Staying One Step Ahead
Proactive Steps to Minimize and Prevent Cyber Attacks Based on the Latest Threat Research


How to Effectively Implement Zero Trust Architecture in Your Organization
Getting the Most Out of Your Attendance at the 16th Annual ISAC Meeting
New Guidance to Defend Against Living off the Land Attacks
Today’s cyber threat landscape is constantly evolving. It requires constant vigilance and adaptation to stay ahead of the attackers . An ounce of prevention is worth a pound of cure. That’s why we’re always on the hunt for new, innovative solutions to help our community improve their cyber defenses and stop cyber attacks before they happen.
A PUBLICATION FROM
Security that never sleeps.
24×7×365 Network Monitoring and Management

LEARN MORE
David Bisson
Aaron Perkins Autum Pylant
Jay
Stephanie Gass
Josh Moulin
Aaron Perkins
Natalie Schlabig
Karen Sorady
Valecia Stocchetti
Summer 2023 i Contents Featured Articles Service That Never Settles An in-depth look into how CIS develops new services and solutions to help advance the cyber defense programs of U.S. SLTTs 3 A Cyber Attack on Your Organization Is Not Inevitable, but You Should Plan for It Evaluating today’s cyber threat landscape based on the latest research from Rubrik Zero Labs and proactive steps your organization can take to improve its cyber defenses 6 Zero Trust Architectures Deliver Better Security Outcomes Expert advice on the key components needed to develop an effective Zero Trust Architecture in your organization 10 Abusing Scheduled Tasks with Living off the Land Attacks Our new guidance to help address cyber attacks that take advantage of your organization’s regular tools and procedures to conceal themselves 15 Quarterly Regulars Quarterly Update with John Gilligan 1 News Bits & Bytes 2 Cyberside Chat 14 ISAC Update 17 Event Calendar 19
2023 Volume 7 Issue 2 Editor-in-Chief
Mineconzo
Editor
Summer
Michael
Supervising
Laura MacGregor
Copy Editors
Contributors
Staff
Billington
Cybersecurity Quarterly is published and distributed in March, June, September, and December. Founded MMXVII. Published by Center for Internet Security, 31 Tech Valley Drive, East Greenbush, New York 12061
questions or information concerning this publication, contact CIS at info@cisecurity. org or call 518.266.3460 © 2023 Center for Internet Security. All rights reserved.
For
Stop cyber attacks in their tracks.
Ad Placement
CIS Endpoint Security Services, now with Spotlight
LEARN MORE
QuarterlyUpdate
with John Gilligan
As the warmer weather arrives and the days get longer, we are pleased to present the summer issue of Cybersecurity Quarterly.
The past several months have been quieter with regard to major cyber attacks. However, we recently saw the vulnerability in the MOVEit product resulting in the compromise of many organizations, including a number of government organizations. At this time, it does not appear that the government organizations were victims of targeted attacks; rather, they were opportunistic targets due to their use of unpatched versions of MOVEit. Nevertheless, the number of affected organizations indicates that many organizations are not responding quickly enough to newly discovered vulnerabilities.
In addition to MOVEit, ransomware and other attacks continue to increase – particularly under the sponsorship of nation states who are using cyber attacks to pursue their political objectives. For instance, Russia and their surrogates have stepped up their cyber campaign against Ukraine as well as against countries and organizations that are viewed as supporters of Ukraine.
Appropriately, the theme of this issue is preventative security. The objective is to share insights into how you can take steps to reduce your cyber attack surface and to reduce the potential of becoming a victim of an attack.
Josh Moulin, SVP and Deputy General Manager of CIS Operations and Security Services (OSS), has provided an article on the process used to evaluate products for potential use by U.S. State, Local, Tribal, and Territorial (SLTT) organizations. The process is called ‘proof of value’ and is intended to validate the effectiveness of candidate technologies that appear to meet SLTT needs. This article discusses two ongoing proof-of-value efforts on email security solutions and web application firewalls (WAF). Email is the delivery method for many cyber attacks. As such, the proof-of-value is examining potential commercial solutions that can be both cost-efficient and operationally effective for SLTT organizations. The WAF proof-of-value is assessing possible technologies to strengthen websites against the most common cyber
attacks. The SANS organization has also contributed a piece that discusses the components of an effective zero trust architecture and how implementing zero trust improves the outcomes of your cybersecurity program.
Our partners at Rubrik contributed a piece that summarizes their recent report entitled, “The State of Data Security: The Hard Truths.” Rubrik’s research highlights the challenge that many organizations don’t have a good handle on the sensitive data they possess, and it identifies strategies to assess your data and to protect against common attack vectors.
CIS’s Valecia Stocchetti has provided an article that addresses Living off the Land (LotL) attacks, which are cyber attacks that utilize routine system functions to mask or hide the attack and thus increase the difficulty of discovery. In her article, Valecia explores one particularly complex aspect of LotL attacks that focuses on leveraging the scheduling of what would otherwise be routine tasks and identifies effective countermeasures in the implementation of the CIS Critical Security Controls.
Karen Sorady, Vice President for MS-ISAC Member Engagement, has provided updates on the status of the Multi-State and Elections Infrastructure ISACs and provides a preview of the upcoming MS-ISAC Annual Meeting that will be held in Salt Lake City August 6-9.
Finally, Stephanie Gass, Director of Governance, Risk & Compliance at CIS, authored this quarter’s CISO column. Stephanie’s column focuses on the importance of proactive security measures.
Please enjoy this quarter’s issue, and have a great summer!
Best Regards,
 John M. Gilligan President & Chief Executive Officer Center for Internet Security
John M. Gilligan President & Chief Executive Officer Center for Internet Security

Summer 2023 1
“
The theme of this issue is preventative security. The objective is to share insights into how you can take steps to reduce your cyber attack surface.”
NewsBits&Bytes
Center for Internet Security, Google Cloud Announce Strategic Alliance
The Center for Internet Security (CIS) has launched the CIS & Google Cloud Alliance to help advance security and resilience for the broader technology ecosystem, with an emphasis on the public sector. The Alliance will combine the companies’ extensive experience to offer greater security to these organizations.
“The launch of the CIS & Google Cloud Alliance is just the start in our collaboration and ability to help more organizations through these continual challenges,” said MK Palmore, Director, Office of the CISO at Google Cloud. To learn more, read our recent press release.
CIS Announces Grant Recipients of Alan Paller Laureate Program
CIS is proud to announce the inaugural grant winners of the Alan Paller Laureate Program. The program awards up to $250,000 annually to eligible organizations or individuals whose pilot projects, proofs of concept, or existing programs are selected through a competitive application process.
The 2023 winners are Stan Stahl, President of SecureTheVillage; Jonah Wisch, Program Director of the National Cybersecurity Center and leader of Project PISCES (Public Infrastructure Security Cyber Education System; and Chris Abell, Executive Director of Carroll Technology and Innovation Council. Visit our website to learn more about the program.
Center for Internet Security Joins the Microsoft Intelligent Security Association


CIS has been inducted into the Microsoft Intelligent Security Association (MISA). Microsoft created MISA to build an ecosystem of intelligent security solutions that defend against a world of increased threats. Today, MISA boasts a vibrant ecosystem of over 300 members.
As cyber threats continue to escalate, CIS and Microsoft are combining their expertise to better serve organizations of all types with impactful cybersecurity best practices. This announcement highlights the importance of the overall strategic partnership between CIS and Microsoft. To learn more, read our recent press release.
10 Winners Selected in National Cybersecurity Poster Contest
Ten students from across the U.S. are helping educate others about the dangers they may encounter online. Their artwork has been selected by CIS and the MultiState Information Sharing and Analysis Center (MS-ISAC) from hundreds of submissions in the national “Kids Safe Online” poster contest. The annual contest is a way to teach students about the dangers lurking online and how they can protect themselves. The winning artwork will be featured in the 2024 cyber safety kid’s activity book. Congratulations to this year’s national winners:

