
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
Varun Singh
1
1B.Tech Student, Dept. of Electronics Engineering, Madhav Institute of Technology & Science [MITS] Gwalior, India ***
Abstract: In today's digital era, data holds a significance comparable to that of oil, serving as the lifeblood for countless businesses and governmental operations, propellingdecision-makingprocesses,fosteringinnovation, and enhancing operational efficiency. However, this escalating reliance on data has illuminated the critical importanceofdatasecurity.Asinstancesofdatabreaches and cyberattacks continue to escalate, the imperative for robustprotectivemeasureshasbecomemorepronounced thanever.Datasecurityinvolvestheproactivesafeguarding ofdigitalinformationfromunauthorizedaccess,corruption, theft,oranyothernefariousactivities.
Conventionalsecuritymeasures,oncedeemedeffective,now prove inadequate in the face of increasingly sophisticated cyber threats. Cybercriminals have adeptly adopted new tactics and powerful tools to infiltrate, attack, and compromisedatasystems.Thankfully,ArtificialIntelligence (AI) technologies have stepped into the digital arena, offering ingenious systems capable of bolstering defenses against cyberattacks. This paper explores AI techniques deployedacrossvariousapplicationsintheongoingbattle againstcyberthreats.
Key Words: Data security, artificial intelligence, cyber attacks , Data , cybersecurity
1.INTRODUCTION
The spotlight on data confidentiality has intensified, particularly as ubiquitous internet access exposes critical corporatedataandpersonal informationtonovelsecurity threats. On the other hand, data sharing across different entities and for diverse purposes is crucial for numerous applicationsincludinghomelandsecurity,medicalresearch andenvironmentalprotection.Data securityencompasses various measures and protocol designed to safeguard sensitiveinformationandensuresitconfidentiality,integrity andavailability.Datasecurityaimtopreventunauthorized disclosure, modification or destruction of data, whether storedelectronicallyortransmittedovernetwork.
1.1 Key Aspects of data security
1.Confidentiality: Ensuringthatonlyauthorizedindividuals or system have access to sensitive data. confidentiality measures include encryption, access control to prevent unauthorizeddisclosure.
2.Integrity: Ensuringthatdataremainsaccurate,complete & unaltered during storage, processing & transmission. Integrity controls such as checksums & digital Signatures, detect&preventunauthorizedmodificationstodata.
3.Availability:Ensuringthatdataisaccessibleandusable when needed by authorized users. Availability measures includeredundantstorage,backupandrecoverysystems& robust network infrastructure to minimize downtime and disruptions.
4.Authentication: Verifying the identity of users and systems accessing data to prevent unauthorized access. authentication mechanisms include passwords, biometric authentication&multifactorauthenticationtovalidateuser identities.
5. Prevention of Financial loss:Businessandindividuals cansuffersignificantfinanciallossesduetodatabreaches; cybercriminalsmayexploitvulnerabilitiestostealfinancial data,conductfraudulenttransactionsorextortmoney.
6.Legal Compliance: many countries have strict data protectionlaws®ulations,adheringtotheselawssuchas theGeneralProtectionRegulation(GDPR)inEuropeorThe Health Insurance Portability & Accountability (HIPAA) in UnitedStatesisessentialtoavoidlegalconseques&fines.
7.Preventing Business Disruption: Cyberattacks & data breaches can disrupt normal business operation. Ransomware attacks for example can encrypt important data,renderingitinaccessibleuntilaransomispaid.thiscan leadtosignificantdowntime&financiallosses.
8.Intellectual Property Protection:Companiesoftenhave valuableintellectual property,tradesecrets&proprietary information.
9.National Security Concerns:Insomecases,compromised data can pose a threat to national security. Criminal infrastructure,defensesystem&governmentsinformation needrobustdatasecuritytopreventcyberthreats&attacks.
10.Preservation of Customer Data: Customercanexpect theirdatatobehandledresponsibly&securely.protecting customerdatanotonlyfulfillslegalðicalobligationsbut alsohelpsbuildcustomerloyalty&satisfaction.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
AIsystemsareundergoingrigoroustrainingtoexcelinthe identification of malware, execute intricate pattern recognition, and discern even the most minute characteristicsofmalwareorransomwareassaultsthrough the utilization of sophisticated algorithms. Leveraging natural language processing, AI extends its capabilities to offer enhanced predictive intelligence. It achieves this by autonomouslyscanningaplethoraofarticles,newspieces, and research on cyber risks, curating relevant material independently.
