

Multiple Cyber Attack Detection using Machine Learning
*1 Prof. Department of Comp. Eng. SCOE, Pune, India. *2,3,4,5 Student, Department of Comp. Eng. SCOE, Pune, India.
Abstract - In the current landscape of cybersecurity, the efficacy of traditional single-layer defences has significantly diminished due to the relentless evolution of cyber threats. Attackers continuously refine their tactics, techniques, and procedures, rendering organizations and individuals vulnerable to increasingly sophisticated attacks. In response, there is a growing recognition of the necessity to implement multiple layers of defence to mitigate these risks effectively. This paper proposes a proactive and comprehensive approach termed "multiple cyber-attack detection." This approach entails the strategic integration of diverse tools, techniques, and strategies aimed at enhancing the detection and response capabilities against cyber threats. By adopting a multifaceted approach, organizations and individuals can better safeguard their digital assets and sensitive information froma myriad of potential threats. However, the success of such initiatives hinges upon the clear definition of project scope, encompassing goals, resources, and timelines. Additionally, there is a crucial need for adaptability to adjust the scope in alignment with the evolving threat landscape and the changing needs of the organization. This paper underscores the imperative of adopting a dynamic and flexible cybersecurity strategy to ensure robust protection against the ever-evolving cyber threat landscape.
Key Words: Cybersecurity, Multi-layered defence, Cyber threats,Attacktactics,Threatdetection.
1.INTRODUCTION
Cyberattacks have become a ubiquitous and persistent threatinourincreasinglydigitizedworld.Asorganizations and individuals rely more on technology and interconnected systems, the potential for malicious actors to exploit vulnerabilities and compromise data and infrastructure has grown substantially. The digitization of critical infrastructure, the widespread adoption of cloud computing, and the proliferation of Internet-connected devices have expanded the attack surface, providing attackers with a plethora of opportunities to infiltrate systemsandperpetratecybercrimes.Tocounterthiseverevolving threatlandscape, effectivecyber-attack detection mechanisms have become paramount. Traditional cybersecurityapproachesprimarilyfocusondetectingand mitigating single, isolated attacks, such as malware infectionsornetworkintrusions.Whilethesemethodshave
proveneffectivetosomeextent,theyoftenstruggletokeep pace with the rapidly evolving tactics and techniques employed by cybercriminals. Attackers are continuously developing new strategies to evade detection, exploit vulnerabilities, and bypass traditional security measures, posing a significant In this research paper, we aim to explore the application of machine learning for cyberattackdetectionandmitigation.WewillinvestigatehowML algorithms can be effectively deployed to detect a wide rangeofcyberthreats,includingmalware,phishingattacks, insider threats, and advanced persistent threats (APTs). Additionally, we will examine the challenges and limitations of ML-based detection systems and propose strategies to overcome them. Our research seeks to contribute to the advancement of cybersecurity by developing more robust and adaptive mechanisms for detecting and responding to cyber-attacks. By leveraging the power of machine learning and data-driven analytics, we aim to enhance the resilience of organizations and individualsagainstthethreatofcybercrime.
2.LITERATURE SURVEY
I) Prediction of Cyber Attacks using Machine Learning Algorithms: In response to the escalating threat of cyberattacks, this paper highlights the pressing need for effective detection and prevention strategies. It underscoresthesignificanteconomicharminflictedby cybercrime on individuals and nations alike. The importance of understanding attack tactics and identifying cybercrime perpetrators to combat this growing menace is emphasized. While artificial intelligence techniques have been increasingly employed to address these challenges, predicting cybercrime strategies remains a formidable task. The paper suggests leveraging actual data to pinpoint specific attacks and their perpetrators as a potential solutiontothisongoingchallenge.
II) Cyber-attack Detection in Network Traffic using Machine Learning: This research addresses the rampant proliferation of cyber threats as a consequence of the rapid expansion of internet usage by individuals, government sectors, and companies. With the transition towards online provision of services and products, vulnerabilities in network securityhavebecomeincreasinglyexploitableby
Prof. P.M. Kamde *1, Rakesh Patil *2, Ganesh Kadam *3, Vedant Pokale *4, Shriram Narkhede