First Place – Faith, Grade 11, Virginia
2nd – Maliyah, Grade 7, South Dakota
3rd – Michael, Grade 10, Texas
4th – Deangelo, Grade 5, Texas
5th – Jax, Grade 4, Mississippi
6th – Livian, Grade 12, Iowa
7th – Sahana, Grade 3, New York
8th – Victoria, Grade 5, Texas
9th – Rosalind, Grade 11, Virginia
10th – Isaac, Grade 2, New York
2 Cybersecurity Quarterly
Service That Never Settles
How CIS continues to advance on the front lines of cyber defense for the U.S. State, Local, Tribal, and Territorial government organizations that depend on it.
By Josh Moulin
In the ever-evolving threat landscape, there is no such thing as “perfect protection” from cyber threat actors (CTAs). With new cyber threats evolving daily, U.S. State, Local, Tribal, and Territorial (SLTT) governments must be able to similarly evolve in their cyber defense efforts. At the Center for Internet Security, Inc. (CIS®), we consider our support to SLTT government organizations and members of the Multi-State and Elections Infrastructure Information Sharing and Analysis Centers (MS-ISAC® and EI-ISAC®) a dynamic responsibility. Our low- and no-cost services are constantly being improved, and we are always looking for new ways to support the cyber defense programs of our highly-targeted SLTT constituents. We believe that cybersecurity is a full-contact sport, not a chess match. It requires constant vigilance and adaptation to stay ahead of the attackers.
The Good Keeps Getting Better
Existing services like Malicious Domain Blocking and Reporting (MDBR), Albert Networking Monitoring and Management, and Endpoint Security Services (ESS) are constantly being updated with new threat intelligence by our full-time cyber threat intelligence team and our partners in industry, the federal government, SLTT members, and other ISACs. The massive amount of threat data aggregated by the MS- and EI-ISACs is one of our
strongest assets in protecting SLTTs from CTAs. By using human analysts and new data analytic and automation capabilities introduced this year, we are able to push updated intelligence to our suite of products and services across the United States, helping our members detect and respond to malicious activity before it causes harm.
The Strong Keeps Getting Stronger
The strength of the services offered to MS- and EI-ISAC members is directly linked to the strength of the ISACs themselves. As the MS-ISAC celebrates its 20th anniversary this year, it has seen rapid growth in recent years, from 1,500 members in 2017 to over 15,600 as of the writing of this article. That exponential growth in members has come with a corresponding growth in our data set, benefiting the larger MS-and EI-ISAC community. When the CIS Security Operations Center (SOC) identifies an attack against a monitored SLTT using a new technique or tactic, our SOC works in conjunction with other CIS teams to rapidly push that information to our membership, partners, and portfolio of services. So, when it comes to the MS-ISAC, more members sharing threat intelligence and using our monitoring tools translates to better threat data and ultimately more protection for the rest of the SLTT membership.

Summer 2023 3
We are always looking for new ways to support the cyber defense programs of our highly-targeted SLTT constituents. We believe that cybersecurity is a full-contact sport, not a chess match. It requires constant vigilance and adaptation to stay ahead of the attackers..
The Front Lines Keep Moving Forward
In the ever-important work of improving the overall cybersecurity posture of U.S. SLTTs, we are always pushing the front lines of cyber defense forward. As computer scientist Alan Kay said, “The best way to predict the future is to create it.” While we continue to improve our existing services to MS-ISAC and EI-ISAC members, we’re always exploring potential new services that can create a better, more secure future for SLTT organizations. Currently, the ISACs are exploring new cost-effective and innovative technologies including an email protective service and a web application firewall (WAF) based on attack trends and member feedback.

The email protective service pilot is currently in a proofof-value (POV) stage with SLTT members providing feedback and value assessments. The email protection service focuses on providing a simple yet effective email protection against phishing attacks, malicious file attachments, spam, and other email-based attacks such as ransomware for our MS-ISAC and EI-ISAC members who may lack basic inbound email protection aside from built-in capabilities. Already, the email security solution has blocked some 28,000 malicious emails from reaching their destined SLTT inbox.
WAF is a newer initiative for the ISACs and is currently in the pre-kickoff stage of POV testing. This POV is
intended to test the viability of providing a cloud-based solution to protect applications and APIs from a wide range of network and application-layer threats, including distributed denial of service (DDoS) attacks against internet-accessible systems. We’re currently exploring the most appropriate technology provider for this service and determining which vendor’s WAF solution can be provided at low cost and with particular benefit to the SLTT community. MS- and EI-ISAC members will hear about this important development more in the coming weeks as we look to onboard interested organizations to participate in the POV process.
Cyber Defense in Motion
Physics tells us that an object in motion tends to stay in motion. Cyber threat intelligence tells us that cyber threat actors seem to never rest, and by some estimates, a new attack appears somewhere online every 39 seconds. CIS is committed to remaining in motion when it comes to evolving cyber defense solutions to meet the evolving cyber threat to SLTTs.
You can learn more about how we’re supporting SLTT organizations at https://www.cisecurity.org/ms-isac or by reviewing our ISAC Weekly Digest that goes out to MS-ISAC members. If you’re a member and are not currently receiving that informative resource, contact info@cisecurity.org to be added to the distribution list.
Recognized globally for his expertise in cybersecurity, Josh Moulin is the Senior Vice President of Operations & Security Services at CIS and has worked in cybersecurity since 2004. Prior to joining CIS, Moulin was an Executive Partner at Gartner and advised federal government and defense executives, a CIO and CISO within the U.S. nuclear weapons complex, and a commander of an FBI cybercrimes taskforce. He holds a master’s degree in Information Security & Assurance and over a dozen certifications in digital forensics and cybersecurity.
4 Cybersecurity Quarterly
Physics tells us that an object in motion tends to stay in motion. Cyber threat intelligence tells us that cyber threat actors seem to never rest, and by some estimates, a new attack appears somewhere online every 39 seconds.
Rubrik Zero Labs
of organizations received half or less of their data after paying a ransom.
See what 1,600+ IT and security leaders said about how cy bercrime affects their organizations in this new report by Rubrik Zero Labs.

