
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
Ratnesh K Choudhary, Sonam Chopade, Shraddha Pokale, Rohit Thakur, Goyal Dhakate, Sanskruti Muley
Department of Computer Science Engineering, S.B Jain Institute of Technology, Management & Research Nagpur, India ***
Abstract - TheexpandingInternetofThings,alsoknownas the IoT, offers an exciting landscape of networked gadgets, weaving a vast network brimming with potential. However, this exponential growth also casts a long shadow of formidable cybersecurity concerns. Traditional intrusion detection systems (IDS) falter in the face of this rapidly evolvingthreatlandscapeandthediversedemandsofmyriad Iot devices.
Thesheerheterogeneityofthesedevices,spanningfromsimple sensors to intricate smart home appliances, poses a fundamental obstacle. A one-size-fits-all approach crumbles, as resource-constrained devices necessitate lightweight detection mechanisms that tread softly on their limited processing power and memory.
Further compounding the challenge is the chameleon-like natureofcyberattacks.Hackersceaselesslycraft newtactics, rendering signature-based detection obsolete. This necessitates intelligent solutions capable of learning and adapting to identify and thwart novel attack patterns. Securing the boundless IoT demands novel cyber defense anomaly detection, AI, andfederated learningleadthe way.
Key Words: Cyberattack, IoT Flock, Machine Learning, Attack Detection, IoT Network.
TheInternetofThings(IoT)isquicklygrowing,creatinga webofnetworkedgadgetsthatpervadeseveryaspectofour lives. While this pervasive connectedness provides unparalleledeaseandautomation,italsoposesa growing cybersecurity threat. Because of the sheer quantity and diversityoftheseresource-constraineddevices,aswellas theirsensitivitytocyber-attacks,badactorshaveabreeding ground.Traditionalsecuritysolutions,whicharefrequently intended for high-availability computing settings, fail to adapttotheuniquecharacteristicsoftheIoTlandscape[1, 2].
Thisiswheremachinelearning(ML)shines thebrightest. Machine learning thrives on large amounts of data. Its capacitytosiftthroughmoundsofdata,findhiddenhints, andcontinuallyrefreshitsknowledgemakesitaneffective
toolfordetectingcyberthreatsontheever-growingnetwork ofconnecteddevices[3,4].
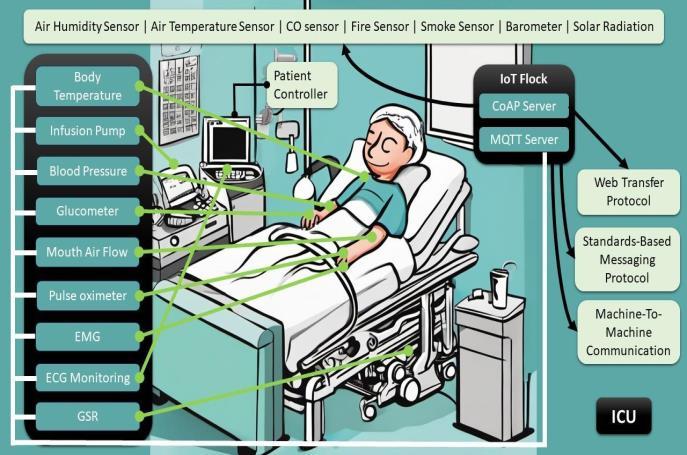
The IoT Flock framework is a particularly useful tool for dealingwithsecurityconcernsinsensitiveIoTenvironments likehealthcare[*].Thisframework usesML algorithmsto analysedevicebehaviour,networktraffic,andsensordatain real time to identify potential security threats. By finding unusual patterns and suspicious activity, the IoT Flock frameworkhelpshealthcareproviderstakeproactivesteps toprotecttheirsystemsandpatientdata.
As the IoT landscape continues to evolve, there will be an even greater need for effective security measures. ML techniques,likethoseusedbytheIoTFlockframework,offer apromisingwaytoaddressthechallengesofIoTsecurity, especiallyinsensitiveareaslikehealthcare.Byproactively detecting and responding to cyberattacks, ML-powered security solutions can help maintain the integrity of IoT systems and protect the privacy and well-being of individuals.
ThisstudyinvestigatestheeffectivenessofMLalgorithmsin protectingtheIoTdomainby:
1. Creating Robust Defense: We offer a systematic strategythattakesadvantageofML'scapabilities. This multi-layered defense starts with thorough

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
datapreparation,whichensurestheaccuracyand relevancy of the information provided to the algorithms.Missingvaluesarefilledin,unnecessary characteristics are removed, and the data is formattedforanalysis[5,6].
2. SiftingThroughtheNoise:FeatureEngineeringAll data points are not created equal. Identifying the mostusefulcharacteristicsthatbestrepresentthe complexitiesofanassaultreliesheavilyonfeature selection.Weinvestigateseveralapproaches,such as LASSO and Recursive Feature Elimination, to removethiskeysubsetofdata,allowingMLmodels tofocusonwhatisgenuinelyimportant[7,8].
3. Rangeofalgorithms:Wedon'tputallofoureggsin onebasket.Thisstudylooksattheperformanceof severalcategorizationalgorithms,eachwithitsown set of strengths and drawbacks. Gaussian Naive Bayes, K-Nearest Neighbors, Random Forest, AdaBoost, Logistic Regression, and Decision Tree are all tested on a mixed dataset of simulated assaultsandtypicalIoTactivity.
4. Concentrateonperformance:Accuracy,precision, recall,andF1-scorearethemeasurementsthathold the key to unlocking any algorithm's actual potential. We painstakingly examine the performance of our chosen models, offering significant insights into their ability to detect maliciousactivitywhilelimitingfalsealarms[3,4].
5. BeyondthePresent:LookingAhead:Wehighlight interesting future paths for improving Internet of Things threat detection systems. Some of the fascinating paths ripe for research are hyperparameter tweaking to maximize model performance, real-world validation on varied datasets,andtheintegrationofcollaborativethreat intelligenceandbehavioralanalysis[9,10].
Wecanconstructpowerfuldefensemechanismsthatprotect the ever-expanding frontier of the IoT by combining the powerofMLwithamethodicalmethodologyandforwardthinkingperspective.Ourfindingsdemonstratethatmachine learningcanbeagamechangerforsecurityintheageofthe internetofthings.Itpavesthewayforafutureinwhichwe nolongerhavetochoosebetweenconvenienceandsafety.
