
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
Ibrahim Alahmad 1 , Mouhamad Ayman Naal 2 , Mahmoud Shaar 3
1First Graduate student (PhD), Department of Computer Engineering, College of Electrical Engineering And electronic, Aleppo University, Syria
2Professor in the Department of Computer Engineering, Faculty of Electrical and Electronic Engineering, University of Aleppo, Syria
3Lecturer in the Department of Computer Engineering, Faculty of Electrical and Electronic Engineering, University of Aleppo, Syria ***
Abstract - Millions of users routinely use Google or Facebook to log in to websites that support the OpenID Connect single sign-on protocol. So the security of this protocol is therefore of critical importance. As revealed in previous studies, systems using OpenID Connect are vulnerable to attack as the users of these systems are typically unaware of these issues and are therefore at risk of attacks that may lead to unauthorized access to user accounts.
In this paper, a large-scale practical study of the Single SignOn Protocol "OpenID Connect" was carried out by analyzing the stages of the protocol's work. A group of attacks that were developed in order to penetrate the protocol were also defined, and the session attack was applied to the protocol, and then a new method was proposed to prevent the session attack in the first stage of the protocol by making two-factor authentication method by using the One Time Password to protect session tokens.
Key Words: Single Sign-On, One Time Password, One Time Pad, OpenID Connect, identity provider
1.INTRODUCTION
Singlesign-onisamethodofaccesscontrolthatrequiresthe user to log in once and allows him to access multiple resourcesandservicesaftersuccessfullylogginginwithout requiringhimtologinagain.Thus,theSSOapproachallows userstoauthenticateonlyonceandthenenjoyeasyaccessto other applications securely [1]. The OpenID Connect protocolisthelatestversionofsinglesign-onprotocols.This protocol wasreleasedin2014andhasbeensupportedby manylargecompanies[2]
Thisresearchaimstoprovideacomprehensiveanddetailed analytical study of the OpenID Connect single sign-on protocolandthestagesofitsworkindetail,inadditionto studyingthemaliciousattacksthathavebeendevelopedin order to uncover security vulnerabilities in this protocol. Sessionattackswillalsobeappliedtotheprotocolandthe results of the attack will be observed. The research has
presented a method to protect the protocol. From session attackbyusingOTPwheredone
TheOpenIDConnectprotocolwasbuiltbasedonOAuthto enableuserauthentication.Italsoincludesanewfeaturein it,whichisthestageofdynamicregistration,discovery,and automatictrustachievementbetweentheserviceprovider (RP) and the identity provider (Idp), through which the service provider can automatically discover the identity provider(IDP)responsibleforGivingidentity.Thefollowing figure(1)showsthegeneralworkingprincipleofOIDC[3].
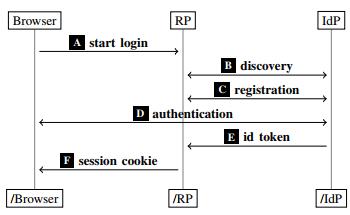
Where the user begins by requesting the service from the serviceprovider(RP)(A),thentheserviceproviderretrieves (obtains) some information (URLs), and this is called the discovery phase (B). Then he registers with the identity provider(IDP)(C),andthentheusergoesFortheidentity providertoauthenticateitself(D),afterwhichtheidentity providerissuesanId_tokentotheserviceprovider,which verifiesittoprovidetheservicetotheuser(E).
TheOpenIDConnectprotocolallowsuserstoauthenticateto service providers using existing accounts at the identity provider.OIDCwasdesignedbasedontheOAuthprotocolto enableuserauthentication.Italsoincludesanewfeaturein it,whichisthestageofdynamicregistration,discovery,and

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
automatictrustestablishmentbetweentheserviceprovider (SP)andtheidentityprovider(Idp)[4].
TherearethreedifferentpartieswithintheOIDCprotocol. TherelationshipbetweenthesepartiesisshowninFigure (2).
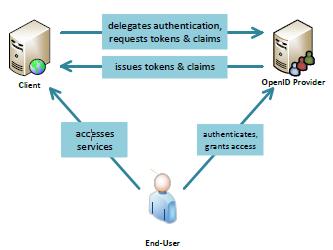
Figure(2)Therelationshipbetweenthethreepartiesin theOIDCProtocol
Eachofthesepartiesassumesadifferentroleasfollows:
1. End-User: wants to access the services of the client (serviceprovider)andthereforeneedstoprovehisidentity totheclient.Italsohasthepossibilitytoauthorizetheclient toaccessaspecificsetofitsresourcesstoredintheidentity provider(OP).
