




Out-of-band monitoring and security IT and OT network tools include technologies such as:
◼ Network Analyzers (e.g., Wireshark)
◼ Application Performance Monitoring (APM)
◼ Security & Information Event Manager (SIEM)
◼ Deep Packet Inspection (DPI)
◼ Lawful Intercept
◼ Intrusion Detection System (IDS)
◼ Network Detection and Response (NDR)
◼ OT security sensor
These tools are installed outside of the active, production network and need to receive passive, out-of-band data to optimize or secure the network as promised. Out-of band tools need to receive traffic indirectly from the network, as opposed to receiving direct traffic flows. Indirect traffic is delivered to out-of-band tools via copies of the live network traffic. Without copies of traffic, out-of-band tools cannot function and are not effective. Out-of-band tools require 100% network visibility to monitor and protect successfully. This 100% visibility is only possible by receiving 100% of the network packets that traverse the network links or segments the out-ofband tools are connected to.
There are a handful of ways to send copies of network packets to out-of-band tools:
1. SPAN Mirroring Port
2. Network TAP (hardware)
3. Encapsulation
4. Virtual TAP
5. Aggregator or Network Packet Broker
This Best Practice Guide is focused on connecting out-of-band tools via SPAN Mirroring Ports.
There are several best practices to keep in mind when connecting an out-of-band tool to a SPAN mirroring port to gain access to network packets.
#1 Protect the SPAN Port
Example A: (1) SPAN Mirror Port and (1) out-of-band tool
Example B: (2) SPAN Mirror Ports and (1) out-of-band tool
#2 Aggregate Multiple SPAN Ports
Example C: (8) SPAN Mirror Ports to one (1) out-of-band tool
Example D: (9) SPAN Mirror Ports to one (1) out-of-band tool
Example E: (10) plus SPAN Mirror Ports to two (2) out-of-band tools
Example F: SPAN traffic up to 100G with specific packets required
#3 Remote SPAN Links Are Not Out of Reach
Example G: Remote site with SPAN Links connected to one (1) out-of-band tool at main site
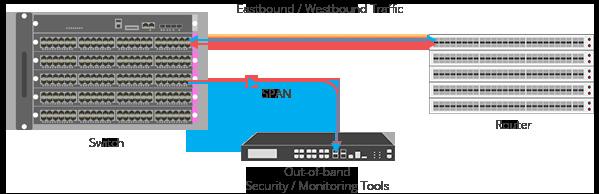
Before we beginning to dive into Best Practices, let’s define SPAN Mirroring. For starters, SPAN is an abbreviation for “Switch Port Analyzer.” It’s also sometimes referred to as port mirroring. For the sake of formal definition, SPAN is the use of a specialized port on a network switch to mirror network packets for analysis.
The SPAN port was originally created by Cisco with their Catalyst series of switches in the mid 90s. It was a quality assurance test point that provided some network visibility for the primary purpose of troubleshooting.
There are several best practices to keep in mind when connecting an out-of-band tool to a SPAN mirroring port to gain access to network packets.
There are situations where the use of a SPAN Mirror Port on a Switch is needed to connect an out-of-band tool or sensor to the IT or OT network. In this instance, it is a best practice to use a Hardware Data Diode between the SPAN Mirror Port and the out-of-band tool or sensor. The Hardware Data Diode will pass copies of network traffic from the SPAN Mirror Port to the out-of-band tool or sensor and, most importantly, eliminate bidirectional traffic flow so no data is passed back into the Switch Mirror port from the tool or sensor. Hardware Data Diodes isolate the production network if the tool or sensor is ever compromised. Hardware Data Diodes are useful and cost-effective solutions to help provide an additional layer of security in IT and OT networks relying on SPAN mirror ports for network access.
Problem: An out-of-band security tool (NDR) has a single input port and needs to connect to the network via a single SPAN Mirror Port. There is a concern about packet injection back into the network from the out-of-band tool.
