheuseofSplunk'sreal-timealertingandnotificationfeatures,securityteamscanstayinformedaboutpotential securitythreatsandquicklyrespondtoinvestigateandaddressthem.
Integrating Cribl LogStream and Splunk with AWS security services can greatly improve an organization's security monitoring capabilities. By utilizing native AWS services like AWS Security Hub, AWS Config, and AWS IAM Access Analyzer,organizationscanenhancetheirunderstandingoftheirsecuritystatusandoptimizetheirincidentdetectionand responseworkflows.

Volume: 11 Issue: 05 | May 2024 www.irjet.net
CloudTrail LogsAPIactivityanduseractions
VPC Flow Logs Capturesnetworktrafficinformation
GuardDuty Detects malicious activity and unauthorizedbehavior
Security Hub Aggregates and prioritizes security alerts
Config Records and evaluates resource configurations
Table 1: AWS security services and their integration with Cribl LogStream and Splunk [98, 99]
AWS SECURITY HUB
TheAWSSecurityHubservesasacentralizedplatformthatbringstogetherandprioritizessecurityfindingsfromarange of AWS services and third-party tools [46]. This solution offers a comprehensive overview of an organization's security status,empoweringsecurityteamstoefficientlydetectandresolveanypotentialissues.
IntegratingCriblLogStreamandSplunkwithAWSSecurityHuballowsorganizationsto:
1. IngestsecurityfindingsfrommultipleAWSservicesandthird-partytoolsintoacentrallocation
2. Normalizeandenrichsecurityfindingswithadditionalcontextandmetadata
3. Correlatesecurityfindingswithotherlogdataandeventsformorecomprehensiveanalysis
4. Createcustominsightsandalertsbasedonaggregatedsecurityfindings
ByleveragingAWSSecurityHub,organizationscansignificantlyreducethetimeandeffortrequiredtocollect,analyze,and prioritizesecurityfindingsacrosstheirAWSenvironment[47].
AWS CONFIG
AWSConfigisaservicethatenablesorganizationstoassess,audit,andevaluatetheconfigurationsoftheirAWSresources [48]. It continuously monitors and records resource configurations, allowing security teams to detect and investigate changesthatmayintroducesecurityrisks.
IntegratingCriblLogStreamandSplunkwithAWSConfigenablesorganizationsto:
1. IngestAWSConfigconfigurationitems(CIs)andconfigurationhistoryintoSplunkforanalysis
2. MonitorandalertonchangestocriticalAWSresourcesandconfigurations
3. Correlateresourceconfigurationchangeswithothersecurityeventsandlogdata
4. Assesscompliancewithinternalpoliciesandindustryregulations
ByleveragingAWSConfig,organizationscan maintaina moresecureandcompliantAWSenvironment,reducing therisk ofmisconfigurationsandunauthorizedchanges[49].
AWS IAM ACCESS ANALYZER
TheAWSIAMAccessAnalyzerisavaluableservicethatassistsorganizationsinidentifyinganyunintended accesstotheir AWSresources[50].ItcontinuouslymonitorsAWSIAMpoliciesandresourcepolicies,identifyingpotentialsecurityrisks suchasunintendedpublicorcross-accountaccess.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
ByintegratingCriblLogStreamandSplunkwithAWSIAMAccessAnalyzer,organizationsgaintheabilityto:
1. IntegrateAWSIAMAccessAnalyzerfindingsintoSplunkforthoroughanalysisandtimelyalerting
2. IdentifyandaddressunintendedresourceaccessandmisconfigurationsinIAMpolicies
3. ExamineIAMAccessAnalyzerfindingsalongsideothersecurityeventsandlogdata
4. EnsurestrictadherencetoleastprivilegeaccessprinciplesthroughouttheAWSenvironment.
ThroughtheuseofAWSIAMAccessAnalyzer,organizationscantakeaproactiveapproachtoidentifyingandaddressing security risks associated with IAM. This helps to minimize the potential for attacks and ensures that access control is properlymanaged[51].
