

To evaluate the proposed routing protocol across several networks circumstances
Thrisha V.S1 , Dr.Anitha T.N2
1Assistant Professor, Dept. of CS&E, Sir. M Visvesvaraya Institute of Technology, Bangalore
2Professor & Head, Dept. of CS&E, Sir. M Visvesvaraya Institute of Technology, Bangalore ***
Abstract - This Internetv ofThingsv(IoTv)vhasbecomeone of the greatest noteworthy areas of computing because to the quick development of technology and internet-connected gadgets. IoTv ecosystem-targeting standards, technologies, and platforms are being created quickly. For a variety of uses, includinghealthcare,homeautomation,disasterrecovery,and industry automation, IoTv makes it possible for things to communicate andplan activities. Itv isvanticipatedthatitwill eventually cover even more applications.Thisarticleexamines several standards developed by the IEEEv, IETFv, and ITUv that support technologies allowing the explosive rise of IoTv To fulfil the needs of the IoTv, these standards encompass protocols for the communicationsv, routingv, networkv, and sessionv layers. The issue also includes management and security standards, providing details on the research being done to address these difficulties in addition to the current IoTv challenges. We propose simulation-basedresearchtoput a number on how important a cross-layerv designv is for better-quality QoSv sustenance in radiocommunication adv hocv systems. Using the J-Simv simulator, we contrast the layeredarchitectureutilizingtheAODVvroutingprotocolwith the CROSS-LAYERv Engine designusingQoS-PARvasarouting protocol. We make use of J-Sim since cross-layer implementations are suited for it. In addition to the recommended routing protocol, QoS-PARv, and the LYMPv protocol, we usedit to create the entire CROSS LAYERvEngine architecture. The movement of nodes in mobile ad hoc networks frequently changes the network structure, making routing in MANETsv a challenging problem. The efficient routing algorithms could considerably benefit mobile ad hoc networks in terms of performance and reliability. Such networks have been the subject of several routing protocol proposals thus far. There have been some studies published in the literature evaluating the performance of suggested routing protocols under CBRv traffic with various network conditions, but little attention has been paid to evaluating their performance when applied to traffic generators other than CBRv, such as FTPv, TELNETv, etcv. The complexity of traffic in actual applications is not reflected by CBRv trafficv, and the trafficv scenarios described here are more like the network loads experienced by MANETsv intherealworld.This article examines the performance of the three routing protocols AODVv, DSRv, and WRPv for FTPv, TELNETv, and CBRv traffic in terms of packet delivery ratio, throughput, average end-to-end delay, and routing message overhead. Many network circumstances are considered, including the
effects of modifying the halt length and the quantity of source destinations. For the consolidation and centralization of the public safety network's main services, it is essential to assess which routing protocol provides the best performance and throughput in a mission-criticalv setting. The following routingv protocolsv are evaluated: Routingv Informationv Protocolv (RIPv), Openv Shortestv Pathv Firstv (OSPFv), Interior Gatewayv Routingv Protocolv (IGRP), andEnhancedv Interiorv Gatewayv Routingv Protocolv (EGIRPv). Convergencev, throughputv, and queuingv delay are also evaluated. The network is simulated using Riverbed Modeler Academic Edition 17.5vv. According to a study of the results, which procedure should be utilized.
Key Words: IoT, GSM, RPL, RFID.
1. INTRODUCTION
This document is template. We ask that authors follow A similar approach has been used for radio adv hocv and instrument systems due tov thev Internet's widespread popularity, which is largely due to its layered design. Unfortunately, a rigid layered structure is not adaptable enough to deal with the changing situations, which will obstruct performance improvements. Due to the unpredictability and unreliability of the underlying radiocommunication intermediate, cross-layerv design researchinradiocommunicationinstrumentgridsandadv hocvnetworkshasrecentlyattractedalotofattention.Many studies have been undertaken on various elements of the cross-layerv design. Finding a method for each layer's abstraction and an appropriate coupling mechanism is essential for successful cross-layer optimization. Crosslayerv designv may be broadly split into layer trigger schemev,jointoptimizationvschemev,andcompletevcrosslayerv designv depending on how many layers (singlev, multiplev,orwholev)areengagedinoptimizations.Inboth wired and wireless networks, layer triggers predefined signals that alert to situations like data transmission problems between protocols are often utilized. Samples contain the Obvious Cramming Announcement method, whichv alerts the receiver whenever network congestion happens,andtheL2vtrigger,whichisinsertedamongthev link and Disposable etiquette coating to effectively notice variations inv thev condition of radiocommunication systems. International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 Volume: 11

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072

Fig 1: Thev IoT Ecosystem
The coat gun trigger technique offers optimizationv and benefitsbytakingaperpendicularcrosscutacrossthesheets whileretainingthecurrentprotocolstackintheforeground. Thesetriggersmaybesetoffonaregularbasisbynetwork eventsoranadaptivecontrolsystem.Althoughifmorethan two tiers of the protocol stack may be included in such a trigger mechanism, only a particular layer component overseesotherpartsatupper-orlower-layerlayersharvest relevantparametersandprovidethemtothedefinedlayer, whichiswheretheoptimizationprocessistakingplace.For instance, a control loop based on cross-layer information shared betweenthemediumaccessandnetwork layersis proposed, the physical layer transmission mode used to predict link stability and link lifetime is monitored, route rearrangement protocols are enabled to act quickly and prevent route breaks and packet loss, TCPv is the most popular transport and the foundation for various other protocols in both wired and wirelessv networksv. The prolongedhidden-/exposed-terminalissue,however,leads topoorend-to-endvconnection,whichnegativelyimpacts TCP'svperformanceinmultihopIEEE802.11vnetworks. In ordertosolvetheseissues,cross-layervinteractionvofTCPv andadvhocvroutingvprotocolsv,therearesomesuggested options,liketheTCPvfractionalwindowincrementscheme and the route-failure notification using bulk-loss trigger policy. Without altering the core TCPv window or the wireless MACv process, these protocols allow for the separationofcongestionfromothernetworkevents.

