




Conference
June 7-9, 2023








Scott entered law enforcement in 1999, initially as an Auxiliary Constable with the RCMP in BC followed by becoming a full-time constable shortly after. Scott completed his law enforcement career in 2008 with a municipal police department in Alberta. Scott made the jump to Corporate Security & Emergency Management in the Oil & Gas Industry and spent the majority of the past 14 years with PetroChina Canada
With PetroChina Canada, Scott was tasked with leading security operations (physical, personnel, EP) and intelligence for the company’s oil & gas assets. As an Incident Command System (ICS) instructor, Scott also oversaw incident management and ICS training for his company as well as numerous global affiliates. Scott’s work with PetroChina has taken him around the globe assisting the organization with developing security and emergency management programs.
In May of 2022, Scott accepted a role as the Director of Security for a Family Office in Northern California In that role Scott leads a talented team of Executive Security Agents, SOC Operators & Security Systems Specialists
Scott has recently completed many years of volunteer leadership with ASIS International having just completed two years of service on the ASIS Global Board of Directors and before that, three years on the Executive Board of the ASIS CSO Center.




























Executive Security Operations Conference
June 7-9, 2023


Research Electronics International R.E.I.







Chris is a proven and highly-trained Law Enforcement executive. He has operated in every aspect of modern policing, to include: large scale narcotics investigations, Homeland Security, white-collar crime, public corruption, voter and election fraud, violent crime, jail management and community oriented policing.
Chris is a graduate of the FBI National Academy, held the positions of Police Chief and Chief of Investigations for the Alabama Attorney General’s Office. After 20 years in Law Enforcement, Chris started a Private Investigative agency which included TSCM services for individuals and corporations in the southeast. Research Electronics International’s equipment and training were widely used in this capacity.


