2.Client:Anapplicationthatprovidescertainservicesthat requireauthenticationtotheend user.Theauthentication processisdelegatedtotheidentityprovider(OP).
3.OpenIDProvider:Handlestheauthenticationoftheend user and issues an authentication token that contains a specific setofclaimsthatprovetheenduser'sidentity. In addition, it can issue a license code in order to allow the clienttoaccessend-userresources.
ThestagesoftheprotocolareillustratedinFigure(3)[3]. Initially, the user begins the login process by entering the emailaddress,whichhesendstotheRPserviceproviderin step 1. After that, the service provider uses the discovery service to collect information from the identity provider (IDP), where the service provider uses the WebFinger mechanism to discover information from the identity provider.Forthisdiscoverytheserviceprovidercontactsthe serverasdescribedinstep2whichrespondsbysendingthe addressoftheidentityproviderinstep3
Thediscoveryprocesscontinuesbytheserviceproviderby sending a request to obtain the settings in step 4, and the server responds in step 5 by obtaining all the information fromtheendpointaddressesthatwillbeusedinthestagesof theprotocol.Italsorequestsandobtainstheaddressofthe
publickeyusedinencryption,asshowninsteps6and7.Here thediscoveryphaseendsandtheregistrationphasebeginsin steps 8 and 9, where a registration request is sent to the registrationendpointaddress,andtheresponseiscompleted bysendingsecretcodes(client_id,client_secret).Itisprivate betweentheserviceproviderandtheidentityprovider.Here thefirststageoftheprotocol’sworkendsandthenthebasic partoftheprotocolbegins:Theserviceproviderredirectsthe user's browser to the server in step 10. The redirection processcontainsinformationabouttheauthorizationcode, the identifier (client_id) of the service provider, and the status value. Then this data is sent by the browser to the identityproviderinstep11.Theauthenticationprocesstakes placebetweenUserandserverinsteps12and13.Thenitis directedtotheserviceproviderinsteps14and15,wherethe statusvalueandtheauthorizationcodearematchedbythe serviceprovider.Iftheyarecorrect,itcontactstheidentity providerinstep16attheendpointofthecodesandsends him the authorization code and secret codes (client_id, client_secret). If they are If correct, the identity provider respondsandsendsthe tokens (access_token, id_token)in step 17 to the service provider, which verifies them and authenticatestheuser’sloginprocess.
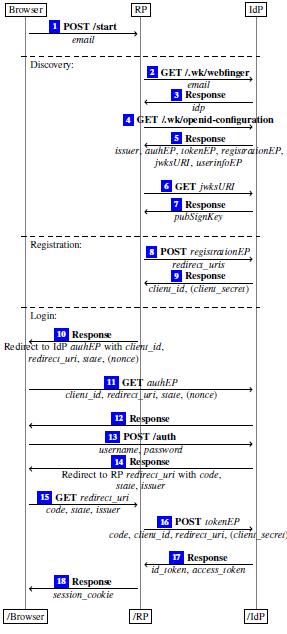
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072 © 2024, IRJET | Impact Factor value: 8.226 | ISO 9001:2008

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Anidtokenisasecrettokenthatcontainsclaimsaboutthe end user's identity and its JSON Web Token (JWT) data structure.Figure(4)showsanexampleofanidtoken[4][5]
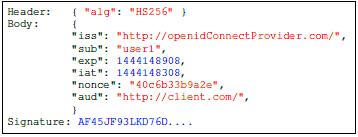
Figure(4)isanexampleofanidtoken
Wenotethattheidtokenconsistsofthreeparts:
First:Theheader:containsinformationincludingthe encryptionalgorithmused.
Second:Thebody:Itcontainstheinformationneededto authenticatetheenduserandincludes:
•Enduseridentity:Itconsistsoftwoparts:
oIssuer(iss):Tofindouttheidentityprovider.
oSubject(sub):Toknowtheuser’sidentity.
Bothareusedtoidentifytheenduser.
• The timestamp(iat) and expired(exp) define the time periodwhenthecodewasproducedandexpired.
