https://ebookmass.com/product/meeting-people-via-wi-fi-and-
Instant digital products (PDF, ePub, MOBI) ready for you
Download now and discover formats that fit your needs...
Cyber Security Awareness for CEOs and Management 1st Edition Dalziel
https://ebookmass.com/product/cyber-security-awareness-for-ceos-andmanagement-1st-edition-dalziel/ ebookmass.com
Meeting Expectations in Management Education 1st ed. Edition Elizabeth Christopher
https://ebookmass.com/product/meeting-expectations-in-managementeducation-1st-ed-edition-elizabeth-christopher/
ebookmass.com
Inter-Regional Relations and the Asia-Europe Meeting (ASEM) 1st Edition Bart Gaens
https://ebookmass.com/product/inter-regional-relations-and-the-asiaeurope-meeting-asem-1st-edition-bart-gaens/ ebookmass.com
Challenging a Fictitious Neutrality: Heidegger in Question 1st ed. 2022 Edition Luce Irigaray (Editor)
https://ebookmass.com/product/challenging-a-fictitious-neutralityheidegger-in-question-1st-ed-2022-edition-luce-irigaray-editor/ ebookmass.com
Ahuman Pedagogy: Multidisciplinary Perspectives for Education in the Anthropocene Jessie L. Beier
https://ebookmass.com/product/ahuman-pedagogy-multidisciplinaryperspectives-for-education-in-the-anthropocene-jessie-l-beier/
ebookmass.com
Die unglaubliche Wunderreise des Freddie Yates Pearson
https://ebookmass.com/product/die-unglaubliche-wunderreise-desfreddie-yates-pearson/
ebookmass.com
The Handbook of Board Governance, 2nd Edition Richard Leblanc
https://ebookmass.com/product/the-handbook-of-board-governance-2ndedition-richard-leblanc/
ebookmass.com
Puntos (Student Edition) 10th Edition, (Ebook PDF)
https://ebookmass.com/product/puntos-student-edition-10th-editionebook-pdf/
ebookmass.com
CISSP Exam Cram, 5th Edition Michael Gregg [Michael Gregg]
https://ebookmass.com/product/cissp-exam-cram-5th-edition-michaelgregg-michael-gregg/
ebookmass.com
Student Services: A Handbook for the Profession (Jossey
Bass Higher and Adult Education)- 6th Edition -2016, Ebook
PDF Version
https://ebookmass.com/product/student-services-a-handbook-for-theprofession-jossey-bass-higher-and-adult-education-6thedition-2016-ebook-pdf-version/ ebookmass.com
MeetingPeopleviaWiFi andBluetooth MeetingPeopleviaWiFi andBluetooth JoshuaSchroeder
ContributingEditor
HenryDalziel
AMSTERDAM
SyngressisanimprintofElsevier
SyngressisanimprintofElsevier 225WymanStreet,Waltham,MA02451,USA
Copyright r 2016ElsevierInc.Allrightsreserved.
Nopartofthispublicationmaybereproducedortransmittedinanyformorbyanymeans, electronicormechanical,includingphotocopying,recording,oranyinformationstorageand retrievalsystem,withoutpermissioninwritingfromthepublisher.Detailsonhowtoseek permission,furtherinformationaboutthePublisher’spermissionspoliciesandourarrangements withorganizationssuchastheCopyrightClearanceCenterandtheCopyrightLicensingAgency, canbefoundatourwebsite: www.elsevier.com/permissions
Thisbookandtheindividualcontributionscontainedinitareprotectedundercopyrightbythe Publisher(otherthanasmaybenotedherein).
Notices
Knowledgeandbestpracticeinthisfieldareconstantlychanging.Asnewresearchand experiencebroadenourunderstanding,changesinresearchmethodsorprofessionalpractices, maybecomenecessary.
Practitionersandresearchersmustalwaysrelyontheirownexperienceandknowledgein evaluatingandusinganyinformationormethodsdescribedherein.Inusingsuchinformationor methodstheyshouldbemindfuloftheirownsafetyandthesafetyofothers,includingpartiesfor whomtheyhaveaprofessionalresponsibility.
Tothefullestextentofthelaw,neitherthepublishernortheauthors,contributors,oreditors, assumeanyliabilityforanyinjuryand/ordamagetopersonsorpropertyasamatterofproducts liability,negligenceorotherwise,orfromanyuseoroperationofanymethods,products, instructions,orideascontainedinthematerialherein.
ISBN:978-0-12-804721-7
BritishLibraryCataloguing-in-PublicationData
AcataloguerecordforthisbookisavailablefromtheBritishLibrary LibraryofCongressCataloging-in-PublicationData
AcatalogrecordforthisbookisavailablefromtheLibraryofCongress
ForInformationonallSyngresspublications visitourwebsiteat http://store.elsevier.com/Syngress
ABOUTTHEAUTHORS HenryDalziel isaserialeducationentrepreneur,founderofConcise AcLtd,onlinecybersecuritybloggerande-bookauthor.Hewritesfor theConcise-Courses.comblogandhasdevelopednumerouscybersecuritycontinuingeducationcoursesandbooks.ConciseAcLtddevelopsanddistributescontinuingeducationcontent(booksandcourses) forcybersecurityprofessionalsseekingskillenhancementandcareer advancement.ThecompanywasrecentlyacceptedontotheUK Trade&Investment’s(UKTI)GlobalEntrepreneurProgram(GEP).
Theauthor, JoshuaSchroeder,originallyfromNorthCarolina,first startedlearningaboutcomputersfromhisdad,DonaldSchroeder,a SeniorServiceEngineer.Mostofhisworkconsistedofassistancein applications,service,training,andsalesforseveraldifferentcompanies supportingthemanufacturingeffortsoftheSouthEastUnitedStates. ManynightshewouldbringhomecomputersandotherbitsoftechnologyforJoshuatoplayon.Hisskillsandinterestinthefielddeepenedwhenhismother,MichelleSchroeder,whohomeschooledhim K-12,decidedtostarttakinghimweeklytotheHispanicLearning Center(todayknownastheInternationalCenterforCommunity Development)wherehehelpeddesign,run,andfixtheircomputernetworktohelpstudentslearnreading,writing,andmathintheirafterschoolprograms.Thisfoundationofskillspropelledhimtobe successfulinInformationTechnologyandSecurity,andfortheirhelp andguidanceheisverythankful.
Incollege,hegraduatedwithaMastersinITwithaConcentration inSecurityandPrivacyfromtheUniversityofNCatCharlotte(UNC Charlotte)wherehealsoisknownforhelpingfoundthe49thSecurity Division asecurityclubthatstillhelpstoinstillinterestinsecurity andotherpiecesoftechnologyforstudentsattheuniversity.Sincecollege,hisresearchandworkincludepresentationsatShmooConand SkyDogContitled “CCTV:SetupAttackVectorsandLaws,” Carolina Conwherehepresented “Spam,PhishandOtherThingsGoodto Eat,” and “BurpSuite:AComprehensiveWebPenTesting” aswell asparticipationinthesecuritygroupNoVAHackersinVirginia.
HecurrentlyworksdoingincidentresponseinNorthernVirginia,howeverthisresearchisdifferentfromtheresponsibilitiesofhisjob.Many ofthetricksandtipsincludedinthisbookwouldnothavebeenpossiblewithoutthetrainingandguidanceoftheteamthathelpsrunthe WirelessVillageatDEFCON,andfortheirdedicationyearafteryear, hewouldliketoexpresshisthanks.
OVERVIEW Thischapterwillcontainanoverviewofhowtotrackpeopleusing Wireless802.11radiofrequencies(Wi-Fi)andBluetooth802.15radio frequencies.ThecontentcontainedherecamefromresearchandmaterialsoriginallypresentedatDefconWirelessCTFVillageinAugust 2015entitled “MeetingPeopleViaWi-Fi.”
Wewillgooverthehardwareandsoftwareneededinordertodo thistracking,howtousetheseparticulartoolsinordertodoattribution,andtipsforprotectingyourselffrombeingattributedviathose signals.
CHAPTER 1 1 Overview:ScanningforDeviceAssociation Overview Attacker Source: https://openclipart.org/
Everydaypeopleuseallkindsofdevicesthatemitradiofrequencies (RFs)thatprovideidentifyinginformationaboutthem.Overtheyears, governments,privateinvestigators,andradioenthusiastshavedesigned andcreatedtechniquestotriangulateandidentifyindividualsforthe purposeofcatchingillegals,findingmissingpersons,shuttingdown radiointerference,aswellasinterceptingcommunications.
Thedevicesusedeverydaytomakecommondatacommunications allowustoconnecttotheInternetorinternalnetworksinourhome, work,orcar.Manyofthesehelpusbemoreproductive,safer,and stayintouchwiththoseweknowandlove.However,witheveryconnectionwemake,thereexiststheopportunityforsomethingcalledRF signalleakage.
