

Industrial Ethernet Book
The only publication worldwide dedicated to Industrial Ethernet Networking and the IIoT. Visit iebmedia.com for latest updates.

New website offers deepest, richest archive of Industrial Ethernet and IIoT content on the web.




View and/or download latest issue of Industrial Ethernet Book and past issues.
Search our database for in-depth technical articles on industrial networking.
Learn what's trending from 5G and TSN, to Single Pair Ethernet and more.
Keep up-to-date with new product introductions and industry news.
GET CONNECTED…
In this issue of the Industrial Ethernet Book, we explore two interrelated topics that have become a key focal points for automation networking solutions: industrial cybersecurity and IT-OT convergence.
As industrial companies have advanced digital transformation efforts, there has been an ongoing and increasing need to adopt solutions that improve cyber-resilience and streamline compliance to meet growing regulatory requirements. But at the same time, by fostering IT-OT collaboration in parallel with making strategic investments in security, businesses have prioritized melding these two different and distinctive parts of organizations.
The dual mandate, improving cybersecurity and increasing the collaboration between Information Technology and Operations Technology personnel has become an important part of the solution.
An IDC InfoBrief published in conjunction with Cisco presents the following logic. Because of the scale and the way OT assets communicate, securing industrial operations necessitates embedding security into industrial networking as part of a proactive risk-based strategy.
Because cybersecurity needs expertise, OT and IT teams must work together to secure industrial environments, breaking down silos. IT security technologies can easily be used to secure OT with the right context to industrial processes.
And finally, because OT needs more access to IT and cloud resources, security must converge. The industrial SOC needs to combine telemetry from the IT domain with rich OT visibility to best address modern threats to industrial environments.
In this issue, we present both sides of this dual mandate, and the opinions of industrial experts on the state of industrial cybersecurity solutions and IT-OT Convergence.
A summary of these opinions illustrates a broad consensus on cybersecurity solutions. AI-driven threat detection is cited as a driving force along with use of “zero-trust” security architectures and advanced network segmentation. The result: integrated security spanning both the IT and OT domains.
IT-OT convergence is playing a role from advanced endpoint protection to OT-calibrated network monitoring. And industrial cybersecurity is also being reshaped by regulatory frameworks, the NIS2 Directive and Cyber Resilience Act (CRA), increasing the need for product standardization and international specifications.
Check out the two major feature articles starting on pages 6 and 25 to learn more. Al Presher


Industrial Ethernet Book
The next issue of Industrial Ethernet Book will be published in November/December 2025. Deadline for editorial: November 14, 2025 Advertising deadline: November 14, 2025
Editor: Al Presher, editor@iebmedia.com
Advertising: info@iebmedia.com
Tel.: +1 585-598-6627
Free Subscription: iebmedia.com/subscribe Published by IEB Media
1247
Next-gen LAN Firewalls: 22
New Products: 58
Networks focus on the future of Single Pair Ethernet
The two leading Single Pair Ethernet networks, the SPE Industrial Partner Network e.V. and the Single Pair Ethernet System Alliance e.V., join forces for the future of industrial communication.

The board members of SPE Industrial Partner Network e.V. and Single Pair Ethernet System Alliance e.V. are excited about shaping the SPE ecosystem together. From
AFTER NEARLY SIX YEARS OF SUCCESSFUL but separate work, the two major networks promoting Single Pair Ethernet (SPE) technology are joining forces.
The SPE Industrial Partner Network e.V. and the Single Pair Ethernet System Alliance e.V., consisting of numerous well-known industrial companies, have been committed to the dissemination and further development of SPE since their inception. Until now, they have operated independently with their own members, working groups and areas of focus.
Growth of Single Pair Ethernet
With the growing awareness and relevance of SPE in the market, the networks have come closer together since the Hannover Messe 2025 and now plan to coordinate their activities in the future. The aim is to bring the strengths and combined expertise of both networks even more effectively to bear in the market and to further accelerate the spread of SPE. The first joint activities are already planned for 2025: both networks will be represented with a joint stand at SPS Atlanta
2025 – Smart Production Solutions USA from 16 to 18 September. Both networks will also play a key role in shaping the SPE Forum on 22–23 October in Ludwigsburg, Germany, with coordinated presentations. The year will conclude with a joint exhibition stand at SPS – Smart Production Solutions from 25–27 November 2025 in Nuremberg.
Both networks have been committed to the development of international standards for SPE since the beginning. Together, they support the SPE connector standard IEC 63171-7 and are consistently driving forward its expansion to include a uniform IP20 SPE mating profile. This standard forms a connecting element for the world of automation and creates a uniform basis for future-proof industrial communication. Other existing connector solutions and the associated international standards remain unaffected and continue to be valid for the numerous fields of application of SPE.
A central focus of the collaboration is the further internationalisation of Single Pair Ethernet. The aim is to make the advantages of SPE visible worldwide and to give users around
Tim Kindermann Phoenix Contact.
the globe access to a powerful, efficient and future-oriented network technology.
The numerous member companies of both networks are pooling their extensive expertise and innovative strength to create a strong and sustainable SPE ecosystem. This will enable users worldwide to benefit from practical solutions that pave the way for digitalisation.
About the networks
The two SPE networks bring together leading companies from different industries with the aim of advancing the development and adoption of Single Pair Ethernet as a key technology for digitalisation and the Industrial Internet of Things (IIoT).
Further information on the networks can be found at: www.single-pair-ethernet.com www.singlepairethernet.com
Contact via email: info@single-pair-ethernet.com (SPE Industrial Partner Network e.V.) info@singlepairethernet.com (SPE System Alliance e.V.)
left to right: Claus Kleedörfer TE Connectivity, Simon Seereiner Weidmüller, Kilian Schmale HARTING,
Compact, powerful, predictive: The Beckhoff power supplies with EtherCAT

24/48 V DC power supplies with EtherCAT interface increase plant availability with predictive diagnostics reliable current and voltage monitoring prewarning thresholds individually adjustable detection of input transients monitoring of internal device temperature output switchable via EtherCAT
2025 State of Industrial Cybersecurity Solutions
The current landscape of industrial cybersecurity technology solutions is rapidly evolving to meet the growing complexity and scale of cyber threats in smart manufacturing. In this special report, industry experts weigh in on the current state of affairs and how networking technologies and AI are strengthening security solutions.

FOR OUR 2025 REPORT ON CYBERSECURITY, the Industrial Ethernet Book reached out to industry experts to get their perspective on the trends driving new developments in industrial cybersecurity. A summary of these opinions illustrates a broad consensus on cybersecurity solutions. AI-driven threat detection is cited as a driving force along with use of “zero-trust” security architectures and advanced network segmentation. The result: integrated security spanning both the IT and OT domains.
IT-OT convergence is playing a role from advanced endpoint protection to OT-calibrated network monitoring. And industrial cybersecurity is also being reshaped by regulatory frameworks, the NIS2 Directive and Cyber Resilience Act (CRA), increasing the need for product standardization and international specifications. Read on to learn more.
AI technology driving new cybersecurity solutions
Solutions aim to keep up with the pace of innovation on the attackers’ side.
“Enhancements in artificial intelligence (AI) is currently the biggest driving force towards modern industrial cybersecurity solutions,” Andrew McPhee, Senior OT Security Solutions Manager at Cisco told IEB recently. “HackerGPT for example, is an AI tool created specifically for ethical hackers and research teams, but like anything else, it can be exploited by malicious actors. For example, if I present a CVE to HackerGPT, it can help build the code to exploit it. Industrial networks are known for being insecure, and now attackers don’t even need to understand how to code to create the perfect exploit."
"The newest wave of industrial security solutions must keep up with the pace of innovation on the attackers’ side, and to combat AI threats, we need to figure out quickly how to use AI for cyber defense," McPhee said.
Smart manufacturing impact
He added that smart manufacturing networks have seen the rise of the industrial data center. What was once a server room located somewhere in the plant has now become a key compute environment for hosting critical applications as traditional operational workloads get virtualized and hosted in a traditional IT manner. This has led to tighter collaboration between IT and OT teams, who are required to deploy preventative solutions, not just threat detection.
"Enhancements in artificial intelligence (AI) is currently the biggest driving force towards modern industrial cybersecurity solutions,” -- Andrew McPhee, Senior OT Security Solutions Manager, Cisco.

New cybersecurity solutions offering preventative measures, such as creating a real time asset inventory and segmenting the network into zones and conduits, and ensuring secure remote access, make sure that if the “greenfield” elements of a plant network, for example a new body shop in a vehicle assembly plant were to be compromised, the impact of that does not cross into the rest of the assembly plant, the “brownfield” sectors. Additionally, having accurate and real-time visibility of the plant enables alerting on anomalous activities taking place, for example, a new unauthorized IoT device being added to the network, unusual device activity, or suspicious remote user activity.
Cybersecurity solutions
"Cybersecurity solutions produce a lot of data, across many different data sources, and trying to make sense of this data is difficult,” McPhee said.
Cisco Cyber Vision for example is embedded within Cisco Industrial Ethernet Switches which enables complete visibility coverage across the operational network. Switches connecting industrial assets also profile them, score their risks, and map their communication activities. However, this may result in observing thousands of devices, and even more communications. Pair that with the outcome for visibility driven segmentation, it becomes an operational nightmare.
AI promises to do many things, but one thing machines are great at doing is processing numbers and performing pattern recognition, and cutting-edge cybersecurity technologies should be using these advancements to process this vast amount of data and present it to the users in a form that is easily consumable. Cyber Vision as an example groups the communication data it observes in the industrial network and automatically organizes it into a “zones and conduit” model,
which can be used as the starting point for a zero trust network segmentation project.
Applications
McPhee said that zero Trust is not a new model that in cybersecurity, but one that is becoming a reality for industrial networks. Organizations are taking the threat of remote access more seriously, replacing legacy remote access VPNs with zero trust network access (ZTNA) solutions to provide access to only the assets that are necessary, during a scheduled time window, and recording each session for auditing. ZTNA is also being enhanced with technology such as identity threat detection and response (ITDR) which provides insights if identities have been compromised. ITDR answers questions such as: is a user logging in from an unusual country, are they using a new device, are they logging in during irregular hours?
Zero Trust within the industrial network can also be realized with the implementation of the IEC62443 Zones and Conduits model. Visibility solutions such as Cyber Vision are being used as the starting point for a network segmentation project, helping organizations understand their existing communication patterns and make informed decisions on how to divide their network into logical zones of trust. These products then integrate into network access control (NAC) solutions such as Cisco Identity Services Engine (ISE), enabling segmentation to be driven by OT context. Using Cyber Vision to document assets that are part of each network segment helps drive collaboration between IT and OT teams. OT can leverage a user interface that understands the industrial process and IT gets pre-configured groups in their NAC. OT stays in control and IT enforces policies that will not disrupt production.
Industry challenges
“There is continuous skill shortage within the cybersecurity market, and even less of those
people who have a deep understanding of the unique requirements faced by operational networks, McPhee said. “Cybersecurity is critical to protecting these networks, and the tools, techniques and guidance can often lead to a steep learning curve to implement them correctly. Organizations should turn to solutions, rather than products, to make sure each security capability that may be required – visibility, segmentation, remote access, identity and access management, SIEM, SOAR, etc. – can all operate as one cohesive solution. My advice is to focus on the outcomes, not on the latest buzzword in the security market.”
Zero-trust architecture
All connections between devices should be authenticated and encrypted.
According to Dan White, director of technical marketing at Opto 22, “one of the biggest trends changing industrial cybersecurity is zero-trust architecture. You stop assuming anything is safe, just because it's inside your firewall. Every connection between devices should be authenticated and encrypted. When your HMI connects to your PLC, both sides should verify who they're talking to.”
“That level of verification is done using certificates—like checking IDs at both ends of the conversation. TLS encryption with proper certificate management protects data everywhere it travels. You're not just using passwords that can be guessed or stolen. Each device has its own cryptographic certificate that proves its identity. Even if someone intercepts your data, they can't read it or pretend to be your equipment,” White said.
Edge-originated, outbound-only communications solve another huge cybersecurity problem. Instead of external systems reaching into your networks and controllers to pull data, your edge devices

push data out when it’s ready. You publish data through MQTT Sparkplug B to whoever needs it, but nobody can reach back in to mess with your controls. Your equipment becomes impossible to hack remotely because it doesn't accept incoming connections.
Technology solutions
“You're trying to protect your plant without slowing down operations or making life harder for your operators and maintenance team. But smart manufacturing depends on sharing data between systems. Zero-trust architecture and edge-originated communications help make it safer to share that data,” White added.
White said that zero-trust with proper certificates means you know exactly what's talking on your network. That temperature reading from Tank 1? You know it actually came from Tank 1's sensor, not from someone spoofing data to cause problems. Your operators can trust what they see on their screens because every piece of data is cryptographically verified.
Edge-originated communications give you a huge benefit; your control systems keep running even if your IT network gets compromised. Since your PLCs and edge controllers only push data out through MQTT Sparkplug B, attackers can't reach in to
change setpoints or force outputs. When that ransomware attack hits the front office, your production lines don't even notice. Outboundonly publishing makes the difference—your MES gets production data without having any ability to control equipment.
MQTT Sparkplug B
According to White, the MQTT Sparkplug B with TLS reduces network traffic and helps secures data. The MQTT publish/subscribe architecture eliminates polling noise that clogs industrial networks. Instead of hundreds of clients asking a controller “what are your values?” every second, devices publish data only when values change. You cut network traffic by 90% or more compared to traditional poll/response protocols like OPC UA or Modbus/TCP.
When an edge controller comes online, it publishes data with a birth certificate that defines every tag, its data type, and its engineering units. Subscribers to that data know exactly what they're getting and get only what they need. The TLS layer encrypts everything and verifies certificates at both ends. Even if someone taps the network, they see only encrypted gibberish.
These cybersecurity technologies work for both greenfield and brownfield applications. For legacy equipment that can't handle
these modern, cybersecure communications, edge gateways create secure proxies. Your 20-year-old PLC talks normal Modbus to the gateway. The gateway then wraps that data in encrypted, authenticated MQTT Sparkplug B messages. You get modern security without touching working control logic.
Applications
“You face different security challenges depending on your industry. Here are some industries where modern cybersecurity solutions make the biggest difference,” White said.
Water and wastewater systems have remote sites everywhere—lift stations, pump houses, treatment plants miles apart. Edge controllers with MQTT Sparkplug B and cellular connections securely handle remote installations. Each remote site publishes its data outbound through encrypted channels. Nobody can hack in through the cellular connection because the device doesn't accept incoming connections. You monitor everything centrally while each site stays protected.
Oil and gas operations need to protect both pipeline SCADA and refinery controls. Zero-trust architecture helps here because you stop trusting devices just because they're on your OT network. Every flow computer,
“One of the biggest trends changing industrial cybersecurity is zero-trust architecture. You stop assuming anything is safe, just because it's inside your firewall. Every connection between devices should be authenticated and encrypted. When your HMI connects to your PLC, both sides should verify who they're talking to,” -- Dan White, Director of Technical Marketing, Opto 22.
every RTU, every control valve actuator must authenticate itself. When contractors bring in equipment for maintenance, it can't talk to your systems without proper certificates. Digital transformation and Unified Namespace (UNS) projects create new security challenges. You're connecting hundreds of diverse machines—different ages, brands, protocols—into a single data architecture. Edge devices with certificate-based MQTT become your security layer. Each machine publishes to your UNS through encrypted channels while legacy equipment stays protected behind edge gateways. Your 1990s equipment joins your Industry 4.0 initiative without compromising security.
Engineering challenges
“Your biggest worry when adding cybersecurity? Breaking something that works. Your 20-year-old PLC runs perfectly. You can't risk production downtime to add security features it wasn't designed for. Modern edge gateways resolve this worry—they sit beside your existing equipment, monitoring and securing communications without touching your control logic,” White added. He added that legacy equipment creates real headaches. Older devices don’t support certificates or encryption. They speak over serial networks or use Modbus/TCP and other
protocols that have no built-in security. But edge devices with built-in protocol translation can speak to your old equipment and publish data securely on your network using encrypted MQTT Sparkplug B communication. Your legacy gear stays untouched while gaining modern security protection.
Impact of IT-OT Convergence
Increasing interconnectivity of IT and OT networks.
“The dominant trend in the adoption of industrial cybersecurity solutions is IT and OT convergence. The increasing interconnectivity of IT and OT networks and the growing coordination between traditional IT security teams and the OT security team or process control team has allowed for a range of sophisticated cybersecurity solutions that would have been impossible for all but the most mature sites to implement 10 years ago from advanced endpoint protection to OT calibrated network monitoring solutions,” said Patrick O'Brien, safety and cybersecurity engineer at exida.
O'Brien added that, within cybersecurity solutions, the buzzword of AI is being incorporated into every marketing brochure and presentation. With all of the claims being
made about AI it is important to separate the noise from the new ground. AI has a number of different sub-categories that are often confused or mis-represented. Some categories like supervised machine learning have been incorporated into common security solutions for years and are undergoing a rebranding effort to highlight that they are part of the AI boom, while in some technologies and platforms newer advances like unsupervised machine learning and Generative AI support tools for users are being implemented.
Technology benefits
“When machine learning is applied for a cybersecurity solution from anti-virus/ endpoint protection to network monitoring (whether it is a network monitoring solution, SIEM, or Security Operations Center (SOC)) the primary benefit is the ability to make inferences beyond the known data set,” O’Brien said. “For anti-virus software it is limited based on the frequency of virus table updates (and compatibility with the control system in use) and may go months to years without ever being updated.”
This greatly reduces the effectiveness of the control as the solution will not be able to identify newer strains, and even the most diligently updated system is unable to detect novel strains. The hope with incorporating
Robust Ethernet Networks














• Unmanaged 10/100/1000 Mbps Ethernet Switches
• Single Mode and Multimode Fiber Optic Switches and Media Converters
• Diagnostic Switches for Network Troubleshooting
• PoE Switches, Mid-Span Splitters and Injectors
• Wired and Cellular IP Routers for Secure Remote Access
• Custom Configurations and Outdoor-Rated Options Available

machine learning is that the systems will be much more robust for detecting new variants that have yet to be incorporated into the virus table.
On the network monitoring side, he said that one of the primary challenges with traditional network monitoring solutions and SIEMs is the sheer volume of data and alerts being collected. We have worked with sites who are very proud of their state-of-the-art solution, only to quickly find that they are overwhelmed with a high volume of alerts for normal activity, making it challenging to identify where a real threat may exist. Security Operations Centers (SOCs) with dedicated and competent security analysts helps to address some of these concerns, but better event correlation and tuning will help to further manage the load of information being collected and highlight the scenarios that require response actions.
Machine learning impact
“Understanding the different categories of AI being used in cybersecurity solutions is key to communicating the benefits effectively. For this discussion we will group technologies into three categories: supervised machine learning, unsupervised machine learning, and Generative AI,” O’Brien added.
Machine learning particularly supervised
machine learning has been implemented for tasks like malware identification and intrusion detection systems for years. Supervised machine learning excels at identifying patterns from large data sets which makes it a good choice to identify new malware variants based on similarities to previous malware variants or common characteristics or identifying suspicious traffic patterns.
Using unsupervised machine learning or a hybrid model (combination of supervised and un-supervised) is human behavior analytics that are sometimes incorporated into a System Information and Event Management system. Unlike malware design, human behavior changes over design and can vary significantly in the realm of “usual” site support for industrial facilities making it much more difficult to discern the malicious from the benign. The final area where AI is being incorporated into cybersecurity solutions is the use of Generative AI in cybersecurity platforms to provide a new user interface that is easier to query ask for trends and access the massive amounts of data being collected in a more user-friendly way.
The computing power for the further analysis of event logs and traffic patterns using machine learning (particularly unsupervised) is almost never done directly in the factory environment instead collectors are
deployed to gather the information from the factory network and communicate out to the business network or cloud platform. Correctly configuring and deploying the cybersecurity solution to function as intended without negatively impacting operations is one of the key challenges facing automation engineers with these new technologies.
Applications
‘For the application of machine learning, we have seen this become a focus for almost every cybersecurity solution including anti-virus/ endpoint protection, network monitoring, SIEMs, and SOCs. The ability to more effectively detect unusual or malicious activities in fundamental to many cybersecurity protection technologies and is a natural fit,” O’Brien said.
For Gen AI the deployment has been a bit broader in what areas it can support. Ultimately Gen AI is providing a new easier way for security analysts to access information with the goal of lightening the load on existing security analysts to complete the many tasks necessary for achieving security. This could take the form of making it easier for them to interrogate the information collected by the SIEM to understand related event logs that tie back to the same incident to asking their security platform to generate report out on security metrics. Any time intensive manual
“The dominant trend in the adoption of industrial cybersecurity solutions is IT and OT convergence. The increasing interconnectivity of IT and OT networks and the growing coordination between traditional IT security teams and the OT security team or process control team has allowed for a range of sophisticated cybersecurity solutions,” -- Patrick O'Brien, safety and cybersecurity engineer, exida.

task for security engineers is a prime candidate for Gen AI to address when implemented at the platform level, and many organizations are viewing this as the way forward for achieving better visibility and maintainability in their security program overall.
Engineering challenges
For all industrial facilities, O’Brien said that the number one priority is maintaining the safety and availability of the facility. Because of this once a control system and site network is reliably running many automation engineers are very hesitant to make changes. Certain technologies like Intrusion Prevention Systems (IPS) or automatic anti-virus updates or patch deployment which are commonly employed in IT systems would be a non-starter for many industrial sites. In some cases, even network monitoring or SIEM systems which are not supposed to have a very limited impact on network communications load have actually led to loss of availability of certain devices or in one case a trip of the production network due to misconfiguration.
Additionally, automation engineers are often overloaded with the ongoing maintenance and support activities for the site, and dedicating even 4 hours a week solely to cybersecurity can be a challenge.
“This is where IT/OT convergence
can be a significant advantage. If the combined cybersecurity team has a common understanding of the objectives for security in the industrial site (safety and availability first), the knowledge and experience of the IT team with these technologies and solutions can be a great help in correctly configuring and deploying the solution,” O’Brien concluded.
OPC UA Standard APIs
Implementing factory networks using centralized tools based on open standards.
Randy Armstrong, Chair of the OPC UA Security Working Group, said that “cybersecurity is a problem that industrial equipment operators have to address whether it is because of the increasing number of attacks against industrial installation or government regulation such as the EU CRA. However, deploying a secure system can be expensive and there is a need to control costs by managing the security configuration of factory networks using centralized tools based on open standards. OPC UA defines standard APIs that are suited for this purpose.”
OPC UA standard APIs
OPC UA defines standard APIs for security configuration that allows equipment from
different vendors to be centrally managed by an off-the-shelf security management service designed to run locally on the factory network. This service ensures the security of all devices is kept up to date and adapts to changes in the factory environment. OPC UA greatly reduces the cost of deploying secure solutions by reducing the need for human administration and not forcing the factory operator to commit to a proprietary, single vendor solution.
“Modern security requires the management of public key infrastructure (PKI) which is used to distribute certificates to devices and applications,” Armstrong said. “The certificate allows them to authenticate themselves when connecting to other applications. The OPC UA standard is being deployed in factories around the world to automate management PKI during initial set up and while the factory is operating.”
The OPC UA certificate management APIs are suitable for any manufacturing environment that has devices communicating over TCP/IP based networks.
Engineering feedback
“The feedback the OPC Foundation has gotten is the cost of managing PKI is a major barrier to adoption of the modern cybersecurity practices. OPC UA provides an open standardsbased solution that allows factory operators to
“Cybersecurity is a problem that industrial equipment operators have to address whether it is because of attacks against industrial installation or government regulation such as the EU CRA. Deploying a secure system can be expensive and there is a need to control costs by managing the security configuration of factory networks using centralized tools based on open standards," -- Randy Armstrong, Chair of the OPC UA Security Working Group.

