
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
Rumaiya Naz1 , Sakshi K2 , Saniya Khanum3, Shivanagouda M Totada4 , Mr. Rajesh T H5
1Rumaiya Naz ,PES Institute of Technology and Management, Sagar Road, Shimoga
2Sakshi K , PES Institute of Technology and Management, Sagar Road, Shimoga
3Saniya Khanum , PES Institute of Technology and Management, Sagar Road, Shimoga
Mr.Rajesh T H Dept. of CS Engineering, PES InstituteofTechnologyandManagement,Karnataka
Abstract - This abstract outlines a project focused on advancing fraud detection capabilities through the integrationofcloudcomputingandsemanticdatamining.In response to the evolving landscape of financial security challenges,thisinitiativeaimstoharnessthepowerofthese technologiesformoreaccurateandefficientfrauddetection. Theprojectbuildsonthepremisethatcloud-basedsolutions providescalableandflexibleinfrastructure,enhancingthe processing and analysis of large datasets crucial for fraud detection.Semanticdata mining, withitsability to extract meaningfulpatterns,ispoisedtocontributesignificantlyto theproject'sobjectives.Byleveragingthesynergybetween cloudcomputingandsemanticdatamining,theprojectseeks todevelopaninnovativeframeworkcapableofdetectingand preventingfraudulentactivitiesin real-time.Thisabstract introducesaforward-lookinginitiativethatholdspromise foraddressingthe dynamic natureof contemporary fraud threatsintherealmoffinancialsecurity
Key Words: CLOUD COMPUTING, DATA MINING, FRAUD DETECTION, DATA MINING TECHNIQUE, FINANCIAL SECURITY
1.INTRODUCTION
In the specific context of fraud detection, data mining emergesasa critical toolforunravelingintricate patterns and anomalies within vast datasets. As businesses and financial transactions become increasingly digitized, the need for effective fraud detection mechanisms has never beenmorepronounced.Dataminingservesasacornerstone in this domain, providing a sophisticated approach to identifyingfraudulentactivitiesthatmayeludetraditional statisticalmethods.
Frauddetectionthroughdataminingextendsitsapplication to various sectors, with finance and e-commerce being primary beneficiaries. The approach involves leveraging algorithmssuchasclusteringanddecisiontreestodiscern patterns indicative of potential fraud. This is particularly crucial in uncovering irregularities such as unauthorized transactions,identitytheft,anddeceptivefinancialactivities.
Monetary extortion is a fundamental issue that influences boththemoneyareaanddailyexistenceandassumesabasic partininfluencingtrustworthyqualitiesandconfidencesin monetary areas as well as the people's cost for many
everyday items [3]. Monetary extortion is known as monetarymaltreatmentwhichisamajorworryinfinancial societymakingcolossalmisfortunestheeconomyofstates, associations, corporate areas or even people. It very well may be characterized as a demonstration of unfair or unlawfulwayofbehaving,bringingaboutausefulincrease tooneortheotherindividualorassociationfromdishonest and unlawful ways [4]. Extortion location methods were acquaintedwithdistinguishstrangeexercises,thathappened in past exchanges planning to find cases that fraudsters meantodisregardthequalitiesthattheassociationsmakein return for providing administrations. Different strategies have been proposed to distinguish extortion, yet these techniquesareinfeasiblebecauseofthesteadyadvancement of new techniques created by fraudsters or in new advancementslikedigital money. Asindicated bythe way thatanyWebbasedbusinessframeworkthatincludesonline exchanges, for example, monetary administrations is helpless against be undermined by fraudsters [5]. Hence, hostiletoextortionhasturnedintoasubjectofinterestby numerous researcherstoinvestigatetheissues connected withthisfield. Thesignificantissuesofmisrepresentation roused researchers to foster location techniques or even gaugeextortionrisk
Informationminingisamethodologyutilizedinseparating significantinformationfromagivendatasetutilizingatleast one methodologies such as factual, AI, numerical or computerized reasoning methods. Among these methodologies,varioustypesofprocedurescanbeapplied for monetary extortion like Innocent Bayes (NB), support vectormachine(SVM),CalculatedRelapse(LR),furthermore, alotmore[11].Byandlarge,informationminingisgenerally used to find monetary fakes that can be arranged into six classifications like grouping, perception, exception discovery,bunching,relapse,andexpectation[4]
Thekeyobjectivesinclude:
1. EnhancedDetectionAccuracy:Developandimplement advancedsemanticdataminingalgorithmswithinacloud infrastructuretoimprovetheaccuracyoffrauddetection. Thisinvolvesidentifyingintricatepatternsandanomalies indicativeoffraudulentbehavioracrossdiversedatasets.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
2. Real-timeFraudPrevention:Implementareal-timefraud detectionsystemthatoperatesseamlesslywithinacloud environment. The objective is to detect and prevent fraudulentactivitiesastheyoccur,minimizingpotential financiallossesanddamages.