ForaseamlessintegrationofCriblLogStreamandSplunkwithAWSsecurityservices,organizationsshouldkeepinmind thefollowingstrategies:
1. Utilize Cribl LogStream to efficiently handle and standardize data from AWS security services, guaranteeing a uniformdataformatandstructure[52].
2. Utilize Splunk's AWS Add-on to effortlessly gather and analyze data from a range of AWS services, such as AWS SecurityHub,AWSConfig,andAWSIAMAccessAnalyzer[53].
3. Developpersonalized Splunk dashboardsand alertsfor effectivemonitoringand visualizationofcritical security metricsandfindingsderivedfromAWSsecurityservices[54].
4. Utilize Splunk's integrations with AWS Lambda and other AWS services [55] to implement automated response andremediationworkflows.
Through the implementation of these integration strategies, organizations can establish a cohesive and efficient security monitoring solution that utilizes the inherent capabilities of AWS security services, while also taking advantage of the robustdataprocessingandanalysisfeaturesofferedbyCriblLogStreamandSplunk.
When implementing real-time security monitoring pipelines in AWS with Cribl LogStream and Splunk, it is crucial to prioritizeperformanceoptimizationandscalability.Thisensuresthatthe solutioncaneffectivelyhandlethehighvolume andvelocityofsecuritydata.
Efficientlyprocessingandanalyzingdatainthesecuritymonitoringpipelineisessentialforoptimizingresourceutilization andavoidingunnecessarycosts.
Herearesomeimportantstrategiestooptimizeresourceutilization:
1. Optimizing AWS instances: Choose the most suitable instance types and sizes for Cribl LogStream and Splunk, takingintoaccounttheanticipateddatavolumeandprocessingneeds[56].
2. Leveragingauto-scaling:Implementauto-scalingforCriblLogStreamandSplunkinstancestoautomaticallyadjust thenumberofinstancesbasedontheincomingdatavolumeandprocessingload[57].
3. Enhance data ingestion efficiency: Leverage Cribl LogStream's powerful features for data filtering, routing, and transformation to decrease the amount of data being ingested into Splunk. This will help to minimize the processingandstorageneeds[58].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
4. Enhancing Splunk indexing and searching: Enhance the performance of Splunk's indexing and searching capabilitiesbyproperlyconfiguringindexers,searchheads,andforwardersandutilizingrecommendedpractices fordatamanagement[59].
Maximizing resource utilization enables organizations to guarantee that their security monitoring pipeline effectively managesdatavolume,reducesexpenses,andsustainsperformance.
Managingdatastorageisessentialassecuritydatavolumeincreases.Itisimportanttoensurethatthemonitoringpipeline canhandlethegrowingdatavolumewithoutsacrificingperformanceorincurringhighstoragecosts.
Herearesomeeffectivestrategiesformanagingdatavolumeandstorage:
1. ImplementingdataretentionpoliciesinSplunkallowsfortheautomaticarchivingordeletionofolderdatabased onpredefinedcriteria,suchasageorrelevance[60].
2. Utilizedatacompressiontechniqueslikegziporlz4todecreasethestoragesizeofsecuritydatainSplunk[61].
3. Utilize Splunk's SmartStore feature to automatically tier data between different storage levels based on access frequencyandretentionrequirements[62].
4. Datapruning:LeverageCriblLogStream'spowerfuldatapruningcapabilitiestoselectivelyeliminateormaskany sensitiveorirrelevantdatapriortoforwardingittoSplunk,effectivelyreducingtheoveralldatavolume[58].
Implementing effective data volume and storage management strategies allows organizations to ensure their security monitoringpipelinecanhandlegrowingdatavolumes,optimizestoragecosts,andmaintainperformance.
Effectivesecurity monitoringpipelines need to beabletohandle highloadsand easilyscaletomeetsudden increases in datavolumeorprocessingneeds.