wirelessHART Architecture
Duringthelastseveralyears,wirelessmeshnetworkshave drawnmoreattention.Wirelessmeshnetworks(WMNs)vis being installed at an increasing rate. There are several prosperousnewbusinesses,or"meshfirms."Theirbrands arewell-knownnowthattheyaresellingmeshequipment and providing wireless mesh solutions to customers even thoughtheyhavebeeninbusinessforalong.Wirelessmesh networksarereceivingmoreattentionandpublicationsasa result of the growing number of press reports and publicationsonthem.ThenumerousnewWMNvstandards organizations and the significant interest in them are anothersignoftheincreasingnoticeinradiocommunication webgrids.NetworkmeshWLANsvarestandardizedbyIEEE 802.11sv. Network schmoozing for radiocommunication private part networks is a focus of IEEEv 802.15.5v. The term wireless multi-hop relaying is defined by IEEE 802.16jv.OvertraditionalwirelessLANsv,wirelessvmeshv networksv offer more performancev, flexibilityv, and dependabilityv. Wireless communication between nodes throughseveralradiocommunicationjourneysonvavmesh net diagram is the primary feature of wireless mesh networking.
Effective routing protocols offer routes done the radiocommunicationwebandrespondtoactivevicissitudes invthevnetworktopologysothatmeshnodesmayinteract with oneanother evenv if theyvare not straight inv radio
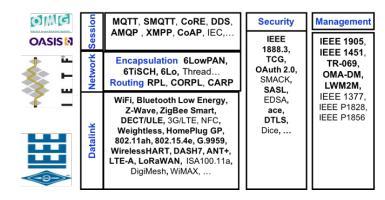
Fig 2: Protocols of IoT
Fig 3:

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072
variety of one another. The packets will be sent to the destination via intermediate nodes on the route. The foundation of mobile ad hoc networks (MANETs)v is the same: effective routing techniques for wireless meshed network graphs and wireless multi-hop communication. MANETv-specific routing techniques are often used in wireless mesh networks. The same fundamental ideas underlie both radio net systems and moveable adv hocv systems,howevertheyplacedifferingemphasisoncertain factors. With an emphasis on end-userv strategies, movement,andadvhocvcapabilitiesv,MANETsvemerged fromanacademicsetting.Asopposedtothis,WMNsvhavea commercial background and concentrate mostly on still strategies,frequentlyorganizationstrategies,dependability, networkv capacityv, and, of course, practical implementation.BetweenWMNsvandMANETsv,however, thereisnocleardistinction.Articlesorpublicationsthatuse bothtermstogetherdosotoshowhowcloselyrelatedthey are.Nowadays,publicwifivaccessisthemostwell-known useforwirelessmeshnetworks.WLANvaccesspointsare dispersed throughout cities, as well as on college and corporate campuses, and the wirelessv meshv networkv offersacustomizablebackhaulvforvthem.Inyoumayfinda studyonradionetworksystems.Includedinisasummaryof routing in WMNsv. This article describes the suggested routing for the future IEEEv 802.11svv WLANv mesh networkingstandard.ThepresentdraughtstandardD0.01v fromMarch2006vservesasthebasisforthedocument.
2 RELATED WORKS
[1]AvReviewvofvCurrentvRoutingvProtocolsvAdvHocv Mobilev Wirelessv Networksv, the author of thisv paperv describesmorethanafewdirection-findingstrategiesforv adv hocv moveable systems. We also categorize these schemes basedontheroutingtechnique(i.e.,table-driven and on-demand) We have contrasted these two groups of 54v routing methods, showing their similarities and differences. Lastly, we have explored potential uses and difficultiesposedbyadhocmobilewirelessnetworks.Each protocolhasobviousbenefitsanddrawbacksandissuitable forsomecircumstances,evenifitisunclearwhichalgorithm or family of algorithms is the best in all circumstances. Althoughtherearestillmanyobstaclestoovercome,thearea of ad hoc mobile networks is expanding and changing quickly. It is expected that over the next few years, these networkswillbeusedextensively.
