
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 p-ISSN:2395-0072

Volume:11Issue:04|Apr 2024 www.irjet.net


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 p-ISSN:2395-0072

Volume:11Issue:04|Apr 2024 www.irjet.net

Prof. Jayshree Muley1 , Anirudh Dhokale2 , Sudarshan Khedkar3 , Prajwal Aher 4 , Sairup Urudwad5
1Guide and Professor, Department of Computer Engineering 2,3,4 Students, Department of Computer Engineering JayawantraoSawantCollegeofEngineering,Pune,India
Abstract - The rise of the internet and social media platforms has revolutionized communication, enabling individualsandgroupswithextremistideologiestopropagate theirbeliefsandrecruitfollowersonaglobalscale.Thispaper presents a comprehensive overview of the methods and technologiesemployedinthedetectionoftheonlinespreadof terrorism.Terroristorganizationsexploittheanonymityand reachoftheinternettodisseminatepropaganda,coordinate activities,andradicalizeindividuals.Detectingandpreventing these activities are critical for national security and the preservationofonlinespacesasplatformsforfreeexpression.
Key Words: Online Terrorism, Terrorism Detection, Extremism Online, Counter terrorism, Machine Learning,OnlineSafety.
1. INTRODUCTION
The detection of the online spread of terrorism involves monitoring and identifying individuals or groups that use the internet and social media platforms to promote, plan, or execute acts of terrorism. This is a critical aspect of counterterrorism efforts in the digital age, as the internet provides a powerful platform for recruitment, radicalization, communication, and propaganda by extremistorganizationsandindividuals.
The detection of the online spread of terrorism is an ongoing challenge that requires a multifaceted approach, including technology, international cooperation, legal frameworks, and efforts to counter radicalization and extremism.Itisadynamicfieldthatcontinuestoevolveas terrorists adapt to new online platforms and communicationmethods.
The methodology for developing a Terrorism Detection starts with defining clear objectives and selecting appropriatetechnologies.Followingthis,architectsdesign thesystem'sstructurewhiledeveloperscreateanintuitive userinterface.Integrationoftranslationlogicwithchosen APIs or libraries, as well as implementation of NLP

capabilitiesanduserauthentication,arekeysteps.Thorough testingensuresfunctionalityacrossvariouslanguagesbefore deploying on a suitable platform. Continuous monitoring post-deployment ensures optimal performance, while iterative feedback collection drives refinement and improvementtomeetuserneedseffectively.
1.CharacterizeGoalsandExtension:
•Obviouslyframethegoalsoftheventure.Figureoutwhat dialectsthesitewillsupportandwhathighlightsitwilloffer.
•Characterizetheextentoftheundertaking,includingthe interestgroupandaparticularnecessitiesorrequirements.
2.MarketExplorationandInvestigation:
•Directstatisticalsurveyingtocomprehendtheinterestfor language interpretation benefits and recognize expected contenders.
•Dissectexistinglanguageinterpretationsitestograsptheir highlights,assets,andshortcomings.
3.RequirementsSocialaffair:
• Assemble definite necessities from partners, including languagesupport,friendlyUI,uphelddocumenttypes,and soforth.
4.TechnologyStackChoice:
•Thiscouldincorporateprogrammingdialects,structures, andlibrariesforfrontendandbackendimprovement,aswell asdatasetarrangements.
5.DesignStage:
• Makewireframesandmodelstopicturethedesignand usefulnessofthesite.
•PlantheUI(UI)andclientexperience(UX)toguarantee naturalrouteandavailability.
6.Development:
•Carryoutthefrontendandbackendusefulnessasperthe endorsedplansandprerequisites.


