ASIS Ottawa panel discussion examines technology and pandemic trends p. 6 Hudson’s Bay Company takes top spot in cybersecurity contest p. 7

How security professionals can benefit from effective use of social media p. 27

ASIS Ottawa panel discussion examines technology and pandemic trends p. 6 Hudson’s Bay Company takes top spot in cybersecurity contest p. 7

How security professionals can benefit from effective use of social media p. 27











Young security professionals in retail, government, guarding, cybersecurity, finance and more share their stories
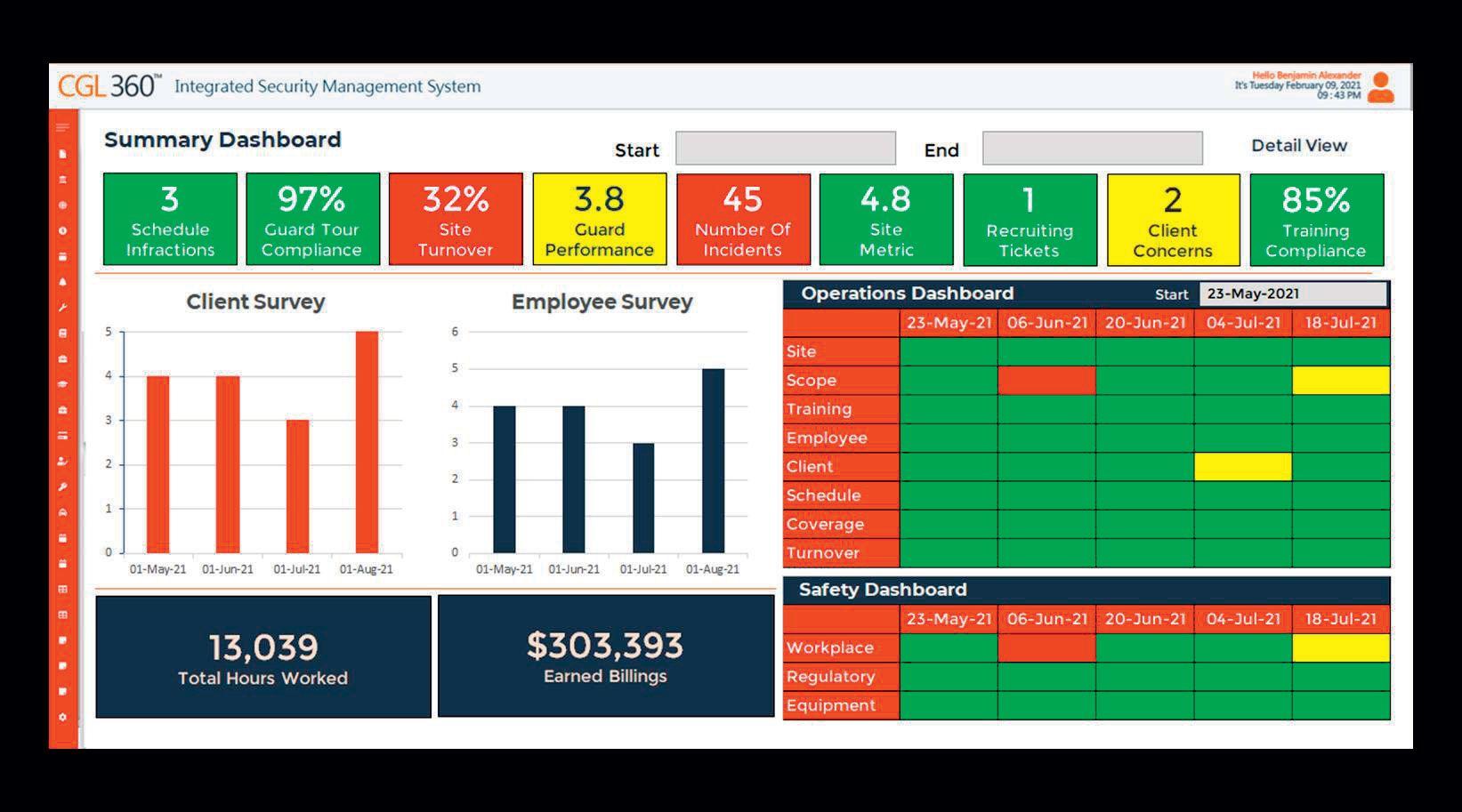
CGL 360™ is a fully integrated enterprise solution designed specifically for security managers. Using our intuitive cloud-based platform, we’ve automated virtually every process within the static guarding industry to measure and manage site performance. We believe in the power of data science to transform an industry that has been slow to innovate. CGL 360™ has become an indispensible tool to manage KPIs for contracted security providers.

Our solution includes a full suite of applications to manage:
Schedules
Post Orders
Timesheets
Incidents
Shift Logs
Checkpoints
Visitors
COVID 19
Recruiting
Training
Financials
Surveys
Floaters/Spares
Onboarding
Uniforms
Site Analytics
Motion Sensors
Projects
Security Guards ▪ Clients



By Neil Sutton and Alanna Fairey
By Pat Patton

By Suzanna Alsayed




IBy Neil Sutton
Knowledge sharing has never been easier or more welcome
recently participated in a virtual ASIS Ottawa chapter meeting, invited to speak as part of a larger panel discussion on technology trends in security and the impact of COVID-19 on the industry.
You can read more about the details of that meeting in our ASIS Update section on p.6. I remember I closed off my presentation by saying I was glad to be part of a meeting that, under more normal circumstances, would have meant me taking a roundtrip flight and a full day out of work.
“The removal of the stigma around mental health is just the first step.”
At this point — month 14 of the pandemic — many of us are looking for the proverbial silver lining in what is still a fairly bleak storm cloud.
Susan Munn, assistant regional vice-president (ARVP) for ASIS Women in Security and a member of the Ottawa chapter, noted during her presentation that it is important to recognize that the pandemic is a marathon. (I would add that we should take to heart that there is a finish line ahead — even if it’s not always clear how much further we have to go.)
All the panelists urged meeting attendees and security professionals everywhere to take advantage of the learning opportunities that have been given to them during this time.
Whether that means engaging with online education, taking a hard look at your policies in light of new work practices or perhaps more importantly, recognizing the urgent need for positive mental health programs and the provision of services to those who need it most.
I have heard the mental health crisis referred to as the “second pandemic” — but it is not one that can be managed through social distancing or vaccination programs. As was pointed out during the ASIS panel, the removal of the stigma around mental health issues is just the first step in another marathon journey.
About this time last year, we published several articles that focused on dealing with the initial onslaught of the coronavirus pandemic. And we also presented our annual Top 10 Under 40 list of winners.
It felt like a welcome respite from all the COVID news and a good reason to celebrate the accomplishments of young security professionals in Canada.
I’m pleased to say we’re back with our 2021 list, featuring another 10 deserving winners representing many aspects of professional security, from retail to government to cybersecurity and more.
Their stories reflect some of the positive changes that have occurred in professional security over recent years, and reinforce that education doesn’t stop with that first certificate, degree or diploma. Nor does it stop at 40! Thank you to the security professionals at all career stages who continue to inspire us with their dedication to life-long learning.