RFsignalleakageoccurswhensomeoneotherthantheintended recipientreceivesaRF.Thismaybeattackerrelated,suchasrunning ascannerorinterceptor,oraccidentallikewhenacordlessphoneor radiopicksupanothercordlessphoneusingthesamechannel.Either waythisgivessomeonewithnefariousintentionsanopportunityto
profileandtracktheirtarget’sdailymovementsand,insomecases,the possibilitytointercepttheircommunication.
RFsignalleakageisnotlimitedtoaudiotransmissions,itcanaffect dataandvideotoo.IfHigh-DefinitionMultimediaInterface(HDMI) cablesorexternalkeyboardsusedinatarget’shomeorbusinessconsist ofunshieldedcables,thenRFsignalleakagecouldpresentaproblem.An attackercouldlistentoanddecodetokeystypedorreplayanddecode imagestransmittedviatheHDMIcable.Thisiswhymanykeyboards, suchastheLogitech,nowencrypttheircommunicationswithencryption standardssuchasAES(Logitech,Inc.,2015).Evenwithencryption though,someoftheunderlyingtechnologyindicatorslikedevicetype anddistancefromthesnifferorscannercouldbedetermined,asthesefactorspresentthemselvesinordertoestablishtheconnection.
Anotherexample,thesmartphone,presentstheopportunityforseveralvectorsofprofiling.Some,butnotall,wouldincludecellphonesignaltransmittingviaGlobalSystemforMobile(GSM)orCodedivision multipleaccess(CDMA),theprobingforWi-Fihotspotstosaveondata ratesorBluetoothtoconnecttoexternalperipherals.Allofthesedifferent RFsignalscanessentiallybeusedtoidentifyapersoninagivenspace.
Thiscanbeaccomplishedthroughtheuniqueidentifiersthattellthe network,beitcelltowers,Wi-FI,orpointtopoint(P2P)Bluetooth, whichallowthedevicetosendandreceivethecommunications.For example,eachSIMcardcontainsauniqueidentifierthattellsthe towerwhoyouaresotheprovidercanknowwhatphonenumberand dataallowancetogiveyourdevicewithagivennumber.Thesameis truewithBluetoothandWirelesscommunications,exceptthosetwo technologiesnormallyuseMediaAccessControl(MAC)address.
AllcommunicationdevicespossessaFederalCommunications CommissionissueddeviceMACaddress.Thisidentifierallowsdevices tocommunicateandpreventscollisionsandpreservestheuniqueness ofadeviceonanetwork.BluetoothalsohasUUIDcodesthatitdisplaysduringpoint-to-pointassociationsearchesthatareuniqueper deviceandcouldassistinprofiling.
TheremaybeadditionalIDsandsignaturesthatcanbeassociated butallWi-Fi,Bluetooth,CellPhoneRadioFrequencies,orsome othersimilarconnections,itwillhaveaMACaddressintheformof
XX:XX:XX:XX:XX:XX,wheretheXX’ swillbereplacedwitha givenuniqueMACconsistingofhexcharacters.Theformatfor Wi-FIandBluetoothconsistsofaformatofXX:XX:XX:AA:BB:BB, wherethefirstthreehexadecimalsaresetasideforthedevicemanufacturerwhopurchasedthelicensetocreatethedevice,andthelast threehexadecimalsrepresenttheIDthatthemanufacturerassigned tothatdevice.Wewillshowlaterhowthiscanbeusedtocreatea comprehensivetargetprofile.Thisallowsanattackertocreatea profile,ordatabasekey,everytimetheyseecommunicationfrom thatdeviceaswellasgivingthemaformattolookupdevicetypein onlinedatabasesprovidedbytheFCCandothernetworkcompanies.
Itisimportanttonote(accordingtoarecentarticle www.arstechnica.com)thatiPhoneswithiOS8.0andabovehave startedtospoofMACaddresses.Basedonavarietyoffactors,the mostnotableofwhichisarebootofthephoneforces,thisprotection techniquehastobetriggered.FurtherresearchshowsaMACaddress fromaniPhoneincrementingitsaddressbyonehexdigitviaWi-Fi probeswhensearchingforanaccesspoint.
Also,whenattemptingtofindsomedevicetypes,themanufacturer codesometimesrepliedasPrivateorUnknownwhichmeansthatthey areeitherprotectedfromdisclosurebytheFCC(intheinterestof NationalSecurity),ormaybeprotectedunderdevelopmentlawsforthe interestofprotectingpatentsornewtechnologies,asexplainedbyJohn Abraham,thecreatoroftheAndroidBluetoothscanningtoolBlueScan.
Beforewecontinue,let’sclarifythatallofthisprofilingcanbe donebymeanscoinedunderthetermof “WarDriving,” atermfirst establishedbyPeterShipleytomean “togooutandsearchforopen wirelessLANS.” Theactofwardrivingislegal;theactofbreaking encryptiononnetworksisnot.Iftheattackerweretodecrypt encryptedcommutationswithoutpermission(exceptionsfrompermissiongivenbythetarget,oracourt-issuedorder),thiswouldinmost courtcasesbeillegalbecausetheattackeristhenbreakingthebasic conceptscontainedwithinlawssurroundingreasonableexpectationof privacy.Theconceptsandtechniquestalkedaboutlaterwillfocuson legalmeansforconductingsurveillancewithouttheneedforconsent orpermission.Thatbeingsaid,becauselawschangeandaredifferent fromplacetoplace,ifyouhaveconcernspleasecontactanattorney.
ThetwomostcommonRFsignals,Wi-FiandBluetooth,cantell usenoughaboutasuspectthatwouldallowustoseewheretheyhave been,whotheymayhavecommunicatedwithandmakeinferences abouttheirexactcurrentlocationsandhowmanytimestheyhavevisitedthelocation.Allofthesecommunicationsallowanattackerto knowsomethingaboutthetargetthatcanbecategorizedasradiosignalleakage;andprettymuchanydevicehasittosomeextent.
MosttimesWi-FicommunicationisaresultofanattempttoestablishInternetconnection,ortransferdatatoabasestation(suchasa homerouteroraccesspoint)connectedtoabackbone,whichhasties withaphysicallocation.Knowingthenameofthebasestation’ s Service Set IDentifier,orSSID,allowsfortheabilityforsomeoneto lookupinadatabasetheuniquenameofthatbasestationandallows theattackertoknowwherethetargethasvisited(PCMagazine Encyclopedia.22October2015).
Additionally,point-to-pointcommunicationssuchastethering whensomeoneusestheirphoneforInternetaccessonalaptoportabletpresentstheabilitytodetermineotheridentifiers.Forexample,if theattackersawthatsomeonehadconnectedtoahotspotnamed “VerizonMifi877624” theycouldinferthatthetargetusesVerizon. Thiswouldallowthemtostageadditionalattacksorpotentially figureoutwhoismakingthosecommunicationsbasedonphysical activitiespresentintheenvironment.
Bluetooth,ontheotherhand,normallyshowsitselfthroughpointto-pointconnections;ithasalowerrangeandcanbeusedtohelppinpointatargetordetermineiftheyhavebeentoalocationbefore.
Forexample,youcouldputaBluetoothscanneroncellphone pluggedintothewallthatislocatednearanentrancetoabuilding. FromtheBluetoothMACaddressofalltheuserswhopassthrough, youcouldfindoutwhatpercentofemployeeshaveBlackBerrys, iPhones,orAndroidDevices.Theattackercouldalsoprofileandlog physicalfitnessdevicesthatpeoplewearthemselves,suchasaFitbitor Garmin,sincethesegadgetstransmitviaBluetoothtothephonein ordertohelpunderstandwhat’sgoingonwiththetarget’sbody.Every devicesomeonecarriesisjustanotherdatapointthatallowsthe attackertodeterminesomethingaboutthemorthepeoplewhotravel inthesamegroupasthem.Ifanattackerdidthisfordaysatatime,
hecouldpairitwithCCTVinformationandbuildadatabaseofall usersandtheirdeviceprofiles.
Additionally,thisprofilingcouldbeusedtodeterminewhocomes toworkontimeorwhensomeonedoesn’tshowuponacertainday.If anattackercreatedadatabaseofallthelawenforcementofficersor securityguardswhogoinandoutofagivenbuilding,theycouldlater keepadeviceonthemthatalertedthemtothepresenceofaguardor officerwhentheycameclosebyidentifyingtheirFitbitorcellphone (thattheykeeponthematalltimes).
Theproblemisthatweneedtheseinordertogoaboutourdaily lives.YouhavetouseitinordertoconnecttotheWi-Fihotspotat work,home,orintheairportorcoffeeshop.YouneedBluetoothin ordertotalkonthecellphonewithouthavingyourhandsleavethe wheel.Youcanencryptyourconnections,usingaVPNorSSLencryption,butthisdoesn’tstoptheidentifyingvectorsfromhavingRFsignalleakage.
