









We are thrilled to have you join us for what promises to be an inspiring, actionpacked and community-driven event It is our privilege to welcome a group of cyber security leaders and enthusiasts who are as passionate about cyber security as we are This years event is all about uniting the cybersecurity and business communities like never before based on our values, that in simple terms are COMMUNITY & CONTENT

With multiple theatres - including ‘Culture & Strategy’, ‘Prevention & Resilience’, ‘OT & Cloud Security’ - as well as our Keynote stage, we have carefully curated an agenda which brings together the leaders in cybersecurity. From companies such as Google, Microsoft, TikTok and the NFLin roles including ‘Lead Threat Intelligence Advisor’, ‘Director of Cyber’ and ‘Head of Strategic Solutions’ - our speakers will cover topical issues and provide innovative solutions for current cyber security challenges
This event is not just about education - it is about connection and community We have designed the show floor to provide ample opportunities for you to network with other passionate experts, converse with our leading speakers and connect with our key exhibitors.
Get ready for an inspiring event full of thrilling speaker sessions and valuable conversations over 2 brilliant days!

*Please note that the details ofthis brochure are subject to change
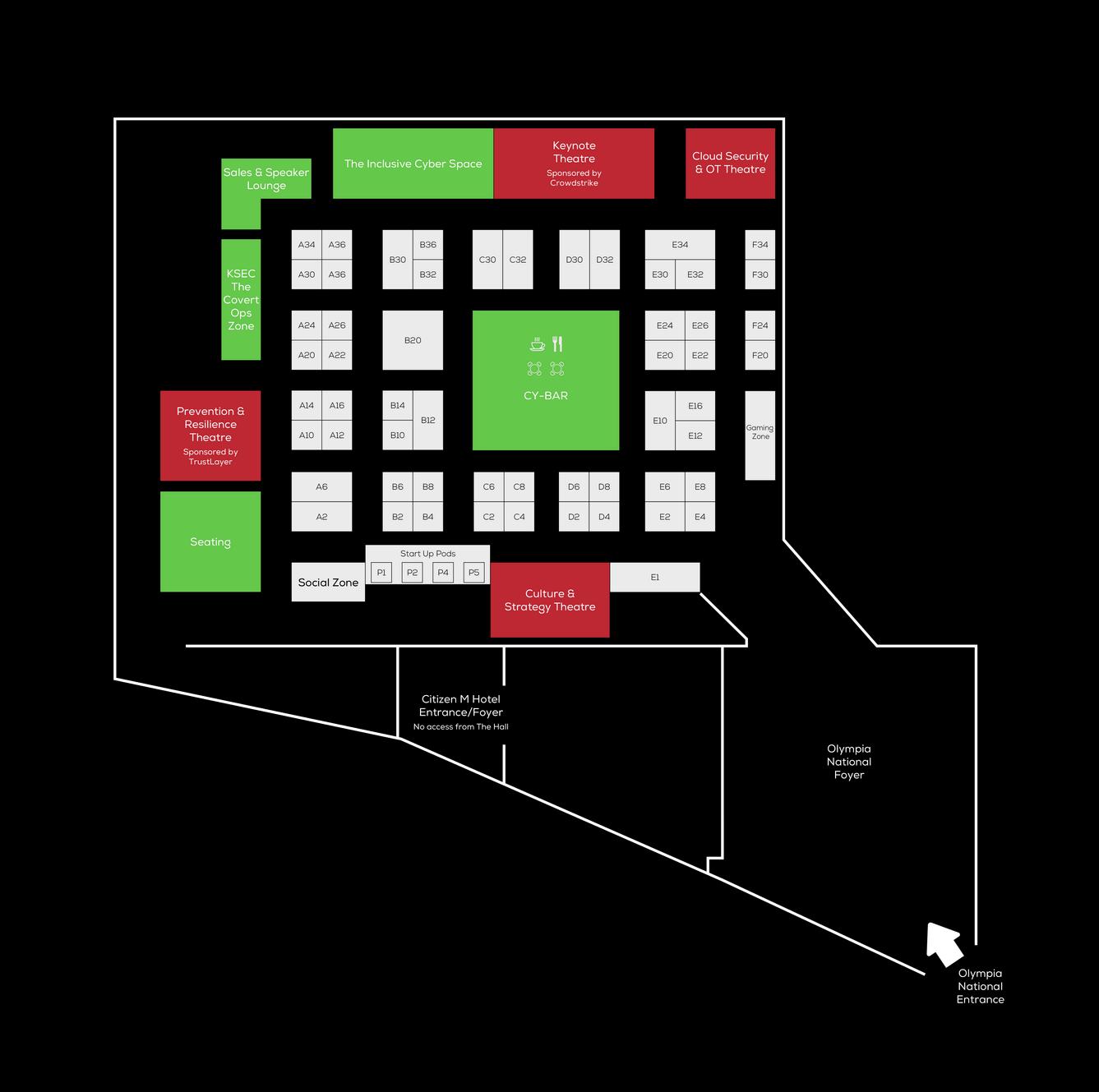