• Nonce: A random string sent by the client during the authenticationrequestusedtomitigateattacks.
•Audience(aud):Todeterminewhichcustomerstheidentity codebelongsto.
Third:Signature:Itprovidesareliableidtoken.
Many previous studies have focused on single sign-on protocols by developing techniques to test, analyze, and identifysecurityvulnerabilitiesinthem.Belowwereviewthe mostimportantofthesestudies.
Theresearchersconductedananalysisofthesinglesign-on protocolagainstimpersonationattacks,whereatechnology was developed based on opening a secure communication channel between the service provider and the identity provider,whichreliesonredirectingtheusertotheidentity provider to prevent the attacker from impersonating the identity of the client from whom the user is requesting a service. The performance was tested and evaluated. The protocol showed a time delay of 650 milliseconds and additional costs in the hard entity, but it provided strong
protection and confidentiality in a clear and acceptable manner[6].
A confidential and in-depth analysis of the OpenID Connect single sign-on protocol was conducted and a developed model of OpenID Connect was built, where the secret properties of the protocol were employed to avoid previouslydiscoveredattacksandnewattacks[3].
The security properties of the GoogleOIDC protocol were studiedandexaminedonagroupofclients.Atypeofattack wasappliedthroughwhichusercodescouldbeobtainedand thenusedtoimpersonatetheusertoreachclients.Theyalso presented a set of future advice that should be taken into accountinfuturesystemsforbothproviders.Service''RPand IdentityProviderop[7].
Byconductinganin-depthanalysisofthenewfeatureinthe OIDC protocol, which is the dynamic registration and discoveryphase,anddefininggeneralattackconceptsonthe OIDCSingleSign-OnProtocol,theypresentedanewtypeof attack (Malicious Endpoints) that belongs to the class of second-degree attacks, where the attack consists of two stages. This attack exploits the information exchanged between parties to the protocol between the three stages. Theywereabletobreaktheuser'sprivacyandexplainthe defectsofthenewfeatures,andthereforethesecurityofthe protocol cannot be guaranteed in its current form, as the attackerintheseattacks(MaliciousEndpointsAttacks)seeks to steal documents between the client (Client) and the identity provider (OP) and also seeks to steal the authorizationcode(token_access)thatAllowsaccesstouser resources[4].
By providing a tool for testing attacks on the OIDC protocol and testing sophisticated attacks (malicious endpointattacks)inwhichtheidentityproviderisdiscovered inthediscoveryphase,thishelpedinbetterunderstanding theflowofmessageswithintheprotocol[8].
Theresearchersalsoanalyzedtheknownattacksonthe OIDC protocol and classified these attacks into two basic categories:
Single-stageattacks:Theseareattacksthatareappliedto oneofthestagesoftheprotocol.
Two-stageattacks:Theseare attacksthat relyon more thanonestageoftheprotocolduringtheattack.
The researchers have presented a tool to improve the confidentiality of the protocol and identify security vulnerabilitieswithinit.
Building the OIDC protocol from several layers allows attackerstointervenebetweenanytwoofthethreestages, which allows for a deeper study of these stages and the possibilityofhackingthem[9].
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072 © 2024, IRJET | Impact Factor value: 8.226 | ISO 9001:2008

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
By secretly analyzing a group of attacks such as impersonationattacks,phishingattacks,andreplayattacks on the OAuth protocol, they found that there are vulnerabilities during user authentication. A method is proposed to securely authenticate a user by verifying the authorization code using an email authentication server through access token distribution. Although the attacker obtains some user information, he cannot use it for authentication[10].
Researchershaveidentifiedthecausesofthecross-site forgeryprobleminOAuth2.0andOIDCandproposedanew approachofmitigationsthatcanbeappliedbycombiningthe referrer header with the different identity provider URLs used by the service provider in order to prevent CSRF redirectionattacks[11].
ResearchershaveproposedawaytoprotectOIDCURLsfrom session hijacking attacks by adding additional innovative parametersduringthesessionsuchasaspecialalphanumeric string(SAS)andaprivatesecurityPIN(SSP).