[2] Av Surveyv ofv Protocolsv andv Standardsv forv InternetvofvThingsv,inthisresearch,itisshownhowthe Internetv ofv Thingsv (IoTv)v has become one ofv thev greatest important areas of computing thanks to the fast developmentoftechnologyandinternet-connectedgadgets. A lot of ground is being made in the development of standards, technologies, and platforms for the IoT ecosystem.Healthcare,homebasedmechanization,tragedy retrieval,andbusinessmechanizationarejustvavfewvofv
thev frequent areas where the Internet of Things (IoT)v enablesthingstocommunicateandcoordinateactionsInthe future,furtherapplicationsareanticipatedtobeadded.This articleexaminesseveralstandardsdevelopedbytheIEEEv, IETFv,andITUvthatsupportthetechnologiesallowingthe explosiveexpansionoftheIoTv.Toaddresstheneedsofthe InternetofThings,thesestandardsencompassprotocolsfor the infrastructures, direction-finding, net, and meeting layers.ThetopicincludesthecurrentIoTchallengesaswell asmanagementandsafetyvalues,providinginformationon theresearchbeingdonetoaddressthesedifficulties.
[3]ProposedvRoutingvforIEEEv802.11svWLANvMeshv Networksv, basedv onv thev currentv draught standardv D0.01vfromMarch2006v,thisresearchgivesadescription oftheplanneddirection-findingforvIEEE802.11svWLANv websystems.Anextensibleframeworkforroutingisdefined byIEEEv802.11sv,alongwithanewmeshdataframetype. ItdescribesHWMPv,thestandardroutingprotocol.AODVv is the foundation of HWMPv, which also contains a customizablepostponementforvpracticaldirection-finding nearso-calledvwebdoorways.Forlayer2vrouting,itmakes useofMACvaddresses,andwhiledeterminingpathways,it employs a radio-aware routing metric. There is also information on the RA-OLSRv optional routing protocol. Notethat,atthetimeofwriting,workisstillbeingdoneto standardize WLANv Mesh Networking in IEEEv 802.11sv. The suggested routing protocols' specifics are likely to evolve, even though their fundamental ideas appear to be fairly set. It also offers a comprehensive analysis of the planned routing for the future IEEEv 802.11svv WLANv meshnetworkstandard.IEEEv802.11s'vvcomprehensive pertinency to a variety of radiocommunication network usage scenarios is a result of the configurable evasion steering procedure HWMPv, the extensible outline forv steeringwithvRA-OLSRvasanelectiveconsistentsteering etiquette,andvthevaptitudetovparticipateimprovedandv vendor-specificvsteeringetiquettes.Theinformationbeing provided is based on the initial draught of IEEE802.11sv, which will change before it is officially accepted. The fundamentalideasbehindtheroutingsystem,HWMPv,and RA-OLSRvare,nonetheless,widelyacceptedandveryrobust. Eventhoughitisquitepossiblethatcertainelementsmay alter,thismeritsapublishinglikethis.Theworkgroup"s"is activelyexaminingandenhancingthedraughtstandard.In response to suggestions from a preliminary internal evaluation,contributionshavebeenmadepublic.Laterthis year, during the first letter ballot, a lot of comments and adjustmentsareanticipated.TheIEEE802.11svstandardis anticipatedtoreceiveitsfinalcertificationin2008v
[4] Intercommunication in Packet Network Protocol, the sharing of resources between various packet switching networksissupported bya certain protocol.The protocol supports end-to-end error checking, sequencing, flow control, changes in individual network packet sizes, transmissionfailures,andtheestablishmentanddeletionof

Volume: 11 Issue: 04 | Apr 2024 www.irjet.net
logicalprocess-to-processlinks.Considerationsaremadefor several implementation challenges, and issues with accounting,timeouts,andnetworkroutingarerevealed.In our discussion of the connectivity of packet switching networks, we covered some important topics. We have detailed a straightforward yet very robust and adaptable protocol that allows for the modification of individual networkpacketsizes,transmissionerrors,sequencing,flow management,andtheformationanddissolutionofprocessto-process relationships. By considering some of the implementation-related concerns, we discovered that HOSTSv with significantly different capacities may implement the proposed protocol. The creation of a comprehensivespecificationfortheprotocolisacrucialnext step,allowingfortheexecutionofcertainfirsttests.These tests are required to establish some of the operational characteristics of the proposed protocol, such as the frequency and extent of packet arrival out of order, the amount of segment acknowledgment delay, and the appropriateretransmissiontimeouts.
[5] Network Throughputv, End-to-Endv Delayv, andv NormalizedvRoutingvOverheadvComparativeStudyofTwo RoutingProtocolsWeproposeasimulation-basedstudyto placeavalueonthenecessityofacross-layervprojectforv enhanced QoSv sustenance inv radiocommunication adv hocvnetworksv.UsingtheJ-Simvsimulatorv,wevcontrast the CROSS-LAYERv Engine architecture's use of the QoSPARv direction-finding procedure withv the coated construction'suseofthevAODVvroutingvprotocolv.Dueto itssuitabilityforcross-layerimplementations,weemployJSimv.Inadditiontothesuggestedroutingvprotocolv,QoSPARv, and the LYMPv protocol, we used it to create the wholeCROSSLAYERvEnginevarchitecturev.Incontrastto AODVv,whoseperformancedeclinesnoticeablyasnetwork size or the number of accepted flows increases, QoSvperformancevPAR'svwasalsovirtuallyunaffectedbythese factors.IfwecompareQoSPARvoverCROSSLAYERvEngine withAODVvoverthelayeredbuilding,theperformanceof AODVvdegradessubstantiallywhenthenetworksizeorthe numberofflowsisraisedwhilethatofPositionvAssistedv RoutingvProtocolvwasnotsensitivetoeither.
