Dedication
TheSuccessChariotVictoryLap
Idedicatethisbooktomythreefixturesofmylife.First,my wifewhoisaformidablepowerhousewithsparklingenergyall dayallthetime.Sheisadrivingforceinwritingandcompleting thiswonderfulsubjectofDNAHacking.Second,mydaughter NadiaHinedi,thehigh-spiritedattorneywhoshineswith dynamicmaturity,intellectualeloquence,andjudgmental brilliance.Third,mysonDr.SamiTermaniniMDforhis audacitytoclimbthemountainoflife,thetenacityofa marathonrunnertoovercomeallunknownbarriers,andhis couragetobelieveheistougherthanlife.Godgiveshishardest battlestohisstrongestsoldiers. Despitethepandemicthathasstillitsarmsaroundus,few peopledeserveastandingovationandamedalofHonor:My SeniorAcquisitionsEditorChrisKatsaropoulos,AnaClaudia Garcia,mySeniorProjectEditorMs.EmilyThompson, myContentManagerSajanaDevasiPK,andMr.Mohanraj RajendranCopyrightsCoordinator.
Thispageintentionallyleftblank
1.Themiraculousarchitectureof thegenepyramid
MynameisDNA1
Initialthoughts1
AnatomyofDNA1
Watsonandcrickstory2
DNAdoublehelix2
Whatisagene?3
Whatisthechromosome?3
Chromosomesinforensics3
Thecentraldogma3
Proteins4
Aminoacid5
RNAstructure5
Transcription(phase-1ofcentraldogma)5
Thetranscriptionprocess5
Translation(phase-2ofcentraldogma) process5
AnatomyofCRISPRmachine6
CRISPRstructure7
Drawbacksandunethicalissues8
Bio-hackingCRISPR,crackingthe biologicalatom8
CRISPRcyberhacking9
Appendix9
Appendix-A:GlossaryofDNA(courtesy MERITCyberSecuritytechnical library)9
Appendix-B:LandmineNobelsweet irony12
Appendix-C:CRISPERpioneers13 Recommendedsources13
2.Historyofbio-hackers,psychological profiling,andfingerprintingofthe bio-hacker
ThechemistryofDNAbio-hacking15
Hackerswearfourcolorfulhats16
TheemergenceofDNAbio-hacking16 HalloffameofDNAbio-hackers16 AdvancedDNAbio-hacking technologies18 ThecloudofmalwareofDNAbiohacking19 Eysenck’stheory20
Profiling,Dr.EdwardJones,ouractor20 OurhypotheticalDNAlab21 Achangeofbelief21 Dr.Edward’sDNA-hackingrationale21 Dataguardianturnedintohacker22 The“toxicstress”syndrome23 DNA-hackerfingerprinting23 Thecrimedatabases24 ThecombinedDNAindexsystem (CODIS)24 ThenationalcrimeinformationcenterDB (NCIC)25 Howdoesransomwarework?25 ThestoryoftherecentNorthKorean WannaCryransomwareattack25 What’sthenextstepforDr.Edward?26 Appendices26 Appendix-AGlossary:CourtesyofThe NationalAcademiesofSciences, Engineering,andMedicine26 Notes: HansEysenck29 Recommendedsources29
3.The E.coli storyasthecarrierof DNAmalwarecode
Whatis Escherichiacoli (E.coli)?31 Defensebyoffense32 TheCRISPR-Casimmunityprojects33 CODISdatabankstructures33 Themaliciouscodeinjectionmethod33 Dr.Edward’sbio-attackplan34 Strategicattacktimeline34 Anatomyofspyware35 Spyware’sspyingprocess36 Digitalmalwaredatadestruction process36
DNAsequencemalwaresetup36
DNAfingerprinting36
DesignoftheDNAsequence malware37
Thedroneflightformalwaredelivery37
DNAgenomebrowser37
Genomebrowserusers38
Appendices39
Appendix-ASQLstorageonDNA39
Appendix-BSQLcommandconvertedto DNAcode40
Appendix-CDNAprofiling(fingerprinting) technology40
Appendix-Dhowtoconvertgenesequence intoprotein41
Appendix-EtheBLASTbrowser42
Appendix-Fglossaryofgenometechnology extractedfromMERITcybersecurity library42
Recommendedsources43
4.CRISPRthemagicalknife,the good,thebad,andtheugly
Awarmupthought45
Crystalballingthefuturewithblurry vision45
Game-changingdiscovery,aneureka moment46
DoudnaandCharpentiergetnobel46
HistoricalCRISPRovation46
CRISPRthenewsunriseofgene editing47
ThegrimsideofCRISPR47
Thepartnerswhoareracingfor bio-geneticsfame49
JenniferA.Doudna49
EmmanuelleCharpentier50 FengZhang51
Embryoconcerns51
Acrackinthecreation52
DoudnameetsCharpentier52
Nobel2020winnersinchemistry52 CRISPRtimeline53
Theimpossiblebecamepossible53
TheFrankensteinunfortunatelegacy54
Geneticmanipulationgoneawry55
HeJiankui,China’sDr.Frankenstein55 WhoisHeJiankui?55
LuluandNana56 Appendices56
Appendix-A:thehumangenome56
TheHumanGenomeProject(HGP)57
Appendix-B:CRISPRglossaryfromMERIT cybersecurityarchivelibrary58 Recommendedsources61
5.Thegenomevandalism.“WhenISIS meetsCRISPR”
Apreciousthought63
Thenextgenerationofbio-hacking63 ISIS,thearmyfromhell64 ISISwasborn65
Thebitcoinstory65
Bio-hackingisamoney-making service66
ISISmeetsCRISPR66 CRISPR10166 DNA10167
DNAphysicalandsequencedata banking70
DNAecosystem70
AnatomyofDNAsynthesizers70 AnatomyofDNAsequencers71 AnatomyofCRISPR71 MiraculouspowerofCRISPR72 Autonomyofthehumangenome (NHG)72 Mappingofthegenome73 Hardcopyofthegenome74 Biovandalismandgeneticallyengineered bioweaponry thenewparadigm shift74 Bio-hackingstrategiesandtools75 Hackingtheprisoncomputersystems, itreallyhappened76 CRISPRtheunethicalsawingmachine, gene-editingbabies76 SARS-CoV-2omicronvariant76 ThevirusstartedinWuhan,China77 GeneratingmaliciousDNAsequence77 DNAforensics,goingbackintimewith reversebio-hacking78
Genomevandalism78 Hackingthehumangenomedatabases79 Whatarethedatabases79 Bio-hackingDNAecosystem80 Bio-hackingDNAdatastorage80 TheTrojanhorsesaga80 TheTrojanhorsemalware80 Theransomformula81
TheDillingerransome81
DNAbio-hackingwithwebsite-powered ransomattack82
DNAbio-hackingwithSQLinjection (SQLI)attack82
DNAbio-hackingwithmicrochip83
AwordonRFID83
DNAbio-hackingwithexternalbuffer overflowpayload84
DNAbio-hackingwithinternal sequencedmaliciousbinary84
Appendices85
Appendix-A:StrategictermsusedinDNA cyberhacking85
Appendix-B:Thenationalcenterfor biotechnologyinformation(BCBI)85
Appendix-C:Immune-systemarms race86
Appendix-D:DNAdataformat87 Recommendedsources87
6.The E.Coli plasmidsand COVID-19saga,loadeddirectly intoDNA
DNAthenewbeast91
