

Stronger Together

Community and collaboration have been the drivers of CIS's mission since its inception. From our community-developed security best practices contained in the CIS Critical Security Controls® and CIS Benchmarks® to the collective shared defense model of the Multi-State Information Sharing and Analysis Center® (MS-ISAC®), we've worked together with our global community to make our connected world a safer place
The Evolution of Our Consensus-Based Best Practices to Meet the Changing Threat Landscape
Improving Cyber Resilience and Addressing Future Challenges in the U.S. SLTT Community
Harnessing the Power of AI to Improve
Security Operations
Strategies to Defend Against the Biggest Anticipated Cyber Threats of 2025
CIS CyberMarket
Rigorously vetted cybersecurity solutions with negotiated pricing just for SLTTs.
Optimize your use of industry-leading security best practices with benefits, tools, and resources available to SLTTs at no cost.
Albert
Powerful, cost-e ective IDS solution that identifies SLTT-specific malicious network activity.
CIS Endpoint Security Services
Ad Placement
CIS Hardened Images
Securely pre-configured virtual machine images available to deploy from major cloud service provider marketplaces.
Cost-e ective endpoint protection and response solution with additional capabilities o ering real-time vulnerability data, mobile device visibility at your fingertips, and multi-tenancy for larger organizations that oversee numerous organizations.
Malicious Domain Blocking and Reporting Plus
Customizable secure PDNS service that blocks access to harmful web domains and o ers real-time reports.
The Role of Retrieval
The Biggest Cybersecurity Threats of 2025 and How to Prepare for Them
Cybersecurity Quarterly is published and distributed in March, June, September, and December. Founded MMXVII. Published by Center for Internet Security, 31 Tech Valley Drive, East Greenbush, New York 12061
For questions or information concerning this publication, contact CIS at learn@cisecurity. org or call 518.266.3460
© 2025 Center for Internet Security. All rights reserved.
Editor-in-Chief
Michael Mineconzo
Supervising Editor
Laura MacGregor
Copy Editors
Jay Billington
David Bisson
Staff Contributors
Anthony Essmaker
James Globe
Patrick Johnston
Carlos Kizzee
Natalie Schlabig
Charity Otwell

CIS Implementation Group 1
Develop Cybersecurity Capacity
Small and medium-sized organizations face the same modern cybersecurity threats as larger enterprises, but often lack the resources and expertise to defend against them effectively. SEC366 bridges that gap by equipping non-security professionals with the foundational skills needed to implement essential security controls, empowering organizations to safeguard their critical assets and stay resilient in the face of evolving cyber risks.
Why CIS IG1 is Essential
CIS Implementation Group 1 (IG1) provides a foundational set of 56 cyber defense safeguards—a baseline standard of security for organizations of all sizes. These safeguards are particularly valuable for smaller organizations and can be implemented by nonsecurity personnel using readily available commercial off-theshelf hardware and software. IG1 focuses on establishing essential protections to defend against the most common cyber threats, ensuring a strong foundation for any organization’s cybersecurity efforts.
Hands-On CIS IG1 Training
Deliver Immediate Impact
Ad Placement
Hands-on labs engage participants with simulated real-world scenarios that enhance one’s understanding of how to apply CIS IG1 safeguards in a practical, cost-effective way.
These labs cover:
• CIS Navigator and policy library review
• CIS Self-Assessment Tool (CSAT)
• Device and software inventory with PowerShell
• Secure configuration with CIS-CAT
• Scanning for sensitive data
• Building tabletop exercises
• CIS Risk Assessment Method (CIS-RAM)
Upon completion, participants will be able to:
• Efficiently reduce cyber risks with actionable safeguards
• Align cybersecurity measures with business and compliance requirements
• Report cybersecurity efforts to leadership in clear, business-focused terms

Register

QuarterlyUpdate with John Gilligan
“The MS-ISAC and EI-ISAC have operated on the fundamental principal of community and they've facilitated many community-based efforts"
The world continues to see ever-increasing cyber attacks, including those launched by nation states such as Russia, China, Iran, and North Korea. Many of these attacks target key elements of the U.S. critical infrastructure including water treatment facilities, K-12 schools, local governments, and law enforcement organizations.
The actions taken by the new U.S. Presidential Administration over its first two months in office have raised questions about the commitment of the U.S. Executive Branch to strengthening our nation’s resilience against these attacks. The Administration's decision to terminate federal funding for the Multi-State Information Sharing and Analysis Center® (MS-ISAC®), which works to help the “cyber-underserved” (smaller organizations who have very limited resources and are not well served by traditional cybersecurity organizations) to improve their security resilience, is but one confusing signal.
Its decision to terminate federal funding for the Elections Infrastructure Information Sharing and Analysis Center® (EI-ISAC®) governance structure is another. As noted in our last issue of Cybersecurity Quarterly, the efforts of the EI-ISAC over the past seven years have resulted in rapid improvements in the ability of U.S. election offices to defend against cyber, physical, and information operations. The enormous success of the 2024 General Election was the result of years of preparation and coordination despite significant increases in actual threats to disrupt the election process.
The theme of this issue is cybersecurity through community. The MS-ISAC and EI-ISAC have operated on the fundamental principal of community. They've facilitated many community-based efforts, including sharing best practices, collaboration among organizations to improve resilience, mentorships for less-experienced security professionals, collective buying power to reduce security monitoring costs, tailored threat signatures, and focused training and education.
A featured article in this issue highlights several recent reports, including the 2025 CIS MS-ISAC
K-12 Cybersecurity Report and Strengthening Critical Infrastructure: SLTT Progress and Priorities. Together, these reports provide a detailed assessment of the growing threats to U.S. State, Local, Tribal, and Territorial (SLTT) government organizations, including the fact that 84% of K-12 organizations have experienced cyber threat impacts in the past 18 months. The reports also highlight progress that has been made in improving cyber resilience as well as future challenges.
In another article, Charity Otwell, CIS’s Director of the Critical Security Controls, traces the evolution of the CIS Controls, our consensus-based and community-developed security best practices, over the past 10 years.
In a separate article, Brian Calkin, in his role as CTO with our partner CyberWA, examines the most significant cyber threats for 2025. Then, James Globe, VP of Strategic Cybersecurity Capabilities at the Center for Internet Security® (CIS®), discusses how to enhance security operations with retrieval augmented generation (RAG) and chatbots.
Finally, Brian Hajost, COO at our partner organization SteelCloud, explores how implementing the CIS Benchmarks®, our secure configuration guidelines developed in conjunction with a global community of cybersecurity experts, can result in improved cyber defenses for an organization in 100 days or less.
I hope you enjoy this quarter’s issue. Have a great quarter!
Best Regards,

John M. Gilligan President & Chief Executive Officer Center for Internet Security

NewsBits&Bytes

CIS Year in Review 2024
The Center for Internet Security® (CIS®) has released its comprehensive 2024 Year in Review. CIS continued its important role as a global thought leader in security; continued to play a pivotal role in supporting the cybersecurity posture of the U.S. State, Local, Tribal, and Territorial (SLTT) community; built an effective intelligence clearinghouse with law enforcement agencies across the country; supported CIS employees to continue the winning culture we have built; and much more. Read the full report here.