The TAP to ToolTM Solution: A portable Hardware Data Diode installed between the SPAN Mirror Port and the out-of-band tool ensures the tool receives the copies of traffic it requires to perform as intended and ensures the tool cannot send traffic back into the network. The Hardware Data Diode enforces one-way data flow for SPAN links with physical hardware separation inside the device.

In this scenario, the Hardware Data Diode is accepting an input from one (1) SPAN Mirror Port and sending copies of packets from that Switch to the NDR.
◼ SPAN from Switch 1 input into Port A of Hardware Data Diode
◼ Port C of Hardware Data Diode is connected to the NDR
◼ Hardware Data Diode copies Switch traffic
◼ Hardware Data Diode sends copies to the NDR
Hardware Data Diode has physical separation between A & C and A & D, therefore traffic cannot flow from the NDR to the Switch.
Problem: An out-of-band tool (IDS) has a single input port and needs to connect to the network and receive traffic from two (2) SPAN Mirror Ports. There is a concern about packet injection back into the network from the out-of-band tool.
The TAP to ToolTM Solution: A portable Hardware Data Diode installed between the SPAN Mirror Port and the out-of-band tool ensures the tool receives the copies of traffic it requires to perform as intended. A Hardware Data Diode that can aggregate copies of traffic is needed to send two (2) inputs to the IDS with only one (1) open port to receive the copies of traffic. Also, the Hardware Data Diode ensures the tool cannot send traffic back into the network. The Hardware Data Diode enforces one-way data flow for SPAN links with physical hardware separation inside the device.
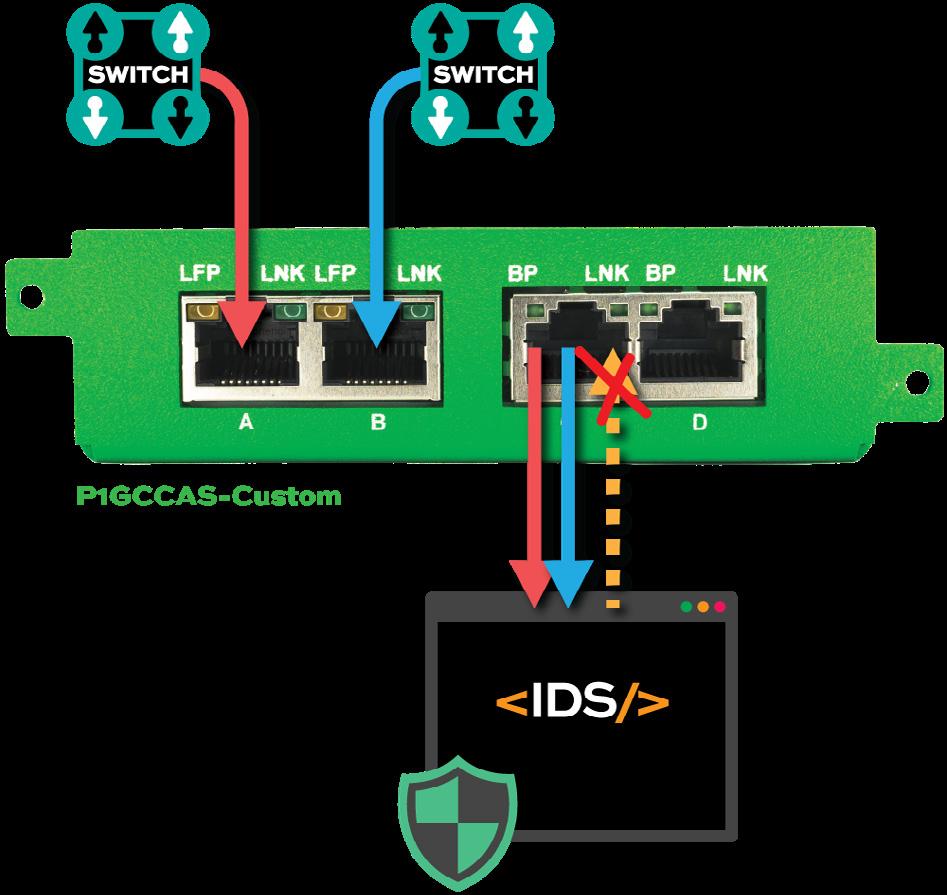
In this scenario, the Hardware Data Diode is accepting an input from two (2) SPAN Mirror Ports and sending copies of packets from those Switches - aggregated together - to the IDS.
