
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net
p-ISSN:2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net
p-ISSN:2395-0072
P.AKSHAYA1, Dr.E.SREE DEVI.,M.E., Ph.D.,2
1PG Student, Dept. of Electronics And Communication, Rohini College of Engineering and Technology, Kaniyakumari,Tamil Nadu, India.
2Professor, Dept. of Electronics And Communication, Rohini College of Engineering and Technology, Kaniyakumari, Tamil Nadu, India.
Abstract Gadgets equipped for catching pictures should be visible in places as normal as jam-packed stores, workplaces, schools, or even at home, looking like reconnaissance cameras, cell phones, robots, and expert and activity cameras. A Colour Filter Array (CFA) is included in the majority of devices that can take pictures. Pictures produced by these gadgets can be investigated to distinguish the so known CFA antiques left by demosaicing strategies. These relics are significant in advanced picture criminology since they demonstrate helpful for deciding the realness of a picture. In existing work, examination of the green band of the Bayer channel, ignoring the data in the leftover groups. In this undertaking a cycle to gauge the example left by CFA curios no matter what their setup is proposed, which can be utilized no matter what the size or varieties utilized by the channel, or even in various variety spaces, getting in this way new wellsprings of data for legal examination. The awareness of these proposition to post-handling techniques, for example, pressure and separating will likewise be audited. JPEG pressure is a lossy pressure strategy ordinarily used to diminish the document size of pictures by disposing of some picture information. This interaction can present antiques and debase picture quality, making it trying to identify any altering or adjustments that could have been made to the picture. The proposed strategy has the capacity to distinguish controls notwithstanding the difficulties presented by elevated degrees of JPEG pressure. It proposes that the technique has a more elevated level of vigor or aversion to recognize irregularities, relics, or examples that might show altering, no matter what the pressure prompted mutilations in the picture.
Key Words : JPEG Compression, Color Filter Array, Demosaicig, image manipulation
Image tampering location is an advanced field that breaks down the legitimacy of a suspect picture. The intention of picture altering is to make bogus ideas about a picture
according to the watcher's viewpoint. In the present advanced world, such altered pictures can be made, circulated and sent without any problem. The goal behind thealteringcouldbenoxious,forexample,inthephotosof political social affairs, war fields, logical diaries articles andsoon.,orontheother handcouldbeinnocuousas on account of nature photos, photos of landmarks, and so forth. Picture with innocuous duplicate move altering. Messing with innocuous aim adds some photograph impacts and does changes like obscuring, contrast improvement, splendor modification and variety. In some cases, modification in a picture is finished to work on the visualnatureofthepicturethroughactivities,forexample, contrast change, brilliance change, extending, low pass/highpasssifting,andsoon.Bethatasitmay,change in a picture should likewise be possible with a malignant goalwhichmighthavebearingonlegitimatecases,proofin court,policeexamination,criticismandmisrepresentation cases,copyrightissues,legislativeissues,photojournalism, big names ways of life, style explanations, excellence and wellness items, diversion area, promotions, wrongdoing against teenagers, clinical science, biometric pictures and scientificcases.[1]
Alatawi et.al. [2] proposed Computerized picture steganography review and examination. These days, steganography articles, particularly overviews, seldom expressly characterize steganography in view of its objectives. Thus, this overview adds to characterizing steganographic research in view of objectives and its appraisals. This paper likewise audits the utilization of evaluationdevicesinsideandoutonthegroundsthatit is firmlyconnectedwiththeobjectiveofsteganography.
ArmasVegaet.al.[3]proposedDuplicatemovefalsification recognition strategy in light of discrete cosine change blockshighlights.Theyperformsidentificationofduplicate movechangesinsideapicture,utilizingthediscretecosine change.Thequalitiesgotfromthesecoefficientspermitus to acquire move vectors, which are gathered together.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net
Using a resilience edge, it is feasible to decide if there are districtsreorderedinsidetheinvestigatedpicture.
