

Protecting Data: Privacy, Security, and Compliance for Tailored Care Management
What’s required to safely manage sensitive data in behavioral health and I/DD services, including emerging AI tools?



What’s required to safely manage sensitive data in behavioral health and I/DD services, including emerging AI tools?
In an era of increasing cyber threats and expanding data sharing requirements, protecting sensitive information has never been more critical. This session will equip providers with practical strategies to safeguard data privacy and security while ensuring compliance with HIPAA, North Carolina confidentiality laws, and other regulatory standards.
Participants will explore best practices for handling Protected Health Information (PHI), learn about common vulnerabilities and safeguards, and discuss the ethical considerations of using emerging technologies such as AI in care coordination.
Attendees will leave with actionable insights to strengthen their organization’s data protection practices and maintain the trust of the individuals and families they support.
By the end of this session, participants will be able to:
1.Identify key regulatory requirements for data privacy and security in TCM, including HIPAA and NC Mental Health Confidentiality laws.
2.Describe practical strategies to protect PHI and implement effective safeguards within their organization.
3.Explain the ethical considerations and potential impacts of emerging technologies, such as AI, on data management and compliance.
“If we lose people’s trust by failing to protect their health information, we lose the opportunity to improve health outcomes.”
— Dr. David Blumenthal, former National Coordinator for Health

HIPAA – Safeguards for Protected Health Information (PHI)
HITECH Act – Strengthens HIPAA & promotes secure EHR use
42 CFR Part 2 (Substance Abuse and Mental Health Services Administration,SAMHSA) – Strict confidentiality rules for substance use (SUD) records
Identity Theft Protection Act (§ 75-60) – Breach notification & data security requirements
Confidentiality of Social Services Records (§ 108A-80) – Limits disclosure of DHHS client info
Public Records Law (§ 132-1) – Protects sensitive info in government records (including SSN)
Privacy Act of 1974 – Limits federal use of personal data
NC DHHS Privacy Policies – Operational standards for access, sharing, and compliance

HIPAA Privacy Rule: Protects PHI and governs how it can be used/disclosed.

HIPAA Security Rule: Requires safeguards for electronic PHI (ePHI).

Breach Notification Rule: Requires reporting of breaches to affected individuals, DHHS, and sometimes media.

Your Responsibility: Only access PHI needed for your role, protect it at all times, and report concerns immediately.
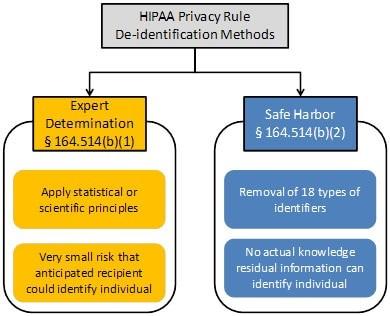
https://www.hhs.gov/hipaa/for-professionals/special-topics/de-identification/index.html
Personal Identifiers
• Name
• Photos or images
• Electronic record number, Medicaid ID, SSN, health plan numbers
• Biometric data (fingerprints, voice)
• Phone & fax numbers
• Email addresses
• Home addresses & all geographic info smaller than a state Contact Info
• Birth
• Service plan
• Death Dates
• Admission, discharge, transfers
• Service authorizations
• Diagnoses
Clinical Data
• Procedures
• Medications
• Lab results

Permitted Uses without Authorization: Treatment, payment, healthcare operations, required reporting.

When Authorization is Needed: Marketing, most disclosures to third parties.