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 p-ISSN:2395-0072

Volume:11Issue:04|Apr 2024 www.irjet.net
• IncorporatelanguageinterpretationAPIs orfosteryour interpretationmotoriffundamental.
7.Testing:
•Leadfarreachingtestingtorecognizeandfixanybugsor issues.
•Testthelanguageinterpretationexactnessandexecution underdifferentcircumstances.
8.Deployment:
• Set up the site for arrangement to the creation climate. Send the site and perform last checks to guarantee everythingisworkingaccurately.
9.Post-SendoffObservingandImprovement:
• Screen the site's exhibition, including uptime, reaction times,andclientinput.
• Gather investigation information to figure out client conductanddistinguishdevelopment.
10.MaintenanceandBacking:
•Giveprogressingupkeepandbackingtoresolveanyissues orupdates.
•Consistentlyupdatelanguageinterpretationmodelsand calculationstofurtherdevelopprecisionandexecution.
•Remaininformedaboutarisingadvancesandpatternsin language interpretation to integrate new highlights and upgradesintothesite.
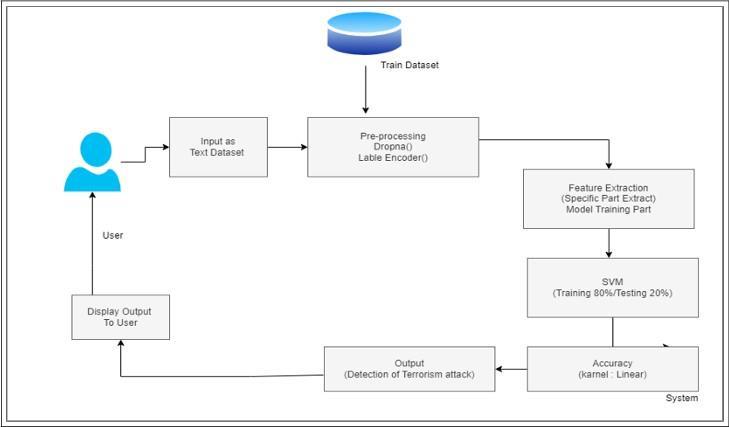
Fig. 1 : ArchitectureDiagram


2 : LoginForm
3 : RegistrationForm


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 p-ISSN:2395-0072

Volume:11Issue:04|Apr 2024 www.irjet.net
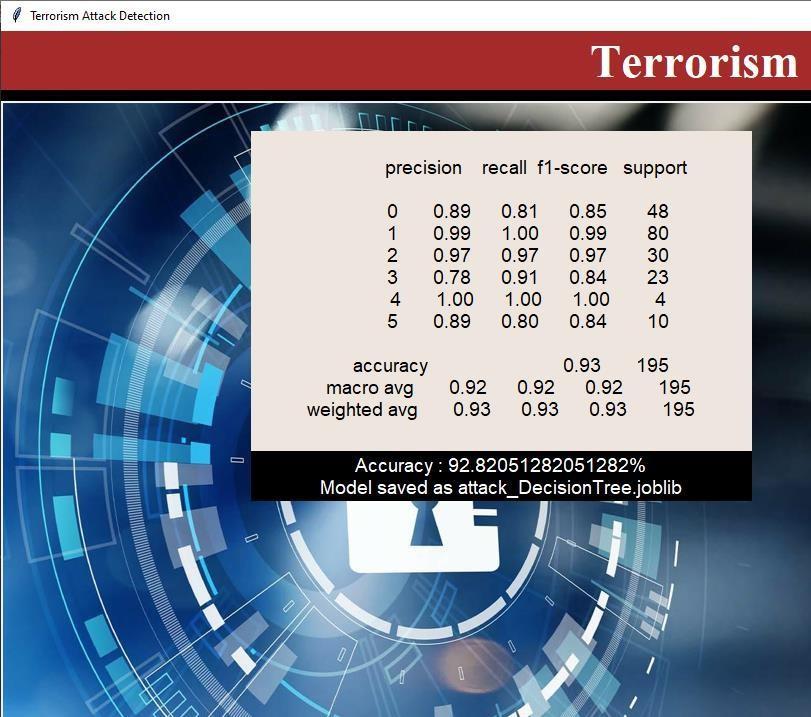
4. CONCLUSION
Thedetectionoftheonlinespreadofterrorismisacritical andmultifacetedendeavorwithprofoundimplicationsfor national and international security. As technology has evolved,terroristsandextremistgroupshaveincreasingly turnedtotheinternettodisseminatetheirideologies,recruit