manage the PKI in the factory without being locked into expensive single vendor solutions,” Armstrong said.
He added that another concern is the need for access to cloud base systems that a lot of IT centric systems require. The OPC UA model presumes that the management service is running locally within the factory network and only needs to manage the devices on the local network.
CRA cybersecurity standards
Global impact due to product standardization and international specifications.
According to Dr. Al Beydoun, ODVA President and Executive Director, "the EU Cyber Resilience Act (CRA) mandates cybersecurity requirements for all products with digital elements. This includes any hardware or software that processes digital data and connects to other digital systems. The extensive scope of CRA covers IT, IoT, industrial control systems (OT), embedded devices, machinery, and more."
Starting December 11, 2027, any digital product sold in the EU must adhere to the cybersecurity standards set by CRA. Even earlier, on September 11, 2026, manufacturers must have a process in place to report vulnerabilities and security incidents for their digital products. To indicate compliance, manufacturers must apply the CE mark, a certification already recognized for ensuring safety in various products.
“This standardized approach aligns cybersecurity regulations across the EU, integrating digital products into existing harmonization laws. While this regulation doesn’t cover all world areas, it’s likely that the CRA will have a substantial global impact because of product standardization and international specifications,” Beydoun said.
Industrial cybersecurity solutions
“For most digital devices and software, companies can conduct their own assessments to confirm compliance. Most products incorporating Common Industrial Protocol (CIPTM) technologies will fall into this lowest risk category, allowing manufacturers to apply the CE marking independently,” Beydoun said.
However, products with higher security risks (defined as Important Class I or Important Class II within CRA) must meet specific harmonized standards, and the most critical category (defined as Critical within CRA) will require independent third-party evaluation before being approved for sale. By December 11, 2027, every digital product made available in the EU must adhere to the CRA, regardless of when it was originally developed or launched. This includes both existing products on the market and products available after that date. Harmonized standards are expected to be developed to support CRA implementation.
Technology innovations
Beydoun added that, starting December 11, 2027, manufacturers of industrial Ethernet
devices, including EtherNet/IP products, will need to adhere to documentation, development practices, and cybersecurity measures to comply with the EU CRA.
Manufacturers and vendors bear full responsibility for ensuring that Technical Documentation, End-User Documentation, and Secure Development Practices are integrated into the secure product development lifecycle. These processes must be tailored to the specific product, department, manufacturer, the product’s intended use, and the company’s development framework.
Regarding Vulnerability Management Requirements, the primary responsibility lies with the product manufacturer. Each vendor must establish a structured process for vulnerability reporting, management, disclosure, and the distribution of security advisories and updates. For vulnerabilities related to CIP technologies, ODVA has developed a vulnerability management framework that aligns with CRA requirements, ensuring that any identified weaknesses are addressed and disclosed appropriately.
While most of the CRA’s 13 cybersecurity requirements (listed in Annex I, Parts 1 and 2) apply directly to product design and fall outside the scope of CIP technologies, four specific requirements are influenced by CIP technologies. In all cases, CIP Security, an EtherNet/IP network extension, leverages widely adopted security standards such as TLS and OpenID Connect, as well as proven encryption algorithms.
"The EU Cyber Resilience Act (CRA) mandates cybersecurity requirements for all products with digital elements. This includes any hardware or software that processes digital data and connects to other digital systems. The extensive scope of CRA covers IT, IoT, industrial control systems (OT), embedded devices, machinery, and more,” -- Dr. Al Beydoun, ODVA President and Executive Director.
Key CRA Requirements Addressed by CIP Security
Secure by Default (Annex I, Part 1, 2b)
Requirement: CIP Security Contribution: The CIP Security Pull Model is designed to function automatically by default. Devices implementing this model can independently locate a certificate authority and request provisioning certificates. Once deployed, all security configurations can be automatically retrieved from a server and applied to the device. Furthermore, devices must have non-TLS/DTLS ports disabled by default. End users may enable these non-secure EtherNet/ IP ports later, based on their risk assessment, using the TCP/IP Interface Object. Port 44818/ UDP, used for ListIdentity, can likely remain open by default, as it is solely intended for device identification purposes.
Protection Against Unauthorized Access (Annex I, Part 1, 2d) Requirement: CIP Security Contribution: CIP Security offers multiple layers of protection against unauthorized access. The EtherNet/IP Confidentiality Profile supports authentication via both certificates and pre-shared keys, using mutual TLS. Additionally, for enhanced security, the CIP Security User Authentication Profile enables Role-Based Access Control and allows integration with external identity providers.
Confidentiality of Transmitted Data (Annex I, Part 1, 2e) Requirement: CIP Security Contribution: CIP Security ensures secure data transmission using TLS and DTLS protocols, requiring AES encryption - a globally trusted standard. Users can configure cipher suites based on security needs, though all CIP Security-compliant devices must support confidentiality measures. While CIP Security secures data in transit, encryption for stored data falls under the manufacturer’s responsibility.
Integrity of Transmitted Data (Annex I, Part 1, 2f) Requirement: CIP Security Contribution: Data integrity within CIP Security is ensured through TLS and DTLS, with all cipher suites defined by CIP Security incorporating strong integrity protections via SHA-based HMACs. Additionally, specific data elements - such as digital certificates and access tokens - are further protected using digital signatures. While CIP Security provides robust integrity measures for data in transit, ensuring data integrity at rest is the manufacturer’s responsibility.
Engineering challenges
Beydoun said that the CRA introduces comprehensive cybersecurity regulations for digital products in the EU, requiring compliance by December 11, 2027. Covering a broad range of products and markets including Operations Technology (OT), the CRA mandates strict security standards, vulnerability management processes, and robust documentation practices. Manufacturers
are responsible for implementing secure development processes, maintaining technical and end-user documentation, and ensuring proper vulnerability handling mechanisms.
“For CIP products, including EtherNet/IP, compliance with CRA requirements is critical,” Beydoun said. “CIP Security helps meet key regulatory obligations by leveraging industry standards like TLS, OpenID Connect, and strong encryption protocols. Specifically, CIP Security enhances protection against unauthorized access, ensures secure data transmission, and supports integrity mechanisms, aiding manufacturers in meeting CRA’s cybersecurity mandates. As the enforcement date approaches, companies must proactively align their cybersecurity frameworks with CRA requirements to maintain market access and enhance digital resilience across industrial automation and connected systems.”
For more details, download the CIP Security: A Valuable Tool for CRA Compliance white paper: https://www.odva.org/technologystandards/distinct-cip-services/cip-security/
Impact of AI and Automation
Technologies driving the newest industrial cybersecurity solutions.
“AI and automation are two of the most prominent technology trends that are driving the newest industrial cybersecurity solutions,” Natalie Kalinowski, OT Cybersecurity Consultant at Rockwell Automation told IEB recently.
Kalinowski said that most manufacturers, 95%, have either already invested in AI or plan to in the next five years. As AI is being used to improve security posture, the same technology is also being used by attackers to automate intrusions and evade detection. As a result, companies are increasingly testing this technology to catch unusual device activity or predict when a vulnerability might become a serious issue. AI is also being implemented to take over tedious, repetitive monitoring tasks, letting security teams focus on higher value tasks.
“Another trend driving the newest solutions is accelerated IT/OT convergence,” Kalinowski said. “By blending IT’s ability to handle data with OT’s focus on operations, companies are finding ways to work smarter, faster and more efficiently. But this growing integration expands the attack surface and opens the door to new cybersecurity vulnerabilities. However, real-time monitoring tools can help teams catch issues early and minimize them before they cause significant disruptions.”
Critical infrastructure operators have increasingly adopted cloud-connected systems — such as analytics platforms, remote monitoring tools and supply chain management platforms — to stay competitive. However, as operations adopt
hybrid architectures, we’re seeing threat actors pivot from traditional IT infiltration to abusing misconfigured cloud access, remote connections and weak credential controls. This is a massive operational risk, and it’s only continuing to accelerate. The assumption that cloud environments are secure by default is a dangerous one, especially when attackers are “logging in” instead of “breaking in.” These aren't just IT problems anymore. When attackers move laterally from compromised cloud credentials into operational networks, we're talking about potential impacts on safety systems and process control.
Cybersecurity solutions
“Industrial cybersecurity solutions aren’t just about protection,” Kalinowski added. “They help enable smart manufacturing at scale. Since many manufacturers rely on legacy systems that weren’t designed for today’s modern cyber threats, they’re often prime targets for threat actors that can cause financial burdens, pose health and safety risks and contribute to downtime. Industrial cybersecurity solutions can help detect threats in real-time, quickly deploy patches and decrease downtime.”
Additionally, they can assist with obsolescence planning projects where operational environments can use risk prioritization to identify key areas for modernization projects to update and secure their infrastructure. According to a recent State of Smart Manufacturing report, 53% of manufacturers cite that securing OT assets is one of the primary reasons for investing in AI, and more than half of respondents are already adopting security at-scale. This digital transformation shift recasts security leaders as growth enablers. Hardened networks can also help serve as the foundation for predictive maintenance, helping reduce risk and protect revenue from costly impacts.
Industrial cybersecurity solutions allow for secure remote access for third-party and internal use, network segmentation to limit attack surfaces and security monitoring and response. Manufacturers are also embedding security into hardware as a standard practice, enabling layered, robust security measures that minimize risk and bolster resiliency. Solutions have evolved to meet the modern threat landscape. Where it used to be about locking down the perimeter, it’s now about real-time threat intelligence across a distributed infrastructure.
Newer solutions can also translate cyber scenarios into financial terms to support datadriven decision-making. Executives and the insurance agencies that underwrite their risk now expect precise metrics. Security leaders can use these advanced solutions to translate the technical vulnerabilities into business terms so executives can weigh cybersecurity spending against other capital priorities.

Impact on operational technology
“Industrial cybersecurity solutions are specifically unique to industrial and operational technology (OT) environments, designed for the specific realities of the factory floor without focusing on repurposing specialized IT tools,” Kalinowski said. “This OT specialization helps these solutions integrate seamlessly with existing infrastructure and reduce implementation challenges. Not to mention, most typical IT security tools can't fully solve the challenges and threats that are present in OT environments."
By implementing cybersecurity solutions that combine secure-by-design principles, network segmentation and real-time threat detection, organizations can protect critical assets without disrupting production. Real-time monitoring and threat visibility help industrial organizations receive a detailed look into all of their connected assets, helping to prioritize risks as well as identify and respond to key vulnerabilities. This real-time insight also helps organizations quickly respond to security threats and address resource gaps and operational inefficiencies.
Often, industrial organizations are understaffed, overwhelmed by alerts and struggling to make sense of what’s actually happening across increasingly connected environments.
Security monitoring and response solutions can provide alert optimization and response guidance. By ingesting a wide range of data sources including behavioral analytics and correlation, OT-specific logic can help detect true positives and suppress
the noise. When bolstered by the expertise of a trusted partner, newer cybersecurity solutions can go beyond just detection, delivering a clear, contextualized response plan that helps internal teams act quickly and effectively.
Applications
These solutions are targeting several areas in OT environments and are helping to minimize the increased cyber risks in multiple industries, including critical infrastructure, automotive, food and beverage, consumer packaged goods, and more. The newest solutions help these organizations focus on centralizing asset inventory, correlating configuration data and assessing network segmentation. As a result, they can uncover high-risk paths from IT into OT, move toward implementing mitigation steps such as secure remote access controls and network segmentation.
“Solutions are also applied to offer plants automated patching, centralized alerting and improved endpoint visibility. The improvements help to bolster defenses against a range of modern risks, including those associated with cloud-based services, remote access and identity management,” Kalinowski said.
“Additionally, by monitoring sensors and production, companies can free their information from “functional silos,” detect anomalies and threats and contain cyber incidents before they compromise the entire supply chain. Frequent asset inventory audits help secure operations and preserve product quality and safety.”
Addressing engineering challenges
When implementing industrial cybersecurity strategies, Kalinowski said that one of the major concerns companies are facing is gaining comprehensive asset visibility. On the factory floor, there are many devices in play, some that may be hard to spot right away. Limited visibility makes it hard to protect all assets. This can slow or complicate the deployment of cybersecurity strategies. Without a comprehensive map, troubleshooting a suspected breach feels like searching for a single misplaced bolt in a vast warehouse.
In plenty of plants, older machines still serve as a backbone for production. Unfortunately, those same systems may also be the least prepared to deal with modern cyber threats. They were built for stability, not for advanced security. This can bring inherent compatibility issues and complicate integrating industrial cybersecurity solutions, all while trying to keep systems up and running. You can’t simply tack on encryption or multi-factor authentication if the hardware isn’t equipped to handle it.
“Bridging the IT/OT divide is also a concern, as IT pros see the world through data confidentiality and software patches and OT teams focus on uptime, worker safety and consistent production,” Kalinowski said. “It’s not hard to see how these differing viewpoints might clash. A quick software patch might be child’s play for IT, but a single system reboot can halt an entire production line on the OT side. Without a shared language or framework, both sides might struggle to coordinate on a response plan for potential attacks.”
“AI and automation are two of the most prominent technology trends that are driving the newest industrial cybersecurity solutions. Most manufacturers, 95%, have either already invested in AI or plan to in the next five years. As AI is being used to improve security posture, the same technology is also being used by attackers to automate intrusions and evade detection," -- Natalie Kalinowski, OT Cybersecurity Consultant, Rockwell Automation.

IT-OT Convergence
AI-driven threat detection, zero-trust architectures, advanced network segmentation.
According to Michael Metzler, Vice President, Horizontal Management Cybersecurity for Digital Industries at Siemens, “the convergence of Information Technology (IT) and Operational Technology (OT) is a rapidly evolving trend in the industrial sector.”
“As companies increasingly look for ways to optimize their operations and improve efficiency, the need for seamless communication between traditionally separate systems becomes paramount. It lays the foundation for data-driven decision making,” Metzler told IEB recently. “The integration of IT and OT systems requires a robust communication infrastructure that can handle the demands of both realms.”
Current technology trends in industrial cybersecurity include the increased adoption of AI-driven threat detection, zero-trust architectures, and advanced network segmentation. To this end, Siemens – a major supplier for industrial cybersecurity – is offering solutions that offer real-time monitoring, automated response capabilities, and enhanced visibility across both IT and OT environments. These solutions are designed to be scalable, allowing companies to protect both modern and legacy systems without significant overhauls.
Technology impact
Metzler said that industrial networks are the nerve pathways in production – they are
becoming in sum ever more complex. Hardware alone no longer determines their performance. Software-based network management and the use of cybersecurity tools have become indispensable.
New industrial cybersecurity solutions offer several benefits, including improved threat detection, reduced response times, and enhanced protection against both internal and external threats. These solutions can significantly reduce the risk of costly downtime due to cyber incidents, thereby improving overall operational efficiency. The potential impact on manufacturing networks is substantial, as these solutions enable a more resilient and secure production environment, which is crucial in an era of increasing cyber threats.
“The risk of cyberattacks on industrial plants is real - and the frequency continues to increase. To comprehensively protect industrial plants against cyberattacks from inside and outside, all levels must be addressed simultaneously - from the operational to the field level, from data protection to secure communication,” Metzler said. “With Defense in Depth, Siemens provides a multi-layered security concept that offers industrial plants comprehensive and far-reaching protection in accordance with the recommendations of the international IEC 62443 standard.”
It is aimed at plant operators, integrators and component manufacturers and covers all relevant aspects of industrial cybersecurity. Cutting-edge cybersecurity technologies in industrial environments are characterized by their ability to seamlessly integrate with
existing systems, including legacy OT devices. Technologies such as machine learning-based anomaly detection, industrial firewalls with deep packet inspection, and secure remote access solutions are being applied in factories to provide real-time threat detection and automated incident response. What makes these technologies unique is their focus on the specific needs of industrial environments, where uptime and safety are paramount.
Application targets
Metzler said that the newest industrial cybersecurity solutions are specifically targeting areas such as critical infrastructure protection, secure remote access for industrial control systems, and the protection of industrial IoT devices. These solutions are also being applied to ensure compliance with stringent regulatory requirements and to safeguard sensitive production data.
“With the increasing convergence of IT and OT, traditional defense concepts are increasingly reaching their limits. Softwarebased network management and the use of cybersecurity tools have therefore become indispensable,” Metzler said.
To be able to detect potential vulnerabilities in OT networks at any time, Siemens has designed a complementary tool set for plant operators with the SINEC software family. The SINEC Security Inspector determines the security status of individual components or entire production networks. The SINEC Security Monitor analyzes network traffic and detects anomalies through passive, non-intrusive continuous security monitoring. One of the
“The convergence of Information Technology (IT) and Operational Technology (OT) is a rapidly evolving trend in the industrial sector. As companies increasingly look for ways to optimize their operations and improve efficiency, the need for seamless communication between traditionally separate systems becomes paramount," -- Michael Metzler, Vice President, Horizontal Management Cybersecurity for Digital Industries, Siemens.

newest tools in the SINEC portfolio is the SINEC Security Guard, an intuitive cloudbased software-as-a-service that displays vulnerabilities for OT-Assets and enables optimized security management for industrial operators without dedicated cybersecurity expertise. The SINEC NMS network management system also enables centralized monitoring and configuration of networks as well as security through encrypted data communication and local documentation.
Focus on OT
Metzler said that the special framework conditions in Operational Technology (OT), including continuous operation, high performance requirements, and availability, demands an in-depth understanding of industrial processes so that security concepts can be optimally introduced and implemented. For many companies, this task has become too complex. They need a partner who is familiar with and has mastered the special requirements of industry and cybersecurity.
When implementing industrial cybersecurity strategies challenges include protecting legacy systems that were not originally designed with cybersecurity in mind, ensuring the secure integration of IT and OT (Operational Technology) networks, managing the growing complexity of industrial networks, and addressing the shortage of skilled cybersecurity professionals. C Additionally, companies must ensure that all components, including new and legacy
devices, are equipped with robust security functionalities. This includes implementing technologies like industrial firewalls, intrusion detection systems, and secure remote access solutions that are specifically designed for industrial environments. Companies must also balance the need for robust security with the requirement for minimal disruption to production processes and safety systems.
“Beyond technology, the correct handling of cybersecurity measures by personnel is crucial,” Metzler said. “This involves training staff to adhere to defined policies and procedures, such as incident response protocols and regular security audits. A lack of cybersecurity awareness or poor adherence to security protocols by employees can undermine even the most advanced technical defenses. Overall, the shortage of skilled cybersecurity professionals presents a challenge, making it essential for companies to not only invest in technology but also in ongoing training and education for their workforce.”
NIS2 Directive and Cyber Resilience Act
Industrial cybersecurity landscape being reshaped by regulatory frameworks.
Thomas Rummel, Managing Director at Softing Industrial Automation GmbH, told IEB that “the industrial cybersecurity landscape is being reshaped by regulatory frameworks such as the NIS2 Directive and the Cyber Resilience
Act (CRA).”
“These initiatives drive companies to adopt security-by-design principles, integrate real-time vulnerability management, and enforce supply chain security. Another major trend is the adoption of the IEC 62443 standard, which provides structured, risk-based security for automation systems,” Rummel said. “Technological enablers include network segmentation, secure communication protocols, and identity and access management. Vendors are also increasingly embedding long-term update mechanisms into IIoT devices to ensure resilience. Collectively, these trends reflect a shift from reactive to proactive security strategies, designed to align IT and OT teams and ensure compliance across global supply chains.”
Industrial cybersecurity solutions
Rummel said that the latest industrial cybersecurity solutions bring multiple benefits for smart manufacturing. First, they enhance operational resilience by reducing the likelihood of successful cyberattacks through network segmentation and encrypted communications. Second, they increase visibility into industrial assets.
For example, Softing’s plantPerfect Monitor enables real-time inventory of devices and firmware, which is essential for patch management and regulatory compliance. Third, they strengthen supply chain trust by enforcing standardized security processes, making collaboration easier across global
"The industrial cybersecurity landscape is being reshaped by regulatory frameworks such as the NIS2 Directive and the Cyber Resilience Act (CRA). These initiatives drive companies to adopt security-by-design principles, integrate real-time vulnerability management, and enforce supply chain security,” -- Thomas Rummel, Managing Director, Softing Industrial Automation GmbH.

supply chains. The impact on smart manufacturing is substantial: more secure networks allow for the safe integration of IIoT and cloud analytics, thereby supporting efficiency, predictive maintenance, and datadriven optimization.
“Ultimately, cybersecurity is no longer just a defensive measure but an enabler of digital transformation,” Rummel said.
He added that cutting-edge industrial cybersecurity solutions are characterized by their integration into core automation systems. One example is Softing’s smartLink HW-PN, which provides a secure access point to PROFINET networks. The device ensures segmentation by isolating higher-level application networks from field-level devices, while using OPC UA with certificates for encrypted and authenticated communication. What makes them unique is the balance between OT integration and adherence to IT security principles, ensuring that cybersecurity does not hinder but rather facilitates operational performance.
Application areas
Rummel said that new cybersecurity solutions are targeting several critical application areas. Asset management is a major focus, where tools like Softing’s smartLink HW-PN allow secure parameter setting and state monitoring of field devices. Network monitoring and process analysis are also key areas, enabling companies to identify abnormal behaviors and prevent disruptions in IIoT environments.
Additionally, real-time inventory through solutions like Softing’s plantPerfect Monitor ensures companies can align as-built device configurations with planned security policies. Beyond these, secure communication channels and segmentation architectures are being applied in industrial control networks to isolate critical systems and reduce attack surfaces. Together, these applications form the backbone of secure, connected manufacturing ecosystems that meet NIS2 and CRA requirements.

Overcoming engineering challenges
“Automation engineers face several challenges when implementing cybersecurity strategies. Legacy systems often lack modern protection and must be upgraded or isolated,” Rummel said. “Management workload is another concern: implementing continuous monitoring, vulnerability patching, and regulatory reporting adds complexity.”
He added that there are also training gaps, as staff must be educated to confidently apply new standards like IEC 62443. Moreover, companies must navigate the tension between IT and OT priorities. Where IT focuses on strict security policies, OT emphasizes uninterrupted operations. Supply chain security is equally pressing, as vulnerabilities can propagate through third-party devices and services. Addressing these concerns requires not just technology, but a holistic approach combining processes, people, and tools, aligned with NIS2 and CRA obligations.
Holistic security strategies
More integrated security approaches spanning both the IT and OT domains.
Georg Stoeger, Senior Principal Customer Solution Architect at TTTECH, said that “the industrial cybersecurity landscape is rapidly evolving, driven by several key technology trends that are shaping the newest solutions. The ongoing convergence of Information Technology (IT) and Operational Technology
"The industrial cybersecurity landscape is rapidly evolving, driven by several key technology trends that are shaping the newest solutions. The ongoing convergence of Information Technology (IT) and Operational Technology (OT) creates new attack surfaces but also enables more integrated security approaches if a holistic security strategy that spans both domains is used,” -- Georg Stoeger, Senior Principal Customer Solution Architect, TTTECH.
Softing’s smartLink HW-PN allows for secure parameter setting and state monitoring of field devices.
(OT) creates new attack surfaces but also enables more integrated security approaches if a holistic security strategy that spans both domains is used.”
Stoeger said that another significant trend is the adoption of Artificial Intelligence for advanced threat detection and response. AI-powered solutions can analyze vast amounts of data from industrial control systems (ICS) and OT environments to identify anomalies, which can be used for threat detection in real-time to enable early response to ongoing attacks. We need to consider AI as an enabler for new levels of threat to cybersecurity, but also as a critical component for maintaining cybersecurity.
The “Zero Trust” security model is also gaining traction. This approach, which assumes no implicit trust or safe “firewalled” network zones and instead verifies every access request, is particularly relevant in networked environments where granular control over access to critical assets is essential.
He added that the increasing adoption of cloud technologies and the Industrial Internet of Things (IIoT) is pushing for more robust and scalable security solutions that can protect distributed and interconnected systems. The need for secure-by-design principles, as mandated by regulations like the EU's Cyber Resilience Act (CRA), is also a major factor influencing the development of new cybersecurity solutions.
Enhanced operational resilience
“A key requirement and also a primary benefit of state of the art cybersecurity solutions for industrial systems is enhanced operational resilience. As threats to system integrity such as zero-day exploits and advanced persistent threats (APTs) evolve and become more complex, real-time visibility into industrial control systems (ICS) and OT environments is necessary to allow organizations to proactively identify and mitigate these threats, minimizing the risk of downtime and production disruptions,” Stoeger said. “Managing system integrity starts with asset inventory, extensive access and event logging, and real-time exposure management across all assets. Based on these (often very large) amounts of data, AI-powered solutions can detect sophisticated attacks that traditional security tools might miss.”
Apart from technical capabilities, new solutions also need to support compliance with emerging regulations like the EU's Cyber Resilience Act (CRA) and the NIS2 directive. Certified platform solutions can help organizations meet these stringent requirements. Scalability, flexibility and openness of smart manufacturing systems
and networks is essential to support digital transformation such as the adoption of IIoT and cloud technologies, but the security challenges that come with this flexibility and openness require a very capable and widereaching security architecture that is equally scalable and adaptable. This goes beyond securing the actual infrastructure and must include supply chain integrity, maintenance and update procedures, and interaction with any third-party system.
“In the age of IIoT and the edge-cloud continuum, industrial cybersecurity technologies need to address operational technology (OT) requirements, IT environments, and their interactions over datacenter networks, on-premise networks, and edge-local networks,” Stoeger said. “Unlike IT systems, OT systems often consist of legacy equipment with long lifecycles, proprietary network interfaces and protocols, and a high sensitivity to latency. Therefore, modern industrial cybersecurity solutions are designed to be non-intrusive and passive, using techniques like deep packet inspection (DPI) to monitor network traffic without affecting operations.”
He added that OT security solutions that can focus on operational context are capable of not only identifying vulnerabilities but also understanding the criticality of assets and processes, allowing for risk-based prioritization of security measures. For example, a vulnerability in a critical production-line controller would be prioritized over a similar vulnerability in a non-critical system. In factory environments, these technologies can perform continuous monitoring and threat detection, providing real-time alerts on suspicious activities.
As mandated by IEC 62443, solutions for industrial cybersecurity also need to support creating security zones and conduits to limit the spread of attacks. Even when proper segmentation is achieved in this way, secure remote access for maintenance and support may still be needed, using granular access controls and monitoring to prevent unauthorized actions. Edge computing solutions provide capabilities to achieve segmentation, secure remote access and management of industrial assets in a single comprehensive platform.
Application areas
Although cybersecurity cannot be applied selectively to just a few critical areas in the industrial system, Stoeger said that there are indeed some applications that have the strongest need for cybersecurity because they protect critical infrastructure and manufacturing operations from a growing number of cyber threats. One primary application area is the protection of the “brains” of the production systems
- Industrial Control Systems (ICS) including Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs). These systems are the backbone of industrial automation and are increasingly being targeted by attackers.
Another key application area is the security of the Industrial Internet of Things (IIoT). As more and more devices are connected to industrial networks and add attack surfaces, securing these devices and the data they generate is crucial. This includes providing visibility and control over the traffic between IT and OT systems to prevent threats from spreading from the IT network to the OT network.
Last but not least, the protection of legacy systems is a significant application area. Many industrial organizations still rely on older systems that were not designed with security in mind and may not even have basic authentication or encryption capabilities, and industrial edge cybersecurity solutions need to provide a layer of protection for these vulnerable assets.
Engineering challenges
“One of the biggest concerns is the potential for disruption to operations. Unlike IT environments, where a system reboot or a temporary outage is often acceptable, in OT environments, any disruption can lead to significant production losses, safety risks, and financial damage,” Stoeger said. “Therefore, ensuring that security measures do not impact the availability and reliability of control systems is a top priority. This includes deploying certificates, cryptographic keys, security patches and software updates in a way that does not make the control system unstable.”
He added that another major concern is the complexity of industrial environments. They often consist of a heterogeneous mix of new and legacy equipment from different vendors, using a variety of protocols. This complexity makes it challenging to implement a unified and consistent security strategy.
“The skills gap is another significant concern. There is a shortage of cybersecurity professionals with expertise in OT environments, which makes it difficult for companies to find the talent they need to implement and manage their security programs,” Stoeger said.
“Finally, the cost of implementing and maintaining a robust cybersecurity program is a major concern for many companies, especially small and medium-sized enterprises,” he added. “Balancing the need for security with budget constraints is a constant challenge.”
Al Presher, Editor, Industrial Ethernet Book
A secure future for robotics: the role of cybersecurity
This article explores security risks and effective security measures in robotic control systems. It covers industrial security standards and analyzes the essential requirements to meet these standards.