WhatistherealvalueofcollectingtheMACaddressofadeviceofa target?Well,thiswouldbeimportantinformationiftheattackerwere goingtofollowupthatinformationwithaspearphishingcampaignor SMSattackonphonenumbersassociatedwiththeorganization.When youhavetheMACaddressofadeviceyoucandetermineanswersto thequestionssuchas:IsitaniPhone?OranAndroid?Manytimes exploitsaretargetedatspecifictypeofphoneordevice;knowingwhata companyemployeesusedaytodaycouldallowthemtopurchasethe rightexploitsordevelopanattackwithagreatersuccessrate.
GovernmentsandIntelligenceagencieshavedesignedSCIFs, SensitiveCompartmentedInformationFacilities,toprotectcommunicationsfromleavingthesecurefacility.Whataboutthenaming schemesofthewirelessatotherpartsofthecomplex?Ifthehotelon basesays “Base1215-USAF-Wi-Fi,” wecannowfigureoutwherethat employeeisstayingandbyotheropen-sourceintelligence(Google Maps,MicrosoftMaps,YahooMaps,etc.)maybeabletoguesswhere theywork.Researchshowsthatmanyhotels,schools,andotherplaces thathavelargenumbersofuserspubliclypostinstructionsforhowto gainaccesstothenetworkinPDFsorinstructionalwebsitesonline. Theseinstructionsareindexedbysearchengines,whichthenallows foreasycorrelationtoagivenlocation.
Weneedtolearnwhatdataleakagewehaveinordertounderstand howvulnerableourdevicesmakeusandlearnhowtoprotectourselves alittlebitbetter.
WhenitcomestoWi-Fi,everysingleWi-Fiaccesspointyou’ ve everconnectedtoisstoredinanaccesslistonyourcomputerorcell phoneorotherdevice.Thinkofitasawebhistoryforyournetwork connections.Theadvantagetokeepingthisinformationisthatit allowsyoutoconnecttoanetworkwithouthavingtotypeinyour passwordagainorrememberwhatthenameoftheWi-Fiaccesspoint wasforthatparticularlocation.Thedisadvantageofthisisthatthey broadcasttheSSIDthatyouaretryingtoconnectto.
Forinstance,wemighthaveahotellobbythatthetargetpreviously connectedtobutevenifIwasn’tinthatlocation,mycomputerwould say, “Hey,ishotelwifi1lobbyaround?” Anditwouldattempttoconnect tothoseandtelleveryonearoundthatthetargetislookingforthatparticularWi-Fihotspot.Asanattacker,wecanpickthesecommunications upusingspecifictoolsandgainattributionaboutthepersonsattempting tomakethoseconnections.Theseparticularwirelesshotspotnamesor SSIDscangiveawayinformationaboutwherethetargetlives,works,or eventhenetworksoffriendswhohaveconnectedtointhepast.
AsimilarthingcanalsobedoneforBluetooth.Indiscoverymode, whentwoBluetoothpiecesoftechnologyareattemptingtoconnectto eachother,theywilldistributetheMACaddressordiscoveryinformation,aswellasotheridentifyingfeaturesoftheparticulardevice.And eveniftheyaren’tindiscoverymode,whichistheset-upprocessfor Bluetoothdevice,theyarestillattemptingtoconnectandfindother Bluetoothdevicesintheareathattheypreviouslyconnectedto.Thisis goodfortheattacker,sincetheycanjustlistenanddon’thavetoalert thetargetthattheyarepickingupthedevice.Theattackercanalso usesomethingcalled “decibel” toguessthedistancetheyarefromthe target’sdevice.Decibel,whenitpertainstoRFs,ismeasuredinnegativenumbers,unlikethedecibelforaudiowhichispositivenumbers. Thecloseritistozero,thecloserthescanneristotheactualtarget device.Anattackercouldthenusetriangulationtolocatethetarget.
TherearethreetypesofBluetoothtechnologythatarecurrently beingusedtodayinversion4.0ofthespecineverydaydevices. Bluetoothinclass3radioshasarangeof1mor3feet.Class2radios,
whichgenerallyyouwillfindinmobiledevices,havearangeof10m or33feet.Andfinally,Class1radios,theonesthatareusedinfactoriesorotherindustrialareasinordertotrackshipmentsorotherpieces ofequipment,haveamuchlongerrangeofabout100mor300feet (BluetoothSIG,Inc.,2015).
Class3BluetoothisalsoknownasLowEnergy.Generallyyousee thisinlong-termBluetoothsensors,suchasonafirehydrantorafire extinguisher,orstoredsomewhereinabuildingwhereyouarenot goingtobeusingiteverysingledaybutyouwantittolastforyears, anditwillhavesomethinglikea9-voltora5-voltbatterythatdoesn’t needalotofchargeinordertopowerit.
Class2hasbeenreferredtoas “Classic.” Thisistheonewethinkof todaywhenwehaveouriPhonesorAndroidsonandsendpicturesto eachotherusingBluetoothorcommunicateusingaheadset.Thisrequires alotmorebatterypoweranditwilldrainmorequicklybutithasalot morefeatures.WealsoseealotofiPhonesandAndroids,andsometimes weseeentertainmentsystems.IfIwasinanapartmentcomplexwhere peoplehavevariousdevicesthattheyareusinginordertostreammusic, I’llsometimespickupthosedevicesandbeabletosharesomefeatures aboutthem.It’snotasusefulasaFitbitoniPhone,whereIcantrackthe personastheymovearoundaparticulargeo-demographic,likeasubway ortheirhome,butitdoesgivemesomecontextandsomeinformation thatIcanuseinordertofiguresomethingsout.
DB to Distance Ration
Imentionedthatweusedecibelsinordertofigureouthowclosewe are.Noticethatifweweretographthisrelationshipout,atzeroweare veryclosetothedevice.Andasthedecibelsbecomefartherawayfrom zero,thedistancebetweentheattackerandthedevicealsoincreases.
Overview: Scanning for Device Association 100 meters Class 3 radios – have a range of up to 1 meter or 3 feet. Class 2 radios – most commonly found in mobile devices – have a range of 10 meters of 33 feet. Class 1 radios – used primarily in industrial use cases – have a range of 100 meters or 300 feet. Basics | Bluetooth Technology Website www.bluetooth.com/Pages/Basics.aspx
Thisishelpfulforknowinghowclosetothetargettheattackeris basedonthetechnicallimitationsofthedevice.Otherfactorstoconsiderareweatherconditionswhere,forexample,humidityandrain restrictssignalranges,aswellasbuildingsandwalls.
ThegoalofBluetoothishoning again,veryclosetothetarget whileWi-Fiisforlongerranges.Wehaveseveraldifferentversionsof Wi-Fi.ThereisA,B,G,andN,aswellasAC,allhavingvaryingdegrees ofdistance.Alloftheseareintheformofthestandard802.11x,wherex istheappendingletterofthestandard.Ifanattackerpositionedinabusy malltotracktheirtarget,inmostcasestheywouldbeabletofindthem relativelyeasily.ComparethattoBluetooth,whereyouwouldonlyneed tobeinthesameroomorsamestoreasthatparticularindividual.
OtherfactorstounderstandarethatifyouaretryingtopickupAC signalswithaBorGdevice,inmostcasesunlessthedevicechecksthose otherfrequenciestheattackerwouldmissthosesignalsbecausetheywork ontotallydifferentfrequencies.Also,eachletterhasdifferentchannels, forexample,Ghas1-11intheUnitedStatesanduptochannel14inother countries.Whenanattackerisscanningthedevice,theycanonlylistenon onechannelatatimeandtheprocessofcollectinginformationfromall thechannelsiscalledchannelhopping.Topreventmissinganything, ifpossibleuse4cardson1,6,and11and14(ifapplicable).Thatwaythe cardwon’tmissactivityonchannel1whenitishoppingtoahighchannel like7or8.
CHAPTER 2 2 HardwareandSoftwareNeeded Hardware Needed - Wifi Inthisbook,wearegoingtodiscussatoolcalledtheALFA 802.11b/gRTL8187chipset.Thisparticularpieceofequipmentis reallyversatileandisusedbyalotofpentestersbecausethereisan importedversionthatworksonAndroids.Ilikeitbecauseitisrelativelysmall;IcanfititinmypocketandIcanbeinconspicuouswhen I’mgoingaboutscanning.Italsoworksinapromiscuousmodeon LinuxandWindowsinordertoallowmetopickupthingsthereifI sochoose.Forexample,ifIwasinacoffeeshopImightbeableto useitontargetsusingAndroiddevices.