CIS Launches CIS Controls v8.1 Cloud Companion Guide
CIS Critical Security Controls (CIS Controls) version 8.1 (v8.1) is an iterative update to version 8.0. As part of our process to evolve the CIS Controls, we establish "design principles" that guide us through any minor or major updates to the document.
In this document, we provide guidance on how to apply the security best practices found in CIS Controls v8.1 to any cloud environment from the consumer/customer perspective. For each top-level CIS Control, there is a brief discussion on how to interpret and apply the CIS Control in such environments along with any unique considerations or differences from common IT environments. Learn more and download a copy here.

CIS CyberMarket® Announces New Vendor
CIS CyberMarket has added CyberWA as a new vendor to its list of valued partners. CyberWA's Cyber Audit Platform provides users with an interactive dashboard that visualizes their security posture across several key domains.
CIS CyberMarket is a cybersecurity marketplace specifically designed to help connect U.S. State, Local, Tribal, and Territorial (SLTT) government organizations with rigorously-vetted, cost-effective cybersecurity solutions from industry-leading vendors. To view all of our current offerings from eleven unique vendors, please visit our official CIS CyberMarket webpage

CIS Joins Take9 Initiative to Remind Users to Pause to Protect Against Cyber Threats
CIS has joined the Take9 public awareness campaign, reminding internet users to take nine seconds to stop and think before clicking, opening, or sharing something that could be malicious.
Cyber threats come in varying forms. An email from the boss, a text from the bank, or a Facebook message from a friend are often not what they appear. The evolution of artificial intelligence is making it more difficult to detect the subtle clues that give bad actors away. They convey a sense of urgency to prevent victims from having time to think until it’s too late. A simple, nine-second pause may be all it takes to prevent someone from becoming a victim and stop the ripple effect through an organization or friends list.
"Whether you are a senior government official, a corporate executive, a student, or a retiree, simply taking a moment before clicking a link can protect your personal security, your employer, and your friends and family,” said John Cohen, Executive Director of Program for Countering Hybrid Threats at CIS. Learn more about the Take9 awareness campaign and other online safety tips at www. pausetake9.org
The Ongoing Evolution of the CIS Critical Security Controls®
In an ever-changing threat landscape, it's imperative that the security best practices contained in the CIS Controls change and adapt to the times. Learn how our team and the global community has continuously updated their guidance over their decades of existence to meet evolving cyber threats
By Charity Otwell
For decades, the CIS Critical Security Controls® (CIS Controls®) have simplified enterprises' efforts to strengthen their cybersecurity posture by prescribing prioritized security measures for defending against common cyber threats.
In this article, we'll review the story of the CIS Controls before taking a closer look at the current version.
A Brief History of the CIS Controls
The Early Days
They were once introduced as the SANS Critical Security Controls (SANS Top 20) in 2008 by an international, grassroots consortium bringing together companies, government agencies, institutions, and individuals from