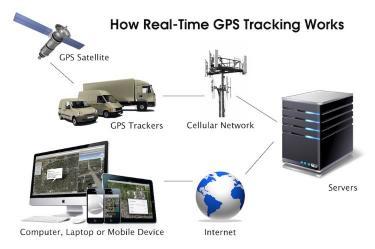




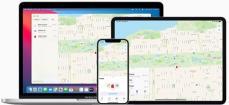



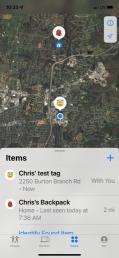
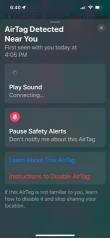
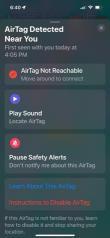
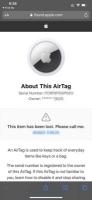
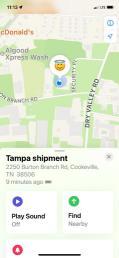
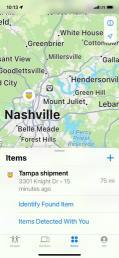
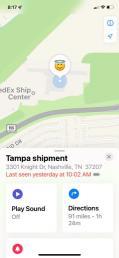
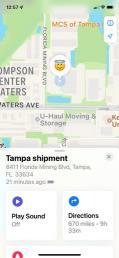
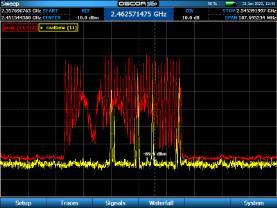
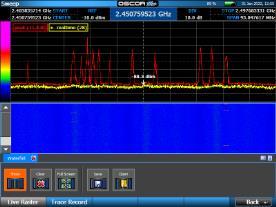
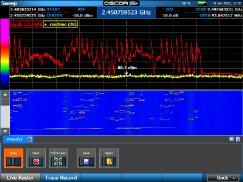
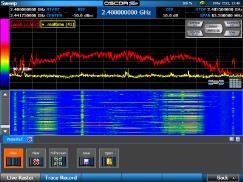
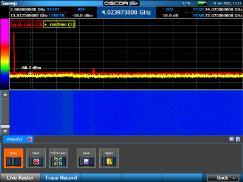
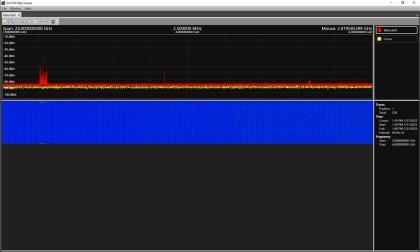
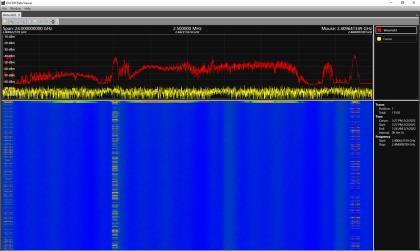
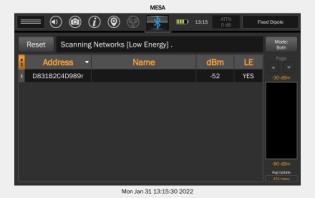
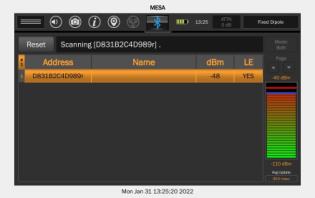
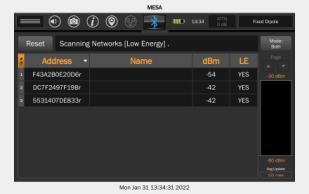
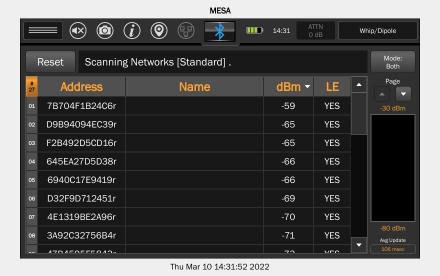
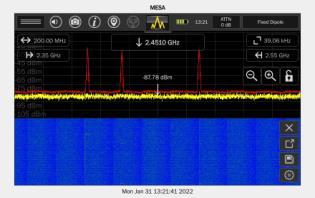
Utilizes 3 different antennas/frequency bands 1. Bluetooth Low-Energy – 2.400 GHz to 2.4835 GHz. Utilized for reporting itself to nearby iPhones

2. Near-Field Communication (NFC) – 13.56 MHz. Utilized when more information about a found AirTag is desired AirTag is held close to iPhone
3. Ultra-Wideband – 6.5 GHz to 8 GHz. Utilized for precision directionfinding of an AirTag via the “Find My” app





1.
2.
3.
4.
5.
6.

7.
































































































Executive Security Operations Conference
June 7-9, 2023


U.S. Secret Service







As a senior advisor with the U.S. Secret Service, Dr. Keeney advises executive management on operational and policy decisions based on an understanding of protective intelligence investigations and psychological, social, and behavioral science.
Dr. Keeney serves as the Secret Service's only psychologist conducting threat assessments and consulting on Secret Service protective intelligence investigations. Also offer guidance on strategic goals for research and training related to the protective intelligence mission of the agency; and conduct training related to threat assessment, mental illness, interviewing techniques, de-escalation, and other topics.
Dr. Keeney also served as the Chief of the National Threat Assessment Center from November 2007 through December 2016, during which time she oversaw the Center's research, training, and consultation activities. SES-certified.



















1. Not affiliated with major corporations/ no EP
a. 2020: Individual murdered Fahim Saleh, CEO of Nigerian motorcycle rideshare start up, in his Manhattan apartment Greed/Jealousy/Financial
b. 2022: Husband murdered Maria Christina Jimenez, CEO of Coral Gables Hospital, in their home Domestic/Interpersonal
c. 2023: Individual murdered Bob Lee, tech executive with various companies, on a street in San Francisco, CA Personal


1. Presence of executive protection and other security measures would have prevented some of these incidents
a. Occurred in vulnerable locations (e g , driveways, inside residences, unsecured offices)
b. No security was present
2. However, would it prevent those with the most intimate access?
a. What vetting/ intelligence occurs within the inner circle?
i. Do we know about their finances personal stressors relationships?
b. Are access and targeting more likely to occur from those closest to the principal?
c. Intimacy effect – The closer the relationship, the more likely the violence, the more likely a threat will be acted upon