Herearesomestrategiestoensurescalability:
1. Horizontal scaling: Utilize Cribl LogStream's distributed architecture and Splunk's clustering capabilities to expandthepipelinecomponentshorizontallybyincorporatingadditionalinstancesasrequired[63].
2. Load balancing: Implementing load balancing for Cribl LogStream and Splunk components allows for even distributionof the processingloadacross multipleinstances,resulting inimprovedperformanceandavailability [64].
3. Auto-scaling: Set up auto-scaling policies for Cribl LogStream and Splunk instances to automatically adjust the numberofinstancesbasedonspecificmetrics,likeCPUusageordataingestionrate[57].
4. Implementingcomprehensivemonitoringandalertingforthesecuritymonitoringpipelinecomponentsallowsfor proactivedetectionandresponsetoperformanceissuesorcapacityconstraints[65].
By strategically designing the security monitoring pipeline and implementing effective scaling strategies, organizations canguarantee that theirsolution iscapable ofhandling peak loadsandaccommodating future growth while maintaining optimalperformanceandavailability.
Automation and orchestration play a crucial role in a well-functioning real-time security monitoring pipeline, allowing organizationstostreamlinerepetitivetasks,speedupincidentresponse,andenhanceoverallsecurityposture.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
Automating common security monitoring tasks can greatly decrease the need for manual intervention, decrease the likelihoodofhumanmistakes,andenhanceoverallefficiency.Someexamplesoftasksthatcanbeautomatedinclude:
1. Automate the collection and ingestion of security data from various sources using Cribl LogStream's built-in integrationsandAPIs[66].
2. Utilize Cribl LogStream's pipelines and functions to automatically enhance and standardize security data, guaranteeinguniformityandpreparednessforanalysis[67].
3. Alertcreationandnotification:SetupSplunktogeneratealertsaccordingtopredefinedrulesandthresholds,and notifytherelevantstakeholders[68].
4. Streamline compliance checks and generate reports effortlessly with Splunk's comprehensive compliance frameworksandreportingcapabilities[69].
By automating these common tasks, security teams can prioritize higher-value activities like threat hunting and incident response,ensuringthesecuritymonitoringpipelineoperatesefficientlyandeffectively.
Efficiently managing incident triage and coordinating response is crucial in security monitoring, and automation and orchestration can play a significant role in enhancing these processes. Here are some strategies for effectively utilizing automationintheseareas:
1. Automated incident prioritization: Leverage Splunk's powerful machine learning capabilities to automatically prioritize incidents, taking into account factors such as severity, impact, and historical data. This ensures that high-priorityincidentsarepromptlyaddressedandresolved.
2. Strategicapproach:IncorporateautomatedplaybooksutilizingSplunkPhantomorsimilarSOARtoolstoprovide incidentresponderswithastructuredframeworkforexecutingpredefinedstepsandactions[71].
3. Streamlineintegrationwithticketingsystems:Streamlinetheprocessofcreatingandupdatingincidentticketsin popularsystemslikeServiceNoworJira,ensuringthatallnecessaryinformationiscapturedandtracked[72].
4. UtilizeSplunk Phantom or other SOAR toolsto automatecontainmentand remediationactions,suchasisolating affectedsystemsorblockingmaliciousIPaddresses[73].
By automating incident triage and response coordination, organizations can significantly reduce the time required to detect,investigate,andmitigatesecurityincidents,minimizingpotentialdamageandensuringamoreeffectiveresponse.
Both Cribl LogStream and Splunk offer powerful automation capabilities that can be leveraged to streamline security monitoringtasksandimproveoverallefficiency.
CriblLogStreamprovidesthefollowingautomationfeatures:
1. Packs: Cribl LogStream Packs are pre-built configurations that automate common data processing and transformationtasks,suchasdatamasking,fieldextraction,anddataenrichment[74].
2. RESTAPI:CriblLogStream'sRESTAPIenablesprogrammaticcontrolovertheplatform,allowingorganizationsto automate tasks suchas deploying and managing pipelines, monitoring system health, and integrating with other tools[75].
