Interview:
Josip Filipović, CRIO, Aldra Alameen
Security Services

Markets: Qatar Security and Safety Market

Interview:
Josip Filipović, CRIO, Aldra Alameen
Security Services

Markets: Qatar Security and Safety Market





Advanced Access Control That:
Simultaneously Captures & Authenticates in Iris/Face Modes
Allows Multifactor Authentication


Works with MIFARE®/DESfire® (HID® SEOS/iCLASS®)13.56MHz
Proximity Cards
Protects Physical Infrastructures
Ensures Privacy
Co-exists with Iris ID iCAM 7 Legacy Systems
Sets Industry Standards






AI, CT, and connected screening ecosystems are redefining the security lane. With automated detection, modular architectures, predictive maintenance, and biometric-linked passenger journeys, airport X-ray scanners are evolving into intelligent platforms that reshape how airports manage risk, efficiency, and compliance
16 Josip Filipović, CRIO, Aldra Alameen Security Services Integration of People, Data, and Operations Is a Core of Modern Security Management
22 Qatar Security and Safety Market Building the Backbone of a Post-Oil Future
FOCUS 40 Inside the Paradigm Shift How Middle Eastern Distributors Are Powering the Next Generation of Security
50 The Vision 2040 IDtech Strengthens Its Presence in Oman
Taking AI to the Edge From Conventional Surveillance to AI Video
The Intelligence Behind the Ecosystem Unifying Voice, Video, and Data for a More Resilient Future
Years of Rapid Change in Digital
Away From Surveillance and into Strategy Can AI-Powered Video Analytics Become Retail’s Source of Intelligence?
World’s First Object Detection
64 A Robust and Holistic Approach Rethinking Physical Access Control in the Age of Cyber Threats
66 The ScreenCheck Approach Building Efficiency Through Interconnected Security
68 Designing Access Control Systems Three Pillars of Identity: Security, Privacy, and Convenience
70 Fully Wireless Detection Technology Reconeyez’s Advanced Solutions at Intersec Dubai
72 Panduit Press Conference We Witnessed What the Future Looks Like
76 Intersec Saudi Arabia 2025 Record Number of Exhibitors and Participants
78 UAE’s Vision for a Safer Future Intersec 2026 Expands to Meet Record Demand
80 ISE 2026
Where Smart Spaces and CyberSecurity Come to Life

Securing oil&gas infrastructure
in the Middle East for over 15 years.


Enterprise Access Control

Professional media for complete security solutions
Management
Mahir Hodžić, General Manager mahir.hodzic@asmideast.com
Adis Hodžić, CEO adis.hodzic@asmideast.com
Editorial Staff
Damir Muharemović, Editor-in-Chief mahir.hodzic@asmideast.com
Mirza Bahić, Associate Editor mirza.bahic@asmideast.com
Dženana Bulbul, Assistant Editor editorial@asmideast.com
Orhan Hadžagić, Journalist orhan.hadzagic@asmideast.com
Fatima Al Husseiny, Journalist editorial@asmideast.com
Roman Ivanković, Journalist editorial@asmideast.com
Art Staff
Sanel Palislamović, Art&Design Editor sanel.palislamovic@asmideast.com
Nelmedin Kolubara, DTP&Art Design dino.kolubara@asmideast.com
Sales Amar Pap, Business Development Manager amar.pap@asmideast.com
International Sales Israel Gogol, International Sales Director Israel.Gogol@taiwan.messefrankfurt.com
International Associates Qatar – Mirsad Selimović, mirsad@techman.qa
a&s Middle East offers the latest news and insights on video surveillance, access control, intrusion detection, fire alarm, mechanical protection, man guarding, cyber security, artificial intelligence, IoT, big data, smart homes and buildings, industrial automation, information, communication technology to Middle East region professional channel players.
a&s Middle East is part of the media network of the Messe Frankfurt Ltd – Taiwan Branch, which offers several media platforms — asmag.com and a&s magazines, published in English, traditional Chinese, and three other languages, providing the most comprehensive industry trends, product, and supply chain information. The total annual circulation is approximately 515,000 copies around the globe. a&s Middle East is published 6 times a year, Jan/Feb, March/ April, May/June, July/August, Sept/Oct, and Nov/Dec.
Payment Instructions
Annual subscriptions are payable in USD, EUR, or AED. Subscription inquiries per your request.
EUR: AE340400000653005131002
Account No. 0653005131002
USD: AE070400000653005131003
Account No. 0653005131003
AED: AE610400000653005131001
Account No. 0653005131001
Copyright Statement
© Copyright by Privus Agency Ltd. All rights reserved. Any republication, copying, redistribution, or reproduction of the magazine in any form, including electronic, without the prior written consent of the publisher, is prohibited. Advertisers are solely responsible for the content of advertising material. The publisher bears no responsibility regarding possible legal, patent, content, or brand disputes of the advertiser.
Legal Disclaimer
The information in this magazine has not undergone any formal testing by Privus Agency Ltd. and is distributed without any warranty expressed or implied. Implementation or use of any information contained herein is the reader’s sole responsibility. While this information has been reviewed for accuracy, there is no guarantee that the same or similar results may be achieved in all environments.
Corporate Address
Privus Agency FZ-LLC
JT010006, Al Shohada Road, Ras Al Khaimah, UAE
Tel: +971 58 983 4258
Web: www.asmideast.com
Marketing: marketing@asmideast.com
Reaching the 18th edition of a&s Middle East is a reminder of how rapidly both time and technologies move. This issue looks at how the region’s security landscape is being transformed by intelligent systems, deeper data insight, and rising operational complexity. In our cover story, we look at the transformation of airport X-ray screening, from traditional 2D images and operator-heavy workflows to CT-based platforms driven by deep learning, automation, and tightly integrated smart-airport ecosystems. What was once a mechanical process is becoming an intelligent decision engine capable of reducing false alarms, improving throughput, and delivering consistent performance as passenger volumes continue to grow.
Complementing this aviation focus, our in-depth report on Qatar’s security and safety market reveals how one of the region’s most ambitious infrastructure programs is redefining national security strategy. Under Qatar National Vision 2030, security is no longer a final layer but a foundational requirement woven through airports, metro systems, LNG facilities, critical infrastructure, and smart-city platforms. The result is a market where interoperability, resilience, and digital readiness are not ambitions but baselines.
Taken together, these stories underscore a central truth for security professionals across the Middle East: the era of standalone systems is over. Security now depends on platforms that communicate, adapt, and operate continuously under real-world pressure. Still, technology may accelerate detection, automate workflows, and elevate efficiency, but human oversight remains essential, especially as cybersecurity, data governance, and regulatory compliance become inseparable from physical operations.
Please visit our official website www.asmideast.com and select ‘Subscribe Now’ option under THE MAGAZINE menu.
Subscription includes all six editions.
Digital edition is FREE and readily available at the official website.

The new IDIS Edge AI Plus Camera range takes security and safety to a new level of efficiency for real-time monitoring and incident review

Supercharge your security and safety operations with the IDIS Edge AI Plus Camera range. It features IDIS A-Cut Monitoring and IDIS Deep Learning Analytics (IDLA) Pro event functions - including crowd detection, abandoned object, removed object and fall detection. These new functions enable faster investigations and response times thanks to automatic image cropping, intuitive attribute searches, and advanced automated alerts, as standard.
The latest market research by Memoori forecasts steady growth for the global video surveillance industry, projecting revenues to rise from $35,5 billion in 2024 to $47,9 billion by 2030.
According to the report “The Physical Security Business 2025 – Video Surveillance Market Research”, the sector continues to expand despite economic uncertainty, driven by technological innovation, AI-enabled analytics, and growing demand for integrated cloudbased systems.
Memoori notes that the video surveillance industry is increasingly influenced by software-centric business models, where value creation is shifting from hardware manufacturing to intelligent solutions. The emergence of subscription-based services, edge computing, and cybersecurity integration are among the defining trends reshaping the market landscape.
The research also highlights regional differences in adoption: while Asia remains the largest market, accounting for nearly 50% of global revenues, North America
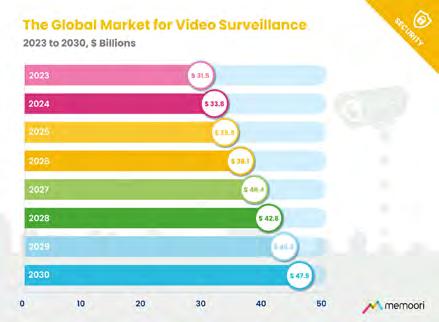
and Europe continue to show strong growth momentum in enterprise and public-sector projects, particularly in smart cities and critical infrastructure.
Memoori’s comprehensive study offers detailed insights into competitive dynamics, vendor strategies, and innovation trajectories within the industry. n
BILLION BY
The global access control market is set for steady expansion, rising from $ 10.62 billion in 2025 to $ 15.80 billion by 2030, according to a new report from Marketsandmarkets. The growth, at a compound annual rate (CAGR) of 8.3%, is primarily driven by the adoption of IoT-enabled security systems and cloud-based platforms.
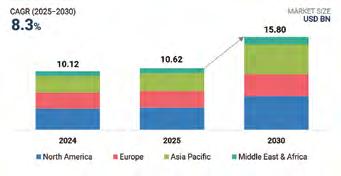
The report highlights that Internet of Things (IoT) technologies are enhancing automation efficiency by enabling secure, real-time data exchange. At the same time, cloud integration offers scalability, remote monitoring, and lower maintenance costs. Together, these technologies underpin the rise of Access Control as a Service (ACaaS), enabling organizations to manage access rights across multiple locations through flexible, centralized platforms. Hosted ACaaS solutions are expected to hold the largest market share in the coming years due to their scalability, flexibility, and cost-effectiveness. Unlike traditional systems, ACaaS removes the need for on-site infrastructure, as data is stored and managed remotely by third-party providers. This setup enables users to manage credentials, access rights, and monitoring tasks from anywhere, ensuring seamless system updates and enhanced cybersecurity resilience.
The study notes that cloud-based access control eliminates the need for client-side software while enabling centralized monitoring across multiple facilities. Automated updates, security patches, and remote troubleshooting contribute to system continuity and reliability—key factors in the growing preference for ACaaS over on-premises models. n







Strong and elegant, the Xpro range combines multi-technology security with full customization. Powered by Xsecure®, it delivers a unique layer of advanced protection.
Compatible with MIFARE® (13.56 MHz) and supporting RS-485, OSDP, and Wiegand, Xpro is easy to configure via USB-C or programming card.
Includes free setup software, and is certified IK10 / IK11, IP65, withstanding -30 ºC to +65 ºC.
Digital Dubai announced a landmark initiative to empower its employees with AI capabilities in partnership with Microsoft. The move follows Microsoft’s recent announcement to enable local data processing for Microsoft 365 Copilot in the United Arab Emirates.
The initiative ensures that employees across departments benefit from AI tools that streamline workflows, enhance decision-making, and foster collaboration—while maintaining the highest standards of data security and regulatory compliance.

H.E. Hamad Obaid Al Mansoori, Director General of Digital Dubai, said: “This partnership with Microsoft is part of a long-standing commitment to collaborate with major global corporations that serve our mutual goals of advancing AI-powered digital transformation for the benefit of people. We view Artificial Intelligence not merely as a tool but as an engine for change, dedicated to building a smart city that offers its residents proactive, holistic digital experiences, embodying the principle of ‘City as a Service.’
Al Mansoori added: We believe that equipping employees with artificial intelligence capabilities effectively empowers society as a whole, advances the process of shaping the future, and achieves human happiness. We will therefore ensure this partnership serves Dubai government entities by empowering their employees and equipping them with the robust capabilities of Microsoft’s AI ecosystem.” n
Riyadh Municipality has launched the “Smart Surveillance System” in the capital’s parks and public plazas as part of its ongoing efforts to utilize advanced technologies that improve the quality of life, enhance public safety and security, and provide a healthy, safe environment for residents and visitors.
The project aims to strengthen protection for visitors and public property through an advanced monitoring system comprising over 1,600 cameras distributed across parks. These cameras use artificial intelligence to analyze data and detect abnormal or unsafe behaviors, enabling rapid emergency response.
The system’s cameras monitor park activities around the clock, covering incidents such as fainting, child safety or loss, and unauthorized gatherings. They also detect violations such as lighting fires, damaging plants, graffiti, or tampering with public facilities. The system relies on advanced analytical technologies capable of instant

recognition of violations and alerting supervisors to take immediate action.
Furthermore, the system provides direct digital connectivity with the Municipality’s central control rooms, enhancing decisionmaking speed and efficiency in handling
reports and incidents within parks while ensuring service continuity and quality. It also utilizes AI-driven data analysis to generate regular reports that support improved park management and the development of future operational plans. n


Telecom Infrastructure
Antennas, cables, and passive components for reliable connectivity.
• RF Antennas
• RF Cables & Connectors
1/2” - 7/8” - D10 and more
• DAS & Passive Components
• Mounting Accessories
• Towers & Shelters



Adaptive radios and tactical solutions for security and defense.
• Ad-Hoc Mesh Base Stations
• Portable Repeaters
• Industrial 5G Outdoor CPE
• Mission-Critical Radios
• Integrated LTE Solutions
• Tactical Surveillance










Microwave & Broadband
High-capacity backhaul and 5G-ready wireless solutions.
• High-Capacity Point-to-Point
• Point-to-Multipoint Networks
• Legacy Microwave (E1)
• 5G-Ready Connectivity







The Integrated Transport Centre (ITC), an affiliate of the Department of Municipalities and Transport (DMT), has launched a fleet of Robosweeper autonomous cleaning vehicles on the Abu Dhabi Corniche.
The project, developed by K2 subsidiary Autogo under the supervision of the Smart and Autonomous Systems Council, is overseen by the DMT. It underscores the emirate’s aim to innovative, intelligent, and sustainable public facility management.
The Robosweepers offer an advanced cleaning and sanitisation solution utilising sensors and modern navigation technologies.
The units move along pre-programmed routes, cleaning without direct human intervention.
Designed for urban environments such as pavements, squares, and pedestrian areas, they help reduce the reliance on manual labour while ensuring optimal public hygiene services.
The initiative is a crucial step in Abu Dhabi’s efforts to build an integrated, advanced services system, aligning with the Emirate’s strategy to enhance operational efficiency and quality of life.
Dr. Saif Sultan Al Nasri, Acting Under-Secretary at DMT, said, “The deployment of such technology exemplifies our proactive approach to integrating cutting-edge technology into public in-
DESC

frastructure. By pioneering such solutions, we are actively shaping a future where innovation directly contributes to operational management and enhances the well-being of our community. This programme reinforces Abu Dhabi’s global standing as a forward-thinking, highly efficient capital city. n
On the occasion of Cybersecurity Awareness Month, the Dubai Electronic Security Center (DESC) launches the “Scan Smart” campaign from 24th to 30th October 2025, an initiative aimed at raising awareness, empowering every citizen with cybersecurity knowledge, protecting
businesses, and preventing QR coderelated cyber threats across all audience groups.
As QR codes become increasingly integrated into everyday transactions at restaurants, retail outlets, hotels, events, and other facilities, the risk of tampered

or malicious codes poses a significant cybersecurity challenge. Threat actors can exploit public QR codes by replacing or overlaying them, potentially redirecting users to phishing sites, installing malware, or capturing sensitive personal data.
Reports indicated that more than 4.2 million attempts to forge QR codes were detected globally in the first half of 2025 alone, highlighting the urgent need to raise awareness about these risks and encourage users to adopt safer habits when scanning codes.
Through the “Scan Smart” campaign, DESC seeks to equip both individuals and businesses with the tools to recognize legitimate QR codes, avoid tampered ones, and report suspicious activity, transforming awareness into action to strengthen Dubai’s digital resilience.
The campaign includes an interactive kiosk and an engaging microsite designed to educate the public on safe QR code practices. The campaign also promotes RZAM, DESC’s free browser extension, which detects suspicious websites that may appear after scanning QR codes. n

Dubai Police introduced its innovative Biometric Tunnel- a project by Dubiometrics, at GITEX Global 2025 which is being held at the Dubai World Trade Centre.
The smart tunnel uses artificial intelligence and machine learning to record and analyse a person’s movements (aka

Gait) as they walk through it, creating a unique motion fingerprint that can help identify individuals by their walking style.
Lt. Col. Dr. Hamad Mansour Al Awr, the project director, explained that the Biometric Tunnel is one of Dubai Police’s new innovations and is currently in the research and development stage. It supports forensic experts in identifying individuals through precise measurements of their body movements and physical features.
He said the tunnel captures a person’s motion fingerprint in just five seconds by recording detailed movements such as joint motion, walking rhythm, and unique traits like the influence of flat feet.
Al Awr added that the system combines artificial intelligence and machine learning to link motion biometrics with other identifiers such as facial, ear, and body measurements. This integration provides strong evidence in criminal investigations, especially when traditional identification methods are not possible.
He concluded that analysing walking patterns and body movements helps forensic experts identify individuals more accurately, providing valuable evidence that strengthens police investigations and supports justice. n
Emirates has launched a series of technology upgrades at Dubai International Airport, aimed at making travel smoother and more inclusive for all passengers, Gulfnews reports. The reveal took place during the AccessAbilities Expo 2025, where the airline introduced enhanced Smart Tunnel cameras, voice-activated check-in ki-
osks, and a reimagined business class mattress design.
At Terminal 3, Emirates has upgraded its Smart Tunnel system to include dual-height facial recognition cameras—a move that benefits children, wheelchair users, and all travelers. Previously, the system’s placement favored average adult height. The new lower camera is

positioned around one meter high to ensure greater inclusivity.
With the Smart Tunnel, travelers pass through immigration in seconds without needing to present passports or boarding passes manually. The system matches live facial images with digital records stored in immigration databases.
Emirates is also rolling out redesigned self-service check-in kiosks equipped with:
Braille-enabled navigation bars that speak the screen steps aloud, assisting visually impaired users.
Highly responsive touch sensors, allowing even light taps to register without requiring strong presses.
Improved display settings, including contrast adjustments, to enhance visibility for color-blind users or those with visual limitations.
The kiosks have been upgraded across all Dubai Airport self-service and bag-drop points. Emirates notes that the technology aligns with standards used in U.S. airports, such as those in New York. n
The Technology Innovation Institute (TII) and ASPIRE, both subsidiaries of the Advanced Technology Research Council, in collaboration with the General Civil Aviation Authority (GCAA), are helping to position the UAE among the glob -

al pioneers in achieving an AAM regulatory framework, where TII will work on providing evidence-based recommendations to guide the development of Advanced Air Mobility (AAM) interfaces and solutions. This work is being overseen by the Smart and Autonomous Council, which plays a central role in guiding national efforts in autonomous systems and mobility.
While global interest in Advanced Air Mobility (AAM) is growing, few countries have introduced operational regulations or corridor simulation tools specific to autonomous air taxis. By launching simulation-driven trials across Abu Dhabi, the UAE is helping define the technical and regulatory standards for this next era of urban mobility.
TII is spearheading the UAE’s first simulation-based regulatory models for airspace corridors, with a focus on wind dynamics and flight safety boundaries. These models are foundational in informing data-driven regulation for both manned and autonomous aerial vehicles, ensuring orderly airspace management while minimizing ground risk. ASPIRE has played a central role in enabling the collaboration, supporting the broader ecosystem that underpins the safe and scalable deployment of autonomous air mobility. n
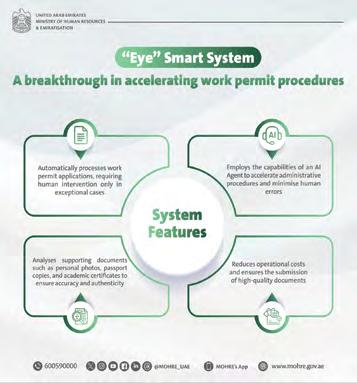
The Ministry of Human Resources and Emiratization (MoHRE) has launched the Eye AI system during its participation at GITEX Global 2025, marking a major leap in digital transformation and automation within the UAE’s labour market services.
The MoHRE Eye AI system is designed to enhance the speed and accuracy of work permit issuance by automating administrative processes and minimizing the need for human intervention. The system employs an AI-powered agent to verify required documents, including personal photos, passports, and academic certificates, ensuring their authenticity and compliance with ministry standards.
Rashid Hassan Al Saadi, Acting Assistant Undersecretary for Labor Market Services at MoHRE, stated that, “The system forms part of a broad portfolio of digital transformation and AI initiatives that elevate the standards of government services and pioneership.”
“The system reflects the ministry’s high level of digital readiness, our leading role in supporting ambitious national directives, and our commitment to advancing innovation and AI applications across all labor market fields,” Al Saadi added. The Eye AI system delivers tangible benefits by reducing operational costs, cutting processing times, and improving the accuracy of document submissions. By ensuring faster and more reliable approvals, the technology enhances the overall customer experience and sets new standards for efficiency in labor market management. n

We built what we call an operational intelligence framework. It’s both a philosophy and a digital architecture. Every piece of information enters one secure environment. From there, it feeds analytical dashboards accessible to the management level. The key is that people and data don’t compete, they cooperate. Technology supports professionals, not the other way around
n By: Damir Muharemović damir.muharemovic@asmideast.com
a&s Middle East: The position of Chief Resources and Information Officer remains uncommon in the private security sector. What does the CRIO role represent in practice?
Filipović: Security today is a system of systems. You can’t protect a client or a facility effectively if your own organization is fragmented, meaning that if human resources, operations, and information technology all speak different languages. The CRIO role at Aldra exists to prevent that disintegration. It connects the human side of the business, our people, their skills, their readiness, with the informational backbone that drives every decision. At Aldra Alameen, the CRIO position sits at the intersection of technology and leadership. My team ensures that the information generated on the ground: incident and regular reports, movement logs, training data, risk analyses, etc., flows seamlessly to those who plan strategy. It’s not about managing IT for its own sake, but rather about turning raw data into usable awareness, into information. When that loop functions correctly, decision-making becomes faster, accountability becomes transparent, and our clients see the difference immediately.
a&s Middle East: How did your own background lead you to this integrative approach?
Filipović: My early career in the military and various security organizations in multiple international operations has shaped how I see information. In those environments, success depends on two things: clarity and timing. You can have the best plan in the world, but if information arrives late or incomplete, everything falls apart. That lesson never leaves you. When I transitioned to the corporate side, I noticed that many private-sector companies still suffered from delayed communication and isolated departments.
So I started enhancing bridges between human resources, logistics, and command centers by using digital tools guided by human discipline. Over time, that became our culture at Aldra: everyone understands that accurate reporting is not bureaucracy, it’s a form of protection.
a&s Middle East: Information management has existed for decades at the managerial level across industries. What makes its integration at the operational and employee level so important today?
Filipović: You’re absolutely right. Information management is not new. For decades, it has been present in most organizations, especially at the managerial level: human resources, logistics, finance, and planning. What is changing now is the direction of information flow. It’s no longer enough for informatization to live only in offices or control rooms. The real breakthrough happens when we move it down to the operational level, to the people actually performing the task. At Aldra, we aim to make information collection immediate and continuous throughout the day, directly from the field. Our systems are designed so that the last person in the chain, whether it’s the operator, guard, or manual technician, can enter data directly into the platform using specialized devices. That data might be
spreadsheets, and finally processed hours or even days later. That method wastes time at every step. Managers are making decisions on outdated information, and teams lose valuable time to bureaucratic paperwork after their shift. Our approach builds the report dynamically, as the day unfolds. By the end of the shift, management already sees what has happened, what needs attention, and where resources must move next.
Of course, this requires capable and welltrained personnel. Digital systems are only as good as the people who use them. We invest heavily in training our staff not only in operational duties but also in data discipline and digital literacy. They must understand that the information they enter is not only administrative but also operational. It directly influences logistics, readiness, and risk decisions made at the highest level.
a&s Middle East: In practical terms, how does Aldra integrate information and resource management?
Filipović: We built what we call an operational intelligence framework. It’s both a philosophy and a digital architecture. Every piece of information, whether it’s a training record, equipment status, or site daily and incident report, enters one secure environment. From there, it feeds
At Aldra, everyone understands that accurate reporting is not bureaucracy, it’s a form of protection. Over time, that became our culture
very raw at first, but its value lies in the fact that it is already inside the system, timestamped, geolocated, and visible to the right managers. From there, it’s automatically filtered through various levels, refined, and used for decision-making almost in real time.
This approach replaces the old “hardcopy” cycle, where data was written on paper, carried back to base, typed into
analytical dashboards accessible to the management level.
For example, a project manager can instantly see staffing levels, qualifications, and readiness indicators across multiple locations on the allocated project. If one’s certification is about to expire, the system flags it automatically. If a pattern of incidents starts emerging, the analytics visualize it before it becomes a problem.

