CREDITS
Figure 1-8
Figure 1-9
Screenshot of The command prompt in Windows 10 © Microsoft 2020
Screenshot of A typical text screen result when entering the ipconfig /all command in the command window.
© Microsoft 2020
Figure 1-15 courtesy for Linksys
Figure 1-18 courtesy Zoom Telephonics, Inc.
Figure 1-19 courtesy for Linksys
Figure 1-27
Figure 2-34
Screenshot of (a) An example of displaying the IP address for computer 1 using the ipconfig command in Windows and (b) an example of the displayed IP address in macOS for the built-in Ethernet connection © Microsoft 2020
Screenshot of DTX-1800 certification report: Failure due to a termination problem. ©Fluke Corporation
Figure 2-35 Screenshot of DTX-1800 certification report: Failure due to excessive insertion loss. ©Fluke Corporation
Figure 2-36
Figure 2-37
Screenshot of The certification report for Test 1, showing that a short jumper cable passes the CAT5e link test.
©Fluke Corporation
Screenshot of The results for Test 2, showing that the cable failed the CAT5e link test. ©Fluke Corporation
Figure 2-38 Screenshot of The Test 3 CAT5e link test, showing failures with attenuation. ©Fluke Corporation
Figure 2-39 Screenshot of A CAT5e link test, showing failures with delay skew (Test 4). ©Fluke Corporation
Unnumbered
Figure 2-1
Unnumbered
Figure 2-2
Unnumbered
Figure 2-3
Screenshot of Answer the following questions related to the certification report shown here. ©Fluke Corporation
Screenshot of Answer the following questions related to the certification report shown here. ©Fluke Corporation
Screenshot of Answer the following questions related to the certification report shown here - OMNI Scanner. ©Fluke Corporation
Figure 4-7 Screenshot of An example of the information displayed when an association is formed between a client and an access point. © Microsoft 2020
Figure 4-8
Screenshot of An example of a lost association. © Microsoft 2020
Figure 4-18 Screenshot of The window for configuring Bluetooth settings on a Mac. © 2020 Apple Inc
Figure 4-19 Screenshot of The Mac window showing the settings for a file transfer. © 2020 Apple Inc
Figure 4-20 Screenshot of The Mac window showing that a text file is coming in from another Bluetooth device. © 2020 Apple Inc
Figure 4-28
Screenshot of The excellent signal quality measured for the multipoint distribution. © Microsoft 2020
Figure 4-29 Screenshot of The poor signal quality measured at the remote site near the lake. © Microsoft 2020
Figure 5-7 Screenshot of The data traffic captured by computer 2 for the LAN using a hub. © Microsoft 2020
Figure 5-8 Screenshot of The data traffic captured by computer 2 for the LAN using a switch. © Microsoft 2020
Figure 5-9 Screenshot of The startup menu of a Cisco Catalyst switch in the CNA software. © Microsoft 2020
Figure 5-10 Screenshot of The highlighted ports showing the current connections and the location of the stacked switches icon. © Microsoft 2020
Figure 5-11 Screenshot of The window listing the MAC addresses currently connected to a switch. © Microsoft 2020
Figure 5-13 Screenshot of Configuring an IP address on an interface. © Microsoft 2020
Figure 5-19 Screenshot of Putty configuration © 1997-2020 Simon Tatham
Figure 5-20 Screenshot of The HyperTerminal Connect To dialog © 1997-2020 Simon Tatham
Figure 5-21 Screenshot of The Properties dialogs for configuring the serial port connection PuTTY © 1997-2020 Simon Tatham
Figure 5-23 Screenshot of The macOS dialog for configuring the settings for the serial interface. © 2020 Apple Inc
Figure 5-24 Screenshot of The macOS dialog for setting the serial port to PL2303-000. © 2020 Apple Inc
Figure 5-25 Screenshot of The macOS window listing the serial communication link settings. © 2020 Apple Inc
Figure 6-6 Screenshot of An example of the three packets exchanged in the initial TCP handshake. © Microsoft 2020
Figure 6-8 Screenshot of An example of the four-packet TCP connection termination. © Microsoft 2020
Figure 6-10 Screenshot of An example of a UDP packet transfer. © Microsoft 2020
Figure 6-12 Screenshot of Captured packets showing the (a) ARP request and the (b) ARP reply. © Microsoft 2020
Figure 6-13 Screenshot of The details of the ARP broadcast packet. © Microsoft 2020
Figure 6-14 Screenshot of An example of the use of hex numbers in data packets. © Microsoft 2020
Figure 7-3 Screenshot of The TCP/IP dialog for setting the default gateway address for computer A1. © Microsoft 2020
Figure 7-6 Screenshot of The Net-Challenge screen. © Microsoft 2020
Figure 7-7 Screenshot of The check box window for the Net-Challenge software User EXEC Mode challenge.