Reader Service
Print and digital subscription inquires or changes, please contact
Barb Adelt, Audience Development Manager
Tel: (416) 510-5184
Fax: (416) 510-6875
Email: badelt@annexbusinessmedia.com
Mail: 111 Gordon Baker Rd., Suite 400, Toronto, ON M2H 3R1
Group Publisher Paul Grossinger pgrossinger@annexbusinessmedia.com
Associate Publisher Jason Hill jhill@annexbusinessmedia.com
Editor Neil Sutton nsutton@annexbusinessmedia.com
Associate Editor Alanna Fairey afairey@annexbusinessmedia.com

Media Designer Graham Jeffrey gjeffrey@annexbusinessmedia.com
Account Coordinator
Kim Rossiter krossiter@annexbusinessmedia.com
COO Scott Jamieson sjamieson@annexbusinessmedia.com
Editorial and Sales Office 111 Gordon Baker Rd, Suite 400, Toronto, ON M2H 3R1 (416) 442-5600 • Fax (416) 442-2230 Web Site: www.canadiansecuritymag.com
Canadian Security is the key publication for professional security management in Canada, providing balanced editorial on issues relevant to end users across all industry sectors. Editorial content may, at times, be
as controversial but at all times serves to inform and educate readers on topics relevant to their individual and collective growth and interests. Canadian Security is published four times per year by Annex Business Media.
Publication Mail Agreement #40065710
0709-3403







Canadian retailer the Hudson’s Bay Company recently took first place in the International Cyber League (ICL), organized by Cyberbit, a cyber skilling platform headquartered in Ra’anana, Israel.
The Cyberbit platform delivers a “Zero to Hero” skilling, training and assessment solution on-demand. Stephen Burg, director of product marketing at Cyberbit, says ICL was conceived as an idea sometime at the beginning of 2019.

“We had said we wanted to start the Cyber League to find the world’s best cybersecurity team,” said Burg.
Analysts, incident responders, forensic investigators, threat hunters, and other specialized roles can be broadly classified under the category of “blue team.” Their purpose is to defend an organization from cyber-attacks and respond in the least possible time against such attacks. The “red team” consists of penetration testers and vulnerability assessors.
“There are no judges — the judge itself was the platform,” Burg explained. “The top six teams who knew how to communicate with each other, who had to work together without spoken communication but knew exactly what their partners were doing, created a much more time-efficient experience. That’s why these were our top teams — they could work together and they can talk together; they knew each other’s skills.”
Burg said the team from Hudson’s Bay excelled in all of the cyber skilling platforms.
“The Hudson’s Bay Company SOC and incident response team is thrilled and humbled to have recently won the title of Best Cyber Defence Team in the Americas,” said Omer Odabasi, security
operations centre senior analyst, at Hudson’s Bay Company, in an emailed response. “Cyberbit is an excellent simulation platform that provides handson practical experience.”
Burg was impressed by the quick response the Hudson’s Bay cybersecurity team demonstrated.

“These were people who were able to quickly identify an attack. They knew exactly what steps to take during an investigation,” Burg said. “Even though the steps were different for every scenario, they were able to identify the behaviours to the investigation and mitigate the attack in a very time efficient way, which is exactly what you want from your cyber defence team.”
The experience studying and preparing for the stimulated attacks was one that helped the team at Hudson’s Bay to build on their cyber skills and internal communication, according to Odabasi.
“The ICL was a priceless experience for me, especially working with my teammates Erik Mercado and Jorge Lozada,” Odabasi shared. “Live fire exercises are essential to help blue teams prepare for real cyberattacks. We look forward to continuing our hard work, and we thank ICL for recognizing our efforts.”
With over 100 organizations participating in this year’s competition, Burg hopes that next year’s ICL will expand to Europe and Asia, in addition to another competition in the Americas.
“We’re going to bring on more organizations, and we’re going to bring on new content,” Burg said. “Next year it’s going to be all new scenarios and an even bigger competition.”
— Alanna Fairey
May 26, 2021
Focus On Cyber Security Online www.canadiansecuritymag.com
June 9-10, 2021
Security Canada Virtual – Spring Online www.securitycanada.com
June 15-17, 2021
ESX Virtual Summit Online www.esxweb.com
June 22-25, 2021
IACLEA Annual Conference and Exhibition Online www.iaclea.org
July 19-21, 2021
ISC West Las Vegas, Nev. www.iscwest.com
August 22-26, 2021
BICSI Fall Conference and Exhibition Las Vegas, Nev. www.bicsi.org
October 4-6, 2021
ESA Leadership Summit Frisco, Tex. www.esaweb.org
October 7, 2021
Canadian Security Honours Online www.canadiansecuritymag.com
November 3-4, 2021 Sector Toronto, Ont. www.sector.ca
November 8-10, 2021
IAHSS Annual Conference and Exhibition Myrtle Beach, S.C. www.iahss.org
November 17-18, 2021
ISC East New York City, N.Y. www.isceast.com
December 2, 2021
Focus On Healthcare Security Online www.canadiansecuritymag.com


By Mark Seenarine
Porch piracy — thieves swiping consumer packages from doorsteps before their rightful owners can bring them safely into their homes — is on the rise. Here are some steps you can take to mitigate this type of theft, and what you can do if you become a victim.
Best practices
• Monitor communications from the retailer you purchased from for shipping status, ship time, arrival time, as well as photos from delivery personnel of packages placed in front of your door upon arrival. Minimize the time the package is left unattended.
• Redirect high value packages to a Post Office Box.
• Install a smart mailbox at the front of your home or request package drop off in the garage, side garden or backyard (a more secure location).
• There are cost-effective CCTV camera companies that can install day/night cameras, with 14 to 30 days video retention and mobile app to ensure your package is always on camera. Cameras will assist with
any potential investigations and serve as a deterrent. Cameras should not solely be relied upon to prevent theft nor do they always identify criminals. You can also utilize webbased doorbell devices that provide immediate notification and a video camera.
• It’s encouraged to create a trusted network and communication tool (WhatsApp, text or email group) to report suspicious activity as a neighbourhood watch.
• Contact your purchase retailer, as the package could have been delivered to the wrong location, still in transit or lost in transit.
• Review your own CCTV or if applicable, contact your building management to start an investigation to review video and building logs.
• Know your municipal police nonemergency contacts and online reporting portals for theft.
Additional considerations for condominiums and rental buildings
• Is there a space or location for
secured storage?
• Does your building have adequate CCTV camera coverage to monitor the continuity of the package, from delivery to owner?
• Does an on-site security guard or concierge accept the package in the lobby entrance? Or are packages left unattended in the lobby area or in front of your unit?
• Does your building have amenities/ package-tracking software? There are several software options available to property management.
• Due to the recent increase in online shopping, some buildings are allowing delivery drivers to go directly to the floor/unit and leave the package in the hallway in front of the owners’ door. Building managers are also considering installing CCTV cameras on each floor and increasing security guard patrols.
*Friendly reminder to break down your packages/boxes and recycle. Remember to first remove shipping/address labels to protect your personal identifiable information.
Mark Seenarine is manager, corporate security & loss prevention, Canadian Tire Corp.
Toronto-based Resolver recently previewed the newest version of its incident management suite, featuring AI technology designed to automate certain reporting features.
The suite is designed to reduce the time it takes to create incident reports, as well as improve data accuracy and cross-reference data to establish incident patterns.
The report writer is expected to tell a story in a narrative fashion when creating the report — the AI engine will automatically recognize details such as key actors, companies, dates, times, places, etc., and query that information against an established database.
In the event that the report contains a detail that is not already know to the database, the report writer can amend and tag it as necessary. The AI engine
will learn these details over time and with repetition, improving its recognition abilities with each subsequent report. A reference to a retailer, for example, could indicate a specific location or an entire company. Tagging it as one or the other will enable the software to identify it correctly in future reports.
“The goal of all this is to remove work from your security team and ideally just completely automate triage, seeing as we already have the data in the narrative,” said Resolver CEO Will Anderson during a live demo.
A key feature of the software is integration with Amazon Translate, allowing the report writer to input data in his or her preferred or local language, then have it translated into the organization’s operating language. Future releases of the software
will be able to recognize more report data such as vehicles and monetary amounts. Resolver is also working on an algorithm to set up flags like weapon involvement and EMT response, which could automatically escalate an incident as a priority.
Customers who have previewed the platform have asked for the software to be able to query the internet for specifics in addition to a closed database, said Anderson. That feature could be added to future releases.
“We want to help you do more with the resources you have and better illustrate the value you create for your organization. AI is not a be-all and endall of this, but it is a powerful technology that we will harness to drive the industry forward,” said Anderson.
— Neil Sutton