2|SEC Limited - Stand: E4
AppCheck - Stand: E10
BlueVoyant - Stand: C32
Bob's Business - Stand: A12
BullWall - Stand: C6
Claranet - Stand: E32
Cloud Security Alliance - Stand: F34
Cloudflare - Stand: E24
Crowdstrike - Stand: D30
Cyan Digital Security - Stand: P1
Cyber Protection Group - Stand: A36
Cyber Resilience Centre Network-Stand:E1
CyberCX - Stand: B30
Cynet - Stand: A10
DarkInvader - Stand: P5
Defense com - Stand: D6
Edgescan - Stand: E20

Embli Solutions / Akamai - Stand: A14
Exponential-e Group - Stand: B36
HelloFresh - Stand: D4
Hexiosec - Stand: A16
Huntress Labs - Stand: D32
Intruder - Stand: B32
iSTORM - Stand: F20

J2 MSSP - Stand: A24
Keyfactor - Stand: A6
KnowBe4 - Stand: B20
KSEC - Stand: F40, The Covert Ops Zone
Logically - Stand: E6
Lookout - Stand: B12
Mobius Consulting - Stand: P4
MOBSTR - Stand: E22
Netskope - Stand: C8
Orpheus Cyber - Stand: A20
OSINT Industries - Stand: B10
Pentest People - Stand: A26
Pluralsight - Stand: C4
PRPR - Stand: A34
Sentrium Security - Stand: P2
Setyl - Stand: B8
Snare - Stand: A22
Stellar Cyber - Stand: B14
Tech Channel Ambassadors - Stand: E8
techUK - Stand: F10

ThreatLocker - Stand: C30
Tines - Stand: B6
TrustLayer - Stand: D8
Tulpa - Stand: E12
TXOne Networks - Stand: E30
UKC3 - Stand: E16




Watch and learn as our incredible Keynote Speaker line-up, which features the masterminds behind some of the biggest brands, share their expert industry knowledge.


We curated speaker tracks and activities: to foster learning, forge connections, and cultivate a sense of belonging within the cybersecurity community.
Hear from industry leading experts as they provide valuable insights into the challenges the sector is facing and what is pertinent for cyber professionals, whilst giving real world examples.


Attendees can journey through the renowned hacker hardware store, where gadgets and tools are out to empower Red Teamers, from stateof-the-art penetration testing devices to covert ops equipment.
2-Sec Consulting is a leading cybersecurity consultancy, providing expert guidance and innovative solutions to help businesses safeguard their digital assets and strengthen their security posture
Our mission is to empower organisations to anticipate, prevent, and respond to cyber threats with confidence
AppCheck is a Dynamic Application Security Testing (DAST) and network vulnerability testing solution, developed and supported by experienced penetration testers.
We approach security testing as a hacker would, leveraging multiple proprietary crawling engines to analyse target behaviour across both modern and traditional technologies, including Single Page Applications (SPAs), APIs, and complex authentication flows such as SSO, 2FA, and TOTP
BlueVoyant delivers a comprehensive cloudnative security operations platform that provides real-time threat monitoring for networks, endpoints, and supply chains, extending to the clear, deep, and dark web The platform integrates advanced AI technology with expert human insight to offer extensive protection and swift threat mitigation, ensuring enterprise cybersecurity Trusted by more than 1,000 clients globally, and the 2024 Microsoft Worldwide Partner of the Year, BlueVoyant sets the standard for modern cyber defence solutions.
BullWall is the pioneer in ransomware resilience, providing robust defenses against the relentless threat of ransomware Our focus on the latest ransomware tactics uniquely addresses critical gaps left by other security solutions By delivering server-based protection without an endpoint agent, BullWall keeps critical IT infrastructure secure and operational during the core stages of an attack – before, during and after

Bob's Business is the cybersecurity culture company They help every organisation, big or small, to develop and embed a cybersecurity culture that protects their data
Claranet is a global technology services provider with capabilities across cloud, cybersecurity, applications, data and AI, networks and workplace productivity solutions We enable organisations to make modern happen by being big enough to deliver and small enough to care; by offering adaptive, scalable technology solutions; and by being right where our customers need us to be, moving at their pace, in their local region.