In computerized variety imaging, the crude picture is regularly gotten through a solitary sensor covered by a variety channel exhibit (CFA), which permits just a single variety part to be estimated at every pixel. The system to recreate a full variety picture from the crude picture is known as demosaicking. Since the CFA might cause irreversible visual antiquities, the CFA and the demosaicking calculation are essential to the nature of demosaicked pictures. Luckily, the plan of CFAs in the recurrence space gives a hypothetical way to deal with taking care of this issue. In any case, practically all the current plan strategies in the recurrence space include extensivehumanexertion.[4].
Bianchi, T et.al. [5] proposed Identification of neutral twofoldJPEGpressure.Theyproposeastraightforwardyet dependable technique to identify the presence of neutral twofold JPEG pressure (NA-JPEG). The technique depends on a solitary element which relies upon the number periodicity of the DCT coefficients when the DCT is registered by the framework of the past JPEG pressure. Regardlessofwhethertheproposedhighlightisprocessed depending just on DC coefficient measurements, a straightforward edge indicator can characterize NA-JPEG pictures with further developed precision as for existing strategiesandonmoremodestpicturesizes.
Chierchia, G et.al. [6] proposed Bayesian-MRF Approach for PRNU-Based Picture Fraud Location. Designs altering projectsofthelastagegivealwaysincredibleassets,which take into account the correcting of computerized pictures leaving practically zero hints of altering. The dependable location of picture fabrications requires, in this way, a battery of reciprocal devices that exploit different picture properties.Proceduresinviewofthephotographreaction non-consistency (PRNU) clamor are among the most significant such devices, since they don't recognize the embedded item yet rather the shortfall of the camera PRNU, a kind of camera unique finger impression, managing imitations that evade most other discovery methodologies.
Dang, L et.al. [7] developed Face picture control recognition in light of a convolutional brain organization. Facial picture control is a specific occurrence of computerized picture altering, which is finished by compositinga districtfrom one facial pictureintoanother facialpicture.Counterfeitpicturescreatedbyfacialpicture control currently spread like quickly on news sites and interpersonal organizations, and are viewed as the best
p-ISSN:2395-0072
dangertosqueezeopportunity.Pastexplorationdepended intensely on carefully assembled elements to examine altered locales which were wasteful and tedious. This paper presents a system that precisely identifies controlled face picture utilizing profound learning approach.
p Color Filter Array (CFA) demosaicing based tamper detection techniques which can be used to detect both local and global tampering operations. The proposed procedures focus on no particular activity except for are material to different tasks like joining, correcting, repressure, resizing, obscuring and so on. The procedures depend on processing a solitary component and a straightforward limit based classifier. The viability of the methodologywastriedmorethangreatmanyreal,altered, andPCproducedpictures.[8].
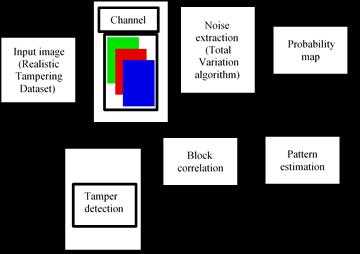
A series of filters detect various wavelengths, or "light colors," before the light enters directly through the lens. The cycle begins with a smoother or ''denoised'' form of the first picture, expected to unveil relics that are not effectively apparent to the exposed natural eye. Antiquity location: Accepting that CFA or comparative relics are availableonapicture,occasionalconductinadecentblock size is normal. The proposed strategy can identify an example left by JPEG and other obscure examples, potential consequences of equipment deformities or restrictive post-handling calculations. Design identification: The periodicity of the curios permit the examples to be characterized as a �� × �� cluster, with �� a modest number, regularly, 2, 4, or 8. Using a similarity analysis, it is possible to distinguish between the altered and original regions in a tampered image. Include extraction: When intermittent examples have been

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net
recognized, the accompanying step is to play out a comparability examination of each block against the got design. The worth proposed to quantify likeness is a relationship between's the dissected subblock and the block design, creating blended circulation. Alter recognition: The final step is to detect the suspicious manipulation after generating a feature map and synthesizinginformationfromeachpartitionblock.