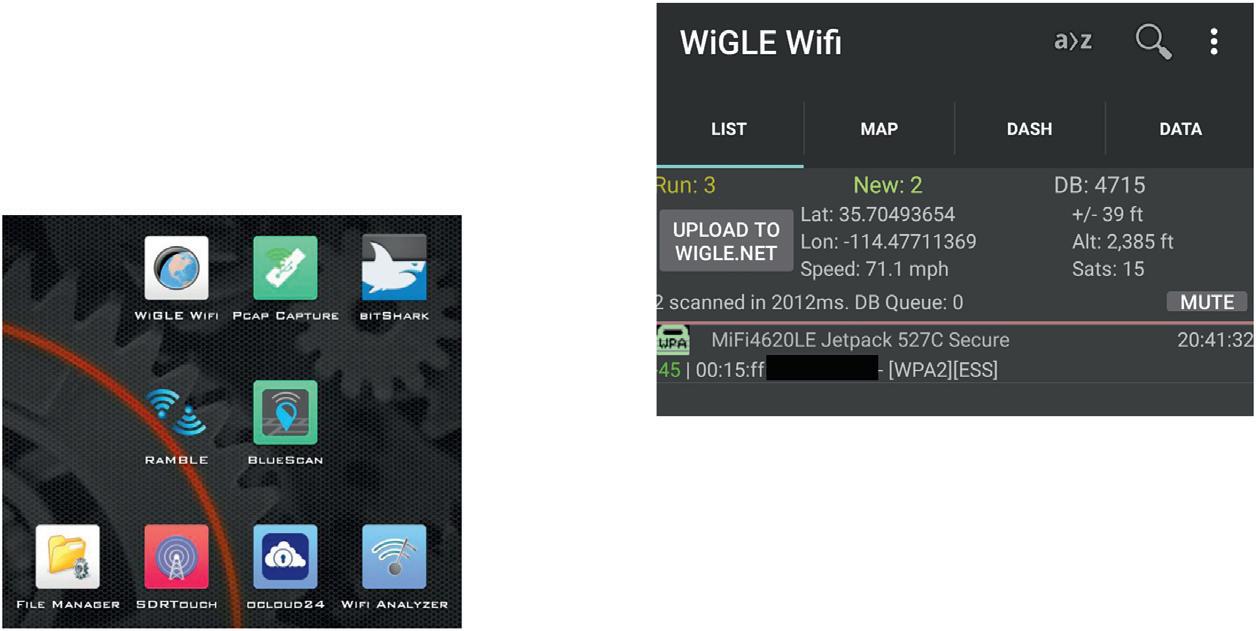
Hardware Needed - Wifi Showing Today on Linux and Android + OTG Adapter Inmycasestudy,wewilluseaLinuxlaptop,anAndroid,andan OTGadapter,whichstandsfor “OnTheGo” adapter.WhattheOTG adapterallowsustodoisplugtheUSBcableoftheALFAcordinto theAndroiddevice.SoyouplugtheOTGcableintothebottomwhere youwouldchargeitandthenyousequentiallyplugtheactualALFA cordintothatandnowyouareabletouseaparticularWi-Fiscanning toolontheAndroidusingthatexternaldevice.Asfarassoftware needed,we’regoingtouseWigleWi-Fiforwhat’scalledwardriving. Thiswillallowustoaccessthedatabaseofpreviouswardrivesand pickuptheaccesspoint.
Essentially,peopletraveltheworldandpickupaccesspoints,log thegeolocation,anduploadthemtotheWigleWi-Fisitesothatpeoplecansearchitandseewherethataccesspointwasfound.Thisis reallyhandyifweweretosearchforanareaandseeaparticularSSID thatwaslocatedinJapan,becausewecanactuallyusepeoplethat havedonewardrivinginJapan,andwecannowdothecorrelation withouthavingtogothere.Inthesamecases,wecanaddourdata andpeopleinothercountriesorotherareasoftheworldcanactually lookatthedatathatwescannedandwhataccesspointswerepicked upandwheretheywerelocated.
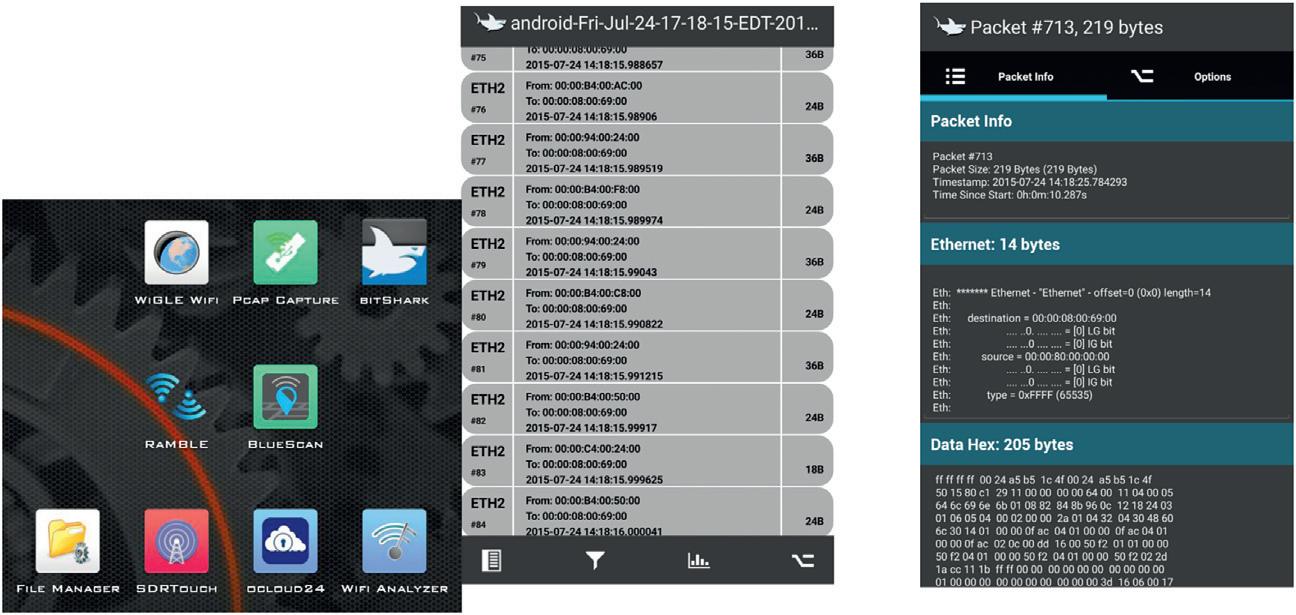
TheothertoolthatwearegoingtouseisaPacketCapture(PCAP) Scanner,whichisessentiallyaKismetporttotheAndroid.Kismetisa toolthatallowsforscanningandcapturingPCAPs,alltheWi-Fidata intoaparticularfilesothatwecangobacklaterandseewhatwas actuallybeingcommunicatedattheaccesspointsIattempted. BitSharkShareisapaidwirelessPCAPtoolthatisavailableon
Android;it’sabout$3.00,andIfinditveryhelpfulforwhenyouare actuallydoingthePCAPscanning,tobeabletomakesurethatitis actuallyworkingcorrectly.Essentiallyit’sWiresharkforAndroid.So ifyouweregoingtousealaptop,Iwouldrecommendeitherusing KismetorAircrack,bothofwhichworkonLinuxorWindowsfairly seamlessly.IfyouhaveaMAC,IwouldrecommendgettingaLinux VMorWindowsVMandusingitonthere.Inmostofmytesting,I havenotbeenabletofindatoolthatworkswellwithMACsoit’ seasiertopurchaseaconnectionbetweentheALFAcordandtheVMand justdoitthere.Thatbeingsaid,onceyou’veactuallycapturedthe PCAPusingAircrackorKismetorevenAndroid,youcanuse WiresharkortcpdumponMAC,Linux,orWindows.
Software Needed - WiGLE Wifi HereisanexampleofcapturesthatIwasdoing,withsomeWar DrivingwithWigleWi-Fi.Asyoucanseeinthetopleft,youhavea WigleWi-Fiicon,andonceyouclickonthatyouopenupadashboardanditallowsustoseelatitude,longitude,andspeedofthemovingdevice,andaltitude,andtheSSID whichinthiscasewasa JetpackMIFIprovidedbyVerizon.TheMACaddressofthatdevice isvisible,andalsointhebottomlefthere,wehavethedecibelthattells ushowclosewearetothedeviceanditwas 45.Italsoshowsthe timingofwhenwesawthisdevicefirst,anditallowsustouploadthat tothewebsothatwecanactuallyhaveitforlatertrackingandprovideittoothersaswell.