Not-for-profit UK chapter of the Cloud Security Alliance, providing context and guidance and supporting events and sponsors in our region
MOBSTR (mobile application security testing and ratings) is a next generation mobile security assessment and ratings SaaS platform that addresses Governance, Risk Management and Compliance (GRC) challenges in mobile apps Cyber Security
Cloudflare, Inc (NYSE: NET) is the leading connectivity cloud company on a mission to help build a better Internet It empowers organizations to make their employees, applications and networks faster and more secure everywhere, while reducing complexity and cost Cloudflare's connectivity cloud delivers the most full-featured, unified platform of cloud-native products and developer tools, so any organization can gain the control they need to work, develop, and accelerate their business
CrowdStrike (Nasdaq: CRWD), a global cybersecurity leader, has redefined modern security with the world's most advanced cloudnative platform for protecting critical areas of enterprise risk endpoints and cloud workloads, identity and data
At cyan, we deliver smart, scalable cybersecurity powered by AI-based threat intelligence Our solutions protect telecoms, finance, insurance, SMBs, and digital service providers - with seamless integration and low complexity
Visit us at Stand P1 to learn how we can protect your business
At Cyber Protection Group, we specialise in safeguarding all of your organisation's digital assets.
With our all-in-one solution, Cyber Protect, you get quick and easy access to all of the cuttingedge technology and expertise you need to keep your business secure.
The CRC’s work with students from the top universities nurturing the brightest and best cyber talent to develop a student talent pipeline The students are mentored and supported to engage with business to deliver affordable cyber security services from Security Awareness Training to Vulnerability Assessments The objectives are to build this talent pipeline and direct this back into policing for the benefit of law enforcement and business so the students will be career ready with strong cyber security skillsets in business and policing

CyberCX is a leading provider of professional cyber security and cloud services across the United Kingdom, United States, Australia and New Zealand. With a workforce of over 1,300 professionals, we are a trusted partner to private and public sector organisations helping our customers confidently manage cyber risk, respond to incidents and build resilience in an increasingly complex and challenging threat environment

Cynet's end-to-end, natively automated All-inOne platform, backed by 24/7 security experts was purpose-built to enable lean IT security teams to achieve comprehensive and effective protection regardless of their resources, team size or skills
DarkInvader helps organisations identify and mitigate external cyber threats by scanning the internet, dark web, and hidden channels for risks like data leaks and shadow IT.
Defense com is transforming the way businesses manage cyber security by allowing them to easily identify, prioritise and remediate threats Our powerful XDR platform with optional managed SIEM offers complete and cost-effective protection
Edgescan offers a continuous security testing and unified exposure management SaaS platform that manages thousands of assets for businesses large and small in a wide variety of industries across the globe.
Consisting of Exponential-e, Vysiion, and Xpertex, along with EXPO e and EXPO e Networks, the Exponential-e Group boasts a unique blend of experience, expertise, and technical capabilities Working closely together, teams from across the Group drive new digital innovations and successfully execute the most challenging projects across numerous sectors, delivering ‘ peace of mind as-a-service’ Our commitment to innovation and customer satisfaction is at the forefront of our endeavours and is reflected in our nine ISO accreditations and industry leading NPS score, updated live on our website
Home Delivery Food Subscription
Huntress is the enterprise-grade, people-powered cybersecurity solution for all businesses, not just the 1% With fully owned technology developed by and for its industry-defining team of security analysts, engineers, and researchers, Huntress elevates underresourced tech teams

Hexiosec is a UK-based cyber security company led by engineers with deep experience in defence, intelligence, and government They provide practical, high-impact cyber security solutions to help organisations reduce risk and operate securely in today's complex digital landscape
Intruder is an exposure management platform for scaling to mid-market businesses Over 3000 companies - across all industries - use Intruder to find critical exposures, respond faster and prevent breaches. Unifying Attack Surface Management, Vulnerability Management and Cloud security into one powerful, easy to use platform, Intruder simplifies the complex task of securing an everexpanding attack surface.
We are an award winning consultancy, specialising in supporting organisations with a range of Privacy, Security and Penetration testing related challenges
Our team of specialist consultants and penetration testers support our clients to help improve their compliance and security standings by providing advice, guidance, training and testing and that focusses on you and your unique challenges
J2 Software has been helping businesses stay secure since 2006 with managed cybersecurity services built off our proven cyber resilience framework. We focus on providing real value, not just ticking boxes. We build resilience. Resilience gives you visibility, visibility gives you the capability to respond

