










































Ready for what’s next Ludwig Decamps, General Manager, NCIA 07
A strong NATO: ready for any challenge Mark Rutte, NATO Secretary General 11
Editors’ pick
Lara Vincent-Young and Simon Michell, Editors, NITECH 17
The NATO Allied Reaction Force: readiness in action
Lorenzo D’Addario, Commander, NATO Allied Reaction Force 22
Exercise Dynamic Mariner 25: cyber security at sea Loic Fortemps, NCIA’s NATO Cyber Security Centre Rapid Reaction Team 28
Being ready François-Marie Gougeon, Acting Assistant Secretary General, Defence Policy and Planning, NATO 34
Achieving readiness: NCIA technology strategy Antonio Calderon, Chief Technology Officer, NCIA 40
Enhancing industry collaboration Zoe White and Pablo González, NATO Industrial Advisory Group 46
The quantum conundrum: defending multi-cloud networks from tomorrow’s threats
Andrew Lord, Senior Manager, Optical Networks and Quantum Research, BT 52
View from the Nations: Estonia Hanno Pevkur, Minister of Defence, Estonia 58
Lessons from Ukraine Kateryna Chernohorenko, Deputy Minister of Defence of Ukraine for Digital Development, Digital Transformation and Digitalization 61
JATEC analysis training: learning lessons Admiral Pierre Vandier, Supreme Allied Commander Transformation 66
WIDE25: demonstrating innovative warfighting Hugh Blethyn, Innovation Manager, NATO’s Joint Force Command Brunssum 72
NSATU: supporting Ukrainian readiness levels
Colonel Patrick Schuetterle, Deputy Chief, NCIA Service Operations, Gregor Gosepath, Lead Early Engagement Europe, (Chief Technology Office), and Michail Kanellakis, Senior Project Manager, NCIA’s NATO Integrated Mobile Services Centre 75
Balancing service levels to demand
Paul Hammond, Head, Crisis Management and Business Continuity, and Angelo Talarico, Head, Service Management and Control, NCIA 80
NATO Digital Workplace
Laura Bercan, Senior Business Analyst, NATO Digital Workplace Centre
83
Enabling NATO air and missile defence
John Booth, Chief, AirC2 (Air Command and Control), NCIA 88
Steadfast Dart 25
Darius Žibalis, former Exercise Staff Officer, NCIA DCSU OPEX 94
NCIA support to Exercise
Loyal Leda
Major Derek Aubin, NCIA Operations and Exercises 97
SATCOM ground station upgrade
Philippe Margot, Principal Project Manager, NCIA 102
Hyperscale cloud and the power of partnerships
Amazon Web Services 108
NWCSP: The NATO Wireless Communications Standards Project
Dr Alexander Hamilton, Director of Standardization and Science & Technology, Nokia and Chair, NATO Wireless Communications Standards Project, and Juan Ramirez, U.S. DoD CIO, Director, 5G Cross Functional Team 114
CWIX: testing emerging technology Brigadier General Thorsten Jørgensen, Assistant Chief of Staff for Requirements, Allied Command Operations 117
Quantum leaps: beneath the waves
Dr Pietro Paglierani, Senior Scientist , NATO Centre for Maritime Research and Experimentation (CMRE) 120
Anatomy of a Ransomware Attack
Michael McLaughlin, Head, Cyber Security and Data Privacy, Buchanan Ingersoll & Rooney PC 123

In our increasingly complex security environment, readiness is key to NATO’s ability to respond swiftly and firmly to new security challenges, ensuring that our forces are able to deter and defend at a moment’s notice, across all domains and against any threat. For NCIA, readiness is at the core of our mission. It means delivering at speed the technology, expertise and services that enable our Allies to act together securely and seamlessly.
In this 13th edition of NITECH, I am in great company to define what readiness means for the Alliance and how we will balance supply and demand as threats and pressure surge. NATO’s new Secretary General, Mark Rutte, joins me to discuss the components of NATO’s readiness and share his vision for the future. This edition offers a deeper look at how NATO, NCIA and our industry partners are translating that vision into practical steps to enhance our collective readiness.
This past year, NCIA brought together more than 1,800 attendees from across the Alliance, industry and academia at NATO Edge 2024 in Tampa, Florida. The conference was a powerful reminder that NATO’s technological edge is not inevitable; it must be actively maintained.
At the heart of NATO’s technological transformation is the launch of our Technology Strategy, unveiled at NATO Edge last year. In this edition of NITECH, Antonio Calderon, our Chief Technology Officer, outlines the thinking behind the strategy and how it is already helping us support operational readiness, drive innovation and deliver capability at pace (p40).
We were also fortunate enough to have representatives from the Ukrainian Department of Defence attend NATO Edge and reflect on the changing nature of conflict. As a follow-up to this, Kateryna Chernohorenko, Ukraine’s Deputy Minister of Defence for Digitalization, shares first-hand insights into how digital


transformation is shaping modern warfare (p61). These lessons are deeply relevant to NATO’s readiness, as conflict is increasingly fought as much in cyberspace as it is in the physical domains.
NATO’s collective defence lies in the credibility of Article 5, which is based on the strength of our forces, the unity of political will across the Alliance and the ability to respond swiftly and decisively. As the Alliance adapts to today’s unstable security environment, readiness is built in the field, through operations, missions and exercises. These are the proving grounds, where our impact at NCIA is most tangible. We enable NATO’s operational commands with the capabilities they need, ensuring that mission-critical data can flow reliably, securely and in real time.
Over the past year, this mission has only grown in significance. In 2024, we supported more than 130 NATO exercises, enabling 72,000 participants to train in realistic, cyber-resilient environments. As our colleague Major Derek Aubin outlines, Loyal Leda — a major exercise of Alliance collective defence — demonstrated NATO’s ability to operate seamlessly across domains (p97). Similarly, as former Exercise Staff Officer Darius Žibalis explains, Steadfast Dart enhanced our ability to rapidly deploy secure and reliable communications under pressure (p94).
As NATO undergoes its most significant military transformation in decades, the creation of the Allied Reaction Force represents a bold leap forward. In his article, Lieutenant General Lorenzo D’Addario describes how this high-readiness, multi-domain force offers the Alliance immediate deterrence and decisive
capability (p22). Supporting such initiatives demands the very best from NCIA, agility, innovation and deep operational understanding.
This summer, the Alliance will come together for the NATO Summit in The Hague, an occasion of particular relevance to NCIA. With our major campus based in this beautiful city, we have a special role to play in supporting the summit and showcasing how our people and our technologies are driving NATO’s digital transformation.
As NATO’s Secretary General has emphasized, the summit will address NATO’s long-term adaptation, including readiness, resilience, innovation and defence production. These are areas where NCIA contributes daily — from advancing secure connectivity and cyber defence to integrating disruptive technologies such as quantum and artificial intelligence into NATO’s digital ecosystem.
This year will be one of bold progress, but progress is only possible through delivery. We are living in an era defined by both opportunity and uncertainty. Technology is transforming defence and threats are evolving at speed. Yet the fundamentals remain unchanged: we must be connected, resilient and ready, and we must do this together — alongside our Nations, with our Partners, and each other.
Thank you for joining us for this edition of NITECH. I invite you to read on and discover how NATO and NCIA are working every day, to stay ready for what’s next.































Multi-domain operations require rapid decisional superiority across all domains. The Airbus Multi-Domain Combat Cloud empowers operational system-of-systems by integrating sensors and effectors, coupled with command and control to ensure digitised, AI-enhanced and cyber-resilient missions. This allows forces to act as one and help to keep the world a safer place.


























Mark Rutte, NATO Secretary General
“If you want peace, prepare for war” is a concept attributed to the ancient Roman philosopher and military strategist Vegetius. The idea is simple: make your defences so strong that no one dares to attack you. From the bow and arrow to the battle tank, having strong and ready defences backed by the latest technologies has always been key to deterring aggression and keeping us safe. For more than 76 years, peace through strength has made NATO the most successful defensive Alliance in history.
Today, however, NATO’s military edge is being aggressively challenged. Russia has brought industrialscale conflict back to Europe and put its economy on a war footing. China, Iran and North Korea are providing decisive support to Russia’s rapidly reconstituting war machine. These countries are deepening their cooperation and they are investing heavily in new capabilities, from artificial intelligence (AI) to hypersonic weapons, which have already been tested on the battlefield. We are not at war, but we are not at peace either. We face intense strategic competition, turbocharged by the latest technologies, from those who threaten our interests and way of life.
NATO is responding by increasing our readiness and investing in our defence. We have carried out the most significant transformation of our Alliance in a generation and accelerated these efforts following Russia’s full-scale invasion of Ukraine. NATO now has the most robust defence plans in place since the Cold War. They define how we will defend every corner of Allied territory, with the right forces, resources and capabilities. We have increased the number of troops on high-readiness across the Alliance, ready to respond to any threat across all domains, land, sea, air, space and cyberspace. Together, European Allies and Canada have invested an additional US$700 billion in defence in recent years and many Allies are now going further and faster.


Maintaining our military edge, however, will not only be determined by our continued investment in conventional capabilities, but increasingly by our ability to develop and adopt new technologies at speed. NCIA plays a crucial role in this effort, delivering digital solutions and resilient communication and information services. Strong cyber defences, secure supply chains and societal resilience matter in a world where access to microchips defines our military superiority as much as missiles.
We see this in Ukraine, where bits and bots have proven as decisive as bullets and bombs. The clever use of new technologies has helped Ukraine counter conventional advantages in military and manpower. The Ukrainians use $400 drones to take out $2 million Russian tanks, for example, and systems such as GIS Arta use data from smartphones and drones to match targets with the closest capabilities to strike them, dramatically increasing speed and precision, and reducing costs.
The war in Ukraine has also demonstrated, however, that technological advantage only applies until your adversary adapts to it. Innovation cycles have been as short as two to six weeks, from Ukraine deploying a new innovation to Russia neutralizing its effects. This means we need to adapt at speed and scale to stay ahead. At our Washington Summit last year, NATO leaders agreed to an innovation cooperation roadmap with Ukraine to boost our cooperation. This February, we opened the Joint Analysis Training and Education Centre (JATEC), a one-of-a-kind joint civilian and military organization with Ukraine to learn lessons from Russia’s brutal war.
Integrating these lessons and cutting-edge technologies also requires a step change in the way we work with industry. Beyond the golden age of large government-funded defence contracts, many
of today’s breakthrough technologies are developed by private-sector start-ups for dual-use in the civilian sector. NATO’s new Rapid Adoption Action Plan will substantially accelerate the Alliance’s ability to acquire and adopt innovative technologies, including through joint experimentation with industry, clearer market signals and modernising our procurement processes. We already have good examples of how NATO is deploying new technology, for example, through ‘Task Force X,’ which has piloted unmanned underwater systems in the Baltic Sea to protect our critical infrastructure.
NATO is also strengthening our Allied innovation ecosystem. NATO’s Defence Innovation Accelerator for the North Atlantic, DIANA, has selected more than 100 start-ups across the Alliance to receive funding, mentoring and support to test and develop new defence solutions in areas from data and information security, to energy and critical infrastructure. The NATO Innovation Fund, the world’s first multi-sovereign venture capital fund, will invest €1 billion over the next 15 years in cutting-edge deep-tech start-ups. It has already invested in 16 companies and funds, working in areas from AI, autonomy and quantum, to space and novel materials.
To stay safe in this more dangerous world we need to invest more urgently in both conventional capabilities and new technologies. It is not either/or, we need both. This will require a massive effort from governments, industry, academia and from all of us. Our Allied Nations put a man on the moon, split the atom and invented the internet. We have always been the ones to solve the big problems and shape the big ideas that keep our people and values safe. Together we will continue to build a strong and ready NATO at our Summit in The Hague. By preparing for war, we will continue to ensure peace.
















Grow confidently with the most comprehensive and flexible solution to meet your sovereignty needs, worldwide.
Innovate faster with our AI solutions to build, deploy, and manage AI applications.




Learn more at goo.gle/sovereign-cloud



“
THE QUANTUM REVOLUTION IS HAPPENING NOW — UNDER THE SEA!”
Quantum Leaps Beneath the Waves — Dr Pietro Paglierani, Senior Scientist, NATO Centre for Maritime Research and Experimentation (CMRE)
Quantum technology is incredibly complex and a bit mind-bending! But trust me, this article makes it accessible. I recently had the chance to visit the quantum lab at the Centre for Maritime Research and Experimentation, and seeing this tech in person was truly demystifying. Dr Pietro Paglierani paints a clear picture of how quantum advancements are becoming real-world tools to enhance navigation, secure communications and boost situational awareness in the Alliance’s vast seas. It’s a deep dive (pun intended!) into the future of maritime tech. Spoiler: You’ll never look at GPS the same way again.
“ HELICOPTERS, CYBER-ATTACKS, AND A SPECIALIST TEAM ON THE HIGH SEAS — MEET NCIA’S A-TEAM”
Cyber Security at Sea — Loic Fortemps, Head Cyber Threat Investigation Section, NATO Cyber Security Centre
Sticking with the maritime theme, my second pick has all the elements of a high-stakes thriller! This piece gives you the inside scoop on the NATO Cyber Security Centre’s Rapid Reaction Team’s first-ever deployment on a ship during Exercise Dynamic Mariner 25. This wasn’t just another exercise, it was a real test in a uniquely challenging environment. If you saw the video on NCIA’s social media, this article breaks down what happened, why it matters and how NATO is defending the digital battlespace offshore. It’s a great read, but the photos alone are worth a look.


“ THIS IS A STRATEGIC MILESTONE FOR NATO”
SATCOM Ground Stations Upgrade — Philippe Margot, NCIA Principal Project Manager
I have been fascinated by space systems and the space sector for decades. So, it is great to see military capabilities enjoy a muchneeded boost, particularly within NATO itself. David Hayhurst’s interview with Philippe Margot underscores how the Alliance is forging ahead with its space campaign by modernizing its installations into truly impressive facilities. Read how NATO stays connected and is able to communicate across the globe from the High North to the deep sea.
“AT
THE FRONT LINE, INNOVATION HAPPENS IN WEEKS, SOMETIMES DAYS. IF YOU’RE NOT EVOLVING, YOU’RE FALLING BEHIND”
Lessons from Ukraine — Kateryna Chernohorenko, Ukrainian Deputy Minister of Defence for Digital Development, Digital Transformation and Digitalization
Despite being vastly outnumbered, Ukraine has managed to outperform Russia in a number of key areas. Innovation and digitalization are absolutely critical. I was amazed when I read my Co-editor’s early drafts of her interview with the Deputy Minister of Defence, Kateryna Chernohorenko. I think readers will find her revelations about how tech is tearing down bureaucratic walls and creating unheard of battlefield situational awareness awe-inspiring. There are lessons here for everyone.

Build a comprehensive cloud architecture for sensitive workloads in national security and defence using Trusted Secure Enclaves (TSE) on AWS.
Trusted Secure Enclaves (TSE) on AWS secures mission-critical workloads through:
• Meeting strict and unique security and compliance requirements
• Providing standardized, repeatable and automated secure foundations
• Enabling access to all the benefits of AWS

Connect to our dedicated NATO Team

Defining your security posture relies on more than just the strength of technology

Every time a high-profile security breach hits the headlines, the first questions asked are technical: Was the firewall up? Was the software patched? But time and again, the source is far more familiar: a click on a suspicious link, a reused password or a red flag that was missed. As NATO and its partners continue their digital transformation, it’s essential to remember that no system is truly secure unless its people are empowered, alert and cyber-aware. The weakest link? Often, it’s not the technology. It’s us.
This is not a criticism of individuals, but a reflection of reality. And for NATO — an alliance built not only on shared systems but shared trust across nations, governments and industries, and every member of their supply chain — acknowledging and addressing human vulnerability is more than just good practice. It is a strategic necessity.
At BT, we use the term ‘cyber agile’ to describe organizations that
successfully balance security with flexibility, enabling innovation without compromising resilience. These organizations engage experts, train staff, communicate values, align security strategies with organizational ones and maintain complete visibility of not only their own IT network, but also the values and preparedness of suppliers and clients along the supply chain. Sounds self-evident enough, but its implementation requires top-level buy-in, and continuous engagement at every level.
Our research study conducted among 2,500 C-suite leaders across organizations showed that — apart from the financial benefits — cyber agile organizations also enjoy greater (customer) trust, improved efficiency and enhanced collaboration than their less prepared counterparts. The benefits, that could prove essential for an organization such as NATO, aren’t achieved through technology alone but begin with people and culture.
Cyber agile culture starts with awareness; not just of threats, but of each individual’s role in the defence against them. It’s not enough for an IT department to be skilled and alert. Every employee must understand the ‘why’ behind security protocols. Confidence and competence are critical. When people understand their responsibilities and feel equipped to act, they’re more likely to recognise risks, respond appropriately and raise the alarm when needed.
A human-centric approach can help to accelerate NATO’s digital transformation, especially as the
Alliance increasingly relies on AI-enabled, multi-cloud infrastructures. These highly distributed and complex systems involve a wide array of stakeholders, from internal teams to external vendors, suppliers and mission partners. Each node represents a potential vulnerability.
That’s why cyber agility isn’t just about NATO itself — it’s about everyone in its physical and digital supply chains. A single lapse in awareness from a subcontractor, or a careless click in a partner organization, can also have cascading effects across the entire ecosystem — it’s not just about people within NATO. Human error doesn’t respect organizational boundaries.
Embedding a cyber agile mindset across the full spectrum of organizations connected to NATO is not just done through policies, but through mindset, culture and daily practice.
But how can you begin to become more cyber agile? The first step is diagnosis. Conduct a comprehensive review of your digital environment and culture. Where are the gaps in awareness? How aligned are different departments? Are behaviours helping or hindering resilience?
From this starting point, realistic goals can be set, and leadership, teams and technologies can be aligned around them. Progress is iterative. It requires feedback loops, flexibility and honest communication. But throughout, a focus on three fundamental areas

must be maintained: empowering people, using the right tools and developing the right processes. And it all starts with leadership.
Leaders must set the tone by continuing to ensure that cyber security is a visible, shared priority by demonstrating behaviours, creating safe spaces for reporting concerns and rewarding proactive risk management. Developing a system of continuous vigilance and a sense of responsibility is key. That is why technical teams need to stay ahead of the threat curve, but non-technical staff also need continuous training and support as threats such as social engineering, which are directed at individuals personally, become ever more sophisticated. Cyber security is often seen as someone else’s responsibility, but in a truly cyber agile organization, it’s everyone’s job.
At BT, we know this better than most. As a provider of critical national infrastructure, our exposure to threats is constant. We identify more than 2,000 signals of a potential cyberattacks every second — over 200 million per day. In such an environment, there is no alternative to
making cyber awareness part of our organizational DNA. Every employee has clear obligations tied to security and must complete cycles of compulsory training to refresh and update their knowledge. And these objectives are constantly reinforced and evolve with new technologies. It is a never-ending process of learning from mistakes and encouraging cross-functional collaboration.
In spite of — or possibly because of — all these efforts, we understand that a 100% secure system is a myth because technology and the nature of cyber threats constantly evolve. What matters is how prepared your people are to recognise and respond when something does go wrong.
Cyber agility is not a luxury, a trend or a checkbox. It is a fundamental building block of a secure organization that needs to be refreshed and reaffirmed constantly, for the organization itself and the entire physical and digital supply chain.
At BT, we stand ready to support this transformation. Through innovation,
consulting, training and strategic partnerships, we help organizations become not just more secure, but more agile, more resilient and more capable of thriving in a volatile digital age. In the end, it’s not just the strength of your technology that defines your security posture. It’s the strength of your people.
www.business.bt.com


NATO’s Allied Reaction Force (ARF) Commander, Lieutenant General Lorenzo D’Addario, outlines how the newly created force offers the Alliance a strategic, high-readiness, multi-domain capability that can be deployed and employed immediately to deter aggression and enhance security
The NATO Allied Reaction Force (ARF) was established on 1 July 2024 to enhance the Alliance’s ability to respond rapidly and effectively to crises. This high-readiness force operates directly under the command of the Supreme Allied Commander Europe (SACEUR) and is tasked with ensuring the protection of NATO member countries while reinforcing deterrence across the Euro-Atlantic area.
The decision to create the ARF was made to address new geopolitical challenges, ensure a timelier response compared to the NATO Response Force (NRF) and enhance interoperability among Allied forces.
Overall, ARF provides a level of readiness and operational flexibility that surpasses that of the previous NRF. Unlike its predecessor, it can deploy at significantly shorter notice and operate across multiple domains, including land, sea and air as well as, notably, cyber and space. This makes it a
highly versatile force, capable of responding swiftly to emerging security challenges with a substantial strategic impact. Its versatility enables it to address both conventional and hybrid threats, including collectivedefence operations, crisis management and advanced deterrence. Additionally, thanks to its modular organization, the ARF can quickly adapt to the specific needs of each mission, ensuring a more effective response in complex and evolving scenarios.
The ARF is designed to be deployed swiftly by land, air and sea, depending on operational needs, and although its primary focus remains the protection of NATO’s eastern flank, it retains the capability to respond to crises anywhere within the Alliance’s area of responsibility. Moreover, the size and composition of the force can vary according to mission requirements, ensuring flexibility in addressing different security scenarios.

Consequently, the ARF plays a crucial role in NATO deterrence, providing a credible and immediate response to any threat to the Alliance’s security. Its ability to deploy quickly and operate in multidimensional environments strengthens NATO’s defensive posture, sending a clear signal of solidarity and operational readiness. Additionally, through joint exercises and forward-presence missions, the ARF helps improve collective-response capabilities, deterring potential aggressors and ensuring stability in the Euro-Atlantic area.
The HQ is located in Solbiate Olona, Italy, where HQ NATO Rapid Deployable Corps - Italy (NRDC-ITA) is based. NRDC-ITA is to be the framework of the ARF HQ up until 2028. As a multinational high-readiness command, NRDC-ITA is responsible for coordinating ARF operations, ensuring a rapid and well-structured response whenever and wherever it is needed. In order to deliver the capability, the HQ Staff is enhanced and has undertaken a specific training path to re-role as a joint, multi-domain team able to operate under the direct command of SACEUR.
The leadership of NRDC-ITA includes officers from multiple nations. The Commander and the Chief of Staff are provided by Italy, the Deputy Commander by the United Kingdom, and the rest of the staff comes from the 19 NATO Nations that are signatory of the Memorandum of Understanding. The command structure is designed to facilitate rapid planning and
mission execution, allowing for high responsiveness in crises, and its multinational composition contributes to the effective integration of the force provided by the Nations on a yearly basis.
The ARF’s size and composition are adaptable based on operational needs. For instance, during Steadfast Dart 2025 (STDT25), approximately 10,000 troops from nine NATO nations were deployed. The force included land, naval and air units, featuring armoured vehicles, fighter aircraft, warships and special operations forces. This demonstrated its ability to conduct large-scale, multi-domain operations under complex conditions.
In addition to operating in the traditional land, air and sea domains, the ARF is also equipped to address challenges in the cyber and space domains, reflecting the evolution of modern threats. NATO plans to further enhance the ARF in the coming years by investing in technology, advanced equipment and greater integration among Allied forces.
New strategies are being developed to improve ARF mobility and interoperability, ensuring an even more effective response to emerging challenges. Furthermore, the expansion of cyber warfare capabilities and the creation of specialized units to address hybrid threats are being considered, consolidating the ARF’s role as a central element in the security of the Alliance.
Supporting Interoperability, Data Synchronization, Cross-Domain Information Exchange, and Command & Control




Developed for ARBIT by MilDef — available in two compact, ruggedized configurations:
▬ Single Gateway: 1GbE, 1.5U 19”/2-rack (Pictured above)
▬ Full Cross-Domain Solution: Two 1GbE Gateways, 2U 19”/2 rack (See illustration below)
▬ Open API architecture enables seamless integration with existing systems and adaptation to evolving client-specific requirements
▬ Developed to meet rugged military standards and flexible mounting (Smaller and lighter)

Accredited for NATO SECRET – Proven for Mission-Critical Communications
Available for Market Release End of 2025. Please note: Images shown are not of the final product. Specifications and design details may be subject to change.
Arbit Solutions are designed for integration into armored CIS platforms and air defense vehicles, enabling secure, interoperable information exchange across domains - in contested environments. The systems support cross-domain Command and Control (C2), such as SitaWare, for Blue Force Tracking, Call for Fire, and more. Arbit Solutions are proven and tested in both NATO CWIX and BOLDQUEST exercises. With clients in most of Europe, as well as in Asia and North Africa, Arbit is a trusted supplier under a 20-year framework agreement with the Danish Ministry of Defence.
Artificial intelligence is essential for achieving information superiority and decision dominance — two of NATO`s key priorities


Daniael Kallfass
Senior Expert for 3D Simulation of System of Systems, Airbus Defence and Space GmbH
In the ever-evolving battlespace, how is artificial intelligence (AI) revolutionizing how military commanders observe, orient, decide and act, particularly within the context of multidomain operations (MDO)?
Modern combat is experiencing a digital transformation, requiring high levels of flexibility, mobility and efficient decision-support services. This shift is driven by several key demands:
• Increased speed and tempo: Military operations require faster action and reduced decision-making timelines.
• Manned and unmanned systems: The integration of both manned and unmanned weapon systems and sensors is essential.
• Seamless cooperation: Effective collaboration is necessary within armed forces, across organizational areas and among alliance partners.
Hans-Martin Zimmermann
Head of Engineering, Defence Digital and Cyber, Airbus Defence and Space GmbH
By combining AI methods and processes with suitable analysis simulation systems, the possibilities of accelerating decision-making processes in all phases of the military cycle can be significantly expanded. Therefore, it is crucial to involve users and foster national competencies in developing AI capabilities for the military sector.
Defence operations today require faster and closer coordinated action across multiple domains. How do you see AI supporting better decision-making in this context?
The modern battlespace is multidomain with threats and effects moving fluidly across land, air, maritime, cyber and space. This is why AI is becoming essential for managing this complexity and enabling true decision dominance. The core
responsibility of military leaders has remained consistent for centuries: analyse the situation, develop courses of action and make informed decisions.
AI is the key enabler that allows NATO forces to turn massive volumes of multi-source data into shared, actionable insight. Airbus sees AI as a support tool for platforms, sensors and mission systems. Whether it’s optimizing satellite imagery, supporting tactical decision-making or managing resilient communications in contested environments, AI is essential for achieving two of NATO`s key priorities: information superiority and decision dominance.
At Airbus, we are embedding AI as a decision-support layer across systems and platforms to enhance the full decision cycle. For instance, in our work on the Future Combat Air System (FCAS), AI helps by fusing sensor data from manned and unmanned systems, evaluating threat patterns and suggesting mission responses within a short amount of time. That data is shared via a secure Combat Cloud, giving operators and commanders real-time insight into the operational picture.
Simulation and data
exploitation are increasingly important for both preparation and operational agility. Is Airbus applying AI to these areas?
AI has become crucial in simulation because it transforms traditional analysis simulations into adaptive decision-support and rehearsal
platforms. Ongoing studies at Airbus aim to adapt successful advanced AI methods such as Deep Reinforcement Learning from games to battlefield simulations. These simulations can replicate complex military combat situations that require effective resource management and unit coordination with limited information. The training of AI agents involves developing options for a wide range of situations and terrains, and evaluating them based on their probability of success. Without doubt, Reinforcement Learning, which enables AI systems to deal with uncertainty, offers very promising results.
Deep Reinforcement Learning trains AI agents to learn complex control problems in simulated environments such as military combat. Through trial and error, the agent learns how to calculate the probabilities of success for a range of potential actions. We have learned, however, that continuous technical support and monitoring are crucial during the training process.
Airbus has also deployed AI in mission-planning environments, where it can propose multiple courses of action based on goals, constraints and likely adversary reactions. These tools enable forces to explore different scenarios quickly, which improves mission resilience and confidence. Put another way, think faster and adapt smarter.
communication.
Managing high volumes of real-time battlefield information is not an easy task. It requires advanced data
analysis capabilities that integrate data from multiple sources, including sensors, intelligence reports and historical data. That is why AI-enabled advanced sensors and surveillance systems as well as AI-enhanced data analytics capabilities are now being integrated into military platforms.
At Airbus, we’re developing new AI systems such as Fortion® Massive Intelligence, which uses naturallanguage processing, including the latest Generative AI (GenAI), to analyse messages in real time. In doing so, it is possible to extract key operational data points and patterns that might otherwise go unnoticed.
This is an area where AI can, for example, help to uncover repeated contact reports, identify silent (concealed) units and detect shifts in tactical posture based solely on communication flows. Fortion® Massive Intelligence also supports multilingual environments, thus helping multinational NATO teams operating on a shared semantic footing. In recent trials, this system significantly reduced operator cognitive load, enabling greater focus on what matters most while maintaining full situational awareness.
In collaboration with the German MoD, we are currently conducting a range of studies, including Artificial Intelligence for Tactical Chat in Simulation Systems (KITCH — its German name) to explore how GenAI can be utilized to automate military processes, including planning and monitoring activity. This involves leveraging GenAI to automatically integrate information from a comprehensive database containing all national and NATO regulations, tactics and other documentation, as well as utilizing tools such as simulations.
As NATO moves towards more connected and data-driven operations, how is Airbus ensuring interoperability and responsible use of AI?
We design all our AI capabilities using open, modular architectures that align with NATO standards and federated networking principles. Whether it’s satellite intelligence, airborne platforms or ground-based command and control (C2) systems, we ensure our solutions can share data seamlessly and securely across NATO forces.
The goal of AI is not to replace human decision-making. Human discretion and responsibility will always be maintained, and AI should always serve as a support tool and not as an all-encompassing stand-alone system.
We fully support NATO’s Principles of Responsible Use, ensuring that AI is governed by transparency, accountability and human oversight. Our systems are designed for AI to support the operator and never as a substitute for human judgement. We’re also investing in explainable AI, so users can understand and audit AI recommendations, which is critical in high-stakes scenarios.
Ultimately, our aim is to build trusted AI systems that enhance performance and uphold the ethical, operational and strategic values shared across the Alliance.