In securing the future of robotics, cybersecurity is paramount. Robust measures, such as secure authentication, encrypted communication, and supply chain security are crucial to protect against threats.
MANUFACTURERS ARE RAPIDLY ADOPTING
Factory automation is at the center of Industry 4.0 and industrial robots, autonomous mobile robots (AMR), and collaborative robots play a crucial role in enabling the implementation of modern Industry 4.0.
Robots are becoming smarter, more collaborative, and better positioned to handle complex tasks with and without human intervention. Higher levels of automation and higher use of robots also drive the demand for higher safety and security of robotic control systems. Robots were initially mostly used on factory floors but now robots are used in different domains like medical, military, logistics, and agriculture. The need for safety and security is of much more importance than a decade back. Accidents are bound to occur, but the ones caused by malicious attacks are critical. Malicious hijacking and control of robots can cause serious economic and financial losses.
Security risks: robotic control
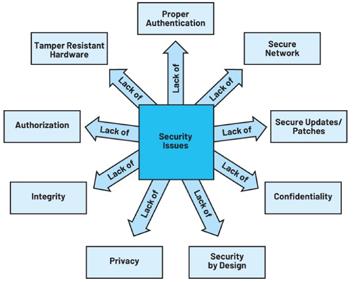
Figure 1 shows typical security risks
that can lead to malicious attacks on robotic control systems. An overview of some of the concerns can be found in Table 1.
The cybersecurity landscape is rapidly evolving, and there are a growing number of regulations as well as acts that target
SOURCE: ANALOG DEVICES
the industrial and robotics sector. Among the many, some of the acts that target cybersecurity are EU Cybersecurity Act, EU Cyber Resilience Act, and U.S. Cyber Incident Reporting for Critical Infrastructures Act. There are regulations and acts evolving in China and India as well. The NIST Guide to Operation Technology (OT) Security and standards like IEC 62443 provide us guidance, enable us to take the secure-bydesign approach and design, and develop our control systems to be resilient against cybersecurity attacks.
IEC 62443 Requirements for Industrial Automation and Control Systems Security (IACS) IEC 62443 is security for IACS.2 It is a widely adopted standard for developing industrial automation control systems, and most regulations recommend it and recognize its importance. It enables us to be compliant with relevant regulations, mitigate potential cybersecurity risks in control systems, address security
Figure 1. Security risks in robotic control systems.
Lack of Impact and Description
Secure networking
Proper authentication
Confidentiality
Integrity
Secure boot and update
Tamper-resistant hardware
Renders the communication between robotic control systems insecure and prone to spoofing, tampering, and eavesdropping. It may impact the availability of the system as well.
This leads to unauthorized access using default usernames and passwords. Lack of device or peripheral authentication may lead to the use of counterfeit peripherals/ accessories in robotic systems presenting safety or security risks.vAlso leads to accepting data inputs from untrusted, non-identified sources.
Lack of encryption or weak encryption algorithms leads to the interception and exposure of robotic sensitive data and design plans.
This can lead to the alteration of robotic sensitive data, configuration, and firmware either stored or in transit.
Without this, we are unsure if authentic firmware/software is running on our robotic control system. Lack of secure updates could potentially enable hacking into robotic control systems by doing either rollback to vulnerable older software or by programming nonauthentic software into robotic control systems.
Sometimes robots store extremely sensitive information (for example, robots used in military/ defense). It is very crucial to protect this information from access to unintended actors. Without tamper-resistant hardware, it becomes difficult to protect information against invasive attacks.
Secure by design
Updates
Most control system developments until recently did not adopt the principle of secure by design approach. This leads to breaking into the robotic system’s architecture and design to scan and exploit its vulnerability for launching an attack.
Lack of updates for the robotic operating system, firmware, and software may result in cyberphysical attacks.
gaps in control systems, protect critical assets, and many others.
While some parts of the standard focus on processes and procedures, IEC 62443-4-1 and IEC 62443-4-2 specifically address component security. According to IEC 62443-4-2, component types include software applications, host devices, embedded devices, and network devices. The standard defines the capability security level (SL) for each component type based on the component requirement (CR) and requirement enhancement (RE) they meet. It defines four security levels (SL) SL0 to SL3. The SL2 and SL3 levels specifically require hardware-based security.
Capabilities and technologies for robotic security system solutions
To build secure robotic control systems, we need to address the risks highlighted in the Security Risks in Robotic Control Systems section. Key technical capabilities and
technologies needed include:
Secure authentication: Integration of secure authenticators to verify device/ component identity.
Secure coprocessors: Utilization of dedicated hardware for secure storage and cryptographic operations.
Secure communication: Implementation of encrypted protocols for protected data exchange.
Access control: Enforcement of granular permissions to restrict unauthorized system access.
Physical security measures: Incorporation of measures to protect against physical tampering.
Turnkey security ICs, such as secure authenticators and coprocessors, are purposebuilt to meet these requirements, offering ease of implementation and cost efficiency. These fixed-function ICs are complemented by comprehensive software stacks designed for host processors.2
Note: Using a discrete secure element enhances system resilience by preventing a compromised application processor from accessing credentials stored in a separate IC (isolation).
In addition to these aspects, system developers must adopt a structured approach to secure development that encompasses requirements gathering, threat modelling, secure design, implementation, testing, certification, and maintenance. Following a secure development life cycle (SDL) ensures security is built into the development process from the beginning.
Partner for engaging in robotic security system solutions
ADI goes beyond being a mere vendor of turnkey security ICs like the MAXQ1065 and DS28S60—we empower customers to fulfill diverse security requirements in the robotics industry. By integrating extensive expertise in security and robotics, ADI emerges as an
Table 1. Security Risk Concerns.
ideal solution provider capable of tackling the distinctive challenges involved in securing robotic systems. Profoundly acquainted with these domains, we enable customers to construct comprehensive solutions that encompass hardware, software, and systemlevel considerations.
Recognizing that security in robotic systems requires a comprehensive approach, ADI goes beyond component-level offerings and adopts a system-level perspective. We consider factors such as hardware, software, communication, and integration, ensuring all critical components are seamlessly integrated.
ADI’s collaboration with the automotive industry is exemplified by its wireless battery management system (wBMS), showcasing its exceptional capabilities in implementing robust security measures. Through close collaboration with customers, ADI has developed a fully safe and secure ISO 21434certified wBMS system, underscoring ADI’s commitment to delivering comprehensive solutions. Encouraging similar collaborative efforts within the robotics industry would leverage ADI’s expertise in security implementation. By partnering closely with stakeholders, ADI can contribute to the development of safe and secure robotics systems, drawing from its experience and success in the automotive sector.
With its extensive capabilities and dedication to security, ADI emerges as the preferred partner for system design, offering unparalleled expertise and support in all cybersecurity-related endeavors.
To learn more
Engage with the embedded security community by joining discussions on securityrelated blogs at EngineerZone™. Search for “security” to find valuable articles and resources dedicated to the topic. Contribute to the ongoing dialogue by sharing insights, asking questions, and participating actively. Explore a range of security products and gain valuable insights at Embedded Security and 1-Wire®. Access recent technical articles, application notes, and videos to enhance your understanding of the subject. Stay up to date with the latest advancements in the field and discover more about our security offerings.
Sample use case in a robot joint controller
A potential system design of a robotic joint control system within a robotic joint is illustrated in Figure 3.
In this design, the potential application of the MAXQ1065 becomes apparent as it enables the implementation of secure boot functionality, thereby enhancing the overall security of the system.
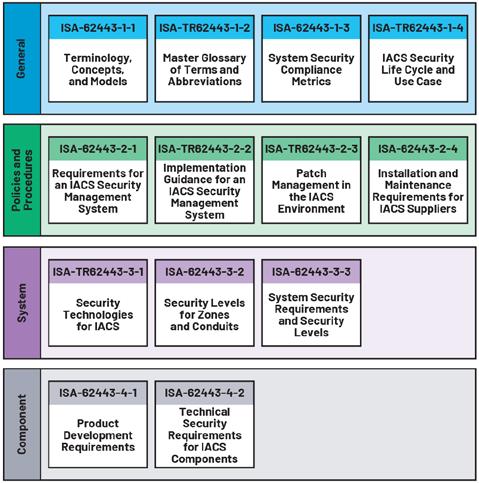
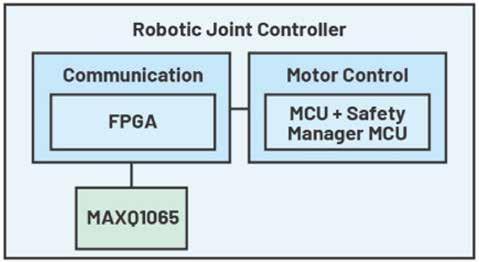
The MAXQ1065 also encompasses an array of additional features, such as secure key storage, secure communication protocols, and cryptographic operations. Subsequent articles will delve deeper into these use cases and explore their practical applications.
Conclusion
In securing the future of robotics, cybersecurity is paramount. Robust measures, such as secure authentication, encrypted
communication, and supply chain security are crucial to protect against threats. By prioritizing cybersecurity and leveraging ADI’s expertise, we can unlock the full potential of robotics while safeguarding against emerging risks in an interconnected world.
Manoj Rajashekaraiah, Principal Engineer Analog Devices.
Visit Website
Figure 2. The IEC 62443 is a comprehensive security standard.
Figure 3. Potential use of the MAXQ1065 in a robotic joint control system.
Next-gen LAN firewalls enhance industrial network security
Four concerns are faced by industrial networking users when implementing firewall solutions. The article highlights how next-gen industrial LAN firewalls overcome these challenges to strengthen network security and ensure uninterrupted network operation.

BECAUSE OF THEIR FREQUENCY, CYBERATTACKS on critical infrastructure are no longer the sensational news they once were. However, these types of cyberattacks always heavily impact citizens and organizations, as our daily lives are closely tied to critical infrastructures, such as power substations, intelligent transportation, and water treatment.
To mitigate the impact of cyberattacks, governments worldwide are implementing laws and regulations to strengthen cybersecurity for critical infrastructure. For example, by October 2024, EU members are required to incorporate the NIS2 Directive into their national laws to strengthen cybersecurity for critical infrastructure.
Therefore, industrial organizations need to adopt a comprehensive cybersecurity framework and implement robust solutions
to meet these cybersecurity standards and regulations.
Defense-in-depth strategies
Usually, industrial cybersecurity standards and regulations recommend defensein-depth strategies, which involve implementing multiple layers of protection to minimize security risks for organizations. Industrial operators usually concentrate on fortifying network boundaries and establishing security zones to minimize potential threats from external access. However, addressing internal threats is just as critical because internal devices without protection can compromise the entire network. For example, plugging in a portable storage device that carries malware can compromise your network and have your network controlled by others. Thus,
protecting your network from internal and external threats is of utmost importance.
Industrial firewalls effectively filter traffic to prevent potential threats from internal and external access. However, industrial operators usually have concerns about network performance when deploying industrial firewalls in LANs near their critical assets.
This article focuses on four concerns faced by various stakeholders— asset owners, chief information security officers (CISOs), system integrators, OT network administrators, and industrial network design experts—when implementing firewall solutions. The article also highlights how next-gen industrial LAN firewalls overcome these challenges to strengthen network security and ensure uninterrupted network operation.
Industrial firewalls effectively filter traffic to prevent potential threats from internal and external access. However, industrial operators usually have concerns about network performance when deploying industrial firewalls in LANs near their critical assets.
The EDF-G1002-BP Series industrial-grade LAN firewall with IPS and DPI functionality protects mission-critical assets and network zones. Softwareconfigurable Gen3 LAN bypass achieves bump-in-the-wire installation and minimizes the installation impact for industrial applications.
Four big worries when implementing firewall solutions
Although implementing firewall solutions increases the security level of your industrial operations, these changes can affect your current operations.
Striking a balance between network security and performance is challenging. Learn more about the four concerns that are pushing industrial operators to find solutions for smoother implementations.
Concern 1: Adding New Devices Requires Changes to the Existing Network Design
Deploying industrial firewall solutions into existing corporate operational networks can lead to significant network topology changes. Redesigning the topology and reconfiguring IP subnets to integrate the new firewall solution into existing networks will demand substantial efforts and time from industrial engineers. This is particularly difficult for critical applications that cannot afford any network downtime. Therefore, industrial operators need a firewall solution
that does not alter their present network configuration.
Concern 2: Adding New Devices Affects Network Performance and Services
Seamless system operations rely on smooth network communications. The big worry when adding new devices to enhance cybersecurity is whether they meet current network performance standards, such as boot time, network latency, and operating environment needs. Furthermore, the addition of new devices raises the likelihood of network downtime caused by maintenance or device malfunctions. Therefore, a firewall solution must prioritize network performance and mitigate the risk of complete shutdown from a single point of failure.
Concern 3: Protecting Legacy Devices at Field Sites Is Challenging
Standards such as IEC 62443 and frameworks like NIS2 require critical assets to protect against DoS attacks and maintain event logs
during incidents. However, many critical assets in industrial applications are legacy devices that usually use older versions of operating systems and cannot be replaced right away to meet these network security requirements.
To safeguard legacy devices from growing threats, a firewall solution is required that doesn’t require frequent system updates. Moreover, a significant number of legacy devices at field sites use diverse industrial communication protocols for different application needs. For improved communication security, a firewall solution needs to support these protocols and conduct detailed data analysis in industrial control networks.
Concern 4: Monitoring Networks and Cyberthreats Is Not So Simple
To ensure the safety of your networks, constant monitoring and management of network security is crucial. It requires a lot of time and effort for administrators to keep their eyes on the network status, making sure

they receive real-time notifications when a network error or security event occurs. The absence of an effective monitoring mechanism for firewall solutions leads to delays in network error notifications and security event alerts, resulting in extended network downtimes and compromised operational performance.
Maximize industrial network security and uptime with next-gen LAN firewalls
With our EDF-G1002-BP Series industrial LAN firewalls, industrial operators can overcome networking challenges, ensuring both network security and uptime. Operating in transparent firewall mode, the LAN firewall prioritizes safeguarding your critical assets and facilitating secure east-west communication within the LAN.
Do you know what types of firewall solutions fit a current application scenario? See the infographic above for information on how to choose the right industrial firewall solutions for different application scenarios.
Simplified
installation
The nature of the LAN firewalls allows you to deploy firewalls without reconfiguring IP subnets. Such designs are perfect for those critical applications that cannot afford to change their existing network topology. To simplify network installations, our 2-port LAN firewalls allow bump-in-thewire installations so that engineers can simply connect these LAN firewalls in front
of critical assets without reconfiguring IP subnets. This way, our LAN firewalls ensure minimal disruption to existing configurations and enhance network security.
Optimized network uptime
It only takes 30 seconds of boot time to enable our LAN firewalls. This quick boot time ensures that, during a power outage and subsequent restoration, the anomaly detection mechanism between the control center and terminal PLC equipment does not trigger mistakenly. Also, our LAN firewalls have a LAN Bypass function that prevents any hardware or software anomalies from causing the firewall to interrupt operational services. Both mechanisms aim to achieve uninterrupted operations.
Legacy device protection
Making it easy to protect legacy devices is the core mission of our LAN firewalls. We design them for industry use and incorporate IPS and DPI technology to strengthen network security. Industrial-grade IPS designs ensure the security of your legacy devices, including PLC and HMI. Our IPS functions safeguard your legacy devices from current threats using virtual patches and pattern-based protection, allowing you additional time to update your systems. With our DPI technology, you have greater control over the security of your industrial communications. To maintain data integrity, you can define rules that limit Modbus equipment to read-only access, for instance.
You can effortlessly safeguard legacy devices using different protocols and benefit from our DPI technology’s support for multiple industrial protocols and advanced traffic filtering capabilities.
Simplified network management
If you use our LAN firewalls to secure your network and legacy devices, you can simplify network monitoring and security management using our MXview One network management software and MXsecurity network security management software. MXview One software provides a holistic view of network security status and notifies you when a network error occurs.
With the MXsecurity software, users can effectively manage firewalls and monitor security events. Implementing firewall policies on a centralized platform minimizes manual errors in individual configurations. Furthermore, the software notifies users of security events for quick responses and risk mitigation.
The EDF-G1002-BP Series is an advanced LAN firewall that boosts industrial cybersecurity and provides the reliability required for your applications.
Visit the Moxa website using the link below to learn more about the features the EDF-G1002-BP Series.
Technology article by Moxa.
Four frequently seen user scenarios illustrate the need to choose a firewall solution that meets the needs of a particular network installation.
IEB Special Report: IT-OT Convergence in Focus
Industry experts provide their perspective on advances in IT-OT convergence. Key trends include innovations in network automation, software defined networking and advanced cybersecurity solutions along with hybrid cloud-edge architectures, software virtualization, containerization technologies and the impact of AI.

," --
IT-OT CONVERGENCE REMAINS A TOP PRIORITY for most in smart manufacturing as networking and IT technologies are reshaping plants into more agile, efficient and data-driven ecosystems.
The push for greater levels of IT and OT connectivity has resulted in a push within industry to provide solutions for standardization of network operation, advances in security technology, software virtualization and containerization technologies and more effective system architectures.
For this special report, the Industrial Ethernet Book reached out to industry experts in this area. Their responses point to importance of innovative technologies that are continuing to break down the traditionally separate domains of factory floor and enterprise IT, creating a more unified data ecosystem.
Standardization of OT networks
The impact of network automation, softwaredefined networking and advanced cybersecurity frameworks.
“Achieving true IT/OT convergence is improbable and may even be undesirable in many cases because of fundamental differences between the two environments,” Vivek Bhargava, Product Marketing Manager, Cisco Industrial IoT, told IEB recently. “While IT focuses on Confidentiality, Integrity, and Availability, in that order, OT’s focus is reversed – Availability, Integrity, and Confidentiality. A more realistic and desirable approach is to bring proven IT principles and methods including network automation, software-defined networking, and advanced cybersecurity frameworks to standardization
of OT networks.”
Bhargava said that as organizations modernize their operations and invest in advanced robotics, software-defined industrial automation and AI, they are experiencing increased demands on their network. Allowed to grow unchecked, these networks are at risk of becoming complex and harder to scale, made flexible, and secure. Industrial companies are increasingly seeing IT/OT collaboration as a strategic way to simplify their processes, making them more efficient, profitable and innovative.
IT-OT convergence
“Three distinct technologies can help partnership between IT and OT. First, many OT systems having been built largely piecemeal over decades consist of a diverse array of
"IT-OT convergence remains both highly important and an area where significant progress has been made — but it’s still a work in progress because of the inherent complexity of merging two worlds with very different priorities and constraints. Considerable progress has been made in bridging the gap between OT and IT. Common platforms such as Cisco IOS XE running on both ruggedized industrial and enterprise devices give teams a unified toolset.
Vivek Bhargava, Product Marketing Manager, Cisco Industrial IoT.