F40, The Covert Ops Zone
Step into the world of ethical hacking and physical security with the KSEC Popup Store, your go-to destination for cutting-edge hacker hardware, lock picking kits, and covert entry tools Explore our interactive space and get hands, on with real gear used by professionals in the field
Keyfactor brings digital trust to the hyperconnected world with identity-first security for every machine and human By simplifying PKI, automating certificate lifecycle management, and securing every device, workload, and thing, Keyfactor helps organizations move fast to establish digital trust at scale – and then maintain it. In a zero-trust world, every machine needs an identity and every identity must be managed.
Visit KnowBe4 to discover how we transform human vulnerability into your greatest security asset
Don't miss our expert speakers on the Culture & Strategy stage!
Pick up some exclusive swag while learning how our Security Awareness Training and simulated phishing platform create a human firewall for your organization
Empower your workforce to make smarter security decisions every day
At Mobius we believe organisations cannot confidently accelerate their digital journey without trust That's why we work with you to develop sustainable data risk resilience into your business systems, by building and implementing practical and relevant solutions that ensure you know your digital landscape and can secure it

Lookout, Inc. is the data-centric cloud security company that uses a defense in-depth strategy to address the different stages of a cybersecurity attack Data is at the core of every organization, and our approach to cybersecurity is designed to protect that data in the modern threat landscape With a focus on people and their behavior, the Lookout Cloud Security Platform ensures realtime threat visibility, and quickly halts breaches from initial phishing attempts to data extraction
Netskope, a leader in modern security and networking, addresses the needs of both security and networking teams by providing optimized access and real-time, context-based security for people, devices, and data anywhere they go.
Thousands of customers, including more than 30 of the Fortune 100, trust the Netskope One platform, its patented Zero Trust Engine, and its powerful NewEdge network to reduce risk and gain full visibility and control over cloud, SaaS, web, and private application activity providing security and accelerating performance without sacrificing either

Orpheus Cyber is committed to providing organisations with the proactive defense and intelligence-led approach necessary to safeguard against evolving cyber threats Recognizing the unique reporting needs of each organisation, we provide different levels of access, offering tailored threat data, analysed reports, or strategic management-level insights Strengthen your security stance with Orpheus today Visit us at E63 to learn more
OSINT Industries (https://osint.industries/) specializes in providing real-time intelligence, focusing on discovering the digital footprint of selectors (phone numbers and email addresses) Unlike conventional intelligence solutions, OSINT Industries does not store personal information or have a database of information
Pentest People is a UK-based leader in Penetration Testing as a Service (PTaaS), offering expert services such as web and mobile application testing, infrastructure assessments, and cloud security reviews, with accreditations such as CREST, ISO270001, NCSC and CHECK Their innovative SecurePortal platform transforms how penetration testing results are managed, providing real-time insights, streamlining remediation, and reducing risk efficiently
Pluralsight empowers organisations to build future-ready technology teams through expertled learning, hands-on experiences, and datadriven insights. As a trusted partner in tech skills development, we support cybersecurity, software development, cloud, and IT operations, ensuring teams have the expertise needed to innovate, collaborate, and drive business success
PRPR is a UK-based public relations and marketing communications agency specialising in the cybersecurity and technology sectors With over 25 years of experience, PRPR offers a comprehensive range of services, including media relations, digital content creation, event management and bespoke communication training PRPR is known for its friendly and flexible approach and combines traditional PR strategies with modern digital tools to help clients stand out and grow their business in competitive markets
Setyl is a cloud-based IT asset management platform, which connects to your existing systems Use Setyl to gain full visibility and control over your hardware assets, software applications, usage and spend in one place helping you to streamline operations, cut costs and prepare for security audits