Efe Gürbüz speaks with Loïc Fortemps from NCIA’s NATO Cyber Security Centre Rapid Reaction Team about their recent training deployment for Exercise Dynamic Mariner 25, highlighting NATO’s growing emphasis on maritime cyber defence capabilities
What is the role of NCIA’s NATO Cyber Security Centre Rapid Reaction Team, and why is this capability essential?
NCIA’s NATO Cyber Security Centre (NCSC) Rapid Reaction Team (RRT) was established several years ago at the request of NATO member countries. Since effective cyber defence is now considered integral to NATO’s deterrence and defence strategy across all domains, the RRT plays a critical role in ensuring the Alliance can respond rapidly and effectively to cyber incidents. Its primary mission is to provide immediate, specialized technical cyber defence support whenever NATO or its Allies experience significant cyber threats.
In short, if a country or NATO entity comes under a cyber-attack, we can deploy NCIA cyber security experts, enabling the deployment of capabilities similar to those of the NATO Cyber Security Centre (NCSC), but at remote locations and in response to cyber security incidents and crises.
This capability is essential, particularly given the increasing frequency and complexity of cyber threats

facing the Alliance. As cyber incidents could severely disrupt command, control and communication systems, rapid response is essential for maintaining operational capacity and preventing potentially catastrophic outcomes.
How has the Rapid Reaction Team already enhanced NATO’s and NCIA’s cyber defence capabilities?
The RRT has become an indispensable asset in NATO’s broader cyber defence architecture. Since its inception, it has enabled rapid, targeted incident response, helping to neutralize threats before they escalate into full-blown operational crises. By deploying across different domains, including land-based and now maritime threats, the team has developed a comprehensive playbook for incident containment and recovery. These deployments have directly influenced the refinement of NATO’s cyber-response doctrines, incorporating real-world lessons into training, policy and technological innovation.
Within NCIA, the RRT serves as a valuable reference point for emerging cyber-defence practices. Their field


experiences help validate and improve NCIA’s broader cyber security frameworks and tools. Moreover, the feedback loop between operational deployments and institutional learning ensures the continuous evolution of NATO’s cyber posture. Through this adaptive approach, the RRT not only provides immediate incident resolution but also strengthens long-term resilience across the Alliance.
What was the purpose of Dynamic Mariner 25, and why are exercises like this so important to the Alliance’s preparedness?
Dynamic Mariner 25 (DYMR25), a tactical-level live exercise, sponsored by Allied Maritime Command (MARCOM), took place in the western Mediterranean Sea and Atlantic Ocean including Spanish territorial waters, from 24 March to 4 April 2025. The exercise brought together 1,500 marines and personnel, 30 ships, two submarines, amphibious units and aircraft from France, Germany, Italy, Portugal, Spain and Türkiye.
The main purpose of the exercise was to provide an opportunity to enhance the readiness and responsiveness of NATO’s maritime forces, as well as to train and improve interoperability among the staff, forces and units by ensuring that Allies stand ready to protect the sea domain in every threat environment scenario. In addition, DYMR25 marked the beginning of a new series of exercises. During this period, MARCOM also explored a cyber-related scenario involving a simulated cyber-attack on a vessel’s communication systems, offering an ideal opportunity for the RRT to deploy in a live-training environment.
Exercises such as DYMR25 are critical in ensuring the Alliance’s cyber defence strength, because they provide the opportunity to rehearse real-world scenarios, identify potential gaps and evaluate how well tools and teams perform in a controlled yet realistic environment. For NATO, which depends on seamless multi-domain interoperability, being able to simulate sophisticated cyber threats during exercises such as these is not merely a training opportunity; it’s an operational necessity.
Why was Dynamic Mariner 25 significant for the Rapid Reaction Team in particular?
DYMR25 represented a significant milestone for the RRT because it was the first deployment of the team on board an active NATO naval vessel. Traditionally, our operations have been land-based, where logistical support and reliable internet connectivity are more readily available. This maritime context posed unique challenges, including limited physical space on board, the constant motion of the vessel and severely restricted connectivity. It provided an invaluable opportunity to test and validate our readiness and operational procedures in isolated, confined and unpredictable environments.
The scenario simulated a realistic cyber incident, specifically designed to test our ability to adapt to maritime cyber threats. By operating in such demanding conditions, we aimed to enhance NATO’s defensive posture against increasingly advanced cyber threats targeting naval assets, as maritime operations heavily rely on advanced digital communication and control systems.
How did your team prepare for this complex maritime cyber mission?
Preparation for this mission involved meticulous, but high tempo, planning due to the specific challenges of maritime deployment. Firstly, we identified the most suitable personnel from existing staff based on the required technical expertise and availability. Prior to deployment, extensive communication took place with MARCOM to obtain detailed information on the affected systems and ship configurations, enabling us to select the most appropriate tools and equipment.
By understanding the isolated nature of maritime operations, we ensured that our equipment and logistics were thoroughly prepared. Every item that the RRT would need had to be packed and taken with them, as obtaining extra gear at sea would have posed complex logistical challenges. Critical items included specialized hardware and software tools capable of capturing and analysing system images and memory dumps. Satellite phones were also essential, enabling communication with NATO’s operational headquarters at Supreme Headquarters Allied Powers Europe (SHAPE) and MARCOM, especially in the face of limited connectivity at sea. Moreover, extensive thought was put into contingency planning, given that any missing equipment or oversight could severely compromise mission success.
Can you elaborate on the scenario encountered during your Dynamic Mariner 25 deployment?
During the exercise, the scenario involved a suspected ransomware infection affecting critical on-board communication systems. Initially, our information was limited to knowing that files had been encrypted and one system’s display had been compromised. Upon arrival, our immediate priority was to set up a secure
workspace aboard the vessel. After gathering further information from the crew, we were able to rapidly initiate forensic investigations.
We swiftly captured detailed forensic images of the infected systems, performed advanced malware analysis and recovered potentially deleted artefacts. This comprehensive approach enabled us to pinpoint the malware precisely, assess its operational impact and confirm that it was contained within a single compromised system. By isolating and neutralizing the malware quickly, we prevented any further operational disruptions, and helped the crew regain operational access to their systems.
What critical lessons did the Rapid Reaction Team take from Dynamic Mariner 25 that will inform future deployments?
Each deployment provides valuable insights, and Dynamic Mariner 25 was particularly instructive. A primary lesson was the importance of complete self-sufficiency and exhaustive pre-mission preparation when operating in isolated maritime environments. It reinforced the necessity of anticipating logistical, technical and environmental challenges specific to naval deployments.
The experience underscored the need for robust contingency planning, enhanced equipment management protocols and the refinement of operational strategies tailored specifically to maritime cyber defence. By documenting these insights comprehensively, we are continuously improving our readiness, adaptability and capability to respond effectively to future maritime cyber incidents, thus strengthening NATO’s overall cyber defence capacity.

Hugh Carroll, VP of Corporate and Government Affairs, Fortinet Alessandro Liotta, EMEA Regulatory Affairs Lead, Fortinet
Fortinet has been a leader in the ‘Secure by Design’ effort, how do you implement this approach?
Fortinet is proud to be one of the companies leading the collaboration between the US government and industry to develop voluntary goals and approaches that will build our collective cyber resilience by ensuring that IT and communications products are Secure by Design and by Default.
Since being an early signatory to CISA’s Secure by Design pledge last year, Fortinet has made significant progress in implementing its specific goals. Examples of this progress include eliminating default passwords during the installation process, selectively implementing automatic updates for products used by the customer groups that are least likely to patch, and disclosing the class of software weakness associated with a Fortinet Common Vulnerabilities and Exposures listing.
Fortinet is committed to adhering to robust product security scrutiny at all stages of the product development lifecycle, helping to ensure that security is designed into each product from inception all the way through to end of life.
Why should NATO help push this important concept?
Secure by Design is a valuable tool for enhancing our collective cyber security but requires government support to push adoption by vendors and demand by customers. Although it’s encouraging that many vendors have embraced these principles, more work is required. Implementing Secure by Design practices comes at a cost for
manufacturers, and vendors are more likely to spend resources if they see a market requirement from customers in the public and private sectors. Technology buyers should demand that their vendors embrace Secure by Design and that they share their progress in meeting pledge goals. In other words, Secure by Design should be matched by a signal for ‘Secure by Demand’ products in the marketplace.
Increasing the security of the IT products NATO’s members rely on across both their public and private sectors will improve the Alliance’s cyber resilience, and technology producers are more likely to commit resources if they see a market demand from NATO’s members for greater product security. As a company, Fortinet looks forward to continuing to work with our partners in both the public and private sectors to advance the Secure by Design philosophy. Together, we will build a safer and more resilient digital future for all.
Why is Fortinet’s approach unique in terms of responsible transparency and vulnerability disclosure?
Because of Fortinet’s commitment to product security, the majority of Fortinet vulnerabilities discovered in 2024 were identified internally. This proactive approach to seeking out and finding potential vulnerabilities enables us to develop and implement fixes before malicious exploitation can occur. We also work closely with our customers, independent security researchers, consultants, industry organizations and other vendors to identify issues.
Timely and ongoing communication with our customers is essential in our efforts to help protect and secure their organizations. All remediated issues, whether internally or externally discovered, are transparently and responsibly published through channels such as our Monthly Vulnerability Advisory, published on the second Tuesday of each month.
The Fortinet Product Security Incident Response Team (PSIRT) policy diligently balances our commitment to the security of our customers and our culture of researcher collaboration and transparency. This continued commitment to responsible development and disclosure empowers our customers to make informed, risk-based decisions about their security.
How does Fortinet stay at the forefront of cuttingedge technologies in artificial intelligence (AI), machine learning (ML) and quantum computing?
Fortinet has been at the forefront of cutting-edge technologies such as AI and ML for years. Incorporating AI into our security fabric, Fortinet’s platform provides protection across an organization’s digital attack surface. Our response centers on an integrated approach that leverages AI-driven technologies for proactive threat detection and response. Our solutions span from securing IoT devices to fortifying edge environments and addressing the need by users for both cutting-edge innovation and security.
While many of our competitors outsource their security intelligence from different vendors, Fortinet’s FortiGuard Threat Intelligence has
been built in-house, enabling us to apply AI consistently across different sources to expand the scope and scale of how and where it can be used.
To counteract emerging cyber threats, organizations must also adopt quantum-safe encryption techniques that can withstand quantum computing advancements. Making the shift towards adopting quantum-safe encryption is a collaborative effort requiring input from researchers, policymakers and industry leaders.
Ensuring data security for the future demands a collective commitment to innovation, standardization and the adoption of quantum-safe encryption practices. Fortinet has already introduced quantum-safe security solutions, including integrating the NIST Post-Quantum Encryption (PQC) CRYSTALS-KYBER algorithm in FortiOS 7.6. We are doing our part to pave the way for a future where data security transcends the bounds of classical computing, ushering in a new era of quantum-safe communications and cryptography.
NATO faces cyber adversaries who are likely to be among the first to develop cryptographically relevant quantum computers and to be early adopters of quantum attack technology. By investing in quantum-safe solutions today, NATO members can future-proof their cryptographic infrastructure, ensuring resilience in the face of rapid technological advancements that may occur with little warning. While the transition to quantum-safe encryption is complex, the benefits of securing sensitive data far outweigh the costs.
What is Fortinet’s strategic public-private partnerships approach and why is it vital for disrupting global cybercrime?
Fortinet has a long-standing commitment to public and private partnerships with organizations that aim to boost intelligence sharing and strengthen countries’ cyber defences.
These include the Cyber Threat Alliance (CTA), International Criminal Police Organization (INTERPOL) and the World Economic Forum (WEF).
Public-private partnerships are more than just a defence against a growing list of threats — they are a catalyst for the cyber security industry’s growth and maturity. As the saying goes, “a rising tide lifts all boats”. And when we establish a foundation of collaboration and trust through public-private partnerships, we set higher standards for security practices that enable our collective cyber resilience to improve. As the threat landscape grows increasingly complex, the industry must embrace these partnerships as essential rather than viewing them as optional. The future of our industry depends on our ability to work together, relying on our collective expertise to protect organizations and individuals around the world.
How can Fortinet support regulatory compliance and innovation?
Efficient frameworks for secure information sharing will likely start to become more clearly defined from 2025 as NIS2 and CRA implementation takes shape. Public and private organizations must embrace compliance frameworks that facilitate collaboration while ensuring robust data protection.
As the need to move systems to the cloud increases across NATO and national defence ministries, ‘data sovereignty’ is already becoming a buzz phrase, encompassing anything from the desire to set data localization boundaries to maintaining jurisdiction over their most critical and valuable asset: data.
At Fortinet, we’ve been deeply engaged in helping organizations navigate the complexities of Europe’s regulatory environment. Here’s how we’re making a difference:
We will continue to work closely with European authorities to share insights on how regulations impact businesses and to advocate for practical, effective solutions.
and Partners: We are committed to helping organizations navigate this evolving regulatory landscape and ensure their compliance strategies are as seamless and efficient as possible. Our tailored solutions and experienced insights simplify compliance and enhance security.
Development: Through initiatives such as our European Commission Cyber Security Skills Academy pledge, we’re addressing the skills gap with robust training programmes. We also offer accessible training and certifications through our Fortinet Training Institute. Upskilling isn’t just about filling immediate gaps — it’s about creating a workforce ready to meet the demands of an increasingly complex threat landscape.
Our certification under the US-EU Data Privacy Framework and the appointment of our Data Protection Officers demonstrates our commitment to upholding the highest standards of data protection.
This year is shaping up to be pivotal for cyber security in Europe. As new regulations enter into effect and organizations move into implementation mode, the focus will shift from compliance as a checkbox exercise to a more collaborative and strategic effort.



NATO Acting Assistant Secretary General for Defence Policy and Planning, Marie-François Gougeon has worked on a centrepiece of NATO’s adaptation and one of its core tasks: the deterrence and defence agenda. This has been critical for sharpening the Alliance’s overall readiness. He outlines to Simon Michell what the agenda covers, and highlights the important role NCIA has played in its development
Why has it been necessary to increase NATO readiness levels, and is the requirement more important now than it was before Russia invaded Ukraine?
Our world has become more contested and unpredictable. Not only since 2022, but back in 2014, NATO started shifting back to a focus on great power competition, resulting in a new baseline for collective defence. At the same time, within its three core tasks, the Alliance has certainly not lost sight of the constant threats from terrorism and regional instability.
NATO’s strength, lying in its ability to adapt to the ever-changing security environment, led to a significant overhaul from being prepared for a ‘war of choice’ to a ‘war of necessity’. After the end of the Cold War, NATO’s efforts initially concentrated on shaping European security by dialogue and cooperation. It then gradually shifted its focus to address terrorism. Now, NATO’s main focus is, once again, on being ready for a potential attack on the Alliance.
“Si vis pacem, para bellum”, a Latin adage translated as “If you want peace, prepare for war”, can be seen as the underlying principle of NATO’s deterrence and defence agenda. In this vein, NATO is prepared and ready to defend against all threats from all directions, based on a multi-domain, 360-degree approach with the primary aim of discouraging any potential aggressor from an attack in the first place.
What role has the NATO Defence Policy and Planning (DPP) Division played in assisting the Alliance achieve greater levels of readiness, and how will it support this continued effort in the future?
Against the backdrop I have just outlined, the DPP Division has the lead on handling policy related to its re-emphasis on collective defence through its military adaptation. In coordination with military authorities, DPP is in charge of developing policy related to strategic planning, organization of forces, command and control, logistics, enablement and resilience. Ensuring political
support for the strengthening of the Alliance’s military posture and the improvement of our ability to respond to any aggression is at the core of DPP’s agenda.
To this end, we have, for instance, supported the adoption of the NATO Force Model, which calls for generating more forces across all domains at higher readiness levels — 500,000 troops ready within 30 days. DPP has equally supported the strengthening and rapid forward enforcement of the Alliance’s eastern flank in the form of its Forward Land Forces. Today, these consist of eight battlegroups, with a ninth in the making. All are scalable up to brigade level. In addition, the DPP-led NATO Defence Planning Process (NDPP) ensures that Alliance defence plans are met with the necessary capabilities, both in quality and quantity as well as in the short, medium and long term. In this context, and with respect to the possibility of a ‘war of necessity’, today the Alliance — for the first time since the early 1990s — has aligned its operational and defence planning. Instead of providing limited, rotational, multinational contingents to prevent and manage regional crises, the Alliance is again ready for a large-scale, sustainable conventional defence from the outset and is able to create strategic dilemmas for any possible aggressor.
How has NCIA supported DPP in this effort? NCIA plays an important role in supporting DPP’s work on defence planning, one which goes way beyond computers and IT. What is less well-known, perhaps
even within NCIA itself, is the existence of a small team of operational analysts based in The Hague. These people work at the heart of the NDPP and provide an unbiased and science-based approach that underpins the whole lifecycle of the process, including political guidance, establishing requirements, apportioning targets and evaluating delivery.
This analytical work by NCIA is essential in bringing together the connected disciplines of operations planning and defence planning. By boiling down complexity, their work is fundamental in giving Allies confidence and in helping to establish trust in the likely operational effectiveness of the capabilities required, the fairness of the apportionment and the impact of the rate of implementation and sustainment of those capabilities. Essentially, NCIA applies science to the ‘art’ of political-military judgement. In doing so, NCIA creates credibility and gives confidence through knowledge to military commanders. It also provides the indispensable assurance of rigour and fairness to politicians and budget holders.
How have these heightened levels of readiness been manifested, and what operating domains are mostly affected?
In a new era of collective defence, the Alliance will need to keep pace with military modernization and expansion of any potential aggressor. This, for example, means that Allies will need to increase the readiness of their forces


across domains. For example, they will need to grow their air-defence capabilities to meet the full spectrum of missile and UAV threats. They will also need to further enhance the ability to strike deep into enemy territory, and in doing so, overcome the range of anti-access/area denial (A2/AD) and electronic warfare challenges that they are likely to meet.
Efforts will also be necessary with regards to logistics and enablement capabilities. These are of utmost importance to ensure that forces can be deployed when and where they are most needed to deter. Furthermore, multidomain command and control will require more investment in modern and interoperable communications systems. Overall, NATO will need to enhance its ability to respond in a timely manner and fight with larger land formations (divisions and corps) in complex high-intensity operations. This will require a significantly increased front-line capability than today, one that is held at readiness for warfighting against a peer opponent.
In your opinion, how will the need for even greater Alliance readiness in Europe be achieved?
In the end, and with the aim of altering the decision-making calculus of any potential adversary, readiness concerns us all. It is not just the Alliance and its Allies, but also their governments, forces, people, industries and, of course, agencies such as NCIA. It is both a national and collective task, best fulfilled by
doing it together. NATO’s defence plans and the respective aligned national plans of Allies need to be executable by trained, jointly exercised and ready forces with respective capabilities.
This vital emphasis on collective defence needs greater and more sustained defence spending and defence industries that are able to absorb these funds to deliver interoperability and innovation at scale. Greater Alliance readiness is not purely a military task; it requires a combination of military and civilian capacities and the willingness to adapt our thinking and actions. Only if NATO is strong and resilient in the areas such as energy, water and food supplies where Allies and their citizens are most vulnerable, and only if NATO has secure access to and use of key enablers such as communication and transportation systems and the maintenance of governance and associated supporting structures, can it credibly retain its readiness advantage, deter potential adversaries and defend the Alliance’s population and territory the moment it has to.
Google Cloud has refined its sovereign cloud offerings, empowering organizations to act with confidence

Like most organizations, Google Cloud is continually engaging with customers, partners and policymakers to deliver technology capabilities that reflect their needs. When it comes to digital sovereignty solutions, Google Cloud has worked with customers for nearly a decade.
Today, we’re pleased to announce significant technical and commercial updates on our sovereign cloud solutions for customers, and details on how we’re helping them achieve greater control, choice and security in the cloud — without compromising functionality.
Building on the first sovereign solutions we introduced years ago, we’ve massively scaled our infrastructure footprint globally, now consisting of more than 42 cloud regions, 127 zones, 202 network edge locations and 33 subsea cable investments.
We have also forged key partnerships in Asia, Europe, the Middle East and the United States to help deliver these sovereign solutions, including Schwarz Group and T-Systems
(Germany), S3NS (France), Minsait (Spain), Telecom Italia (Italy), Clarence (Belgium and Luxembourg), CNTXT (Saudi Arabia), KDDI (Japan) and World Wide Technology (United States).
Digital sovereignty is about more than just controlling encryption keys. At its core, it’s about giving customers the flexibility their global businesses require. It’s about enabling them to operate on multiple clouds. And it’s about securing data with the most advanced technologies.
We’ve long been committed to enabling customers to choose the cloud provider and solution that best fit their needs, and not locking them into a single option. Sovereignty in the cloud is not one-size-fits-all. We offer customers a portfolio of solutions that align with their business needs, regulatory requirements and risk profiles.
Our strong contractual commitments to our customers are backed by robust sovereign controls and solutions that are all available today. Our updated sovereign cloud solution portfolio includes:
Google Cloud Data Boundary, which gives customers the ability to deploy a sovereign data boundary and control where their content is stored and processed. This boundary also enables customers to store and manage their encryption keys outside Google’s infrastructure, which can help customers meet their specific data access and control requirements no matter what market.
Google Cloud Data Boundary customers have access to a large set of Google Cloud products, including artificial intelligence (AI) services, and can enable capabilities, including Confidential Computing and External Key Management with Key Access Justifications to control access to their data and deny access for any reason.
In addition, Google Workspace customers can take advantage of Google Cloud Data Boundary’s sovereign controls to limit the processing of their content to the United States or EU, choose a country to locally store data, and use client-side encryption to prevent unauthorized access (even by Google) to their most critical content.
Today, we are also announcing User Data Shield, a solution that adds Mandiant services to validate the security of customer applications built on top of Google Cloud Data Boundary. User Data Shield provides recurring security testing of customer applications to validate sovereignty postures.
Google Cloud Dedicated delivers a solution designed to meet local sovereignty requirements, enabled by independent local and regional partners. As an example, Google Cloud has partnered with Thales since 2021 to build a first-of-its-kind Trusted Cloud by S3NS for Europe.
This offering with Thales is designed to offer a rich set of Google Cloud services with GPUs to support AI workloads and is operated by S3NS, a standalone French entity. Currently in preview, S3NS’ solution is designed to
meet the rigorous security and operational resilience requirements of France’s SecNumCloud standards. We are expanding our Google Cloud Dedicated footprint globally, launching next in Germany.
“For France to truly embrace digital sovereignty, it is essential to have a cloud solution that marries the immense power of hyperscale technology with the strictest local security and operational controls. S3NS is committed to providing French organizations with access to advanced cloud services, including critical AI capabilities, all operated within France by a European operator to meet and exceed the rigorous SecNumCloud standards,” said Christophe Salomon, EVP, Information Systems and Secured Communication, at Thales.
Google Cloud Air-Gapped offers a fully standalone and air-gapped solution that does not require connectivity to an external network. This solution is tailored for customers in the intelligence, defence, and other sectors with strict data security and residency requirements. The air-gapped solution can be deployed and operated by Google, the customer or a Google partner.
It is built with open-source components and comes with a targeted set of AI, database and infrastructure services. Because air-gapped solutions run on open-source components, they are designed to provide business continuity and survivability in the event of service disruptions. Google Cloud Air-Gapped received authorization in 2024 to host US government Top Secret and Secret-level data.
“Working with Google Cloud to introduce sovereign offerings can give our joint clients greater control, choice, and security in the cloud, without compromising the functionality of their underlying cloud
architectures,” said Scott Alfieri, Senior Managing Director and Google Business Group Lead at Accenture. “Google Cloud’s extensive global infrastructure, coupled with Accenture’s transformation and industry expertise, helps organizations build an agile and scalable foundation, unlocking opportunities for growth and continuous innovation.”
Security and sovereignty are two sides of the same coin. Local control of data and operations can provide customers a greater level of confidence in their security, but it’s also true that no organization can be considered sovereign if dependencies on legacy infrastructure leave its data vulnerable to loss or theft.
Analysis from the Google Threat Intelligence Group and Google Cloud’s Office of the CISO suggests that the global cyber threat landscape will only become more complex as malicious actors tap into AI-powered tools and techniques to prey on older software products, platforms and outdated infrastructures.
With Google Cloud, customers not only get sovereign solutions, but also gain access to our leading security capabilities. This includes our rigorous focus on secure by design technology and deep expertise from Google Threat Intelligence Group and Mandiant Consulting, who operate on the frontlines of cyber conflicts worldwide and maintain trusted partnerships with more than 80 governments around the world.
In addition, Google Cloud CyberShield provides AI and intelligence-driven cyber defence to help governments defend against threats at national scale. And Mandiant Managed Defense services make it easy for
customers worldwide to extend their security teams with our security team.
Google Sovereign Cloud solutions ultimately enable customers to leverage the secure foundation of Google Cloud, while gaining access to advanced security features — such as Confidential Computing, Zero Trust, post-quantum cryptography and AI-powered platform defences — faster and more cost-effectively than they could achieve on their own.
We remain dedicated to fostering an environment of trust and control for our customers, empowering organizations globally to navigate the complex landscape of digital sovereignty with confidence. We continue to work with customers, partners and policymakers around the world to refine our sovereign cloud offerings and deliver technologies that address their needs.
This blog was first published on the Google Cloud blog channel on 21 May 2025. goo.gle/sovereign-cloud



NCIA’s Chief Technology Officer, Antonio Calderon , officially announced NCIA’s Technology Strategy at the 2024 NATO Edge conference in Tampa. Simon Michell asks him how the strategy will enable the Alliance to improve readiness levels and address threats to the member countries
Why does NCIA need a technology strategy and how will it enhance technology innovation and collaboration?
One of the most obvious reasons for the Technology Strategy is to help NATO maintain its treasured technological advantage in the upcoming years. To achieve this, we have to anticipate and engage with technology trends to ensure we incorporate the most impactful ones into future Alliance planning cycles.
Not surprisingly, technology is one of the three pillars of NATO’s Digital Transformation, and the NCIA Technology Strategy therefore lays out the roadmap for how we intend to meet the Digital Transformation strategic deliverables by 2030. In fact, NCIA’s Technology Strategy adopts the NATO Digital Transformation vision approved by the nations.
One of the key features of our Technology Strategy is how we developed it. We did it in full coordination with
numerous entities, including all teams within NCIA and NATO enterprise stakeholders. We also opened it up for nations, industry and academia to provide feedback to the last version before release and final approval by our Agency Supervisory Board. That made it more meaningful, understandable and aligned with realworld trends, so our various stakeholders can use it to align our roadmaps with theirs and vice versa.
In terms of impactful collaboration, the Technology Strategy outlines one of the strategy’s key tenets — the NATO Digital Foundry (NDF). This is a new NATO-wide concept that will establish an open and secure platform for rapid technology adoption, innovation and acquisition. It is a hybrid environment (virtual and physical) that seeks to interconnect and streamline existing Labs and enable collaboration among the entire NATO community, including external stakeholders such as not-for-profits (NFPs), industry and academia.