devices, leading to inefficiencies and higher maintenance costs. Standardization simplifies these complexities by creating a unified framework,” Bhargava said. “Second, the vast majority of industrial companies have only deployed point security solutions and lack the skills and processes to actively manage threats. OT networks need the same level of security as enterprise IT systems. Extending IT cybersecurity practices and capabilities to OT environments offers a robust defense against these threats. Third, management and automation tools, long used in IT environments, are now transforming OT operations, bringing benefits such as automating the configuration and deployment of network devices with zero-touch provisioning, and automating proactive network issue detection and resolution.”
Technology benefits
Bhargava said that although industrial and enterprise networking equipment necessarily differ because of environmental needs, they can still be standardized when it comes to their networking functions and common operating systems. Deploying standardized networking equipment across IT and OT can benefit from consistency and predictability.
Extending IT cybersecurity practices and capabilities to OT environments improves defense against growing threats. Such defenses include zero-trust architectures that ensure that every device and user has access only to the resources it needs to perform its job, network segmentation that isolates different parts of OT stopping lateral movement of threats, early detection of threats, and integration of OT networks into centralized SOCs to respond to threats quickly.
Similarly, utilizing the same familiar platform, for example Cisco Catalyst Center, for both IT and OT means that OT teams can manage industrial switches with workflows they already know or can easily learn from IT colleagues, reducing the steep learning curve and the need to master multiple systems. With the same tools and policies as IT, modern enterprise best practices can be directly extended into OT.
“As I mentioned earlier, IT-OT integration
is challenging because they have traditionally been built, operated, and governed in very different ways — with different priorities, stakeholders, and technology stacks. While true convergence may not be completely feasible, a partnership between IT and OT can benefit the organization in very significant ways,” Bhargava said.
Standardization of networking equipment, not only within OT but also between IT and OT, removes a major source of friction, disparate technologies, management tools, and operational practices. When both IT and OT networks use the same switching, routing, and wireless platforms, teams work with the same interfaces, protocols, and diagnostics tools and eliminate the “two sets of playbooks” problem.
For example, all Cisco networking devices, industrial and enterprise, run the same operating system IOS XE. Having this common OS creates a common technical foundation that unifies operations (with the same CLI commands, automation APIs, telemetry, and troubleshooting workflows), simplifies training reducing the skills gap, streamlines management, and enables consistent security and policy enforcement.
Looking ahead
“From a technology perspective, IT - OT convergence remains both highly important and an area where significant progress has been made — but it’s still a work in progress because of the inherent complexity of merging two worlds with very different priorities and constraints,” Bhargava said.
He added that considerable progress has been made in bridging the gap between OT and IT. Common platforms such as Cisco IOS XE running on both ruggedized industrial and enterprise devices give teams a unified toolset. Platforms like Cisco Catalyst Center now manage campus, branch, and industrial sites from one pane of glass. OT-aware threat detection, network segmentation, and secure remote access are now built into network infrastructure.
But challenges still exist. Many OT assets have lifecycles of 20+ years and were not designed for IP networking. IT and OT teams
still have different priorities with differences in refresh cycles and downtime windows.
“In summary, though, IT-OT partnership is no longer optional. It is a critical enabler for modern industrial organizations,” Bhargava said. “We’ve seen strong progress through standardization, unified management, and integrated security, but the journey is ongoing.”
Evolving technology solutions
Increased impact from new cloud computing solutions, security advances and AI.
According to Scott Reynolds, senior security and network engineering manager at Johns Manville and 2025 president of the International Society of Automation (ISA), “Let’s start with what IT-OT Convergence means to me. Ideally, it should mean leveraging the tools and knowledge from the IT stack and taking advantage of them in the OT space. With that definition, there are a few trends that are shaping this discussion. First, people are getting comfortable with the cloud, and we are seeing OT slowly leveraging the cloud when it makes sense. Second, security trends are having a heavy impact on both IT and OT: zero trust, identity is the new perimeter, and the password is dead all impact OT as well, and leveraging tools like this at an enterprise level makes them manageable to secure IT and OT. Finally, we can’t avoid talking about AI, especially learning language models (LLM), and it is finally giving us accessible information from the big data journey we talked about over 10 years ago.”
IT-OT technology solutions
Reynolds said that he believes the biggest impact on IT-OT technology solutions is private LLMs / MLs solutions (Enterprise Microsoft Co-Pilot, for example).
“OT has done a great job collecting lots of information, but the effort it takes from having a hunch, to observing a trend, to root cause is mostly spent figuring out where the data is and how the data relates to P&ID, functional specs, and control narratives, and quality control. What if I can just ask “if pH is
Four frequently seen user scenarios illustrate the need to choose a firewall solution that meets the needs of a particular network installation.
on the higher end of the acceptable tolerance, how much does that impact the amount of solid waste generated vs the quality of the effluent stream?” What about “give me a report of these quality issues times and the environmental conditions of the site.” Those are some very powerful questions that we could see answered very quickly even if the person asking doesn’t know where to start looking for the data if the LLM can see where that data is,” Reynolds said.
New levels of enterprise/ automation integration
“Going back to security. When I think of zero trust, I think it’s pretty much the same idea as zone and conduits in ISA/IEC 62443 series of standards,” Reynolds said. “The best part about this is that we can leverage the knowledge of IT cybersecurity and apply it to OT cybersecurity in this scenario. This is usually done with firewall rules in the OT network, and it is something the IT side is very comfortable with at this point. The other type of zero trust is around ZTNA, replacing traditional VPN with other more secure remote access solutions. These, again, can leverage the knowledge from IT security and apply them to the OT environment.”
Going back to LLM, Reynolds said that the biggest challenge is securely getting data from the OT network and moving it to a location
that is accessible to the enterprise or cloud environment. The simplest technical solution to accomplish this is a data diode. This is a firewall that physically only allows data to go in one direction. There are many advantages and disadvantages to using this method, so keep that in mind before going in this direction.
With that said, he added that users can leverage common communication protocols (such as SQL) to pass the data out from the OT network in a way that doesn’t allow for that network path to be used to get into the OT network. Once the data is on the enterprise or cloud side, it is easy to start using tools to gain insights from that information. One catch with many of these LLM solutions is the risk of the data being used for the LLM to learn. Make sure you work with a lawyer to understand the privacy in intellectual property risks and impacts of using different tools.
Challenges
“At the end of the day, being able to look at data and leverage data in an agile way gives your organization a competitive advantage,” Reynolds said. “Tools like LLM let people ask questions without know exactly how to get the information. Security tools help you get that information, while continuing to secure your industrial environment. Without being able to get data from the shop floor, it is very
hard to make informed decisions, or to quickly validate hypothesis on industrial issues, or industrial performance improvements that you want to use to learn how you can become more effective at your process.”
“In summary, first getting useful data, second being able to interpret that data, and third quickly being able to validate that change you made is impacting the system they way expected, are how you are going to be successful leveraging the IT-OT Convergence,” he added. “With that said, if it is not done in a secure way, it can lead to an entry point for compromising the process network, so security needs to be prioritized when working on your convergence journey.”
Intelligent, autonomous manufacturing systems
Led by hybrid cloud-edge architectures, software virtualization and containerization technologies.
“The industrial edge computing landscape is shifting towards intelligent, autonomous manufacturing systems. Real-time data processing directly at the edge reduces latency and cloud dependency and supports missioncritical operations as well as predictive maintenance and improved operational efficiency,” Georg Stoeger, Senior Principal Customer Solution Architect at TTTECH told

Call 1-800-999-2900 or visit www.miinet.com/tcs-ieb to learn Moore.


IEB recently.
He said that hybrid cloud-edge architectures, also called the “edge-cloud continuum”, optimize bandwidth and enhance data privacy by processing information locally while selectively transmitting data to the cloud for applications such as digital twins and asset management.
Software virtualization and containerization technologies enable workload consolidation on single devices, improving resource utilization.
“Cybersecurity challenges are becoming even more complex due to IT-OT convergence, with IEC 62443 compliance ensuring secure communication and device integrity through hardware-based security features. Notably, the EU Cyber Resiliency Act (CRA) is expected to drive the industry towards even more comprehensive cybersecurity architectures and processes including supply chain security; organizations that currently provide digital products but cannot meet CRA requirements may drop out of the industrial market supply chain,” Stoeger said.
“Finally, AI-driven predictive analytics embedded at the edge leverage sensor telemetry and machine learning models for real-time anomaly detection, predictive maintenance, and process optimization, creating truly intelligent manufacturing ecosystems,” he added.
Potential solutions
Stoeger said that, whether custom-built or using standard products, industrial edge computing
platforms which bring data processing and analytics closer to the source of data on the factory floor are certainly a key solution for IT-OT convergence. Running data processing of OT data directly at the edge minimizes latency and enables real-time decision-making, a critical requirement for optimized industrial processes. Complementing edge computing are open communication protocols like OPC UA and MQTT, which facilitate seamless and secure data exchange between disparate industrial assets and IT systems.
The importance of these technologies lies in their ability to break down the traditionally separate domains of factory floor and enterprise IT, creating a more unified data ecosystem. This integration helps businesses to improve operational efficiency, agility, and innovation. By harnessing real-time data from the OT environment, companies can optimize production processes, predict maintenance needs, and develop new data-driven services. Similarly, being able to manage OT and edge software assets from a secure cloud-based platform, leveraging common IT services such as role-based user account management and repositories and orchestration of containerized software improves operational efficiency of the IT related processes in a converged IT-OT infrastructure.
Technical benefits
“The technical benefits of IT-OT convergence, when properly applying the necessary technology, are based on a much more
standardized and standards-based landscape – communication protocols, software management methods, cybersecurity capabilities, and many more,” Stoeger said. He added that the resulting advantages include enhanced operational efficiency e.g. through
• real-time data analytics and monitoring, which allows for expedited responses and more precise decision-making, or
• transparent management of deployed software versions and patches to maintain consistency and security. Cost reduction is another significant (although less “technical”) benefit, achieved through predictive maintenance capabilities that preemptively identify potential issues, reducing downtime and maintenance expenses. For automation integration, this means moving from rigid, pre-programmed systems to more adaptive and intelligent automation. This new level of integration allows for dynamic adjustments to production processes, optimized resource allocation, and the creation of a truly agile and responsive manufacturing environment.
Multi-layered approach
On a technical level, Stoeger said that IT-OT convergence requires a multi-layered approach. At the base is the edge computing platform, which typically consists of industrial-grade servers, industry PCs (IPCs) and/or gateway computers located at the machinery or on the factory floor. These computers run a
"First is getting useful data, second being able to interpret that data, and third quickly being able to validate that change you made is impacting the system they way expected, are how you are going to be successful leveraging the IT-OT Convergence. With that said, if it is not done in a secure way, it can lead to an entry point for compromising the process network, so security needs to be prioritized when working on your convergence journey.,” -- Scott Reynolds, senior security and network engineering manager, Johns Manville.

specialized software stack that includes a real-time operating system and a hypervisor, allowing for the simultaneous execution of both OT and IT workloads. The hypervisor supports “virtual machines” or software containers that can run both legacy control applications (the “OT” side) and modern data processing and analytics applications (the “IT” side) on the same hardware.
Furthermore, various networking capabilities including industrial field bus networks (mostly Ethernet-based), LAN connectivity and potentially also WAN/internet connectivity are supported by most edge computing devices. Data from industrial assets is collected using a variety of protocols, such as OPC UA, PROFINET, EtherCAT and Modbus/TCP, and is then processed at the edge. This edge processing allows for immediate analysis and action, such as triggering a maintenance alert or adjusting a machine's parameters. Raw and/or processed OT data can also be securely transmitted to the cloud or an on-premise data center for further analysis, training AI models, and other types of integration with enterprise systems. This architecture provides a scalable and secure way to bridge the IT-OT divide, enabling a new class of data-driven industrial applications.
Challenges for IT-OT Convergence
“Despite the challenges, mastering IT-OT convergence is essential to get the optimum benefits from digitalization. Industry 4.0 is not possible without this convergence. Cybersecurity is clearly a primary concern; it
should be addressed not by creativity, but only by the adoption of standards like IEC 62443 and the development of secure-by-design edge platforms,” Stoeger said. “The complexity of integrating legacy systems is being mitigated by the development of flexible and open platforms that can communicate with a wide range of industrial protocols.”
He added that the continued development of edge computing, artificial intelligence, and machine learning will accelerate this trend, resulting in even more capable but also more complex IT-OT systems. We clearly believe that IT-OT convergence is a fundamental and irreversible shift in how industrial enterprises will operate. Especially in the EU, where strict normative cybersecurity frameworks such as the EU Cyber Resiliency Act are coming into force in these years, the overarching need for comprehensive design and management of the entire digital infrastructure including all IT and OT systems will require organizations to become very competent in all aspects of IT-OT convergence, from designing the infrastructure to managing the entire lifecycle in a centralized and platform-oriented way.
OT and IT connectivity
Effective technology for data transport to the edge and cloud for analysis to optimize processes.
“The fundamental concept of interoperability has increased in importance with the
continued rise in connectivity between OT and IT networks. Industrial Ethernet networks contain vast amounts of data that are critical to the performance of automation in process, hybrid, and discrete facilities globally. This data can be transported to the edge and cloud for analysis to optimize processes to improve quality, throughput, and uptime,” Steve Fales, ODVA Director of Marketing, told IEB.
“It’s necessary for the plant floor OT data to be available with the proper context, semantics, and format to be both easily transportable and usable with higher level IT systems. Additionally, it’s important for network devices to be able to be interchangeable with similar devices from other manufacturers in the event of an unplanned failure or device obsolescence. Network coexistence is another advantage for end users to ensure that different industrial communication networks don’t negatively interfere with each other,” Fales said. “A significant amount of work has been done since the advent of industrial Ethernet to ensure interoperability can be achieved by end users through adherence to IEEE and IEC specifications, independent conformance testing, and collaboration between standards development organizations resulting in consistent data models and other collaborative specifications.”
IT-OT Convergence solutions
Fales said that industrial communication networks, such as EtherNet/IP, support solutions such as the Process Automation
"The technical benefits of IT-OT convergence, when properly applying the necessary technology, are based on a much more standardized and standardsbased landscape – communication protocols, software management methods, cybersecurity capabilities, and many more -- Georg Stoeger, Senior Principal Customer Solution Architect, TTTECH.

"The importance of industrial Ethernet communication interoperability is increasing in automation as the number of device connections, driven by IT-OT convergence, continues to grow. Interoperability is key to successfully running an automation facility that can be efficiently run for decades to come.” -Steve Fales, Director of Marketing, ODVA.
Device Information Model (PA-DIM) and the OPC UA information model to make sure that data from the factory floor can be easily understood and used by edge and cloud applications.
While most data can be used for analysis, the time and cost required to provide the proper formatting, labels, and consistent scaling can make optimization projects unfeasible. PA-DIM is a specification that allows for protocol agnostic communication of common instrument parameters, including semantic IDs as defined by IEC 61987, using OPC UA information modelling techniques.
PA-DIM is specifically targeted at the process automation sectors. OPC UA enables reliable, secure diagnostic communications between industrial control system devices and the cloud as well as to enable common cloud gateway and device management tasks across a wide variety of industries. Both data models ensure that the proper data context and metadata are available to be able to best use the information with database tools like SQL.
Process device profile specifications
ODVA has also released process device profile specifications that address level, temperature, flow and pressure measurement devices. Process device profiles for EtherNet/IP network capable devices help end users more easily commission new instruments in critical environments, replace sensors regardless
of vendor, and support a harmonized data structure. Process device profiles provide a standard format for process variables and diagnostics, with semantics and scaling that align with PA-DIM, across an array of devices for easier DCS and PLC data integration from EtherNet/IP-enabled field devices.
One of the driving factors behind the advent of Standards Development Organizations (SDOs) was enabling interoperability to provide end users with alternatives if vendors went out of business or stopped supporting a given product line.
As time has gone on, SDOs, such as ODVA with EtherNet/IP, have achieved a significant number of installed nodes globally, strong multivendor support, independent conformance testing, and continued specification enhancements to address the latest technologies while still retaining backwards compatibility.
Engineering challenges
“Industrial communication SDOs have been cooperating globally for many years now for the benefit of the technology end users. An example of this can be seen with the interface standard for the acquisition of energy consumption data in industrial manufacturing being co-developed by ODVA, OPC Foundation, PROFIBUS & PROFINET International, and VDMA based on OPC UA,” Fales said. Further cooperative efforts include the
Industrial Security Harmonization Group (IESHG) between FieldComm Group, ODVA, OPC Foundation, and PROFIBUS & PROFINET International. The IESHG is working to harmonize cybersecurity strategies and concepts so that end users do not face unnecessary complexity when using security concepts in their automation systems. Also, a single conformance test plan for the IEEE/ IEC 60802 Time Sensitive Networking (TSN) profile for Industrial Automation is being worked on by the Avnu Alliance, comprised of the CC-Link Partner Association, ODVA, OPC Foundation, and PROFIBUS & PROFINET International.
“The importance of industrial Ethernet communication interoperability is increasing in automation as the number of device connections, driven by IT-OT convergence, continues to grow,” Fales said. “Whether it’s the need to quickly and easily move data from the factory floor to the cloud and back for process optimization with the aid of data models like PA-DIM and OPC UA, to have networks fairly coexist together with Time Sensitive Networking, or to be able to easily replace devices if the original product isn’t available via EtherNet/IP Process Device Profiles, interoperability is key to successfully running an automation facility that can be efficiently run for decades to come.”
Al Presher, Editor, Industrial Ethernet Book
Process-X: moonshot thinking in the process industry?
NOA, AAS, and Process-X not only allow for secure data exchange between OT and IT but also lay the foundation for digital collaboration between companies. Looking at specific use cases and security architectures, it becomes clear how "moonshot thinking" can also become a reality in the process industry.
THE PROCESS INDUSTRY IS AT A TURNING point ; digitalization, sustainability, and regulatory requirements demand new ways of thinking and innovative technologies. This article shows how concepts such as NOA, AAS, and Process-X not only allow for secure data exchange between OT and IT but also lay the foundation for digital collaboration between companies.
Looking at specific use cases and security architectures, it becomes clear how "moonshot thinking" can also become a reality in the process industry—and why now is the right time to get started.
What does the "X" in GAIA-X, Manufacturing-X, and Process-X stand for? Originally, the focus was probably on "eXchange," i.e., the idea of sharing information. In view of a 20% decline in production the German chemical industry has been facing since 2021, something else would make sense: the “X” of the tech industry in Silicon Valley, i.e., the idea of "moonshot thinking" of radical innovation and scaling by "10X".
These are big words that seem to completely ignore technical and financial realities. However, there is a good reason for optimism: decades of intensive collaboration between a number of important user, manufacturer, and standardization organizations have made the increasingly automated integration of devices, systems, processes, and applications possible within and outside of core industrial processes, providing a solid foundation for a real digital revolution in the process industry.
NOA as the basis for secure OT/IT data exchange
NAMUR Open Architecture (NOA) is a concept that was introduced in 2016 and has been continuously developed since then. It allows IT applications to securely access data from process control systems, i.e., the heart of chemical, petrochemical, and pharmaceutical production, without compromising the integrity of the control systems. NOA separates the classic automation domain from a new monitoring and optimization domain (M+O), which is more closely associated with the IT and Io world.
A central element is the use of PA-DIM (Process Automation Device Information

The combination of technologies such as NOA, AAS, and standardized information models forms the technical and semantic basis for the scalable digitalization of the process industry. It allows for lower CO2 emissions, reduced energy consumption, and the conservation of resources in addition to the smart compliance with regulatory requirements.
Model) as an implementation of the NOA information model. It permits a semantically standardized description of the most important field device data based on OPC UA—a game changer for interoperability and the result of collaboration between the FDT Group, FieldComm Group, ISA 100 WCI, NAMUR, ODVA, OPC Foundation, PROFIBUS and PROFINET International, VDMA, and ZVEI.
NOA for greenfield and brownfield NOA makes two things possible: in new installations (greenfield), which increasingly rely on modern technologies such as the modular approach (Module Type Package, MTP) and field devices based on Ethernet APL, the significantly faster exchange of larger amounts of data can extend to the M+O domain. In existing plants (brownfield), process data can be easily and
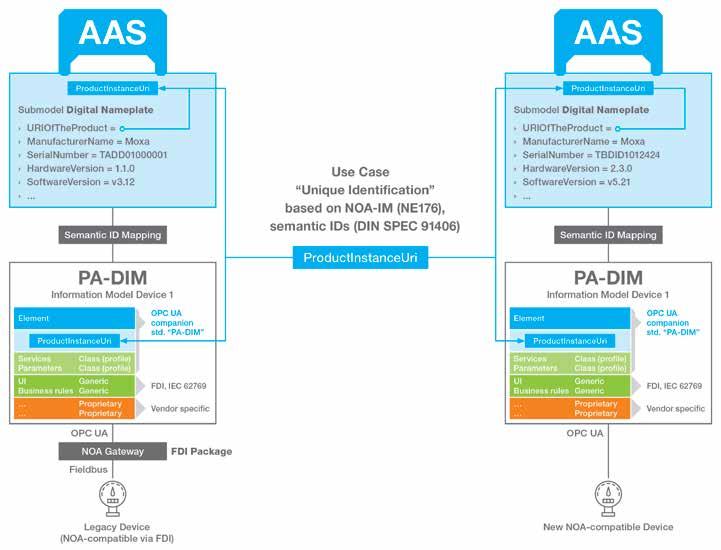
securely extracted from the core process automation and thus used for monitoring and optimization applications outside the process control systems. In a pilot project at the Höchst Industrial Park, an existing plant is currently being made "NOA-capable" thanks to 4-to-20mA-based field devices that can transmit data externally via the NOA channel with minimal effort using HART, PROFIBUS, and a NOA gateway. This is part of the ongoing NOA implementation project, a collaboration between NAMUR and ZVEI. The results will be presented at NAMUR’s general meeting in November 2025.
Process-X: automated digital collaboration between companies
If NOA is now accelerating the digital transformation within a manufacturing company, what could be achieved if companies in the entire supply chain could collaborate digitally in an automated way?
ZVEI presented a groundbreaking example at this year's Hannover Messe: the "Predictive Steam Production" use case from NAMUR's Process-X initiative. By intelligently
networking energy companies, the operator of the industrial park, and the various users of process heat on site, the available energy on the one hand and the required process heat on the other can be reconciled in advance. This saves CO2 emissions and costs.
Data spaces provide a trustworthy environment and form the basis for this cross-company digital collaboration. Here, companies can share information confidently, securely, and in a standardized way while retaining full control over their data. This means that data is not stored centrally in a cloud, but exchanged directly between companies—without the firms involved having to develop the necessary infrastructure themselves. The first data room providers have become established, e.g., Cofinity-X for the Catena-X initiative in the automotive industry. But even without an established data room provider, companies in the process industry can and should create the conditions for automated cross-company data sharing internally. In addition to NOA, this can be achieved by an administration shell infrastructure with semantic anchoring
of the parameters.
The asset administration shell
The asset administration shell (AAS) was and is being developed as a digital twin or digital administration shell for industrial assets as part of a collaboration between the Industry 4.0 platform and a large number of research institutions, industry partners, and standardization bodies. The Industrial Digital Twin Association (IDTA) coordinates the description of the AAS itself and the creation of so-called submodels for the AAS, which ensure the interoperability of data for specific use cases. A good example is ZVEI's submodel "Digital Nameplate for Industrial Equipment," which is also used in the KI-sy Twin project. The AAS is a digital container for all relevant information about an asset—divided into submodels. It is modular, machine-readable, and based on standardized submodels. Like the NOA information model PA-DIM, it uses semantic IDs such as IEC CDD (Common Data Dictionary) or eCl@ss to uniquely describe data, and can use established formats such as JSON, XML, and OPC UA. This makes
NOA connects field devices to their Asset Administration Shell via Semantic IDs.
Expansion of existing approaches as a basis for the efficient and flexible implementation of Industry 4.0 in the process industry
• Complementary (additive) to the existing structure
• Open to new approaches within Industry 4.0
• Based on existing standards
• Easy integration of rapidly changing IT components from the field to the enterprise level
• Significantly reduce cost of information through open, scalable and integrative approaches
• No risk to the availability and security of the installed base
it ideal for securely extracting data that previously existed in process control systems but could not be accessed externally without considerable effort as NOA data from the automation pyramid and then exchanging it across companies via the AAS—without translations or manual data mapping.
KI-sy Twin project: end-to-end communication from field to cloud
In the KI-sy Twin project, Fraunhofer IFF and IOSB-INA, together with partners from industry, are creating a new mobile demonstrator for digitalization. Real industrial hardware in a mobile demonstrator (see photo) is brought together with machine learning models, AAS and data space technology in a production-like system. The AAS is the key interface.
The information from the industrial sensors and field devices that are part of the control system and from newly added sensors is transferred to the PA-DIM format and mapped to the AAS via a NOA gateway. For components where this cannot be done automatically, or as an additional comparison, the AASs of the components are created with the help of large language models (LLM). These are also used to map the plant structure as an AAS. All components are integrated in a securitycompliant way with an IEC 62443-certified firewall from Moxa. The architecture of the demo plant is based on the NOA security concept.
Based on this digital image, productionrelated systems such as CAE, ERP, and Datahub are connected. If changes are made to the AAS, e.g., due to the replacement of a device, these systems are notified. The systems then decide for themselves to what extent the user needs to be involved or whether the changes can be applied automatically. Sven Schiffner from the Fraunhofer Institute for Factory Operation and Automation IFF in Magdeburg explains: "Based on the planned implementations in the project, it is easy to use digital tools even in existing plants.
Plant operators can deploy valuable human resources more efficiently and collect additional data easily by integrating new sensors. We are creating a language that all systems speak, the AAS." At NAMUR's general meeting in November 2025, the project participants will present challenges and best practices, providing valuable tips for similar projects. The demonstrator will be shown here, and participants will have the opportunity to try it out for themselves.
Security as an enabler
A well-thought-out security concept is an absolute must for the digital transformation of the process industry. Before NOA, opening up the automation pyramid was unheard of. With a solid security concept for NOA and the integration of AASs, cross-company digital cooperation via data spaces can become a reality – without incalculable risks for
production.
Conclusion and outlook
The combination of technologies such as NOA, AAS, and standardized information models forms the technical and semantic basis for the scalable digitalization of the process industry. It allows for lower CO2 emissions, reduced energy consumption, and the conservation of resources in addition to the smart compliance with regulatory requirements. It also provides employees with a platform for the automated sharing of data, knowledge, and innovations, which can significantly increase productivity. This is a historic opportunity for the German process industry—from chemicals and petrochemicals to pharmaceuticals to food production. In Europe, and especially in Germany, there is an ecosystem of associations, research institutions, and companies as well as a network of experts who are making remarkable efforts to develop new standards and technologies together that set global benchmarks.
Standardization and implementation still require a little more moonshot thinking. This means that everyone can look forward with great anticipation to the VCI's 2030 economic report.
Technology article by Moxa Europe.
The NAMUR Open Architecture (NOA) aims to make production data easily and securely usable for plant and asset monitoring as well as optimization. Smart sensors, field devices, mobile devices and the widespread use of IT equipment are generating more and more data that is often difficult to access within the classic NAMUR automation pyramid.
How IT/OT convergence increases network vulnerabilities
This article debunks the myth of IT/OT convergence as an effective manufacturing strategy, and explains why IT and OT should be prioritizing cooperation rather than convergence to protect both operational safety and business continuity.
THE MYTH THAT IT/OT CONVERGENCE IS an effective strategy for manufacturing management is widespread throughout the automation industry. This misconception gained popularity over the last twenty years as Factory Floor systems increasingly deployed Ethernet technology. Given that IT systems inherently rely on Ethernet, a fundamentally flawed idea took root: the merging of the two organizations.
This article debunks the myth of IT/OT convergence as an effective manufacturing strategy and explains why IT and OT should be prioritizing cooperation rather than convergence to protect both operational safety and business continuity.
“Two peoples divided by a common technology”
The George Bernard Shaw phrase describing America and England as "two nations divided by a common language" can be restated to describe how IT and OT are two organizations divided by a common technology. Both organizations use Ethernet but operate it differently.
Large messages & Scheduled Transactions
User (office worker)
Small continuous packets in Real Time
User (plant resource) responsible for not responsible for equipment equipment
Limited Switch Hierarchy
Multi-tiered switch hierarchy
Figure 1 – Enterprise IT networks tend to be flat. Production Networks are hierarchical as in this example of an eight Level production network in the lumber industry.
Additionally, the priorities of the organizations are different. Enterprise IT prioritizes confidentiality, integrity and availability. OT prioritizes availability, integrity and confidentiality. Where downtime is often a nuisance in enterprise IT systems, downtime is critical and costly in a factory floor OT system. It is not uncommon for downtime costs to reach a million dollars per hour in critical factory floor systems.
IT and OT systems are different
Enterprise IT systems can be characterized as an unknown number of users every day, using an unknown number of applications connecting to various and unknown URLs on the Internet, executing applications and downloading unknown numbers and types of files. That creates a very challenging environment for Enterprise IT security specialists. It can be further characterized by a distinct separation between the enterprise network and the user applications. The enterprise network can exist without the user applications. User applications can often exist without a network connection.
Cybersecurity threats in this environment include malware, phishing, ransomware and other threats leading to data breaches, financial losses, and disruptions of services.
Factory floor OT systems can be characterized by having a fixed number of users, using a fixed and well-known number of applications, and connecting to a fixed and well-known number of devices of known type and manufacture.
The factory network, combined with a control application, forms a production system. Neither the network or the control application can exist without the other. While cybersecurity threats to factory floor systems can also include data theft, sabotage and intentional or unintentional data leaks from insiders possessing legitimate access, the consequences of failure are fundamentally different.
An IT security breach may result in financial loss or data theft. An OT security failure can kill people. When a safety system gets compromised, when a pressure vessel's controls are manipulated, when emergency shutdown systems are disabled - workers die. Equipment worth millions can be destroyed in seconds. Every security decision in OT must be evaluated through this lens: will this change increase the risk to human life or catastrophic equipment failure?"
The number one threat to factory floor systems is the enterprise IT network. There are very limited opportunities for an attacker to reach an OT control network from anywhere but the enterprise IT network.
This isn't hyperbole - a Fortinet study found that 75% of OT organizations experienced at least one intrusion in the past year, while Rockwell Automation's 'Anatomy of 100+ Cybersecurity Incidents in Industrial Operations' found that 80% of OT attacks pivot from IT networks.