TechRepublicreportsthat,onadailybasis,mid-sizedfirms encounter warnings for approximately 200,000 cyber incidents. The sheer volume of these attacks would overwhelmthesecuritystaffofanaveragecompany,leaving somethreatsundiscoveredandcausingsubstantialnetwork damage.Inresponse,thereisagrowingrecognitionthatto operate effectively and shield organizations from the escalating realm of cyber threats, security professionals must rely significantly on the assistance of intelligent machinesandcutting-edgetechnologieslikeAI.
AI
AIexhibitsremarkablecapabilityinmanagingvastvolumes of data within a company's network, particularly in the bustling environment of a typical mid-sized firm where substantial traffic is the norm. The extensive exchange of databetweencustomersandthecompanyonadailybasis necessitates vigilant protection against potential threats posed by malicious individuals or software. Traditional cybersecurityexpertsfacechallengesinmanuallyinspecting thesheermagnitudeofdataforpotentialthreats.
AIemergesastheoptimalsolutionforuncoveringthreats cleverlydisguisedasroutineactivities.Itsautomatednature allows it to efficiently sift through large datasets and
network traffic. AI-based technologies, such as personal proxies,notonlyfacilitatesecuredatatransferbutalsoplay a vital role in detecting and identifying potential hazards concealed within the chaos of data flow. This automated vigilanceensuresarobustdefenseagainstthreatsthatmight otherwise go unnoticed, safeguarding the integrity and securityofthenetwork.
Duplicative Processes Reduce: As highlighted earlier, cyber attackers frequently evolve their methods, yet the foundationalsecuritypracticesremainsteadfast.However, entrustingtheseresponsibilitiestoahumanworkforcemay leadtoboredomandpotentialnetworkrisks.Incontrast,AI excels at managing redundant cybersecurity operations, emulatingthemosteffectivehumantraitswhileeliminating inherent flaws. This not only assists in the continual detectionandpreventionoffundamentalsecurityrisksbut alsoinvolvesacomprehensiveanalysisofyournetworkto identifyanypotentialsecurityflawsthatcouldposeharm.
Detection and response times are boosted:Inthequestto secureyourcompany'snetwork,theinitialimperativeisthe prompt detection of threats. Ideally, the ability to swiftly identify issues such as untrustworthy data is crucial for shielding your network from lasting harm. The most effective approach to achieve real-time detection and response to attacks involves the integration of AI with cybersecurity.Artificialintelligencemeticulouslyscrutinizes yourentiresystemforpotentialrisks,showcasingadistinct advantageoverhumancapabilities.Bydetectingrisksearly on, AI streamlines and simplifies security operations, fortifyingyourdefensesandenhancingoverallcybersecurity effectiveness.
Authenticity Protection :Themajorityofwebsitesprovide auseraccountfeatureforloggingin,accessingservices,or making purchases. Some sites incorporate contact forms where visitors input personal information. Given the inclusion of private and sensitive data on such sites, it becomes imperative for businesses to implement an additional layer of protection. This enhanced security ensuresthesafetyofguestsaccessingyournetwork.When usersintendtoconnecttotheiraccounts,AIplaysapivotal roleinauthentication.Utilizingvarioustechniquessuchas face recognition, CAPTCHA, and fingerprint recognition, among others, AI identifies and verifies users. The data derivedfromthesecharacteristicsaidsindeterminingthe legitimacy of login attempts. In the realm of business network security, hackers often employ tactics like credential stuffing and brute force assaults to gain unauthorizedaccess. The implementation ofadvanced AIdrivenauthenticationmeasuresservesasarobustdefense againstsuchmaliciousactivities.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
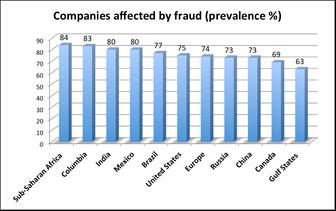
Fig2:Countrieswisecompaniesaffectedbycyberattacks
3. Data Security Challenges that AI Solve
Artificial Intelligence (AI) addresses several challenges in datasecurityintoday'scybersecuritylandscape.Someofthe challengesthatAIhelpssolveinclude:
1. Threat Detection and Prevention:
- Challenge: Thegrowingintricacyandsophisticationof cyber threats pose a challenge for traditional methods in detectingandpreventingattacks.
- AI Solution: ThreatdetectionsystemsenhancedbyAIcan sift through extensive datasets, recognizing patterns, anomalies, and established signatures. This empowers a more precise and proactive approach to identifying and addressingpotentialthreats.