◼ SPAN from Switch 1 input into Port A of Hardware Data Diode
◼ SPAN from Switch 2 input into Port B of Hardware Data Diode
◼ Port C of Hardware Data Diode is connected to the IDS
◼ Hardware Data Diode copies Switch traffic and aggregates the copies together
◼ Hardware Data Diode sends aggregated copies to the IDS out Port C
Hardware Data Diode has physical separation between A & C and A & D, therefore traffic cannot flow from the IDS to either Switch.
There are situations where the number of SPAN links is greater than the quantity of input ports on an out-ofband tool. Example B highlights the benefit of aggregating or consolidating multiple links down to a smaller, manageable number of ports. But what if there are more than just two (2) SPAN links, say 8 or 20? In this instance, it is a best practice to use a SPAN Aggregator or Network Packet Broker. These solutions are engineered to aggregate multiple SPAN inputs to one (1) or more out-of-band tools. Aggregation helps network engineer see more of the network without needing to invest in multiple units of the same out-of-band tool.
Problem: An out-of-band OT security sensor has a single input port and needs to connect to the network and receive traffic from eight (8) SPAN Mirror Ports. There is a concern about packet injection back into the network from the out-of-band sensor.
The TAP to ToolTM Solution: A 1U Half-Rack SPAN Aggregator installed between the SPAN Mirror Ports and the out-of-band sensor ensures the sensor receives the copies of traffic it requires to protect as intended. With its data diode design, the Aggregator makes it physically impossible to send packets back into the network via the monitoring ports of the Aggregator - preventing hackers from interrupting critical systems. The SPAN Aggregator can aggregate copies of traffic from up to eight (8) SPAN Mirror Ports and send to an out-of-band sensor with a single input port.
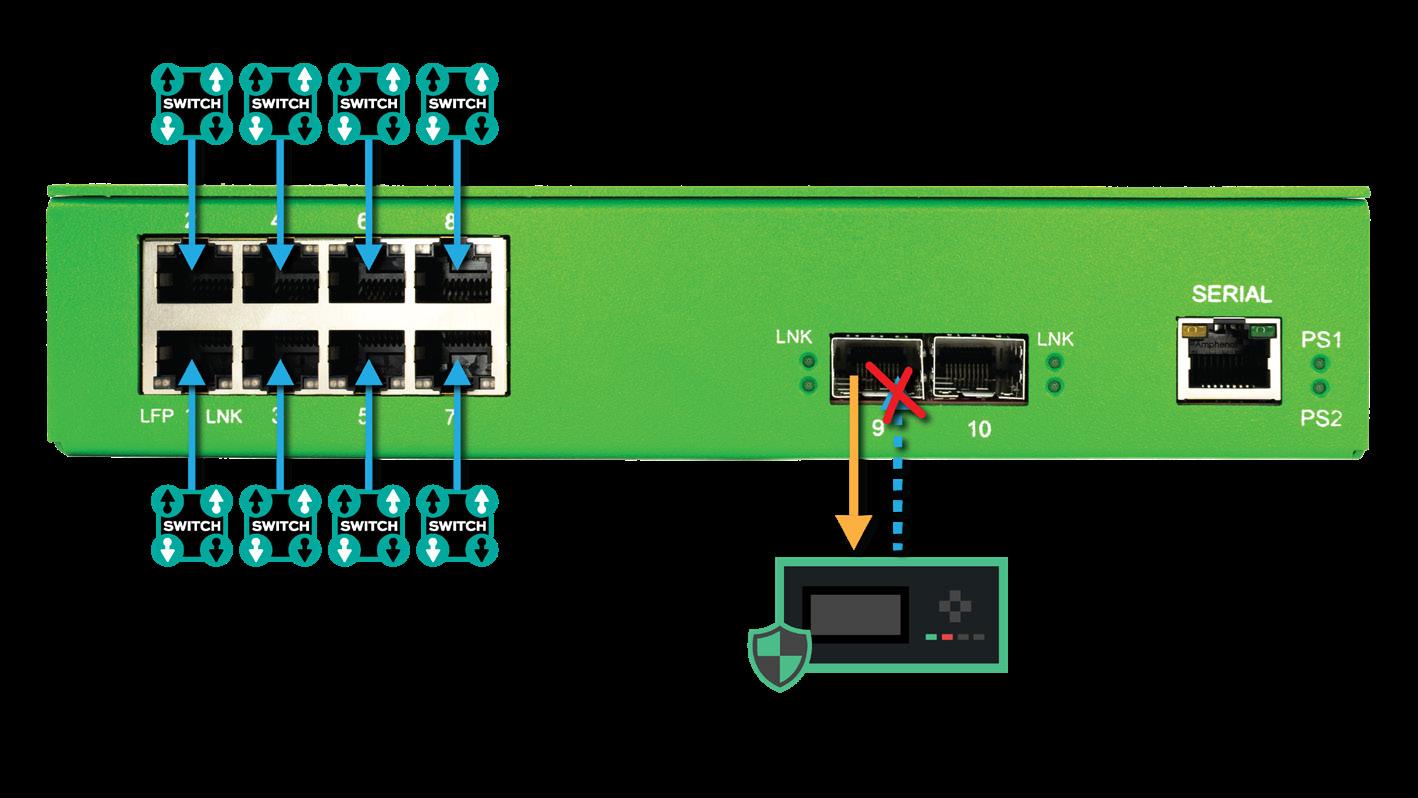
In this scenario, the SPAN Aggregator is accepting inputs from eight (8) SPAN Mirror Ports and sending copies of packets from those Switches - aggregated together - to the OT security sensor.
◼ SPAN inputs from the eight (8) Switches are plugged into Ports 1 - 8 on the SPAN Aggregator