every part of the ecosystem who banded together to create, adopt, and support the Controls. In 2015, the Center for Internet Security® (CIS®) officially took ownership of the CIS Controls with Version 6. The idea behind the CIS Controls was to provide enterprises with actionable guidance to enhance their cyber defense capabilities meaningfully.
Over time, several updates have been introduced to keep pace with evolving cyber threat and organizational needs. The CIS Controls are updated and reviewed through a consensus-based process. Practitioners from government, industry, and academia each bring deep technical understanding from across multiple viewpoints (e.g., vulnerability, threat, defensive technology, tool vendors, enterprise management) and pool their knowledge to identify the most effective technical security controls needed to stop the attacks they are observing.
Version 7.1: A Focus on Prioritization
One of the biggest shifts in the CIS Controls took place in Version 7.1 when CIS introduced the concept of Implementation Groups (IGs) — IG1, IG2, and IG3 — as a new way to prioritize the CIS Controls. These IGs provide a simple and accessible way for enterprises of different sizes to focus their scarce security resources while still leveraging the value of the CIS Controls program, community, and complementary tools and working aids.
Version 8: 18 Is the New 20
In May 2021, CIS introduced Version 8 of the Controls, offering a simplified and more focused approach toward cybersecurity than its predecessor. Version 8 combined and consolidated the CIS Controls by activities rather
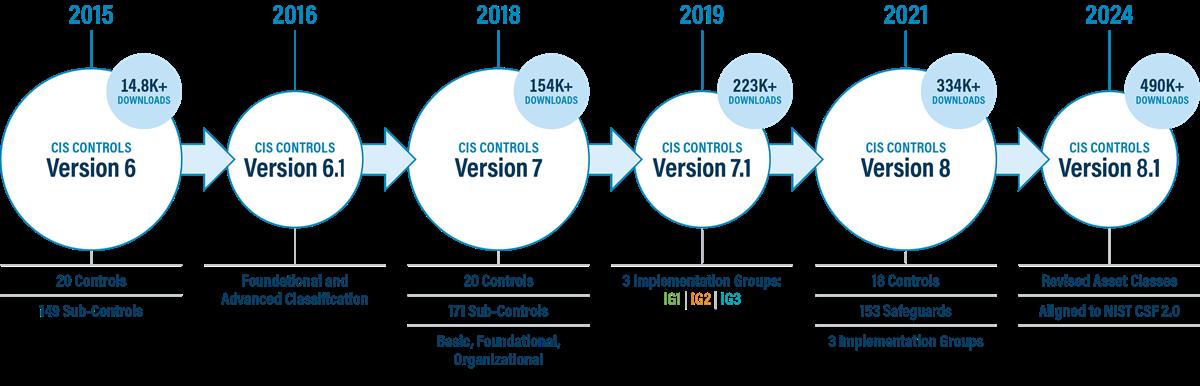
than by who managed the devices, dropping the number of Controls from 20 to 18 and introducing CIS Safeguards (rather than Sub-Controls). This significant change made it easier for enterprises to strategize and implement security measures effectively. Version 8 also shifted its approach from device-centric defensive strategies to data-centric strategies aimed at protecting data regardless of its location, including public and private clouds along with on-premises systems. This version also officially defined IG1 as essential cyber hygiene, the starting point and minimum standard of information security for all enterprises.
Version 8.1: Governance and Compliance
Fast forward three years to the release of Controls v8.1 in June 2024. This new iterative update seeks to streamline operations further and enhance context, coexistence, and consistency.
The Current Version of the CIS Critical Security Controls
CIS Controls v8.1 is an iterative update to Version 8. As part of our process to evolve the CIS Controls, we establish "design principles" that guide us through any minor or major updates to the document. Our design principles for this revision are context, clarity, and consistency. Context enhances the scope and practical applicability of CIS Safeguards by incorporating specific examples and additional explanations. Clarity aligns with other major security frameworks to the extent practical while preserving the unique features of the CIS Controls. Consistency maintains continuity for existing CIS Controls users, ensuring little to no change due to this update.
Here are the broad changes we’ve made for each design principle:
The CIS Controls aim to streamline the process of designing, implementing, measuring, and managing enterprise security. This involves simplifying language to reduce duplication, focusing on measurable actions with defined metrics, and ensuring each CIS Safeguard is clear and concise. CIS continues to balance the need to address current cybersecurity challenges and maintain a stable, foundational cyber defense strategy.
Context
We've updated the CIS Controls with new asset classes to better match the specific parts of an enterprise's infrastructure to which each CIS Safeguard applies. New classes require new definitions, so we've also enhanced the descriptions of several CIS Safeguards for greater detail, practicality, and clarity.
Coexistence
The CIS Controls have always aligned to evolving industry standards and frameworks, and they will continue to do so. This is a core principle of how the Controls operate; it assists all users of the Controls. The release of National Institute of Standards and Technology
(NIST) Cybersecurity Framework (CSF) 2.0 necessitated updated mappings and updated security functions.
Consistency
Traditionally, any iterative update to the CIS Controls should minimize disruption to Controls users. This means that no IGs were modified in this update, and the spirit of any given CIS Safeguard remains the same. Additionally, the new asset classes and definitions needed to be consistently applied throughout the Controls, and in doing so, some minor updates were added.
With these principles in mind, we’ve scoped the CIS Controls v8.1 to the following updates:
• Realigned NIST CSF security function mappings to match NIST CSF 2.0
• Included new and expanded glossary definitions for reserved words used throughout the Controls (e.g., plan, process, sensitive data)
• Revised asset classes alongside new mappings to CIS Safeguards
• Fixed minor typos in CIS Safeguard descriptions
• Added clarification to a few anemic CIS Safeguard descriptions
We've also added the “Governance” security function. Enterprises can't steer their cybersecurity program toward achieving their goals without the structure provided by effective governance. CIS Controls v8.1 specifically identifies governance topics as recommendations that enterprises can implement to enhance their governance of their cybersecurity program.
The CIS Controls aim to streamline the process of designing, implementing, measuring, and managing enterprise security. This involves simplifying language to reduce duplication, focusing on measurable actions with defined metrics, and ensuring each CIS Safeguard is clear and concise. CIS continues to balance the need to address current cybersecurity challenges and maintain a stable, foundational cyber defense strategy, all the while steering clear of overly complex or inaccessible technologies. Technology is constantly shifting, and the CIS Controls team is aware of the developments in artificial intelligence , augmented reality, and ambient computing working to reshape our enterprise infrastructure in subtle and radical ways. We’re keeping both eyes open and already working on ideas for Version 9 of the CIS Controls.

The CIS Controls Ecosystem
As the CIS Controls updates to future versions, we are always keeping our resources and tools updated in parallel. We are excited to share that we have a new webpage for CIS Controls Resources . Not only can you find our resources by version, but you can also find them by category, making it even easier to follow our prioritized set of actions to protect your organization and data from cyber attack vectors.
Cybersecurity isn't a one-time endeavor — it's an ongoing process of adaptation and improvement. Updating your organization to CIS Controls v8.1 will not only help meet the current challenges but also lay a robust foundation for future upgrades to your cybersecurity strategies
Charity Otwell is the Director of the CIS Critical Security Controls for CIS. She has nearly 20 years of experience in the financial services industry and has built and led various programs such as Business Continuity, Disaster Recovery, Technology Governance, and Enterprise Architecture in a highly regulated environment. Before coming to CIS, Otwell was a GRC champion and practitioner with a focus on risk assessment, process optimization, process engineering, and best practice adoption for a top-50 bank within the United States. She also helped manage the relationship with federal regulators and the management of federal regulatory exams. She completed undergraduate and graduate studies in Birmingham, Alabama, and holds multiple industry certifications.
Enhancing Security Operations: The Role of Retrieval Augmented Generation (RAG) and Chatbots
When utilized and trained effectively, generative Artificial Intelligence (AI) is poised to radically transform how security operations centers analyze, detect, respond to, and mitigate cyber threats to defend the systems and data they protect
By James Globe
The integration of Retrieval-Augmented Generation (RAG) and chatbot technologies is set to revolutionize Security Operations (SecOps) by enabling highly specialized, AI-driven threat detection, analysis, and prevention. These advanced models, trained on sector-specific and organization-specific threat intelligence, will enhance security teams' ability to detect, respond to, and mitigate cyber threats with unprecedented speed and accuracy. By seamlessly integrating with chatbots, RAG-powered systems will not only generate real-time security alerts but also analyze evolving threat patterns to inform dynamic security posture adjustments. These insights will be distributed across Endpoint Detection and Response (EDR) platforms, Network Defense and Response (NDR) technologies, firewalls, and Cloud Access Security Brokers (CASB), ensuring that defensive measures remain proactive and adaptive.
This automation is driven by generative AI models that assess vulnerability scans, threat intelligence feeds, and cybersecurity priorities to make real-time policy adjustments. By continuously learning from new attack vectors and countermeasures, RAG and chatbot technologies will transform static cybersecurity protocols into dynamic, AI-orchestrated defenses. As cyber threats grow more sophisticated and unpredictable, organizations must embrace AI-driven SecOps to safeguard critical infrastructure and sensitive information. This article explores how security operation centers (SOCs) are leveraging RAG and chatbot technologies to enhance threat event analysis, incident determination, automated reporting, and advisory generation — ushering in a new era of intelligent, automated cybersecurity.
By
continuously learning from new attack vectors and countermeasures, RAG and chatbot technologies
will transform static
cybersecurity protocols
into
dynamic,
AIorchestrated defenses. As cyber threats grow more sophisticated and unpredictable, organizations must embrace AI-driven SecOps to safeguard critical infrastructure and sensitive information.
RAG Technology and AI-Driven Threat Intelligence in Security Operations
Retrieval-Augmented Generation (RAG) technology, when trained on industry-specific and organization-specific threat intelligence, transforms static cybersecurity processes into adaptive, intelligence-driven defense mechanisms. Unlike traditional machine learning models that rely solely on pretrained datasets, RAG dynamically retrieves and synthesizes relevant security intelligence from curated threat feeds, previous attack analyses, and
RAG and Chatbots Roles in Security Operations
real-time security alerts to generate context-aware security responses.
For IT professionals and cybersecurity analysts, this means AI-powered models can continuously refine their threat detection capabilities by integrating historical attack data, incident response logs, and sector-specific threat indicators into their analytical workflows. A RAG-enhanced SOC can automatically correlate threat data from diverse sources — such as MITRE ATT&CK frameworks, industry threat intelligence platforms (TIPs), and internal incident response reports — to generate high-fidelity alerts with actionable intelligence. This drastically reduces false positives while ensuring that emerging attack vectors are rapidly identified and countered. For organizations lacking in-house IT and cybersecurity talent, RAG technology and AI-orchestrated automations can be game changers, especially for medium and small organizations with limited resources.