The key is that people and data don’t compete, they cooperate. Technology supports professionals, not the other way around.
a&s Middle East: Many organizations claim to be data-driven. What distinguishes Aldra’s model?
Filipović: Being data-driven means little unless the data is reliable and interpreted correctly. We emphasize discipline in data. Every entry is verified and timestamped; every report follows a structured template; every access is logged. This discipline creates trust in the logged facts. Then comes interpretation. Our analysts don’t work in isolation. They collaborate directly with operations and other relevant staff. That dialogue turns statistics into understanding. We don’t drown in data; we refine it until it supports action. Ultimately, the value of information lies not in volume but in precision.
a&s Middle East: Integration also involves people. How does information management improve human-resource performance?
Filipović: The connection is direct. Information reveals patterns that help us manage people fairly and effectively. Our internal platform tracks training history, fitness results, evaluations, and incident involvement. From that, we generate a readiness index for each individual. Leaders can see who is prepared for
a&s Middle East: How does information management change the role of leadership?
Filipović: Today, when we talk about information management, time is the most critical factor. The speed at which accurate data moves from the field to decisionmakers defines the efficiency of the entire organization. That’s why informatization must start from the bottom. The role of leadership then is not to re-enter or re-create data, but to interpret, verify, and act on it. It’s a complete change of mindset. From post-event reporting to real-time management. In our industry, that immediacy can make the difference between preventing a problem and merely documenting it afterward.
more responsibility, who might need support, and where additional mentoring is required. This makes HR truly operational, so there is no longer administrative paperwork but a living system of competence management. It also supports transparency. When people know that promotions or assignments are based on verified performance data, morale improves. We’re not guessing; we’re recognizing merit.
a&s Middle East: What challenges do you see when companies attempt digital transformation in security?
Filipović: The main challenge is cultural, not technical. You can buy software, but you can’t buy discipline. Some organizations believe that a new platform will automatically solve communication or accountability issues. It never does. If re-
porting habits are weak or if leadership doesn’t use the data consistently, even the best system will collapse into confusion. Technology strengthens existing habits. It doesn’t create them. That’s why digital transformation always begins with people, culture, and leadership, not with coding or servers.
Another major challenge is the fear of complexity. Many professionals worry that technology will replace human judgment or make their jobs more complicated. However, when properly designed, digital tools simplify work. They eliminate unnecessary repetition, bring clarity, and guide people toward the right decisions faster. The best compliment we can receive from our teams is when someone says, “This system actually makes my job easier and saves a lot of time.” That’s when you know the system is doing its job.
And finally, transformation cannot succeed without strong leadership vision. In any organization, digitalization is not an IT upgrade. It’s a strategic shift toward transparency, reliability, and long-term efficiency. At Aldra Alameen, we are fortunate to have a CEO, Mr. Lario Lovrić, whose vision and sense of timing have been crucial in this process. He clearly saw that modern security management would soon depend on the integration of people, data, and operations into one structure. As he often says, “If information doesn’t move as fast as the operation, the operation will slow down.” That mindset set the tone for everything that followed.
a&s Middle East: You’ve mentioned “discipline” several times. How do you instill that in such a diverse workforce?
Filipović: By linking it to pride rather than punishment. People respect rules when they understand that those rules protect their colleagues and reputation. We explain the why behind every procedure. If a guard knows that accurate logs help prevent confusion during emergencies, compliance becomes natural. We also train supervisors to lead by example. When leaders submit reports on time and verify data carefully, the habit spreads. Discipline is contagious when it’s modelled and not demanded. It’s part of what we call presence-based leadership, leaders visible in practice, not just in policy.
a&s Middle East: How do you manage to keep the “human touch” when so much is digital?
Filipović: By remembering that technology serves relationships. Every digital tool we introduce is meant to strengthen communication, trust, and collaboration among people. The purpose of informatization is not to reduce human contact but to make it more meaningful. For example, when routine reporting becomes automated, managers no longer spend their day chasing paperwork. They spend it coaching, mentoring, and engaging with their teams. When field staff can instantly report from a site or receive guidance from headquarters through a secure mobile platform, the distance between management and operations disappears. What used to take days of phone calls or emails now happens in real time. Conversation is still human,

Custom-built software gives us the freedom to design exactly what we need – a complete ecosystem built around our own procedures, risk models, and command structure. We don’t have to adapt our operations to the tool; the tool adapts to us
a&s Middle East: How do you define Aldra Alameen’s mission in this broader context of the security industry?
Filipović: Our mission is to build trust through precision. We believe that reliability is earned, not advertised. By integrating information management with disciplined resource leadership, we give clients confidence that every action is traceable, every risk is considered, and every response is accountable. Aldra Alameen’s culture rests on three pillars: professionalism, transparency, and adaptability. Those values transcend any single industry segment. Whether protecting a corporation, a government installation, or an individual mission, the logic is the same: combine technology with ethics, data with discipline, and people with purpose. Security will always evolve, but one thing remains constant: success belongs to those who can connect knowledge with action. That’s what we strive for every day.
just faster, clearer, and better informed. We also invest a lot in digital empathy, understanding what our people actually experience when using these tools. If a process feels bureaucratic or impersonal, we redesign it. The best systems are invisible: they support without distracting, they inform without overwhelming. That’s how you keep technology humancentered.
a&s Middle East: Many security companies rely on commercial off-the-shelf software for managing their operations. Why did Aldra Alameen choose to invest in developing its own customized systems instead?
Filipović: Because commercial solutions almost never reflect the real tempo or structure of field operations. Most are designed for office use or for industries with stable connectivity and predictable workflows. In security, especially when you operate across multiple continents and in complex environments, the situation is completely different. Our people work in locations where internet access is limited, conditions are harsh, and operations cannot wait for “system updates.” Custom-built software gives us the freedom to design exactly what we need, not 80 percent of it, not a template adjusted to fit, but a complete ecosystem built around our own procedures, risk models,
and command structure. We don’t have to adapt our operations to the tool; the tool adapts to us. That’s a major difference. Another key reason is integration. In many commercial systems, you end up with isolated modules for HR, logistics, operations, and reporting that don’t communicate well with each other. We built our platform so that recruitment, training, logistics, and field operations are all connected in one flow. When a new employee completes a training module, the information immediately updates readiness records, deployment eligibility, and client compliance dashboards. It’s seamless and eliminates duplication. Security is another decisive factor. With custom development, we have full control over where data is stored, who accesses it, and how it is encrypted. That level of data sovereignty is crucial in our industry, where confidentiality is not just a business concern but an operational necessity. And finally, customization allows us to evolve. Our software is growing together with the company, adapting to new types of projects, new client requirements, or regulatory frameworks without waiting for an external vendor’s update cycle. It’s not about owning a piece of technology. It’s about owning our process and protecting our standards. For a company like Aldra Alameen, that independence is a strategic advantage, not a luxury.
a&s Middle East: How important is specialized equipment when operating in demanding environments?

The next transformation will be convergence. Physical security, cybersecurity, and information management will no longer be separate disciplines. Organizations that still separate those elements will find themselves too slow

Filipović: It’s absolutely essential. You can have the best software design, but if the hardware fails in the field, your whole system collapses. Our teams work in deserts, offshore platforms, and other challenging environments where dust, humidity, heat, and rough handling are daily realities. Ordinary commercial tablets or laptops don’t last there. That’s why we use rugged equipment designed for these conditions: tablets and handhelds with reinforced cases, sunlight-readable screens, extended battery life, and sealed ports. They can take a fall, survive rain, or operate in 55-degree heat. This is what makes digitalization truly operational. A rugged tablet replaces entire binders of manuals and checklists, providing procedures, communication tools, and incident-reporting apps right in the hands of a user. It bridges the gap between technology and field practicality, between what’s planned at headquarters and what’s executed on the ground. When your technology survives the environment, your system survives the mission.
a&s Middle East: The security sector often deals with sensitive personal data. How do you balance operational transparency with privacy?
Filipović: Through proportionality and clear intent. We collect only the information necessary for safety and performance, nothing more. All staff are
informed about what data is stored, for how long, and, most importantly, who can access it. Transparency eliminates suspicion. We also anonymize data whenever possible. For analytics, we look at aggregated trends instead of individual names. That allows us to improve operations while respecting privacy. Ultimately, ethical handling of data is not just compliance, it’s respect for the people who make the organization work.
a&s Middle East: How has the profile of a security professional changed during your career?
Filipović: Twenty years ago, physical strength and obedience were the main criteria. Today, we look for adaptability, communication, and digital awareness. Security professionals now operate equipment, manage data, and interact with multinational clients. They must think like analysts while acting like protectors. That evolution requires new training methods. We teach not only tactics but also decision-making, ethical reasoning, and situational analysis. The goal is a professional who can respond effectively in both physical and informational dimensions of security. It’s a more demanding profile, but also a more rewarding one.
a&s Middle East: For young professionals entering the field, what skills should they focus on?
Filipović: Learn technology, but never forget judgment. Understand data, but understand people better. The best security professionals of the future will be translators between machines and humans. They’ll know how to read dashboards and also how to read a room.
I also recommend developing communication and writing skills. Reporting clearly is as important as acting quickly. A wellwritten incident report can save an operation days of confusion. And finally, stay curious. Technology will change, but curiosity keeps you adaptable.
a&s Middle East: Finally, what do you see as the next major transformation in the industry?
Filipović: The next transformation will be convergence. Physical security, cybersecurity, and information management will no longer be separate disciplines. They will operate through unified platforms where incidents, data, and personnel are managed in one continuum. Organizations that still separate those elements will find themselves too slow.
Artificial intelligence and automation will continue to grow, but the real revolution will be in mindset. Companies will need leaders who understand both the human and the digital terrain. That’s where the CRIO function will become standard. Every serious organization will need someone who bridges resources, information, and strategy. n

WHEN QATAR UNVEILED ITS NATIONAL VISION 2030, THE MESSAGE WAS UNAMBIGUOUS: THE COUNTRY’S HYDROCARBON WINDFALL WOULD NOT LAST FOREVER, AND IT INTENDED TO BE READY. FIFTEEN YEARS LATER, THAT VISION HAS TRANSLATED INTO ONE OF THE MOST AMBITIOUS INFRASTRUCTURE BUILDOUTS IN THE GULF. WITH IT, A SECURITY AND SAFETY MARKET THAT HAS QUIETLY BECOME ESSENTIAL TO THE ENTIRE ENTERPRISE
n By: Roman Ivankovic editorial@asmideast.com
The numbers tell part of the story. In 2025, the Qatari government allocated USD 57.75 billion to infrastructure expenditure, a 4.6% year-on-year increase that signals continuing momentum across transport, energy, and urban development. Oil revenues, meanwhile, now account for 78% of projected income, down from 82% just two years ago. It is now completely clear that diversification is not merely aspirational but actively underway. Yet what distinguishes Qatar’s approach is not the scale of investment alone, but its underlying philosophy: security and safety systems are treated not as compli-
ance afterthoughts, but as foundational enablers of modernization itself.
After the FIFA 2022 World Cup ended, Qatar used the infrastructure as a stepping stone for further developments. Following huge transportation, communication, digital, and other investments, the country continued to expand capacity and operational capabilities, sustaining demand for integrated screening, perimeter protection, and command-andcontrol upgrades. For security vendors and integrators, this constellation points to predictable, multi-year demand rather than event-driven spikes.
Underpinning all of this is Qatar’s push toward a connected, data-driven state. The TASMU Smart Qatar program catalogs

over a hundred digital use cases across priority sectors, promoting shared platforms that accelerate service delivery and demand interoperability across video, access control, fire/life-safety, and OT sensor networks. End users are no longer simply buying hardware; they are prioritizing systems that integrate into centralized command centers, support cloud and hybrid architectures, and remain auditable and maintainable in one of the world’s harshest operating climates. This is the context in which Qatar’s security and safety market now operates: policy continuity under QNV2030, premium infrastructure requiring lifecycle protection, and a structured digital transformation that rewards platforms over
point solutions. The sections that follow examine how these dynamics are shaping market performance, vertical activity, technology adoption, and the outlook for the sector.
Qatar’s economy remains underpinned by a strong fiscal base, enabling sustained investment in infrastructure and enabling sectors, both of which drive the security and safety market. In 2025, the Qatari government allocated USD 57.75 billion to expenditures aimed at infrastructure, marking a 4.6 % increase year on year. The capital outlay signals continuing momentum in large-scale projects, from road networks and urban redevelopment to energy facilities and transport hubs. Further, macro-economic data suggest that diversification efforts are underway: oil revenues are projected to account for 78 % of total projected revenues in 2025, down from 82 % in 2023, reinforcing the push into non-oil sectors such as infrastructure, services, and technology. Sargunan Sellamuthu, Business Development Manager for the Middle East in fire-safety solutions company Advanced, stresses that Qatar’s fire and life safety market continues to advance in line with the nation’s Vision 2030, driven by substantial investments across healthcare, education, commercial, and residential developments. “Qatar Civil Defense is among the most advanced authorities in the GCC, actively adopting new technologies such as wireless fire alarm systems and prioritizing international best practices,” he says.
These are critical for the security and safety market: large infrastructure builds demand for integrated surveillance, access control, lifecycle safety systems, as well as cyber-physical protection. Meanwhile, non-oil sector growth means more commercial buildings, logistics hubs, and smart city deployments – all of which raise the profile of security investments. According to the market report overview by 6wresearch, the Qatar security services market is expected to grow strongly by 2031, with the construction and infrastructure sector cited as a key contributor.
Operationally, throughput indicators at critical nodes remain strong. Hamad International Airport also marks a steep increase

Ashok Warrier, Regional Business Manager from Panduit, points out that Qatar wants to be recognized among the safest and most secure nations globally, while ensuring an exceptional quality of life for both citizens and visitors. Stressing the importance of a proactive approach, he notes it all boils down to continuous modernization and system upgrades: “We note that Qatar, as an early adopter, uses advanced technologies to stay one step ahead of ever-evolving threats. This commitment reflects the country’s strategic focus on creating a resilient and secure environment that also supports its broader economic and digital transformation goals.”
in passengers (up 15% YoY), aircraft movements (+10%), and cargo (+12%).
Such volumes sustain demand for largescale screening, perimeter, terminal safety, and command-and-control upgrades.
Several interlinked forces are driving growth in Qatar’s security and safety segment. First, the drive for smart national infrastructure (transport, utilities, buildings, and city services) has pushed demand for advanced security systems.
“In Qatar, where mixed-use spaces and remote developments are growing in popularity, we have seen an increase in the demand for flexible, high-integrity fire detection systems to meet the needs of these complex constructions,” underlines James Morrison, Regional Sales Manager at Hochiki. He explains that the envi-
ronment has matured to the point where compliance and innovation are essential, stressing that growth is especially evident in areas where protecting people and assets is non-negotiable, such as hospitality, healthcare, and education.
For example, the adoption of cyber security as a growth vector is evidenced by market size estimates: the cyber security market in Qatar was estimated to grow at nearly 13% percent year over year, reaching over US $1.6 billion by 2026. This digital security growth reflects the broader convergence of physical and cyber security.
Additionally, Qatar continues investment in critical infrastructure, such as ports, rail, subway, and energy facilities (The North Field expansion program), which creates persistent demand for traditional security: access control, perimeter defense, surveillance, fire and life safety systems, as well as emergency management. According to GCC Business Watch, the

Sargunan Sellamuthu, Business Development Manager, Middle East, Advanced


Manager, Hochiki
infrastructure market in Qatar is forecast to reach US$41.3 billion by 2030. Regulatory and operational imperatives are sharpening demand. The Gulf climate imposes harsh operational conditions (heat, dust) that require resilient, reliable safety equipment. At the same time, regulatory compliance and risk mitigation (especially in areas like oil and gas and industrial logistics) are forcing entities to upgrade legacy systems.
Finally, global event legacies, such as the FIFA World Cup 2022, and the accompanying attention on safety, security, and public-event infrastructure, have left a legacy of heightened expectations. These combined forces ensure that the security and safety market is not just projectbased, but moving into lifecycle upgrade and system-replacement mode.
Companies operating around infrastructure security, industrial safety solutions, cyber and physical convergence, as well as systems integration, are especially well-positioned in Qatar’s market.
Thomas Deville, IDtech’s General Manager for the Middle East, Africa, and Asia, explains that the post-World Cup period has brought a slowdown, as Qatar works
to regain economic momentum and restore investor confidence after a period of turbulence. “In this evolving context, the next wave of growth in the security and safety sector will likely stem from carefully planned, strategically monitored investments led by key Ministries and state-owned enterprises - ensuring that modernization continues in line with the nation’s long-term vision,” he concludes. In terms of where the largest investments are flowing, three clusters stand out. One is the infrastructure and transport sector: Qatar’s 2025 budget emphasizes expansion of high-quality roads, large-scale construction developments, and urban facility upgrades. For stakeholders in the security and safety industry, this means major contracts around airports, metro systems, ports, and highways where large-scale access, surveillance, and safety systems are required. Another cluster is energy and industrial infrastructure. The country’s big LNG expansion and petrochemical builds necessitate high-specification safety, perimeter defense, industrial-cybersecurity integration, and health, safety, and environment (HSE) systems. According to a Nexdigm market research, the infrastructure construction market in Qatar is valued at USD 65.7 billion in 2024 with a projected CAGR of ~10.2 % to 2030.
Additionally, investment in the digital do-
“Qatar Civil Defense is among the most advanced authorities in the GCC, actively adopting new technologies such as wireless fire alarm systems and prioritizing international best practices” — Sargunan Sellamuthu, Advanced
main has increased considerably, especially in cybersecurity, IoT, analytics, and integrated command systems. As noted, the cybersecurity market is growing at double-digit rates. Moreover, national-level programs such as the TASMU Smart Qatar initiative emphasize platform-based deployments (cyber, IoT, command centers) that require layered investment across hardware, software, and services.
Hamad International Airport (HIA) has been one of the most technologically advanced airports in this part of the world for some time now. It is the first airport in the region introducing C2/CT technology that allows many passengers to leave electronics in their bags, while maintaining the highest aviation security standards. This smart security concept depends not only on CT scanners but also on tightly managed access control for staff and secure areas, high-resolution video surveillance across terminals, and resilient network and storage platforms capable of handling large volumes of security data. Its progress might be described as centered on new checkpoint technologies and backend data infrastructure.
Ashok Warrier from Panduit underlines that technologies such as perimeter intrusion detection using fiber optic and hybrid systems, as well as AI-driven traffic management, are seeing strong adoption in airports, ports, and smart mobility initiatives. “From Panduit’s perspective, these technology trends represent tremendous opportunities. Our approach is to work closely with multiple stakeholders — especially end users — to understand their requirements and provide state-ofthe-art infrastructure solutions.”
Rail and port projects provide another clear window into how Qatar invests in integrated security. Large transport and maritime logistics projects in Qatar routinely bundle access control, IP video, critical network infrastructure, and perimeter security into single, integrated safety and security packages. Doha Metro is relying on an advanced system that has been relying on signaling, telecommunications, and security systems, passenger services, a fully integrated operational