You 'II learn what happens at each stage of a ransomware attack-from the intrusion to the response-featuring a real-life case study.
See the hard truths of data security

rubrik.com/zero-labs




l □□ I l □□ I l □□ I
• p
A Cyber Attack on Your Organization is Not Inevitable, but You Should Plan for It
Whether the result of a sophisticated cyber threat actor or a more mundane attack vector, cyber attacks can and do happen to even the best of organizations. However, many can be prevented or minimized with proactive preparation.
By John B. Murphy and Steven Stone
In today’s interconnected world, cyber threats pose a significant risk to organizations across all industries. While they may seem like an unavoidable part of operating, many cyber attacks can be prevented, or their impact minimized, through proactive planning and robust security measures.
A common misconception is that cyber attacks are purely the result of sophisticated, targeted efforts by cybercriminals or nation states. But it’s important to note that nation state-level attacks are not that common for the vast majority of organizations.
Instead, a significant number of attacks are often attributable to unintended risk decisions, hard work by determined “competitors” (we’ll explain shortly), and some measure of bad luck. Each of these underlying causes can be effectively and proactively managed.
In this article, we’ll reference the latest Rubrik Zero Labs report, The State of Data Security: The Hard Truths, to explore why cyber attacks aren’t necessarily inevitable but are still very much worth planning for. The report
consolidates findings from our client base of over 5,000 organizations as well as data from our survey of 1,600 organizations globally. We’ll also talk about why you should think of incident response and recovery as separate things, and we’ll discuss the importance of planning for potential threats to ensure business continuity and cyber resilience.
Understanding the Cyber Threat Landscape
Zero Labs Report Finding: Rubrik Zero Labs noted that 99% of IT and security leaders dealt with at least one cyber attack in 2022, with the average organization experiencing 52 events in 2022.
Cyber threats are constantly evolving, and while it’s true that cybercriminals employ increasingly sophisticated tactics, techniques, and procedures to compromise organizations, all attacks are not created equal. In fact, the victim organization may do more to harm itself than the attacker – even though that may not be apparent until after the attack.
Zero Labs Report Finding: 61% of cyber attacks leverage a known vulnerability or method.
Attacks come in all forms, but some of the most common attacks involve the following: email or text phishing, business email compromise, data exfiltration, zero-day vulnerability exploits, known vulnerabilities that haven’t been patched yet, insider threats, and ransomware.
Cause #1: Unintended Risk Decisions
If you had to capture the challenges of managing your organization’s cyber threat landscape, Whack-A-Mole would be a pretty good choice.
6 Cybersecurity Quarterly
A common misconception is that cyber attacks are purely the result of sophisticated, targeted efforts by cybercriminals or nation states. But it’s important to note that nation state-level attacks are not that common for the vast majority of organizations.
Looking past the emotional elements of an attack for a moment, it’s important to note that attacks are often successful because of the unintended consequences of your risk management practices or lack thereof.
This is what happens when organizations forego formally assessing risk impacts and instead rely on instinct, experience, or concern about the potential unintended consequences of making changes rather than a more structured risk evaluation.
Simple examples might include:
• Not patching all instances of a vulnerability or patching just those instances on the most critical (or least critical) apps.
• Not prioritizing needed application security changes in the same way as new business functionality.
• Security patches or enhancements are automatically deferred due to unquantified concerns about impacts on application performance or network throughput.
Zero Labs Report Finding: While malicious cyber attacks dominated the focus for IT and security leaders, accidental incidents also led to profound impacts. In 2022, 42% of these leaders dealt with inadvertent data exposure, and 44% dealt with production outages from non-malicious insiders or events.
Actively managing those risk decisions can prevent attacks and deliver the following benefits:
• Minimizes the likelihood of a successful attack that can result from focusing too much on “keeping the lights green” (i.e., not periodically evaluating longstanding operational or security practices to ensure that they still add value or can cause blind spots in the environment).
• Reduces potential damage from an attack by actively evaluating potential risks before attacks occur.
• Helps ensure business continuity. Forethought and planning can reduce the time it takes to restore key capabilities and services, speeding your recovery following an incident.
• Helps ensure regulatory and legal compliance. Data protection is high on the priority list for many countries and states. The California Privacy Rights Act (CPRA) and the Health Insurance Portability and Accountability Act (HIPAA) are examples of heightened expectations by global regulators. Managing the potential risks in how you store and manage
data and knowing what sensitive data you have are paramount.
Cause #2: Hard Work by Determined Competitors
Cyber attacks are often carried out by persistent threat actors. But terms like “threat actor” may not frame them in a way that helps you to think about who they are or what they’re after when it comes to formulating your defense plan.

You may find it more helpful to think of them as external organizations that are competing with you for control of your organizational data. Just as you need to protect critical data to meet your key objectives, they also need your data to meet their key business objective: monetizing its value and forcing you to pay for its return. Ransomware gangs are not nonprofits. Like most competitors, they’re committed to their mission and will put in the necessary effort to make themselves as financially successful as possible because they know they won’t be around long if they don’t.
Zero Labs Report Finding: 99% of global organizations reported having a data backup solution. Notably, these solutions were targeted in 93% of malicious attacks, and the attackers were at least partially successful in more than 73% of their efforts to affect data backups.
How
can you thwart this competition?
Investing in targeted data security controls that provide concrete data protections like immutability, an air gap from your production network, continual monitoring, and guaranteed recoverability may be better ways to compete against them than adding a new endpoint tool or building more monitoring solutions that no one has the time to look at. Secure your data when it becomes valuable, do
Summer 2023 7
so frequently to shorten any data gaps between your backups and your production data, and continually test your recovery plans. Keeping “competitors” out of your production data may not always be possible, but keeping them out of your backup data certainly is.
Additionally, you can incorporate red, blue, and purple team practices to help reduce the value of your data to a competitor. This can start with a simple scan of your environment to find unencrypted, sensitive data. If your scans find any, that’s a good indicator that the bad guys will too. But you can reduce that potential risk by working with your stakeholders to encrypt visible sensitive data and continually rescan to ensure that the problem is no longer there. This way, even if the data is exfiltrated, it can’t be used as leverage against your organization, customers, suppliers, or employees.
Cause #3: Bad Luck
Sometimes, despite the best plans and robust security measures, bad luck can still play a role in cybersecurity incidents. In this section, we’ll discuss the various ways bad luck can manifest and the actions organizations can take to mitigate its impact.
First, identities are sometimes compromised. Despite strong security measures, user identities can still be compromised through phishing attacks, data breaches, and shoulder-surfing, for example. To combat this, continually review individual user entitlements and reduce privileges to only those that are strictly needed for day-to-day work (i.e., the principle of least privilege). This helps reduce the impact of any credentials that may fall into the wrong hands and can significantly make determining the blast radius easier.
Second, zero days are unpredictable. Zero-day vulnerabilities will happen, but they are difficult to defend against. That’s why you should assume that the unthinkable will happen. Actively plan for and conduct cyber resiliency exercises with this in mind. Stay up to date with the latest threat intelligence, patch vulnerabilities promptly, and continuously monitor systems and data stores for signs of intrusion.
Zero Labs Report Finding: While virtually all organizations are concerned about zero-day attacks, it was only the top concern in 13% of organizations globally in 2023. Data breaches and ransomware occupied the top two concerns overall.
Also, the third parties you depend on sometimes have issues that will impact you. All organizations leverage third parties for software, technology services, and identity services, and this will only increase as more
applications move into cloud technology providers or SaaS services. You should thoroughly inventory your third-party vendors and leverage cybersecurity assessments and software bill of materials (i.e., what components are in the software) to understand potential risk impact on your environment. Make sure that suppliers have adequate security measures in place as well as establish clear communication channels and mutually agreed expectations for incident response.
Zero Labs Report Finding: For organizations with a successful intrusion in 2022, 48% of these organizations changed third-party partners and vendors as a direct result of the intrusion.
Finally, recognize that the very nature of technology and operations gives us confidence that things won’t always go as planned. Acknowledge that the complexity of technology and business operations means that things can and will go wrong. Accept that the unexpected will occur, and focus on your operational resilience. Also, test your incident response plans thoroughly and frequently so that everyone knows what to do and who is doing it. How well and how quickly you react to the problem can be just as important as the actions you take to remediate it.
Zero Labs Report Finding: 45% of Rubrik clients secured data across on-premises, cloud, and SaaS environments in 2022. More than a third (36%) of organizations use multiple cloud vendors concurrently. Across all of these distinct environments, a typical organization secured more than 25 million sensitive data records in these diverse hybrid environments.
Simple Actions You Can Take Today
While any or all three of these causes can play a role in cybersecurity incidents, you can take pragmatic steps to minimize their impact. You can better navigate these challenges by acknowledging the complexity of your work, objectively reporting on opportunities to improve your responses, and maintaining open communication with stakeholders. We’ll leave you with a few practical things to try today.
• Test your data recovery plans routinely. Regularly testing data recovery plans helps ensure that Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) are realistic and achievable.
Zero Labs Report Finding: Only 54% of global organizations tested their data recovery actions in 2022.
• Build a few meaningful metrics (start with three) and regularly communicate to all stakeholders on your cyber recovery capabilities. Don’t let perfect be the
8 Cybersecurity Quarterly
enemy of good. Focus on areas such as the effectiveness of incident response plans, recovery time, and the impact of security incidents on business operations. And encourage suggestions that improve their value. Embrace the maxim that “no plan survives first contact with reality.”
• Communicate results in terms of business risk and impact. When discussing cybersecurity incidents and recovery efforts, it’s important to frame the conversation in that context. Speaking about the potential impacts on your mission in that language helps everyone collaborate and prioritize efforts more effectively.