What are the technology themes of the strategy and why were they chosen?
Through extensive consultation with the entire NATO community and the stakeholders I mentioned earlier, we have selected six technology themes, and within them, we have deliberately sought a subset of technology strategic initiatives that we anticipate will have the greatest impact.
We are adopting a dual-track approach, where, on the one hand, we have identified mature areas, such as cloud and data exploitation, where we aim to accelerate scaling efforts. On the other hand, we have also included lower-maturity areas, such as quantum technologies, where we can focus on experimentation and ensuring technology readiness. The six interconnected technology themes are:
Cloud Computing: This theme focuses on cloud adoption, aiming to address the sourcing, building and federation of cloud solutions. As capabilities become increasingly software-based and software-defined, the cloud’s role as an open, secure and scalable platform driving modern innovation and collaboration approaches, such as DevSecOps, has become essential.
Cyber Security and Cyber Operations: Two aspects of cyber security are of particular interest. The first is the introduction of modern cyber security architectures and best practices to ensure the secure and resilient delivery of
ICT (information and communication technology) services. The second is focused on supporting cyberspace operations as one of our operational domains.
Data Exploitation: The aim here is to leverage data as a strategic resource to contribute to cognitive and decision superiority and to enable multi-domain operations (MDO). It is not only artificial intelligence (AI), but also a wider pillar that looks at how, when and where we can manage and exploit data, and how different technologies are interrelated to make the most of our vast amount of NATO data.
Next-Generation Networks: The Next-Generation Networks (NGN) theme hopes to deliver static and deployable secure, resilient communication services that have high throughput and low latency from our core to the edge. They should also be integrated, standardized and interoperable. NCIA is already delivering successful initiatives in the NGN arena, such as the MN5G multinational project, which has been covered by NITECH in earlier issues.
Quantum Technologies: Despite being relatively new for defence use cases, quantum technologies are expected to have a significant impact on NATO operations by 2030, particularly in defensive areas such as algorithms, computing, communications, cryptography, key distribution, Precision Navigation and Timing (PNT), programming languages, random

number generators and sensing/imaging. Quantum’s potential offensive threat to NATO operations and security also needs to be considered so we can anticipate risk mitigations.
Space Technologies: Space offers a unique and expanding opportunity for the transformative application of technology to enable NATO MDO. The operational significance of space continues to accelerate, driving two key aspects: the need to guarantee NATO’s access to essential space data, products and services (DPS) and capabilities, as well as limiting the use of space-enabled and space-based systems against NATO, once again, is all about anticipating countermeasures.
Can you describe what the NATO Digital Foundry will be and how it will assist with the implementation of the Technology Strategy? NDF aims, among other things, to integrate across various experimentation, developmental, testing and reference environments. The goal is to provide unified access to technology to the community of innovators across the Alliance and its wider stakeholders. NDF also aims to establish a unified environment for data sharing
to enable innovative digital solutions. This will allow innovators to gain access to data catalogues as well as datasets to accelerate their development cycles. In other words, you come with your innovative product, and we offer you the interconnectivity with the rest of NATO capabilities to test it with.
Through the NDF, we also aim to achieve interoperability across innovation efforts throughout the Alliance. By adopting ‘Everything-as-Code’ and consistent DevSecOps philosophies across NDF environments, we expect to reduce the friction between development environments across NATO entities, industry, Nations and NFPs.
To further facilitate collaboration, the NDF will also include a secure physical space open to Alliance innovators designed to enable co-development of digital solutions. We are also building an NDF community, which serves to bring together Alliance innovators, so that we all pull in the same direction.
NDF aims to test, verify and validate new products and systems and ensure two key requirements: MDO
interoperability with our existing C4ISR capabilities and cybersecurity compliance levels towards accelerating security accreditation. Equally important, together with our colleagues in Acquisition, we also aim at offering NDF as part of our acquisition platform to the NATO Enterprise and Nations, leveraging the work being done on our Rapid Adoption Service we have in place with DIANA — Defence Innovation Accelerator for the North Atlantic.
How will the Technology Strategy support further development of multi-domain operations?
NCIA’s Technology Strategy directly adopts the NATO Digital Transformation vision, which is: “By 2030, NATO Digital Transformation will enable the Alliance to conduct multi-domain operations, ensure interoperability across all domains, enhance situational awareness, and facilitate political consultation and data-driven decision-making.”
More specifically, the Data Exploitation Technology theme directly contributes to MDO by delivering cognitive and decision superiority, as well as enabling the exchange, aggregation and processing of data across domains. The Space and Cyber Security themes directly contribute to technology readiness and advantage in their respective domains.
The Cloud and Next-Generation Networks themes will introduce new technologies leading to automation and the formulation of domain-specific systems, which will allow for the development of cross-domain digital solutions, including interfaces with Non-Military Instruments of Power (NMIoP).
While the Quantum Technology theme has direct relevance to the cyber security domain in the near term, we also anticipate that quantum technologies can deliver technological advantage to situational awareness, Intelligence, Surveillance and Reconnaissance (ISR) and Computer Information Systems (CIS) capabilities across the five operating domains.
Why will the development of cyber-immune systems enhance cyber security?
An important element of cyber security is availability. The development of cyber-immune systems will directly enhance the resilience of our CIS systems, while also reducing the ‘time-to-recovery’ for critical operations such as repair, isolation and failovers.
In many ways, cyber-immune systems can be thought of as minimizing the human intervention needed for the protection and continuous operation of our CIS systems to combat the increasing sophistication and autonomy of cyber threats.
What role will quantum technologies play in the strategy?
The most talked about sub-theme in the Quantum Technologies theme is securing NATO data and communications from the threat of Cryptographically Relevant Quantum Computers (CRQC) that could be capable of breaking existing cryptography and encryption methods. To this end, the Technology Strategy advocates for the development of communications capabilities that are resistant to quantum-computing attacks by leveraging technologies such as Quantum Key Distribution (QKD), Quantum Random Number Generation (QRNG), and, in the longer term, quantum networks and communications.
In addition, there are two other areas where quantum technologies can deliver a technological advantage to NATO. The first is sensing, the second is information science and quantum computing. The first can contribute not only to cognitive superiority, but also to the resilience of ISR capabilities. The latter can establish technological advantage in modelling and simulation, leading to a significant improvement in the decision-making and operational effectiveness of NATO operations — particularly given the added complexity of MDO.
What are some key success factors for a successful implementation of NCIA’s Technology Strategy?
Funding and workforce are obvious areas where we need to consciously allocate and prioritize resources to the 17 strategic initiatives outlined in the Technology Strategy — starting with the NATO Digital Foundry. Having a digital-ready workforce will ensure that we recruit, retain and retrain the right skills so that we are always ready to engage with and exploit emerging technologies.
As I have already highlighted, collaboration is key, especially with industry, NFPs and the NATO Nations. And, last but not least, ‘Smart Sourcing’ will enable us to tap into industry, academia and the Nations to ensure that NCIA can rapidly procure the latest advancements in digital technology matching the urgent capability needs of NATO. MDO readiness is all about going faster together.
Taking the decisive approach for organizations in the current threat environment


How can data-centric security improve an organization’s information security beyond perimeter security?
Traditionally, much of the effort related to technical information security control focuses on securing the perimeter. To do this, an organization first defines trust zones and then reduces the risk of an adversary breaching the perimeter and entering them. Within a trust zone, there is implicit trust between humans and machines. So, in theory,
data and processes that are handled within a trust zone should be secure, based on the effectiveness of the existing perimeter security controls and the implicit trust.
In practice, however, there is always a risk of an attacker gaining access to a trust zone and thus to the assets within it — data and processes. Furthermore, there is an increasing need to communicate data outside a trust zone with, for example, external partners. Consequently, relying only on traditional perimeter-focused measures means that it is impossible to control the data once it leaves the trust zone. Data-centric security, on the other hand, enables an organization to retain control, even over shared data, with the help of encryption, tokenization or rights management. To some extent, data-centric security also aligns with the ‘assume breach’ principle of the zero-trust approach.
In general, to what extent would this be enough to keep malicious actors off an organization’s network and prevent attacks?
Reducing the risk of threat actors breaching perimeter controls to 0 percent is an impossible task. That said, data-centric security adds multiple additional layers of security to an existing security infrastructure. This is achieved by attaching controls such as encryption and attribute-based access control (ABAC) at a highly granular level to sensitive data, including PII, IP or classified information. Consequently, even if a threat actor gains direct access to the files containing
sensitive data, they cannot process them without the respective decryption keys or the permissions that are required by the ABAC solution that has been put in place.
How can data-centric security help reduce insider threats?
Total reliance on perimeter security implies that threats are mostly external by nature. In reality, insider threats can also originate from employees and partners, both current and former, who have, or had, access to internal systems. Such threats are common and pose a significant risk. This is also the case when business relationships change but permissions do not get revoked, for example, after the dismissal of an employee or the termination of a business/work relationship with a partner organization. Other examples of potential threats include apprentices, interns and students undertaking work experience, especially if they move from department to department of an organization.
A key concept of data-centric security is the implementation of dynamic access policies and attribute-based access control (ABAC). In contrast to a role-based approach, ABAC permissions are granted based on attributes that are attached to a specific user or machine rather than on the role that person or machine undertakes. Users might, for example, only be able to access certain files if they are physically located in a specific location and/or during specific times of the day. If any of these attributes do not match the requirements, permission to access the files will not be granted. It is even possible to grant (or revoke) permissions for whole
communities of interest, based, for example, on changing geopolitical circumstances. In this way, misuse, whether unintentional or malicious, can be significantly reduced.
Which workflows in today’s highly interconnected business and IT environments can be supported by datacentric security and how?
Data constantly moves between trust zones and partners that might belong to different organizations with diverse security postures, requirements and, especially, security maturity levels. Data also moves through cloud services, SaaS solutions, hybrid work environments and other platforms. In such cases, data-centric security binds security controls cryptographically to sensitive files, ensuring continuous protection of the information regardless of where the data is located or through which communication points it moves.
What role does industry regulation play and is a data-centric approach compatible with it?
Regulations such as GDPR, NIS2 or NIST SP demand control over how sensitive data is stored, used and shared.
Data-centric security enables an organization to comply with the regulatory requirements regarding data through the use of encryption and attribute-based access control.
Additionally, data-centric security requires organizations to make use of monitoring functions in order for it to be effective. This, in turn, enables the creation of compliance checks and the setting up of relevant reporting processes, which strongly support audit activities related to these regulations.
How does data-centric security support incident response activities?
Even data-centric security will not be able to fully prevent security breaches. However, when a security breach occurs, it is a strong indicator of failed perimeter security controls. But with data-centric security in place, the additional security layers are likely to reduce the impact of a potential breach. Therefore, even if an attacker gains access to sensitive files, they will almost certainly not be able to decrypt them without the required cryptographic keys. This also reduces the impact of breaches that occur on a partner organization’s infrastructure.
Zero-trust architecture has been a prominent concept of information security for decades. What is the relationship between zerotrust architecture and data-centric security?
The zero-trust approach consists of four fundamental principles, and data-centric security supports at least two of them — ‘assume breach’ and ‘least privilege’. Assume breach implies no implicit trust, even inside the perimeter. Least privilege means no system, and no user — internal or external — is able to access files based solely on their roles or affiliation to a certain network. Data-centric security aligns perfectly with this approach as it ensures that trust and verification happen at the data level, not just at the network’s entry or exit points. Some experts might even say that data-centric security is the fifth principle of zero trust.
How does infodas support nations and alliances in the data-centric security approach?
By developing information security solutions, such as the SDoT product family, we ensure that our clients are ready to tackle previous and future security challenges.
Our cybersecurity consulting services are tailored to the unique needs of defence, public sector and critical infrastructure, ensuring compliance with international regulations paired with the use of actual security paradigms like DCS, thus enhancing overall cyber resilience.




The 2024 NATO Industrial Capacity Expansion Pledge represents a very substantial reaffirmation of the commitment by NATO and its member countries to enhance readiness by thoroughly and systematically accelerating defence industrial capacity and production across the Alliance.
The long-term objectives of the pledge involve strengthening industry through reciprocal and enhanced cooperation among Allies, and developing and sharing individual national plans and strategies. It also urges increasing and accelerating large-scale joint procurement (including through multinational programmes) in accordance with national plans. In addition, it promotes strengthening the implementation of standards to increase interoperability as well as speeding up the adoption of new technologies. Further aspirations include ensuring that urgently needed critical capabilities can be delivered in a timely manner, removing barriers to trade and investment, securing defence-critical supply chains and enhancing cooperation with NATO partners and Ukraine.
NATO Head Policy, Plans and Partnerships, Strategy Defence Investment Division, Zoe White and Pablo González from the NATO Industrial Advisory Group tell David Hayhurst how a new NATO Industrial Capacity Expansion Pledge is helping to accelerate defence industrial capacity and production across the Alliance
The pledge has taken the Defence Production Action Plan of 2023 as a blueprint for understanding the challenges being faced. Zoe White, Head of Policy, Plans and Partnerships from NATO’s Defence Investment Division, thinks the plan was integral in enabling the current reset, which strives to provide a better understanding of demand aggregation, defence industrial challenges, as well as interoperability and standardization concerns.
“Over the past 30 years, NATO Allies have been focusing more on ‘just-in-time’ production and on efficiency in terms of cost. The Allies have an incredibly strong and robust industrial base, but we weren’t looking at it deeply enough from an Alliance collective perspective,” she says.
NEW PARTNERSHIP FRAMEWORK
Pablo González, Director of NATO and European Defence Programmes at Indra, and head of a new NATO Industrial Advisory Group (NIAG), feels that a new partnership framework needs to be created between industry and Allied defence ministries to greatly accelerate procurement, development and deployment as well as to facilitate risk sharing and to increase productive capacity.

As part of industry’s commitments to the Action Plan, he says, “We need not only to be able to produce much more hardware such as munitions and missiles, but we also need to change our culture in today’s digital world, to be able to evolve software in near real time to counteract the evolution of threats which adversaries can pose, mainly in the fields of electronic warfare and cyber technology. This is another way of doing digital production that demands far closer industry/government cooperation.”
González stresses the need to adopt different methodologies for both testing and speeding up the integration of new technologies: “There are some elements of the ‘war economy’ that you can develop in a time of crisis in order to test new technologies. Up to now, you could only test the technology when it was very mature. This is not the right way. In a conflict situation, you go with the technology immediately, to test it quickly, to learn from operational experiences.”
As part of the pledge’s call for optimal delivery of critical capabilities in accordance with the NATO defence-planning process, battle-decisive munitions and air and missile defence systems are currently considered priorities, both to support Ukraine and as part of wider objectives.
Both the newly created Defence Industrial Production Board and the NIAG are currently working closely with the Conference of National Armaments Directors (CNAD) to
better understand how to help governments and industry achieve more cost-effective and efficient procurement and production policies for refilling depleted munitions stockpiles, along with related issues.
In future, this will involve more joint procurement, including through multinational programmes, in accordance with national plans. In 2024, the NATO Support and Procurement Agency (NSPA) enacted more than €8 billion worth of new ammunition contracts, including €600 million for Stinger missiles and €5 billion for procuring 1,000 Patriot missiles.
The latter is also an example of how NATO wants to utilize the aggregation of demand as a tool for incentivizing an uplift in industrial production capacity. The Allies’ commitment to acquire such a large number of missiles stimulated industry, which committed to establishing a new production facility in Europe to respond to these new requirements.
“We encourage Allies in setting up these kinds of arrangements more broadly moving forward by building on the outputs of the dedicated new NATO mechanisms for aggregating Allied requirements,” White confirms. “This is an area where we have been working closely with industry. We have been taking industry’s lessons and challenges and using those to support how we have developed the pledge and our policies and initiatives, because it was these lessons
from industry about cost and effectiveness and the ability to invest that have driven how we have been approaching these new initiatives.”
NIAG also recently conducted a set of highly detailed studies for the Conference of National Armaments Directors to determine which critical raw materials are of paramount importance as part of defence-critical supply chains. After identifying 12 such materials, discussions are now underway among the Allies regarding strategic stockpiling, as well as recycling, potentially sourcing alternative materials, and otherwise collectively reducing critical vulnerabilities. “It’s not only raw materials. It’s also components like chips. We have been strongly dependent on outreach for production of these kinds of things,” explains González. Presently, the Defence Industrial Production Board is engaging with member countries through three working groups, considering industrial capacity and supply chain-related concerns.
The national plans will be submitted at the next NATO summit in June and will clearly represent a major milestone in terms of commitments to capacity expansion under terms set by the Defence Production Action Plan.
While recent progress in reducing bureaucratic obstacles to increasing production in many NATO countries has often been robust, initiatives like repurposing factories take time. Moreover, as White points out, “Production is one issue, procurement is the other. We want more production from industry, but that has to go hand in hand with Allies spending more and investing more for the long-term in industry. That’s our key message to the Allies. We need to fix both the procurement and the production issues.”
White and González are confident that a successful evolution of procurement and production methodologies within the Alliance will enable the improvement of operational capabilities across all operational domains. “This will provide the best systems for the best military capabilities, improving our capability to fight together and being able to maintain a large-scale conflict over a long period if necessary. Defence industry within the Alliance will become a real deterrence factor, amplifying resilience and flexibility from a production capacity point of view, and enabling Allies to adapt and facilitate a rapid transition to a war economy in case of a conflict,” ends González.

The AWS Nitro System transforms cloud infrastructure security. Its architecture creates hardware-enforced workload isolation, including from cloud service provider operators

The AWS Nitro System transforms cloud infrastructure security design. At its core there’s a fundamental principle: isolation of customers’ workloads from AWS operators. By design, there is no mechanism for AWS operators to log into EC2 Nitro hosts, access the memory of EC2 instances, or access customer data stored on local encrypted instance storage or remote encrypted EBS volumes. Even AWS employees with the highest privileges can only interact with the system through a limited set of authenticated, authorised, logged and audited administrative APIs. None of these APIs provide an operator with the ability to access customer data on the EC2 server. These designed and tested technical restrictions are built into the Nitro System itself, so no AWS operator can bypass these controls and protections.
Traditional virtualization systems typically run device models and
management software within a privileged virtual machine, historically known as dom0 in virtualization technologies such as VMware, Xen or HyperV. AWS Nitro’s radically different approach offloads these functions to purpose-built hardware components called Nitro Cards. These cards, powered by AWS-designed System on Chip (SoC) packages, operate independently from the main system board where customer workloads run, creating physical separation between traditional software-defined hypervisor functions.
The system’s security architecture is built around three core components. The Nitro Controller serves as the hardware root of trust, using its dedicated Trusted Platform Module (TPM) to manage the server system and firmware through a secure boot process. The Nitro Security Chip extends the control of the Nitro Controller to the system main board, making it a subordinate component of the system. The minimalist Nitro Hypervisor provides only essential virtualization functions while eliminating unnecessary attack surfaces like networking stacks, peripheral drive support and file systems. It operates without any interactive access possible, further reducing its attack surface.
AWS Nitro’s three components — the Nitro Controller, the Security Chip and the minimalist Nitro
Hypervisor — make the system particularly effective against side-channel attacks. The architecture enables precise resource allocation to customer instances with minimal overhead and intrusion from the hypervisor. Central processing unit (CPU) cores are never simultaneously shared among customers. Customers receive dedicated CPU cores, even for small instances, so core-specific resources are never shared. This includes Level 1 and Level 2 caches, which can be common vectors for side-channel attacks.
Building on this foundation of hardware-enforced isolation, the system implements a passive communications design that adds another security layer. Components never initiate outbound communication. Instead, they respond only to authenticated and authorised commands through well-defined APIs. This design creates clear security boundaries, as any attempt by system components to initiate unexpected communication is immediately flagged as a potential security breach.
For Input/Output (I/O) operations, AWS Nitro employs dedicated hardware cards that process customer data independently from the main system. These cards implement encryption for networking and storage through a combination of hardware offload engines and secure key storage
integrated in their System on Chip (SoC). For EBS volumes, the system employs an encryption process where volume data keys are decrypted by AWS KMS, then re-encrypted with the specific Nitro host’s public key before transmission, creating multiple layers of encryption protection.
Encryption keys only exist in plaintext within the protected volatile memory of the Nitro Cards, making them inaccessible to both AWS operators and customer code running on the host system’s main processors. This separation ensures that I/O data processing remains isolated at the hardware function level, never residing in host memory or processor caches where it might be vulnerable to side-channel
attacks. The system supports live updates without compromising security controls, enabling AWS to rapidly respond to new security challenges while maintaining workload continuity.
For customers who want different trust levels within their own applications, for example separating sensitive cryptographic operations from general application code, AWS Nitro Enclaves provides isolated computing environments within EC2 instances. The enclaves run on dedicated CPU cores and memory that are completely separated from the parent instance, making the sensitive data and processing inaccessible even to EC2 instance administrators.
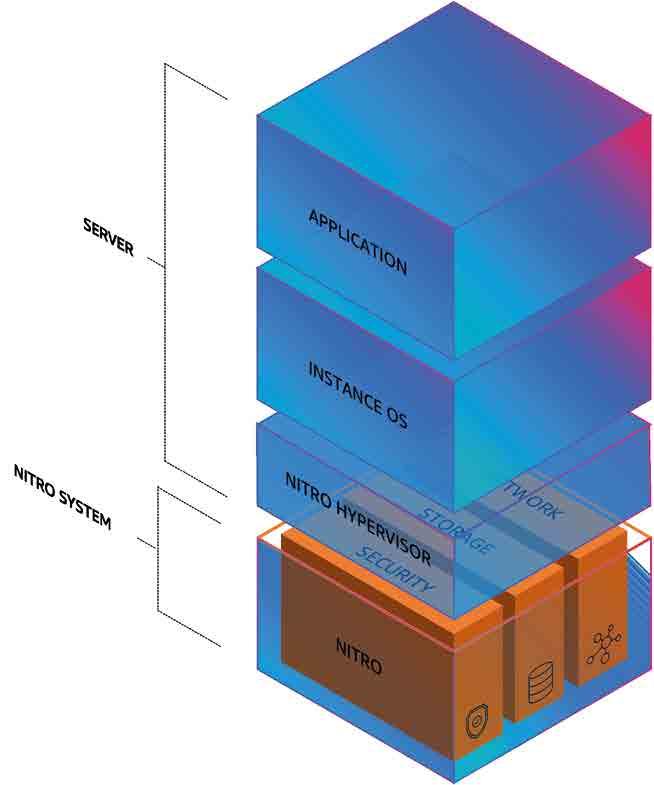
Alessandro Fusco has extensive expertise in cloud security and sensitive data protection. As a member of the AWS Global National Security and Defence team, he advises defence industry leaders about processing classified data in the cloud.



Andrew Lord, Senior Manager, Optical Networks and Quantum Research at BT offers an extensive and compelling perspective of the threats and opportunities presented by quantum computers and their associated technologies and capabilities
At once a threat, as well as an opportunity: quantum technologies cannot be ignored. Sustaining the lead in the quantum race may define the security of international organizations in a future that may be a lot closer than we think. As NATO deepens its reliance on cloud infrastructure and interconnected digital command environments, quantum secure communications offer a way to make these systems fundamentally safer. From quantum key distribution to post-quantum encryption, these innovations are set to become the invisible fabric that underpins the security of cloudcentric defence operations, offering resilient and future-proof links among headquarters, Allies, partners and autonomous systems operating at the cutting edge.
Quantum secure communications — the application of quantum principles to protect digital communications — will likely become a critical domain. As Allies and adversaries pour resources into quantum research, new global technology rivalries are unfolding.
NATO’s Strategic Concept, agreed by Allies in 2022, recognises the critical role of technology in shaping the Alliance’s future. Quantum technologies stand out as a key enabler of secure, scalable digital transformation
and could play a key role in securing access to the multi-cloud infrastructure in which NATO’s apps and data are securely processed and hosted. Although the full potential of quantum technologies has yet to be realized, it is important to note that progress in their development is moving at pace, no more so than in quantum secure communications, where BT has achieved significant milestones in its proof-of-value trials in the UK. We believe it deserves its place in NATO’s forward-looking technology roadmap.
Quantum technologies cover many areas, but two of the most urgent for NATO are quantum computing and quantum secure communications. These are separate but closely linked fields.
Quantum computing uses quantum bits (qubits) to solve problems too complex for classical computers, with potential breakthroughs in logistics, materials science, weather forecasting and codebreaking.
But this power comes with risk: quantum computers will eventually be able to break today’s encryption. Sensitive data — like diplomatic messages, satellite links or

defence communications — could be intercepted now in transit across networks and decrypted later. This is known as the ‘store now, crack later’ threat.
In response to the many unavoidable challenges on the horizon, there is a great incentive to invest in quantum secure communications, which aims to future-proof networks against quantum-enabled adversaries. Such a need is evident in the public and business sphere, but is incredibly urgent in NATO’s own multi-cloud military ecosystem.
QUANTUM SECURE COMMUNICATIONS: THE FOUNDATION OF FUTURE-PROOF NETWORKS
Quantum secure communications primarily encompass three pillars:
• Post-Quantum Cryptography (PQC) – encryption methods created for both conventional and quantum computers, which are designed to resist attacks from quantum computers. These algorithms typically rely on mathematical problems that are believed to be hard for both classical and quantum computers.
• Symmetric Key Cryptography (SKC) involves encryption techniques that use symmetric key
encryption (SKE), that is, where the same secret key is used for both encrypting and decrypting information. It is used in many protocols and systems today, such as AES (Advanced Encryption Standard), which underpins secure communications, VPNs and data-at-rest protection. These are considered quantumresilient when cryptographic key lengths are extended to mitigate the quadratic speed-up offered by quantum computing.
• Quantum Key Distribution (QKD) is a cutting-edge communication method that enables two parties to generate a shared, secret cryptographic key by using quantum properties of particles — typically photons. It leverages principles such as superposition and quantum entanglement to detect any eavesdropping attempt, as any measurement of a quantum system inevitably alters it, alerting the communicating parties. That means it does not rely on mathematical complexity for its security, but the laws of physics.
Of these, QKD represents the most radical departure from current security models and also represents the central component supporting quantum secure networks.
QKD could be a game-changer for NATO. The Alliance relies on distributed decision-making, multi-domain operations, and joint cloud environments — all of which require secure communication. QKD is especially critical for protecting high-value links among command centres, operational theatres and autonomous systems. It also complements PQC and SKC by enabling secure key exchange with guarantees rooted in quantum physics.
Although QKD may seem like a future technology, its urgency is underscored by the rapid progress of the global quantum ecosystem. A ‘quantum race’ is already under way, with strategic rivals investing heavily in both quantum computing and quantum secure communication. Several countries are piloting national QKD networks, and others are turning to satellite-based QKD for global coverage.
The European Union is deploying a cross-border QKD infrastructure through the Euro QCI initiative. China has built a 4,600 km QKD backbone and launched quantum satellites. The US is advancing quantum research and deployment through its National Quantum Initiative, and the ever-increasing requests for allies to up their defence spending must also be considered.
For NATO, this is not just about keeping up — it is about leading. Adopting quantum secure technologies into its roadmap early is crucial in a world where adversaries can intercept and store encrypted data for future decryption. Solutions such as QKD and PQC provide a viable path to:
• protect data across federated, multi-cloud environments,
• secure mission-critical communication over contested or untrusted networks,
• build scalable, resilient infrastructure for NATO’s integrated command systems.
Beyond adopting post-quantum algorithms, the Alliance should also consider building a QKD and broader ecosystem that will enable secure communications at scale. Encouragingly, NATO has already begun moving in this direction.
NATO’s strategy for digital transformation has embraced the cloud — not just as a technology, but as a paradigm for operational agility. From joint cloud computing, integrated digital command environments, to federated AI tools — the cloud is central to ensuring collective security.
When talking about the cloud it is important to realize that there is not just one cloud, but many, all of which have to be interconnected. Digital workloads are
typically fragmented between different clouds, with data centres hosting those clouds located in the same or different countries. This means connectivity is of vital importance to the performance, security and resilience of commercial, sovereign and tactical applications as well as sensitive data access. This is where dense networks are needed, known as ‘fabrics’, and why BT recently launched its AI-ready Global Fabric network-as-a-service platform, which in future will include quantum secure communications services.
As these multi-cloud architectures expand, so too does the attack surface. Adversaries are already exploiting the vulnerabilities of today’s public-key encryption, and quantum computing threatens to render many of those defences obsolete.
Quantum secure communications offer NATO the tools to mitigate this risk. By enabling secure key distribution even over untrusted or degraded networks, and by providing long-term confidentiality through provably secure cryptographic methods, these technologies ensure that mission-critical communications remain protected — even against future-state quantum threats.
The path forward for NATO is clear: the evolution of its quantum secure capabilities is a necessary enabler of its broader digital and cloud transformation — providing the trust and resilience needed to operate securely at speed, across domains and at scale.
To enable quantum secure connectivity, NATO and its partners may wish to consider investing in several foundational layers:
• Projects that demonstrate both satellite QKD and Earth-space optical communications, as these are essential for validating technology in real-world conditions.
• NATO has a role to play in shaping, adopting and enforcing the international standards for QKD and PQC across its entire digital ecosystem.
• Developing scalable and agile solutions across multiple domains, including integration with satellites, edge computing nodes and future quantum data centres.
• Upskilling the workforce. Quantum technologies require specialist skills, and having a workforce, and working with partners with dedicated quantum research teams is essential.
NATO has a long tradition of driving interoperability and security through standardization and joint development. Quantum secure communications is the next logical and necessary extension of this legacy.