Splunkoffersthefollowingautomationcapabilities:
1. SplunkAPI:Splunk'sextensiveAPIallowsorganizationstoautomatevarioustasks,suchasdataingestion,search andreporting,alertcreation,andusermanagement[76].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
2. Splunk Phantom: Splunk Phantom is a SOAR platform that enables organizations to automate and orchestrate securityoperations,includingincidenttriage,investigation,andresponse[71].
3. Splunk Machine Learning Toolkit: The Splunk Machine Learning Toolkit (MLTK) provides a set of tools and algorithmsthatenableorganizationstoautomatedataanalysis,anomalydetection,andthreathunting[77].
By leveraging the automation capabilities of Cribl LogStream and Splunk, organizations can create a more efficient and effectivesecuritymonitoringpipeline,reducingmanualeffortandenablingsecurityteamstofocusonhigh-valueactivities.
Real-world case studies and examples provide valuable insights into how organizations have successfully implemented Cribl and Splunk in their AWS environments to enhance their security monitoring capabilities. These examples highlight specificusecases,challengesencountered,andtheoutcomesachievedthrougheffectivesecuritymonitoringpractices.
Several organizations have successfully implemented Cribl and Splunk in their AWS environments to improve their security monitoring capabilities. One such example is the case of a large financial services company that leveraged Cribl LogStream to ingest and process security data from various AWS services, such as CloudTrail, VPC Flow Logs, and GuardDuty[78].ByusingCriblLogStream,thecompanywasabletonormalizeandenrichthedatabeforeforwardingitto Splunkforanalysisandvisualization.
Another example is the implementation of Cribl and Splunk by a global healthcare organization to monitor its AWS environment and ensure compliance with regulatory requirements such as HIPAA [79]. The organization used Cribl LogStreamtomask sensitivepatientdata androuteittotheappropriateSplunk indexesbasedondata classificationand retentionpolicies.
Financial Services
Compliance monitoring and threat detection
Healthcare HIPAA compliance and patient dataprotection
Retail PCI DSS compliance and fraud detection
Technology
Insider threat detection and incidentresponse
Improved security posture and reducedMTTD
Ensured regulatory compliance and dataprivacy
Enhanced security and reduced fraudincidents
Faster incident response and minimizeddataloss
Organizations face various use cases and challenges when implementing security monitoring solutions in their AWS environments.Onecommonusecaseistheneedtomonitorandinvestigatesuspicioususeractivitiesandpotentialinsider threats[80].Insuchcases,organizationscanleverageCriblLogStreamtoingestandcorrelatedatafrommultiplesources, such as AWS CloudTrail, AWS Config, and third-party identity and access management (IAM) solutions, to create a comprehensiveviewofuseractivities.
Anotherchallenge encountered byorganizationsisthe needtoensurecompliance withindustry-specific regulationsand standards, such as PCI DSS for financial institutions or NIST frameworks for government agencies [81]. To address this challenge, organizations can use Splunk's built-in compliance dashboards and reports, as well as create custom dashboardsandalertstomonitorspecificcompliancerequirements.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
Effective security monitoring practices using Cribl and Splunk in AWS environments have helped organizations achieve significantoutcomes,suchas:
1. Improved threat detection and response times: By leveraging Cribl LogStream's data processing capabilities and Splunk'sadvancedanalyticsandmachinelearningfeatures,organizationshavebeenabletodetectandrespondto securitythreatsmorequicklyandeffectively[82].
2. Enhancedcomplianceposture:OrganizationshaveusedCriblandSplunktomonitoranddemonstratecompliance withvariousregulatoryrequirements,reducingtheriskofnon-complianceandpotentialpenalties[83].
3. Increased operational efficiency: By automating security monitoring tasks and leveraging the scalability and flexibility of AWS, organizations have been able to reduce manual effort, streamline processes, and improve overalloperationalefficiency[84].
4. Better collaboration and decision-making: The centralized visibility and insights provided by Cribl and Splunk have enabled security teams to collaborate more effectively and make data-driven decisions to improve their organization'ssecurityposture[85].