3. Scalability and Adaptability: Design the fraud detection systemtobescalable,allowingittohandlelargevolumes of data and adapt to changing circumstances. Cloud computing provides the necessary infrastructure for scalability, ensuring the system can handle increasing dataloadsefficiently.
4. Integration of Diverse Data Sources: Enable the integrationofdiversedatasources,includingstructured and unstructured data, from various cloud-based repositories. This integration enhances the comprehensiveness of fraud detection by considering multipleaspectsandsourcesofinformation.
5. Semantic Understanding of Data: Apply semantic data mining techniques to understand and interpret the contextofdatamoreeffectively.Thisinvolvesextracting meaningfulinsightsbyconsideringtherelationshipsand semantics associated with data elements, thereby improvingtheprecisionoffrauddetection.
6. Reduced False Positives: Minimize false positives by refining the algorithms to distinguish between normal and fraudulent activities more accurately. This optimizationensuresthatlegitimatetransactionsarenot incorrectly flagged as fraudulent, providing a more reliablefrauddetectionsystem.
7. PrivacyandCompliance:Incorporateprivacy-enhancing measures to protect sensitive information during the fraud detection process. Ensure compliance with data protection regulations and standards within the cloud environment.
8. User-Friendly Interface: Develop a user-friendly interfaceforadministratorsandanalyststointeractwith thefrauddetectionsystem.Thisincludesdashboardsand reporting tools to visualize and interpret the results generatedbythesemanticdataminingalgorithms.
9. Continuous Monitoring and Updating: Establish mechanisms for continuous monitoring of the fraud detection system's performance and update the algorithms based on evolving fraud patterns and technologicaladvancements.
10. Knowledge Transfer and Documentation: Facilitate knowledgetransferbydocumentingthemethodologies, algorithms,andbestpracticesimplementedinthecloudbased fraud detection system. This ensures that the insightsgainedfromtheprojectaretransferableandcan beutilizedinfutureendeavors.
Misrepresentation location has been concentrated by specialistsandresearchersindifferentstudiesandsurvey articlesthathaveariseninscholasticdistributions.In[1720],forinstance,directedoverviewsacrossdifferentsortsof
extortiononchargecardandillegaltaxavoidanceinviewof measurable and information mining methods. Also, Delamaireetal.[21],madeaconcentrateonafewkindsof extortion on charge cards including fake extortion, liquidationmisrepresentation,andtalkedaboutlegitimate techniquestoforestallthem.Conversely,Zhang also,Zhou [22] investigated information mining procedures on monetaryapplicationsincludingthesecuritiesexchangeand misrepresentationidentification.Rajetal.[23]inspecteda fewstrategiesusedtouncovermisrepresentationonVisas. Phua etal.[24]reviewedmisrepresentationidentification information mining (DM) strategies in different sorts that are Visa, protection, and telecoms membership misrepresentation. In [6,9,25], examined a few extortion discovery procedures in medical care areas utilizing measurable techniques. Ngai et al. [7] led a survey and arrangement of a few monetary extortion discovery proceduresthatareappliedtoinformationminingcovering 49 articles going from 1997 to 2008. Sithic and Balasubramanian [10] give a broad overview of different kindsofextortiontodistinguishmisrepresentationinclinical andaccidentcoverageframeworksinviewofDMmethods. Popat and Chaudhary [13] broke down a few AI order strategieswiththeirstrategyanddifficultiestodistinguish misrepresentationinchargecards.Ryman-Tubb,Krauseet al. [12] studied and benchmarked existing strategies for installmentcardmisrepresentationlocationutilizingvaluebased volumes in 2017. The overview affirmed that main eighttechniqueshaveapragmaticpresentationtobesentin thebusiness.RichhariyaandSingh[8]presentedathorough studyandsurveyforvariousinformationminingprocedures usedtodistinguishmonetaryextortion.Intheaugmentation workofNgaietal.AlbashrawiandLowell[11]introduceda correctionformulti decadefrom2004to2015coveringDM devices to uncover extortion in monetary spaces. Nonetheless,thiswasnotextensiveenoughastheyleftout approvaltechniques,masters,andconsofmostinformation miningstrategies.Therehasbeenaperceptibleascentinthe quantityofmonetaryextortionandfalseexercisesinlater years [16]. Thusly, this propelled us to expand the Albashrawifurthermore,Lowell[11]audit.Table1shows the examination of the current audit with the current surveys connected with monetary extortion recognition applying information mining procedures. Examination is performed in view of the misrepresentation region, characterization of extortion types, advantages and disadvantagesofinformationminingmethods,dataset,and assessmentmeasurements
Thispaperbeginswithanintroductionoffinancialfraudand data mining technique to detect the fraud in Section 1 includesobjectivesandliteraturesurvey.Section2includes typesoffinancialfraudanditsbriefdescription. Section3 involvesmethodologyandproposedsolutionforthesame. Section 4includesprosandconsofdataminingtechniques.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
Finally we conclude the paper with conclusion and referencesusedforthispaperinSection5.