The diagram above illustrates the flow of security operations, starting with inputs from monitoring devices, threat intelligence feeds, and system logs. These inputs are collected and aggregated by Security Information and Event Management (SIEM) and Threat Intelligence Platform (TIP). The data is then analyzed and correlated to produce outputs such as alerts, escalation notifications, advisories, and reports, which are delivered to customers, members, and other stakeholders using chatbots, dashboards, and other communication mechanisms. Additionally, organization-specific RAG implementations can be trained on proprietary security datasets, allowing AI models to map threat behaviors unique to a company’s infrastructure, supply chain, and operational technology (OT) environment. By leveraging curated threat feeds, the AI dynamically updates its threat landscape model, learning from active exploit campaigns, known adversary tactics, and geopolitical cyber threats that are particularly relevant to the industry in which the organization operates.
This continuous learning and adaptation cycle enables SecOps teams to preemptively adjust security policies; automatically deploy updated defense mechanisms across firewalls, EDRs, and cloud security tools; and enhance SOC efficiency by eliminating the manual correlation of threat intelligence sources. By integrating RAG-powered AI models, cybersecurity teams can shift from reactive security postures to proactive and predictive cybersecurity operations, effectively mitigating risks before they escalate into breaches.
Enhancing SecOps with AI-Driven Chatbots and Contextualized Alerts
In the rapidly evolving landscape of cybersecurity, the role of chatbots and Generative AI (GenAI) technologies in SecOps is becoming increasingly crucial. These
AI-driven tools enhance the responsiveness of security operations and provide a sophisticated layer of intelligence that supports policy adjustments and prioritizes vulnerabilities. Chatbots with GenAI capabilities serve as advanced interfaces for SIEM and threat intelligence platforms. They effectively translate complex security data into actionable intelligence. By processing inputs from various sources like system logs, monitoring devices, and threat intelligence feeds, these AI-enhanced chatbots generate contextualized alerts. This streamlines the detection process and ensures that security analysts can swiftly grasp the nuances of each threat to decide whether to escalate it or determine its non-malicious nature. The alerts provided are enriched with metadata that includes detailed information about the threat's nature, origin, and potential impact. This metadata is crucial for SIEM and TIP systems, enabling them to perform deeper analysis and correlation, which in turn helps in generating precise security advisories. Furthermore, this contextualization helps in reducing the noise of false positives, which are often a significant drain on SecOps resources.
In environments where skilled staff are limited, the ability of GenAI to provide input for policy adjustments and threat intelligence is invaluable. AI-Driven systems assess vulnerability scans and real-time threat intelligence to recommend policy updates dynamically. This automation extends to configuring and updating EDR, NDR, and CASB as well as Secure Access Service Edge (SASE) technologies. One of the critical decision points for organizations, especially those with insufficient cybersecurity personnel, is the prioritization of vulnerabilities and countermeasures. GenAI aids in this aspect by analyzing potential threats against the backdrop of existing security postures and suggesting prioritizations that align with the organization’s risk management strategies. This not only optimizes the response times but also ensures that the most critical assets are protected with appropriate urgency.
Conclusion
In conclusion, the integration of chatbots, RAG, and GenAI capabilities into security operations transforms traditional SecOps into dynamic, intelligent defense systems. These technologies augment existing capabilities, ensure robust security postures even with limited staffing, and preemptively detect and respond to sophisticated cyber threats. As cyber threats grow more sophisticated, the role of AI in preemptive threat detection and strategic response continues to be a game-changer.
In the rapidly evolving landscape of cybersecurity, the role of chatbots and Generative AI (GenAI) technologies in SecOps is becoming increasingly crucial. These AIdriven tools enhance the responsiveness of security operations and provide a sophisticated layer of intelligence that supports policy adjustments and prioritizes vulnerabilities.
James Globe, CISSP, is the Vice President, Strategic Advisor Cybersecurity Capabilities at the Center for Internet Security® (CIS®). Globe serves as the senior leader within Operations and Security Services (OSS) responsible for advising on strategic cybersecurity capabilities, cybersecurity workforce, data analytic analysis, frameworks, and emerging and enabling technologies for use by U.S. SLTT members.
He has more than 20 years in technology leadership, including extensive experience engineering signal intelligence mission systems, workflow management systems, financial and banking systems, modeling and simulation systems, and web-based information portals for top-tier banking and defense contracting organizations, including Bank of America, SAIC, BAE Systems, and L3 Harris Technologies.
Globe earned a Bachelor of Science in computer science and mathematics from Georgia State University. He also holds a Master of Science from John Hopkins University in telecommunications and security engineering.
The Biggest Cybersecurity Threats of 2025 and How to Prepare for Them
As we proceed through 2025, cyber threat actors will continue to evolve and adapt to take advantage of new technologies and attack vectors. Here are some of the largest security threats anticipated to dominate 2025 and strategies for how your organization can defend against them
By Brian Calkin
As technology continues to evolve, so do the threats in cyberspace. Cybercriminals are becoming more sophisticated, leveraging emerging technologies like artificial intelligence (AI) and exploiting vulnerabilities in supply chains and remote work environments. As we move into 2025, businesses and individuals alike must stay vigilant. In this post, we will explore the biggest cybersecurity threats of 2025 and provide actionable steps to mitigate them.
1. AI-Powered Cybercrime
AI is revolutionizing many industries, including cybersecurity. However, it is also being weaponized by cybercriminals to conduct highly advanced phishing attacks, deepfake scams, and automated hacking attempts. AI-Driven attacks can mimic human behavior, making them harder to detect for cyber defenders.
How to Prepare:
• Implement AI-driven security solutions to detect and respond to threats in near real-time.
• Educate employees on identifying AI-generated phishing attempts and deepfake scams.
• Implement cyber best practices such as the use of strong passwords, multi-factor authentication (MFA), as well as ensuring systems and software are fully up to date.
2. Ransomware and Cybercrime-as-a-Service
Ransomware attacks continue to evolve, with cybercriminals now offering "Cybercrime-as-a-Service" to
less-skilled hackers. This has led to an increase in attacks targeting businesses of all sizes, often causing operational disruptions and financial losses.
How to Prepare:
• Regularly back up critical data and store it in secure, offline locations.
• Invest in endpoint detection and response (EDR) solutions.
• Train employees on cybersecurity best practices, especially on how to avoid downloading and opening files from suspicious emails and websites.
3. Supply Chain Vulnerabilities
With businesses increasingly reliant on third-party vendors, cybercriminals are targeting supply chains as a weak link. A compromised supplier can give malicious hackers access to multiple organizations, leading to widespread damage.
How to Prepare:
• Conduct regular security assessments of thirdparty vendors.
• Require suppliers to follow cybersecurity best practices and compliance regulations.
• Implement a zero trust security model to verify every user and device before allowing access to the organization’s IT infrastructure.
4. Geopolitical Cyber
Threats
State-Sponsored cyber attacks are on the rise, targeting critical infrastructure, financial institutions, government agencies, and individuals holding critical positions within those organizations. These attacks can disrupt economies and compromise sensitive data.
How to Prepare:
• Stay informed of emerging geopolitical cyber threats.
• Strengthen your cybersecurity posture by monitoring threats, securing critical infrastructure, and preparing for disruptions.
• Work with cybersecurity experts like CyberWA to develop contingency plans for potential attacks.
5. Social Engineering and Human Error
Cybercriminals continue to exploit human psychology through social engineering tactics such as phishing, pretexting, and business email compromise (BEC) scams.
How to Prepare:
• Conduct frequent cybersecurity awareness training for employees.
• Implement email filtering and anti-phishing tools.
• Establish clear verification processes for financial transactions and sensitive data requests.
Conclusion
The cybersecurity landscape is becoming increasingly complex, but by staying informed and proactive, businesses and individuals can better protect themselves against evolving threats. Investing in AI-driven security, strengthening supply chain defenses, and focusing on cybersecurity awareness training for employees will be key to maintaining cyber resilience in 2025 and beyond.
By implementing these strategies, you can stay one step ahead of cybercriminals and safeguard your organization and its digital assets. Are you ready for the cybersecurity challenges of 2025?