• Ensure that you are backing up your organization’s most critical systems and data. (This may be a VM, a database, an email, or a SaaS application.) These backups must be treated like your organization’s crown jewels and thus must be natively immutable, isolated from the network or other applications, and continuously monitored for suspicious activity.
• Ensure that your security operations team is familiar with the security capabilities of your backup solutions (if present).
• With the right underlying backup technology, you can create triage, hunt, and recovery functions in your operational plans and procedures. The right technology can also reduce the likelihood that you’ll tip off the bad guys or impact production users while conducting investigations.
• Enabling other security and business continuity stakeholders in your organization to leverage
capabilities native to your data backups can help reduce downtime, rapidly build trust and protection, and even enhance your brand.
To dive deeper into what’s top of mind for IT and security leaders and to see how cybercrime affects their organizations, read the latest report from Rubrik Zero Labs. You’ll learn what happens at each stage of a ransomware attack – from the intrusion to the response – featuring a real-life case study. See the full report at https://www. rubrik.com/zero-labs .
John B. Murphy, Ph.D., CISSP, CISM, ISSMP is Rubrik’s Global Field Chief Security Officer. Murphy is an experienced Cyber Security and Enterprise Technology leader with more than 20 years of leadership experience at some of the world’s largest financial organizations. He is responsible for working with Clients and Partners to help maximize the cyber and business benefits from their investments in Rubrik’s technologies and solutions. Prior to joining Rubrik, Murphy held senior leadership positions at Bank of New York Mellon, Deutsche Bank, and Automatic Data Processing in addition to advisory roles for several software startups.
Steven Stone leads Rubrik’s data threat research unit to uncover real-world intrusions from a range of threats including espionage-based data breaches and ransomware attacks as well as to inform customers and partners of the best ways to proactively address risk in their business operations. He has over 15 years of experience in threat intelligence with roles in the U.S. military, intelligence community, and private sector, including Mandiant/ FireEye and IBM. Most recently, Stone was Vice President of Adversary Operations at Mandiant, leading global teams who were responsible for adversary hunting, attribution, and data collection efforts.
Summer 2023 9
Zero Trust Architectures Deliver Better Security Outcomes
Trust nothing, validate everything. By removing implicit trust throughout an enterprise, today’s zero trust security architectures affect identity, devices, networks, applications, workloads, and data.
By Ismael Valenzuela
In today’s digital era, the way we live, learn, communicate, interact, work, and generally experience the world relies heavily on virtual technologies. Highly sensitive information once protected by its inaccessibility to anyone outside of a small number of people with physical access to a medical record, bank ledger, government file cabinet, or personnel file is now potentially accessible to anyone with enough time, resources, determination, and adversarial know-how. As more and more critical data is surrendered through transactions into the digital universe, the need to protect that data intensifies. At the same time, the effectiveness of traditional perimeter-centric cyber defense strategies has proven time and again to be insufficient against increasingly savvy adversaries.
Enter zero trust – a term introduced in 2010 by Forrester research analyst John Kindervag, who described an approach that assumes neither those outside nor inside the organization’s network perimeter should be blanketly trusted. Fast forward to 2023, and zero trust architectures (ZTA) have become the aspiration and objective of cyber defense operations nationwide. Federal, state, and local government agencies have taken explicit steps in recent years to address cybersecurity shortcomings by embracing the concept of zero trust. The release of Executive Order (EO) 14028, “Improving the Nation’s Cybersecurity,” in May of 2021 followed by the Office of Management and Budget’s (OMB) release of a “Federal Strategy to Move the U.S. Government Towards a Zero Trust Architecture ” are a testament to our nation’s zero trust-centric cyber priorities, with those concerning state, local, and tribal governments following suit.
A zero trust architecture is not a security product, a tool, or a configuration. Rather, it is a strategy. It is a data-centric approach to cybersecurity that embraces core tenets of a zero trust mentality. The ZTA objective is to
reduce implicit trust across the enterprise and establish a modern security architecture that affects the security approach to identity, devices, networks, applications, workloads, and data. Adopting zero trust is a journey toward better cybersecurity rather than a destination –one that may take multiple years to fully adopt but for which every organization should aim.
8 Core Components of ZTA
A quick search of ZTA returns numerous results, each presenting a unique interpretation of zero trust. Many regulatory bodies and government agencies have published descriptions of zero trust in the context of their organizational or community objectives. Most zero trust strategies share all or some of the following eight core components, which are represented by five pillars and three cross-cutting elements.
Implementing a zero trust architecture begins with a journey-mapped plan that incrementally moves an organization from an initial to an advanced to an optimal zero trust posture. The plan should consider an extensive list (not covered in this article) of desirable approaches and operations across the five pillars and three cross-cutting ZTA elements. Each organization’s plan would follow an assessment of their current systems, processes, prior-
10 Cybersecurity Quarterly
Adopting zero trust is a journey toward better cybersecurity rather than a destination – one that may take multiple years to fully adopt but for which every organization should aim.
ities, personnel, resources, and infrastructure. The following section provides high-level examples of how each zero trust component may realistically affect cybersecurity operations.
Users and Identity Pillar
Zero trust represents a shift away from traditional perimeter-based security to an identity-, session-, and data-centric approach focused on high-value assets and continuous re-evaluation of trust. This means identity and access management (IAM), strong multi-factor authentication (MFA), and privileged access management (PAM) are fundamental capabilities leveraged to achieve zero trust maturity. Access to organizational resources would be granted on a per-session basis and determined by risk-based dynamic policies that inform the monitoring of users, devices, applications, network infrastructure, and expected behaviors. This adaptive and continuous re-evaluation of trust aims to reduce implicit trust across systems.
Pillar
Maintaining a strong asset management program is a key component of a mature cybersecurity operation –and is not a small undertaking given the explosion of mobile computing devices and bring-your-own-device scenarios. Implementing ZTA includes but is not limited to establishing mobile device and Internet of Things (IoT) policies, maintaining a hardware bill of materials (HBOM), and implementing robust asset discovery, device authentication, and analysis capabilities.
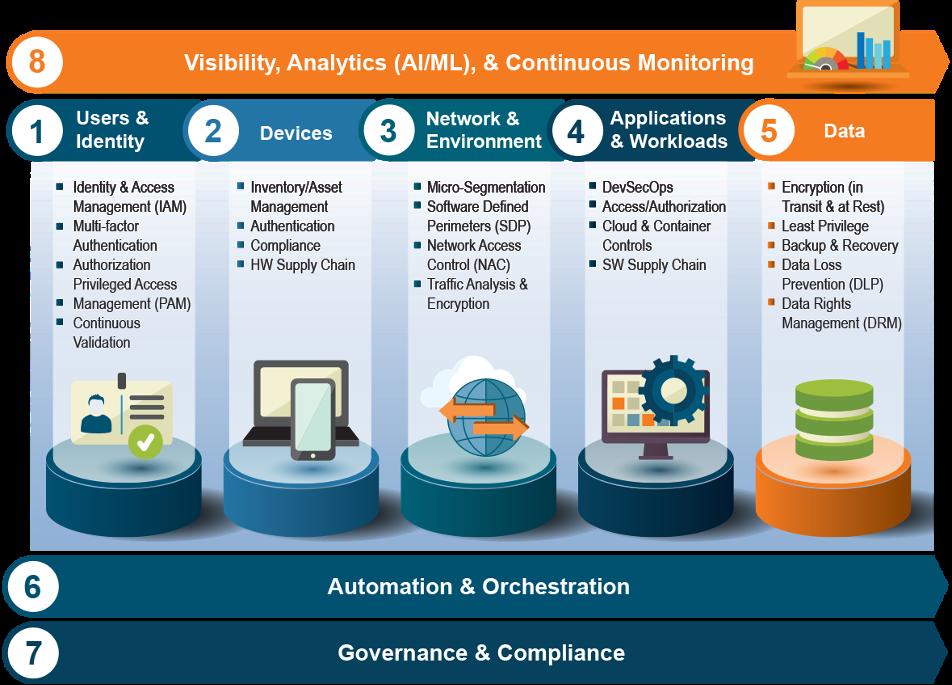
Network and Environment Pillar
All network traffic, ports, protocols, interfaces, and connections should be monitored and managed at the session level to prevent, identify, and respond to suspicious activity. Further, the ability to apply granular controls and access rights throughout a network or system – a hallmark of ZTA – requires some degree of network segmentation. ZTA leverages network segmentation (micro and/or macro) by dividing the network into
Summer 2023 11
Devices
granular homogeneous zones. While approaches vary, segmentation can occur in cloud, on-prem, and hybrid environments.
Applications and Workloads Pillar
Software applications and workloads, including internal and external services and interfaces, present complexities for zero trust systems. Because zero trust views all identities and actors as potentially untrustworthy, system-to-system handshakes buried deep within applications must be configured to frequently or continuously validate their identities. Establishing and maintaining a software bill of materials (SBOM) including supply chain information on third-party suppliers and connections is a likely place to begin with this pillar.
Data Pillar
Zero trust assumes a breach will happen and therefore requires all data be encrypted in transit and at rest. This limits the damage and degree of exposure caused by a breach. Being the currency and crown jewel of digital systems, data should also be routinely backed up to support data loss prevention (DLP). Further, data must be protected based on its sensitivity level, with protections that are commensurate with the data’s sensitivity and need for confidentiality, integrity, and availability.
Automation and Orchestration Element
Security incident and event management (SIEM) tools and security orchestration and automation (SOAR) tools can help maximize other cybersecurity investments. When expertly implemented, these tools can shore up gaps in cybersecurity posture and help automate zero trust configurations and operations across zero trust pillars. Equipped with evolving machine learning capabilities, the tools are becoming smarter, especially when operated by skilled cybersecurity specialists whose inputs train machine learning algorithms.
Governance and Compliance Element
Zero trust is a complex and evolving journey best supported by cybersecurity policies and procedures as well as continuous monitoring and improvement activities. A reasonable first step in a zero trust effort is to establish a governing entity to create a plan. Growth can then be managed in an intentional and stepped manner that aligns the goals and objectives of the organization. The following resources contain helpful information for any organizations looking to implement zero trust:
• NIST Special Publication 800-207 on Zero Trust Architecture
• CISA Zero Trust Maturity Model
• DOD Zero Trust Strategy
Visibility, Analytics, and Continuous Monitoring Element
Maintaining a zero trust posture is an exercise in in-depth, complex cybersecurity management. It requires continuous monitoring and end-to-end visibility into a system’s cybersecurity posture, assets, data, configurations, traffic and user activities, anomaly detection, privileged account events, and incident response activities, to name a few. SOC teams should increasingly look to automation and machine-driven analytics to help manage the zero trust systems of today and tomorrow.
ZTA is About Managing the Who, What, When, Where, and Why of IT Systems
ZTA isn’t a trivial task and requires a shift in mentality and culture. There is no one size fits all. Fundamentally, ZTA is about managing access and protecting data at all levels of a system in a least-privilege fashion – trusting nothing and validating everything. This is mostly accomplished by limiting the rights of users and transactions by granting the minimum allowances required to accomplish specific tasks.
Embracing zero trust aspires to ensure over time that only those who need access will be authenticated and authorized to access specifically what they need, when they need it, from where they are allowed to access it, and to complete the specific tasks associated with why they need it throughout an enterprise system. Anything less would be contrary to the concept of zero trust.
Embrace Your Zero Trust Journey with SANS
Learn more about SANS resources targeting zero trust architectures by visiting https://www.sans.org/ cyber-security-courses/defensible-security-architecture-and-engineering/
Ismael Valenzuela is a senior instructor at SANS; author of SANS’ Cyber Defense and Blue Team Operations course, SANS SEC530: Defensible Security Architecture and Engineering; and co-author of SEC568: Combating Supply Chain Attacks with Product Security Testing. Valenzuela is Vice President of Threat Research and Intelligence at BlackBerry Cylance, where he leads threat research, intelligence, and defensive innovation. Valenzuela is a top security professional who has contributed to numerous projects across the globe for over 20+ years, including being the founder of one of the first IT security consultancies in Spain.
12 Cybersecurity Quarterly
A Par tnership for State, Provincial, Local, Tribal, and Territorial Government
The SANS Institute and Center for Internet Security Partnership Program