Sentrium was founded with the belief that cyber security services should be straightforward and tailored to the needs of our clients. We work tirelessly to help businesses address their security challenges and understand how they are at risk from the ever-changing threat landscape
Snare by Prophecy International is a complete Security Data Engine that powers Security Analytics, SIEM and MDR/XDR platforms. Snare is a mature, market ready and proven technology and a trusted supplier to Defence and Military organisations across the globe.
Stellar Cyber's Open XDR platform delivers comprehensive, unified security without complexity, empowering lean security teams of any skill to secure their environments successfully With Stellar Cyber, organizations reduce risk with early and precise identification and remediation of threats while slashing costs, retaining investments in existing tools, and improving analyst productivity The company is based in Silicon Valley For more information, contact https://stellarcyber ai

Tech Channel Ambassadors is a Community Interest Company founded to change the lives of thousands of children by introducing them to the career opportunities in the IT Channel. It supports volunteers (Ambassadors) to visit schools to share this message, with a focus on disadvantaged groups and a goal of increasing diversity in the channel.
techUK is the trade association that brings together people, companies and organisations to realise the positive outcomes that digital technology can achieve
We create a network for innovation and collaboration across business, government and stakeholders to provide a better future for people, society, the economy and the planet
Stop ransomware! ThreatLocker® improves enterprise-level server and endpoint security with zero trust controls, including Allowlisting, Ringfencing™, Elevation, Storage, Network Control, Configuration Management, and Operational Alert solutions.
Tines is the smart, secure workflow builder for your whole team Break down barriers across systems with fewer duplicate efforts, unnecessary alerts, and information silos
Validate your end-to-end defences against realistic threats driven by AI
Tulpa emulates adversaries while operating on real networks and cyber ranges, across the full scope of offensive tradecraft In this way you can not only enumerate where risks may exist, but pinpoint exactly where they do exist and how an adversary can exploit them, reducing false positives and focusing previous human resources on the most critical vulnerabilities.
Granular controls over agent bounds and behaviour enable users to tailor their operations to mimic particular adversary behaviours or target specific aspects of their defence
Cyber threats disrupt critical industrial operations
TXOne Networks, a global OT security leader headquartered in Taiwan, delivers specialized solutions protecting assets and ensuring continuous uptime for 3600+ enterprises With offices and partners across Europe, the Middle East, Asia, and the Americas, we empower organizations to leverage digital transformation while maintaining operational safety and security throughout the asset lifecycle

UKC3 (UK Cyber Cluster Collaboration) is a national body that supports regional cyber clusters across the UK It promotes innovation, skills development, and collaboration to strengthen the UK's cyber ecosystem




Step into the dynamic world of Gen AI, social engineering, intelligent malware, and the rising threat of deepfakes. As the cybersecurity landscape evolves, so too do the opportunities and challenges that come with it. From real-time anomaly detection to combating increasingly sophisticated attacks, staying ahead requires innovation and vigilance
In an era of shrinking budgets and expanding threats with more environments, devices and software, the challenge is clear: if you are not an enterprise organisation with the budget and headcount to mitigate risk how can you protect yourself as an SMB while optimising resources? Afterall - 24/7 cyber security is for everyone.
In today’s evolving digital landscape, cyber threats are not just a technical issue they are a cultural challenge
From fostering a cybersecurityfirst culture to empowering employees as the ultimate human firewall, we’ll explore the soft skills required to turn your workforce into a robust line of defence From strategies to educate teams on advanced social engineering threats, build resilience, and instil a securityfirst mindset that protects your organisation from the ground up.