In the face of misinformation, clear, precise communication is paramount
What have we learned?
The first part of 2021 is behind us and we’re starting to see some positive changes — tempered with our race to vaccinate citizens versus the spread of new variants of COVID-19.
The virus is teaching us more lessons about vigilance, resilience and adaptability. These are lessons we need to consider as security professionals.
During the pandemic, we locked down our businesses and cities, stayed home, and restricted activities thinking we had some measure of control. These actions worked — for a while. Then, as we saw declines to the numbers constantly being published on news and social media, behaviours changed. Some began traveling, disregarding recommendations from global health professionals. Citizens began protesting the “lockdowns,” citing freedoms being compromised for “fake science.” And some of the most influential leaders in the world provided conflicting advice (at best) and downright dangerous comments (at worst) that further spurred the wrong behaviours.
And here we are, facing a third (or even fourth) wave of the COVID-19 virus being pitted against a number of fast-tracked vaccines that have faced shortages, delays in delivery, and nationalist approaches to restrict the distribution of vaccines outside of home countries or trading blocks. After all what we’ve witnessed these past 14 months, what lessons can we extract and learn from as security professionals?
Let’s start with data and science.

A foundational component of a riskbased, businessfocused approach to developing a security practice (like Enterprise Security Risk Management) is to make recommendations to reduce risks facing an organization based on data and facts — not personal opinion, or hearsay or rumours. We don’t
support our recommendations using social media memes, or the testimony of friends and acquaintances. We must rely on data.
Seeing how the citizens of cities and towns across the globe responded to restrictions to reduce the spread of the virus provides more insight into how people react to change, especially change invoked by organizations and governments.
We saw the collective response from people who don’t believe in science or vaccines, who felt their own personal freedoms outweighed the collective good of a town or city, and the refusal to apply simple controls to reduce risk: wear a mask, stay six feet apart, wash your hands. We reaffirmed the human element of any security practice is going to be the most difficult aspect to address in an ESRM approach.
Let’s apply this to our own ESRM-based security practice. We can’t assume employees will simply follow security standards, guidelines and procedures because they’ve been created and published. Nor can we assume that leaders in our organizations will fully understand the security risks facing our enterprises if we don’t objectively present these risks against our assets, goals and objectives.
Now we must spend more time collaborating with other teams to assess risks to assets. We need to spend far more time educating our employees about the role they play in our security program, and how security professionals are here to enable the business to achieve its objectives. We need to ensure we are transparent in our approach to assess risks facing our enterprise assets and provide practical, objective recommendations to reduce them. We have to spend time collaborating on our assessments and constructively challenge the data we collect to reduce our security risks.
We must take what we’ve seen and learned from this experience and focus on the human elements of our ESRM-based security practice. It will take work, it will be frustrating, and it will profoundly challenge us as security professionals. But it’s worth the effort.
Tim McCreight is managing director, enterprise security,



By Kevin Magee

Too many employers are looking for ‘unicorns’ to fill cybersecurity roles
Everyone in cybersecurity is talking about the skills gap and most agree it is a serious problem.
The thousands of cybersecurity job postings that go unfilled each week appear to confirm this, along with stories of employers fiercely competing for the seemingly handful of qualified candidates out there.
And yet, every day I meet plenty of aspiring cybersecurity professionals of all different ages and backgrounds with incredibly diverse educations, experiences, degrees and self-taught skills who would make excellent additions to our industry. All of them have amazing potential and display considerable passion and aptitude for doing the work.
competency who are ready and willing to take just about any role in cybersecurity that they can get.
Unfortunately, their qualifications don’t seem to align to the practical skills and depth of experience employers say they are looking for.
So, what exactly does “qualified” mean? Well, for starters, many employers seem to want highly educated and deeply technical prodigies who graduated with honours from a prestigious program and school.
“These trends have the effect of continually narrowing the pipeline of potential qualified candidates further and further.”
These are effectively the people that employers say they desperately need, but many of them are struggling to find jobs because they are considered unqualified.
I also regularly meet with colleges and universities across Canada that are seeing record applications and enrolment in deeply technical courses designed for what they believe will best prepare students for lucrative and fulfilling careers in cybersecurity.
These same schools are graduating thousands of students each year with significant academic proficiency and technical

In response, educators are designing academic programs to prepare graduates to meet this very narrow profile. Students who aspire to be cybersecurity professionals are gravitating towards these programs, which is consistently driving up admission acceptance rates.
As a result, many students who have the potential to make excellent cybersecurity professionals and contribute to closing the skills gap either don’t make the cut or selfselect out.
This doesn’t, in any way, account for the thousands of candidates who opt not to go to college or university, have backgrounds in other areas such as history, journalism or law enforcement as well as others looking to retrain or change careers.
In addition to top marks from top schools, many employers also believe qualified candidates should come complete with “Jedi” level skills on major vendor solutions as well as the coveted five-plus years of handson practical experience. This requirement even leaves many top graduates otherwise unqualified for most positions.
Employers are looking for, and often will accept nothing less than, “unicorns” and no one seems to want to take on the risk and burden of training inexperienced new graduates, forcing many to take whatever work they can find.
Overall, these trends have the effect of continually narrowing the pipeline of potential qualified candidates further and further while raising the bar of entry to the
profession ever higher — all while the number of open positions in the industry exponentially increases. This begs the questions, is the real problem that there are not enough qualified candidates to close the cybersecurity skills gap? Or, is what we perceive to be a skills gap simply a result of fragmented approaches and systemic challenges that persist in how we attract, educate, train, develop and ultimately hire the pipeline of talent for our industry? And, what can we do to fix it?
Stop talking about diversity as an aspirational goal and start thinking about it as an absolute business imperative.
If ransomware is a top concern for your organization, then engineering skills alone won’t mitigate this risk, but perhaps adding someone with a criminology degree to your team might. Employers also need to stop trying to buy their way out of the skills gap and start investing in diverse and entrylevel talent as a game changer and competitive advantage.
Educators:
Find more ways to get employers embedded in the development, delivery and ongoing assessment of your curriculum.
Industry advisory boards, engagement in student-led capstone projects, guest lectures and student mentoring can create considerable value and impact for everyone involved. Also, make sure to provide your students hands-on experience with vendor solutions by asking for licence and equipment donations, access to realworld training courses and finding other creative ways vendors can assist.
Candidates:
Hackers always find a way in! Don’t give up when you see “five-plus years experience” but look for the opening the phrase “or equivalent” often offers. How can you find ways to demonstrate you have the equivalent skills leveraging free online training, creating videos,
writing blog posts or presenting at cybersecurity meetups? Find ways to show employers what you are really capable of!
In order to solve the problem of the skills gap, we need to rethink what “qualified” really means.
Employers need to shift left well into the earliest stages of developing talent for our industry, partnering with
educators and supporting aspiring cybersecurity professionals throughout the earliest stages of their careers or risk continuing to perpetually compete with each other for the same narrowly defined profile of candidates who they deem to be “qualified.”
Kevin Magee is chief security and compliance officer at Microsoft Canada (www.microsoft.ca).



With the ANNT Hostile Vehicle Mitigation (HVM) K12 bollard a full-size, speeding vehicle is brought to a dead stop.*
• Versatile Operation: choose from fixed, removable, semi-automatic or automatic bollards.
• A Reliable Sentry: a single 275 K-rated bollard is certified to K/M standards.
• Easy to use: operated by key fob, RFID card, keypad or smart phone.
• Blend in: with your urban landscape with brushed stainless steel or powder coated in any RAL colour.