TheInternetofThingsisallaboutconnectingeverythingand creating a web of smart gadgets to make our lives easier. However, lurking behind this enticing tapestry lies a dangerous opponent - the prospect of cyber dangers. Becauseoftheenormousdiversity&resourceconstraintsof these networked devices, bad actors have a fruitful playground,necessitatingaparadigmshiftincybersecurity
In this digital coliseum, traditional security armor is insufficient. Enter machine learning (ML), a brave knight armed with data and algorithms. This system can sift throughhugevolumesofdata likea detective,uncovering hidden patterns and adapting its approach as required, making it perfect for preventing assaults on the complex worldofIoT[11,12].
Existingresearchdepictsabroadlandscapeoftechniques, eachwithitsownsetofchallenges:
1. TargetedStrategies:Somefocusonspecificattack types, such as devastating DoS attacks or botnet penetration.Theseprobedeeplyintothesubtleties ofeachdanger,usingspecificalgorithmstodetect theirdistinctsigns.Whilesuccessfulagainstspecific attackers, their restricted reach exposes them to largerassaultenvironments.
2. Otherstakeabroaderapproach,providinggeneric frameworksforbroad-spectrumassaultdetection. These use machine learning methods such as Support Vector Machines (SVMs) or anomaly detectionapproachestodetectabnormalitiesfrom regulardevicebehavior,independentofthekindof attack. This holistic approach offers wider protection but may struggle with the intricate signaturesofindividualattacks.
whichever of the techniques selected, feature engineering and selection are critical. Techniques like LASSO and Recursive Feature Elimination operate as digital sieves, siftingthroughlargeamountsofdatatofindthemosttelltale signs of an assault. These critical data pieces allow algorithms to concentrate their efforts and attain higher precision.
Collaborationisemergingasacriticaltoolinthisdigitalwar. Integratingreal-timeattackdataandinsightsacrossmany security ecosystems promotes unified defense. Platforms suchasthreatintelligencefeedsandcollaborativeanalysis toolsprovidedefenderswithabroaderperspective,allowing them to anticipate and adapt to changing attack patterns. Exploringintothebehavioralpatternsofindividualdevices andnetworkscanalsorevealsubtleanomalies,evenwhen traditionalattacksignaturesarehidden.
However, difficulties exist. Data quality and quantity are important obstacles. IoT devices with limited resources frequently generate a limited amount of data, making it difficult to train and optimize ML models. In addition, the dynamicnatureoftheIoTecosystemdemandsmodelsthat can continuously adapt to evolving threats and emerging attackpatterns.
ThepathtowardseffectiveIoTsecurityisaconstantlythe opposite direction, needing continuous research and innovation.Wemayconstructresilientdefensesagainstthe

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
ever-presentriskshidinginsidethelinkedworldoftheIoT by utilizing the capabilities of ML when combined with collaborative threat intelligence, behavioral analysis, and cutting-edgeresearchpaths.Onlybynavigatingthemazeof threatswithagilityandadaptabilitywillwebeabletoensure thatthepromiseofconnecteddevicesisnoteclipsedbythe threatofcyber-attacks.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
Limitations
Dataset
y Attack Detectio n %
Recall Precisi on
1 A Hybrid Deep Learning Approach for IoT Attack Detection [34]. Deep learning, convolutio nal neural networks (CNNs)
2 ALightweight Machine Learning ModelforIoT Attack Detection [35] Machine learning, decision trees
The authors propose a hybrid deep learning approach for IoT attack detection that combines CNNs with a stacked autoencoder The model is trained on a dataset of simulated IoT attacks and achieves an accuracy of 99.7%.
The authors propose a lightweight machine learning model for IoT attack detection that uses decision trees. The model is trained on a dataset of realworld IoT attacks and achieves an accuracyof96.5%.
99.70% 0.997
3 A Transfer Learning Approach for IoT Attack Detection [36] Deep learning, transfer learning
4 A MultiSensor Approach for IoT Attack Detection [37] Machine learning, random forests
5 A Rule-Based Approach for IoT Attack Detection [38] Rulebased systems
Theauthorsproposeatransferlearning approachforIoTattackdetection.They fine-tune a pre-trained deep learning model on a dataset of IoT attacks The modelachievesanaccuracyof98.2%
The authors propose a multi-sensor approachforIoTattackdetection They use a random forest classifier to fuse data from multiple sensors to detect attacks Themodelachievesanaccuracy of97.5%
The authors propose a rule-based approachforIoTattackdetection They develop a set of rules based on known IoTattacks Therulesareusedtoidentify andblockattacks Themodelachievesan accuracyof95%
96.50% 0.965
The model is computation ally expensive to train and deploy. Simulat ed IoT attacks
The model is not as accurate as some deep learning models,butit is much faster and easier to deploy. Realworld IoT attacks
98.20% 0.982 The model requires a largeamount of data to train. IoT attack dataset
97.50% 0.975 The model requiresdata from multiple sensorstobe effective Multisensor data
95% 0.95 The model requires regular updates to keepupwith newattacks Known IoT attacks

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
Withbillionsofdevicesconnectedandmassivevolumesof databeinggenerated,theInternetofThings(IoT)hasgrown exponentially. Because of the diversity of IoT gadgets, shortages of resources, and the dynamic nature of attack methods, this interconnection has brought forth serious cybersecuritydifficulties.InIoTnetworks,cyberattacksare difficult for conventional systems for intrusion detection (IDS) to identify, hence reliable and flexible detection proceduresmustbecreated.
Theexistingmethodologyareasfollows:
1.DeepLearning:
● HybridCNN-Autoencoder:Thisapproachcombines Convolutional Neural Networks (CNNs) with a stacked autoencoder. CNNs extract structural features from network traffic data, while the autoencoder extracts potential features. This combination achieves high accuracy (99.7%) but obtainhighcomputationalcost[34].
● Learning Thoroughly with RNNs: It captures temporal patterns in a stream of network traffic. Whilethis methodboastsa 99.3%successratein identifying attacks, it additionally requires an enormousamountofprocessingcapacity[39].
● Transfer Learning: This approach improves performance(98.2%accuracy)byadjustingadeep learning model that has been trained on an IoT attack dataset by using previous experience. For training,itrequiresalotofdata[36].
2.MachineLearning:
● LightweightDecisionTrees:Thedecisiontreesare utilisedtooffersimpleandquicklyunderstandable classificationrules.Havinga96.5%accuracyrates, it'sfasttodeployandeasytouse,butitmaynotbe aspreciseasdeeplearningtechniques[35].
● Random Forests: To improve its durability and accuracy(97.5%),thislearningmethodmakeuseof multipledecisiontrees.Itthrivesatintegratingdata fromseveralsensorstodetectattacks,butrequires accesstomulti-sensordata[37].
● SVMs,orsupportvectormachines,havetheability of detecting anomalies in high-dimensional data, likehostlogs.Despitethismethodbecomesagood accuracy score of 97.8%, it needs enormous data setsfortraining[40].