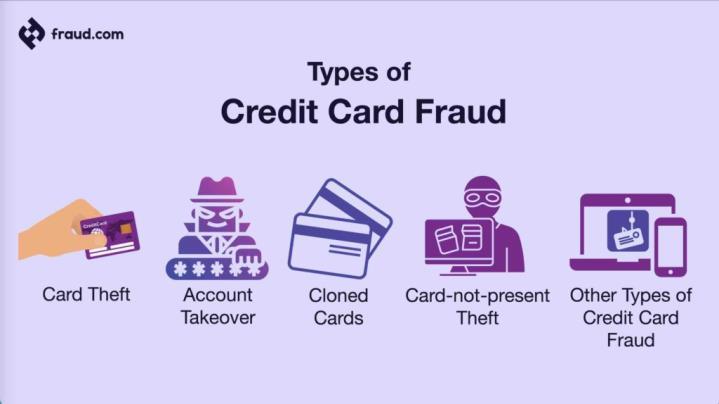
Card Theft: Cardtheftisatypeofcreditcardfraudwhere the physical credit or debit card is stolen from the cardholder.Thiscanoccurthroughvariousmeans,suchas pickpocketing, purse snatching, or theft from unattended belongings.Onceinpossessionofthestolencard,thethief can use it to make unauthorized purchases until the cardholderreportsthethefttotheissuingbank.Cardtheft posesa directrisk toindividuals,andpromptreporting is crucialtolimitpotentialfinanciallosses.
Account Takeover: Account takeover refers to the unauthorizedaccessandcontrolofanindividual'sexisting credit card account. Cybercriminals often gain access to accountcredentialsthroughphishing,hacking,orotherillicit means.Oncecontrolisestablished,thefraudstermaychange account details, including contact information and passwords,toimpedethevictim'sabilitytoregaincontrol. Account takeover can lead to fraudulent transactions, unauthorizedchanges,oreventhecreationofnewfinancial productsinthevictim'sname.
Cloned Cards: Cloned cards are created by copying the information stored on the magnetic stripe of a legitimate credit or debit card. Criminals use a skimming device to capturethecard'sdataduringalegitimatetransaction,and thenreplicatethatinformationontoa blank orfraudulent card.Theclonedcard,essentiallyaduplicateoftheoriginal, canbeusedforunauthorizedtransactions.Clonedcardfraud often involves criminals physically tampering with card readers,suchasATMsorpoint-of-saleterminals,tocapture carddatasurreptitiously.
Card Not Present (CNP) Fraud: Card Not Present (CNP) fraudoccurswhenstolencreditcardinformationisusedto makeonlineorphonetransactionswherethephysicalcard is not required. This type of fraud is prevalent in ecommerce and other remote payment systems. Criminals obtain card details through various means, including phishing,databreaches,orpurchasingstoleninformationon the dark web. They then use these details to make unauthorizedonlinepurchases,exploitingthefactthatthe physicalcardisnotneededforthetransaction.