[6] Wireless Sensor Networks: Routing Protocols and SecurityIssues,theauthorofthisstudyholdsthatawireless network made up of a lot of sensor nodes is the Wireless Sensor Network (WSN)v Network communication is facilitatedbyroutingprotocols.Routingprotocolsestablish andkeepuptheroutesinthenetworkbydeterminingthe best way for data transmission. There have been several suggestedroutingmethodsforWSNsv.Yet,theseprotocols can only be used to a certain extent without security. Anotherkeyaspectisensuringsafecommunicationbetween nodesThisstudyanalysesroutingprotocols'categorization andcomparison.Furthermore,coveredinthisresearchare differentsecurityriskstowirelesssensornetworkrouting methodsaswellasafewcountermeasures.Thearchitecture
of the routing protocols utilized in the wireless sensor networkisalsoattemptedtobeclarified.Yet,thesecurityof routingprotocolsfallsshortofourexpectationsintermsof security. Protection against attacks in WSNsv requires networklayerencryptionandauthentication.
[7]PerformancevEvaluationvofvRoutingvProtocolsvforv MANETsv underv Differentv Trafficv Conditionsv, in this article,itisshownhowtheflexibilityofbulgesinamovable advhocvsystemcausesfrequentchangesinvthenetworkv architecture, creation direction-finding in MANETsv a difficultoperation.Invtermsvoftogetherpresentationand dependability, the effective routing protocols can provide mobile ad hoc networks several advantages. There have alreadybeenseveralroutingprotocolssuggestedforthese networks. Studies analyzing thev recital of suggested direction-finding procedures below CBRv traffic under various net circumstances have been described in the literature, but less attention has been paid to assessing theirv presentation whenv practical tov circulation producersothervthanvCBRv,suchasFTPv,TELNETv,etc.In contrasttoCBRvtraffic,whichdoesnotaccuratelydepictthe multifaceted countryside ofv trafficv in actual requests, thesevcirculationstatesaremorelikethesystemdemands thatwouldbeimposedonreal-worldMANETsv.Intermsof throughputv, averagev end-to-endv delayv, packetv deliveryvratiov,androutingvmessageoverhead,thisarticle comparesthepresentationofvthreevroutingvprotocolsv AODVv, DSRv, and WRPv for FTPv, TELNETv, and CBRv traffic.Avarietyofnetworkcircumstancesareconsidered, including the impact of changing the pause duration, the quantity ofv source-destinationv pairsv (i.e., the provided loadv),andthenormalnoderapidity.
[8]ImplementationDSDVvroutingvprotocolvforvwirelessv mobilevad-hocvnetworkv,usingvNS-2vsimulatorv,Dueofv theextremelydynamicenvironment,routinginMANETvis thefocusofthisresearch.Everytimeapacketvneedsvtov bevtransportedtovitsterminusacrossmanyprotuberances, a routingv protocol is required, and numerous directionfinding methods consume stood suggested forv ad-hocv networksv.Inthisstudy,weattempttocomparetheeffects ofresponsiveandpracticalkindetiquettesbyincreasingthe nodedensityinthesystem, keepingthesourcenodefixed andmovingthedestinationnode,andultimatelykeepingthe destination node fixed and moving the sourcev nodev. In each of the three scenarios, the routing protocol's effectiveness has been examined in order to enhance, choose,andcreateaneffectiveroutingprotocolfornetwork configuration and realistic situation. Packet loss, delivery fraction, and end-to-end latency are all included in the performancematrix.Intermsofnodemobilityandnetwork nodedensitygrowth,thisarticlerealisticallycomparesthe threeroutingprotocolsDSRv,AODVv,andDSDVv.Keepthev basis bulge constant andv thev terminus protuberance variable in the first case. In comparison to AODVv and DSDVv, the performance of the DSRv routing protocol is International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072
relativelygood.In eachofthethreescenarios,the routing protocol's effectiveness has been examined in order to enhance,choose,andcreateaneffectiveroutingprotocolfor network configuration and realistic situation. Packet loss, deliveryfraction,andend-to-endlatencyareallincludedin the performance matrix. In terms of node mobility and network node density growth, this article realistically compares the three routing protocols DSRv, AODVv, and DSDVv.Keepthebasisbulgeconstantandthejourney'send protuberance variable in the first case. In comparison to AODVv and DSDVv, the performance of the DSRv routing protocolisrelativelygood.