Anatomyofcoronavirus91
Bio-hackingDNAwithCOVID-1993
TheCORONAattack(Act-1)93
TheCORONAattack(Act-2)93
Neuro-invasionofCOVID-19inthe humanbrain94
E Coli physicaltransport(spyware delivery)95
PathogenstransportedintoDNAlab96
Labdefinitions96
DNAbio-hackingwithFASTQmethod97 Appendices100
GlossaryofCOVID-19 fromMERIT CyberSecurityconsulting100 References101
7.DNAfingerprinting,biohackingas-aservicetoaltercriminal recordsfromDNAnational Banks
Godcreatedthefingers,wecreated theDNAfingerprinting103 DNAistheHolyGrail104
DNAprofilingistheenemyof privacy104
Bio-medicalengineeringand bio-informatics104
Definitionofforensicscience104
Inthebeginningwehadfingerprints105
Definitionofhumanfingerprinting105
IAFIS theintegratedautomated fingerprintidentificationsystem105
AFIS(automatedfingerprintidentification system)recordlayout;hackingIAFIS system106
Themillionstolenfingerprints107 DNAprofiling107 MitochondrialDNA107
Thetwobio-hackingscenarios108
Scenario-1:hackingthecombinedDNA indexsystem(CODIS)109 Introduction109
ArchitectureofthealmightyCODIS109
NDISthesmartDNAindexingengineof CODIS111
CODIStechnologyandDNA analysis112
Biohacking-as-a-service(BhaaS) organizations112
ThestrategyofattackonCODIS113 CODISvulnerabilities113
REDIS:remotedictionaryserver (Redis)114
CODISmanagement114
CODISstoragestats114 HackingCODISexecution115
HackingthecombinedDNAindex system(CODIS)116
Scenario-1hackingCODISDNA criminaldatabase117 Hacker’szeroday119
Scenario-2hackinggenome databanks120
Goalsforthehumangenomeproject (HGP)121
Medicalimplications122
FirststepinhackingHGP:knowingthe CODISsystemasageneticistand systemguru123
Blastsearchengine123 Importantdatabasetools123
Thecancermoonshotproject124
Hackingprerequisites124
Hackingbiometricstechnologies126
Asnapshotofhistory126
Themedicalexaminersystem126 CODIS126
Theonionrouter(TOR)andthedark web127
Thedarkweb128 Appendix129 Appendix-AREDIStechnology129 Appendix-BGlossaryofCODIS129 Biologicalsibling131
Appendix-Cglossaryofthedark web150
Appendix-Ctheonionrouter(TOR) glossary153
Appendix-Dtheopensystem interconnection(OSI)model153
Recommendedsources154
8.HowtoselectaDNAbio attack.Howtoplanit,assess itsdamage,andits vulnerability
DNAbioweaponryandDNAbio-hacking warfare155
CRISPRthetwo-edgedsword156
CRISPRisthenewDNAbio-bomb156
Life-extensionandagereversing euphoria156
Whyissynthesisbiologytherightarm forbio-hacking?157
Bio-hackerhackingqualifications159
Bio-hackmethod-1(Boobytrap)159
Bio-hackmethod-2(remotecontrol)160
Stuxnetthedevil’sterminator161
Stuxnetmissilearchitecture161
NowwehaveDNAxnet162
DNAbio-hackingcategories162
DNAxnetworkofthedevil163
ThepossibilitiestohackDNA databanks165
JosiahZayner“thefirstbodybiohacker” story165
Zayner’spioneeringwork165
Theawesomepostmortembio-hacking story166
Evaluationofthecriticalsuccessfactors (CSF)forDNAbio-hackmission166
DNAbio-hacksuccessfactors167 EvaluationofsuccessinDNAbio-hack mission169
Appendices172
Appendix-AChinesescientistwho producedgeneticallyaltered babies172
Makinggeneeditinganequalplaying field172
Appendix-Bthestoryofstuxnet,the missilefromhell173
Appendix-Cglossaryofhackingterms listofimportanttermsusedinthe fieldofhacking173
Recommendedsources175
9.Thedronetechnology,transport strategy,andriskevaluation,and biomedicalrevolution
Introduction177
SteppingalittledeeperintoDNA forensics179 Theworldofbiohackers179 Knowingthyenemy180 Nanotechnologythenewparadigm shift180
Nanotechnology,thesunriseofthe future181 ThenanoDNAbio-hacking,anew disruptivetechnology182 Internet-of-Nano-Things(IoNT),the nextthinginbio-hacking182 CODIS,theDNAcrimeprofilesystem, thecrimemagnifier183 Memorandumofattachagreementwith bio-hackingorganization184 Strategyofattackofthenano Bio-drone185
Stage-1:Attackplanningand engineering185 Stage-2:Droneflight185 Stage-3:bio-hackepisode185 TargetedKillingwithnanodrones-the newDNAvandalism186 ThelaunchofthenanoDNAbio-drone attack186 AnatomyofthenanoDNAbiohack drone186 AnatomyofNano-DNAxnet,the futuristicbiohacknanochip187 EngineeringoftheDNAxnet nanochip188 DNAxnetnanochipcomponents189 DNAxnetmissiledesign specifications189 REDIS/CODIStechnology191 Functionalityofthezookeeper,the frontendtrafficcoordinator192 FunctionalitiesoftheCODIS/proxies, thesmartIPfilter192 FunctionalityofCODISloadbalancer192 FunctionalitiesoftheREDISSentinel193 REDISmemoryspecifications193 CODIStransactionsequence194 ThenanoDNA-bio-droneattack194 Strategyoftheattack194
Launchingtheattack195
DNAxnetdeliveryonboardthe nano-drone196
Then,whathappenedafterthehack196
RemovingCODISrecordsisslippery slope196
Thedigitalimmunityecosystem(DIE) andTheSmartVaccine198
Appendix199
AppendixA199
AppendixB201
References203
10.Dronedeliverymethods andhowtocommunicate withthedestination
Historyofdrones205
Nanotechnology,thesunriseisso bright207
Bio-hackingservicesadopteddrone nanotechnology207
Givelawenforcementahand208
Quantumcomputers,quantum supremacy208
Quantumcomputing,thefertileground forbio-hackers209
Nanoquantumcomputing211
Deliverymethods211
WeaponizedNanoBio-Hacking (WNBH)212
Quantumdroninganddelivery213 QuantumNetwork213
Everythingisconnected214
Appendices215
Appendix-A:godandtime215
Appendix-B:Shor’salgorithminthe quantumcomputing216
Appendix-C: Glossaryofquantum computing: NationalAcademiesof Sciences,Engineering,andMedicine. 2019216
Recommendedsources219
11.TheDNAxnetBiowarfare andevaluationofits impact
WhatisDNAbio-hacking-asa-service?221
Stuxnetisthedevil’skeytohell221
ThebioDNAxnet,thefruitfrom hell224
Theattackscenario224
DesignofthebioDNAxnet nano-chip224
BioDNAxnetmissileusesUNIX225