Financial Statement Fraud: Financialstatementfraudisa deceptive practice wherein a company deliberately manipulatesitsfinancialstatementstopresentadistorted and misleading picture of its financial health and performance. This type of fraud is characterized by intentionalmisstatements,omissions,ormisrepresentations infinancialreports,aimingtodeceivestakeholderssuchas investors, creditors, regulatory bodies, and the public. Financialstatementfraudcanhaveseriousconsequencesfor acompany'sreputation,stockvalue,andlegalstanding.
Embezzlement: Embezzlement is a white-collar crime involvingthemisappropriationortheftoffundsentrustedto an individual, often an employee, for personal gain. This deceptiveacttypicallyoccurswithinthecontextofaposition of trust, where the perpetrator has access to financial resources or assets belonging to an organization. Embezzlementischaracterizedbythefraudulentdiversion offundsorpropertythatwereentrustedtotheembezzler forlegitimatepurposes.
Automobile Insurance Fraud: Automobileinsurancefraud refers to deceptive activities aimed at exploiting car insurancepoliciesforillicitfinancialgain.Thistypeoffraud encompassesvariousschemesperpetratedbypolicyholders, individuals,ororganizedgroups,resultinginincreasedcosts forinsurersandhigherpremiumsforhonestdrivers.
Healthcare Insurance Fraud: Healthcareinsurancefraud involves deceptive practices aimed at exploiting the healthcareinsurancesystemforfinancialgain.Perpetrators mayincludepolicyholders,healthcareproviders,andeven organized crime groups. Healthcare insurance fraud contributes to rising healthcare costs, compromises the integrityofthehealthcaresystem,andcanresultinfinancial lossesforinsurers.
Securities and Commodities Fraud: Securities and commodities fraud involve deceptive practices within

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
financialmarkets,impactingthetradingofsecurities(stocks, bonds,etc.)andcommodities(preciousmetals,agricultural products, etc.). Perpetrators may include individuals, financialinstitutions,orcorporationsseekingtomanipulate market conditions for personal gain. Securities and commodities fraud undermines market integrity, erodes investor confidence, and can have far-reaching consequences.
Calculatedrelapseisoneofthestrongclassification instrumentsacquiredbyAIfromtheheld ofmeasurements.Itisastraightforwardyetstrongmethod fordisplayingbinomialresultswithatleastone anticipatingfactors.Itestimatestheconnectionbetweenthe indicatorandtheobjectivefactorsbyworkingout probabilities utilizing a calculated capability, which is the totalstrategiccirculation.Thevectorβ=(β1,β2,β3,…,βn) addresses the coeficients and X = (X1, X2, X3,… , Xn) addressesthedifferentindicatorsinthedatasetandϵisthe model'smistake.
1)
Equ.1addressestheessentialcalculatedcapability. The likelihood of the classes not set in stone by the logarithmiccapabilitygivenbeneathinEqu.2
l = logb ( ) = β0 + β1 X1 + β2 X2 (Equ.2)By basic
mathematical control to Equ. 2, we get p, which is the likelihoodoftheminorityclass
In light of closest neighbors for a given question point, a non-parametric strategy KNN is contrived. For guaranteedinformationalcollection,theeuclidiandistanceis figuredbetweentheinformationalindexandtheaccessible informational index. Among the informational index, the dataofinterestwithnegligibleEuclidian(Equ.3)
Equ.3showstheEuclideandistancecapability.
InnocentBayesisaclassi cationmethodinlightof BayesHypothesisofcontingentlikelihood.Itworksunder thesuspicionthattheindicatorsareautonomous.Theclass of the groundbreaking perceptions are identified and it ascertainsitslikelihood.Thelikelihooddependsonupsides of the factors. This procedure lets us know how different factorsin uencethelikelihoodofanoccasion.
P(Y/X1,X2,...,Xn)=(Equ.4)
Equ.5showsBayesiancontingentprobabilitiesofeachclass regardingtheindicatorsX1,X2,….,Xn

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
Achoicetreeisa treeinformationstructurewhichassists withshowingupatinductiondeductioninlightofconditions toanticipatetheresults.Aclasscharacteristicisaddresseda leaf hub and each middle of the road hub is parted to sub hubs in light of trait. The way gotten from Root to leaf is utilizedforshapingtheclassificationrule. Informationisclassifiedbyutilizingthetraitsofeveryhub.It isutilizedforadditionalclassificationandrelapsemodels.