The results show that adding the above parameters reduces the risk of session hijacking in an OIDC communicationenvironment[12]
ByconductingthefirstformalanalysisoftheOpenBanking ApplicationProgrammingInterface(FAPI)basedontheweb infrastructuremodel,acomprehensivemodelfilewasbuilt that includes all participants in the protocol. The security properties were identified, namely authentication, authorization, and session integrity. While trying to prove these properties, they found many security vulnerabilities that enable the attacker to Access protected resources or perform session integrity attacks. Methods have been proposed to mitigate these attacks and thus prove the securityoftheOpenIDFAPI[13].
OAuthGuardisascannerandprotectorthatworkswith ISPsusingOIDC.Thetoolwasusedtoscanagroupofsitesin searchofpossiblesecurityvulnerabilities.Amongthesesites that had security vulnerabilities, the OAuthGuardtool was able to protect the user's security and privacy for some of them and warn the user that he was using an unsafe applicationonothersites[14].
AdynamicidentitymanagementmodelbasedontheOIDC protocol has been proposed. The model consists of three steps: discovering the service provider that indicates the location of the partner organization, registering the authorized party with the OIDC, which allows the organization and its partners to negotiate information to create the federation, and creating a trust federation dynamically. This model allows providing services to hundreds of users from different organizations and thus saving time through dynamic federation during operation[15].
TheattacksdevelopedontheOpenIDConnectsinglesign-on protocol, which exploit the mechanism of the protocol throughseveralstages,areamongtheattacksthattakeplace throughseveralstages,astheyexploitthepresenceofthe newstageintheprotocol,whichisthedynamicregistration anddiscoverystage.
Mostwebapplicationsneedtosavesomeobjectsbetween different requests. This way the web application saves certain data over subsequent accesses. The end user accessingthewebapplicationisassignedauniquesession identifier,whichistypicallystoredinacookie.
Inthissectionwewilldescribeanewattackthatresultsin authenticationfailureontheenduser.Theideaoftheattack is to overwrite the elements stored in the session, which leadstosecurityissues.
Thebasicsetupfortheattackisasfollows:
1. The end user (victim) has an active account on the real client.Weassumethattheusertruststhisclientandthatthe clientfollowstherulesoftheOpenIDConnectprotocol.
2. The end user is registered with the identity provider Honest OP on the domain http://honestop.com. The user trusts this provider, which also follows the rules of the OpenIDConnectprotocol.
3.Tocarryouttheattack,theattackermustsetuphisown discovery service that runs on the domain http://Malisious.com.Theactionsofthisdiscoveryservice donotdeviatefromthenormalprotocolflow.
4.Accordingtotheattackmodel,theattackerdoesnothave any control over the client, the end user, the service provider,orthetrafficbetweenthesethree elements.The attacker is able to send an HTTP request through the end user'sbrowser,forexamplebyembeddinganimagewithin thewebsitethatcausesthebrowsertoissueanautomated requestwhenthewebsiteisdisplayed.
Theattackdescription:
We will describe the stages of the protocol attack flow as showninFigure(5)[16].
Service provider data (Metadata Honest) is stored in the session.Theattacker'sintentioninthefirststageistoforce thecustomertousetheunderlyingserviceproviderHonest OP.Forthispurposeitcreatesamaliciouslinkandstoresit onthewebsite.
By visiting the website containing this malicious link an HTTP request will be sent to the client through the end user's browser. As a result, the customer begins the discovery phase with the discovery service

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
http://honestop.com.Theclientsendsarequest,determines the endpoint addresses, and stores them in the current session.Theenduserauthenticationprocesstakesplacein the next stage where the client redirects the user to the token endpoint to authenticate himself and authorize the client.Thesecondphasefollowstheregularprotocol flow where there is no routing to malicious sites or network monitoringbetweenthethreeparties.
The attacker's intent is to overwrite data stored in the session to force the client to use the attacker's malicious detectionservice.Forthispurpose,itsendsasecondrequest to the client containing the identity alice@malicious.com. The attacker forces the user's browser to send two HTTP requests. As a result, the client detects the malicious detection service, identifies endpoints, and replaces old session data with new data (Metadata EvilOP). The client thenreceivesthecodefromthepreviousstageandsendsit withitscredentials(client_id,client_secret)totheendpoint ofthecodesstoredintheattacker'ssessiondata.Asaresult, theattackerreceivesaccesstokensandisabletoaccessthe lockedresourcesintheOPidentityprovider.