Howdidthebio-hackerssimulatethe attack?226
Environmentaldata226
Hackingbackgroundandtechnical experience226
Resultsofthebio-hackingsimulation model226
Thedashboardscreen227
Theactivityscreen227
Thegraphicsscreens228
ThelaunchoftheDNAxnetTrojan daemon228
Postattackimpactandtrackingthe CODIS sabotage229
Biohackriskcomputation230
Furtherbio-hackingsuccess formulas231
Criticalityisdeterminedbynumberof components231
Whatiscriticality?232
Whatisseverity?232
Humancriticalsurvivability232 Appendices234
Appendix-Athecompletestoryof stuxnet234
Recommendedsources237
12.Storageandexecution ofDNAcontaminated code
We’restilloncrutches239 Evenconcertwallscry240 Solarwindscrater240
Thecentraldogma240
SteppingintoGod’sdomain, CRISPRgeneediting241
AnatomyofCRISPR,thetwo-edge sword241
ThisishowCRISPRworks241
AsnapofCRISPhistory242
CRISPRthetooltohackthehuman genome243
Injectingbio-malwarewith CRISPR243
Thethreecontaminationattack scenarios244
ScenariosofDNAgenescontamination anddistribution244
Appendices246
Appendix-A:GlossaryOfDNAAnd Protein(CourtesyoftheNational CenterforBiotechnology Information);MERITCyberSecurity isamemberoftheNationalInstitute ofHealth246
Appendix-B:GlossaryofCRISPR (CourtesyoftheUSLibraryof Medicine)255
Appendix-C:GlossaryofGenetics (FromMERITBio-Engineering Library)256
Recommendedsources263
13.Encryptiontechnologyand camouflagingcontaminated DNA-codeinjection
Inthebeginning,therewasCaesar’s cipher265
Interestingfactsaboutthemanwho broketheEnigma Alanturing266
AlainTuringthehacker267
TheuniversalTuringmachine,the granddaddyofcomputing267
DNAgenebio-hackingtechnologies267
DNAbio-hackingwithcryptography (firstcamouflagetechnology)269
DNAbio-hackingwithcryptography, theholygrailofbio-hackers271
TheRosettaStonestory271
Bio-hackerstheDNAHoudinis272
DNAbio-hackingwithwatermarking, (secondcamouflagetechnology)273
Bio-hackersandadvantagesof watermarking274
Watermarkingandmasking optimization274
DNAbio-hackingwith steganography (thirdcamouflagetechnology)275
CODISbio-hackingprocess278
Bio-hackingwithquantum cryptography279
AdvantagesofQCandquantumkey distribution279
Bio-hackersarethemastersofquantum keydistribution(QKD)279
Bio-hackingreactiontoquantum computing280
Google’squantumcomputer,the Sycamore280
Bio-hackingattackmanifesto281 Appendix285
Appendix-A: QuantumCryptography Glossary. NationalAcademiesof Sciences,Engineering,and Medicine.2019. QuantumComputing: ProgressandProspects.Washington, DC:TheNationalAcademies Press.285
Recommendedsources287
14.ForecastanddetectionofDNAsurprisebio-attacks,bio-defenseand eradication.HowtosecureDNA datafiles
Bio-attacksincethebeginningof time289
ThePlagueofKaffa289
DetectionofsurpriseDNA bio-attack290
ThestoryofGenBankDNAsequence database291
BuildinganautonomicAI-centric smartsystemtostopDNA bio-attack293
TheDNAbio-response295
CouldDNAprotectitself?295
GovernmentresponsetoDNA bio-attack295
TheDNAbio-hackingachilles’ heel296
Americaisfacingnewtypeof bio-attack296
TheviewCovid-19attackforDNA sabotage296
Biotechnologyimpacton bio-hacking297
Thenewplanforanational Bio-DefenseDepartment (BDD)297
ArchitectureoftheNationalDNA DefenseCenterAgainstthe Unknown(NDDATU)298
SecuritymeasuresofTheNational DNADefenseCenteragainstthe Unknown(NDDCATU)299
Alookatthequantum computing300
Howdoesquantumentanglement work?301
Howdoesquantumteleportation work?301
Teleportationbyoptical tweezers302
Humanteleportation,what?302
Ourdailydigitalcomputers razzledazzlewillsoonrest inpeace303 Appendix303
Appendix-A:TheSARS-CoV-2, NationalInstituteofAllergy,and InfectiousDiseases(NIAID)303
Appendix-B:NCBI’sGenBank Reactor . Thesourceofmedical knowledge304 Recommendedsource305
15.HowtoreverseengineerDNA andquantumbio-attacks
Reverseengineering,toolof survival307
AnatomyofaDNAbio-hacking308
AnatomyofourDNA309
Whatiscryonics,death-2-lifereverse engineering310
Bio-hackersloveDNAtreasures311
HowtoreverseengineeraDNAbioattack311
Bio-hackerswillsimulatethefuture oftheattack312
Portfolioofbio-hackingattacks312
TheTurinreverse-engineeringprocess thatsavedthewar312
CrackingtheEnigma312
Reverseengineeringisbreakdown, copyandrebuildengineering313
ReverseengineeringstrategyinDNA bio-hacking314
Thefourstepsofreverse engineering314
Reverseengineering reformulation findfromknownproteintheproper DNA315
Reverse-engineeringimplementationin quantumbio-attacks316
Digitalcircuitryandphenomenonof Moore’slaw316
Andthen,quantumcomputing prevailed317
Howcanbio-hackingpenetrate quantumcomputing317
Bio-hackingstrategicplanofattack319
Bio-hackingorganizationsattack targets319
Anatomyofthequantumcomputer321
Quantumhardware321
Softwareandtutorialsfromquantum computerhardwareproviders322
Quantumsoftwareandquantum programming322
Finally,quantuminternet(QI),the favoriteforbio-hacking323
Goalsofbio-hackingorganizationsfor quantumcomputingandquantum internet324
Theothersurprise,quantuminternet ofthings324
Bio-hackingorganizationsaregoing aftertheQuantumInternetof MedicalThings(QIoMT)325
Nowthequantumcloud,capitalofthe quantumInternetofMedicalThings (IoM)325
Designofquantumbio-hackapplications forInternetofMedicalThings (IoMT)326
DesignofthequantumInternetof MedicalDevices(IoMD),themedical yellowpages326
Testingthequantumkillerapplication withsimulation327
Thearchitectureofabio-meddata centermodel329 Appendix330
Appendix-A:softwarecompanies thathaveSoftwareDevelopmentKits (SDKs)forquantumcomputing330
Appendix-B:companiesgivingaccess toquantumcomputers331 Appendix-C:technicalcomparison betweenclassicalsoftwareand quantumsoftware331 Recommendedsources331