2. Anomaly Detection:
- Challenge: Identifyingunusualpatternsinuserbehavior ornetworktraffic,whichmayindicateasecuritythreat,can bedifficult.
- AI Solution: AIalgorithmsexcelatanomalydetectionby learningnormalbehaviorpatternsandflaggingdeviations, helpingtoidentifypotentialsecurityincidents.
3. Advanced Persistent Threats (APTs):
- Challenge: APTs are stealthy, long-term cyber-attacks thatcangoundetectedforextendedperiods.
- AI Solution: AIsystemshavethecapacitytopersistently monitor and scrutinize network activities, adeptly identifyingsubtleindicatorsofAdvancedPersistentThreats (APTs)andenablingtimelyintervention.
4. Zero-Day Attacks:
- Challenge: Zero-dayattacksexploitvulnerabilitiesthat are unknown and, therefore, lack established defense mechanisms.
- AI Solution: Machine learning models can identify previouslyunseenpatternsassociatedwithzero-dayattacks, enhancing the ability to recognize and mitigate emerging threats.
5. Phishing Detection:
- Challenge: Phishing attacks, often relying on social engineering, can be challenging to identify through traditionalmeans.
- AI Solution: AI-powered phishing detection systems analyzeemailcontent,senderbehavior,andotherfactorsto identifyandblockphishingattemptsmoreeffectively.
6. Automated Response:
- Challenge: Rapidlyrespondingtosecurityincidentsand automatingcontainmentactionscanbechallengingwithout real-timeanalysis.
- AI Solution:AIenablesautomatedresponsesbyquickly analyzing large datasets, determining the severity of incidents, and initiating predefined actions to contain threats.
7. Insider Threats:
- Challenge:Detectingmaliciousactivitiesfromauthorized usersoremployeeswithprivilegedaccesscanbecomplex.
- AI Solution: Behavioral analytics powered by AI can identifyanomalousbehavior,helpingtodistinguishbetween normaluseractionsandpotentialinsiderthreats.
8. Data Encryption and Privacy:
- Challenge: Ensuring secure data transmission and storage can be complex, especially with the increasing volumeofdata.
- AI Solution: AI contributes to enhancing encryption methods and ensuring data privacy by automating encryptionprocessesandmonitoringdataaccesscontrols.
9. Network Security:
- Challenge: Traditionalnetworksecuritymeasuresmay struggletokeeppacewithrapidlyevolvingnetworkthreats.
- AI Solution: AI-drivenintrusiondetectionsystemscan analyze network traffic in real-time, identifying patterns associatedwith maliciousactivitiesandenhancingoverall networksecurity.
10. Threat Intelligence Analysis:
- Challenge: Analyzing and correlating vast amounts of threatintelligencedatamanuallyistime-consuming.
- AI Solution: AI systems can automate the analysis of threat intelligence feeds, helping security teams quickly assesstherelevanceandseverityofpotentialthreats.
WhileAIpresentsvaluablesolutionstothesechallenges,it's importanttonotethatAIitselfisnotimmunetocertainrisks and adversarial attacks. A holistic approach combining AI withothersecuritymeasures,regularupdates,andhuman expertiseiscrucialforarobustdatasecuritystrategy.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
As wedelve into 2024 the future of AI in data security is exciting and filled with possibilities. Several trends and developmentsaresettoshapethislandscape.
1.Quantum Computing and Post-Quantum Cryptography
The emergenceofquantum computingbringsfortha new spectrumofintricacieswithinthedomainofdatasecurity, posingathreattomanyconventionalencryptionmethods. Nevertheless,artificialintelligencestandspoisedtoassumea crucial role in post-quantum cryptography, charting the courseforinnovativeencryptiontechniquesresilientagainst quantumthreats.
2.Deep Learning and Threat Hunting
Deeplearning,aspecializedbranchofartificialintelligence, isexperiencingagrowingapplicationintherealmofthreat hunting. By delving into extensive datasets, scrutinizing network traffic, and parsing system logs, it excels in unveiling concealed threats that may elude detection by conventional security tools. This underscores its effectiveness in enhancing cybersecurity measures by uncoveringlatentrisksandfortifyingdefenses.
3.AI in IoT Security
TherapidexpansionofIoTdevicesintroducesnovelsecurity challenges.ArtificialIntelligenceispoisedtoplayapivotal roleinfortifyingthesecurityofthesedevicesandvigilantly overseeing their activities to detect any indications of compromise.ThisunderscorestheindispensableroleofAI in safeguarding the integrity and resilience of IoT ecosystems.
