
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 02 | Feb 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 02 | Feb 2024 www.irjet.net p-ISSN: 2395-0072
Sagar Rajebhosale1 , Rajeshwari Dandage2 , Shravan Jadhav3, Anushka Jawalkar4, Adnan Mulla5 , Anjali Yadav6
1Professor, Dept of Computer Engineering, Keystone School of Engineering, Maharashtra, India
2Professor, Dept of Computer Engineering, Keystone School of Engineering, Maharashtra, India
3BE student, Dept of Computer Engineering, Keystone School of Engineering, Maharashtra, India
4BE student, Dept of Computer Engineering, Keystone School of Engineering, Maharashtra, India
5BE student, Dept of Computer Engineering, Keystone School of Engineering, Maharashtra, India
6BE student, Dept of Computer Engineering, Keystone School of Engineering, Maharashtra, India ***
Abstract - In response to heightened security concerns, safeguarding sensitive locations is now a top priority. This project introduces an advanced surveillance system utilizing cutting edge technologies like AI, IoT, CC, and ML to ensure comprehensive situational awareness and bolster security measures. By deploying a network of IoT devices equipped with high resolution cameras and sensors, the system continuously gathers data. Leveraging Cloud Computing, this data undergoes efficient processing and secure storage, enabling scalability and real-time analysis. At its core, AI and ML algorithms are meticulously trained to detect anomalies, identify suspicious activities, and recognize potential threats. Through deep learning techniques, the system adapts to changing scenarios, reducing false alarms, and optimizing resource allocationfor amoreeffectiveresponse.Emphasizing privacy, the project implements advanced encryption and compliance measures, ensuring that sensitive data remains confidential and accessible only to authorized personnel
Keyword’s: Real-time Monitoring, Security Infrastructure, Intelligent Security, Threat Detection, Facial Recognition
TheEyeSpyprojectisaconceptthatharnessesthepowerof existingClosed-CircuitTelevision(CCTV)infrastructureto createanintelligentandproactivesurveillancesystem.This solutioninvolvesenhancingtraditionalCCTVsystemswith advanced computer vision, machine learning, and automation capabilities to improve security, situational awareness, and efficiency. The primary objective of this projectistotransformpassiveCCTVsystemsintoproactive andintelligentsurveillancenetworks,capableofidentifying andrespondingtosecuritythreatsandcriticaleventsinrealtime. The Eye Spy projectrepurposes existing CCTV infrastructure, making it a cost-effective and efficient solutionforimprovingsecurityandsituationalawareness. By integrating artificial intelligence and automation, it transforms passive surveillance into an active and
responsivesystemcapableofsafeguardingvarioussectors andimprovingpublicsafety.
ThesystemarchitecturebeginswithalivestreamofCCTV video,capturingthereal-timeactivitiesineachenvironment. This video stream is the input for the system, which then processes the incoming frames to extract valuable information. Thefirststepinthisprocessispre-processing, wheretherawimagesarerefinedandpreparedforfurther analysis.The pre-processed images are then subjected to feature extraction, a crucial step in identifying unique characteristicsthatdistinguishonefacefromanother.Thisis whereFaceNet,afacerecognitionsystem,comesintoplay. FaceNetutilizes advanced technologies like OpenCV, TensorFlow,andConvolutionalNeuralNetworks(CNN)to analyzeandextractdistinctivefeaturesfromeachfaceinthe images.Theextractedfeaturesarethenfedintoaclassifier,a componentresponsiblefordeterminingwhetherthefacein theimageisknownorunknown.ThesystemreliesonaFace Databasetocomparetheextractedfeatureswithpreviously storedinformation,enablingittorecognizefamiliarfaces.
Iftheclassifiersuccessfullyidentifiesaknownperson,the systemgeneratesaneventrecordandstoresrelevantdata. This data includes information about the recognized individual,creatingacomprehensiverecordofevents.The system also allows for the review of past data, providing userswithinsightsintohistoricalpatternsandoccurrences.
Ontheotherhand,iftheclassifierfailstoidentifytheperson, indicatingthatthefaceisunknown,thesystemtakesspecific actions.Itnotifiestheadministratoraboutthepresenceofan unrecognized individual, generating an event record and storingpertinentdataforfuturereference.