Brian Calkin is the President of Executive Cyber Protection Services at CyberWA. In this role, he oversees the delivery of premium cybersecurity services to high-net-worth clients, A-list celebrities, family offices, and enterprise organizations. Engaging directly with high-value clients, Calkin identifies cybersecurity concerns and develops innovative solutions to strengthen their security posture.
Calkin is also a Senior Technical Advisor at Center for Internet Security, Inc. (CIS®). He is responsible for providing subject matter expertise on the design, development, and implementation of cybersecurity products and solutions, such as Malicious Domain Blocking and Reporting (MDBR), a cybersecurity-focused DNS service offering that has been helping to secure nearly 4,000 U.S. State, Local, Tribal, and Territorial (SLTT) government organizations throughout the country since its inception in 2020.
Prior to his Senior Advisor role, Calkin served as Chief Technology Officer (CTO) at CIS. In that role, he was responsible for establishing CIS' technological vision, technical strategy, and technology-related plans for growth. He also coordinated CIS’ Internal Research and Development program. Prior to this role, Calkin also served in a number of leadership roles in CIS operations services, culminating in his role as Vice President of Operations, where he oversaw all aspects of CIS operations activities, including the 24x7x365 CIS Security Operations Center (SOC) and the Cyber Incident Response Team (CIRT). Prior to CIS, Calkin also held roles at Symantec Corporation and the Rochester Institute of Technology.
Calkin is CISSP-certified. He earned a Bachelor of Science in applied networking and systems administration from the Rochester Institute of Technology as well as a Master of Science in information assurance from Norwich University.
CIS Benchmarks®: From Zero to Implemented in 100 Days
A solid cyber defense policy is one of the best ways to protect your organization against cyber threats, but where to start in developing that policy can be challenging. The CIS Benchmarks provide a simple path toward creating an effective cybersecurity policy
By Brian Hajost
There are two ways to find out how effective your current cybersecurity policy is. The first way is to get hacked. The second way is to implement superior policy.
After facilitating several CIS Benchmarks® implementations, there is something we consistently hear: “We were surprised at all the holes in our previous policy.” It doesn’t matter how big the organization is or how skilled their team is. The light bulb moment is the same.
The topic is especially critical as bad actors are progressing at a speed faster than most organizations can meet on their own. What may have seen us through 2024 is no match for 2025. The heads of the snakes are growing faster than you can chop them off.
We have found you can implement CIS Benchmarks into any size organization in 100 days and end up with the kind of world-class cybersecurity that exhausts bad actors and keeps them away from your valuable
We have found you can implement CIS Benchmarks into any size organization in 100 days and end up with the kind of worldclass cybersecurity that exhausts bad actors and keeps them away from your valuable data — more affordably and with the staff you currently have.
data — more affordably and with the staff you currently have. It all comes down to planning, policy, and operationalization.
Create a Plan and Reframe Your Mindset
One common obstacle we’ve noticed is a lack of planning and pre-planning. Without planning, there can be false starts and a failure to make any significant progress. Here are some of the questions you’ll want to answer before implementing CIS Benchmarks:
• Do we want Level 1 or Level 2 security?
• What is our budget and how do we justify it?
• How and to whom will we communicate our initiative?
• What will our implementation process be?
• Are there tools or automation that can help?
• How will we report on and visualize ongoing efforts?
• How will we handle ongoing maintenance and support?
Along with the above, there needs to be a change in mindset. Implementing cybersecurity is not a project. It is a practice that becomes a habit. One of the benefits of following a best-practice standard like CIS Benchmarks is that new vulnerabilities are regularly updated, keeping you current on the threats of the day.
You can’t just implement a cybersecurity program and be done. Cybersecurity is a living, breathing, constantly changing animal — not something you only tend to when there are issues or alerts. Without CIS Benchmarks, it’s up to you to hunt down new vulnerabilities and fix them. It’s up to you to address drift and maintain policy. Following a standard simplifies all of that and establishes a process you can turn into a daily practice as routine as brushing your teeth.
Establish a Rock-Solid Policy
The policy you establish determines the strength of your secure baseline and everything that sits upon it, from application control, micro segmentation and zero trust to incident response and anti-virus scanning. Holes in the policy lead to holes in everything else.
Everybody has a policy. And nobody thinks their policy or set of configurations has holes. But then, policy usually comes from an individual or team that only knows as much as they know. CIS Benchmarks are globally crowdsourced and consensus-driven among organizations who face a body of threats that may or may not be currently on your radar. Aligning with CIS Benchmarks takes the guesswork out of establishing and maintaining policy and leaves you with nearly impenetrable security in its wake.
Operationalizing Policy and Maintaining a Hardened Baseline
Once you have a policy, you must operationalize it. With a proprietary solution, this means either implementing that policy manually or developing proprietary tools to use for scanning or remediation. You can’t use commercial tools because they have no established policy to scan to. It’s all homegrown by you.