These case studies and examples demonstrate the real-world benefits and outcomes that organizations can achieve by implementingCriblandSplunkforsecuritymonitoringintheirAWSenvironments.
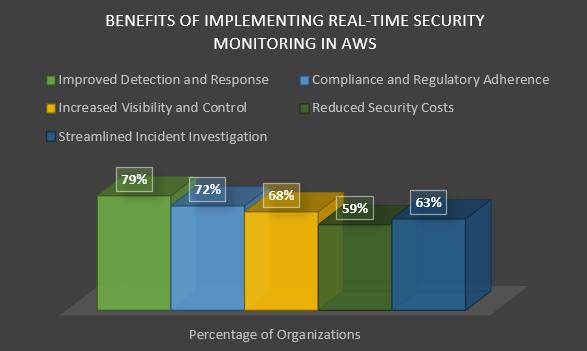
As the cybersecurity landscape continues to evolve, it is essential to stay informed about emerging trends, technological advancements,andregulatoryrequirementsthatshapethefutureofreal-timesecuritymonitoringpractices.
There are several emerging trends that are anticipated to have a significant impact on the future of real-time security monitoring:
1. The growing use of artificial intelligence (AI) and machine learning (ML) techniques in security monitoring solutionsallowsorganizationstoidentifyandaddressthreatswithgreaterspeedandprecision[86].
2. Emphasize proactive threat hunting: Organizations will increasingly prioritize proactive techniques to identify andmitigatepotentialthreatsbeforetheycausesignificantdamage[87].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
3. Theintegrationofsecuritysolutions,includingSIEM,SOAR,andXDR,offersorganizationsamorecomprehensive andunifiedviewoftheirsecurityposture[88].
4. Cloud-native security approaches are becoming increasingly important as organizations embrace cloud-native architectures. This shift brings a greater focus on cloud-native security solutions and practices, including containersecurityandserverlesssecurity[89].
The impact of technological advancements and the evolving threat landscape on real-time security monitoring practices cannotbeunderestimated.Somekeyconsiderationsinclude:
1. 5G and IoT security: The increasing use of 5G networks and the growing number of Internet of Things (IoT) devices will bring about fresh security concerns and broaden the potential for attacks. This will necessitate organizationstomodifytheirsecuritymonitoringapproaches[90].
2. Quantumcomputingandcryptography:Theriseofquantumcomputingcouldmakesome existingcryptographic algorithmsweak,soquantum-resistantcryptographyneedstobecreatedandusedinsecuritymonitoringsystems [91].
3. The rise in ransomware attacks and supply chain compromises demands that organizations strengthen their securitymonitoringcapabilitiestoeffectivelydetectandrespondtothesethreats[92].
Compliance with industry-specific and regional regulations is essential for organizations to shape their security monitoringpracticesinaccordancewithregulatoryrequirements.Hereareafewnoteworthyregulatorydevelopments:
1. DataprivacyregulationsliketheGeneralDataProtectionRegulation(GDPR)andtheCaliforniaConsumerPrivacy Act (CCPA) will have a lasting impact on how organizations handle personal data in their security monitoring practices[93].
2. Regulations specific to certain sectors: Organizations must ensure that their security monitoring practices align withspecificrequirements,suchastheHealthInsurancePortabilityandAccountabilityAct(HIPAA)forhealthcare andtheFederalInformationSecurityManagementAct(FISMA)forU.S.federalagencies[94].
3. Cybersecurity standards and frameworks play a crucial role in guiding organizations towards implementing effective security monitoring and risk management processes. Examples of such standards include the NIST CybersecurityFrameworkandISO/IEC27001[95].
Given the ongoing changes in trends, advancements, and regulations in the cybersecurity landscape, it is crucial for organizationstoremainflexibleandproactiveintheirreal-timesecuritymonitoring.Thisisnecessaryto ensureastrong securitypostureandsafeguardcriticalassets.