© Microsoft 2020
Figure 7-8 Screenshot of The display for step 6, using the show command. © Microsoft 2020
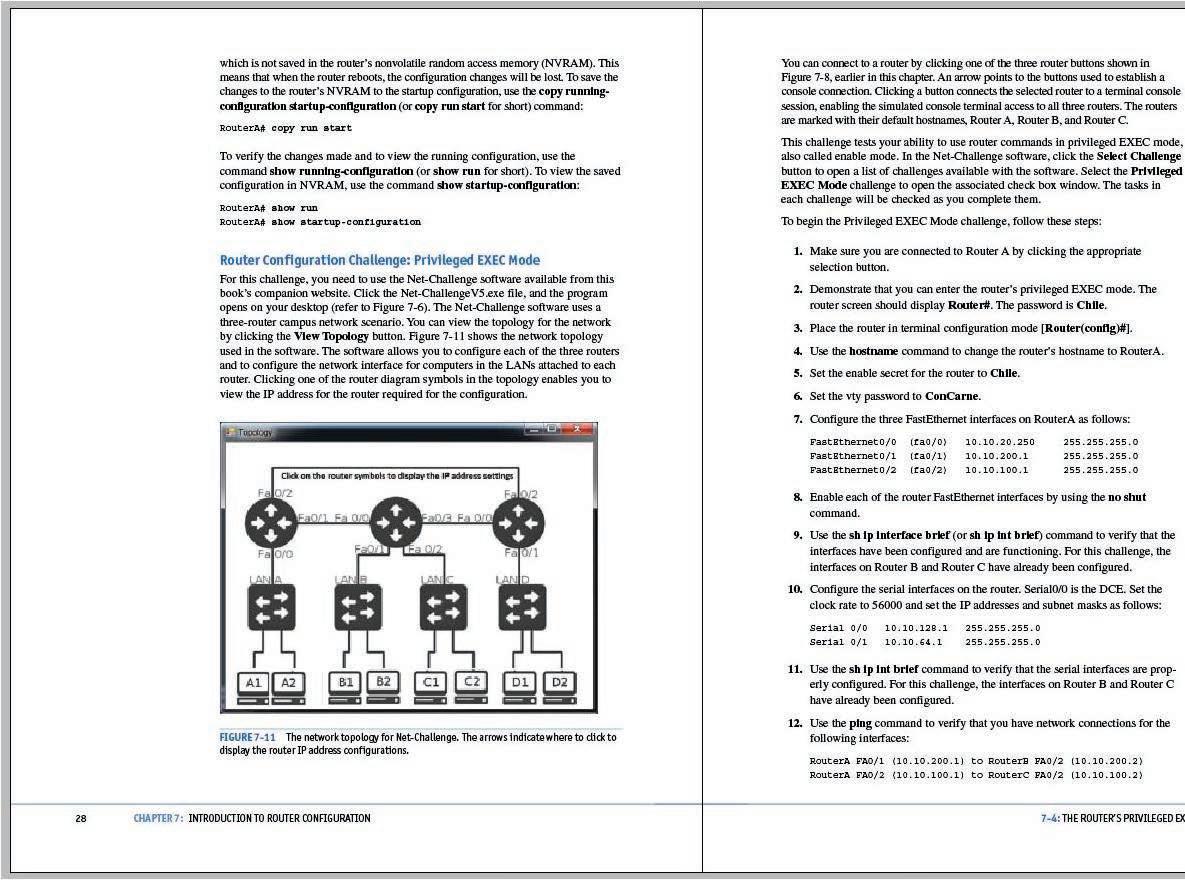
Figure 7-11
Figure 7-14
Figure 9-1a
Figure 9-1b
FIG10-4
FIG10-9
FIG10-11
FIG10-12
FIG10-23
FIG10-24
FIG10-25
FIG10-26
FIG10-27
FIG10-28
FIG10-30
FIG10-31
FIG11-9
Screenshot of The network topology for Net-Challenge. The arrows indicate where to click to display the router IP address configurations. © Microsoft 2020
Screenshot of An example of the port management options available with a Cisco switch: (a) Speed auto-negotiation option; (b) Duplex auto option. © Microsoft 2020
Screenshot of Setting the default gateway address or default static route on a host computer (PC). © Microsoft 2020
Screenshot of Setting the default gateway address or default static route on a host computer (macOS). © Microsoft 2020
Screenshot of Captured DHCP packets. © Microsoft 2020
Screenshot of An example of using an SNMP software management tool to obtain descriptions of a router’s interfaces using the MIB ifDescr. © Microsoft 2020
Screenshot of Using an SNMP software management tool to obtain interface speed settings. © Microsoft 2020
Screenshot of An example of using SNMP to collect data traffic statistics. © Microsoft 2020
Screenshot of Initializing Wireshark to capture data packets from a network. © Microsoft 2020
Screenshot of Starting a capture. © Microsoft 2020
Screenshot of The captured packets showing the ping from computer 1 to computer 2. © Microsoft 2020
Screenshot of Computer 2 replying to computer 1 with its MAC address. © Microsoft 2020
Screenshot of Computer 1 is sending an echo request to computer 2. © Microsoft 2020
Screenshot of The echo reply received by computer 1. © Microsoft 2020
Screenshot of (a) The beginning of the FTP data packet transfer and the request for an ASCII data transfer by the client. (b) The FTP data packet transfer and the closing of the FTP transfer. © Microsoft 2020
Screenshot of Figure for problems 64–68. © Microsoft 2020
Screenshot of Windows Firewall in Windows 10. © Microsoft 2020
FIG11-10 Screenshot of Windows 10 Firewall status. © Microsoft 2020
FIG11-11
FIG11-12
Screenshot of Windows 10 allowed apps. © Microsoft 2020
Screenshot of Windows 10 advanced firewall settings. © Microsoft 2020
FIG11-13 Screenshot of Windows 10 echo request properties. © Microsoft 2020
FIG11-14 Screenshot of Windows 10 echo request protocols and ports. © Microsoft 2020
FIG11-15
Screenshot of macOS firewall. © 2020 Apple Inc
FIG11-16 Screenshot of macOS advanced settings. © 2020 Apple Inc
FIG11-17 Screenshot of Linux iptables © The Netfilter’s webmasters
FIG11-19
Screenshot of An example of setting WEP encryption on a wireless client. © Microsoft 2020
FIG11-26 Screenshot of The traceroute from the VPN server to the VPN remote client. © Microsoft 2020
FIG11-27 Screenshot of The first window, the VPN Client status window, is displayed after starting the VPN client software. © Cisco systems
FIG11-28
Screenshot of The connection screen for establishing a VPN link. © Cisco systems
FIG11-29 Screenshot of The initial handshake screen for the VPN client. © Cisco systems