•
Improving Your Security Posture
Cyberthreats appear as fast as a mouse click in today's environment. Your best defense is an educated workf orce. Eligible organizations use this Partnership Program to al locate technical cybersecurity and security awareness training to their employees, taking advantage of highly discounted rates on superior training to protect national security.
SECURITY AWARENESS
Special Offer:
For a limited time, save more than 50% when you purchase SANS technical and security awareness training through our partnership purchase windows. Special discounts are available:
Winter Program:
December 1 - January 31
Summer Program:
June 1 - July 31
Make a positive impact on your cybersecurity protection. Get the training you need at an affordable cost.
Technical training is a critical component for adoption of core security awareness concepts. Compliance and behavior change becomes difficult for non-technical individuals without the proper content. SANS Security Awareness offers a comprehensive solution for end users and individuals of all levels with expert-authored content. Created b y a trusted global network of cybersecurity professionals, this Partnership Program includes several key Security Awareness products:
• End User - Comprehensive security awareness training for all computer users based on the Critical Security Controls

• Healthcare - Computer-based security awareness training tailored to healthcare organizations
• Developer-Train your developers in secure coding techniques and how to recognize current threat vectors in web applications

• ICS Engineer- Rigorous computer-based training for those interacting or operating with Industrial Control Systems
• Phishing-Test your employees through phishing simulations consistent with real-world attacks
• CIP- Relevant training addresses NERC CIP reliability standards for the utility industry
�J S Centerfor � ® Internet Security®
CybersideChat
Be Proactive in Your Security Posture
By Stephanie Gass, Director of Governance, Risk & Compliance, CIS
When organizations and stakeholders envision the concept of cybersecurity, they often envision implementing measures that are more reactive than proactive. (For example, when ransomware hits an organization, it is often the response that is a “cybersecurity” issue rather than the protection of the systems to prevent such an event from occurring.) As we continue the path forward to maturity and redefine the vision of cybersecurity, organizations should begin to evaluate how to implement proactive security.
How Does an Organization Begin to Look at Security Proactively?