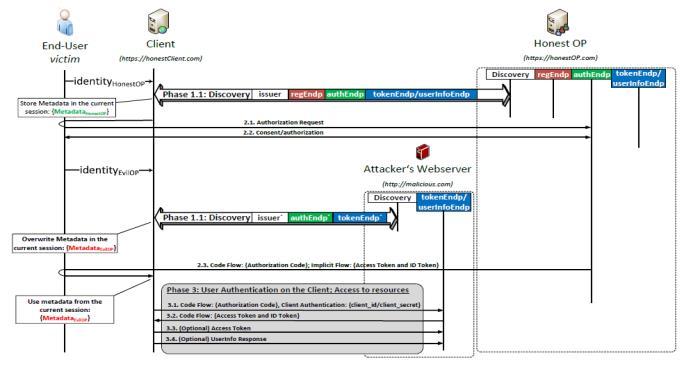
(5)Stagesofasessionattack
7.APPLYING THE SESSION ATTACK
Attackassumptions:
1.Usercredentialsaremanagedinoneplace.
2.Usercredentialsarestoredintheidentityprovider.
3.Theattackerisredirectedtotheurlswithoutanyaction fromtheuserandthisiscalledopenredirection.
Theattackwasimplementedonthelocalhostwebsiteusing theAsp.netcoreframework.
SQLServerdatabasewasused.
A website was created that includes a login using OpenID Connect.
Figure(6)showstheuseraccountsregisteredontheserver:
Figure(6)Useraccountsontheserver
Hash encryption technology protects passwords on the server,andtheuser'spagesarenavigatedaftersuccessful login using explicit e-mail. This is the method used in the protocol in general, where e-mail is the only explicit and secureinformationinthedatabasequeryprocessafterthe transition.Totheuser'spersonalpage.
First,theprotocoltokensobtainedthroughamix-upattack areusedtoobtaininformationrelatedtotheuser,suchas histokenID,whichisshowninFigure(7).
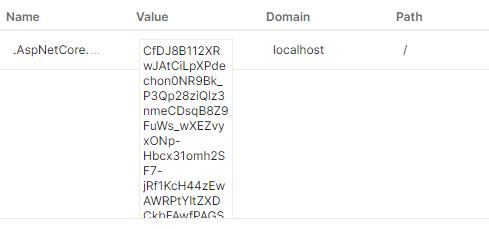
Figure(7)idtokenvaluesafterapplyingtheattack
The url is then obtained from the tokens and the token stored in the value generated by the attack application is usedtoformtheuser'saccesstoken.
Thenarequestismadetocreateasessionfromthe“service provider”server.
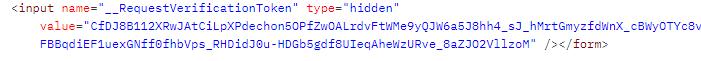
TheAccesstokenisusedtoaccessuserdataafterforming thefullURLfortheprotocol
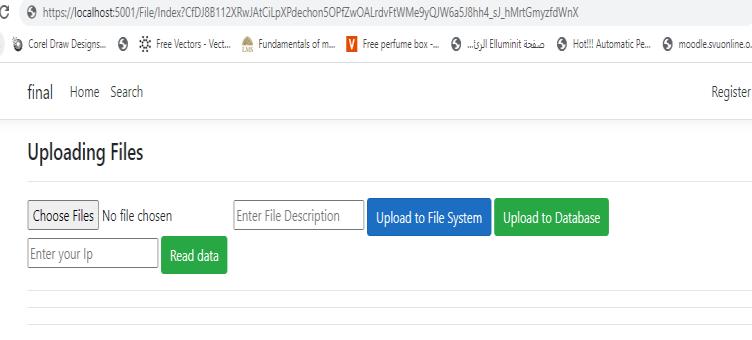
Hereuserdatawasaccessedwithoutloggingin.
Theresultsoftheattackanditsimpactontheprotocolare limitedtoobtainingtheuser’saccesstokenthattheattacker

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
willuseinordertoaccesstheprotocol,ashewillpassthe protocol’s protection and access the user’s data, which means losing the user’s data and account, and this means achieving large losses for users when working with the protocol,andthisiswhatmakesusneedtouseTechniques thatpreventtheattackerfromforminganaccesstokenURL sothatthesessionisprotectedbyaddingcodesthatchange foreachsessionandareuniformbetweenthepartiestothe protocol.