Columbia Uncompressed Image Splicing Detection dataset is used. The Realistic Tampering Dataset is also used for the proposed system. The images were captured by four differentcameras:Sonyalpha57,Canon60D,NikonD7000, NikonD90.

SeparateeachRGBvarietychannel,(orthechannelsasper the considered variety space). The RGB variety model addressescolorsutilizingblendsofred,green,andblue.By extricating individual channels, we can isolate the picture into its constituent variety parts. Removing individual channelscanbeaforerunnertovarietychangeorrevision tasks. In the event that there's a variety cast in a picture, we could change the force of explicit channels to address thegeneralvarietybalance.
Apply the total variation (TV) denoise algorithm to each channelofthecolourimage.TotalVariation(TV)denoising is a popular method used in image processing for removing noise while preserving edges and other important image features. It depends on the standard of limiting the complete variety of the picture, which estimates how much variety or change between adjoining pixelpowers.Bylimitingtheabsolutevariety,thestrategy plans to lessen how much unexpected changes (or
p-ISSN:2395-0072
varieties) in pixel forces, which are frequently brought aboutbyclamor.
2.4
ExpectingthatCFAorcomparativecuriosareavailable on a picture, occasional conduct in a proper block size is normal. The absence of this way of behaving or irregularities found is helpful to distinguish potential controls. To display the way of behaving of the curios, commotion can be straightforwardly inspected or further changed for further developed results, e.g., utilizing a likelihood.Testingforvariousconceivableexhibitsizeshas driven us to see that the proposed technique can distinguishotheroccasionalexamplestoo,forexample,an example left by JPEG and other obscure examples, potential consequences of equipment deformities or restrictivepost-handlingcalculations.
From the blunder framework, it is feasible to get a reasonableexampleevenbyapplyingbasicproportionsof focal propensity, for example, mean or middle insights applied component wise on the arrangement of ��×�� blocks. In the green channel, we see that blunders in gainedpositionsarebiggerinoutrightworth.Thisconduct rehashes in the red channel. At long last, in the blue channel,anotherpeculiarityisapparent:ina2×2square, 3outof4blundersarenegativeornearnothing.Thisdata will demonstrate helpful to identify controls not uncovered by examining the green channel alone. One more example has arisen in the wake of carrying out a similarmethod,thistime,subsequenttolooking ata JPEG compacted picture. Pixels in edges of each block present higher outright qualities than those in the focal 6 × 6 square.Thisgivesproofthatthepicturehasbeenexposed to smoothing in 8 × 8 blocks because of DCT change and quantisation; processes related to the standard JPEG pressurecalculation.
To have a better understanding of the behaviour or observed patterns detected in the residual errors map, furthertransformationsmaybeusedtonormalisedata.
This becomes necessary, since large errors may mislead further analysis since very large values (either positive or negative) can be observed in regions where the scene shows abrupt changes, for example, in edges or a surface with texture. A first proposal is to use a transformation defined.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net
f(x)=erfc(|x|/(σ√2)) (1)
Where��canbeestimatedasthestandarddeviationofthe errorsoraselectedsubset, anderfcisthecomplementary errorfunction,definedas
erfc(x)=1-2/√π∫_0^x▒e^(-t^2)
This transformation can be considered as a probability maporamembershipfunction:errorsnearzerowillgeta valuecloseto1(interpolated),while errorsfar fromzero, get values close to 0 (acquired). Higher values should be assigned to pixels that belong to a certain close more frequently.
The periodicity of the curios permit the examples to be characterizedasa ����exhibit,with ��a modestnumber, generally, 2, 4, or 8. In an altered picture, changed and unique locales are supposed to have unique, which might become recognizable utilizing a similitude examination. A few troubles distinguished with this approach are the point at which the change creates an ideal grafting of the relics.Thisismorenormalwhentheperiodicityislow.