One of the benefits of adopting CIS Benchmarks is that there are commercially available tools you can use to automate parts — or nearly all— of the process. If you want to implement world-class cybersecurity in 100 days, automation will make that possible. Which means, you are currently within 100 days of:

• A more in-depth and involved cybersecurity posture
• Significant cost reductions in terms of effort saved
• Containment and minimal damage if bad actors do get through
• Standards you can easily afford and implement with current staff
• An approach that fits into your daily tempo
• Implementation of the CIS Benchmarks, which are universally-recognized cyber security best practices
The number one reason cybersecurity plans don’t get off the ground is because it’s a daunting task to launch them. We see it every day. Coming up with the plans, policies, and operationalization is more than organizations have the wingspan to tackle. CIS Benchmarks handles some of the heavy lifting for you, while automation turns that heavy lift into a moderate effort you can work into your daily groove when you turn the project into a process by using industry best practices.
Brian Hajost is the founder and COO of SteelCloud, a CIS CyberMarket® vendor partner that develops automated CIS Benchmarks implementation technology. Hajost has transformed SteelCloud into a recognized leader in delivering new technologies that allow organizations to effectively meet the compliance mandates of RMF, NIST 800-53, NIST 800-171, CMMC, and IRS Pub 1075. His technical career has spanned over thirty years, and he holds 13 patents in IT security and two patents in mobile security. Hajost is an active contributor to AFCEA International and is also the Vice Chair of the Advanced Technology Academic Research Center (ATARC) Continuous ATO Working Group.


ISACUpdate
Helping Address Major Cyber Challenges Facing Our Communities with New Research and Strategies
By Carlos Kizzee, Senior Vice President of MS-ISAC Strategy & Plans, and Anthony Essmaker, Senior Regional Engagement Specialist, MS-ISAC
In every community across America, services on which Americans rely — from water treatment and trash pickup to business permitting and public schools — face unrelenting attacks. These attacks, when successful, have significant and costly direct impacts on government services and the everyday lives of citizens.
The effects also ripple throughout the community. When systems such as healthcare, education, water, power, and transportation are disrupted, the impact can be devastating: lockeddown medical records, shuttered schools, compromised water supplies, and/or stalled local economies. Even brief interruptions erode trust in local institutions while depleting limited resources and lowering employee and citizen morale, making normal day-to-day life difficult if not dangerous.
U.S. State, Local, Tribal, and Territorial (SLTT) governments as well as their departments and agencies are the defenders of much of America’s critical infrastructure that keeps everyday life moving forward. These SLTT organizations are uniquely positioned to address local threats and collaborate
with federal entities to share actionable intelligence. Their involvement is crucial in national security efforts, particularly in enhancing cybersecurity and emergency communications. Even privatized services still are dependent on government availability and responsiveness.
To increase awareness about the challenges faced by the SLTT community and recommend a strategy to address key priorities, the Multi-State Information Sharing and Analysis Center® (MS-ISAC®) recently released two reports focused on critical infrastructure and the K-12 sector — the largest and fastest growing member community within the 18,000+ MS-ISAC membership.
Strengthening Critical Infrastructure: SLTT Progress & Priorities - Part 1
Because of the wealth of data and critical infrastructure they maintain, state and local governments represent lucrative targets to threat actors who use ransomware, phishing, and physical disruptions to sow chaos and undermine public confidence. According to data collected by the
MS-ISAC for the Strengthening Critical Infrastructure Report, 80% of SLTT organizations are focused on the threats associated with phishing, 66% see ransomware as a top threat, and 37% admit they are not confident in handling a serious incident.
Cyber and physical threats are increasing in number and complexity. SLTT leaders are often forced to fight this persistent war with outdated technology as well as limited resources. Many SLTT organizations are small and rural jurisdictions that are underfunded, understaffed, and not well served by traditional cybersecurity companies. That’s where the MS-ISAC helps fill the gap by providing critical resources to the SLTT community, which often identifies the MS-ISAC as a key ally and resource.
Battle-Tested Solutions: What is Working
The SLTT community identifies MS-ISAC membership as well as the services and support it provides as key elements of its security program success. SLTTs report seeing incredible results from a number of related