This section presents and discusses the proposed OpenID Connect Architecture. The proposed approach has three components:DIFFIE-HELLMANKEYEXCHANGE,ONETIME PASSWORD,ONETIMEPAD.Thesecomponentsarefurther elaborated.
Diffie-Hellman key exchange is a method of securely exchanging cryptographic keys over a public channel that allows two parties to create a shared secret key over an unsecuredcommunicationchannelandthenusethiskeyto encryptsubsequentcommunicationsusingasymmetrickey.
Diffie-Hellmankeyexchangeworksbyallowingtwoparties (Alice,Bob)toagreeonasharedsecretkeyoveraninsecure channelwithoutanyotherpartybeingabletointerceptthe keyorlearnanythingaboutit.Keysareexchangedaccording tothefollowingstepsshowninFigure(8)[17].
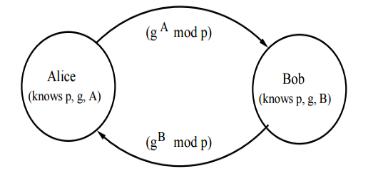
Figure(8)StepsforkeyexchangeinDiffie-Hellman
AliceandBobagreeontwolargeprimenumberspandgand analgorithmforpublickeyswapping.
AlicechoosesasecretintegeraandthensendsBobthe A=g^amodp
BobchoosesasecretintegerbandthensendstoAlice B=g^bmodp
Alicecalculatess=B^amodpandBobcalculatess=A^bmodp
AliceandBobthenhavesharedsecretkeysthatcanbeused tocreateasecurecommunicationchannel.
ThesecurityofDiffie-Hellmankeyexchangeisbasedonthe fact that it is computationally infeasible for an attacker to determinethesharedsecretkeysfromthepublicvaluesofp, g, A, and B. This allows Alice, Bob to exchange the key securely,evenoveraninsecurechannel.
A one-time password is an automatically generated, onetimestringofnumbersandlettersthatauthenticatesauser forasingletransactionorloginsession.
Aone-timepasswordismoresecurethanastaticpassword, especiallyauser-generatedpasswordthatcanbeweak or reusedacrossmultipleaccounts.Aone-timepasswordmay replacelogininformationforauthentication,plusitcanbe used as an additional layer of security for an account. Or similaronlineentityafterthepassword.Ifthepasswordis exposed,itcannotbereusedandthenextloginbytheuser will require a completely different authentication code becauseitchangeswitheachlogin.One-timepasswordhas severalforms[18]:
1-TimeSynchronization:Dependingonthetimecomparison betweenthedynamictokenandthedynamicpassword,the time synchronization token usually generates a new password every 60 seconds, which meets the strict requirementsforauthentication.
2- Event Synchronization: The server and token use the specified sequence of events and the same initial value to calculatethepasswordusingtheHASHalgorithm.
3- Challenge/Respond: The server generates a challenge number (chg) and sends it to the token, which both calculates the password using the challenge number and somepre-arrangedparameters.
OTPisanunbreakableencryptionsystemifusedcorrectly.A randomlygeneratedprivatekeyorpadisusedonlyonceto encryptamessageofthesamelengthastheciphertextwhich isthendecryptedbythereceiverusingamatchingone-time pad and key. Each bit or character of the plaintext (unencrypted) is encrypted by a combination of standard arithmeticwithabitorcharacterofasecretrandomkey(or pad) of the same length as the plaintext, to produce the ciphertext. Messages encrypted with random-based keys havetheadvantagethatthereisnowayintheorytobreak thecode by analyzinga stringofmessages. Eachcipher is unique and unrelated to the next, making it impossible to detectapattern[19].

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
Thesingle-paneencryptionschemeissimpleyetpowerful with absolute security unmatched by modern encryption algorithms.Thereareasetofrulesthatmustbefollowedso thattheone-timepadencryptioncannotbebroken,which are:
•Thekeymustbeaslongastheencrypteddataormessage.
•Thekeyisgeneratedrandomly.
• Each key is used only once and the sender and receiver mustdestroytheirkeysafteruse.
• There should be only two copies of the key: one for the senderandoneforthereceiver.
9.Improving authentication technology in OIDC:
Figure (9) shows a sample flow of the authentication protocolproposedinOpenIDConnect:
BytheRPserviceprovider:
•RPprovidesOPwiththeemailexplicitlybecauseitisnot confidentialdata.