In the UK, public and private sectors are joining forces to position the country as both a user and developer of quantum technologies — with BT playing a leading role. As a national telecoms leader, BT has launched the world’s first commercial trial of a quantum secure metro network and demonstrated real-world QKD applications with international financial and data centre partners HSBC, Equinix and AWS.
BT is also engaged in international satellite QKD projects, in quantum sensing and shaping security assurance frameworks for emerging technologies. Importantly, it supports initiatives such as the UK government’s Quantum Missions and Euro QCI, helping align research, standards and commercial readiness. These efforts highlight a key truth: building quantum capabilities requires strategic collaboration, not isolated innovation.
NATO’s digital transformation — including its shift toward AI-driven, multi-cloud environments — will define how the Alliance operates and defends itself for decades. But without future-proof security, these innovations become liabilities rather than assets.
At BT, we believe quantum secure communications are not optional; they are a strategic necessity and should be treated as core infrastructure. Preparation starts by asking suppliers how they’re addressing the postquantum challenge and ensuring cloud providers have clear quantum strategies.
Allies may wish to start exploring the integration of post-quantum and QKD technologies into network plans, while also considering investment in workforce skills and support for pilot projects and international collaboration.
The quantum arms race has already begun. NATO should act now to secure its networks — not only for today’s threats, but for tomorrow’s. BT stands ready to support this mission and help NATO build a resilient, quantum secure future.
Compromised systems can jeopardize entire missions, but Panasonic has the solutions to deliver robust security

Manager Defence, DACH, CEE, Türkiye, Mobile Solutions Business Division (TOUGHBOOK)
What are the most significant threats to data during military operations and how do they affect operational readiness?
Modern military operations are increasingly data-driven, making data security a strategic priority. The most critical threats include cyber-attacks, unauthorized access, data loss through stolen or misplaced devices and electromagnetic interference (EMI). These threats can disrupt vital communication channels, delay operational decisions or leak
sensitive information to adversaries. A compromised system doesn’t just endanger individual units; it can jeopardize the success of entire missions.
Can data security threats impact mission success, and if so, how?
Yes — data security threats can have immediate and severe consequences to the outcome of military missions. Cyber-attacks that cripple networks can interrupt communication between forces and command centers. Weak encryption or data leaks may result in sensitive information falling into enemy hands, giving them strategic advantages. Additionally, manipulation or disinformation can distort the decision-making process, putting units at considerable risk.
How do Panasonic CONNECT solutions help protect military data in the field?
Panasonic TOUGHBOOK devices and solutions are purpose-built for military environments and deliver robust security features:
• Hardware-level protection: TPM
2.0, smartcard readers, encrypted Viasat SSDs, BIOS-level safeguards
• Certified software and encryption tools: Secure Boot, R&S®Trusted solutions approved for classified use (VS-NfD), full disk encryption, Zero Trust security concepts
• Physical security: Ultra-rugged and tamper-resistant devices that perform reliably in hostile and extreme environments
• Advanced network security: VPN integration, private LTE/5G connectivity, and hardened communication protocols for military-grade operations
• Flexible Security Accessories: Customizable — directly on-site
TOUGHBOOK devices are designed with a modular architecture that provides maximum flexibility for security-related accessories. Components such as the Fingerprint Reader (Windows Hello), Fingerprint Reader with Multi-User Authentication and Contactless Smart Card Reader (HF-RFID) can be easily ordered and installed directly on-site, without the need to send the device back to the factory. This modular approach enables IT
“ TOUGHBOOK devices are designed with a modular architecture that enables IT departments and system integrators to upgrade devices as needed — quickly, cost-effectively and without impacting operational readiness”
departments and system integrators to upgrade devices as needed — quickly, cost-effectively and without impacting operational readiness.
How do military organizations benefit operationally from these technologies?
Armed forces worldwide rely on TOUGHBOOK solutions to enhance their mission capabilities across a range of activities, including:
• Field communications: Soldiers use rugged TOUGHBOOK tablets to share real-time data over encrypted networks and to track enemy movements
• Maintenance and logistics: Air force and naval technicians use TOUGHBOOK laptops for system diagnostics and maintenance
• Tactical operations: Special forces deploy TOUGHBOOK devices for mapping, target acquisition and mission planning — even in extreme conditions
• Cyber security operations centres: The combination of TOUGHBOOK hardware and specialized security tools creates secure IT infrastructures for command and control
What technological innovations is Panasonic CONNECT developing with partners to enhance data security?
Panasonic CONNECT works closely with leading technology partners to advance military-grade data protection employing a multiplicity of technology innovations, such as:
• AI-powered threat detection: Early identification of cyber-attacks using machine learning
• Post-quantum cryptography: Development of encryption methods resistant to future quantum computing threats
• Zero Trust architecture: Defaultdeny access models where every user and device is individually authenticated

• TEMPEST certification: TOUGHBOOK devices are certified by EUROTEMPEST to meet NATO emission security standards
Does Panasonic CONNECT integrate emerging disruptive technologies (EDTs) into the TOUGHBOOK portfolio — and if so, what are the benefits?
Yes, Panasonic CONNECT actively incorporates Emerging Disruptive Technologies (EDTs) into its TOUGHBOOK portfolio to support military users at the highest level, for example:
• 5G and private LTE: Secure, high-speed data communication on the battlefield
• Edge computing: On-device data processing without reliance on the cloud — lower latency and improved security
• AI (artificial intelligence): For enhanced image recognition, autonomous decision-making and real-time threat analysis
• Cyber-resilient hardware: Advanced defences against both physical and digital attacks
• Operating systems like RedHat Linux and Windows LTSC: Tailored for military applications, increasing both security and flexibility
These technologies empower military organizations to boost operational efficiency, protect critical infrastructure and maintain reliable, secure communication — anytime, anywhere.

eu.connect.panasonic.com/gb/en/ toughbook/industries/ defence-solutions
Estonian Minister of Defence,
Hanno Pevkur, highlights how Estonia has become number one for cyber security in Europe and how it shares its experience and know-how with its NATO Allies

As a country where 100% of public services are available digitally throughout a citizen’s entire life, Estonia is deeply committed to ensuring that digitalization remains a strategic asset — one we are fully equipped to protect, not a vulnerability to exploit. The development and delivery of every digital service starts and ends with security, which is never a fait
accompli, but rather the daily work of hundreds of experts in both the civilian and military spheres.
Skilled experts and supporting structures are essential for robust cyber defence. That is why we established our Cyber Command six years ago, which enables better control over cyberspace in our military defence. We also established cyber conscription and a voluntary-based Cyber Defence Unit in our Defence League. These have enabled us to establish a vast community of cyber specialists across the country, which can deploy in times of crisis and offer additional support in peacetime.
NATO’s deterrence and defence are inherently a cross-domain effort and so is Estonia’s approach to both
national defence as well as our contribution to NATO. Lessons learned from Ukraine also inform us that communication and information systems are not secondary to military operations — they are central to their success and incrementally so, as innovation drives developments in the defence industry. In the following, I would like to highlight the areas in which Estonia contributes to Allied success towards readiness in the cyber domain.
NATO CCDCOE AND CR14
After experiencing the first ever cyber-attacks perpetrated by one nation (Russia) against another (Estonia) in 2007, we quickly boosted capacities and expertise to increase resilience. Today, according to the Global Cybersecurity Index, we rank number one in the European Union and third in the world for cyber security readiness.

In 2008, this rapid development led to the establishment of the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) in Tallinn.
Since then, the CCDCOE has shown amazing thought leadership, which it shares with like-minded nations through publishing cyber defence research, offering a large variety of cyber education courses and organizing exercises. The centre’s flagship exercises include Locked Shields, the world’s largest cyber defence exercise, and Crossed Swords, which focuses on training offensive cyber capabilities. In addition, the Centre supports other cyber exercises, such as NATO’s largest cyber exercise Cyber Coalition. The main developments of the CCDCOE in research and development are shared yearly at CyCon, the acclaimed international conference on cyber conflict.
Although the cyber domain does provide for remote opportunities for exercising capabilities, there is still nothing that takes the place of interaction and sharing expertise in person. This is where the CR14 Foundation comes in — the Estonian Ministry of Defence founded its national cyber range in 2014 to support the delivery of exercises such as Cyber Coalition, and deliver international R&D projects, including through the European Defence Fund. Today, CR14 is also a testing ground for new ideas, available to governments and the private sector alike.
After Russia’s unprovoked full-scale invasion of Ukraine, the NATO DIANA regional hub was launched in Tallinn — creating dual-use deep tech products with potential on the
battlefield. Since 2024, this regional hub has played a leading role in NATO’s DIANA accelerator, one of the first five Alliance sites hosting innovators in dual-use and defence technology. Together with Estonia’s excellent business environment and VC networks, NATO DIANA is laying the groundwork for the rapid defence industry development that NATO urgently needs.
In its pilot year, more than 1,300 companies applied to NATO DIANA’s inaugural cohort, with nine completing the programme in the Tehnopol accelerator in Tallinn and three advancing to a second phase with additional funding. The first tests within the NATO DIANA network were carried out at CR14. Interest in the opportunities NATO DIANA offers is growing fast — in the second cohort, more than 2,600 applied, 73 were selected and seven are now

“Time is a relentless force when it comes to cyber security, making the swift sharing of threat and incident information absolutely essential”
based in Estonia. A call for the third batch, launching in 2026, is expected at the beginning of June 2025.
Our cyber resilience is dependent on the cyber security and defence capacity of our Allies and partners. Therefore, in today’s context, it is very important to support Ukraine’s efforts, which Estonia has done and continues to do. Additionally, we need to learn from Ukraine’s experience. I am glad that Ukraine is also a member of the NATO CCDCOE, which supports exchanging such knowhow.
Within the Ukraine Defence Contact Group format, Estonia and Luxembourg with Ukraine established and co-lead the IT Coalition to help Ukraine’s Ministry of Defence and Armed Forces
develop NATO-standard compatible and resilient ICT systems. To date, the coalition has brought together 18 member countries that have gathered more than €1 billion in both financial and in-kind contributions. These contributions are already making a difference on the battlefield in Ukraine, which in turn provides us with valuable information on the rapid changes and developments that occur in times of war. Through helping Ukraine, we are also helping boost the Alliance’s readiness for possible future scenarios, and we invite further states to join this effort.
Time is a relentless force when it comes to cyber security, making the swift sharing of threat and incident information absolutely essential. Although enhancing
cooperation on information sharing may seem like a well-worn strategy, it remains the foundation for strengthening our collective defence — especially as the threat landscape continues to expand with rapid technological advancement. Ukraine’s success in neutralizing cyber-attacks on critical infrastructure demonstrates the power of shared intelligence. To build true resilience, we must deepen information exchange not only among Allies and partners, but also across civil, military and private sectors. Only through trusted, timely and inclusive collaboration can we stay ahead of evolving cyber threats.


NITECH editor Lara Vincent-Young speaks with Deputy Minister of Defence of Ukraine for Digital Development, Digital Transformation and Digitalization, Kateryna Chernohorenko, about how Ukraine is turning the tide in digital warfare
Since Russia’s full-scale invasion in 2022, Ukraine has undergone a remarkable evolution, not just on the battlefield, but in its digital infrastructure and defence technology ecosystem. Today, technology is not simply a tool for Ukraine’s military; it is a central pillar of strategy, survival and sovereignty.
“Technology has become the cornerstone of our new forms of defence,” says Kateryna Chernohorenko, Ukraine’s Deputy Minister of Defence for Digital Development, Digital Transformation and Digitalization. “We’re using everything from first-person view (FPV)
drones and artificial intelligence (AI) to situational awareness platforms and cyber tools. Innovation has become both our shield and sword.”
The scale and speed of transformation are unprecedented. More than 1,500 companies now make up Ukraine’s rapidly growing defence tech sector, creating cutting-edge tools such as drones, robotic systems, missiles and electronic warfare devices. More than 60% of this market is focused on unmanned systems, an area where agility and fast iteration are vital.

“At the front line, innovation happens in weeks, sometimes days. If you’re not evolving, you’re falling behind,” Kateryna says. “The result is a unique defence innovation ecosystem where startups, government programmes and breakthrough technologies work together. It’s both helping us defend our country and build the foundation for future economic resilience.”
Ukraine’s digital transformation didn’t begin with the war. Before the invasion, Ukrainians already lived in a highly digitized society, managing healthcare appointments, banking and official documentation entirely online. But war shifted this momentum towards defence and security.
“We identified two major challenges,” Kateryna explains. “Externally, we faced a numerically superior enemy. Our answer is technology. Internally, bureaucracy slowed us down. Our answer is digital tools.”
To overcome these challenges, the Ministry of Defence launched two mobile apps: Army+ for active-duty personnel and Reserve+ for conscripts, reservists and those liable for military service. Together, they have attracted over 4.8 million users.
Army+ enables soldiers to access official requests, training resources, reform surveys and benefits.
More than 800,000 soldiers are already using the app to submit digital reports, buy discounted supplies and upskill with courses on field life, drones and cyber security. Meanwhile, Reserve+ digitizes military registration and mobilization processes, eliminating queues and paperwork, and enabling reservists to apply for roles in the army or deferments directly from their smartphones.
“Mobilization used to be hampered by bureaucracy,” says Kateryna. “Now, with just a few taps, citizens can update data, get referrals and access over 9,000 military job listings. The app even uses smart matching to suggest positions based on skills and preferences. We’ve had more than 50,000 applications already.”
One of Ukraine’s most significant achievements has been its rapid dismantling of bureaucratic inefficiencies. Previously, the military generated 20 million paper documents annually. Processes such as unit transfers could take months.
“Today, that’s changing fast,” says Kateryna. “We have removed 16 redundant inventory logs, merged a dozen personnel records into one digital profile and introduced user-friendly digital reports. A change-ofduty request used to involve intermediaries and long delays. Now it takes days, not months.”
“ Perhaps no system exemplifies Ukraine’s digitalization on the battlefield better than DELTA, a comprehensive combat information platform that delivers real-time situational awareness and mission planning”
In the first eight months of launching Army+, more than 400,000 digital reports were submitted. Around 30,000 soldiers have already successfully transferred units using this streamlined process.
In logistics, the Ministry’s DOT-Chain system has transformed food distribution. Deliveries are now four times faster, documentation time has dropped from 60 days to just two weeks, and paperwork has been reduced by over 30,000 documents weekly. A new extension, DOT-Chain Defence, enables units to submit digital equipment requests, aligning procurement with real battlefield needs. “We’ve proven that even during war, a digital state not only survives, it saves lives,” says Kateryna.
INTELLIGENCE IN REAL-TIME: DELTA AND AVENGERS
Perhaps no system exemplifies Ukraine’s digitalization on the battlefield better than DELTA, a comprehensive combat information platform that delivers real-time situational awareness and mission planning. More than 90% of Ukraine’s defence units now use the platform, which has helped destroy over $15 billion worth of enemy equipment to date. “Thanks to DELTA, our troops know exactly where the enemy is, every trench, every dugout, every convoy,” Kateryna says. “It has played a vital role in nearly every major operation and continues to deliver data that enables precise strikes.”
A critical component of DELTA is the AI-driven AVENGERS platform. It processes over 12,000 images of enemy hardware each week from drones and surveillance feeds, helping operators identify and target threats faster. Trained on real combat footage — an advantage most countries lack — AVENGERS is a rare, field-tested AI model born from necessity. “This is data no simulator can replicate. And that’s why international partners are taking notice. We believe DELTA and AVENGERS have the potential to support Allied forces far beyond Ukraine.”
The Ministry is now using these digital systems to automate analytics of confirmed enemy destruction. Verified service members can submit encrypted reports through Army+, attaching geolocated media from DELTA. This data populates a secure dashboard that enables the Situation Center to validate losses and trigger payments. “At this stage, the feature is available to selected units only. After initial testing and feedback from commanders, we’ll refine the system and scale it across all units of the Armed Forces and National Guard,” Kateryna explains. “The goal is to build a real-time war dashboard to track effectiveness, guide production and assess munitions use across the front lines.”
Looking ahead, the Ministry is investing in the future through the new project, aimed at creating a national defence innovation platform built on three pillars: military expertise, hands-on technical mentorship and substantial funding.
The Ministry will launch a dedicated environment for building next-generation AI-powered defence technologies and startups. Led by top industry experts and backed by the full support of the Ministry of Defence, the platform is designed to accelerate the most impactful solutions to the front line. The aim is to build sustainable, AI-driven defence startups with global potential.
Kateryna stresses, “This is the Y Combinator of defence tech. We’re combining war-tested urgency with clear market demand, guided by domain experts. For investors and innovators, this is a rare opportunity. That’s why I’m inviting investors who are seeking high-impact opportunities in defence and AI to engage with and explore the opportunities, to help shape the future of global security.”
Taking a data-centric approach ensures Janes data and AI offering is providing superior insights across domains


In a NATO context, data centricity supports enterprise coherence and decision advantage across multinational operations.
Leendert Van Bochoven: That is true, but the way data is treated and integrated by a data-centric organization also influences decisionmaking processes. So, being datacentric requires a culture of data literacy because it is about people, processes and technology. They go hand in hand with the structures Jerome mentions. Another crucial element is the toolset used to manage the data. But, the tools themselves are not the silver bullet; it is about the quality of the data, how you work with it and how consistent all the data sets are. And in these days of artificial intelligence (AI), data quality and consistency are becoming ever more important.
How would you describe NATO’s current challenge in terms of data exploitation and management?
Leendert Van Bochoven: Another significant challenge is identifying all the communities of interest within the Alliance to whom the data is applicable. For example, is the data for the NATO Enterprise itself, the member countries, both or another entity? After all, everybody needs data for their decision-making processes. Moreover, there are so many use cases and processes happening across all of these communities and much of the data originates from the nations themselves. Therefore, it is crucial to achieve alignment between the Enterprise and the nations and the wider stakeholders that feed in. There are so many seams and borders in the data models and NATO’s challenge is to align them.
What are the advantages of, and requirement for, an enterprise-wide digital transformation?
What does it mean for an organization to be data centric?
Jerome Kühnert: A data-centric organization treats data as a strategic asset — one that is structured, shareable and embedded across all decision-making workflows. It ensures data is discoverable, interoperable and accessible at the point of need. It enables consistent, trusted insights across domains.
Jerome Kühnert: NATO faces structural challenges in harmonizing intelligence across nations, domains and classification levels. Fragmentation, siloed workflows and inconsistent data standards often impede rapid exploitation and integration. These issues limit both real-time decisionmaking and the effective use of AI/ machine learning (ML) tools essential for modern threat environments.
A good example of how NATO is addressing and overcoming this challenge is the ‘Enterprise Data Strategy’ — an ongoing data-related initiative for the NATO Enterprise.
Jerome Kühnert: Enterprise-wide digital transformation will enable NATO to break down data silos, automate intelligence workflows and ensure secure, scalable access to critical information. This transformation underpins interoperability, enhances resilience and delivers faster, more accurate decision-making. It also ensures that intelligence infrastructures are future-ready and aligned with evolving operational demands.
Leendert Van Bochoven: NATO’s digital transformation seeks to eliminate the individual functional and organizational data silos and replace them with a more horizontal model that connects the communities of interest. In short, NATO is creating a ‘digital backbone’ that enables rapid access to data for everyone.
This is for multiple datasets provided by the NATO Enterprise, the nations, private contractors and other stakeholders. These data sets should be customer agnostic so that they can be used by everyone for their specific use cases — simulation teams, planners, logisticians, intel, operations… Essentially, it is the same data used by different communities of interest for different purposes. This will have enormous benefits. It will also address numerous data-related challenges — quality, veracity and data standards to name just a few.
Can you explain the importance of data exploitation management and governance?
Jerome Kühnert: As Leendert has mentioned, effective data exploitation depends on robust governance — ensuring data is structured, validated and integrated into secure, compliant workflows. For NATO, this governance is essential to bridge classified and unclassified domains, reduce duplication and optimise intelligence cycles. It lays the foundation for consistent decision-making and AI-readiness across the Alliance.
Another positive example driving NATO’s data cohesion is its ‘Data Governance Operating Model’, which has been put in place to drive digital-policy coherence, standards harmonization and interoperability. It will ensure clear accountability and ownership of critical data governance and management efforts within the Alliance.
Leendert Van Bochoven: It is very important to understand which essential data components need to be managed and how best to manage them. Janes has spent decades working through our data to do just that. We have built ontologies and data models to describe the operational domains, their associated equipment and systems on land, at sea and in the air. We have been on
that digital transformation ourselves — from a document-centric organization to a data-centric organization. We had to put in the governance elements in order to create the datasets that we have today. NATO will need to do that too and scale it out to other datasets and insights to create its own data model.
What are the benefits of an enterprise-wide use of Janes data, and how might it result in decision advantage across all domains?
Jerome Kühnert: Janes provides a verified, structured ‘Baseline’ dataset, which enhances interoperability, reduces duplication and accelerates time-to-decision, especially when classified intelligence is constrained. Our API-delivered OSINT integrates seamlessly into NATO’s digital backbone and multi-domain operations. It provides a consistent intelligence foundation across all security levels and enables scalable, real-time insights and supports NATO’s shift to a ‘need to share’ model.
Leendert Van Bochoven: Having gone through our own digital transformation, our data model is now captured in an ontology by our subject matter experts and expressed as a knowledge graph. The essence of this knowledge graph is a vast number of data nodes each with a range of relationships to each other. We have created a huge and growing number of dynamically connected entities which can be exploited in a multiplicity of ways. This is unique within the defence and security sector.
In addition, over the past five years, we have been adding value to that knowledge graph with a set of AI ‘named-entity recognition’ algorithms that we have been developing. Using AI/ML helps us scale that knowledge graph and expand it very rapidly. So much so that, last year, we estimated that there were 120 million connected entities. At the beginning of this year
there were around 185 million, and in the not too distant future we expect to pass the 300 million mark.
The fine-tuning of our algorithms specifically to the military and intelligence domains is the golden nugget that lies within the data that Janes has been gathering for over a century. Together with partners, we have integrated our data in RAG (Retrieval Augmented Generation) implementations so that you can query the knowledge graph and get a natural language response — think of it like a sort of JanesGPT. This is the secret sauce that creates the decision advantage that is so important in today’s quickly changing threat environment. The next step on this journey is to enable Agentic AI so we can develop AI agents that do some of the work for analysts. This will make our data/AI offering even more powerful, turning decision advantage into decision superiority.

Use the QR code for more information and a closer look at our unique data offering or visit Janes at DSEI on 9–12 September 2025

janes.com


The agreement to establish the NATO-Ukraine Joint Analysis Training and Education Centre in Bydgoszcz, Poland was a key element of NATO’s Washington Summit declaration of July 2024. Supreme Allied Commander Transformation, Admiral Pierre Vandier, explains how the centre will enhance Ukraine’s ability to gain battlefield advantage and enable NATO to understand the evolving threats Ukraine has to address
At the Washington Summit in July last year, the Allies gave the nod to the creation of the NATO-Ukraine Joint Analysis, Training and Education Centre (JATEC) as an important tool for practical cooperation. Following its activation by the North Atlantic Council in December, the joint NATO-Ukraine entity opened in Bydgoszcz, Poland, in record time, I might add. The centre is the result of the combined efforts of Allied Command Transformation (ACT) and NATO Headquarters, working hand in hand with the governments of Poland and Ukraine. We marked its Initial Operating Capability just a few months ago, in February 2025.
It is, in many ways, a remarkable and unique organization, the first to result from the collaboration between the Alliance and a Partner country. Bringing together a mix of civilian and military experts, it will contribute to shaping NATO, Ukrainian and individual Allies’ capability development, fully drawing on the lessons learned and experience acquired as Ukraine continues its heroic defence against Russian invaders.
I would particularly draw attention to two projects in the Centre’s programme of work (POW), which serve
“No one would dispute the indispensable role of data in modern warfare, and it is naturally just as critical for how the Alliance operates”
as prime examples of how innovation and collaboration can produce rapid advances and deliver in record time.
The 15th edition of the ACT Innovation Challenge took place in March, focusing on finding technological solutions to the threat posed by glide bombs, low-cost precision-guided munitions and the challenge those characteristics pose to air defence. Winning solutions were selected with the help of Ukrainian experts to ensure their relevance to the operational situation on the ground. The winning submissions, whether relying on early detection and rapid identification or on a proposed interceptor, will now be tested, with Ukraine involved in all stages of their testing and assessment.
A second project was included, at Ukraine’s urging, in the JATEC POW. It deals with how best to counter fibre optic-controlled first person view (FPV) drones. The scenario for an Innovation Challenge is being prepared for its Pitch Day in June 2025. Here again, working with Ukrainians on scenarios, assessment and selection of solutions as well as their testing, will enable us to shorten the innovation cycle from identification of battlefield requirements to the fielding of systems. At a time when we are faced with imposing challenges in difficult circumstances, I think we can be inspired by these reactive and smart efforts that mirror the rapid development, testing and deployment of solutions by the Allies in World War II.