activities, including shared services and whole-of-state solutions, peerto-peer collaboration among IT and cybersecurity professionals in the SLTT community, and multi-year investments that provide long-term funding streams to build long term cyber resilience.
Shared Services and Whole-ofState Solutions
• Security Operations Centers like the 24x7x365 Center for Internet Security® (CIS®) Security Operations Center provide roundthe-clock monitoring and incident response, delivering critical capabilities that smaller jurisdictions can’t sustain on their own. They are also a trusted partner and support system, ensuring you are never alone.
• Centralized threat intelligence ensures that even the smallest municipalities have access to the best information on emerging threats to strengthen their cybersecurity posture.
• Cyber navigator programs and managed security services provide real people in the field to support, discuss, and work collaboratively with SLTTs. SLTT organizations who have used them find these partners to be extremely helpful.
Collaboration and Networking
Through shared after-action reports, audits, real-time communication, and in-person events, the MS-ISAC helps local governments learn from each other. A breach in one city becomes a warning for others, helping communities stay one step ahead as they
mature their cybersecurity programs in trusted collaboration with similarly situated peers.
Multi-Year Investments
Long-Term funding streams enable SLTTs to move from reactive fixes to proactive strategies for effective solutions. With stable funding that is budgeted based on the risks and threats targeting them, organizations can hire permanent cybersecurity staff, modernize infrastructure, and build long-term resilience against ever-evolving threats.
Protecting State and Local Critical Infrastructure
SLTTs are on the front lines of defending vital government services on which their citizens rely and protecting their data, so failure is not an option. Fortunately, they find several things to be helpful in this fight. Leveraging their input and observations, the MS-ISAC recommends focusing on five key priorities for supporting state and local government cybersecurity:
• Invest in supporting real-time threat sharing through active participation in the MS-ISAC and in services like the free protective domain name service Malicious Domain Blocking and Reporting (MDBR) to support early detection and swift containment as well as to protect the critical infrastructure on which Americans rely.
• Build public trust through open data initiatives, .gov domain use, and transparent, simplified, and accessible communication with the public.

• Strengthen security for small, rural communities through low-cost cyber navigator programs, cyber advisory services, and managed security services.
• Take steps to mitigate insider threats by enforcing strict access controls, running background checks, and providing cybersecurity awareness training to employees.
• Address IT and OT talent shortages among state and local governments through workforce development, recruitment, and retention initiatives
To read the full report, please visit https://www.cisecurity.org/insights/white-papers/ strengthening-critical-infrastructure-sltt-progress-priorities .
2025 CIS MS-ISAC K-12 Cybersecurity Report
K-12 schools are prime targets for cybercriminals due to the wealth of student data they maintain and the community-wide impacts of disruptions to their operations. Schools provide critical services beyond education, including nutritional programs, safe spaces, mental

health services, and special education support. Cyber incidents create a ripple effect: parents miss work; vulnerable students lose support; sensitive parent, student, and employee data including health and financial information gets compromised; and entire communities suffer.
Unfortunately, these threats won’t go away, and the K-12 community will continue to be a lucrative data target for threat actors. CIS and the MS-ISAC completed an 18-month study using data collected from multiple sources to identify the current threat trends and provide realistic, actionable recommendations for K-12 schools to improve their cybersecurity efforts. All this and more is included in the 2025 CIS MS-ISAC K-12 Cybersecurity Report.
Threat Trends Facing K-12 Schools
Cybercriminals aren’t just exploiting software vulnerabilities; they are exploiting people through activities such as phishing that targets human behavior. Attacks targeting people exceed other attack vectors by at least 45%. This creates a situation where teachers, administrators, and support staff are on the front lines of cybersecurity without really knowing it, requiring a greater emphasis on

enhancing security awareness across this largely non-technical population.
Cyber threat actors are timing their attacks to achieve maximum impact — often attacking during peak operation times for K-12 schools like exam weeks. Schools experiencing a ransomware attack during one of these peak times may feel that they face an impossible choice: pay a ransom or risk compromising students’ futures.
Thankfully, more and more K-12 schools are learning that they don’t have to defend alone. They’re gaining immense benefits from active participation in communities like the MS-ISAC, which offers no-cost services, guidance, threat intelligence, and opportunities for collaboration as well as critical support before, during, and after cyber incidents.
Cyber Resilience Through Collaboration
K-12 schools cannot build an effective defense alone. In partnership with the MS-ISAC, the K-12 community continues to mature by collaborating together and learning from each other while facing similar challenges.
Early engagement with the MS-ISAC during a cyber incident improves outcomes. Schools that leverage free cybersecurity resources from CIS and the MS-ISAC gain great advantages by leveraging effective cybersecurity capabilities at low or no cost. Proactive cybersecurity strategies reduce risk. They include:
• Multi-Factor authentication designed to support teachers’ workflows
• Backup systems that protect data without adding burden to the education process
• Network segmentation to protect sensitive data while keeping resources accessible
• Community partnerships to maintain critical services during an attack
Additionally, school administrators can avoid making the hard decision of what to do in the face of a ransomware attack by proactively ensuring that their organizations are actively involved in security collaboration with their peers. The MS-ISAC is supporting this collaboration by establishing and sustaining online communities and in-person events to encourage networking and communication. School administrators can all work to ensure that they're implementing security measures like the CIS Critical Security Controls. By focusing only on CIS Controls Implementation Group 1, known as essential cyber hygiene, school administrators can reduce ransomware risk by 80%.
To read the 2025 CIS MS-ISAC K-12 Cybersecurity Report, please visit https://www.cisecurity.org/insights/ white-papers/2025-k12-cybersecurity-report .


UpcomingEvents
April
April 16
The Identity and Access
Cybersecurity Summit will take place virtually. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats affecting identity and access management. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ identityaccess25/.
April 28 - May 1
The National Association of State Chief Information Officers (NASCIO) will host the 2025 NASCIO Midyear Conference at the Sheraton Philadelphia Downtown in Philadelphia, PA. The event will bring together state CIOs and their staff from across the country to network and collaborate with peers, learn from industry though leaders, and discover innovative solutions. Learn more at https://www.nascio.org/conferencesevents/midyear/.
April 28 - May 2
RSAC™ 2025 Conference will take place at the Moscone Center in San Francisco, CA. The event is where the cybersecurity world comes together to gain invaluable insights, engage in deep conversations, and discover transformative solutions that can make an impact on your organization. Attendees will be able to participate in the industry's most comprehensive agenda, featuring hundreds of sessions covering the latest cybersecurity challenges and best practices. CIS CISO Sean Aktinson will lead a session at the event, Game Theory Informed Security Chaos , as will Marcus Sachs, SVP and Chief Engineer, discussing Application of Cyber-Informed Engineering to Municipal Utility Security. Additionally, Tony Sager, SVP and Chief Evangelist, will present a session on Thought Leadership = Mission Leadership: How Ideas Shape Our Cyber Future , while Stephanie Gass, Senior Director of Information Security, and Kennidi Ortega, Senior Information Security Analyst, will discuss Policy Pyramid to Deployment: A Community Approach to Deploying Security. Additionally, the CIS team will be at Booth N-4329 in the North Expo Hall, sharing our cybersecurity resources with attendees. We'll also be hosting an evening reception with members of our global community to celebrate our 25th anniversary. Learn more about the event and what CIS has planned for it at https://www.cisecurity.org/eventcalendar/rsa.
May
May 13 - 15
America's Credit Union Cybersecurity Conference will take place in Charleston, SC. Attendees will explore emerging security risks, AI-driven technologies, and global cybercrime threats. This dynamic event will cover critical topics such as PCI readiness and compliance, offering hands-on cybersecurity planning and interactive workshops designed to provide real-world applications. Learn more at https:// www.americascreditunions.org/ events-training/conference/ cybersecurity-conference-2025
May 15
The 6th Annual Nashville Cybersecurity Summit will take place at the Renaissance Nashville Hotel in Nashville, TN. It will bring together leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/nashville25/.
May 15
The 2nd Annual Toronto Cybersecurity Summit will take place at the Marriott Downtown at CF Toronto Eaton Centre in Toronto, ON. It will bring together leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/toronto25/.