IT/OT convergence makes this problem worse
This converged threat is compounded when enterprise IT attempts to impose its policies without understanding OT requirements. Restrictive IT policies applied to OT environments directly cause shadow IT in manufacturing: operators forced to choose between following policy and keeping production running creating workarounds that bypass security controls entirely.
Combining two organizations with different goals, applications, and operating philosophies is akin to merging basketball and football teams. Both want to win games, but what’s important to them and how they move a ball around a playing field is completely different.
Personnel from each organization are skilled in the application of Ethernet, but the particular methods they use to meet their organization’s objectives are different: how they solve problems, the training they need and the focus they have and the tools they use are all different.
This is nowhere more apparent than in the choice of cybersecurity tools. IT cybersecurity tools are designed for flat networks and focus on ransomware, malware, phishing, social engineering, insider threats, data breaches, DDoS attacks, supply chain attacks, thirdparty exposure, and vulnerabilities in cloud and IoT devices. OT networks require no such complicated cybersecurity tools. In fact, many enterprise IT cybersecurity tools are all but useless in OT systems with five, six or even seven hierarchical layers of switches.
OT threats are principally from the enterprise IT network. OT cybersecurity requires a fundamentally different approach, as the users, applications, devices and messages never vary. This predictability enables denyby-default systems, such as the Dynics ICS Defender (https://dynics.com/cybersecurity/ ics360defender/), which explicitly define
allowed communications and block everything else.
SOURCE: REAL-TIME
The key distinction is that effective OT security tools are designed for deterministic environments with known users, applications and traffic patterns - not the unpredictable chaos of enterprise networks. Yet most vendors still push rebranded IT solutions.
Cooperation not convergence is needed
Over the past two decades, boosters have cited the widespread adoption of Ethernet and TCP/ IP on the plant floor as proof that a full-scale amalgamation of IT and OT is both inevitable and beneficial. The logic is seductively simple: shared protocols imply shared management. Yet protocols alone cannot erase the profound differences in mission, lifecycle, and risk posture that separate corporate networks from production lines.
Unfortunately, the reality is less a seamless fusion and more akin to forcing a cat and a Roomba to cooperate simply because they both occupy the floor. Treating them as a single domain threatens both cybersecurity and operational resilience.
Instead of that full-scale amalgamation of IT and OT, a forward-leaning alternative is required: disciplined cooperation. Unfortunately, this is often not the case. The enterprise IT organization often imposes requirements that hinder the OT organization from achieving its goals of availability, integrity and confidentiality, failing to recognize that overly restrictive policies drive the very shadow IT behaviors they seek to prevent.
The mission of OT must be respected. The OT organization must have the authority to choose the architecture, equipment and tools that meet the particular requirements of the production systems they operate and maintain.
However, with this authority comes responsibility. When IT defines specific data requirements from production systems, OT must be prepared to deliver. Meeting these requirements means establishing clear levels of service - defining what the network can reliably provide and committing to those specifications.
This requires OT organizations to have the expertise and tools to implement network architectures that satisfy both production needs and agreed-upon service expectations.
By embracing boundary - respecting cooperation, shared vernaculars, and mutual commitments to defined service levels, organizations can harvest the agility they crave without sacrificing the deterministic performance and safety their factories demand.
John Rinaldi, Chief Strategist, Real Time Automation; and River Caudle, Chief Strategy Officer, River Risk Partners. Learn More
Figure 2 - ICS Defender
Harnessing the power of OT networking
As the industrial landscape continues to evolve, the convergence of IT and OT represents a fundamental shift in industrial networking. Therefore, the ability to leverage the full potential of OT networking becomes increasingly critical to operational success. The overarching goal is seamless IT/OT integration.

WITH NEW TECHNOLOGIES EMERGING ALMOST every day, the industrial landscape is changing fast. Businesses are increasingly embracing IT/ OT convergence to stay ahead and capitalize on advantages such as smarter factories and higher efficiency. What is the engine powering this transformation? OT networking.
Think of OT networking as the all-important wiring that connects everything in an industrial setup. But moving from the old, isolated OT systems to the new, open and interconnected infrastructure is like swapping out your old flip phone for a top-of-the-line smartphone – cool, but also kind of complicated.
Whenever a critical network connection fails, it could cost thousands in downtime every minute or put public safety at risk. That’s why taking full advantage of OT networking is no longer optional. This article provides practical insights and guidance to help you navigate these challenges effectively.
Facing the OT Security Surge
The threat landscape for operational technology has dramatically intensified in
recent years. Only a few years ago, in 2021, a hacker attacked a water treatment facility in Oldsmar, Florida, attempting to increase sodium hydroxide levels in the public water supply to dangerous concentrations. This attack illustrates how OT security breaches can directly threaten public safety and critical infrastructure.
Even more concerning, ransomware groups have increasingly targeted industrial entities, with 65% of manufacturing organizations falling victim to ransomware attacks in 2024 alone—a sharp increase from 56% the previous year. Some attacks have resulted in complete operational shutdowns, causing significant economic damage and disrupting essential services.
Unlike IT environments, OT networks present unique security challenges:
• Operational continuity: In OT, uptime is everything. Security solutions cannot compromise the 24/7 availability demands of industrial processes.
• Legacy systems: Many industrial environments operate decades-old equipment that wasn't designed
with security in mind, making them vulnerable to modern cyber threats.
• Real-time performance: Security measures should not interfere with time-sensitive control communications.
These challenges make conventional IT security approaches inadequate. When evaluating security solutions for OT environments, it’s important to choose solutions that can adapt to the unique operational requirements and risk profiles of industrial networks.
A comprehensive defense-in-depth security strategy is your best defense against threats targeting your OT infrastructure. While most modern OT solutions provide security features, looking for OT-tailored solutions that meet the rigorous requirements of internationally recognized security standards such as IEC 62443 can boost the overall security of your network. Though, having secure devices alone isn’t enough. Other measures such as network segmentation to keep critical equipment isolated from more risk-prone devices, and real-time visibility
Figure 1 – Enterprise IT networks tend to be flat. Production networks are hierarchical.

of your OT network to quickly identify issues and threats, provide an additional layer of security for your operations.
Lacking Real-time Precision? Enhance Industrial Control and Synchronization With TSN
Beyond security, modern industrial applications are also driving the need for greater precision and synchronization in OT networks. Picture a manufacturing line where multiple robotic arms must perform coordinated movements with microsecond precision. Traditional Ethernet cannot guarantee the consistent timing required for such synchronized operations. This is where time-sensitive networking (TSN) comes in.
But
what exactly is TSN?
TSN is a set of next-generation IEEE 802.1 networking standards that enable deterministic communication over standard Ethernet infrastructure. In essence, TSN ensures that critical data is always delivered at guaranteed times with minimal latency, even in congested networks.
To better illustrate the capabilities of TSN, let’s take a prominent home appliance manufacturer’s case as an example. Using TSN solutions, the manufacturer achieved better synchronization between robots, reduced changeover times in production lines, and a significant increase in overall productivity.
This case demonstrates how TSN exceeds the limitations of traditional networking to provide new capabilities and opportunities for innovation.
Reducing Complexity and Minimizing Costs: Efficient OT Connectivity
Designing, deploying, and maintaining modern OT networks can be complex and costly. On top of that, OT engineers must deal with harsh environmental conditions, integration complexities, and demanding reliability requirements— all while managing costs and planning for future growth.
Challenging OT Environments
Conditions in industrial facilities are often harsh, facing extreme temperatures and high levels of vibration, electromagnetic interference (EMI), dust, and humidity. Industrial-grade hardware is specifically engineered for these environments. OT network planners should seek out robust hardware solutions that are designed for maximum reliability and uptime, minimizing the risk of failures and reducing the need for frequent replacements.
IT/OT Integration Complexities
The rapid growth of IT/OT converged applications is introducing countless numbers of sensors and machines into industrial networks, leading to even more data exchanges. However, OT networks often rely on a mix of legacy protocols and newer technologies, creating interoperability issues. If that wasn’t enough, installing new devices in already crowded control cabinets adds another layer of complexity.
To ensure optimal flexibility while taking future expansions into account, network planners should prioritize network devices with a smaller form factor that can be easily added to the existing infrastructure. Another important feature to consider is protocol compatibility. Choosing devices with multiprotocol support means easier integration with both legacy and modern industrial equipment. Lastly, Power over Ethernet (PoE) capabilities can help streamline device connectivity and power distribution across OT networks.
PoE-capable switches can power compatible end devices such as IP cameras or access points. This not only simplifies wiring efforts but also provides additional flexibility when adding more end devices to the network later down the line.
High Maintenance Costs
Unplanned downtime is any OT engineer’s nightmare. Just a brief unexpected interruption can lead to significant production losses and costly maintenance.
Troubleshooting network issues in a complex industrial environment is also often timeconsuming and labor-intensive.
To keep operations going 24/7, it’s important to invest in redundancy. Network devices with robust redundancy features such as backup power and embedded redundancy functions to ensure data continuity are the bedrock of any reliable OT network. If something does go wrong, having access to user-friendly centralized management tools also helps engineers quickly identify and troubleshoot network issues from anywhere to keep downtime to an absolute minimum.
Navigating the Future of OT Networking
As the industrial landscape continues to evolve, the convergence of IT and OT represents a fundamental shift in industrial networking. Therefore, the ability to leverage the full potential of OT networking becomes increasingly critical to operational success. The challenges we've explored—security vulnerabilities, real-time performance requirements, and network complexity— represent both obstacles and opportunities for forward-thinking organizations.
Moxa's industrial networking portfolio has solutions to help overcome OT challenges, including industrial cybersecurity, real-time communication, network integration, and maintenance. To learn more, visit the microsite by clicking on the link below.
Technology article by Moxa.
Learn More
Additional Resources
• https://www.foley.com/insights/ publications/2024/09/cybersecurityindustry- 4-part-1/
• https://www.moxa.com/en/ case-studies/automating-home-appliancemanufacturing-with-tsn-technology
A comprehensive defense-in-depth security strategy is your best defense against threats targeting your OT infrastructure.
IT/OT convergence for edge and cloud for industrial customers
Collaboration to advance data management, AI and generative AI capabilities. Integration of shop floor data is made available via Siemens Industrial Edge and IT data in the Snowflake AI Data Cloud.

SIEMENS IS COLLABORATING WITH SNOWFLAKE, the AI Data Cloud company, to help manufacturers unlock operational efficiency, scale and AI-driven insights. The collaboration enables mutual customers across the globe to connect their operational technology (OT) data from the shop floor with information technology (IT) data, such as supply chain management and financial data.
By connecting Siemens Industrial Edge and Snowflake’s AI Data Cloud, manufacturers can access plug-and-play Industrial Edge applications to contextualize and transfer OT data into IT systems. This integration empowers customers to build a robust data foundation, which is the prerequisite for gaining deeper insights, improving machine performance, increasing machine availability and optimizing production processes across their facilities.
“This collaboration brings together the best of both worlds,” said Rainer Brehm, CEO of Factory Automation at Siemens. “Siemens has deep expertise in how to bring OT and IT together on the shop floor, while Snowflake excels in managing and analyzing both large-scale OT and IT data. Together, we enable customers to bridge the IT/OT divide and scale their digital
transformation across machines, lines, and factories.”
“Together with Siemens, we’re enabling manufacturers to harness the full potential of their data through Snowflake’s easy, connected and trusted platform,” said Christian Kleinerman, EVP of Product at Snowflake. “The ability to apply AI across both IT and OT data isn't just an advancement; it unlocks a new reality of possibilities for unparalleled quality improvement and radical performance optimization, as well as new ways of process automation powered by AI agents.”
FFT bridges factory data from edge to cloud
FFT, a leading global provider of innovative, flexible and complex manufacturing systems, leverages the Siemens Industrial Edge ecosystem and helps manufacturers to securely, scalably, and efficiently transfer production data into the Snowflake AI Data Cloud through its DataBridge app. This solution is already implemented within FFT’s own production lines and facilities, demonstrating its capability to meet the highest standards of efficiency and data-
driven optimization. The Siemens-Snowflake collaboration supports FFT’s role as an integrator and trusted Snowflake partner for automated and flexible production systems across the mobility and industrial sectors. It also underscores FFT’s status as a Siemens Xcelerator partner.
This joint solution, for production managers, data engineers, and IT leaders, tackles common challenges such as data silos, limited transparency, and inefficient analytics. Siemens Industrial Edge enables seamless integration of OT data by connecting to sources including PLCs, sensors, and manufacturing systems. It aso pre-processes data at the edge and runs transformed OT data models, like AI models, in closed-loop with production automation.
Snowflake’s platform then delivers actionable insights through AI-powered analytics and agentic AI capabilities. The result is a measurable boost in operational efficiency, with higher machine performance, enhanced product quality, and reduced maintenance needs.
Technology article by Siemens.
Learn More
By connecting Siemens Industrial Edge and Snowflake’s AI Data Cloud, manufacturers can access plug-and-play Industrial Edge applications to contextualize and transfer OT data into IT systems (Source: Siemens).
2025 Corporate Profiles

Learn about the companies and technologies shaping the future of Industrial Ethernet, the IIoT and Industry 4.0.

Beckhoff Automation: New Automation Technology
Beckhoff implements open automation systems using proven PC-based control technology. The main areas that the product range covers are industrial PCs, I/O and fieldbus components, drive technology, automation software, control cabinet-free automation, and hardware for machine vision.

PRODUCT RANGES THAT CAN BE USED AS separate components or integrated into a complete and mutually compatible control system are available for all sectors from Beckhoff Automation. New Automation Technology stands for universal and industryindependent control and automation solutions that are used worldwide in a large variety of different applications, ranging from CNC-controlled machine tools to intelligent building control.
PC-based control technology
Since Beckhoff’s foundation in 1980, the development of innovative products and solutions on the basis of PC-based control technology has been the foundation of the company's continued success. We recognized many standards in automation technology that are taken for granted today at an early stage and successfully introduced to the market as innovations. Beckhoff’s philosophy of PC-based control as well as the invention of the Lightbus system and TwinCAT automation software are milestones in automation technology and have proven themselves as powerful alternatives to traditional control technology. EtherCAT, the real-time Ethernet solution, provides a powerful and future-oriented technology for a new generation of control concepts.
Worldwide presence on all continents
The corporate headquarters of Beckhoff Automation GmbH & Co. KG in Verl, Germany, is the site of the central departments such as development, production, administration, sales, marketing, support and service. Beckhoff’s presence in the international market is guaranteed by its subsidiaries. Beckhoff is represented in more than 75 countries by worldwide cooperation partners.
EtherCAT – the Ethernet Fieldbus
Selecting the communication technology is important: it determines whether the control performance will reach the field and which devices can be used. EtherCAT, the Industrial Ethernet technology invented by Beckhoff, makes machines and systems faster, simpler and more cost-effective. EtherCAT is regarded as the "Ethernet fieldbus" because it combines the advantages of Ethernet with the simplicity of classic fieldbus systems and avoids the complexity of IT technologies. The EtherCAT Technology Group (ETG), founded in 2003, makes it accessible to everyone. With over 8,000 member companies from 72 countries (as of February 2025), the ETG is the world's largest fieldbus user organization.
EtherCAT is an international IEC standard that not only stands for openness, but also for stability: until today, the specifications
have never been changed, but only extended compatibly. This means that current devices can be used in existing systems without any problems and without having to consider different versions. The extensions include Safety over EtherCAT for machine and personnel safety in the same network, and EtherCAT P for communication and supply voltage (2 x 24 V) on the same 4-wire cable. And also EtherCAT G/G10, which introduces higher transfer rates, while the existing EtherCAT equipment variety is integrated via the so called branch concept: even here there is no technology break.
Beckhoff Automation at a glance
• 2024 global sales: €1.17 billion
• Headquarters: Verl, Germany
• Managing owner: Hans Beckhoff
• Employees worldwide: 5,300 (FTE, March 2025)
• Engineers: 2,000
• Subsidiaries/representative offices worldwide: 41
• Sales offices in Germany: 23
• Representatives worldwide: >75
Beckhoff Automation GmbH & Co. KG info@beckhoff.com Phone: +49 5246 963-0
Visit Website
Enabling the Future of Industrial Networking
Moxa offers scalable, secure and reliable solutions that help enterprises strengthen their digital operations, drive IT/OT convergence and build future-proof industrial organizations.
WITH OVER 35 YEARS OF INDUSTRY EXPERIENCE , Moxa is a global leader in edge connectivity, industrial computing, and network infrastructure solutions that empower the Industrial Internet of Things (IIoT). The company has connected more than 111 million devices worldwide and serves customers in over 91 countries, delivering reliable networking solutions and unparalleled customer service.
Moxa introduced the world’s first IEC 62443 certified network appliance in the OT market and continues to advance OT security as a CVE Numbering Authority while helping customers respond to NIS2 requirements. Moxa’s approach integrates robust industrial networking with cuttingedge OT cybersecurity: security-hardened devices that meet IEC 62443-4-2, advanced network segmentation with proactive threat prevention, and customized OT deep packet inspection for effective industrial IPS.
Defense-in-Depth Network Security
Industrial control systems face rising cyber risk as connectivity grows. Moxa aligns product design and lifecycle practices with IEC 62443 to help operators apply multilayer protection across devices, cells, and sites. This secure-by-design foundation supports real-time visibility, segmentation, and rapid recovery to keep operations reliable.
Network Segmentation
Create zones and conduits that reflect how operations run. Moxa’s EDR-G9010 Series industrial secure routers and EDS-4000/G4000 Series industrial managed Ethernet switches enable segmentation at Layer 2 and Layer 3 using VLANs, ACLs, and routing. Administrators can restrict access by VLAN ID or MAC address and control traffic by IP and ports. Policy firewalls and NAT establish conduits between zones and help shield internal addressing. OT DPI validates industrial traffic, so only approved content moves between production cells. The result is a reduced blast radius, clearer responsibilities, and simpler control across plants and sites.
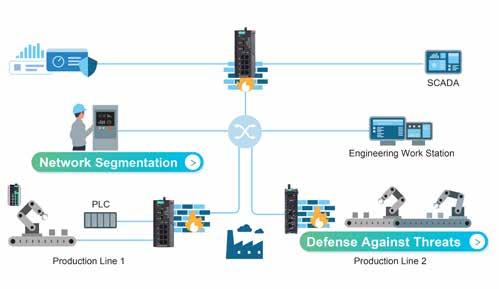
Simplified Industrial Network Management
Effective management is essential for resilience. MXview One provides unified monitoring, diagnostics, and change control across wired, wireless, and IEC 61850 substation networks. Role-based access, topology views, baselines, and log collection give lean OT teams the context to act early and support audit readiness for programs such as NIS2.
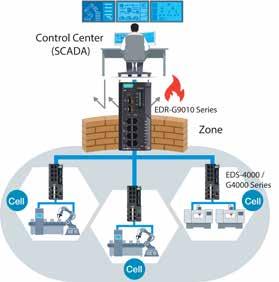

Delivering Lasting Business Value
Moxa empowers industries with secure and reliable networking solutions that support continuous operations. By combining ruggedized hardware, software with long-term support, and proven cybersecurity practices, Moxa helps businesses stay competitive, secure, and ready for the future.
Moxa GmbH
Website: moxa-europe.com/solutions/ ot-cybersecurity Email: europe@moxa.com Visit Website
Segment the network and block threats to keep industrial operations online.
Opto 22: Your Edge in Automation
READY TO CONNECT AUTOMATION, ENTERPRISE, and cloud data? Opto 22’s groov family of industrial edge controllers and I/O gives you the integrated control, connectivity, and cybersecurity tools to do it.
With groov EPIC and groov RIO, you can bring brownfield systems into the next generation of industrial automation.
Create cohesive OT data systems from multi-vendor networks with OPC UA, MQTT, and more.
Secure PLC, I/O, and equipment data with built-in cybersecurity features like encryption, mandatory user authentication, and configurable device firewalls.
And you can collect, process, and publish OT data where it’s needed, into on-premises and cloud-based applications like databases, CMMS, SCADA, and ERP.
Control and I/O options at the edge For groov EPIC, develop real-time control programs in a language you know: ladder logic, function block diagram, flowcharts, Python, C/C++, and more. Build HMI screens for embedded or external touchscreens, PCs, and mobile devices. Run Inductive Automation’s Ignition Edge on the EPIC programmable industrial controller.
groov RIO edge I/O combines security,

software-configurable I/O, embedded software, and even CODESYS control programming in a single compact edge device.
Why choose groov?
Built on Opto 22’s over 50 years of experience, groov products are backed by lifetime guarantees on solidstate I/O, UL Hazardous Locations approval, ATEX compliance, and a wide -20 to 70°C operating temperature range.