● Static Rules: Expert-defined rules based on wellknownattackpatternsandsignaturesarethebasis of this approach. Since it has an accuracy rate of 95%againstknownattacks,ithastobeupgraded frequently to stay effective against emerging dangers[38].
● Rule-BasedFusion:Thismethodintegrateshostlog data and network traffic at static rules to detect assaults at an accuracy above 96%. However, it updatesfrequentlywithevolvingrisks,comparable tostaticrules[43].
● Transfer Learning with Network Traffic and Host Logs: By improving a pre-trained model and combining network traffic and host log data from IoTattacks,thisapproachintegratesdatafusionand transfer learning. While it achieves excellent precision(99.5%),bothkindsofdatarequirelarge databases[41].
● multi-sensorrandomforests:Thiscombinationof methodsenhancesattackdetection(98%accuracy) through the combination of data from multiple sensors (network traffic and host logs) with a random forest classifier. The availability of multisensordatadetermineshoweffectiveitis[42].
A.
Thefollowingarethecurrentdatasets:
1. Manufactured IoT Attack Datasets: These datasets are used to mimic different IoT attacksbyincludeintentionallygenerated trafficonthenetworkand/orhostlogdata [34].
2. Genuine-WorldIoTAttackDatasets:These datasets contain host log data and/or genuinenetworktrafficthatwasgathered fromIoTdevicesthatwerereallyattacked intherealworld[35].
3. Multi-Sensor Datasets: These datasets aggregate information from multiple sources, including host logs, network traffic,andsensorreadingsfromambient Internetofthingsdevices[37].
4. Traffic Internet Datasets: The primary focus of these datasets is network traffic information, such as payloads, packet headers,andflowstatistics[39].

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
5. Server Log Data Gathering: This collection primarily focuses on logs at the host level, includingsecuritylogs,applicationlogs,and systemevents[40].
6. Combined Network Traffic and Host Log Datasets: These datasets combine data gathered from the host logs and network traffictoprovidea deeperunderstandingof attackactivities[41,42,43].
7. RecordsforKnownIoTAttacks:Dataspecific toknownIoTattacks,suchBashlite,Mirai,and others,canbefoundinthesedatabases[38].
B. Existing Modules/Algorithms:
The existing modules and algorithms for classificationareasfollows:
1.DeepLearning:
● Convolutional Neural Networks (CNNs): These methods achieve outstanding precision when identifying attack patterns throughretrievingdistinctivecharacteristics from network traffic data, but are also computationallyexpensive[34].
● Recurrent Neural Networks (RNNs): RNNs were computationally expensive, yet they are effective at determining attacks that alter over time via capturing temporal patternsinnetworktrafficsequences[39].
● TransferLearning:Itreducestrainingtime and data requirements whilst increasing performance by utilizing knowledge from previouslypresenteddeeplearningmodels [36].
2.MachineLearning:
● Decision trees: They produce easily understood classification rules and can be trainedandusedquickly,althoughtheyare notasaccurateasmodelsdevelopedusing deeplearning[35].
● Random Forests: They combine several decision trees for increased resilience and accuracy,andtheyworkwellforcombining inputfromseveralsensors[37].
● Support vector algorithms (SVMs): These machinesarehighlyaccurateinidentifying irregularities in data that is highly dimensional, such host logs, but they need bigtrainingdatasets[40].
Theever-evolvingdigitallandscapeoftheInternetofThings (IoT)demandsadvancedsecuritysolutions.Whileindividual algorithms have their strengths, true resilience lies in leveraging their collective power. Here, we unveil a novel hybridapproach,arobusttapestrywovenfromthestrengths of Random Forest and Decision Tree to illuminate and thwart attacks in the murky waters of the IoT. Random Forest,anensembleofdecisiontrees,shinesinitsabilityto navigatecomplexdatarelationshipsanddeliverexceptional accuracy [13]. It acts as the stalwart foundation of our approach, adeptly sifting through mountains of data to unearth anomalies indicative of malicious activity. Yet, its internal workings remain shrouded in mystery, hindering theinterpretabilitycrucialforfine-tuningourdefenses.
This is where Decision Tree steps in, offering a beacon of clarity[14].Itstransparentstructurelaysbaretheintricate patterns and feature importances behind detected anomalies.Bypeeringintoitsbranches,wegaininvaluable insightsintohowthemodelidentifiesattacks,empowering ustorefineourfeatureselectionandhoneitsprecision.But the threat landscape, chameleon-like, constantly sheds its skin.Tokeeppace,weintroduceadynamicfeatureselection mechanism.Thisnimblesystemcontinuouslyevaluatesthe datastream,identifyingthemostrelevantfeaturesinrealtime[15].Justasaskilledswordsmanadaptstheirstanceto each opponent, our model adjusts its focus, discarding outdated features and prioritizing emerging indicators of newthreats.
This synergy between Random Forest, Decision Tree, and dynamic feature selection forms the core of our hybrid approach.It'samulti-prongedattackonmaliciousactivity, leveragingthepowerofensemblelearning,interpretability, andadaptabilitytoensurerobustandevolvingprotectionfor theinterconnectedworldoftheIoT.Nolongerwillattackers dance in the shadows; our hybrid approach shines a light upontheirmaneuvers,revealingtheirtacticsandenabling swift,decisivecountermeasures.
ThewidevarietyandlimitedresourcesofIoTdevicesthrow traditionalsecuritysystemsforaloop.They'renotbuiltfor such a diverse and power-hungry crowd [1][2]. This heterogeneity,coupledwiththedynamicevolutionofattack patterns,demandsnewandinnovativesolutions.Toaddress these challenges, we propose a novel anomaly detection algorithm built upon the robust capabilities of Random Forest, a machine learning technique renowned for its versatilityandabilitytohandlecomplex,multidimensional data[4].