Theentirerecognitionsystemoperatesseamlessly,utilizing thecapabilitiesofFaceNet,OpenCV,Tensorflow,andCNNto ensureefficientandaccuratefacerecognition.Thissystem notonlyenhancessecuritybyidentifyingknownindividuals

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 02 | Feb 2024 www.irjet.net p-ISSN: 2395-0072
but also keeps administrators informed about potential securityconcernswhenencounteringunknownfaces.The combination of advanced recognition technologies and a well-structured architecture makes this system a robust solutionforsurveillanceandsecurityapplications.
Therealmofsurveillancetechnologyhasseenremarkable strides, showcased through a rich tapestry of research endeavors.MichaelDavis,StefanPopa,andCristinaSurlea's 2010 exploration delved into fortifying face recognition systemstailoredforsurveillancevideos.Thisstudyplaced emphasis on bolstering resilience against a multitude of environmental variables, offering promising avenues for robustnessenhancement.[1]
Contrastingly,the2020endeavorledbyNgoTungSonand team showcased a practical application a seamless deployment of an automated attendance system in educationalsettings.Employingdeepfacialrecognition,this systemadeptlyidentifiedstudentsinreal-time,surmounting challenges posed by real-world conditions while accentuatingaccuracyusingfacialmovementcues.[2]
PrajaktaJ.LavateandSagarB.Shinde's 2021contribution introduced a novel camera-based face detection system, skillfully integrating OpenCV and machine learning. Achieving high detection rates, this research not only spotlightedtechnologicaladvancementsbutalsotracedthe evolutionoffacialrecognitiontechnology,tracingitsrootsto manuallandmarkinginthe1960s.[3]
Building on this momentum, Rehmat Ullah and collaborators, in 2021, engineered a real-time face recognitionframework,harnessingafusionofmachineand deep learning techniques. This framework aims to fortify security systems, underscoring the potential for real-time surveillanceenhancementsindiversescenarios.[4]
Thesubsequentyear,M.Naveen,J.VenkataManoj,andDr. Om Prakash Yadav's ingenious proposal outlined a smart surveillanceparadigm. Itheraldedapotentialrevolutionin storageandsurveillanceefficiencybystrategicallymitigating data redundancy in CCTV cameras, envisioning a transformativeshiftinsurveillancetechnology.[5]
ArpitSingh,SaumyaBhatt,VishalNayak,andMananShah,in 2022,navigatedresourcelimitationsandprivacyconcerns while constructing a real-time facial recognition system using deep learning. Their work provided a robust frameworkandaddressedpivotalchallengesforimminent advancements.[6]
Theculminationin2023bySathyabamaInstituteofScience and Technology (SIST) introduced an advanced CCTV surveillance system, amalgamating theft detection, facial recognition, and zone monitoring. This comprehensive
approach laid the groundwork for sophisticated security solutions,offeringaglimpseintothefutureofsurveillance technology. Collectively, these studies stand as pillars of innovation, fortifying security measures across various domains and ushering in a new era of surveillance technology.[7]
Theproposedsystemisacomprehensivesecuritysolution that utilizes cutting-edge technologies such as Python, MachineLearning(ML)andreactforcreatingtheapplication and Cloud for storing the data generated to enhance surveillanceandthreatdetection.Theprocessbeginswith theinitiationofavideostream,typicallyfromClosed-Circuit Television (CCTV) cameras. This continuous stream of footageisthenprocessedinreal-timeusingcomputervision algorithms.The core functionality of the system lies in its ability to recognize faces within the video feed. By employingadvancedfacialrecognitiontechniquespowered byML,thesystemcanidentifyaPersonofInterest(POI)by comparingthecapturedfaceswithapredefineddatabase.If a match is found, the system generates an event record, providing crucial information about the recognized individual.
Thesystemdoesnotstopthere;itgoesontostorethisevent data for future reference. Users, typically security administrators,canreviewpastdatatoanalyzepatterns,and potential security threats, or to retrieve historical information.In cases where a recognized face does not matchanyknownindividualsinthedatabase,anautomatic notificationissenttotheadministrator. Thisensuresaswift responsetopotentialsecurityconcerns,evenifthepersonis notapre-identifiedthreat.