Count on free pre-sales engineering help and product support as well. All Opto 22 products are developed, manufactured, and supported in the U.S.A.
Contact our engineers today, and let’s talk about what you want to do.
An edge programmable industrial controller, groov EPIC® is much more than a PLC or a PAC. It can secure and simplify automation and IIoT projects, while reducing cost and complexity.
Contemporary Controls: Your Trusted Partner
Providing innovative and reliable solutions to the industrial automation industry for more than 50 years, Contemporary Controls has been a leader in innovative solutions for industrial automation.
WITH MORE THAN 50 YEARS OF experience, Contemporary Controls has been a leader in innovative solutions for industrial automation. Contemporary Controls’ CTRLink products are designed for unattended operation in environments not conducive to office-grade equipment.
The products provide convenient DIN-rail mounting in control panels, 24 VAC/DC power, UL 508, improved EMC compliance and reliability. Contemporary Controls’ repeating hub, switches, media converters and IP routers adhere to IEEE 802.3 standards and more. Specialty regulatory needs are addressed in selected models.
Rugged Ethernet Switches
Whatever the Ethernet infrastructure need, a solution is available from CTRLink products. For simple systems, plug-and-play unmanaged switches provide a cost-effective method for expanding Ethernet networks. Most models include features such as auto-MDIX and autonegotiation. For demanding applications, managed switches provide features such as VLANs, SNMP, Quality of Service, port security, port mirroring, alarming and cable redundancy.
Innovative Diagnostic Switches
For troubleshooting, diagnostic switches allows a network sniffer to attach to an unused port on a switch and observe all traffic on the network.
Cost-Effective, Trusted IP Routers
Contemporary Controls’ Skorpion series of IP routers ease the integration of new machines into the existing network. Each machine consisting of multiple IP devices

SOURCE: CONTEMPORARY CONTROLS
SOURCE: CONTEMPORARY CONTROLS
connects to the LAN side while keeping the same IP settings for the devices and the application, lowering installation cost and eliminating trouble shooting.
The IP address for the WAN port on the IP router is the only setting that requires modification allowing multiple machines to reuse the same configuration on the LAN side. Skorpion routers have been successfully used in Robotics, Automated Guided Vehicles (AGVs), Packaging and Scientific Equipment.
Simplified, Secure Remote Communication
Utilizing the EIPR/EIGR series VPN routers, Contemporary Controls offers three VPN solutions that deliver secure, remote access—RemoteVPN subscription service, and Self-HostedVPN and BridgeVPN solutions. Hosted on the Internet and maintained by Contemporary Controls, RemoteVPN provides secure communication and the convenience of remote access without having to maintain a VPN server.
Contemporary Controls’ Self-HostedVPN and BridgeVPN solutions allow users to set up and maintain their own secure remote access without subscription fees and without the need for a cloud-based VPN server.
Solutions You Can Depend On
With automation systems, applications vary and can require a special product or need. Contemporary Controls has worked with OEMs in obtaining UL 864 compliance with some CTRLink switches and can help in other areas such as private-labeling, unique packaging or extreme environmental design.
Contemporary Controls’ customers are systems integrators, contractors and OEMs seeking simple, reliable networking and control products from a dependable source. With headquarters based in the US, Contemporary Controls also has operations in the UK, Germany and China and is well suited to fulfil your application needs.
Contemporary Controls www.ccontrols.com
Visit Website
Softing Industrial Machine and Device Connectivity
SOFTING INDUSTRIAL IS A LEADING PROVIDER of advanced and easy-to-use products and solutions for the digitalization and networking of industrial systems and processes. Our mission is to deliver secure, flexible, and scalable connectivity that helps customers unlock the full potential of their data. With Softing, manufacturers can increase production efficiency, integrate operations across OT and IT, and seamlessly connect to edge and cloud platforms.
Controller Connectivity - Scale Projects Faster, Cut Operating Cost
Our controller connectivity products simplify access to automation equipment from leading manufacturers, making it easier to scale projects and reduce operating costs. They provide a robust bridge between OT and IT, enabling industrial IoT applications for both brownfield and greenfield environments.
Connectivity for Field DevicesDiagnostics & Maintenance Efficiency
Softing’s software and hardware gateways provide direct access to HART, PROFIBUS, and other field device data. By integrating this information into Plant Asset Management applications, users can streamline commissioning, enhance maintenance efficiency, and improve diagnostics.
OPC UA Unified Name Space - Data Consistency Across the Plant
We help customers implement a single source of truth through the OPC UA Unified Name Space

(UNS). This ensures consistent and structured data across the enterprise, making it readily available for SCADA, MES, ERP, and other higher-level applications.
CNC Machine Connectivity - Secure Data from Legacy and Modern Machines
Our CNC solutions provide secure data access without altering machine configurations. This enables manufacturers to connect legacy and modern CNC assets to IoT and cloud applications quickly and reliably.
Embedded Ethernet & Ethernet-APL – Accelerate Product Development

and Extend Connectivity to the Field
Softing supports device manufacturers in embedding Industrial Ethernet and Ethernet-APL into their systems. We provide proven solutions for real-time Ethernet protocols, ensuring reliable and future-proof communication. Our flexible software stacks and integration services help accelerate development cycles and maintain market competitiveness.
By implementing Ethernet-APL, we enable process automation networks to extend Ethernet connectivity right down to the field level, supporting faster data access, simplified architectures, and greater transparency in harsh environments.
Driving Digital Transformation –Future-Proof Industrial Operations
With Softing Industrial, you gain a trusted partner committed to advancing your connectivity strategy. Our solutions enable:
• Optimized data exchange
• Seamless OT/IT integration
• Resilient and scalable industrial networks Empowering your digital transformation and preparing your operations for the future.
Softing Industrial Automation GmbH
Email: info.automation@softing.com
Seamless OT-IT Integration Drives Data-Driven Insights for Optimized Processes.
German Engineering for your Automation
For more than 40 years, W&T has been designing networking & automation components that make people’s work easier - so they can focus on what really matters.
HEADQUARTERED IN WUPPERTAL, GERMANY, Wiesemann & Theis offers a wide range of components for industrial ethernet communication.They stand out through German precision engineering and manufacturing as well as the most dedicated and proficient customer support.
Durable Devices for Any Application
What is most disruptive in any kind of process, may it be industrial automation, building technology or IT/OT security? When something does not work and needs to be fixed. Therefore, our primary goal is to offer components that are durable, robust, and always functional. We achieve this goal through highly qualified designing, precise manufacturing, high testing requirements and the continuous development of our products in close cooperation with our customers.
W&T reliable hardware comes with all necessary industry standards, from classical Ethernet to Single Pair Ethernet, from MQTT to OPC UA, Modbus/TCP, and other common protocols.Thanks to simple commissioning and integration as well as user-friendly interfaces, components are quickly ready for their, literally, lifelong use.
Our aim is to enable reliable access, secure data transfer, and flexible network integration — optimized for use cases in energy management, access control, traffic infrastructure, mechanical engineering and any IIoT application. As different as they may be from each other, all of these industries

W&T components include IO and sensor modules, serial and USB device servers and edge computing platforms.
have in common that they require secure and seamless data communication and often enough very individual, customized solutions.
Since 1979. IIoT, Retrofitting and Customized Solutions
W&T did not start out with IIoT components like web sensors and IO modules. In the beginning there were simple, yet revolutionary printer interfaces and switches. These made it possible to use document printers simultaneously from multiple workstations and allowed printers to be integrated into commercial networks regardless of

SOURCE: WIESEMANN & THEIS
manufacturer or built-in interface. What seems completely natural today, was quite progressive at the time and made W&T the market leader for printer interfaces in the 1980s.
To this day, W&T has remained true to its basic idea of offering devices and services that make customers' work a little easier: with W&T, devices, machines, and systems can be supplemented, networked, and modernized in a way that is simple, flexible, and sustainable.
One of our key technologies has always been industrial retrofitting, which for example with the help of serial device servers catapults wellestablished, powerful machines into the age of the Industrie 4.0. Our Com Servers remain among the most popular products because they prevent older production machines and other devices from having to be replaced at a great expense.
Besides the wide range of IoT components, including the first Single Pair Ethernet components, a growing focus is on development services for both software and hardware in the areas of automation, switching, reporting and connecting all kinds of data points.
Wiesemann & Theis
www.wut.de
Email: info@wut.de
Phone: +49 202 26 80 0
Visit Website
Reliable products from reliable people: Michael Fazenda (Sales Manager), Tobias Theis (CEO) and Patrick Knabe (Technical Sales Manager)
Rugged instrumentation for reliable measurement and control
Moore Industries is a world leader in the design and manufacture of exceptionally rugged, reliable and highquality field and DIN rail-mounted instrumentation for the process monitoring and control industries.
MOORE INDUSTRIES WORLDWIDE SALES AND support offices provide first rate customer service and solutions for the chemical, petrochemical, utilities, petroleum extraction, refining, pulp and paper, food and beverage, mining and metal refining, pharmaceuticals, and biotechnology industries.
IIoT Solutions built to Deliver Field Data to your Host Systems
HART and MODBUS industrial communication protocols have dramatically increased access to device and process information that allows you to make more effective operational process decisions. Our Remote I/O systems, including the NCS Net concentrator System® and HART gateways and converters such as the HES HART to Ethernet Gateway System with HART Tunneling and the HCS HART to MODBUS Converter, help integrate valuable data into your monitoring and control system strategy.
Instrument Panels and Systems Engineering
Moore Industries can specify, procure, and assemble your multi-vendor electronic and pneumatic instrumentation/hardware into custom-built instrument panels, systems and enclosures. We will provide complete documentation, expert technical assistance, and the assurance that complete and thorough testing has been performed.
Complete Temperature Solutions
Moore Industries Universal PC-Programmable, Smart HART® Temperature Transmitters convert and send RTD or thermocouple signals ready for

direct interface with an indicator, recorder, PLC, DCS, or SCADA system. Temperature assemblies and measurement components include the WORM® flexible RTD and thermocouple sensors, connection heads and enclosures, thermowells and fittings. Our TCS Temperature Concentrator System now enables highdensity temperature monitoring over Ethernet, supporting more connections while providing precision measurements via HART, MODBUS RTU, MODBUS/TCP, and HART-IP, significantly reducing hardware, wiring, and installation costs.
Programmable Alarm Trips
Provide on/off control, warn of trouble, or provide emergency shutdown with one or more programmable alarm (relay) outputs when a monitored process signal falls outside

SOURCE: MOORE INDUSTRIES
of a selected high and/or low limit. Our SLA Multiloop and Multifunctional Safety Logic Solver and Alarm bridges the gap between single-loop logic solvers and costly safety PLCs. With up to 16 alarms and eight physical alarm outputs, simple and complex alarming strategies can be implemented. The SLA is SIL 3-capable, simple to program, and offers costeffective protection by reducing installation and engineering time.
Functional Safety Solutions
Our spectrum of SIL 2 and SIL 3 capable FS Functional Safety Series instruments include signal isolators and splitters, single and multi-loop alarm trips and logic solvers, temperature transmitters and more. Every instrument is built and approved for use in Safety Instrument Systems and is third-party certified by exida to IEC 61508 standards.
More Than 55 Years Designing and Manufacturing Rugged and Reliable Instruments
Moore Industries has been proudly serving the process instrumentation needs of global manufacturers and automation companies since 1968. Designing, building and supporting more than 170 products across 14 product lines with unmatched systems, support and services expertise.
Moore Industries-International www.miinet.com Email: info@miinet.com
Visit Website
HiveMQ: The Most Trusted IoT Data Streaming Platform
With a focus on reliability, scalability, and security, HiveMQ helps organizations get their data AI-ready— enabling advanced analytics, predictive maintenance and digital transformation.

SOURCE:
HiveMQ Swarm tests the reliability and scalability of deployments.
Build AI-Ready Data Backbone
HiveMQ prepares industrial data for analytics, industrial automation, predictive maintenance, and AI/ML applications by ensuring high-quality, governed, and secure data streaming from edge to cloud. HiveMQ Pulse Distributed Data Intelligence Platform helps standardize and govern data streams through Unified Namespace (UNS), so data becomes more reliable and AI-ready.
Real World Industrial Applications Where
HiveMQ
Delivers Value
HIVEMQ EMPOWERS BUSINESSES TO UNLOCK the full potential of their data with the most trusted edge-to-cloud IoT data streaming platform.
Built on MQTT’s publish/subscribe architecture for seamless and flexible integration across operational technology (OT) assets and information technology (IT) applications, HiveMQ ensures businesses can efficiently connect, stream, and govern their data in real-time. With a focus on reliability, scalability, and security, HiveMQ helps organizations get their data AI-ready—enabling advanced analytics, predictive maintenance, and digital transformation.
With HiveMQ, individual customers have achieved:
• $35M annual savings from a 20% reduction in energy usage
• $83M in savings by cutting production downtime by 40%
• $2M in savings through a 25% boost in workforce efficiency
Unlock the Value of Your Data
with HiveMQ
Securely collect, stream, and govern industrial data in real-time, from edge to cloud, for smarter decision-making.
Quickly Connect to Any Data Source
Power seamless connectivity across your enterprise with HiveMQ’s trusted MQTT platform. Easily connect any device using our open-source MQTT client libraries, bridge legacy industrial protocols to MQTT with HiveMQ Edge, and extend functionality with HiveMQ Extensions to integrate data into existing streaming services, databases, and IT systems.
Stream IoT Data in Real-time
Leverage HiveMQ MQTT Broker, the eventdriven messaging platform designed for fast, efficient, and reliable data movement between IoT devices and enterprise systems. 100% MQTT-compliant, it enables instant, bi-directional communication, ensuring seamless, real-time data exchange for automation, analytics, and AI-driven insights.
Govern Your IoT Data
Take control of your IoT data with advanced data management tools. The HiveMQ Control Center monitors the health of the system, while HiveMQ enterprise security features ensure robust protection. HiveMQ Data Hub enables validation, enforcement, and transformation of data in motion, and
Smart Manufacturing: Enables real-time data flow between OT and IT systems to reduce downtime, improve efficiency, and drive data-driven decisions.
Automotive: Powers connected car platforms and automotive manufacturing with reliable, secure data streaming to enhance connected vehicle experiences and optimize production.
Transportation & Logistics: Provides real-time fleet and supply chain visibility to streamline fleet management, improve service, and reduce costs.
Energy: Connects remote assets, optimizes operations, and supports energy transition initiatives through real-time insights.
Trusted by Global Leaders
Trusted by industry leaders like Audi, BMW, Liberty Global, Mercedes-Benz, Siemens, and Eli Lilly, HiveMQ helps organizations modernize operations, accelerate innovation, and deliver smarter, datadriven experiences.
HiveMQ GmbH Website: www.hivemq.com Visit Website
Secure and scalable data backbone built on MQTT.
HIVEMQ
Enabling CIP communication over Bluetooth for automation
This article explores the feasibility and potential of implementing Bluetooth Low Energy (BLE) for industrial automation by enabling Common Industrial Protocol (CIP) communications possibilities over BLE. It delves into the Bluetooth specifications, addressing aspects such as security, stability and technical specifications.
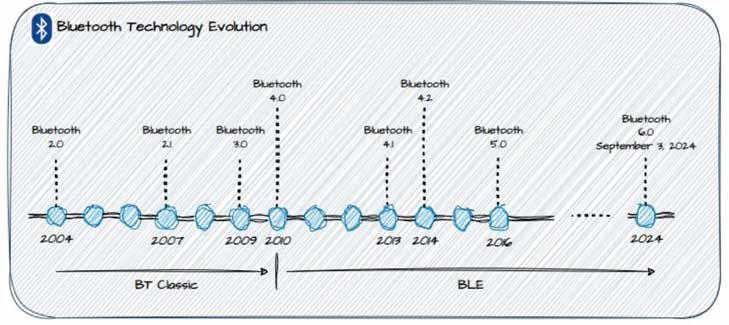
General Background – BlueTooth Evolution.
WIRELESS COMMUNICATION TECHNOLOGY IS becoming increasingly used in our daily lives and as such has found its way into industrial automation through a variety of mediums. Of these wireless technologies, Bluetooth is a respected technology for wireless communication in the consumer market due to its reliability, universal adoption, ease of use, and low cost.
Bluetooth is a key communication technology driver behind the Internet of Things and with the increased adoption and implementation of the Industrial Internet of Things, Bluetooth technology expands the communication selection in the industrial automation ecosystem.
This article aims to explore the potential for implementing Bluetooth for industrial use cases with CIP communications as the application layer interface for devices and software clients. It will examine the recent enhancements to the Bluetooth specifications that allow its potential use in the market, along with Bluetooth's security, stability, technical specifications, and the mapping of CIP onto Bluetooth transport with the exploration of implementing extensions of CIP onto Bluetooth. Additionally, feasibility by exploring use cases, industrial considerations, security at the application layer, and ODVA impact will be considered.
Introduction
Wireless technology as a medium represents 7% of the total market for industrial networks as of 2024 and has seen steady growth throughout the previous years. Bluetooth, specifically Bluetooth Low Energy (BLE) has proven to be a key technology for short range wireless applications due to its reliability, ease of use, and low cost. By implementing CIP communications over BLE, industrial devices may be enabled to communicate wirelessly while maintaining commonality and compatibility when communicating with the existing CIP-based systems in today’s market. The use cases in this article, reference utilizing CIP over BLE in a system including scenarios for the connected worker through smart devices such as phones, tablets, and sensors and IO mesh networks.
In the case of “the smart worker”, personnel can be locally present on the plant floor with a tablet or phone, already utilizing BLE while connected to the machine, panel or device through a BLE enabled access point and view diagnostics, read/write parameters, and perform troubleshooting and commissioning procedures. If the device or network of devices which a mobile client is already connecting to, is utilizing CIP for communications, providing data over a BLE transport in CIP formatting will allow
for a cohesive integration utilizing common familiar building blocks. Additionally, when commissioning the machine, there may arise a situation where a safe stop is needed in which case a virtual e-stop could be utilized on the application running on the mobile device by leveraging CIP Safety, thus completing CIP Safety over BLE.
Implementing BLE for sensor networks may also allow for alternative connectivity where wired connectivity is difficult, such as in hazardous areas, or situations that are not plausible for dynamic applications (Examples: slip rings and robotic end effectors). The mesh network feature of BLE may be leveraged to provide many-to-many (m:m) connections which optimize creating large scale device networks by enhancing the reliability and flexibility of the network. Implementing CIP transferred through BLE on these IO networks, the commonality of data used across the network will allow for a scalable and diverse solution to meet industry needs.
In many cases, there will be limitations that will be addressed in the sections below, some of which include range, data rates, and outlining the security concerns and recommendation to address these concerns such as introducing CIP Security to allow for continuous secure access throughout a
network architecture. Additionally, these applications of BLE offer a personal area network (PAN) solution to the broader local area network (LAN) or wide area network (WAN) of the devices, machine, and plant. In order for data on the Bluetooth network to be utilized by the broader network, a gateway would need to be employed to facilitate this data transition. Some of the key reasons for utilizing a gateway in this context can include:
Protocol translation: translate between BLE and various Ethernet protocols, in this case EtherNet/IP. Such as switching the transport mechanism from that of BLE to TCP/IP and UDP.
Routing: Utilization of CIP Routing for gateway to route aggregated CIP data to the appropriate destination.
Device Management: Gateway providing services to manage BLE connections including pairing, authentication, and maintaining these connections, as well as serve as the security manager.
Network segmentation: Allow only the necessary data to pass to and from the Operational Technology (OT) networks, minimizing unnecessary data traffic.
Security: Gateway to provide additional layer of security by serving as a firewall, controlling data flows and access to a machine network.
Scalability: Ease of integration for adding more BLE nodes or a new network to a machine.
As an alternative approach to utilizing a gateway to segment the BLE PAN to a broader area network, functionalities described could be embedded into an IPC, edge computing device, or integrated directly into the firmware of an alternative device on a network such as a PLC or HMI. However, in comparison, a gateway provides a scalable and feasible approach to implementing a BLE interface into a broader CIP based network.
The operating range of Bluetooth is

Sample system diagram.
highly variable depending on several conditions such as radio spectrum, transmit power, receiver sensitivity, obstacles, radio reflection, electromagnetic interference (EMI), and beacon orientation. It has been estimated for an industrial environment with a BLE transmission rate at 2 Mb/s, a 0 dBm transmit power configuration, using a 0 Transmitter Antenna Gain, and 0 dBm receiver gain, a probable range for appropriate communications can be expected to be 23-55m.7
Bluetooth Stack Comparison
Bluetooth Classic and BLE (also referred to as Bluetooth SMART) protocol have two distinct stacks with the same three building blocks including Controller, Host, and Application blocks. The individual layers in the BLE stack starting at the bottom include:
Physical Layer (PHY): the physical radio interface that operates in the 2.4 GHz band, where the BLE packets are transmitted and received.
Bluetooth Low Energy
Link Layer (LL): the layer responsible for establishing and maintaining connections, advertising, scanning for devices.
Host Controller Interface (HCI): provides the interface between the host and controller layers, which is used to send and receive commands via USB, SPI, or UART.
Logical Link Control and Adaptation Protocol (L2CAP): Handles segmentation and reassembly of data packets for higher layers of message processing through logical channels.
Security Manager Protocol (SMP): responsible for device pairing, bonding, and key distribution and management.
Attribute Protocol (ATT): utilizes clientserver model to define how data is represented in BLE server database, and how this data is read or written.
Generic Attribute Profile (GATT): Defines hierarchy of ATT attribute types so data is exchanged between devices in structured way.
Generic Access Profile (GAP) - Responsible
Bluetooth Classic
for how devices can discover and connect to each other.
Reliability
Bluetooth’s characteristic reliability features are two-fold with its method for channel usage of Frequency Hopping Spread Spectrum (FHSS) and the type of frequency modulation it uses, Gaussian Frequency Shift Keying (GFSK).
BLE operates on 40 channels - 3 advertising and 37 data channels – in the 2.4 GHz ISM (Industrial, Scientific, and Medical) frequency band and uses FHSS as the method to hop between each of these channels within the frequency band. The BLE devices follow a pseudo-random hopping sequence that is dictated by the master device and communicated to slave device(s). These spectrum hops can occur up to 1600 times per second and during the time of hopping, the BLE devices continuously monitor the quality of communication on the present channel; if interference is present or poor signal quality is detected, the device will flag the channel to not use and continue with the remaining data channels. This frequency shifting also includes use of a Gaussian filter, as the name implies, allowing for smoother transitions between channel shifting by shaping the edges of the transmitted signals. This filtered keying helps reduce the bandwidth of the transmitted signals and reduces out-of-band interferences because the signal occupies less spectrum due to the Gaussian filtering.
Linking
When establishing an encrypted link between two devices, the two devices will negotiate a suitable key length which each can support, and which is deemed acceptable for the application associated with the connection.
This involves the central device sending a suggested key size to the peripheral device. The central device is typically a smartphone or tablet while the peripheral device would be a headset, fitness tracker, etc. In the use case for industrial automation and purpose of this article, the central device would be the BLE gateway, and the peripheral device would be the sensors or a tablet. In either case, the central device initiates the connection, scans for advertising peripherals, and controls the data flow; where the peripheral device broadcasts its presence, waits for a connection request from a central device and provides data when connected.
The suggested key size is always set to the maximum key size supported by the central device to begin with. If the peripheral device can accommodate the central device’s suggested key size, it accepts it. If not, it replies with a suggestion of its own. This exchange of suggestions between central and peripheral continues until an agreement is
reached or it is concluded that no mutually acceptable key length can be established, in which case the encryption setup is abandoned.
Pairing
BLE offers two primary pairing methods: LE Legacy and LE Secure Connections. LE Legacy, part of Bluetooth v4.0 specification, uses less robust security, relying on pairing methods such as Just Works or Passkey Entry. LE Secure Connections, introduced in Bluetooth v4.2, provides enhanced securing using Elliptic Curve Diffie-Hellman (ECDH) cryptography for key generation and exchange.
In the BLE pairing process, there are various association models used to establish secure connection between the two devices . These include:
1. Just Works: This model does not provide protection against man-in-the-middle (MITM) attacks and is typically used when there is no user interface for entering or displaying a passkey.
2. Passkey Entry: This model involves the user entering a passkey for one or both devices. It provides MITM protection.
3. Numeric Comparison: Both devices display a number, and the user verifies that the numbers match, providing strong MITM protection.
4. Out of Band (OOB): Uses an external communication method (like NFC) to exchange cryptographic information, providing strong MITM protection.
LE Legacy Pairing Overview
LE legacy supports the Just Works, Passkey entry and Out of Band association models for pairing. The pairing phases for LE Legacy are as follows:
1. Pairing Feature Exchange: The devices exchange information about their input/ output capabilities and device which association model to use.
2. Short Term Key (STK) Generation: Depending on the chosen association model, the devices generate a temporary key (STK) that is used for encrypting the link during the pairing process.
3. Long Term Key (LTK) Generation and Distribution: Devices generate and exchange the LTK and other keys (such as Identity Resolving Key (IRK) and Connection Signature Resolving Key (CSRK)) that will be used for future secure connections. Security Capabilities:
Limitations of LE Legacy Pairing
Vulnerable to MITM Attacks, the "Just Works" association model is vulnerable to MITM attacks because it does not authenticate the devices. Limited to Bluetooth 4.0, LE Legacy Pairing is part of the Bluetooth 4.0 specification, and newer versions of Bluetooth
(starting from Bluetooth 4.2) introduced LE Secure Connections, which provide stronger security features and mitigations against known vulnerabilities in LE Legacy Pairing.
LE Secure Connections Pairing Overview:
The key features of LE Secure Pairing include the following characteristics: Elliptic Curve Diffie-Hellman (ECDH) Key Exchange:
LE Secure Pairing uses the ECDH algorithm to generate a shared secret key, or DiffieHellman key, between the two devices. This key is then used to derive the Long-Term Key (LTK) and other encryption keys.
ECDH provides a higher level of security by ensuring that the key is not transmitted over the air and is resistant to eavesdropping. The association models LE Secure Connections supports are Just Works, Passkey Entry, Numeric Comparison, and Out of Band.
Pairing Phases:
1 . Pairing Feature Exchange: Devices exchange information about their input/ output capabilities and decide which association model to use.
2. Public Key Exchange: Devices exchange their public keys using the ECDH algorithm to generate a shared secret.
3. Authentication Stage: Devices authenticate each other using the chosen association model (e.g., Passkey Entry, Numeric Comparison).
4. Short Term Key (STK) Generation: Devices generate a temporary key (STK) using the shared secret key.
5. Long Term Key (LTK) Generation and Distribution: Devices generate and exchange the LTK and other keys, such as Identity Resolving Key (IRK) for resolving random private addresses and Connection Signature Resolving Key (CSRK)) for data signing to ensure authenticity of messages.
Security Capabilities:
Protection Against Passive Eavesdropping: ECDH key exchange ensures that the shared secret is never transmitted over the air, making it resistant to eavesdropping.
Protection against MITM Attacks: Depending on the association model used (e.g., numeric comparison, passkey entry), LE Secure Pairing provides strong protection against MITM attacks by authentication bot devices.
The advantages of LE Secure provide enhanced security features compared to LE Legacy Pairing, making it suitable for applications requiring high levels of security. These include improved user experience due to association models like Numeric Comparison and Passkey Entry which offer a balance between security and user convenience. Along with backward compatibility of devices which can still fall back to LE Legacy Pairing
when communicating with older devices that do not support the newer method.
LE Secure
The three common attack types that BLE must protect are as follows:
1.) Identity tracking which exploits the Bluetooth address to track a device on the network.
2.) Passive eavesdropping or sniffing, where the attacker is listening in to the data being transmitted between devices.
3.) Active eavesdropping or man-in-themiddle (MITM) where the attacker can impersonate a Bluetooth device on the network allowing them to listen in and potentially alter the data being transmitted.
As identity tracking exploits the Bluetooth address to track a device, protecting from such requires privacy protection. This can be done by enabling the LE Privacy feature provided by BLE to prevent the device information from being exposed during advertising mode. This feature functions by allowing the MAC address (Media Access Control) within the advertising packets to be changed to a random value thus disguising the real MAC address.
This process is initiated during the pairing process where the devices exchange encryption keys so the underlying devices can understand the real MAC address which this random MAC address will be translated to. The encryption key that allows for this feature is the Identity Resolution Key (IRK), which allows for the first device to translate the random MAC address, which appear in the advertising packets from the second device to the real MAC address of the second device. Generally, the random private MAC address change in accordance with a timer the device manufacture implements in the product firmware, allowing the devices to know how often the MAC addresses will change.
To prevent against actors listening in to the data exchange with passive eavesdropping, BLE encrypts the data being transferred using AES-CCM (Advanced Encryption Standard with CBC- MAC (Counter Mode Cipher Block Chaining Message Authentication Protocol)) cryptography while checking the integrity of the data itself. This cryptography specifically utilizes AES-128, Advanced Encryption Standard with 128-bit key, with it being a symmetric key meaning the same key is used for both encryption and decryption by the sender and receiver, all managed by the security manager protocol (SMP).
To protect the network from MITM attacks, the devices must adhere to security level 3 at a minimum of the security levels BLE defines for authentication and encryption. These levels are: security level 1 – no security with no authentication nor encryption, the devices simply connect without pairing; level