16.CRISPRcontroversywithreligion andethicsadvocatestocontrol evolutionandembryology enhancement,andtoeliminate geneticallyinheriteddiseases
Athoughtfromthelaunchpad333
CRISPRanatomy334
CRISPRthesilentguillotine apparatus335
Bio-hackersaregettingreadytouse biologicalweapons336
Droneshavebecomepartofthe bio-weaponry337
Let’snotforgetDr.Zhangcontribution inCRISPR338
CRISPRbestinventionintheworld338
Peacebetweenscienceandreligioninjecting“scriptural”DNAintothe body339
TheAdrienLocatelliSaga339
Steppingintothedomainofgod340 CRISPR’sreligionenigma340 PlayinghardballCRISPR340 Bio-academia,intelligence enhancement,bettereducation341
Theblessingofbacteria341 WhatismoreimportantDNAor religion(extractedfromthe telegraph3-3-2019)341
Bio-hackingaffinityforCRISPR342
Someatheisticarrogance342
TheDr.FrancisCollinsdefense, directorofthenationalinstitutesof health342
HeJiankuigene-editingscandal343
Religiouscommunitiesarenot happy344
Dr.CrickandChurchillarguments344
Nobelscientisthappyto“playgod” withDNA345
NowreligionspeaksaboutDNA345
Conflictbetweenscienceandreligion onevolution345
WheredoesCRISPRfitbetween creationandevolution346
Franc¸oiseBaylis347
WeighingCRISPRonthescale347 Concludingthoughts349 Religionfightingreligion349 Appendices350 Appendix-A:GlossaryofCRISPR350 Appendix-B:Watch:meetoneofthe world’smostgroundbreaking scientists.Heis34350 Recommendedsources350
Epilog353 Index355
MeetDr.JosiahZayner,the Pasteurofbiohacking 363
Acknowledgment
DNAisthedigitalcodeoflife.Itencodeshowwearebuiltandhownatureoperates,andscienceislearningmoreandmore aboutthisuniquelydigitallanguage.Itisamagicwordandisgalvanizedwithsomanymysteries.Biohackingisanother eye-openinghighlyspecialized field;althoughbiohackingisinitsinfancy,itisthenewparadigmthatwillcreateanew generationofZayners,asshowninNetfl ixfast-pacedthriller “Biohackers ”
Ihavetalkedandlistenedtomanypeopleonthesubjectofbiohackingandabsorbedalotofnewideasandlearned aboutthedarkcornersofthistechnology,whicharejustasexcitingasthenewdiscoveriesoftheblackhole.Bytheway, StephenHawkingcouldhavebeenagreatbiohackerifhehadbeenalive.
Inaddition,Isalutethefollowingpeopleandwantedtoacknowledgetheiradmirationandenthusiasmonthesubjectof DNAhacking!
Ms.LinaTermanini,Director,GlobalMethods,Ernst&Young,SanFrancisco,CA
Dr.NeylaHinedi,AspiringResearchScientist,Pittsburgh,Pennsylvania
Ms.NadiaTermaniniHinedi,AttorneyatLaw,Pittsburgh,Pennsylvania
Dr.SamiTermanini,MD,GeneralMedicine,Dublin,Ireland
Dr.ZaferTermanini,MD,OrthopedicSurgeon,Florida,USA
Ms.MiaWilliams,BusinessConsultant,Florida,USA
Ms.GarciaAnaClaudia,SeniorAcquisitionsEditor,PolymerScienceandNanotechnology,ElsevierPublishing,Brazil
RadwanTermanini,SeniorEconomist,Doha,Qatar
SamirTermanini,AttorneyatLaw,ComputerScienceExpert,NewJersey,USA
Dr.EesaBastaki,PresidentoftheUniversityofDubai,Dubai,UAE
Dr.HussainAl-Ahmad,DeanoftheCollegeofEngineeringattheUniversityofDubai,UAE
Dr.WathiqMasoor,ProfessorChairofElectricalEngineering,UniversityofDubai,UAE
Dr.BushraAlBlooshi,Director,ResearchandInnovation,DubaiElectronicSecurityCenter,UAE MeshalBinHussain,CIO,MinistryofFinance,UAE
Dr.AdelAlAlawi,ProfessorofMIS,UniversityofBahrain,Bahrain
Dr.HodaAlkhzaimi,Director,CenterforCyberSecurity,ProfessoratNYUAbuDhabi,UAE
Dr.SameeraAlmulla,BoardMemberoftheEmiratesScienceClub,AbuDhabi,UAE
Ms.AlisonRyan,PA-C,DiabloValleyOncologyandHematology,CaliforniaCancerandResearchInstitute,Pleasant Hill,CA
Dr.SiripongMalasri,DeanofEngineering,ChristianBrothersUniversity,Memphis,Tenn.
Ms.AmnaAlmadhoob,SeniorSecurityandResearcher,AMXMiddleEast,Bahrain ChandaBanwat,MD,InternalMedicine,JohnMuirMedicalGroup,WalnutCreek,CA JudsonBrandeis,MD,ComprehensiveCareforSexualMedicine,SanRamon,CA
Dr.SuzeeEurieLee,MD,UniversityofCalifornia,SanFrancisco,CA
Dr.RobertRobles,MD,DiabloValleyOncologyandHematology,SanRamon,CA
Dr.NavjeetBoparai,MD,IntegratedPainManagement,WalnutCreek,CA
Ms.AkilaKesavan,Partner,Ernst&Young,SanFrancisco,California
Dr.YigalArens,Director,USC/InformationScienceInstitute,LosAngeles,CA
Dr.KristinaNyzell,CEO,DisruptivePlayConsulting,Sweden
JohnandDanielleCosgrove,CosgroveComputerSystems,ElSegundo,CA
Also,Iwouldliketothanktherestofmyvisionaryandcreativefriendsfortheirgraciousassistanceandsupport.
Dr.RockyTermanini WalnutCreek,CA94595
Thispageintentionallyleftblank
Themiraculousarchitectureofthegene pyramid
ThereisenoughstoragecapacityintheDNAofasinglelilyseedorasinglesalamanderspermtostoretheEncyclopedia Britannica60timesover.Somespeciesoftheunjustlycalled “primitive” amoebashaveasmuchinformationintheirDNAas 1000EncyclopediaBritannica.
RichardDawkins.
Theresultssuggestahelicalstructure[ofDNA](whichmustbeverycloselypacked)containingprobably2,3,or4coaxial nucleicacidchainsperhelicalunitandhavingthephosphategroupsneartheoutside.
Dr.RosalindFranklin DoubleHelixDiscoverer.
DNAislikeMidas’sgold,everyonewhotouchesitgoesmad.
Dr.MauriceWilkins.
Blindindividualswhohavetriedtheseartificialretinashavebeenamazedthattheycanseecolorsandoutlinesofimages.Itis onlyamatteroftimebeforewehaveartificialretinasthatcanrivalhumansight.
Dr.MichioKaku.
MynameisDNA
Forlifetoexist,aninformationsystemisneededtoproduceandregulatelifefunctions.Thisinformationsystemmustalso beabletoaccuratelycopyitselfforthenextgeneration.DNA(deoxyribonucleicacid)istheinformationsystemforlife.
Initialthoughts
ImagineaworldwhereyoucouldgooutsideandtakealeaffromatreeandputitthroughyourpersonalDNAsequencer andgetdatalikemusic,videos,orcomputerprogramsfromit.Well,thisisallpossiblenow.Itwasnotdoneonalarge scalebecauseitisquiteexpensivetocreateDNAstrands,butitispossible.