FIG11-30 Screenshot of The menu showing that the VPN client has successfully connected to the virtual private network. © Cisco systems
FIG11-31 Screenshot of The Preferences window for the VPN client. © Cisco systems
FIG11-32 Screenshot of The Statistics window (a) and Route Details window (b) for the VPN client. © Cisco systems
FIG12-1 Screenshot of Enabling Hyper-V © Microsoft 2020
FIG12-2 Screenshot of Using Hyper-V Manager © Microsoft 2020
FIG12-3 Screenshot of Creating a virtual switch in Hyper-V © Microsoft 2020
FIG12-4 Screenshot of Specifying the name of a virtual switch © Microsoft 2020
FIG12-5 Screenshot of Creating a virtual machine © Microsoft 2020
FIG12-6 Screenshot of Specifying the name and location of a virtual machine. © Microsoft 2020
FIG12-7 Screenshot of Specifying the generation of the virtual machine © Microsoft 2020
FIG12-8 Screenshot of Specifying the desired memory size for a VM. © Microsoft 2020
FIG12-9 Screenshot of Selecting the connection name of the virtual switch. © Microsoft 2020
FIG12-10 Screenshot of Specifying a virtual hard disk name, location, and size. © Microsoft 2020
FIG12-11 Screenshot of The options for installing the VM’s operating system. © Microsoft 2020
FIG12-12 Screenshot of Starting the new VM. © Microsoft 2020
FIG12-13 Screenshot of The final VM screen, showing that the machine is up. © Microsoft 2020 Peter Mell (NIST), Tim Grance (NIST), The NIST Definition of Cloud Computing, SP 800-145
Cover Artistdesign29/Shutterstock
ABOUT THE AUTHORS
Jeffrey S. Beasley is a professor emeritus in the Information and Communications Technology program at New Mexico State University, where he taught computer networking and many related topics. He is coauthor of Modern Electronic Communication, ninth edition, the author of Networking, second edition, and co-author of Networking Essentials, fifth edition, and A Practical Guide to Advanced Networking. Piyasat Nilkaew is the director of Computing and Networking Infrastructure at New Mexico State University and has more than 20 years of experience in network management and consulting. He has extensive expertise in deploying and integrating multiprotocol and multivendor data, voice, and video network solutions. He is co-author of Networking Essentials, fifth edition, and A Practical Guide to Advanced Networking.
ABOUT THE TECHNICAL REVIEWER
Chris Crayton is a technical consultant, trainer, author, and industry-leading technical editor. He has worked as a computer technology and networking instructor, information security director, network administrator, network engineer, and PC specialist. Chris has authored several print and online books on PC repair, CompTIA A+, CompTIA Security+, and Microsoft Windows. He has also served as technical editor and content contributor on numerous technical titles for several of the leading publishing companies. He holds numerous industry certifications, has been recognized with many professional and teaching awards, and has served as a state-level SkillsUSA final competition judge. Chris tech edited and contributed to this book to make it better for students and those wishing to better their lives.