From these words, one could say that the key term is integration, which was also proven in the rail and urban transport. Qatar Rail’s Doha Metro and Lusail Tram networks operate on a level of technical integration that far exceeds traditional transport systems in the region. These systems were designed from the outset as tightly integrated, IP-based transport networks, where signaling, telecommunications, security, passenger information, and fare collection are all centrally managed. Every train, tunnel, station, and depot is continuously linked through IP-based fiber networks, ensuring millisecond-level synchronization across hundreds of subsystems. Maintaining this level of operability requires 24/7 data availability, automated incident workflows, and cybersecurity-hardened infrastructure, underscoring why such an advanced access-control system is not an optional enhancement but an operational necessity in Qatar’s rail and tram environment. According to Thomas Deville, security today extends beyond physical barriers; it lies at the intersection of hardware, software, IoT connectivity, and data protection.
“Without a doubt, the Qatari market is undergoing a significant transition – from isolated, standalone solutions to fully integrated, controller-based high-security systems. The focus is no longer on video surveillance, access control, or intrusion detection as separate components, but on the seamless interconnection of these systems within a unified, easily managed platform,” he notes.
control center, and automatic fare collection, which inherently includes networked CCTV, access-controlled areas, and station communication systems tied into a central command room. In parallel, Qatar’s new Hamad Port, being one of the world’s largest greenfield ports, has an integrated solution featuring a video surveillance system, access control system, and IT communication network, all supervised by a dedicated security commandand-control center.
The North Field Expansion program, aimed at boosting QatarEnergy’s output by some 85% by 2030, stands out as the core industrial driver of safety and secu-
rity demand. Public project descriptions emphasize the unprecedented scale of onshore gas-processing trains, offshore platforms, and associated utilities being built around the North Field gas reserves. Such LNG complexes, by necessity, depend on automated and layered processsafety systems, fire and gas detection, explosion-proof and thermal video surveillance, industrial-grade access control for hazardous zones, and OT-secure network backbones that link field equipment to central control rooms.
One of the players in the oil and gas sector is IDtech, which has been designing and deploying tailored access control so-
lutions for major regional energy companies as well as several high-profile ministries. “Our strongest demand came from projects requiring modernization of existing systems without disrupting ongoing operations,” says Thomas Deville, adding that three key factors have driven the success of his company in Qatar: flexibility of their technology, high level of built-in cybersecurity protection, and long-term commitment.
Taken together, these projects highlight four verticals where activity is most intense. The energy and industrial vertical is anchored by the North Field program, which has been described as the world’s largest gas field, comprising over 14% of the global gas reserves. The expansion program is set to introduce new offshore wells and infrastructure, including wellhead platforms, pipelines, and onshore facilities, substantially increasing the field’s production capabilities. Such huge developments require resilient industrial access control, secure OT networks, hazard-rated CCTV, and SIL-rated fire and gas systems to meet both international and national safety norms.
The aviation vertical, centered on HIA, remains a heavy consumer of high-end checkpoint technology, perimeter security, and terminal safety systems. HIA’s adoption of CT-based C2 screening solutions and its investment in modernized CCTV storage explicitly point to continued demand for biometric and credentialbased access control, large-scale IP video



systems, high-availability network and storage infrastructure, and integrated fire/life-safety systems in airside and landside facilities. In collaboration with Airport Council International (ACI), the airport launched a Smart Data Hub initiative to enhance data-driven operations, interoperability, and analytics in airport operations. This is a clear signal that the security and data infrastructure is being treated as a strategic operational domain.
Adel Mrabet, Regional Sales Manager at Velasea, notes that Qatar has showcased the robustness and reliability of its security ecosystem. “Qatar has made remarkable progress in implementing enterprise-grade security infrastructure and is now recognized as one of the leading countries globally in physical security systems, spanning networks, VMS, surveillance cameras, access control, and more.”

Extreme weather conditions in Qatar ruthlessly eliminate anything less than industrial-grade. The market gravitates toward robust, longlifecycle solutions that can simultaneously feed continuous data streams into central command environments
Qatar is the regional leader in connectivity and telecommunications infrastructure. The IoT market size in Qatar grows at a rate of approximately 30% annually, expecting to reach USD 1.6 billion in 2026, with Qatar’s smart city initiatives, such as the Tasmu Smart Qatar program, being a major driver of this growth. The level of IoT component integration is about 40% of TASMU use cases. Smart urban development projects generate cross-sector demand for connected safety and security solutions. The entire system relies on networked access control, sensor-driven video surveillance, smart-building fire detection, and robust IP networks tying devices into city-level platforms.
Bipin Kumar, Regional Technical Sales Manager at Suprema, deems that the market is clearly moving toward unified, intelligent, and contactless ecosystems. Strong adaptation has already been visible in facial recognition and mobile credentials, cloud-based access control and SaaS models, AI and analytics integration, as well as cybersecure and interoperable access control systems. “End users in Qatar are prioritizing data privacy, system interoperability, and future-proof solutions that can integrate seamlessly with building management, HR, and visitor systems.”
Against this backdrop, the product categories that appear to gain the most traction are those that directly support high throughput, centralized control, and IoT-level connectivity.
Bipin Kumar points out that his company has been actively engaged in Qatar across multiple verticals through our trusted partners and system integrators, deploying their solutions in government, education, oil and gas, and real estate sectors. “Our biggest reference in Qatar is The Pearl Island (UDC), where more than 50,000 tenants rely on Suprema’s Access Control and mobile credential system.”
In aviation and public-facing transport hubs, the move to CT-based checkpoint screening at HIA shows how advanced access and identity management, combined

Qatar Civil Defense (QCD) has built one of the world’s most demanding compliance frameworks. Every fire and life-safety component must pass certification in accredited laboratories. Installation is restricted to licensed contractors. Ongoing inspection and maintenance cycles are written directly into the legal code – not as guidelines, but as enforceable requirements.
The result is that there are no shortcuts. This is a market where only toptier, fully documented, internationally compliant solutions survive. Due to the country’s digital-economy strategy and cybersecurity posture, there is a high demand for secure-by-design platforms, identity/access management, and data governance, which favors suppliers that can evidence compliance and secure cloud and hybrid architectures.
with analytics-enabled video, can deliver faster, smoother security with higher detection performance. High-capacity, scalable network and storage infrastructure is now a core part of security modernization, not an afterthought. The company’s core lineup in the country blends AI, multimodal biometrics, and rugged design: the FaceStation F2 combines face, fingerprint, card, and mobile authentication with powerful anti-spoofing; the BioStation 3 delivers fast, touchless access through advanced AI facial recognition; while the BEW3 brings durable, outdoor-ready fingerprint verification with IP67 and IK09 protection.
In transport corridors and ports, contract descriptions for the Doha Metro, Lusail LRT, and the New Port Project highlight integrated packages that combine video surveillance, access-control systems, and IT communication networks under a unified command-and-
control layer. This pattern favors IPbased video, standards-compliant access control, and carrier-grade network infrastructure that can support both safety-critical systems and operational services. In smart-city deployments, TASMU-related documentation and market analyses of Qatar’s smart cities & IoT infrastructure point to strong demand for IoT-ready CCTV, access, and fire-safety systems that can feed data into cloud and edge platforms. Panduit is leading the modernization of infrastructure in Qatar across various sectors, including government, transportation, security and defense, energy, healthcare, and education, says Ashok Warrier. “Our commitment focuses on enterprise cabling and data center solutions to ensure that critical digital and security systems are supported by reliable, scalable, and future-proof networks and infrastructures,” he notes.
When it comes to fire-detection and alarm systems, regulatory requirements play a decisive role in shaping what sells. Guidelines from the Qatar Civil Defense (QCD) emphasize that fire protection and life-safety system products must be listed, labelled, or approved in accordance with international codes and standards, and that equipment used in buildings must be tested and certified. As a result, addressable fire detection, intelligent control panels, and voice-evacuation systems are typically the default choice for major buildings, industrial plants, and infrastructure projects in Qatar.
This is also confirmed by James Morrison from Hochiki: “In environments where traditional infrastructure can be a challenge, solutions must be robust, reliable, and importantly offer minimal disruption.” His company’s most active verticals are healthcare, hospitality, and education, all sectors that demand not only compliance but long-term performance. However, there is another factor that should not be overlooked, he stresses, and that is graphical management that is simple to understand for the end user.
This is what it takes to compete in Qatar’s security and safety ecosystem: regulatory compliance as the baseline, seamless integration as the expectation, and IoT-native intelligence as the differentiator. The technologies that meet these conditions form the backbone of the country’s next-

“Qatar market is clearly moving toward unified, intelligent, and contactless ecosystems. Strong adaptation has already been visible in facial recognition and mobile credentials, cloudbased access control and SaaS models, AI and analytics integration, as well as cybersecure and interoperable access control systems” — Bipin Kumar, Suprema
generation critical infrastructure. Those who don’t simply don’t get in.
Sargunan Sellamuthu from Advanced, whose company has delivered over 40 fire alarm systems to retail stores across Doha malls over the past year, notes that their solutions are trusted for their scalability, reliability, and compliance with QCD requirements. “Axis AX, approved to UL 864 10th Edition, offers modular architecture, advanced causeand-effect programming, and integrated smoke control, making it ideal for complex environments. Its ability to support voice evacuation and fireman’s telephone systems ensures coordinated emergency response, which is critical for highrise and mixed-use projects.”
But what makes Qatar truly distinctive isn’t just the high bar; it’s the phi-
losophy behind it. Major infrastructure investments are built around a single design principle: integration over isolation. Signaling, communications, access control, video surveillance, emergency response, and fare collection – all of it flows through centralized OCCs. Forget siloed subsystems. The winners here are technologies that speak the common language of converged IP networks, share data across domains, and synchronize in real time across entire asset bases. Having in mind heavy investments in IoT, one might say that network hardware is only as valuable as its ability to plug into IoT and cloud platforms. Open APIs, interoperable protocols, analytics-ready telemetry, and robust cybersecurity posture are no longer “nice to have” features. They’re entry tickets.
Qatar’s shift into a highly connected, data-driven infrastructure era is rapidly transforming its security and safety ecosystem. According to some projections by Mordor Intelligence, the country’s IoT market alone is projected to grow over 24% year-on-year, reaching USD 3.94 billion by 2030. That growth is being propelled by national programs, which envision that security systems are not just standalone installations, but parts of a single sensorand data-driven ecosystem.
Adel Mrabet from Velasea stresses that the forefront of innovation is artificial intelligence, which is no longer just a concept, but a practical tool: “Qatari organizations stand to benefit immensely from AI by leveraging data from surveillance cameras, IoT sensors, and other systems to generate actionable insights and anticipate incidents before they occur.”
Indeed, the AI is emerging as an inevitable force. The AI market in the country is expected to reach USD 2.16 billion by 2031, with some estimates by 6wresearch indicating 18% growth year-onyear for the “AI as a Service” within the same timeframe.
Mrabet is encouraged by the growth of “Made in Qatar” solutions and local expertise. “The knowledge and innovation

being developed locally have the potential to serve not just Qatar, but the wider MENA region,” he said, noting that his company, Velasea, can enable local actors to expand and reach broader customer bases. For security and safety solution providers, the growth of AI means opportunities in analytics, predictive risk modelling, sensor-fusion platforms, and incident-response orchestration. Imagine video feeds, access logs, and fire-alarm data merged into real-time AI dashboards, enabling proactive rather than reactive security.
James Morrison from Hochiki praises Qatar’s progress towards smarter systems. “As the region moves further into smart city initiatives and green construction practices, demand will increase for systems that are both adaptive and transparent, capable of integrating with wider networks and enabling data-driven oversight.” He stresses that there is a strong potential in technologies that serve complex, multi-use sites, where detection systems must meet diverse regulatory requirements while remaining cost-effective and scalable.
Smart city investments are the connective tissue between the IoT/AI technology vectors and the physical infrastructure rollout. Rapid urbanization is the main driver behind the ever-growing smart infrastructure market. One of the brightest examples of the brick-and-mortar infrastructure meeting the cloud solutions
is probably Msheireb Downtown Doha. Namely, through the implementation of the IoT-based management system, they have managed to reduce energy consumption by 30%. This helps Qatar be not only at the forefront of energy production, but also on the side of energy conservation.
“Qatar’s security and digital transformation are creating strong demand for highgrowth, niche technologies, especially in smart cities and critical infrastructure. End users across government, transport, energy, and education are prioritizing reliability, regulatory compliance, and integrated security operations,” underlined Ashok Warrier from Panduit. He further explains that the priorities should be depicted as AI-driven accuracy with reduced false alarms, lifecycle support through
managed services, local presence for fast support, and unified security platforms that combine physical security, cybersecurity alerts, and operational intelligence. This means that over the next 5-10 years, the security and safety market in Qatar will most probably increasingly pivot around platforms rather than products. The future will be dominated by the systems that can integrate IoT devices, feed AI engines, all connected into smart-city command centers.
In such an environment, supplier strength will not be determined simply by hardware features, but by interoperability, scalability, data-management capabilities, and the ability to support lifecycle analytics. With major infrastructure projects (aviation, energy, transport, urban redevelopment) all scheduled or active, the demand window for integrated IoT/AI-enabled security and safety solutions is wide open.
For investors and solution-providers, the convergence of smart solutions in Qatar reveals multiple high-potential entry points. Network infrastructure and sensor platforms are high on that list. Highbandwidth and low-latency networks create demand for secure, resilient accesscontrol and connectivity systems. Under the national digital strategy, the Qatari ICT market is estimated at USD 6.25 billion and growing. The country aims to position itself as a leader in digital government with the aim of digitizing 90% of its services to citizens. Under such circumstances, security vendors with expertise in high-availability networking, ruggedized


“Qatar has made remarkable progress in implementing enterprise-grade security infrastructure and is now recognized as one of the leading countries globally in physical security systems — spanning networks, VMS, surveillance cameras, access control, and more.” — Adel Mrabet, Velasea
sensors, and unified systems position themselves strongly for both new builds and retrofit programs.
Sargunan Sellamuthu from Advanced notes that scalable systems will be essential to meet the demands of Qatar’s rapidly evolving built environment. “Innovation will focus on smart monitoring, cloudbased management, and false alarm reduction technologies to improve efficiency and minimize disruption.” As for his company, Sellamuthu notes that the greatest potential lies in integrated fire safety solutions that combine detection, smoke control, and voice evacuation, particularly for high-rise developments, healthcare facilities, and transport hubs.
Big data and AI-driven security services represent another promising layer for investors. The Qatari government is determined to start employing AI-powered tools to improve its services. The country’s
Ministry of Communications and Information Technology stressed they are ready to adopt tools such as predictive analytics, automation, and advanced data analysis in an effort to streamline operations.
This was also recognized by Bipin Kumar from Suprema. His prediction is that Qatar’s security market will continue expanding with key opportunities in several different areas, including smart city infrastructure, energy, cloud, education, and healthcare. All these sectors will need integration of AI-driven solutions, from the digital ID integration and predictive security to insight-driven management. “Innovation will be driven by AI-powered identity verification, IoT-based sensors, and data-centric security platforms. At Suprema, we are committed to supporting this evolution through continuous innovation and close collaboration with our regional partners,” he concluded.

Thomas Deville from IDtech adds that this presents a valuable opportunity to develop bespoke, long-term security solutions in collaboration with the Qatari stakeholders.
Indeed, localization, ecosystem development, and public-private partnership models are recognized as strategic priorities. According to the Qatar National Vision 2030, the country has been encouraging knowledge transfer, local manufacturing, and skills development.
For international players, this means early localization plans, partnerships, and training programs can become differentiators. Incentive programs, such as USD 1 billion Invest Qatar’s incentive fund for digital and technology investment, underscore that the government is prepared to support companies that align with national transformation goals.
Deville stressed this is a pivotal moment for Qatar to promote sustainability, resilience, and innovation across all layers of its security ecosystem. “In the longer term, this visibility positions Qatar to play an even greater strategic role in the Gulf region. To achieve this, the country must carefully balance its immediate economic recovery with the need to foster regional cooperation, invest in adaptable and advanced technologies, and modernize its security infrastructure.” n
Airport X-Ray Scanners

AI, CT, and connected screening ecosystems are redefining the security lane. With automated detection, modular architectures, predictive maintenance, and biometric-linked passenger journeys, airport X-ray scanners are evolving into intelligent platforms that reshape how airports manage risk, efficiency, and compliance
n By: Mirza Bahić mirza.bahic@asmideast.com
For years, the X-ray scanners at the checkpoint symbolized a compromise. It was a compromise between security and convenience, and between safety and speed. Passengers unpacked their belongings into plastic trays, queues moved through terminals, and operators stared at flat, two-dimensional silhouettes for hours on end. The process felt fixed and was shaped by limitations that appeared non-negotiable. That age-old compromise is now being rewritten thanks to a new generation of airport X-ray screening technologies.
Across the globe, airports are deploying a new generation of scanners built around 3D computed tomography (CT), deep-learning-based automatic threat recognition, and tightly connected smartairport ecosystems. The combined result is not merely gradual improvement but a shift in the very architecture of screening. What once required disassembly, slow belt movement, and focused operator attention can now be achieved with higher accuracy, less friction, and dramatically improved passenger flow.
Regulators, too, are reshaping this part of the security landscape, pushing standards toward higher detection performance while allowing new operational freedoms, such as leaving liquids and electronics inside the bag at airports equipped with certified CT technology. In parallel, regulatory evolution is accelerating the technological one.
To understand where airport screening is heading, we examine the perspectives of three industry manufacturers, Smiths Detection, Gilardoni, and Nuctech, through a unified thematic lens. Their experience, placed against the wider global context, reveals not only how far the sector has advanced, but the direction of the coming decade. At the heart of that evolution is a shift in who, or more precisely what, performs the first layer of screening.
First things first, the most significant change in airport screening is not visible to passengers. It lives inside the
software stack of modern scanners, where threat detection is increasingly performed by algorithms rather than by
regulators and airport stakeholders in order to keep pace with changing threats and test regimes.

Pilot programs are testing facial recognition and other biometric identifiers to create a continuous chain of custody

False alarms can be reduced by a factor of four to five in fully automated configurations
of typical threat shapes such as knives, guns, and similar objects, and stresses that these algorithms are continuously updated to keep up with changing forms and concealment methods.
Yet, the company is not tackling AI only in the context of new CT platforms. It is explicitly developing AI solutions compatible with existing conventional scanners, so that airports can upgrade detection capability without wholesale hardware replacement. To support operator training and maintain detection proficiency, Gilardoni integrates Threat Image Projection (TIP) software into its systems, allowing simulated threats to be inserted into live screening sessions for continuous competency assessment without disrupting operations.
Another company, Nuctech, describes a deep-learning-based AI layer running on what it calls its Intelligent Inspection Platform. Rather than using generic models, the company trains on a proprietary baggage image database that includes 3D CT data generated through simulation and through curated real-world samples. This
dual approach, which combines simulated threat scenarios with ethically sourced real-world data, allows Nuctech to expand its training datasets rapidly. At the same time, it preserves strict data protection standards.
This allows the algorithms to consider not only shape but also material properties derived from CT, such as density and effective atomic number, when identifying explosives, narcotics, and other contraband. Nuctech stresses that these models are validated through independent tests under ECAC and national civil aviation standards. It also operates a formal “Threat Response Cycle” which takes in new threat information and then pushes updated models into the installed base through secure software updates.
This flexible R&D framework enables the company to respond to emerging threats within weeks rather than months, ensuring airport security keeps pace with evolving risks.
Across these three perspectives, AI is clearly no longer an afterthought. It is becoming the first filter in the lane, clearing
the majority of baggage automatically and handing only a fraction of images to human operators for further scrutiny. The operator’s role is changing from continuous first-line screening to exception handling. But even the most advanced detection algorithms depend on the quality of the underlying X-ray data, which brings the focus back to CT architecture.
So, if AI is the brain, CT is the vision system. The way scanners acquire and reconstruct X-ray data has a direct impact on detection performance, false-alarm rates, and throughput, and here the industry is exploring more than one path. Smiths Detection continues to build on conventional rotating-gantry CT. Kappler points out that “rotating gantry CT systems have reached a high level of maturity, offering hundreds of views per rotation to achieve exceptional image resolution.” The rotating geometry, combined with anti-scatter grids, produces high-quality volumetric images that feed both explosives-detection algorithms and deep-learning models. At the checkpoint, this design underpins the HI-SCAN 6040 CTiX, which combines full 3D imaging with a belt speed of 0.2 meters per second.