Here’saninterestinganecdotethatwillcatchyoueye:AFrenchhighschoolerhasallegedlybioengineeredDNAbased onversesfromtheBibleandQuranandinjecteditintohisownleg.AdrienLocatelli,16,fromGrenoble,France,posteda shortpapertotheOpenScienceFrameworkpreprintserverinwhichheclaimedtoproducestrandsofDNAthatcorrespondedtoversesfromtheBibleandtheQuran.AccordingtoLocatelli,hetheninjectedtheDNAcontainingtheBible versesintohisleftthigh,andtheDNAwiththeQuranicversesintohisrightthigh. “Ididthisexperimentonlyforthe symbolofpeacebetweenreligionsandscience,” Locatellitoldmeinanemail. “It’sjustsymbolic.” Theproteinscreatedby LocatelliarebasicallyjustshortstrandsofDNA,whichismadeofnucleotidesthatcanonlybecombinedinspeci ficways.
AnatomyofDNA
Deoxy-ribo-nucleicacidisalargemoleculeintheshapeofadoublehelix.That’sabitlikealadderthat’sbeentwisted manytimes.ManypeoplebelievethatAmericanbiologistJamesWatsonandEnglishphysicistFrancisCrickdiscovered DNAinthe1950s.Inreality,DNAwas firstidentifiedinthelate1860sbySwisschemistFriedrichMiescher.Then,inthe decadesfollowingMiescher’sdiscovery,otherscientists notably,PhoebusLeveneandErwinChargaff conducteda seriesofresearcheffortsthatrevealedadditionaldetailsabouttheDNAmolecule,includingitsprimarychemical
componentsandthewaysinwhichtheyjoinedwithoneanother.Withoutthescientificfoundationprovidedbythese pioneers,WatsonandCrickmayneverhavereachedtheirgroundbreakingconclusionof1953:thattheDNAmolecule existsintheformofathree-dimensionaldoublehelix.
Thefactis1869wasanimportantmilestoneyearingeneticresearch.ItwastheyearinwhichFriedrichMiescher,the Swissphysiologicalchemist fi rst,identi fiedwhathecalled “nuclein” insidethenucleiofhumanwhitebloodcells. Miescher’sdiscoveryofnucleicacidswasuniqueamongthediscoveriesofthefourmajorcellularcomponents(i.e., proteins,lipids,polysaccharides,andnucleicacids)inthatitcouldbe “datedprecisely [to]oneman,oneplace,one date.” DNAisactuallyabiologicalUSBdrive,acarrierofgeneticinstructionsforthedevelopmentandlifeofanorganism toanotherorganism.
Watsonandcrickstory
Itisworthmentioningfewwordsabouttwoformidablemindsthatleapfroggedthehumanmindby1000years.They revealedDNA’sdouble-helixstructurein1953,FrancisCrickandJamesWatsonhelpedtoinventbiotechnology,provided thefoundationforunderstandingthediversityoflifeonEarth.NowthattheyrevealedthatDNAistheblueprintoflife, Watsonandcrickhaveahair-raisingdogmaabouttheSupremeBeingandnotgivinghimcreditforthecreationofthe universe.Dr.Crick,86,saidrecentlyinSydneyMorningHeraldinMarch22,2003: “TheGodhypothesisisrather discredited.” Indeed,hesayshisdistasteforreligionwasoneofhisprimemotivesintheworkthatledtothesensational 1953discovery.ItpuzzlesthemindthatWatsonandCrickdeviatedfromthemainstreamtheology.In1961Crickresigned asafellowofChurchillCollege,Cambridge,whenitproposedtobuildachapel.WhenWinstonChurchillwrotetohim, pointingoutthat “noneneedenter[thechapel]unlesstheywish,” Dr.Crickrepliedthatonthosegrounds,thecollege shouldbuildabrothel,andenclosedachequefor10guineas.Also,Mr.Watsonboldlyclaimed “Onlywiththediscovery ofthedoublehelixandtheensuinggeneticrevolutionhavewehadgroundsforthinkingthatthepowersheldtraditionally tobetheexclusivepropertyofthegodsmight1daybeours.”
DNAdoublehelix
Let’sgobackanddescribethemiraculousmodule.In1953JamesWatsonandFrancisCrickpublishedtheirtheorythat DNAmustbeshapedlikeadoublehelix.Adoublehelixresemblesatwistedladder.Each “upright” poleoftheladderis formedfromabackboneofalternatingsugarandphosphategroups.EachDNAbase(adenine,cytosine,guanine,thymine) isattachedtothebackboneandthesebasesformtherungs.Thereare10 “rungs” foreachcompletetwistintheDNAhelix. Fig.1.1 showsthe3DrepresentationofDNA.Thenotation50 -and-30 isusedtoshowthatDNAhasadirectionwhere50 is the “head” oftheDNAstringwhile30 isthetailoftheDNAstring.(50 isreadas “five-prime ” and30 isreadas “threeprime.”).ThetotallengthofDNAstrandsinthehumanbodyisequivalentto:120billionmiles.
BiologyhasearnedaglobalreputationbecauseofthediscoveryofDNAstructureandcomposition.Thesequencingof thehumangenomehasgivenanewviewtobiologyasaninformationscience.TwoattributesofDNAstructurehave createdanimpressiveinfluenceonscience:
Digitalnature: (Theorderofbasesoneachstrandmakesupthedigitalcodethatcarriestheinstructionsforlife), wherebyonestrandofthehelixbindsperfectlywithitspartner.DNAhastwotypesofdigitalinformation thegenesthat encodeproteins,whicharethemolecularmachinesoflife,andthegeneregulatorynetworksthatspecifythebehaviorof thegenes.
Basecomplementarity: (Inotherwords,thenucleotidesoftheDNAhavethepropertyof basepairing),wheretheletter A(Adenine)formsahydrogenbondwiththeletterT(Thymine)andtheletterC(Cytosine)formsahydrogenbondwith theletterG(Guanine).Let’suseanexampleofastringofDNAlikethis:ACGT.
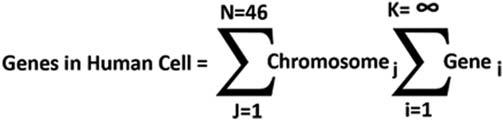
FIGURE1.1 Here’ssomestatisticsthatwillnotonlyblursyourvision, butalsoyoumind:Thehumanbodyconsistsofsome37.2trillioncells. Thetotalnumberofchromosomesthatarefoundineachandeveryhuman cellis46.DNAexistsinsidethenucleusofeachofthebody’scells.DNA isarrangedasacoilofcoilsofcoilsofcoilsofcoils!Thisallowsthethree billionbasepairsineachcellto fitintoaspacejust6micronsacross.The sequencegoeslikethis:genesinDNAinchromosomesincells.
Whatisagene?