DEDICATIONS
This book is dedicated to my family: Kim, Damon/Heather, and Dana/Sam. —Jeff Beasley
This book is dedicated to my family: Boonsong, Pariya, June, Ariya, and Atisat. —Piyasat Nilkaew
ACKNOWLEDGMENTS
I am grateful to the many people who have helped with this text. My sincere thanks go to the following technical consultants:
● Danny Bosch and Matthew Peralta for sharing their expertise with optical networks and unshielded twisted-pair cabling
● Don Yates for his help with the initial Net-Challenge software
I would also like to thank my many past and present students for their help with this book:
● Abel Sanchez, Kathryn Sager, and Joshua Cook for their work on the Net-Challenge software; Adam Segura for his help taking pictures of the steps for CAT6 termination; Marc Montez, Carine George-Morris, Brian Morales, Michael Thomas, Jacob Ulibarri, Scott Leppelman, and Aarin Buskirk for their help with laboratory development; Josiah Jones and Raul Marquez Jr. for their help with the Wireshark material; and Ariya Nilkaew for her help with revising and editing many of the captured pictures
● Aaron Shapiro and Aaron Jackson for their help testing the many network connections presented in the text
● Paul Bueno and Anthony Bueno for reading through an early draft of the text
Your efforts are greatly appreciated.
We appreciate the excellent feedback of the following reviewers: Phillip Davis, DelMar College, Texas; Thomas D. Edwards, Carteret Community College, North Carolina; William Hessmiller, Editors & Training Associates; Bill Liu, DeVry University, California; and Timothy Staley, DeVry University, Texas.
Our thanks to the people at Pearson for making this project possible. Thanks to Brett Bartow for providing us with the opportunity to work on the sixth edition and for helping make this process enjoyable. Thanks to Marianne Bartow, to all the people at Pearson IT Certification, and also to the many technical editors for their help editing the manuscript.
Special thanks to our families for their continued support and patience.
WE WANT TO HEAR FROM YOU!
—Jeffrey S. Beasley and Piyasat Nilkaew
As the reader of this book, you are our most important critic and commentator. We value your opinion and want to know what we’re doing right, what we could do better, what areas you’d like to see us publish in, and any other words of wisdom you’re willing to pass our way.
We welcome your comments. You can email or write to let us know what you did or didn’t like about this book— as well as what we can do to make our books better.
Please note that we cannot help you with technical problems related to the topic of this book.
When you write, please be sure to include this book’s title and author as well as your name and email address. We will carefully review your comments and share them with the authors and editors who worked on the book.
Email: community@informit.com
READER SERVICES
Register your copy of Networking Essentials, Sixth Edition at www.pearsonitcertification.com for convenient access to downloads, updates, and corrections as they become available. To start the registration process, go to www.pearsonitcertification.com/register and log in or create an account.* Enter the product ISBN 9780137455928 and click Submit. When the process is complete, you will find any available bonus content under Registered Products.
*Be sure to check the box that you would like to hear from us to receive exclusive discounts on future editions of this product.
INTRODUCTION
This book provides a look at computer networking from the point of view of a network administrator. It guides readers from an entry-level knowledge of computer networks to advanced concepts related to Ethernet networks; router configuration; TCP/IP networks; routing protocols; local, campus, and wide area network configuration; network security; wireless networking; optical networks; voice over IP; network servers; and Linux networking. After reading the entire text, you will have gained a solid knowledge base in computer networks.
In our years of teaching, we have observed that technology students prefer to learn “how to swim” after they have gotten wet and taken in a little water. Then they are ready for more challenges. In this book, we therefore show you the technology, how it is used, and why, and you can take the applications of the technology to the next level. Allowing you to experiment with the technology helps you develop a greater understanding.
ORGANIZATION OF THE TEXT
This book has been thoroughly updated to reflect the latest version of the CompTIA Network+ exam. Networking Essentials, sixth edition, is a practical, up-to-date, and hands-on guide to the basics of networking. Written from the viewpoint of the network administrator, it requires absolutely no previous experience with either network concepts or day-to-day network management. Throughout the text, you will gain an appreciation of how basic computer networks and related hardware are interconnected to form a network. You will come to understand the concepts of twisted-pair cable, fiber optics, LANs interconnection, TCP/IP configuration, subnet masking, basic router configuration, switch configuration and management, wireless networking, and network security.
The textbook’s companion website contains laboratory exercises, the Net-Challenge software, Wireshark captures, and the Network+ terminology quizzes.