10:15-10:45
FromMaslowto Malware:Rethinking CyberLeadershipinthe AgeofAI
JaneFrankland CEOofKnewStart, FounderofINSecurity Movement
11:00-11:20
KeyInsightsforSecurity Leaders:CrowdStrike 2025GlobalThreat Report
JohnSpencer Director,Sales EngineeringCrowdStrike
12:05-12:25
TheCyberThreat:It’s Changed,ForAChange
CiaranMartin Professor
13:05-13:45
AGlobalPerspective: Navigating CybersecurityinaTime ofCrisis
SadieCreese UniversityofOxford
BenDonaldson CyberSecurity EngagementPartnerTesco
CiaranMartin -Professor
JaneFrankland -FounderofINSecurity Movement -CEOof KnewStart
14:00-14:20
Facingreality:Hacking facialrecognition
JakeMoore
GlobalCybersecurity Advisor-ESET
11:00-11:20
AISecurityThreatsAre Here-IsYourTeam Prepared?
JamesDyer ThreatIntelligenceLeadKnowBe4
11:30-11:50
Hack,Break,Learn:The PowerofHands-on CyberTraining
MatthewLloydDavies PrincipalAuthor,Security -Pluralsight
12:05-12:25
TheHumanElement: FacingFearintheAge ofPersonalisedAttacks
MarkHamill VPofProductat Metacompliance
12:35-12:55
BuildingaCareer&a BusinessUsingYour Brand
JoeHead Founder-Molto
14:00-14:20
CybersecurityisBoring! WhatCanYouChange?
NeilFrost ChiefExecutiveOfficerBob'sBusinessLtd
14:30-14:50
HowModernSocial EngineeringAffects YourWorkforceand ThreatensCorporate Data
TomDavison Sr Director,EMEASales EngineeringatLookout
11:00-11:20
Areyoureallysitting comfortably?
GarethLockwood CTO-Censornet
11:30-11:50
HowRiverIslandTurned aTightBudgetintoa SecuritySuccessStory SunilPatel
InformationSecurity Officer-RiverIsland
ChrisWallis Founder&CEO-Intruder
12:05-12:25
CyberSecurityBeyond theHeadlines–What BusinessesOverlook andWhyItMatters
DavidGriffiths CEO-HexiosecLimited
12:35-12:55
ClosingtheGaps:Using OpenXDRtoTransform CybersecurityResilience HugoBishop Director,Northern Europe-StellarCyber
13:05-13:25
Highlightsofthe2025 VulnerabilityStatistics Report-thegood,bad andbrutal EoinKeary CEO-Edgescan
13:30-13:50
Broughttoyouby OrpheusCyber
14:00-14:20
Broughttoyouby Huntress
11:00-11:20
DevSecOps,Detection, Defense:Stopping HackersBeforethey Strike
NickBlundell
HeadofResearch& DevelopmentAppCheck
11:30-11:50
Howtoenabledigital transformation, accelerateIT/OT convergenceand ensurecompliancewith zero-trustOT cybersecurity
AnjayMandalia PrincipalSecurityLead, UK&Ireland-TXOne
12:05-12:25
TheCybersecurity Dilemma:Maximising Effectivenessand Simplicity
ThomasKicker CEO-CyanDigital Security

12:35-12:55
SecurebyDesign:The essentialcomponentsto thesuccessandsecurity ofaconnecteddigital strategy
PeterClapton CEO-Vysiion
14:00-14:20
ChatGPTtoDeepseekto ? HowtoFutureProof SecurityfortheNextAI Boom
15:30-15:50
BuildingUnbreakable BusinessResilience AgainstRansomware
AndrewGrant SalesDirector-BullWall
14:30-14:50
AIinCybersecurity: FromHypetoReality JamieCollier LeadThreatIntelligence Advisor(Europe)-Google
15:00-15:20
Don'tPanic!PostQuantumCryptography isComing(andwe’ve gotyourguideonhow toprepare) <<NCSC>>Classified
15:30-15:50
UnmaskingHidden Risks:TheEssential GuidetoSupplyChain SecurityAssurance
AndySimpson ChiefInformation SecurityOfficer-Supply Assure
15:30-15:50 DecodingCyber Insurance:WhatYou NeedtoKnow ChrisBurgess Markel-DirectorofCyber
16:00-16:20
‘Oh,Behave!’Aglobal outlookoncyber behavioursandthe sciencebehind’
JasonNurse DirectorofScienceand Research-CybSafe
14:30-14:50 Automatedetectionand responsewithasmart, secureworkflowbuilder
StephenCreedon SeniorSecurity AutomationEngineerTines
15:00-15:20 MitigatingAIThreatsin ModernSupply Networks:APractical DefenceFramework DamieteKing-Harry SolutionsArchitectCloudfare
15:30-15:50 Whyattackersare winningandhowto fightback OliverPinson-Roxburgh CEO&CoFounderDefensecom
16:00-16:20
Thegrowingchallenges organisationsfacewhen securingtheirhybrid cloudenvironments
AliceCarlisle RegionalVicePresident UK&I-Wiz