Juergen Kappler, Portfolio Director of Aviation & Critical Infrastructure, Smiths Detection

Riccardo Bianchi, Product Manager of the Security Business Unit, Gilardoni
The graphical interface deliberately uses the same color scheme as the company’s 2D X-ray systems, easing the learning curve for operators.
At the same time, the company is not limiting itself to conventional CT. It has introduced the SDX 10060 XDi, a system that uses X-ray diffraction instead of tomographic reconstruction. This system has no rotating components. Instead, it analyzes diffraction signatures to identify materials based on their crystalline structure. In early deployments, XDi is positioned as a way to further reduce false alarms in fully automated configurations, especially when combined with CT in a system-of-systems approach. Early trial results show promising outcomes.
“False alarms can be reduced by a factor of four to five in fully automated configurations,” Kappler states. In the end, this should lower the need for manual bag checks and improve the overall lane throughput.
Gilardoni is also closely watching this architectural evolution. It recognizes that airports are pushing for higher throughput, lower maintenance, and more costeffective alternatives to rotating-gantry CT. Bianchi notes that non-rotating CT designs can simplify the mechanical structure and potentially reduce lifecycle costs, but is frank about the fact that static architectures still face challenges in representing objects with the realism and fidelity that rotating CT supports today. According to him, the company is “exploring innovative ways to overcome such technological limitations in order to fully
exploit the potential of non-rotating CT machines.”
For Nuctech, static CT is already a strategic choice rather than a future option. The company says it has “pioneered a non-rotating staticgantry CT architecture” that eliminates the heavy rotating assembly, reducing weight and footprint while improving reliability. The simplified mechanical structure significantly improves Mean Time Between Failures (MTBF), translating to higher system availability and lower maintenance costs over the equipment lifecycle.
Nuctech also claims that this architecture provides high-resolution 3D images with full 360-degree coverage and no blind spots, while enabling very high conveyor speeds. With XT2100HS, the company states that this design supports throughputs up to 1,800 bags per hour under standard assumptions for bag length and spacing. Static CT thus becomes not only an imaging choice but a maintenance and throughput strategy.
The industry is therefore not converging on a single architecture. Instead, it is using more powerful software to get the most out of both rotating and static hardware, and, in some cases, adding diffraction-based techniques on top. For airports, the choice will increasingly depend on their mix of performance targets, lifecycle costs, and space constraints.
Yet, all the imaging and AI sophistication in the world is irrelevant if a system cannot keep up with the passenger flow of a modern terminal. Throughput remains the metric that makes or breaks a deployment.
In hold baggage, Smiths Detection gives the classic benchmark: assume an average bag length of eighty centimeters, a gap between bags of twenty centim-
Future checkpoints could become fully automated lanes in which bags are screened and routed with minimal human involvement
eters, and a belt speed of half a meter per second. Under those conditions, the theoretical maximum is about 1,800 bags per hour.
Kappler notes that its SDX 10080 SCT platform is designed to allow even smaller gaps between bags than the standard twenty centimeters and that it performs calibration in the background, so there is no need to stop the belt for routine system checks. In practice, this means that the system comes close to the theoretical throughput ceiling in real-world baggage-handling environments. The SCT’s dynamic calibration capability runs seamlessly during operation, eliminating the traditional need for periodic conveyor stoppages and ensuring sustained performance at optimal throughput levels throughout operational hours.
For cabin baggage, the CTiX runs at 0.2 meters per second and, depending on tray length and spacing, can process on the order of 850 to 900 trays per hour. In the typical configuration, CTiX is integrated with an automated tray return system so that when its detection algorithms trigger an alarm, the tray in question is automatically diverted to a recheck position without interrupting the main flow.
On the other hand, Gilardoni relies on its dual-view systems, which often operate in smaller or mixed-technology airports. They are configured for belt speeds up to 0.3 meters per second in checkpoint roles and up to 0.5 meters per second in hold-baggage systems, where the limiting factor is usually baggage handling rather than operator capacity. Bianchi stresses that its workflow logic allows flagged baggage to move to secondary screening without stopping the lane, and that its algorithms are tuned to minimize false alarms, even at high throughput. Operational feedback from Gilardoni deployments highlights reduced false alarm rates and improved system uptime through scheduled and predictive maintenance as key performance improvements valued by security managers.
Nuctech’s XT2100HS, built on its static CT architecture, is also rated up to 1,800 bags per hour in hold-baggage scenarios. The company emphasizes that throughput is as much about process design as it is about belt physics. It describes a three-level, risk-based screening model where AI performs the first pass and automatically clears most bags, a smaller proportion of images is

Across the globe, airports are deploying a new generation of scanners built around 3D computed tomography, deep-learning-based automatic threat recognition, and tightly connected smart-airport ecosystems
routed to local or remote operators for detailed review, and only a very small fraction is sent to manual inspection. By structuring operations this way, Nuctech argues that the lane can sustain its mechanical throughput even under peak passenger loads. After 6 to 12 months of operational deployment, airport partners usually report significant reductions in false alarm rates and substantial increases in throughput during peak periods. They also highlight a notably improved operator experience, supported by clearer and manipulable 3D images that enable faster and more confident decision-making. Throughput is no longer determined solely by belt speed or gantry type. It is the outcome of how imaging, algorithms, automation, and staffing are orchestrated together. While airports now focus heavily on throughput and automation, another foundational aspect of screening systems
has reached a level of maturity and regulatory stability.
Although CT and AI are advancing rapidly, radiation safety is a domain where the fundamentals are stable and heavily regulated.
Kappler underlines that all aviation X-ray systems must comply with strict limits on external dose rate, and that independent radiation-safety officers measure equipment before it goes into operation. To keep leakage as low as possible, the company uses high-end solid-state detectors that require less internal X-ray dose to achieve image quality, along with multi-layer curtain systems and shielding. The inevitable leakage that remains “has been reduced to an absolute minimum,” Kappler notes.
Gilardoni leans on its experience in medical imaging, where dose management has long been critical. Bianchi highlights that the company relies on quality components and X-ray generation and detection to keep X-ray intensity at the minimum level compatible with image quality and certified detection performance. Crucially, Gilardoni’s scanners activate the X-ray beam only while luggage is physically present in the detection area. This beam-gating approach reduces overall radiation emission and optimizes energy consumption throughout operational hours. Bianchi also notes ongoing research into shielding materials and architectures and states that residual leakage is already “orders of magnitude below regulatory limits.”
Their competitor, Nuctech, refers to the ALARA principle, i.e., “As Low As Reasonably Achievable,” as the foundation of its approach. It describes how highsensitivity detectors allow good images to be formed at lower doses, and how multi-layer physical shielding combined with safety interlocks keeps radiation levels outside the device close to the natural background. All of its systems, it says, are tested by national radiationprotection authorities as part of the certification process.
It is evident now that modern scanners are conceived not as standalone boxes, but as nodes in a connected system of baggage handling, operations control, IoT monitoring, and analytics.
Juergen Kappler, Portfolio Director of Aviation & Critical Infrastructure at Smiths Detection, emphasizes that his company’s scanners are designed to integrate “seamlessly into smart airport ecosystems,” supporting open architecture and multiple integration options. Its forthcoming ELECTORA platform is described as an open-standards engine for extracting operational and maintenance insight from scanner data. It is intended to scale across fleets and feed advanced analytics, including predictive maintenance and long-term performance trends. Built on open technical standards and designed for scalability, ELECTORA should provide comprehensive reporting and monitoring capabilities with flexible data export options, enabling airports to contribute scanner telemetry to advanced analytics and realtime operational dashboards.
Riccardo Bianchi, Product Manager of the Security Business Unit at Gilardoni, says that this company presents its scanners as operational-technology components in IoT environments. Machines support real-time diagnostics and health monitoring. This means that data can be exported for analysis, and dynamic dashboards are used to supervise machines, track key performance indicators, and integrate with external monitoring tools.
The company also offers web-based remote control and monitoring dashboards for centralized oversight, and its systems can also be retrofitted with sensors for advanced analytics and predictive maintenance frameworks. The company’s Breva 2.0 automated tray return system adds its own data stream, exposing selfdiagnostics that can be used for performance tuning and predictive maintenance across dozens of lanes. Currently operating on approximately 80 lanes deployed worldwide, Breva 2.0 is fully customizable and can integrate with both Gilardoni and third-party scanners, providing advanced self-diagnostics that interface with airport IoT systems to enable comprehensive health and performance monitoring.
Finally, Nuctech describes its systems as “intelligent data nodes” that interface with baggage-handling systems, airport operations centers, and other infrastructure. The company’s systems support standard protocols such as DICOS (Digital Imaging and Communications in Security), facilitating seamless integration with airport Baggage Handling Systems (BHS) and Airport Operations Centers (AOC). Scan results can be used to instruct baggage-routing systems in real time, diverting bags that require further screening, while embedded IoT sensors feed predictivemaintenance platforms that seek to detect wear and anomalies before they result in failure. This shift from reactive repair to proactive prevention allows maintenance teams to schedule interventions during off-peak hours. As a result, it minimizes operational disruption while maximizing system availability.
The net effect is that scanners are no longer just detection devices - they are part of a live data fabric that airports can use to manage flow, maintenance, and risk.
For airport operators, the conclusion is that radiation is not the differentiator it once might have been. All credible systems operate within a narrow band of regulatory limits and are designed to do so over long lifecycles. The competition now is in how effectively that allowed dose is converted into image quality and detection performance. Yet, screening performance is no longer about standalone machines. Airports increasingly evaluate whether a system can evolve over time and not simply comply today.
With CT, AI, and regulatory standards all evolving, airports are increasingly wary of investing in equipment that cannot be upgraded. In line with this, all three manufacturers therefore stress modularity and long-term upgrade paths.
Smiths Detection’s Kappler gives concrete examples. The company’s first-generation hold-baggage CT systems were installed in 2013 and certified to ECAC EDS 3.0. As standards have progressed
to 3.1 and now 3.2, those systems have been upgraded via software. The company notes that EDS 3.2 compliance for the SDX 10080 SCT platform can be achieved through software-only changes, thanks to a CT design with sufficient energy resolution and number of views from the outset.
For cabin baggage, the HI-SCAN 6040 CTiX is built so that new EDS-CB algorithms and iCMORE detection modules can be loaded directly onto existing hardware. In effect, the scanner is a platform whose detection capabilities can be extended and sharpened over time. Kappler also points out that the SCT detector array is designed to allow the addition of more detectors in the future, opening the door to higher belt speeds, and that the platform is engineered to host X-ray diffraction modules if future ECAC or TSA standards require CT-XRD combinations. The SCT system also offers the flexibility to configure with or without an integrated Line-Scanner, which is a complementary imaging technology that enhances specific detection capabilities. This should allow airports to optimize for their operational requirements and budget constraints while maintaining a clear path to future capability upgrades.
On the other hand, Gilardoni focuses strongly on compatibility with existing equipment in the field. Its AI solutions are being developed to run on installed conventional X-ray scanners, preserving the airport’s investment in the mechanical platform. The company also designs integration architectures that can combine data from Gilardoni and third-party equipment, recognizing that many airports operate mixed fleets and will continue to do so while transitioning between generations of technology.
Yet, Nuctech’s approach to the modularity aspect has two strands. On the software side, it positions its systems as “software-defined,” meaning that new AI-based detection functions for emerging threats can be deployed via software updates rather than by swapping out machines. On the hardware side, it highlights field-replaceable modules for critical subsystems such as detector arrays and image processors, allowing targeted hardware upgrades where necessary while keeping the overall platform. The stated aim is to keep pace with evolving standards and capabilities without forcing airports into “rip and replace” cycles.

Throughput is no longer determined solely by belt speed or gantry type, and it is the outcome of how imaging, algorithms, automation, and staffing are orchestrated together
Modularity has thus moved from marketing slogan to procurement requirement. The question is no longer only whether a scanner can meet today’s standards, but whether its design and vendor roadmap make it likely to meet tomorrow’s.
As scanners become networked devices exposing images and system logs to external systems, they also become part of the airport’s cyber-attack surface. All three manufacturers address this head-on. Kappler describes a multi-layered security architecture in which data is transferred using encrypted protocols, stored behind strict access rights and authorization controls, and protected by regular vulnerability scanning and security testing. Smiths Detection applies operatingsystem hardening based on industrystandard CIS benchmarks, leverages
Security-Enhanced Linux (SELinux) for additional kernel-level protection, and deploys Host Intrusion Detection Systems (HIDS) to continuously monitor for suspicious activity.
At the device level, kiosk modes, disabled auto-start from external media, and strong password policies reduce the risk of local compromise. Automated vulnerability scans and patch management processes ensure that potential security risks are quickly identified and remediated. Customizable security policies then enforce rigorous access controls across the operational environment.
Other approaches are equally valid. According to Bianchi, Gilardoni’s systems follow data-protection-by-design principles. Scanners can send images to external storage over secure channels with cryptographic protection, and access to those images and related metadata is controlled by role-based access, segregation of duties, and password policies. For
systems utilizing removable media, Gilardoni implements OEM-managed secure data-erasure processes to ensure that no sensitive information remains postdisposal, addressing the full data lifecycle from creation to destruction.
Next, Nuctech explicitly references alignment with international data-protection regulations, including GDPR. It uses AES256 encryption at rest and in transit, enforces strict role-based access control with extensive audit logging, and supports configurations with network segmentation and image anonymization. The company emphasizes that clients retain full control over their data, positioning itself strictly as a technology provider and ensuring that airports maintain complete data sovereignty over all screening information collected by the systems. Nuctech also highlights remote-screening architectures in which operators review images in physically separate facilities, reducing the amount of personal data handled at the checkpoint itself.
This focus reflects a broader shift in the industry: security equipment is now treated as critical IT infrastructure as much as electromechanical machinery, and is assessed accordingly by airport IT and cyber teams.
No matter how sophisticated the technology is, it only reaches the airport floor if it passes regulatory certification. All three companies pay close attention to this. Juergen Kappler, Portfolio Director of Aviation & Critical Infrastructure at Smiths Detection, notes that his company’s products are certified by ECAC, TSA, ACSTL, and CAAC, among others. He stresses that the HI-SCAN 6040 CTiX was the first scanner certified for an algorithm that allows screening of liquids up to two liters in cabin baggage, and that its iCMORE automated prohibited-item detection solution was the first to receive APIDS Standard 1 approval at the national level. Riccardo Bianchi, Product Manager of the Security Business Unit at Gilardoni, mentions a range of certifications across Gilardoni’s conventional portfolio, including ECAC EDS-CB C1, ECAC LEDS, TSA, ENAC, and STAC. He frames certification as an ongoing effort rather than a one-off step, with continuous work to align products to current and emerging standards.
Another competitor, Nuctech, states that its systems have achieved approvals from ECAC, STAC in France, the UK Department for Transport, and CAAC in China, and that it participates in the development of international and national standards. In fact, the company sees itself as “a contributor to the definition of tomorrow’s test regimes rather than merely a respondent.” Beyond pursuing certifications, Nuctech has led or contributed to the development of numerous international and national standards, positioning itself not merely as a compliant vendor but as an active participant in shaping the future regulatory landscape of aviation security.
Given the evolving nature of standards, particularly in cabin-baggage CT levels and potential future CT-XRD combinations, this certification posture matters as much as the current approval list. As a result, Airports increasingly ask not only “is this certified now?” but “is this vendor clearly committed and technically able to keep the system certified as requirements change?”
Looking forward, the three manufacturers outline trend trajectories that, while distinct, strongly overlap in their direction. Kappler sees his company’s CTiX as the checkpoint hardware platform on which increasingly capable software will move toward fully automated first-level screening. By combining ECAC EDS-CB algorithms for explosives with APIDS algorithms for prohibited items, and by pushing both toward higher standards such as C4-limited and APIDS 2 or 3, the company expects to reduce the share of images requiring human review to a very small minority. It has already demonstrated proof-ofconcept checkpoints where trays are linked to passengers via biometric capture, such as facial recognition or biometric boarding passes. This foreshadows a future in which passenger identity and baggage are associated throughout the screening process for enhanced security and seamless tracking. For future regulatory requirements, such as potential ECAC EDS 4 or TSA 9.0 standards that may demand CT-XRD fusion, Smiths’ Detection platform strategy enables integra-
tion of X-ray diffraction modules into existing CT scanners rather than requiring complete system replacement.
For Gilardoni, Bianchi articulates a strategy defined by modular innovation. Current scanners are deliberately designed so that they can host future automateddetection modules and biometric components, rather than requiring replacement. At the same time, cybersecurity remains a cornerstone of this evolution, with ongoing investments in secure software development, cryptographic protocols, and compliance with evolving global cyber standards as systems become increasingly connected and data-rich. Finally, Nuctech describes a long-term goal of creating a seamless, intelligent, and integrated security process. The company is actively exploring multi-technology fusion approaches, such as combining CT imaging with trace-detection techniques to improve chemical specificity and precisely identify suspicious substances that CT alone may not characterize properly. It is also exploring biometric-baggage linkage that associates passengers with their luggage throughout the security journey. Pilot programs are testing facial recognition and other biometric identifiers to
create a continuous chain of custody. In this model, each bag is digitally linked to its owner from check-in through final loading, which enables enhanced security tracking and differentiated screening based on passenger risk profiles. In this vision, future checkpoints could become fully automated lanes in which bags are screened and routed with minimal human involvement, and security officers shift into remote supervisory roles, intervening mainly on complex or exceptional cases. This transformation would leverage automation and increasingly powerful AI to achieve operator-free screening lanes, redefining security officers as high-level remote supervisors and managers rather than frontline operators.
All three vendors therefore converge on a picture of the checkpoint as a data-driven, largely automated decision engine that is deeply integrated with passenger identity and airport operations, rather than as an isolated X-ray tunnel with a human operator at the center.
The combined perspectives of Smiths Detection, Gilardoni, and Nuctech show an industry that is changing at multiple levels at once. CT imaging is being refined and diversified through both rotating and static architectures. AI-driven detection is moving into the core of the screening workflow, and throughput is increasingly becoming the result of coordinated system design rather than raw belt speed. For security professionals, airport X-ray scanners can no longer be evaluated as standalone machines bought for a fixed period and then replaced. They are now platforms, embedded in a wider system of systems, whose value is determined as much by their upgrade path, their integration interfaces, and the vendor’s regulatory posture as by the performance of the hardware at the moment of purchase. The old compromise between security and convenience is not solved overnight, and legacy fleets will remain in operation for years. But the direction is clear: baggage screening is becoming smarter, more connected, and more automated. The strategic question for airports is no longer whether to adopt this new generation of technology, but how quickly, in what configuration, and with which partners they will move into that future. n

Inside the Paradigm Shift
As the Middle East undergoes rapid urban expansion, its security needs are evolving just as fast. Distributors are no longer simple intermediaries but strategic technology orchestrators shaping integrated, compliant, and resilient systems. Their role now spans design, enablement, and lifecycle support across diverse environments. This feature explores how industry leaders are redefining distribution to meet the region’s ambitious development vision
n By: Fatima Al Husseiny editorial@asmideast.com
The Middle East is experiencing one of the fastest rates of urban growth in the world, and driving demand for advanced security technologies. As cities expand and infrastructure projects multiply, governments and private enterprises are placing greater emphasis on building systems that combine hardware, software, and analytics.
According to insights from Construction Business News Middle East (CBNME) and ACI Asia-Pacific & Middle East, this transformation is not simply about adopting global technologies. Instead, it calls for localized, adaptable solutions, ones that fit each nation’s local regulations and conditions. Consequently, distributors across the region are evolving into technology orchestrators, designing and delivering endto-end systems that promote resilience and maintain regulatory compliance.
The region’s distribution landscape faces numerous obstacles: fragmented logistics networks, inconsistent regulatory environments, and infrastructure bottlenecks. Adding to these difficulties are high transport costs, geopolitical uncer-
tainties, and outdated delivery models. To overcome these challenges, success is grounded on the basis of innovation, regional insight, and supply chain agility.
Industry pioneers such as Loubna Tabbara, Marketing and Sales Director from Tabbara Electronics, and Shaji Abdul Kadar, Chief Operating Officer, ScreenCheck Middle East and Executive Board Member, Centena Group, exemplify this forward-thinking approach. Through their insights, they demonstrate how distributors can transcend traditional roles, becoming vital enablers of the region’s evolving security landscape and shaping the future of technology distribution in one of the world’s most dynamic markets.
Distributing security and safety equipment across the Middle East presents a unique blend of opportunities and challenges shaped by the region’s rapid development, environmental extremes, and complex regulatory landscape. Massive infrastructure projects such as NEOM underscore the growing demand for advanced, reliable, and intelligent security
systems. Yet, this progress unfolds in environments defined by harsh heat conditions that often compromise the performance of traditional security tools.
Beyond environmental hurdles, the absence of standardized regulations across Middle Eastern countries complicates operations for distributors and slows the adoption of modern biometric and AI-driven solutions. This fragmented regulatory landscape means companies must navigate a maze of import laws, licensing requirements, and certification standards.
Both Tabbara and Abdul Kadar exemplify how turning these challenges into strengths can become a strategic differentiator. As Tabbara explains, “While regional diversification introduces different import regulations, licensing requirements, and certification frameworks across countries, our strong channel partner network turns this complexity into a strategic advantage. With established partners in every major Middle Eastern market, Tabbara Electronics is able to navigate local compliance efficiently, anticipate regulatory changes, and maintain seamless delivery and support.”
Abdul Kadar emphasized the region’s major challenges, “ScreenCheck distributes

While urban centers such as Dubai benefit from mature supply chains and efficient logistics, remote sites face delivery delays, higher costs, and difficulties in maintaining consistent quality control. The diversity of working environments across the region means that a one-size-fits-all approach rarely works

our products in more than 35 countries across the Middle East and Africa, as we operate through a wide network of 400-plus partners across the GCC and African region. We noticed that the biggest challenges are related to regulatory approvals, integration & interoperability, supply chain management, cybersecurity assurance, skill enablement, and financial barriers in certain African markets.”
Logistical and workforce challenges further complicate distribution. While urban centers such as Dubai benefit from mature supply chains and efficient logistics, remote sites face delivery delays, higher costs, and difficulties in maintaining consistent quality control. The diversity of working environments across the region means that a one-size-fits-all approach rarely works. As highlighted by ACI AsiaPacific & Middle East, security technologies must be tailored to local operational realities. Moreover, the transient nature of labor poses an additional hurdle: workforce training.
Abdul Kadar puts an emphasis on structure and process, as he believes in “a compliance-first mindset, designing every project around local and international regulations, data privacy mandates, and site-specific safety requirements, while ensuring system reliability at scale with high uptime, durability, and proven environmental resilience. Our solutions are built for interoperability and openness, supporting open architectures that integrate seamlessly across VMS, ACS, fire, and building management systems, and we provide
Amid these challenges, building trust through quality emerges as the defining principle for success in the Middle Eastern security equipment market. In an industry where reliability can mean the difference between safety and vulnerability, trust is built on uncompromising quality. Every component, system, and partnership must meet the highest standards of performance, compliance, and endurance. As industry leaders emphasize, credibility is earned through consistent excellence. As a matter of fact, Abdul Kadar adds, “Additionally, building trust with new regional partners often requires assurance of reliability and authenticity.”
Equally important to Tabbara, she states that, “Trust, quality, and resilience are non-negotiable. We focus on distributing technologies that have been fieldtested, certified, and proven in mission-critical environments, whether for law enforcement, public safety, or critical infrastructure. Quality assurance begins with brand selection. All our partners, including Motorola Solutions, Avigilon, Pelco, Silent Sentinel, and Barrett Communications, are global leaders recognized for reliability and compliance with international standards. I often say that Motorola’s commitment to quality is quite literally out of this world. That legacy of engineering excellence continues to define the standards we uphold in every solution we deliver.”
lifecycle support that spans the full project journey, from design and commissioning to post-installation maintenance.
To ensure quality and reliability, we work through authorized distribution only, partnering exclusively with the world’s leading manufacturers in their respective fields, and rely on factory-trained technical teams and ISO-aligned operational processes. Every system undergoes predeployment testing and proof-of-concept (PoC) validation in our in-house lab, is deployed with standardized hardening baselines to guarantee secure configurations
and version control, and is backed by tiered SLAs, warranty, and RMA support with structured escalation and spare-part strategies. Ultimately, distributing security and safety equipment in the Middle East demands more than supply; it requires deep regional understanding, technological adaptability, and an unwavering commitment to quality. Companies that can integrate compliance, reliability, and innovation are the ones best positioned to build lasting trust and contribute meaningfully to the region’s ambitious development vision.”