The technology stack involved includes Python for the backend processing, ML algorithms for facial recognition, andReactfortheuserinterface.Thiscombinationresultsin arobust,intelligent,anduser-friendlysecuritysystemthat not only identifies and records security events but also empowers administrators with the tools to review and manage security data efficiently. The system’s real-time capabilities and integration of machine learning make it a powerfulassetintherealmofsurveillanceandsecurity.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 02 | Feb 2024 www.irjet.net p-ISSN: 2395-0072
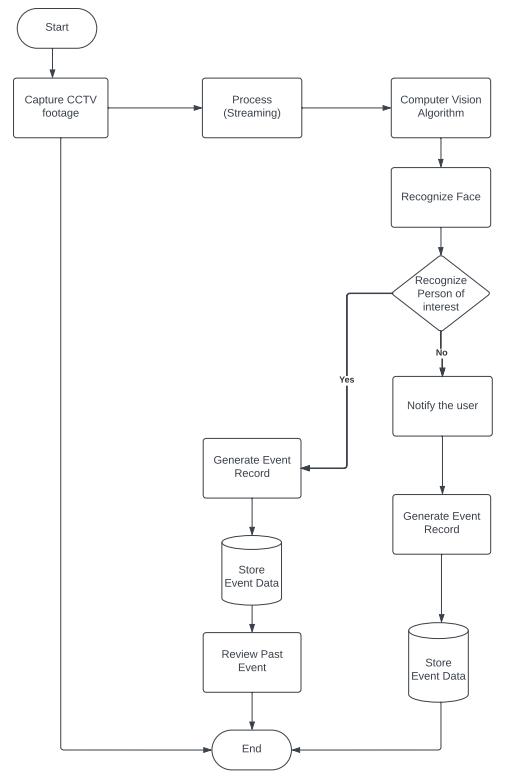
1 Flow Diagram
Themethodologyforthecomprehensive securitysolution leveraging Python, Machine Learning (ML), and React involves a systematic process aimed at enhancing surveillanceandthreatdetectioncapabilities:
5.1 Video Stream Initiation:
Thesystemstartsbycapturingacontinuousvideostream, commonly sourced from Closed-Circuit Television (CCTV) camerasstrategicallyplacedinthemonitoredarea.
5.2 Real-Time Processing:
Computer vision algorithms are employed to process the incomingvideofeedinreal-time. Thesealgorithmsanalyze eachframeofthevideotoextractandisolatefacialdata.
5.3 Facial Recognition:
Advanced facial recognition techniques are applied, leveraging Machine Learning (ML) modelsspecificallytrainedforfacialrecognitiontasks.This processinvolves:
Comparing the facial features extracted from the video framesagainstapredefineddatabaseofknownindividuals orpersonsofinterest(POIs).
UtilizingMLalgorithmstoidentifyand matchfaceswithin thevideofeedwiththedatabaseentries.
UponsuccessfulidentificationofaknownindividualoraPOI from the database, the system generates an event record. Thisrecordincludes:
Crucial information such as the recognized individual’s identity or ID, timestamp, and the location where the recognitionoccurred.
Theeventrecordservesasalogofidentifiedindividualsand theiractivitieswithinthemonitoredenvironment.
Allgeneratedeventdataissystematicallystoredinasecure andaccessiblerepository.Thisstoredinformationactsasa historical archive for security administrators.It enables retrospective analysis, pattern recognition, and the identification of potential security threats based on past occurrences.
5.6.
In scenarios where a recognized face does not match any knownindividualsinthedatabase, an automaticnotificationisimmediately dispatchedtothe security administrator or concerned personnel.This proactive notification system ensures rapid responses to potential security concerns, even for unidentified individuals.
Python serves as the backbone for backend processing, orchestrating data handling, and interaction with the ML algorithms.
MLalgorithmspowerthefacialrecognitiontasks,ensuring accurateandefficientidentificationofindividuals.
React,aJavaScriptlibrary,isutilizedfordevelopingtheuser interface, offering a seamless and interactive platform for securityadministratorstointeractwiththesystem.
The React-based user interface provides security administrators with intuitive tools and dashboards for efficientmanagementofsecuritydata.
Administratorscanreviewpastevents,analyzepatterns,and manage security protocols effectively through the userfriendlyinterface.
Leveraging real-time processing capabilities and the integration of machine learning algorithms, the system

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 02 | Feb 2024 www.irjet.net p-ISSN: 2395-0072
facilitates instantaneous recognition and response to securityevents.
This integration enhances surveillance efficiency, threat detection, and overall security management within the monitoredenvironment.
The proposed model is under development phase. Some partofprojectedsystemisworkingveryaccurateandthe initialresultsofprojectedsystemisasfollows.
Login Page:
The initial landing page of the smart surveillance system facilitatesuseraccessthroughlogincredentials.Thispage prominently features dedicated fields for entering the user'semailaddressandpassword.Additionally,itoffersa convenient "Signup" button, providing users with direct accesstotheregistrationorsignuppage.