•Encrypteddata,includingthehashpasswordandone-time passwordcodes,isexchangedbetweenthetwoparties.
•OPandRPcontaintwoidenticalcopiesoftheOneTimePad algorithm, and data is not exchanged between them, but emailisusedastheencryptionkey.
FromtheOPidentityprovider:
•ReceivesemailfromRPandencrypteddatafromonetime password.
•ProvidestheRPwithaccesstoresources.
The proposed method added new symbols to the session thatpreventedtheattackerfromformingtheaccessurl.On theotherhand,thenewmethodcausedatimedelayinthe operationoftheprotocolduetothetimeaddedtoformand authenticatethesymbols.Figure(10)showstheresultsof the time delay that occurred after adding the proposed methodonthefirsttwosites.Itisaready-madeMVCmodel provided by Microsoft and runs on its ASP.NET Core platform.Thesecondisafilemanagementsystemthatwe createdusingthesameplatform.
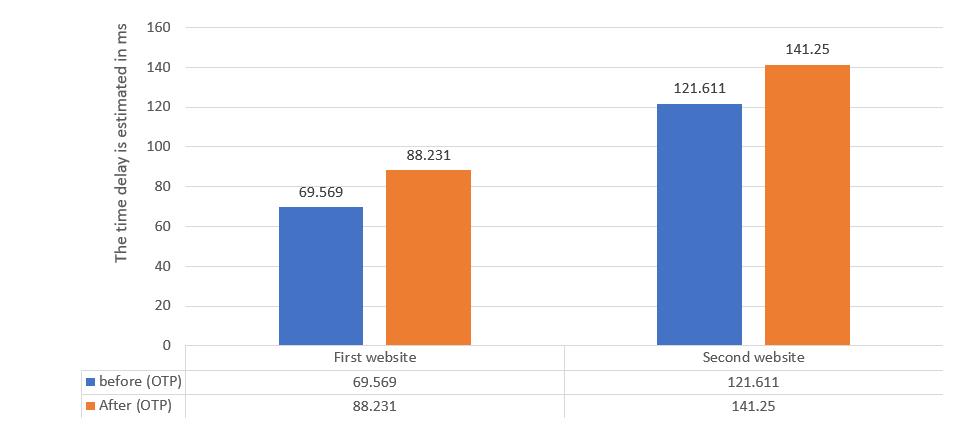
Figure(10)Timedelayresultsbeforeandafterapplying theOTPtechnique
Theproposedmethodfortheauthenticationprocessenables the user to protect the user’s access token from session attacks by generating a new access token every time a sessioniscreated.
Usingtheproposedmethodtoimprovetheperformanceof theprotocol,makethevalueofthesessionexpirationperiod meaningless,whichisconsideredoneofthecodesextracted frommaliciouspointattacksandwhichtheattackerusesto knowthevalidityofthesessioninordertoaccesstheaccess token.
Theproposedmethodincreasesthetimecomplexityofthe protocol due to the addition of time to the one time pad algorithm,whichcreatesanewaccesstokenfortheuserin eachsession.
Figure(9)Theflowoftheproposedauthentication protocolinOpenIDConnect
Theresultingtimedelayhasanalmostnegligibleimpacton the added protection value. The reason is due to the simplicity of the one time pad algorithm from a mathematical standpoint, in addition to the fact that the protocolisintendedtoworkonserverswithhighhardware.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 03 | Mar 2024 www.irjet.net p-ISSN: 2395-0072
The research presented a new method to prevent session attacks by adding codes that prevent the attacker from creatingan accesstokenURL for the victim by generating permanentlyvariableandencryptedcodesforeachsession. Theproposedmethodincreasedtheprotectionofthesites, but it caused a time delay. We will work during the next stagetoreducethedelay.Timedelaybyformingadditional symbolsthatarederivedfromthecurrentsessionandthe previoussession,whichmeansreducingthetimedelay.
[1]S,Suoranta,K,Manzoor,A,Tontti,J,RuuskanenandT,Aura, "Logoutinsinglesign-onsystems:ProblemsandSolutions", journalofinformationsecurityandapplications,2014,pp. 61–77.