1. ONTIC Survey - 2022

a. Executives of U S Companies – over half anticipated missing ¼ or more of threats before harm or damage occurred
2. Knowing this – that we will miss threats before harm occurs – what intelligence would change your operations?
a) Break into manageable steps – using traditional intelligence cycle as a guide
i. Scope the intel
ii. Gather information
iii. Understand how your PI partners analyze the information
iv Identify what to report, to whom, when, and in what manner

1. Narrow the aperture

a. What do you need to know to make decisions and meet your goals?
b. What information might influence your principal’s behavior, change their attitudes toward protection and security?
c. Start small and build out your PI mission, similar to the concentric circles of physical security
2. Prioritize even more – Intel that is:
a. Risk-based – relevant to the threats and vulnerabilities of your principal
b. Proximal
Close in space time and relation
c. Actionable

1. From people and open sources

a. Receptionist, security officers, neighbors, local news station, etc
b. Sometimes close informal sources will give you more actionable intelligence than formal ones
c. Some examples
2. Train folks on what to look for so they can gather information too and understand what they are seeing
a. Are you training your security officers? Are they invested in the company or are they contractors who are not integrated into your mission?
b. QAnon example


1. You and your team will be taking in information and synthesizing it
2. But also, ask questions about how the threat management program/ PI side of the house puts it together
a. Are they following a process recognized by others or is it just one person s way of doing things?
b. Is it transparent, repeatable, and scalable?
c. Are people easily trained in it?

1. Avoid silos in your team and in the organization

2. What do you need to know about immediately?
a. What types of things are unimportant?
b. Matrix this out and have a discussion
3. Do you want a three-bullet brief or an email that you can share with your team?
4. Who is responsible for ensuring information is received and shared, when relevant? Does the PI team know this?


1. High-stakes mission in polarizing climates
2. Imperative to manage emotions
a. Anger can color perceptions, impact decisions, and guide behavior, regardless of whether the decisions at hand are related to the source of anger
b. Example – 2014 Michigan Technological University Study
i. Consistent with other studies ii. Anger impaired situational awareness and driving performance compared with




1
7





June 19-21, 2024









Kevin Koharki MBA, PhD, consults with, provides keynote speeches for, and advises some of the world’s largest firms (e.g., Fortune 100) across various industries such as banking, insurance, distribution, manufacturing, aerospace and defense, law firms, among others He specializes in developing employees’ and Executives’ financial acumen so they understand and can communicate the financial value of their work, optimizing CEOs’capital allocation priorities across their respective organizations
Kevin is a sought-after keynote speaker for firms of all sizes, as well as various trade organizations, such as the American Institute of Aeronautics and Astronautics. He has conducted financial keynote speeches in lieu of firms’ Chief Financial Officers, presenting to Executives and board members. In addition, Kevin has conducted “Investor/Analyst Day” presentations for internal personnel so they understand the key strategies and metrics senior leaders focus on to drive business performance, as well as how external markets participants evaluate and influence firms
Firms seek Kevin out because he is an expert financial analyst who has analyzed hundreds of firms over a 20-year career (including as an M&Aanalyst) In addition, he has taught financial statement analysis at the Executive, Masters, and Undergraduate levels for 15 years at leading universities such as Pennsylvania State University, Washington University in St Louis, and Purdue University, winning numerous awards He earned his B S (Accounting), MBA (Finance), and PhD (Accounting) from the Pennsylvania State University



























































































1















1. All Speaker Bio’s
2. All Presentations
3. All ESOC Sponsor/Partner Information

While supplies last, previous copies of conference guidebooks can be purchased at:
ESOC 2023
https://www.ep-board.org/product-page/esoc-2023conference-presentations-book
ESOC 2024
https://www.bepp-esoc.org/product-page/2024-esocresource-guide

Tickets are on sale now for the 2025 ESOC June 3-5 Disney Properties, Florida
https://www.bepp-esoc.org/esoc-2025
Every ESOC attendee receives this printed and bound invaluable resource