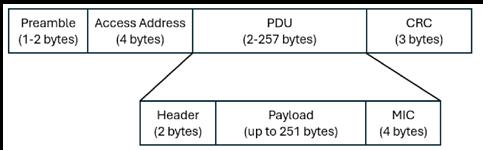
2 – unauthenticated pairing with encryption, the device requires pairing but in the notion of it ‘just works’; level 3 – authenticated pairing with encryption, where the pairing mechanism could be out of band (OOB), such as through near field communication (NFC), or through passkey; level 4 – the most secure option utilizes authenticated LE secure connections pairing with encryption using a 128-bit encryption key.
Throughput
In all network communications, the time it takes to send and receive data will dictate the throughput of the underlying technology. For BLE, a simplified diagram looks as shown in figure 1:
‘T’ is the transmission packet, ‘R’ is the receive packet from peer device acknowledging the packet has been received. ‘T_IFS’ is the inter frame space or time between two consecutive packets.
For any version of BLE 4.2 and above, the T_IFS will be 150µs and the length of time for transmission packet (T) and receive packet (R) will depend on the packet length and PHY used. The PHY used on the BLE device will dictate the baud-rate, the baud-rate of a LE 1M PHY would be 1 Mbps, while the baud rate of a LE 2M PHY is 2 Mbps. The LE 1M PHY is commonly used across BLE devices, while the 2M PHY is gaining market acceptance with its release in Bluetooth version 5.0.
The throughput of BLE depends on numerous factors such as the payload, Bluetooth version, mode used, and PHY. First regarding the payload of a BLE packet, the total packet length of BLE in v4.2 and above is 265 bytes total, with a payload of up to 251 bytes. To break this down further in the figure above, it is comprised of:
Preamble (1-2 bytes): used in the receiver to perform frequency synchronization, gain control, and symbol timing estimation. 1 byte for LE 1M PHY and 2 bytes for LE 2M PHY10.
This results in a total packet of 265 bytes for LE 1M PHY and 266 bytes for LE 2M PHY. Access Address (4 bytes): unique to each connection to avoid collisions.
PDU (2-257 bytes): Protocol Data Unit, consisting of header, payload, and MIC (Message Integrity Check), and can either be an advertising PDU to establish connection or as a data PDU to transmit the data with. CRC (3 bytes): Cyclic Redundancy Check to detect errors in the packet.
For the transmission packet as noted in figure 2, the maximum size with the largest payload will be 265 bytes and the receive packet length will be an empty payload to acknowledge receipt of data with just a preamble, access address, header, and CRC, thus a total of 10 bytes.
The version of BLE will impact the overall throughput attainable, as the maximum data rate of v4.2 is 1 Mbps with the corresponding LE 1M PHY, whereas the data rate of v5.0 and above is 2 Mbps with the LE 2M PHY. To illustrate how this will affect the overall throughput, in v4.2 the time it takes to send a transmission packet of 265 bytes at 1 Mb/s will be 2120 µs. Similarly, the time it takes to receive the receipt packet of 10 bytes at 1 Mb/s will be 80 µs.
The total time to transmit a packet and receive the target device’s advertisement packet is 2500 µs. The payload to be transferred is 251 bytes; however, including CIP components of encapsulation layer (24 bytes), common packet format (16 bytes) and CIP services such as the Set Attribute Single (8 bytes), will leave the actual written data payload in CIP format to be up to 203 bytes. Therefore, the possible throughput for v4.2 of BLE utilizing the LE 1M PHY will be .65 Mb/s. In following similar logic for BLE v5.0 and above utilizing a 2M PHY with a maximum data rate of 2 Mbps, the time to transmit a packet would come down to 1060 µs, receive packet to 40 µs and therefore the resulting
Figure 1 - Transmission Timing.
Figure 2 – Bluetooth Low Energy Packet
Characteristics of Service
GATT Service: Temperature Sensor Service: Handle of Service: 0x0001 | UUID: 0x1234. In this example, the GATT client (mobile device or control system) can read the temperature value by referencing handle 0x0002 and set the temperature threshold by writing to handle 0x0003.
maximum throughput is 1.16 Mb/s.11
Within a BLE network, there may arise an instance where a CIP message is larger than the MTU (Maximum Transmission Unit) of BLE itself, or the 251-byte payload. In this case, messages can be separated into multiple packets through a fragmentation process which occurs within the L2CAP layer. This process occurs by way of the following:
1. Application Layer sends data to the L2CAP Layer.
2. If data is larger than the MTU, or 251 bytes, the L2CAP layer divides this message into multiple smaller fragments.
3. Each fragment is encapsulated into its own packet payload.
4. The receiving device’s L2CAP Layer receives these fragmented packets and reassembles into the original data stream. This functionality will prove useful in the
case where an EtherNet/IP packet, commonly much larger than the MTU of BLE, is needed to be fragmented into multiple smaller packets, and sent over a BLE network. For example, in the case of connected worker, if the mobile device connected to the machine via BLE needs to read an EtherNet/IP message on mobile device, the data read will be fragmented and sent over Bluetooth.
Profiles
The host layer within the BLE stack sits below the application layer and above the control layer and is responsible for standardizing the method in which applications communicate with devices. The host layer provides the profiles which consist of a standard collection of services for a specific use case(s). Namely, the Generic Access Profile (GAP) defines the devices discovery and connections of the BLE
network and Generic ATTribute (GATT) Profile which manages how attributes and data, are transferred once devices have established a dedicated connection.
The GAP defines how devices interact with each other at a high level such as how they advertise themselves, establish connections, and manage security of the connections. GAP dictates how devices discover and establish connections, as a result, there are four main roles a device can play on a BLE network. In the GAP, a device can be specified as a broadcaster – device that broadcasts data but does not allow connections; observer – device listens for broadcasted data without establishing connections; central – device actively scans for and connects to other devices; and peripheral – device that advertises its presence and allows other devices to connect to it. Regarding
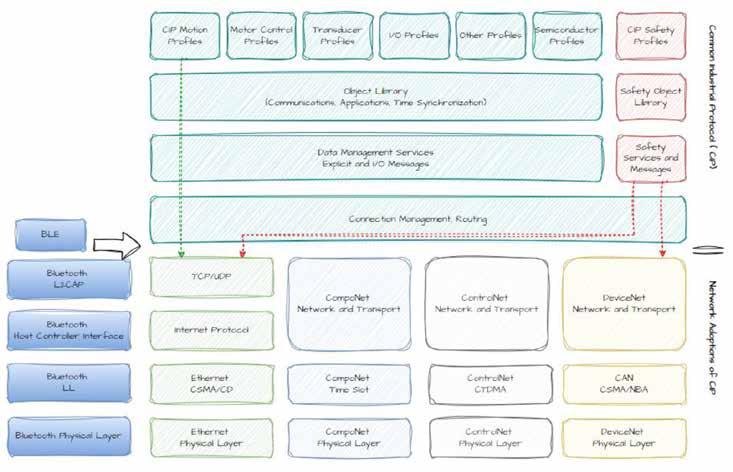

Reference the following diagram “PAwR operation”.
the aforementioned use cases, the primary GAP roles for industrial automation would be utilizing central and peripheral devices where a reliable, secure connection is made between devices. GAP is also responsible for managing the connection’s security through the underlying Security Management Protocol (SMP) and setting the BLE device address, which is similar to that of the MAC address. The BLE device address is a unique 48-bit value comprised of 12 hexadecimal digits with the format: XX:XX:XX:XX:XX:XX.
Once the discovery and connection of devices has been achieved, the GATT profile manages and defines how the data is structured in the form of services, characteristics, and attributes, as well as how these items are read or written. There are two roles the device can serve defined by the GATT, the server or client. The GATT Server is implemented on the device side and contains one or more services which encapsulate functionality related to the characteristics, and attributes being the
information transferred between devices. A typical characteristic may be comprised of the following attributes: characteristic value, characteristic value UUID (universal unique identifier), characteristic value handle, properties, and descriptors such as format or unit, all of which would be stored in the GATT server in an attribute table.
In addition to the values of above attributes, also in the attribute table will be the handle – index of attribute in the table, type – indicates what the attribute data represents, and permissions – enforces if and how a GATT client device can access the attribute. The type for each attribute is represented by a UUID, some of which are defined by Bluetooth SIG and if not, can be custom generated. If the UUID is Bluetooth-SIG defined it will be 16-bits and if it is custom generated, or vendor specific, it needs to be 128-bits.
An example of a custom GATT Server profile for a simple temperature sensor is as above.
CIP Profile Mapping: CIP Model Representation:
As the Common Industrial Protocol (CIP) model representation is a comprehensive framework designed for industrial automation and control systems, facilitating seamless communication across various devices and networks. At its core, CIP integrates multiple layers, including the application, transport, network, and data link layers, to ensure robust and reliable data exchange. By incorporating Bluetooth technology, the CIP model can further enhance wireless communication capabilities, providing flexible, low-power, and cost-effective connectivity solutions for industrial applications.
Adaptability to CIP
The integration of Bluetooth Low Energy (BLE) Periodic Advertising with Responses (PAwR) with the Common Industrial Protocol (CIP) may offer a scalable, low-power, and efficient communication framework
Class Attribute Name
Revision
Maximum Instance Id
Number of Instances
for industrial devices. CIP, widely used in industrial automation and the process industry, organizes data into a hierarchical structure of Classes, Instances, and Attributes, with Services facilitating access and modification of these attributes. BLE PAwR, introduced in the Bluetooth 5.4 specification, provides a mechanism for managing large numbers of devices with minimal energy consumption, making it well-suited for industrial environments. By combining the two, process industries can achieve real-time monitoring, configuration, and diagnostics in a centralized and flexible manner.
Process industries, such as oil and gas, chemical manufacturing, and water treatment, rely heavily on continuous monitoring of critical parameters like pressure, temperature, flow rate, and pH levels. CIP’s Class 1 messaging, designed for cyclic and time-critical data exchange, can be implemented using BLE PAwR to enable real-time monitoring of these parameters. In this setup, a central device, referred to as the Access Point (AP), periodically broadcasts advertising packets to a group of devices (Responders) identified by Group IDs. Each device within the group is uniquely assigned an ESL ID (or a similar identifier) and a specific Response Slot for communication.
Sensors deployed across the process plant can aggregate multiple CIP attributes into an Assembly Object (e.g., Class 0x04), encapsulating real-time operational data. For example, a pressure sensor might aggregate readings such as Pressure = 150 psi, Temperature = 80°C, and Flow Rate = 50 L/min into an Assembly Object. The AP triggers data exchange by broadcasting periodic requests, and each sensor responds in its designated Response Slot with the latest data. BLE PAwR’s short Periodic Advertising Intervals and support for multiple Subevents ensure low- latency, deterministic communication, making it ideal for real-time process monitoring where timely decisions are critical to maintaining operational efficiency and safety.
In addition to cyclic data exchange, BLE PAwR supports explicit messaging for non-cyclic tasks such as sensor configuration, calibration, and diagnostics. CIP’s hierarchical structure allows specific attributes to be accessed or modified using services like Get_
Attribute Description
Indicates the revision of the object class definition.
The highest instance number currently created.
The count of instances currently created.
Attribute_Single or Set_Attribute_Single. BLE PAwR enables these operations by leveraging its targeted communication model. Devices periodically broadcast key attributes, such as Vendor ID, Product Type, or Product Code (from the CIP Identity Object, Class 0x01), in their advertising payloads. A mobile device or AP can query or configure a specific sensor by targeting its ESL ID and sendinga request in the appropriate Response Slot. For instance, an operator might use a mobile application to recalibrate a pH sensor or update its operational range. Similarly, fault codes or diagnostic data can be retrieved to troubleshoot issues with a flow meter or temperature sensor. BLE’s ubiquity ensures seamless integration with mobile devices, enabling technicians to perform these tasks without requiring specialized hardware. This capability enhances flexibility and reduces downtime in process plants, where maintaining uninterrupted operations is critical.
Benefits:
The combination of CIP and BLE PAwR delivers several advantages for process industry applications. Scalability is achieved through PAwR’s ability to manage thousands of devices using Group IDs and Response Slots, enabling large-scale deployments in sprawling process plants. Low power consumption ensures that battery-operated sensors and devices can operate for extended periods, reducing maintenance overhead. The collision-free communication provided by Response Slots ensures deterministic and reliable data exchange, even in dense device environments. Furthermore, the ability to support both cyclic (real-time) and non-cyclic (configuration and diagnostics) communication provides a unified framework for diverse process monitoring and control applications.
Example Use Case: Water Treatment Plant
In a water treatment plant, multiple sensors are deployed to monitor critical parameters such as water pressure, flow rate, pH levels, and turbidity. Each sensor aggregates these readings into a CIP Assembly Object and communicates with the central AP using BLE PAwR. The AP periodically broadcasts requests to the sensor group (e.g., Group ID for water quality sensors), and each sensor responds in
its designated Response Slot with real-time data. For example, a pH sensor might report pH = 7.2, while a turbidity sensor reports Turbidity = 5 NTU (Nephelometric Turbidity Units). If an anomaly is detected, such as a sudden drop in pH or an increase in turbidity, an operator can use a mobile application to connect to the specific sensor via BLE PAwR. The operator can retrieve diagnostic data, recalibrate the sensor, or adjust its operational parameters in real time. This approach ensures continuous process monitoring, reduces the risk of plant downtime, and improves overall operational efficiency.
Summary : By mapping CIP’s hierarchical structure to BLE PAwR’s efficient communication model, process industries can achieve a new level of scalability, flexibility, and energy efficiency. This integration enables real-time monitoring, configuration, and diagnostics for thousands of sensors and devices, making it an ideal solution for some industry applications in the process sector. Whether it is for water treatment, chemical production, or oil and gas operations, the combination of CIP and BLE PAwR provides a robust foundation for modern industrial ecosystems.
Bluetooth Interface Object:
The Bluetooth Interface Object represents the interface and link-level security configuration of Bluetooth Classic or Bluetooth LE (Low Energy) interfaces. This object provides the necessary external interface for devices capable of communicating through a close proximity wireless interface for configuration, monitoring, network commissioning, and additional functions. It also offers a structured representation of security configurations for Bluetooth devices, facilitating the management and implementation of security settings in industrial automation devices.
The Bluetooth Interface Object would include class attributes that define its general properties as normal for CIP Objects.
Common Services
Possible Bluetooth Interface Object supported common services:
Get_Attribute_Single (0x0E): Retrieves a single attribute.
Set_Attribute_Single (0x10): Sets a single attribute.
Instance
Attributes
Attribute Name:
Enable
Bluetooth Version
Bluetooth Address
Attribute Description:
Allows the interface to be enabled or disabled.
Specifies the version of the Bluetooth standard in use (e.g., Bluetooth Classic or Bluetooth LE, 2.0, 2.1, 3.0, 4.0, 4.1, 4.2, 5.0, 6.0. etc.).
Note: Most recent versions of Bluetooth specifications are recommended for implementation due to reliable, robust, and secure operation.
Connection State Operating state of the Bluetooth interface (Active Mode, Sniff Mode, Hold Mode, Park Mode).
Power Class Defines the power class of the Bluetooth interface (e.g., Class 1, Class 2, Class 3).
Bonded Device List
BLE Device Roles
Supported Profiles
Lists Bluetooth addresses currently associated with the interface.
Specifies the device roles implemented. (e.g., Peripheral, Central, Broadcaster, Observer).
Supported Bluetooth profiles: GATT [Generic Attribute Profile]; BNEP [Bluetooth Network Encapsulation Profile – BT Classic Only] PAN [Personal Area Network]; DIP [Dev ID]; SDAP [Service Discovery]
Connection Interval The time between two connection events
Slave Latency
The number of skipped connection events allowed for a peripheral device.
Supervision Timeout The timeout period from the last data exchange until a link is considered lost.
Supported Range
Maximum Data Rate
Supported Services
Pairing Method
Describes the supported range of the Bluetooth interface.
Describes the maximum supported data rate.
Provides bitmapped identification of supported services. Discoverable through SDAP profile: Examples are Service Discovery Service - Allows a device to retrieve information on services offered by a neighboring device; Generic Access Service: Procedures related to discovery and link management aspects; Generic Attribute Service: Defines structure in which data is exchanged and how attributes are grouped to form services; Link Loss Service – Defines behavior when Link is lost between devices; Tx Power Service – Identifies current power transmit levels of a device while participating in a connection; Authorization Control Service – Enables authorization to access specific or protected GATT resources of server; Transport Discovery Service – Enables a device (BLE) to expose services that are available on another transport (Ethernet); and Indoor Positioning Service – RTLS – Location tracking enabler.
Specifies the pairing method used (e.g., SSP, Passkey Entry, Just Works).
Authentication Enable Allows authentication to be enabled or disabled.
Encryption
Resolvable Private Address
Security Mode & Encryption Level
Indicates the type of encryption used on the interface.
Enables privacy features for Resolvable Private Address.
Defines the security mode and encryption levels supported by the Bluetooth interface.
Turn Off When Not In-Use Allows the Bluetooth interface to be disabled when not in use to prevent unauthorized access.
Reject Unknown Pairing Request
Use Strong Passkeys
Disable Unnecessary Services
Prevents pairing requests from unauthorized devices.
Requires the use of strong passkeys for device access.
Provides a list of services to be enabled or disabled based on device requirements.
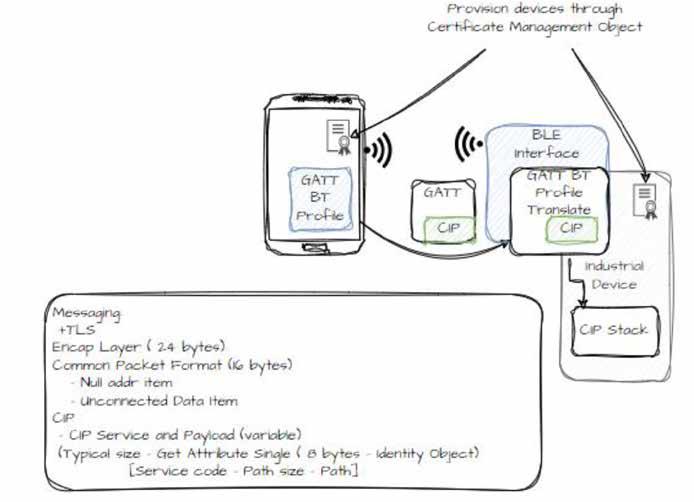
Object Specific:
Clear_Bonded_Device_List (0xXX): Clear the array of DB_ADDRs bonded to a device.
Summary: The Bluetooth Interface Object is a possible framework for managing Bluetooth interfaces in industrial automation devices. It offers robust security configurations, flexible interface management, and detailed control over Bluetooth communications, making it a vital component for modern industrial applications.
Other CIP Extensions:
CIP Safety: CIP Safety as an extension of the CIP suite provides safety critical communications in industrial environments and is typically used in high-availability, low-latency, and fault tolerant systems. In assessing the implementation of CIP Safety over BLE there are inherent benefits to BLE lending itself to this application such as its high reliability and stability from its frequency hopping mechanism. Some of the initial use cases for implementing CIP Safety over BLE can include:
• Remote E-Stop on a tablet in connected worker example, providing a safe stop mechanism when commissioning a machine from the remote device.
• Wireless E-stop local to the machine
if dynamic application with rotating equipment.
• Additional stationary safety IO needed within close proximity of machine as part of mesh IO network.
Applications where CIP Safety would not be suitable over BLE would include where roaming is needed such as in AMRs/AGVs and applications with distances exceeding the limitations of BLE. For these use cases, BLE and the respective gateway necessary to connect to the LAN could act as a ‘black channel’ for the safety data that is being transmitted. CIP Safety has a relatively low payload of 74 bytes that would be able to fit within the BLE packet’s payload. Additionally, as the latency can be as low as 6 ms on BLE, this would be suitable for most functional safe applications. However, more testing would need to be completed to understand the safety rated levels BLE can provide in terms of reliability, latency depending on payload and distance, as well as an understanding of the application and the risks posed.
CIP Motion:
In assessing CIP Motion over BLE, this is not something that would be feasible at the moment due to CIP Motion’s requirement
low-latency communication and determinism. One use case for utilizing BLE for motion applications in general could be to monitor or configure standalone motion applications that do not require real-time communication.
CIP Security:
Security
(Routability) - General
CIP Security (Common Industrial Protocol Security) provides mechanisms to ensure confidentiality, integrity, and authenticity of data in industrial networks. Implementing CIP Security over BLE transport involves leveraging BLE's capabilities to secure communication channels between industrial devices. This section outlines the key considerations and steps for implementing CIP Security over BLE.
Implementing CIP Security over Bluetooth Low Energy (BLE) Transport
Possible Implementation Steps
Step 1: Device Pairing and Bonding
• Pairing: Initiate the BLE pairing process using a suitable method (e.g., Passkey Entry or Numeric Comparison) to establish a secure link between devices.
• Bonding: Store the long-term keys generated during pairing for future secure
Originate CIP Message from BT Capable Client: a. Originate CIP Message from BT capable clients. b. Securely Route to other devices on EIP network.
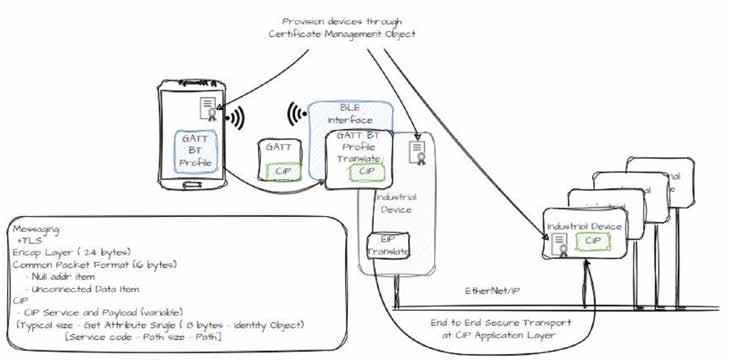
connections.
Step 2: Enabling Encryption
• Encryption Setup: Enable AES-CCM encryption on the BLE link to protect data during transmission. This ensures that all data exchanged between devices is encrypted and secure.
• Encryption Keys: Use the long-term keys generated during the pairing process to establish encrypted connections.
Step 3: Implementing CIP Security Protocols
• Secure Messaging: Implement CIP Security's secure messaging protocols over BLE transport. This involves encapsulating CIP messages within BLE's encrypted data packets.
• Message Authentication: Use cryptographic techniques (e.g., HMAC) to authenticate CIP messages. This ensures that messages are from legitimate sources and have not been tampered with.
Step 4: Privacy Protection
• Resolvable Private Address (RPA): Enable RPA to periodically change the device's address, enhancing privacy and making it difficult for unauthorized parties to track the device.
Step 5: Handling Security Modes and Levels
• Security Modes: Configure the BLE interface to operate in the appropriate security mode, as defined by CIP Security. This includes setting the security mode and encryption level to meet the required security standards.
• Security Levels: Ensure that the
BLE transport meets the security level requirements specified by CIP Security, such as authenticated link keys and encryption. Example/Possible Implementation could incorporate the following:
An example implementation of CIP Security over BLE transport could involve the following steps:
• Device Pairing: Use Numeric Comparison to pair two industrial devices, establishing a secure link.
• Bonding: Store the long-term keys generated during pairing for future connections.
• Encryption: Enable AES-CCM encryption on the BLE link to protect data during transmission.
• Secure Messaging: Encapsulate CIP messages within BLE's encrypted data packets, ensuring data integrity and confidentiality.
• Message Authentication: Use HMAC to authenticate CIP messages, verifying their authenticity.
• Privacy: Enable RPA to periodically change the device's address, enhancing privacy.
Implementing CIP Security over Bluetooth
Low Energy transport involves leveraging BLE's built-in security features to ensure the confidentiality, integrity, and authenticity of data exchanged between industrial devices. By following the outlined steps and utilizing BLE's pairing, encryption, and privacy mechanisms, a secure communication channel can be established, meeting the requirements of CIP Security in industrial automation environments when there are point to point connections that are
established. However, the consideration of including the mechanisms designed for CIP Security utilizing TLS should be used when transporting through multiple physical media segments, such as Bluetooth to Ethernet to provide an end-to-end security solution.
Conclusion:
This article explored the feasibility and potential of implementing Bluetooth technology, more specifically Bluetooth Low Energy (BLE), for industrial automation by enabling Common Industrial Protocol (CIP) communications possibilities over BLE. It delves into recent enhancements in Bluetooth specifications, addressing aspects such as security, stability, and technical specifications. Therefore, it is strongly recommended to use the latest version of the BLE specification to take advantage of the most up to date capabilities.
The article discusses mapping CIP onto Bluetooth transport, extending CIP functionalities, and evaluates use cases including smart devices for connected workers and sensor networks in challenging environments. It also considered industrial considerations, security implications, and the role of gateways in integrating BLE with broader industrial networks, ultimately proposing a scalable and secure approach for adopting Bluetooth in industrial automation.
Mark Trautman Strategic Account Manager and Zach Farmer, Business Manager, HMS Industrial Networks; Todd A. Wiese, Principal Software Systems Architect, Rockwell Automation. Learn More
Securely route to other devices on EIP network.
EtherCAT and EtherCAT P box modules
New EtherCAT and EtherCAT P box modules with ID switches amplify I/O system addressing. IP67 I/Os offer simple hardware identification and addressing via a built-in ID switch.
Beckhoff has expanded its portfolio of EtherCAT and EtherCAT P Box products with modules that offer additional hexadecimal addressing via built-in rotary selector switches. This means that these machine mountable IP67 I/Os can be clearly and easily addressed regardless of their installation location.
In modular and distributed systems, individual devices must be uniquely addressed within an EtherCAT network with its variable topology. I/O devices with rotary selector switches enable quick and easy assignment of the corresponding addresses. The new EtherCAT Box and EtherCAT P Box modules feature three additional hexadecimal rotary addressing switches.
Individual addresses from 0 to 4095 can be set and given a unique, position- independent identification. This is required for some device profiles for certain industries, such as in the semiconductor industry.
Three I/O Box modules are initially planned. Each one is available in a version for EtherCAT (EP) and for the EtherCAT P one cable solution (EPP):