[2]N.NaikandP.Jenkins ,"AnAnalysisofOpenStandard IdentityProtocolsinCloudComputingSecurityParadigm", IEEE14thIntlConfonDependable,AutonomicandSecure Computing, 14th Intl Conf on Pervasive Intelligence and Computing, 2nd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress, 2016,pp.428–431.
[3]Fett,D,Küsters,RandSchmitz,G,"TheWebSSOStandard OpenIDConnect: In-DepthFormal Security Analysis and Security Guidelines", IEEE 30th Computer Security FoundationsSymposium(CSF),2017,pp.189-202.
[4]Mainka,C,Mladenov,VandSchwenk,J."Onthesecurityof modern Single Sign-On Protocols – Second-Order VulnerabilitiesinOpenIDConnect",2016
[5] Fett,D, Küsters,R and Schmitz,G, "A Comprehensive FormalSecurityAnalysisofOAuth2.0",InProceedingsofthe 2016 ACM SIGSAC Conference on Computer and CommunicationsSecurity,2016,pp.1204–1215.
[6] Yinzhi Cao, Yan Shoshitaishvili and Kevin Borgolte, "Protecting Web-based Single Sign-on ProtocolsagainstRelyingPartyImpersonationAttacksthrough a DedicatedBi-directionalAuthenticated Secure Channel" , ResearchinAttacks,IntrusionsandDefenses,2015,pp276–298.
[7]]Li,WandMitchell,C."AnalysingtheSecurityofGoogle’si mplementationofOpenIDConnect",InternationalConference onDetectionofIntrusionsandMalware,andVulnerability Assessmen,2016,pp.357–376.
[8]Mainka,C,Mladenov,VandSchwenk,J."Donottrustme: UsingmaliciousIdPsforanalyzingandattackingSingleSignOn", IEEE European Symposium on Security and Privacy (EuroS&P),2016, pp.321-336 .
[9] Mainka,C, Mladenov,V, Schwenk,J and Wich,T, " SoK: SingleSign-OnSecurity–AnEvaluationofOpenIDConnect", IEEE European Symposium on Security and Privacy (EuroS&P),2017,pp.251-266.
[10] C,Chae, K,Kim and H,Cho , "A study on secure user authentication and authorization in OAuth Protocol", Springer Cluster Computing volume 22, 2017, pp. 1991–1999.
[11]W.Li,C.J.Mitchell,andT.Chen,"MitigatingCSRFattacks on OAuth 2.0 and OpenID Connect", http://arxiv.org/abs/1801.07983.
[12] M,Bilal, M,Asif and A,Bashir, "Assessment of Secure OpenID-BasedDAAAProtocolforAvoidingSessionHijacking in Web Applications", Security and Communication Networks Volume 2018, Article ID 6315039, 10 pages, https://doi.org/10.1155/2018/6315039.
[13] D. Fett, P. Hosseyni, and R. Kusters , "An Extensive FormalSecurityAnalysisoftheOpenIDFinancial-gradeAPI", IEEE Symposium on Security and Privacy (SP), 2019, pp. 1054–1072.
[14] W. Li, C.J. Mitchell, and T. Chen, "OAuthGuard: Protecting User Security and Privacy with OAuth 2.0 and OpenIDConnect",2019,https://www.researchgate.net/public ation/330672797.
[15]A,Alsadeh,N,Yatim,Y,Hassouneh,"ADynamicFederated Identity Management Using OpenID Connect", Future Internet2022,14,339.https://doi.org/10.3390/fi14110339.
[16]Mladenov,VandMainka,C,"OpenIDConnectSecurity Considerations",https://www.nds.ruhr-unibochum.de/media/ei/veroeffentlichungen/2017/01/13/OI DCSecurity_1.pdf,asofSeptember30,2020.
[17] Nan Li, "Research on Diffie-Hellman Key Exchange Protocol",InformationEngineeringTeachingandresearch section,2010.
[18] M, Abousteif, A,F,Tammam and A,Wahdan," A Novel ApproachForGeneratingOne-TimePasswordWithSecure Distribution",FourthWorldConferenceonSmartTrendsin Systems,SecurityandSustainability(WorldS4),2020
[19]E,M,Manucom,B,GeradoandR,Medina,"AnalysisofKey Randomness in Improved One-Time Pad Cryptography", IEEE13thInternationalConferenceonAnti-counterfeiting, Security,andIdentification(ASID),2019