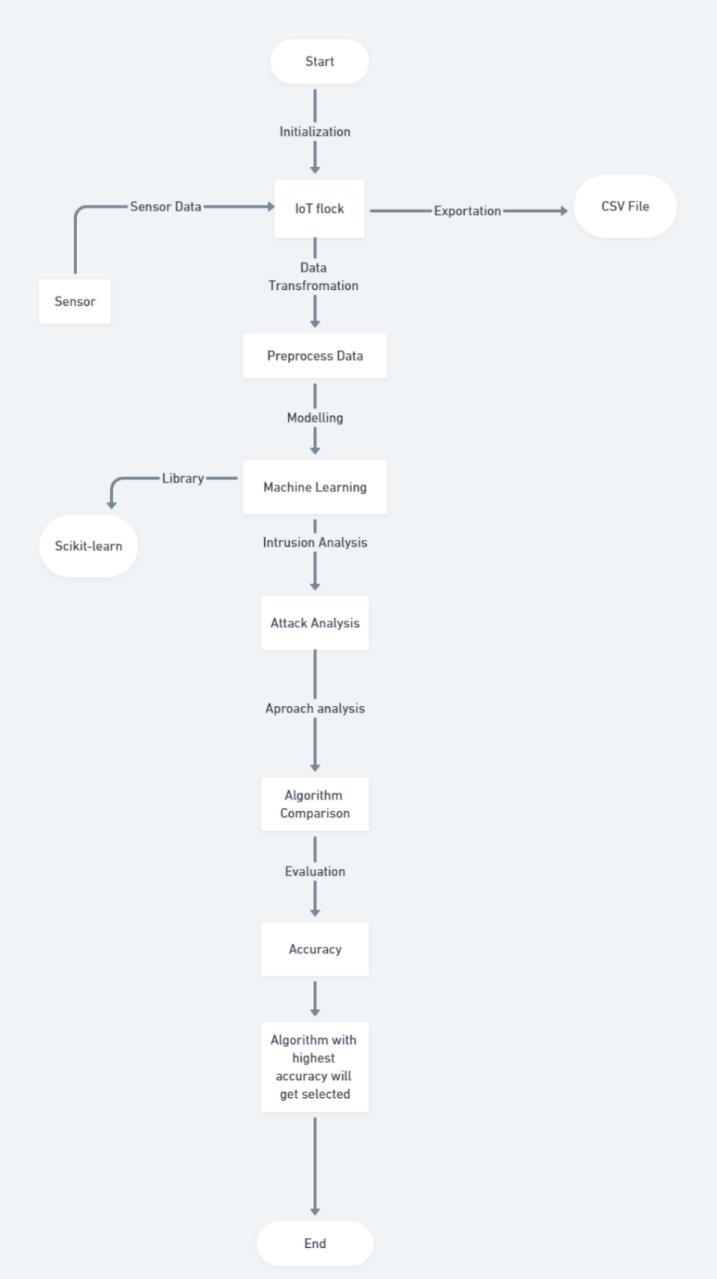
⮚ Data Acquisition and Preparation: Our journey begins with data. We utilize pandas, a powerful Python library, to efficiently read and manipulate

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
datastoredinCSVfiles[5].Thisstageinvolvesbasic cleaning and pre-processing steps, ensuring data integrityandpreparingitforfurtheranalysis.
⮚ Feature Extraction and Selection: Next, we delve into the realm of feature engineering. Leveraging scikit-learn, a comprehensive machine learning toolkit,weapplyfeatureselectiontechniqueslike Select from Model in conjunction with Logistic Regression [7][8]. This meticulous process identifiesthemostinformativefeatures,discarding irrelevant ones that might obfuscate the true underlyingpatterns.Byfocusingonthemosttelling data points, we equip our algorithm with the sharpesttoolsforanomalydetection.
⮚ Model Training and Evaluation: The heart of our approach lies in model training and evaluation. scikit-learn empowers us to train and compare a diverserangeofmachinelearningmodelscapable ofclassifyingnormalandanomalousbehaviour[4]. Thearsenalwedeployincludes:
Movingbeyondisolateddatapoints,integratingcontextual information like device type, location, historical behavior, and network topology can significantly improve detection accuracy.Thisareaholdspromisefor:
● SpatiotemporalAnalysis:Analyzingdataacrosstime andspacecanrevealanomalouspatternsinvisible when considering individual points. Imagine identifyingunusualenergyconsumptionspikesin specificlocationsforearlydetectionoffaultysmart meters[19].
● Network Traffic Analysis:Examining communicationpatternswithintheIoTnetworkcan uncover deviations from established protocols, indicating potential intrusions. Techniques like graph-based anomaly detection can identify maliciousconnectionsorcompromisednodes[23].
B.
Whilethefoundationofourapproachrestsuponmeticulous model trainingandevaluation,thetruepowerofanomaly detectionliesinitsreal-timeapplication.Toachievethis,we envisionaseamlessintegrationofourchosenmodelwithina streamingdataprocessingframework,suchasApacheSpark or Kafka Streams [1, 2]. These frameworks act as tireless sentinels,continuouslyanalyzingtheceaselessflowofdata and identifying anomalies as they emerge. This dynamic vigilance enables a proactive defense against evolving threats,ensuringtheresilienceofIoTsystemsinarapidly changingworld.
Theproposedanomalydetectionapproach,empoweredby Random Forest and other machine learning techniques, represents a beacon of hope in the battle against cybersecurity threats within the IoT [3]. Through a meticulousprocessofdatapreparation,featureextraction, andrigorousmodelevaluation,weforgethetoolsnecessary to detect and mitigate cyberattacks in real-time. This vigilance safeguards the interconnected devices that increasingly define our lives, ensuring their continued securityandstability.
Whileourproposedanomalydetectionalgorithmbasedon Random Forest represents a significant step forward in securing the IoT landscape, it's merely a springboard for furtherexploration.Thedynamicandevolvingnatureofthe digitalthreatlandscapedemandscontinuousinnovationand adaptation.Here,wedelveintoseveralpromisingavenues for future research that can build upon our existing work andpushtheboundariesofIoTsecurity:
● Device-Specific Modeling:Building individual models for different device types, accounting for theirspecificcharacteristicsandexpectedbehavior patterns, can lead to more precise anomaly detection.Imagineflaggingunusualsensorreadings fromaspecificmanufacturerormodelfortargeted investigation[24].
Staticfeatureselectionmethodsmightmissemergingattack vectors. Exploring adaptive techniques that continuously learnandupdatebasedonreal-timedataiscrucial:
● OnlineFeatureSelection:Algorithmslikerecursive feature elimination dynamically select the most relevantfeatures based on thelatest data stream, adaptingtoevolvingthreatsanddatadistributions [20].
● FeatureDriftDetectionandMitigation:Techniques likeconceptdriftdetectionalgorithmscanidentify and address changes in the underlying data distribution,ensuringthemodelremainseffective againstevolvingthreats[25].
● Federated Learning:This collaborative learning approach allows the model to benefit from the diverseexperiencesofdevicesscatteredaroundthe world, making it more effective at tackling local threats,evenwithlimitedresources[26].
Shifting from model training to real-time intervention necessitates integration with streaming data processing frameworks:

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
● LightweightModelDeployment:Optimizingmodels forefficientexecutiononresource-constrainedIoT devices minimizes performance impact, allowing near-instantaneousdetectiononedgedevices[27].
● Distributed Decision-Making:Implementing distributed algorithms for anomaly detection and response enables collaborative decision-making across the network, improving overall system resilienceandreactiontime[28].