[9]AnalysisvofvRoutingvProtocolsvinvanvEmergencyv CommunicationsvCenterv,thefocusofthisessayisRoutingv protocolsvarevcast-offineverynetworktoselectthemost ideal routes forv sending and receiving packets between different sites. An imagined rational system forv a cooperativevEmergencyvCommunicationsvCenterv(ECCv) between two towns is presented in this study. Whichv routingvprotocolvofferstheoptimumspeedandamountin a mission-criticalv situation must be assessed in order to consolidate and centralize the public safety network's essentialfunctions.Convergence,throughput,andqueuing timearetestedforfourdifferentroutingprotocols:Routingv Informationv Protocolv, Openv Shortestv Pathv Firstv, Interiorv Gatewayv Routing Protocolv, and Improved InteriorGatewayRouting Protocol.The netismodelledin RiverbedvModelervAcademicvVersion17.5vforWindows. Whichproceduretobeusedmaybedeterminedbyanalysing thefindings.Thedirection-findingproceduretodeployina netthatiscrucialtooperationshasbeendeterminedaftera comprehensive examination and contrast ofv thev chosen routingv protocolsv. In almost every measurable metric, EIGRPvconsistentlyperformedbetterthantheotherthreev protocolsv. File attendant packages tov thev ECCv switch weretheonlycircumstanceinwhichEIGRPvwasassessedto performbetterthantheotherthreeprotocols.Themarginby which EIGRPv beat the other routing protocols was substantial,givenhowcrucialdatabaseaccessandtrafficare to a public safety network. The speed of convergence is a crucialcomponentofeverynetwork.Inanetworkforpublic safety,whensecondscount,thisisextremelyimportant.The decision here was EIGRPv without a doubt. Although it would be logical to think that no new networks would be developedusingFDDIvbecauseitisanobsoletetechnology, manypublicsafetygroupslackthefundingandtechnological know-howthataprivatecompanycouldhave.Despitethis, EIGRPv remains the ideal protocol to employ because it experiencedtheleastamountoflatency.
[10]Proposed Routing Protocol for clouds, As the name indicates,thecloudthatservesasaplatformfornumerous onlineservicesiswhatwerefertoasthe"cloudcomputing" inthisstudy.Thecloudisarepresentationofthepay-peruse model used for internet-based services. Open-source routing protocols are frequently used in the cloud. Also
Fig: Relationv among diverse International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
compatible with our cloud system is a wireless sensor network.Anetworkisallthatthecloudis,anditprovidesa variety of services, but in order to do so, a good network setupandpackettransmissionmustbedone.Severalrouting protocols are needed in order to transport a packet. The study compares routing systems based on network efficiency. One of the primary problems is how communicationcanbecarriedoutviaawirelessnetworkon thecloud.Thefundamentalsofthevariousroutingprotocols usedinnetworkingwerecoveredinthisessay.Asuggested protocol is provided for a cloud network that really has greater advantages in the clouds. Although each of the describedroutingprotocolshasauniquesetofbenefits,they allhavethedisadvantageofrequiringaprotocolthatisboth scalable and mobile in order to support big networks and mobiletechnologies.Sincethesourcenodesearchesforits destination'sneighbors,thisstrategypracticallyminimizes networkcongestionwhilealsoassistinginadecreaseinthe frequency of broken links. There is no doubt that this strategyshouldbeusedasitdoesn'tneedalotoflabor.
3.METHODOLOGY
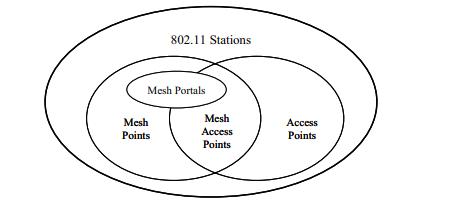
InJuly2004v,theIEEE802.11vworkinggroup'sresearch groupforESSmeshnetworkingwasrenamedtaskvgroupv "sv" (TGsv)v. Its objective is to create a wireless mesh network standard that is versatile and extendable and is based on IEEE 802.11v. Radiocommunication multi-hopv routingv, which establishes the routes forv radiocommunication promotion, is one of IEEEv 802.11vs main features. IEEE 802.11s'sv scope and some specifications are defined in the PAR document. The IEEE 802.11v standard refers to mesh nodes as mesh points (MPsv)v. A station that supports both IEEE 802.11v and meshisreferredtoasameshpoint.Inaccordancewiththe proposed 802.11sv amendment, the term "meshv capabilitiesv" refers to the ability to contribute in the net steering etiquette andv to advancing information onv behalfvofothernetfacts.revealedinvFigure1asthenet grid.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net

WLANv net system
Anewfangledwebinformationborderformatisdefinedby theIEEE802.11svmodification(Figure3)v.Whensending data within a WLANv meshv networkv, this MACv frame formatisutilized.Thisformataddsamesh-specificcontrol fieldtothealreadyexistingdataframeformat.Thetwoflags toandfromDS,aswellasthetypeandsubtypeforthemesh dataframe,areincludedintheframecontrolfieldtogether withadditionalcontrolinformation.Thetwoflagsvaresetto 1v to indicate that the data frame is in the mesh network because it is part of the wireless distribution system. The fouraddressfieldsinclude48-bitvMACvaddresses,which arelong.Itisspecifiedbythereceiveraddress,oraddress1, which mesh point must receive the wireless signal. The transmitter address, or 2v, identifies the mesh point that sentthiswirelessdataframe.Address3v,whichservesas the data frame's destination, indicates the final (layer 2v) location of the data frame. This data frame's source is identifiedbyaddress4v,whichisthesourceaddress.The3byte-longvmeshforwardingcontrolfieldhastwofields.The 16-bitv long mesh end-to-endv sequence number enables the broadcast flooding control and the transmission of orderedmeshdataframes.Framesareuniquelyidentifiable by a source mesh e2ev sequence number for a particular sourcemeshpoint.Throughouttheforwardingofmeshdata frames,thesourcemeshpointestablishesandmaintainsthe meshend-to-endsequencenumber.The8-bitlongtimeto livefield(TTLv)isusedtotimeoutmeshdataframesthat may have inadvertently become stuck in an endless forwardingloop.Sendingcommandsforthepathselection protocolrequirestheusageofmanagementframesoftype action. The update to IEEEv 802v.11sv defines a new category of mesh management for action management frames. The action field's value dictates what kind of management message will be sent. As an IEEE 802.11v informationelement,theactualmessageisdisplayed.