16:00-16:20 Broughttoyouby Keyfactor

10:15-10:45
Cultivatingacyber security-firstculture–cultivatingawareness, resilienceanda proactivesecurity mindsetacross organisations
RobertHannigan Chairman,BlueVoyant EMEAandFormer DirectorofGCHQBlueVoyant
11:00-11:20
CalminaCrisis: UnveilingtheSecretsof IncidentCommand Management
DavidColes IncidentCommander andStrategicInitiatives Lead-TikTok
11:30-11:50
UnpackingQuantum Threats:TheFutureof Encryption ZygmuntLozinski QuantumSafeNetworks -IBM
12:05-12:25
CyberSecurityona Shoestring
RosieAnderson HeadofStrategic Solutionsth4ts3cur1tycompany
13:05-13:45
UnlockingPotentialand Bridgingthe CybersecuritySkillsGap JoeHead Founder-MOLTO
KamKaraji Director,CyberSecurity& RiskManagementNationalFootballLeague
14:00-14:20
HuntinginAzure subscription
11:00-11:20
CultivatingasecurityconsciouscultureWhile PreservingEmployee Morale
JavvadMalik LeadSecurityAwareness Advocate-KnowBe4
11:30-11:50
BroughttoyoubyPunk Security
12:35-12:55
Areyoubeing monitoredorareyou monitoringthem?
MatthewBell Founder-Cyber ProtectionGroup
13:05-13:25
BroughttoyoubyISSAUK
14:30-14:50
SmallBusiness,Big Threats:Cybersecurity StrategiesonaBudget
GlennWilkinson Hacker,Speaker,Founder -Maervo
11:00-11:20
Howtoescapethe midmarketsecuritygap CharlesMilton VPofStrategicAlliancesCensornet
MillieZah HeadofProduct,Cyber Security(SMB)-BT Group
11:30-11:50
DevSecOps,Detection, Defense:Stopping HackersBeforethey Strike
NickBlundell HeadofResearch& DevelopmentAppCheck
12:05-12:25
EmpoweringSecurity ThroughPrivileged AccessManagement (PAM)
JayGray HeadofCyberSecurity andCloudSolutionsExponential-e
12:35-12:55
Broughttoyouby Logically
13:30-13:50
DemocratisingCyber SecurityforAll-aNew EraofDefenceand Threats
PaoloPalumbo VPIntelligence WithSecure 14:30-14:50
ProtectMicrosoft365 datafromcyberattacks
VanessaToves Microsoft365Solutions Architect-Druva
11:30-11:50
BroughttoyoubyJ2 Software

OluwatobilobaMary Asaolu SecurityResearcherMicrosoft
12:35-12:55
HowCommon MisconfigurationsCan LeaveYouOpento Hackers
TomLarge
SeniorSecurity Consultant/TrainerClaranet
14:00-14:20
SecuringTelecom Networks:Navigating GlobalRegulations& EmergingThreats
BenRatcliff PracticeHeadTransformationSecurity Consulting-Nokia


14:30-14:50


11:00-11:10
IntroductiontoNeuroCyberandTheInclusiveCyber
Space
MikeSpain Founder&ExecutiveDirectoratNeuroCyber
11:10-11:35
30YearsofCyberSecurityinitiatives:TheEvolutionof Diversity&Inclusion
IanGlover ManagingDirectoratInspired2Ltd
11:45-12:30
ThefutureofCSEducationandIndustryRecruiting
IanGlover ManagingDirector Inspired2Ltd
KolawoleAbolarin Co-FounderofCyberAwareGroup LorneRolinson
CYBERCommunityManagerandProduct AssociatatTheHackingGames
ZofiaKolodziej
MarketingandOperationsAssociateatTheHacking Games
12:45-13:30
Cybercrime,theinitiativesandinterventions.
IanGlover ManagingDirectoratInspired2Ltd
RichardJones DirectoratCyberBehaviourSpecialists
SarahWard SeniorAccountExecutiveatPRPR
13:45-14:30
ACaseStudyfromTheCyberScheme –including actionsandtipsforsupportingneurodiverse individualsintheworkplace
DebiMcCormack
CommunicationsDirector-TheCyberScheme
14:45-15:30
NeurodiversityintheWorkplace
AlexHunter
PeerSupporttrainerandconsultantatWith-You Consultancy
11:00-11:30
TechChannelAmbassadors Encouragingmore (diverse)peopleintotheIndustry‘OneLofa Difference’
DaveStanley ManagingDirectoratGrillatech

11:45-12:30
AccessibilityinCyber
JemmaDavis FounderofCultureGem
QasimBhatti CEO&Co-FounderatMeta1st
12:45-13:30
RecruitmentadviceforallontheperfectCVandhow tooptimiseyoursocialmedia
DanHathaway Founder&DirectoratSecureSource
SarahWard Founder&DirectoratSecureSource
13:45-14:30
InclusiveLeadership
AndyPowell CISOatAP Moller-Maersk EddHardy DirectorofCyberSecurityatAlixPartners
PriyankaAgarwal TechnicalSecurityConsultant-BAESystems DigitalIntelligence