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072
malicious actors. The critical need for effective cyberattackdetectionmechanismstomitigatefinancial lossesandsafeguardvaluableresourcesisemphasized. By employing machinelearning techniques, the paper proposes a proactive approach to identify and neutralize potential cyber threats within network traffic.Thisproactivestanceiscrucialinmitigatingthe risksposedbycyberattacksandensuringtheresilience ofnetworkinfrastructures.
III) Predictive Analysis of Cyber-attacks using Machine Learning: This study delves into the development of models aimed at anticipating and preempting cyber threats. By leveraging historical data and advanced machine learning algorithms, organizations can forecastpotentialcyber-attackswithgreateraccuracy, enabling proactive defense measures. The paper highlights the significance of continuous model refinement and data-driven insights in enhancing the predictivepowerofcyberdefensesystems,ultimately contributingtoamorerobustcybersecurityposture.
3.Methodology:
Intherealmofcybersecurity,severaltypesofattackspose threatstodigitalsystemsandnetworks.Onecommonattack is a Denial of Service (DoS) assault, which overwhelms a system with excessive traffic, rendering it unable to serve legitimate users. Benign activities, on the other hand, are harmless actions that do not intend to cause harm, contrasting with the malicious intent behind various cyberattacks. Port scanning involves probing a system to identifyopenports,similartocheckingifdoorsorwindows areunlocked.Meanwhile,bots,orautomatedprograms,can be both beneficial, such as automated customer service responses,ormalicious,asinbotnetsusedforcoordinated attacks. Web attacks target vulnerabilities in websites or web applications, utilizing methods like phishing or injection attacks. Lastly, brute force attacks involve systematicallyguessingpasswordsorencryptionkeysuntil the correct one is found, resembling trying every key in a bunch to unlock a door. Each of these tactics underscores the importance of robust cybersecurity measures to safeguardagainstpotentialthreats.
3.1. Existing System:
Theexistingcybersecuritylandscapereliespredominantly on single-layer defense mechanisms, such as antivirus software, firewalls, and intrusion detection systems (IDS). Whilethesesolutionsoffersomelevelofprotectionagainst knownthreats,theyoftenfallshortineffectivelymitigating advanced and emerging cyber threats. Additionally, the reliance on standalone security tools creates silos of
information,makingitchallengingtocorrelateandanalyse dataforcomprehensivethreatdetectionandresponse.
Disadvantages of Existing System:
1. LimitedProtection: Single-layer defences are insufficienttoaddressthecomplexityandsophisticationof moderncyberthreats,leavingorganizationsvulnerable to advancedattacks.
2. Lack of Integration: Standalone security tools operate in isolation, leading to fragmented security postures and hinderingeffectivethreatdetectionandresponse.
3. Inability to Detect Unknown Threats: Conventional security solutions primarily focus on known threats, making them ineffective against zero-day exploits and otheremergingvulnerabilities.
4. High False Positive Rates: Legacy security systems often generate a high volume of false positives, overwhelmingsecurityteamsandleadingtoalertfatigue.
5. Reactive Approach: The reactive nature of existing systems means that organizations often only respond to cyber incidents after they occur, resulting in delayed detectionandmitigationefforts.
3.2. Proposed System:
The proposedsystemadvocatesfor the implementation of a multi-layered cybersecurity approach, termed "multiple cyber-attack detection." This approach integrates various tools, techniques, and strategies to enhance threat detectionandresponsecapabilities.Keycomponentsofthe proposedsysteminclude:
Advanced Threat Detection: Leveraging machine learning,anomalydetection,andbehaviouralanalyticsto identifyunknownandsophisticatedthreatsinreal-time.
Centralized Security Orchestration: Implementing a centralizedsecurityorchestrationplatformtostreamline the integration and management of security tools, enablingseamlesscollaborationandautomatedincident response.
Threat Intelligence Integration: Incorporating threat intelligence feeds from reputable sources to enrich securityanalyticsandenhancethreatvisibilityacrossthe organization.
Continuous Monitoring and Analysis: Implementing continuous monitoring and analysis of network traffic, endpoint activities, and user behaviour to detect and respondtothreatsproactively.
Adaptive Défense Strategies: Employing adaptive defence strategies that dynamically adjust security controls based on evolving threat intelligence and organizationalriskprofiles.
By adopting the proposed multilayered cybersecurity approach, organizations can strengthen their defence posture,mitigatecyberriskseffectively,andrespond

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072
rapidlytoemergingthreats,therebysafeguardingtheir digitalassetsandsensitiveinformation.
3.3. Algorithm:
Support Vector Machine (SVM): Powerful algorithm for classification and regression tasks. It finds the best line or hyperplane to separate data classes in high-dimensional space, maximizing margin for clear classification. Handles complex data by transforming into higher dimensions. Widely used in image recognition, text classification, and bioinformatics.
Random Forest: Ensemble learning method building multipledecisiontrees,combiningoutputsfor predictions. Each tree uses random data subsets to reduce overfitting. Robust, scalable, and effective for high-dimensional data. Commonly used in classification, regression, and anomaly detectioninfinance,healthcare,andmarketing.
Decision Tree: Simple yet powerful algorithm for classification and regression. Recursively splits data based onfeaturevalues,optimizingcriterialikeinformationgain. Createsatreestructurewithnodesrepresentingdecisions and leaves representing outcomes. Easy to interpret but prone to overfitting. Used in finance, healthcare, and engineering for tasks like customer segmentation and risk assessment.
3.3. Functional Requirements:
• Admin:Adminmodulewillbeonwebmodule.Admin willverifyuserinformationandalloworrejecttouser. LoadtheDataset.
• User: User registers into system with personal information. Automatically user verification request send to admin. After verification user can login into system.
• System:ByusingSVM/NB/NNalgorithm,Enhancethe MultipleCyberAttackDetection.