Byanalogy,ageneislikeawordthatcarriessomeinheritanceknowledgeofeverylivingsoul.GenesinDNAencode proteinmolecules,whicharethe “workhorses” ofthecell,carryingoutallthefunctionsnecessaryforlife.Genesare attachedtothehelixtwistedladderlegsstrand-1andstrand-2.Thetwostrands(thesidesoftheladder)aretightlyconnectedtogetherwithsteps(bases).Genesmakeupsentenceswithatotalof1000 25millionwords.Thesesentenceswith variablelengthsaretightlypackedintooneofthe46chromosomes(23frommaleparent,23fromfemaleparent).Wecan comparethechromosomesto filesstoredin fi lecabinet.Thesechromosomes filesareusedincrucialforensiccrimeinvestigations.Thechromosomes fi lesarecontinuallyretrievedandcopied;andthenreturnedtothe filecabinet.Ouranalysis haveshownthatdefiningageneisproblematicbecauseongenecancodeforseveralproteinproducts,somegenescode onlyforRNA,twogenescanoverlap,andotherunpredictablecomplications.Theinformationinourgenesispresently programmable;thisisnolongerafear.Researchhasnowdemonstratedthatourdestinyisnotprede fined:itissetbythe choiceswemakeeveryday.
Whatisthechromosome?
Simplisticallyspeaking,itisaheavy-duty filecabinetwithalock,tostoreDNAgenes.Chromosomesalwaysremain inthenucleus,butproteinsaremadeatribosomes.Chromosomesareidenticalineverycell,whichcontainaperson’s genes(DNAdata).Achromosomecontainshundredstothousandsofgeneswhicharetightlywrappedaroundinside histones.DNA,offullyextended,itslengthwouldbe1.7mlong.UnwrappingalltheDNAsinallourcells,itwould equaltothedistancefromEarthtomoon6000times.Anormalhumancellcontains23 2pairsofchromosomes, foratotalof46(maleandfemale)chromosomes.FemaleshavetwoXchromosomesintheircells,whilemaleshave oneXandoneYchromosome.Wecanusethismathematicalformulain(Fig.1.1)tosymbolizethenumberofgenes ineverycell.
Chromosomesinforensics
Crimedoesn’tpayisajusticeboardthatDNAcreatedandhangedineverycourtroom.AY-STRisa shorttandemrepeat (STR)ontheY-chromosome.Y-STRsarepowerfultollusedinforensics.ThereareregionsonDNAthataremadeupof multiplecopiesofshortrepeatingsequencesofbases(e.g.,TATT)whichrepeatavariablenumberoftimesdependingon theindividual.These “repeat” regionsareexaminedwhenconductingSTRanalysis.Itisextremelyrareto findtwopeople havingthesamenumberofrepeatedsequences.Forensicscientistsusethepolymerasechainreaction(PCR)tomake millionsofcopiesofrepeatedgenesintheSTRregions.Gelelectrophoresisthen “yieldsthenumberoftimeseachrepeat unitappearsinthefragment. ”.Forensiccrimeanalystsusedthistechniquetoisolatethecriminal.Forensicexpertsaround theworldrecognizedthepotentialofthemethodforsexingandexclusionandpromotedY-chromosomeanalysisforsex crimes.
Thecentraldogma
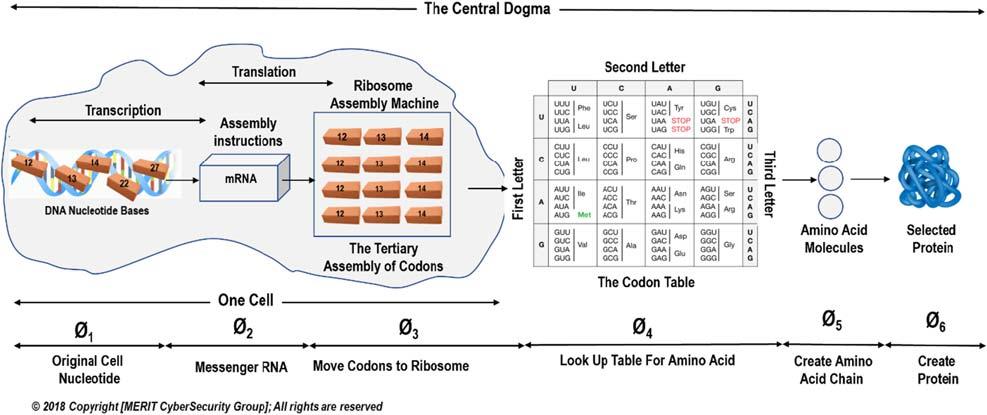
CentralDogmaisaverycomplexanddeeptermindeed,whichwascoinedbyFrancisCrickdiscovererofthestructureof DNAin1958.Dr.FrancisCrickeloquentlystated “Icalledthisideathecentraldogma,fortworeasons,Isuspect.Ihad alreadyusedtheobviouswordhypothesisinthesequencehypothesis,andinadditionIwantedtosuggestthatthisnew assumptionwasmorecentralandmorepowerful.” Thecentraldogmaconcept(prettymuchlikeaproductionline)explainshowthe flowofgeneticdata(bases)fromDNAtoRNAandtoribosomeswhichusesaminoacidinstructionsto makecustomizedtoprotein.Theribosomesserveasfactoriesinthecellwheretheinformationis “translated” fromacode intothefunctionalproduct.
LetusgoalittledeepertounderstandthemechanicsofthecentraldogmaandDNAasshownin(Fig.1.2).Itstartswith theproteinwhichisessentialnutrientforthehumanbody.Proteinisoneofthebuildingblocksofbodytissueandcanalso serveasafuelsource.Asfuelsupplier,proteinsprovideasmuchenergydensityascarbohydrates.So,ifacertainpartof thebodyneedsmusclebuildupanditwillinformtheDNAofthecellabouttheneedforprotein.Proteinsarelargeorganic compoundsmadeofaminoacidsarrangedinalinearchainandjoinedtogetherbetweenthecarboxylatomofoneamino acidandtheaminenitrogenofanother.Thediagram(Fig.1.3)givesavisualrepresentationofthewholecycleofthis phenomenoncentraldogma.
FIGURE1.2 Thisisthemiraculousproductlineofmakingprotein.SixphasesstartingfromCrudeDNAallthewaytoarefinedprotein.
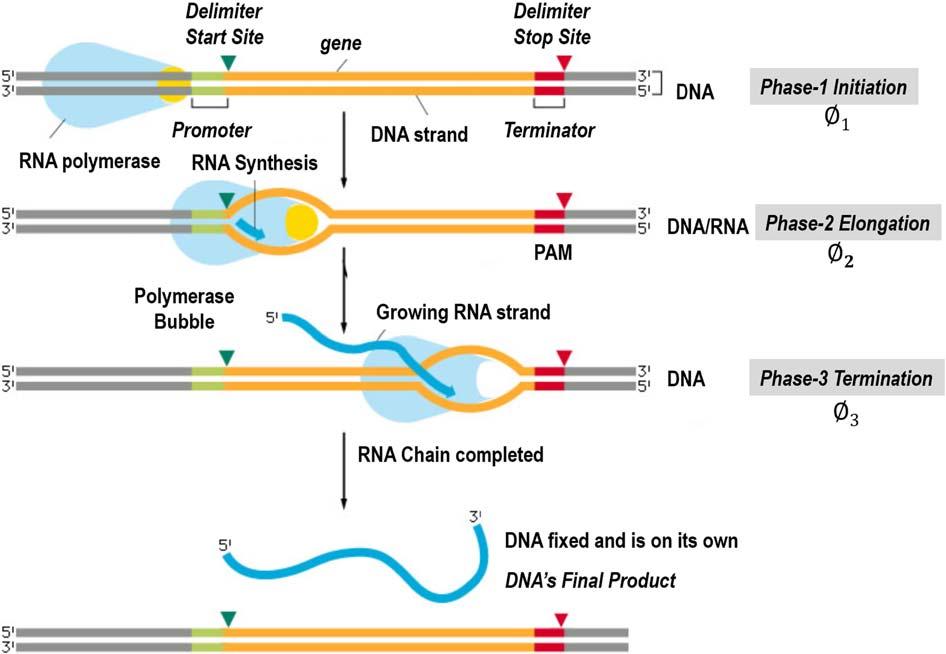
FIGURE1.3 Thediagramclearlyshowsthethreephases,startingwiththeinitiationphasewhereRNAgetsthemessagefromDNA.Intheelongation phase,mRNAisbuilt.IntheterminationphasewheremRNAleavesahealthyDNAonitsown.