In today's rapidly evolving cybersecurity landscape, real-time security monitoring and alerting have become essential componentsofarobustsecuritystrategy,especiallyasorganizationsincreasinglyadoptcloudplatformslikeAmazonWeb Services (AWS). The integration of powerful data processing and analysis tools,such asCribl LogStream and Splunk, has proventobea game-changerintherealmofreal-timesecuritymonitoring,allowing organizationstooptimizetheirdata pipelines, ensure timely analysis, and gain actionable insights. Splunk's extensive security analytics features, combined with its ability to integrate with various AWS security services, provide organizations with a comprehensive and centralizedviewoftheirsecurityposture,enablingsecurityteamstodetect,investigate,andrespondtopotentialthreats more efficiently and effectively. However, implementing a successful real-time security monitoring solution requires careful planning and consideration of various factors, such as data volume, performance optimization, scalability, and automation.Asthethreatlandscapecontinuestoevolveandnewtechnologiesemerge,organizationsmuststayinformed about the latest trends and developments in real-time security monitoring, embrace advancements in AI, machine learning, and cloud-native security approaches, and ensure compliance with regulatory requirements and industry standards. By adopting a proactive and adaptable approach to security monitoring, powered by the integration of Cribl

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
LogStreamandSplunkinAWSenvironments,organizationscanbuildastrongandresilientsecurityposturethatenables themtosafeguardtheircriticalassetsandthriveinthedigitalage.
[1] Gartner.(2021).MarketGuideforCloudWorkloadProtectionPlatforms.Gartner.
[2] NIST.(2020).NISTSpecialPublication800-53,Revision5:SecurityandPrivacyControlsforInformationSystems andOrganizations.NationalInstituteofStandardsandTechnology.
[3] Cribl.(2023).CriblLogStream:DataPipelineforObservabilityandSecurity.Cribl.
[4] Splunk.(2023).SplunkEnterprise:TheData-to-EverythingPlatform.Splunk.
[5] AWS.(2023).AWSSecurityMonitoringandAnalytics.AmazonWebServices.
[6] AWS.(2023).AWSCloudTrailUserGuide.AmazonWebServices.
[7] Splunk.(2023).SplunkAdd-onforAWS.Splunk.
[8] Splunk.(2023).SplunkAlertingManual.Splunk.
[9] AWS.(2023).AWSSecurityHubUserGuide.AmazonWebServices.
[10] Cribl.(2023).CriblAppScope:AutomateDataDiscoveryandObservability.Cribl.
[11] Splunk.(2023).SplunkCustomerSuccessStories.Splunk.
[12] Gartner.(2022).TopSecurityandRiskManagementTrends.Gartner.
[13] Cribl.(2023).CriblBlog:EnhancingSecuritywithCriblLogStream.Cribl.
[14] Splunk.(2023).SplunkSecurity:Detect,Investigate,andRespondtoThreats.Splunk.
[15] AWS.(2023).AWSSecurityMonitoringandAnalytics.AmazonWebServices.
[16] AWS.(2023).AWSCloudTrailUserGuide.AmazonWebServices.
[17] AWS.(2023).AWSCloudTrailEventReference.AmazonWebServices.
[18] AWS.(2023).VPCFlowLogs.AmazonWebServices.
[19] AWS.(2023).AnalyzingVPCFlowLogswithAmazonAthena.AmazonWebServices.
[20] AWS.(2023).AmazonGuardDutyUserGuide.AmazonWebServices.
[21] AWS.(2023).AmazonCloudWatchLogsUserGuide.AmazonWebServices.
[22] Cribl.(2023).CriblLogStream:DataPipelineforObservabilityandSecurity.Cribl.
[23] Cribl.(2023).CriblLogStreamDocumentation:EventProcessing.Cribl.
[24] Cribl.(2023).CriblBlog:EnhancingSecuritywithCriblLogStream.Cribl.
[25] AWS.(2023).AWSSecurityMonitoringandAnalytics.AmazonWebServices.