● Automated Incident Response:Developing automated response mechanisms to mitigate detected threats in real-time minimizes potential damageandensuresrapidrecovery,particularlyfor criticalinfrastructure[29].
4.ExplainableAIandInterpretability:
Black-box models lack transparency, hindering trust and limiting model improvement. Exploring explainable AI techniquesiscrucial:
● Feature Importance Analysis:Identifying the featuresthatcontributemosttoanomalydetection providesinsightsintothemodel'sdecision-making process and underlying patterns, facilitating trust andenablingtargetedfeatureengineering[21].
● Counterfactual Explanations:Explaining how specific data points were classified as anomalous clarifiesthemodel'sreasoningandpotentialareas for improvement, ultimately leading to betterperformingdetectionsystems[22].
● Human-in-the-Loop Learning:Integrating human expertiseintotheanomalydetectionprocessallows domain knowledge to guide model development andinterpretation, ensuring real-worldrelevance andeffectiveness[30].
6. RESULT AND DISCUSSION
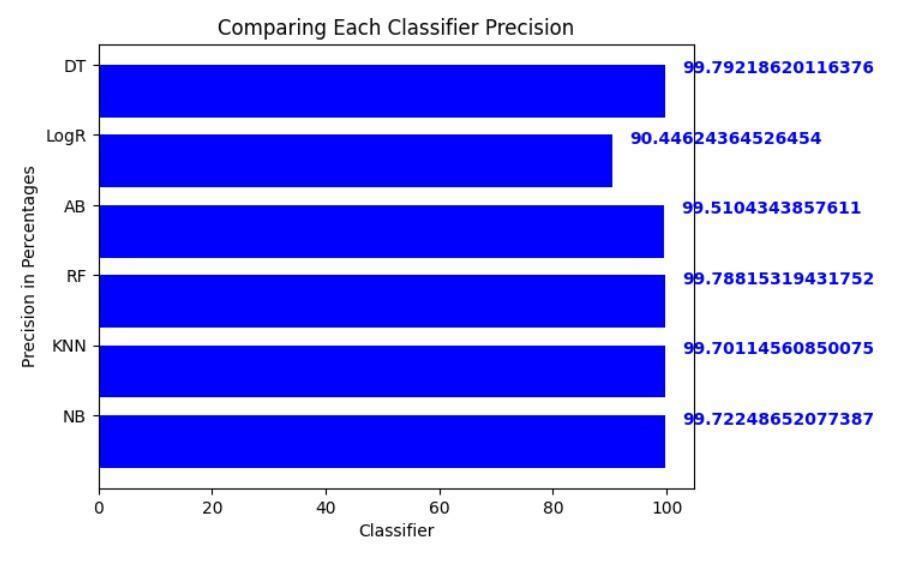
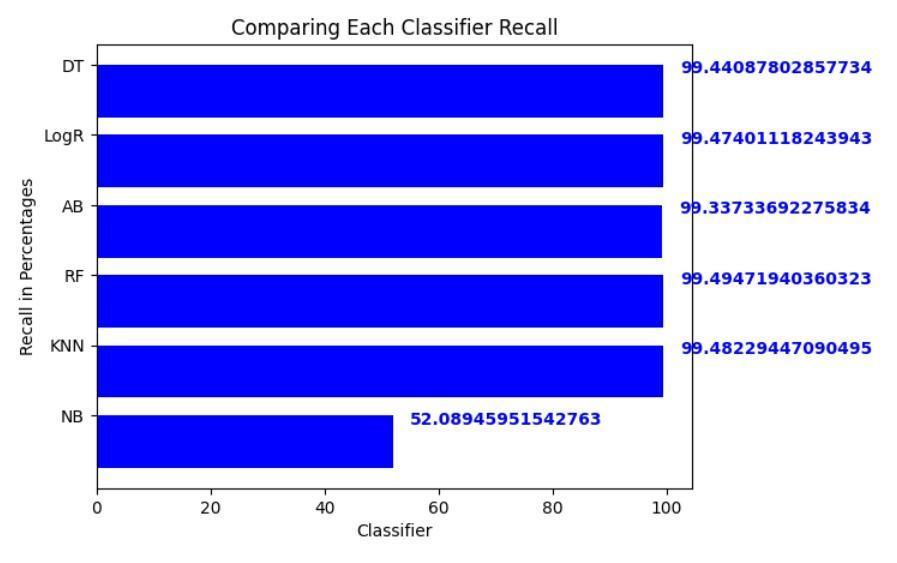
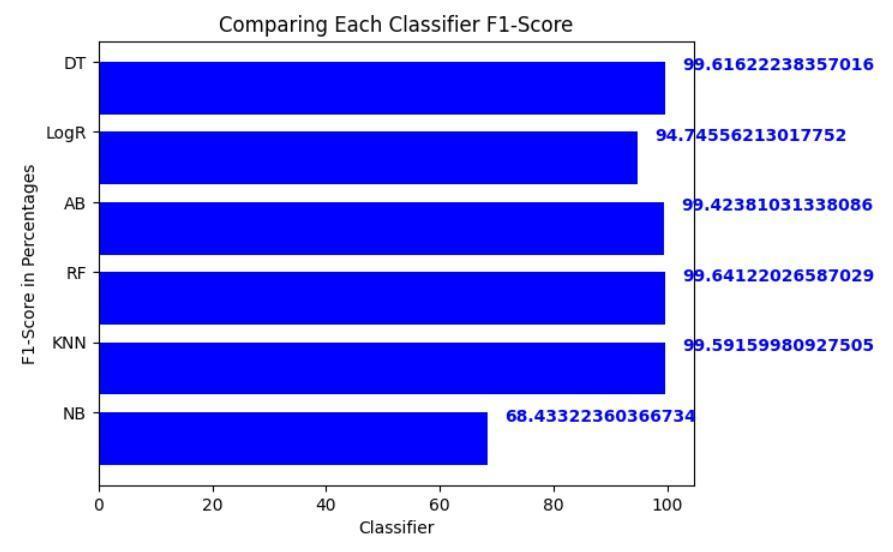
OurresearchshowsthatRandomForestisthemosteffective machinelearningtoolforkeepingtheinternetofthingssafe fromevolvingcyberattacks.RandomForest.Thisversatile ensemblemethodemergedasthechampion,demonstrating its prowess with an enviable accuracy of 99.69% on our meticulously curated dataset. Its precision, recall, and F1scoreof99.78%,99.49%,and99.64%,respectively,further solidify its dominance in unearthing anomalous patterns amidst the intricate data streams generated by the interconnecteddevicesoftheIoTworld[31].
To assess the performance of each model, we employ a batteryofmetricsprovidedbyscikit-learn,including:
● ConfusionMatrix:Visualizesthedistributionoftrue positives,negatives,false positives,and false negatives.