In an industry defined by rapid innovation and technological convergence, selecting the right brands has evolved into both an art and a science. It is no longer about merely expanding product portfolios; it’s about curating a cohesive ecosystem where each solution complements the next. The modern security landscape demands technologies that not only address current operational needs but also anticipate emerging challenges, ensuring longterm scalability and resilience. Achieving this requires a strategic balance between innovation, interoperability, and compliance, allowing distributors to align with partners who share a unified vision for integrated, intelligent, and future-ready security systems.
For Tabbara, this translates into a meticulous and purpose-driven approach to partner selection. As she explains, “we select our partners based on technological innovation, ecosystem compatibility, and long-term reliability. We look for brands that complement our existing portfolio and strengthen our end-to-end security offering.”
Abdul Kadar expands on this perspective from a technology-driven approach, underscoring how strategic partner-
ships fuel innovation across security domains.
Ultimately, both Tabbara and Abdul Kadar exemplify how success in today’s security and safety sector depends on more than technological acquisition; it hinges on strategic orchestration. By fostering ecosystems where hardware, software, and intelligence converge, they are enabling organizations to achieve holistic, secure, and scalable operations capable of meeting the Middle East’s evolving security demands.
In today’s dynamic security ecosystem, customers have evolved from being mere end users to becoming co-creators of innovation. Across the Middle East, as industries undergo rapid digital transformation and develop smart infrastructure, customer feedback has become the heartbeat of strategic decision-making. This evolution empowers companies to move beyond reactive support models and intelligent ecosystems that address real-world challenges in real time.
As Tabbara elaborates, “customer feedback directly shapes how we evolve. The region’s growing focus on interoperability, AI analytics, and real-time situational awareness has pushed us to expand beyond traditional hardware and into integrated software-driven solutions. For example, many of our public safety and energy sector clients sought unified control rooms that consolidate communications, video, and sensor data. This led us to align more closely with Motorola Solutions’ Command-
The modern security landscape demands technologies that not only address current operational needs but also anticipate emerging challenges, ensuring long-term scalability and resilience. Achieving this requires a strategic balance between innovation, interoperability, and compliance
Central suite, enabling us to provide endto-end situational intelligence that connects field units with command centers.”
Abdul Kadar adds a complementary dimension from the healthcare and enterprise sectors, illustrating how customer collaboration drives market innovation. Customer feedback and vertical-specific needs are the foundation of how ScreenCheck shapes its portfolio. As security solutions evolve from standalone systems to integrated digital ecosystems, end-users increasingly expect frictionless operations, mobile convenience, and centralized data visibility. For example, a major hospital in the UAE required seamless identity management for patients, visitors, and staff. ScreenCheck integrated Suprema biometric access, TiSO turnstiles, EVtrack, and AxxonSoft analytics with a central ID issuance system (Evolis/Entrust) linked to their information system.
Demand in the Middle East is shifting from hardware procurement toward solution-driven ecosystems. “We see increasing demand for AI-enabled video analytics, secure LTE and 5G communication solutions, and integrated command platforms. Governments and private sectors are investing in smart city infrastructure, critical asset monitoring, and border protection areas that depend on seamless coordination between multiple technologies. In parallel, cyber-resilience and data protection are becoming integral to physical security procurement, meaning solutions must now combine encryption, redundancy, and secure connectivity by design,” Tabbara elaborated.
Abdul Kadar adds, “The Middle East market continues to be driven by infrastructure development, smart city projects, and compliance-oriented digital transformation.” He notes that they are seeing consistent demand for AI-powered video surveillance with advanced analytics and facial recognition. He also points to growing interest in biometric and mobile credentialbased access control, with multi-factor authentication increasingly integrated into broader security ecosystems. Cloud-based and hybrid access systems remain a priority for distributed enterprises. In addition, data-center security solutions that merge physical and logical access control, along with smart cabinets featuring built-in cooling, are becoming an important part of the regional requirements.

These reflect a broader shift from hardware-centric procurement to solution-driven ecosystems that combine analytics, automation, and data governance.
In the Middle East, demand is increasingly driven by AI-powered video analytics, next-generation biometric and mobile access control, cloud and hybrid access platforms for distributed enterprises, and advanced data-center security that unifies physical and logical protections with intelligent, temperature-controlled infrastructure.
As the Middle East moves into a new era of intelligent infrastructure and digital transformation, its physical security landscape is undergoing significant change. Over the next three to five years, technological convergence will shift security from reactive systems to predictive, integrated ecosystems.
Technologies such as predictive analytics, edge intelligence, cloud-hybrid models, and 5G are redefining how organizations design and manage security frameworks. At the same time, priorities like energy efficiency, local manufacturing, and technology sovereignty are shaping procurement as governments emphasize sustainability and self-reliance.
Looking ahead, both Loubna and Abdul Kadar envision a converging future
In today’s security industry, success is no longer measured by the range of products offered. Distributors have evolved from being simple intermediaries into strategic enablers, trusted partners who empower clients, integrators, and end users with the tools, knowledge, and expertise needed to ensure excellence across every phase of a project. From pre-sales consultation and system design to post-deployment optimization and lifecycle management, the focus has shifted from transactional value to long-term empowerment and partnership.
Tabbara explains, “Beyond strategic distribution, we offer complete technical enablement through system design, integration, configuration, certified training, and after-sales support. Our in-house Technical Service Center in Dubai tests, configures, and optimizes equipment before delivery, ensuring every system is fully interoperable and deployment-ready.”
This approach redefines distribution as an end-to-end support ecosystem. By combining technical expertise with proactive collaboration, Tabbara Electronics ensures that every deployment delivers reliability, interoperability, and market differentiation. Its Technical Service Center serves as a bridge between manufacturers and integrators, transforming complex technologies into ready-to-deploy, field-proven solutions while fostering stronger brand alignment and regional impact.
Abdul Kadar’s model reflects a similar understanding, “built on a lifecycle-oriented approach that embeds enablement at every stage of engagement. Our approach focuses on enablement and partnership, not just distribution. We provide: consultative pre-sales design and tender support (drawings, specs, and BoQs), integration engineering and SDK-level customization, demo labs and proof-of-concept testing environments, on-site testing and commissioning, certified technical training programs for integrators and partners, remote monitoring and SLA-backed after-sales support, and lifecycle management, firmware governance, and security patch coordination. This 360° engagement ensures that every project is delivered with technical precision, backed by ongoing enablement and support.”
Together, these approaches redefine the meaning of “distribution” in the modern security ecosystem. No longer confined to supply and delivery, distribution has become a 360° partnership model that spans design, integration, and continuous enablement. By aligning technical excellence with collaborative support, leaders like Loubna and Abdul Kadar are shaping a future where value is measured not by the products sold but by the ecosystems built, and the trust sustained, long after deployment.

grounded in integration, intelligence, and sustainability, one where Middle Eastern distributors and manufacturers play an active role in co-developing next-generation technologies.
Loubna describes this transformation with a forward-looking perspective: “The future of security in the Middle East will be defined by integration, intelligence, and autonomy.”
Her vision highlights a paradigm shift where security becomes anticipatory, driven by interconnected systems that merge communication, data, and intelligence. By aligning technology with national sustainability goals and digital agendas, organizations like Tabbara Electronics are preparing to play a pivotal role in the region’s journey toward autonomous, self-reliant, and future-ready security ecosystems.
Abdul Kadar complements this outlook with a focus on AI-driven decentralization and cyber-secure convergence. “The security landscape is rapidly evolving, driven
by technological advancements and the growing need for intelligent, interconnected solutions. Edge AI and embedded analytics are enabling faster, decentralized decision-making, while hybrid and cloud-native architectures strike a balance between flexibility and data sovereignty. Mobile and digital credentialing are becoming the norm for unified access, and cyber-secure physical systems are increasingly built on zero-trust principles. At the same time, interconnected ecosystems are linking ACS, VMS, BMS, and IoT platforms through open protocols, supported by computer vision and behavioral analytics that power predictive security. Automation and robotics are transforming traditional manpower-based models, and sustainability and energy efficiency are shaping design and procurement decisions. ScreenCheck remains dedicated to investing in these transformative technologies, ensuring our partners and clients stay future-ready in an everevolving security environment.”
In the Middle East, demand is increasingly driven by AI-powered video analytics, next-generation biometric and mobile access control, cloud and hybrid access platforms for distributed enterprises, and advanced datacenter security that unifies physical and logical protections with intelligent, temperaturecontrolled infrastructure
The Middle East’s rapid urban growth and digital transformation are reshaping the role of security distributors from product suppliers into strategic partners and ecosystem builders. As Loubna Tabbara and Shaji Abdul Kadar show, winning in this market means more than moving boxes; it requires deep regional insight, strict compliance, robust logistics, and a relentless focus on quality and trust. Distributors now curate interoperable portfolios, blend physical and cyber security, listen closely to customer needs, and provide end-toend value: design, integration, training, and lifecycle support. Looking ahead, demand will increasingly center on AI, edge intelligence, cloud and hybrid architectures, and sustainable, locally relevant solutions. Those distributors who invest in enablement, openness, and co-innovation will not only support the region’s megaprojects and smart cities, but they will also help define the next generation of security technologies built in and for the Middle East. n
Historically, students and staff needed a mix of tools to navigate campus life: physical keys, RFID cards, passwords and PINs, and even cash. Today, expectations have changed; they want one credential—ideally on the smartphone they already carry—to do it all. That’s why many institutions are now looking beyond isolated systems toward unified access: a model where a single credential (physical or mobile) can be used everywhere on campus
n By: ELATEC Group middle-east-info@elatec.com
Alongside their educational mission, universities and schools carry a second responsibility: protecting people, spaces, and data across sprawling, multibuilding campuses. User identification and access control are fundamental to campus security, safety, and compliance with privacy regulations. Managing access to classrooms, dorms, labs, lockers, printers, and cafeterias for thousands of users is a daily challenge—one that traditional ID cards and passwords are no longer equipped to handle.
In a recent implementation, more than 150 European educational institutions transitioned to mobile-ready, integrated access systems built around universal RFID reader technology. This example offers a blueprint for how campuses everywhere can modernize authentication without sacrificing flexibility or control.
Traditionally, physical and digital access systems have operated in silos. A student might use a plastic ID card to enter a building, a physical key to unlock a storage space, a password or PIN to log into campus systems, and cash to make a vending machine or canteen purchase. This frag-

mented approach leads to inefficiencies and security vulnerabilities. It also creates friction for users who must juggle multiple credentials, as well as for administrators responsible for managing and maintaining disparate systems.
At the same time, universities must respond to the rapid rise of mobile credentialing. Students increasingly expect the convenience of using their smartphones to access everything on campus, just as they already do for payments, transit, and entertainment. Digital credentials offer clear advantages: they’re more convenient for users, easier to manage at scale, and reduce the cost and environmental impact of plastic cards. To meet evolving expectations without
disrupting daily operations, institutions need a way to support both digital and physical credentials during the transition. That means finding flexible solutions that can bridge old and new, creating a path toward modernization without sacrificing continuity or control.
As both security expectations and regulatory pressures rise, universities need to rethink how they manage identification and access: not just as a series of isolated tools, but as part of a strategic, campus-wide infrastructure. The vision behind unified access is simple:

a single credential—physical or mobile— that works everywhere on campus. This approach not only simplifies life for end users but also enables a more efficient, centralized model for administrators and IT. One system, one database, and one set of hardware can now manage access to everything from exterior doors to multifunction printers.
Unified access isn’t just a convenience upgrade; it’s a strategic modernization of campus infrastructure. It creates a more agile, scalable environment that can adapt to changing technologies and user needs. Critically, it reduces operational overhead while enhancing the experience of everyone who lives, learns, or works on campus.
A multi-campus access modernization effort in Central Europe offers a real-world example of how universities and schools can streamline campus infrastructure using flexible, mobile-ready technologies. The project began as a pilot initiative to support mobile credentials alongside traditional ID cards across a handful of campuses. It has since grown into a broad deployment, now used at more than 150 educational institutions.
The initiative focused on replacing fragmented legacy systems with a unified

platform for access and credential management. A cloud-based access control solution, provided by Czech systems integrator Etugate, enables centralized control of building entry, lockers, printers, and payment systems. Mobile provisioning is powered by LEGIC Connect through the AliveApp, offering secure mobile credential issuance through smartphones or digital wallets. Students and staff can use their smartphones as access badges via NFC, BLE, or digital wallet integration (Apple Wallet and Google Wallet).
To enable broad compatibility and ease of deployment, the project relied heavily on universal reader technology provided by ELATEC. One key reason: ELATEC’s platform-agnostic architecture supports a wide range of access technologies, making it ideal for complex, mixed environments like university campuses. At many participating institutions, the existing infrastructure varied significantly, not just in the types of ID cards or mobile credentials in use, but also in the protocols that determine how access devices like readers and controllers communicate and exchange information. These systems often weren’t designed to work together, making it difficult to roll out new capabilities without disrupting what was already in place. To modernize successfully, universities needed a way to bridge across legacy and modern systems, supporting new use cases while preserving compatibility with existing infrastructure. Universal readers from ELATEC provided the technical foundation to unify these disparate systems. Supporting over 60 transponder technologies, 99 physical and digital credential standards, and multiple communication protocols (including legacy protocols like Wiegand and modern, secure protocols like OSDP), the readers ensured that both mobile and physical credentials could be used interchangeably across a range of campus applications. Their versatility allowed Etugate to standardize hardware across access points, from doors and turnstiles to printers, lockers, and canteen systems, without the need for custom development or system overhauls.
Key devices included the TWN4 Slim, a micro-sized reader ideal for tight spaces like printers and lockers, and the Secustos SQ80, a sleek, IP65-rated wall reader built for more demanding physical access points. Both models supported BLE and NFC, enabling mobile credentials through apps or digital wallets while maintaining backward compatibility with existing cardbased systems.
The result was a smooth transition path to mobile-first access, allowing institutions to modernize at their own pace while continuing to support current users and infrastructure. Remote configuration and firmware update capabilities simplified rollout and scaling across multiple campuses, while centralized credential management reduced administrative workload for IT teams. The case illustrates how universal readers can serve as the connective tissue in a flexible, future-ready campus access system.
As universities work to modernize their infrastructure for a mobile-native generation, unified access systems built on flexible, future-ready hardware offer a practical and forward-looking path. Universal readers play a key role in this transition. By supporting a broad range of credential types and communication protocols, they enable institutions to consolidate systems, simplify credential management, and scale access across campus applications without starting over. For students and staff, the result is a smoother, more intuitive campus experience. For IT teams, it’s easier maintenance and greater control.
The European multi-campus project demonstrates how this vision becomes reality. With universal reader technology as the backbone, universities can modernize step by step while maintaining continuity. And the lesson extends far beyond this case: with the right foundation, any institution can create an access environment that is secure and efficient today—and ready for the next generation. n
TRASSIR delivered a unified, AI-powered security platform that transformed surveillance at the Misstanbul Evleri residential complex. By integrating cameras, access points, and analytics into a single ecosystem, the solution eliminated blind spots, reduced operator workload, and enabled faster, more accurate incident response. The community can now scale effortlessly as new devices are added, ensuring long-term safety, efficiency, and peace of mind for residents
n By: Irina Ivanova, Content Manager, TRASSIR welcome@trassir.com
Security has become a defining factor in modern residential life. As developments grow into multi-building complexes with hundreds or even thousands of apartments, ensuring safety, smooth operations, and resident comfort becomes a complex challenge. Separate camera systems, disconnected monitoring rooms, and expanding perimeters can create blind spots, delayed responses, and inefficiencies. Even when unnoticed, residents can feel these gaps — in slower entry procedures, unclear access rules, or delayed reaction to unusual events.
For property managers and security teams, the issue is rarely the lack of technology — it’s the lack of integration. Different systems from multiple vendors often fail to communicate, forcing operators to juggle between screens and interfaces, which increases workload and the risk of missed incidents.

To overcome these challenges, forwardthinking residential communities are adopting intelligent video management platforms that bring all surveillance, access control, and analytics into a single environment. Such systems provide a real-time, comprehensive view of the entire property — from
lobbies and parking areas to playgrounds and perimeters — allowing operators to see, understand, and act quickly. AI-driven analytics automatically detect unusual movements, unauthorized access, or safety hazards, helping security teams respond instantly. Integrated access control ensures that only residents and approved visitors can enter sensitive zones such as gyms, pools, or

maintenance areas. Mobile tools allow supervisors to stay in control even when away from the monitoring center. Flexibility is key for growing estates. Modern systems scale effortlessly — from a few cameras to thousands — and integrate with most existing hardware, allowing developers to expand without replacing their entire infrastructure. This protects earlier investments while ensuring that the community remains ready for the future. Operators benefit from intuitive interfaces that simplify daily tasks: adjusting
image quality, masking private areas, and organizing multiple camera feeds on one screen. Built-in tools for user management, system monitoring, and video archiving turn security operations into a streamlined, proactive process rather than a reactive one.
The Misstanbul Evleri complex in Istanbul — home to nearly a thousand apartments

and extensive shared facilities — faced the challenges familiar to many large communities: cameras from multiple manufacturers, separate monitoring stations, and a growing perimeter that was increasingly difficult to oversee.
Working with a local technology partner, the management team implemented an AI-enabled video management platform developed by TRASSIR. The solution unified all surveillance feeds and access points into a single, cohesive system. Security personnel now monitor the entire 101,000 m² property from one interface, supported by intelligent analytics that detect incidents, manage entry points, and maintain situational awareness across both public and private areas.
The results were immediate and measurable. The team gained seamless monitoring across previously incompatible systems, enabling faster and more accurate incident response. The workload was reduced, resulting in fewer operational errors. Expansion also became significantly simpler as new cameras and devices were added.
Residents gained a stronger sense of safety and trust, while security teams achieved greater efficiency and control. Misstanbul Evleri now stands as an example of how technology can transform a residential complex into a connected, intelligent community.
Modern residential security is no longer just about installing cameras — it’s about creating a network that sees, understands, and acts. Integrated, AIpowered security platforms transform fragmented systems into unified ecosystems that deliver actionable insights, empower operators, and enhance residents’ peace of mind.
For developers and property managers, such solutions mean scalable, futureready communities where safety, efficiency, and comfort go hand in hand. n
THE VISION 2040
Aligned with Oman Vision 2040, IDtech is helping the Sultanate build a modern and resilient security infrastructure. Through advanced access control and intelligent visitor management, the company is enabling safer government environments and supporting the country’s wider digital transformation
n By: Thomas Deville, General Manager, Middle East & Africa, IDtech tdeville@idtech.eu
Oman’s commitment to sustainable growth and innovation under Vision 2040 has placed security and infrastructure modernization high on the national agenda. Within this context, IDtech has played a key role by delivering an advanced access control and visitor management system for the new Ministry of Culture, Sports, and Youth compound in Muscat. The project, which includes four buildings – offices, archives, and administrative areas – marks a milestone in the protection of critical government facilities and the digital transformation of public institutions.
At the core of this success lies a strong partnership model. Working closely with its Omani partner MFGB, and with TBS as its technology partner, IDtech combined local expertise with European innovation. MFGB’s in-depth knowledge of the local market and regulations ensured efficient deployment and long-term support. At the same time, TBS provided state-of-the-art biometric technology that enhanced both security and convenience. Together, these collaborations demonstrate IDtech’s belief that sustainable success comes from trusted partnerships and shared responsibility. The new system integrates several key security layers: access control, biometric

IDtech participated for the second consecutive year at OFSEC, alongside its strategic technology partners TBS and STid. Last year’s participation generated strong interest and excellent feedback, which has since been transformed into tangible deployments such as the Ministry’s project
identification, visitor management via QR codes, and vehicle control through Automatic Number Plate Recognition (ANPR). Managed from a centralized platform, the solution provides real-time visibility and
easy administration for security teams. The platform simplifies operations while maintaining a high level of protection, allowing staff and visitors to move seamlessly within a secure environment.