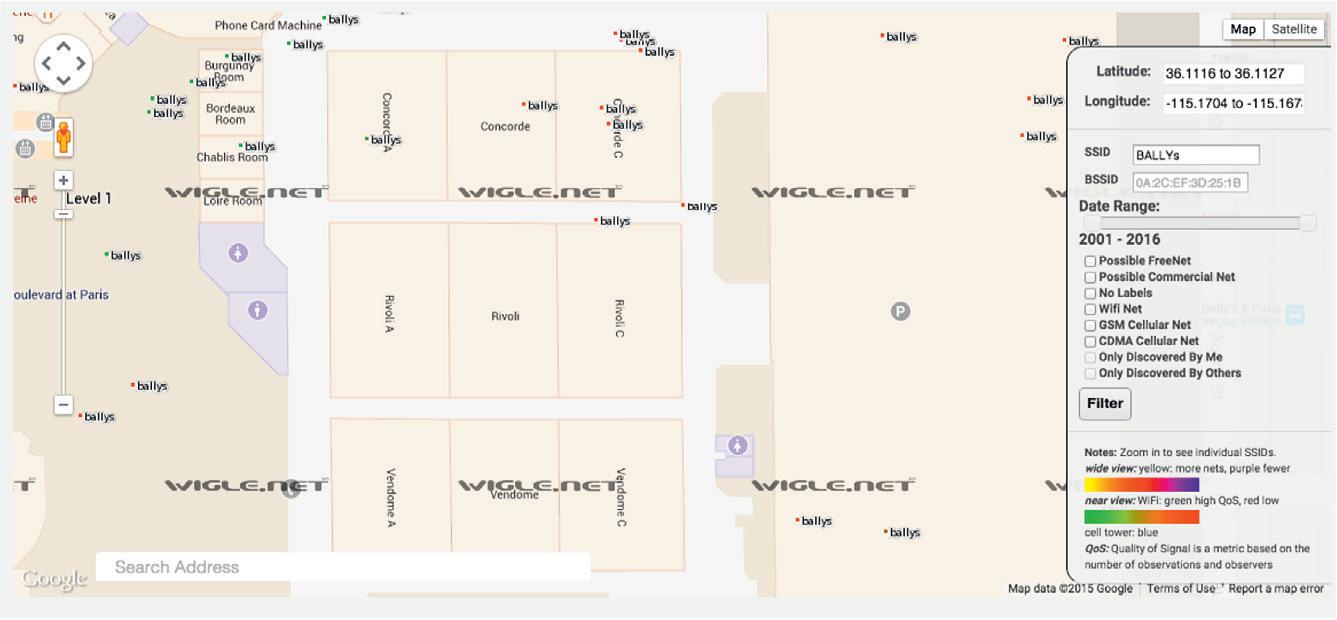
Software Needed - WiGLE Wifi Hereisanexampleofwhatitlookslikeafterweuploadthedata. Inthisparticularinstance,IwasatBlackhatandIwasdoingsome searchesforSSIDsrepresenting BALLYS Wi-Fi,thehotelhostingthe conference.Youhavelatitudeandlongitude,andyoucanalsoseethe rangeofdata.Noticethattheyhaveactuallybeendoingthisfora very,verylongtime,backfrom2001allthewayuptothemhaving thedatabase,to2016.Youcandovariousfiltersonitandyoucan alsosearchbyaddress(seethebottomleftoftheimage),andI’lltell youhowthat’shelpfullateron.
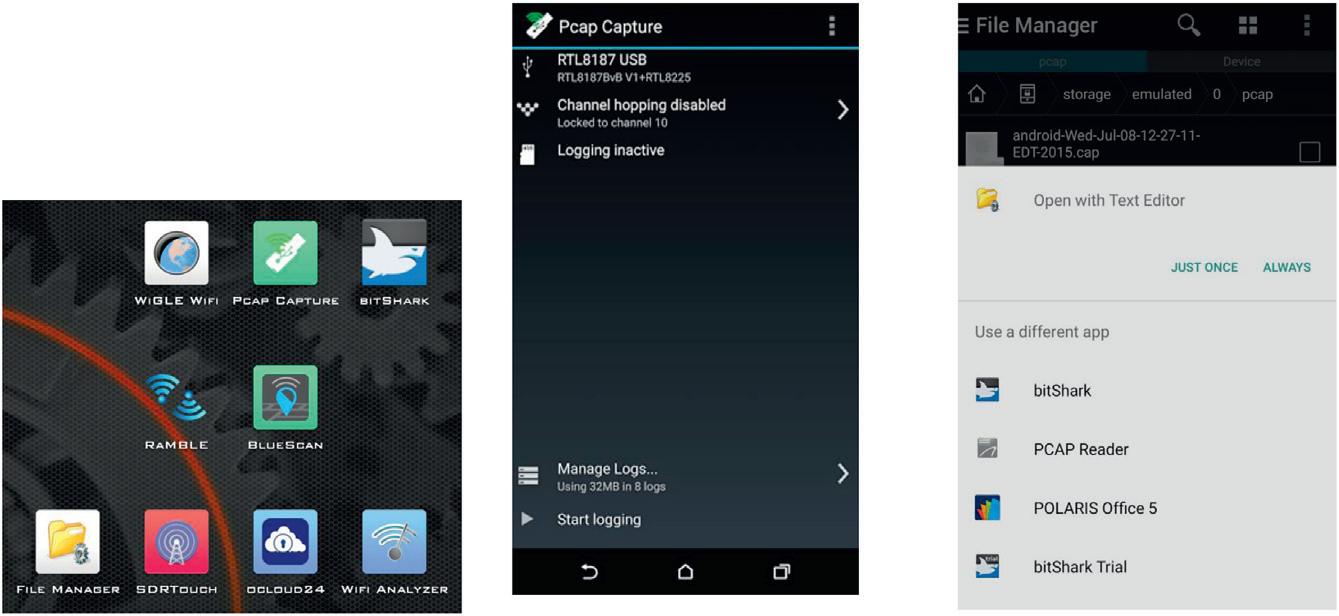
Software Needed - PCAP Scanner HereisanexampleofPCAPcapture.Theiconforthatisinthetop middle.WehavetheRTL8187alreadyconnected,andyouhavethe optionofselectingachannelsothisisalittlemorehelpfulifyou
actuallyknowtheSSIDandwhereit’srunning,butgenerallyI’llleave thistojustdowhat’scalledchannelhoppingsowehavenorestrictions thereandwegetallthetrafficwewant.Wegoaheadandclickstart logging,andwecanalsolookatpreviouslogsorcurrentrunninglogs inthemanagelogssection.Overhereontheright,thisiswhatthe managelogsectionlookslikeandwecanexportthatdatatoanyapp ontheAndroidthatsupportsPCAPsortextediting.
Software Needed - BitShark Scanner Inordertoverifythatthefilesareactuallyworkingcorrectly,here isanexampleofBitSharkScanner.Noticetheiconforthatisinthe topright;inthemiddlewehavethemenuscreensowehaveeth2, whichistheEthernetportthatwasconnectedatthattime.Wehave thetimeanddateaswellasMACaddress,andwehavethesizeofthe actualpacketsthatwerecaptured.Thisshowsnumber713,thesizeof thePCAP,anditshowsframeddetailsandHexinformation.Wecan actuallyseethatthePCAPisbeingcommunicatedsuccessfully,and weareabletocaptureitaswell.Italsohasmultiplefilters(although wedon’twanttonecessarilydiveintothatinthisbook).