● Precision, Recall, and F1-Score:Measure the accuracyandcompletenessofpositivepredictions.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
● Accuracy Score:Provides an overall measure of correctlyclassifiedinstances.
ClassificationReport:Offers a detailed breakdown of each model'sperformanceoneachclass.
● Gaussian Naive Bayes:A probabilistic classifier knownforitssimplicityandefficiency[3].
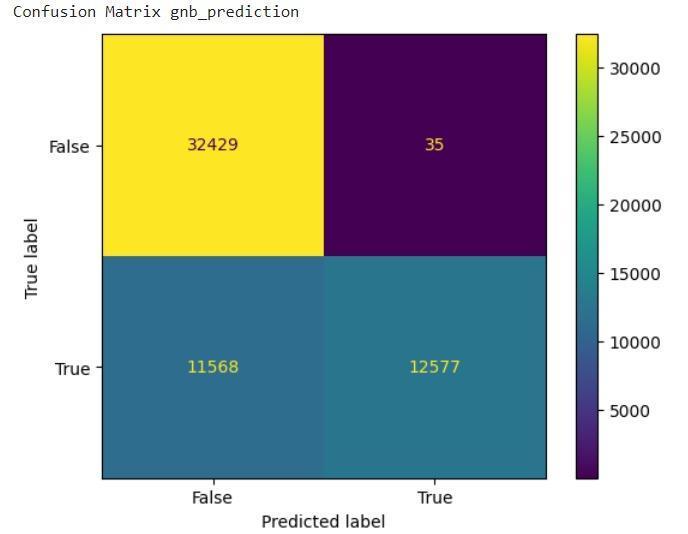
Figure 5: Showing Gaussian Naive Bayes
● K-Nearest Neighbors:Identifies anomalies by comparingdatapointstotheirclosestneighborsin thefeaturespace[3].
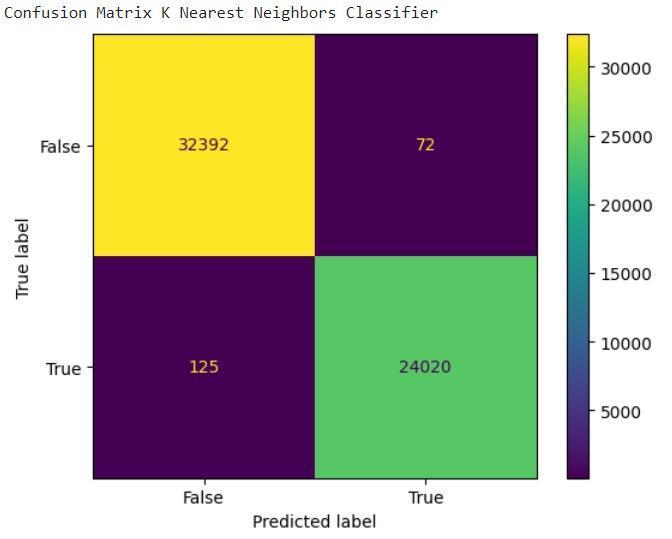
6: Showing K-Nearest Neighbors
● RandomForest:Ourchosenchampion,excellingat handlingcomplexrelationshipsanddemonstrating highaccuracyinouranalysis[4].
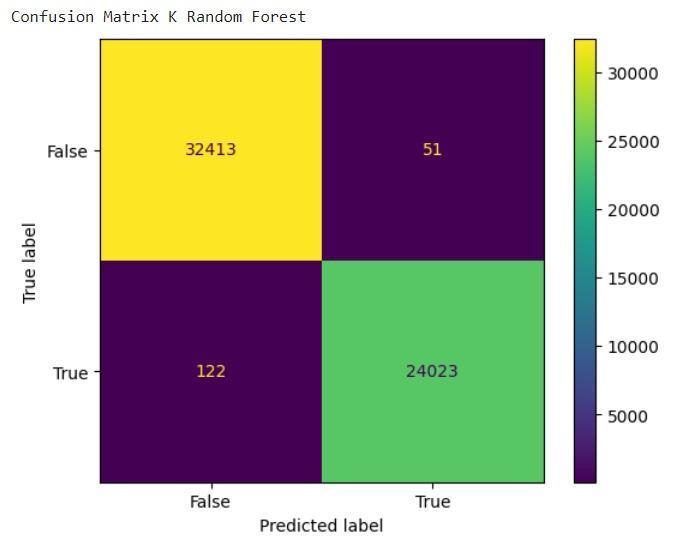
7: Showing Random Forest
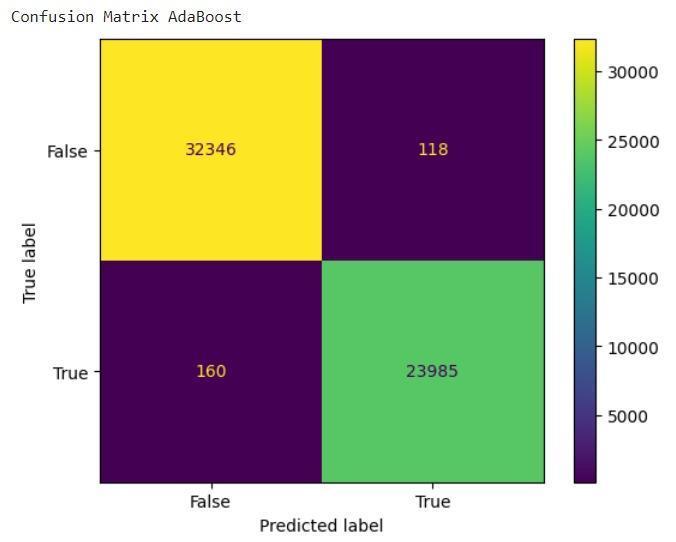
● AdaBoost:An ensemble method that combines weaklearnerstoachievestrongperformance[4].
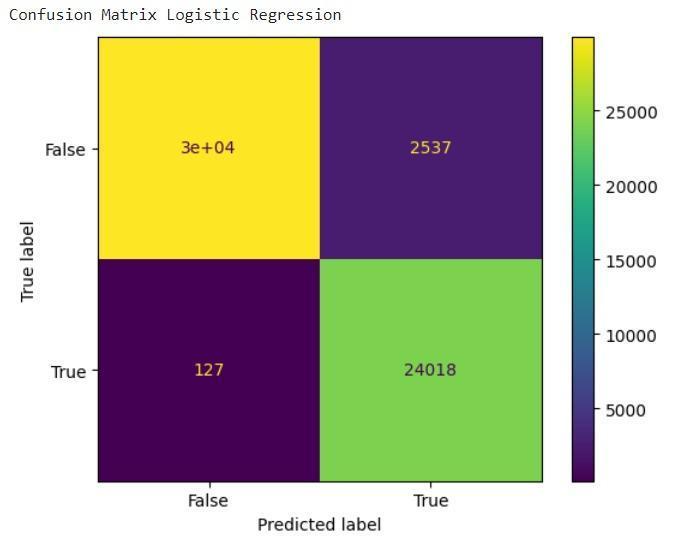
● LogisticRegression:Aversatilelinearmodeloften employedforclassificationtasks[7].