User experience was a central priority. Employees benefit from fast, reliable biometric access, while visitors can pre-register online and receive digital QR codes, reducing waiting times and improving flow management. All access data is securely encrypted and stored on-premises to meet Oman’s data sovereignty requirements, ensuring full compliance and peace of mind. The system’s analytics tools also help the Ministry optimize operations, providing insights that support proactive security management.
Beyond its technical success, the project represents the beginning of a long-term strategic partnership with the Ministry. In October, two senior representatives from the Ministry visited IDtech’s headquarters in Belgium to explore its latest innovations and discuss future cooperation. These exchanges opened new perspectives for securing cultural institutions, museums, and stadiums across the Sultanate — further aligning with Oman’s national vision for cultural preservation and youth development. To reaffirm its ongoing commitment to the country, IDtech has participated for the second consecutive year at OFSEC, alongside its strategic technology partners

TBS and STid, and its local partners MFGB and Seeracom. Last year’s participation generated strong interest and excellent feedback, which has since been transformed into tangible deployments such as the Ministry’s project. Returning to OFSEC allowed IDtech to showcase real-world results and strengthen the growing partner ecosystem dedicated to protecting Oman’s most critical infrastructure.
Every project IDtech undertakes in Oman is designed to contribute to Vision 2040 — fostering knowledge transfer,
promoting local expertise, and supporting digital transformation. Through advanced, integrated security systems, the company helps institutions achieve both operational efficiency and resilience in an evolving landscape. The Ministry’s project illustrates this approach: a secure, userfriendly, and future-ready environment built on collaboration, innovation, and trust. As we look ahead, IDtech remains fully committed to Oman’s progress. Its goal is to continue empowering local institutions with reliable, adaptable, and technologically advanced solutions that safeguard the country’s heritage and support its ambitions for a secure and prosperous future. n

As users move from conventional video into the new, AI-powered world, one of the most helpful options currently available is the new generation of edge AI cameras. With the latest tech releases, these devices are becoming more powerful, more capable, and – not surprisingly - more popular in a wider range of settings
n By: Dennis Choi, General Manager, IDIS Middle East & North Africa sales_mena@idisglobal.com
We are witnessing huge opportunities to leverage AI video technology to strengthen security, drive efficiency, and unlock new productivity-boosting applications across businesses. By running upgraded analytics engines, the new generation of edge AI cameras supports faster investigation tools without the need to rely on server processing, thereby also reducing load on central servers, and adding a layer of resilience, with edge processing and detection capability continuing to function in the event of network or server outages. Among the most compelling advantages of the latest edge AI cameras are ease of adoption, scalability, and lower total cost of ownership (TCO).
Ease of adoption is an important consideration, and edge AI cameras enable organizations to deploy and leverage analytics in a controlled, location-by-location manner.
This means they can avoid potentially costly purchasing errors, disappointing results, or – even worse in the case of security – equipment performance failures and breaches. They can minimize cybersecurity risks; assess platform reliability;

manage any regulatory or compliance requirements; and, of course, control that all-important cost metric, Total Cost of Ownership (TCO).
There may be other considerations as well. For security teams to use the new AI surveillance tools effectively, changes to operations, dispatch, and incident-handling workflows need to be planned and managed. There’s little point in sending automated alerts to security personnel on their phones if response protocols and training haven’t been updated to ensure they’re always received and acted on quickly.
In some cases, edge AI video analytics may be adopted for wider business functions beyond security – for example,
a camera set up to send alerts when a queue builds in a reception area, or to notify staff when a vehicle arrives at a loading bay. There are countless applications, but to ensure the best value, teams that will leverage the new analytics and whose capabilities will be strengthened by it need to be closely involved in the implementation. Where the plan is to leverage intelligence gathering from AI video, for example, to improve workflows, inventory management, marketing, or customer service, then the designers of the video solution need to work hand-in-glove with the department heads who will be using that data. The process of adopting edge AI cameras and leveraging new AI video surveillance tools is more effective when it involves all the relevant stakeholders from an early stage.

Predominantly, though, we are seeing edge cameras adopted to strengthen security, plug vulnerabilities at key points, and enable automated detection of potential threats. By providing more reliable alerts and eliminating false alarms, edge AI enables faster, more consistent security responses. It’s freeing up staff from labor-intensive monitoring tasks, allowing them to be deployed more effectively, and ensuring more consistent threat detection without human error or lapses in attention. Thanks to the latest, enhanced edge AI camera capabilities, the force-multiplying functionality of AI video is becoming more
widely available to more users, across settings from retail and hospitality to healthcare and logistics.
The latest cameras enable automated detection of a wider range of risk events, offer easier real-time video search features, and can be enhanced with other useful innovations, including more accurate live privacy masking. Essential functions, including crowd detection, abandoned and removed object detection, and fall detection, support more preventative and proactive security and safety responses. Fall detection, for example, is being adopted to improve safety in healthcare and assisted-living settings. The same technology is being used to reduce the risk
of harm from accidents in industrial and logistics settings, and to improve safety in public spaces.
Removed or abandoned object detection is being used to detect potential terrorist activity in public spaces, transit networks, and critical infrastructure settings; elsewhere the same detection capability is providing automated warnings if fire extinguishers are removed, if fire doors are blocked or left open, if emergency exit routes are obstructed, or if high value equipment or assets are moved - everything from medical equipment to vehicles and machinery.
And surveillance using edge AI cameras is even more powerful when combined with the latest AI live monitoring search tools designed to overcome the challenge of identifying crucial scenes within vast amounts of video footage.
These provide the option of making any target object or person easier to find by automatically extracting the best representative images, cropping them, and presenting them to operators for selection. By simply clicking the cropped image, the operator is taken to the precise moment in the video stream when the object last appears (i.e., the moment their most recent activity was captured on camera).
Each cropped image can also be indexed as a searchable visual moment, supporting faster identification. When each cropped image is classified into categories, such as people, faces, and vehicles, AI identification of object attributes also allows for filtered searches – such as searching for people by age and gender, clothing color, or whether they have accessories like glasses, hats, masks, or bags; or searching for vehicles by color or type.
Thanks to these developments, where it would once have been too expensive or impractical for human eyes to monitor multiple scenes 24/7, AI edge cameras now make this practical and affordable. n
Across today’s complex security landscape, safety is no longer defined by reaction but by foresight. As digital transformation accelerates across the Gulf and MENA region, solving for safer means uniting the technologies that see, hear, and understand, empowering decision-makers with real-time intelligence and seamless coordination when every second matters
n By: Loubna Tabbara, Marketing and Sales Director, Tabbara Electronics loubna@tabbara-electronics.com
Motorola Solutions brings this vision to life through a connected portfolio of trusted brands that work together to detect, analyze, communicate, and manage — enabling smarter, faster, and safer outcomes.
Reliable communication remains the backbone of operational success. Whether through MOTOTRBO DMR systems, ASTRO P25, or TETRA mission-critical networks, Motorola Solutions provides secure and resilient communication channels for frontline teams. For broadband environments, LTE handhelds and Push-to-Talk over Cellular solutions extend coverage beyond traditional radio systems, keeping teams connected across any distance.
These platforms form the foundation of real-time awareness, ensuring that voice remains uninterrupted, encrypted, and synchronized with data and video streams. Together, they enable seamless coordination between command centers and field personnel during both daily operations and critical incidents.
At the foundation of the ecosystem lies Avigilon, where advanced imaging meets AI-driven analytics. From city centers to critical infrastructure, Avigilon transforms surveillance from passive monitoring to active intelligence.
Its high-resolution cameras and analytics platforms, including Avigilon Unity and Avigilon Cloud Services, provide instant visual clarity and automated detection of unusual behaviors or threats. This intelligent layer ensures that security teams are not just recording events but anticipating them.
When environments demand awareness beyond the visible spectrum, Silent Sentinel extends the reach of surveillance. Its
rugged, multi-sensor and thermal camera systems are built for border protection, perimeter defense, and industrial applications where distance, weather, or darkness can obscure visibility. By integrating long-range detection with precision optics, Silent Sentinel delivers real-time situational awareness that complements Avigilon’s intelligent analytics. Together, they provide a seamless transition from wide-area monitoring to focused threat verification.
Pelco adds another layer of depth to the visual ecosystem. Known for its reliability and precision engineering, Pelco’s camera systems capture the details that matter most. Through Calipsa analytics and open-platform architecture, Pelco solutions integrate easily with other systems, enabling smooth interoperability within command environments. In large-scale operations such as airports, energy facilities, and transportation hubs, Pelco helps unify visual intelligence into a single, intuitive view that enhances control and accelerates response.

Voice remains the lifeline of mission-critical operations. ASTRO P25, TETRA, MOTOTRBO DMR, and Push-to-Talk over LTE systems deliver reliable, encrypted, and high-clarity communication for teams working in demanding conditions. For beyond-line-of-sight communication, Barrett HF systems extend this reach even further, enabling long-distance connectivity when conventional networks are unavailable. From tactical deployments to emergency coordination, HF radio remains an essential layer of resilience within the broader Motorola Solutions ecosystem.
Motorola Solutions transforms intelligence into action through systems that learn, connect, and adapt. The result is faster response, clearer communication, and stronger resilience across every sector
Together, these communication platforms form the backbone of situational awareness, connecting field personnel, vehicles, and command centers into a single operational network that ensures continuity, coordination, and confidence in every mission.
At the center of it all lies CommandCentral, Motorola Solutions’ command and control suite. Here, voice, video, and data converge into one operational picture. With AI-powered analytics, real-time location tracking, and incident management tools, CommandCentral empowers operators to detect anomalies, coordinate responses, and manage evidence within a unified environment. Automation tools like Orchestrate further streamline workflows, allowing command centers to move from reactive control to proactive management.
Each of these technologies plays a vital role on its own, but their true strength lies in integration. Avigilon, Pelco, Silent Sentinel, P25, MOTOTRBO, TETRA, HF Communications, and CommandCentral are connected through Motorola Solutions’ unified ecosystem, where voice, video, and data communicate seamlessly. This is how Motorola Solutions transforms intelligence into action — through systems that learn, connect, and adapt. The result is faster response, clearer communication, and stronger resilience across every sector. United by purpose, powered by intelligence, and strengthened by innovation, Motorola Solutions is solving for safer. n
The latest edition of ASSA ABLOY’s long-running Wireless Access Control Report shows a maturing market where digital and mobile solutions are becoming the norm. Alongside continuing trends such as wireless adoption, sustainability, and cloud services, the focus for many now turns to increasingly intelligent integrations and to demonstrating ROI to cement access control’s role in a new generation of smart, secure, and efficient buildings
n By: Thomas Schulz, Director & Head of Marketing DAS EMEIA, ASSA ABLOY Opening Solutions EMEIA thomas.schulz@assaabloy.com
Security professionals are entering an era of convergence – not only between physical and digital systems, but also between disciplines and objectives.
Organizations that lead in access control will be those that view it not only as a security tool, but as an enabler of transformation. Integration of digital access management with other systems is critical to the holistic smart building.
One expected finding from the new Report is that wireless access solutions are now mainstream. Adoption has climbed steadily, from 39% in 2023 to 42% in 2025, according to data from a survey carried out exclusively for the 2025 report. These solutions are now integral to modern access management strategies and workflows. According to ASSA ABLOY, this is the first time in over a decade of researching and publishing their report that wireless (either fully or partly) systems have overtaken wired systems among those who manage access digitally. Wireless access systems provide the flexibility needed for managing everything

from schools, hospitals, and manufacturing plants to mixed-use buildings, multiresidential housing, and agile workspaces. Adopters cite reduced wiring, easier retrofits, and integration-readiness as just a few of the advantages. Wireless is also foundational to mobile-first environments, making it easier to support touchless entry, remote management, and real-time control.
Why do organizations continue to digitalize access management? The single most important factor, according to ASSA ABLOY’s data, is convenience. When employees, contractors, and temporary
Data and insights in ASSA ABLOY’s biennial report can help businesses get their access ready for what’s ahead. ASSA ABLOY Opening Solutions EMEIA
visitors can come and go with ease, operations for building and security managers are made more efficient, including in terms of costs. Digitalizing access provides a concrete ROI – something that, from a strategic perspective, may be turned into a competitive advantage.
“We are delighted to offer our biennial look into the ongoing digitalization of access, which is also becoming a wirelessfirst technology,” says Richard Sharp, VP & Head of Product Unit Wireless Locks, DAS at ASSA ABLOY Opening Solutions EMEIA.
“Now running for more than a decade, our report highlights ways for security depart-
ments and consultants to contribute to their overall business. It also helps nonspecialist decision-makers to stay on top of what’s happening right now in access – and more importantly, to see what’s ahead.”
Mobile digital access is no longer a novelty. Increasingly, it is an expectation. Adoption has boomed, as widely forecasted. Fully mobile credential environments now account for 17% of all survey respondents, more than triple the rate of 2023’s report. For some organizations, mobile still is not a fit. Think, for example, of specific healthcare environments, pharmaceutical premises, or food preparation businesses. Yet respondents who rule out mobile continue to shrink from edition to edition: just 19% of survey respondents now reject altogether the idea of going mobile, down from 31% in 2023.
“Where our 2023 report captured strong momentum towards mobile access, the 2025 edition finds increasing market maturity,” adds Sharp. “As many organizations modernize their security in-
frastructure, digital access systems are becoming standard, with a clear shift to mobile credentials. Our own digital offering includes several widely adopted mobile solutions, including the Openow™mobile app for SMARTair wireless locks, CLIQ and eCLIQ Connect for mobile workforces, and the new ABLOY CUMULUS mobile key platform.”
Biometric access is also emerging as a serious, scalable option – not just for sensitive facilities, but increasingly for general commercial settings, especially with the launch of powerful solutions at accessible price-points, like the iDFace reader from Control iD*. Survey data showed that a vast majority of professionals (91%) now view biometrics as a practical access and authentication technology, with more than half of respondents (58%) already using it to some extent.
According to the International Energy Agency (IEA), buildings consume approximately 30% of global energy. The 2025 ASSA ABLOY Report confirms sugges-
tions that, increasingly, end-users and security professionals value the concrete ways in which digital access can help to reduce unnecessary energy use.
For many respondents to the survey, sustainability has gone beyond ‘merely’ a consideration: for 27% of respondents, it is the top factor when considering investments to enhance access management reach or capability. “Sustainability was also a major factor in the design and specification of our own new HQ, DubaiOne,” explains Sharp.
“For many organizations, across multiple and diverse sectors, sustainability is moving from a supporting role to a strategic driver,” he adds. “Wireless systems, which reduce the need for cabling and complex infrastructure, are often seen as a ‘greener’ alternative. Battery-powered and energy-harvesting devices generally consume much less energy than equivalent wired locks. We also see fast-growing demand for green building solutions and documentation, such as Environmental Performance Declarations (EPDs), which also count towards several green certification schemes we support, including BREEAM, LEED, WELL, and others.” n
Excel sheet with
Sustainability
Retailers are entering a new era in which in-store video can deliver far more than surveillance. By transforming visual data into behavioral insights, AI-powered analytics has the potential to shape strategy, improve customer experience, and drive smarter decision-making. The real opportunity lies in elevating video intelligence from a security function to a core source of retail insight
n By: Andrea Babayan, Demand Growth Strategist, Ipsotek andrea.babayan@ipsotek.com
After 15 years in demand generation, retailers are struggling to turn customer experience data into real intelligence. Many leaders still admit: “We have more data than ever - but less clarity on what to do with it.” AI-powered video analytics may hold part of the answer, yet it remains curiously under-recognized as a strategic data partner. While digital teams analyze online behavior and loyalty data, the behavioral insights inside stores often stay locked in security systems.
Video systems were built to monitor and protect, not to analyze or predict. Procured by security departments and integrated long before data governance became mainstream, those early conditions defined how the sector still sees itself today - as a function rooted in protection rather than prediction. However, change is starting to emerge, with a growing appetite for capabilities and data-driven insights in recent RFPs. Procurement frameworks are beginning

to reflect this shift, as retailers look for solutions that link operational intelligence with customer experience goals. For example, at Media One Hotel in Dubai, Ipsotek’s video analytics helped rebalance staff allocation using real-time flow analysis. Modern AI systems can now interpret dwell time, directional flow, and engagement hotspots - insights once impossible to quantify on a shop floor.
When used responsibly, video analytics reveals the “why” behind the “what.” It shows how customers move, hesitate, or disengage before purchasing, turning behavior into actionable insight. While responsible AI systems can maintain full privacy compliance, they also ensure

that customer identity remains protected while behavioral analytics operate in real time.
As highlighted by the ECR Retail Loss Group, many retailers are now using video analytics not only to reduce loss but to improve merchandising and service efficiency. Yet many still struggle to embed this intelligence into existing business intelligence systems - not because the technology is immature, but because data ownership is fragmented. Until visual data sits alongside CRM and marketing intelligence, decision-making will rely on partial truths.
Retail and analytics teams speak in outcomes and conversion rates; video analytics providers talk in detection models and accuracy. That disconnect keeps the technology operational, not strategic. Some retailers still cite complexity or privacy concerns, while others struggle to link legacy systems with new AI capabilities. To gain a voice in retail’s data dialogue, providers must connect visual intelligence to performance and experience outcomes. The real shift is from counting events to understanding behavior - that’s
when visual data becomes business intelligence. At Ipsotek, this momentum is becoming clear as privacy-first analytics and edge computing mature, enabling data flows between systems, sensors, and strategy.
Across the Gulf Cooperation Council (GCC) region, retailers are beginning to connect the dots. Groups such as LuLu, working with Microsoft, are building AI-enabled ecosystems that merge operational, customer, and environmental data. Regional forecasts - including analyses by Mordor Intelligence and IDC - predict AI investment in the retail sector to grow by over 20 percent annually through 2027, driven by smart-mall and omnichannel projects. Elsewhere, new collaborations between integrators and analytics providers are redefining what video means - no longer a feed for surveillance, but a layer of operational context.
For video analytics providers to be seen as data partners, they must shift their
mindset and language. It’s not about alerts but alignment; not just about motion detection but movement understanding. This trend echoes DTIQ’s 2024 Future of Store Intelligence report, which found that retailers integrating video analytics into their decision frameworks see sustained improvements in efficiency and experience.
Retailers report reduced queues, better staff allocation, and more responsive service, an experience their own customers constantly seek. Ipsotek’s mission is to turn visual data into contextual intelligence that drives profitability, efficiency, and responsible innovation.
By its very nature, AI-powered video analytics is a maturing discipline - finding new ways to connect visual insight with strategic decision-making. As it moves from a background safeguard to a frontline instrument of strategy, its potential to connect visual and digital intelligence is finally being recognized. As AI systems mature and regulation catches up, those who integrate these capabilities will lead the next retail transformation. The real opportunity lies in partnership: when security integrators, technology providers, and retailers combine their perspectives, video analytics brings more than observation - it becomes operational understanding.
It’s worth considering: will the next generation of retail intelligence rely not only on new sensors, but, more importantly, on using data already in front of us to understand and engage customers in ways that truly resonate with them?
The future of retail intelligence won’t be defined by who has the most cameras or the most data, but by who can translate insight into meaningful action. For retailers, that means embracing visual data as a core part of their intelligence framework. For technology providers like Ipsotek, it means continuing to push the boundaries of context-aware AI responsibly, transparently, and with measurable impact. n
Inside the lens of every camera, an evolutionary leap is taking place. Previously, humans would look through cameras to see things. Now, machine learning enables cameras to do it for them. Say hello to a new generation of intelligent monitoring and surveillance solutions, thanks to a technology that, ironically, can’t be seen
n By: Sienna Cacan, Enterprise Segment Marketing Manager, Axis Communications sienna.cacan@axis.com
Between 2025 and 2033, the global AI video analytics market is expected to grow at a CAGR of 21.4%, reaching $71.3 billion in value, according to Grand View Research. This growth is being driven by its ability to deliver datadriven insights that enhance operational planning and decision-making. In the Middle East and among GCC member states, the integration of AI into video surveillance cameras is reshaping the market and driving strong growth projections. Market insights from Precedence Research show that Saudi Arabia led the sector in 2024, while the UAE is expected to witness significant growth in the years ahead. However, video analytics is only as valuable as its outcomes, and its results are only as impactful as they are tangible. It also represents an ecosystem of technologies, including network surveillance, motion detection, and edge computing, that are coalescing and reshaping security and surveillance as we know it. For that to happen, technology vendors have to demonstrate the efficacy of their solutions. The best ones are those that get creative. When that happens, companies see the potential of analytics to modernize themselves, strengthen security, and improve business performance.