People You Support Have the Right to:
Access their records
Request amendments
Request restrictions on uses/disclosures
Receive notice of privacy practices

• Just because you’re speaking softly doesn’t make it private.
• Protected Health Information should never be discussed in public spaces—privacy isn’t just a policy, it’s a right.
• This extends to the digital / electronic world too.
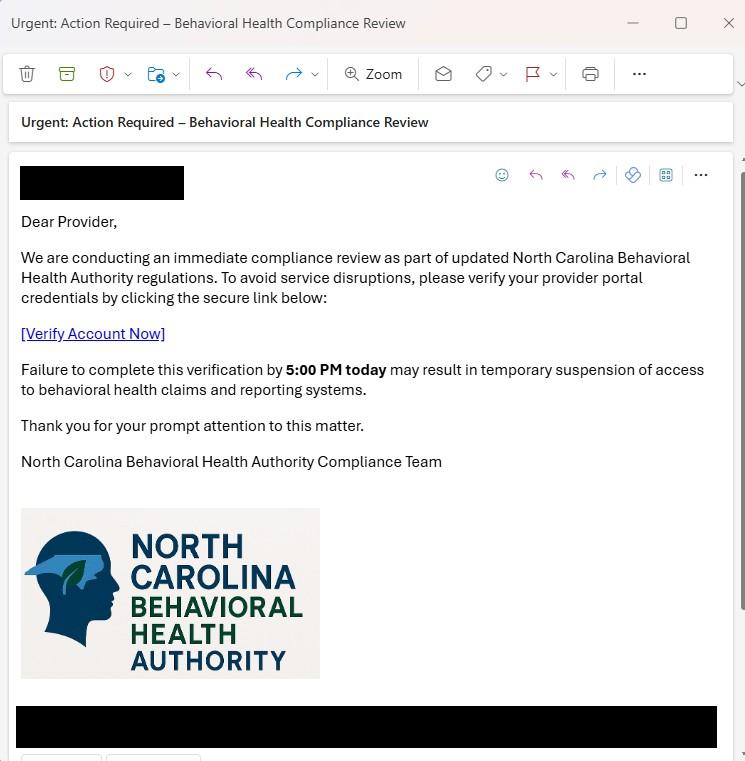
• Phishing is a cyberattack where attackers impersonate someone you think you might know or trust to trick you into revealing sensitive information, clicking malicious links, or downloading harmful attachments.
• Example: In 2020, AspenPointe, a Colorado behavioral health organization, experienced a phishing attack that compromised employee email accounts containing sensitive client data, including Social Security numbers and clinical information. This resulted in:
• Breach of over 295,000 individuals’ records
• Cost millions in notification, legal, and remediation expenses
• Damaged community trust and reputation https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
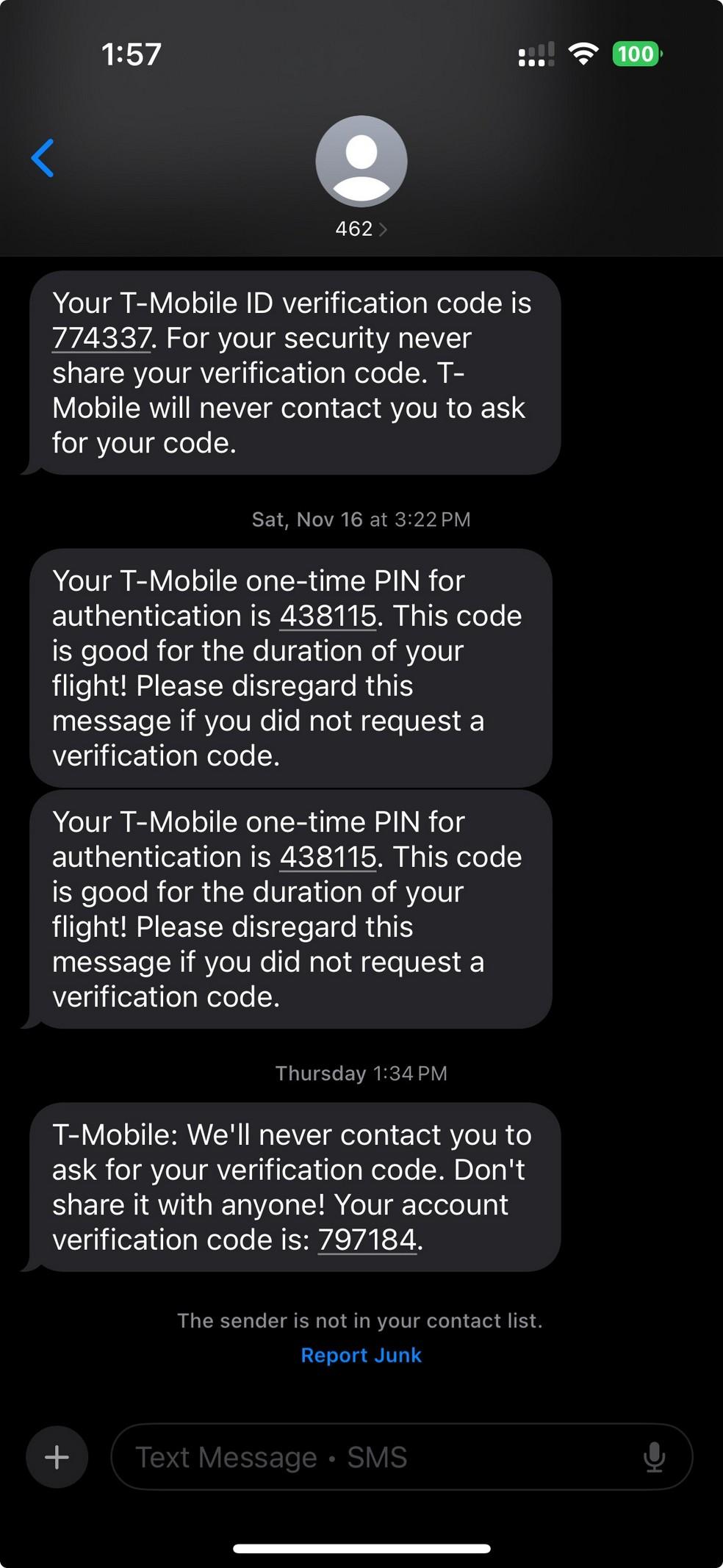
• Multi-Factor Authentication (MFA) is a security process that requires users to provide two or more verification factors to access a system, adding an extra layer of protection beyond just a password.
• To log in, you must enter:
• Something you know (password)
• Plus one of the following:
• Something you have (e.g., a code from an authenticator app or text message)
• Something you are (e.g., fingerprint or facial recognition)
• Prevents unauthorized access, even if passwords are stolen.
• Protects sensitive PHI and organizational systems from cyberattacks.
• Required or strongly recommended under cybersecurity best practices for all systems with health data.
Breaches often result from simple mistakes – an unencrypted email, clicking a phishing link, or a lost unprotected device can expose sensitive client data.