◼ Port 9 of SPAN Aggregator is connected to the security sensor
◼ SPAN Aggregator copies Switch traffic and aggregates the copies together
◼ SPAN Aggregator sends aggregated copies to the security sensor out Port 9 Ports 1 through 8 on the SPAN Aggregator do not transmit packets to the network elements linked to them. Ports 1 through 8 are sending packets to both Ports 9 and 10, and Ports 1 through 8 are not paired.
This ensures the SPAN Aggregator enforces one-way data flow.
Problem: An out-of-band monitoring tool (APM) has a single input port and needs to connect to the network and receive traffic from nine (9) SPAN Mirror Ports.
The TAP to ToolTM Solution: A 1U Half-Rack 10-port Network Packet Broker (NPB) installed between the SPAN Mirror Ports and the monitoring tool ensures the APM receives the copies of traffic it requires to perform as intended. The the 10-port NPB can aggregate copies of traffic from up to nine (9) SPAN Mirror Ports and send to an out-of-band APM with a single input port.

In this scenario, the 10-port NPB is accepting inputs from nine (9) SPAN Mirror Ports and sending copies of packets from those Switches - aggregated together - to the APM.
◼ SPAN inputs from the nine (9) Switches are plugged into Ports 3 - 11 on the 10-port NPB
◼ Port 12 of 10-port NPB is connected to the APM
◼ 10-port NPB copies Switch traffic and aggregates the copies together
◼ 10-port NPB sends aggregated copies to the security sensor out Port 12
Problem: Two (2) out-of-band security tools - IDS and NDR - need to connect to the network and receive traffic from fifteen (15) SPAN Mirror Ports of different network speeds. Both the IDS and NDR each have one (1) available input port to receive the copies of network traffic.
The TAP to ToolTM Solution: A 1U Network Packet Broker (NPB) without Passive TAPs is installed between the SPAN Mirror Ports and the two (2) out-of-band tools ensuring an architecture that is reliable and not over-subscribed.

In this scenario, a 1U NPB without Passive TAPs accepts inputs from multiple Switches of different network speeds (i.e., 1G, 10G, and 40G). This NPB is useful because it allows for use of out-of-band tools of varying speeds.