Video analytics marks a fundamental shift away from manual surveillance, where human operators were required to monitor multiple camera feeds and identify people, vehicles, and other objects in their lines of sight. The image of security personnel sitting in a backroom looking at a stack of CCTV feeds is now very much obsolete, especially as the Middle East, its urban areas, and critical industries like oil and gas invest in security technologies
that aim to enhance their efficiency and resilience.
The enterprise value of AI-enabled edge analytics is seismic. It boasts incredible potential where devices and servers at the edge of networks can perform storage and analytics locally, thus reducing latency and bandwidth requirements. As a result, vendors like Axis have prioritized the development of those capabilities, culminating in ARTPEC-9, the ninth generation of its purpose-built systemon-chip (SoC). Building on and refining the capabilities of previous generations,

To demonstrate the customization capabilities of its network surveillance cameras, Axis turned them into musical instruments. Cameras were trained to identify a selection of different objects, and each object was allocated a sound that would trigger whenever it was detected in a specific zone. The result was the world’s first object detection orchestra
ARTPEC-9 advances AI-powered analytics and supports the AV1 video encoding standard from the Alliance for Open Media (AOM), a first for network video and helping operators reduce storage costs without compromising forensic detail.
Edge AI is one of the primary areas where the technology is being applied in the security industry, and it now plays a valuable role in hybrid solution architectures. Edge AI analytics help boost accuracy by analyzing video footage at the source, avoiding potential data degradation that may arise from transferring footage between environments.
Consider the following: a camera is no longer just a camera. Transformed by analytics, it is a high-performing piece of hardware that industries, companies, and security teams can use to automate actions and deliver valuable insights. For that to happen, analytics solutions need to be intuitive. Built on open platforms, they can be user-friendly and integrate seamlessly with existing network systems, allowing for scalability and systems to grow as organizations do and infrastructure is rolled out.
The value proposition of analytics remains the same regardless of application or use
case. An oil and gas plant wants to monitor the number of employees present in potentially hazardous areas. A city planner wants to power a digital twin of the urban environment and conduct traffic management tests. A retail chain wants to set up a self-checkout service at its stores that lets staff keep a lookout for items that haven’t been scanned and paid for. All these use cases are feasible using the same approach. By integrating AI into video surveillance, operators can increase their situational awareness and accelerate their response times in the event of incidents. It improves accuracy levels and delivers data insights that companies can use to improve their operational efficiency.
Video analytics applications have evolved quickly over the last five years. Coupled with advancements in camera technology and the maturation of regulations regarding privacy and data protection, companies can now access and deploy entire suites of tools dependent on their security and surveillance needs.
Manifested, analytics is also indicative of new business value at no extra cost. For example, Axis Object Analytics comes preinstalled on compatible Axis network
cameras. Customers do not have to pay extra for it. The application is edge-based, thereby eliminating the need for additional servers, and it can run multiple, customized detection scenarios simultaneously. Again, it’s all about doing more with less. To demonstrate the customization capabilities of its portfolio of network surveillance cameras, Axis turned them into musical instruments. Cameras were trained to identify a selection of different objects, and each object was allocated a sound that would trigger whenever it was detected in a specific zone.
The result was the world’s first object detection orchestra, overseen by the Axis team and music producer Jonas Quant, performing a synthwave rendition of Strauss’s ‘Also sprach Zarathustra’. It was a novel idea that went a long way in showing not just how the technology works, but its inherent versatility. Analytics could be the world’s next big pop music star, so just imagine what it can do for business.
At its core, analytics must contribute to a shared vision of a smarter and safer world. It is a means to better understand our surroundings and what is taking place and what is taking place, enabling industries, companies, and personnel to make informed decisions and best protect people, resources, and infrastructure.
The market for video analytics in the Middle East will continue to grow, requiring developers, manufacturers, and installers to up their game to meet demand. Meanwhile, the technology continues to evolve. Already, we’re reaching new frontiers as analytics are integrated into surveillance drones, used to analyze highly detailed patterns of human behavior, and form part of IoT networks that span entire regions.
The future of AI and analytics in video surveillance is not just about the technology getting smarter; it’s also about using the technology in smarter ways. Backed by strategic thinking and with the help of trusted brands, companies can set a new standard in intelligent surveillance. n
Alongside rapid development in the Middle East, the region is experiencing fast growth in demand for fire safety products. Current trends in Saudi Arabia and the wider region show that UL-approved fire safety systems with integrated smoke control are gaining popularity, offering solutions suitable for both high-rise residential buildings and large commercial sites
n By: Shadi Elhag, Business Development Manager for the Middle East, Advanced shelhag@advancedco.com
The Middle East is in the midst of a historic construction cycle. In Saudi Arabia, this has been visible through the development of giga projects, new high-rises, vast transport hubs, and dense mixed-use districts. The Kingdom now boasts approximately 47 skyscrapers with an average floor count of 60 to 70 floors. However, this development is set to further rise with a shift away from oil exports towards a new growth in tourism. One such example of this shift is the Rise Tower, which is a planned 2km tall skyscraper in Riyadh, Saudi Arabia, designed to be the world’s tallest building.
However, alongside this growth is a demand for fire safety to protect inhabitants. This has led to UL fire safety systems gaining significant popularity in the region. However, with smoke inhalation recognized as the primary cause of firerelated deaths, UL fire safety systems that include integrated smoke control are becoming particularly popular. This has been consolidated by several recent tragedies, which have resulted in deaths

due to smoke inhalation. A recent example was the blaze at Cairo Telecommunications in Egypt in July 2025, where four workers were killed, with at least 22 injured. A health ministry spokesperson stated that the injuries were mostly due to smoke inhalation.
In light of such tragedies, smoke control has risen up the agenda in Saudi Arabia, with a chapter on Smoke Control Systems included in the new Saudi Fire Protection code. This signals the importance of designing and installing fire safety systems, which include robust smoke control. Consequently, UL fire safety systems that
include integrated smoke control have taken center stage.
Witnessing an increased number of requests from customers for smoke control, especially from residential projects and hotels with six floors and above, Advanced offers a versatile fire alarm system with its Axis AX addressable fire panel featuring an innovative smoke control approach with its DynamixSmoke, which is approved to UL864 standards
and complies with UUKL requirements. Advanced’s Axis AX combines addressable panels, the latest in sensor technology, CO devices, audio systems, and command centers, delivering high performance, quality, and ease of use. Its powerful networking capabilities, extensive configuration options, and comprehensive cause-and-effect programming put end-users in complete control of their fire alarm system. An impressive feature of the Axis AX is its scalability. It can deliver fast, reliable communications from a two-panel network up to a large 200node network. Very few manufacturers can offer the capacity to connect up to 200 panels, making the Axis AX ideal for small and large projects. The Axis AX also features additional integrated features, including smoke control and voice evacuation.
Simplifying smoke control design, the Axis AX’s DynamixSmoke gives complete and active control of fans and dampers from the fire system, and it also makes smoke control easier to install, configure, and operate. This is thanks to its simple four-step configuration process. Using a simple grid format to configure fans and dampers saves hours of setup time, allowing a working system in minutes instead of days, and gives an at-a-glance view of all settings. Listed for both dedicated and non-dedicated applications, it provides automatic and manual options for controlling fans and dampers. Offering quick, clear configuration of smoke compartments across sites, DynamixSmoke also provides simple cause-and-effect programming and autoconfiguration of fan and damper interfaces. In addition, it offers complete customized control, including post-alarm purge, cascade options, interlocks, sequential fan restart, automatic testing, and stairwell pressurization, helping control smoke and airflow for safe evacuation.
with voice evacuation. This is particularly important for the raft of high-rise developments. Despite the emergence of hightech fire engines equipped with new taller evacuation ladders, generally, ladders only extend to the tenth floor, making a robust fire system essential.
The flexible Axis AX therefore offers critical voice evacuation with integrated audio for automatic (and manual) fire
detection and voice evacuation but also smoke control, all in one system.
Axis AX voice evacuation allows 16 prerecorded messages and multiple language variants, so the panel can operate autonomously without interaction to evacuate a building if the fire brigade isn’t present. If the fire brigade is in attendance, Axis AX provides robust telephone communication channels to ensure maximum safety. The fire and emergency telephone system identifies the location of field telephone users during emergencies since users can plug a telephone into an Axis AX fire panel to communicate the situation on a given floor to aid in evacuation.

However, with voice evacuations, problems can sometimes arise if audio doesn’t sync, and people can hear multiple messages at once. To solve this, the Axis AX range features the unique PerfectSync, which ensures audio synchronization across the entire network to avoid confusion from mixed messages. This includes large networks where it is possible to deliver a message from the first panel to the 200th with highly synchronized fast messaging to help people evacuate faster in case of fire. This is ideal for high-rise residential buildings, large shopping centers, or universities. The clarity it provides helps ensure safer evacuation.
Another feature that customers are increasingly asking for is fire-alarm systems
alarm signaling and live voice paging during emergencies. For example, the Axis AX was selected to provide fire protection for the Marassi Galleria Shopping Mall in Bahrain. This large-scale development required a total of 47 Axis AX fire panels to be installed in a network, complete with voice evacuation systems, amplifiers, and firefighter telephones. This project illustrates the demand for centralized high-performance solutions that ensure easy access and control for firefighters in emergencies, with customers preferring integrated solutions, like the Axis AX, that combine not only fire
With high-rise construction booming across the Middle East, the need for dependable and fully integrated fire safety solutions has never been greater. By streamlining critical functions, such as smoke control and voice evacuation through a single fire panel, integrated systems enable faster, more coordinated responses for fire services. Advanced’s Axis AX is designed to combine fire detection, smoke control, voice evacuation, and communications in one resilient system. This makes it the ideal solution for the Middle East’s high-rise developments. n
Security has become a top agenda item in boardrooms across the Middle East. As the region undergoes rapid digital transformation, the once-clear boundaries between cyber and physical threats are dissolving, creating a complex and evolving risk landscape. The integration of physical access control systems with broader cybersecurity strategies is no longer a luxury; it is a strategic imperative.
n By: Sam Cherif, Sr. Director, Regional Business Head, MEA sam.cherif@hidglobal.com
Recent statistics paint a stark picture of the escalating threat landscape. IBM’s Cost of a Data Breach Report 2025 found that the average cost of a data breach globally has reached $4.4 million. In the Middle East, this figure stands at around $7.1 million, highlighting the region’s heightened vulnerability and the significant financial repercussions that organizations face from cyber incidents. HID’s 2024 State of Physical Access Trend Report also found that the threat is tangible and growing, with 76% of IT leaders reporting a rise in threats to physical security systems over the past year.
Furthermore, the World Economic Forum’s Global Cybersecurity Outlook 2024 projects that cybercrime costs are set to nearly double over the next three years, largely fueled by vulnerabilities in outdated systems. These alarming statistics reveal a critical gap: many organizations are failing to connect their physical security infrastructure to their overall cybersecurity posture. In fact, HID’s re-

search found that 28% of organizations still rely on outdated and easily compromised magnetic stripe technology. This reliance on legacy systems creates a gaping vulnerability that cybercriminals can and will exploit.
To effectively keep hackers out and assets safe, organizations must adopt a robust and holistic approach to physical access control systems (PACS). As highlighted in
our PACS Perspectives Report: Bridging the digital and physical divide, this requires careful consideration of several key areas. First, in a connected environment, PACS devices are no longer static. The ability to securely update and upgrade these devices remotely via a cloud service is a game-changer. This enables organizations to maintain the highest level of security by ensuring their systems are always running the latest firmware, patching vulnerabilities in real-time, and adapting to new threats without requiring on-site intervention.

HID’s trusted identity solutions give people convenient access to physical and digital places and connect things that can be identified, verified, and tracked digitally. Millions of people around the world use HID products and services to navigate their everyday lives, and billions of things are connected through its technology. The company works with governments, educational institutions, hospitals, financial institutions, industrial businesses, and some of the most innovative companies on the planet. Headquartered in Austin, Texas, it has over 4,500 employees worldwide and operates international offices that support more than 100 countries. HID is an ASSA ABLOY Group brand
Second, the adoption of artificial intelligence (AI) and machine learning (ML) capabilities is becoming more common, enhancing operational precision and efficiency. IBM found that organizations that extensively deployed security AI and automation across their operations saved an average of $2.2 million on breach costs compared with those that did not – a clear demonstration of the ROI that advanced PACS technologies can deliver when implemented correctly.
Finally, the evolution toward mobile access is fundamentally reshaping how people interact with secure spaces. In fact, nearly 80% of organizations plan to
deploy mobile IDs within the next five years, with 39% already using them today, according to HID’s State of PACS survey. Organizations across sectors are increasingly recognizing that mobile access doesn’t just offer convenience; it brings stronger protection through encrypted communication, instant credential revocation, and even biometric verification. These are all features that physical cards cannot match.
Take, for example, HID Mobile Access. This solution empowers users to unlock doors, gates, networks, and systems using their smartphones, tablets, or wearables, eliminating the need for traditional physical cards. By transforming the smartphone into a secure credential, organizations gain a more flexible, conveni-
ent, and sustainable way to manage identity while strengthening security through multi-factor authentication and encrypted communication channels.
Another important innovation is the use of mobile credentials within digital wallets, which is redefining access and identity experiences across campuses, enterprises, and public spaces. Across the Middle East, digital wallets are seeing rapid adoption as users embrace mobile-first solutions that combine ease of use with high security. In fact, in the GCC region alone, mobile wallet usage is booming, with 38 million users in 2024 and a projected market value of $932 million by 2030. With solutions like HID Mobile Credentials, employees, tenants, and guests can use their digital wallets, whether on Android devices or on their iPhones, to securely enter buildings, open doors, move through turnstiles, or access specific floors with a simple tap near a reader. This seamless experience enhances both security and convenience, eliminating the need for physical cards while meeting modern expectations for connected, contactless environments.
Selecting the right PACS partner is just as critical as selecting the right technology. HID understands that organizations need more than just hardware and software; they need a trusted ally who can help them navigate today’s complex security landscape with confidence. Every day, millions of people in more than 100 countries rely on HID’s products and services to securely access physical and digital spaces.
As a trusted supplier for organizations of all sizes, HID has the cybersecurity standards, policies, procedures, and frameworks in place to help our customers stay protected. By moving beyond the traditional notion of physical security and embracing an intelligent and digitally-enabled approach, it can build a more resilient and secure world for everyone. n
In today’s hyper-connected world, security has evolved from a gatekeeper into an enabler of efficiency. ScreenCheck engineers interconnected ecosystems where access control, video analytics, alarm management, visitor management, and IoT sensors work together seamlessly. The result is smarter environments, faster responses, and measurable operational gains
n By: Mohamed Zakky, Sales Director, ScreenCheck mohamed.zakky@centena.com
The modern enterprise no longer measures success solely by how tightly it locks down its environment, but by how efficiently it operates. True security is achieved when systems communicate, anticipate, and act — allowing protection and productivity to coexist.
Traditional siloed systems create friction: separate platforms for access control, surveillance, and identity management lead to wasted time, manual oversight, and inconsistent reporting. Integrated access control has demonstrated measurable operational benefits. Research from Grand View and Precedence indicates that organizations deploying smart security systems have seen up to a 35% improvement in response times and a 25% reduction in administrative overhead related to manual credentialing and visitor processing.
ScreenCheck’s ecosystem delivers this unification. By linking identity management, video analytics, vehicle access, and environmental controls under one architecture, organizations gain a single version of operational truth. Every cre-

Mohamed Zakky, Sales Director, ScreenCheck
dential issued, every entry authorized, and every alarm triggered aligns with a unified data framework, improving decision-making and response while reducing overhead.
When systems interlink, productivity rises. In ScreenCheck’s architecture, identity management becomes immediate and
synchronized: credential issuance and access provisioning occur at the same time, allowing users to be onboarded instantly through pre-mapped permissions and eliminating manual configuration. Visitor workflows follow the same principle. Guests receive mobile or QR-based credentials before they arrive, while integrated access control and video verification automatically validate and track their movement, reducing check-in times by up to 60 percent and generating complete, end-to-end audit trails.
Intelligence operates in the background to reinforce these processes. AI continuously monitors for anomalies such as tailgating, unauthorized entry, or unusual dwell times, and triggers automated responses that may include alerts, lockdowns, or temporary access suspension. Predictive intelligence further enhances security by using IoT-derived data to anticipate risks before they escalate.
Data from across the facility feeds into this unified workflow. Sensors embedded in doors, racks, lockers, and turnstiles provide real-time information on movement, occupancy, and environmental conditions. Combined with access logs, these insights support manpower planning and facility optimization. All relevant events — from access attempts to video feeds and alarms — converge within a single dashboard, enabling operators to visualize, verify, and

act immediately. According to industry benchmarks, this consolidated view can reduce incident-resolution times by nearly half.
Efficiency becomes tangible when technology adapts to the environment it protects. In data centres, ScreenCheck integrates rack-level access, biometrics, video, and IoT sensors into a single control point. Each event is time-stamped, validated, and stored as blockchain-secured audit data, creating tamper-proof records and reducing manual verification. Hotels, hospitals, corporate offices, and educational campuses function as digital ecosystems. A single ID can operate as an access key, attendance tracker, and resource pass, while visitors and contractors are authenticated through the same workflow. This interconnected environment ensures transparency, safety, and efficient movement across facilities. Across sectors, it delivers measurable results: faster incident response, fewer administrative hours, and improved compliance readiness.
ScreenCheck’s solutions are designed for scalability and simplicity. Cloudready, API-driven, and OEM-integrated, they grow as organizations expand — from single-site deployments to enterprise-wide networks.
Multi-factor authentication and blockchain-verified credentialing maintain identity integrity, while AI-driven analytics adapt continuously to usage patterns, anticipating risks and optimizing operations. IoT integration enables devices and systems to share intelligence, creating proactive security environments that evolve dynamically.
The global access control market — projected to exceed USD 25 billion by 2034 — is driven by these capabilities: integration, automation, and intelligence. Efficiency is no longer a by-product; it has become a defining measure of performance.
ScreenCheck’s integrated solutions redefine how security contributes to organizational outcomes. They enable faster
Hotels, hospitals, corporate offices, and educational campuses function as digital ecosystems.
A single ID can operate as an access key, attendance tracker, and resource pass, while visitors and contractors are authenticated through the same workflow
onboarding and simplified credential management, centralized policies and global scalability, lower operational costs through unified system management, reduced false alarms and faster verification, and audit-ready transparency for compliance and governance. By linking access control with AI video analytics, alarm monitoring, and IoT systems, organizations gain the situational awareness and agility required to stay secure and efficient.
For more than two decades, ScreenCheck has supported enterprises, governments, and campuses across the Middle East, India, and Africa in creating connected, intelligent, and efficient security ecosystems. The mission is to make technology invisible yet impactful — delivering seamless safety and operational clarity through a unified framework.
ScreenCheck believes security should accelerate progress rather than interrupt it, with interconnected systems that do more than protect — they empower, enabling smarter, safer environments for tomorrow. n
The future of access control lies in unifying privacy, security, and convenience without sacrificing one for the other. The most successful organizations will design access control systems combined with identity frameworks rooted in trust and usability, where technology enhances the human experience
n By: Mohammed Murad, Chief Revenue Officer, Iris ID mohammed.murad@irisid.com
In an era where both cybercrime and physical identity breaches are constant threats, the disruption and financial strain they cause cannot be overstated. Each data breach or unauthorized entry leaves companies scrambling, spending millions to upgrade systems, compensate victims, or pay ransoms. Meanwhile, individuals are left helpless, wondering when the next attack will strike.
Under the current circumstances, traditional approaches to authentication and identity have proven insufficient. To move forward, we must begin to manage identity through a new lens, one grounded in the three essential pillars of privacy, security, and convenience.
Access control and identity are not siloed disciplines—they must work together to protect both the individual and the or-

ganization. As threats evolve, companies must prioritize multifactor and multi-modal biometric authentication. Using biometrics alongside traditional credentials like PINs or smart cards creates a stronger, more dynamic defense against attack that targets a physical door or a digital space. Unlike static credentials, biometrics are inherently more secure, harder to steal, replicate, or misuse. However, technology alone is not enough. Organizations must design strategies and policies that balance security, privacy, and convenience. The question becomes not if to invest in such systems, but when, because the cost of inaction is measured in breached data, broken trust, and lost reputation.

Balancing privacy, security, and convenience means developing identity authentication solutions around the user. When users are in control, they place more trust in the systems and are more likely to be more engaged with adhering to proper protocols. A successful identity framework should be: simple to use, without sacrificing rigor, compliant with global biometric governance, and designed for effortless deployment and management. For example, pairing a biometric identifier with a smart card or mobile credential adds both security and convenience. If the device is lost or stolen, the biometric remains uncompromised, rendering the credential useless to anyone else. In this way, organizations protect both the Personally Identifiable Information (PII) and the system, while users retain confidence in how their identity is safeguarded.
The future of identity management depends on trust, transparency, and adaptability. Users must understand how their personal data is collected, stored, and used. Organizations, in turn, must commit to protecting that data through encryption, secure storage, and compliance with privacy regulations such as GDPR and others. The industry must coalesce to enforce strict regulations that are globally and uniformly followed. As technology continues to evolve, identity authentication systems will need to be compatible with AI tools. Artificial intelligence and machine learning will help systems recognize behavior patterns and detect anomalies in real time, strength-
Using biometrics alongside traditional credentials like PINs or smart cards creates a stronger, more dynamic defense. Unlike static credentials, biometrics are inherently more secure, harder to steal, replicate, or misuse
ening protection without adding friction. Access control will need to operate seamlessly across these multiple complex ecosystems.
Ultimately, the future of access control lies in unifying privacy, security, and convenience without sacrificing one for the other. The most successful organizations will design access control systems combined with identity frameworks rooted in trust and usability, where technology enhances the human experience.
To strengthen identity systems today, organizations can take several immediate steps. They can analyze the authentication ecosystem to identify potential gaps and leverage multimodal biometrics and MFA for higher security with effortless usability. It is also essential to embed transparency and informed consent into all aspects of data handling, while building trust and a strong compliance culture through user and stakeholder education.
Access control can no longer just focus on keeping the wrong people out. It must take into account the total picture and include solutions that foster secure, private, and seamless interactions between people and technology.
By embracing a holistic, user-centric approach grounded in privacy, security, and convenience, we can build systems that protect what matters most, while empowering individuals to engage confidently in both the physical and digital worlds. n
Reconeyez is preparing to present its latest technologies at the Intersec Exhibition in Dubai from 12–14 January 2026. Visitors will be able to meet the company at Hall S1, Booth B42, where Reconeyez will highlight how its intelligent platform is redefining remote surveillance for critical infrastructure, construction, and temporary or hard-to-secure sites
n By: Andy Keeley, Marketing Director, Reconeyez andy.keeley@reconeyez.com
Founded on the mission to provide reliable security in locations where traditional CCTV systems struggle, Reconeyez has become known for its fully wireless, long-range detection technology. The company’s solutions combine advanced motion analytics, military-grade communications, and cloud-based device management, creating a high-accuracy, low-maintenance security ecosystem.
At the heart of the Reconeyez system is its AI-enhanced detector. Using computer vision and machine-learning algorithms, the detector distinguishes between human activity, vehicles, and environmental noise—dramatically reducing false alarms. This smart classification is especially valuable for sites exposed to weather, wildlife, or heavy machinery, where conventional sensors often fall short. Reconeyez devices are also designed for rapid deployment. Their wireless architecture and multi-year battery life allow units to operate without power or network infrastructure, making them a great option for temporary or remote environments. Coupled with a long-distance radio communication network, the detectors can be spread across large areas while remaining connected to the Reconeyez Cloud platform.