Email: Only send PHI through encrypted email or secure portals. Never include sensitive data in the subject line.

Phishing: Always check sender addresses. Be cautious of urgent requests, suspicious links, or attachments from unknown sources.

Passwords: Use strong, unique passwords for each system and enable multi-factor authentication whenever possible.
• Examples of Security Incidents: Lost/stolen laptop or phone, misdirected email with PHI, suspected phishing click.
• What To Do:
• Report immediately to your supervisor and Privacy Officer
• Do not attempt to fix or hide the issue yourself
• Timely reporting helps protect individuals and meet legal obligations
A Data Governance Framework is the set of policies, roles, and processes that ensure data is managed securely and responsibly, including clear procedures for detecting, reporting, and responding to security incidents to protect sensitive information.
RISK MANAGEMENT & CYBERSECURITY
Building Trust, Ensuring Compliance, and Driving Better Outcomes with Smarter Data Management
Data Stewardship & Ownership
Privacy & Security Compliance
Data Quality & Integrity
Data Access & Use Policies
• Assign clear roles for who manages, accesses, and is accountable for different types of data (e.g., EHR admin, billing lead, clinical director).
• Implement HIPAA-compliant controls: role-based access, device encryption, secure file transfers, and regular staff privacy training.
Incident Reporting & Breach Response
• Set standards for accurate, complete, and timely documentation in EHRs, forms, and spreadsheets; conduct periodic data audits.
• Define who can access clinical, financial, and quality data—and for what purpose (e.g., reporting, quality control, grant writing).
• Maintain clear procedures for reporting data breaches, unauthorized access, or system failures—aligned with NC DHHS IRIS and HIPAA rules.
Reporting & DecisionMaking Framework Helpful Resource: https://www.ncdhhs.gov/ncdhhs-data-sharing-guidebook/open
• Establish a simple reporting calendar and metrics (e.g., ED use, engagement, noshow rate) to guide leadership decisions and quality improvement.