Very much like Choice tree, irregular backwoods can likewisebeutilizedforbothclassi cationandrelapseissues. Itisessentiallyutilizedforclassi cationissues..Verymuch like a genuine backwoods is comprised of many trees, irregularbackwoodsisonlythemixofnumerousdynamic trees.Hubsofthearbitrarywoodlandaremadeoutofchoice trees,everyonegettingtheexpectationfromthedataset.Itis agatheringmethodcomprisingofdifferenttrees.Themain issueis the over fitting of themodel.Figures presentsthe workingoftheIrregularBackwoodsmodel.
SupportVectorMachine(SVM)isamanagedAIcalculation. Ittendstobeutilizedtodealwithboth
classification and relapse issues. Very much like irregular timberlandSVMisessentiallyutilizedasaclassifier.InSVM, theinformationfocusesareplottedinalayeredspace,where thedirectionistheworthofthe
factors. Presently the classi cation can be performed by findingthehyper-plane.Figmakessenseofthepartingofthe dataofinterestinan-layeredspace
3.2
OutlineofExistingFrameworksInvolvingCNNforMonetary MisrepresentationDiscovery:
1.Transaction Example Examination: CNNs can be used to dissect exchange designs. In this situation, exchange informationischangedintoapicturelikeconfiguration(like aheatmap)whereexamples,irregularities,andrelationships canbespatiallybrokedownbytheCNN.
2.SequenceInvestigationforTime-SeriesInformation:For monetarytime-seriesinformation(likestockcosts,account adjustsoverthelonghaul),CNNscanbeutilizedtorecognize dubiousexamplesdemonstrativeoffakeexercises.Thetimeseriesinformationisorganizedinamannerthatpermitsthe CNN to deal with it likewise to how it would handle a successionofpictureoutlines.
3.IntegrationwithDifferentInformationTypes:CNNscanbe joined with different types of information applicable to monetary exchanges, like text information from exchange portrayals. Regular Language Handling (NLP) strategies preprocess the text, which is then incorporated with mathematicalinformationforCNNinvestigation.
4.Network Examination: In situations where exchanges structure an organization (like cash moves between accounts),CNNscanbeutilizedtobreakdownthedesignof theseorganizationstorecognizepossibleextortion.
Benefits:
•Highlight Extraction: CNNs are superb at independently extricating applicable elements from complex datasets, which is significant for distinguishing modern misrepresentationdesigns.
•Taking care of Enormous Volumes of Information: These organizationscandealwithhugedatasetscommonplacein finance, making them reasonable for large information examination.
•Flexibility: They can adjust to new sorts of extortion by retrainingonrefresheddatasets.
•Proficiency: Once prepared, CNNs can handle new exchangesrapidly,takingintoconsiderationclosetoongoing extortionlocation.
Limits and Difficulties:
•InformationPortrayal:Onetestistheportrayalofmonetary informationinastructurethatsuccessfullyuseCNN'sassets. Not at all like pictures, monetary information may not intrinsicallyhaveaspatialortransientconstruction.
•InformationProtection:Monetaryinformationisdelicate. Guaranteeingprotectionandconsistencewithguidelineslike GDPRispivotal.
•Intricacy and Overfitting: CNNs can be perplexing and inclined to overfitting, particularly while possibly not appropriately regularized or on the other hand whenever preparedondeficientlydifferentinformation.
•Reliance on Information Quality: The exhibition of CNNs vigorously relies upon the quality and amount of the preparationinformation.
•Interpretability: Choices made by CNNs can be murky, making it hard to comprehend the reason why certain exchangesarehailedasdeceitful.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
3.3 Strategy Clarification
Module 1:
Inthismodule,wehaveloaded,pre-handledandvisualized thedataset.Themethodisasperthefollowing;
1. Crude information is separated from the information archive, and information stacking includes bringing the informationintodatasets.
2. Information preprocessing, including dealing with missing qualities, encoding downright factors, and scaling mathematical highlights, is performed to make the informationappropriateforexamination.
3. Representation strategies are utilized to give bits of knowledgeintothedispersionofinformation,particularly zeroing in on the count of fake installments. This aides in grasping the information and distinguishing any lopsided characteristics.