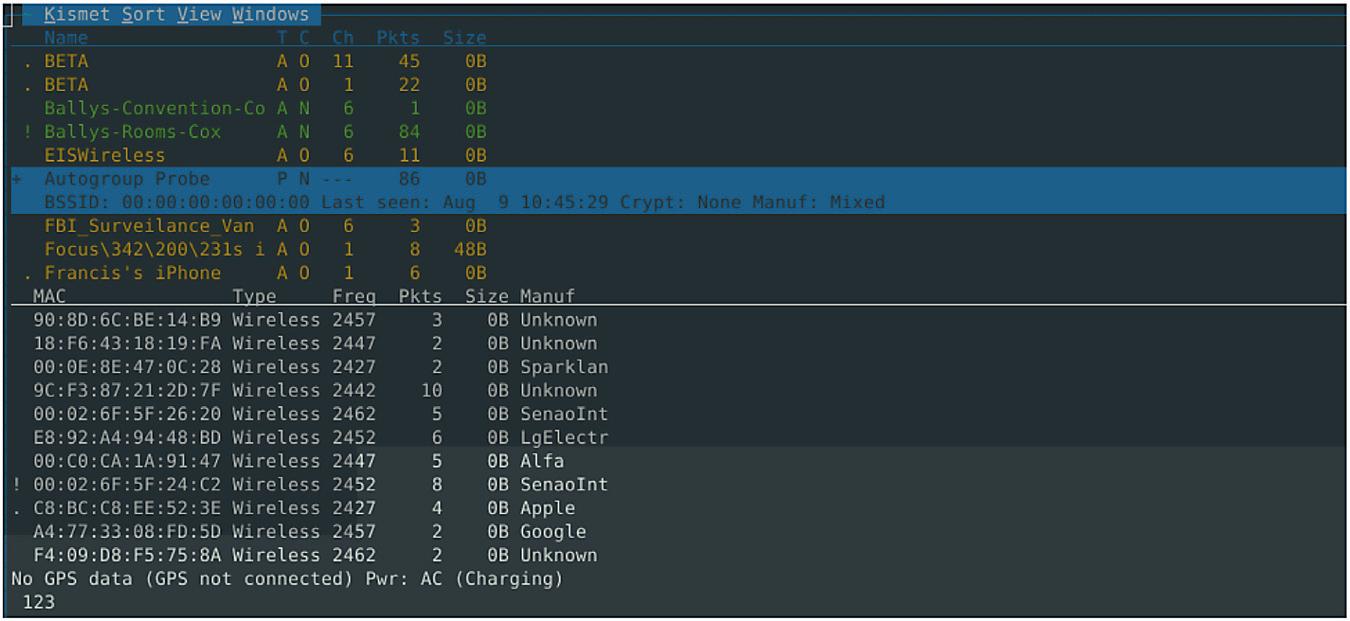
Software Needed - Kismet Ifyouaregoingtoactuallydoacaptureonalaptop,Iwouldrecommendonlydoingthatwhenyouareinanenvironmentthatcondones laptop.Soifyouwereatacoffeeshoporyouworkwheretherearehotspotswherepeoplearealsoworkingonlaptops,onlydoitthere.Ifyou areoutinthemall,youdon’twanttocarryaroundalaptopbecause thatmightlookcreepy.Inthissituation,wehaveselectedtheauto probegroupandessentiallythisshowsusseveraldifferentdevicesthat areattemptingtoconnecttoSSIDsbuthavenotsuccessfullyconnected. WehaveanAppledevice,wehaveanAndroid,andsomeonewasusing anALFAcordaswell.Wecanparsethroughthis,andit’sallbeing recordedinaPCAPthatwecanlatergobackthroughandparse.
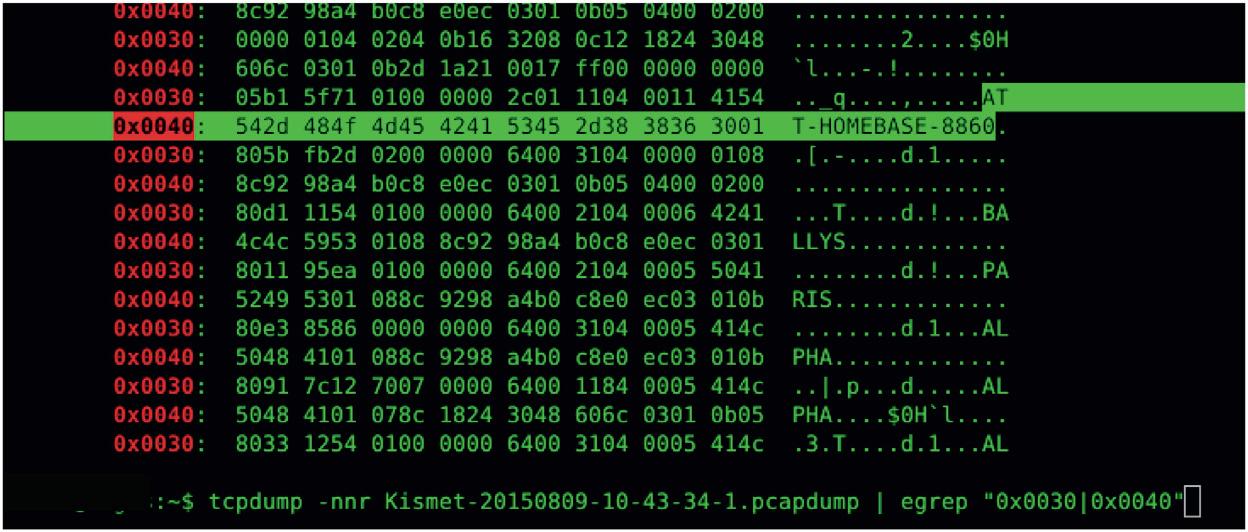
usingthegrepcommandtoparseoutaparticularhexpositioninthe fileof0x0030and0x0040whichcontaintheSSIDofthedevicethat wastryingtoconnect.Itwasaparticulardevicetryingtoconnectto AT&Thomebase8860.OtherSSIDsthatshowupinthePCAPcapture were BALLYS,and ALFA.
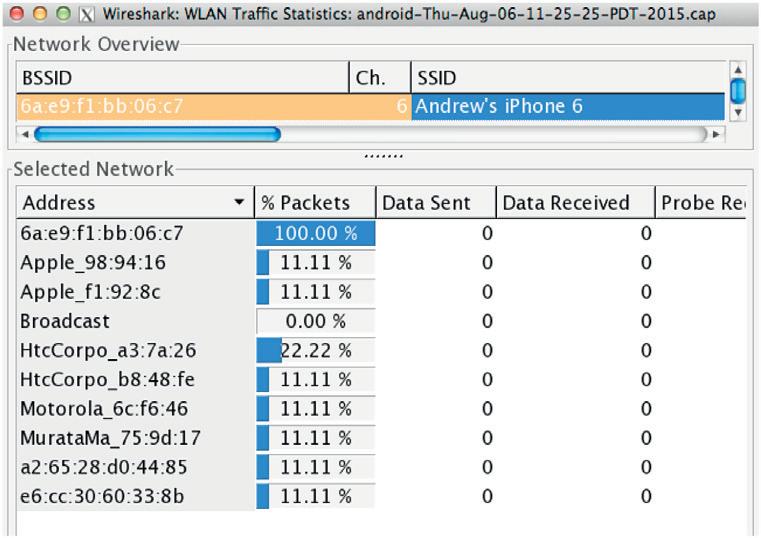
Software Needed - Wireshark/tcpdump Statistics -> WLAN Summary Make
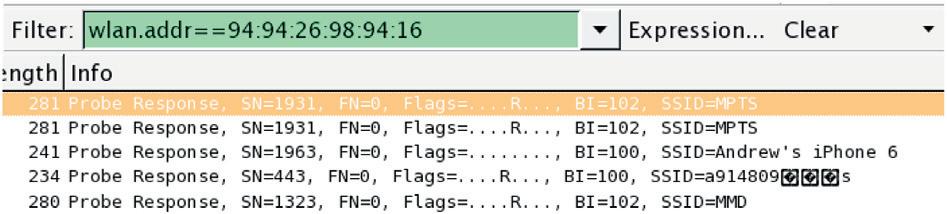
UsingthecommandlinetoparsePCAPscanbekindofmessy,butit isimportanttounderstandhowtoparsethingsoutanduseitonthe commandlinesoifthereisanerrorormissingdatayoucanadjustfor it.IfyouwanttousetheGUI GraphicUserInterface Wiresharkis agoodsolution.Inordertogetthesameinformationandparseit,from thedropdownmenuclick “Statistics” andthen “WLANSummary” . Thatwillgothroughandtakeafewminutestoparse,butitwillshow alltheSSIDsthatotherdevicesareattemptingtoconnectto.Inour samplePCAP,someonewastryingtoconnectto Andrew’siPhone6. ThismostlikelywasatetherediPhonesomeonewasusingforInternet. Sothisshowsawholebunchofdevicesinthelisthere,butwecanactuallymakeafilterforthisMACthatwasattemptingtogoto Andrew’ s iPhone6 andfindoutwhatelseitwasattemptingtoconnectto.
Software Needed - Wireshark/tcpdump Statistics -> WLAN Summary
Oncewemakethefilter,wecanuse “wlan.addr 55 XX:XX:XX:XX: XX”,whereXX:XX:XX:XX:XXistheMACaddressoftheassociating device.ThiswillpresentaviewshowingwhatotherSSID’stheuserwas tryingtoconnectto.InoursamplePCAP,wesaw MPTS twice, Andrew’ s iPhone6,and MMD.Nowwehaveallthedetailsthatweneedinorderto startfiguringouttheattributionofwhoAndrewreallyisandwhereheis from.I’mnotgoingtogointotoomuchdetailherebecauseIhavesome otherinterestingcasesbutIwouldrecommendyoutrythisathomewith yourowndevicesandseewhatnetworkstheyaretryingtoconnectto. Chancesareyouwillseeyourhomenetworkaswellasmaybeyourwork, andafewotherlocationsyouhavepreviouslyvisited.