[26] AWS.(2023).AmazonKinesisDataStreams.AmazonWebServices.
[27] Cribl.(2023).CriblLogStream:DataPipelineforObservabilityandSecurity.Cribl.
[28] Splunk.(2023).SplunkEnterprise:TheData-to-EverythingPlatform.Splunk.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
[29] Cribl.(2023).CriblLogStreamDocumentation:EventProcessing.Cribl.
[30] Splunk.(2023).SplunkEnterprise:DashboardsandVisualizations.Splunk.
[31] Bhatt, S., Manadhata, P. K., & Zomlot, L. (2014). The operational role of security information and event managementsystems.IEEESecurity&Privacy,12(5),35-41.
[32] AWS.(2023).AWSSecurityMonitoringandAnalytics.AmazonWebServices.
[33] Schuh,G.(2021).DataCorrelation:TheKeytoEffectiveSecurityMonitoring.DarkReading.
[34] NIST. (2021). NIST Special Publication 800-150: Guide to Cyber Threat Information Sharing. National InstituteofStandardsandTechnology.
[35] Cribl.(2023).CriblLogStream:DataPipelineforObservabilityandSecurity.Cribl.
[36] Splunk.(2023).SplunkEnterprise:TheData-to-EverythingPlatform.Splunk.
[37] Splunk.(2023).SplunkDocs:Aboutlookups.Splunk.
[38] Splunk.(2023).SplunkDocs:AboutCorrelationSearches.Splunk.
[39] Splunk.(2023).SplunkMachineLearningToolkit.Splunk.
[40] Splunk.(2023).SplunkEnterpriseSecurity.Splunk.
[41] Splunk.(2023).SplunkDocs:Aboutalerts.Splunk.
[42] Splunk.(2023).SplunkDocs:Saveareportorsearch.Splunk.
[43] Splunk.(2023).SplunkDocs:Alertactions.Splunk.
[44] NIST.(2011).NIST Special Publication 800-137:Information SecurityContinuous Monitoring(ISCM) for FederalInformationSystemsandOrganizations.NationalInstituteofStandardsandTechnology.
[45] Scarfone, K., & Mell, P. (2007). NIST Special Publication 800-94: Guide to Intrusion Detection and PreventionSystems(IDPS).NationalInstituteofStandardsandTechnology.
[46] AWS.(2023).AWSSecurityHub.AmazonWebServices.
[47] AWS. (2023). AWS Security Hub: Automated and Centralized AWS Account Security Findings. Amazon WebServices.
[48] AWS.(2023).AWSConfig.AmazonWebServices.
[49] AWS.(2023).AWSConfig:ContinuousResourceConfigurationMonitoringandAssessment.AmazonWeb Services.
[50] AWS.(2023).AWSIAMAccessAnalyzer.AmazonWebServices.
[51] AWS.(2023).AWSIdentityandAccessManagement(IAM).AmazonWebServices.
[52] Cribl.(2023).CriblLogStream:DataPipelineforObservabilityandSecurity.Cribl.
[53] Splunk.(2023).SplunkAdd-onforAWS.Splunk.
[54] Splunk.(2023).SplunkDocs:Createdashboards.Splunk.
[55] Splunk.(2023).SplunkDocs:SplunkandAWSLambdaIntegration.Splunk.
[56] AWS.(2023).AmazonEC2InstanceTypes.AmazonWebServices.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
[57] AWS.(2023).AWSAutoScalingUserGuide.AmazonWebServices.
[58] Cribl.(2023).CriblLogStream:DataReduction.Cribl.
[59] Splunk.(2023).SplunkDocs:CapacityPlanningManual.Splunk.
[60] Splunk.(2023).SplunkDocs:Configuredataretention.Splunk.
[61] Splunk.(2023).SplunkDocs:Usedatacompression.Splunk.
[62] Splunk.(2023).SplunkSmartStore.Splunk.
[63] Cribl.(2023).CriblLogStream:DistributedDeployment.Cribl.