Module 2:
In this module we have assembled Information Element ExtractionutilizingAICalculation
1.Machine learning calculations are used to remove significantfeaturesfromthepreprocessedinformation
2.TechniqueslikeDestroyed(ManufacturedMinorityOverexaminingProcedure)mightbeappliedtoaddressawkward natureinthedataset,particularlyinextortionrecognition wherefakeexchangesarefrequentlyuncommon
3. Include extraction expects to recognize examples and qualitiesthatarecharacteristicoffraudlentexercises
InthismodulewehavepreparedmodelutilizingPrescient Examination:
1.Buildaprescientmodelutilizingtheremovedelementsto dissectandforeseedeceitfulexercises.
Clarification:
•The dataset is parted into preparing and testing sets to prepareandassessthemodel.
•Characterizationcalculations,forexample,AImodels,are utilizedtoanticipateregardlessofwhetheranexchangeis deceitful.
•Assessment measurements like disarray grid, grouping report, ROC bend, and AUC are utilized to evaluate the model'spresentation.
Module 4:
This module demonstrates plan of Front End for Client Application:
Foster an easy to use front finish to cooperate with the cloud-upgradedinformationminingframework.
Clarification:
AUIisintendedtopermitclientstohandilyinterfacewith theframework.
The front end gives functionalities to information input, modelexpectations,andrepresentationofresults.
Itimprovesclientexperienceandworkswithproductiveuse oftheextortiondiscoveryframework
Proposed arrangement
Cloud Framework Arrangement:
Pickasolidandsecurecloudstage(e.g.,AWS,Purplishblue, GoogleCloud)tohavetheextortionlocationframework.
Use versatile cloud administrations like processing occurrences,stockpiling,andinformationbasestodealwith shiftingresponsibilities.
Information Ingestion and Preprocessing:
Gather and ingest information from different sources, including exchange logs, client profiles, and verifiable information.Preprocesstheinformationtodealwithmissing qualities,anomalies,andirregularities.
Use cloud-based information capacity arrangements like Amazon S3 or Sky blue Mass Stockpiling for proficient informationstockpiling.
Semantic Information Displaying:
Apply semantic information displaying to address the connectionsandimplicationsbetweenvariousinformation components.
Use cosmology based models to characterize elements, qualities,andconnectionsinanormalizedway.
Make a misrepresentation recognition cosmology that catches the space explicit information connected with extortiondesigns.
Include Extraction:
Distinguishimportantelementsforextortionidentification, consideringvalue-baseddesigns,clientconduct,andcontext orienteddata.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
Utilizesemanticthinkingtoextricatecomplexhighlightsin lightoftheconnectionscharacterizedinthephilosophy.
Influence cloud-based AI administrations for productive componentextractionandmodelpreparation.
Train AI models, for example, peculiarity location calculations,choicetrees,oroutfitstrategies,onthemarked dataset.Integrate semantic data to upgrade the's comprehensionmodelmightinterprettheinformationand furtherdevelopprecision.
Exploit cloud-based AI stages like AWS SageMaker or Sky blueAIformodelturnofeventsandarrangement.
4.PROS AND CONS
Pros:
1.Versatility: Cloud-based arrangementsofferadaptability considering the handling of huge volumes of information that are commonly experienced in misrepresentation recognitionsituations.
2.Cost-Viability:Cloudbenefitsfrequentlyworkona paymore only as costs arise model, which can be more savvy thansettingupandkeepingupwithon-premisesfoundation.
3. Availability: Cloud-based arrangements give openness from anyplace a web association, empowering remote observing and the board of misrepresentation location processes.
4.AssetEnhancement:Cloudstagesfrequentlygiveassets on-request, considering effective allotment and use of registeringassetsinlightoffluctuatinginterest.
5.Reconciliation:Cloudconditionsworkwithjoiningwith different information sources and administrations, empowering consistent consolidation of assorted informationtypesandhotspotsformoreextensive misrepresentationlocation.
6. Cooperation: Cloud-based arrangements support coordinated effort among various partners, considering ongoing sharing of bits of knowledge and cooperative examination to improve misrepresentation discovery viability.
7. Security Enhancements:Data mining can help organizationsrecognizeandforestallextortion,distinguish securitydangers,andsafeguarddelicatedata.
Bybreakingdowndesignsininformation,youcanrecognize peculiaritiesandpotentialsecuritybreaks.Thispermitsyou togotoproactivelengthstoforestallsecurityoccurrences andsafeguardyourbusinessandclients.