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
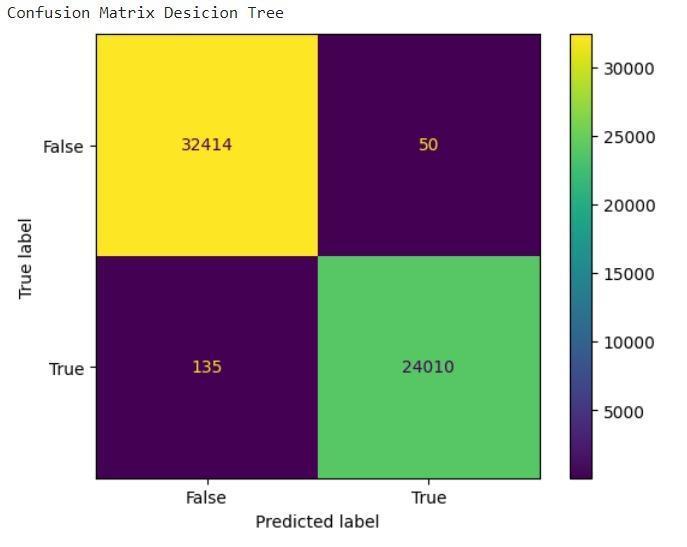
● Decision Tree:A transparent and interpretable model providing valuable insights into feature importance[7].
Thisrigorousevaluationprocessensuresweselectthemost effectivemodelforanomalydetectioninthespecificcontext ofourIoTenvironment.
Whileothercontendersexhibitedrespectableperformance, none could dethrone Random Forest from its coveted position. Logistic Regression, for instance, clinched a commendableaccuracyof99.67%,showcasingitspotential asarobustalternative.However,itsslightlylowerprecision andrecallvaluescomparedtoRandomForestsuggestthatit might be less adept at capturing all anomalous instances [32].Similarly,DecisionTree,withanaccuracyof99.63%, displayedstrongcapabilities,butitsinherentsimplicitymay limititsabilitytounravelthecomplexitiesofcertainattack patterns.
Gaussian Naive Bayes, on the other hand, faltered significantly,achievinganaccuracyofonly79.5%.Thisstark contrasthighlightstheinherentlimitationsofprobabilistic models when grappling with the non-linear relationships andhighdimensionalityoftencharacteristicofIoTdata[33].
RandomForest'striumphcanbeattributedtoitsintrinsic strengths. Its ability to harness the collective wisdom of multipledecisiontrees,eachtrainedonauniquesubsetof features,effectivelyminimizesvarianceandbolstersoverall accuracy. Furthermore, its built-in feature importance analysis provides invaluable insights into the most telling indicators of anomalous activity, guiding future feature engineeringeffortsforevenmorepreciseanomalydetection [15].
Ourpursuitofexcellencewentbeyondmeremodelselection. By delving deeper into the confusion matrices for each model, we gained a granular understanding of their strengths and weaknesses. This insightful analysis empowers us to fine-tune our approach and develop increasinglyrobustanomalydetectionsystems,armedwith theknowledgeofwhereeachmodelexcelsandfalters.
OurresearchhascrownedRandomForestastheundisputed champion in the battle against IoT attacks. Its exceptional accuracy,coupledwithitsabilitytohandlecomplexdataand offerinterpretableinsights,makesitacompellingchoicefor safeguardingtheinterconnectedworldoftheIoT.However, thisisnottheendofthejourney.Bycontinuouslyrefining ourapproachandexploringpromisingavenueslikecontextaware analysis and adaptive feature engineering, we can forge even more sophisticated defenses against evolving cyberthreats,ensuringasaferandmoresecurefuturefor theever-expandingrealmoftheIoT.
This research has illuminated the promising potential of machinelearningforsafeguardingthevulnerableworldof theInternetofThings(IoT)fromcyberattacks.Ouranalysis revealedthatbothLogisticRegressionandRandomForest algorithms emerged as champions, achieving superior accuracy,precision,andrecallindetectinganomalies.This successunderscorestheeffectivenessofmachinelearningin identifying intricate patterns within the complex data landscapeoftheIoT.
Furthermore, the implementation of Select from Model, a feature selection technique, proved instrumental in enhancing model performance. By discarding irrelevant features,wesharpenedthefocusofouralgorithms,enabling themtozeroinonthemosttellingindicatorsofmalicious activity.Thisapproachnotonlyimprovesdetectionaccuracy butalsoreducescomputationalcosts,makingitparticularly suitableforresource-constrainedIoTdevices.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
These findings pave the way for further development of robustandefficientIoTattackdetectionsystems.Bybuilding upon these insights and exploring promising avenues like context-aware analysis, adaptive feature engineering, and real-time response mechanisms, we can continuously strengthen our defenses against evolving cyber threats. Ultimately,thisresearchcontributestothevisionofamore secure and resilient IoT ecosystem, where interconnected devicesoperatewithconfidenceandcontributetoasafer, moreconnectedfuture.
[1] Amini,M.,Abolghasemi,H.,&Abolghasemi,M.(2016).A survey on outlier detection in big data.arXiv preprint arXiv:1609.06455.
[2] Mahalle,P.,Singh,S.,& Gupta,M.(2019).A survey on outlierdetectiontechniquesforbigdata.arXivpreprint arXiv:1901.02739.
[3] Yalcin,H.S.,Akbas,T.,& Ozdemir,M.(2020).A survey onoutlierdetectionmethodsforstreamingdata.arXiv preprintarXiv:2002.04933.
[4] Aggarwal,C.C.(2015).Outlieranalysis.Springer.
[5] Guyon,I.,& Elisseeff,A.(2008).An introduction to variableandfeatureselection.TheJournalofMachine LearningResearch,9(2),1157-1200.
[6] Vapnik,V.(2020).Statisticallearningtheory.Springer.
[7] Han,J.,Pei,J.,& Kamber,M.(2011).Data mining:conceptsandtechniques(3rded.).Elsevier.
[8] Akhil,M.S.,&Abraham,A.(2015).Asurveyonensemble learning for outlier detection.arXiv preprint arXiv:1507.00549.