[64] AWS.(2023).ElasticLoadBalancingUserGuide.AmazonWebServices.
[65] Splunk.(2023).SplunkDocs:MonitoringSplunkEnterprise.Splunk.
[66] Cribl.(2023).CriblLogStream:Sources.Cribl.
[67] Cribl.(2023).CriblLogStream:Pipelines.Cribl.
[68] Splunk.(2023).SplunkDocs:Alertactions.Splunk.
[69] Splunk.(2023).SplunkDocs:Compliance.Splunk.
[70] Splunk.(2023).SplunkDocs:MachineLearningToolkit.Splunk.
[71] Splunk.(2023).SplunkPhantom.Splunk.
[72] Splunk.(2023).SplunkDocs:ServiceNowintegration.Splunk.
[73] Splunk.(2023).SplunkPhantom:Playbooks.Splunk.
[74] Cribl.(2023).CriblLogStream:Packs.Cribl.
[75] Cribl.(2023).CriblLogStream:RESTAPI.Cribl.
[76] Splunk.(2023).SplunkDocs:RESTAPIReferenceManual.Splunk.
[77] Splunk.(2023).SplunkDocs:SplunkMachineLearningToolkit.Splunk.
[78] Cribl. (2021). Case Study: Financial Services Company Improves Security Monitoring with Cribl LogStream.Cribl.
[79] Splunk.(2022).CustomerStory:GlobalHealthcareOrganizationEnsuresHIPAACompliancewithSplunk andAWS.Splunk.
[80] AWS. (2023). AWS Security Blog: Detecting and Investigating Suspicious Activity with AWS CloudTrail andAmazonAthena.AmazonWebServices.
[81] Splunk.(2023).SplunkDocs:Compliance.Splunk.
[82] Cribl.(2022).Blog:EnhancingThreatDetectionandResponsewithCriblLogStreamandSplunk.Cribl.
[83] Splunk.(2021).Whitepaper:AchievingRegulatoryCompliancewithSplunkandAWS.Splunk.
[84] AWS. (2023). AWS Case Study: Improving Security Operations Efficiency with Splunk on AWS. Amazon WebServices.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
[85] Splunk.(2022).Blog:HowSplunkandAWSEnableBetterCollaborationandDecision-MakingforSecurity Teams.Splunk.
[86] Deloitte.(2021).TechTrends2021:TheNextFrontierofCybersecurity.Deloitte.
[87] SANSInstitute.(2022).ProactiveThreatHunting:StrategiesandTechniques.SANSInstitute.
[88] Gartner.(2022).TopTrendsinCybersecurity2022.Gartner.
[89] AWS.(2023).AWSCloudSecurity:Cloud-NativeSecuritySolutionsandPractices.AmazonWebServices.
[90] NIST.(2021).NISTSpecial Publication800-207:Zero TrustArchitecture.National Instituteof Standards andTechnology.
[91] IBM.(2022).Quantum-SafeCryptographyandSecurity.IBMResearch.
[92] McAfee.(2022).McAfeeLabsThreatPredictions2022.McAfee.
[93] Splunk.(2023).SplunkDocs:GDPRCompliance.Splunk.
[94] HIPAAJournal.(2022).HIPAAComplianceandSecurityMonitoringBestPractices.HIPAAJournal.
[95] NIST.(2018).NISTSpecialPublication800-37,Revision2:RiskManagementFrameworkforInformation SystemsandOrganizations.NationalInstituteofStandardsandTechnology.
[96] Cribl.(2022).CustomerCaseStudies.Cribl.
[97] Splunk.(2023).SplunkCustomerSuccessStories.Splunk.
[98] AWS.(2023).AWSSecurity,Identity,andCompliance.AmazonWebServices.
[99] Splunk.(2023).SplunkAdd-onforAWS.Splunk.
[100] Deloitte.(2020).Deloitte's2020CloudSecuritySurvey.Deloitte.
[101] PaloAltoNetworks.(2022).Unit42CloudThreatReport.PaloAltoNetworks.