By Winston Stewart

Documentation and report writing continue to be crucial security skills
The security surveillance tools we have at our disposal today would have been the stuff of science fiction to our grandparents’ generation.
From biometric keypads to facial recognition software, our ability to monitor properties, protect people and either prevent or respond to crime has improved exponentially in the past decade alone. And yet two of a corporate security guard’s most important tools are still their report-writing skills and observational abilities.
While technology is indispensable and has truly revolutionized the security industry, in most cases it merely complements the services delivered by on-site security professionals.
case of an emergency or a criminal act. When the latter occurs, they need to be able to document what they see and report to the tenant, the property owner or manager and, in some cases, emergency responders such as the fire department or police.
The occurrence report is their information-laden summary of major events when a more involved response, review and debriefing effort is required.
“No detail is too small to record and no amount of information is too much to share.”
Increasingly, their role is to act as de facto corporate concierges, providing useful information to tenants and visitors alike, liaising with delivery teams or maintenance contractors and generally helping to set and maintain a property’s tenant experience. But their primary duty is still to protect, to pay attention, to remember faces, to respond to slip and fall incidents or accidents or, in a worst case, to be the first on the scene in the

The importance of the observational and reportwriting skillset simply can’t be overstated. A guard’s ability to compose a coherent and comprehensive site report — which documents incidents ranging from building damage to recording observations and flagging potential sources of danger, such as faulty mechanical componentry or icy sidewalks — is vital to helping address issues and ensure they don’t reoccur.
As we note in our training materials, no detail is too small to record and no amount of information is too much to share. If it seems even somewhat relevant, it’s worth reporting.
The general purpose of a properlywritten report is six-fold:
• To recreate an event
• To prevent the loss of relevant information
• To provide detailed accounts of events and to eliminate confusion
• To facilitate easier recollection of an event
• To inform appropriate parties of what has occurred
• To reduce the risk of hearsay evidence impacting an investigation
But it’s the quality of the report, the ability to produce a document that covers the 5Ws (who, what, where, why and when), that summarizes key details and is written in a way that aligns with the 5Cs of report composition (clear, concise, complete, correct, chronologically-ordered)
that differentiates both guards and the security firms that employ them. Those skills are not always inherent, nor should they be taken for granted.
Firms must ensure their personnel are adequately trained to observe the mundane and the unusual with equal attention to detail.
A guard’s engagement is key, which is why effective recruitment is so important for security firms.
to foster the right employee culture to get the very best from their staff, they need to have management structures in place that reinforce quality control and service expectations.
“A piece of technology has yet to be invented that can replace the talents of a security guard with a keen eye.”
Disengaged guards — spending shifts texting or talking on the phone rather than doing their job, for example — simply won’t see the same situation unfolding as will their more dedicated and attentive colleagues.
Security companies not only need


If poor observational performance is tolerated, it will become the norm.
The same goes for report writing. If guards aren’t trained and provided with the necessary supports to compose satisfactory incident reports — which is especially important if a portion of a firm’s workforce does not speak or write English as their first language — they won’t be able to perform to expected levels.
Onboarding and ongoing report-


writing workshops are essential tactics for maintaining quality, reducing guard turnover and ensuring value for corporate clients.
In the end, we should remember that security firms are essential first responders.
As such, firms have a responsibility to go above and beyond to ensure they’re not only covering the basics as service providers, but also doing what’s necessary to aid investigations, to create an exceptional atmosphere at the properties they protect and to engage with people in a meaningful, positive way.
Observing and recording are still essential tools to achieve those goals.
A piece of technology has yet to be invented that can replace the talents of a security guard with a keen eye and strong attention to detail.
Winston Stewart is the president and CEO of Wincon Security (www.wincon-security.com).








Canadian Security’s annual Top 10 Under 40 recognition program is back for a third year with another impressive roster of young security professionals. This year’s winners include representatives from guarding, retail, government, cybersecurity, banking and more. Once again, we were impressed not only by the quantity, but very high quality of nominations. These professionals are helping to lead in security through their work ethic and accomplishments, as well as other key factors that make all the difference, like mentorship, education, participation in associations, and a genuine willingness to help others succeed. Please join us in congratulating the 2021 winners. (Winner profiles by Neil Sutton and Alanna Fairey.)
LUANA PASCU, CYBERSECURITY RESEARCHER, FLARE SYSTEMS

Luana Pascu explored a few different career options — including selling magazine advertising — before she discovered her talent for cybersecurity research.
Intrigued by the inner workings of the criminal mind, she now spends much of her time on the dark web, frequenting chat rooms and message boards. There, she absorbs information and generates reports for her employer Flare Systems, a Montreal-based digital risk protection provider. Those reports help Flare’s clients better prepare their own cybersecurity processes and increase their awareness of the potential dangers lurking online.
Pascu’s path to cybersecurity also included a trans-Atlantic move. She emigrated from her native Romania almost two years ago and is now settled in the Ottawa area. “I liked that Canada was really starting to invest in the tech sector and cybersecurity,” she says. “At the time, it kind of felt like Silicon Valley was moving to Canada.”
Pascu is no stranger to international travel — she has also studied in Amsterdam and lived in the U.S. for two years as a child. The pandemic created some unforeseen challenges in terms of settling into life in Canada, but she is confident the move is the right one for her, particularly in terms of the number of professional opportunities for women.
Her cybersecurity background includes work experience in Romania with technology company Bitdefender.
She has also written for a Toronto-based biometrics publication and is one of the organizers of the BSides Security conference, with a Montreal event planned for later this year.
Pascu initially thought her interest in criminal psychology might lead her to a career in law enforcement, but she’s discovered her niche and has fostered an online persona that enables her to move around the dark web. “Basically I’m a completely different person,” she says.
While there is a growing recognition of the importance of network security, Pascu says she would like to see more resources dedicated to cybersecurity education and raising awareness.
“People are the weakest link,” she says. “It’s enough for someone to make a mistake and it can compromise your entire company.”
She would also like to see fresh approaches to security implementation — it’s unrealistic, for example, to expect most people to remember a dozen different passwords. “If we can figure out how to use biometrics in a safe way, this could be improved,” she says.
Pascu says she has found a home in Canada and plans to stay for the foreseeable future. She has discovered important professional relationships since settling here and has found a supportive mentor in Dominic Vogel, chief security strategist at Cyber.sc, whom she met via LinkedIn. She was also recently accepted to the Accelerated Cybersecurity Training Program, Rogers Cybersecure Catalyst in the RBC Women in Cyber Stream, at Ryerson University. Pascu hopes to return to Romania to visit her family as soon as COVID-19 travel restrictions lift.
KELPESH
Kelpesh Mistry joined Amazon almost two years ago as a loss prevention manager and has quickly made his mark. Initially, Mistry looked after Amazon’s largest Canadian facility in Brampton, Ont. Covering a maternity leave, he then expanded his role to most of Eastern Canada, including eight
fulfillment centres. In March, he was promoted to regional loss prevention manager, leading Amazon’s robotics team in Canada.
In addition to its more traditional approach to staffing fulfillment centres (with pickers and packers who prepare items for shipment), the company also operates robotics facilities, where robots scurry along the miles of warehouse space, locating and moving pallets of items.