Risk Assessments
An organization should start with a risk assessment. To ensure that your risks are appropriately identified from both an internal and external perspective, including regulatory and contractual obligations, begin with an inventory of system assets, internal resources, and data. Using this inventory, perform an analysis aimed at understanding what the attack vectors for your organization are. Then, evaluate what levels of protection and investment are needed to defend against these threats. A great starting point to understand vectors and emerging threats is to utilize threat intelligence.
Incident Response Plan
Iteratively build and practice an incident response plan. By defining an incident response plan, you can address the ability to perform scenario analysis using the threat intelligence and risk-informed assessment. You can also provide a greater probability to enable the organization to minimize the downtime, damages, and costs that arise from security incidents. The plan should be designed in a manner that provides the organization a step-by-step process, which includes:
1. An identification of stakeholders
2. Critical processes
3. How to control the incident
(The Cyber Kill Chain may be an appropriate capability to apply at this stage.)
Disaster Recovery
Don’t be afraid to incorporate disaster recovery testing during this time. Make it a requirement, as it helps establish a baseline in the event there is an incident. It enables the organization to contextualize lessons identified and determine how to create plans of action. The goal of the organization is to be able to achieve a level of assurance that the incident response plans are functioning as intended and to
stress test disaster recovery plans so the organization can swiftly return to high-priority activities.
Security Awareness Training
People are an organization’s most valuable asset. Investment in those resources is a key proactive approach. Training and awareness should be built into the culture and should align with organizational priorities. Individuals need to be aware of the risks and threats that the organization faces as well as the threats confronting them as employees, contractors, etc. of that organization. With this approach, they’ll be more equipped to identify techniques in social engineering that are aimed at gaining access to sensitive data and systems.
A Focus on Proactive Security
Proactive security comes in many forms. These include security and privacy by design, baselining the technology stack, strong access controls, intrusion prevention systems, anti-virus, and patching and maintenance activities, to name a few. When we are looking at being proactive, the focus should be on what can we prevent or minimize now versus the “should have” plans and hindsight controls.
14 Cybersecurity Quarterly
Abusing Scheduled Tasks with Living off the Land Attacks
Cyber attacks taking advantage of existing tools and routine processes on your organization’s systems or networks can be difficult to detect and defend. Our new guidance based on the CIS Controls can help.
By Valecia Stocchetti
Living off the Land (LotL) attacks involve the use of existing tools and tactics on targeted systems or networks to carry out a cyber attack. Why do attackers use LotL techniques? It’s simple. These techniques are easily accessible, capable of evading detection, highly adaptive, and supportive of automation. According to CrowdStrike’s 2022 Global Threat Report, 62% of attackers are using LotL tools or techniques in their attacks.
We at the Center for Internet Security (CIS) have published several guides to provide you with specific guidance on defending against many of these LotL techniques. These include PowerShell, Remote Desktop Protocol (RDP), Windows Management Instrumentation (WMI), and Server Message Block (SMB). The next guide in the series – Living off the Land: Scheduled Tasks – provides you with an overview of how this tool is legitimately used, how it is abused, and how you can use the CIS Critical Security Controls (CIS Controls) to protect against an attack that abuses scheduled tasks.
Why do attackers use LotL techniques?
Attacks Abusing Scheduled Tasks
Part of defending against a LotL attack is knowing how the tool operates normally within your environment. This helps you understand what is normal and begins to establish a baseline in your systems for identifying when activity is abnormal.
Scheduled tasks are a common technique used by attackers to automate and perform malicious activities on target systems. In fact, Scheduled Task (T1053.005) was the seventh most prevalent LotL MITRE ATT&CK® sub-technique used in 2022, according to Red Canary. Attackers use scheduled tasks for a variety of reasons, including to initiate an infection, to recurrently establish persistence on a system, and to move laterally from system to system.
There are several ways an attacker can abuse scheduled tasks. Many of them are legitimate use cases, while others are more obvious in their malicious intent. Many threat actors abuse scheduled tasks and incorporate them into several malware variants. Some more well-known malware variants, past and current, that use scheduled tasks in their attacks include Tarrask (used by HAFNIUM), RedLine, Agent Tesla, Emotet , IcedID, Ryuk , TrickBot , and others.
Securing Scheduled Tasks
Unfortunately, a “block all scheduled tasks” approach to defense is not realistic. Your system administrators often use scheduled tasks to automate activities across the network so that tedious and time-consuming tasks are more manageable. Because of this, a defender’s approach involving LotL tools must be multi-faceted.
Summer 2023 15
It’s simple. These techniques are easily accessible, capable of evading detection, highly adaptive, and supportive of automation. According to CrowdStrike’s 2022 Global Threat Report, 62% of attackers are using LotL tools or techniques in their attacks.
Ultimately, defending against a LotL attack does not need to be a reactive process. The CIS Controls offer a set of best practice recommendations that work together to develop a defense-in-depth approach to cybersecurity. Additionally, our CIS Benchmarks offer secure configuration guidelines for 100+ technologies, including operating systems, applications, and network devices. Combined, they form a formidable defense against a scheduled task attack.
With any good cybersecurity program, the first step in implementing strong defenses against any attack is to know your environment. In order to defend a network, you must first know what is on the network. This includes enterprise assets (e.g., workstations, servers), software, and data. Without taking this first step in your cybersecurity program, it is difficult to implement additional Safeguards. This includes Implementation Group 1 (IG1) Safeguards that are a part of CIS Controls 1, 2, and 3.