followers,andplanattacks.Detectingandcounteringthese onlineactivitiesisessentialtopreventingactsofterrorism, disruptingterroristnetworks,andsafeguardingthepublic. By addressing the challenges and limitations while leveraging the advantages of detection efforts, society can betterprotectitselfagainsttheevolvingthreatofterrorism inthedigitalage.
Weexpressourgratitudetothedivineforbestowinguswith blessingsandguidingoureffortstoasuccessfulconclusion. We deeply appreciate the invaluable guidance and advice provided byouresteemed mentor, Prof.JayshreeMuley, duringcritical moments,steeringus intherightdirection. for granting us access to necessary facilities. Our sincere appreciationalsogoestoallthefacultymembersfortheir support.Finally,wearegratefultoourfriendsandfamilyfor theirunwaveringencouragementthroughoutthisendeavor.
[1] Begum A., N., Rakavi S., H., R., M., R. H., A. (2019). Detectionofonlinespreadofterrorismusingwebdata mining.InternationalJournalofAdvanceResearch,Ideas and Innovations in Technology, 5(1), 342–346. https://www.ijariit.com. (IBIGDELFT), 51–55. https://doi.org/10.1109/ibigdelft.2018.8625289.
[2] Goradia,R.,Mohite,S.,Jhakhariya,A.,Pinjarkar,V.(2020, June). Web Min ing to Detect Online Spread of Terrorism. International Journal of Engineering Research Technology (IJERT), 9(7), 645–648. http://www.ijert.org.
[3] Negandhi, A., Gawas, S., Bhatt, P., Porwal, P. (2021, March).DetectOnlineSpreadofTerrorismUsingData Mining.IOSRJournalofEngineering(IOSRJEN),13,17–19.https://www.iosrjen.org.
[4] Ahsan,S.,Shah,A.(2020.Datamining,semanticweband advanced infor mation technologies for fighting terrorism.2021InternationalSymposiumonBiometrics and Security Technologies, 1–5. https://doi.org/10.1109/isbast.2008.4547644
[5] Shaikh, M. A., Jiaxin, W. (2020). Investigative Data Mining: Identifying Key Nodes in Terrorist Networks. 2021 IEEE International Multitopic Conference, 201–206.https://doi.org/10.1109/inmic.2021.358163
[6] Sachan,A.(2020). Counteringterrorismthrough dark webanalysis.2020ThirdInternationalConferenceon Computing, Communication and Network ing Technologies (ICCCNT’12), 1–5. https://doi.org/10.1109/icccnt.2020.6396055


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 p-ISSN:2395-0072

Volume:11Issue:04|Apr 2024 www.irjet.net
[7] Chung, W., Tang, W. (2021b). Building a web collection for online surveil lance of U.S. domestic terrorism. 2021 IEEE International Conference on IntelligenceandSecurityInformatics,195. https://doi.org/10.1109/isi.2012.6284306
[8] Simanjuntak,D.A.,Ipung, H. P.,lim,C.,Nugroho, A. S. (2010). Text Clas sification Techniques Used to Faciliate Cyber Terrorism Investigation. 2010 Second International Conference on Advances in Computing, Control, and Telecommunication Technologies, 198– 200. https://doi.org/10.1109/act.2020.40
[9] [ Kiruba, J., Sumitha, P., Monisha, K., Vaishnavi, S. (2019, September). En hanced Content Detection Method to Detect Online Spread of Terrorism. In ternational Journal of Engineering and Advanced Technology (IJEAT), 8(6S3), 1166–1169. https://doi.org/10.35940/ijeat.F1195.0986S31.
[10] Aakash Negandhi, Soham Gawas, Prem Bhatt , Priya Porwal “Detect Online Spread of Terrorism Using Data Mining”.IOSR Journal of Engineering Volume 13,17 April 2019. So here they propose anefficient web data mining system to detect suchweb properties and flag them automatically for humanview. Keywords: Anti- Terrorism, Data Mining, Online,Terrorism,World