Contrary to a popular misconception that these types of facilities are taking work away from human beings, Amazon’s AR centres actually employ more people, says Mistry. “Our AR buildings tend to be our largest and the biggest headcounts.”
Mistry has been involved in loss prevention for his entire career. A University of Toronto graduate with a communications degree, he took an entry level position at Best Buy as a receipt checker at the door. Enticed by the potential of a security career, he moved through the ranks of the company on the investigations side, ultimately staying for almost 10 years.
“It was really eye-opening. It showed me the impact that LP had. The role itself felt like a very meaningful career, especially in today’s marketplace,” says Mistry. “There’s few missions that are more important than protecting people, data and products.”
He also worked in loss prevention roles with Entertainment One, a distributor of film and TV media, and Home Depot, before joining Amazon.
Mistry’s role has been complicated

somewhat by the pandemic — as many security vocations have. “It’s everevolving,” he says. “We have to adapt our security protocols and practices to meet social distancing guidelines and ensure that our associates are safe. That’s our No. 1 priority — making sure that every security measure that we’re doing is taking into consideration the associates as well as adhering to local laws and recommendations from government officials as to how we should be operating in our buildings.”
While at Amazon, Mistry has also helped to drive several internal initiatives, including the promotion of diversity and inclusion within the company, as well as outreach with local law enforcement. “That’s a big focus for us here in Canada. We aim for every single one of our buildings to have strong partnerships with first responders,” he says.
Mistry has big ambitions to further develop his loss prevention career. “I’d like to be that senior director leading the vision for Amazon one day.”
VIKTORIJA GRAHAM, SENIOR MANAGER, PHYSICAL SECURITY OPERATIONS AND CRIME PREVENTION, TD BANK

was always meant to have a career in security, dating back to when someone hit her red car in the parking lot back when she was in high school.
“They had left this big mark on the bumper and I could tell that it was a white car. I went around investigating
to see which other white cars in the parking lot might have had red paint on them, and then marched into our vice principal’s office and said, ‘I want to see the video footage,’” Graham recounts with a laugh. “I’ve always been very interested in law and security. It wasn’t a surprise to me that this was the path I ended up choosing.”
Her current role at TD is one that marries her knowledge when she first joined the company 14 years ago and corporate communications. Her responsibilities include oversight of security and life safety incidents and “anything that happens within our retail and corporate locations.
“I’m also responsible for oversight of our vendor relationships on the guarding side as well, and to an extent with some of our other security integrator vendors,” Graham adds.
In addition, Graham represents the bank on external forums such as the Canadian Bankers Association. Graham says that she is responsible for attending and liaising with other people in the bank. “If they’re looking at making a change, they’ll engage us as a risk partner to see what the implications are from a security perspective,” Graham says. “I think we’ve done a really good job building our relationships with our partners in the bank.”
Working during COVID-19 has been an “out-of-body” experience, according to Graham, but she says there was a tremendous work effort that paid off. Graham was nominated for the League of Excellence, a major corporate award within the bank. She was also nominated for — and won — the Vision in Action Award, TD’s highest honour. Understandably, that was a major career milestone for Graham. She describes the past year as “the biggest in terms of my contributions” to the industry.
Looking ahead, Graham would like to continue to take on more senior executive level positions, as well as helping to build diversity and inclusivity in the industry. Graham also wants to be known for developing great leaders.
“Being able to speak in a passionate way about what I’m doing is incredibly important to me,” Graham concludes.
AMIR ATRI, REGIONAL DIRECTOR, GARDAWORLD

When Amir Atri was least expecting it, he found his calling to the security industry.
When he was in his senior year of high school, Atri was working at the Hudson’s Bay Company in Vancouver. During that time, he stopped a theft and the loss prevention manager expressed interest in Atri joining the security team. Although he initially had aspirations to be a paramedic or a nurse, Atri says that there was a natural progression to a career in security.
“That’s always kind of what I wanted to do — to help others,” Atri says. “I was always interested in trying to be that person that really goes above and beyond for somebody in their time of need.”
As regional director, Atri’s everyday tasks and responsibilities are “a good mixture” of mentoring those who report to him and a range of duties which include “managing our security account managers and folks that are servicing customers to supporting our finance and billing department in the branch, recruiting, scheduling and resource management.”
A large part of Atri’s job is to oversee GardaWorld’s 5,000 Security Services employees in the Greater Toronto Area, meet with customers, share advice and act on client feedback. Due to the pandemic, most of these meetings have moved to an online platform.
Atri shares that he recently started an internal study group to help staff prepare for ASIS International’s Associate Protection Professional (APP) credential,
with about 30 GardaWorld managers attending. Atri, along with colleague Alan Cakebread, will be teaching that course over 10 weeks. “It’s certainly a certification that we strongly encourage all our managers to achieve,” says Atri.
In addition, Atri teaches at Seneca College for their police foundations program.
True to his desire to help people, Atri aims to continue to be a mentor for young professionals and help them develop their skills. “I’ve worked with a number of different people and part of the joy that I have is seeing others succeed — so bringing people up and watching them grow, especially if they’re excited and they want to stay within this industry,” he says.
As Shopify’s physical security lead, Cory
Oliveira leads his team to look after the physical security of their office spaces.
When COVID-19 forced everyone to work from home, Oliveira and his team had to pivot their strategy and adjust to the new normal.
“A year and a half ago, before the world ended, nobody would have asked, ‘Do you feel safe at your apartment? Do you feel like you can do your best work at home?’” Oliveira

says. “An entire new set of challenges has taken its place, which has definitely been an interesting experience and then an interesting challenge.”
Reflecting on his career in the security industry thus far, Oliveira is most proud that he was able to get his Physical Security Professional (PSP) and Certified Protection Professional (CPP) certifications before he turned 30.
Receiving his PSP was made all the more meaningful when he took the test shortly after his mother passed away in 2017.
“It was one of those situations where I’ve been studying for it and talking about it and after everything that happened, I didn’t want to give up on it,” Oliveira says. “It was more of a ‘now I have to do it.’”
Working out of Shopify’s Ottawa location, Oliveira very much enjoys the company culture and the people he works with. While Oliveira one day sees himself 31

Critical Event Management for Today’s Uncertain World. The OnSolve Critical Event Management Platform enables you to identify adverse events, analyze the risks posed by those incidents without human intervention, rapidly communicate to key stakeholders and activate response teams overseeing incident management quickly and accurately. You’ll have the actionable intelligence needed to protect your people and operations and respond quickly when it matters most.

as a director and continuing to advance through the ranks, he is happy at Shopify.
“I’m not looking to go anywhere — I’m not in a rush, you know. I love where I am, I love the people I work with, I love what I do.”
SARAH MILLER, DIRECTOR OF OPERATIONS, SYNERGY PROTECTION GROUP

Working for a smaller company, Sarah Miller often “wears a lot of hats,” since her daily responsibilities vary on a dayto-day basis.
Miller started work at Synergy Protection Group as director of operations at the beginning of the new year, and begins her day checking emails before getting ready to come to work.
“I could be writing policies and procedures, I could be meeting with clients, I could be in our operations centre, doing recruiting discipline at any variety of things,” Miller says.
“It’s just what needs to be done, and I go do that and then move on to the next task.”
Outside of her day job, Miller has been involved with International Association for Healthcare Security and Safety (IAHSS), where she serves on the executive team for Ontario as the treasurer. Last year, Miller also began volunteering with the Toronto ASIS chapter as a mentor.
people,” Miller explains.
She sees so much value in mentorship in the industry that she is co-authoring a book on the subject with Brine Hamilton, IAHSS president-elect and a 2020 Top 10 Under 40 winner. The book will be coming out later this year.
“It’s really important to find a mentor,” Miller says. “At the beginning of my career, I did not have one and I did not advance very quickly and I didn’t have anybody to bounce ideas or questions off of. It’s just so critical to be able to access people in order to make connections, learn from people and grow from there.”
He attended La Cité Collegiale in Ottawa, graduating from their security management program, and participated in a government co-op. That led to his first official engagement as a casual employee at Public Services and Procurement Canada (PSPC). He moved on to the Canadian Food Inspection Agency as a screening officer before returning to PSPC, where he attained his current management role.
Before the pandemic, his Ottawabased team would travel frequently to help conduct security inspections for government contracts across Canada. The adjustment to working from home has been quite smooth, says Racine, since his department was already paperless and his staff accustomed to working remotely. In some cases, onsite inspections have moved to virtual walkthroughs.