2.Login Page
Signup Page:
Theregistrationportalofoursystemisspecificallydesigned to welcome new users seeking access. Within this page, individualscaninputtheirpersonaldetailslikename,e-mail address,passwordtocreateanaccount.
3.Sign Up Page
Face detection:
Inthedepictedscenario,thesystemisactivelyengagedin real-timefacedetectionbyacquiringlivevideofeedsfroma camera source. Additionally,itisaccessinga databasefor reference purposes. The face detection process itself is conductedthroughtheutilizationoftheOpenCValgorithm

DevelopinganadvancedSmartCCTVSystemenhancedby Machine Learning (ML) and Deep Learning represents a significant leap forward in surveillance technology. This system excels in detecting threats, conducting real-time analysis,andmanagingresourcesefficientlywhileupholding privacy standards. Its flexibility and scalability ensure continualenhancements,makingitwell-preparedforfuture advancements.
Thisholisticapproachnotonlystrengthenssecuritybutalso facilitatespromptdecisionmaking,contributingtoproactive monitoring and safer environments. Integrating ML and DeepLearningintoSmartCCTVforsensitiveareassignifiesa groundbreaking progression, enhancing surveillance and response mechanisms to promote safety.As technology evolves,thesesystemswillcontinuetoimprove,reinforcing securitymeasuresandsafeguardingcriticallocations.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 02 | Feb 2024 www.irjet.net p-ISSN: 2395-0072
AcknowledgmentsareextendedtoDirectorProf. Y.R.Soman, PrincipalDr.SandeepKadam, HOD,ProjectguideProf.Sagar Rajebhosale,and ProjectCo-guideProf.RajeshwariDandage for theirinvaluablesupportandguidancethroughout the project.Theirdynamism,vision,andmotivationhavebeen deeplyinspiring,enrichingourlearningexperience.Weare gratefulfortheirfriendship,empathy,andhumor,aswellas the contributions of each group member, which were instrumental in project success. Special thanks to the Teaching staff of the Computer Department for their constantencouragement,support,andguidance.
[1] Real-Time Face Recognition from Surveillance Video, MichaelDavis,StefanPopa,CristinaSurlea,(2010) Reference:https://doi.org/10.1007/978-3-642-17554-18
[2]FacesearchinCCTVsurveillance,MilaMilevaandA. MikeBurton(2019)
Reference:https://cognitiveresearchjournal.springeropen. com/articles/10.1186/s41235-019-0193-0
[3]ImplementingCCTV-BasedAttendance-TakingSupport SystemUsingDeepFaceNgoTungSon1,*,BuiNgocAnh1, TranQuyBan1,LePhuongChi1,BuiDinhChien1,Duong XuanHoa1,LeVanThanh1,TranQuangHuy1,LeDinhDuy 1andMuhammadHassanRazaKhan(2020) Reference:doi:10.3390/sym12020307
[4] Face Detection and Recognition Using Python and OpenCV,PrajaktaJ.Lavate\#1,SagarB.Shinde(2021) Reference:https://doi.org/10.37896/jxu15.7/008
[5]AReal-TimeFrameworkforHumanFaceDetectionand Recognition in CCTV Images Rehmat Ullah, Hassan Hayat, Afsah Abid Siddiqui, Uzma Abid Siddiqui, Jebran Khan, FarmanUllah,ShoaibHassan,LaiqHasan,WaleedAlbattah, MuhammadIslam,5,andGhulamMohammadKarami(2021) Reference:https://doi.org/10.1155/2022/3276704
[6]IntelligentSurveillanceSystemwithCNN Algorithm& Machine Learning M. Naveen1, J. Venkata Manoj2, Dr. Om PrakashYadav3,(2022).
Reference:ISSN:2349-6002
[7]Automationofsurveillancesystemsusingdeeplearning andfacialrecognitionArpitSingh1,SaumyaBhatt1,Vishal Nayak1,MananShah,(2022)
Reference:
https://link.springer.com/article/10.1007/s13198- 02201844-6
[8]SMART CCTV SURVEİLLANCE Sathyabama Institute Of ScienceAndTechnology(SIST),Chennai,TamilNadu,India. (2023)
Reference:doi:10.3390/sym12020307
[9] Face Recognition Based on MTCNN and Convolutional NeuralNetwork
Reference:https://dx.doi.org/10.22606/fsp.2020.41006