8.TreatmentofHazardandMisrepresentation:Information miningcanhelpinrecognizingdangersandextortionthat maynotbedistinguishedthroughconventionalmethodfor information examination as it uncovers troublesome exampleswhichmaynotbequicklytakennote.Monetary, legitimate,andonlineprotectiondangerscanbetakencare of appropriately through information mining and steps/measures to deal with such dangers can be created fromtheoutcomesgotten.
9. Cross-Area Experiences: Semantic information mining strategiescanincorporateinformationfromdifferentspaces, likemonetaryexchanges,clientconduct,andoutergamble factors.Thiscross-spaceexaminationgivesexhaustivebitsof knowledge into false exercises spreading over different aspects.
10. Cross-Channel Identification: Semantic information mining works with cross-channel recognition of deceitful exercisesacrossnumeroustouchpoints,likeinternetbased exchanges,versatileconnections,andactualareas,givinga morecomprehensiveperspectiveonextortionrisk.
Cons:
1.SecurityConcerns:Puttingawaydelicateinformationin the cloud raises security concerns, including information breaks, unapproved access, and consistence issues. Appropriateencryptionandaccesscontrolsarefundamental tomoderatethesedangers.
2. Information Security: Consistence with information protection guidelines (e.g., GDPR, HIPAA) can be testing whileutilizingcloud-basedarrangements,particularlywhile managing by and by recognizable data (PII) or delicate monetaryinformation.
3. Idleness: Contingent upon the cloud supplier and organizationframework,theremightbedormancygivesthat influence the continuous idea of extortion recognition frameworks,especiallyinhigh-throughputconditions.
4. Reliance on Web Availability: Cloud-put together arrangements depend with respect to web availability, making them powerless against blackouts or organization disturbances that can influence the accessibility and executionofmisrepresentationrecognitionprocesses.
5.MerchantLock-In:Embracingaparticularcloudsupplier's administrations might prompt seller secure in, restricting adaptabilityandmakingitchallengingtorelocatetoelective arrangementslateron.
6. Information Sovereignty:Compliance with guidelines in regards to the capacity and handling of information in unambiguousgeographicdistricts(informationpower)can present difficulties while involving worldwide cloud supplierswithserverfarmsinnumerouswards.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
7.PotentialforMistakes:Informationminingiscertainlynot anidealinteraction,andthereisgenerallythepotentialfor blunders.Thesemistakescanbebroughtaboutbyvarious elements, including human blunder, information quality issues,andspecializedproblems.Asanoutcome,itisvitalto painstakinglysurveytheconsequencesofanyinformation mininginvestigationtoguaranteethattheyarepreciseand solid.
8. It Requires Huge Datasets to Be Viable: One of the disadvantages of information mining is that it requires enormousdatasetstobesuccessful.Examplesandpatterns can be gotten from a bigger dataset than from a little one sincedatacanbegatheredbetterwhengivenanadequate numberofinformation.
9. Information Elicitation: Securing and formalizing space information for semantic information mining requires critical exertion and aptitude from area specialists. Informationelicitationcyclesmightbetediousandabstract, promptinglikelypredispositionsorerrorsinthesemantic portrayal.
10. Information Administration: Guaranteeing powerful informationadministrationworkson,includinginformation quality administration, metadata the board, and access control, becomes pivotal in semantic information mining conditionstokeepupwiththehonestyanddependabilityof informationutilizedinmisrepresentationlocation.
5. CONCLUSIONS
Misrepresentation discovery is a fundamental piece of current monetary foundations, particularly in huge and delicatespecializedregions.Therehasbeenanobservable ascentin the quantityofmonetarymisrepresentationand false exercises lately. Conversely, a few examinations and overviews in monetary misrepresentation discovery have beenproposedtoresolvetheseissues.Nonetheless,thiswas not far reaching enough as they left out some monetary extortion types, approval strategies, geniuses, and cons of most information mining procedures. In this paper, we introduced an extensive update of the most recent informationmining(DM)proceduresutilizedinidentifying misrepresentationinmonetaryregionsfromtheyear2013 to2023andorderedtheminviewoftheirsortsofextortion andmethods.
Cloud-Upgraded Semantic Information Mining marks a groundbreaking cooperative energy between distributed computing's versatility and semantic innovations' logical lavishness.Thisjoiningspeedsupinformation examination as well as improves the nature of bits of knowledge, encouragingjointeffortandinterdisciplinaryexploration.