<< NCSC >> Classified

Ciaran Martin Professor

David Coles Incident Commander and Strategic Initiatives Lead, TikTok

Robert Hannigan Chairman, BlueVoyant EMEA and Former Director of GCHQ, BlueVoyant

Ben Donaldson Cyber Security Engagement Partner, Tesco

Jamie Collier Lead Threat Intelligence Advisor (Europe), Google

Jane Frankland Founder of IN Security Movement, CEO of KnewStart

Wilkinson Hacker, Speaker, Founder, Maervo

Kam Karaji Director, Cyber Security & Risk Management, National Football League

Oluwatobiloba Mary Asaolu Security Researcher, Microsoft

Jake Moore Global Cybersecurity Advisor, ESET

Zygmunt Lozinski Quantum Safe Networks, IBM



Sadie Creese University of Oxford

Joe Head Founder, MOLTO

Gareth Lockwood CTO, Censornet





David Griffiths CEO, Hexiosec Limited
Jason Nurse Director of Science and Research, CybSafe

Rosie Anderson Head of Strategic Solutions, th4ts3cur1tycompany

Paul Abbott Logistics Consultant, Paul Abbott Advisry

Oliver PinsonRoxburgh CEO & Co Founder, Defensecom
John Spencer Director, Sales Engineering, CrowdStrike

Chris Burgess Markel, Director of Cyber

Sunil Patel Information Security Officer, River Island

Damiete King-Harry Solutions Architect, Cloudfare
Neil Frost Chief Executive Officer, Bob's Business Ltd

Paul Cashmore CEO, Solace Global Cyber Ltd

Nick Blundell Head of Research & Development, Appcheck

Javvad Malik Lead Security Awareness Advocate, KnowBe4


Tom Davison Sr Director, EMEA Sales Engineering, Lookout

Thomas Kicker CEO, Cyan Digital Security

Matthew Lloyd Davies Principal Author, Security, Pluralsight





Paolo Palumbo VP Intelligence, WithSecure
Hugo Bishop Director, Northern Europe, Stellar Cyber

Eoin Keary CEO, Edgescan

Charles Milton VP of Strategic Alliances, Censornet

Ben Ratcliff Practice HeadTransformation Security Consulting, Nokia
Peter Clapton CEO, Vysiion

Stephen Creedon Senior Security Automation Engineer, Tines

Anjay Mandalia Principal Security Lead, UK & Ireland, TXOne

Vanessa Toves Microsoft 365 Solutions Architect, Druva
James Dyer Threat Intelligence Lead, KnowBe4

Chris Wallis Founder & CEO, Intruder

Humza Ismaiel Engineer Team Lead, Netskope

Mark Hamill VP of Product, Metacompliance


Andrew Grant Sales Director, BullWall

Tom Large Senior Security Consultant/Trainer, Claranet

Millie Zah Head of Product, Cyber Security (SMB), BT Group





Ian Glover Managing Director, Inspired2 Ltd
Jay Gray Head of Cyber Security and Cloud Solutions, Exponential-e

Alice Carlisle Regional Vice President UK&I, Wiz

Alex Hunter Peer Support trainer and consultant, With-You Consultancy

Dave Stanley Managing Director, Grillatech
Tim Holman President, ISSA-UK

Jemma D Founder, Culture Gem

Dan Hathaway Founder & Director, Secure Source

Zofia Kolodziej Marketing and Operations Associate, The Hacking Games
Andy Simpson Chief Information Security Officer, Supply Assure

Debi McCormack Communications Director, The Cyber Scheme

Matthew Bell Founder, Cyber Protection Group

Kolawole Abolarin Co-Founder, Cyber Aware Group


Lorne Rolinson CYBER Community Manager and Product Associat, The Hacking Games

Sarah Ward Senior Account Executive, PRPR

Chris Job Channel Solutions Engineer, Keyfactor

Mike Spain Founder & Executive Director, NeuroCyber

Edd Hardy Director Cyber Security, AlixPartners

Qasim Bhatti CEO & Co-Founder, Meta1st

Priyanka Agarwal Technical Security Consultant, BAE Systems Digital Intelligence

Richard Jones Director, Cyber Behaviour Specialists


Andy Powell CISO, A.P. Moller - Maersk


THANK YOU TO OUR PARTNERS & SPONSORS
