4.AI in Edge Computing
Edgecomputing,characterizedbythelocalizedprocessing ofdatanearitsorigin,demandsrobustsecurityprotocols. ArtificialIntelligenceissettoplayapivotalroleinfortifying the security of edge devices and ensuring the integrity of datatransmissioninthisdecentralizedcomputingparadigm.
5.Privacy-Preserving AI
Emerging AI methodologies that prioritize user privacy while facilitating robust data analysis are increasingly gainingtraction.Privacy-preservingAItechniquesempower organizationstoconductanalyticswithoutjeopardizingthe confidentiality of sensitive data, presenting an optimal solution for adhering to regulatory compliance requirements. This innovative approach ensures the safeguarding of privacy while still enabling meaningful insightsthroughdataanalysis.
6. Predictive Analytics:
AIcanleveragepredictiveanalyticstoanticipatepotential securitythreatsbasedonhistoricaldataandcurrenttrends
ArtificialIntelligencestandsattheforefrontoftheongoing battle to safeguard data security. Its prowess in threat detection, automated response, and predictive insights is reshapinghoworganizationsprotecttheirdata.Thefuture holds great promise, with trends like post-quantum cryptography,privacy-preservingAI,andAIintegrationin IoT security poised to redefine the security landscape. Despite these advancements, challenges persist, ranging from biases in AI algorithms to the legal and ethical frameworksgoverningtheirdeployment.
Humanexpertiseandcollaborationremainindispensablein ensuring the responsible and effective use of AI in data security. As technology advances, maintaining a delicate equilibriumbetweenharnessingthepowerofAIforsecurity andupholdingfundamentalprinciplesofprivacyandethical useisparamount.Navigatingtheintricateandever-evolving landscape of data security in 2024 and beyond requires a thoughtfulapproachtostrikethiscrucialbalance.
[1] Denning DE, Denning PJ (1979) Data security. ACM ComputSurv(CSUR)11(3):227–249
[2] Bertino, E.: Data Protection from Insider Threats: SynthesisLecturesonDataManagement. Morgan&ClaypoolPublishers,SanRafael(2012)
[3] Bertino, E., Ghinita, G., Kamra, A.: Access control for databases:conceptsandsystems. TrendsDatabases3(1–2),1–148(2011)
[4] Bertino, E., Takahashi, K.: Identity Management: Concepts,Technologies,andSystems. ArtechHouse,Boston(2010)
[5] GoldaDilip,RamakrishnaGuttula,SivaramRajeyyagari, HemalathaS,RadhaRamanPandey,AshimBora,Pravin R Kshirsagar, Khanapurkar M M, Venkatesa Prabhu Sundramurthy, "Artificial Intelligence-Based Smart ComradeRobotforEldersHealthcarewithStraitRescue System",JournalofHealthcareEngineering,vol.2022, Article ID 9904870, 12 pages, 2022. https://doi.org/10.1155/2022/9904870.
[6] KshirsgarP.,MoreV.,HendreV.,ChippalkattiP.,Paliwal K.(2020)IOTBasedBabyIncubatorforClinic.In: KumarA.,MozarS.(eds)ICCCE2019.LectureNotesin ElectricalEngineering,vol570.Springer,Singapore. https://doi.org/10.1007/978-981-13-8715-9_42.
[7] G. Dilip, R. Guttula, S. Rajeyyagari et al., “Artificial intelligence-based smart comrade robot for elders healthcare with strait rescue system,” Journal of

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
HealthcareEngineering,vol.2022,ArticleID9904870, 12pages,2022.
[8] Prabhu Kavin, Sagar Karki, S. Hemalatha, Deepmala Singh,R.Vijayalakshmi,M.Thangamani,SulaimaLebbe Abdul Haleem, Deepa Jose, Vineet Tirth, Pravin R. Kshirsagar, Amsalu Gosu Adigo, "Machine LearningBased Secure Data Acquisition for Fake Accounts DetectioninFutureMobileCommunicationNetworks", WirelessCommunicationsandMobileComputing,vol. 2022, Article ID 6356152, 10 pages, 2022 https://doi.org/10.1155/2022/6356152
[9] MAbulHasan*,KRaghuveer,PSPandey,AshokKumar, Ashim Bora, Deepa Jose, P R Kshirsagar*, Bui Thanh Hung,PrasunChakrabarti,MMKhanapurkar,“Internet ofThingsanditsapplicationsinIndustry4.0forSmart Waste Management”, Journal of Environmental ProtectionandEcology,22(6):2368-2378,2021
© 2024, IRJET | Impact Factor value: 8.226 | ISO 9001:2008
|