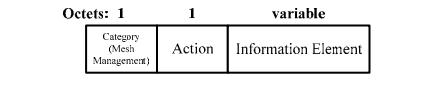
IEEEv 802.11sv meshv managementv actionv framev formatv

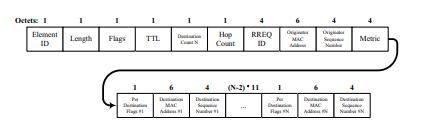
Fig: IEEEv 802.11sv meshv datav framev formatv
Fig: Structurev of HWMPv route requestv (RREQ) informationv elementv
The main advantage of reactive routing is that it only determinesapathwhenoneisnecessarytotransmitdata between two mesh nodes. There is a delay for the initial packetorpacketsbecausethecomputationofthepathtothe desired destination and the discovery of the connections withtheircharacteristicsdonotstartuntilafterthefirstdata packet has already arrived at the routing module of the foundation protuberance. Yet, if there is no trafficv in the meshv networkv or if the road traffic decoration is not changing, this on-demand generation of the paths always uses the most recent link status data, such as from radio aware link measurementsv, and it reduces the routing overhead.TheroutefindingmechanismusedbytheHybridv WirelessvMeshvProtocolviswell-knownvfromAODVvand DSRv
Arouterequestmessageisbroadcastbyafoundationmeshv pointvthatvneedsvawaytogotoalaststopmeshvpointv inordertocompleteitsmission.Eachmeshpointprocesses andtransmitstherouterequestmessage,whichestablishes reversible pathways to the route discovery's initiator. If thereareanyintermediate meshpointsonthewaytothe destination,theywillalsosendaunicastroutereplymessage
Fig: Example of an IEEEv 802.11vsIEEEv 802.11v (meshv) nodes.
Fig:

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072
astheiranswer.Thisishowthepathleadstothedestination isconstructed.InordertocomplywithanIEEEv802v.11sv pathselectionprotocol'svrequirements,whichincludeusing layer2MACvaddressesandradio-awareconnectionmetrics, the route-finding technique has also been updated. The mechanismsoftheHWMPvreactiveroutingaremorefully explainedinthefollowingsentences.
If there is already a path to the source mesh point S, the meshpointdeterminesifitmustbeupdated.ThepathtoSv ischangedifthenewpathmetricintheRREQvissuperiorto thepathmetricintheassociatedroutingtableentryandthe sequencenumberoftheRREQvisequaltoorhigherthanthe sequencenumberofthecurrentroutingtableentryforthe source mesh point Sv. The existing path to Sv is modified regardless of the value of the new path metric if the sequencenumberoftheRREQvishigherthanthesequencev numberv of the linked routing table item by at least a specified threshold value. Additionally, if a more recent RREQv onewithagreater.v

Fig: Configurability of HWMP
WithasingleRREQvmessage,HWMPvenablessimultaneous path discovery to numerous destinations. The destination count parameter indicates how many destination mesh points need to be found. The turfs per journey's end decorations, journey's end discourse, and terminus arrangement quantity are contained in the destination countssequencesoftheRREQv.Itisnecessarytodividethe RREQv control flags into two groups as a result. The matchingperdestinationflagsfieldsaresetindependently foreachdestinationandcontainthecontrolflagsthatmay differinvalueforvariousdestinationsintheRREQv.Asboth the way demand and the course account travel the whole pathandgatherthemostrecentmetricdata,itguarantees thatthefoundpathmetricisaccurate.Theflagsfieldisset withcontrolflagsthatarethesameforalldestinationsinthe
RREQv.Thebroadcast(UB=1)vsettingisthedefaultforthe unicast/broadcastflag(UBv)v.Ithasbeenpresentedforthe HWMP proactive extensions. Insteadv of usingv the hopv totalsteeringmeasured,HWMPvemploysanarbitrarylink metric,oftenaradio-awareonelikethedefaultairtimelink metricdiscussedinsection6v.Thequantityofrelationsin the trail is shown by the hop count field in the RREQv message,butitisnotusedtomakearoutingchoice.Initial valuesforboththehopcountandthemetricare0.Therange oftheRREQvisspecifiedintermsofhopsviathetimevtov livevfield(TTLv)v.Priortogeneratinganewrouterequest, thesourcemeshpoint'sRREQvIDvcounterisincreased.The sequencenumberofthesourcemeshpoint,theoriginator,is increasedby1iftherouterequestwillbeutilizedforroute discovery.