JATEC’s creation also provided an opportunity to confront NATO’s own strategic challenges, notably the need to accelerate the adoption of secure information management structures. No one would dispute the indispensable role of data in modern warfare, and it is naturally just as critical for how the Alliance operates. With this in mind, the stringent security requirements associated with JATEC’s mission have led us to speed up the implementation of a NATO Secret cloud environment.
The scale of data handling and AI integration needed at JATEC — across both NATO Unclassified and NATO Secret domains — necessitates robust, modern storage and processing capabilities, especially given the parameters of our operational collaboration with Ukraine. ACT has already demonstrated its capacity to accelerate cloud adoption with the successful transition to a NATO Unclassified cloud late last year, having recognised that a cloud-based architecture is not merely advantageous but essential.
Building on this momentum, ACT has structured its approach to the NATO Secret cloud around full transparency with all stakeholders, particularly the NATO Office of Security and NCIA. The current
implementation is being led as an initial, standalone increment, deliberately designed to be fully compatible with the unique mission requirements of JATEC, while ensuring strict compliance with NATO security standards.
This initiative, based on isolated ‘Local Edge Clouds’, delivers state-of-the-art cloud technology and advanced AI tools directly to the user, ensuring operational excellence. In addition, data-centred security will be implemented, enabling fine access control of information at the individual data level. It also serves as a catalyst for accelerating the deployment of NATO Secret cloud capabilities within ACT.
Although accreditation remains a complex challenge, our experience to date proves that ACT can lead transformational initiatives within NATO, in close cooperation and full transparency with our key partners, including NCIA, whose help and support has been nothing short of remarkable. In doing so, we are not only enabling JATEC’s success but also laying critical groundwork for broader NATO-wide adoption of a secure, sovereign and operationally resilient cloud environment.
Ericsson is at the forefront of 5G, successfully integrating the dual-use technology into defence communications

How would you describe Ericsson and its core technology offerings?
Ericsson is a global leader in mobile connectivity solutions and we’re leveraging our leadership in 5G, integrating the dual-use technology into defence communications. Commercially developed 5G hits the sweet spot of at-scale innovation, affordability, performance, interoperability and resilient connectivity sought by NATO and its allies.
Can you expand on the at-scale, dual-use benefits of 5G?
Leveraging existing commercial 5G infrastructure reduces deployment time and costs while supporting interoperability across alliance members and multi-domain operations (MDO). This supports integrated operations, real-time coordination, and mission flexibility — critical advantages in any military operation.
Adopting commercially scaled 5G also brings significant innovation and cost benefits. Backed by a vast, competitive global ecosystem, 5G technologies are continuously improved, standardized and readily available. NATO can take advantage of this rapid commercial innovation cycle, avoiding the long development timelines and high expenses often found in bespoke defence-only systems. The commercial sector’s pace and scale enable NATO to stay at the forefront of digital transformation, with more agile, flexible communications infrastructure.
Critically, 5G delivers the performance and security needed for missioncritical defence applications. It supports ultra-reliable, low-latency connectivity essential for MDO, including real-time ISR, command and control, and autonomous systems.
Of course, networks need to be enhanced to ensure performance goes beyond what is needed in a consumer-grade network. This includes hardening of networks, and extended network coverage and capacity — aspects catered for in Ericsson’s features, products and solutions.
5G is the most secure mobile generation yet, and its built-in security features — such as network slicing, PQC encryption and programmable network management — enable networks to be tailored and hardened for specific mission needs.
From immersive training to UAV operations and coalition
coordination, dual-use 5G is integral to the digital fabric and enables allies to do things faster, cheaper and better.
5G… fixed? mobile? satellite? Defence requires ubiquitous, secure and resilient connectivity. All forms of connectivity play a role, but Mobile is the standout technology. Its capabilities have grown exponentially over decades, and it is through Mobile the world overwhelmingly connects to the Internet.
Looking ahead, 5G is expected to become the dominant mobile access technology by subscription in 2027 and its high performance and scale benefits mean it is expanding from traditional mobile broadband and across market sectors such as mission critical, defence and aerospace, and where bespoke solutions exist. Typically, only the best technologies rise to the top on their merits and secure broad adoption.
Which technologies do you see as pivotal going forward?
I expect mobile, cloud and artificial intelligence will continue as the foundational technologies over the coming years, underpinning other emerging and disruptive technologies, such as quantum and digital transformation more generally.
We should continue to expect sectors, benefiting from mobile’s connectivity and AI-based automation, to improve efficiency and productivity, while cloudification supports the delivery of easy-to-use digital tailored services,

immersive experiences and more sustainable solutions.
Where does Ericsson fit into the technology ecosystem?
Our communication service provider (CSP) customers are providing mobile connectivity in every NATO country. For decades, Ericsson has been at the forefront of developing cutting-edge communications technologies and solutions in deploying mission-critical networks for government, public safety and critical infrastructure.
The interdependent advancement of technologies calls for close working, not least among technology leaders, and we work across the tech stack, and with our CSP customers, system integrators, governments, ministries of defence and NATO.
To what extent is Ericsson working with NATO?
Ericsson is a committed and trusted NATO partner across a variety of critical technology development areas, and we look forward to continuing to work with the Alliance and its member countries in their digital transformation.
We have been involved in a wide range of NATO defence-technology consultations, research projects, and testing initiatives, including the Latvian 5G Test Bed in collaboration with the Latvian Armed Forces; the NATO Cooperative Cyber Defence Centre of Excellence; the NATO Industrial Advisory Group; and various technology initiatives and study groups organized under the NATO Science and Technology Committee.
In addition to NATO, Ericsson partners with departments of defence, including the US with its 5G to NextG Testbeds activities, and is a workstream lead for the European Union’s European Defence Fund 5G COMPAD project.
What is next in 5G?
Today’s and tomorrow’s applications — from consumer to defence — demand increasingly diverse network performance.
The difference between buffered video streaming and real-time virtual reality communication highlights the need for more adaptable connectivity, especially where seamless interaction is critical.
A one-size-fits-all model struggles to meet these demands, which is why programmable networks are essential. They allow for tailored performance — adjusting speed, latency, reliability and security based on specific use cases. In defence, this means prioritizing mission-critical traffic such as real-time voice or sensor data, and ensuring ultra-reliable, low-latency links for tasks such as drone control.
Dual-use technology and programmable networks can also unlock advanced capabilities in military operations, including real-time battlefield communication, drone swarm coordination, autonomous vehicle support, enhanced cyber security and situational awareness through the Internet of Battlefield Things (IoBT).
ericsson.com/en/industries/defense ericsson.com/en/security/ ericssons-security-reliability-model


In an era of rapidly evolving threats, NATO’s Joint Force Command Brunssum (JFCBS) launched a bold new step in defence innovation: hosting the Warfighting Innovation Demonstration and Exhibition (WIDE25). Simon Michell speaks to JFCBS Innovation Manager, Hugh Blethyn, about the event
On 25 and 26 March 2025, Joint Force Command Brunssum (JFCBS) gathered more than 750 participants from across NATO, its member countries and the broader innovation community to convene at WIDE25. The ambition was to bridge the gap between operational challenges and real-world solutions through collaborative innovation.
WIDE 25 reinforced NATO’s commitment to operational-level innovation and experimentation, directly supporting its Warfighting Capstone Concept and Digital Transformation strategy. The event enabled cross-domain problem framing at the operational level, ensuring that innovation efforts are operationally grounded. In his opening address, General Guglielmo Luigi Miglietta, Commander of JFCBS noted that the purpose of WIDE25 goes beyond technology saying, “We are creating a vital connection between our operators and industry, academia and our NATO partners.”
Held over several days, WIDE25 went beyond the traditional exhibition format. The event fused practical demonstrations, hands-on testing and in-depth operational dialogues. It showcased how disruptive technologies could support transformation to a fully integrated, digitally enabled warfighting headquarters.
The depth and diversity of WIDE25’s audience was a testament to its strategic relevance. Military decision-makers mingled with AI researchers while logistics officers debated with defence start-ups. NATO’s transformational actors, NCIA, Allied Command Transformation (ACT), the Defence Innovation Accelerator for the North Atlantic (DIANA), the NATO Innovation Fund (NIF) and the NATO Industrial Advisory Group (NIAG), participated as both contributors and collaborators. Key among the event’s speakers was former NCIA Chief of Staff, Major General Hans Folmer, who spoke about NCIA’s role and responsibility in leading NATO’s digital transformation.
General Miglietta emphasized the vital role that innovation plays in overcoming challenges faced by NATO forces: “Today, we are not merely showcasing current and emerging technologies; we are creating a vital connection [among] our operators and industry, academia and our NATO partners to shine a light on the challenges we face in an ever-evolving security landscape, and potential solutions.”
A key element was the involvement of DIANA. DIANA’s Challenge Managers, led by Major General Jorge Côrte-Real Andrade, DIANA’s Military Deputy
Director for Europe and Dr Emma Ryan, explored six key operational-level challenges identified by the JFCBS Team, which were subsequently formally incorporated into the DIANA Challenge 2026 Programme. As a result, JFCBS’s operational-level innovation requirements are now embedded in the broader DIANA challenge architecture, enhancing coherence between operational needs and innovation investments.
WIDE25 delivered hands-on demonstrations of some of the most promising technologies relevant to NATO’s future force posture. These included AI-enabled decision support tools, edge computing capabilities, autonomous ISR platforms and hardened cyber systems. But the focus was not just on spectacle –it was about integration.
A standout example was the live demonstrations of multi-domain operations (MDO) dashboards, which used AI to fuse data from land, maritime, airborne, space and cyber assets. These real-time tools enabled simulated commanders to anticipate adversarial moves, drastically reducing their decision-making timelines.
Participants didn’t just watch, they engaged. Operational personnel provided instant feedback to developers. Engineers explored system interoperability issues on the spot. “This wasn’t about showing off gadgets,” says Hugh Blethyn, JFCBS Innovation Manager. “It was about exploring the cutting edge of available technology stresses, understanding how they can help commanders make faster, smarter decisions.”
For JFCBS, innovation must serve a clear purpose: enhancing the Alliance’s warfighting readiness. WIDE25 was structured with that aim in mind. Events such as this shorten the distance between concept and capability. “If we can connect operational challenges with a startup’s solution, or bring in academic insight that shifts how we think, that is a strategic advantage in action,” says Blethyn.
WIDE25 wasn’t only about long-term transformation. Some of the capabilities explored at the event are already being assessed for inclusion in exercises and trials. As Blethyn notes, “We saw real potential for near-term implementation through our Alliance partners, especially in the areas of MDO situational awareness, digital transformation and decision-making resilience. That’s a direct contribution to NATO interoperability and speed of response.”

Perhaps the most transformative element of WIDE25 was cultural. By bringing together operators, technologists and thought leaders in a collaborative and open environment, the event challenged traditional assumptions about how military innovation happens. “Innovation is key to our warfighting ability: it guarantees superiority in the fight tomorrow — but don’t forget: also in the fight today. In order to do so innovation shall strike the balance between sophisticated long-term projects and quick push for the instant improvements” said distinguished WIDE25 guest, Chief of Staff SHAPE, General Markus Laubenthal, reminding the gathered audience that it requires everyone from the “Allied innovation ecosystem” to maintain NATO’s advantage in the technology adoption race.
Throughout the event, participants echoed the same theme: innovation isn’t a project, it’s a practice. And NATO, through initiatives such as WIDE25, is evolving its institutional mindset to support agility, experimentation and iterative learning.
Far from a one-off, WIDE25 is envisioned as a cornerstone in a broader transformation journey. JFCBS, in coordination with its NATO innovation partners, is already integrating lessons learned from the event into training, exercises and capability planning. “We’ve built momentum,” says Blethyn. “Now we’re looking at how to sustain it. That means identifying technologies for further engagement through our partners in DIANA and Allied Command Transformation to maintain our new connections with innovators, and refining our approach to joint innovation.”
DIANA’s Dr Emma Ryan addressed the conference summary session and expressed her appreciation for the insights from JFCBS operators, subject matter experts and industry, providing invaluable input into future challenge statements for DIANA. “The event was unique in bringing together end users and industry to discuss current and future challenges and technologies to solve them,” she says. “This is critical for the innovation and development of capabilities for the defence and security of NATO and its allies. We look forward to building upon this relationship and supporting future WIDE events.”
General Miglietta closed the event with a call to reinforce the vital role that innovation plays in overcoming the complex challenges faced by NATO forces, saying: “We have the responsibility to shape the change by turning challenges into opportunities. We must execute our mission to the best of our ability and maximize our contribution to the peace development and conflict prevention throughout JFC Brunssum’s Area of Responsibility.”
WIDE25 proved that innovation and warfighting transformation are not opposing ideas; they are deeply intertwined. By building a bridge between operational needs and cutting-edge innovation, JFC Brunssum and its partners are helping NATO remain fit for purpose in an unpredictable world.
With the support of institutions such as DIANA, ACT, NIAG and national innovation centres, the Alliance is laying the foundation for an adaptive, digitally empowered force, ready not just to react, but to shape the future of security. As NATO moves forward, WIDE25 will be remembered not only for what was showcased, but for what it set in motion: a culture, a network and a vision of readiness built on innovation.





NITECH Editor Simon Michell asks Colonel Patrick Schuetterle, Deputy Chief of NCIA Service Operations, Gregor Gosepath, Lead Early Engagement Europe (Chief Technology Office), and Michail Kanellakis, Senior Project Manager for NCIA’s NATO Integrated Mobile Services Centre (NIMSC) about the role that NSATU and NCIA play in assisting Ukrainian Armed Forces maintain high levels of readiness
As the war in Ukraine endures, NATO continues to adapt its support to meet evolving challenges on the ground. When NATO formally announced the NATO Security Assistance and Training for Ukraine (NSATU) portfolio at the Washington Summit in July 2024, it marked a milestone in the Alliance’s coordinated support for Ukrainian Armed Forces. But, for NCIA, this endeavour began much earlier.
“NSATU is not a standard NATO programme,” explains Colonel Patrick Schuetterle, Deputy Chief of NCIA Service Operations (CSO). “It’s a portfolio initiative built on three critical pillars: overseeing training of Ukrainian troops in NATO countries, supporting long-term development of Ukraine’s armed forces and sustaining operational effectiveness during the war by facilitating materiel transfer, coordination and repair.”
As the primary provider of Communications and Information Systems (CIS) to NSATU, NCIA plays a vital role in each of these pillars. According to Schuetterle, delivering such capabilities is a top priority across the readiness domain of NCIA’s operations.
Importantly, NATO’s involvement in NSATU does not make the Alliance a party to the conflict. Instead, the goal is to help the Ukrainian government and armed forces gain a more predictable and sustained level of support, both in the immediate term and in the future. As Gregor Gosepath, Lead for Early Engagement Europe in NCIA’s Chief Technology Office (CTO), notes, “Our support helps Ukraine plan better and stabilize its needs during a very volatile period.”
EARLY ENGAGEMENT AND RAPID RESPONSE
NCIA’s quick mobilization in support of NSATU highlights the importance of foresight and collaboration. The urgency and scope of the effort became clear in mid-April 2024, when NCIA’s General Manager received a call from SHAPE’s Chief of Staff, enquiring whether NCIA could support the emerging NSATU initiative. That Friday call set off a chain of rapid activity. By the following Monday, Schuetterle and Gosepath were en route to Wiesbaden, Germany, where NSATU HQ would be established, to assess the viability of the site.

“ The goal is to help the Ukrainian government and armed forces gain a more predictable and sustained level of support”
“The key to our fast response was early engagement,” says Gosepath. “Thanks to NCIA’s new operating model, which was still being developed at the time, we were able to make swift decisions. A small core team had already been created by the General Manager earlier in 2024, which meant we could immediately engage with key stakeholders, understand funding requirements and begin identifying the necessary CIS equipment and expertise.”
Under CSO lead as Senior Responsible Officer for NSATU, an agile approach led to the formation of a Tiger Team, which quickly evolved into an Integrated Project Team (IPT) under the NATO Integrated Mobile Services Centre (NIMSC). This IPT would become the operational backbone of NSATU’s technical delivery. In parallel, the IPT, together with the already established Mission Technical Design Authority from CTO, demonstrated the need for acceleration in standing up the Mission Portfolio to further streamline NCIA’s support to Ukraine, but also to other ongoing missions and exercises.
“Early engagement allowed us to define clear technical requirements right from the start,” says Michail Kanellakis, Senior Project Manager for NIMSC. “From there, we could expand into broader, more complex needs that didn’t necessarily align with existing NATO standards. The transition from Tiger Team to IPT was a game-changer — it brought together all NCIA functions into a unified team, capable of managing on-the-ground services and fast-evolving capability projects simultaneously.”
Building this IPT wasn’t just about technical integration. As Schuetterle notes, the team also had to understand the operational environment and incorporate existing operational elements from the Security Assistance Group-Ukraine (SAG-U) and the International Donor Coordination Center (IDCC), for example. The IPT ensured that all efforts were both interoperable and effective. “We had to consolidate existing non-NATO activities while enhancing and delivering new capabilities. That was perhaps our greatest challenge.”
At the heart of NSATU’s success lies NCIA’s new Operating Model 2030, which was piloted for this initiative. Designed to accelerate the delivery of services, it introduced five standardized process blocks: Early Engagement, Business Intake, Sourcing and Procurement, Capability Implementation and Service Operation.
“The aim is to reduce waste and increase speed,” says Gosepath. “NSATU was the first full application of the model, and the results speak for themselves. The approach was so successful that NATO’s Assistant Secretary General for Operations recommended applying the same methods to JATEC, the Joint Analysis Training and Education Centre in Poland.”
By January 2025, NCIA had already begun initial deliveries to JATEC, with operational capability declared the following month. The new operating model, says Gosepath, has already proven to elevate service levels across NCIA, which directly translates into enhanced readiness for both NATO and Ukrainian forces.
The NSATU IPT also reduced the required time for the delivery of the Project Proposals and Request for Proposal/Invitation for Bids to industry. As a result, Kanellakis confirms, “NIMSC has decided to exploit this opportunity and adopt the NSATU IPT approach and the established processes creating IPTs in all Business Units, transforming the way NIMSC operates in the future.”
Ultimately, NSATU is a demonstration of NATO’s adaptability in the face of unprecedented challenges. Through early engagement, flexible operating models and close inter-agency cooperation, NCIA has delivered critical services that are directly supporting Ukrainian resilience and readiness. As NATO continues to evolve its operational frameworks, NSATU stands as a testament to what is possible when urgency meets innovation.
With ‘Q-Day’ looming as soon as 2030, organizations should replace all legacy hardware and software with quantum-resistant equipment. Sectra is ready today

Quantum computers solve problems in an unbelievably short space of time using quantum mechanics with ‘qubits’ instead of the ‘bits’ that conventional computers employ.
Scientists can predict and apply quantum mechanics with remarkable precision, but its deeper foundations, such as the nature of wave function collapse and entanglement, remain mysterious and actively debated.
That said, essentially, quantum computers use the principles of quantum mechanics to solve certain problems much faster than traditional computers. Although they’re not universally more powerful, they excel at specific tasks such as simulating quantum systems or cracking certain mathematical problems.
The major IT companies worldwide are in a race to develop the most powerful quantum computer. Every few months they will announce that they have just developed a faster one than their competitors. It is an extremely fast-moving technological
sector with records being broken on a regular basis. To put this in perspective, according to Google, it would take their new Willow quantum chip five minutes to solve a benchmark computation that a conventional computer would need 10 septillion years to solve. That is more than the age of the universe.
Nowadays, there are two main types of cryptography – symmetric and asymmetric. Symmetric cryptography uses a single shared key for both encryption and decryption, making it fast and efficient. In contrast, asymmetric cryptography employs a public key for encryption and a private key for decryption, enabling secure communication and authentication without sharing the private key. To accomplish this, hard-to-solve mathematical problems are used.
Asymmetric cryptography is often used for secure key exchanges, while symmetric encryption frequently handles bulk data transfer due to its speed. Together, they provide strong security, as breaking asymmetric encryption with conventional computers would take so long that the data would likely have become irrelevant by the time the encryption had been broken.
Quantum computers make that assumption questionable, because of the speed at which they can solve the associated math problems. If an organization wants to keep its most important secrets safe for decades, it can no longer assume that this is a
reasonable aspiration because of the impending approach of Q-Day.
In essence, Q-Day represents the point at which quantum computers become sufficiently powerful and reliable enough to run cryptographic breaking algorithms like Shor’s at scale. This would undermine current asymmetric encryption methods such as RSA and ECC-DH (Elliptic Curve Cryptography and Diffie-Hellman). In other words, the immense leap in computational power that will be introduced through quantum computing will put many modern encryption methods such as those used in HTTPS, VPNs, secure emails, mobile communications and much more at risk. Once quantum computers become more advanced and reliable, they will be able to break vulnerable encryption systems more efficiently than conventional computers, decrypting sensitive communications much faster. If this happens, a cryptographic apocalypse — or ‘Q-Day’ — may happen. It is not a certainty, but it would be unwise to bet against it.
What is perhaps more worrying, is that, just as the existence of the Enigma decoding machine was concealed, whoever achieves the levels of quantum-computing power required to crack asymmetric encryption will not necessarily reveal that either.
Almost all future encrypted data might become vulnerable, and most of the encryption systems used today

are fundamentally at risk. The added risk, however, is that it is reasonable to assume that some states have been storing their intercepted communications. Since the dawn of the internet, in particular, the cost of storage has become ever cheaper. Consequently, there may be millions of terabytes of classified data stored on hard discs on the servers of potentially adversarial nations waiting to be decrypted.
As soon as a quantum computer is developed that is powerful enough to break the encryption codes, all of the secrets hidden within this stored data might be revealed. Q-Day is retrospective!
Are governments and industry actually preparing for a post-quantum cryptographic era?
At first, governments and organizations had to be convinced that quantum computing represented a real cryptographic threat, but now most industries and government sectors
have accepted the risk and are putting in strategies for achieving quantum resilience. NATO published its own far-reaching ‘Quantum Strategy’ in 2024 and has started transitioning to quantum-safe cryptography.
Fortunately, the scientific community has been researching new ways of implementing asymmetric encryption for many years to counter quantum computers. These are primarily based on even more complex mathematical conundrums. There are, without doubt, algorithms that scientists agree are quantum resistant. And some of them are being rolled out now.
As you would expect, Sectra has been very proactive in this field and has been using those quantum-safe algorithms in our products.
How can organizations protect their data in preparation for Q-Day? Actually, it’s quite simple. Organizations should replace all legacy hardware and software with
quantum-resistant equipment. In some cases, it might be possible to upgrade some of the old equipment, but many of the new algorithms that have been developed recently for such things as high assurance or Internet-of-Things devices require new hardware. Furthermore, organizations need to have a strategy to do this in the short term. Q-Day may be as close as 2030, according to the Cloud Security Alliance working group on Quantum-safe security. That is only five years away.
When will Sectra be ready to deliver the necessary tools to enable organizations to survive Q-Day, and what will they be?
Sectra is ready today. You don’t have to wait for Q-Day. You can start preparing now. Everything across Sectra’s products for defence organizations and civil authorities are quantum-ready. In particular, Sectra has its Tiger/S ecosystem, which is fully quantum-resilient. Sectra Tiger/S is a secure communication system developed in close cooperation with the Dutch and Swedish security authorities.
It enables the user to share classified information up to and including the SECRET classification level through encrypted speech, messaging and data transfer. NATO already has a large fleet of Tiger/S end-user systems in place.
There are other Sectra products that NATO is not yet using. This includes things like our new Sectra Secure Mission Pack for on-the-go communications. I can also confirm that we have just launched a stationary version of Tiger/S.
communications.sectra.com


Simon Michell calls on NCIA Heads of Crisis Management and Business Continuity, Captain Paul Hammond, and Service Management and Control, Angelo Talarico, to learn how NCIA is adapting to ensure it is able to balance its service levels with the expected increase in demand that a more uncertain world has brought
NCIA has been undertaking work to assess the levels of readiness across the Agency. Can you highlight some of this work and explain how NCIA is adjusting its activities to be able to ensure its readiness levels can consistently meet demand?
Paul Hammond: With increasing global uncertainty, it is imperative that NCIA is immediately ready and fully prepared to respond appropriately in the event of further degradation of the security situation, a transition in the continuum from crisis to conflict, or in the worst case, an invocation of Article 5 by NATO. The NATO Alliance, and thus NCIA, must be ready before a conflict happens. To meet this increasing and urgent demand,

NCIA’s Crisis Management and Business Continuity (CMBC) team and the NCIA Assistant Chief of Staff (ACOS) have been busy applying a military planning process. NATO’s Allied Joint Doctrine for OperationalLevel Planning includes a Mission Analysis as part of the planning process and provides the basis for this work.
NATO’s three core priorities are clearly defined: deterrence and defence, crisis prevention and management, and cooperative security. With this firmly in mind, NCIA’s response will meet the principle demands of Deterrence and Defence of the Euro-Atlantic Area (DDA) and adhere to the directions contained in the Regional
Plans, derived from the DDA requirement. These plans move NATO from a reactive, crisis-response posture to a forward-looking, deterrence-based posture. The Mission Analysis was completed in February. Every Functional and Business Area helped to analyse and report on their requirements and identify any shortcomings or concerns regarding the readiness posture in their respective areas. Analysis of this work revealed clear themes and capability shortfalls in NCIA readiness that are being addressed through innovative leadership and management techniques, such as the establishment of Cross Functional Teams (CFTs) and the Catalytic Leadership model, which NCIA has recently adopted.
What and where are the main challenges that you have been able to identify, and how does NCIA intend to address them?
PH: NCIA’s approach to conflict readiness and responsiveness must mirror that of the wider Allied Command Operations (ACO). In particular, the approach must adhere to NATO’s three core priorities and, when required, the application of the Regional Plan(s). This is the most critical challenge, which requires close coordination with our compatriots in ACO. We must work together, collectively and coherently, to ensure that whenever and wherever ACO needs focused NCIA support, we respond effectively. This has already been proved through activities such as our unwavering support to NATO Security Assistance and Training for Ukraine (NSATU), the development of the Vigilance and Enhanced Vigilence (VeVA) communications network for Supreme Allied Commander Europe (SACEUR) and a raft of enhanced vigilance activities.
The second challenge rests within NCIA itself. Understandably, with NCIA having a relatively small military footprint in comparison to ACO, military processes are less well understood. So, it is imperative that our staff are educated at every opportunity. Our General Manager has made ‘readiness’ one of his main priorities, and therefore, through actions such as the Catalytic Leadership events, weekly operational updates and the enhancement of general awareness of the security situation, the importance of, and urgency for this activity is clearly being recognised by our staff.
The final challenge, again largely NCIA-related, is to break down some of the apparent barriers that exist between Functional and Business Areas (FA and BA), as many of the themes and shortfalls intersect two or more areas. This is where the Catalytic approach comes in; it brings the various areas together to understand each other’s strengths and weaknesses.
To assure our readiness, a holistic approach is essential, as an effect in one FA or BA could have a serious impact on another. This is where the Cross Functional Teams come into play — they create the ability to work horizontally, gather information across NCIA as a team and collectively deliver the service required in a time of conflict or an Article 5 invocation.
In terms of crisis response, what is NCIA doing to ensure that it is able to not only maintain but also boost service levels?
PH: The ongoing work is not necessarily designed to boost service levels, but rather to identify the priorities of service requirements at a time of heightened crisis, conflict or an Article 5 invocation. It pinpoints what SACEUR’s service priorities are. For example, if we have to shift and surge efforts, what services are most important? In recent times, NATO has been actively modifying its posture towards a conflict footing, with the establishment of Supreme Headquarters Allied Powers Europe (SHAPE) as the Strategic Warfighting HQ and the promulgation of the Family of Plans (FoP).
NCIA is doing the same. Our Crisis Management Concept of Operations (CONOP) is being thoroughly refreshed to align it with NATO’s new ‘Response Measures’ language and to incorporate the relevance of DDA and FoP. Armed with a revised CONOP and a thorough understanding of the constraints and limitations of NCIA, we can begin to address these shortfalls and assure NCIA’s collective readiness. The timeline to complete this work is necessarily ambitious and will be stress tested through a comprehensive exercise programme at the earliest opportunity. Starting with an internal tabletop exercise this autumn.
From a service management perspective, what adjustments have already been made to ensure 24/7 service availability?
Angelo Talarico: NCIA is executing a series of coordinated improvements at strategic, operational and tactical levels to ensure that services remain resilient and responsive regardless of scale. Strategically, under the Chief Service Operations (CSO), we are rolling out a new Enterprise Service Delivery Model (ESDM), designed to enhance the integration between project obligations and continuous service imperatives. It reinforces internal service delivery governance, clarifies roles across a multi-entity framework and frames long-term delivery built around service assurance.
Operationally, Service Management and Control (SMC) has implemented more than 10 enterprise-wide service management practices with the exceptional support of
FAs and BAs, including incident management, change coordination, problem management and continual improvement. Just a few years ago, NCIA lacked a real ‘enterprise service delivery’ discipline and culture. These are not theoretical deployments, but practices embedded and active, with technical ownership integrated inside the organization.
At the tactical level, we are leading the creation of the Incident Response and Readiness Team (IRRT), a cross-functional, 24/7-capable structure. This ‘team of teams’ shifts our posture from reaction to readiness. IRRT will be capable of handling escalations at speed and with a cohesive structure, across mission-critical networks like those of Allied Command Operations (ACO) and Allied Command Transformation (ACT).
As indicated by our GM, the hybrid model we have conceptualized is controlled and accountable: industrial partners will extend our capacity, while core functions such as incident triage, escalation paths and performance tracking remain in-house. This balance protects the enterprise while offering the flexibility needed for future demand.
I want to recognise the pivotal support of BA leaders across the organization and beyond, with the excellent support from ACO operational partners. Their commitment and the operational clarity provided by CSO are enabling this transformation. We are no longer debating maturity; we are acting on it.
What do you consider to be the priorities going forward?
AT: NCIA exists to serve, and our purpose is to support the operational partners across the NATO ecosystem. We are NATO professionals serving NATO professionals. Our work is extremely challenging and requires high levels of motivation. Now that the structural foundations are becoming part of our DNA, our priority is the disciplined satisfaction of user requirements. This means consolidating practices, expanding automation and deepening data integration. We are focused on enhancing monitoring and the configuration of systems across static and deployable networks, where much of our critical demand originates. The IRRT will evolve from a reactive force into a forward-looking unit. Soon it will run simulations, identify risks and prepare for the unexpected. This is resilience by design, not by chance.
Another priority is intelligence-led service management. We are putting in place the solid foundations upon which we will build the analysis layers that will enable us to move from data collection to predictive insight. With stronger reporting and decision support, both internal stakeholders
and external partners will be better equipped to anticipate issues and allocate resources efficiently.
But above all, our priority is people. We are investing in the next generation of internal experts. This includes expanding job families, assigning process authority, refocusing the workforce and mentoring future leaders. This article is part of that effort to offer transparency, but also to inspire those within NCIA who are willing to carry this heavy commitment forward.
What planning are you undertaking to meet future requirements?
AT: The operational partners’ demand in service delivery is increasing multifold. Over three years, we moved from ‘next working day’ to on-call and 24/7. But this is a huge commitment, and we need to move at a steady pace, taking reasonable risks. Planning has shifted from roadmap theory to implementation strategy.
Our six-year service management transformation, funded in 2019 by the NATO committees, is almost complete, but we are already facing yet another demand increase due to the global geopolitical crisis. We have to align service management with projected surges, regulatory expectations and integration requirements. ‘Cloudification’ and industrial partnership are the key. This includes phased delivery of new technology such as new systems for ticketing, configuration and event management, all designed for both core and deployable environments.
Outsourcing is no longer supplemental: it’s strategic. But it only delivers value if internal governance remains firmly anchored to NCIA’s core components. That’s why the newly established Transition Planning and Support Office (TPSO) maintains dedicated oversight of these partnerships, ensuring they support, not substitute, our service model.
Internally, in CSO and SMC, we are reinforcing authority through mission-based leadership. Each initiative we lead has been generated from specific mandates in the form of mission command. Our missions are not abstract, but operational, time-bound and aligned with the core service-level requirement obligations of the enterprise and the GM’s priorities.
Finally, this is about culture. Service Management is not only about tools or practices; it’s about belief in the structure, in the people and in the discipline we bring. I hope that comes through clearly in the work of every single SMC member who continues to make this vision real.