Once you’ve implemented these foundational Controls, there are several different ways for you to proactively defend against an attack that abuses scheduled tasks. This new guide provides six simple actions to help strengthen your defenses against a scheduled task attack. Please note that one size does not fit all, and you may need to adjust some settings based on the environment.
Strengthen Your Defenses Against LotL Attacks
Our guide breaks down each mitigation, explains the importance of securing Scheduled Tasks (from an attack perspective), and introduces related CIS Controls, CIS Benchmarks, and MITRE ATT&CK (sub-)techniques. By implementing the recommendations introduced in Living off the Land: Scheduled Tasks, you can confidently strengthen your cybersecurity posture while protecting your assets. Download the guide at https:// www.cisecurity.org/insights/white-papers/living-off-theland-scheduled-tasks .
Valecia Stocchetti is a Senior Cybersecurity Engineer for the Center for Internet Security (CIS). As a member of the CIS Critical Security Controls team, she has led multiple projects, including the CIS Community Defense Model (CDM) v2.0, the CIS Risk Assessment Method (CIS RAM) v2.1, as well as multiple Living off the Land (LotL) guides. Most recently, Stocchetti was one of the principal authors of the Blueprint for Ransomware Defense. Prior to joining the CIS Controls team, she led the Computer Incident Response Team (CIRT) at the Multi-State and Elections Infrastructure Information Sharing and Analysis Centers (MS-ISAC® and EI-ISAC®). While managing CIRT, Stocchetti spearheaded multiple forensic investigations and incident response engagements for the MS- and EI-ISAC’s State, Local, Tribal, and Territorial (SLTT) community. Stocchetti came to CIS from the eCommerce field, where she worked complex financial fraud cases. She holds many certifications, including GIAC Certified Forensic Examiner (GCFE), GIAC Certified Forensic Analyst (GCFA), and GIAC Security Essentials Certification (GSEC). Stocchetti earned a Bachelor of Science degree in Digital Forensics at the University of Albany, State University of New York. She is currently pursuing a master’s degree in Information Security from Champlain College.
16 Cybersecurity Quarterly
Ultimately, defending against a LotL attack does not need to be a reactive process. The CIS Controls offer a set of best practice recommendations that work together to develop a defense-in-depth approach to cybersecurity. Additionally, our CIS Benchmarks offer secure configuration guidelines for 100+ technologies, including operating systems, applications, and network devices. Combined, they form a formidable defense against a scheduled task attack.
ISACUpdate
The 16th Annual ISAC Meeting and the Benefits of Conferences
By Karen Sorady, Vice President of Stakeholder Engagement, MS-ISAC
The MS-ISAC and EI-ISAC are busily preparing final details for the upcoming 16th Annual ISAC Meeting. Scheduled for August 6-9 in Salt Lake City, the premier ISAC in-person event of 2023 will be the 16th iteration of the annual event focusing on cybersecurity among U.S. State, Local, Tribal, and Territorial (SLTT) governments. The theme for this year’s Annual ISAC Meeting is “United and Protecting as One,” and the event will be host to 72 sessions across multiple tracks of relevance to cybersecurity professionals and government leaders, including topics like cybersecurity best practices, cyber threat and risk trends, and lessons learned from industry experts and peer organizations alike. The event provides an ideal environment of sharing and learning for executive decision-makers, including CISOs, CIOs, CTOs, and election officials, as well as IT managers, cybersecurity analysts, privacy officers, compliance managers, and many other professionals in the cyber and IT fields. The Annual ISAC Meeting is often touted by MS-ISAC organizations as one of the most impactful events they attend. As we look forward to
gathering in Salt Lake City, I’d like to highlight a few reasons why the ISAC Annual Meeting is a don’t-miss event for SLTTs.
Breaking the Curse of Knowledge
You may not realize it, but with every new thing you learn as an expert in your particular role, organization, and career field, something else is growing right alongside your professional acumen – the curse of knowledge. This is a cognitive bias where we erroneously assume that others know as much as we do on a particular topic. The more we know, the less we’re able to put ourselves in the position of those with less experience or expertise. In essence, our knowledge has “cursed” us, and we’re less able to effectively communicate with those with less technical professional knowledge. As a leader in IT, this poses a particular problem when you need to communicate security strategies or concepts to individuals who do not work in the cyber or IT space, such as executives, procurement offices, and budget offices. It can also be a particular challenge when explaining technical concepts
to constituents of your state, county, city, or town. Attending a conference like the Annual ISAC Meeting helps to break you out of your daily grind. You’ll encounter others with different levels of expertise and experience and be challenged to see things from different perspectives. In addition, you may be able to get just enough space from a challenge you’re facing to see it in a different way.
Building Your Cyber Intelligence
The MS-ISAC and EI-ISAC membership is full of incredibly hardworking cyber and IT professionals whose time is precious and whose professional demands are nearly stratospheric. That makes us very attuned to cyber risk – what are those things that could really give us and our organizations a bad day? Perhaps that is why we see the most engagement from member organizations when our webinars and content focus on cyber threats specific to SLTT organizations. Cyber threats are evolving every day, so your understanding of those threats should be growing daily, as well. With close to 16,000 organizations among our

Summer 2023 17
The Annual ISAC Meeting is often touted by MS-ISAC organizations as one of the most impactful events they attend. As we look forward to gathering in Salt Lake City, I’d like to highlight a few reasons why the Annual ISAC Meeting is a don’t-miss event for SLTTs.
membership and more than 200 threat intelligence sources feeding our collective cyber intelligence picture, the MS-ISAC and EI-ISAC command the most up-to-date, accurate picture of the threats facing organizations like yours. At the Annual ISAC Meeting, you’ll find that the cyber threat environment of SLTTs is woven throughout the presentations and discussions. You’re sure to walk away with a better understanding of what your organization is up against.
Staying Current on Industry Trends
It would be difficult to find an event more directly tailored to the challenges faced by cybersecurity and IT professionals in the SLTT community. A quick scan of the agenda for the 2023 Annual ISAC Meeting reveals a host of topics directly targeted to state and local governments, including workforce management, incident response, AI and machine learning, zero trust, identity and access management, phishing, and many more. You’ll find practical takeaways in each session. As an added feature this year, the 2023 Annual ISAC Meeting has numerous tabletop exercises to help attendees walk through scenarios simulating

real-world events that could help inform their cybersecurity best practices and programs.
Networking
Collaboration is at the heart of everything we do at the ISACs. In a way, the Annual ISAC Meeting is the networking Super Bowl for our member organizations. Attendees will have the opportunity to selectively connect with SLTT peers, EI-ISAC, MS-ISAC, and CISA staff members, and even vendor companies in the cybersecurity and technology space. According to LinkedIn, 80% of professionals in 2017 considered networking vital to success in their careers. Harvard Business Review found that nearly 100% of professionals believe that in-person meetings are vital to building strong long-term relationships, and our members agree! Annual ISAC Meeting attendees have an open door to greater success and stronger relationships through the networking opportunities this important event provides.
On to the Great Salt Lake
If you are planning to join us in Salt Lake City, I’m excited for you. You’ll
not find another event where the content and experiences are more painstakingly tailored to your needs and interests. If you’re not scheduled to make it for this year’s event, I hope you will consider joining us in June 2024. In the MS-ISAC and the EI-ISAC, we truly believe that we’re better together, and our annual event becomes a richer, more impactful experience with every leader and professional who attends.
18 Cybersecurity Quarterly
Harvard Business Review found that nearly 100% of professionals believe that in-person meetings are vital to building strong longterm relationships, and our members agree!
UpcomingEvents
July
July 9 - 12
The National Association of Secretaries of State (NASS) will host the NASS 2023 Summer Conference at the Grand Hyatt in Washington, D.C. The event will bring together secretaries of state and their staff from across the country to network with peers, learn about the latest topics of interest from industry experts, and collaborate with partners. Learn more at https:// www.nass.org/events/nass-2023summer-conference.
July 13
Cyber Security Summit: RaleighDurham will take place at The Westin Raleigh-Durham Airport in Raleigh, North Carolina. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/raleigh23/.
July 17 - 18
Midwest Tech Talk 2023 will take place at Osage High School in Osage Beach, Missouri. This two-day technical conference will bring together K-12 school technology and IT leaders and professionals from across the Midwest to improve their skills and take knowledge back to their school districts that will improve their overall technology program. MS-ISAC Regional Engagement Manager Megan Incerto will lead a session at the event on strengthening the cybersecurity posture and resilience of K-12 schools. Learn more at https://www. midwesttechtalk.com/.
July 20
Cyber Security Summit: DC Metro will take place at the Ritz-Carlton, Tysons Corner, in McLean, Virginia. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/dcmetro23/.