The periodicity of the artefacts allow the patterns to be defined as a �� × �� array, with �� a small number, commonly, 2, 4, or 8. In a tampered image, modified and originalregionsareexpectedtohavedifferent,whichmay become identifiable using a similarity analysis. Some difficulties detected with this approach are when the modification produces a perfect splicing of the artefacts. Thisismorecommonwhentheperiodicityislow.
Subsequent to getting a component map, and combining datafromeachblockintheparcel,thelaststepcomprises in playing out the recognition of the dubious control. Howeveritisattractivetohaveacompletelyprogrammed approach,theproposedtechniqueactuallyrequireshuman examination, since few out of every odd outcome from a programmeddivisionstrategyisgood.
Characterizingmeasurestogiveaprogrammedreactionto discovery is a troublesome undertaking, and visual investigation and further postprocessing should be expected to get a precise outcome. Said this, the relative examination here characterizedshould be consideredas a
p-ISSN:2395-0072
way for approving proposed methods and contrasting victories.





International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net

(a) Demosaiced Image (b) Artefact detectio

Fig-4 Local Block Matching
Table-1 Comparison of PSNR, SSIM Values
CONCLUSION
Different existing works using fuss features were considered and considered to get a handle on their advantages and blocks and encourage our proposed
p-ISSN:2395-0072
strategy. From this, an all the more impressive methodology could be portrayed, and a system can be represented and extrapolated to other existing strategies, givingmorenoteworthyflexiblility.JPEGcollectiblesmake surface decline in pictures due the lack of information in high frequencies after quantisation. An overview and relationshipsagainsttoptierprojectswatchingoutforthe revelation of controls using CFA knick-knacks are performed. Indeed, even pictures exposed to elevated degrees of JPEG pressure can be identified utilizing the proposed technique. It is doable to see that this improvement licenses acknowledgment of extra changes. Believeitornot,everypreviousworksthatconsideredthe green channel alone show near results. The essential disadvantageofthisapproachliesinthereductionofopen data, which would expect of greater blocks, since the models are decreased, for this present circumstance, by a half. By and by, palatable outcomes have been accomplished with blocks as little as 8 x 8. Substantially more, achieves the green band are basically undefined, having as a main concern that the subsample of missteps showsasimilarapproachtoactingthantheprincipalgame planofacquired(presented)values.
[1] Minati Mishra, unesh Chandra Adhikary, Digital Image Tamper Detection Techniques - A Comprehensive Study.June2013.
[2] Alatawi, H., & Narmatha, C. (2020). The secret image hiding schemes using steganography- survey. In 2020 International conference on computing and informationtechnology.
[3] Armas Vega, E. A., González Fernández, E., SandovalOrozco,A.L.,&GarcíaVillalba,L.J.(2021).Copymoveforgerydetectiontechniquebasedondiscretecosine transform blocks features. Neural, Parallel & Scientific Computations,33(10),4713–4717.
[4] Bai, C., Li, J., Lin, Z., & Yu, J. (2016). Automatic designofcolorfilterarrays inthefrequencydomain.IEEE TransactionsonImageProcessing,25(4),1793–1807.
[5] Bianchi, T., & Piva, A. (2011). Detection of nonaligned double JPEG compression with estimation of primary compression parameters. In 2011 18th IEEE Internationalconferenceonimageprocessing.
[6] Chierchia,G.,Poggi,G.,Sansone,C.,&Verdoliva,L. (2014). A Bayesian-MRF approach for PRNU-based image forgery detection. IEEE Transactions on Information ForensicsandSecurity,9(4),554–567.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 05 | May 2024 www.irjet.net p-ISSN:2395-0072
Dang, L. M., Hassan, S. I., Im, S., & Moon, H. (2019). Face image manipulation detection based on a convolutional neuralnetwork.[6] Expert Systems with Applications,129,156–168
[7] Dirik, A. E., & Memon, N. (2009). Image tamper detection based on demosaicing artifacts. In Proceedings of the IEEE International conference on image processing (pp.1497–1500).Cairo,Egypt.
© 2024, IRJET | Impact Factor value: 8.226 | ISO 9001:2008
| Page1060