The Reconeyez Cloud provides centralized management for all system components. Security teams can configure devices, review events, analyze trends, and respond to incidents from anywhere in the world. High-quality imagery and data-driven insights support faster decision-making and more efficient operations, enabling users to monitor multiple sites simultaneously with confidence.
At Intersec Dubai 2026, Reconeyez will showcase new enhancements to its platform, including improved AI analytics, expanded integration options, and upgraded hardware designed to perform in demanding outdoor environments. Attendees will have the opportunity to see live demonstrations, explore real-world
use cases, and speak with Reconeyez experts about tailored solutions for industries such as construction, utilities, transport, and defense.
Intersec, one of the world’s foremost security and safety trade events, provides an ideal stage for Reconeyez to connect with system integrators, distributors, and industry professionals seeking advanced perimeter protection. With increasing global demand for flexible and reliable outdoor security, Reconeyez aims to highlight how its technology can overcome the limitations of fixed infrastructure and deliver dependable performance in the field. Professionals attending the exhibition are invited to visit Reconeyez at Hall S1, Booth B42 to experience their technology first-hand, discover upcoming product developments, and explore partnerships for 2026 and beyond. n


On September 17, American company Panduit, a premium provider of networking solutions, held its annual European press conference at the elegant Schlosshotel in Kronberg, Germany. As one of nearly thirty attendees from technology and media outlets, we had the opportunity to learn about innovations poised to shape the industry for the next decade
n By: Damir Muharemović damir.muharemovic@asmideast.com
We hadn’t even stepped into the Schlosshotel before our senses were already overwhelmed by the sights and scents of the venue. This luxury castle-hotel, built in the late 19th century as a residence for German Empress Friedrich, the eldest daughter of British Queen Victoria, served as a symbol of ties between the German and British courts. Its charm has been preserved to this day in its authentic form. Every door handle, chair, chest of drawers, or tapestry is a work of art, every room uniquely designed, every wall filled with antiques and artwork from the imperial collection. This blend of historical elegance and modern luxury served as a prelude to another, more contemporary story about quality and durability.
“This is a place where vision, innovation, and history meet. That’s why we chose the Schlosshotel for this conference,” said Martin Kandziora, Senior Marketing Manager for EMEA at Panduit. The belief that this vision is the key to growth drives Panduit, a company with 6,000 employees and revenues in the billions, to innovate and inspire. “I have witnessed this firsthand over the years, from Chicago to Costa Rica. The products we will see today reflect this quality and sustainability. We invest heavily, and our products take time to develop. We don’t hold press conferences often, but today we have something to show and to demonstrate

how Panduit is shaping the future of IT networks,” concluded Kandziora.
Three trends underpin growth in the IT networking industry, explained Jens Holzhammer, Managing Director for EMEA at Panduit. The first and most important driver is the massive increase in generated data, primarily from the proliferation of images and video, and the growing adoption of AI. This demands much higher bandwidth. “This has been the main driver for at least the past three years. Data centers require a lot of power, and each data center demands significant engineering,” said Holzhammer. The second driver is electrification and the transition from fossil fuels to
renewable energy, and the third is reshoring, that is, the return of manufacturing to home countries to reduce costs, improve quality control, and strengthen local economies. The latter is particularly noticeable in the electronics component segment, as supply chains have been disrupted. These trends affect both Panduit and its customers, prompting the company to invest heavily in multi-continent manufacturing. In South America, it opened two state-of-the-art factories in Costa Rica and Mexico. In Southeast Asia, production moved from Singapore to a new facility in Malaysia, and in Indiana, USA, a large, fully automated distribution center was established. In Europe, the Romanian factory, operational for sixteen years, is now set for expansion.




“I asked myself, when I became CEO of Panduit, what is particularly important for this company. Then I visited the Innovation Center and was amazed by the engineering: more than 250 engineers work daily in R&D, resulting in over 3,000 patents. Panduit truly shapes global communications standards,” Holzhammer emphasized, concluding that continuous innovation, high-quality production, and exceptional service and customer expe-
rience are the three pillars of Panduit’s foundation.
Hans Obermillacher, Business Development Manager for Data Centers in EMEA, presented key trends and technological solutions demonstrating how data centers must evolve to meet future chal-

Unlike conventional PoE, which is limited to 100 meters and lower power, FMPS delivers 30 times the distance and six times the power, making it ideal for older buildings or city centers, as well as modern IT infrastructures, industrial campuses, stadiums, airports, and the smart buildings of the future
lenges. The industry focus is on energy efficiency - not only room cooling but chiplevel cooling – followed by power distribution in high-demand environments (currently cited up to 600 kW per cabinet), and the need to redefine infrastructure in networking and industrial applications. Edge computing, intelligent Power Distribution Units (PDUs), and containerized data centers are the three leading trends highlighted by Obermillacher.
As a concrete example, the SUPERPOD in Cologne uses eight NVIDIA H100 GPUs in DGX H100 servers. This data center is designed to support heavy consumer and AI workloads with substantial power consumption, illustrating the scale of modern installations. For edge infrastructure, examples include retail chains, banks, and factories in Europe, “where solutions typically involve a few cabinets, multiple iPDUs, one UPS, a cooling system, and all necessary connectivity (fiber, copper). Key benefits of such edge setups are lower latency, higher bandwidth, and enhanced security,” Obermillacher noted. Panduit’s UPS portfolio covers 1 kVA to 20 kVA devices, supporting single- and three-phase systems. These are high-efficiency double-conversion UPS units (up to 97.5% efficiency in online mode), available with Li-Ion or VRLA batteries. They offer up to nine minutes of autonomy without additional batteries, including network cards for advanced management and monitoring.
Particular attention was given to Panduit’s new EL2P iPDU (Elevate to Power). This intelligent power distribution unit provides simplified installation, greater control over power, and automation. Key features include: precise energy metering (±0.5%) via an intuitive 1.8” touchscreen, 4-in-1 outlets supporting diverse equipment, hot-swappable controller and
display modules with zero downtime, dual 1Gb Ethernet with daisy-chain capability for up to 64 iPDUs on a single IP, and support for high operating temperatures up to 60°C. The EL2P meets advanced cybersecurity standards (UL 2900-1, IEC 62443-4-2), including secure network authentication and intrusion protection. Finally, it integrates with Cisco Nexus Dashboard, providing energy usage insights without additional hardware.
“This iPDU will also have an EL2S version and a higher-capacity model expanding to even greater amperages of up to 100 A that are planned for 2026,” Obermillacher announced.
The third session focused on electrification as a key factor in sustainability and technological advancement. Ferhat Peker, Account Manager for the Solar Industry in EMEA, emphasized that climate change, technological innovation, environmental policies, and economic incentives are accelerating the need for electrification across sectors, particularly transport, renewable energy, data centers, and smart buildings. According to Gartner, 75% of enterprises will implement sustainability programs for data center infrastructure by 2027.
Using a cabling project for an 80 MW facility for Energie Baden Württemberg in Longenenslingen, Peker demonstrated how Panduit’s solution reduced installation costs by 45%, doubled implementation speed, and offered a 20-year warranty on components. Safety was also highlighted: innovative cable cleats allow installers to reduce steps such as pulling or cutting cables, minimizing injury risk and increasing efficiency.
Particular emphasis was placed on Panduit’s Nylon 612 cable ties, designed for extreme weather conditions. “Only Panduit offers a 20-year warranty on cable ties for harsh conditions. In Europe, we have 132 rainy days per year, plus significant temperature variations. Panduit has developed a product that withstands all these conditions,” Peker stated.
The final, highly engaging presentation on the transformation of smart buildings was delivered by Jorge Neyton Avila
A standout innovation that impressed the audience was Panduit’s Fault Managed Power System (FMPS), a power distribution technology combining low-voltage safety with high-power delivery over long distances. It is the world’s first Class 4 power system certified under UL 1400-1 and IEC/UL 62368-1, setting new benchmarks for safe, efficient, and scalable energy distribution in complex infrastructure environments.
In the context of accelerated digital transformation in EMEA and growing IoT, smart building, and wireless network adoption, the need for reliable, efficient, and secure power systems has never been greater. FMPS delivers up to 600 W per pair of Class 4 copper conductors over distances of up to 2 km, with efficiency exceeding 97% and up to 60% cost savings on cabling and installation. It supports multiple hot-swappable transmitter modules, up to nine per chassis, and up to three hot-swappable power units, collectively delivering up to 4.8 kW per chassis.
FMPS uses pulsed power technology, sending energy via short impulses (typically 2 ms on, 1 ms off) over multi-strand Class 4 cables. Each pulse is monitored live to detect faults such as shorts, wire errors, overloads, or grounding faults. When a fault is detected, power delivery stops within 2 ms, greatly reducing shock or fire risk compared to traditional high-voltage systems. Integrated remote monitoring and management allow technicians to track consumption, manage components remotely, and minimize on-site interventions.
“This architecture is far more efficient because future buildings will use DC power. I believe this technology has no limits and will reach homes in the coming years. Today, energy is lost converting AC to DC and back. Fault Managed Power enables direct energy distribution. Even data centers will begin using it,” Pacheco noted, adding that tests for power delivery up to 2 kW are already underway, generating particular interest.

Pacheco, Senior Business Development Manager and expert in AI, smart buildings, and cybersecurity. Growing energy demand, grid limitations, and sustainability requirements necessitate fundamental changes in electricity distribution.
According to the International Energy Agency, global energy demand grew by 4.5% in 2024. At the same time, electricity prices are rising, and data centers are projected to consume 4–6% of total electricity in the near future.

Later this year, Panduit will also bring Eco cable ties to market, made entirely from recycled nylon, yet without compromising on quality or fire safety
In response, Panduit is developing nextgeneration Cat6 cables with an extended transmission reach of up to 150 meters compared to the 100-meter limit of cur-
rent Cat5e, Cat6, and Cat6a Ethernet cables. This will have an impact on multiple industries. “We are developing cables capable of delivering 90 W power and

PoE data over 150 meters. This expands the covered space from 31,400 m² to 70,600 m². When offering this technology, we aim for the highest quality,” Pacheco explained.
In addition, Panduit’s RapidID technology simplifies cable documentation using factory-embedded unique labels. This allows for quick documentation, verification, and cable tracing, saving time and costs and making installations up to 50% faster. It also reduces risk by eliminating manual data entry and enables the identification of all active connections, enhancing cybersecurity. “We cannot protect what we cannot see,” Avila emphasized, underlining the importance of physical infrastructure visibility as a foundation for NIS2-compliant security strategies.
Pacheco also briefly discussed Panduit’s cybersecurity strategy, which is built on three pillars. The first pillar, physical protection, is in fact the first line of defense. The second is network infrastructure visibility, which Panduit achieves by placing sensors inside cabinets, allowing administrators to see within seconds who is attempting to gain access. The third pillar is business continuity planning, encompassing a set of strategies, processes, and technologies that enable the rapid restoration of systems and infrastructure to operational status after a major incident. n
Intersec Saudi Arabia, which took place at the Riyadh International Convention and Exhibition Centre (RICEC) from September 29 to October 1, showcased a significant increase in scale and international presence, featuring a recordbreaking 434 exhibitors from 40 countries
n By: Walid Abdulmoti, Marketing Manager, Messe Frankfurt Middle East GmbH walid.moti@uae.messefrankfurt.com
The seventh edition of Intersec Saudi Arabia served as a vital meeting point for the global and regional security, safety, and fire protection industries, welcoming 23,894 visitors. This year’s edition recorded a 12.5% year-on-year increase in trade buyers, reaffirming the growing commercial significance of the event for the Kingdom’s rapidly expanding security and safety sectors.
With an expanded footprint covering 30,000 sqm gross across seven exhibition halls, Intersec Saudi Arabia 2025 presented the latest technologies and solutions across five sectors, which included Commercial & Perimeter Security, Homeland Security & Policing, Cybersecurity, Fire & Rescue, and Safety & Health. Riham Sedik, Exhibition Director, Intersec Saudi Arabia, Messe Frankfurt Middle East, commented: “With Saudi Arabia’s giga-projects and upcoming global events driving transformation across the security sector, this year’s Intersec Saudi Arabia proved instrumental in bringing together global innovators and local decision makers to help ensure these transformative projects are secure, resilient, and ready for the future.”

This year’s Intersec Saudi Arabia proved instrumental in bringing together global innovators and local decision makers to help ensure these transformative projects are secure, resilient, and ready for the future
The event’s conference program was a key highlight, featuring two flagship summits tailored to the Saudi market. The two-day Future Security Summit, powered by ASIS International – Dhah-
ran Chapter, brought together global thought leaders, policymakers, innovators, and industry professionals to explore the technologies, partnerships, and policies reshaping global security. Representatives from Saudi Civil Defense, the United Nations Office on

Drugs and Crime (UNODC), Aramco, FIFA, and Abu Dhabi Police, among many other leading organizations, highlighted vital topics at the Future Security Summit, including cross-border security, mega event protection, and the security implications of AI.
For the first time, all conference sessions were CPD-certified, offering delegates the opportunity to earn recognized professional credits while engaging with industry-leading insights
The Fire Protection & Technology Summit, which took place throughout Intersec Saudi Arabia, addressed the evolving fire safety landscape through impactful conversations with industry leaders, regulatory authorities, and international experts. This year’s edition included a groundbreaking new collaboration with the National Fire Protection Association (NFPA), which hosted a dedicated program on the second day of the event, delivering world-class expertise in fire protection and safety practices tailored to the Saudi market.

For the first time, all conference sessions were CPD-certified, offering delegates the opportunity to earn recognized professional credits while engaging with industry-leading insights.
Intersec Saudi Arabia is organized by 1st Arabia, licensed by Messe Frankfurt. Building on the momentum of this year’s success, the next edition of Intersec Saudi Arabia will take place from 6–8 October 2026 at RICEC. n
The 27th edition of Intersec is set to deliver its largest edition yet, with the show floor expanding by 11,859 sqm to accommodate a record-breaking lineup of over 1,400 exhibitors from more than 60 countries across five key product sectors
n By: Denver Lobo, Senior Marketing Executive, Messe Frankfurt Middle East denver.lobo@uae.messefrankfurt.com
Messe Frankfurt Middle East has officially unveiled the first details of the 27th edition of Intersec, which will take place from 12–14 January 2026 at the Dubai World Trade Centre (DWTC), with an expanded show floor to address record demand from the global security, safety and fire protection industries. Held under the patronage of His Highness Sheikh Mansoor Bin Mohammed bin Rashid Al Maktoum, Intersec is expected to welcome record numbers, with over 1,400 exhibitors from more than 60 countries and over 50,000 trade visitors. To address this increased global demand, floor space will be expanded by nearly 12,000 square metres, representing a 13% growth through the addition of two halls, and will now span 67,000 square metres of gross exhibition space.
The forthcoming edition is set to deliver an enriched programme and expanded features, with a remit to advance emergency response capabilities and secure digital and physical infrastructure. The event will welcome global leaders showcasing the latest innovative technologies and frontline solutions, aligned with the UAE’s vision for a secure and sustainable future, which has seen the country ranked safest in the world in 2025 by global aggregator, Numbeo. Dishan Isaac, Show Director of Intersec at Messe Frankfurt Middle East, said: “Intersec continues to set the benchmark for advancing global dialogue and partnerships


in security, safety and fire protection. The growth of the 2026 edition underscores the event’s role as a critical platform where industry leaders, innovators and government stakeholders converge to shape the future of emergency response and infrastructure protection. This expansion not only reflects the increased demand for cutting-edge solutions but also reinforces Dubai’s position as a global hub for security innovation and collaboration.”
The show will feature five redefined product sectors, including Homeland Security & Policing, Cybersecurity, Commercial & Perimeter Security, Fire & Rescue, and Health & Safety, reflecting the complexity and interconnectedness of today’s safety and security landscape.
Visitors can expect immersive showcases, pioneering product launches, high-level technical content, and business-critical networking opportunities. Key returning exhibitors include Hikvision, Hanwha, Transguard, Genetec, Gunnebo, Salto, and TP-Link, along with showcases from international pavilions from the UK, Germany, Singapore, Italy, France, and Sweden, among others.
Intersec 2026 will also present a dynamic conference programme, addressing the pressing issues of the global security, safety, and fire protection community. As part of the International Security Lead-

The event will welcome global leaders showcasing the latest innovative technologies and solutions, aligned with the UAE’s vision for a secure and sustainable future, which has seen the country ranked safest in the world in 2025
ers Summit, Fire and Rescue Conference, Health & Safety Conference, Access Control Theatre, and the SIRA Forum, global and regional experts will come together to explore transformative topics, ranging from AI in policing and predictive analytics in emergency response to workforce protection in high-risk environments and smart infrastructure security.

In line with a raft of national objectives and targets, including the ‘1 Billion Readiness’ initiative, which aims to train and raise awareness among one billion people worldwide on safety and fire hazard prevention, the Passive Fire Day, hosted by the Association for Specialist Fire Protection (ASFP), will spotlight the advancements being made in this area.
Eng. Khalid Al Khatib, Chief Executive Officer, NAFFCO, said: “As a global leader in fire safety solutions and a trusted strategic partner of Intersec, NAFFCO values the event as a driving force for innovation, visibility, and industry-wide engagement. Intersec stands out as a global premier event where we unveiled next-generation technologies, connected with decision-makers, and contributed to transforming the future of fire protection.” The event continues to enjoy the support of leading UAE government bodies, including The General Command of Dubai Civil Defense, the Security Industry Regulatory Agency (SIRA), Dubai Municipality, the Cyber Security Council, and the Dubai Electronic Security Center (DESC).n
Integrated Systems Europe (ISE) 2026, the world-renowned annual tech show for the audiovisual and systems integration industry, returns to Fira de Barcelona, Gran Via, 3–6 February, with an electrifying theme: Push Beyond. Prepare for a show-stopping experience that shatters boundaries and reimagines possibilities
n By: Charlotte Theobald-Park, PR Coordinator, Integrated Systems Events ctheobaldpark@iseurope.org
For the world of smart buildings and cybersecurity, ISE 2026 promises more than evolution, it is a leap into the future. Key conferences include the Smart Building Summit, spotlighting how technology is reshaping where we live, work, and connect and the CyberSecurity Summit.
A major new addition for the 2026 content programme, the CyberSecurity Summit is scheduled for Thursday, 5 February 2026. It will address the challenges facing the industry, as digital threats increasingly impact critical infrastructure, smart buildings, venues, and public services. As AV systems become increasingly networked and embedded in enterprise, public sector, and venue environments, they are exposed to the same vulnerabilities as traditional IT infrastructure, making cybersecurity a business-critical priority.
Visitors will see how integrated systems can transform buildings into responsive ecosystems. Demonstrations will reveal spaces where lighting, power, audio, and security interact seamlessly in real time. Key exhibitors include Technology Integration Partners (2J500), who will present a portfolio of design-focused technologies, with brands such as Domotz, Russound, and D-Tools, emphasising the interplay of

smart power management and precise network monitoring. ADI | Snap One + Control4 (2J150) will introduce robust platforms for networked control, automation, and remote management, supporting a wide spectrum of connected devices and use cases. The KNX Association (2J300) will showcase the latest in building control standards, setting benchmarks for interoperability, automation, and personalisation.
All this feeds into two of ISE’s defining mega trends for 2026: Smart Spaces and Cybersecurity. These are environments that adapt to people, integrate devices and data, and balance efficiency with wellbeing. At ISE 2026, you’ll see how the smart building ecosystem is
pushing beyond boundaries and the critical need for cybersecurity measures to protect them.
Sol Rashidi, the world’s first Chief AI Officer for enterprises, will headline ISE on Wednesday, 5 February 2026. Her keynote, ‘The AI Reality Check: What It Takes to Scale and the Future of Leadership,’ will expose the realities of AI beyond the hype, offering practical frameworks and highlighting the importance of AI governance and cybersecurity for successful scaling.
Registration for ISE 2026 is open - don’t miss your place at the forefront of connected living. Use our code ‘asmiddleeast’ for FREE registration here: https://www. iseurope.org/welcome/registration n
ISE 2026

Where endless potential begins.
Fira de Barcelona I Gran Via I 3 - 6 February 2026 A
The space to enjoy time to think. A perfect blend of feel-good and good-to-know. Our first-class content programme puts you first and upgrades what matters most: you. That way, we’ll grow beyond all expectation, together. Because if not now, then when? Deeper Knowledge is where endless potential begins. GET YOUR FREE TICKET Register with code: asmiddleeast at iseurope.org
Key Security Events in 2023
Black Hat MEA
2-4 dec, 2025, Riyadh, KSA RECC Malham https://blackhatmea.com/

Integrated Systems Europe
3-6 Feb 2026 Barcelona, Spain Fira de Barcelona, Gran Via https://www.iseurope.org

Intersec Dubai
12-14 Jan 2026, Dubai, UAE Dubai World Trade Centre https://intersec.ae.messefrankfurt.com/dubai

light+building
8-13 Mar 2026, Frankfurt am Main, Germany Messe Frankfurt https://light-building.messefrankfurt.com
SECON 2025
8-20 March 2026, Goyang-si, South Korea KINTEX www.seconexpo.com

The Security Event
28-30 Apr, 2026, Birmingham, UK NEC https://www.thesecurityevent.co.uk

LEAP
13-16 Apr 2026, Riyadh, KSA RECC Malham https://onegiantleap.com

ISNR Abu Dhabi
19-21 May 2026 Abu Dhabi, UAE ADNEC Centre https://www.isnrabudhabi.com



















Vendor-neutral Physical Security Information Management (PSIM) Bosch empowers you to build a
Advancis Middle East
P.O. Box 73309
Abu Dhabi, United Arab Emirates
Tel. +971 2 444 2503
Email: info@advancis.ae
Web: https://advancis.net


www.assaabloy.com/ae/en patricia.lomboy@assaabloy.com
Man Guarding
Technical protection
• Video surveillance
• Access control
• Intrusion detection
• Item theft protection
• IP and network solutions
• Perimeter protection
• Fire detection
• Gas detection
Mechanical protection
Cash/valuables-in-transit
Cyber security
Digital forensics
Software solutions
Smart home
Internet of things
Security management
Investigations
Building management
Market research
Legislation and standards








DUBAI
Technical protection
• Video surveillance
• Access control
• Intrusion detection
• Item theft protection
• IP and network solutions
• Perimeter protection
• Fire detection
• Gas detection
Mechanical protection
Cash/valuables-in-transit
Cyber security
Digital forensics
Software solutions
Smart home
Internet of things
Security management
Investigations
Building management
Market research
Legislation and standards
intersec@uae.messefrankfurt.com https://intersec.ae.messefrankfurt.com/dubai/ en/about.html