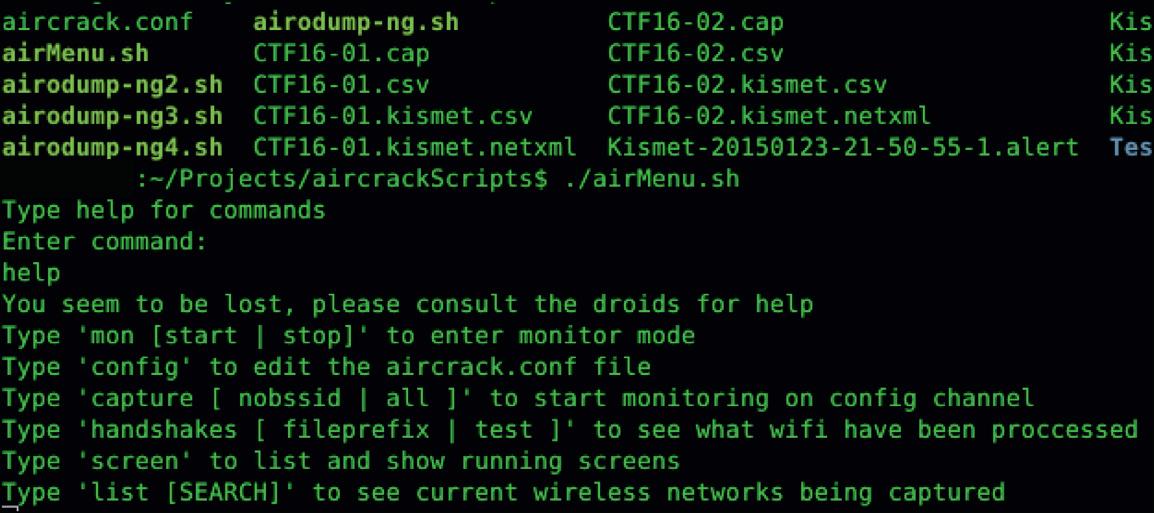
Software Needed - Aircrack/AirMenu Source:http://www.aircrack-ng.org | https://github.com/joshingeneral/airMenu
InordertocapturethewirelessPCAPsonalaptopwecanuseatool Aircrack.AircrackgenerallyisusedforcrackingintoweborWPAnetworks;however,itdoescapturePCAPssoitcanbeusedtoactually parsetheinformationoutandithasaslightlydifferentinterfacethan Kismet,whichsomeofyoumightfindalittleeasiertounderstand.
ThefirstscriptthatIwrotewasonethatdoesaswitchingofthe cordfromregularmodeintomonitormodesowecouldactuallycapturepackets.Ithasaconfigurationfilecalled Aircrack.com,andyou canaddincertainBSSIDorchannelsinthereinordertorestrict thingsdown.YoualsohavetheabilitytocaptureallSSIDsormake restrictionshere.Youcanalsoseethenumberofhandshakes,sothisis reallyonlyusefulifyouaredoingcracking,butasImentioned,thisis anentiremenuofallthefeaturesforAircrack.
Youalsohavethe “ screen ” commandsoyoucandomultiplescans. Generally,ifIamonalaptop,IwoulduseaUSB3.0hub,I’llplug multiplecordsintothatandhavemultiplescansgoingatoncesothat IcanmaximizetheamountofdataI’mgettingandnotmisspackets, becausewhenyouaredoingchannelhoppingyouhaveatendencyto misssomething.Ifyouarelookingatchannel1whilesomethingis happeningatchannel6,you’llmissit.Themorecordsyouhave,the betterchanceyouhaveofthatnothappening.
I’mgoingtofinallylist,andyoucanseeallthescreensthatare availableandlookatthestatusupdateonthat.
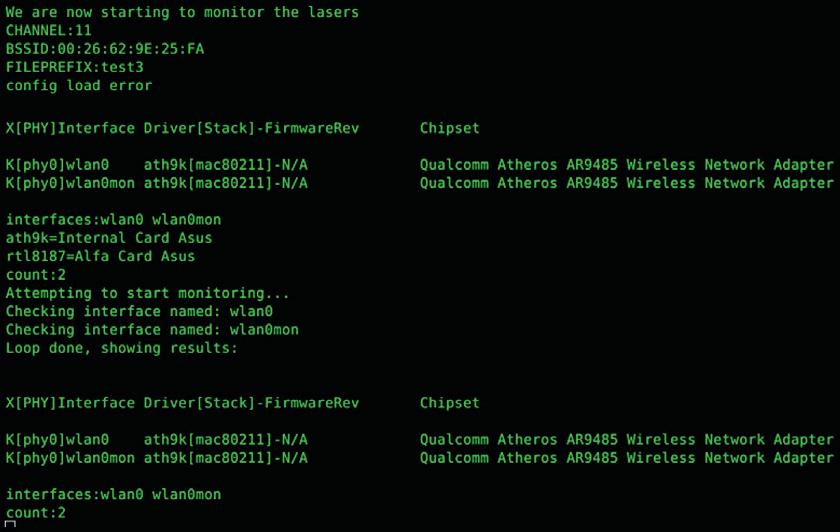
Software Needed - Aircrack/AirMenu Source:http://www.aircrack-ng.org | https://github.com/joshingeneral/airMenu
Hereisanoutputofwhatitlookslikewhenwerunthemenu. AirMenuisessentiallyjustonemenu(Schroeder,2015).Youdocertaincommandsandyouselectthedifferentpiecesfromthat.Herein thisparticularone,wehadchannel11ataspecificBSSID.Iselecteda prefixforallthePCAPstohaveastest3.IhadalreadysettheinterfacefromWLANtozerotomonitormode,soyoucanseethetwo interfacestherethatIhavetointeractwithandherearesomemore detailsabouttheactualcorditself,thechipset,andvariousother things.
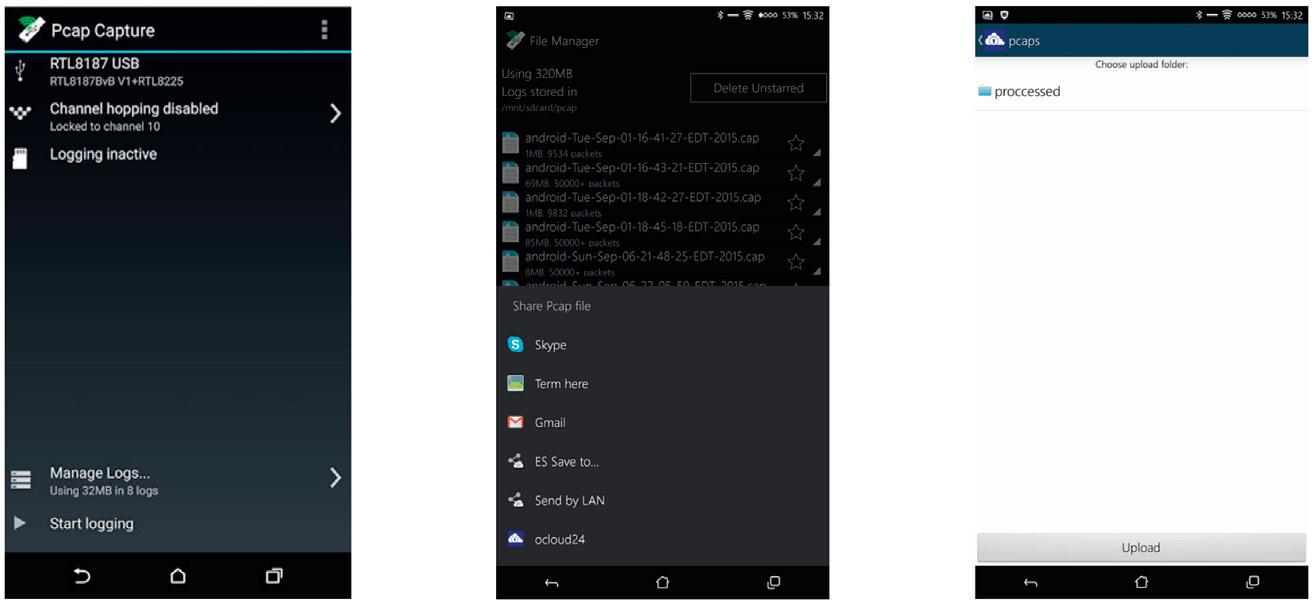
Software Needed - PCAP Scanner IalsocreatedatoolontheAndroidthatwoulddothebackend processingandessentiallyusingT-Sharkandtcpdumpinorderto figureoutwhoiswhoandgetthroughsomemoredatarightonthe Androiddevicesoyouarenothavingtodotoomanysteps.Thisisa PCAPscanner,andwehaveourALFAcordhookedupviatheOTG. We’vestartedloggingandwe’vegotseveralpacketshere,andwe foundonethatwewanttogoaheadandsendtobeprocessed.Inthis particularcase,insteadofsendingasanemailoropeningatextitem, I’mjustgoingtosharethePacketCapture(PCAP)withOwnCloud. OwnCloudIhavemountedonaLinuxVM,andthatwillessentially allowmetorunthisparticularscript.