◼ Bringing multiple SPAN ports from 1G to 40G into the NPB
◼ The NPB’s load balancing capabilities can load balance the traffic to 1G out-of-band tools
◼ The NPB is also capable of filtering the needed or unneeded packets before sending to out-of-band tools because monitoring and security tools may not need to receive every packet on the network - due to bandwidth or type of network traffic
◼ Also, the NPB can aggregate traffic and send the aggregated copies to 40G out-of-band tools
◼ The enhanced functionality of a NPB reduces the process burden on connected tools with unneeded data and provides optimized tapped traffic for multiple tools
Problem: Multiple out-of-band tools have different network traffic requirements and media type incompatibilities exist in the architecture.
The TAP to ToolTM Solution: An Advanced Features Network Packet Broker is engineered with augmented capabilities to enhance the benefits of connected out-of-band tools. A 1U Advanced Features NPB is installed between Switches and the out-of-band tools.
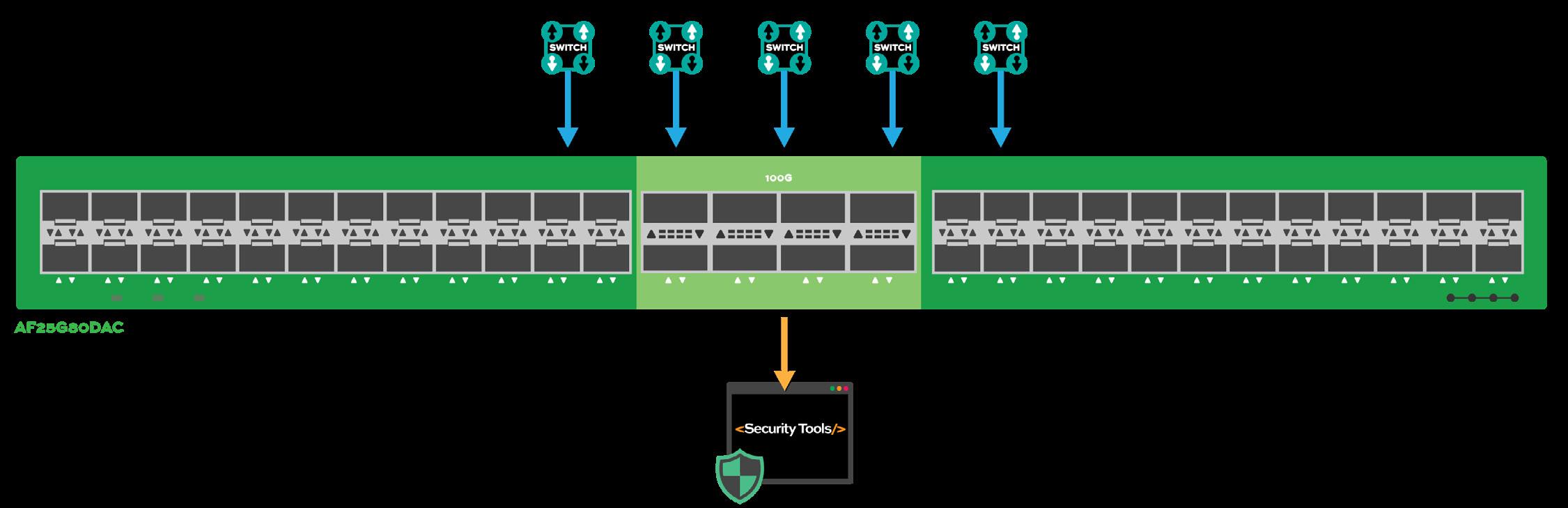
In this scenario, a 1U Advanced Features NPB accepts inputs from multiple Switches of different network speeds (i.e., 1G to 100G) and can groom the copies of traffic send to out-of-band tools based on specific requirements. An Advanced Features NPB can do the following:
◼ Aggregation
◼ Load Balancing
◼ Filtering
◼ Deduplication
◼ Packet Slicing
◼ Time Stamping
◼ Encapsulation / Decapsulation
These functionalities are powerful allies in a network with multiple out-of-band tools of varying speeds, ages, and bandwidths. Some out-of-band tools are unable to remove duplicate packets.v Additionally, an Advanced Features NPB can even perform media conversion when the network and out-of-band tools are incompatible.