The NATO Digital Workplace Centre is maximizing user experience and empowering enterprise readiness through a progressive outsourcing programme. Senior Business Analyst at the NATO Digital Workplace Centre, Laura Bercan, outlines the aims and aspirations of the project to Simon Michell
What is the Managed Device Service outsourcing programme and what does it cover?
The Managed Device Service (MDS) outsourcing programme is a transformational initiative designed to modernize the way NATO manages its end-user devices. This programme enables us to outsource device provisioning, logistics and real-time support to industry, ensuring we align with global best practices. The MDS programme covers a comprehensive range of devices required to create an effective digital workplace on all classification levels: workstations, thin-client devices, laptops, monitors, smartphones, Voice over Internet Protocol (VoIP) phones and keyboard video and mouse
(KVM) switches. This new model mainstreams obsolescence management by monitoring and replacing devices before they become obsolete, eliminating the need for complex standalone obsolescence projects.
The outsourcing programme also brings the added advantage of crisis management, capitalizing on industry’s ability to quickly scale hardware requirements up or down based on changes in customer demand. By leveraging industry expertise, NCIA can focus on core operations while ensuring that our workforce has access to up-to-date and resilient technology.
Can you outline the key aspirations and aims of the MDS programme and why these priorities are important to NATO?
The key aspirations of the MDS programme align closely with NCIA’s digital #OneNATO vision, aiming to enhance operational efficiency and user experience. Our goal is to ensure enterprise readiness through a more efficient and streamlined approach to device management. One of our top priorities is enhanced user experience. As part of this, we want to reduce device delivery times and provide new equipment within days rather than months, which can sometimes be the case at the moment.
Additionally, we are adopting a performance-based acquisition model by shifting from traditional service contracts to an outcome-focused approach. Our suppliers will be held accountable for service quality levels, including a Customer Satisfaction Score target of 75%. Another major focus is moving away from a
single-brand strategy, which has posed resiliency risks in the past. By engaging multiple brands, we enhance supply-chain flexibility and reduce risks associated with hardware shortages or vendor dependencies. This programme also ensures that all devices are tracked through a web-based asset management system, further increasing efficiency and accountability.
How will the MDS programme enhance NATO Readiness and who will be affected?
The MDS programme is a game-changer for NATO’s readiness strategy, as it strengthens our enterprise-wide IT infrastructure. NCIA customers and users will be the primary beneficiaries since they will experience minimal downtime when they need replacement devices. With the new model, devices will be shipped directly to the user’s location, ensuring that business operations continue seamlessly. IT and customer support teams will also benefit because the outsourcing of device

“We want to reduce device delivery times and provide new equipment within days rather than months, which can sometimes be the case at the moment”
management enables them to focus on strategic projects rather than being overwhelmed with troubleshooting and procurement. NCIA will see improvements in operational resilience and financial efficiency, as the programme provides long-term cost predictability and better asset management. Additionally, the new proactive obsolescence management feature prevents disruptions due to outdated technology. Without doubt, this strategic shift ensures that NATO remains agile, resilient and prepared for future challenges.
When do you expect to be able to award the MDS contract and how long will it last?
We expect to award the MDS contract by the end of Q2 2025. This marks the beginning of a structured transition to the new service model, ensuring a seamless implementation. The initial operating capability is planned to be in place five months after the contract is awarded, allowing for a follow-up phased rollout to ensure that all locations and customers experience a smooth transition.
The contract itself will be a multi-year agreement, designed to provide long-term stability and ongoing service improvements. The multi-year structure enables NCIA to maintain a sustained focus on operational efficiency, ensuring continuous refinements based on performance evaluations and user feedback.
How will NCIA measure the success of the MDS contract once it is awarded?
To ensure the success of the MDS contract, we have established a set of well-defined quality metrics. Firstly, all new devices will be accounted for through a web-based asset tracking tool, ensuring transparency and accountability. One of the key success indicators is delivery efficiency — all requested devices must be delivered within five business days. Additionally, as I have previously mentioned, we have set a Satisfaction Score target of at least 75%.
Another crucial metric is obsolescence management, ensuring that devices are refreshed three months before their life expectancy expires. Furthermore, we have introduced a rapid replacement system, where faulty, lost or stolen devices will be replaced within priority timelines that ensure minimal impact on operations. These performance measures will help us continuously refine the MDS service to make sure that it meets the evolving needs of NATO.
The journey to a quantum-ready Alliance has begun, and certain steps will ensure NATO maintains its technological edge

As NATO accelerates its digital transformation to meet the demands of multi-domain operations (MDO) by 2030, quantum computing is emerging not just as a technological breakthrough, but as a strategic necessity. From cryptography to simulation, quantum technologies are poised to reshape the defence landscape — offering both unprecedented capabilities and complex challenges.
Quantum computing leverages the principles of quantum mechanics — superposition, entanglement and tunnelling — to perform calculations that are unfeasible for classical computers. This leap in computational power is already transforming scientific discovery, particularly in fields such as materials science, chemistry and optimization.
Microsoft’s Azure Quantum Elements platform, for example, has demonstrated the ability to accelerate certain chemistry simulations by up to 500,000 times. This is not just a scientific milestone — it’s a strategic asset. In defence, such capabilities can be applied to the development of advanced materials for stealth technologies, energy-efficient propulsion systems and next-generation sensors.
Moreover, quantum simulation can model complex battlefield environments, enabling more accurate wargaming and mission planning. These capabilities are critical for NATO’s ambition to conduct seamless MDO across NATO’s land, sea, air, space and cyber operating domains.
Quantum computing’s most immediate impact on defence lies in three domains: cryptography, sensing and optimization.
Cryptography: Quantum computers threaten to break widely used encryption schemes. This has led to a global race to implement post-quantum cryptography (PQC). NATO’s own quantum strategy acknowledges this risk and prioritizes the transition to quantum-safe cryptographic systems. Microsoft is actively supporting this transition through its Quantum Safe Program, which includes tools to assess cryptographic readiness and implement PQC across hybrid environments including secure cloud infrastructures used by defence and intelligence agencies. This includes support for
NIST-selected algorithms such as ML-KEM and XMSS as well as early access to PQC capabilities in Windows Insider builds and Azure Linux, enabling secure experimentation and deployment at scale.
Quantum sensing: Quantum sensors offer ultra-precise measurements of time, gravity and magnetic fields. These can be used for GPS-independent navigation, submarine detection and enhanced situational awareness — capabilities that are vital for NATO’s operational edge.
Optimization: Quantum algorithms can solve complex logistical problems faster and more efficiently. This has direct applications in supply-chain management, troop deployment and resource allocation — core components of NATO’s operational readiness.
Although quantum computing will eventually touch every scientific domain, several fields stand out for their immediate relevance to defence:
• Materials science will use quantum computing to enable the development of lightweight armour, high-temperature superconductors and stealth coatings for vehicles and soldiers.
• Pharmaceuticals, biosecurity and medical research will harvest the benefits of quantum notably for ultra rapid drug discovery and countermeasures development.
• Climate and environmental modelling will benefit from
quantum computing as it will enable much enhanced mission planning in extreme environments.
• Operations research will benefit from real-time optimization of battlefield logistics and communications with the integration of unmanned vehicles guided by quantum-optimized AI.
In addition to the above, quantum computing will also help to design quantum-enhanced radars to better detect ‘stealth’ objects as well as autonomous systems that make real-time course corrections using onboard quantum calculations to evade defences.
The NCIA Technology Strategy explicitly recognizes quantum as a pillar of NATO’s digital transformation, alongside cloud computing, AI and cybersecurity. NATO’s vision for MDO requires seamless integration of capabilities across all domains.
Quantum computing can act as a force multiplier by enabling:
• real-time data fusion from disparate sensors and platforms,
• secure communications through quantum key distribution,
• enhanced decision-making via quantum-enhanced AI models to analyse very large datasets and deliver better situational awareness.
Quantum computing does not exist in isolation. Its power is amplified when integrated with cloud infrastructure and AI.
Cloud: Microsoft’s Azure Quantum platform provides scalable access to quantum hardware and simulators. This would enable NATO and its partners to experiment, prototype and deploy quantum solutions without the need for costly and complex systems to manage on-premise infrastructure.
AI: AI agents, such as those embedded in Microsoft Copilot, can help scientists and analysts interact with quantum systems using natural language. This lowers the barrier to entry and accelerates the development of quantum applications.
Together, cloud and AI form the digital backbone that supports NATO’s quantum ambitions. They enable secure, scalable and collaborative innovation — key tenets of NCIA’s technology strategy.
In February 2025, Microsoft unveiled Majorana 1 — the world’s first quantum processor powered by topological qubits. This breakthrough represents a major step towards building a fault-tolerant quantum computer capable of scaling to millions of qubits on a single chip. Topological qubits are inherently more stable and less error-prone than other qubit types. This makes them ideal for defence applications, where reliability and resilience are paramount. Microsoft’s roadmap includes:
• Quantum Development Kit (QDK): a suite of tools for writing and debugging quantum algorithms.
• Azure Quantum Elements: for simulating quantum chemistry and materials science.
• Quantum Safe Program: for assessing and implementing PQC across hybrid environments.
Quantum computing is not just a technological challenge — it’s a geopolitical one. NATO’s quantum strategy calls for a “quantum-ready Alliance” that can harness these technologies while safeguarding against their misuse. This requires:
• interoperability: common standards and frameworks for quantum software and hardware,
• talent development: training programmes to build a skilled quantum workforce,
• joint experimentation: platforms such as the NATO Digital Foundry to test and validate quantum solutions,
• secure collaboration: cloud-based environments that enable secure data sharing across nations.
Microsoft is committed to supporting these goals through its partnerships with NATO, NCIA and nations.
We believe that quantum computing, when responsibly developed and deployed, can enhance collective security and strategic stability.
Quantum computing is no longer a distant dream — it is a present-day imperative. For NATO and its partners, the challenge is to move from discovery to deployment — from experimentation to operationalization. By integrating quantum with cloud and AI, and by fostering a collaborative ecosystem of industry, academia and government, NATO can maintain its technological edge and operational superiority. The journey to a quantum-ready Alliance has begun. Let us walk it together — with purpose, urgency and vision.
quantum.microsoft.com


The newly appointed Chief of Air Command and Control at NCIA, John Booth, offers an insight into how AirC2 is evolving and how he expects it to become ever more important as NATO adopts a more MDO-based operational doctrine


Why is Air Command and Control central to NATO’s readiness status in Europe as well as its ability to adopt multi-domain operations?
NATO Integrated Air and Missile Defence evolved from the original concept of NATO Integrated Air Defence, which started in 1961 with the NATO Integrated Air Defence System (NATINADS, latterly NATINAMDS).
Air Command and Control (AirC2) is a critical part of the NATINAMDS and is one of the longest-running collective defence missions both within the Alliance and more broadly. The Alliance has a network of national and NATO systems and sensors across the NATO Command Structure (NCS) and NATO Force Structure (NFS) that are connected and share real-time and non-real-time data to protect the airspace of Alliance member countries 24/7. The networked AirC2 systems enable NATO to rapidly react to incursions and to defend Alliance airspace.
As the Alliance increasingly moves towards integrated activity across all domains through multi-domain operations (MDO), the AirC2 Centre’s products and services support the exchange of the complex data needed to ensure mission success. This routinely occurs between the air and maritime domains and is increasingly involving the land domain as well. The blurring of domains, and the need to securely exchange air, sea,
maritime and space data, is vitally important, especially in a cyber (and physically) contested environment. The staff in the AirC2 Centre have a wealth of domain knowledge and technical expertise to support and work with colleagues across NCIA to provide the very best capabilities to both the NCS and the NFS.
What part does the AirC2 Centre play in the creation and maintenance of a NATO Recognized Air Picture in Europe and how does this relate to NATO Readiness levels?
The NCIA AirC2 Centre, in close collaboration with other areas of NCIA, provides many of the real-time and non-real-time systems and networks that enable the AirC2 warfighters to conduct their mission — from the Control and Reporting Centres (CRCs) through the NATO Combined Air Operations Centres (CAOCs) to NATO Air Command (AIRCOM). Together with NATO national capabilities, our products and tools support both the real-time production of the Recognized Air Picture (RAP) and the planning and execution of the day-to-day missions in both peacetime and times of crisis. It is safe to say that without the team of AirC2 experts within NCIA, the NATINAMDS, and therefore defence of the Alliance, would not be able to function anywhere near as effectively as it does today.

The AirC2 Centre products and services are in hundreds of locations across the Alliance, spanning both NATO and national systems. We also ensure data is exchanged at the appropriate security levels between military and civilian systems; this bidirectional exchange of data increases the awareness of all parties and enhances air safety across Alliance Nations.
How does NCIA AirC2 support the main AirC2 Commands in Torrejón and Uedem?
The fantastic team in the AirC2 Centre, in collaboration with the local NCIA CIS Support Units, provide a vast array of support, from maintaining current systems to working with the operational community to identify new and emerging requirements and troubleshooting issues. We are particularly proud of our deepening engagement with the actual AirC2 operators. Our aim is always to put the ‘warfighter first’ in everything we do.
How do you think that AirC2 will evolve?
Given the events in Ukraine and the ever-evolving threats the Alliance faces, the need to provide a federated ‘system of systems’ that is both resilient and has dual redundancy has become a priority for NATO. The Air Policing mission will undoubtedly endure, but NATO is now focusing on how to conduct much more complex missions in a higher-threat environment. As has been seen in Ukraine, the need to be able to disperse and conduct distributed operations is key to ensuring Alliance security is not compromised.
These requirements also rely heavily on having the resilient network architecture in place to support the exchange of secure data. The need to eliminate ‘single
points of failure’ and to have multiple redundant systems that are both cyber and geographically distributed is now more important than ever.
How do you see the AirC2 Centre evolving to support the new focus?
We are already adapting our approach to enable a ‘fail fast’ methodology. Our aims are twofold. First, we will continue to deepen our work with the operational users to understand how their approach to defending the Alliance is evolving. Staying close to the ‘front line’ will enable us to develop our capabilities quickly and adapt at pace.
Second, the need to move to an increasingly federated system will require us to rapidly assess new capabilities and, if viable, bring them into service much more quickly than before. We have already adapted our technical testing and interoperability facilities so we can respond to the operators’ needs. Importantly, our emerging ‘fail fast’ approach will ensure that capabilities that are of limited use are discarded.
How will the AirC2 Centre achieve such a change?
The technological pace of development is eye watering. Gone are the days where national entities produced cutting-edge technologies which then cascaded into everyday life. Industry now develops and fields capabilities in everyday life at a speed that is breathtaking. Only through closer collaboration with industry, via a combination of outsourcing and NCIA in-house development, will we be able to adapt to that change.
Over five days, from 31 March to 4 April, NCIA held its fourth INTEND (Internal NCIA Test Event for New Development) exercise at NAMIF (NCIA AirC2 System Maintenance Interoperability Facility) in The Hague. The aim of the event was to stress test interoperability levels among various NCIA systems in an effort to demonstrate how well they would perform under realworld conditions. The systems covered in the verification and validation sequence focused on digital connectivity and new software, and included:
•ACCS – Air Command and Control System
•AirC2IS – Air Command and Control Information Services
•CSI – CRC System Interface
•DISG – Data-Centric Information Services Gateway
• FAST– Functional Area Service for Dynamic and Time-Sensitive Targeting
•ICC – Integrated Command and Control
•IOTA – Inter-Operability Test and Assessment
•ITC – Integrated Training Capability
•J-chat to TDL Gateway
•JTS – Joint Targeting System
•NIRIS – Networked Interoperable Real-time Information Services
•SSSB – Ship Shore Ship Buffer
•TEA – Tracker Evaluation Application
Unique in being the only internal NCIA interoperability exercise, INTEND-04, as this fourth iteration is called, was consequently supported by a large number of NCIA experts, including engineers, testers and operators. During five days of intense activity the INTEND-04 participants focused on key interoperability capabilities within NCIA, covering:
• Air operations digital conduct
• Air scenario definition and preparation of relevant messages
•Air to space integration
•Ballistic Missile Defence
• Cross network activities
•Data forwarding from JREAP-C to Link 22 and vice versa
•Over the Horizon Gold
•Real-time target transmission over Tactical Data Link
•Variable Message Format
Guests and VIPs who were visiting NCIA during this event had the opportunity to get fully involved in the test activities and were able to witness at first hand the results in terms of innovation and interoperability in a fully digital multi-system environment. They also actively evaluated some events executed in real time while they were in front of the actual systems.
As the Alliance moves closer towards a federated system-of-systems approach across all five of its operating domains — air, land, sea, space and cyberspace — exercises like INTEND will become progressively more important, not just to validate and verify digital connectivity and new software but also to develop new ways of interoperating. Equally important, according to the course coordinator and planner, Lt Col Mario Cozzolino, is the fact that INTEND strengthens “our ability to create a community inside NCIA which can share knowledge, experience and technical expertise on our journey to a working multi-domain operations capability.”
Nokia’s solutions make it possible to deploy essential capabilities when and where they matter most

Can you describe Nokia and its core technology offerings?
At our core, Nokia is a global leader in the development and deployment of advanced communications technologies. With a legacy rooted in innovation and trust, we provide end-to-end mission-critical networks that serve customers across telecommunications, enterprise, defence and government sectors. Our portfolio spans fixed, mobile, cloud and artificial intelligence (AI)-enabled networks. Each solution is built with security, scalability and resilience in mind.
For defence, Nokia’s value lies in our ability to adapt commercial innovation for defence forces’ information advantage. Our solutions include 4G/LTE and 5G networks, IP/ MPLS routing, optical transport, edge cloud infrastructure and industrialgrade cyber security. The acquisition of Fenix Group and the integration of the Banshee portfolio significantly strengthened our tactical
communications offerings. These technologies give Allied forces resilient, high-throughput, ultra-low-latency connectivity in contested and harsh environments.
Nokia is the catalyst for accelerating defence modernization. We deliver scalable and secure network capabilities that increase mission effectiveness at the tactical, operational and strategic level. Our networks will provide the interconnectivity required to unlock the latest disruptive technologies such as quantum, robotics, AI at the edge and ISR distribution at scale.
How important is R&D to Nokia and how much do you invest each year?
Research and development is at the heart of Nokia’s ability to lead, adapt and serve as a spark for change. We invest over €4 billion annually in R&D to advance our capabilities across mobile networks, cloud infrastructure, optical transport and cyber security.
Nokia Bell Labs, our world-renowned research arm and one of the most storied research institutions in the industry, drives much of this innovation. It has a legacy of pioneering breakthroughs that shape global communications. Today, Bell Labs is focused on the technologies that will underpin 6G, quantum networking and artificial intelligence at the tactical edge.
For defence, this sustained investment ensures our solutions are future-proof, secure and ready to support missioncritical operations. Our focus on R&D enables us to deliver interoperable,
high-performance networks that evolve with the mission while maintaining information resilience under pressure.
Why did Nokia choose to support the defence sector and what capabilities does Nokia offer?
Modern warfare is rapidly evolving as digital transformation drives new demands to maintain a strategic advantage. Success in multi-domain operations now depends on seamless, resilient and interoperable communications. Nokia has the technologies that enable an operational advantage in every domain.
We are actively building the ecosystems that modern defence depends on. That means collaborating with commercial and defence leaders to ensure our technologies are interoperable across platforms and programmes, contributing to NATO and 3GPP standardization efforts, and running joint exercises with Allied forces.
Information superiority is imperative to mission success in today’s increasingly complex landscape. Nokia provides the technologies that can help Allied forces maintain that advantage.
Can you explain why 5G is so important for the defence sector and reveal some of the benefits 5G delivers?
Defence communications must evolve to keep pace with technology and 5G supports this shift. 5G is a force multiplier for defence operations by delivering 10x performance at a tenth of the cost. Unlike traditional systems,
5G networks offer high-bandwidth, low-latency connectivity that scales from headquarters to the tactical edge supporting real-time data exchange across domains and platforms.
Strategic advantage depends on getting the right data to the right person at the right time. That means enabling the Internet of Battlefield Things (IoBT) to support sharing situational awareness in real time, coordinating actions across Allied forces, and moving faster than the threat. Modern wars have taught us the importance of enhancing situational awareness, and such awareness is achieved by connecting devices, sensors, or drones able to retrieve large amounts of data like — but not limited to — videos in real time. This data can now be analysed in real time, leveraging AI applications that are easily hosted at the edge of the network, such as in armoured vehicles on the battlefield. 5G’s ability to support massive device connectivity combined with native support for slicing and automation allows defence forces to tailor networks for specific mission needs while maintaining operational security.
The next point is how to connect this Internet of Battlefield Things to the edge with the right capacity. But capacity is not the only limit of the current tactical technology. As stated by the UK Chief of the General Staff, Sir Charles Roland Vincent Walker, in 2024, “Modern telecommunication networks should connect to any sensor, from any domain, from any partner.”
Interoperability is becoming critical for enabling Allied defence forces to communicate and collaborate, and 5G being based on a standard technology is intrinsically interoperable. This is reinforced by the draft STANAG proposed for ratification within NATO and verified via 5G interoperability testing at NATO CWIX exercises.
5G is more than a new generation of connectivity; it’s the foundation for faster decision-making, smarter operations and more integrated
defence ecosystems. It is an operational asset that gives Allied forces the survivable, sustainable and sovereign network foundation needed to maintain the information advantage in contested environments. Next Gen Communications (5G) is one of the key emerging and disruptive technologies (EDTs) mapped by NATO and it is acknowledged its deployment in the field will be key for enabling other EDTs, such as AI, in the tactical edge.
What are the unique selling points for ‘Nokia 5G for Defence’?
From command and control to tactical operations, we are actively building the 5G ecosystems that modern defence will rely on for connectivity and operational agility.
Nokia’s 5G portfolio for defence, including the Banshee Tactical solutions, provides 3GPP-compliant radios that connect dispersed units and platforms with minimal infrastructure. These integrated capabilities will deliver a significant cost dividend when compared to the current communications concept of operations (CONOPS).
The Banshee portfolio meets NATO’s operational requirements with low SWaP, native PACE support, and a cognitive load that keeps operators focused on the mission. Banshee is built to operate in dynamic and denied environments enabling expeditionary units to maintain resilient, highperformance communications even in electromagnetically contested conditions. Whether it’s a forward operating base or a mobile command post, our solutions make it possible to deploy 5G capabilities when and where they matter most.
Can you share some Nokia 5G use cases to illustrate Nokia’s capabilities in the defence and public sectors? Nokia has delivered on 5G capabilities in recent deployments, illustrating its
real-world impact. In our collaboration with Lockheed Martin and Verizon, Nokia’s 5G solutions were integrated into the 5G.MiL architecture to enable faster data fusion, increased agile response times and improved interoperability across nextgeneration platforms.
During the Joint Viking military exercise with the Norwegian Armed Forces, Nokia’s 5G technology supported live field operations in extreme conditions, showcasing enhanced interoperability and secure mobile command capabilities.
In Finland with Telia and the Finnish Defence Forces, we achieved the world’s first successful cross-border 5G standalone slice handover advancing coalition interoperability and demonstrating how Allied forces can stay connected during transnational operations.
Most recently, Nokia signed a memorandum of understanding with blackned GmbH to create advanced deployable tactical networks for the defence sector. The partnership combines Nokia’s 5G technology with blackned’s defence digitalization expertise to develop high-performance nextgeneration tactical communications solutions tailored to Germany’s needs and adaptable for Allied use.




Throughout January and February 2025, NATO conducted Exercise Steadfast Dart 25 to practice the deployment of the new Allied Reaction Force to enhance the eastern flank. This activity showcased the Alliance’s readiness, capability and commitment to defend every inch of NATO territory.
NCIA’s Talia Goode asks Darius Žibalis, former NCIA DCSU OPEX Exercise Staff Officer, what the Steadfast Dart exercise hoped to achieve in terms of Alliance readiness levels and whether these aspirations were met

Why are exercises such as Steadfast Dart so essential for Alliance readiness and what impact do they have on NCIA?
Steadfast Dart 25 is a tactical-level Allied Reaction Force (ARF) deployment exercise designed to test deployable capabilities and procedures, as well as interoperability among participating troops and host nations. This exercise was a significant contributor to accelerating NATO’s readiness, as it marked the first-ever large-scale deployment of the ARF since its establishment on 1 July 2024.
The training demonstrated NATO’s ability to rapidly deploy forces from Europe to reinforce the defence of its eastern flank. This reinforcement took place alongside a simulated emerging conflict scenario with a near-peer adversary, showing the ARF’s ability to conduct and sustain complex operations across thousands of kilometres, under any condition.
Steadfast Dart 25 gave NCIA a critical opportunity to test and validate its deployable communication and information systems in a live, complex environment.
It helped assess cyber resilience, interoperability and the ability to scale secure communications across multinational forces. The exercise also provided key lessons for improving technical capabilities and ensuring rapid support during real-world operations.
Support to exercises and operations remains an overriding priority for NCIA. How do you and your teams support NATO exercises?
My colleagues and I, working in the Operations and Exercise Service Line at NCIA, are accountable to the Director of Communication and Information Systems (CIS) Support Units (CSU) for providing and supplying services to our customers who plan and/or execute exercises. Our work starts months or years before an exercise execution period and finishes after its conclusion.
Supporting exercises and operations means that we provide the customer interface in a consultancy capacity to deliver customer requirements in accordance with the CIS services offered by NCIA. We are also responsible for the budget coordination and for arranging the deployment of NCIA personnel.

Why are readiness and resilience so important in today’s security environment?
Readiness and resilience are critical in NATO’s security environment, especially from an information technology (IT) perspective, due to the rapidly evolving nature of cyber attacks and the increasing reliance on technology for military operations.
IT readiness ensures NATO can respond quickly to cyber threats and operational demands, while IT resilience supports continuity and recovery from disruptions, both of which are critical for NATO’s effectiveness in modern warfare. A resilient and ready IT infrastructure strengthens NATO’s defence and deterrence posture by making it less vulnerable to cyber attacks and ensuring operational flexibility.
How did Steadfast Dart 25 enhance NATO’s interoperability and what did NCIA contribute in terms of interoperability enhancement?
Steadfast Dart 25 played a crucial role in enhancing the Alliance’s interoperability by testing NATO’s ability to activate the ARF, coordinate its swift transit and project strategic deterrence by bolstering forces along the Alliance’s eastern flank. Interoperability is key for NATO to function as a cohesive alliance, especially given the challenges that arise from Allied forces using different equipment, communication systems and operational procedures.
During exercise Steadfast Dart 25, NCIA provided interoperable IT systems and ensured NATO’s communication networks and IT infrastructure
were compatible across different member countries, enabling seamless data exchange.
To strengthen cyber resilience during the execution period, NCIA secured communication systems by implementing encryption and protecting NATO’s IT infrastructure from cyber threats. Additionally, we supported the integration of tactical communication systems, ensuring compatibility among Nations’ systems for efficient coordination.
What are the key lessons NCIA and NATO learned from the exercise to further improve NATO’s preparedness in the future?
Steadfast Dart 25 provided several key lessons and takeaways for NATO and NCIA to enhance future preparedness. The exercise highlighted the need for better integration of communication systems across NATO Nations to ensure smooth joint operations. It demonstrated the need for faster and more accurate information sharing to accelerate decision-making in complex scenarios. NATO recognised the need for adaptable and scalable communication systems that can quickly respond to changing mission requirements.
Additionally, the mission reinforced the importance of robust cyber security, emphasizing the need for continued efforts to protect NATO’s IT infrastructure against evolving cyber threats. In the future, there will be an increased focus on and drive for cyber exercises alongside traditional military training to prepare all forces for hybrid threats.