30 employees, managing inspectors who conduct physical and IT security inspections for private industry which stems from a government contract, and screening contractors to work with the government.
The team also meets regularly through Microsoft Teams — weekly for senior staff and monthly for the entire group. The check-ins have been an important way for Racine to make sure his team are well and in high spirits. “It’s to see how they’re doing… what’s going on and it also gives me the ability to connect with the staff and verify what I can do to support them as a manager.”
He also promotes a positive attitude towards mental health in the workplace. “If I have a broken arm, I’m going to go to the doctor and get it treated. It’s OK to think the same way if you have a mental health issue,” he says.
“[Volunteering as a mentor] has been exciting as well. I’ve spent so much of my career as a mentee because I’ve only been in security for about seven years, so I find a lot of opportunity to learn and now I can finally pass that along to other
Spring 2021 • www.canadiansecuritymag.com
Those projects could be relatively small, like a translation company hired to translate sensitive information, or a major undertaking, with a large business working on a national defence project, or a public-private partnership (P3). “We ensure that all security measures are in place for our government clients before private industry can begin their work,” explains Racine.
Racine started working for the government right out of school.
Racine encourages his staff to get involved with security associations and fosters an environment that promotes mentorship opportunities. “I want to create a positive-impact environment for young professionals. When I started as a student, I didn’t know anything about the government. I want to be able to show young professionals that this could be a great career for you,” he says.
He represents the Industrial Security Sector-PSPC at the federal government’s Advisory Committee of Physical Security (ACOPS), a group led by the RCMP that also includes senior security representatives across the government. “We fought to be at the table,” says Racine.


Focus On Cyber Security will offer key takeaways from industry experts that attendees can apply to their own businesses.
Sessions will include:
• Cyber security risks faced by businesses today and how cyber leaders are addressing them
• Working effectively with law enforcement on criminal cyber investigations
• Mitigating insider threats and promoting cyber hygiene in the workforce

VICTORIA GRANOVA, SENIOR INFORMATION SECURITY CONSULTANT, CIBC

Victoria Granova discovered her abiding interest in cybersecurity as the result of an early pivot in her career.
Granova’s first professional engagement was as an accountant working for a mid-size accounting firm. When that company sought more cybersecurity expertise, it looked inward and tapped into Granova’s enthusiasm for new knowledge.
She took a part-time Certificate in Cyber Security at Toronto’s York University in 2016 and began to design policies and awareness programs for her employer. “As I was studying, I felt a passion for learning again,” she says.
Granova moved into cybersecurity, becoming the company’s security awareness officer in addition to her accounting duties. In 2017, she wrote the CISSP exam from (ISC)² and joined the organization’s Toronto chapter in 2019 as a board member. In 2020, she successfully ran for chapter president and is currently in the second half of a two-year term.
She has also taught several cybersecurity courses at York — initially as an assistant and now as full instructor, providing a two-week intensive training session for a cybersecurity operations management course.
Granova joined her current employer, CIBC, in early 2019 as a senior information security consultant. She describes her role as helping to coordinate the communication process
for security incidents that impact multiple departments across the bank’s organizational structure. “There’s constant learning. But particularly in my role, no two incidents are the same,” she says. “I get to learn constantly and meet new people as well. It’s such an amazing industry.”
Last December, Granova launched a new cybersecurity event in cooperation with the Toronto (ISC)² chapter.
A free, all-day, virtual seminar, the CyberToronto Conference included a keynote address from former Ontario Privacy Commissioner Ann Cavoukian and internet privacy lawyer Parry Aftab, as well as sessions presented by the ASIS Toronto chapter, Leading Cyber Ladies and OWASP Toronto (the Open Web Application Security Project). Another conference is planned for later this year.
Granova has also found time to further her own education and is currently taking a psychology certificate at Ryerson University — which is really
an appetizer for her impending PhD studies, also at Ryerson. She plans to pursue the doctorate on a part-time basis starting in the fall; it will once again focus on cybersecurity but with a “human centric” approach that encompasses aspects of psychology and business studies.
Fully engaged in a busy professional and academic life, Granova says she is fortunate to be surrounded by a strong network. “I have a really great support system,” she says. “My family is amazing; my workplace is also amazing.”
She’s also grateful to the many mentors she has discovered along her cybersecurity journey, among them Neil Begin, Jeff Clark, Ali Khan, Gaurav Kumar, Jennifer Laidlaw, and Dr. Atefeh Mashatan, who will act as her PhD supervisor at Ryerson.
Granova has also implemented a mentorship program at (ISC)² Toronto. “Mentorship is a wonderful, wonderful thing,” she says.