There are situations where remote sites need to be connected to a main site - like a data center - because the main site houses the out-of-band security or monitoring tools. Network tunneling is commonly used to connect remote sites to a main site. Layer 2 GRE is a way to send remote SPAN links to another device in a separate location. Layer 2 GRE is a form of network tunneling that takes SPAN inputs or TAP monitoring ports and transports the copies via GRE tunneling to the out-of-band tools that have IP addresses or to a Garland Technology Packet Broker. By using a Network Packet Broker with tunneling capabilities, SPAN traffic can be sent from remote sites to out-of-band solutions located elsewhere easily.
Problem: An out-of-band tool (NDR) located at a main site has a single input port and needs to connect to the network and receive traffic from nine (9) SPAN links at a remote location.
The TAP to ToolTM Solution: A 1U Half-Rack 10-port Network Packet Broker (NPB) installed at the remote location to connect to the Switch traffic. The 10-port NPB can be configured for Layer 2 GRE, sending copies of the nine (9) SPAN links to the NDR set-up at the main site.

In this scenario, two (2) 10-port NPBs are used: one (1) at the remote site and one (1) at the main site. The remote site NPB is accepting inputs from nine (9) SPAN Mirror Ports and sending copies of packets from those Switches - aggregated together and encapsulated and sent to the main site NPB, which decapsulates the traffic before sending to the NDR.
◼ SPAN inputs from the nine (9) Switches are plugged into Ports 3 - 11 on the 10-port NPB at the remote site
◼ Port 12 of 10-port NPB is connected to the network
◼ 10-port NPB copies Switch traffic and aggregates the copies together
◼ 10-port NPB sends aggregated copies to the 10-port NPB at the main site over the network via Layer 2 GRE
◼ The network is connected to Port 3 on the 10-port NPB at the main site to receive the Layer 2 GRE encapsulated traffic
◼ The 10-port NPB decapsulates the traffic
◼ The NDR is connected to the 10-port NPB via port 4
◼ The 10-port NPB sends copies of aggregated traffic from the remote site to the NDR
Many out-of-band tool can, and do, successfully use SPAN as an access point to the network. These monitoring products are looking for low bandwidth application layer events like conversation or connection analysis, application flows, and applications where real time and knowing real delta times are not important. These monitoring requirements utilize a small amount of bandwidth and grooming does not affect the quality of the reports and statistics. The reason for their success is that they keep within the parameters and capability of the SPAN ports, and they do not need every frame for their successful reporting and analysis. In other words, SPAN port is a usable technology if used correctly and the companies that use mirroring or SPAN are using it in a well-managed and tested methodology.
Garland Technology is in the network visibility game. If you need to connect an out-of-band tool to your network via a SPAN port so you can monitor or protect your network, then do it! Starting now is better than operating blindly.
But, in critical network deployments like OT environments, if using SPAN is the only option to connect security sensors then additional security measures should be taken.
As this Best Practices Guide has shown, Hardware Data Diodes, Network TAPs, and Network Packet Brokers can enhance SPAN deployments.
◼ Garland Technology can connect SPAN inputs to out-of-band tools from 10M to 100G in any type of media environment.
◼ Garland Technology’s hardware solutions can protect SPAN ports and prevent packet injection back into the network from the out-of-band tool.
◼ Reducing the quantity of out-of-band tools needed to protect the network (and saving limited budget dollars!) is possible with Garland Technology’s aggregation solutions.
◼ Even remote SPAN connections to out-of-band tools are possible with Garland Technology’s portfolio.
Looking to connect an out-of-band tool to your network via a SPAN Mirror Port, but not sure where to start? Join us for a brief network Design-IT consultation or demo. No obligation - it’s what we love to do.