July 21 - 24
The National Association of Counties (NACo) will host the 2023 NACo Annual Conference and Expo at the Austin Convention Center in Austin, Texas. The event is the largest meeting of county officials from across the country. Participants from counties of all sizes will come together to shape NACo’s federal policy agenda, share proven practices, and strengthen their knowledge to help improve residents’ lives and the efficiency of county government. The MS-ISAC team will be on the show floor sharing our cybersecurity resources for county governments. Learn more at https:// www.naco.org/events/2023-nacoannual-conference -exposition.
July
25 - 27
The National Association of State Election Directors (NASED) will host the 2023 NASED Summer Conference in Charleston, South Carolina. The event will bring together election leaders and their staff from across the country to network with peers and learn the latest updates in preparation for the upcoming election season. The EI-ISAC team will be on the show floor sharing our cybersecurity resources for elections offices. Learn more at https://www. nased.org/2023conf.
July 27
Cyber Security Summit: Pittsburgh will take place at the Wyndham Grand Pittsburgh Downtown in Pittsburgh, Pennsylvania. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ pittsburgh23/.
August
August 7 - 8
The West Virginia County Clerks Association will host its 2023 Elections Conference in Davis, West Virginia. The event will bring together county clerks and their staff from across the state to network with peers and learn the latest updates in preparation for the upcoming election season. EI-ISAC Regional Engagement Manager Sarah Kuzniewski will lead a session on the threat landscape and resources available from the EI-ISAC.
August 17
Cyber Security Summit: Detroit will take place at the Marriott Detroit Renaissance Center in Detroit, Michigan. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ detroit23/
Summer 2023 19
August 20–23
GMIS International will host its 2023 GMIS MEETS (Meeting Education and Expo for the Public Technology Sector) at the Sheraton Kansas City Hotel at Crown Center in Kansas City, Missouri. Created by and for leaders in the public sector IT industry, GMIS MEETS offers informative educational sessions on topics important in today’s environment, interaction with industry-leading providers, networking opportunities, and much more. MS-ISAC Regional Engagement Manager Michelle Nolan and Maturity Services Manager Emily Sochia will co-lead a session on incident response and combatting ransomware with resources from the MS-ISAC. Learn more at https://www.gmis.org/ page/2023homepage.
August 21 – 24
VMware Explore will take place at the Venetian Convention and Expo Center in Las Vegas. The conference is VMware’s flagship event for all things multi-cloud. VMware Explore aims to facilitate new relationships, inspire learning, and provide hands-on training and access to thought leadership in the multi-cloud space. Those engaged in enterprise applications, cloud architecture, infrastructure, end users, networking, and security will be among their peers at VMware Explore. The CIS team will be on the show floor sharing our cybersecurity resources with attendees at Booth 317. Learn more at https://www. vmware.com/explore/us.html.
August 26 – 30

The National Association of Election Officials will host its 38th Annual Election Center National Conference at the Grand Cypress Hotel in Orlando, Florida. The conference will bring together election officials representing all levels of government from across the country to work together to improve democracy for voters at the local, state, and national level . Attendees will have the chance to network with peers, attend thought-provoking sessions and professional education courses, and explore the latest resources and technologies. Senior Director for the EI-ISAC Marci Andino will lead a session on new updates and resources available from the organization in preparation for the upcoming election season. Learn more at https://www.electioncenter.org/.
August 29 - 31
Google Cloud Next 2023 will take place at the Moscone Center in San Francisco. The conference is Google’s global exhibition of inspiration, innovation, and education. It’s where decision-makers, developers, and anyone passionate about an accessible, scalable, socially responsible cloud come together to share challenges, solutions, 10x ideas, and game-changing technologies. The CIS team will be on the show floor at Booth 1730 sharing our cloud security resources for Google Cloud with attendees. Learn more at https://cloud.withgoogle.com/next .
August
29 - 31
The State of Oregon will hold the 2023 Oregon State Police Criminal Justice Information Services (CJIS) Statewide Conference at the Seaside Civic and Convention Center in Seaside, Oregon. The event will cover topics relevant to criminal justice and regulatory agencies throughout the State of Oregon. MS-ISAC Regional Engagement Manager Michelle Nolan will lead a breakout session on cybersecurity resources for law enforcement agencies. Learn more at https://www.eventbrite.com/e/2023oregon-state-police-cjis-statewideconference-tickets-600885904917.
September
September 6
Cyber Security Summit: Chicago will take place at the Marriott Marquis Chicago. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ chicago23/.
September 13
Cyber Security Summit: Philadelphia will take place at the Sheraton Philadelphia Downtown. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ philadelphia23/.
20 Cybersecurity Quarterly
September 18 - 21
TribalHub will hold the 24th Annual TribalNet Conference and Tradeshow at the Town and Country Resort in San Diego, California. TribalNet has grown to become the platform to connect and seek opportunities in solutions, best practices, and technology among tribal government, gaming, and healthcare industries. For nearly 25 years, TribalNet has fostered many long-lasting peer-topeer relationships as well as profitable connections. The MS-ISAC team will be on the expo floor sharing our no-cost and low-cost cybersecurity resources for tribal governments. Learn more at https://www.tribalnetconference.com/
September 19
Cyber Security Summit: Atlanta will take place at the Hyatt Regency Atlanta. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ atlanta23-sep/.
September 25 - 27
CyberRisk Alliance will hold InfoSec World 2023 at Disney’s Coronado Springs Resort in Lake Buena Vista, Florida. Now in its 28th year, InfoSec World is known as the “Business of Security” conference, bringing together practitioners and executives for multiple days of top-notch education, networking, and more. The CIS team will be on the show floor sharing our cybersecurity resources with attendees at Booth 322. Learn more at https:// www.infosecworldusa.com/.
September 28
Cyber Security Summit: Kansas City will take place at the Westin Kansas City at Crown Center in Kansas City, Missouri. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ kansascity23/.
September 29
The Virtual Cyber Security Healthcare and Pharma Summit will take place online. It will bring together business leaders and cybersecurity professionals in the healthcare sector to learn about the latest cyber threats facing the industry. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ healthcare23/
October
October 4
Cyber Security Summit: Charlotte will take place at the Westin Charlotte in Charlotte, North Carolina. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ charlotte23/.
October 8 – 11

The National Association of State Chief Information Security Officers (NASCIO) will host the 2023 NASCIO Annual Conference at the Hyatt Regency Minneapolis in Minneapolis, Minnesota. The event will bring together state CIOs and other state leaders as well as senior staff and professionals from across the country to network with peers, learn about the latest topics of interest from industry experts, and collaborate with technology partners. Learn more at https://www.nascio.org/ conferences-events/.
October 9 – 13
The Association of County and City Information Systems (ACCIS) will host the 2023 ACCIS Fall Conference at the Kitsap Conference Center in Bremerton, Washington. The event will bring together local government information system leaders from across the state to network with peers, learn about the latest topics of interest from industry experts, and discuss state and federal legislation and programs affecting county and city information systems’ interests. MS-ISAC Regional Engagement Manager Michelle Nolan will be leading a session at the event on no- and low-cost cybersecurity resources for local governments. Learn more at https://www.accis-wa.org/
Summer 2023 21

Interested in being a contributor? Please contact us: cybermarket@cisecurity.org www.cisecurity.org 518.266.3460 CIS CyberMarket cisecurity.org info@cisecurity.org 518-266-3460 Center for Internet Security @CISecurity TheCISecurity cisecurity




 John M. Gilligan President & Chief Executive Officer Center for Internet Security
John M. Gilligan President & Chief Executive Officer Center for Internet Security


