The hop count measure is more stable than a radioawarev routingv metricv. It is therefore advisable to gather and utilize the link metrics' most recent data. The respond and forward flag (RF)v were implemented in order to eventually obtain the most recent route metric data. If the intermediatev meshv pointv produced an RREPv,theRFvflagvaffectshowtheRREQvissent.Ifthe RFv flag isset (RF=1)v, the intermediary mesh point will forward (broadcast) the updated RREQ. In this situation, setting the terminus only flagv to one (DO=1)v will prevent subsequent RREPsv from the succeeding intermediatevmeshvpointsvonthepathtotheintended destination. According to the established behavior of AODVv,DO=0v,RF=0vshouldbeused.Afterbeingunicast on the reverse path to the original mesh point Sv, the RREPvmessageissentfromwhatevermeshpointcreated it. For each journey's end in the terminus count last stop intheRREQvmessagewithmultipledesireddestinations, thedecisions,andactionsforthecreationofRREPsmust betaken.EndpointDivisdeletedfromthelistofdesired destinationsintheRREQvifanRREPvhasbeenprepared foritandtheRREQvdoesnotneedtobedeliveredtoitin the event of an intermediate mesh point (RFi=0v). The revised RREQv will be broadcast vtogether with the requests for any remaining destinations ifv therev arev anyvdestinationsvinvthisvlistvaftervallvdestinationsv havev beenv processedv. Thev RREQv will not be transmittedfurtherifthereisnodestinationremainingon thelistofdesireddestinations.
Table
-1: COMPARISON OF DIFFERENT TECHNOLOGIES

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072
3 DSRv DSRv allowsv multiplevroutesv doesv notv automaticallyv repairv a brokenv linkv
4 6LoWPANvv scalablevandvselfhealingv lessv securev than ZigBeev
5 OLSRv implementationv is morev userv friendlyv bandwidthvusagev lowv for thev maintainingv ofv thevroutesv
6 Datav Aggregationv Lowv qualityvdatavthatv isvaggregatedvv lotsv ofdatav aggregationv andvmanagementv solutionsv
7 Geographicv Routingv easyv comparisonv ofdatavitemsv retrievingv geographicvdatavis time-consumingv
8 IPv6vv Routingvv protocolv Efficientv Routingv, Increasedv Capacityv Systemv Issuesv, DevicevUpgradev
9 IP/MPLSv Scalabilityv, Efficiencyv Securityv, Maintenancev
10 Load balancingv Staticv IPv Addressesv,Zonalv Isolationv NovSSLv offloadingv
4. CONCLUSIONS
For ad hoc mobile networks, we describe many routing strategiesinthisarticle.Wealsocategorizetheseschemes based on the routing technique (i.e., table-driven and ondemandv). We have contrasted these two groups of 54v IEEEv Personal Communications April 1999v routing technologies,showingtheirsimilaritiesandcontrasts.Lastly, wehaveexploredpotentialusesanddifficultiesposedbyad hoc mobile wireless networks. Each protocol has obvious benefits and drawbacks and is suitable for circumstances, evenifitisunclearwhichalgorithmorfamilyofalgorithms is the best in all instances. Although there are still many obstaclestoovercome,theareaofadhocmobilenetworksis expandingandchangingquickly.Itisexpectedthatduring thenextfewyears,thesenetworkswillbewidelyused.

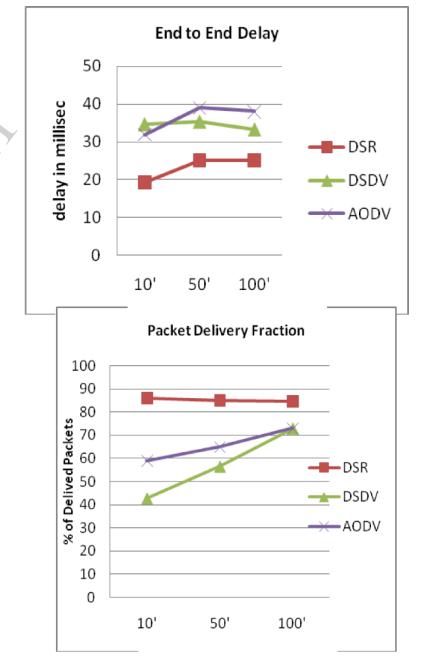
Fig 4: Packet Delivery Fraction1
Fig 5: Packet Delivery Fraction2

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 04 | Apr 2024 www.irjet.net p-ISSN:2395-0072
ThisstudyoffersathoroughanalysisofIoTprotocoloptions. The IETFv, IEEEv, ITUv, and other organizations have created and standardized several of those protocols, and many more are constantly being developed. Due to the enormous quantity, the conversation was short. Referrals havethusbeengivenformoreinformation.Thisdocument aims to provide developers and service providers with informationonthechoicesforvariousIoTprotocollayers andhowtoselectthemv.Wevalienatedthestudyintovfourv sectionsvbasedonvnetworkingvlayers:informationjoining, system direction-finding, system encapsulationv, and sessionv layersv. At each tier, wev highlighted a few draughtsandprovidedmostofthestandardsthathadbeen completed.Wealsoaddressedsomeofthecurrentsecurity standards and work done at various levels of standardization, as well as reviewing IoTv management protocols briefly. We concluded by talking about several issuesthatstillplagueIoTvdevicesandthatscientistsare workingtoresolve.