Proteins
Proteinsarethechiefactorswithinthecell,andtheycarryoutthedutiesspecifi edbytheinformationencodedingenes. Thesequenceofaminoacidsinaproteinisdefinedbyageneandencodedinthegeneticcode.Thebest-knownroleof proteinsinthecellisasenzymes,whichactsasacatalystforchemicalreactions.Conclusively,thenumberofprotein moleculesinacellwascalculatedtobe42million.
Aminoacid
AsDr.LawrenceC.Brody,Ph.D.eloquentlydefinedaminoacid: “Aminoacidsarethesmallmoleculeswith20different flavorsthatmakeproteins.Theseaminoacidsgetlinkedtogetherlikebeadsonastringtomakelongchainsthatwecall polypeptideswhicharethebuildingblocksofproteins.Theneatthingaboutaminoacidsisthattheymakethe finalshape oftheproteinwhichinturndictateswhatitcandointhecell.”
RNAstructure
Itiscalledribonucleicacid(RNA).ItisthebridgethatcarriesDNAproteininstructionstotheribosome(assemblyengine) whereproteinismanufactured.TheorderoftheDNAbases(ATGC)determinesthegeneticcode,similartothewaythe orderoflettersinthealphabetisusedtoformwords.DNA’s “words” arethreeletters(orbases)long,andusedspecifi cally ascodeforgenes,whichinthelanguageofthecell,istheblueprintforproteinstobemanufactured.
Toreadproteinblueprints,DNAisunzippedtoexposetheindividualstrandsandanenzymetranslatestheinstruction intoamassagecalled messenger RNA(mRNA)whichcarriestheinstructionsformakingproteins.ThemRNAisthen leavingthenucleusandmovestoamolecularmachineresponsibleformanufacturingproteinscalled ribosome.The ribosometranslatesthemRNAinstructionstothree-letterwordscalled codons. Thethreelettercodonsareloadedintothe codontable,andtheyextractaspeci ficaminoacidwhichisapolypeptidechainthatwilleventuallybecomeaprotein.
Theribosomeassemblesaproteininthreephases The firststepcalled initiation;a transfer RNA(tRNA)bringsthe specificaminoacidthatwasselectedfromthecodontableintotheribosome.Thesecondstepcalled elongation;each aminoacidissequentiallyconnectedtoalinkinachaincalled polypeptide.Theordereachaminoacidiscrucialtothe functionalityofthefutureprotein;errorsinaddinganaminoacidcanresultindisease.Thethirdstepcalled termination, thecompletedpolypeptidechain,isreleasedfromtheribosomeandisfoldedintoits finalproteinstate.Proteinsare requiredforthestructure,function,andregulationofthebody’stissuesandorgans;theirfunctionalityisseemingly endless.
Transcription(phase-1ofcentraldogma)
Merriam-Websterdictionarydefi nestheterm transcript as “anofficialcopyofastudent’seducationalrecord.” In biochemistry,itistheprocesstocopygeneticsequenceinformationofDNAnucleotidesintonewlysynthesizedmolecules ofRNA,whileDNAservesasatemplate.TherearethreeagentsofRNAwithdistinctfunctionsduringDNAtranscription:
l mRNA(messengerRNA)whichsendsaDNAmessagetotheribosome).
l rRNA(ribosomalRNA)whichmakesuptheribosome.
l gRNAGetsinstructionsfromDNAandguidesCas9tothetargetlocation.
l tRNA(transferRNA)whichtransfersaminoacidsbuildingsuppliesofproteintotheribosome.
Thetranscriptionprocess
Ittakesplaceinthreeconsecutivesteps:initiation,elongation,andtermination.Thestepsareillustratedin(Fig.1.3).
Initiation(step-1): AsDNAisbeingtranscribedbythepolymerase,atranscriptionbubbleforms.RNAenzymeatthe beginningoftranscriptionbindstothepromoteratthebeginningofthegenechain.Thistriggersthebeginningofa “read” messagewhichcreatesthestrandofmRNA.
Elongation(Step-2): ItoccurswhenRNApolymerasestartsbuildingmRNAmoleculewithDNAcomplementarybase pairs “reads,” whereadenine(A)nucleotidesbecomeuracil(U)inmRNA.
Termination(Step-3): istheendingoftranscriptionandoccurswhenRNApolymerasecrossesastop(termination) sequenceinthegene.ThemRNAstrandiscomplete,anditdetachesfromDNA.
Translation(phase-2ofcentraldogma)process
Withinallcells,thetranslationcentralunitiscalledthe ribosome whichcontainstwosubunitsthatcontainproteinsandthe twospecializedRNAmolecules:ribosomalRNA(rRNA)andtransferRNA(tRNA).Withintheribosome,themRNAand tRNAcomplexesareheldjointlytofacilitatebase-pairing.TherRNAcatalyzestheattachmentofeachnewaminoacidto thegrowingchain.
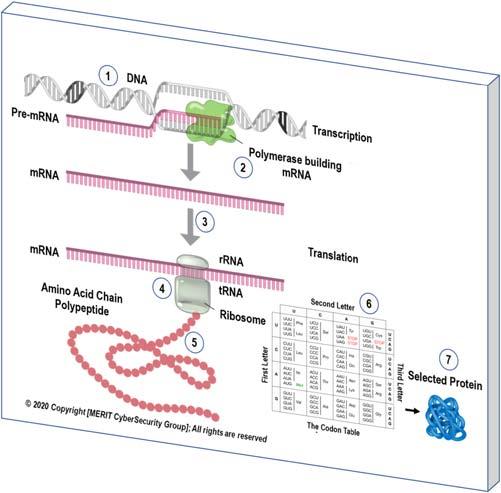
FIGURE1.4 ThisisanotherviewoftheCentralDogmaprocess.(1)Thepre-mRNAisreadytocreatesthemessengerRNA(mRNA)(2)Polymerase buildsthemRNA(3)whichsendsthemRNAtorRNA(ribosomalRNA)whichmakesuptheribosome.(4)TransferRNA(tRNA)transfersaminoacids buildingsuppliesofproteintotheribosome.(5)Aminoacidchainpolypeptideiscreated.(6)Thecodontableextractstheaminoacidscodes.(7)The selectedproteinidcreated.