Exercise Loyal Leda 2025 enabled participating units to showcase their ability to operate across the full spectrum of modern conflicts, where information and reactivity are paramount to success. NCIA’s Mariana Antunes asks Major Derek Aubin, from NCIA Operations and Exercises, to explain how the exercise has increased NATO readiness levels
What is Exercise Loyal Leda and how does it support NATO readiness?
Loyal Leda is a land-domain, tactical-level, computerassisted exercise that encompasses a wide range of modern warfare challenges, including cyber warfare, hybrid threats and multi-domain operations (MDO) to reinforce operational readiness and improve interoperability among Allied land forces.
The exercise is designed to enhance NATO’s collective-defence capabilities under an Article 5 scenario by testing and improving MDO, interoperability and command and control (C2) procedures. With the participation of up to 2,500 personnel across multiple NATO land forces and headquarters in the 2025 edition, the exercise helped improve seamless coordination between NATO
commands and national forces. Together, NATO forces tested their ability to coordinate and operate across land, cyber and hybrid warfare domains under realistic conflict conditions.
This was also the first iteration of Loyal Leda following NATO’s transition from the NATO Response Force (NRF) to the Allied Response Force (ARF), representing a major shift in NATO’s force agility and responsiveness.
How does NCIA support the exercise?
NCIA plays a pivotal role ensuring secure and resilient digital infrastructure during the execution phase.
This year, through the Communications and Information Systems Support Units (CSUs) in Uedem, Germany, Bydgoszcz, Poland and Izmir, Türkiye, NCIA’s key contributions included the provision of secure communications and IT support across multiple strategic locations, and the implementation of classified, interconnected multi-domain IT systems for seamless information exchange.
NCIA’s contributions significantly enhance NATO’s digital infrastructure, cyber resilience and operational effectiveness. For the next edition of Loyal Leda, NCIA experts will focus on delivering faster service transitions, refined cyber coordination and deeper command and control (C2) system integration.
Who else participates in the exercise, and why are they vital for success?
A key feature of the exercise is its multi-location setup, which simulates real-world operational challenges and enhances coordination among Allied forces. Loyal Leda’s 2,500-personnel spans from NATO’s land forces, multiple NATO commands, training centres and operational units. The diverse participation reflects NATO’s multinational approach to interoperability and rapid response, ensuring that forces can operate seamlessly under real-world collective-defence conditions.
Allied Land Command’s (LANDCOM) leadership delivers operational oversight and command structure coherence, while Multinational Corps South-East (MNC-SE) in Romania plays a crucial role in coordinating static land headquarters operations. The Joint Force Training Centre (JFTC), based in Poland, and the NATO Rapid Deployable Corps in Türkiye provide essential training, planning and execution support.
Why is it important to test NATO’s ability to respond to an Article 5 incident?
Testing NATO’s Article 5 response capability is critical for ensuring the Alliance’s ability to deter aggression and defend its member countries. Loyal Leda plays a key role in validating NATO’s readiness to conduct major joint


“ Loyal Leda ensures that NATO remains strategically prepared, technologically advanced and fully capable of defending its members”
operations in response to an attack on any member country, as well as reinforcing its deterrence posture. It demonstrates NATO’s ability to respond decisively and enhances operational agility by ensuring forces can mobilize quickly and coordinate across multiple command levels. Given evolving global security threats, Loyal Leda ensures that NATO remains strategically prepared, technologically advanced and fully capable of defending its members under Article 5 conditions.
What new concepts and capabilities were tested this year, and how successful were these trials?
Loyal Leda 2025 introduced several new concepts and capabilities to strengthen NATO’s digital and operational resilience. These key capabilities, such as the integration of new systems to improve operational planning and real-time situational awareness, and to enhance joint-force synchronization, were proven to be successful.
Trials showed improved decision-making clarity, communication speed, real-time data exchange and operational security that enabled mission continuity with minimal downtime, proving NATO’s resilience against cyber and kinetic disruptions.
Loyal Leda also tested a federated multi-domain IT ecosystem, which successfully enhanced operational agility, reinforcing NATO’s digital warfighting capabilities; and implemented classified interconnected systems for secure digital coordination among NATO forces.
Digital sovereignty isn’t just a technical vision, it’s a strategic imperative

Could you outline HPE’s vision of digital sovereignty, and why it has become so essential for NATO and its partners?
At HPE, we believe digital sovereignty encompasses three essential dimensions. First, data sovereignty enables NATO to control precisely where data resides, how it is transmitted, accessed and managed, helping to preserve confidentiality and compliance and strengthening security. Second, operational sovereignty provides NATO authority over infrastructure management, governance and oversight, including who operates their digital systems and how they’re audited. Finally, technical sovereignty facilitates transparent and more secure technologies, free from hidden external dependencies or vulnerabilities.
In addition, each artificial intelligence (AI) outcome is the result of three interdependent supply chains: energy, infrastructure and information. And they are used at least twice: once during training, and again during inference. Each of these chains can be choked, infiltrated or corrupted, whether
through cyber-attacks, geopolitical disruption or degradation of data integrity. Obtaining control over all three is fundamental to enabling more secure, autonomous AI-powered decisionmaking across NATO operations.
That’s why digital sovereignty isn’t just a technical vision, it’s a strategic imperative. For NATO and its allies, it is foundational to operational freedom, mission agility and long-term resilience.
What is HPE Private Cloud Enterprise with airgapped/disconnected management, and why is it uniquely suited to NATO’s evolving strategic needs?
At first, the idea of an ‘air-gapped cloud’ might sound contradictory. AI workloads are inherently cloud native — they depend on massivescale data and tightly networked compute, accelerators and intelligent data platforms. Although the core mathematics behind AI are decades old, true breakthroughs only emerged once the cloud made it possible to scale both data and compute simultaneously with a high-performance network. At that tipping point, model performance accelerates dramatically with scale.
Paradoxically, the workloads best suited to cloud-native environments, those that tackle the most sensitive, existential problems, are also the ones that must remain fully secured. Cloud-native flexibility and air-gapped security have traditionally been at odds. HPE set out to solve that contradiction.
With HPE Private Cloud Enterprise with air-gapped management, we have created an industry-first solution that merges cloud-native scalability with
strict isolation. It’s a fully integrated, turnkey private cloud platform — compute, storage, networking and software — tailored to customer needs and operated independently from external networks.
This approach is ideal for NATO, providing operational readiness even in situations of extreme cyber or connectivity disruption. Our solution helps ensure NATO’s digital sovereignty through rigorous compliance, operational autonomy and strategic flexibility, facilitating effective mission execution with enhanced security anywhere in the world.
Where have HPE’s sovereign cloud capabilities been adopted in a significant defence project?
Our partner ecosystem includes trusted technology integrators, sovereign cloud providers, secured data center operators and national integrators — all committed to high security, compliance and sovereignty.
A standout example is our recent collaboration with the French Ministry of the Armed Forces and Veterans Affairs, alongside our local partner Orange Business. The Ministry selected HPE and Orange to build Europe’s largest classified AI supercomputer.
This groundbreaking project, located at Mont-Valérien in Suresnes, France, involves an entirely air-gapped computing infrastructure — completely isolated from the internet. This autonomous environment enables more secure handling of classified data and training of sensitive AI models.
Managed exclusively by French nationals with security clearance, the project exemplifies data, operational and technical sovereignty in practice. Once fully operational at the end of 2025, it will significantly boost France’s AI capabilities in defence — underpinning initiatives such as conversational AI agents tailored specifically for military personnel, thereby enhancing operational efficiency and strategic advantage.
This collaboration marks a clear demonstration of HPE’s ability to deliver practical and sovereign infrastructure solutions with enhanced security, tailored precisely to complex national security needs.
How does AI specifically change the equation in air-gapped or limitedconnectivity sovereign environments?
NATO and Allied organizations handle vast amounts of classified or highly sensitive data, which must remain secure yet be rapidly accessible for analysis and decision-making. This increasing data complexity demands specialized solutions — especially in the domain of AI.
What’s needed today are cloud-native, air-gapped systems — designed from the ground up to support the agility, interfaces and operational scale required by modern AI. These are workloads of unprecedented computational intensity, operating at the very limits of what today’s novel GPU and accelerator architectures can deliver. They demand highly optimized infrastructure, including low-latency, AI-optimized networking and storage architectures built specifically to sustain training throughput and inference at scale.
But the demands don’t stop at the infrastructure layer. These environments are pushing into entirely new territory when it comes to energy, cooling and facility management. We’re now
building towards megawatt-scale racks and even gigawatt-scale AI factories. Meeting those challenges requires not just technology, but deep integration between compute, infrastructure and the physical environment.
HPE is at the unique intersection of all these technologies — bringing together cloud-native design with enhanced security features, AI-optimized compute, networking and storage, and a roadmap for more sustainable, scalable power and cooling. For defence and intelligence organizations that need to process critical data securely, extract insights rapidly, and scale without compromise, this synthesis isn’t optional; it’s essential.
How do you see air-gapped and sovereign cloud technologies evolving in the next three to five years, and how are you advising NATO and its partners to strategically approach their investments in these technologies?
Over the next several years, air-gapped and sovereign cloud technologies will become more adaptive, intelligent and resilient — but also increasingly built on commercial off-the-shelf components.
To succeed, we believe NATO must meet three core prerequisites: the ability to admit more data to be reasoned over by leading-edge AI, to gain deep insights in timeframes that matter and to turn those insights into action at scale. By helping to enable more secure, air-gapped AI training and inference to be positioned anywhere, we solve the equations of physics, economics and law that today force us to reduce, redact and discard data. We bring cloud-native, AI-native insights from the data centre to the operational theater — and project those insights to guide decisions where situational awareness, achieved before the adversary, becomes a decisive operational advantage.
Multiple areas of active research from Hewlett Packard Labs and our broader research ecosystem across NATO
partner countries and allies will build on the foundation of air-gapped private cloud. Confidential computing will help protect data not only at rest and in transit, but also during transformation. Quantum and quantum-inspired technologies will offer new capabilities in planning and reasoning — and new threats to conventional cryptography. Photonic, analog and neuromorphic computation hold promise for ultralow-latency, ultra-low-energy inference, enabling projection of AI reasoning to the furthest operational edges — air, land, sea and space.
In advising NATO and Allied organizations, HPE emphasizes a strategic, long-term perspective: digital sovereignty and more secure cloud environments should be seen not merely as infrastructure investments, but as foundational strategic enablers. This includes enabling data sovereignty — control over where data resides and how it is accessed and managed; operational sovereignty — authority over infrastructure operations, governance and oversight; and technical sovereignty — transparent technologies with enhanced security features, free from hidden dependencies. Achieving and sustaining this level of control requires building infrastructure around open standards, interoperability and modularity — so that investments remain protected, adaptable and mission-ready over time.



On 7 June 2024, NCIA celebrated the completion of a major upgrade to NATO satellite ground stations in four Allied Nations: Belgium, Greece, Italy and Türkiye. NCIA’s Principal Project Manager, Philippe Margot tells David Hayhurst how this upgrade has already started to enhance NATO readiness and capabilities
NCIA’s completion of major upgrades to four satellite ground stations in June 2023 represented a significant enhancement of NATO’s SATCOM capabilities.
The Satellite Ground Stations (SGS) project was launched in 2011, with Leonardo UK selected as the industry partner for the comprehensive upgrading and refurbishment of two larger (four-antennae) SATCOM ground sites in Kester, Belgium and Lughezzano, Italy, and two smaller (one-antenna) stations in Atalanti, Greece and Oğlananasi, Türkiye. A formal ceremony to mark the achievement was held in June 2024.
Achieving Final System Acceptance in 2023, the project’s success has vastly enhanced the Alliance’s satellite anchoring capabilities, providing far more reliable, efficient, secure and integrated communications links between Deployable Forces Headquarters and the Alliance’s vast SATCOM network.
Thanks to the outstanding capability delivery of the SGS project, NATO has nearly doubled its previous anchoring
competences, enabling it to achieve significantly more with just four stations, down from the original 21, while continuing to serve all Alliance members.
The SGS project was a NATO Security Investment Programme (NSIP) project, with NCIA acting as host nation. In a significant departure from its conventional degree of involvement, NCIA oversaw a team of more than 100 internal and external experts in this highly complex project. Beyond providing communication equipment and infrastructural capabilities, NCIA also supervised all relevant civil engineering works and infrastructural facility refurbishments at all four sites.
All the NATO SATCOM ground stations and ground terminals are owned by NCIA, which is also responsible for delivering new projects aimed at upgrading the sites or enhancing the existing capabilities. It is also tasked with site maintenance and operational readiness for the 20-year expected lifetimes of all four sites.

Maintenance duties vary depending on the site and domain, and NCIA plans to rely on a prime contractor to help ensure the smooth functioning of satellite anchor components.
NCIA’s Principal Project Manager, Philippe Margot, regards communication competencies as “the lifeblood of NATO”, and the successful site upgrades are “an achievement that is both timely and pivotal”. The near doubling of satellite coverage — achievable with only four sites — represents a profound enhancement of the resilience and effectiveness of the Alliance’s space capabilities. “These upgraded ground stations reinforce our preparedness for crisis and conflict, up to and including NATO Article 5. This is a strategic milestone for NATO,” says Margot.
“By providing NATO with improved coverage and strengthening the Alliance’s access to space capabilities, it’s making us more resilient and flexible.” Also led by NCIA, the NATO SATCOM Services 6th Generation
(NSS6G) consortium builds on the foundation laid by the 2020 Memorandum of Understanding (MoU) between NCIA, France, Italy, the United Kingdom and the United States. This agreement commits to providing critical SATCOM services to NATO over a 15-year period, from January 2020 to the end of 2034. NSS6G is also regarded as the successor to the NATO SATCOM Post-2000 project, which delivered satellite communication services from 2005 to 2019.
The new consortium sees the original partners joined by Luxembourg and Spain. The latter will provide next-generation resilience through super-high frequency (SHF) and ultra-high frequency (UHF) band capabilities that can be readily tailored to meet evolving NATO requirements, along with state-of-theart geolocation services. Luxembourg is providing the services through its GOVSAT satellite, while Spain enhances SATCOM capacities through Hisdesat, the operator of the Spainsat NG-1 satellite.
“NCIA plans to enter into several logistics support contracts that will run over the lifetimes of the ground sites, guaranteeing a comprehensive maintenance environment”
Margot emphasizes that the significant boost to NATO’s SATCOM preparedness was the result of nearly 15 years of dedicated collaboration among the Allies, Leonardo UK and NCIA. He regards the new signatories to the 2020 MoU, Luxembourg and Spain, as valued members of the NATO SATCOM family, able to provide invaluable technological prowess. Looking to the future, he says, “We must continue to work with our industry partners to explore new and innovative ways to leverage commercial SATCOM services to strengthen our space capabilities.
“With the capabilities delivered by SGS, we are ready to support NATO’s ambition to expand its space capabilities and services. This includes anchoring additional military and commercial off-the-shelf satellites, as well as space ships, across all Geosynchronous Earth Orbits (GEO). SGS also enhances resilient and secure political communication and consultation in line with NATO Article 4, and enables the rapid stand-up of exercises and missions in accordance with Article 5.
“In the current political climate, this capability empowers any NATO initiative, whether an operation or mission, to strengthen the Alliance’s eastern flank and sustain NATO’s support for Ukraine. It ensures that the demands of NATO Allies are met with resilience, security and a shared commitment to peace and freedom for all.”
In the interest of ensuring that NATO’s SATCOM systems remain resilient over the coming decades, NCIA plans to enter into several logistics support contracts that will run over the lifetimes of the ground sites, guaranteeing a
comprehensive maintenance environment. “There will also be additional projects under the Capability Package 9A0130 (CP130) that will further enhance our SATCOM anchor components, in particular increasing the number of antennae across the sites to cope with the increased space segment capacity and allow for the use of different frequency bands to enhance diversity,” Margot says.
Moreover, a next-generation Capability Programme Plan (CPP) is being defined by NATO Allied Command Transformation (ACT), based on the recent SATCOM Operational Requirement Statement (ORS) released by NATO Allied Command Operations (ACO). This nextgeneration CPP is expected to take effect by early 2027 and will address all new SATCOM-related challenges faced by NATO in the decades to come.
EMDYN explores geospatial intelligence data fusion in an age of misinformation

Chief Executive Officer, EMDYN
In today’s challenging information environment, deception isn’t just a tactic — it is increasingly a strategy.
From deepfakes to disinformation campaigns, modern conflict zones are flooded with false narratives designed to distort perception, delay response and undermine trust. Adversaries no longer need to outgun — they simply need to outmanoeuvre the truth.
EMDYN believes that the next generation of security depends on a new kind of clarity; one built not from isolated data points, but from fused, verified and mission-ready intelligence.
Whether on the battlefield or at the policy table, today’s leaders are facing a profound challenge: information overload without surety. In an environment where open-source platforms, social media feeds and sensor networks generate data by the second, validation rather than volume is now the key metric.
Geospatial intelligence (GEOINT) has long been a cornerstone of both defence and humanitarian operations. However, its role is crucially evolving. No longer confined to mapping terrain, today’s GEOINT connects the physical world with the digital battlespace.
By integrating diverse data sources — imagery, signals, human intelligence, open-source content and real-time sensors – GEOINT becomes a strategic fusion point for decision-makers currently operating in uncertainty.
And no one fuses data quite like EMDYN.
In-house AI — built for secure environments
What defines our bespoke geospatial intelligence fusion software, EMDYN Platform, is not just what we fuse, but how we fuse it.
Our proprietary, in-house AI is engineered to operate within classified or high-trust environments. Unlike off-the-shelf or clouddependent tools, our models never transmit data outside the secure perimeter. This ensures no third-party exposure, no unverified algorithms and no trade-offs between performance and protection.
This bespoke AI does not just secure data – it saves a huge amount of analyst time by identifying meaningful patterns in motion and behaviour, recognizing travel paths, common meeting points and frequently visited locations automatically. It can even detect when multiple targets are moving together, revealing hidden relationships in seconds. Analysts no longer spend hours cross-referencing data as EMDYN Platform delivers clarity at machine speed.
EMDYN platform: from complexity to instant clarity
EMDYN Platform redefines what is possible in geospatial intelligence. Purpose-built to manage extreme data complexity, it processes trillions of data points and turns them into intuitive, interactive visuals, all on a single screen. Analysts can move from question to insight in seconds, with a platform that feels more like instinct than interface.

By dismantling traditional data silos, EMDYN makes it virtually impossible for new silos to form. Analysts move seamlessly across sources, domains and formats with every query, ensuring all insights remain interconnected, up-to-date and transparent. By ensuring continuous interoperability and eliminating fragmentation, it becomes a force multiplier for intelligence teams, delivering critical clarity precisely when timing is most vital.
Data fusion is far more than aggregation, it is transformation. At EMDYN, we correlate disparate signals across multiple domains to create a single, coherent operational picture. Change detection becomes predictive insight. Noise becomes narrative. Misinformation becomes a challenge you are prepared to meet rather than a risk you have to absorb.
Consider a conflict zone where adversaries flood social media with geotagged disinformation, falsely
claiming humanitarian violations or military activity: on the surface, the claims supported by verified accounts, real video and convincing metadata seem credible.
Yet with fused intelligence from EMDYN, these claims can be rapidly cross-checked against satellite imagery, pattern-of-life baselines and verified sensor inputs. In seconds, the true picture emerges and decisionmakers regain the initiative.
Geospatial intelligence data fusion is far more than a technical capability, it is a strategic imperative. In operations where minutes matter and misinformation can escalate conflict, fused intelligence offers the clarity to protect lives, allocate resources intelligently and maintain the information advantage in an increasingly contested space.
At EMDYN, our mission is simple: to protect what matters most.
This means equipping our partners, not just with more data, but with intelligence that is trusted, timely and secure. In an age where perception is weaponized, truth must be engineered.
With geospatial intelligence data fusion, EMDYN empowers governments, security agencies and Allied organizations to stay ahead of threats, grounded in reality and always on the front foot. When the world is clouded by misinformation, insight becomes your most decisive advantage.

www.emdyn.com/what-we-do/ emdyn-platform

Simon Michell asks Amazon Web Services to explain how the power of partnerships can unlock the benefits of emerging disruptive technologies for NATO and its member countries
In recent years, innovators in technologies that deliver tools to transform national security and defence effectiveness have multiplied. Defence investment in cutting-edge digital technologies is increasingly prioritized alongside kinetic warfighting capabilities and traditional military platforms (air and missile defence, artillery systems and ammunition). Artificial intelligence (AI), cloud and quantum computing, advanced and secure connectivity and autonomous systems are disrupting and transforming traditional approaches to warfare.
Consider, for example, the transformation in opensource intelligence (OSINT) and how this enables accurate situational awareness to give real- and near-real-time visibility to decision makers.
The innovators behind these powerful solutions turn raw OSINT into insights in real time so that decisionmaking is based on accurate data. To do this, they need scalable, secure infrastructure that can handle the vast volumes of data gathered as well as offer advanced AI/ machine learning (ML) capabilities.

Luke Openshaw, Defence Industry Lead, Europe and NATO at AWS, explains: “If you look at the INT domains, such as GEOINT, the average commercial satellite produces over 20,000 high-resolution images a day. The ability to store, process, analyse and derive intelligence from this amount of imagery is only achieved using hyperscale infrastructure.
The global AWS Partner Network (APN) includes enterprises such as Maxar, Planet Labs, Blackshark.AI, Lockheed Martin and NVIDIA that provide dynamic space-domain awareness capabilities. Likewise, OSINT applications leverage hyperscale cloud infrastructure to process hundreds of millions of data points monthly and provide actionable intelligence to analysts at NATO.”
Osavul is a provider of such OSINT applications. It’s a 30-plus person startup founded in 2022, which leverages AWS to combat combination information operations. Its battle-tested solution collects 10-20 million data points daily from 5-10 million sources including social media, websites and messaging platforms. It uses AI to analyse multilingual content across text, images and video. Intelligence analysts use its tools to surface insights in real and near real time, including understanding adversaries’ activity in a specific geographical area.
According to co-founder Dmytro Bilash: “OSINT-based situational awareness is vital for cyber security. It’s the way to identify potential risks for your infrastructure. It gives geopolitical intelligence to assess the trends and risks affecting your organization. At a tactical level, it can provide
intelligence for decision-making during operations. Three years ago, the appreciation of OSINT was theoretical. Now, it can be seen how it really changes the battlefield.
“Adversaries heavily weaponize information to influence public opinion and force people to change behaviour. Malicious actors use social media, online communication and, increasingly, generative AI, as tools for cognitive or non-kinetic warfare. Osavul serves as a solution to identify, analyse and mitigate such threats. It’s our mission to deliver AI-powered, advanced tools to those who protect all of us.”
Experts at Osavul identify key narratives in the information environment, analyse who is spreading them and detect potential state-affiliated or bot-driven Coordinated Inauthentic Behaviour (CIB) malicious campaigns. The tools unify data and so support information sharing and collaboration between organizations.
The company employs hyperscale cloud to handle the immense volume, velocity and variety of data that is integral to operations. It can manage fluctuating volumes, use powerful tools and AI models and adapt rapidly across media formats and more than 30 languages. Cloud-based infrastructure provides low-latency data processing, which is critical for real time, effective threat detection and analysis.
All of this can be achieved with the highest-possible security, Bilash explains: “With hyperscale clouds, Osavul benefits from enterprise-level security measures and compliance certifications, ensuring sensitive data and intelligence are securely managed and protected

against unauthorized access or cyber-attacks. We know that the technology is compliant so we can focus instead on developing the solutions.”
DATAMINR — REAL-TIME EVENT AND RISK DETECTION
Dataminr is another innovator whose tools use OSINT to make national security and defence missions more effective. Phil Taneborne, Dataminr account director, reveals: “It’s during world-changing events that Dataminr’s data and AI need to function resiliently to drive decisions. Every second of advance warning in situations from the battlefield to natural disasters can make the difference in keeping assets and people clear of danger. The speed and resilience of AWS compute and storage facilitates this critical advantage.”
The company uses AWS to provide real-time event and risk detection. It ingests upwards of 43TB of daily data points drawn from more than one million texts, imagery, videos and machine-generated data on channels, including social media, news, blogs, sensors, cameras, audio scanners and the deep web. AWS infrastructure and analytics capabilities enable Dataminr to deploy predictive AI models that detect events by fusing signals from multiple modes of data in real time. An example could be an abrupt aircraft route change in AIS data, plus social media images of smoke and first responders dispatching assets to an unknown incident.
Cloud infrastructure enables Dataminr to assess multiple events/locations and serve multiple service users simultaneously across different geographic locations. The solution uses more than 35 foundational models, such as Domain Specific Language Models, to describe events concisely. Dataminr’s AI labels, locates and assigns impact to all information generated. Such labelling enables data to
be tuned to specific user needs across all geographies and domains of conflict. It also facilitates rapid integration into C2 and visualisation systems needed to conduct military operations. Dataminr uses generative AI to update events in multi-domain environments, globally. Information is sent to users’ devices and there are alerts for users’ specified information needs. Users can integrate other tools to query the information.
Pairing alerts with other sources of understanding accelerates the Orientate, Observe, Decide, Act (OODA) loop. In February, NATO announced a collaboration with Dataminr to expand use of AI to strengthen NATO’s networks, enhance real-time insights and bolster cyber and physical security.
The cloud environment enables Dataminr to continuously develop and deploy new AI capabilities. The team can test and implement new features without disrupting existing operations, ensuring the platform evolves to meet emerging information threats. “AI-based mission command tools offer Allied warfighters in command and in theatre a dynamic view of an operational environment by drawing on hundreds of real-time data feeds,” Openshaw explains. “Nations recognise that hyperscale cloud enables defence organizations to build and deploy resilient, scalable, interoperable and next-generation applications at speed, which maintain the Allied technological advantage over adversaries.
“Amazon is unwavering in our support for strong national security and defence. The strategic partnerships we have formed with defence innovators and defence primes will be fundamental to delivering lasting peace and security in Europe.”
Osavul: AI-powered global trade analysis — revolutionizing intelligence reports
OSINT has gained ground as an essential tool in decision-making in real time, often critical situations, leveraging millions of data points from multiple channels, formats and languages. To illustrate this, Osavul created a tool to assess the international response to trade reforms.
This tool collects data from 30 countries: the top 20 world economies by size and 10 countries most affected by recent trade changes. As a result, it is possible to analyse sentiment and trends within hours versus weeks, all on a dashboard on a laptop or mobile phone, and it is deployable by government economic policymakers and commercial industries.
In this use case, the AI-powered platform categorizes responses to global trade reforms into four overarching attitudes: attack (aggressive economic measures), contract (balanced response), pivot (seeking new partnerships) and friendly negotiate (finding common ground). It collects and processes data from every format — text, video, social media, websites — in more than 30 languages. It produces visual representations, including maps and charts.
The tool doesn’t replace human analysis, rather it provides objective data for decision-making and enables the human to identify anomalies and see trends. In this use case, that could be understanding what an official or expected government position might be versus what is actually being said and communicated.
Dataminr: Evacuating humanitarian workers in time of conflict
The United Nations describes the Sudanese civil war as one of the world’s worst humanitarian crises. When conflict erupted in Khartoum, organizations such as Pact and Save the Children had to evacuate staff amid escalating violence. With local news sources diminishing and on-the-ground intelligence becoming too dangerous to gather, Dataminr emerged as an essential tool for understanding the crisis and carrying out evacuation operations.
As violence intensified, staff relocation began. There were roadblocks and uncertain security conditions around Sudan’s capital, Khartoum. The situation demanded real-time information for swift decision-making.
Before implementing First Alert, Pact relied on messaging apps such as WhatsApp and Signal for local updates. Michael Frayne, Pact’s Global Security Director, noted a transformative change after adopting Dataminr. The platform’s real-time information meant information arrived in time to act, rather than after the event. This bridged the gap between local intelligence and actionable insights and enabled a more proactive security approach.
“It took me a long time to get my head around the power of the information I have at my fingertips,” Frayne admits.
During the Khartoum evacuation, Dataminr’s alerts enabled seamless coordination between field teams and global leadership, so that all stakeholders remained informed of latest developments.
The UK defence industry is shifting towards systems built with security in mind — here’s how

For years, the civilian sector has been transitioning to the cloud, drawn by its flexibility, scalability and reductions in cost and complexity from no longer maintaining its own physical infrastructure.
The defence and security sector has been more cautious to adopt cloud, concerned about data security, the risk of cyber attacks and the lack of control over sensitive information when stored off-site with third-party providers.
Beyond security, the military has some unique requirements compared to the civilian sector, including the need to operate in austere environments, interoperate securely and accelerate new capability.
So how can the military benefit from the opportunities the cloud offers while also mitigating the security risks?
Step forward Secure by Design (SbD). Introduced by the British government in 2023, it emphasizes designing security into systems, products and buildings from the outset rather than as an afterthought.
Today, all capabilities, technology infrastructure and digital services in UK defence must follow the SbD approach. This also applies in the development of legacy systems not built with security in mind, so potentially more susceptible to attack.
Aligning closely with the principles of NATO’s Zero Trust principles for cloud computing, SbD builds security into the very foundations of technology.
Here at Frazer-Nash we have been working on this approach since its inception, bridging the gap between suppliers and defence and security customers.
Secure by Design explained Through SbD, the UK defence industry is shifting away from periodic security accreditation to embedding security throughout the lifetime of any defence programme or capability, from concept to disposal.
SbD replaces periodic risk assessments with continual, risk-based assurance. Delivery teams must own the security risk of their capabilities and manage it effectively through its lifecycle. With any programme or technology, there must be a comprehensive and agreed security strategy with policies and procedures — including to protect sensitive information and maintain the privacy of users.
This new risk-management philosophy is more than just a compliance checklist, it is a change in mindset and a business transformation.
“With any programme or technology, there must be a comprehensive and agreed security strategy with policies and procedures — including to protect sensitive information and maintain the privacy of users”