Artificial Intelligence (AI): Technologies enabling machines to mimic human intelligence.

Machine Learning (ML): Algorithms (rules) trained on data to make predictions without explicit programming.

Generative AI: AI that creates new content (text, images, etc.).

Large Language Model (LLM): An AI system trained on vast amounts of text data to understand, generate, and manipulate human language and reasoning.

OpenAI – GPT-1: June 2018 → GPT-
4.5: February 2025

Microsoft – TuringNLG: February 2020 → Copilot 2023
Oct. 2018
June 2018

Mar. 2021
Feb. 2020

Google – BERT: October 2018 → Gemini 2.0 Flash: Early 2025

Meta AI – LLaMA 1: February 2023 3: 2024

Grok-2: Early 2025
EleutherAI – GPTNeo: March 2021 → GPT-NeoX: 2022 July 2022 Aug. 2022
Amazon – Alexa 20B: August 2022 → Olympus: 2024 Feb. 2023


DeepSeek –DeepSeek-R1: January 2025 → DeepSeek-R2: 2025
AnnieLytics. (2025). AI timeline. Retrieved March 2, 2025, from https://annielytics.com/tools/ai-timeline/

• Systems that can create new content—like text, images, or audio— based on patterns learned from large datasets.

• LLMs enable useful conversations about any topic in fluent, natural language

Person-
Centered Planning Assessment s, Service Notes, Summaries

Quality & Outcome Monitoring Transitions & Life Events by identifying gaps, predicting needs, and generating clearer, more person-centered documentation, for example with:


Service Delivery & Utilization

Health & Behavior Monitoring Inclusion & Engagemen t


Equity & Disparity Analysis Risk Identificatio n Workforce Analysis



Vendors can fine tune public models in order to keep data proprietary and local to HCBS Providers and avoid sending Protected Health Information to the public models
Pros: Security, Confidentiality
Cons: Doesn’t always benefit from the worldwide bi-directional language model learning



Protected Health Information Plagiarism



Closed AI systems keep Protected Health Information (PHI) internal and secure.
Anonymization/deidentification remove personal identifiers before data ever reaches the AI model.
Retrieval-Augmented Generation (RAG) helps prevent AI hallucinations and bias by “grounding” answers in your organization’s trusted documents, like policies and bio-psycho-social best practices and protocols.
Role-Based Access Control (RBAC) ensures only authorized staff can use or view sensitive data.
Ongoing staff training explains responsibilities and how to handle sensitive information appropriately.
Audit logging helps track all AI interactions for accountability and compliance.





Securing Data in Transit and at Rest
Encryption to protect data while it's stored or moving. This reduces vulnerability to external threats, bolstering your defense against security breaches.

Require MFA for all systems accessing PHI, and enforce strong, unique passwords to prevent unauthorized access –even if credentials are stolen.

Ensure laptops, phones, and tablets are encrypted. Always send PHI via encrypted email or secure portals to protect data in transit and at rest.

Train staff to recognize phishing emails, verify suspicious requests before clicking links or sharing information, and report attempted scams immediately.

Keep all operating systems, software, and devices updated to fix known vulnerabilities often targeted in cyberattacks.

Limit PHI access to only those who need it (minimum necessary principle), and audit system logs regularly to detect unauthorized access or unusual activity.