TheextensiblevframeworkvforroutingvwithRA-OLSRvas anoptionalstandardizedroutingvprotocolv,theabilityto integrate optimized and vendor-specificv routingv protocolsv, and the configurablev defaultv routingv protocolvHWMPvallcontributetoIEEEv802.11sv'broad applicabilityv to a varietyv of wirelessv networkv usagev scenariosv.Theinformationbeingprovidedisbasedonthe initialdraughtofIEEE802.11sv,whichwillchangebeforeit is officially accepted. The fundamental ideas behind the routingsystem,HWMPv,andRA-OLSRv,however,arewellestablishedandsolid.Eventhoughitisquitepossiblethat certainelementsmayalter,thismeritsapublishinglikethis. Theworkgroup"sv"isactivelyexaminingandenhancingthe draught standard. In response to suggestions from a preliminary internal evaluation, contributions have been madepublic.Laterthisyear,duringthefirstletterballot,a lotofcommentsandadjustmentsareanticipated.
REFERENCES
[1]ZJosévV.V.Sobralv JoelvJ.P.C.RodriguesvRicardovA. L.Rabêlov ,JalalvAl-Muhtadiv andvValeryvKorotaevv,“ Routingv Protocolsv forv Lowv Powerv andv Lossyv Networksv in Internetv ofv Thingsv Applicationsv” inv Receivedv: 23 Marchv 2019v; Acceptedv: 5 May 2019v; Publishedv:9May2019v
[2] Karimv Rostamzadehv, Studentv Memberv, IEEEv, Hasenv Nicanfarv, Studentv Memberv, IEEEv, Narjesv Torabiv, Studentv Memberv, IEEEv, Sathishv Gopalakrishnanv,Memberv,IEEE,andvVictorvC.M.Leungv, Fellowv, IEEE, “A Context-Awarev Trust-Basedv InformationvDisseminationvFrameworkvforvVehicularv Networksv” in IEEEv INTERNETv OFv THINGSv JOURNALv,VOL.2v,NO.2,APRILv2015v
[3] [1]Z. Safdarv, S. Faridv, M. Pashav, K. Safdarv, “ A SecurityvModelvforvIoTvbasedvSystemsv”invTechnicalv Journalv, Universityv ofv Engineeringv and Technologyv(UET)vTaxilav,Pakistanvvol.22No.4-2017v ISSN:1813-1786vv(print)v2313-7770(online)v
[4]ShubhalikaDihulia,TanveervFarooquiv,“AvSurveyvonv IoTvSecurityvChallengesv”in InternationalvJournalvofv ComputervAppliancesv(0975-8887)vvolume169vv–No.4, July2017v
[5]VandanavSharmav,RavivTiwariv“SecurityvonvIoTv andvitsvSmartvAppliancesv”inInternationalvJournalvof Sciencev, Engineeringv andv Technologyv Researchv(IJSETR),volumev5,Issuev2,Februaryv2016v
[6]Sachinv Upadhyayv “Ongoingv Challengesv andv Researchv Opportunitiesv” in Internationalv Journalv of EngineeringvTechnologiesvandvManagementvResearchv, 5(2:SE)v,216-222v.DOLv:10.6281/Zenodov.1195065v
[7]WeivZhouv,YuqingvZhangv,PengvLiuv“EffectvofvIoTv newv featuresv onv securityv andv privacyv” in Thev CollegevofInformationvSciencesvandTcehnologyv,Thev PennsylvaniavStatevUniversityv,PAv16802,USAv
[8]SaeedvBanaeianvFarv,AzadehvImanivRadv“Securityv analysisvofBigvDatav onv IoTv”invIEEEvtransactionsv invIndustrialvinformaticsv12.3(2016)v:1232-1242v
[9]Mirzav Abdurv Razzaqv, Muhammadv Aliv Qureshiv, Sajidv Habibv Gillv, Saleemv Ullahv “Securityv Issuesv invIoTv” inv (IJASCA)v Internationalv Journalv ofv AdvancedvComputervSciencevandvAppliancesv,volumev 8,No.6,2017v
[10]HuivSuov,JiafuWan,CaifengZou,JianqiLiu“AReview onSecurityinIoT”in2012IntenationalConferenceon
BIOGRAPHIES


Dr.T.N.Anitha, Professor&Head, DeptofCSE,Sir.MVIT Bangalore
Ms.ThrishaV.S, AssistantProfessor DeptofCSE,Sir.MVIT Bangalore