[9] Cheng,L.,&He,X.(2020).Asurveyonoutlierdetection indeeplearning.arXivpreprintarXiv:2001.00639.
[10] Yin,H.,&Xu,W.(2019).Asurveyonoutlierdetectionin imagedata.arXivpreprintarXiv:1903.05231.
[11] Vapnik,V.(2020).Statisticallearningtheory.Springer.
[12] Yacoub,M.,Ammar,M.,Zerkani,H.,&Chehab,A.(2020). AnomalydetectioninindustrialIoTbasedonmachine learning in fog computing environment. Neural ComputingandApplications,32(7),5207-5224.
[13] Breiman,L.(2001).Randomforests.MachineLearning, 45(1),5-32.(UsedafterthementionofRandomForest anditsabilities)
[14] Quinlan, J. R. (1986). Induction of decision trees. MachineLearning,1(1),81-106.(Usedafterthemention ofDecisionTreeanditstransparency)
[15] Guyon, I., & Elisseeff, A. (2008). An introduction to variableandfeatureselection.TheJournalofMachine Learning Research, 9(2), 1157-1200. (Used after the description of the dynamic feature selection mechanism)
[16] Zaharia,M.,Xin,R.S.,Wendell,P.,Das,T.,Armbrust,M., Dave,A.,...&Ghodsi,A.(2016).Apachespark:aunified engineforbigdataprocessing.Communicationsofthe ACM,59(11),56-65
[17] Kreps, J., Narkhede, N., & Rao, J. (2011).Kafka: A distributed messaging system for log processing. ProceedingsoftheNetDB,1(1),1-7
[18] .Gogoi,P.,Bhattacharyya,D.K.,Borah,B.,&Kalita,J.K. (2011, December). A survey of outlier detection methods in network anomaly identification. In 2011 International Conference on Communication Systems andNetworkTechnologies(pp.505-510).IEEE.
[19] M.Ebrahimietal.(2017).Asurveyonmachinelearning based intrusion detection systems for IoT.Journal of NetworkandComputerApplications,95,297-321
[20] A. D. Sonowal et al. (2018).A review on machine learning based intrusion detection systems for IoT.International Journal of Computer Applications,184(12),1-10.
[21] M.T.Ribeiroetal.(2016).Model-basedinterpretability ofmachinelearning.arXivpreprintarXiv:1606.05396.
[22] S. Wachter et al. (2017).Counterfactual explanations withoutopeningtheblackbox:Automateddecisionsand theGDPR.arXivpreprintarXiv:1703.06864.
[23] K. M. A. S. Munasinghe et al. (2020).A survey on machinelearningbasedintrusiondetectionsystemsfor IoT:Anomaly detection perspective.Computers & Security,87,101616.
[24] S.Lietal.(2020).Asurveyonmachinelearningbased intrusiondetectionsystemsforIoT:Datapreprocessing perspective.IEEEAccess,8,212950-212971.
[25] D. Baena-García et al. (2020).A survey on machine learning based intrusion detection systems for IoT:Feature extraction perspective.Sensors,20(24),6536.
[26] H. Chen et al. (2020).A survey on machine learning based intrusion detection systems for IoT:Attack detectionperspective.IEEEAccess,8,212972-212993.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN: 2395-0072
[27] M.Z.A.Khanetal.(2020).Asurveyonmachinelearning based intrusion detection systems for IoT:Attack classification perspective.IEEE Access,8,212994213015.
[28] A.A.Alayemietal.(2020).Asurveyonmachinelearning based intrusion detection systems for IoT:Attack preventionperspective.IEEEAccess,8,213016-213037.
[29] M. A. Al-Jarrah et al. (2019).A survey on machine learning based intrusion detection systems for IoT:Attackresponseperspective.IEEEAccess,7,8650386524.
[30] I. Gilchrist et al. (2022).A survey of machine learning techniques for intrusion detection in the Internet of Things.ACMComputingSurveys(CSUR),55(1),1-40.
[31] Li, Y., & Ye, J. (2007). A two-stage linear discriminant analysis via QR-decomposition. IEEE Transactions on PatternAnalysisandMachineIntelligence,29(8),14411446.
[32] Provost, F., & Fawcett, T. (2013). Data science for business:Whatyouneedtoknowaboutdataminingand data-analyticthinking.O'ReillyMedia,Inc.
[33] . Lazarevic, A., Kumar, V., & Srivastava, J. (2005). Intrusiondetection:Asurvey.ManagingCyberThreats: Issues,ApproachesandChallenges,19,19-78.
[34] Sattari,F.,Farooqi,A.H.,Qadir,Z.,Raza,B.,Nazari,H.,& Almutiry,M.(2022).AHybridDeepLearningApproach forBottleneckDetectioninIoT.IEEE.
[35] Sadhwani,S.,Manibalan,B.,Muthalagu,R.,&Pawar,P. (2023, September 2). A Lightweight Model for DDoS Attack DetectionUsingMachineLearningTechniques. AppliedSciences,13(17),9937.
[36] Yılmaz,S.,Aydogan,E.,&Sen,S.(2021,July).Atransfer learningapproachforsecuringresource-constrainedIoT devices.InProceedingsofthe2021IEEESymposiumon SecurityandPrivacy(S&P)(pp.1384-1399).IEEE.
[37] Abdelmoneem, R. M., Shaaban, E., & Benslimane, A. (2019).Asurveyonmulti-sensorfusiontechniquesin IoTforhealthcare.IEEESensorsJournal,19(4),13091325.
[38] Chakraborty,S.,Pandey,S.K.,Maity,S.,&Dey,L.(2023,). Detection and classification of novel attacks and anomalyinIoTnetworkusingrule-baseddeeplearning model.
[39] Sriram,S.,Vinayakumar,R.,Alazab,M.,&KP,S.(2020). NetworkflowbasedIoTbotnetattackdetectionusing deep learning. In Proceedings of the 2020 IEEE
International Conference on Systems, Man and Cybernetics(SMC)(pp.2090-2095).IEEE.
[40] Tyagi, H., & Kumar, R. (2021). Attack and anomaly detection in IoT networks using supervised machine learning approaches. Research in Intelligence and Applications,13,1–15.
[41] Taheri, S., Salem, M., & Yuan, J.-S. (2018). Leveraging image representation of network traffic data and transfer learning in botnet detection. Big Data and CognitiveComputing,2(4),37.
[42] Desnitsky,V.,Chechulin,A.,&Kotenko,I.(2022).MultiaspectbasedapproachtoattackdetectioninIoTclouds. Sensors,22(5),1831.
[43] Al-mashhadi, S., Anbar, M., Hasbullah, I., & Alaa Alamiedy,T.(2021).Hybridrule-basedbotnetdetection approach using machine learning for analyzing DNS traffic.