Pat Patton, director of security and operations, University of Regina, shares her research on the underrepresentation of women in security leadership roles
By Pat Patton
Ihave been lucky enough to spend my entire career (34 years and counting) in the world of campus security.
Starting at the University of Saskatchewan, fresh out of the Justice Administration program (as it was known then) and Mount Royal University in Calgary, I wanted to work in the security or policing field.
As a woman in this industry, while I wanted to be treated the same, the journey I went through was not the same as my male colleagues. I had wonderful male mentors throughout my career but I found out that a woman working in the same style as a man was not perceived the same.
When I tried to lead or work like my male colleagues, I was called “too abrasive” or “bitchy,” but men who used the same techniques were “tough” and “determined.”
I had the opportunity during my recent MBA studies at the University of Regina to dive deeper into this subject and explore what path we might take in the security industry to create more opportunities for women to get into leadership roles.
During the research for my final capstone project, I interviewed seven fabulous women leaders from the campus security industry. This information added to the academic literature I was able to explore. While my main focus was on the campus security world, I am confident that we can easily transfer this information to all areas of security and law enforcement.
The topic of barriers for women entering into leadership roles has been studied widely in academic literature. According to Statistics Canada in 2016, while
women make up slightly more than half of the population in Canada, 77.5 per cent of women are in the paid workplace versus 85.3 per cent of men.
According to Christy Pettey in her 2019 article “Embrace Gender Diversity and Risk Management Roles,” only 25 per cent of executives are women in the profession of security and risk management. So what is keeping women from reaching leadership levels in the world of security? Through reviewing academic literature and interviewing subjects, I looked further into this subject and I will provide a summary of what I have learned.
It appears clear that having more women in the workplace provides increased diversity, better reflecting the community we live and work in and is a positive business strategy for many reasons. Mainly, diversity provides different perspectives in thinking. It provides workplaces with the ability to bring different experiences and thoughts together to deal with issues and concerns in unique ways. Businesses that are representative of the people they serve can make better decisions and policies to support marginalized people.
A common thread through the various types of security/law enforcement occupations is that women are underrepresented in policing and security front line staff ranks (the pipeline to leadership roles in the security industry). When the number of applicants with required education and experience is so small, this creates recruitment challenges for women. In particular, my interviews confirmed three key barriers for women leaders in campus security, and I suggest more broadly in the security industry as a whole. The barriers I found were not surprising to me: work-life balance, leadership style and workplace culture.
Work-life balance suggests that female participants are required to fit into male-dominated work environments and may therefore face longer than average hours and harsher environments than most female-dominated roles. For
example, in construction and policing, workers identified as high performing, and work more than eight hours per day, which conflicts with traditional roles placed on women as the primary caregiver of children and lead person in household tasks.
The issues of family obligations for women in policing/security, identify that child care and traditional domestic roles are still a problem for women who want to progress to leadership roles. Society has traditionally supported the masculine role in the workplace as the primary bread earner while the feminine role was more expected to perform the domestic role. In my early career, it was expected that I would be the one to take time off for sick kids, etc., while my spouse travelled and it would have been frowned upon for him to do the same. I felt the expectation was on me to arrange child care and work around my shifts and needed sleep periods.
It is true that challenges of shift work and long hours are apparent in female-dominated roles such as nursing as well. We do, however, see that society penalizes women in occupations like nursing in maintaining the role of prime caregiver of children when the same domestic work is not expected as much of men in occupations of shift work and long hours.
In a study of single parents on family arrangements for Stats Canada, 79 per cent of single parents are women compared with 21 per cent men, accentuating the challenge faced by women.
The issue of shift work being a challenge for women entering male dominated work becomes even more problematic when combined with other barriers. In my assessment, industries that are male-dominated may not have had to face the issues connected to child raising/family care pressures as much as
those in occupations that are dominated by women.
Callouts for emergency advising at odd hours, high-pressure situations and the male-dominated environment still offer challenges around family care to the leadership roles in the security world. However, the gender bias is still apparent in performance of jobs needed to progress to leadership roles. Shift work is one factor that appears to be more of a barrier for women in policing and security roles. This was mainly due to family situations. It is the shift work in policing and security before getting to a leadership role that seems to cause the most challenges for women with children.
There is also evidence that men are seen to have a higher level of organizational commitment in shift work roles indicating that it may be more socially acceptable for men to put in the long hours necessary to forward their career. If women do not gain that work experience on the front line, it is difficult to stay in the pipeline occupations leading to leadership roles.
Men and women differ in their leadership styles. In 2002, Eagly and Karau noted in their article “Role Congruity Theory of Prejudice Toward Female Leaders,” men are typically agentic (assertive and confident, more transactional) in leadership style, while women usually lean to a more communal (helpful and kind; generally showing significant concern for the group, more transformational) style. Society’s vision of strong leadership is typically associated with agentic leadership and not communal leadership. These norms create barriers for women who try to lead in a role traditionally used by men and, in fact, may actually penalize them in their efforts as they are not using their natural style and may be seen violating social norms. This is where I would reflect on the example I provided at the beginning of this article. My attempts to emulate the leadership of male mentors was not always seen in the same light and in my opinion, harmed my ability to lead. The formal structure of security lends itself to a more transactional style
of leadership based on basic exchanges and transactions between a leader and follower while transformational leadership involves more engagement and involvement between the two. The transactional form of leadership seems to be the predominant model in paramilitary roles taking into account the formal “topdown” structure.
This authoritarian style leaves minimal room for a transformational style or communal style that may be suited better to women leaders. Despite this, the academic literature shows transformational leadership is seen as one of the most effective forms of leadership. Having more women in leadership roles with a different “natural” style may help with the movement from transactional to more transformational leadership styles. Although the military-style leadership of command and control is needed in times of crisis, it is not as organizationally efficient outside of crisis situations and sometimes it fails to adequately motivate and incentivize employees.
often did not have the consistent role model or support system that their male colleagues had.
There seems to be some opportunities to encourage change and create leadership opportunities for women in security. First, increase mentorship opportunities in pipeline education and occupations leading the industry. This would focus on providing female role models for young women looking to advance their career and build their confidence to compete for leadership positions.
“The vast expanse of opportunities of the security industry is often unknown to students who as a result cannot picture themselves leading a security team.”
Second, raise the profile in the law enforcement and humanities education programs of the security industry. It is very apparent that this industry is not well known or seen as viable a career option for women. The vast expanse of opportunities of the security industry is often unknown to students who as a result cannot picture themselves leading a security team.
In the case of workplace culture, women must try to fit into a work environment that is hyper-masculine and not as supportive for women if they wish to ascend to a leadership role. The maledominated culture in the security/policing industry makes it a challenge to women’s legitimacy in the workplace. In looking at the workplace culture in security, it is noted that the lack of women mentors makes it very difficult for women to see themselves working in a leadership role. The women I interviewed often spoke of powerful male mentors they had in security or policing but a scarcity of strong female leaders in the industry. They mentioned that they could take bits and pieces from each male mentor, but
The third recommendation is to provide leadership training for women by women. This training should focus on enhancing the leadership traits inherent in women while also teaching them how to balance their natural leadership style to a style that fits within the setting of a traditionally male-dominated occupation.
Recognizing the barriers and working to minimize or eliminate them is important in diversifying our workforce. I have been lucky to have a very exciting and fulfilling career in this industry and I am thankful for the men and women I have had the good fortune to work with. But, looking at the barriers of work-life balance, workplace culture and leadership style, it is hoped that this recognition might create career options where more women are better able to flourish and move into leadership roles.
If you’re not active online you’re missing out, but treat this like any project and plan accordingly
By Suzanna Alsayed
Nowadays, there are a myriad of social media platforms available for professionals and companies to use.
I have received many inquiries on how social media platforms should be utilized in the security industry, what they can offer a security firm, and if they can help a business grow or scale.
These are complex questions because there is no single answer. The answers ultimately depends on your business, product, service offerings, targeted audience, and your ability to be versatile. Just like a business is focused on a specific scope, social media platforms function in the same manner, requiring different skills and content that target different demographic groups.
No matter the size of your security business, if you are not on social media, your business could be missing out on potential clients, leads, brand exposure and opportunities to engage with your audience in a personalized way. In fact, using various platforms and even investing in ads, can be a fruitful combination for a security company!
This article will shed light on social media platforms and their benefits, and discuss how these platforms can be adopted in the security industry.
One of the first things that a security business or security professional needs to identify when choosing a social media platform is their target audience and why a particular platform is the best tool to reach one’s business goals.
In order to be successful in any business, you need to
understand your customer, who they are, how they tend to spend their time online, and what content they search for.
You need to ask yourself the following questions:
1. Why is social media the best tool for you to generate more leads and business awareness?
2. Are you going to use it to sell services or only build awareness?
3. What social media platform(s) do your existing or future customers prefer? How frequently do they dedicate time to browse this platform? How much time is spent daily on the platform?
4. How do your customers process information? Through writing, imagery or video? How would they like to find out about your company, services or products?
At the end of the day, you need to identify in detail who your consumer is, prior to even beginning your social media approach, in order to ensure that your chosen platform enables you to properly reach and engage your audience.
When looking for a social media platform for your business or to build your personal brand, be sure not to spread yourself too thin and tackle every possible social media venue. In fact, it is not necessary to be on every available platform. One needs to understand that each social media platform should be approached like an art but tackled mathematically.
I recommend utilizing one or two social media platforms before expanding or adding additional forums to your strategy.

If you or your business can decipher and utilize even just one platform efficiently, that alone can produce significant business results.
LinkedIn appears to be the preferred and most utilized platform for the security industry from my own observations.
Individuals that use the platform are open to networking opportunities, hearing different business pitches, as well as are seeking ways to make their work easier.
LinkedIn primarily adopts the B2B and B2C model. Professionals on the platform tend to be more business-minded and willing to learn. They update their profiles, employer information, job position, and contact information on a regular basis in order to maintain their professional personal brand. Additionally, creating a LinkedIn company page can help you to expand your network reach, find prospects or leads, as well as establish a public image on a global scale as a trusted and legitimate organization.
does reach out to you, you can set up a personalized automated message. Having an automated messaging system provides reassurance and more trust. Hence, accessing both Facebook and the Messenger feature can aid in adding another layer of trust and reassurance for your current or prospective clients.
“This is something that needs to be worked on consistently, just like any other aspect of your business.”
Instagram is owned by Facebook and as such it possesses a similar user base, advertising, and most recently an e-commerce platform. However, compared to the other platforms above, Instagram is more visual and relies on posting photos and videos.