May 19 - 23
The Health ISAC Spring Americas Summit will take place at the Naples Grande Beach Resort in Naples, FL. Attendees will learn vital cybersecurity skills as they explore cyber threat intelligence, cybersecurity compliance, information protection, and more. Learn more at https://health-isac.org/summitmeeting/2025-spring-americas/.
May 20
The Water Information Sharing and Analysis Center (WaterISAC) will host H20SecCon virtually. The event is the premier virtual conference dedicated to fortifying the security of the water and wastewater sector. This essential event brings together top industry experts, thought leaders, and innovators to tackle the most pressing security challenges facing water utilities today. Learn more at https://www.waterisac. org/event/h2oseccon-2025.
May 20 - 23
National Rural Health Association (NRHA) will host its Annual Rural Health Conference in Atlanta, GA. Join NRHA and hundreds of rural health leaders from across the country down in Atlanta to help raise the standard for rural health with over 80 innovative, practical, and cost-saving sessions and much more. Learn more at https://www. ruralhealth.us/events/schedule/annualrural-health-conference
May 21 - 25
The National Association of Counties (NACo) will host its 2025 Western Interstate Regional Conference at the Monument Convention Center in Rapid City, SD. The conference brings together county officials from across the nation to focus on issues facing Western counties and their residents. Attendees will interact with federal, state and regional policymakers, participate in educational sessions, and take home tools to address challenges. Learn more at https://www.naco.org/event/2025western-interstate-region-conference .
May 22
The 2nd Annual Austin Cybersecurity Summit will take place at the JW Marriott in Austin, TX. It will bring together leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/austin25/.
May 28 - 29
The Texas Department of Information Resources (DIR) with host the Information Security Forum for Texas Government at the Palmer Events Center in Austin, TX. The event will feature multiple educational sessions for IT leaders and professionals from across Texas state and local government. MultiState Information Sharing and Analysis Center® (MS-ISAC®) Senior Regional Engagement Specialist Heather Doxon will lead a session covering security best practices and practical applications. Learn more at https:// dir.texas.gov/information-security/ information-security-forum.
June
June 3 - 4
HealthSec Summit USA will take place at the Revere Hotel in Boston, MA. The summit will bring together some of the brightest minds in the industry, uniting 100 cybersecurity and health IT leaders from HDOs, plans/payers, MDMs, and life sciences across the United States to network and share firsthand insights. Learn more at https:// healthsec .cs4ca.com/.
June 4 - 6
The National Center for State Courts (NCSC) will host the NCSC Cybersecurity and Disaster Recovery Southern Region Workshop. This event, as part of a series of regional workshops, will help state courts and their teams make progress on their cybersecurity and disaster preparedness. MS-ISAC Regional Engagement Manager Michelle Nolan will lead sessions at the event on cybersecurity readiness and the CIS Controls.
June 5
The 3rd Annual Salt Lake City Cybersecurity Summit will take place at the Sheraton Salt Lake City Hotel in Salt Lake City, UT. It will bring together leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/saltlakecity25/.

June 8 - 10
Pax8 Beyond will be held in Denver, CO, at the Gaylord Rockies Resort. Master cybersecurity, learn how to grow your business, and elevate your capabilities over three days of groundbreaking sessions with leading industry speakers, MSPs, and vendors. CIS VP of Content Development Phyllis Lee will be a featured speaker at the event. Learn more at https://www. pax8beyond.com/
June 10 - 11
AWS Summit Washington DC will take place at the Walter E. Washington Convention Center in Washington, D.C. This no-cost event is tailored for the public sector community. Attendees will engage in interactive learning, network among public sector industry leaders and AWS experts, engage with partners driving innovation, and so much more. Learn more at https://aws.amazon.com/ events/summits/washington-dc/.
June 12
The 2nd Annual Milwaukee Cybersecurity Summit will take place at the Hyatt Regency Milwaukee in Milwaukee, WI. It will bring together leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/milwaukee25/.
June 16 - 18
AWS re:Inforce will take place in Philadelphia, PA. More than 250 sessions will be available focused on in-depth security learning, including the keynote with AWS CISO Chris Betz, Innovation Talks, breakout content, and interactive learning opportunities. Learn more at https://reinforce. awsevents.com/.
June 17
The 2nd Annual Hartford Cybersecurity Summit will take place at the Hartford Marriot Downtown in Hartford, CT. It will bring together leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/hartford25/.
June 22 - 25
The 18th ISAC Annual Meeting will be held at the Fairmont Scottsdale Princess in Scottsdale, AZ. The event will provide opportunities for attendees to network with peers from other U.S SLTT government organizations, glean key insights from cybersecurity experts, and stay ahead by exploring the latest methods and tools for defending against cyber attacks today and in the future. Learn more at https://www. cisecurity.org/event-calendar/annualisac-meeting.
June 24
The Financial Services Cybersecurity Summit will take place virtually. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats affecting the financial landscape. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/finance25/.
June 24
The 2nd Annual Pittsburgh Cybersecurity Summit will take place at the Westin Pittsburgh in Pittsburgh, PA. It will bring together leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ pittsburgh25/
June 25
The 4th Annual St. Louis Cybersecurity Summit will take place at the Marriott St. Louis Grand in St. Louis, MO. It will bring together leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, U.S. SLTT government entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/stlouis25/.
CIS CyberMarket

Interested in being a contributor?
Please contact us:
CISCyberMarket@cisecurity.org
www.cisecurity.org
518.266.3460
cisecurity.org learn@cisecurity.org
518-266-3460
Center for Internet Security

@CISecurity

TheCISecurity cisecurity CenterforIntSec