I.
MainFlow:
Input as Text: Theprocessbeginswithrawtext input that likely contains data about potential cyberthreats.
II. Preprocessing: This step involves cleaning and preparingthedata,possiblyremovingirrelevant information or formatting the text for further analysis.
III. Feature Extraction: Key features are extracted from the pre-processed text. These features are essential characteristics that will help in identifyingpotentialcyber-attacks.
IV. Multiple Cyber Attack Detection: Theextracted featuresarethenusedtodetectvarioustypesof cyber-attacks. This step might involve analysing patternsoranomaliesindicativeofcyberthreats.
V. Classification Models: Finally, the detected cyberattacksareclassifiedusingdifferentmodels suchasSupportVectorMachine(SVM),Random Forest(RF),DecisionTree(DT),andNaiveBayes (NB).Eachmodelmayofferadifferentapproach to classifying the attacks based on the extracted features.
Thisprocessiscrucialincybersecurity,helpingto identifyandcategorizecyberthreatsefficiently.
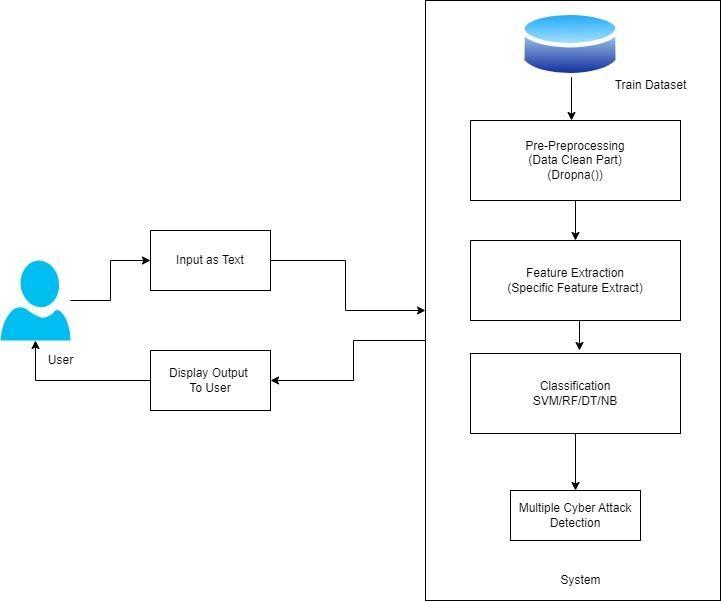
Figure2:System Architecture
Figure 1:DataFlow diagram

Figure 3: Represents the activity diagram for our proposedsystem
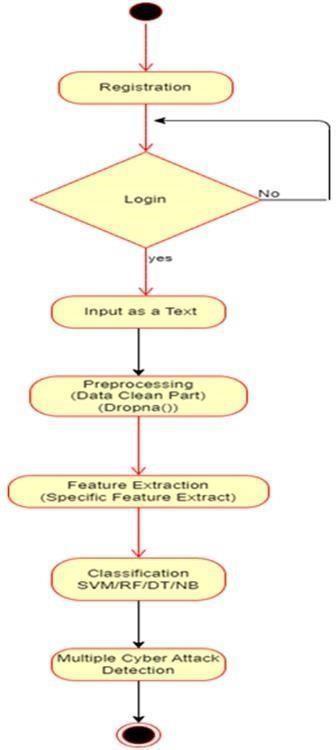
. Figure3:Activity diagram
4. REQUIREMENTS
HARDWARE REQUIREMENTS
RAM: 8GB As we are using Machine Learning Algorithm and Various High Level Libraries Laptop RAM minimum requiredis8GB.
Hard Disk:40GB
Processor: Intel i5 Processor, PyCharm IDE that Integrated Development Environment is to be used and data loading should be fast hence Fast Processor is required. IDE: Spyder Best Integrated Development Environmentasitgivespossiblesuggestionsatthetimeof typingcodesnippetsthatmakes International Research Journal of Engineering and
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072
5.
RESULT AND DISCUSSION:
Operating System: Windows 10 Latest Operating System that supports all type of installation and development Environment.
© 2024, IRJET | Impact Factor value: 8.226 |
Table 1: Model 2 performance in machine learning model
In the cyber-attack detection project utilizing machine learningalgorithmssuchasSupportVectorMachine(SVM), Random Forest (RF), and Decision Tree (DT), the performance metrics reveal insightful observations. Notably, SVM exhibits moderate accuracy at 76.41%, with relativelybalancedprecisionandrecallratesat76.33%and 71.33%, respectively, resulting in an F1-score of 69.83%. Although SVM demonstrates decent performance, its accuracy falls short compared to Random Forest and Decision Tree models. Both RF and DT exhibit remarkably high accuracy rates of 92.82%, demonstrating their effectiveness in correctly classifying instances. Furthermore,RFandDTshowimpressiveprecision,recall, and F1-score percentages, all exceeding 91%, indicating their robustness in accurately identifying cyber-attacks. ThesefindingssuggestthatensemblemethodslikeRandom Forest and traditional Decision Trees outperform SVM in this particular cyber-attack detection task. The high accuracy, precision, recall, and F1-score values associated withRFandDThighlighttheirpotentialutilityinreal-world cybersecurity applications, emphasizing the importance of considering various machine learning algorithms when developingeffectivecyberdefensesystem.