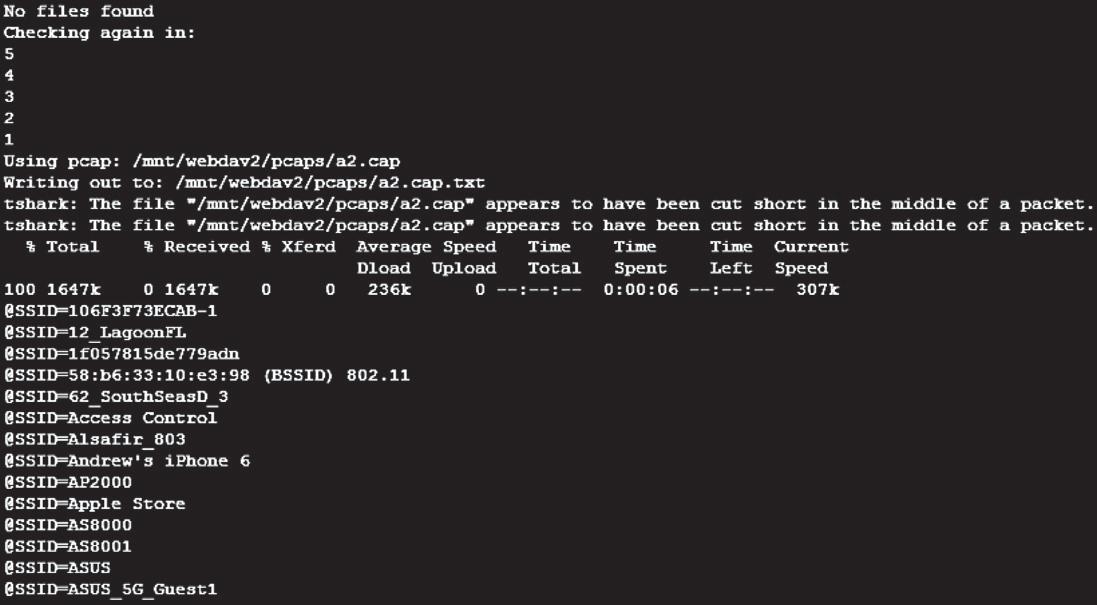
Software Needed - Bash Script Thisscriptchecksevery5secondsfornewPCAPsinaparticular PCAPfolder,anditparsesthemout.Inthisparticularone,itsays there’sanerror,it’sbeingcutshort;essentiallywhatthatmeansisI wasactivelyscanningataparticulartimeanddidn’tclosethePCAP outproperly.Itdoesn’tmeanthatyouwillloseanydata;itjustmeans thatT-sharkisgivingalittlewarningonwhat’supwiththatpacket.
HereisalistingofalltheSSIDsthatsomeoneisattemptingtoconnectto,soIquicklylistthatoutandsortsoyoucanseeinalphanumericsortingandfindtheonesthatareofinteresttoyou.Soonce againhereis Andrew’siPhone6.
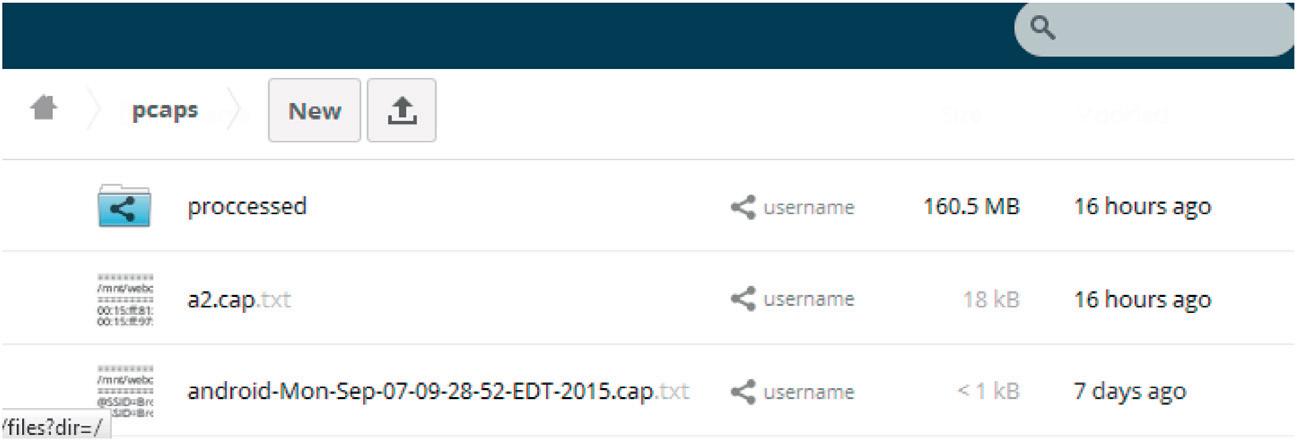
Software Needed - OwnCloud AndhereisanexampleoftheOwnCloudsetup.Noticethatwe haveaprocessfolderandwehavetwoPCAPsherethatwe’vealready processed,andanytimewehaveanyPCAPinhere,essentiallyitgoes throughthescriptandthenwemoveittotheprocessfolder.
Software Needed - Bash script output 514 f0:24:75:87:07:83,->,Marriott_GUEST (Apple)
515 f0:25:b7:4e:dd:c6,->,Broadcast (SamsungE)
516 f0:6b:ca:12:c8:5f,->,Broadcast (SamsungE)
517 f0:6b:ca:13:b1:49,->,Broadcast (SamsungE)
518 f0:6b:ca:1a:fe:f6,->,Broadcast (SamsungE)
519 f0:99:bf:0d:c5:54,->,MathNerdz2.0 (Apple)
520 f0:99:bf:1e:3f:ab,->,Broadcast (Apple)
521 f0:99:bf:3c:f2:45,->,Broadcast (Apple)
522 f0:99:bf:3c:f2:45,->,LAWSON_Wi-Fi (Apple)
523 f0:99:bf:3c:f2:45,->,Marriott_LOBBY (Apple)
524 f0:99:bf:3c:f2:45,->,URoad-64E19C (Apple)
525 f0:99:bf:3c:f2:45,->,VIAINN_NAGOYA (Apple)
526 f0:99:bf:3c:f2:45,->,shinsaibashi (Apple)
527 f0:99:bf:84:82:47,->,Broadcast (Apple)
528 f0:99:bf:84:82:47,->,T-Mobile Broadband26 (Apple)
529 f0:cb:a1:0c:65:15,->,Broadcast (Apple)
530 f0:db:e2:46:c5:41,->,Broadcast (Apple)
531 f0:db:e2:51:d9:e4,->,Marriott_GUEST (Apple)
532 f4:09:d8:ac:41:11,->,Broadcast (SamsungE)
Thisimageshowsanexampleofwhattheactualoutput.Wehave lineitemshereoverontheleftbecauseIopenedit.Wehaveindividual MACaddressesthatwouldhavebeensortedinthesecondpartofthe scriptsothatwecanactuallydocorrelationshere.You’llnoticethata lotofthesefirstonesarejustnotthesameandthatdoesn’treallyhelp ustoomuch.Wehavesomebroadcastingherewhichisjustmerely checkingwhat’saround Marriottguest,MathNerdz individual accessdevicesareactuallylookingatthose.Then,wehavethisparticulardevicehere,whichhasthesameMACaddress,andit’sconnecting toseveraldifferentpoints.Sothisisviabledata.Wecantellit’ san iPhonebasedontheMACaddress;wewereabletoprocessthatvia WireShark,andithasaprettygooddatabase.
Software Needed - Bash Script 1.Defines paths, most of which are mounted on owncloud (No filesize limits)
2.Parses SSID, and MAC’s of devices using tshark
3.Builds Header
4.Updates mac address database from wireshark
5.Matches mac addresses with that database
6.Prints all output as SSID, devices mac address association, and vendor type
7.Code: https://github.com/joshingeneral/airMenu
Essentially,firstthingitdoesisitparsesthepaths,definesthem, seestheonesthataremounted,anditparsesoutSSID,MAC addressesusingtshark.Itbuildsaheadersowehavetimeanddate information,anditupdatestheMACaddressdatabasefrom WireShark.WireSharkkeepstrackofawholebunchofdifferent devicevendorsandtellsuswhattheMACaddressesaresowewantto pullthatdowneverytimeandgetitasupdatedaspossible.Then,it doessomeparsinganditdoessomematchingforouruse.Printoutall theSSIDslikeyousawonthefirstone alphanumeric.Thenitdoes thedeviceMACaddressassociation,tellinguswhatMACsthedevices areattemptingtoassociatetoasSSIDs,anditpipesoutthevendor type.Andjustaquicklocationofwherethescriptisheld;allthese scriptsarein https://github.com/joshingeneral/airMenu/.