• EP/EPP1816-0703: 16-channel digital input, 24 V DC, 10 μs, IP20 connector
• EP/EPP2339-0703: 16-channel digital combi, 24 V DC, 3 ms, 0.5 A, IP20
• EP/EPP3754-0702: 4-channel analog
input, multi-functional, M12
Managed switch offers flexibility
Managed switch from Antaira offers flexibility in industrial network design.
Antaira LMP-1204G-SFP-bt 12-port PoE Gigabit Ethernet managed switches are a strategic choice for industrial organizations needing robust, efficient and flexible networking solutions.
By supplying up to 90W (PoE 802.3bt Type 4) from four of its ports, the LMP-1204GSFP-bt can handle a broader range of Powered Devices than switches that only furnish PoE 802.3af/at 30W output. High-power industrial devices, such as PTZ cameras, LED lighting, Wireless APs, IoT sensors or controllers, and PLCs, benefit by receiving both power and data over a single Ethernet cable from the LMP-1204G-SFP-bt. Besides reducing cabling complexity and eliminating the need for additional power outlets, PoE 802.3bt lowers overall installation costs, especially in hardto-reach or remote locations like warehouses, factories, or transportation systems.
Although it features a highly compact footprint, the LMP-1204G-SFP-bt supports multiple industrial devices via its four PoE 802.3bt (90W) Ethernet ports, four PoE 802.3at (30W) Ethernet ports, and four dual-rate SFP slots, facilitating centralized network management and communication in

complex industrial setups. Industrial networks can be expanded easily by accommodating new devices and system upgrades without replacing the LMP-1204G-SFP-bt switch. Additionally, redundant network configurations are made possible by its high port count, guaranteeing uninterrupted operation in the event that one path fails.
The LMP-1204G-SFP-bt-24 is a fully manageable Light Layer 3 Ethernet switch pre-loaded with a web management console design.
Antaira
Learn More
Beckhoff
Discrete AC input modules
New I/O modules from Acromag sense on/off AC voltage levels and contact closures to monitor remote equipment activity and detect power faults.
Acromag added a new discrete AC input module, the Model NT2140, to their BusWorks® NT Ethernet I/O family. This new discrete I/O module provides six 120V or 240V AC optocoupler inputs for sensing sensing the presence or absence of voltage plus two DC logic I/O channels to monitor/ control TTL or 0-32V logic levels.
Applications include monitoring on/ off levels of pumps, motors, switches (e.g. proximity, limit, float, toggle), push buttons, thermostats, contact closures, and AC voltage power supply levels on a wide variety of equipment. A network interface supports Modbus TCP/IP, EtherNet/IP, or PROFINET protocols to communicate with programmable controllers (PLCs/ PACs) or other networked devices. An OPC UA server, MQTT client, and RESTful API support Industrial Internet of Things (IIoT) applications.
NTE Ethernet models
NTE Ethernet models provide dual RJ45 ports for network communication plus the discrete I/O channels. NTX expansion modules add extra I/O channels to monitor more devices. Up to three NTX modules can link to the NTE communication module through an integrated DIN rail bus interfacing up to 64 I/O over a single network IP address.
Other NT Series analog and discrete I/O modules offering a variety of signal processing functions can also be combined to monitor or control voltage, current, and temperature signals. Remote I/O modules are commonly used in chemical processing, oil/gas production, water/power utility, and manufacturing operations.
“With these discrete AC input modules, you can confidently monitor the on/off power status of remote pumps, motors, and other switched devices,” states Robert Greenfield, Acromag’s Director of Business Development. “The NT2140 will sense the presence or absence of AC voltage levels for communication to your control system using a wide variety of industrial Ethernet protocols.”
The BusWorks NT2000 Series offers a broad variety of I/O signal processing options. Sixteen I/O configurations are available as either NTE Ethernet I/O or NTX expansion I/O models. Analog I/O models feature up to sixteen inputs or eight outputs for monitoring and controlling current or voltage signals. Discrete I/O models provide sixteen tandem input/output channels or six mechanical relays to sense or switch

BusWorks® NT2140 Discrete AC Input Modules with Ethernet communication. The BusWorks NT2000 Series offers a broad variety of I/O signal processing options. Sixteen I/O configurations are available as either NTE Ethernet I/O or NTX expansion I/O models. Analog I/O models feature up to sixteen inputs or eight outputs for monitoring and controlling current or voltage signals.
on/off and high/low logic levels. For temperature measurement, thermocouple and RTD input models support many sensor types and ranges.
Each module supports three industrial protocols (Modbus/TCP, EtherNet/IP, PROFINET) which are selectable using any web browser to configure the network settings and I/O operation. OPC UA, MQTT, and RESTful API support facilitate IIoT applications. The modules typically function as a network server, but also offer Acromag’s i2o® peer-to-peer communication technology to transfer data between modules directly or multicast without a host or master in between. Conditional logic
capabilities let users control operations with IF/THEN/ELSE statements.
Acromag, a mid-sized international corporation, has been developing and manufacturing measurement and control products for more than 65 years. They offer a complete line of industrial I/O products including process instruments, signal conditioning equipment, data acquisition boards, distributed I/O systems, and communication devices.
Acromag
Learn More
Industrial PC AI-enabled automation
Emerson’s next-generation of Industrial PCs provide a powerful and rugged computing platform for AI-enabled automation. New HMI/SCADA software optimize connectivity, development, and run-time performance.
New PACSystems IPCs combine the latest generation of industrial-rated processors with optimized cooling and pre-loaded software to simplify advanced computing and integration.
The PACSystems IPC 6010, IPC 7010, and IPC 8010 industrial computing platform expands Emerson’s family of high-performance industrial personal computer (IPC) models for demanding applications, including artificial intelligence, machine learning and advanced analytics. PACSystems IPCs feature the first CPU in the latest generation of processors designed specifically to support AI-enabled capabilities such as predictive maintenance, process optimization, quality inspection, decision support, supply chain management and more.
Critical digital transformation applications require reliable and ruggedized computing platforms, with the high level of performance needed to support data collection, protocol conversion, historization, and analytics for real-time optimization and visualization capabilities. The new PACSystems line features significant performance updates and more options to develop solutions for challenging industrial applications, with a range of functionality and price points to support scalable operations and lower costof-ownership.
The new line of IPCs use the latest generation of soldered industrial-rated 13th Generation Intel® Core™ Processors with up to 64 GB soldered ECC memory, for maximum resistance against shock and vibration. Their compact form factor employs fan-less cooling for an extended operating temperature range up to 70 degrees Celsius, with thermal monitoring and an optional fan available for high-temperature environments. PACSystems IPCs benefit from Emerson’s patented vibration and thermal technologies to boost reliability and extend deployment life.
With solid-state drive (SSD) storage options ranging up to 4 terabytes, multiple gigabit Ethernet interfaces, up to four PCIe® slots, and other interfaces, PACSystems IPCs can be tailored to deliver high-performance computing required for vision systems, advanced analytics, data processing, historization/visualization, and other similarly rigorous functions for process optimization and improved operational insight.
Available pre-installed, pre-licensed operating systems with edge and visualization software help to simplify deployment of common configurations while also allowing users to fully customize their systems.

The goal of NOA is increasing the productivity of process plants. At a joint workshop attended by experts
Operating system options include Windows IoT Enterprise LTSC 2021, PACEdge, and Linux. Software options include PACEdge, Movicon Connext™, and Movicon WebHMI. Alternatively, users can load their own OS or software. Built-in Trusted Platform Module (TPM) crypto-processors and Secure Boot® software ensure that data and operations are kept secure.
“These innovative next generation IPCs are a key part of the critical hardware backbone supporting Emerson’s Boundless Automation vision,” said Harish Shinde, vice president and general manager for controls and software, with Emerson’s discrete automation business. “PACSystems IPCs are an ideal platform for developers seeking to future-proof industrial systems and achieve continuous uptime even in extreme environments as they create IoT, AI, and other advanced applications.”
For more information on the full range of Emerson’s PACSystems IPCs, including the newest IPC 6010, IPC 7010, and IPC 8010, visit https://www.emerson.com/en-us/ catalog/emerson-ipc
Learn More
Movicon.NExT Release 4.4
Emerson has also announced the release of Movicon.NExT™ Version 4.4, a modern human-machine interface (HMI) and supervisory control and data acquisition (SCADA) platform. Movicon.NExT HMI/SCADA empowers users to create interoperable automation architectures for discrete and process manufacturing applications in the commercial, industrial, and municipal/utility industries. This update delivers enhancements boosting functionality, performance, and flexibility, with an emphasis on user-centric improvements to maximize development efficiency.
Communications and Drivers
Updated industrial communication protocol drivers—for OPC UA, EtherNet/IP, and others—provide support for multi-station, advanced arrays, and more. A new DNP3 driver enables Movicon.NExT HMI/SCADA to integrate seamlessly with power industry and electrical utility networks. Optimized I/O operations more efficiently aggregate read/ write tags for greater throughput, and open connectivity helps users easily connect with digital assets.
Scripting and Development
Native support within Movicon.NExT for Python runtime scripting enables custom, cross-platform logic, so developers can create sophisticated strategies while building on proven work. Updated user interfaces, new graphical properties for controls, and streamlined license management (both local and network-based) enhance and simplify the overall user experience, while accelerating project development.
Data Management
New support for TimescaleDB in the historian offers improved storage efficiency and higher performance, especially with large data volumes. Other enhancements increase data precision and SQL database compatibility, while recipe and alarm management are performed through a centralized connection. Movicon.NExT is built to meet the increasing demand for data to support visualization and analytics.
To learn more about the Movicon.NExT v4.4, visit: https://www.emerson.com/ en-gb/automation/control-and-safetysystems/movicon/movicon-next
Learn More
Digital manufacturing / AI readiness
Siemens and leading machine tools and laser manufacturer TRUMPF have announced a partnership that promises to elevate industrial production by harnessing advanced digital manufacturing solutions.

Siemens and TRUMPF are partnering to accelerate digital manufacturing and AI readiness.
• Partnership unites Siemens' digital expertise and Xcelerator portfolio with TRUMPF's manufacturing and software excellence
• Collaboration addresses critical system integration challenges in modern manufacturing with open and interoperable interfaces
• Support for virtual development and standardized interfaces enable faster time-to-market and significant operational efficiency improvements for customers
The collaboration joins Siemens' Xcelerator portfolio with TRUMPF's renowned machinebuilding and software expertise. It also addresses a critical challenge in modern manufacturing: the disconnect between information technology (IT) and operational technology (OT) systems that has historically hindered production efficiency and innovation. By leveraging Siemens' Xcelerator portfolio and TRUMPF's manufacturing excellence, the collaboration aims to deliver comprehensive solutions that bridge this gap. Both companies are working on open and interoperable IT interfaces that will help to advance artificial intelligence (AI) readiness for motion control applications.
“Real transformation in a factory begins
when machines on the shop floor are connected through a shared digital backbone, so that data flows seamlessly, decisions happen faster, and production responds to changing conditions,” said Cedrik Neike, Member of the Managing Board at Siemens AG and CEO of Siemens Digital Industries.
“By working with TRUMPF, we’re making that connection effortless. We’re bridging the gap between IT and OT so that manufacturers can move faster, adapt in real time, and prepare for the AI era. I’m proud to see two European champions leading the way.”
Overcoming complexity with seamless system integration
In today’s rapidly evolving industrial landscape, software is no longer just an add-on to hardware, it’s becoming the key differentiator in manufacturing. From intelligent control systems to data-driven optimization, a seamless integration of hardware and software enables entirely new levels of flexibility, efficiency, and value creation. For Siemens and TRUMPF, this shift has created significant opportunities, but also new complexities. Therefore, collaboration is essential and will enable faster innovation cycles, better integration of hardware and software, and a more scalable approach to delivering solutions and value through standardized interfaces.
The collaboration will also deliver tangible
customer benefits through modular system architecture and unified system solutions. Standardized interfaces will allow for seamless connectivity between shop floor equipment and enterprise-level systems. Customers will benefit from increased operational efficiency, reduced engineering costs, and futureproof scalability by using open, modular automation solutions. These are critical to ensure future-proof AI readiness, that will permit customers to achieve faster time-tomarket, improved production flexibility, and competitive manufacturing operations.
“TRUMPF is a leading company for smart factory solutions in the sheet metal industry. The cooperation with Siemens underpins our position as a solution provider. Thanks to the open standards, our customers will benefit even more from the digital networking of the production – from our machines to robots, grippers and part recognition with the help of AI. We’re taking industrial manufacturing to a whole new level with Siemens", said Stephan Mayer, CEO of Machine Tools at TRUMPF.
The partnership builds on regular exchanges among development teams at Siemens and TRUMPF, which underscores the importance of vibrant ecosystems for solving industry’s most pressing challenges.
Siemens
Learn More
The Cellulink product family connects network-capable devices to the cellular network worldwide and is certified in accordance with IEC 62443-4-2.
7-inch Multitouch Panel
Multitouch panel combines high performance, brilliant (web) visualization and interfaces.
The latest addition to SIGMATEK's HMI portfolio, the ET 0710, combines compact plastic design with the latest processor architecture and a high-resolution 7-inch multitouch display. This slim operating panel is therefore ideal for smaller machines with limited space and price-sensitive applications that want to enhance with modern HTML5 visualization.
At its heart is a quad-core EDGE3 technology processor with four cores (4x 1.6 GHz), 2 GB LPDDR4 RAM, and 8 GB microSD memory. This allows even memory-intensive web HMI applications to be displayed smoothly.
Thanks to its projected capacitive glass surface, the fanless HMI can be operated precisely and intuitively using multi-finger gestures. The 7-inch widescreen with a resolution of 1.024 x 600 pixels displays colors and visualizations brilliantly. The LASAL VISUDesigner Tool (HTML5) offers a wide range of ready-to-use operating elements and controls for creating visualizations.
The ET 0710 has one Ethernet, one CAN, one USB 2.0 Type A, one USB 2.0 Type C, and one RS485 interface. The ET 0710-02 offers

an additional Ethernet, CAN, and RS232 interface. The ET 0710-01 variant comes with 1x Gigabit Ethernet, 1x Ethernet, 2x CAN, 1x USB 2.0 Type A, 1x USB Type C, 1x RS232, 1x RS485, 1x LP-Bus, and 1x M-Bus. This allows users to select the panel or interfaces that best suit their requirements and achieve cost efficiency. The plastic housing of the
ET 0710 also contributes to an optimized price-performance ratio and is designed for industrial use. A multi-status LED is located on the front.
IO-Link retroreflective area sensor
Retroreflective area sensor with IO-Link reliably detects objects regardless of shape or size.
A new R305 retroreflective area sensor enables reliable detection of thin and irregularly shaped objects from a height of just 2 mm.
The R305 easily out-performs the singlepoint light beams of traditional retroreflective sensors, detecting very small or narrow objects that are not precisely aligned with the point-shaped detection area. For objects with irregular contours, such as bubble mailers and polybags, the point light beam may either miss the object entirely or detect it with a delay, which can trigger multiple switching operations. But the new R305 retroreflective area sensor, with its wide light band, always detects the leading edge of an object and avoids multiple switching.
Using a light band of five individual beams that can be switched off individually, the R305 sensor allows interfering objects to be blocked out or the detection height to be adapted to narrow openings. Its adjustable contrast level ensures reliable detection of challenging targets such as clear glass, while the HighResolution Mode extends this capability by detecting objects with a height of just 2 mm. Beyond simple presence detection, the sensor

measures object height and transmits values via IO-Link, while integrated trend evaluation delivers insights like plastic bag fill levels— enabling quality control, process optimization, and new application possibilities.
With Easy Alignment Mode, the light band can be quickly aligned with the reflector. A right-angle bracket with an integrated
deviation mirror also enables mounting offset by 90 degrees, creating a compact side-looker version for tight spaces.
Learn More
Sigmatek
Pepperl+Fuchs
Feed-in module and LED signal lights
New feed-in module with Modbus TCP communication interface and LED signal lights aid machine integration.
Compact LED signal lights for direct machine integration
The new PSD-SL LED signal light series by Phoenix Contact is a compact solution for application-oriented signaling directly on machine functions. The lights are versatile, robustly built and suitable for both indoor and outdoor use.
The new PSD-SL LED signal lights from Phoenix Contact enable clear, functional signaling directly on the application. They are available in two designs – Point and Tower – and feature a choice of three or seven colors, depending on the version. Various light animation sequences such as flashing and color changes enable flexible adaptation to different signaling tasks, such as machines, automated guided vehicle systems (AGVSs), and service robots.
The lights are connected via a 5-position, A-coded M12 connector and controlled with 24 V DC via 4-bit switching. Mounting is simple with the M22 installation opening; the mounting material is included in the scope of delivery. With IP66, IP67, IP69, IP6K9K and UL Type 4/4X degrees of protection and a wide temperature range of -40 to +70°C, the lights are also suitable for harsh industrial environments both indoors and outdoors. The PSD-SL series complements Phoenix Contact's signaling portfolio with a compact, robust, and versatile solution for the immediate machine environment.
New feed-in module with Modbus TCP communication
interface
The possible applications of the Caparoc circuit breaker system from Phoenix Contact have been extended. With the new feed-in module with Modbus/TCP interface, the system can be used in other communication systems.
The Caparoc electronic circuit breaker system is being extended to include another feed-in module. This new module is equipped with a Modbus/TCP communication interface. It offers users exceptional flexibility and efficiency in terms of overload and shortcircuit protection, while at the same time providing a high level of transparency in the application. Modbus/TCP is often used in industrial applications as it enables reliable and fast communication via Ethernet. It is characterized by its simple integration and high degree of compatibility with various devices. This makes it a preferred choice for modern control systems.
The feed-in module enables real-time monitoring and analysis of all relevant data via the Modbus/TCP interface. This results in


The Caparoc electronic circuit breaker system is being extended to include another feed-in module.
precise control, which minimizes the risk of failures and increases the reliability of the entire system. Due to the simple integration and universal use of Modbus/TCP, the module is compatible with existing systems and devices. Featuring advanced technology, the feed-in module is also ideally equipped for future requirements.
Phoenix Contact Visit Website
New PSD-SL LED signal lights enable clear, functional signaling directly on the application.
Industrial Ethernet Book
The only publication worldwide dedicated to Industrial Ethernet Networking and the IIoT. Visit iebmedia.com for latest updates.

New website offers deepest, richest archive of Industrial Ethernet and IIoT content on the web.




View and/or download latest issue of Industrial Ethernet Book and past issues.
Search our database for in-depth technical articles on industrial networking.
Learn what's trending from 5G and TSN, to Single Pair Ethernet and more.
Keep up-to-date with new product introductions and industry news.