Figure4:ConfusionMatrixforSVM


6. FUTURE SCOPE
In the future, using machine learning for cybersecurity means having super-smart systems that act like powerful digital guardians, learning from past cyber-attacks to stop newonesintheirtracks.Thesesystemscangetreallygood at spotting all sorts of hacker tricks, like denial of service (DoS) attacks, weird but harmless activity (benign anomalies), checking for weak spots in networks (port scanning), sneaky invasions by bots, attacks on websites (web attacks), and attempts to guess passwords (brute force).
With machine learning, it's like having a super detective thatcansiftthroughtonsofdatatofindsignsoftrouble.It can pick up on tiny patterns in internet traffic or strange behavior in user accounts that might mean trouble. By catching cyber threats early and dealing with them automatically,wecankeepourdigitalstuffsafer.Thisway, humanscanfocusonoutsmartingcybercriminals,knowing our digital world is well-guarded by smart, fast, and effectivemachinelearningsystems
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072 7. CONCLUSION
In today's digital world, protecting our information requires more than just one line of defense. That's where theidea of "multiplecyber-attack detection" comesin.It's likehavingabunchofdifferenttoolsandstrategiesworking together to keep our information safe from various cyber threats. By using machine learning, which is like teaching computerstolearnfrompastexperiences,wecanmakeour defensesevenstronger.Thishelpsusspotthingslikedenial of service (DoS) attacks, unusual activities (benign anomalies), checking ports for vulnerabilities (port scanning), sneaky robot invasions (bot invasions), attacks on websites (web attacks), and trying to guess passwords (bruteforce).Thesystemalsoremindsustobeclearabout whatwe'retryingtoprotectandtobereadytochangeour
approach as new threats come up. By combining smart detection methods, keeping an eye on things all the time, andbeingreadytoreactfasttonewdangers,wecanmake sure our digital stuff stays safe. Overall, it's about being smart and flexible in how we protect ourselves from the always-changingworldofcyberthreats.
8.REFERENCES:
[1] Wired,“Insidethecunning,unprecedentedhackof ukraine’spowergrid,”2016,lastaccessedMarch2018. [Online]. Available: https://www.wired. com/2016/03/inside- cunning-unprecedentedhackukraines-power-grid/
[2] D. Kushner, “The real story of stuxnet,” ieee Spectrum, vol.3,no.50,pp.48–53,2013.
[3] ForeignPolicy, “Cyberattack targets safety system at saudi aramco,” 2017, last accessed March 2018. [Online]. Available: http://foreignpolicy. com/2017/12/21/cyber-attack-targets-safetysystem-at-saudi-aramco/
[4] F. Pasqualetti, F. Dorfler, and F. Bullo, “Cyber-physical attacksinpower¨networks:Models,fundamental limitations and monitor design,” in Decision and Control and European Control Conference (CDC-ECC), 201150thIEEEConferenceon.IEEE,2011,pp.2195–2201.
[5] A. Teixeira, D. Perez, H. Sandberg, and K. H. Johansson, “Attack models ´ and scenarios for networked control systems,” in Proceedings of the 1st in- ternational conference on High Confidence Networked Systems. ACM,2012,pp.55–64.
[6] A. Jones, Z. Kong, and C. Belta, “Anomaly detection in cyber-physicalsys-tems:A formalmethods approach,” inDecision andControl (CDC),2014IEEE53rdAnnual Conferenceon.IEEE,2014,pp.848–853.
Figure2:Confusion Matrix forRF