TranslationisthesecondpartoftheCentralDogmamiraclewhichcomesafterthetranscriptionstepiscomplete. InformationfrommessengermRNAcreatedduringtranscriptiongetsdecodedandturnedintoaseriesofaminoacids (throughthecodontable),andlatertheyproduceselectedproteins.Weusetheterm expression astheprocessofdisassemblingageneandassemblingitscorrespondingprotein. Fig.1.4 givesamagni fiedviewoftheCentralDogma process.
AnatomyofCRISPRmachine
Letmeexplainthemeaningofamiracle:Thereligionsinterpretamiracleasdivineintervention.Butthisisnotwhatwe’re interestedin.Inscience,wedonothavemiracles thetermisdrasticallyabusedandtwisted.Wedohaveunexpected surprisesduetoanunearthed,unscheduledevent,whichwillbescienti ficallyexplainedlater.Ascientificmiracleisa steppingstoneforfurthermiracleswhichwillenhancehumanendeavorforfurtherprogress.Ascienti ficmiracleisameans andnotanend.
Muslim ’sfocusonmedicinewasfosteredbytheQur’anandthehadith,asindicatedinthefollowingsayingtheProphet Muhammad: “Allahhasnotsentanydiseasewithoutsendingacureforit.” CRISPRanditsfuturegenerationshavebeen secretlyhiddenintheQur’anandwillbealldiscoveredtoeradicateallthediseasesoftheEarth.
CRISPRisthemininameof(clusteredregularlyinterspacedshortpalindromicrepeats)whichisacrazy longname thatweprobablywillnotneedtoremember.CASstandsforCRISPR-Associatedgene.CRISPRgotitsnamebecause scientistsnoticedthatitcontainedlotsofsmallpalindromicsequencesrepeatedthroughtheDNA.Apalindromicisaword thatreadsthesameforwardandbackwardas “tacocat.” ApalindromicDNAsequencecouldbe “AATTAA,” miraculously powerfulgenomeeditingtool.CRISPRsinceitscreationhatcreatedanewdimensionongeneticengineeringforediting genomes(see Fig.1.5 foradditionalexplanation).Weallarefamiliarwithwordprocessing.Weadd,cut,paste,search, delete,andreplacewordsinatextwithutmostsimplicity.Well,CRISPRisageneprocessor,doingexactlywhatword processorsdo.
Havingsaidthat,wecansaythatCRIPSRisascientifi c miracle withgreatmomentumforhelpinghumanity.Fixing DNAdefectsandeliminatingcomplexdisorderssuchasautism,Alzheimer’sdisease,anddiabetesisanincredible achievementcomparabletothediscoveryofvaccine.JerryLewiswillbecryinginhisgravefromjoywhenhe fi ndsout thathismusculardystrophychildrenwillbeabletowalkin5years.CRISPRistrulyaHolyGrail.
CRISPRstructure
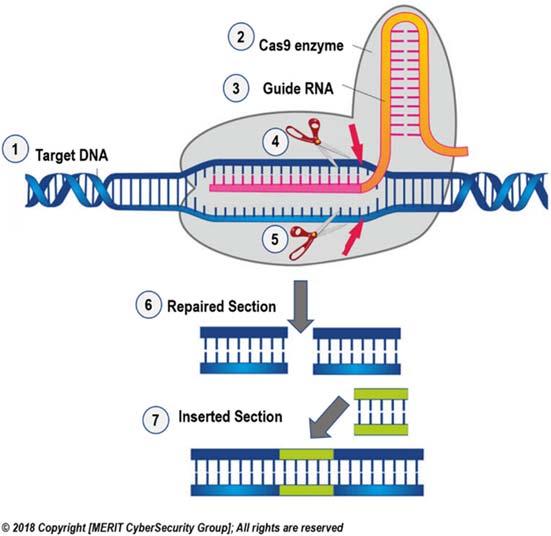
FIGURE1.5 (1)ADNAhasacorruptstripofgenesandneeds tobereplacewithahealthyone(2)UndertheordersofRNA,Cas9isbuilt(3)RNAlearnsthelocationofthedefect(4)and(5)Cas9 cutsthedefectstrip(6)TherepairofthetargetDNAstarts(7)The healthystripisinsertedasareplacementofthemutatedone.
CRISPRtechnologyisasimpleyetpowerfultoolforeditinggenomes.ItallowsresearcherstoeasilyalterDNAsequences andmodifygenefunction.CRISPRislikeaguninthehandofthederangedmind.Inpopularusage,Cas9 “CRISPRassociated ” isanenzymethatactslikeapairofmolecularscissors,capableofcuttingstrandsofDNA.InapaperpublishedNov.10,2017,inthejournal NatureCommunications,MikihiroShibataofKanazawaUniversityandHiroshi NishimasuoftheUniversityofTokyoshowedinavideowhatitlookslikewhenaCRISPRisinactionforthevery first time.
Virusesareacommonthreattocellularlife,nottheleasttobacteriaandarchaeawhoconstitutethemajorityoflifeon Earth.Consequently,avarietyofmechanismstoresistvirusinfectionhasevolved.Arecentdiscoveryistheadaptive immunecalledCRISPR-Cas,whichprovidessequence-specificadaptiveimmunityandfundamentallyaffectourunderstandingofvirus hostinteraction.CRISPR-basedimmunityactsbyintegratingshortvirussequencesinthecellallowing ittoremember,recognize,andclearinfections.
CRISPRusingenzymesasscissorstosliceandsplicesectionsofDNAastheyareunwantedsegmentsandpatchin substitutes.Intheory,italsomightmakeitpossibletocreatedesigner babies thataresmarterorbetter-lookingthanother individuals.Butsomepeoplehavequestionedwhethersuchtinkeringwithhumancellswouldbelikeplayinggod.Many peoplealsoworrythateditingisnotsafe.
NatureMagazineinitsNovember15,2016announcedthat “On28October,ateamledbyoncologistLuYouat SichuanUniversityinChengdudeliveredthemodi fiedcellsintoapatientwithaggressivelungcanceraspartofaclinical trialattheWestChinaHospital,alsoinChengdu.” Theteamofresearchersremovedimmunecellsfromtherecipient’s bloodandthentheyusedCRISPR Cas9,tocutaDNA-cuttingenzymewithamolecularguidecalledgRNAtellsthe enzymepreciselywheretocut.TheprocedurewastocutoffthegenecodesproteinPD-1,whichstopsthecell’simmune responseandallowscancerfunctiontoproliferate.Theteamallowedgrow “culture” thenumberhealthyDNAmolecules andinjectedthembackintothepatient,whohaslargelungcancer.WithoutPD-1,theeditedcellswillbecomepartofthe nativecellsandwillattackanddefeatthecancer.
Ithashappened.The firstchildrengeneticallyengineeredwiththepowerfulDNA-editingtoolcalledCRISPR-Cas9 havebeenborntoawomaninChina.Theiralteredgeneswillbepassedtotheirchildren,andtheirchildren’schildren.Join JenniferDoudna,asweexploretheperilsandthepromiseofthispowerfultechnology.Itisnotthe first-timehuman ingenuityhascreatedsomethingcapableofdoingusgreatgoodandgreatharm.Areweuptothechallengeofguidinghow CRISPRwillshapethefuture?