Frazer-Nash has been working on the SbD approach since its inception, bridging the gap between suppliers and defence and security customers
We have been working with several defence and security customers on applying SbD practices to a range of systems including cloud.
For one customer, we created a bespoke analytical software tool based on a cloud infrastructure, communicating over the internet. To develop this securely, SbD principles were embedded from the outset. Every independent system had to be inherently secure instead of relying on a single source of security that could also be a single point of failure.
For example, our isolated storage area for critical data was designed with strict access requirements. These requirements informed all related design decisions. Throughout development we worked within these requirements. This prevented us from missing key security questions early on and provided the golden thread linking back to the requirements.
We made use of cloud infrastructure in our security thinking too. By offloading all data processing into the cloud instead of on local machines, we designed a system where confidential configuration information and data never left the secured cloud environment. Each part of the system was inherently restricted to only the information it needed to know.
As military operations across all domains rely on secure data for information superiority over adversaries, cloud technology is going to be an essential part of any toolkit. But to reduce cloud vulnerabilities and ensure robustness in defence, every connection and action must be verified.
In the UK, SbD is the necessary tool for managing the security of cloud technology. As an embedded
approach it identifies and resolves common development weaknesses in areas such as coding or encryption that might otherwise have been missed. In today’s complex and connected landscape, adopting SbD with cloud computing can mitigate the cyber security risks of our open world.

fnc.co.uk



Dr Alexander Hamilton , Director of Standardization and Science & Technology at Nokia and Chair of the NATO Wireless Communications Standards Project, and Juan Ramirez , Director, 5G Cross Functional Team, Office of the U.S. DoD CIO, highlight the scope and purpose of the NATO Wireless Communications Standards Project whilst revealing the key agencies and personnel that are driving it through NATO
The fabric of modern warfare is being reshaped by rapid digital transformation. At the forefront of this evolution is the need for seamless, resilient and interoperable communication across military domains. As Major General Devin Pepper of NATO Allied Command Transformation emphasizes, “Multi-domain operations (MDO) must integrate cyber and space domains. It’s essential to interact with non-military actors, synchronize activities and connect for better orchestration.”
Achieving this orchestration demands a robust communications backbone. Yet, for decades, military procurement and standardization cycles have lagged far behind the pace of commercial innovation, particularly in the telecommunications space. While 3GPP and other industry bodies deliver mobile network upgrades on 18-month refresh cycles, military standards can take decades. The result: a growing
capability gap that risks sidelining NATO from the connectivity needed for effective MDO.
By 2023, it was clear that a reset was needed. Rather than dictating standards from the top down, NATO began fostering a new model: a collaborative ecosystem where nations, industry leaders and academia jointly shape interoperable standards, grounded in proven commercial technologies. This vision sparked the creation of the NATO Wireless Communications Standards Project (NWCSP).
Established by the NATO Science and Technology Board (STB) and the Information Systems Technology (IST) Panel, the NWCSP set out with an auspicious but pragmatic goal: profile existing 3GPP standards, beginning with 5G, to develop NATO-compatible profiles, baseline specifications of interfaces,

protocols and parameters to enable secure, high-performance, interoperable deployments across operational domains.
From mobile command posts to maritime platforms and forward-deployed units, this communications infrastructure must function reliably under diverse and demanding conditions. Crucially, it must also be cost-effective, secure and scalable.
The initiative is spearheaded by a dedicated task force, chaired by Dr Alex Hamilton, with Vice-Chairs Germano Capela (NCIA) and Juan Ramirez (U.S. DoD 5G Cross Functional Team), and supported by Gerard Elzinga, Tamsin Moye and John Stephenson from the NATO Digital Staff. This collective endeavour powerfully demonstrates the potential that is unlocked when industry and government agencies forge a true partnership.
“This work demonstrates the value that the STO Collaborative Programme of Work (CPoW) brings to the Alliance,” says John-Mikal Størdal, Director of the STO Collaboration Support Office. “Underpinned by a unique collaborative business model, the CPoW brings together experts from academia, industry and government to deliver timely, impactful and cutting-edge research. I congratulate the leadership and the entire team for their fast, innovative approach to standardization, which will help to accelerate interoperability across the Alliance.”
Chartered in February 2024, the NWCSP Task Group comprises more than 100 experts drawn from government, industry, academic institutions and standards organizations. This carefully curated mix is what enables the project to bridge the commercialmilitary divide. Volunteer standards experts contribute deep technical knowledge, while government
stakeholders ensure alignment with security and strategic priorities. Academia infuses forward-looking insights and analytical rigour.
In just 18 months, the project advanced from concept to the delivery of mature draft standards: STANAG 5665 and its companion, AComP 5665. This pace not only accelerates capability development but sets a new benchmark for future NATO standardization efforts.
The formal submission of STANAG 5665 to NATO’s Digital Policy Committee (DPC) marks a major milestone. Held at the Pentagon and chaired by Dr Hamilton, the fifth NWCSP meeting drew wide participation from NATO member nations and industry leaders, highlighting the strategic importance of this initiative.
Gernot Friedrich, Chair of NATO’s DPC Communications Panel, notes, “The 2025 Spring Plenary of NATO’s Digital Policy Committee showcased the Alliance’s accelerating momentum towards digital readiness, with a clear message: NATO’s communications standardization efforts are being strategically led by the DPC. As the governing body driving digital policy, the DPC — supported by the NATO Digital Staff (NDS) — is central to aligning technological innovation with operational requirements across the Alliance. Crucially, the cooperation agreement between the STB and the DPC has emerged as a key enabler of accelerated, demand-driven standardization. This framework allows for the agile translation of cutting-edge research and commercial best practices into operationally viable NATO standards, such as STANAG 5665. By fusing policy leadership, scientific rigour and industry collaboration, this model represents a new era in NATO standardization — where speed, interoperability and mission relevance are no longer competing priorities, but shared outcomes.”
“ The impact of the NWCSP reaches far beyond technical documents.
It marks a fundamental change in how NATO develops capabilities”
Alongside NWCSP, NCIA plays a critical role through initiatives such as the Multinational Collaboration on 5G (MN5G), which ensures security and interoperability across national forces. MN5G’s work enables secure, reliable coordination regardless of national infrastructure, protecting critical data from interference and surveillance.
The NATO Digital Foundry also drives innovation by providing a platform for experimentation and rapid prototyping of new 5G-enabled capabilities. Coupled with forums such as the Military 5G Conference, these elements create a dynamic ecosystem for sharing knowledge and accelerating technological adoption.
To institutionalize progress, the NWCSP is now evolving into a permanent syndicate under the DPC. This structure ensures sustained oversight and a living standard capable of adapting to future needs, including integration with Non-Terrestrial Networks and the upcoming wave of 6G innovation.
So, what does this mean for NATO and its partners?
• Genuine interoperability: Member countries can confidently procure equipment across vendors, knowing it will operate effectively in joint environments.
• Accelerated capability deployment: Next-gen connectivity can be deployed faster than ever before.
• Enhanced cost-effectiveness: Leveraging commercial standards significantly reduces procurement and lifecycle costs.
• Fortified security and resilience: Military-grade protections are embedded from the outset, ensuring resilience across domains.
• Strategic futureproofing: A standards framework that evolves with technology ensures lasting relevance.
Anthony Smith, Principal Director for Command, Control, and Communications at the U.S. DoD CIO, adds, “The NATO Wireless Communications Standardization Project plays a key role in facilitating interoperability between nations leveraging 5G/NextG technologies and infrastructure. DoD CIO will continue to prioritize
the deployment of 5G across the Department, leveraging these information communications technologies for strategic warfighter advantage.”
STANAG 5665 defines core procedures, interfaces and protocols that ensure interoperable cellular systems can be developed and fielded across NATO. These standards enable integrators to build and commission 5G-enabled infrastructure with confidence as it meets both military and commercial benchmarks. By doing so, it streamlines procurement, accelerates deployment and reinforces mission success.
The U.S. DoD has committed to supporting this work through sustained investment, using it to shape its own 5G modernization programmes and guide broader Alliance priorities. As the lead body for enforcing IT standards across US defence, the DoD CIO recognises the essential role of NWCSP in aligning emerging technology with operational capability.
Dr Hamilton, Capela and Ramirez continue to lead technical efforts that ensure coherence, eliminate duplication and translate national requirements into functional standards. These efforts enable integrators and defence partners to define actionable roadmaps for secure, reliable and advanced wireless capabilities.
The impact of the NWCSP reaches far beyond technical documents. It marks a fundamental change in how NATO develops capabilities, moving from isolated national strategies to an inclusive, collaborative approach that draws from the best of commercial and military worlds.
By embedding collaboration at the heart of its standardization process, NATO is not only catching up to the pace of commercial innovation, it’s helping shape it. Through projects such ad NWCSP, the Alliance ensures its forces are equipped with the technologies they need to meet tomorrow’s defence challenges, securely, affordably and without delay.
Isn’t that exactly what modern defence demands?


Allied Command Transformation (ACT) Assistant Chief of Staff for Requirements, Brigadier General Thorsten Jørgensen, reveals how this year’s CWIX exercise will help the Alliance achieve credible multi-domain operations
CWIX (Coalition Warrior Interoperability eXploration, eXperimentation, eXamination eXercise) is a unique NATO event for two distinct reasons. First, with so many experts conducting technical tests, failure at CWIX is accepted and even welcomed, given that the testing personnel integrate lessons learned and apply fixes that ultimately make systems more resilient. Secondly, CWIX is not just about technicians. Digital interoperability is becoming more complex as the speed, availability and volume of data become increasingly overwhelming. Without warfighter input, there is a risk that systems will provide confusing data or inconsistent operational pictures, leading to ambiguity and inferior decisionmaking. At CWIX, technicians and operators sit side-byside to develop solutions, so that the right information is at the right place with the clarity and consistency needed for instant action.
Every CWIX event brings unique challenges and opportunities. CWIX25 will be no different with its increased focus on Alliance priorities such as multidomain operations (MDO), Federated Mission Networking (FMN) and the need to ensure that new technologies such
as artificial intelligence (AI) are developed and deployed. CWIX is growing, and Nations are increasingly aware that C2 systems are a cornerstone of Alliance warfighting ability. Without the standards and specifications that are the building blocks of digital interoperability — the core business of CWIX — NATO will achieve neither digital transformation nor its MDO ambitions.
Where and when is CWIX25?
This June, more than 3,000 interoperability experts will descend upon the Joint Force Training Centre (JFTC) in Bydgoszcz, Poland, to conduct NATO’s largest digital interoperability exercise. Led by HQ SACT (Supreme Allied Command Transformation) and supported by JFTC and NCIA, CWIX, now in its 26th year, will once again undertake tests and trials to develop and improve the building blocks of Alliance digital interoperability. These building blocks are the technical standards, STANAGS and specifications that, when built into a command and control (C2) system, will deliver seamless connectivity among the 32 Allied Nations and many NATO Partners, enabling NATO’s warfighters to conduct today’s missions and tomorrow’s MDO.
CWIX moved to JFTC in 2010 as it transformed from a demonstration of industry solutions to a test event designed to achieve digital interoperability among deployable, experimental, near-fielded and fielded systems. That’s not to say that industry at CWIX is any less important, but the shift from a demonstration of commercial solutions to testing solutions that are in development or in use has significantly changed its focus. JFTC’s role as a training establishment provides a perfect venue for this transformation with its laboratory environment and experimental networks. Over time, CWIX has grown from a collection of systems connecting and testing standards to the largest event in ACT’s annual calendar, hosting 600 deployable C2 systems focusing on Alliance warfighters’ priorities. JFTC continues to provide the venue, the infrastructure and the support for NATO and nations to conduct more than 20,000 digital interoperability tests over a three-week period across maritime, land, air, cyber and space domains, as well as functional areas ranging from Tactical Data Links, to Friendly Force Tracking to tactical soldier communications and data-centric security.
Describe the planning process that enables such a complex activity to take place.
The planning process for CWIX, by NATO standards, is short. It starts with initial guidance from the Digital Policy Committee (DPC), enabling Nations to provide input and priorities for digital interoperability testing. This also provides a framework for NATO and national ambitions beginning in September with an Exercise Specification Conference attended by national leads of participating nations, and focus area leads representing an operational domain or community of interest. The planning cycle is recognizable as it includes initial, main and final planning conferences before CWIX execution in June. This annual cycle focuses on the people and process elements of digital interoperability before technical tests are performed during execution. In this sense, the nine-month planning period, starting with objective development, capability definition and test-programme development, is every bit as essential for interoperability as the three-week test period itself.
What emerging technologies will be tested at CWIX25, and why have these been chosen?
Emerging technologies are a critical component of CWIX for two reasons. First, it is important to test interoperability between emerging technologies that nations are developing. This may include new standards or standardization organizations yet to be incorporated into the suite of NATO STANAGS or the FMN Roadmap.
One example is the standards being developed by the US National Institute of Standards and Technology (NIST),
which is developing post-quantum cryptography standards that will use public-key cryptography to defend our computers from quantum technologies. This year, four nations, including NATO, will explore and demonstrate systems that will exploit post-quantum technology, such as the 2024 version of the NIST Federal Information Processing Standards (FIPS) that are designed to withstand cyber-attacks from a quantum computer.
Another example is AI, which has been around for many years, but is developing at such speed and across so many disciplines that we struggle to keep up. But until AI standards become mainstream, we recognise that federating and testing AI at CWIX will remain a marginal activity. That said, the few AI capabilities at Bydgoszcz this year will rely heavily on computer vision algorithms to create innovative approaches to data analysis and decision support. Several nations will demonstrate AI-powered solutions for detecting and classifying objects such as aircraft or vessels, whether on satellite imagery or on a video feed. Others will leverage large language models (LLMs) and AI agents to facilitate the retrieval and parsing of information from multiple data sources that would otherwise be siloed. At CWIX, we see AI being integrated into C2 systems to optimize MDO and facilitate seamless data sharing through open APIs and standardized datalinks to enable rapid information exchange. These AI-enabled tools will support faster, more precise decision-making, reduce the cognitive load on warfighters and enhance interoperability by ensuring that diverse systems can communicate effectively within NATO’s FMN.
These are just two examples of emerging technology that will be tested at CWIX in June, highlighting an important question: with 32 Alliance members, why are so few nations testing them? The answer may simply be that nations are not ready to test at CWIX; the standards may not exist, or they are simply waiting for another Ally to develop the right technology before ‘jumping in’. Whatever the reason, at CWIX we evaluate where we are now, what is in the pipeline and where we need to be in the future.
As it has for several years, the CWIX Innovation Working Group will spotlight NATO and national capabilities that demonstrate innovation to the Alliance. The value these capabilities offer can range from new technologies to improved processes, or even a reduction in risk, effort or cost. Out of nearly 600 capabilities, only 10 have been selected for showcasing.
This year’s innovation for CWIX25 sees the introduction of an Innovation Sandbox. The goal is to provide an unclassified space where emerging tech and start-up

companies can demonstrate their capability and perform limited interoperability testing without requiring full-scale network accreditation or advanced technology readiness levels. This is also an ideal opportunity for industry partners to learn about NATO, FMN standards and how to make their capability interoperable from the start. This year’s sandbox will host four NATO DIANA initiatives demonstrating enterprise-level automated cybersecurity and zero trust; remote network segmentation to defeat cyber-attacks; decentralized data exchange to support MDO; and a digitized transit documentation process.
What role does NCIA play in the planning and execution of CWIX events?
CWIX may be led by HQ SACT and hosted by JFTC, but it is underpinned by the systems, technology and expertise provided by NCIA. NCIA’s participation is difficult to quantify but falls into two broad areas. Firstly, NCIA provides a suite of fielded C2 systems and services requested by nations to ensure that, as they are being built, national systems and technologies integrate standards to provide seamless interoperability between the NATO Force Structure and the NATO Command Structure. Secondly, NATO common-funded systems also go through a programme of development as technology updates and new versions of existing standards are agreed. NCIA is crucial for this and, along with partners in ACT and Allied Command Operations (ACO), works continually to ensure that common-funded technology remains at the cutting edge. The continual refresh of capabilities by both nations and NATO often results in multiple instances of systems being tested year after year,
highlighting the simple truth that interoperability is a journey. It must be tested and improved progressively to ensure that, as technology and standards evolve, our ability to exchange information at the speed of relevance is never compromised.
How will CWIX25 enhance NATO’s ability to conduct MDO?
While CWIX is not an MDO exercise, it has an important role in supporting cross-domain activities by testing and enabling the exchange of operational information across all five operational domains. CWIX is organized into Focus Areas that align with communities of interest and the five operational domains. The five operational domain focus areas (maritime, land, air, space and cyber) are led, or supported by, operators from within the NATO Command Structure. ACO and Supreme Headquarters Allied Powers Europe (SHAPE), in particular, have prominent roles leading the MultiDomain Command and Control (MD C2) Focus Area, which connects and integrates the five operational domains to develop a single ‘Top-Cop’ based on the NATO Common Operational Picture (COP) and national strategic COP systems. Achievements from CWIX24 included the provision of Target Engagement and Firing Platform data to a COP, with the addition of data from the emerging NATO Core Data Framework (NCDF) Data Lake, and the provision of data across security domains and between national and NATO networks. The MD C2 Focus Area also leads a joint vignette, which simulates a sequence of operational activities that enable testers to place their own technical test activities into the broader context of real-world operations.

Dr Pietro Paglierani , Senior Scientist at the NATO Centre for Maritime Research and Experimentation (CMRE) assesses the current state of quantum sensing capabilities and their possible maritime domain situational awareness use cases
The race for quantum advantage is no longer confined to theoretical physics labs or science fiction; it is playing out in real time on — and beneath — the global stage. In the maritime domain, the potential of Quantum Technologies (QT) to transform navigation, communication and situational awareness is profound. At NATO’s Centre for Maritime Research and Experimentation (CMRE) in La Spezia, Italy, a new frontier is being explored — where photons replace cables, quantum states replace classical algorithms and the ocean becomes not just a theatre of operations, but a laboratory for some of the most advanced sensing technologies in development today.
CMRE’s quantum research programme is a direct response to NATO’s 2030 Initiative, which aims to preserve the Alliance’s technological edge in the face of rapid innovation. As emerging and disruptive technologies reshape global security, QT offers a strategic opportunity and potential threat. An adversary’s breakthrough in quantum sensing, communication or computation could compromise NATO’s technological advantage, making it imperative to lead in this domain.
To meet this challenge, CMRE established a structured and high-impact Programme of Work (PoW) in Quantum Technologies in 2019. This effort is grounded in a dedicated CMRE Quantum Strategy, further refined through collaborative workshops, including the NATO Science & Technology Organization’s (STO) 2023 Quantum Technologies Workshop in Turin, Italy. These gatherings brought together scientists, defence professionals and policymakers to assess quantum challenges and sketch out a coordinated path forward.
The CMRE QT PoW is built around three interwoven research streams: Quantum Communications and Optics, Quantum Computing for maritime and underwater applications, and Quantum Positioning, Navigation and Timing (QPNT). Each stream addresses core defence needs, while remaining closely integrated to ensure holistic, operationally relevant solutions.
The ocean environment presents unique challenges to secure communication. As quantum computers edge closer to reality, the cryptographic foundations of today’s digital infrastructure face increasing vulnerability. Underwater communications are particularly exposed, where bandwidth, energy and hardware constraints limit the application of classical cryptographic defences.
One promising solution is Underwater Quantum Key Distribution (UQKD), a field in which CMRE has been
conducting experimental and theoretical research since 2019. UQKD enables the exchange of cryptographic keys via individual photons, exploiting quantum properties that make the system inherently secure against eavesdropping. Unlike Post-Quantum Cryptography (PQC), which relies on complex algorithms and heavy processing, UQKD can be implemented on custom-designed, low-power hardware — ideal for constrained maritime environments.
CMRE’s Quantum Lab is focused on building practical, field-ready UQKD systems that can operate at speed and depth. Developing such a system requires not only precision engineering, but also a deep understanding of how light behaves underwater. To that end, CMRE is investigating the effects of scattering, absorption and turbulence on photon transmission, combining classical and quantum optics research to lay the scientific groundwork for operational capability.
Though still in its early stages, UQKD is advancing quickly. Terrestrial quantum communication systems are moving toward commercial deployment, and CMRE is ensuring that similar breakthroughs will soon be possible in underwater contexts, helping NATO stay ahead in the security of subsea infrastructure and missions.
NAVIGATING WITHOUT GPS: A REVOLUTION Of all quantum-enabled technologies, Quantum Positioning, Navigation, and Timing (QPNT) may be closest to practical deployment. As reliance on satellite navigation grows, so too does the vulnerability of systems that depend on it. In environments where GPS signals are unavailable or compromised — such as deep underwater or in contested zones — QPNT offers a powerful alternative.
CMRE initiated its QPNT research in 2022 and has since made it a focal point of the Quantum Lab. These efforts include the use of Quantum Magnetometers, which detect subtle variations in Earth’s magnetic field to support inertial navigation. In 2024, CMRE participated in the MAG24 sea trial and led the QUESTOR24 mission aboard the Coastal Research Vessel Leonardo, conducting at-sea testing of these cutting-edge sensors.
The promise of QPNT lies in its capacity to enable long-duration, signal-independent navigation. In the next five to 10 years, it is expected that quantum sensors will enable submarines, autonomous vehicles and manned platforms to navigate accurately without recourse to external signals — a capability of immense strategic value. CMRE is uniquely positioned to contribute to this emerging field thanks to its operational assets, maritime expertise and commitment to real-world experimentation.

Quantum Computing is often regarded as the most transformative — and elusive — of all quantum technologies. Its potential to solve problems deemed intractable for classical machines could reshape areas ranging from cryptography to materials science. While many of its applications remain hypothetical, CMRE has taken proactive steps to explore its relevance to the maritime domain.
In 2024, the centre launched a dedicated initiative to develop Quantum Computing expertise tailored to underwater and naval scenarios. The initial focus lies in navigation, where quantum algorithms — particularly Quantum Physically Informed Neural Networks — are being investigated for their ability to improve models of motion, fluid dynamics and environmental prediction.
Although the timeline for deployable quantum computers remains uncertain, early experimentation is essential to ensure that NATO is ready to exploit their capabilities as they mature. CMRE’s efforts are building foundational knowledge, nurturing skills and identifying key maritime applications where quantum computing could provide a decisive edge.
As NATO faces increasingly complex threats across multiple domains, Quantum Technologies represent both a strategic imperative and a remarkable opportunity. CMRE’s research, rooted in operational relevance and rigorous scientific methodology, is helping to turn promise into practice. Whether enabling secure underwater communication, resilient navigation or advanced computation, the centre’s quantum work ensures the Alliance is not only reactive, but proactively shaping its future capabilities.
The seas have always demanded innovation — from ancient navigation by stars to sonar and satellite. Today, with quantum technologies on the horizon, CMRE is helping to chart NATO’s course into this next great era of maritime technology. The quantum tide is rising, and the Alliance is ready to ride the wave.

NITECH technology reporter, Eve Michell, asks Michael McLaughlin, the Head of Cyber Security and Data Privacy at the American law firm of Buchanan Ingersoll & Rooney PC, what a ransomware attack looks like and what to do if the worst happens
What is a ransomware attack and what’s unique about them?
A ransomware attack is where a malicious cyber actor compromises an organization’s network, encrypts data and demands a financial payment — a ransom — for their release. Ransomware actually refers to the form of malware that encrypts data and then restricts access to it, which is different from pure extortion. It’s essentially holding an individual’s or an organization’s data or network hostage until they pay up.
How has ransomware evolved over the decades?
The first documented instance of a ransomware incident takes us all the way back to 1989, and it came from an AIDS researcher called Joseph L. Popp. He sent out around 20,000 floppy disks that, after 90 uses, executed a malware programme onto the host computer, which scrambled its files. The victims had to send a small ransom to Cyborg Corporation — less than $200 — by snail mail to a PO box in Panama to unscramble them. Popp was eventually arrested but became something of a trendsetter.
Fast forward to the inception of Bitcoin. This is where ransomware really started to take off. Now criminals had a way to take anonymized or pseudonymized payments. In the early days, ransomware usually targeted individuals for small amounts, but eventually, attackers realized that they could target businesses and demand significantly more money.
Next came the ransomware-as-a-service model (RaaS). RaaS is an affiliate-based model where different individuals or entities specialize in different aspects of attacks. They even have email help desks that coach victims through paying their ransoms. These models have made it much easier for bad actors to launch successful attacks at scale.
How does an organization know that its digital infrastructure has been breached, and what happens after the initial contact with the attackers? In most cases, the victim will get a ransom note on their computer that tells them that they have been breached and that their data has been encrypted. The ransom note usually has a dark web link that will lead the victim towards a method of paying the ransom.
This link could be to a Tox chat, which is an anonymized and encrypted communication mechanism through the dark web. Alternatively, the hackers might even host their chat on their dark website and give you the link. The link is personalized, making clear to the threat actor which victim they are communicating with. Another common communication method uses ProtonMail, an anonymized, encrypted email server based in Switzerland. These examples are the main channels used to negotiate with criminal actors.
How do you negotiate with ransomware actors? Each negotiation is different, and because it is performed through incognito means, it is key to remember that criminals are on the other side. Ransomware groups operate much like a business. These groups have reputations to protect, so they generally will restore data if paid a ransom. They are incentivized to follow through on their word because if people find out that they have taken the money without restoring the data, then future victims might not pay.
Even when a victim refuses to pay the ransom, the ransomware groups still derive some benefit — they get the victim’s name and their data as a trophy to put on their wall. In many cases, it is better to negotiate than to refuse to pay the ransom because of the consequences of a data leak. In some cases, we have negotiated ransoms that started at $8 million down to just a tenth of that, by knowing when to use different pressure tactics.
What types of datasets are the most vulnerable to attack?
Health information is always very sensitive, primarily because the loss of health data can lead to significant reputational damage for an organization entrusted with protecting it. This kind of data is regulated strictly, such as under the GDPR in Europe and HIPAA in the United States. The implications of a medical data breach involve notifying the authorities, facing enforcement action and the spectre of class-action liability.
Another type of data attractive to threat actors is pharmaceutical trade secrets, such as the compounds that a company is developing and hoping to bring to the market. If that data gets compromised, it could potentially be worth billions of dollars. In those situations, paying the ransom can be a lot cheaper than losing potential revenue.
What’s the best way to react if a ransomware attack hits your organization?
It is crucial to call your cyber security attorney immediately. If you do not have an attorney that specializes in cyber security, you should find one straight away. There are so many legal implications that come from a cyber security breach, including collecting forensic evidence, the need to notify customers and contractual obligations that may arise.
If you do not have a cyber security attorney, call your insurance company, especially if you have cyber insurance. They will have vendors with pre-approved rates and will direct you to organizations that can help you with negotiation, restoration and forensics. You need to act quickly to get the best outcomes — within 24 or 48 hours, if possible.

“Ransomware groups operate much like a business. These groups have reputations to protect, so they generally will restore data if paid a ransom”
How do you work with organizations to help them recover from a ransomware attack?
I work from the ‘left of the boom’: before an incident occurs, through to the incident response itself and on all the litigation that follows. On the pre-breach side, we write plans for incident response, business continuity and disaster recovery, all the policies and procedures a company would need if they were going through a Systems and Organizations Control audit 2 (SOC 2), for instance. We also undertake tabletop exercises that are four- to six-hour simulations of incident response procedures to train organizations on how to respond if an incident arises.
In incident response, there are forensics teams that get into the network and do the investigation, restoration vendors that contain the incident and e-discovery vendors that handle data mining to determine which data has been accessed. Our role is to coordinate all of those efforts and to handle the hostile negotiations.
ISSUE 13 | JUNE 2025
Editors
Lara Vincent-Young and Simon Michell
Project Manager
Andrew Howard
Editorial Director
Emily Eastman
Art Direction
Errol Konat
Layout
Billy Odell
Contributing Photographers
Marcos Fernandez Marin, Conrad Dijkstra, Francesc Nogueras Sancho
Printed by Micropress Printers Ltd
Published by
Chantry House, Suite 10a High Street, Billericay, Essex CM12 9BQ
United Kingdom
Tel: +44 (0) 1277 655100
On behalf of
NATO Communications and Information Agency (NCIA)
Oude Waalsdorperweg 61, 2597 AK The Hague, Netherlands
© 2025. The views and opinions, expressed by independent (non-NATO) authors, contributors and commentators in this publication, are provided in their personal capacities and are their sole responsibility. Publication thereof, does not imply that they represent the views or opinions of NCIA, NATO or Global Media Partners (GMP) and must neither be regarded as constituting advice on any matter whatsoever, nor be interpreted as such. References in this publication to any company or organization, as well as their products and services, do not constitute or imply any direct or indirect endorsement, recommendation or preference by NCIA, NATO or GMP. Furthermore, the reproduction of advertisements in this publication does not in any way imply endorsement by NCIA, NATO or GMP of products or services referred to therein.

NATO Edge 26 is on the horizon
Don’t miss the reveal.
Scan the QR code, more details coming soon!