This Task gives an overall thought of information mining, information methods and information mining in different fields. Information Disclosure based Choice Emotionally
supportive network (KDDS) which will fit for giving ideal choiceforresearchinScienceandInnovationinlightofthe interestofthegeneralpublic.Whenevergroupsarefound, they can be named and considered as classes of models. Subsequently,amanagedlearningmethodcanbeutilizedto getextrainformationfromtheseclasses.
[1] Khaled Gubran Al-Hashedi; Pritheega Magalingam, “Financial fraud detection applying data mining techniques”,IEEE2019
[2] Dr.Radhakrishna Rambola;Prateek Varshney;Prashant Vishwakarma, “Data Mining Techniques for Fraud DetectioninBankingSector”,IEEE2020.
[3] AliRezaMohseniIslamicAzadUniversity;QaemShahr BranchQaemShahr,“SaasCloudServiceApplicationsto SolveDataminingProblems”,IEEE2021.
[4] Puninder Kaur;Avinash Sharma;Jasmeen Kaur Chahal;TarunaSharma;VidhuKiranSharma,“Analysis on Credit Card Fraud Detection and Prevention using Data MiningandMachineLearning Techniques”,IEEE 2021.
[5] ArushiJain;SarveshShinde,“AComprehensiveStudyof DataMining-basedFinancialFraudDetectionResearch”, IEEE2019.
[6] MatinN.Ashtiani;BijanRaahemi,“Intelligentfraud detectioninfinancialstatementsusingmachine learninganddatamining”,IEEE2021.
[7] Dhiman Sarma; Wahidul Alam; Ishita Saha; MohammadNazmulAlam;MohammadJahangirAlam, “Bank Fraud Detection using Community Detection Algorithm”,IEEE2020.
[8] AditiSingh;AnoushkaSingh;AnshulAggarwal;Anamika Chauhan, “Design and Implementation of Different Machine Learning Algorithms for Credit Card Fraud Detection”,IEEE2022.
[9] B. B. Sagar; Pratibha Singh; S. Mallika, “Online transactionfrauddetectiontechniques:Areviewofdata miningapproaches”,IEEE2016.
[10] Aanchal Sahu; Harshvardhan GM; Mahendra Kumar Gourisaria,“A Dual Approach for Credit Card fraud detection using Neural Network andData Mining Techniques”,IEEE2020.
[11] QasemA.Al-Radaideh;MahmoudM. Al-Zoubi, “Adata mining based model for detection of fraudulent behaviourinwaterconsumption,” IEEE2018.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN: 2395-0072
[12] M.Vamsi Krishna; J.Praveenchandar , “Comparative AnalysisofCreditCardFraudDetectionusingLogistic regressionwithRandomForesttowardsanIncreasein AccuracyofPrediction”,IEEE2022.
[13] Nityanand Sharma; Vivek Ranjan , “Credit CardFraud Detection : A Hybrid of PSO and K-Means Clustering UnsupervisedApproach”,IEEE2023.
[14] Rajni Jindal, Malaya Dutta Borah “A Survey On Educational Data Mining And Research Trends” “InternationalJournalofDatabaseManagementSystems (IJDMS)”Vol.5, No.3, June 2013 DOI : 10.5121/ijdms.2013.530453.
[15] SonalKataria;MdTabrezNafis,“InternetBankingFraud DetectionUsingDeepLearningBasedonDecisionTree andMultilayerPerceptron”,IEEE2019.
[16] Tao Zhang; Senyu Gao, “Graph Attention Network FraudDetectionBased On Feature Aggregation”, IEEE 2022.
[17] Aayushi Verma; Anu Taneja; Anuja Arora, “Fraud detection and frequent pattern matching in insurance claimsusingdataminingtechniques”,IEEE2017.
[18] Abdulwahab Ali Almazroi; Nasir Ayub, “Online PaymentFraudDetection Model Using Machine LearningTechniques”,IEEE2023.
[19] SamikshyaDash;SimanchalaDas;S.Sivasubramanian; N. Kalyana Sundaram; Harsha K G; T. Sathish, “Developing AI-basedFraudDetection Systems for BankingandFinance”,IEEE2023.
[20] S. Alimolaei, “An intelligent system for user behavior detectioninInternetBanking,in:FuzzyandIntelligent Systems (CFIS)”, 2015 4th Iranian Joint Congress on, IEEE,2015,pp.1–5.