Depending on your strategy and services, your business can benefit from Instagram by telling your brand story in a visually unique and engaging manner. You can share with your audience what inspired you to start a security business, how it came around, what were the ups and downs of your journey, showcase your services, client testimonials, and how your business impacts and safeguards the lives of others.
Thus, if your security business prefers to target consumers based on job titles, company profile, and within a specific company or industry — LinkedIn might be the perfect platform for you!
Facebook and its advertising platform are sophisticated marketing engines compared to other social media platforms currently on the web. On Facebook, you can target your audience by age, gender, hobbies or interests, career, relationship status, and even analyze different groups by their purchasing behaviours and previous engagements. If someone or a business is seeking to acquire new clients, Facebook will give you the power to approach your exact target audience, as well as post ads and develop content that can be published on your audience’s newsfeed. However, with Facebook, you need to pay-to-play. Professionals or businesses will have to set an advertising budget aside to reach their targeted audience in an easier manner.
Security businesses that provide guard management services, consulting services, or sell a security or artificial intelligence software, can benefit from Facebook advertising. As I like to say, everyone needs security, and sometimes a client does not even know they could benefit from having security services until they see or experience it.
Additionally, Facebook Messenger can be utilized as a resource. For instance, when a user clicks on your ad, they will be sent to your Facebook Business Page to find out more about your offerings or diverted to your Facebook Business Messenger to start a conversation with you. If a potential or current client
YouTube is a video-based social media platform that allows its users to watch and upload videos. It has over 30 million active users on a daily basis, who are likely to watch or stumble upon your company’s content. YouTube is actually owned by Google, and thus, you can use Google’s advertising platform to run YouTube ads on your videos.
YouTube is occasionally used in the security industry. Most often it is employed to promote conferences and social events, and showcase security professionals. It has also been used to conduct interviews.
So why aren’t more businesses taking advantage of the YouTube platform if it grants such exposure? It takes a lot of work to get YouTube to work to your advantage. Your business will need to invest time and money in order to produce original content. It could entail acquiring video equipment and creating a filming set up, including proper lighting, microphones, cameras, and even video editing software. Production can become time consuming and impact your business’ budget, however, it remains an effective tool to showcase your company highlights.
Twitter is another platform that is popular within the security industry. It can allow professionals to see real-time events and occurrences, but also reshare work and articles with their following. In simple terms, Twitter is like sending a text message to the entire world. There is a challenge with the platform, however, as you can only express yourself in 280
characters or less. A message needs to be crafted distinctively and concisely.
A business can benefit from using Twitter because it exposes them to new potential leads through the use of hashtags. It is also similar to a feature found on Instagram where you can search a specific hashtag and find other posts and content from current and potential consumers — even competitors.
Social media platforms should be approached like an art, thus, before you jump into creating different profiles and accounts, be sure to also consider these factors:
• What resources (and budget) do you have for this new venture?
• How much time can you dedicate to social media strategizing? Will you hire someone to maintain your social media platforms or do it yourself?
• What are you tackling? Brand awareness? Traffic? Or methods to boost your revenue?
Once you have identified your platform(s) of choice, ensure that you stay on top of the trends and updates, and continuously adjust your current social media strategy. These are not oneand-done tools, this is something that needs to be worked on
consistently, just like any other aspect of your business.
There are many social media platforms with a range of different users that can benefit your security business and the goals that you are trying to achieve. Even if there is no single answer on what the best platform for a security business is, identifying your target audience, branding your product or service, and dedicating a specific amount of time to social media can get you closer to a unique solution and strategy.
No matter the platform that you decide to use, ensure that you invest time into crafting a strong marketing strategy and that you post consistently. Remember to have fun with your content and regularly engage with your audience. This can be done through running contests, advertising special offers, hosting live video events, sharing exciting updates or news and much more.
The best way to ensure that social media brings value to your business is to take the time and devise a strategy that includes all of the platforms that you are planning to use, the kind of content you want to produce and share, and why this avenue of promotion will benefit your security businesses and services.
Suzanna Alsayed is the founder of Evolutz (www.evolutz.com) and Hilt International Security (www.hiltsecurity.com).




LenelS2
Elements is a cloud-based, purpose-built access control and video management system delivered as a software-as-a-service (SaaS) solution. The Elements system is designed to be easily installed and simple to use with a mobile-first, intuitive user interface. Information is available at any time and accessible from anywhere on any device. As a unified solution, the Elements system includes video management functionality, providing system configuration, real-time video verification of alarms and events as well as the ability to view live or recorded video. LenelS2.com
March Networks

X-Series Hybrid Recorders deliver a 400 per cent increase in throughput over previous generation recorders. It is a true hybrid platform supporting a mix of analogue, HD analogue and IP channels, but with the power and storage capacity needed for demanding all-IP installations. Available in 16, 24, 32, 48 and 64-channel configurations, the embedded, Linux-based appliances also feature a dedicated AI engine and SoC technology from NVIDIA. The X-Series platform comes preconfigured with March Networks’ next-generation video management software, which supports future add-on applications like face recognition, as well as features such as object detection, classification and search. X-Series also features a customized and embedded Linux OS which removes unnecessary services and applications and locks all non-essential network ports, reducing the likelihood of attack.
www.marchnetworks.com/x-series
Hanwha Techwin America
The XNF-9010RV is an ultra-high-resolution fisheye camera with 12MP sensors, and is equipped with Wisenet 7, which offers extreme WDR, noise reduction, onboard dewarping and enhanced cybersecurity features. The XNF9010RV fisheye camera can provide 360° monitoring with a single camera and stereographic lens to offer high quality images. The lens ensures high resolution images in the centre and on the edge of the lens. The enhanced WiseIR (infra red) allows users to adjust the IR level of the images’s centre and edge regions independently for different monitoring environments, minimizing light over-saturation caused by the movement of objects or reflections on walls. The camera supports automatic control of IR intensity and up to 150° IR LED for monitoring during day and night. www.hanwhasecurity.com

Bosch Security Systems
Bosch has introduced the first cameras based on its Inteox open camera platform starting with the MIC inteox 7100i. The new MIC inteox cameras share the same characteristics as the rest of the MIC camera family and support predictive solutions with machine learning, neural network based video analytics, and third-party software apps for customized applications. These Inteox cameras can be classified as “Driven by OSSA.” This distinction signifies that the cameras follow the Open Security & Safety Alliance Technology Stack for video security devices, ensuring connectivity with the Security & Safety Things Application Store. MIC inteox cameras range from a 4K enhanced model featuring optical image stabilization to a 1080p model in a base or enhanced version.
www.boschsecurity.com


Genetec states that its solutions are designed to help customers enhance cyber hygiene and respect privacy by making data and privacy protection features more accessible and configurable. Available on-demand for the Genetec Security Center unified platform, the KiwiVision Privacy Protector automatically obscures individuals’ faces caught within a camera’s field of view, so security operators only see what they need to see. Being able to access unobscured footage requires an additional layer of access permissions that is only used when an event warrants an investigation. An audit trail is then maintained that shows who accessed the additional information, and why.
www.genetec.com

VIVOTEK announced an update to its VAST 2 IP Video Management Software. VAST 2 comes with advancements including easy operation on single or multiple monitors, custom layout to accommodate both corridor and panorama orientations, rapid export of multichannel video, and the acquisition of VCA analytics and cybersecurity attack events from VIVOTEK cameras and substations in a hierarchal system structure. With the latest version (2.10), new VAST 2 features include: Embedded web browser on view cell; added watch list for easy management; evidence image of LPR cameras; and an access control solution.
www.vivotek.com
Allied Universal 5 www.ausecurity.ca Commissionaires 32 www.commissionaires.ca
Commissionaires Great Lakes 2 www.commissionaires-cgl.ca FutureShield 19, 25 www.futureshield.com/securitymag Johnson Controls 9 www.cloudvue.io
Systems Inc. 15 www.saltosystems.ca

Working with top educators to deliver a practical approach to professional certification programs.
Paragon Professional Institute (PPI), with expertise in physical security and asset management training, is pleased to announce its partnership with the University of Waterloo, and collaboration with professional educators from Schulich School of Business, DeGroote School of Business, Wilfrid Laurier University, and George Brown College in creating multiple registered professional certi cation and designation programs in the security industry.


Commissionaires offers a complete suite of services including threat-risk assessments, monitoring and response, mobile patrol, guarding and digital fingerprinting.